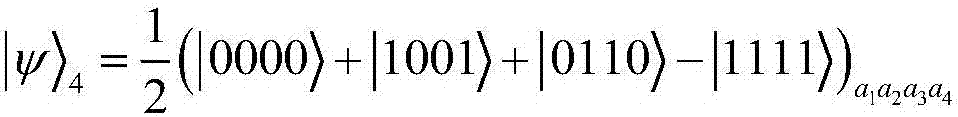Patents
Literature
143 results about "Cluster state" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In quantum information and quantum computing, a cluster state is a type of highly entangled state of multiple qubits. Cluster states are generated in lattices of qubits with Ising type interactions. A cluster C is a connected subset of a d-dimensional lattice, and a cluster state is a pure state of the qubits located on C. They are different from other types of entangled states such as GHZ states or W states in that it is more difficult to eliminate quantum entanglement (via projective measurements) in the case of cluster states.
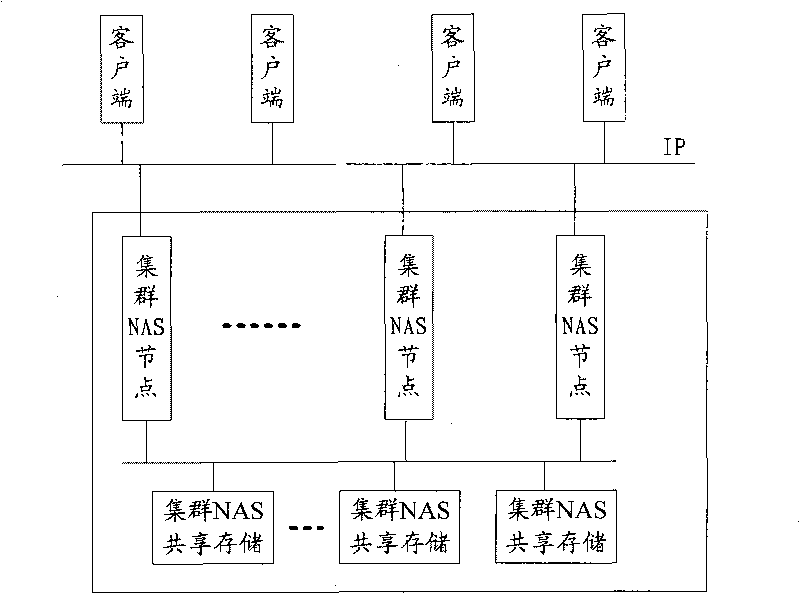
Network file system access method, device and system
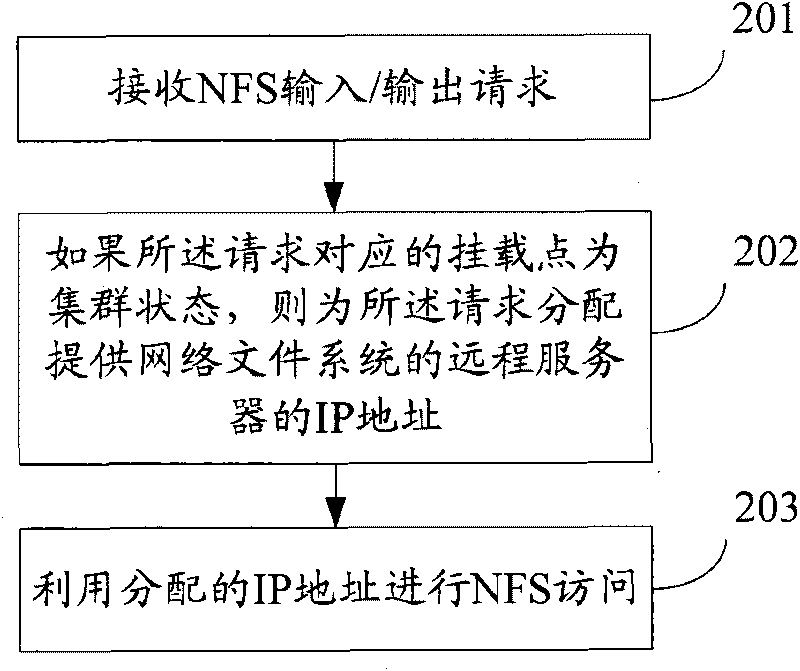
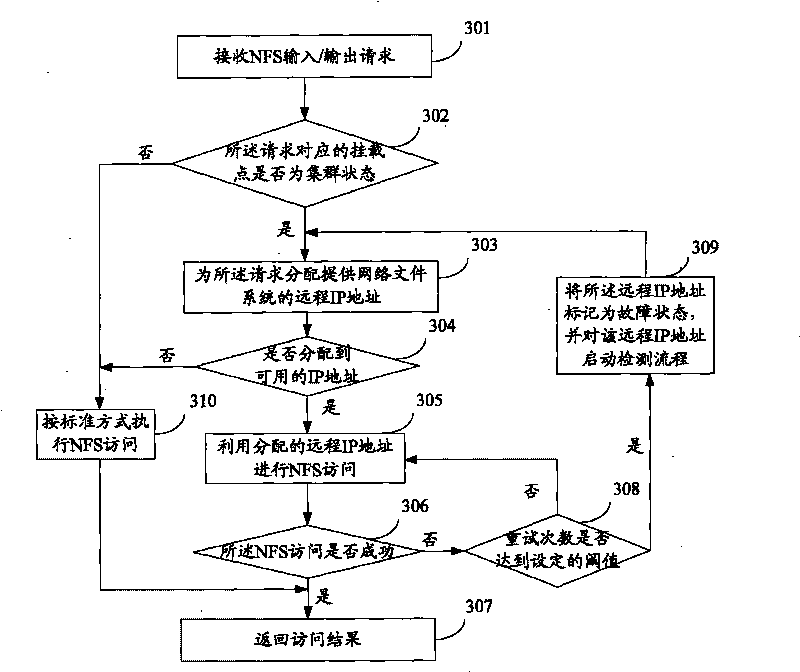
The invention relates to the technical field of cluster network attached storage and discloses a network file system access method and device. The method comprises the following steps: receiving network file system input / output request; if the mount point corresponding to the request is in cluster state, distributing the IP addresses of the remote server providing the network file system according to the request; and utilizing the distributed IP addresses to perform network file system access. By using the network file system access method, device and system of the invention, a plurality of different cluster NAS nodes in the cluster can be selected for NFS shared access so as to realize the load balance among the cluster NAS nodes and the maximization of the resource utilization.
Owner:CHENGDU HUAWEI TECH
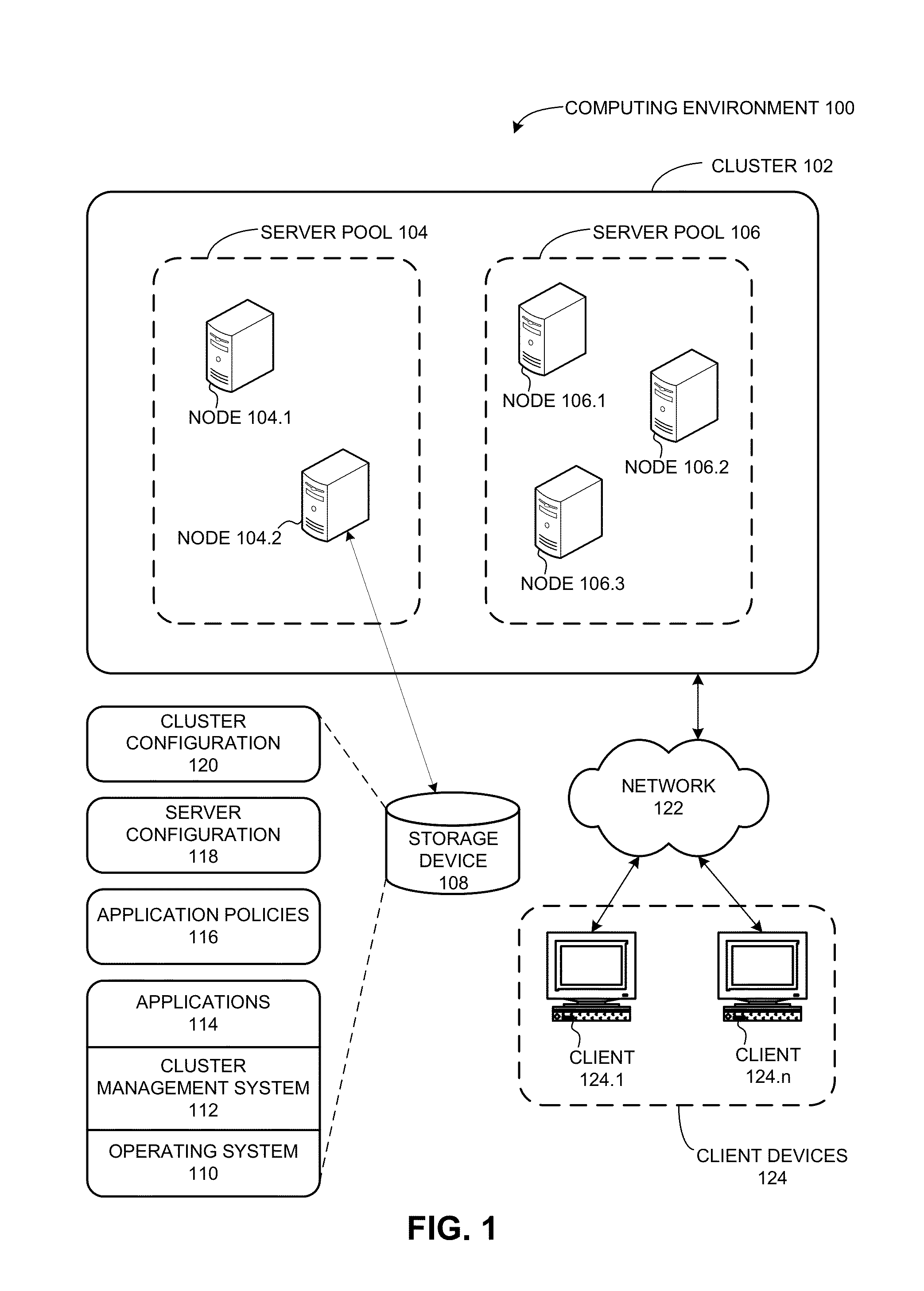
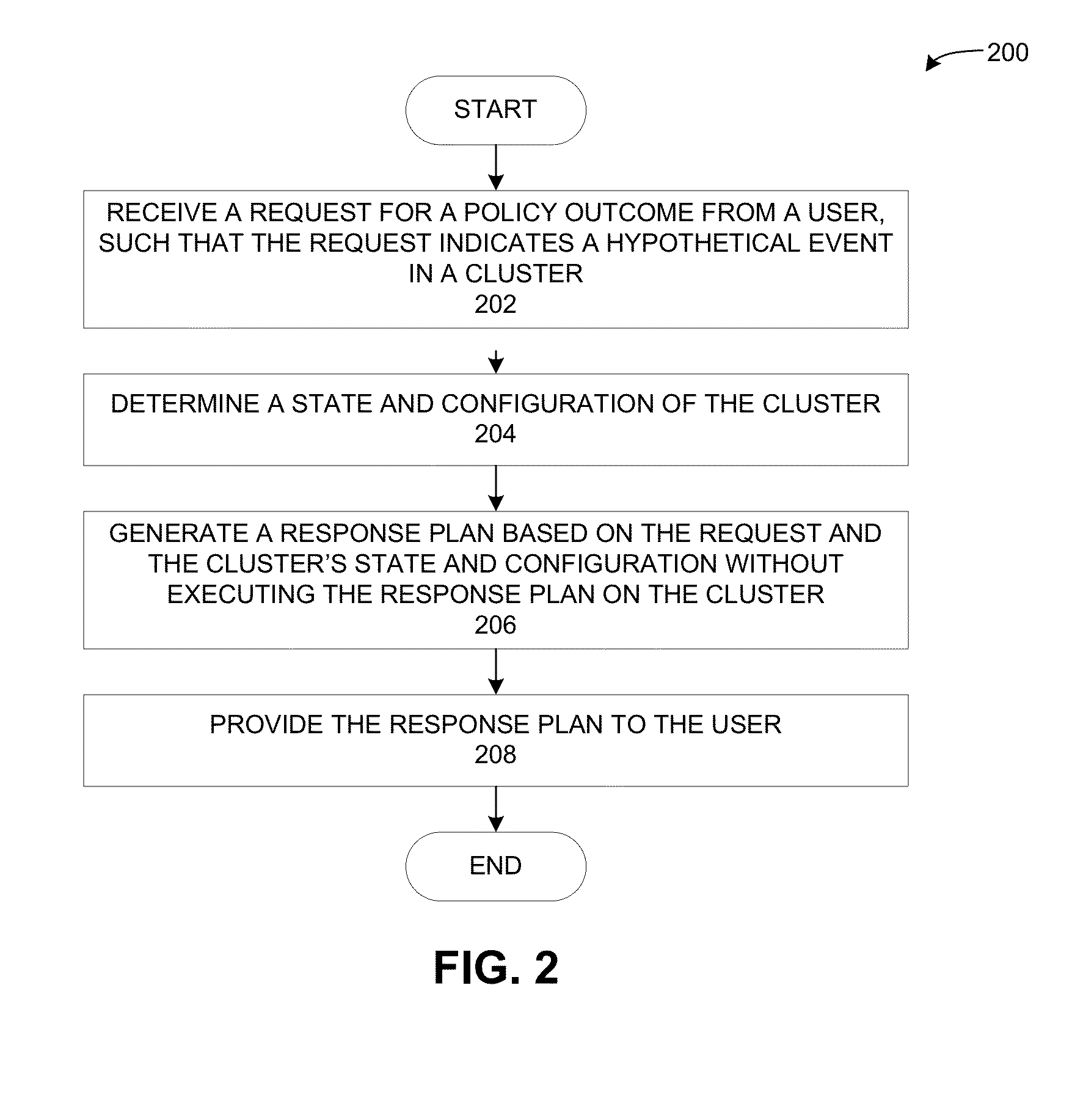
Hypothetical policy and event evaluation
ActiveUS20130219022A1Easy to determineMultiple digital computer combinationsProgram controlComputer clusterCluster state
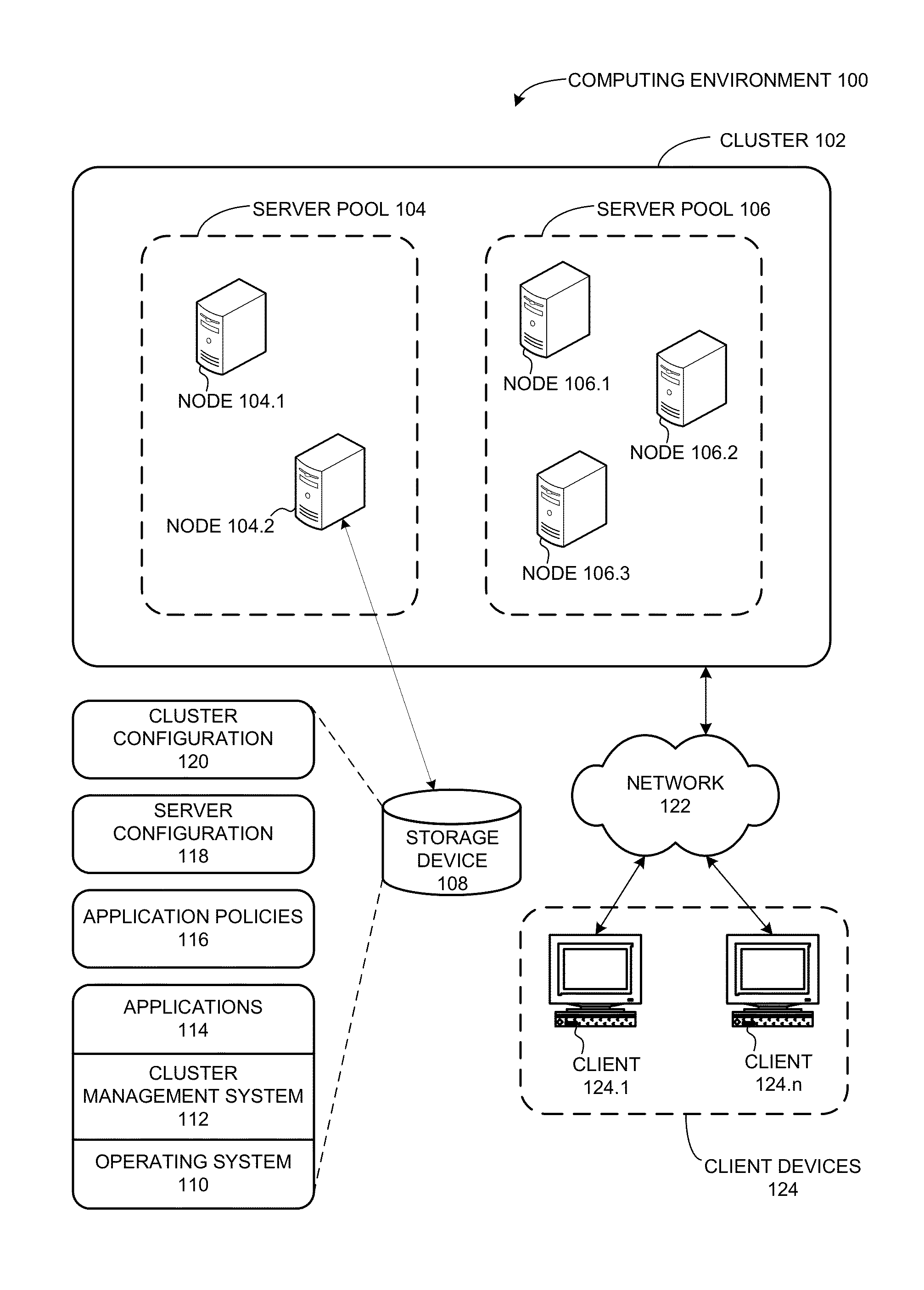
A cluster management system can facilitate determining a response to a hypothetical event by a computer cluster. During operation, the system can receive a request for a policy outcome from a user, such that the request can indicate a hypothetical event within a computer cluster. Next, the system determines a cluster state that includes state information from a plurality of server nodes in the cluster. The system then generates a response plan to the hypothetical event based on the cluster state, without executing the response plan in the cluster. The response plan indicates actions that are to be performed by server nodes in the cluster in response to the hypothetical event. The system then provides the response plan to the user.
Owner:ORACLE INT CORP
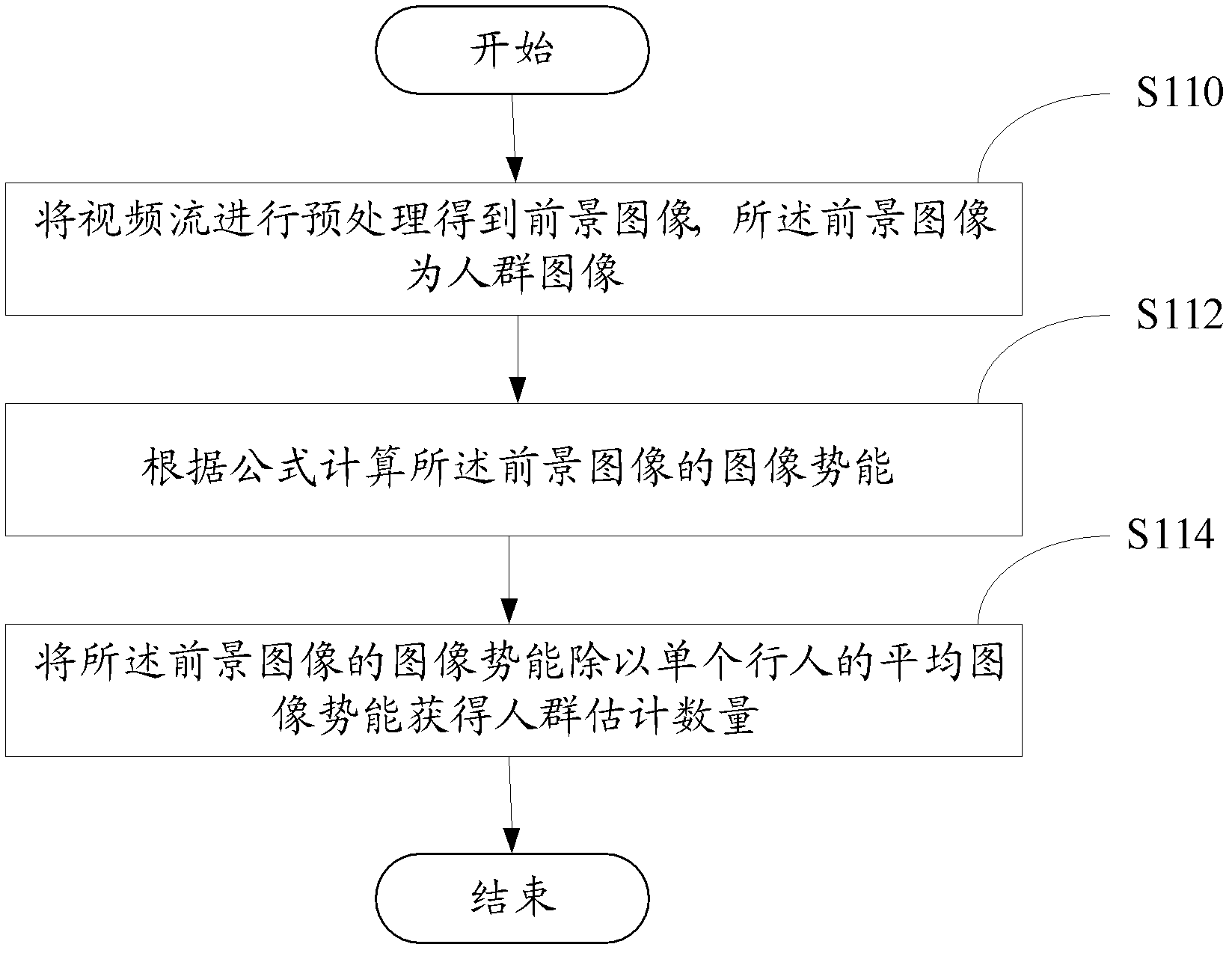
Crowd quantity estimating, local crowd clustering state and crowd running state detection method based on video stream
ActiveCN103077423ACalculation is simple and reliableIncreased sensitivityCharacter and pattern recognitionCounting objects with random distributionPattern recognitionShortest distance
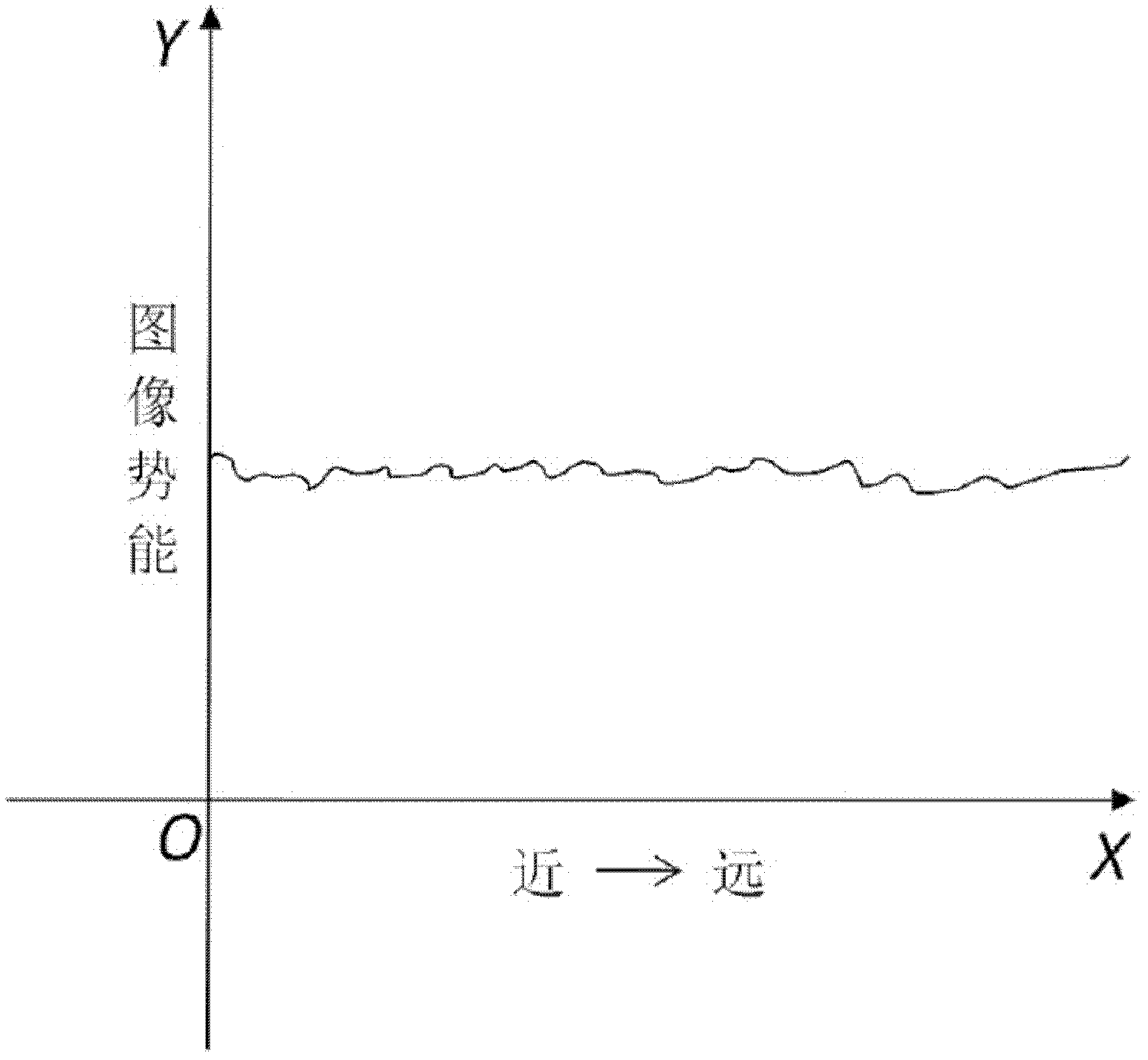
The invention provides a crowd quantity estimating method based on video stream. The method comprises the following steps of pre-treating video stream to obtain a foreground image, wherein the foreground image is a crowd image; calculating image potential energy Ep of the foreground image according to the following formula; in the formula, mij is pixel quality, and the value of mij is ranged from 0 to 1, if the pixel quality is 1, the pixel is the foreground, and if the pixel quality is 0, the pixel is the background; X is the width of the image, and the unit is pixel; Y is the height of the image, and the unit is pixel; gimg is a potential energy coefficient, gimg is a constant; yij is the y-axis coordinate of the pixel; H is the shortest distance of an object to a camera in a scene; and obtaining crowd estimated quantity by dividing the image potential energy Ep of the foreground image by average image potential energy of single pedestrian. In addition, the invention further provides a local crowd clustering state detection method and a crowd running state detection method.
Owner:SHENZHEN INST OF ADVANCED TECH CHINESE ACAD OF SCI
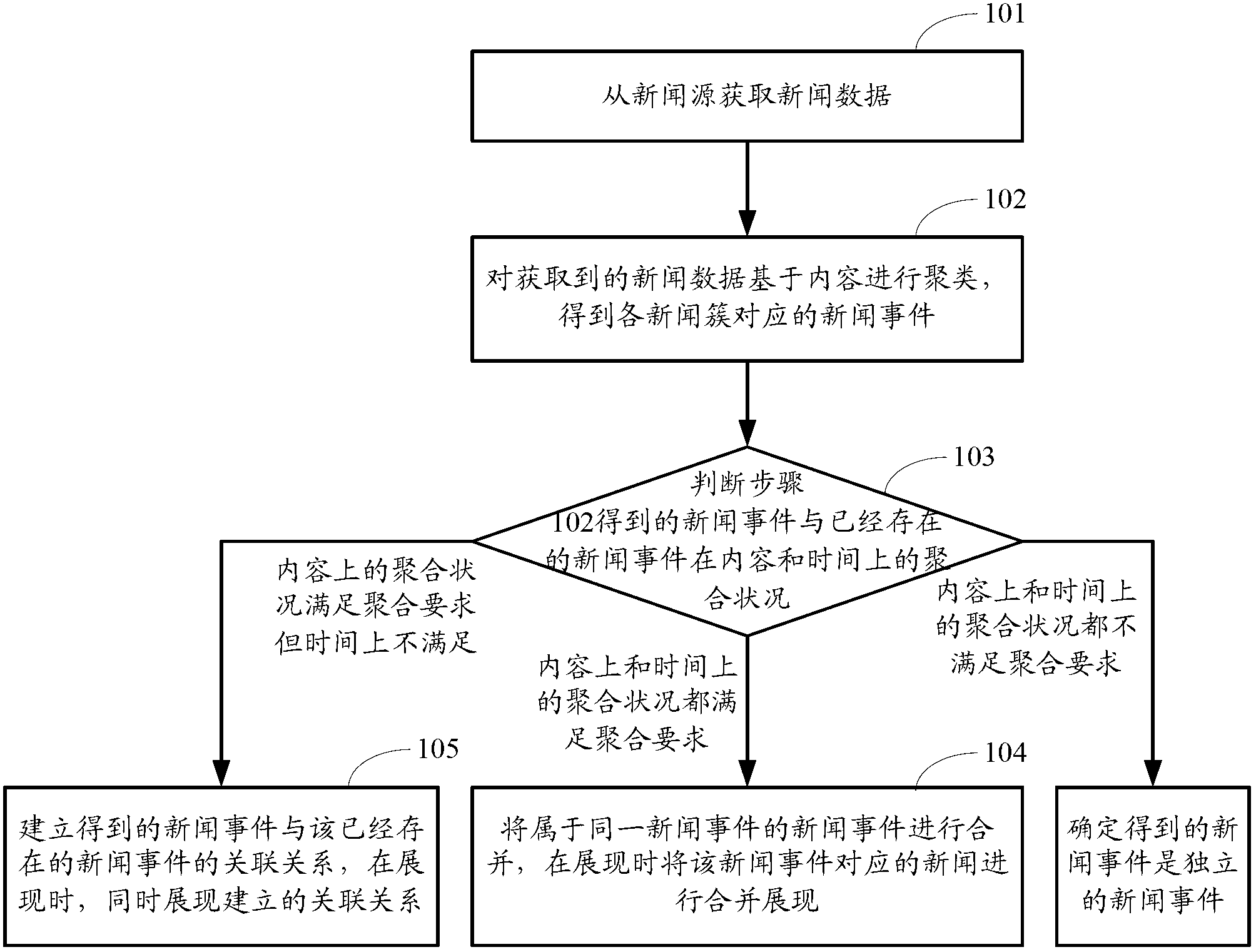
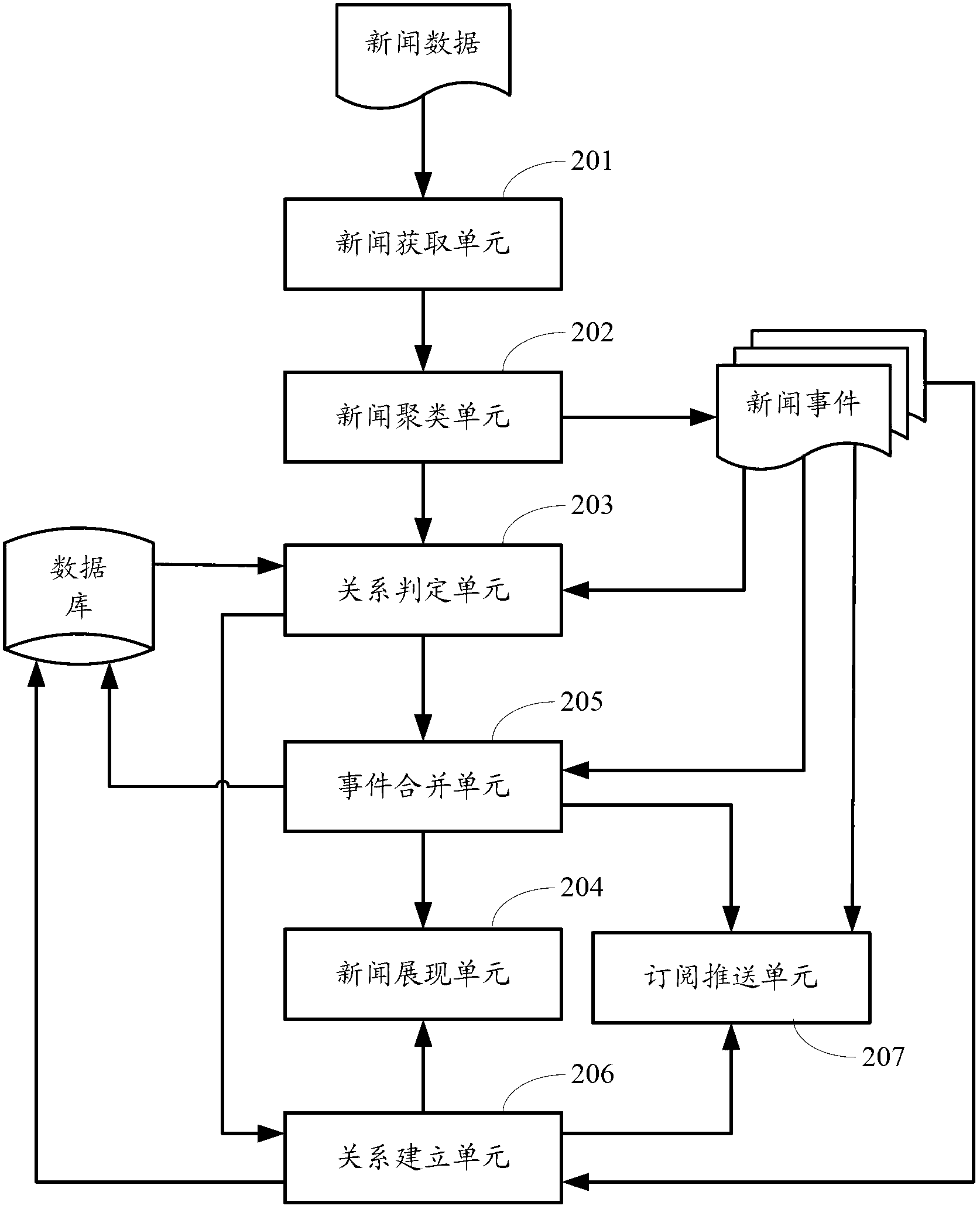
Method and device for news presentation facing events
InactiveCN103020159AReflection of relationshipLow costSpecial data processing applicationsCluster stateInformation retrieval
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
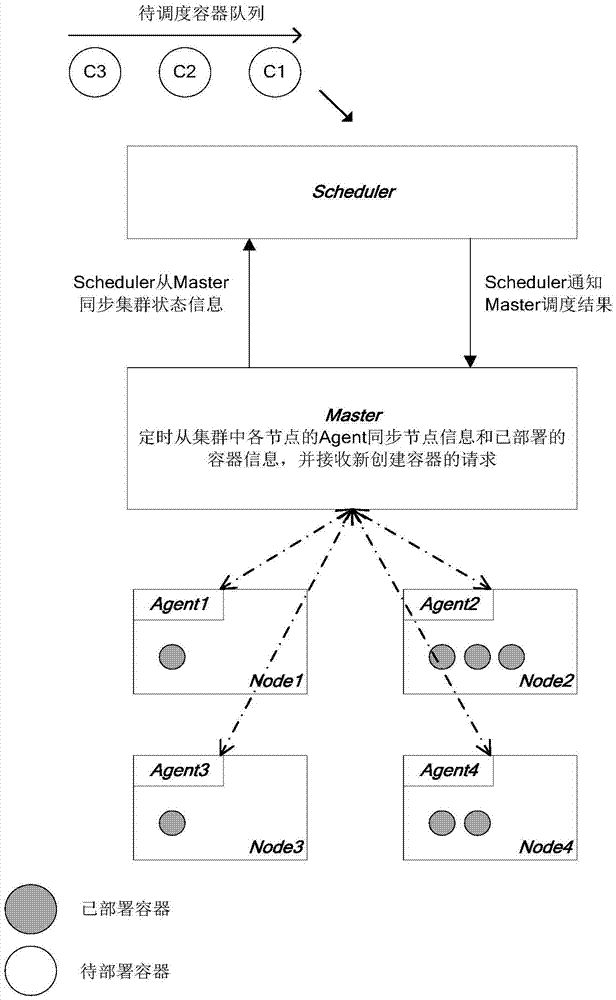
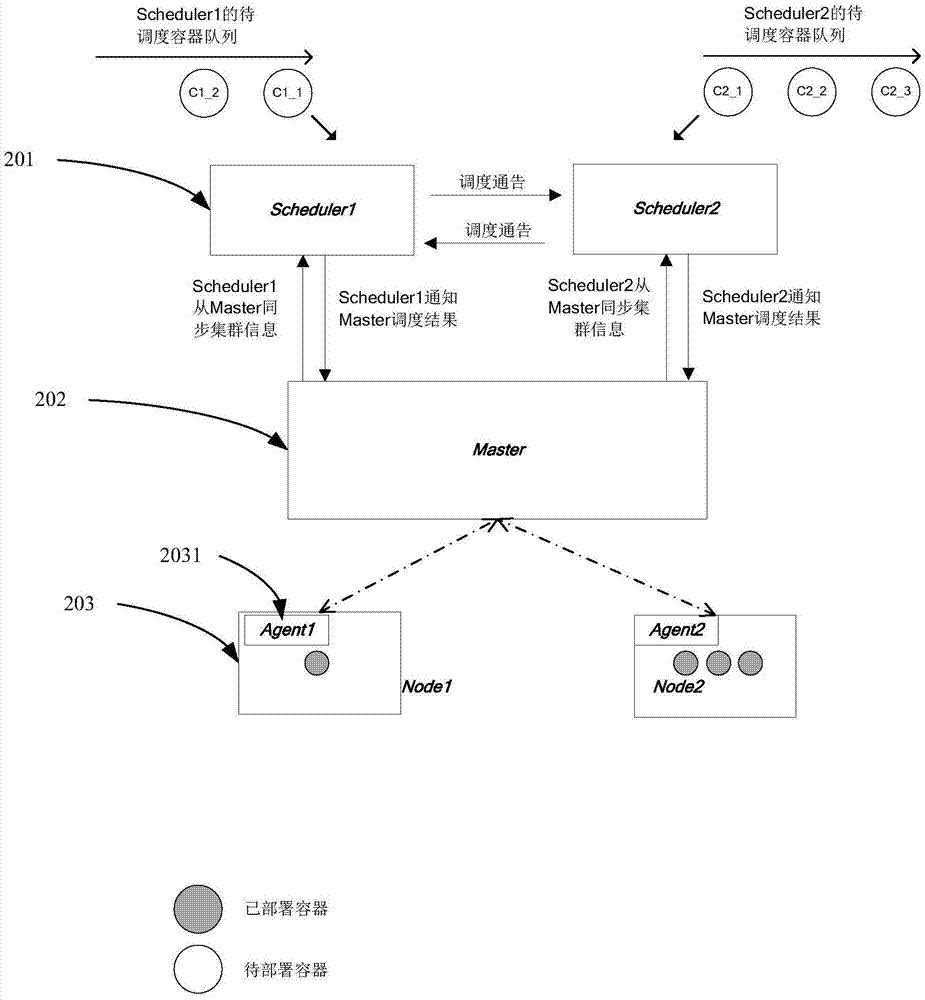
Method and apparatus for scheduling containers in parallel in cluster
ActiveCN106919445AAvoid resource conflictsReduce storage burdenProgram initiation/switchingResource informationCluster state
The invention relates to the technical field of cluster resource scheduling, and provides a method for scheduling containers in parallel in a cluster. The method comprises the steps of periodically obtaining cluster state information by a scheduler, wherein the cluster state information comprises resource information of all nodes in the cluster and description information of all containers in the cluster, the description information of the containers comprises container IDs of the containers, resource demands of the containers and deployment node IDs of the containers, and the resource information of the nodes comprises IDs of the nodes and resource quantities of the nodes; and according to the cluster state information, the container information of the containers scheduled by the scheduler and the container information of the containers scheduled by other schedulers, scheduling to-be-deployed containers to the nodes in the cluster, wherein the scheduled container information comprises container IDs and deployment node IDs of the scheduled containers. Through the scheme, the problem of resource conflicts in parallel scheduling is effectively reduced.
Owner:HUAWEI TECH CO LTD
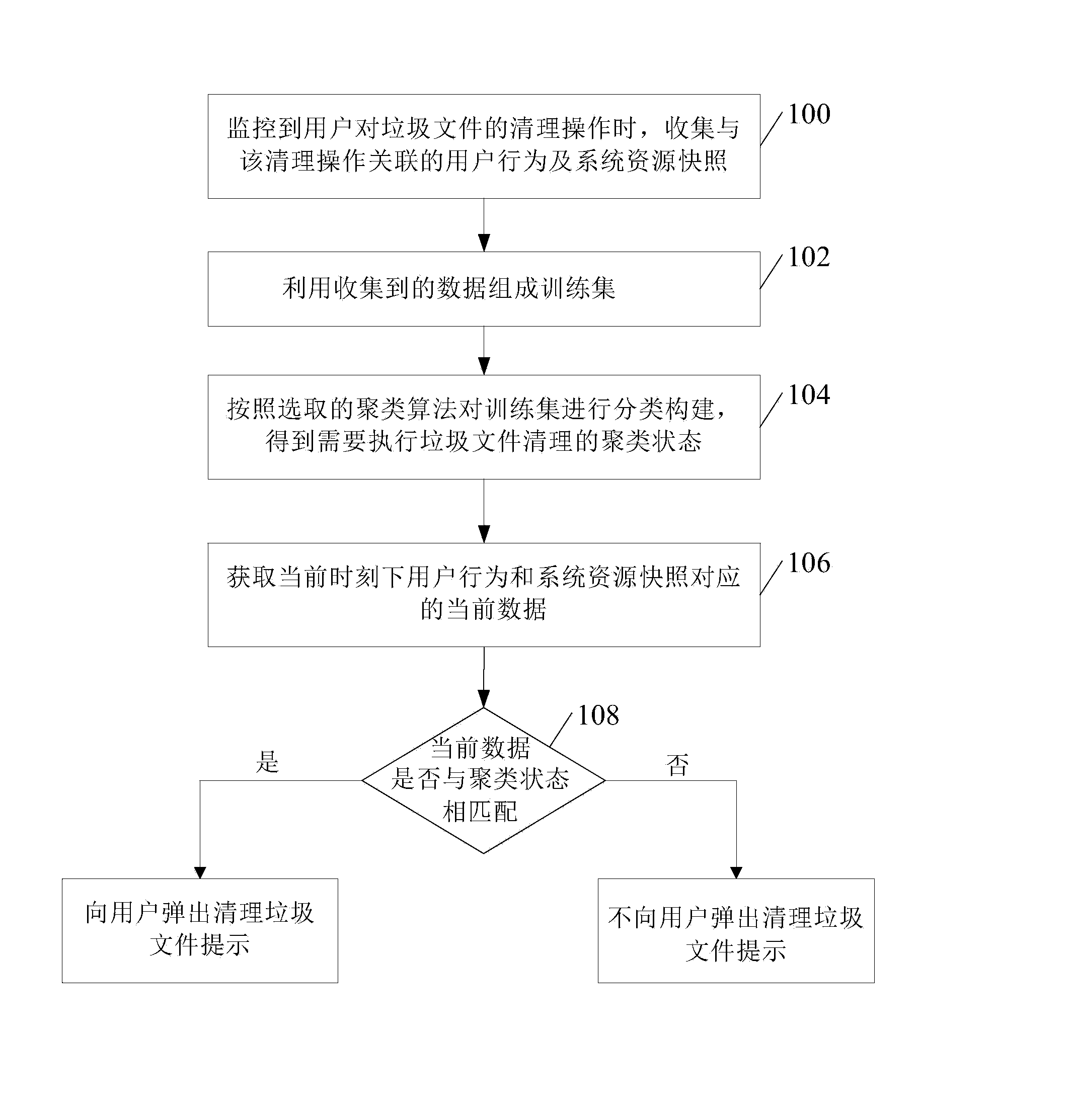
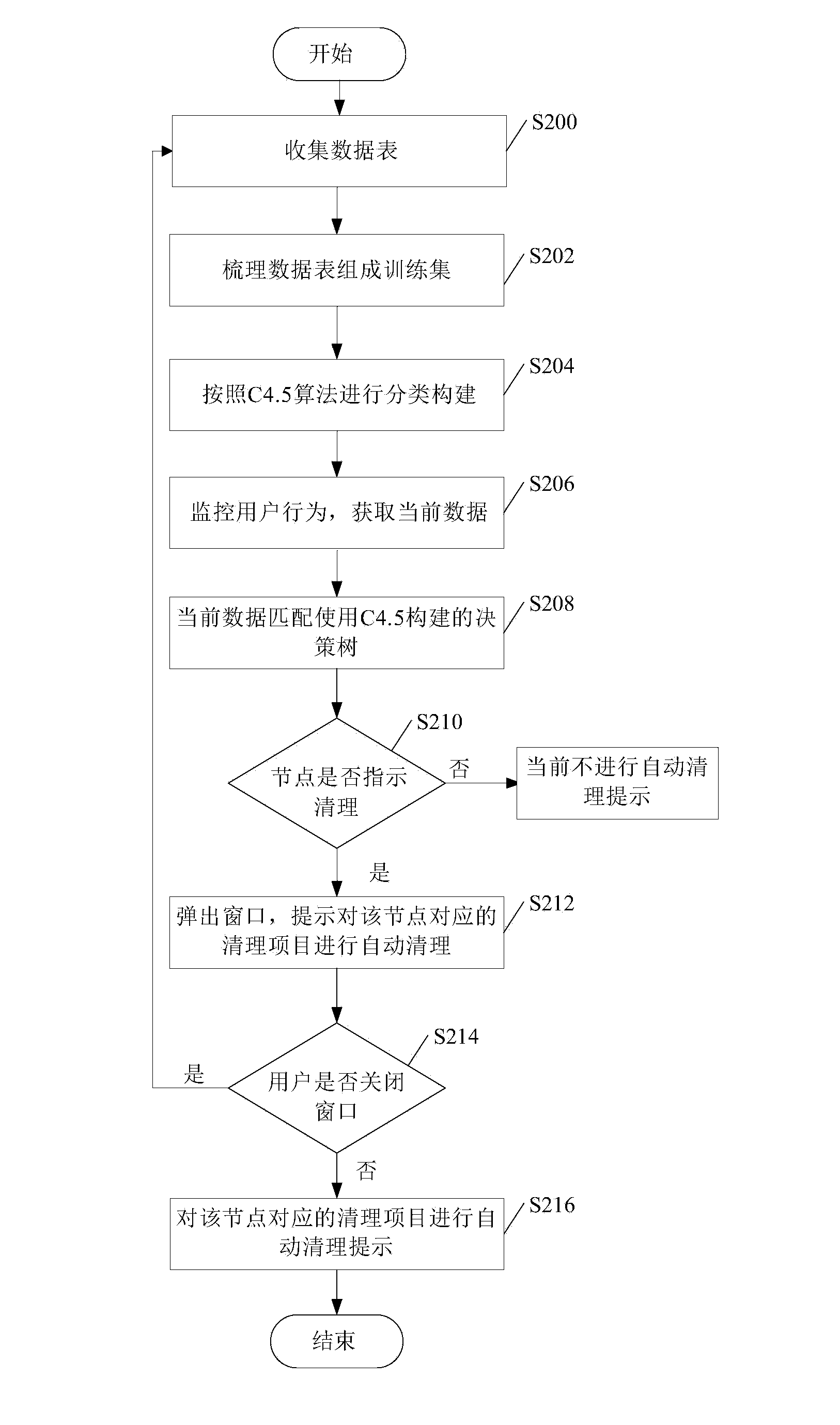
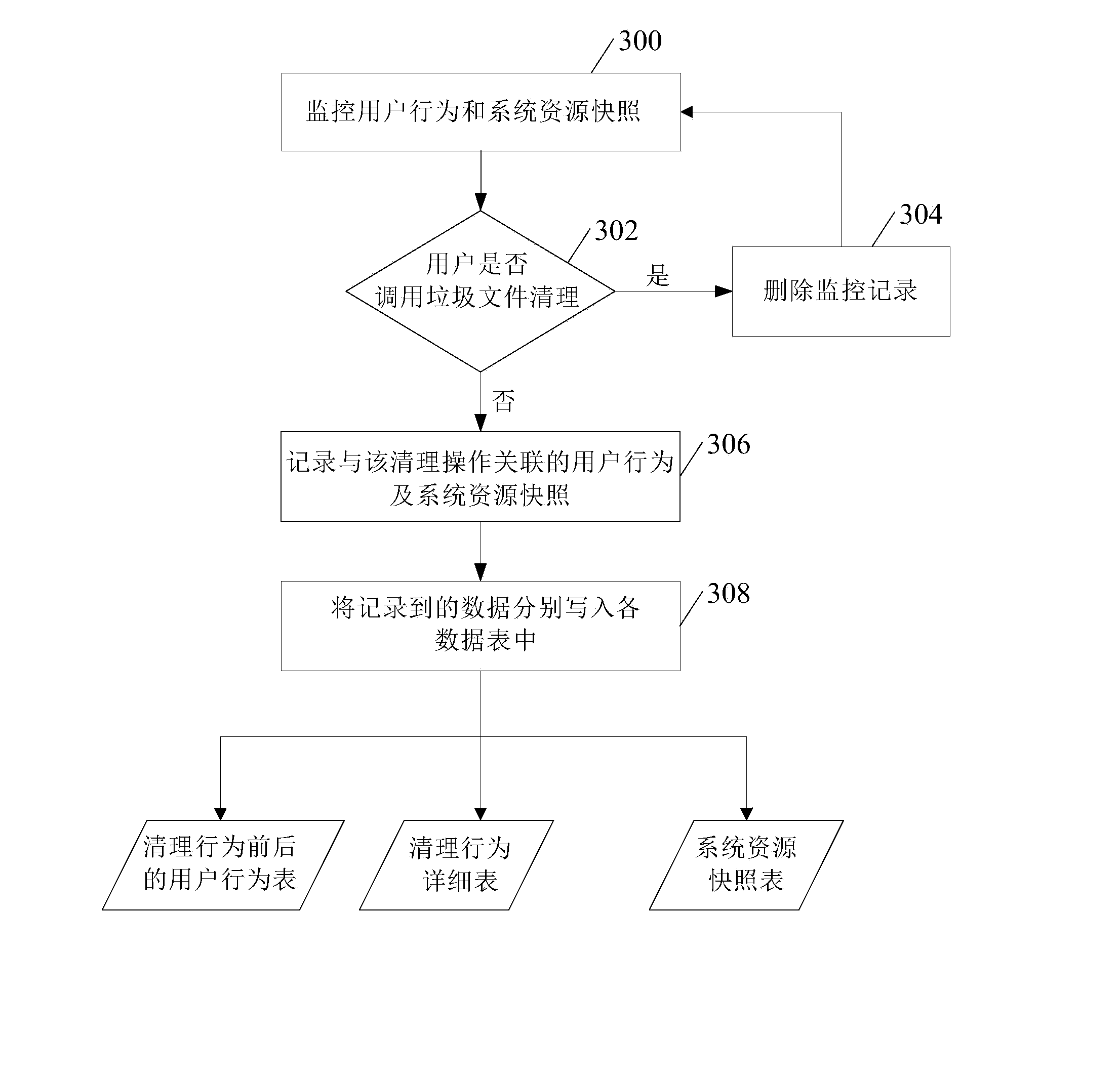
Junk file cleaning method and device
ActiveCN103646086AImprove experienceRelational databasesSpecial data processing applicationsPersonalizationCluster algorithm
The invention discloses a junk file cleaning method and device. The junk file cleaning method provided by the embodiment of the invention comprises steps as follows: a cleaning operation of a user on a junk file is monitored, and user behaviors and system resource snapshots which are associated with the cleaning operation are collected; collected data are used to constitute training sets; the training sets are established in a classified manner according to a selected clustering algorithm, and a clustering state which requires junk file cleaning is obtained; current data corresponding to the user behaviors and the system resource snapshots at the current moment are acquired; and whether the current data are matched with the clustering state is judged, if yes, a junk file cleaning prompt is popped to the user, and otherwise, the junk file cleaning prompt is not popped to the user. According to the junk file cleaning method and device, personalized automatic junk file cleaning for the user is realized, so that the user experience is improved.
Owner:BEIJING QIHOO TECH CO LTD
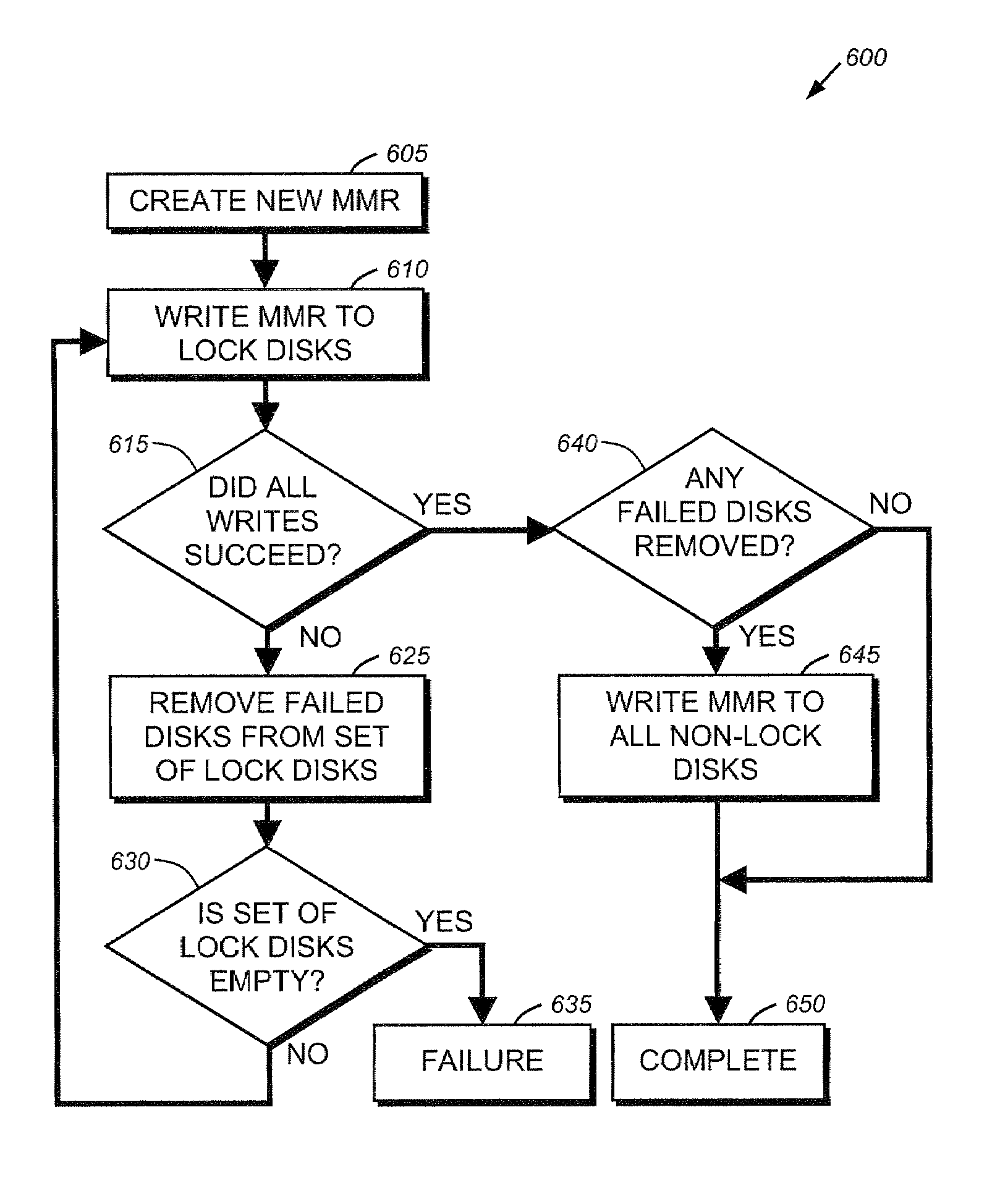
System and method for coordinating cluster state information
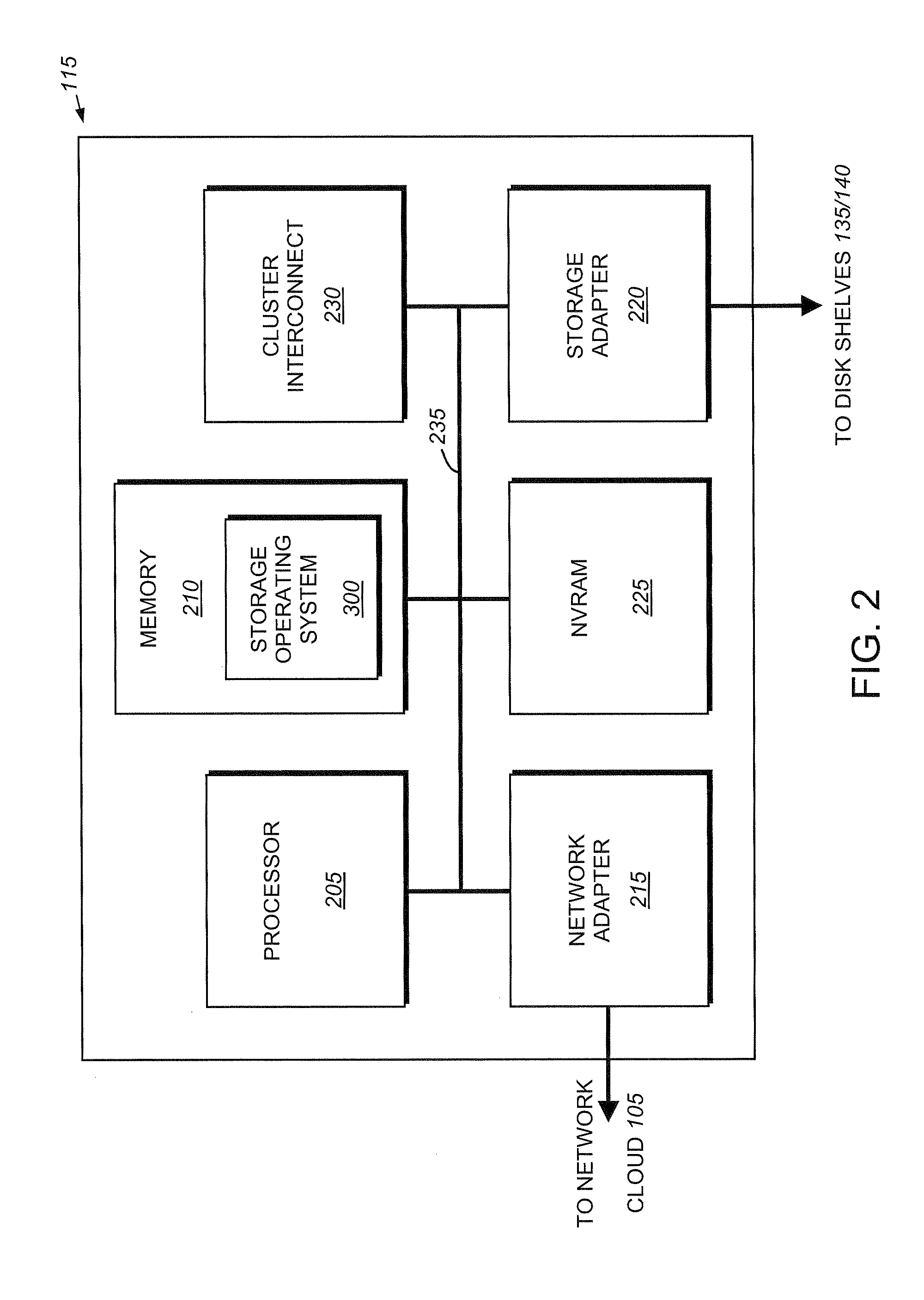
ActiveUS7685358B1Avoid lostError detection/correctionMultiple digital computer combinationsCluster stateFile server
A method for managing a cluster of file servers is disclosed. The method has the first step of writing coordinating information for a plurality of servers of the cluster of servers to a master mailbox record, the master mailbox record written to a specific location on each disk of a set of lock disks, the set of lock disks having a plurality of disks, the plurality of disks chosen so that in the event of failure of a server of the plurality of servers, at least one lock disk will be available to the remaining servers. The method has the second step of writing a second copy of eth coordinating information to the master mailbox record of the set of lock disks.
Owner:NETWORK APPLIANCE INC
Cluster self-feedback type load balancing scheduling system and method
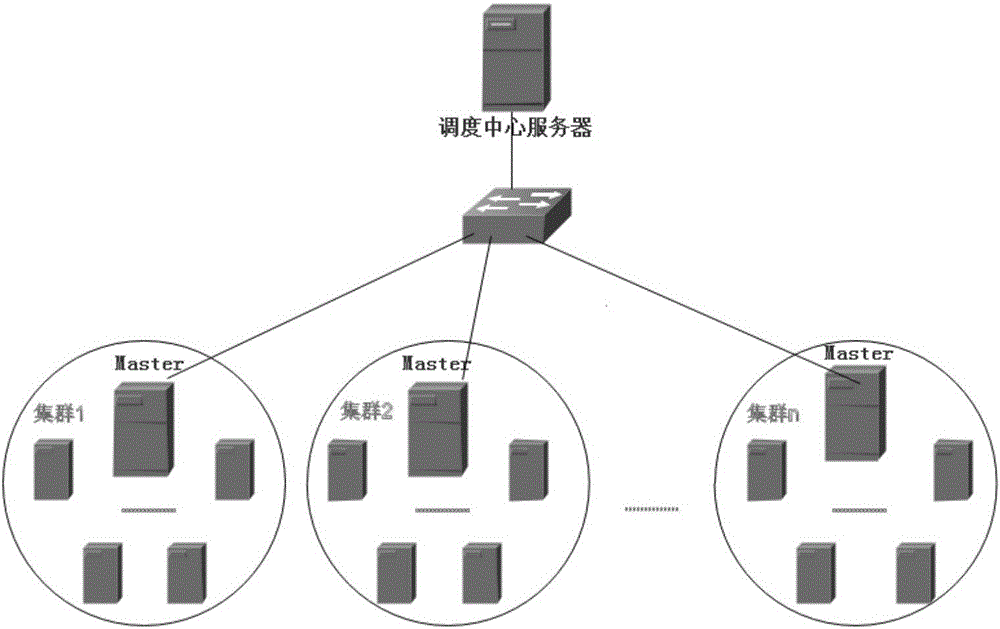
InactiveCN105959395ALoad balancing task scheduling distribution balancingTimely updateTransmissionDistribution methodCluster state
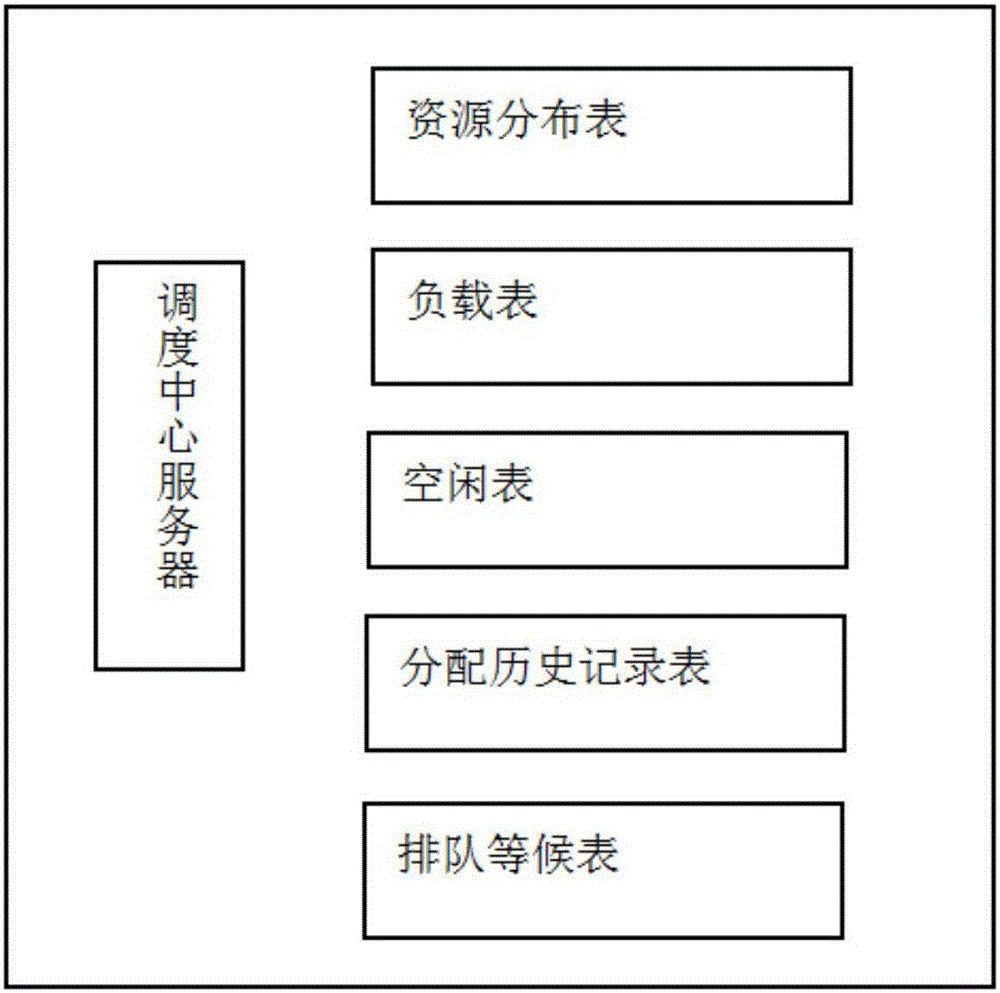
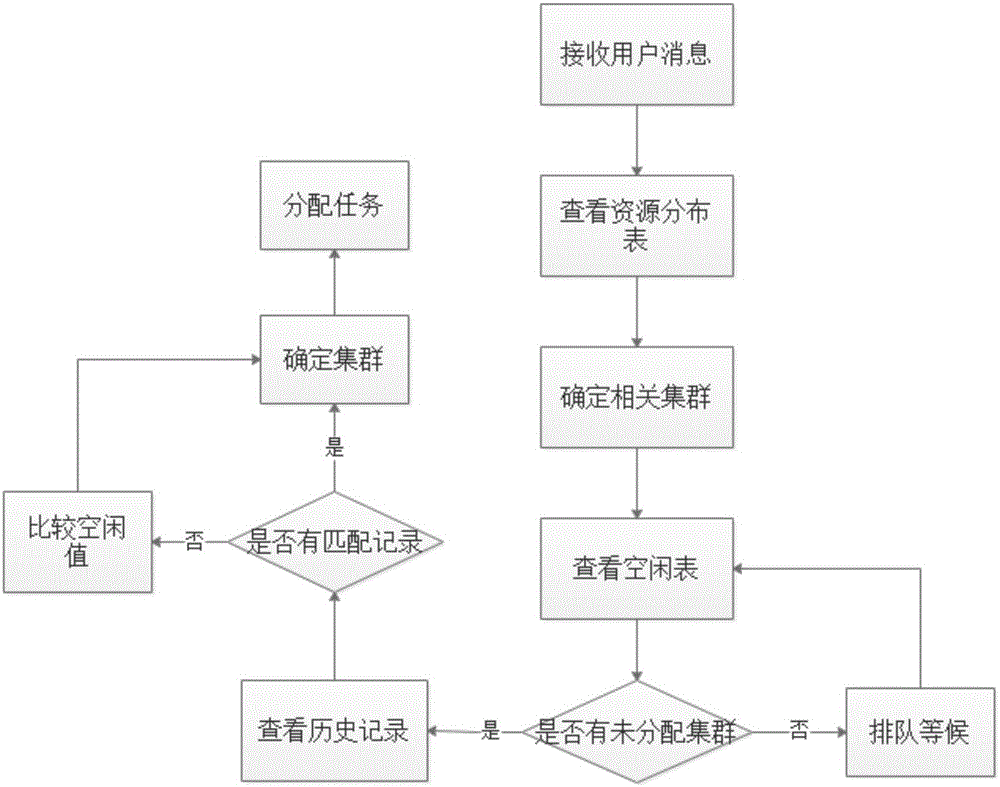
The invention discloses a cluster self-feedback type load balancing scheduling system and method. The method disclosed by the invention comprises the following steps that: a scheduling central server efficiently calls a cluster response service by utilizing self five tables; Master servers in various clusters notify the scheduling central server to update various cluster states in the tables in real time by sending Hello and Update messages; after receiving a user request, the scheduling central server checks a resource distribution table placed therein, determines related processible clusters, and makes the most reasonable processing scheme in combination with an idle table and a distribution historical record table; the Master servers in various clusters periodically send the Hello messages, and notify the scheduling central server of self states; and furthermore, in the event of newly creating or completing a processing task, the Update messages are sent in real time, such that the scheduling central server is notified to modify states of various tables. A feedback mechanism is combined with a reasonable task distribution method, such that the load balancing scheduling method is realized.
Owner:XUZHOU MEDICAL UNIV
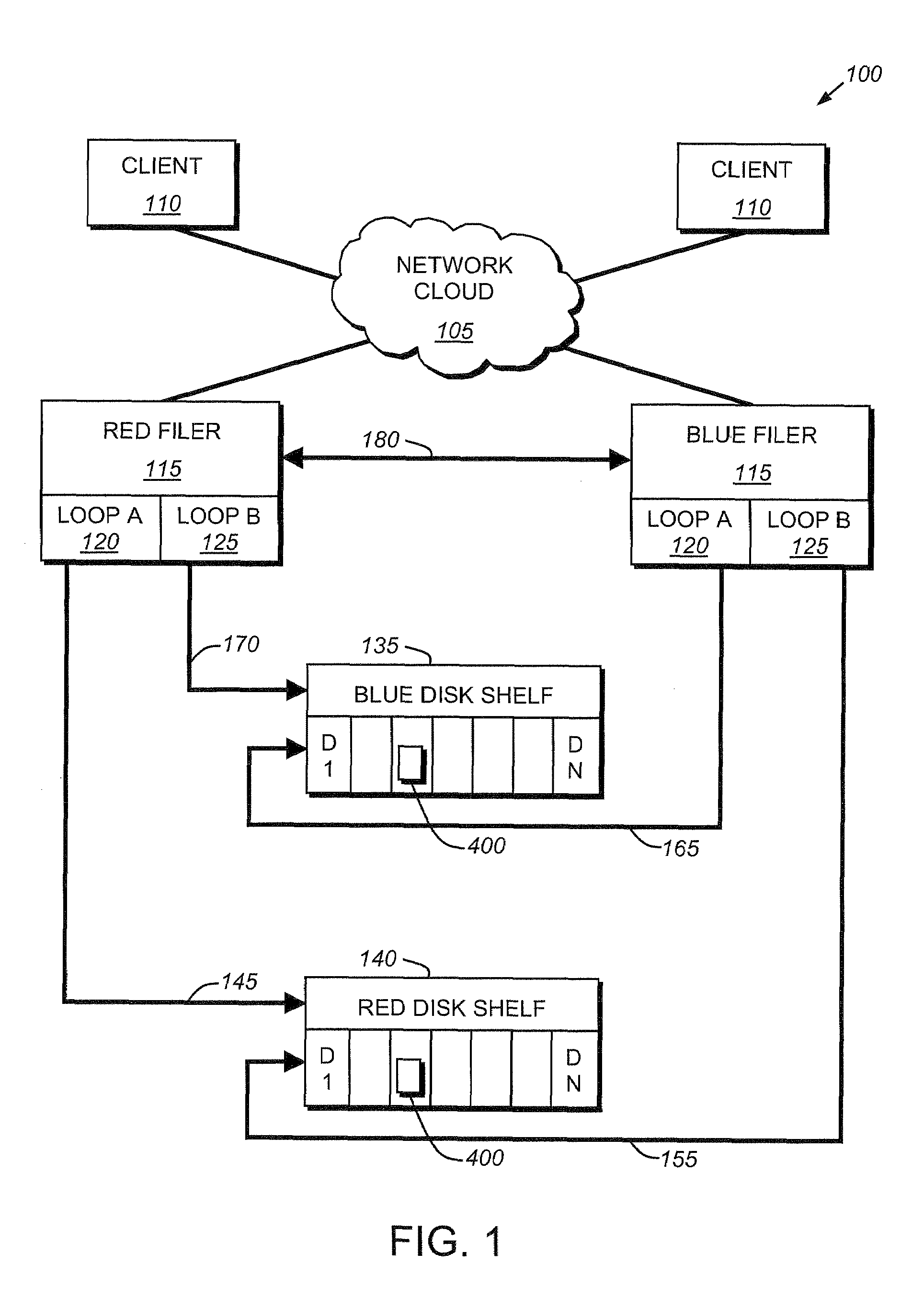
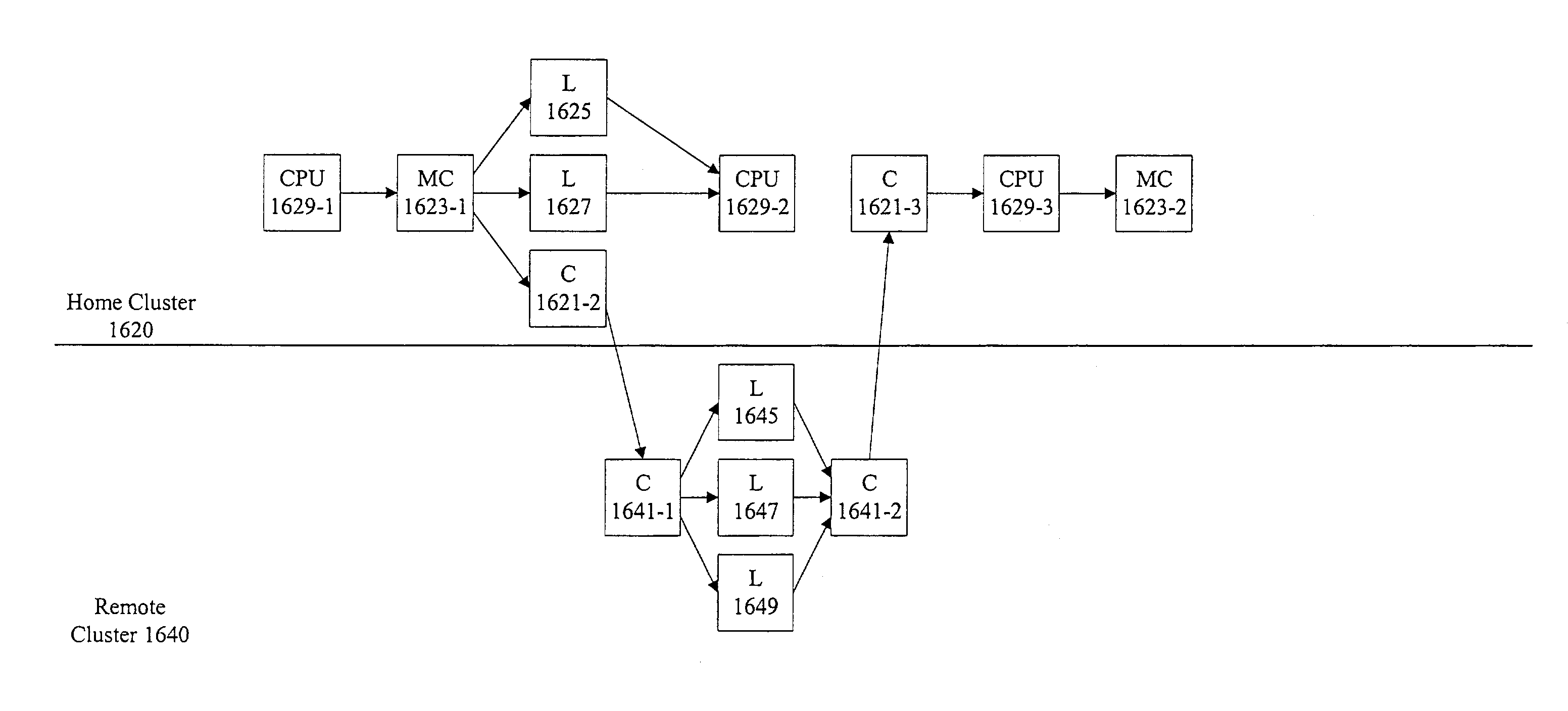
Methods and apparatus for maintaining remote cluster state information
ActiveUS7346744B1Improve data access efficiencyImprove accuracyMemory adressing/allocation/relocationDigital computer detailsCluster systemsMulti processor
According to the present invention, methods and apparatus are provided for increasing the efficiency of data access in a multiple processor, multiple cluster system. Mechanisms for improving the accuracy of information available to a cache coherence controller are provided in order to allow the cache coherence controller to reduce the number of transactions in a multiple cluster system. Non-change probes and augmented non-change probe responses are provided to acquire state information in remote clusters without affecting the state of the probed memory line. Augmented probe responses associated with shared and invalidating probes are provided to update state information in a coherence directory during read and read / write probe requests.
Owner:SANMINA-SCI CORPORATION
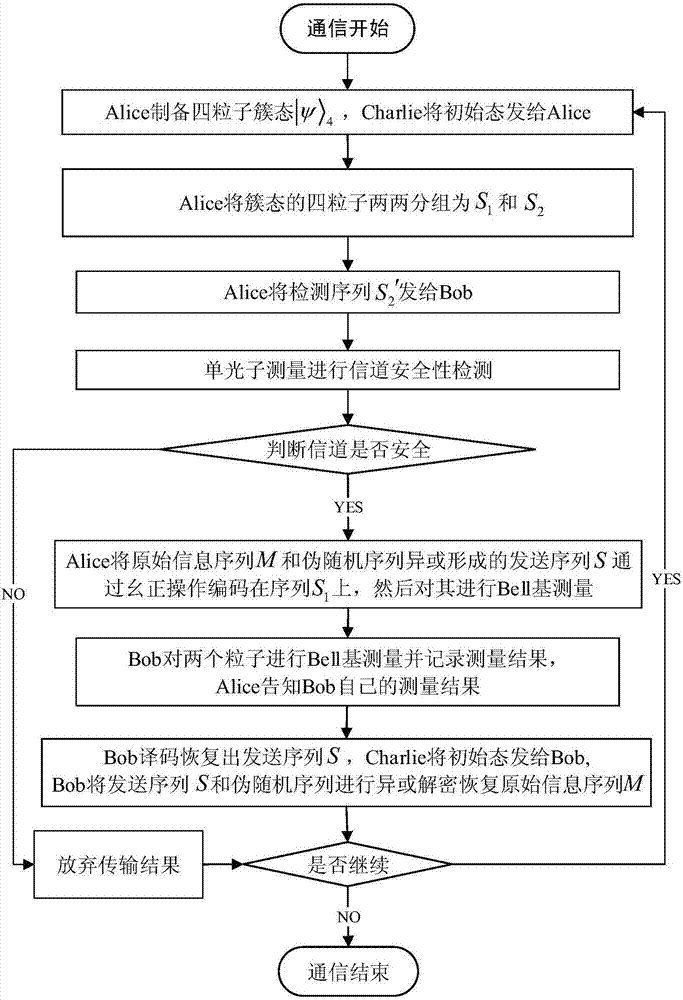
Controlled quantum security direct communication method based on four particle cluster states
ActiveCN107222307AMaintain entanglementLong cycleKey distribution for secure communicationPhotonic quantum communicationAlice and BobQuantum secure direct communication
The invention discloses a controlled quantum security direct communication method based on four particle cluster states. Alice and Bob respectively serve as a legal information sender and a legal information receiver during a quantum communication process, and Charlie serves as a credible scheme control party; information security is achieved by randomly inserting a single photon to perform measurement-based comparison detection, and communication starts after security detection; Alice uniformly divides the prepared four particle cluster states into two groups, after being subjected to an XOR operation with a pseudorandom sequence, the sent information is encoded on the two particles reserved by Alice via unitary transformation. Alice performs Bell-based measurement on reserved particles, and sends measurement information to Bob, and Bob recovers the original sequence via an initial state sent by Charlie after the measurement information is compared. The four particle cluster states used by the method has good entanglement, connectivity and damage resistance, only the receiver Bob in the method gets the permission of the controller Charlie, Bob can recover the original information, so that the information can be effectively prevented from being attacked during a transmission process, and an implementation process is simple.
Owner:NORTHWEST UNIV
Abnormal state detection method of medium and high density crowd
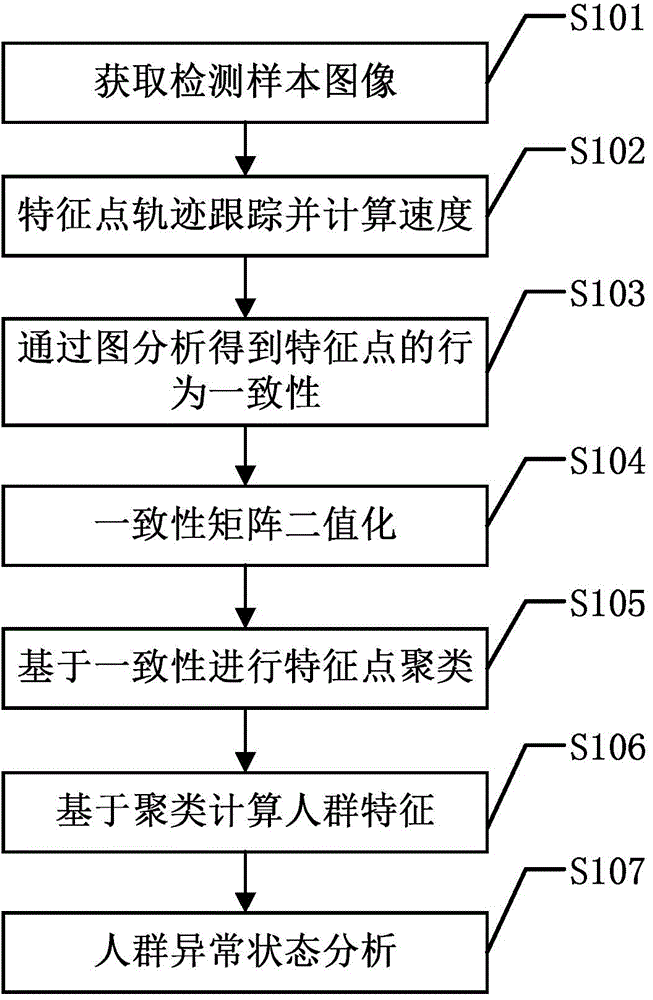
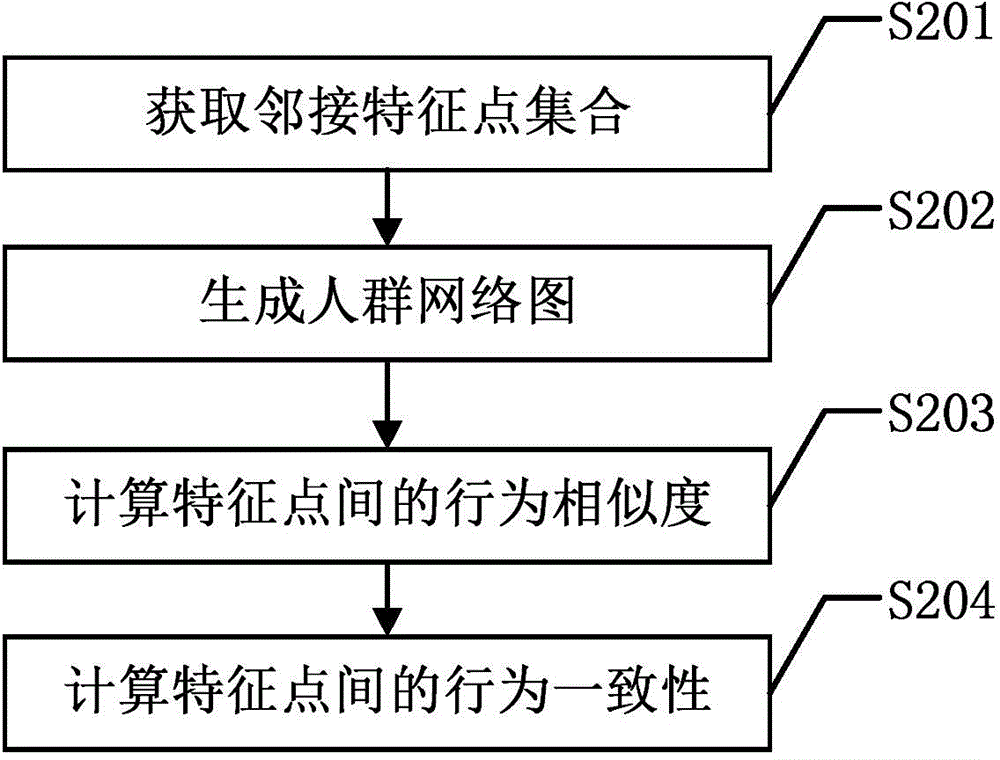
InactiveCN104933412AUnlimited occlusionNot restricted by occlusionCharacter and pattern recognitionPattern recognitionHigh density
The invention discloses an abnormal state detection method of a medium and high density crowd. The abnormal state detection method comprises the following steps: firstly, extracting and tracking feature points, and calculating the speed of each feature point according to the coordinates of the feature point in a previous frame of surveillance video image and a current frame of surveillance video image; then, adopting diagram analysis to obtain behavior consistency among the feature points, ejecting discrete points on the basis of the behavior consistency, and clustering the residual feature points; calculating the crowd aggregation degree, the crowd movement strength and the crowd movement direction variance of all feature points in a cluster; and according to the three parameters in multiple frames of surveillance video images and the amount and the amplification of the crowd cluster, judging the abnormal state of the crowd. The abnormal state detection method carries out crowd state analysis on the basis of a diagram analysis method to realize the detection of three crowd states including a crowd evacuation state, a crowd cluster state and a crowd disturbance state.
Owner:UNIV OF ELECTRONIC SCI & TECH OF CHINA
Efficient construction of quantum computatitonal clusters
ActiveUS20080035911A1Improve efficiencyEffective combinationQuantum computersNanoinformaticsCluster stateComputer science
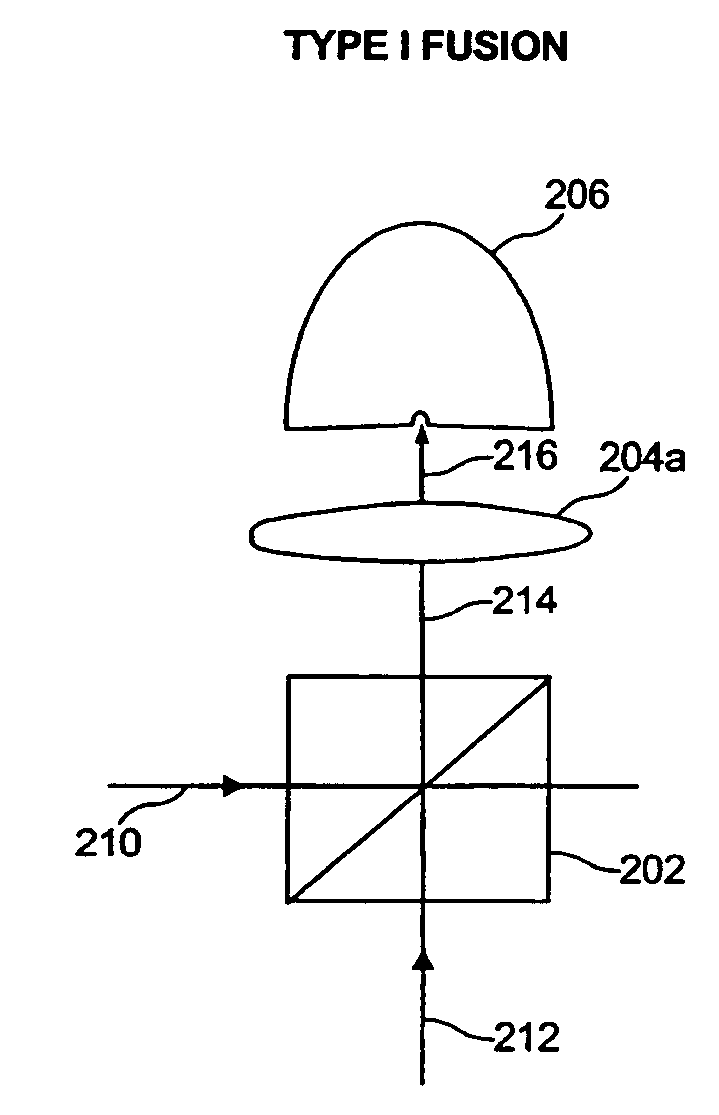
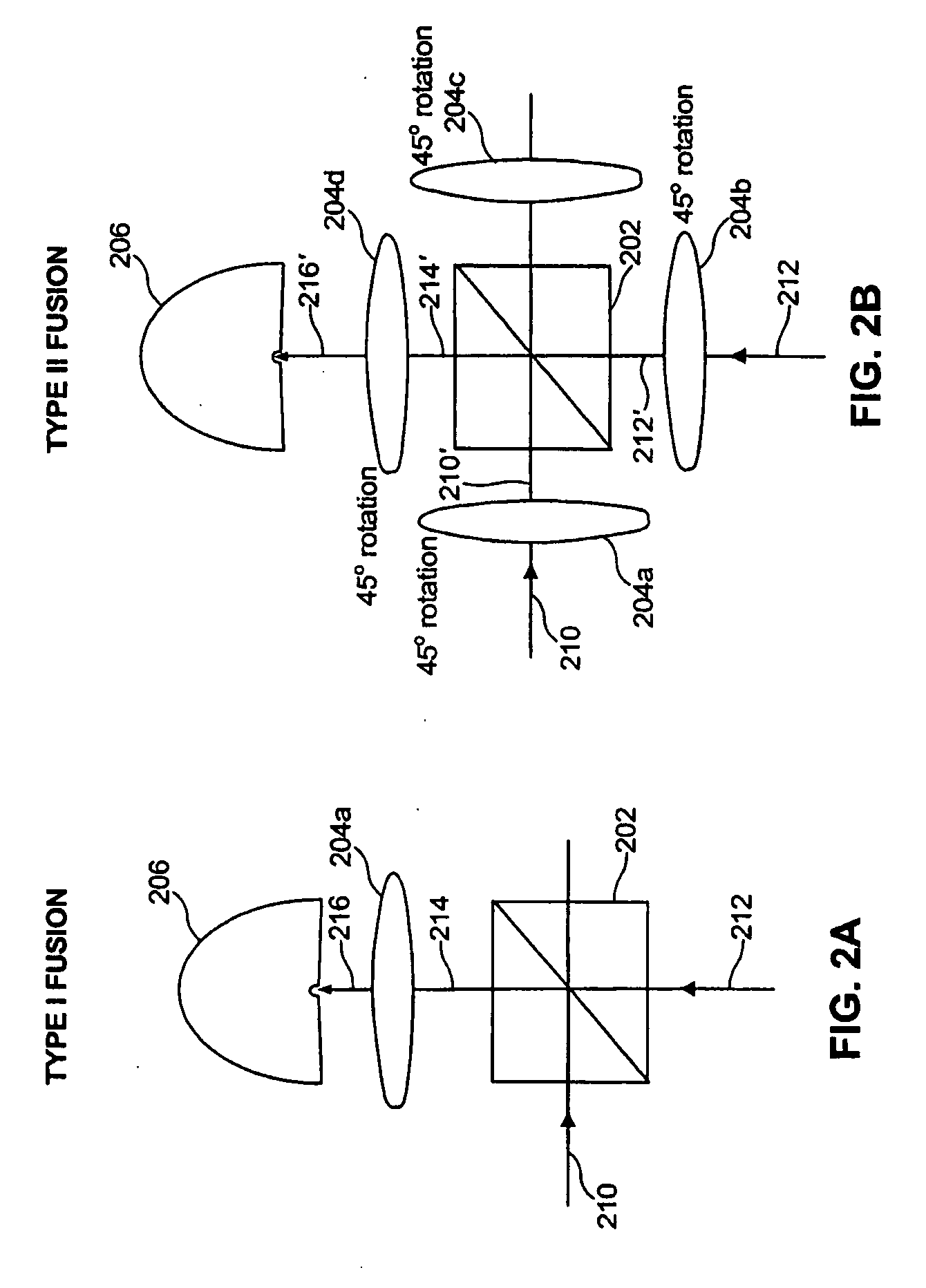
A method of creating two-dimensional quantum computational cluster states is demonstrated that is considerably more efficient than previously proposed approaches. The method uses local unitaries and type-I fusion operations. The increased efficiency of the method compared to previously proposed constructions is obtained by identifying and exploiting local equivalence properties inherent in cluster states.
Owner:MITRE SPORTS INT LTD
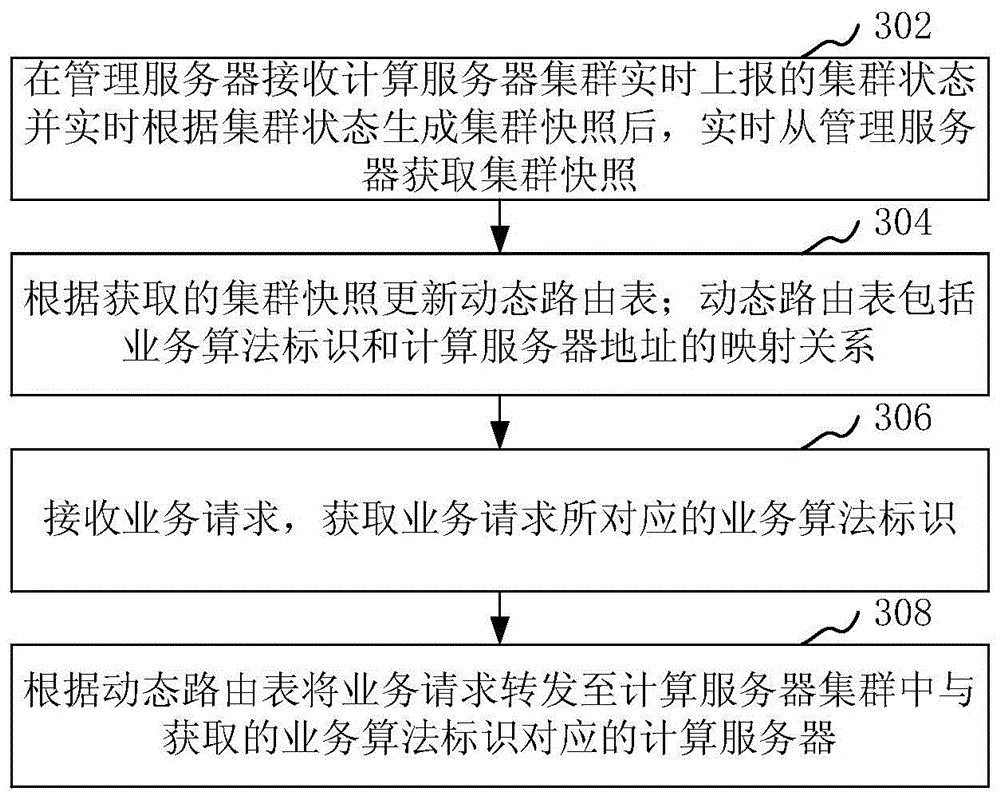
Service request distribution system, method and device
InactiveCN106302611ALower requirementReduce maintenance costsData switching networksCluster stateAdaptive routing
The invention relates to a service request distribution system, method and device. The system comprises a calculation server cluster, a management server and an access server. The calculation server cluster is used for reporting a cluster state to the management server in real time. The management server is used for generating a cluster snapshot according to the cluster state in real time. The access server is used for obtaining the cluster snapshot from the management server in real time and updating a dynamic routing table according to the obtained cluster snapshot. The dynamic routing table comprises the mapping relation between a service algorithm identity and a calculation server address. A service request is received, the service algorithm identity corresponding to the service request is obtained, and the service request is forwarded to a calculation server corresponding to the obtained service algorithm identity in the calculation server cluster according to the dynamic routing table. The invention provides the service request distribution system, method and device, the service request is adaptively forwarded to the corresponding calculation server, the requirement for maintenance personnel is reduced, and the maintenance cost is reduced.
Owner:SHENZHEN TENCENT COMP SYST CO LTD
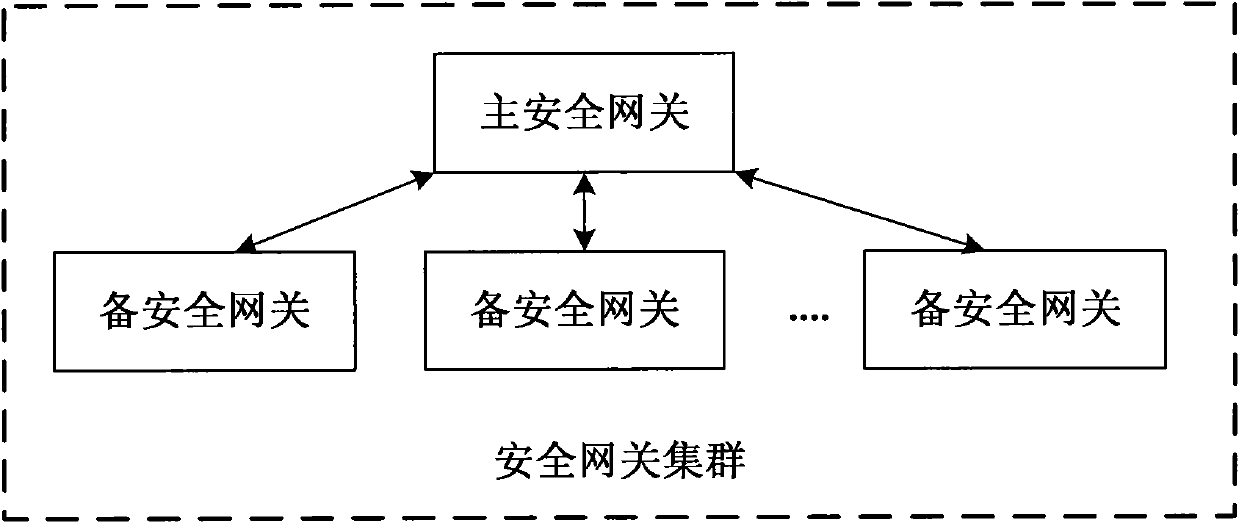
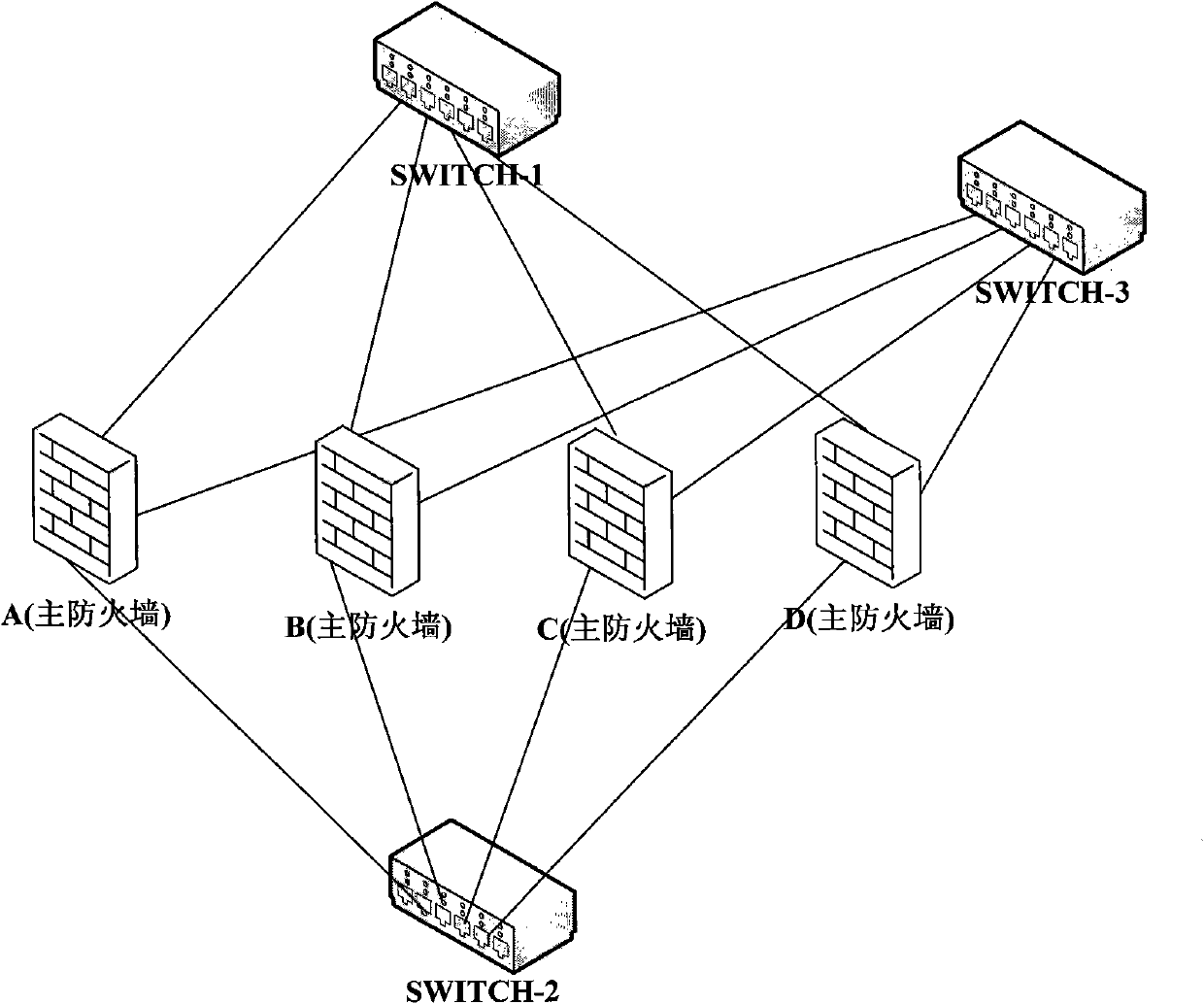
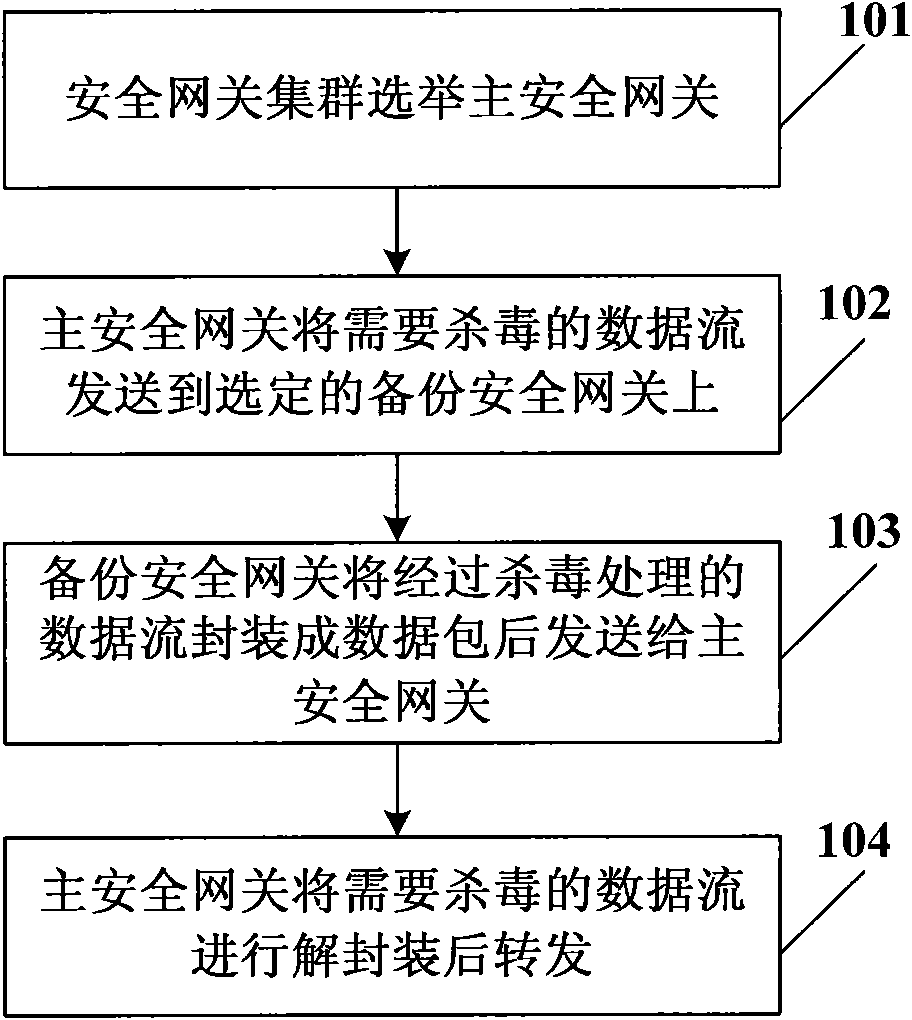
Antivirus method and system for secure gateway cluster
InactiveCN101909067AImprove flexibilityImprove good performanceError preventionData switching networksData streamDynamic load balancing
The invention discloses antivirus method and system for a secure gateway cluster. in the method, the secure gateway cluster selects one of a plurality of secure gateway devices in advance as a main secure gateway, and the other secure gateway devices are used as backup secure gateways; the main secure gateway identifies a data stream needing antivirus processing and sends the data stream needing antivirus processing to the backup secure gateways through inquiring a cluster state database and a predetermined load balancing strategy; the backup secure gateways carry out antivirus processing on the received data stream needing antivirus processing, package and send the processed data stream to the main secure gateway; and the main secure gateway de-package and forward a data packet subjected to antivirus processing. In the invention, the unification of the transparency and the high performance of the secure gateway cluster is realized, and the utilization ratio of overall resources of the secure gateway cluster is improved on the basis of maintaining high availability of the secure gateway cluster through an effective dynamic load balancing mechanism.
Owner:BEIJING TOPSEC TECH
Detection and recovery system and method for RabbitMQ cluster fault
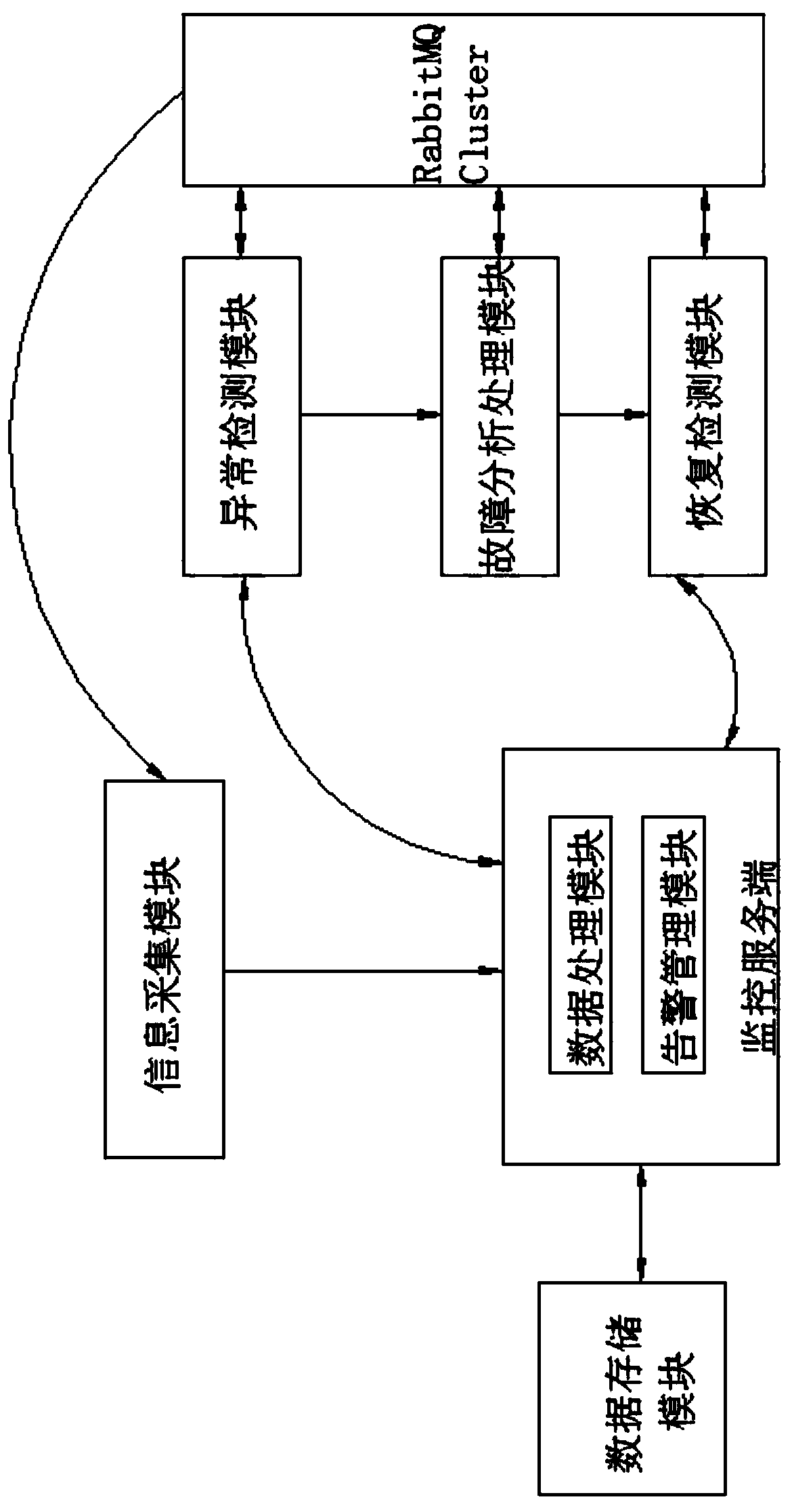
InactiveCN110290012ATimely detection of service anomaliesImprove timelinessData switching networksAnomaly detectionCluster state
The invention discloses a RabbitMQ cluster fault detection and recovery system and method, belongs to the field of cloud computing, and aims to solve the technical problem of how to judge and rapidly recover the fault condition that the RabbitMQ cluster state is normal but cluster queue metadata is inconsistent. The system comprises a structure information acquisition module, an abnormity detection module, a monitoring server, a fault analysis processing module, a recovery detection module and a data storage module. The method comprises the steps of collecting health data; detecting and analyzing the health data, and detecting and analyzing the consistency of the RabbitMQ cluster state and the queue metadata to obtain a detection and analysis result; when it is detected that the analysis result is abnormal, generating alarm information; generating a processing result of the RabbitMQ node according to a detection analysis result; and after the fault processing is finished, verifying the availability of the RabbitMQ cluster.
Owner:SHANDONG LANGCHAO YUNTOU INFORMATION TECH CO LTD
Minimum-cost maximum-flow based large-scale resource scheduling system and minimum-cost maximum-flow based large-scale resource scheduling method
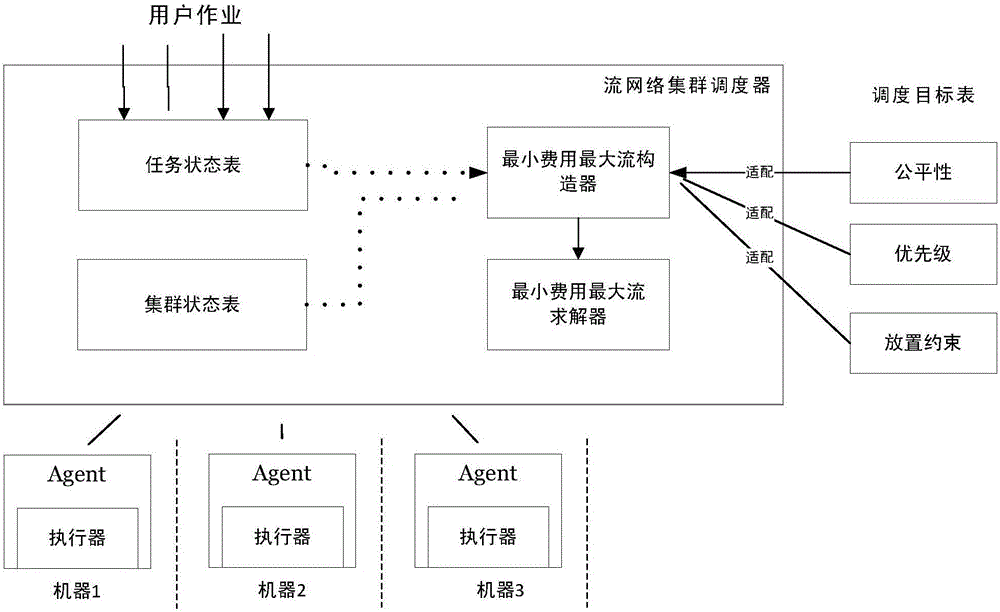
InactiveCN106708625ASolve the problem that it is difficult to apply to various scheduling scenariosReduced solution timeResource allocationCluster stateDistributed computing
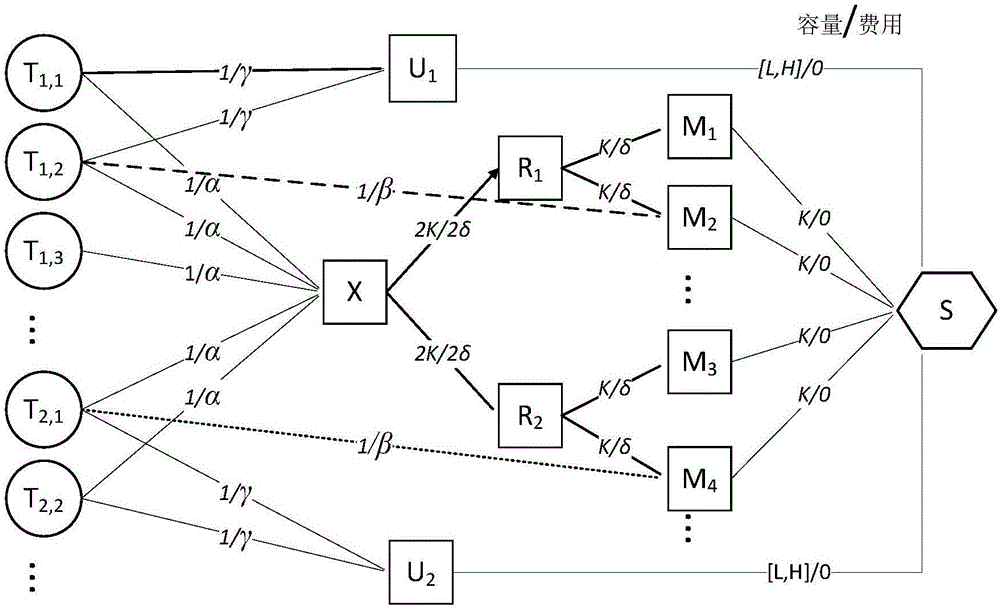
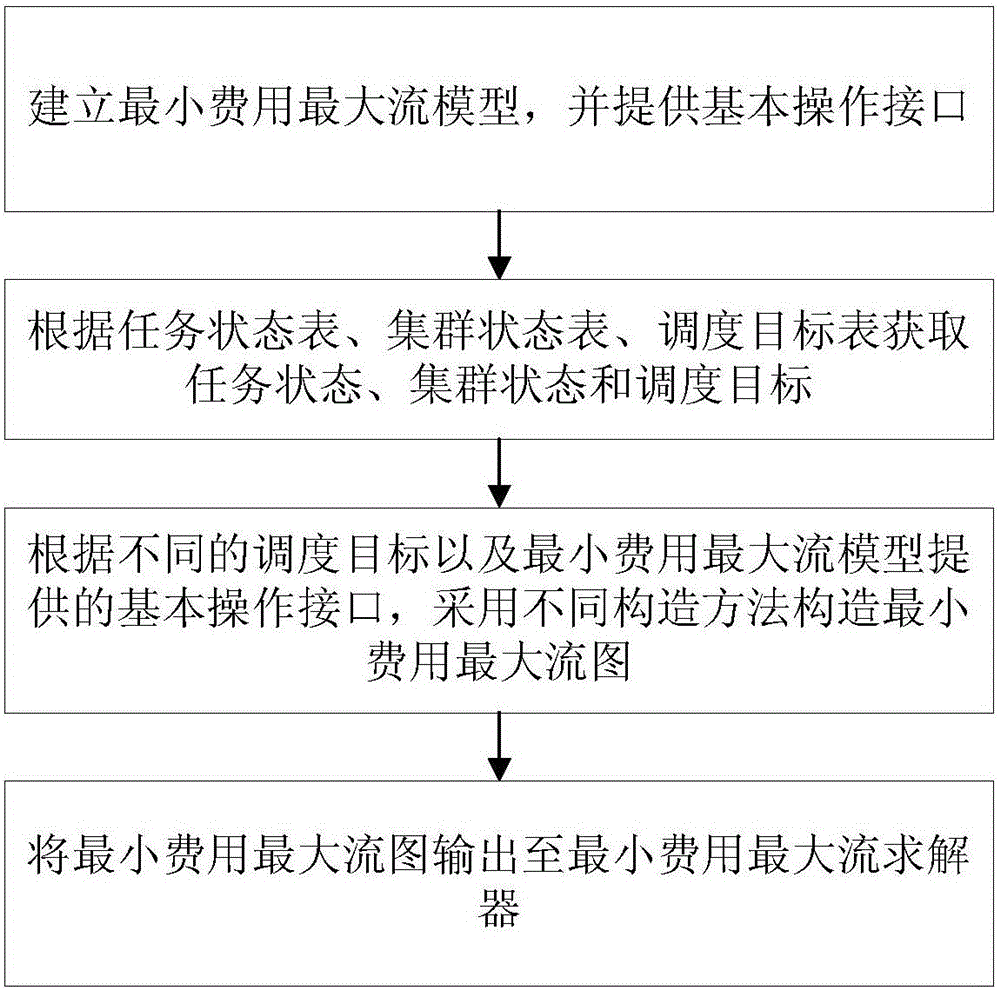
The invention relates to a minimum-cost maximum-flow based large-scale resource scheduling system and a minimum-cost maximum-flow based large-scale resource scheduling method. The system comprises a task state table, a cluster state table, a scheduling target table, a minimum-cost maximum-flow constructor, a minimum-cost maximum-flow solver and a task executor. The task state table is used for receiving and storing task states submitted by users, and the task states include task CPU (central processing unit) utilization rate, memory utilization rate, network I / O, magnetic disk I / O and priority. The cluster state table is used for storing cluster state information including cluster CPU utilization rate, memory utilization rate and network and magnetic disk I / O and updating cluster states when the cluster state change. The scheduling target table is used for storing scheduling targets configured by the users, and the scheduling targets include priority, placement constraint and fairness currently. The minimum-cost maximum-flow constructor is used for selecting the scheduling targets from the scheduling target table according to information of the task state table and the cluster state table to construct a minimum-cost maximum-flow graph. The minimum-cost maximum-flow solver is used for solving the minimum-cost maximum-flow graph constructed by the minimum-cost maximum-flow constructor according to an incremental algorithm. The task executor is responsible for specific execution of tasks. The minimum-cost maximum-flow based large-scale resource scheduling system and the minimum-cost maximum-flow based large-scale resource scheduling method meet the requirement on flexibility of practical business scenarios.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
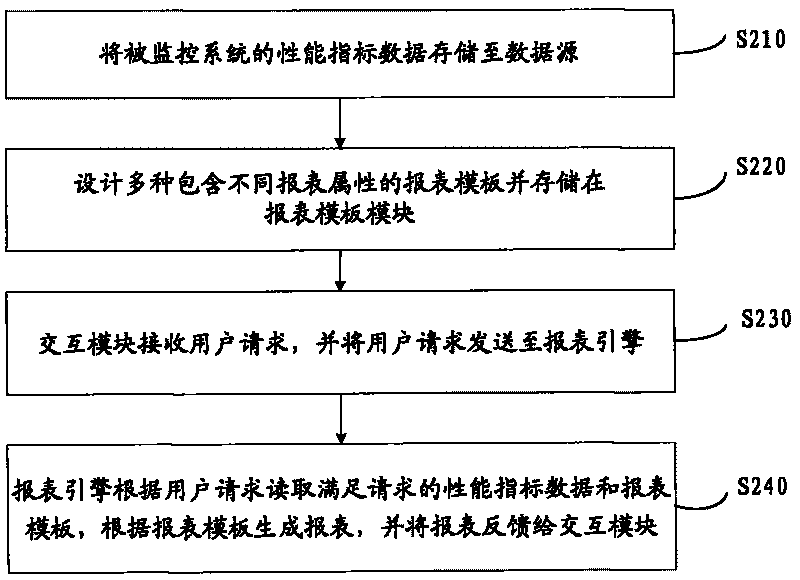
Report generating system and method of cluster monitoring
InactiveCN101694649AMeet the needs of timely understanding of cluster status and evaluation of system performanceMeet scalability requirementsSpecial data processing applicationsCluster systemsCluster state
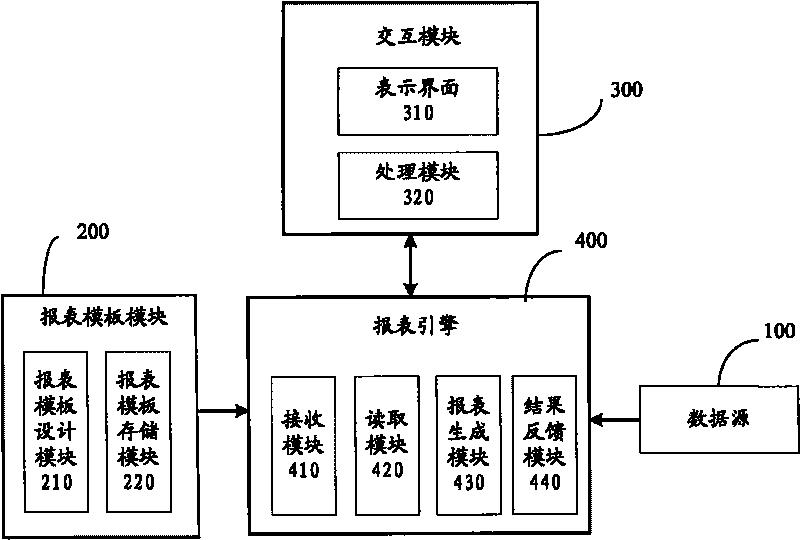
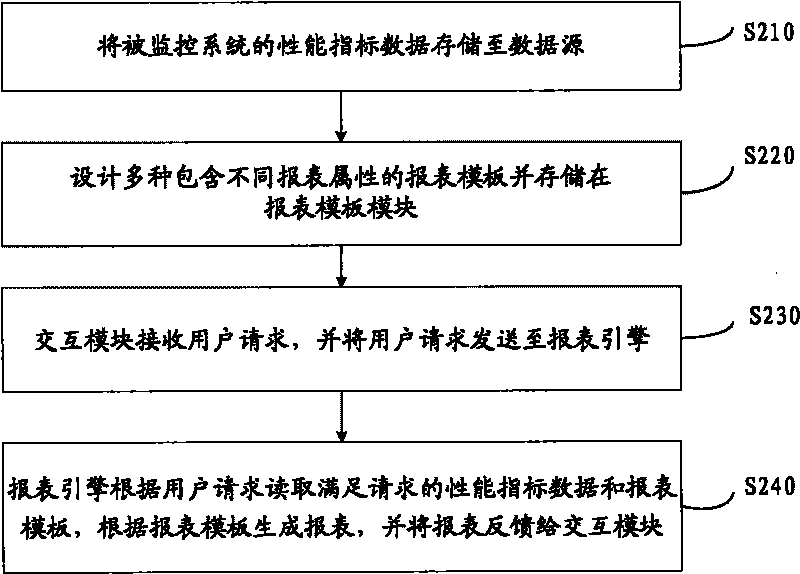
The invention provides report generating system and method of cluster monitoring, wherein the method comprises the following steps: performance index data of a monitored cluster system are stored in a data source; different types of report templates which contain different report attributes are designed and stored in a report template module; an interaction module receives a user request and stores the user request in a report engine; and the report engine receives the user request, reads out performance index data meeting the user request from the data source, reads out report templates meeting the user request from the report template module according to the user request, and sends the report templates to the interaction module for being shown to a user. The invention shows cluster monitoring data to users in a report form, provides different types of data statistics, comparison, analysis and representation modes and meets the requirement of users for learning cluster states and assessing system performance by monitoring data.
Owner:NAT COMP NETWORK & INFORMATION SECURITY MANAGEMENT CENT +1
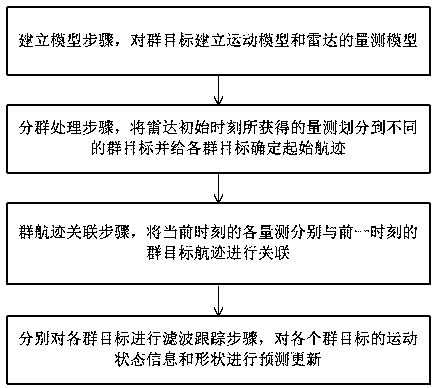
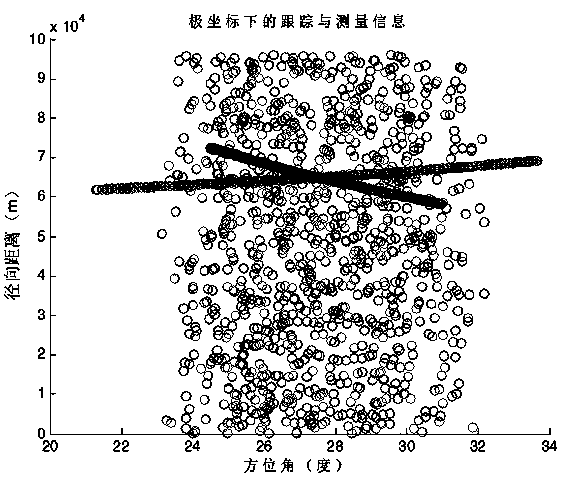
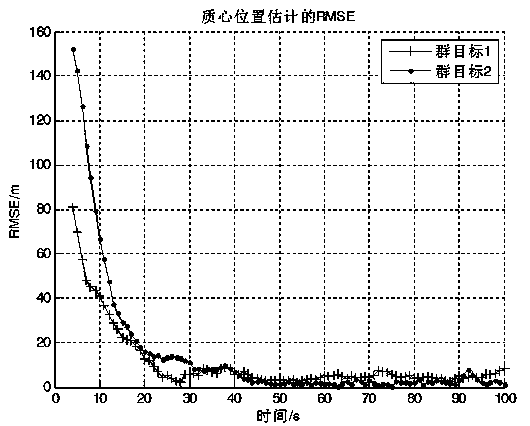
Multi-cluster-target tracking method with shape information
InactiveCN109031279ASave tracking resourcesRadio wave reradiation/reflectionPattern recognitionMulti cluster
The invention discloses a multi-cluster-target tracking method with shape information. The method comprises the following steps of establishing a model, and establishing a motion model and a radar measurement model for the cluster targets; performing clustering processing, wherein the measurement results obtained by the initial moment of the radar are divided into different cluster targets, and aninitial flight path is determined for each cluster target; performing track associating, wherein each measurement value of the current moment is associated with a cluster target track at the previousmoment separately; and performing filtering and tracking on the cluster targets separately, and carrying out prediction and updating on the motion state information and the shape of each cluster target. According to the multi-cluster-object tracking method with shape information, a random matrix for describing the cluster target shape is added in the cluster state, so that the radar tracking resources are saved, more reference information is provided for a driver by estimating the cluster shape in real time, and a higher practical application value is achieved.
Owner:中国人民解放军海军航空大学青岛校区
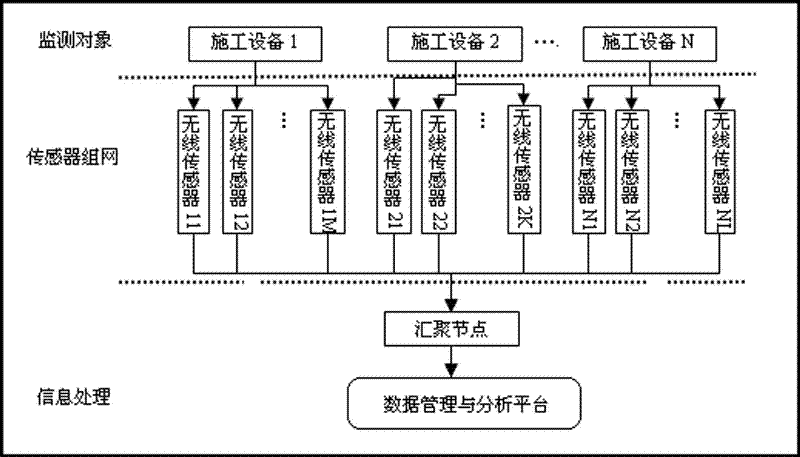
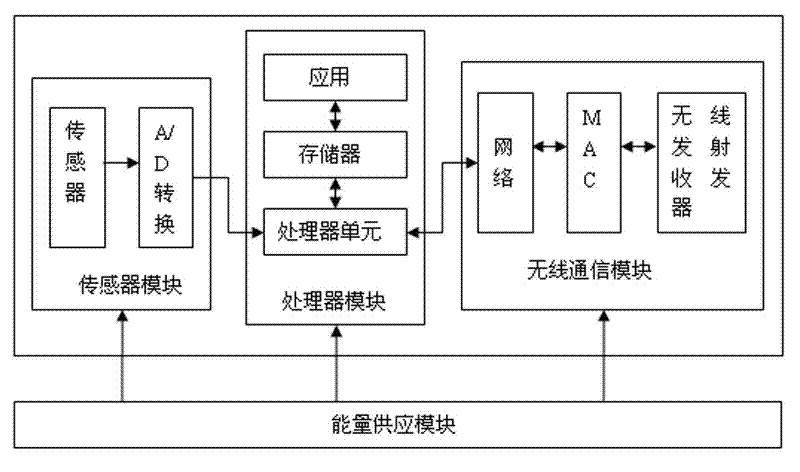
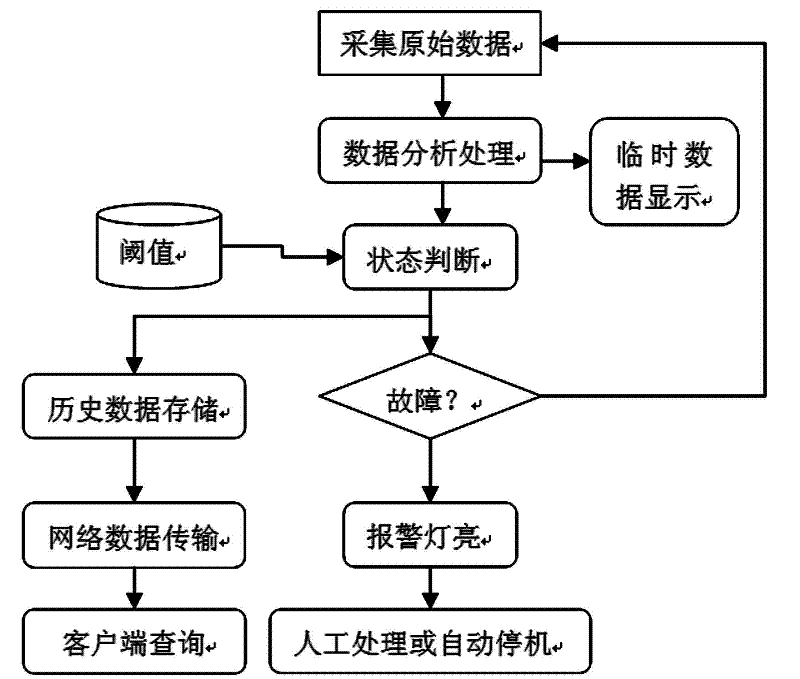
WSN (Wireless Sensor Network) based cluster state monitoring system and method
InactiveCN102404401AEfficient data processingAvoid under-maintenanceTransmission systemsNetwork topologiesDiagnostic systemInstrumentation
The invention relates to a WSN (Wireless Sensor Network) based cluster state monitoring system; a wireless sensor network formed by a plurality of wireless sensor nodes arranged on equipment is connected with a sink node, the sink node is connected with a data management and analysis platform, the data on all the wireless sensor nodes is directly transmitted to the sink node or is transmitted to the sink node in a hop-by-hop manner, the sink node is a sensor mode for enhancing data processing function or is gateway equipment only provided with a wireless communication interface. The invention provides the WSN based cluster state monitoring system and a method; the working state information of construction equipment can be accurately acquired by the wireless sensor network, and a fault diagnostic system constructed based on the virtual instrument technology can timely find the fault type and the fault part, and can gives an alarm at the key moment, so as to avoid inadequate maintenance and excessive maintenance of the equipment, prolong the service life of the equipment, reduce the maintenance cost of the equipment and ensure the construction safety.
Owner:CHINA THREE GORGES UNIV
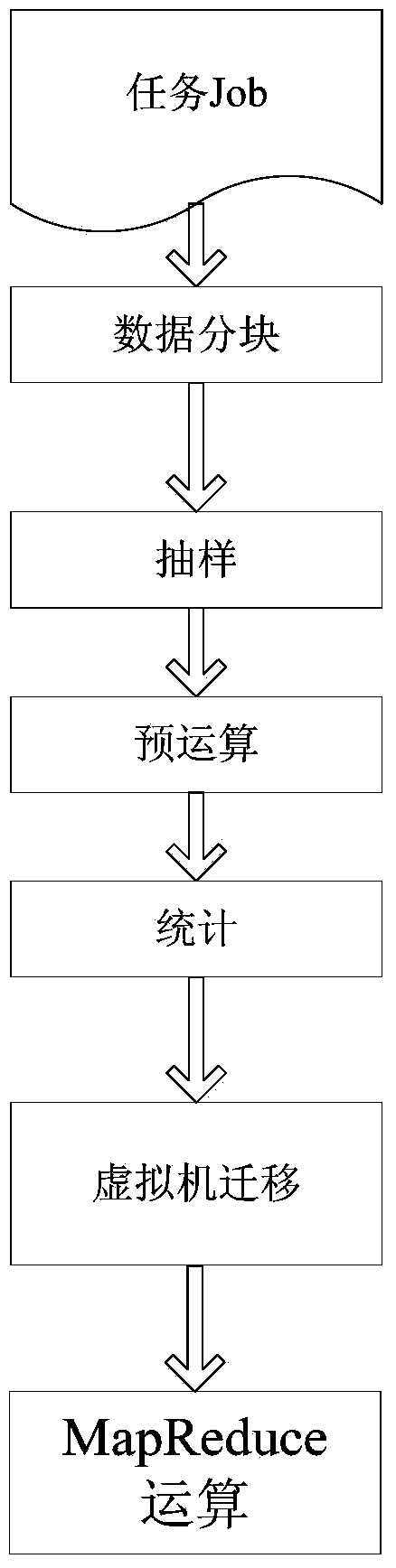
High-performance MapReduce realization mechanism based on dynamic migration of virtual machine
ActiveCN104008012AStrengthen localization operationsImprove performanceProgram initiation/switchingSoftware simulation/interpretation/emulationCluster stateCloud management
The invention discloses a high-performance MapReduce realization mechanism based on dynamic migration of a virtual machine. The high-performance MapReduce realization mechanism based on dynamic migration of the virtual machine comprises the steps of: monitoring a clustering state in real time by applying a cloud management platform of a CloudStack virtual machine, sampling split data segmentations and counting Map task sources corresponding to each key received by the virtual machine where the Reduce task exists, so as to obtain a Map task source which generates most key values; regarding the physic machine of the virtual machine where the obtained Map task resources exist as a migration target of the virtual machine where corresponding Reduce task exists; as the core, enabling the Reduce task to receive output of the Map task with the same key value locally as far as possible through dynamic migration of the virtual machine. Therefore, the network bandwidth is economized.
Owner:长沙麓云信息科技有限公司
Periodic Probabilistic Two-Dimensional cluster State Generator with Arbitrary Interconnections
ActiveUS20150036967A1Synchronization is simpleSimple electrical inputElectromagnetic transmission non-optical aspectsOptical waveguide light guideNear neighborCluster state
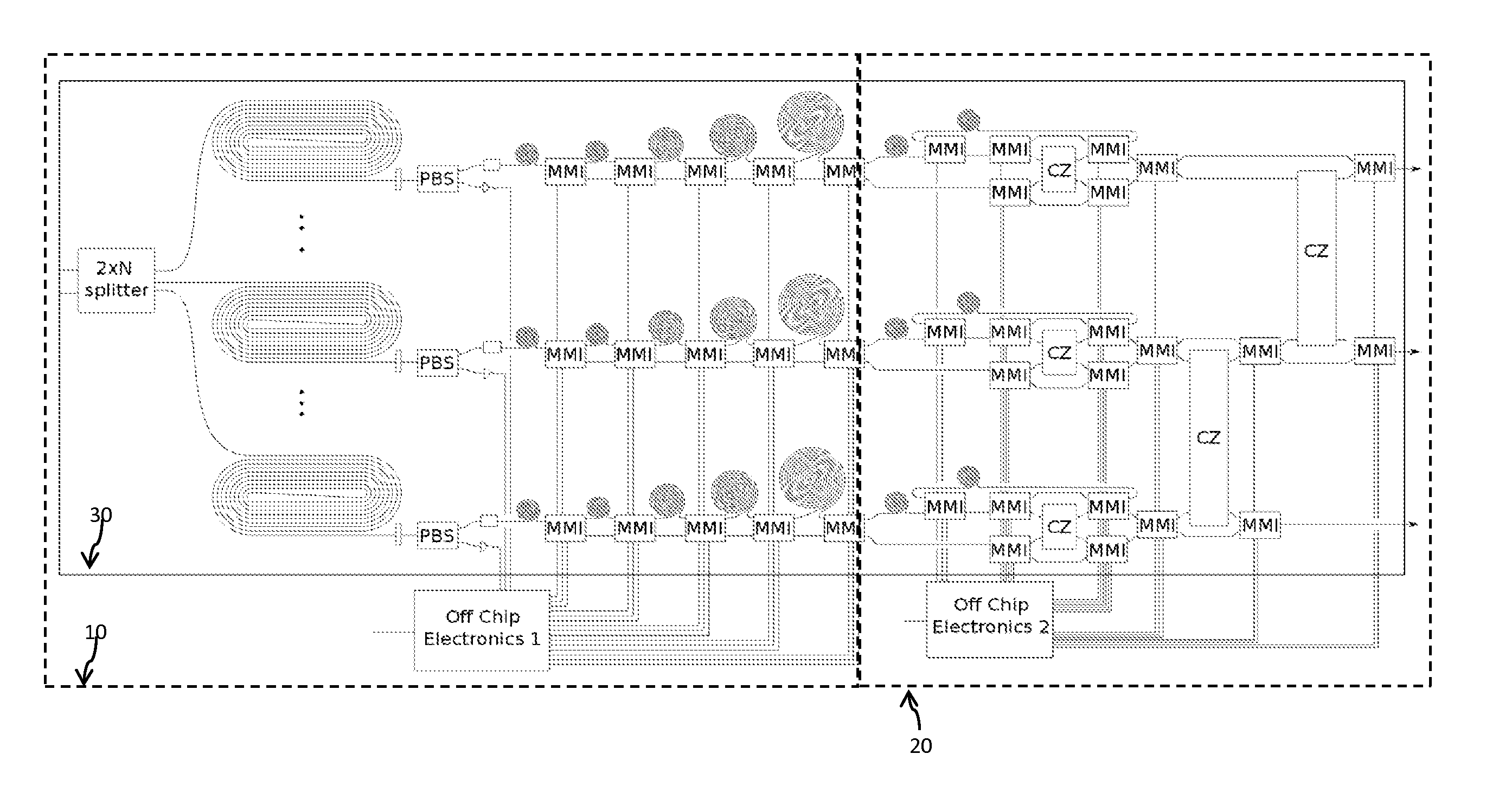
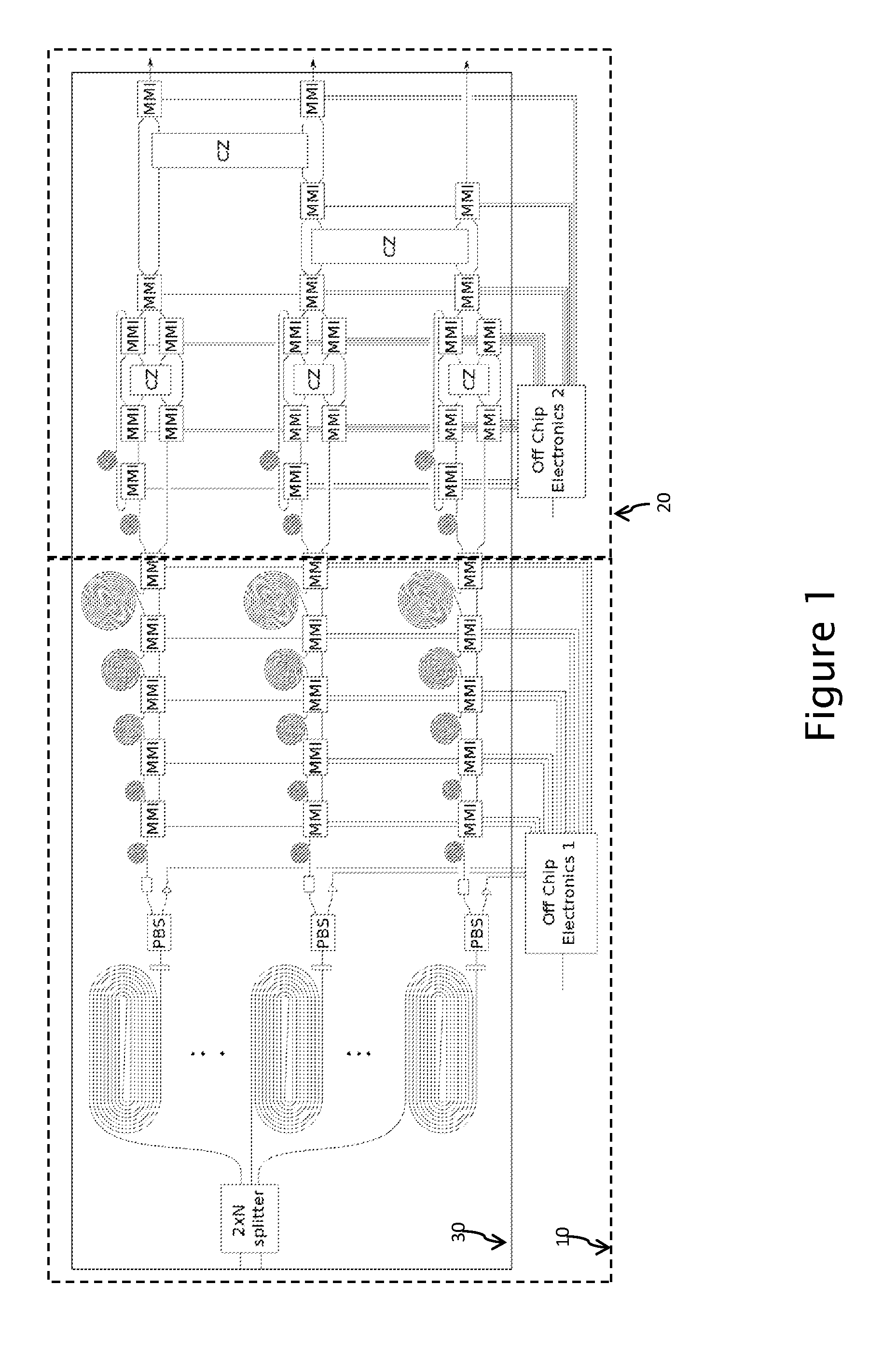
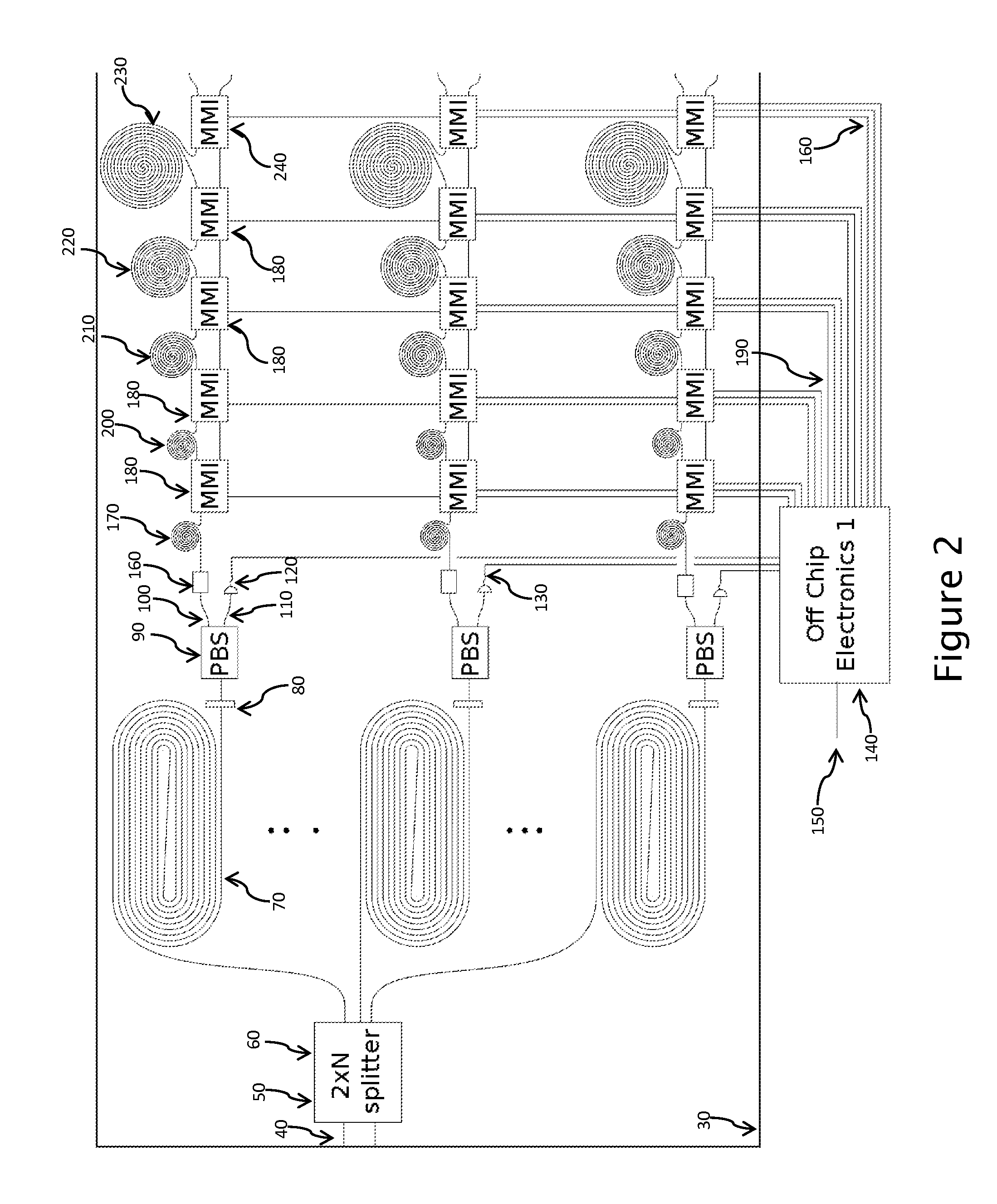
A Periodic Cluster State Generator (PCSG) consisting of a monolithic integrated waveguide device that employs four wave mixing, an array of probabilistic Photon Guns, single mode Sequential Entanglers and an array of controllable entangling gates between modes to create arbitrary size and shape cluster states with several constraints. The cluster state is assumed linear or square lattice. Only nearest neighbor qubits are entangled. Such a cluster state resource has been proven to be able to perform universal quantum computing if the initial state is large enough.
Owner:THE UNITED STATES OF AMERICA AS REPRESETNED BY THE SEC OF THE AIR FORCE
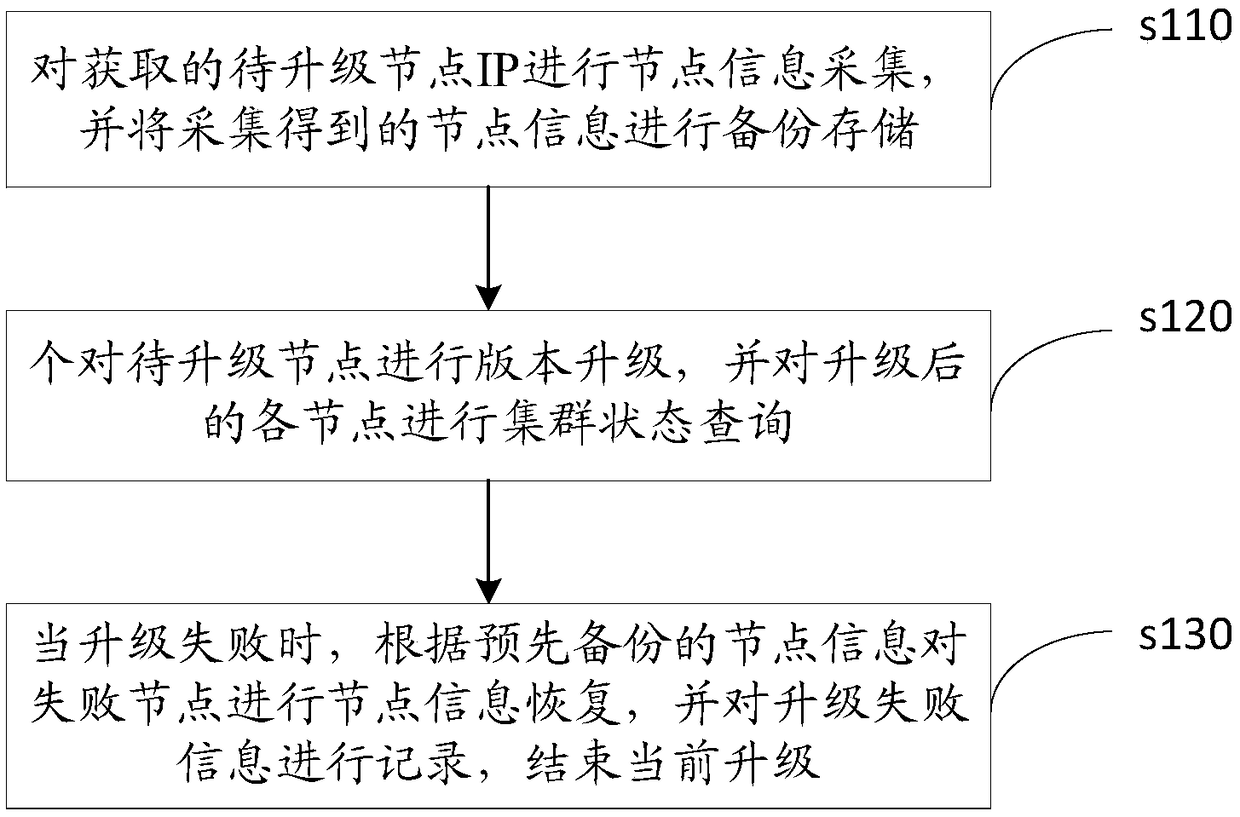
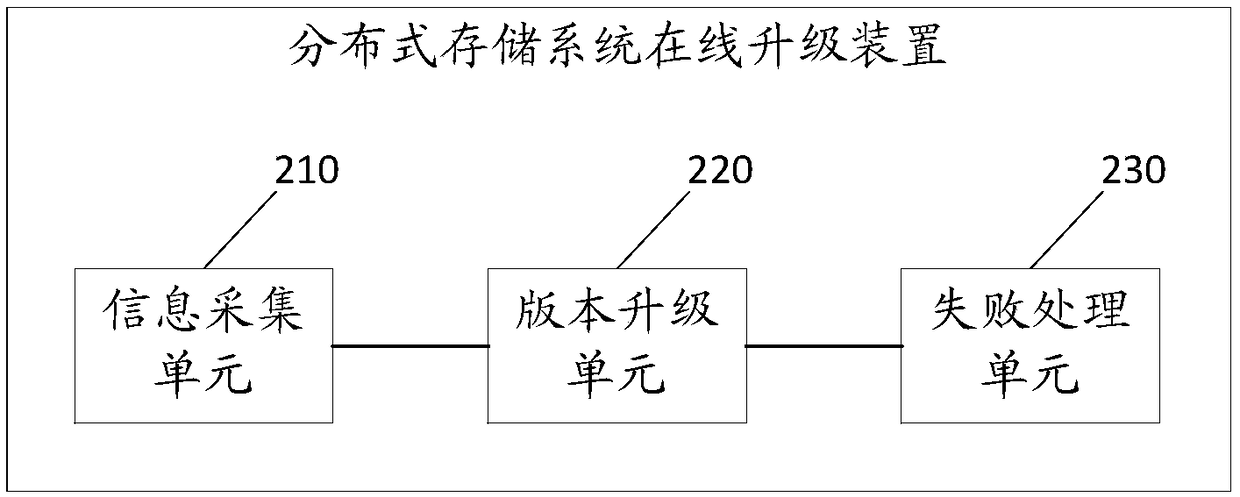
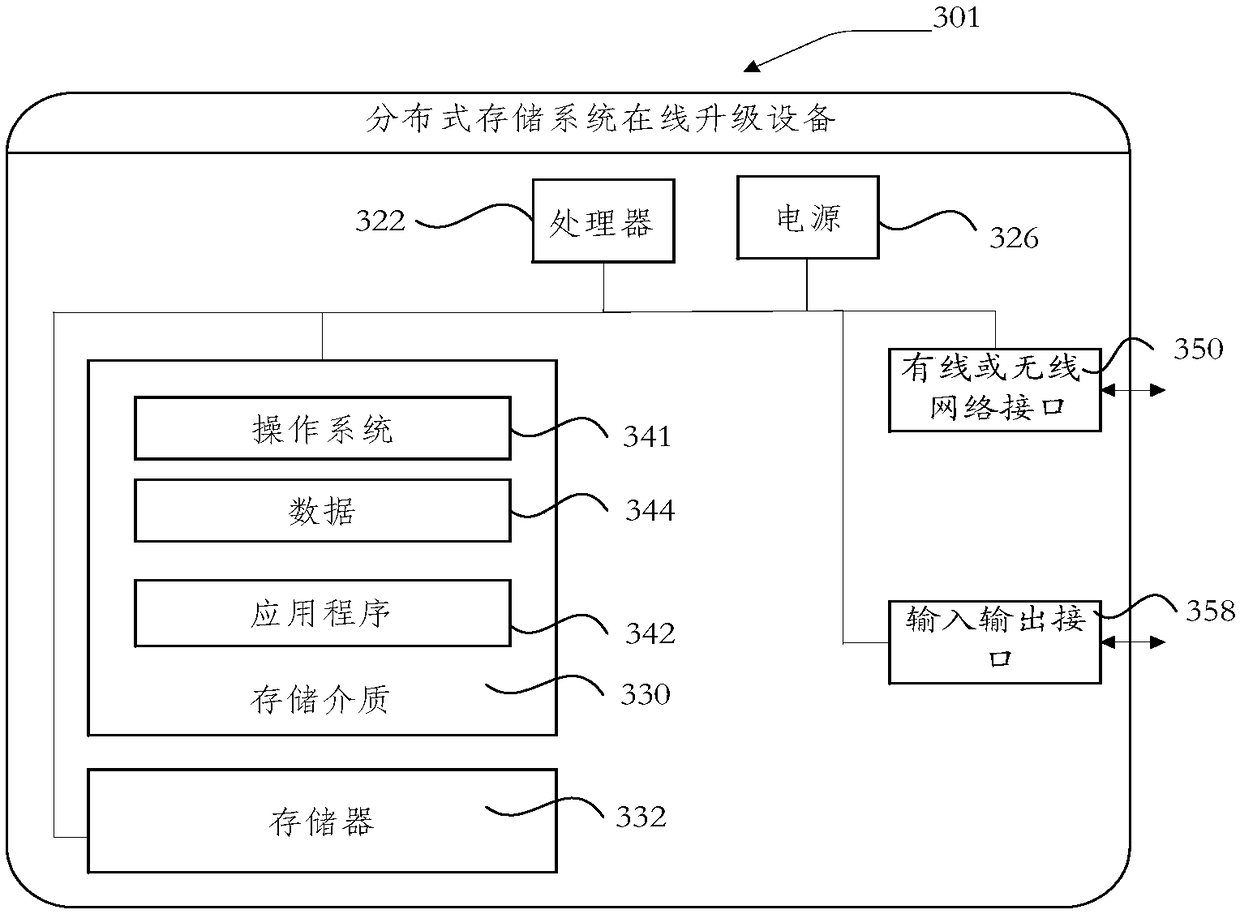
Online update method, device and equipment of distributive storage system and storage medium
InactiveCN108768758AGuaranteed continuous availabilityAvoid situations where the installation succeeds but doesn't workData switching networksCluster stateDatabase
The invention discloses an online update method of a distributive storage system. The method comprises the following steps: acquiring node information of an obtained node IP to be updated, and performing backup copying and storing on the acquired node information; updating the version of each node to be updated, and querying the cluster state of each updated node; in case of failure in updating, recovering the node information of the failed node on the basis of the node information which is subjected to backup copy in advance, and recording the update failure information; and finishing the current update. According to the method, the version of each node is updated, and the storage service remains in the updating process; various abnormal condition are automatically handled during updating; the distributive storing system can be smoothly updated in the application scene, so that the user experience is improved. The invention also discloses an online updating device and equipment of thedistributive storing system and a readable storage medium which have the beneficial effects.
Owner:ZHENGZHOU YUNHAI INFORMATION TECH CO LTD
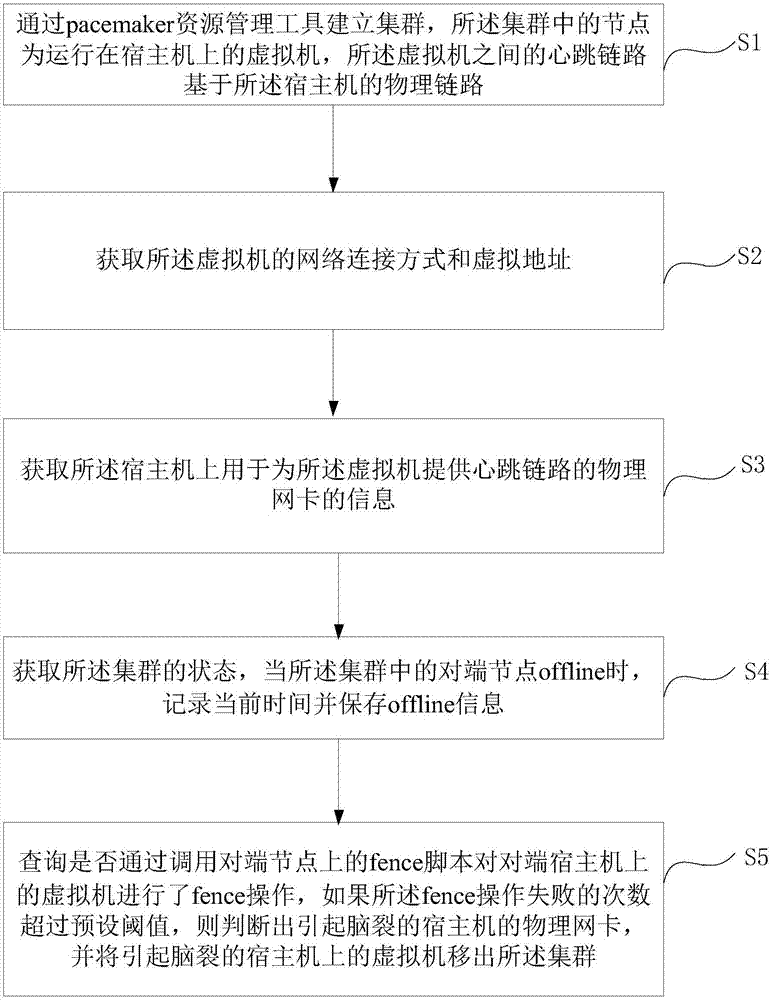
Method and device for realizing high availability of cross-node virtual machine cluster
ActiveCN107404522ASolving the cluster split-brain problemAvoid cluster status exceptionsData switching networksNODALNetwork connection
The invention discloses a method and a device for realizing high availability of a cross-node virtual machine cluster. The method comprises the following steps of establishing a cluster through a pacemaker resource management tool; obtaining network connection modes and virtual addresses of virtual machines; obtaining information of a physical network card use for providing a heartbeat link for the virtual machines on a host; obtaining a state of the cluster; and querying whether to carry out fence operation on the virtual machines on an opposite terminal host through calling a fence script on an opposite terminal node, if the number of failures of the fence operation exceeds a preset threshold, determining the physical network card of the host for causing the fissure and removing the virtual machines on the host for causing the fissure from the cluster. According to the method and the device for realizing the high availability of the cross-node virtual machine cluster, a problem of failure of the physical network card of the host or cluster fissure caused by failure of an external switch can be solved, the cluster state exception caused by an external factor is avoided, and the effective external service provision is guaranteed.
Owner:INSPUR SUZHOU INTELLIGENT TECH CO LTD
Remote teleportation method based on four-bit Cluster state
InactiveCN108900254AImprove transmission efficiencySolving the problem of long-distance long-distance quantum communicationPhotonic quantum communicationAlice and BobNetwork termination
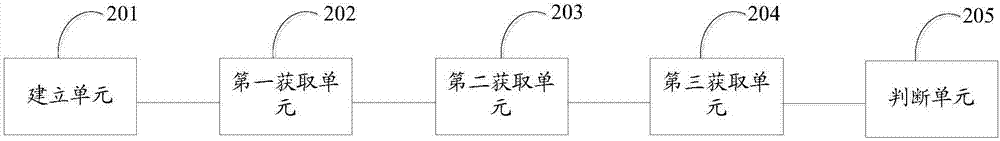
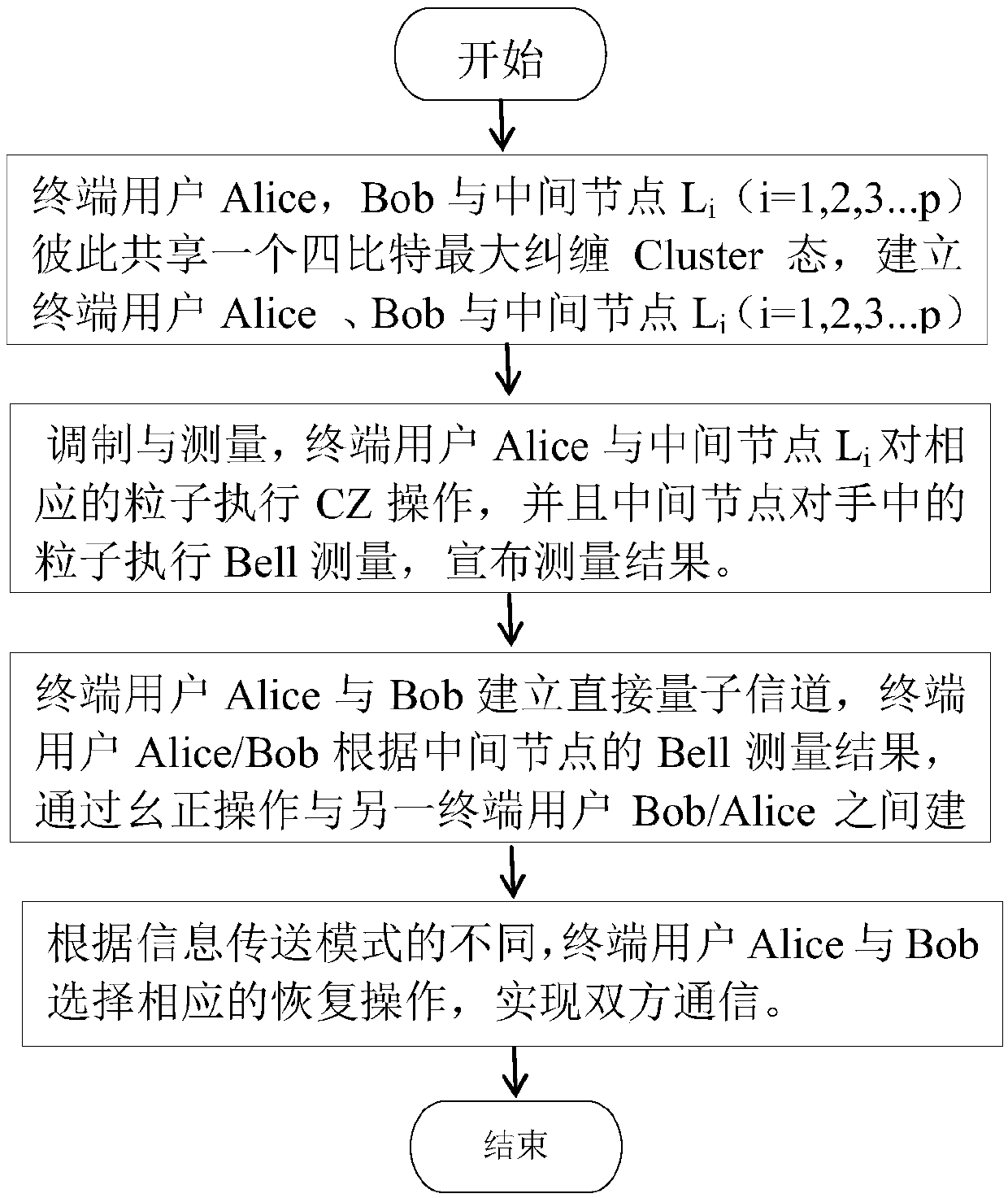
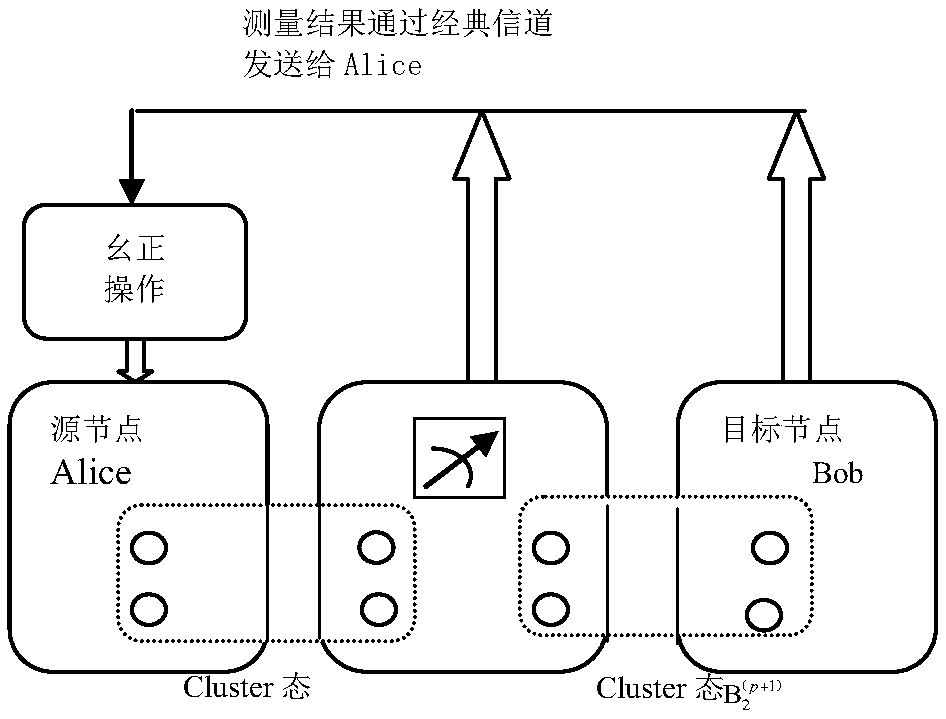
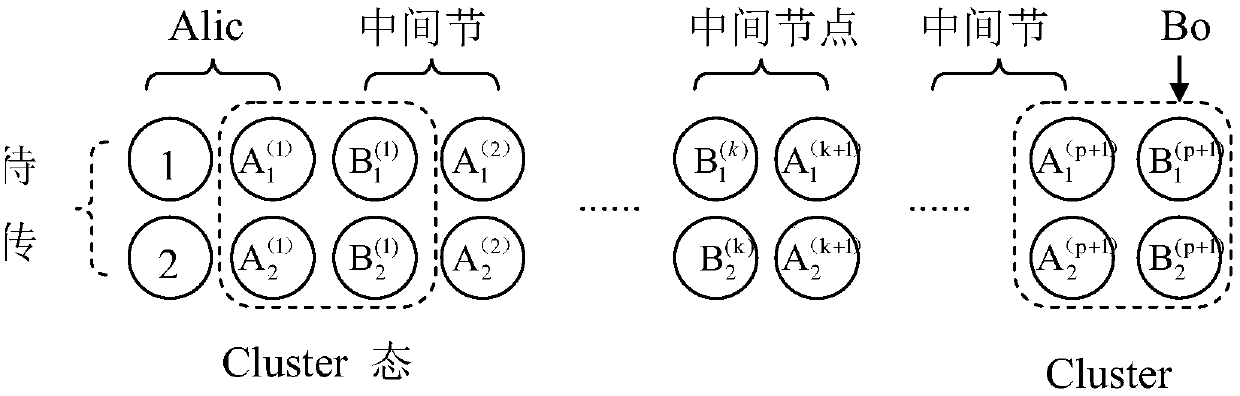
The invention discloses a remote teleportation method based on a four-bit Cluster state. For network terminal users Alice and Bob, through help of an intermediate node, communication between a networkterminal Alice and the other terminal user Bob is completed. The method comprises the four steps that 1, the four-bit most entangled Cluster state is shared by the terminal users Alice, Bob and the intermediate node Li (i=1, 2, 3, ..., p), and a quantum entanglement channel of the terminal users Alice and Bob and the intermediate node Li (i=1, 2, 3, ..., p) is built; 2, modulation and measurementare conducted, wherein CZ operation is conducted on corresponding particles by the terminal user Alice and the intermediate node Li, moreover, Bell measurement is conducted on the particles in handsby the intermediate node, and measurement results are announced; 3, a direct quantum channel between the terminal user Alice / Bob and the other terminal user Bob / Alice is built according to the Bell measurement results of the intermediate node through unitary operation; 4, according to difference of information transferring modes, the terminal users Alice and Bob choose corresponding restoring operation according to the Bell measurement results of each other to achieve intercommunication.
Owner:SUZHOU UNIV
Data access method under hybrid storage architecture
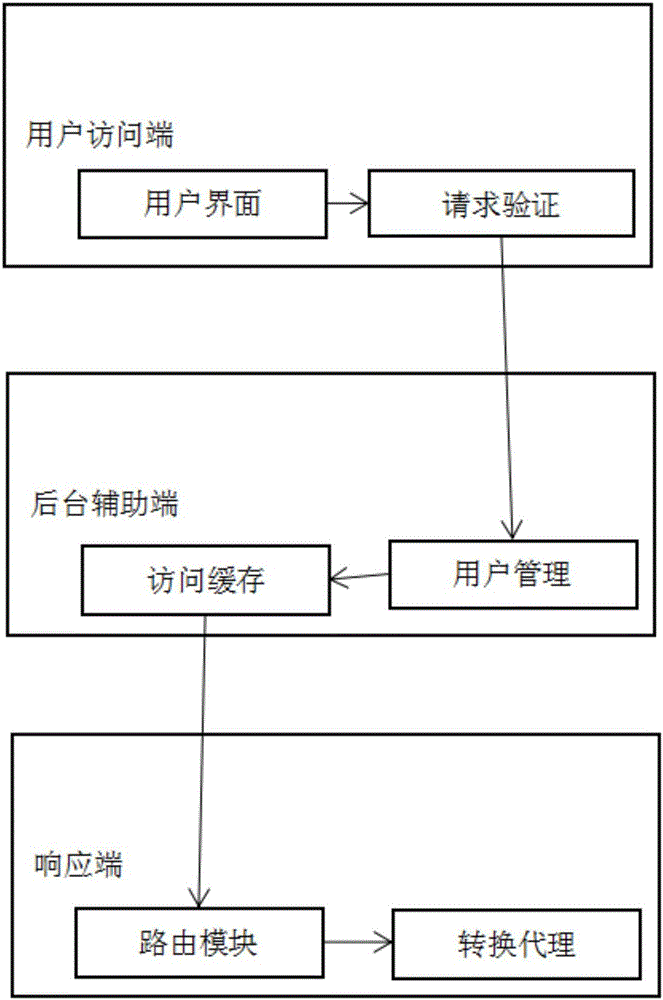
ActiveCN105956029AEasy to manageEasy to useDatabase management systemsDatabase distribution/replicationCluster stateData access
The invention discloses a data access method under hybrid storage architecture, and overcomes the problem that database management and data access exhibit complexity and database system changes and faults lack uniform management under the hybrid storage architecture. The data access method under the hybrid storage architecture comprises the following steps: 1) processing a data request and 2) carrying out software change and fault processing. The step 1) comprises the following steps: (1) verifying the access request of a user: requesting a verification module to inquire the cache of a metadata information item to finish verification, and distributing one partial cache, which aims at a database or cluster state zone bit and the activation bit of an agent module, of one piece of metadata information to the verification module, and utilizing the cache to quicken verification speed; (2) adding the data access request to the access cache; (3) carrying out route processing on the request; (4) processing a transactional agent; (5) executing the request; and (6) generating a result or a report of a uniform format. The step 2) comprises the following steps: (1) carrying out the periodic detection and response of the metadata information; (2) carrying out software change processing; and (3) carrying out fault processing.
Owner:JILIN UNIV
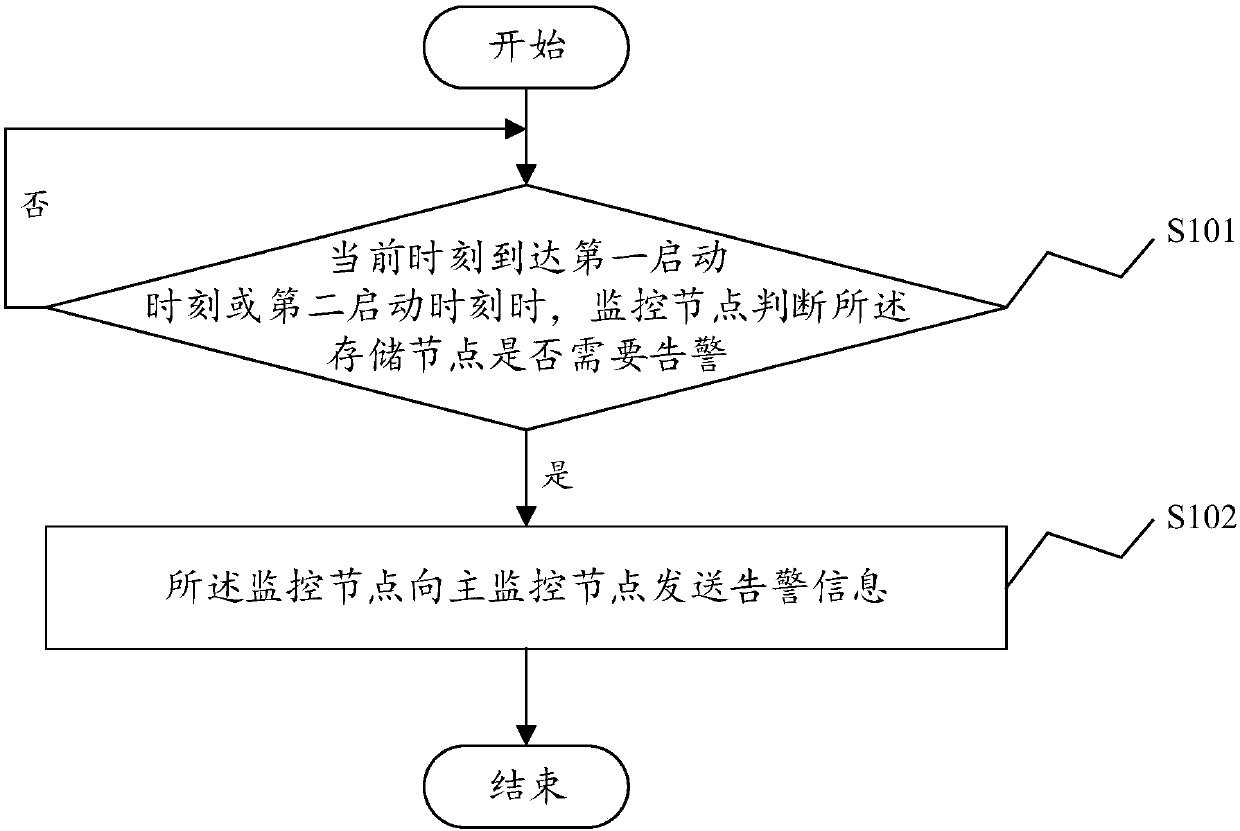
Distributed storage cluster warning method, system and device
ActiveCN108038043AGuaranteed timelinessWithout omissionHardware monitoringCluster stateWarning system
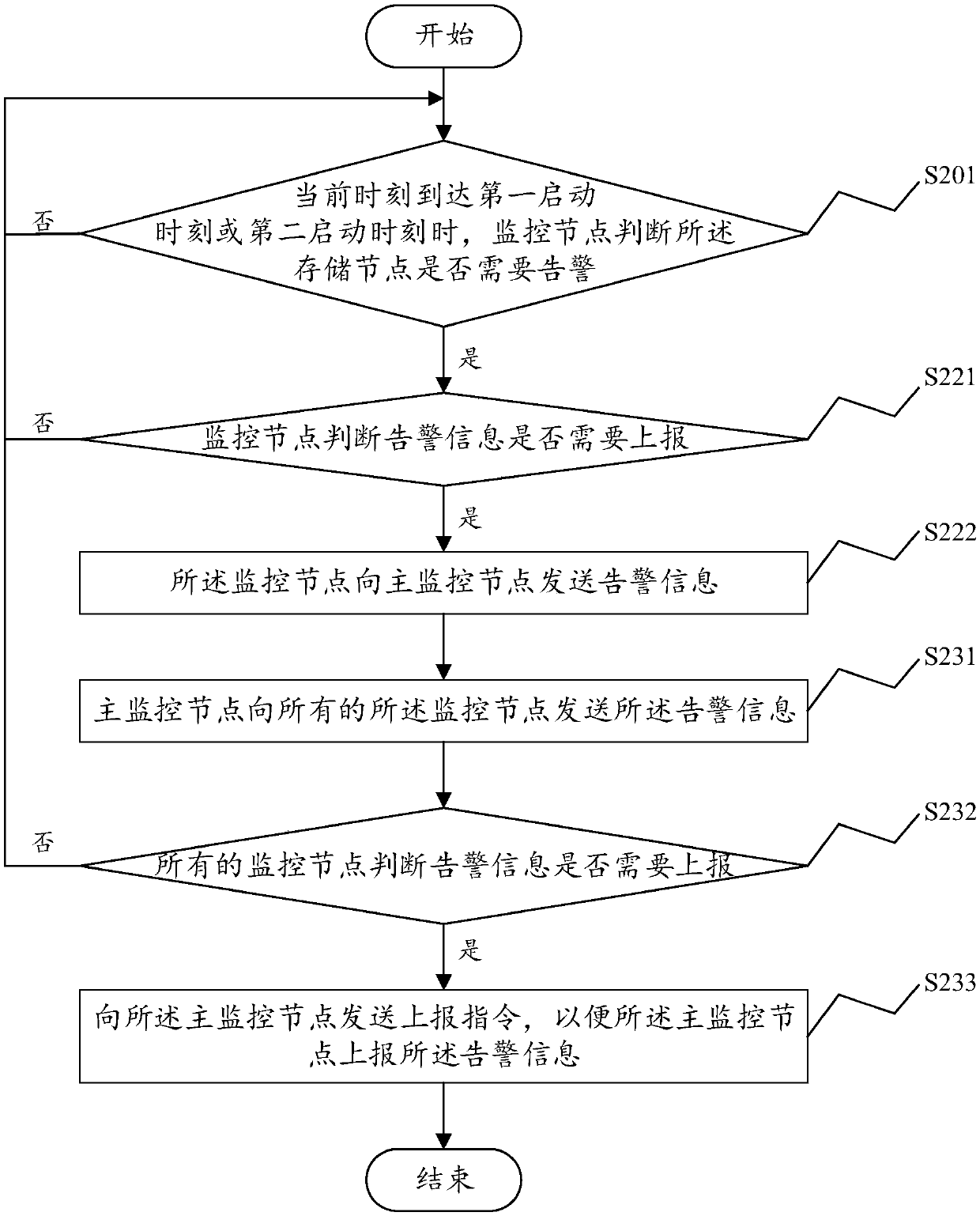
The invention discloses a distributed storage cluster warning method. The method comprises the steps that when a current moment reaches a first startup moment or a second startup moment, a monitoringnode judges whether a storage node needs to be warned or not, wherein the first startup moment is a moment when the storage node in the distributed storage cluster is subjected to data reading-writing, and the second startup moment is a preset periodic moment; and if yes, the monitoring node sends warning information to a main monitoring node. According to the warning method disclosed by the invention, by adopting a joint detection mode, namely, by adopting cluster state update triggering detection under the condition that the storage node is subjected to the data reading-writing, a warning can be timely detected, so that the timeliness of warning detection is ensured; and the warning is detected by utilizing timed communication of the monitoring node and the storage node under the condition of no data reading-writing, so that the completeness of warning detection is ensured. The invention furthermore discloses a distributed storage cluster warning system and device and a computer readable storage medium, which also have the abovementioned technical effects.
Owner:ZHENGZHOU YUNHAI INFORMATION TECH CO LTD
An information physical modeling and control method for aggregating large-scale air conditioner loads
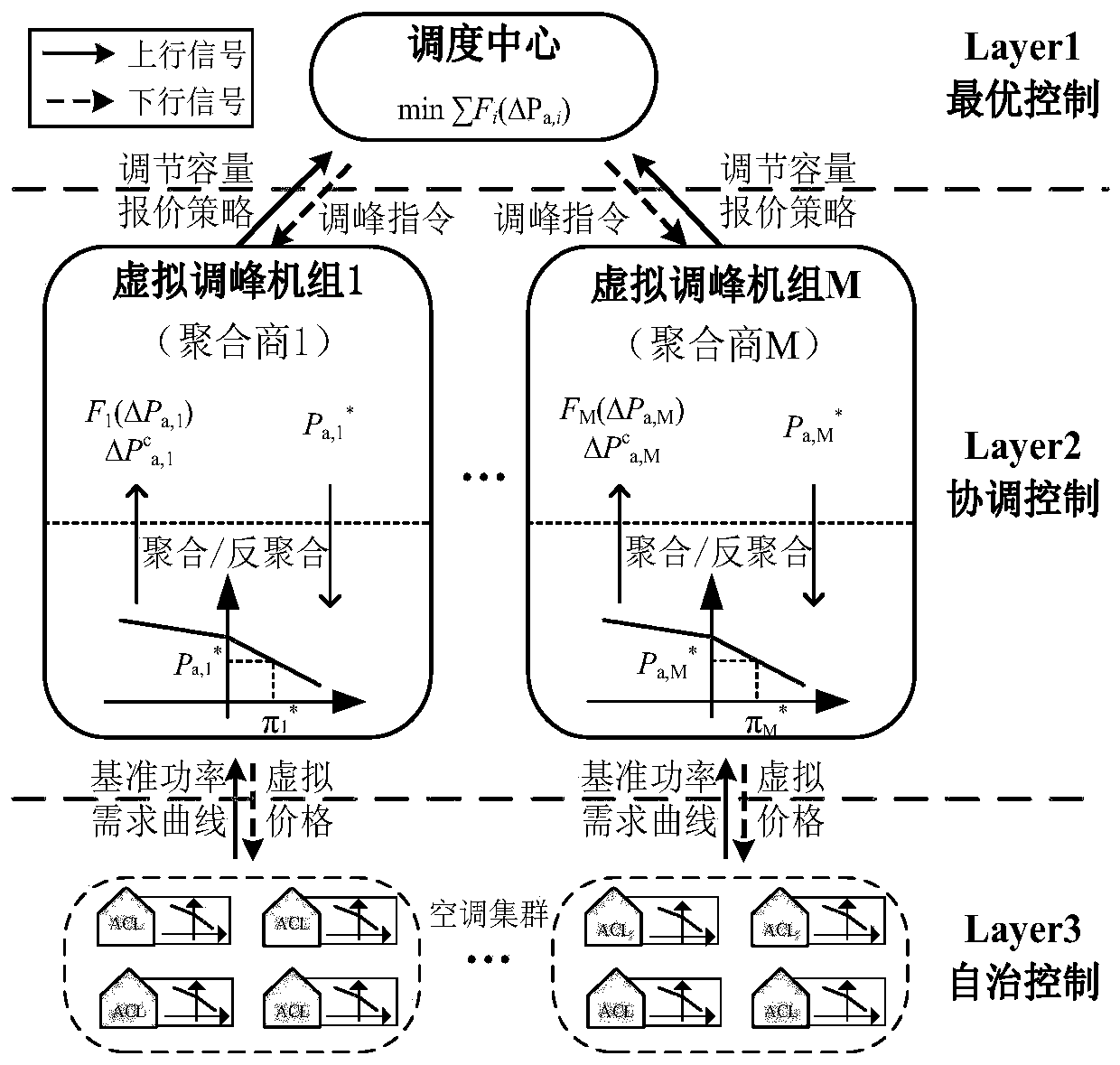
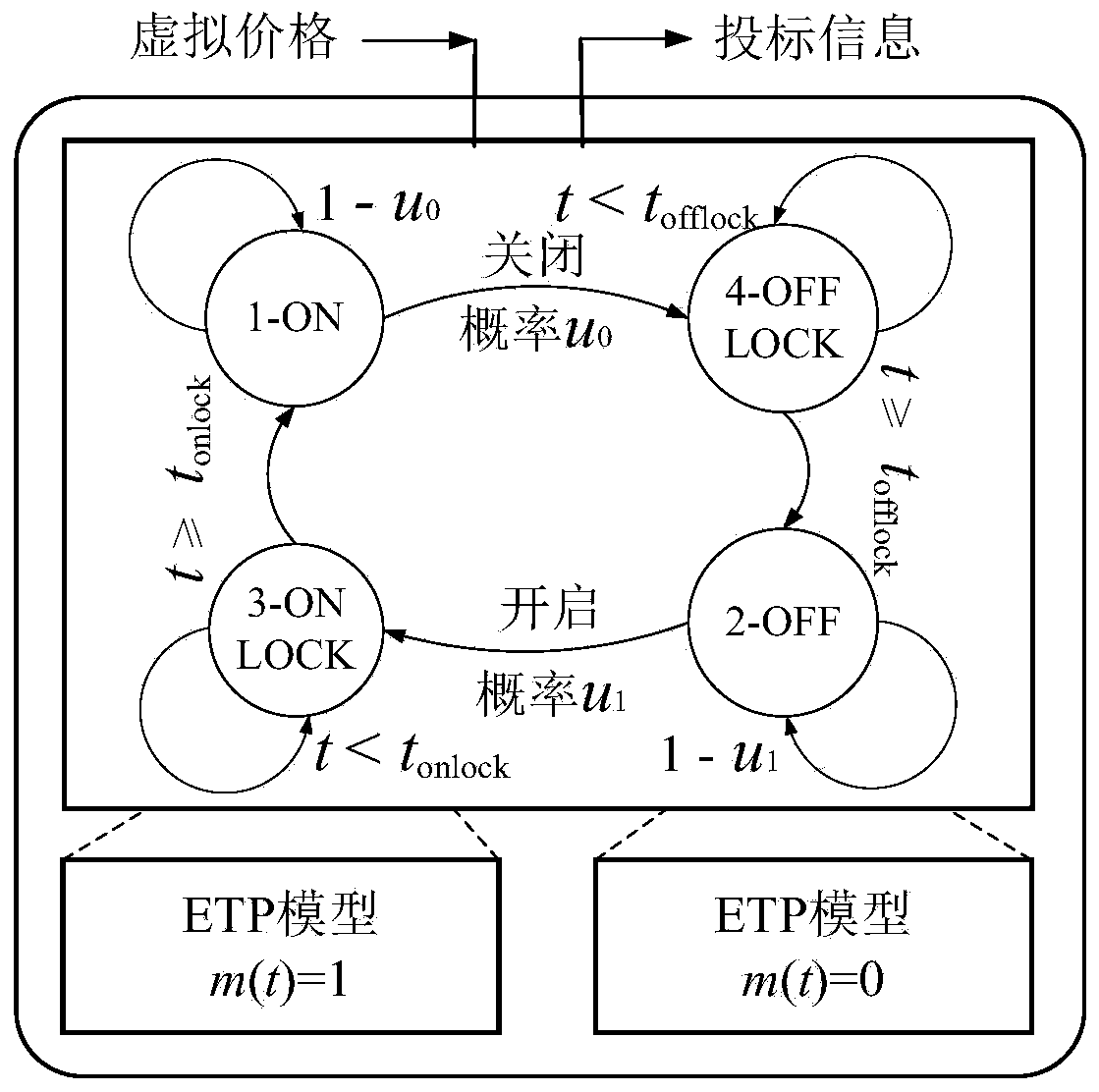
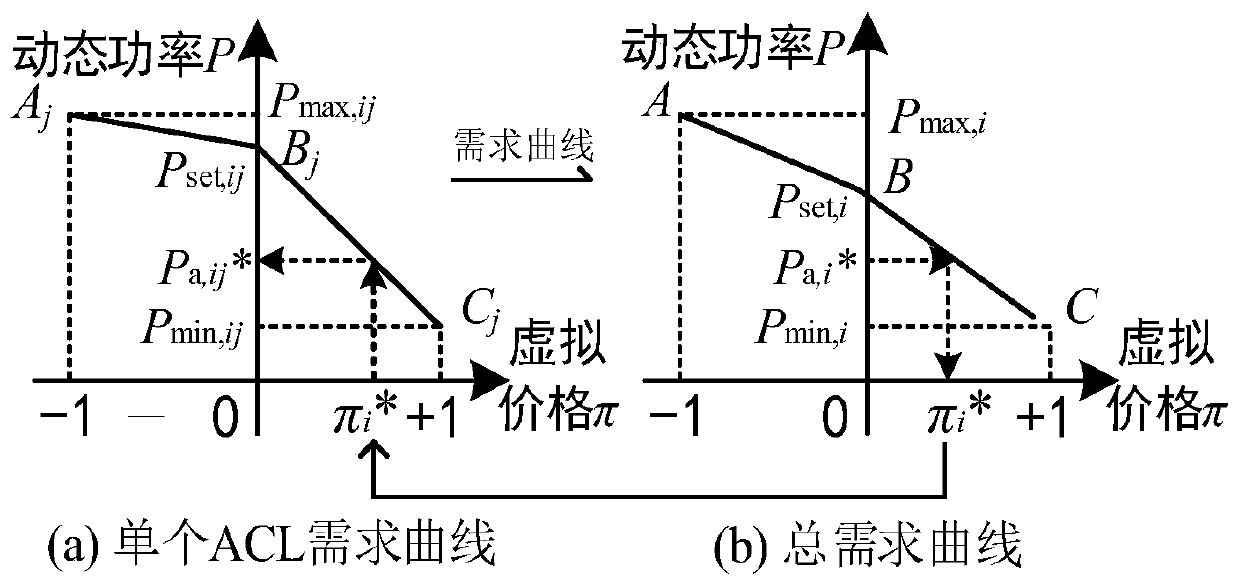
ActiveCN109934470AProtect data privacyReduce communication costMechanical apparatusSpace heating and ventilation safety systemsHybrid systemOptimal scheduling
The invention relates to an information physical modeling and control method for aggregating large-scale air conditioner loads, and the method comprises the steps: the air conditioner loads is regarded as an information physical system (CPS) at a load layer, an air conditioner load probability control method based on a semi-Markov process is provided, and the locking time of an air conditioner canbe guaranteed and the diversity of a cluster state is kept; A hybrid system model is utilized to establish a coupling relation between the air conditioner load physical process and the control process, and autonomous control over the air conditioner load is achieved; In an aggregator layer, a coordination control method for aggregating air conditioner loads into virtual peak shaving units is provided based on a market balance mechanism, and the method can effectively protect user data privacy and remarkably reduce the communication cost. Meanwhile, the virtual peak regulation unit can providea quotation curve and regulation capacity similar to a conventional unit for scheduling, so that the virtual peak regulation unit participates in optimal scheduling of a power grid layer. Compared with the prior art, the method has the advantages of remarkably reducing the communication cost, facilitating optimal scheduling and the like.
Owner:SHANGHAI JIAO TONG UNIV
Four-particle cluster state multi-hop stealth transfer method based on non-maximum entanglement cluster state
ActiveCN110572219AImprove transmission efficiencySolving the problem of long-distance long-distance quantum communicationPhotonic quantum communicationAlice and BobInformation transmission
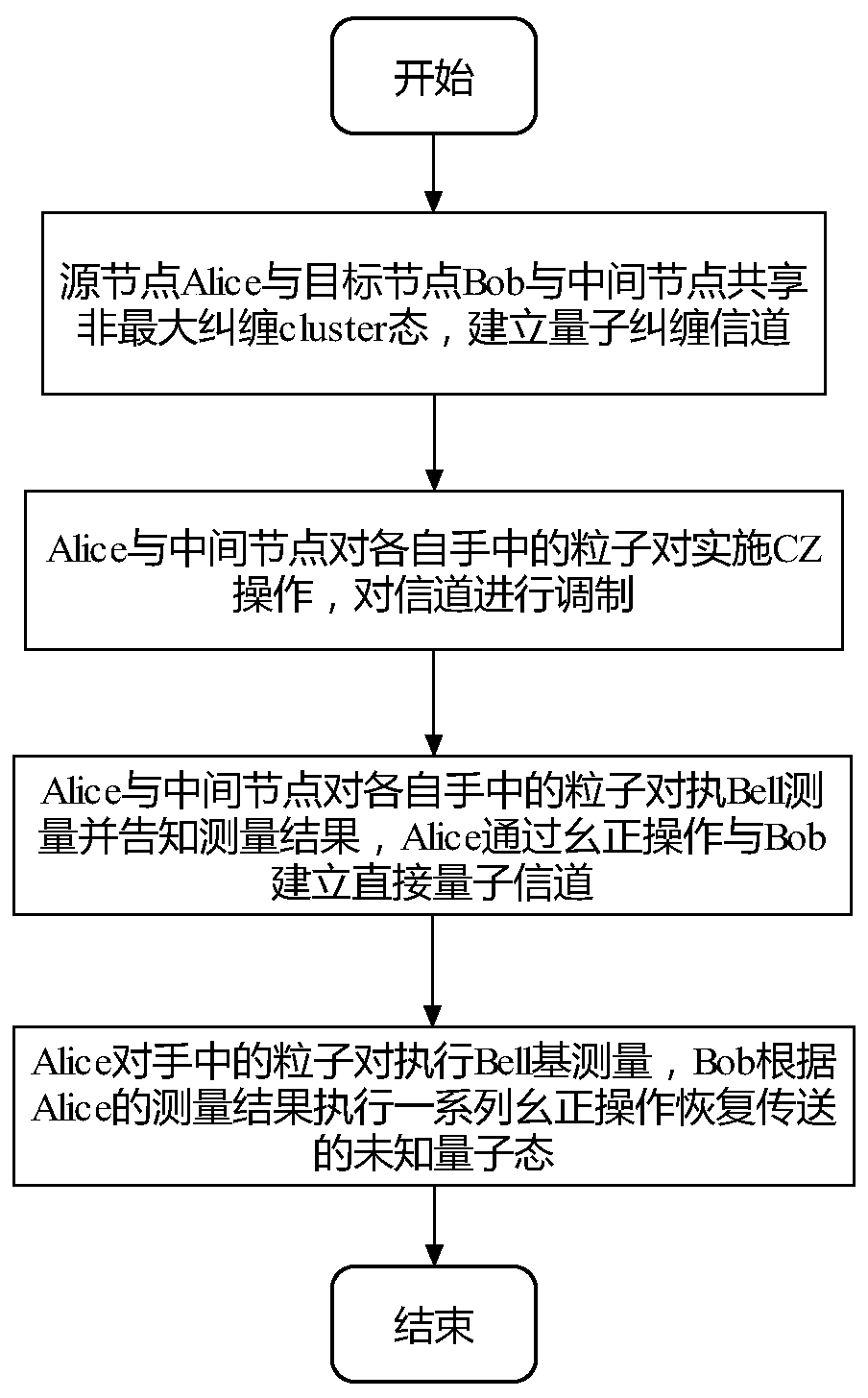
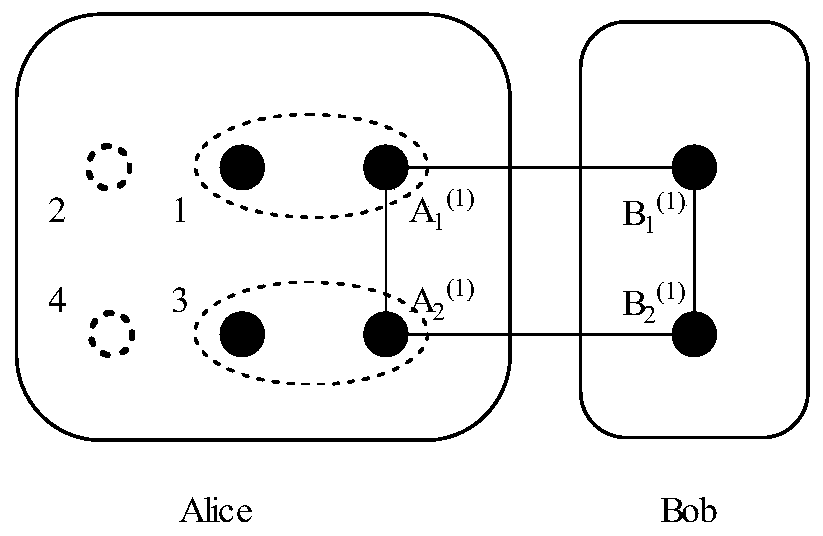
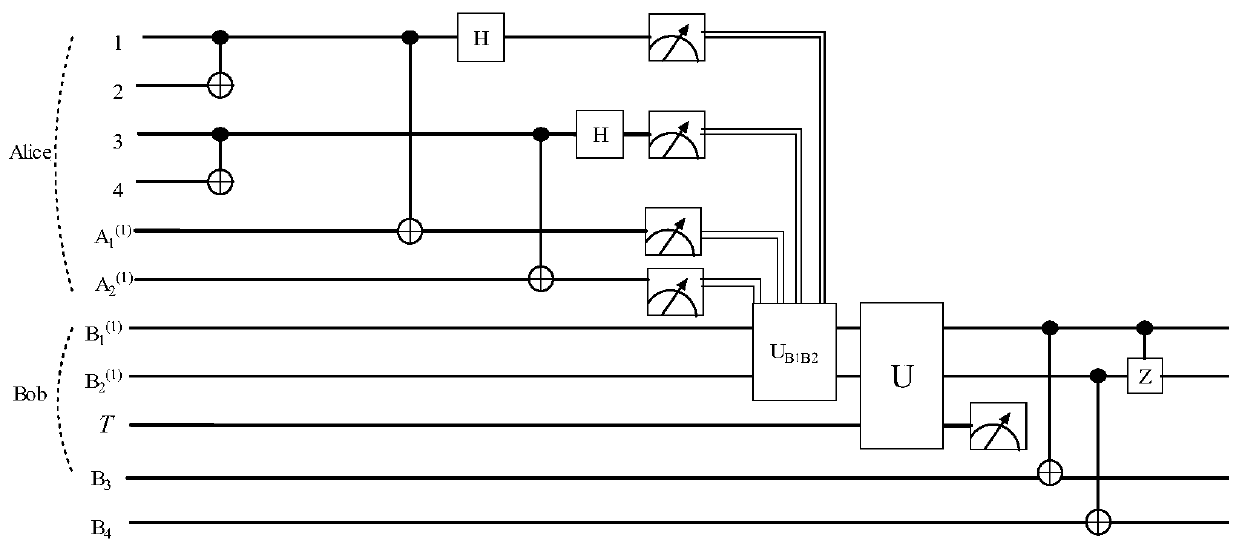
The invention discloses a four-particle cluster state multi-hop stealth transfer method based on a non-maximum entanglement cluster state. A source node Alice and a target node Bob realize long-distance quantum communication between Alice and Bob through the help of an intermediate node. The method mainly comprises four steps that (1) a source node Alice, a target node Bob and an intermediate nodeshare a non-maximum entanglement cluster state, and a quantum entanglement channel is established; (2) Alice and an intermediate node carry out CZ operation on particle pairs in hands of the Alice and the intermediate node, and modulate a channel; (3) the Alice and the intermediate node perform Bell measurement on the particle pairs in their hands and inform the measurement result, and the Aliceestablishes a direct quantum channel with the Bob through unitary operation; and (4) the Alice performs Bell-based measurement on the particle pairs in the hand, and Bob performs a series of unitary operations according to the measurement result of the Alice to obtain a transmitted unknown quantum state. The information transmission efficiency is high, the long-distance remote quantum communication problem can be solved through the help of the intermediate nodes, and the requirement for constructing a complex quantum communication network can be met.
Owner:SUZHOU UNIV
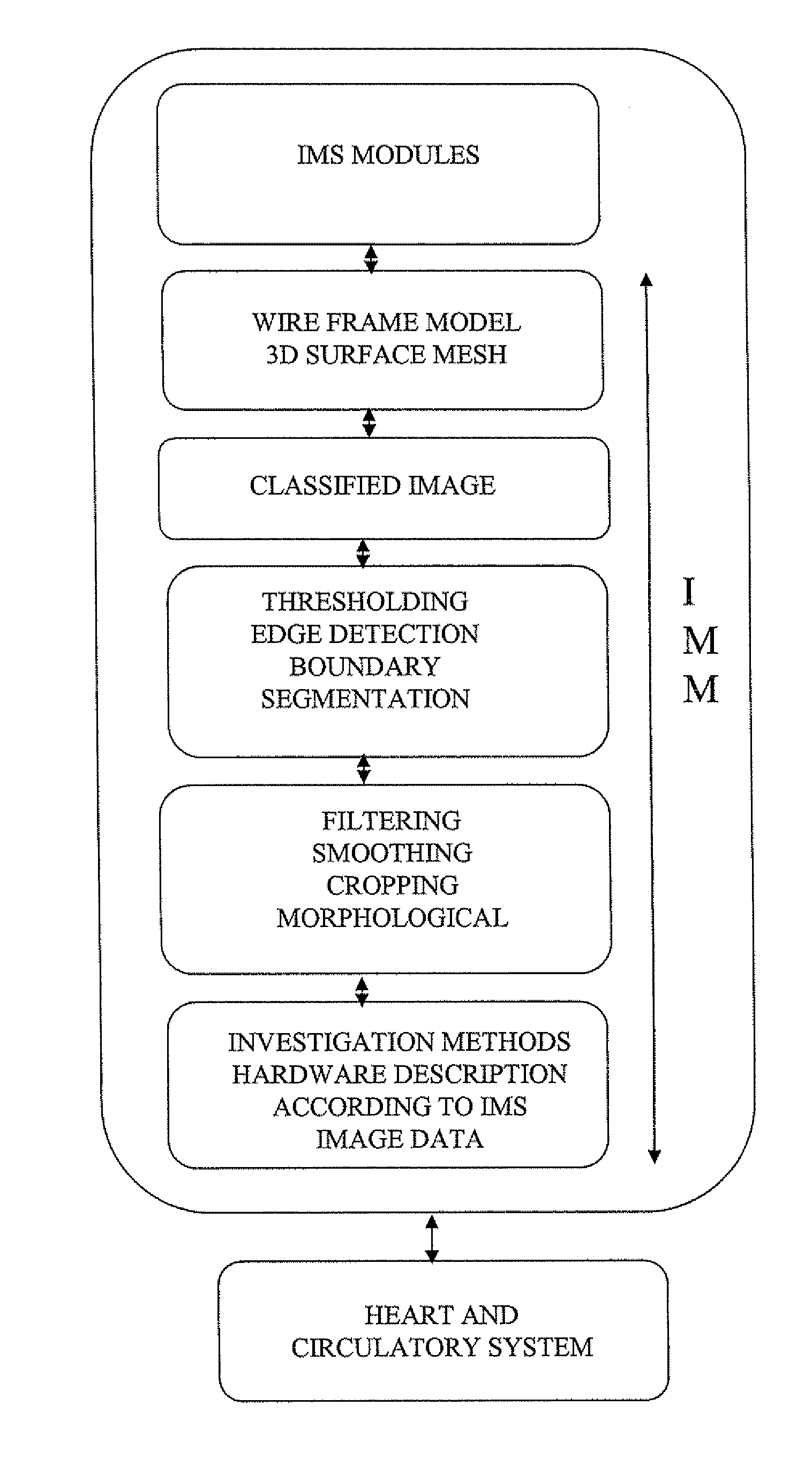
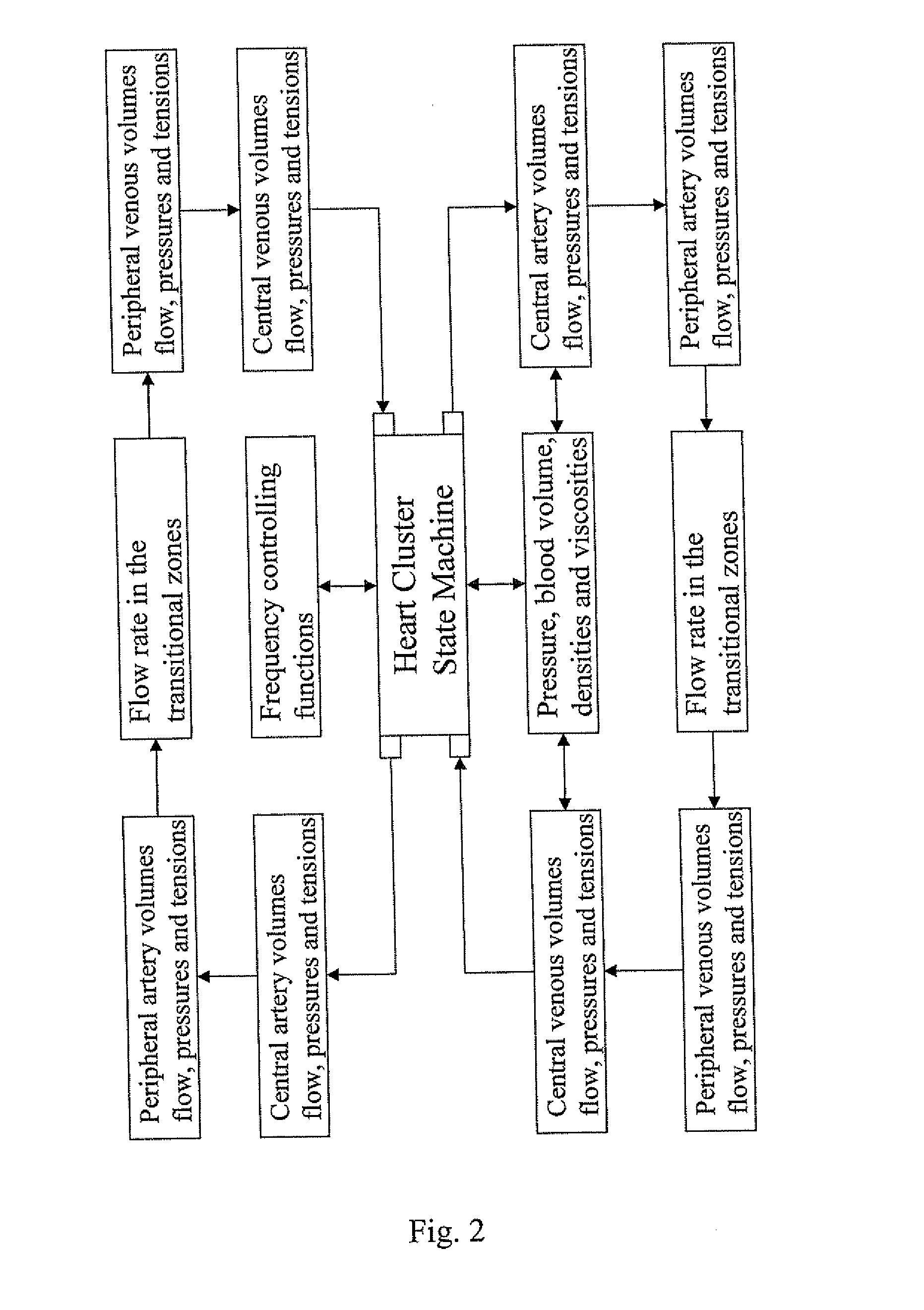
State space model of a heart
InactiveUS20090311656A1Improve heart functionBroaden their knowledgeMedical simulationAnalogue computers for chemical processesHeart Muscle CellCluster state
A state space model (SSM), being a computer-calculated model, adapted to represent the pumping and controlling functions of a heart that have been determined by a heart cluster state machine simulating the heart, and optionally the circulatory system, of an individual. The state space model includes two groups of separate interacting state machines, the heart muscle cell state machines and the displacement pump state machines.
Owner:GRIPPING HEART
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com