Single sign on based grid authentication trust model
A single sign-on, trust model technology, applied in user identity/authority verification, electrical components, transmission systems, etc., can solve problems such as the imperfect authorization function of grid single sign-on system, achieve easy configuration and maintenance, and unified identity Managing and Avoiding the Effects of Entity Deception
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
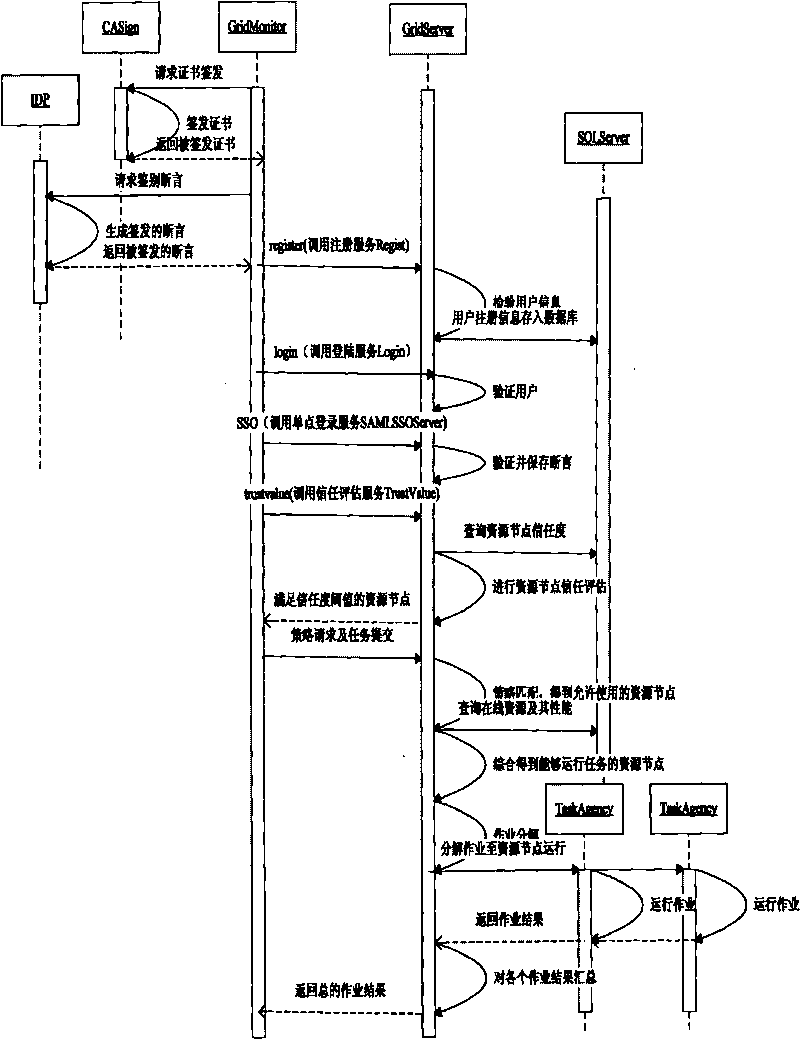
[0051] The authentication trust model based on identity authentication and single sign-on of the present invention applies objective trust to the grid security platform system, and uses the trust model to solve the problem of grid user identity authentication, specifically as follows:
[0052] 1. Architecture
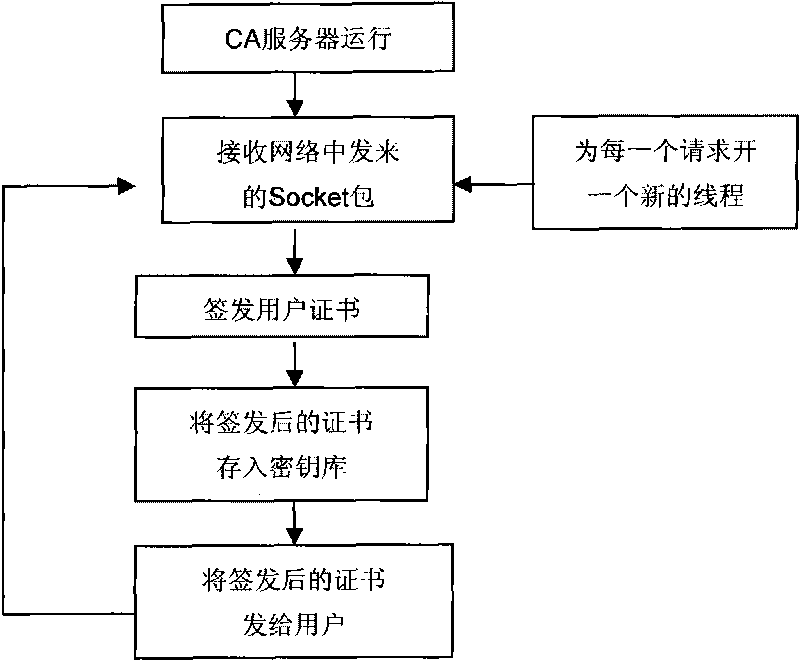
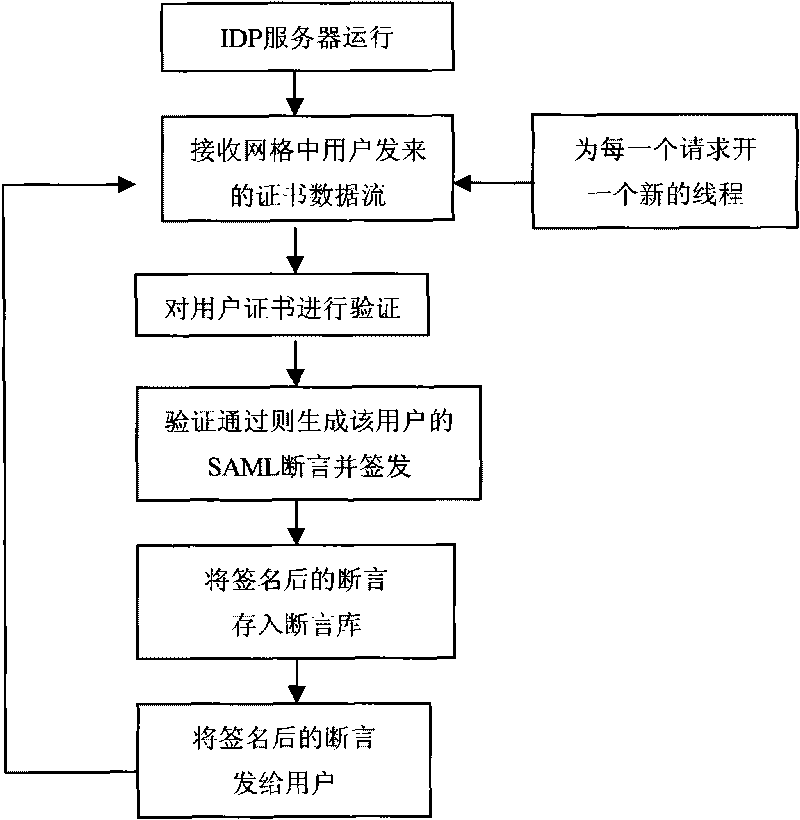
[0053] (1) In this design, the grid user first obtains the X.509 digital certificate issued by the CA server from the CA server. This certificate is the identity certificate that the user can prove himself in this system, similar to the Our ID card, our ID card is a document with a direction mark added by the government, which is unique. The authentication module adopts the traditional PKI model, and the specific operation process is as follows: figure 1 As shown, after the CA server is running, it will always monitor the issuance request on the network. After receiving the certificate from the client, it will check the identity of the client. Sign, store the signed c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com