Internet of Things authentication system and Internet of Things authentication method
An IoT authentication and remote authentication technology, applied in the IoT authentication system and the IoT authentication field, can solve the problems of inability to realize remote authentication, complex verification methods, and difficult development, avoiding the analysis of bioinformatics algorithms and achieving efficient deployment. Safety certification environment, the effect of reducing learning costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
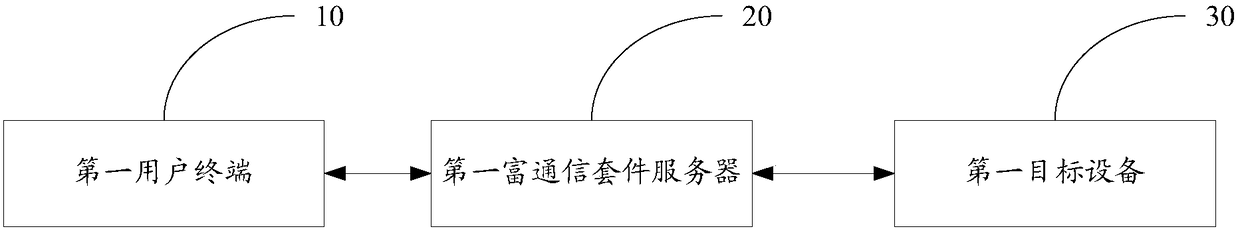
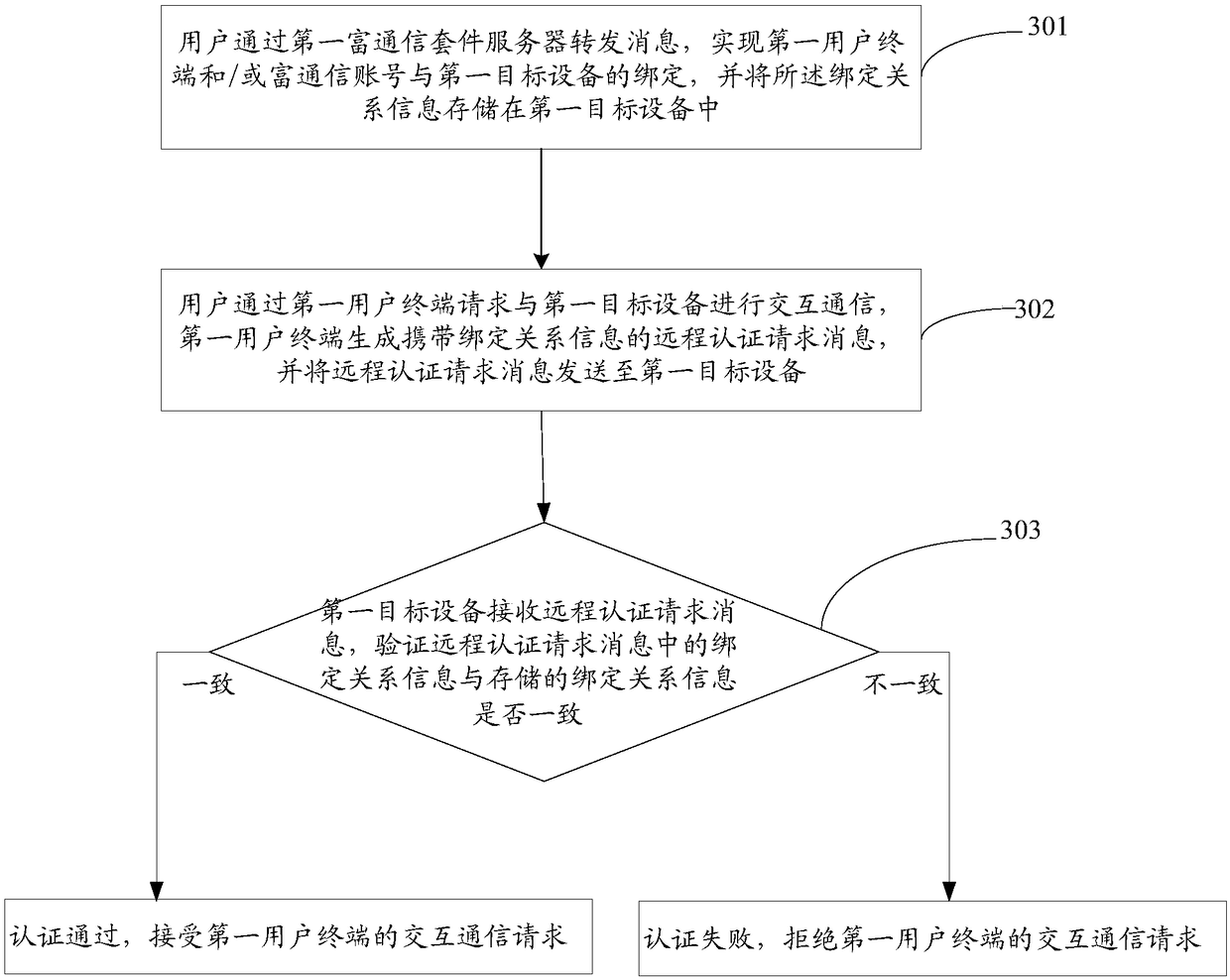
[0145] Such as Figure 8 As shown, user terminal A is equipped with a fingerprint recognition system (such as a common smart phone), and RCS terminal software is installed on user terminal A, and the user is an RCS user; the user needs to remotely start the vehicle-machine system device B through user terminal A, and the vehicle-machine system device B can simply analyze SIP signaling, and has a database for storing binding information. A and B can realize information interaction through the RCS platform.
[0146] (1) The RCS system logging in to user terminal A initiates a binding request;
[0147] (2) The user terminal A prompts the user to authenticate the fingerprint and input the unique identification code of the device B (such as the engine number). or ISDN, etc.), the unique identification code of device B, and the encrypted binding command of the user’s RCS account to device B, and go to step (3); if the fingerprint authentication fails, it will prompt that there is ...
Embodiment 2
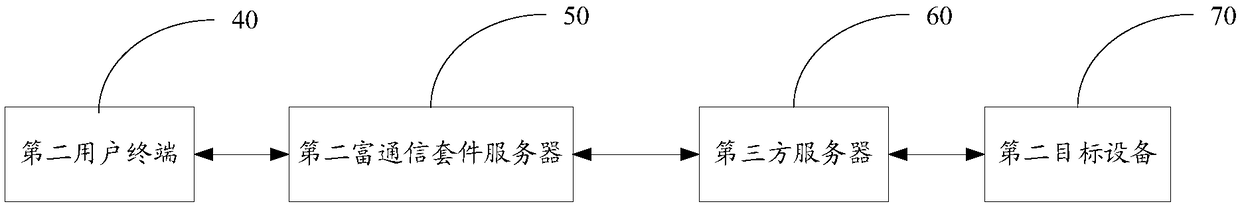
[0154] Such as Figure 9 As shown, user terminal C is equipped with a fingerprint identification system, and RCS terminal software is installed on user terminal C, and the user is an RCS user; the user needs to remotely open access control device D through user terminal C, and access control system device D can simply analyze SIP signaling.
[0155] (a) Log in to the RCS system on the user terminal C, follow and enter the RCS official account server under the brand of access control equipment D;
[0156] (b) Initiate a binding request, user terminal C prompts the user to perform fingerprint authentication, enter the unique identification code (such as network module MAC address) of access control device D to initiate binding, if the authentication is passed, through the forwarding of the RCS server, user terminal C initiates Bind the command to the RCS official account server, and go to step (c); if the authentication fails, it will prompt that there is a problem with the user...
Embodiment 3
[0164] User terminal E is equipped with a fingerprint identification system, and RCS terminal software is installed on user terminal E, and the user is an RCS user; the user needs to remotely unlock terminal device F through user terminal E, and the RCS software client is pre-installed on terminal device F, and there is a terminal The RCS account of device F.
[0165] (i) The user terminal E logs into the RCS system and binds with the terminal device F;
[0166] (ii) The user terminal E prompts the user to perform fingerprint authentication. If the fingerprint authentication is passed, the user terminal E sends the encrypted binding command carrying the user RCS account of the user terminal E to the terminal device F through the forwarding of the RCS server; if the fingerprint authentication fails, Prompt that there is a problem with the user's identity, and end the process;
[0167] (Ⅲ) The terminal device F receives the binding instruction and decrypts it, displays the bind...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com