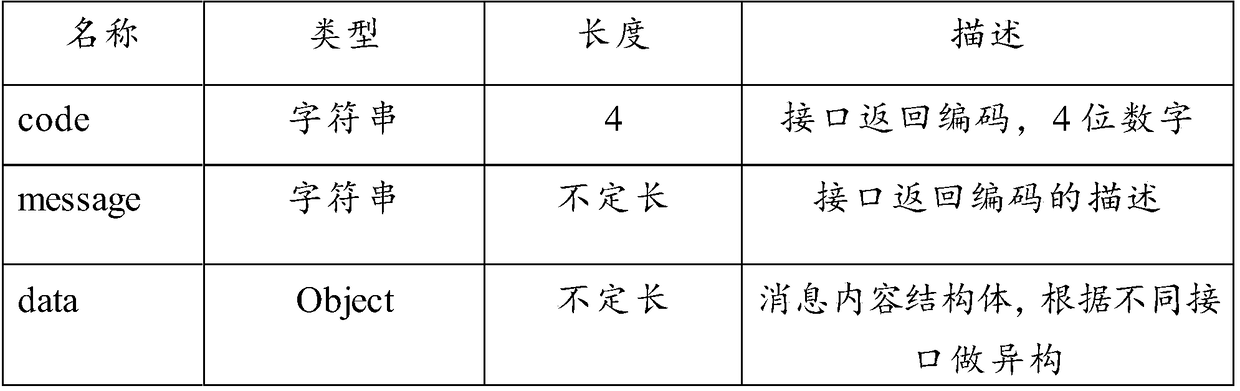
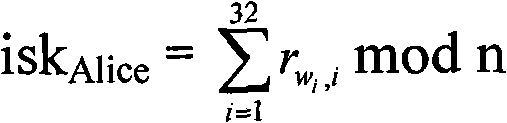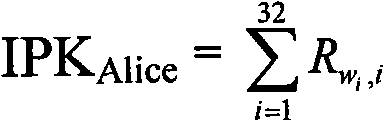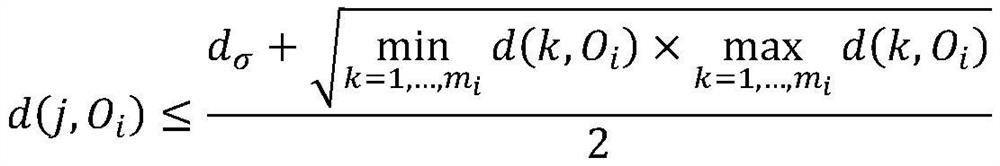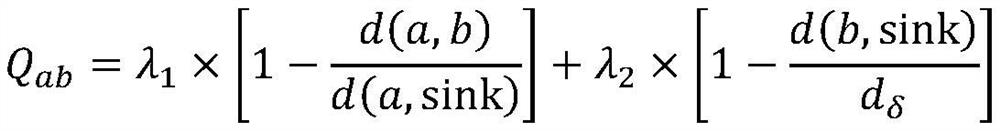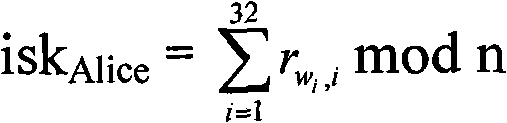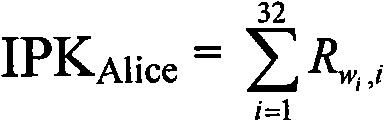Patents
Literature
35results about How to "Enable secure interactions" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Identity authentication method, apparatus and system
ActiveCN106656481AImplement identity authenticationMaintain securityKey distribution for secure communicationComputer terminalEncryption
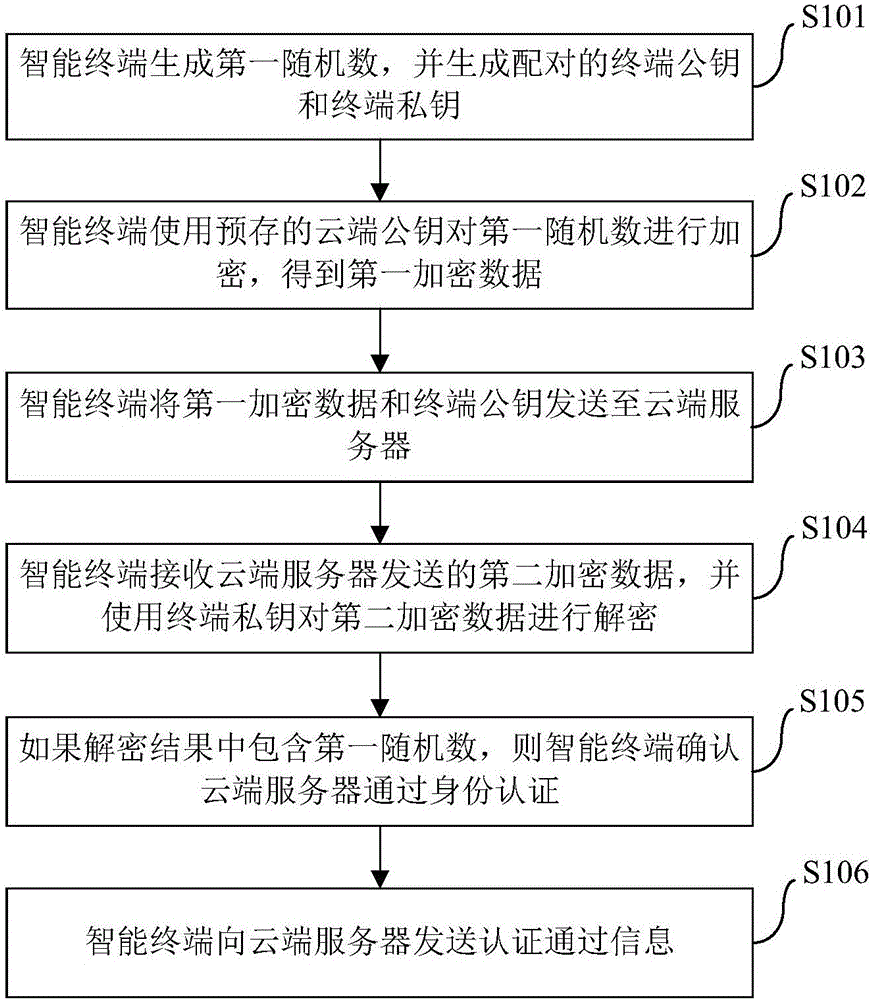
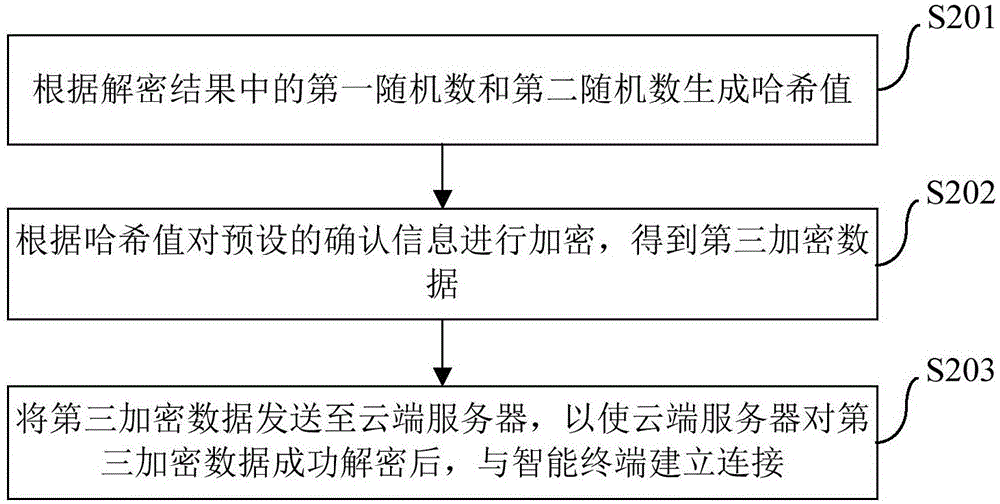
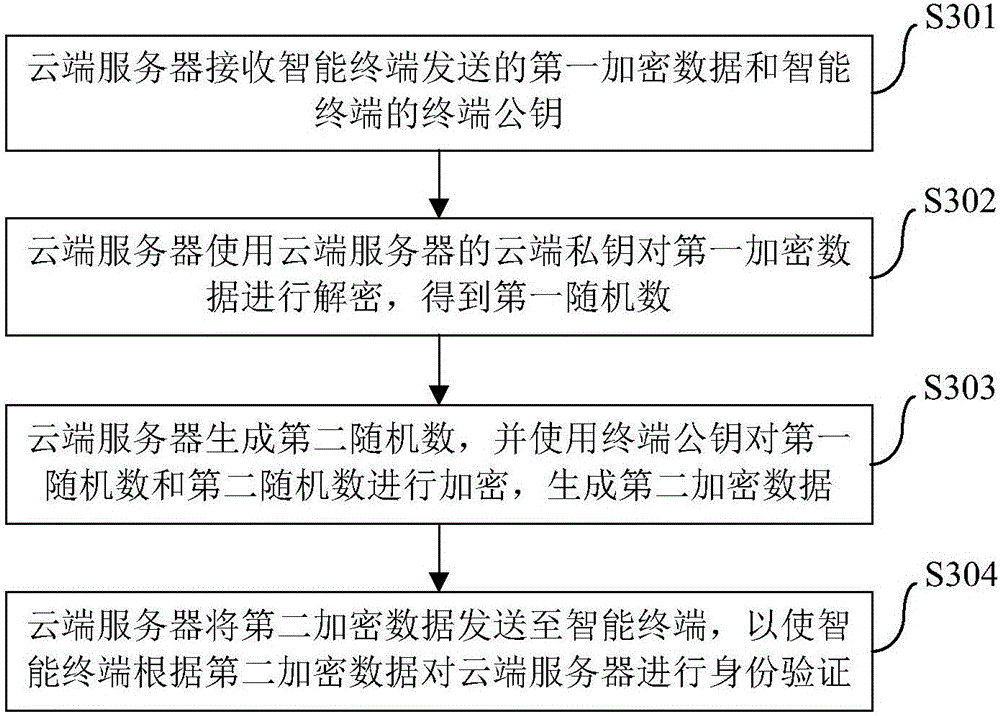
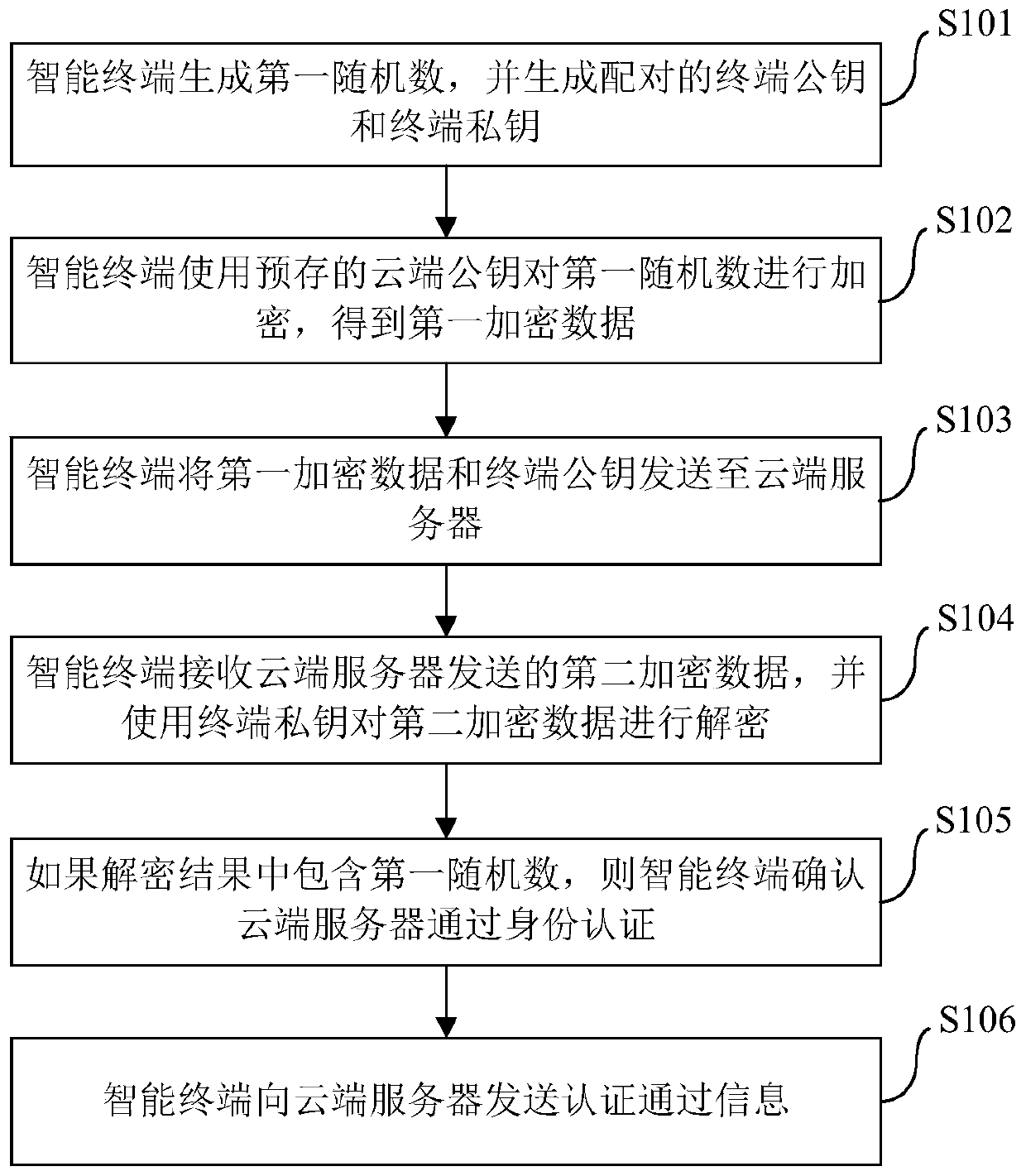
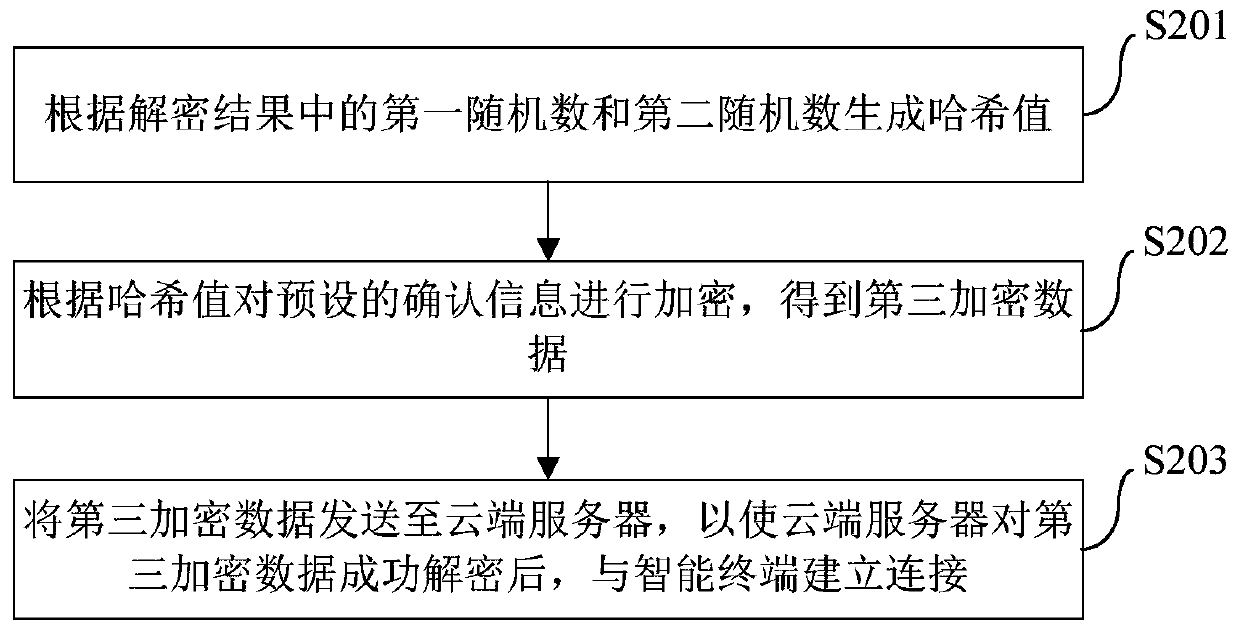
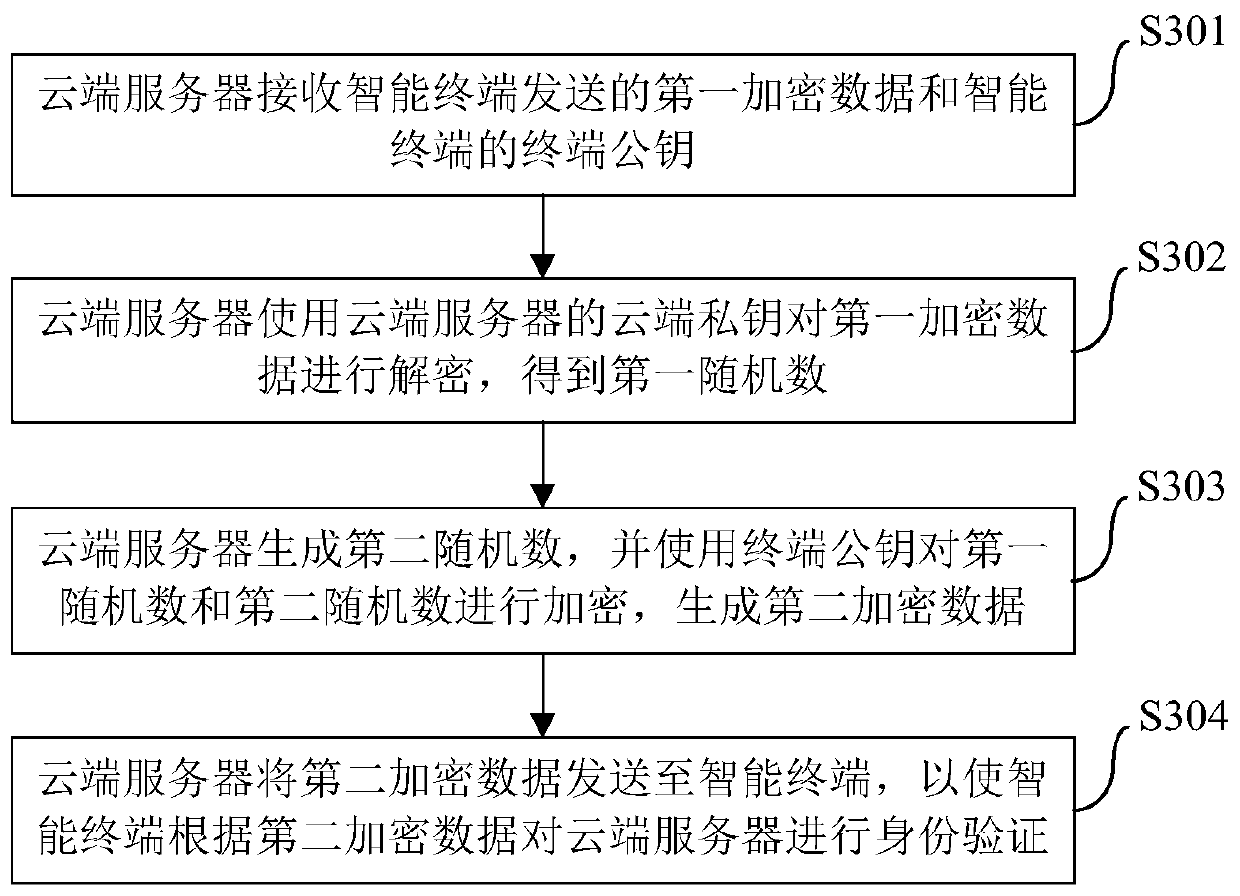
The invention brings forward an identity authentication method, apparatus and system. The identity authentication method comprises the following steps: an intelligent terminal generating a first randomized number and generating a terminal public key and terminal private key which form a pair; the intelligent terminal encrypting the first randomized number by use of a prestored cloud public key so as to obtain first encryption data; the intelligent terminal sending the first encryption data and the terminal public key to a cloud server; the intelligent terminal receiving second encryption data sent by the cloud server and decrypting the second encryption data by use of the terminal private key; and if a decryption result comprises the first randomized number, the intelligent terminal confirming that the cloud server succeeds in identity authentication. The identity authentication method simplifies operation steps, reduces operation resources, at the same time, maintains more secure data channels, promotes development of Internet of things and improves user experience.
Owner:MIDEA SMART TECH CO LTD +1
Method and system for implementing authentication and data safe transmission
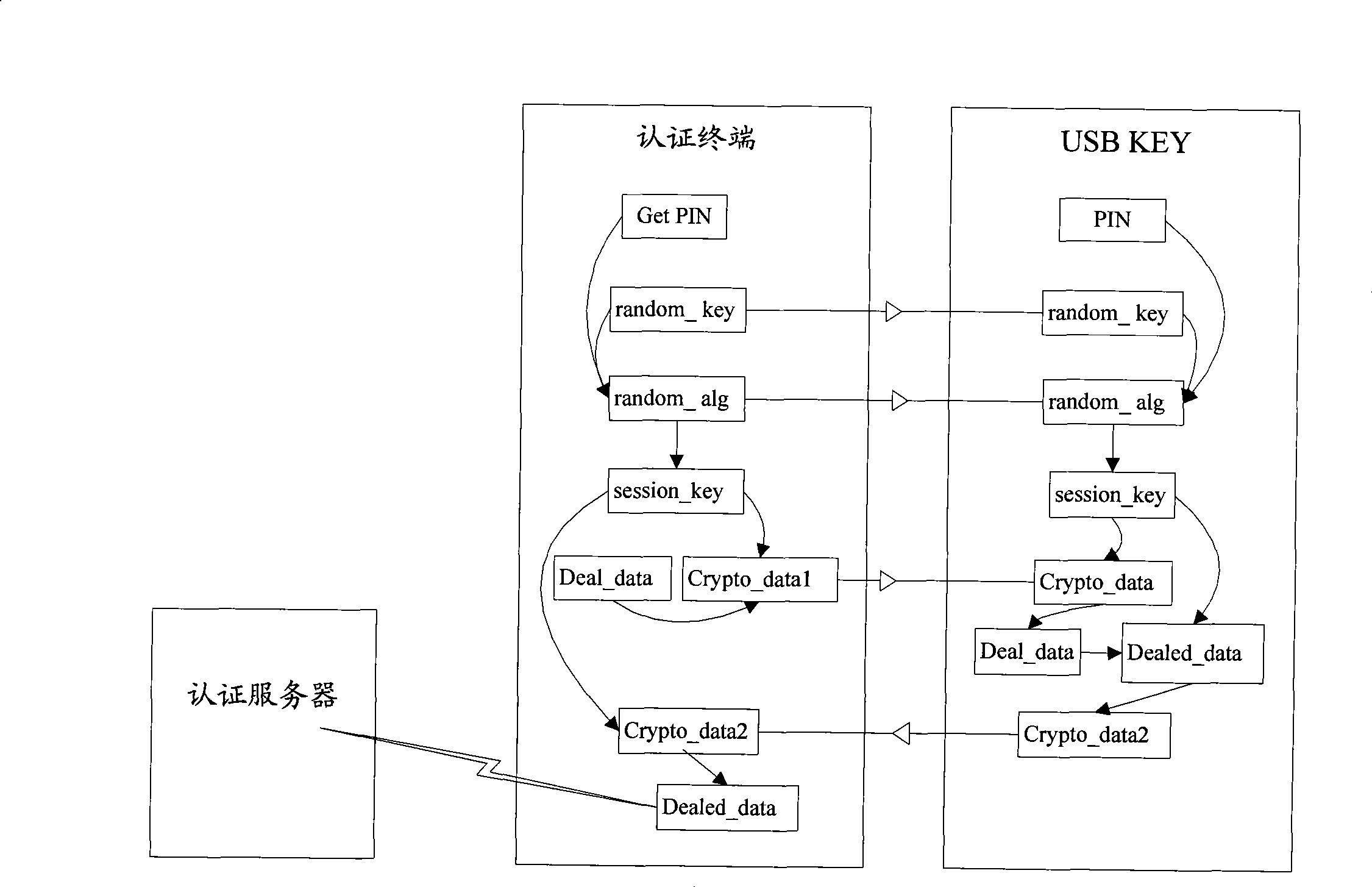
InactiveCN101483654AEnable secure interactionsEnsure safetyTransmissionSecurity arrangementSecure transmissionPassword
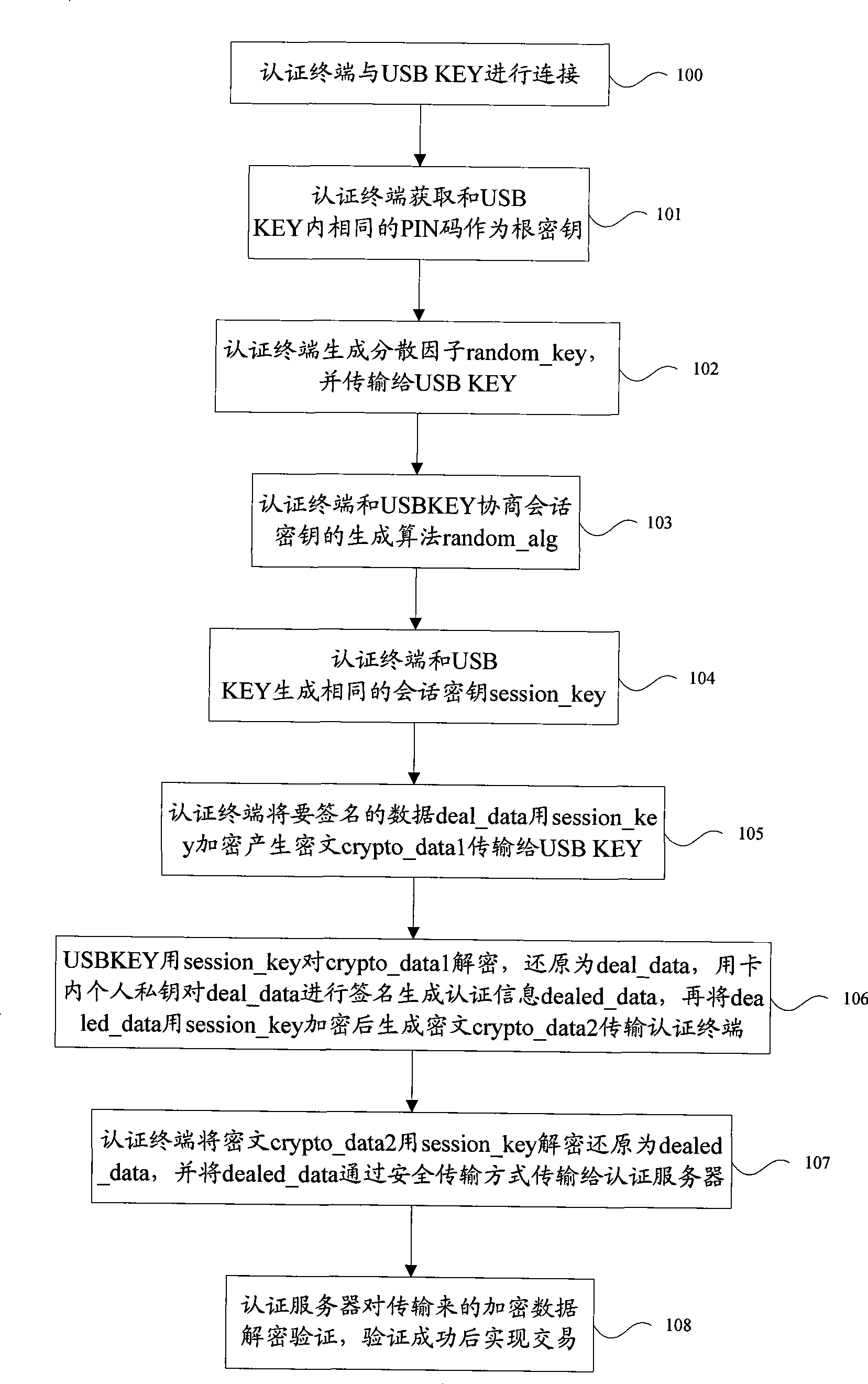
The invention discloses an authentication and safe transmission of data realizing method. A terminal safety device and an authentication terminal after being connected negotiates to have a same data to be used as a root key, and at the same time negotiates to have a same dispersion factor and a same algorithm, the negotiated root key and dispersion factor generate a same session key used as a symmetrical key by using the algorithm, and then, safety authentication and data encryption and decryption can be performed and safety data interaction between the two ends can be realized. The invention also discloses a system for realizing authentication and safe transmission of data, and the system comprises a terminal safety device, an authentication terminal and an authentication server. According to the invention, randomness of the session key for data encryption transmission can be assured, even though a session key is decrypted, the safety of the whole system can be assured, and at the same time, atom manipulation for safety authentication and safe transmission of data can be realized for avoiding that in the current authentication process, once a password is verified by the terminal safety device, limits of authority are totally released and potential safety hazard is generated, therefore, authentication safety is improved greatly.
Owner:BEIJING HUADA ZHIBAO ELECTRONICS SYST
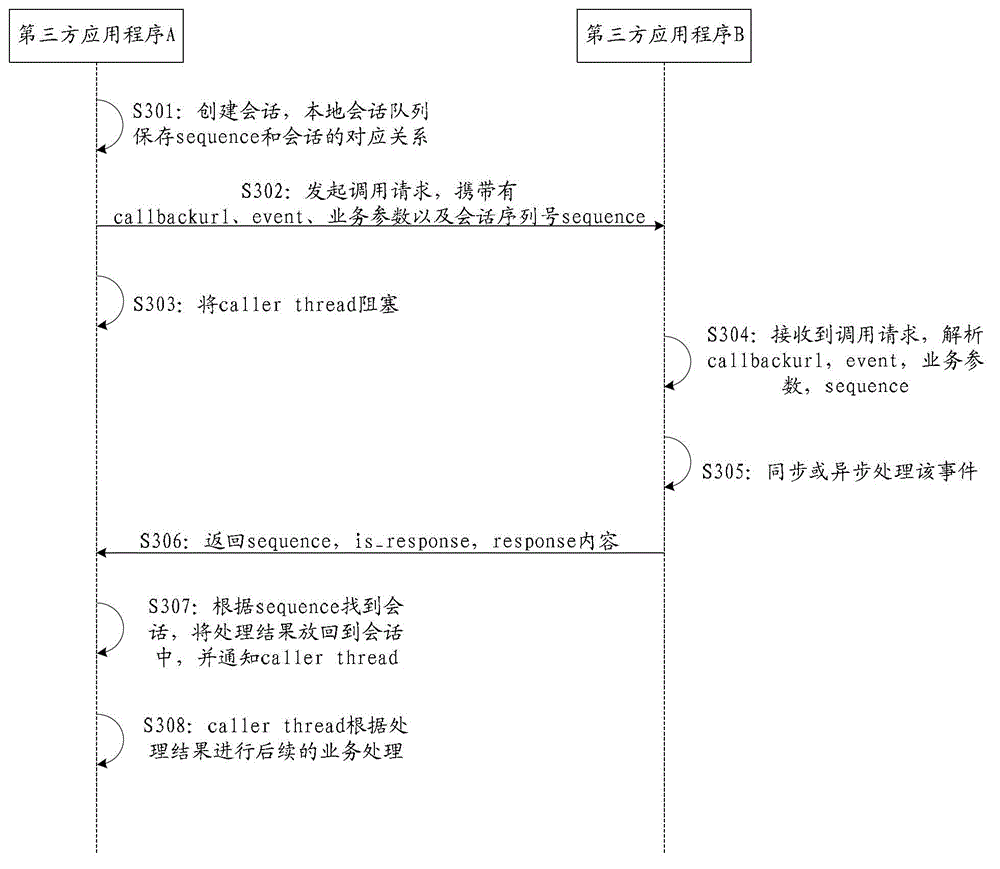
Service processing method and system
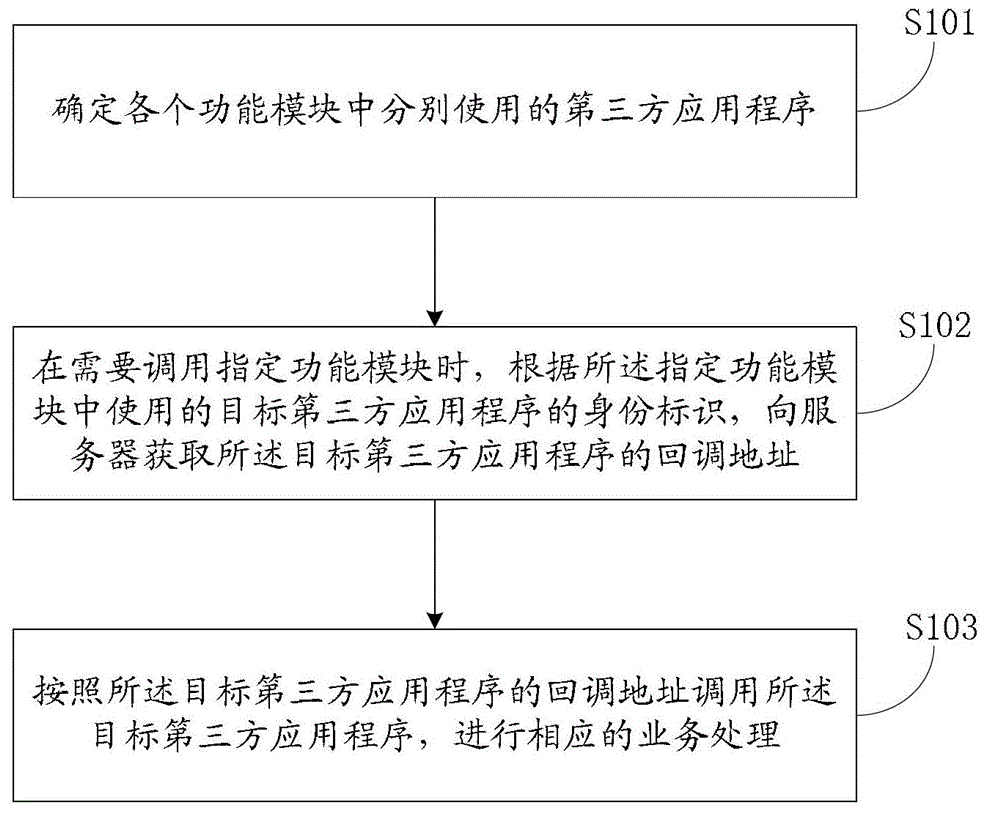
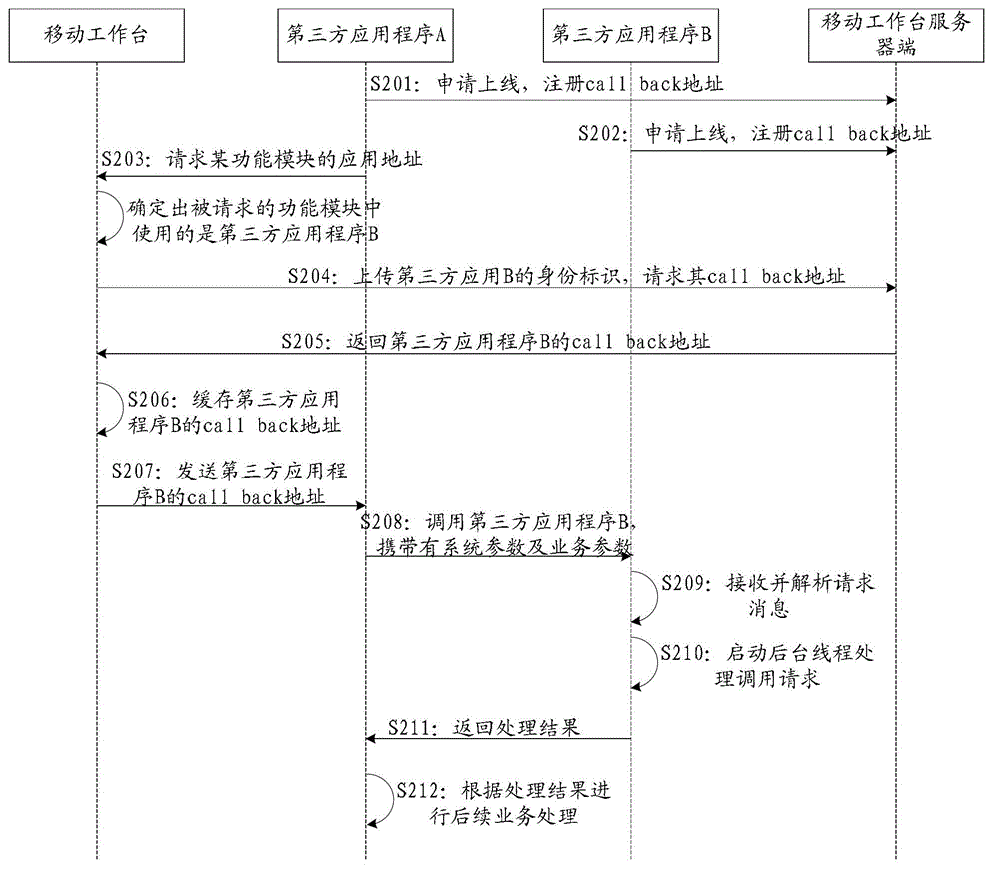
ActiveCN103942093ARealize data interactionEnable secure interactionsMultiprogramming arrangementsCommerceThird partyE-commerce
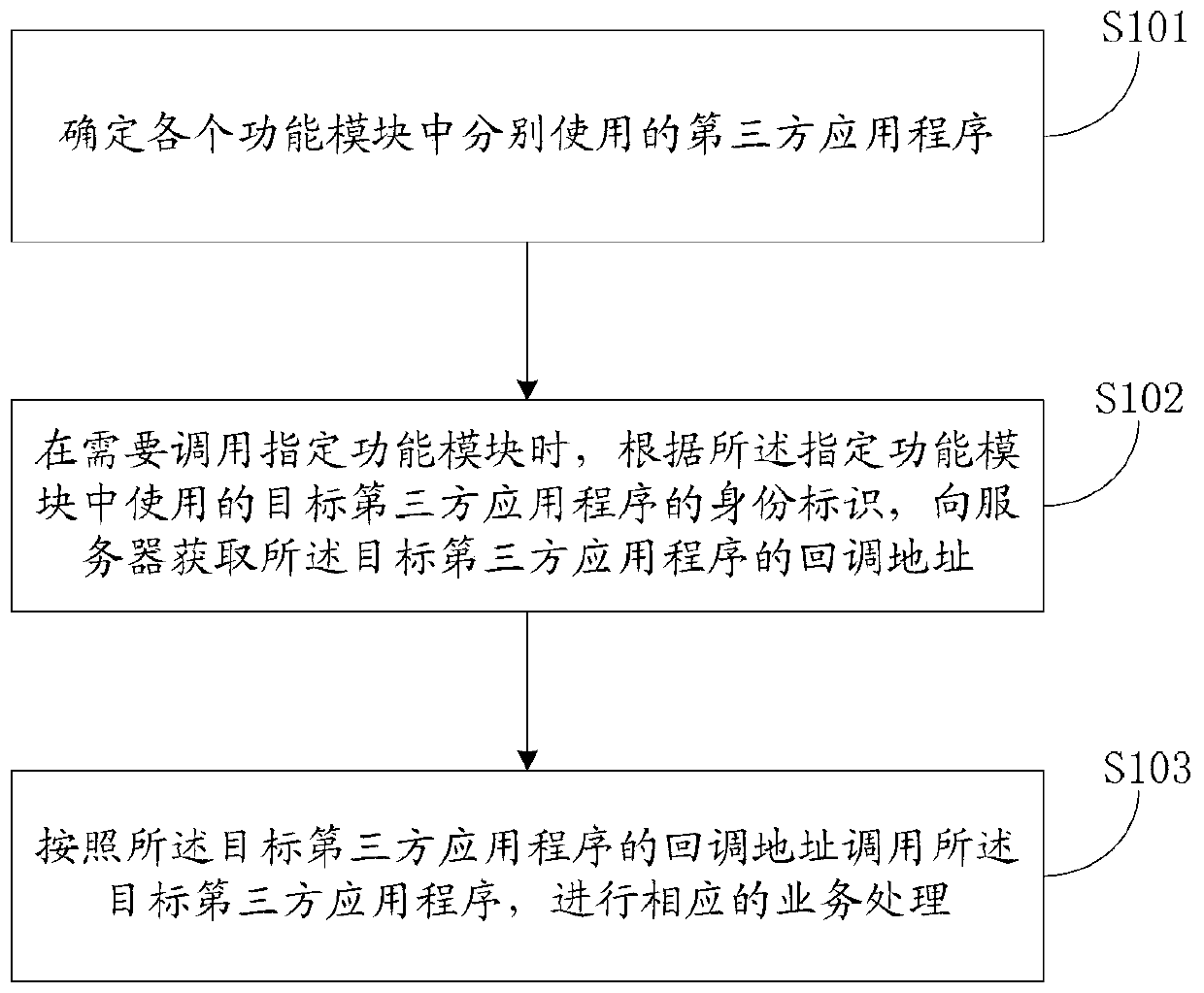
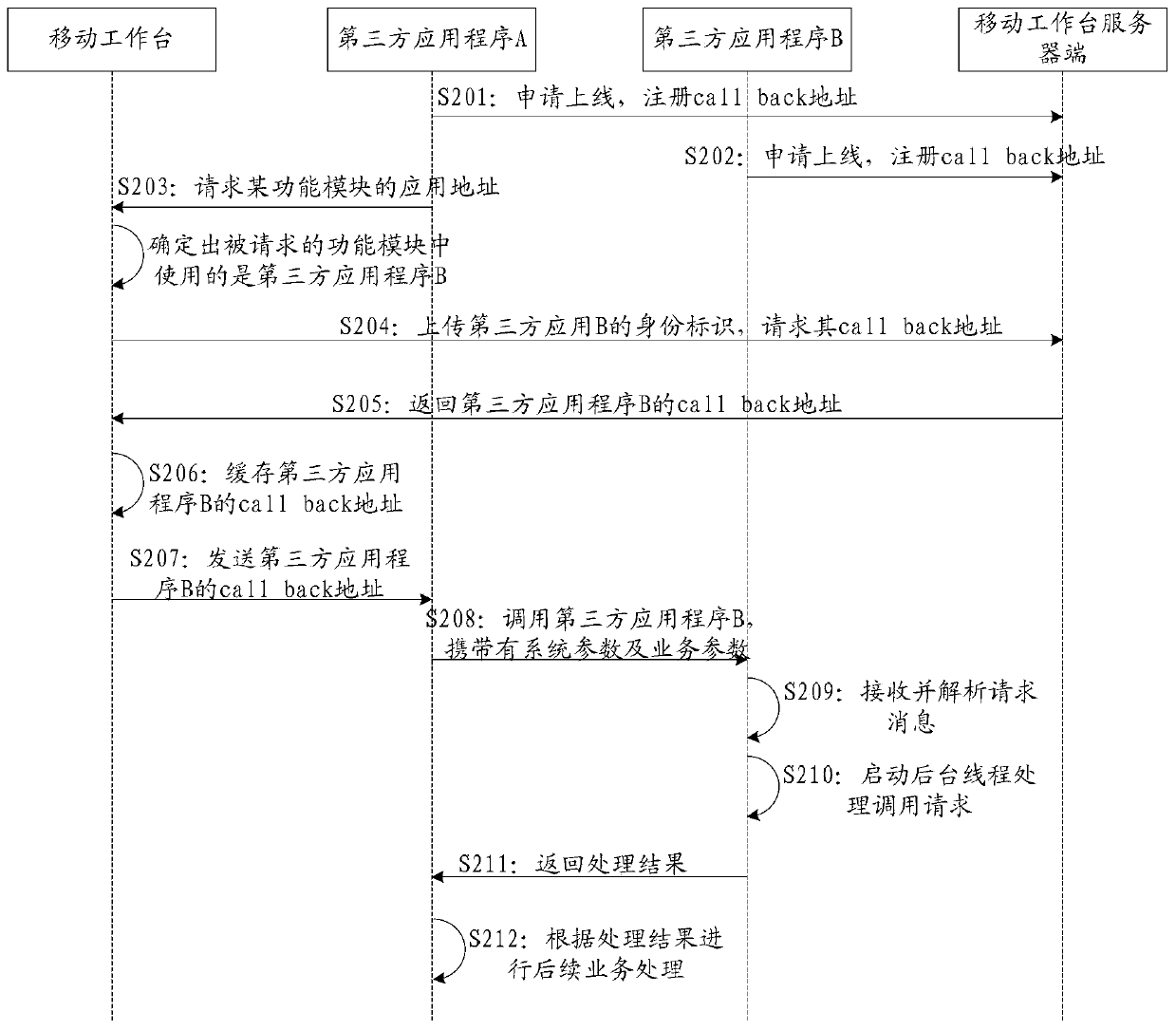
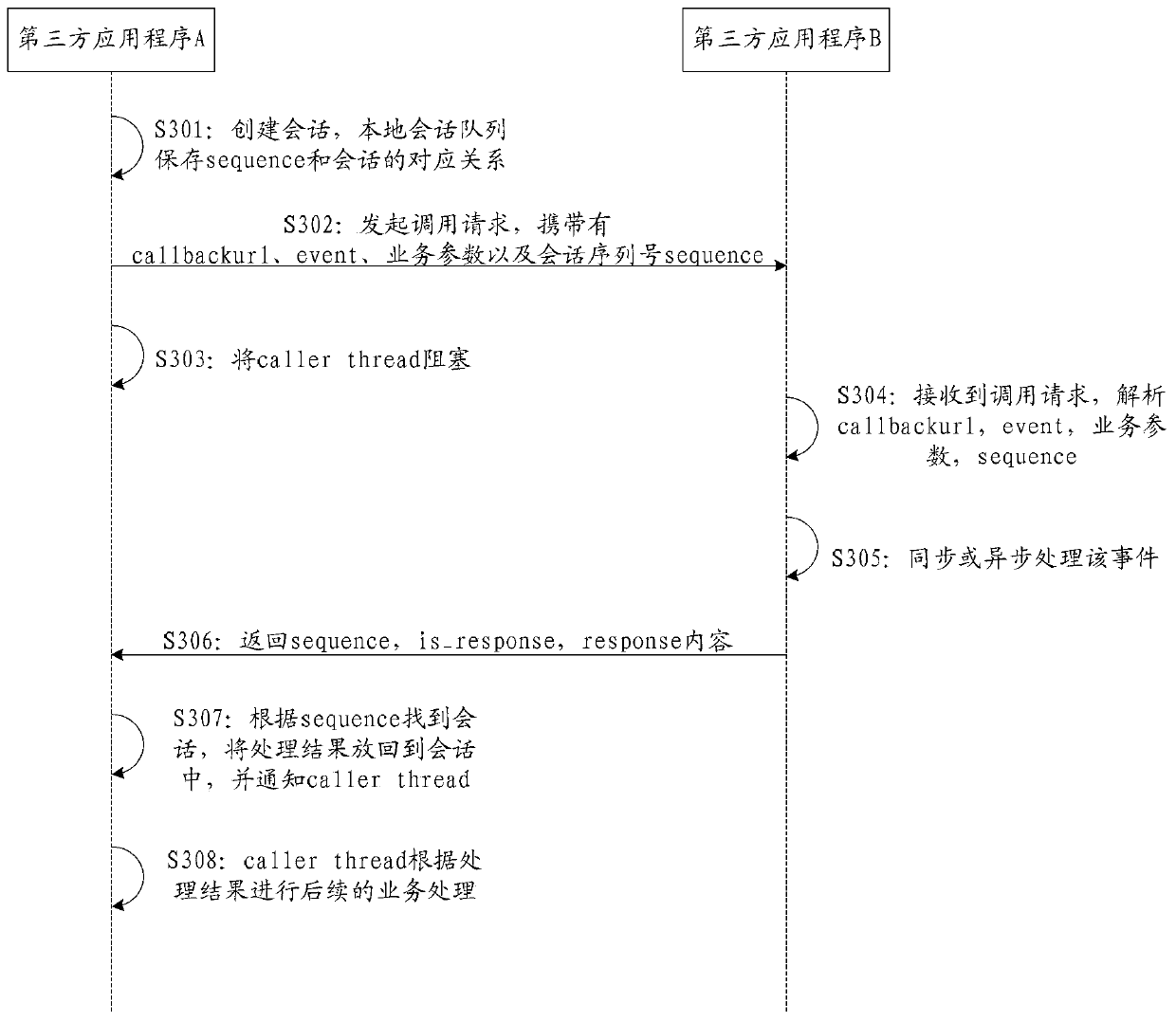
The invention discloses a service processing method and system. The method can include the steps that third-party application programs used in all function modules are determined; when a specified function module needs to be called, and according to an identity label of the target third-party application program used in the specified function module, the callback address of the target third-party application program is obtained from a server; the callback address is generated according to information of a uniform resource locator scheme field of a code written into the target third-party application program, and the target third-party application program conducts registration on the information of the uniform resource locator scheme field in the server; the target third-party application program is called according to the callback address of the target third-party application program, and corresponding service processing is conducted. According to the service processing method and system, inter-application data interaction can be achieved, and multi-application different-stage electronic commerce processes can be assisted to be achieved.
Owner:ALIBABA GRP HLDG LTD
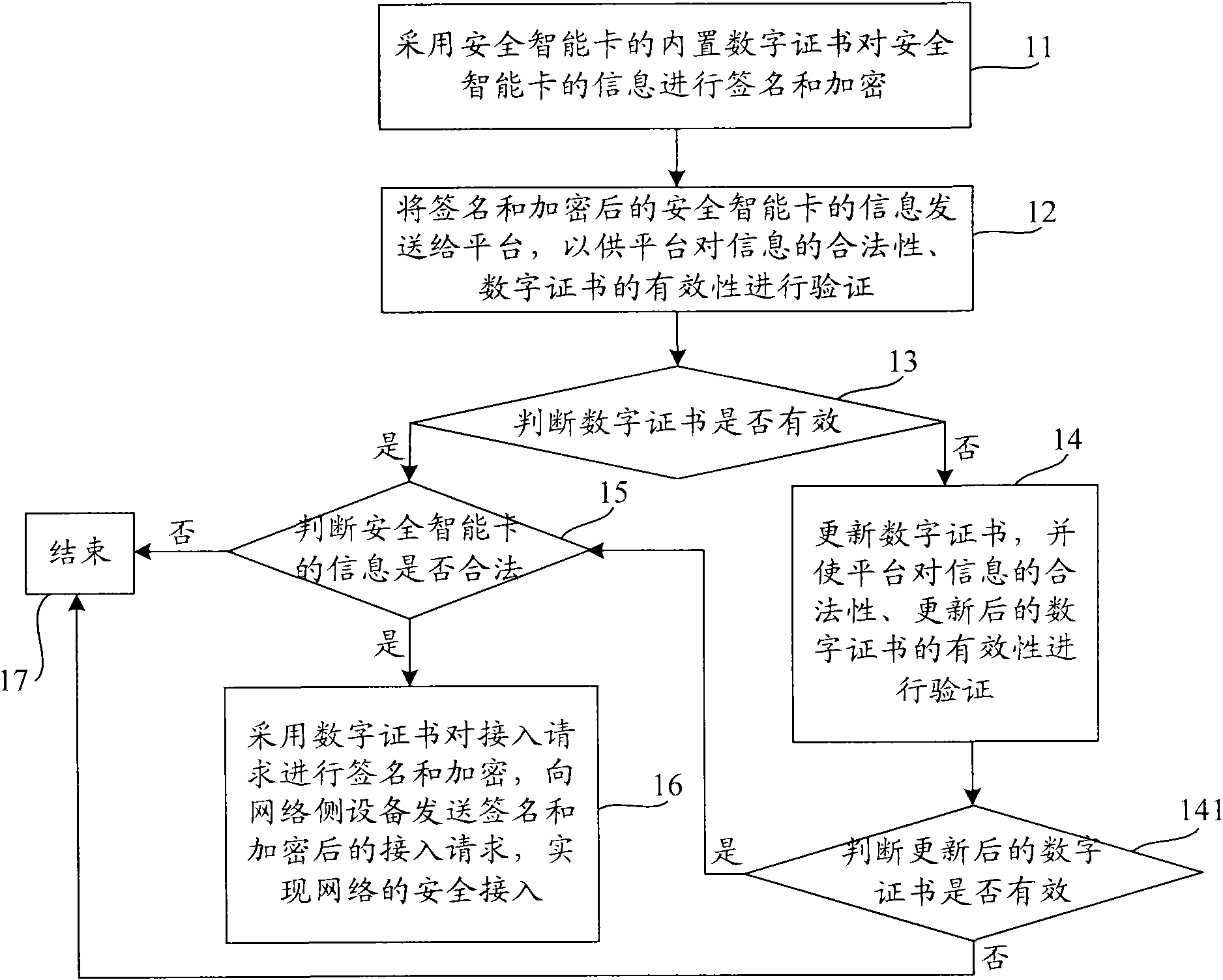
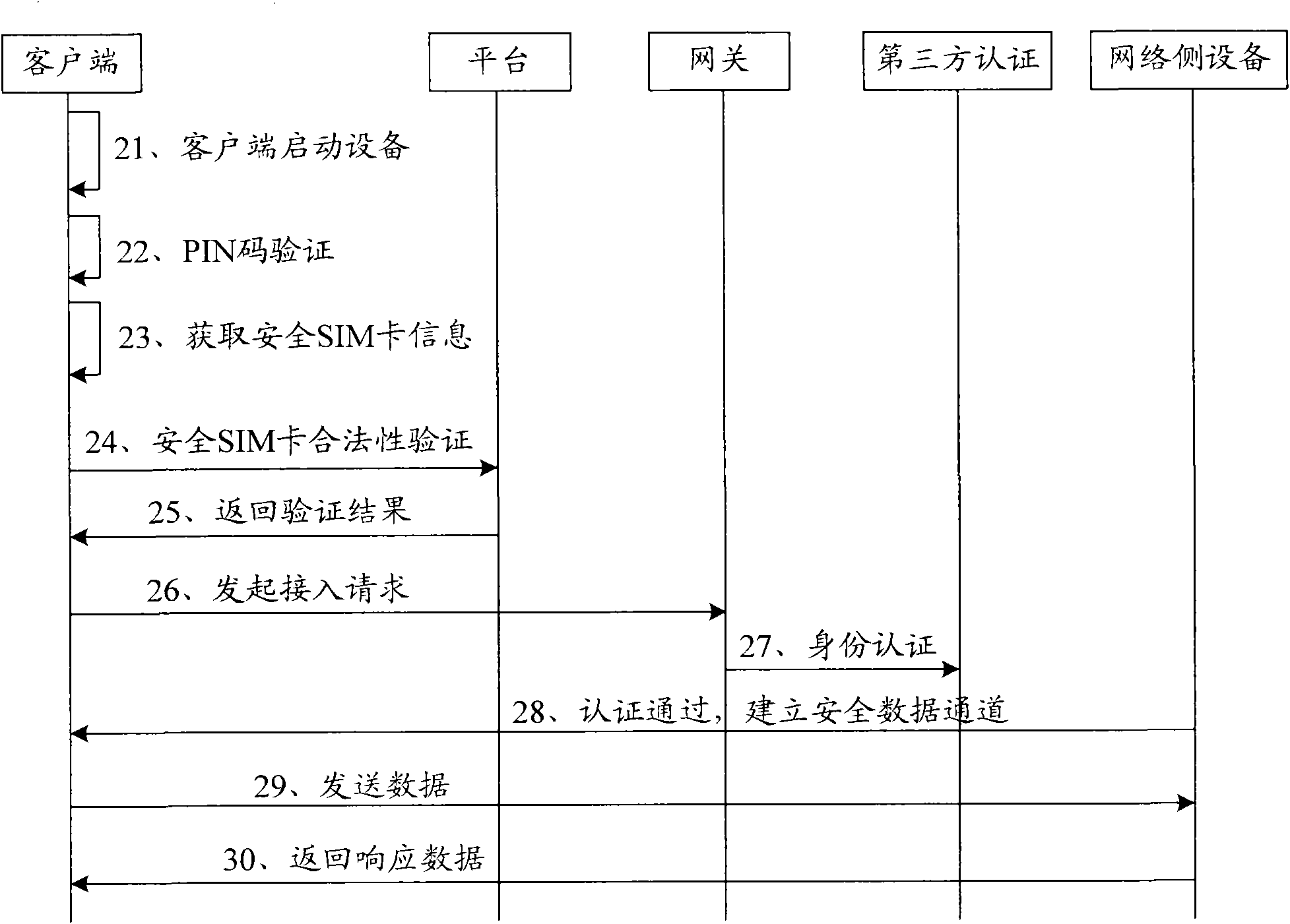
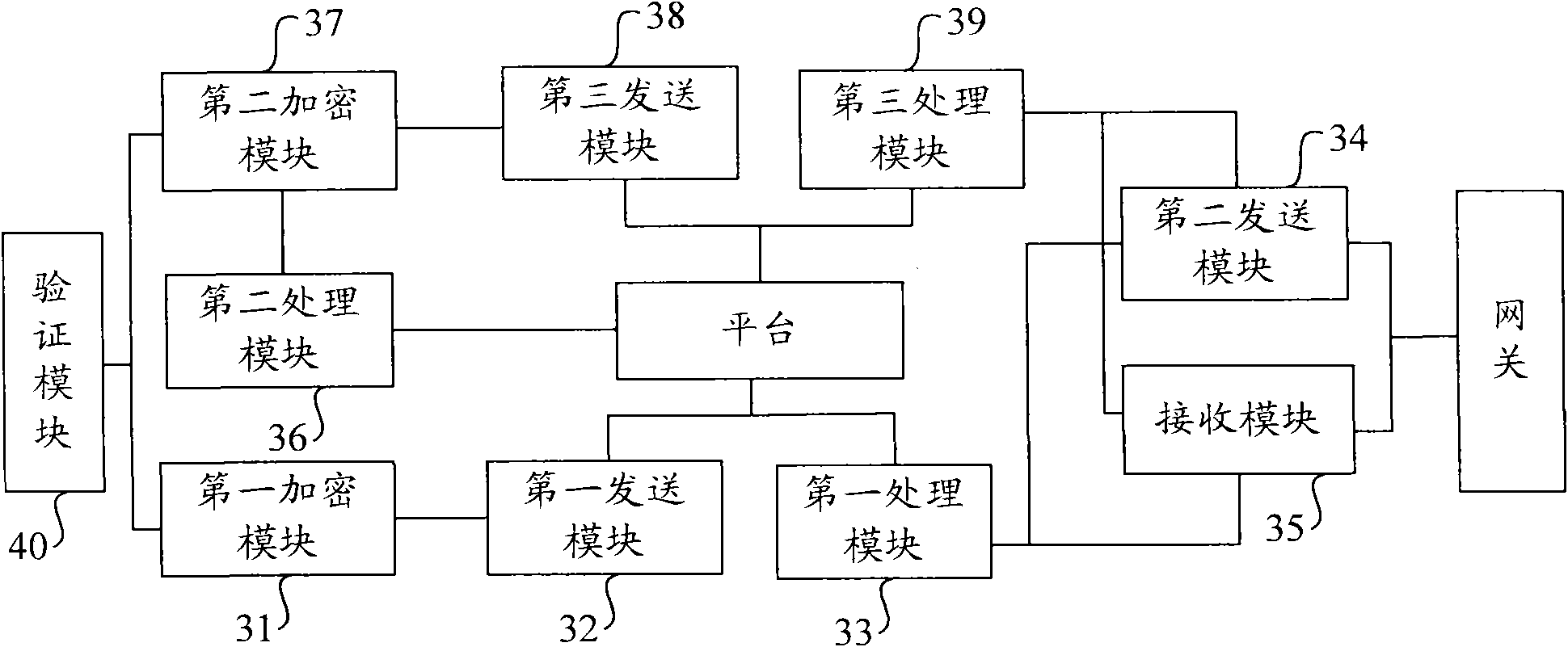
Secure access method, system and client
InactiveCN101841525AEnable secure interactionsImproved security accessUser identity/authority verificationSecurity arrangementAccess methodInternet privacy
The invention provides secure access method, system and client. The secure access method comprises the following steps of: signing and encrypting information inside a secure smart card by using a built-in digital certificate of the secure smart card; sending the information of the signed and encrypted secure smart card to a platform so that the platform can verify the legality of the information of the validity of the digital certificate; after verifying the legality of the information of the validity of the digital certificate, signing and encrypting an access request by using the digital certificate, and sending the signed and encrypted access request to a network-side device to realize secure access. The secure access method, system and client provided by the embodiment of the invention overcome the defect that the legality of hardware KEY can not be guaranteed when network access is realized in the prior art and increase the security of network access.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD +1
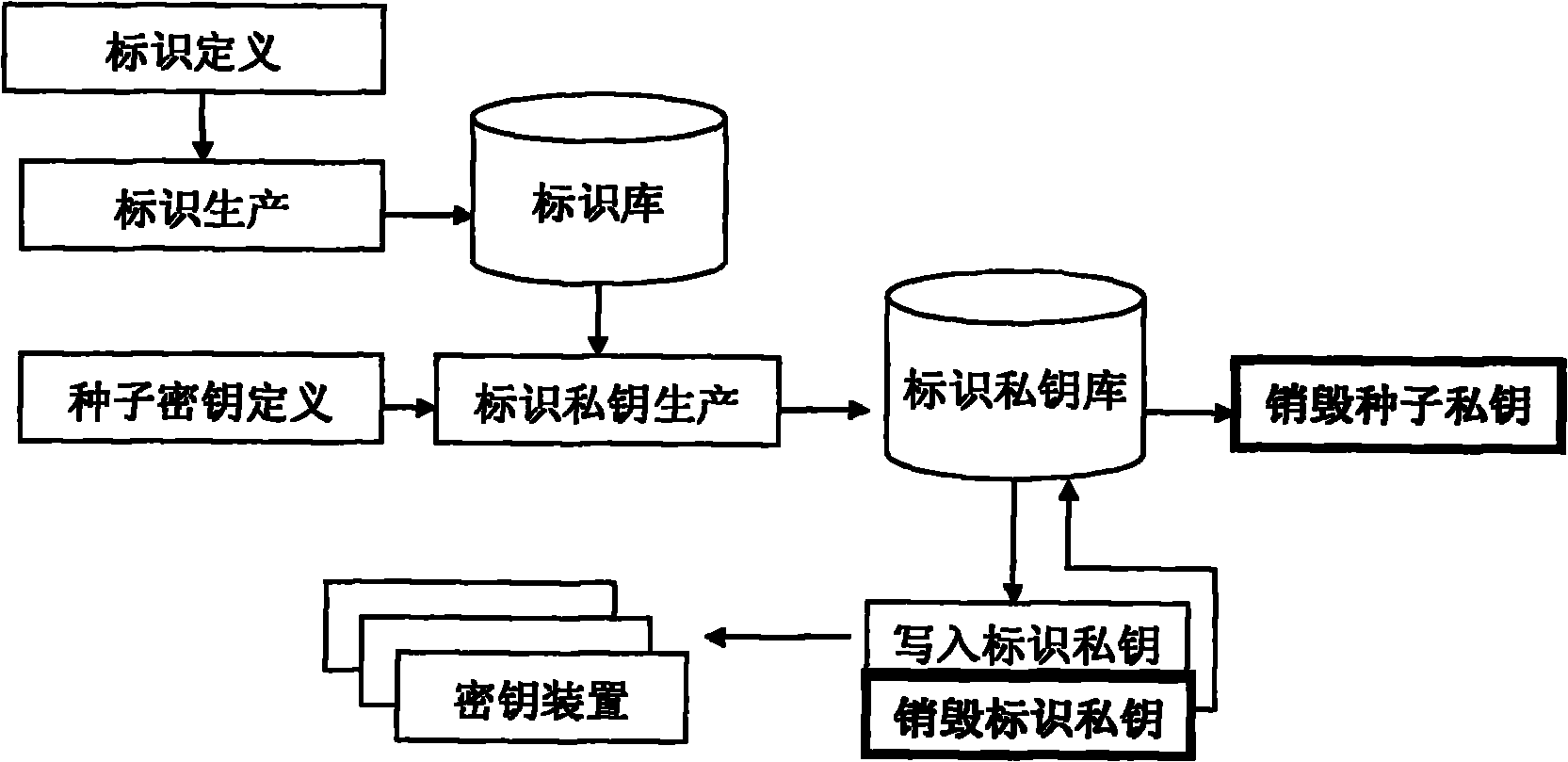
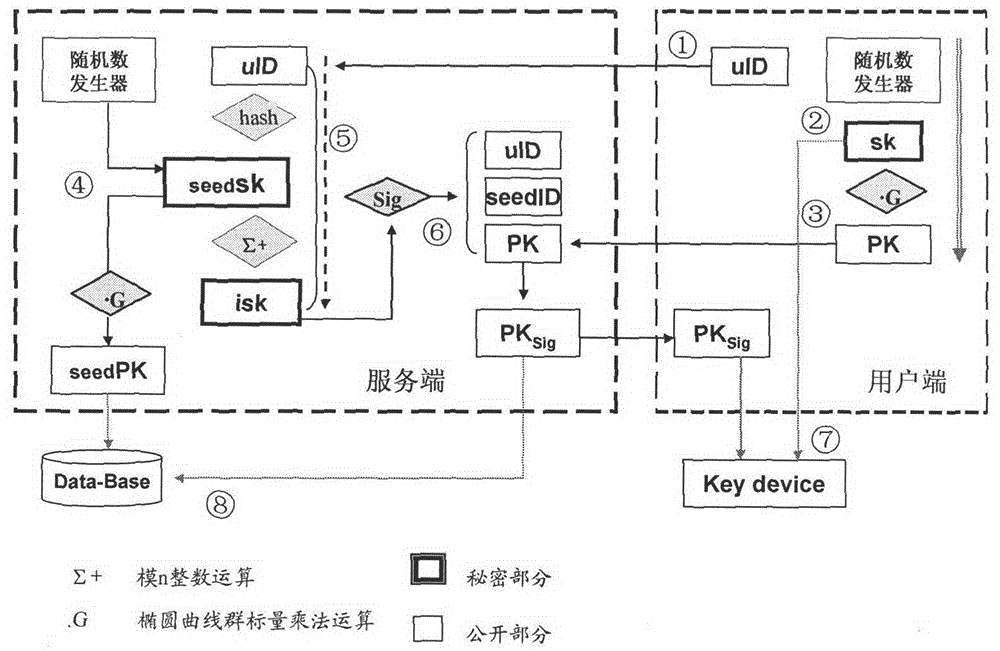
Secret key devices for supporting anonymous authentication, generation method and unlocking method thereof
ActiveCN101958796ABreak through application bottlenecksEnable secure interactionsKey distribution for secure communicationUser identity/authority verificationAnonymous authenticationAnonymous identifier
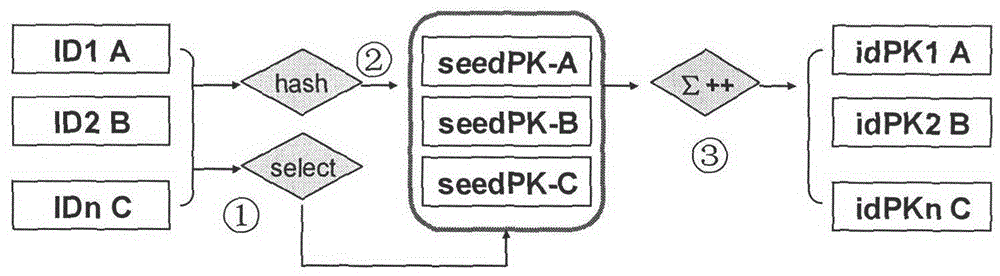
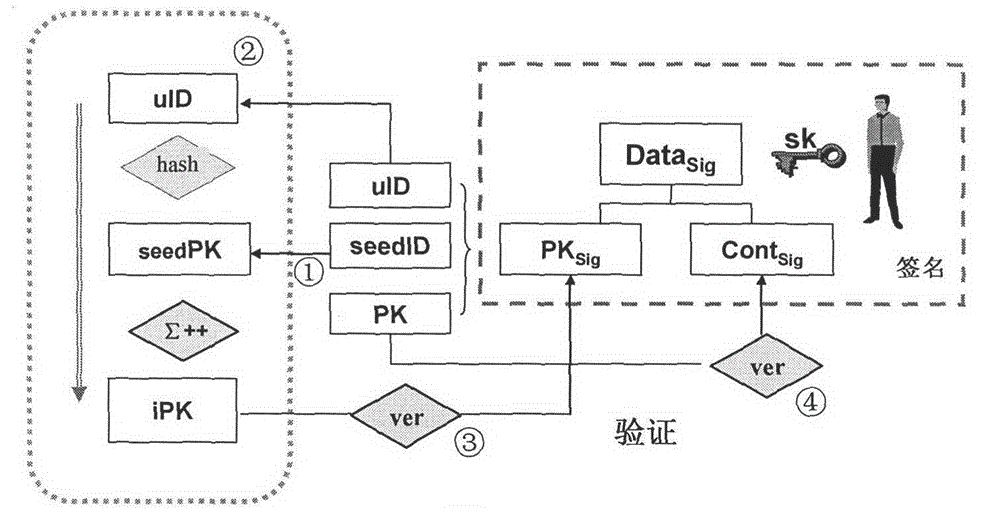
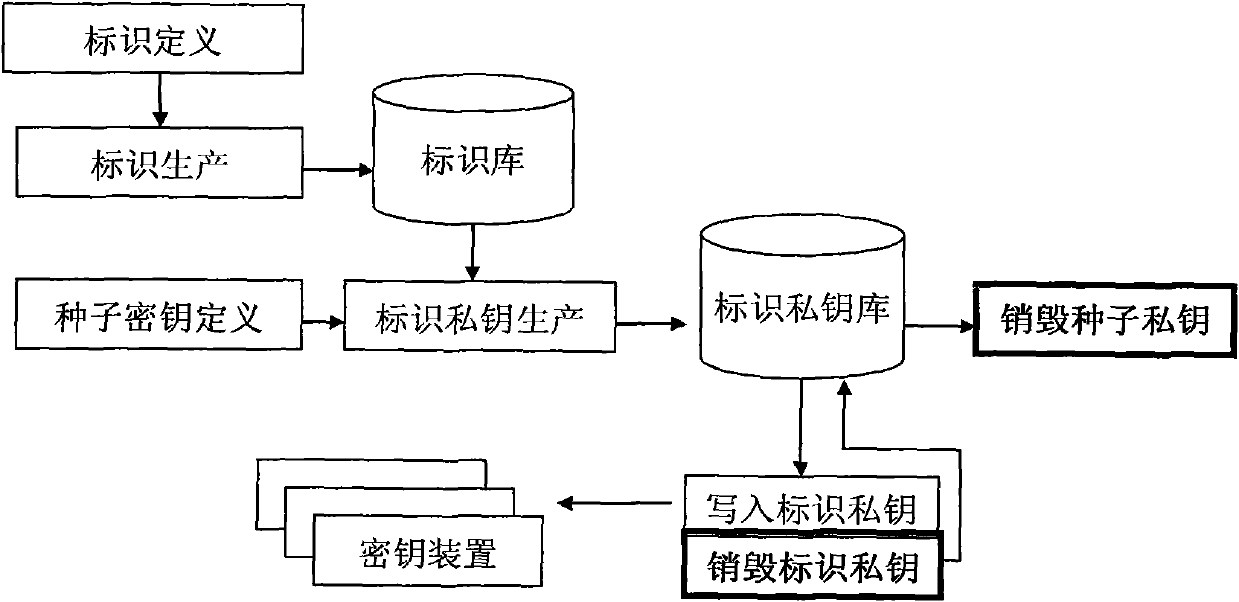
The invention provides identification authentication-based technology, and relates to secret key devices for supporting anonymous authentication. Identification secret keys generated by anonymous identifiers are stored in the secret key devices. The generation method of the secret key devices for supporting the anonymous authentication comprises the following steps of: defining and generating at least one anonymous identifier; defining a seed secret key pair, wherein the seed secret key pair consists of a seed public key and a seed private key; allowing the anonymous identifiers to generate identification private keys corresponding to the anonymous identifiers respectively through the seed private key; and writing the generated identification private keys into each secret key device. The invention also provides a back-up unlocking method of the dual secret key devices. The devices and the method can support requirements of social and publics on anonymous safety service, and reduce theapplication threshold of the authentication technology greatly.
Owner:北京联合智华微电子科技有限公司
User autonomy-based identity authentication implementation method
InactiveCN104901804AAchieve autonomous controlRealize managementPublic key for secure communicationUser identity/authority verificationDigital signatureAnonymous authentication
The invention discloses a user autonomy-based identity authentication implementation method. In a system, both an identity and a key are defined by a user, and real-name and anonymous authentication, and autonomous control and management of the key are supported; a user public key is digitally signed and verified through generation of a user identity key with a seed key, so that binding and proving of the user identity and the key are realized; and direct cross-domain cross authentication among different trust domain users is realized through construction and management of a seed pubic key set. The system is simple, flexible and suitable for anonymous authentication, supports real-time authentication, and can be used for constructing a diversified identity-based authentication service system.
Owner:赵捷 +1
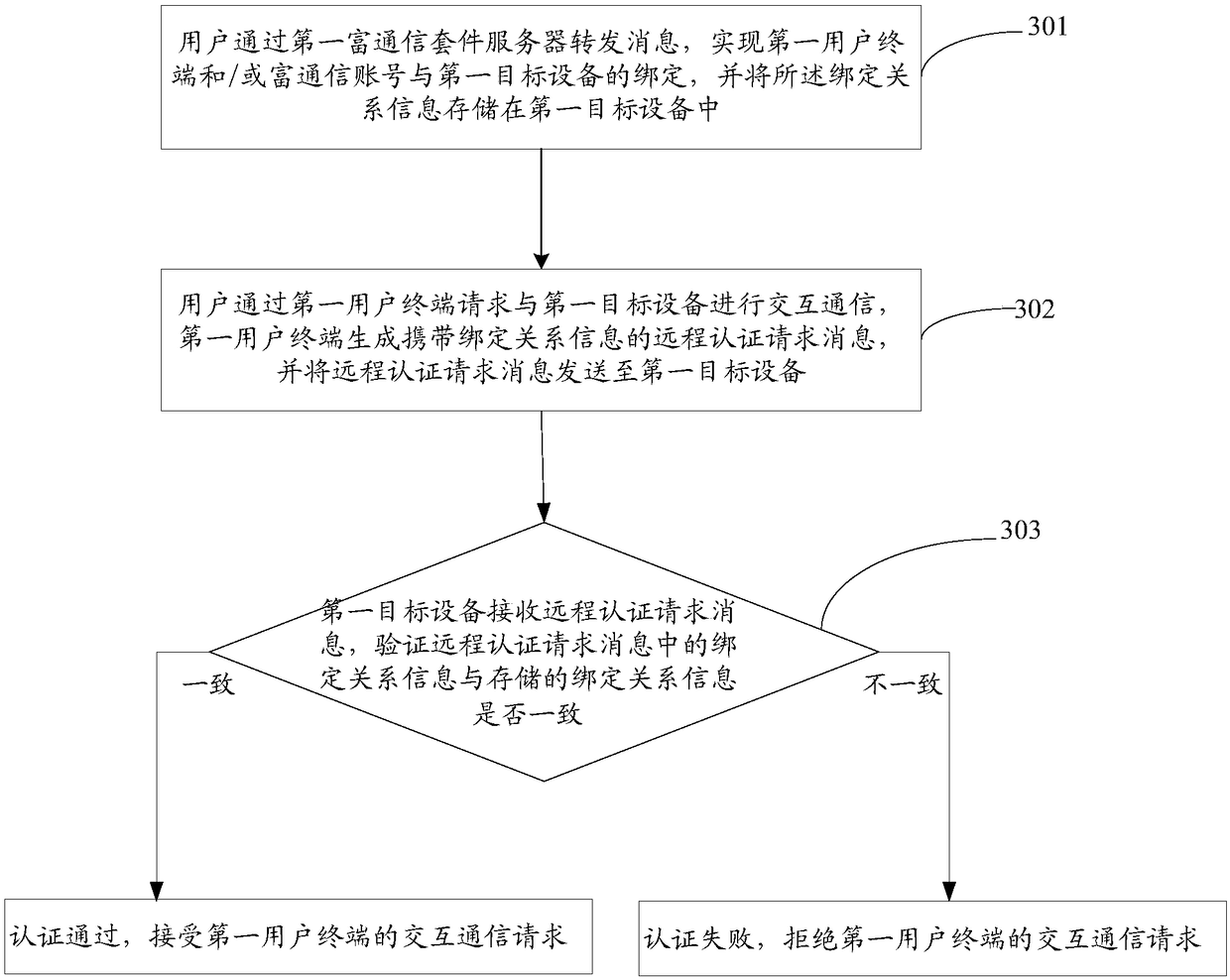
Internet of Things authentication system and Internet of Things authentication method
InactiveCN108696479AEnable secure interactionsAvoid analysisDigital data authenticationTransmissionThe InternetComputer terminal
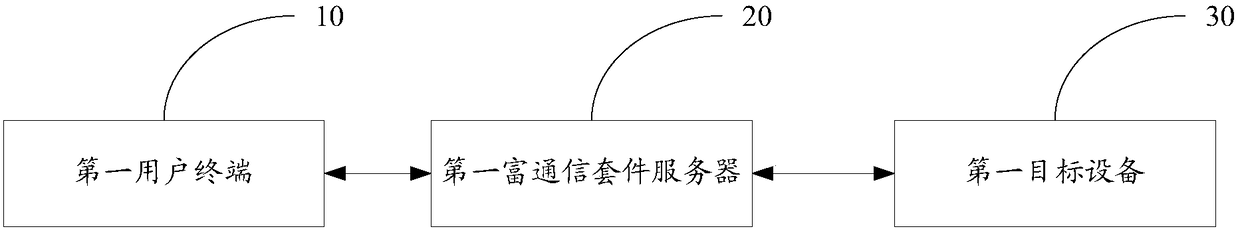
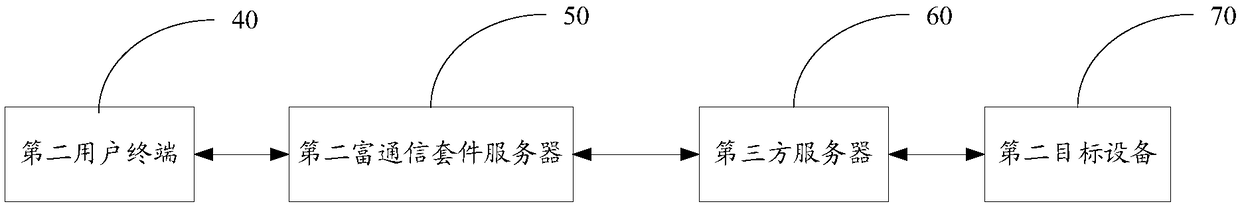
The invention discloses an Internet of Things authentication system and an Internet of Things authentication method. The Internet of Things authentication system comprises a first user terminal for accepting an interactive communication request of a user, generating a remote authentication request message carrying binding relationship information, and sending the remote authentication request message to a first target device; a first rich communication suite server for realizing message forwarding between the first user terminal and the first target device in a process of establishing establishing a binding relationship among the first user terminal and / or a rich communication account and the first target device, and authenticating the binding relationship; and the first target device forstoring the binding relationship information, receiving the remote authentication request message, detecting whether the binding relationship information is consistent with the stored binding relationship information, if yes, indicating that the authentication is passed, and accepting the interactive communication request of the first user terminal. The Internet of Things authentication system disclosed by the invention can conveniently and effectively realize the secure interaction between a user and the device and between the device and the device in the Internet of Things environment by means of the instantaneity, security and standardability of the RCS service.
Owner:ZTE CORP
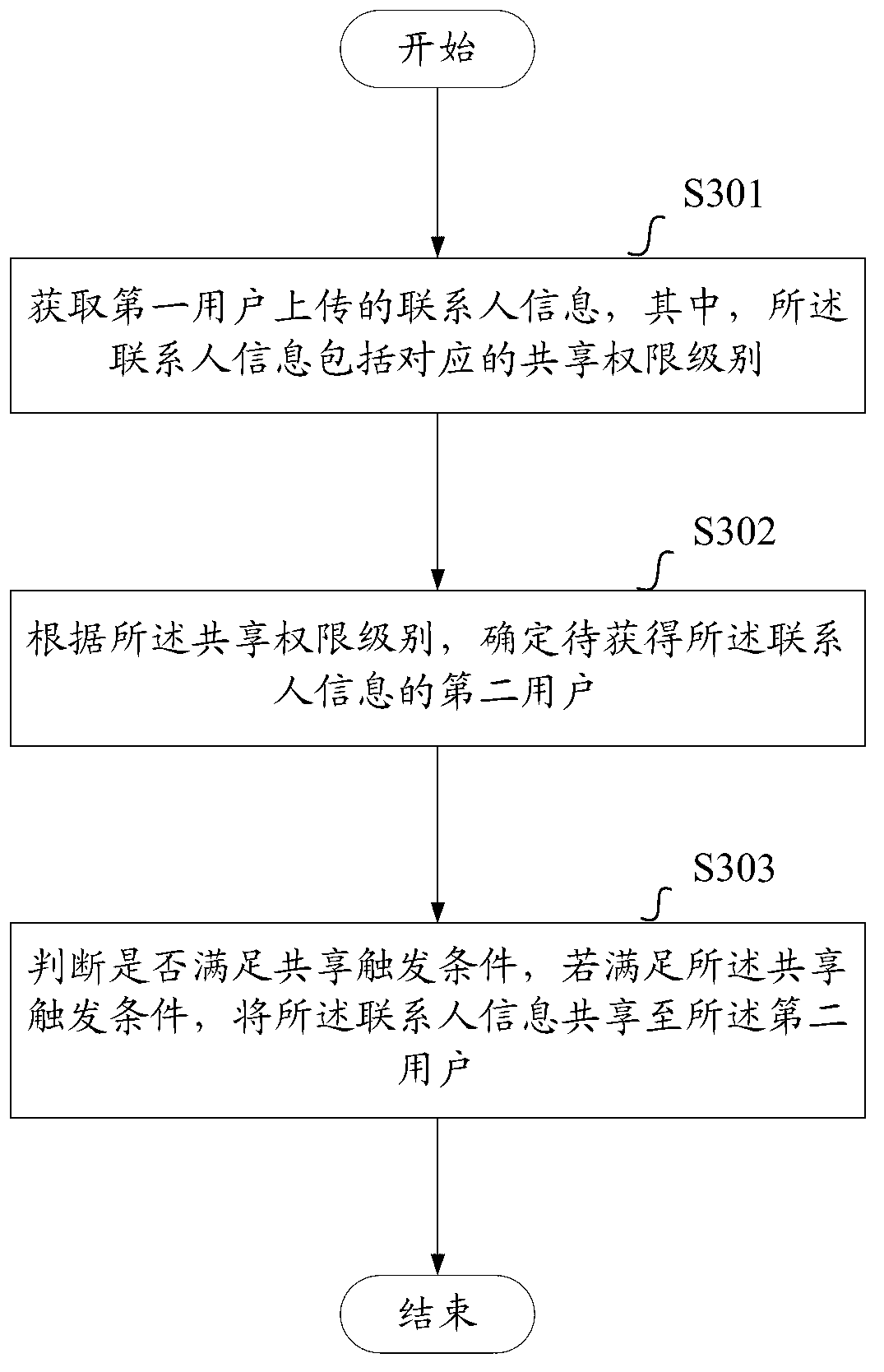
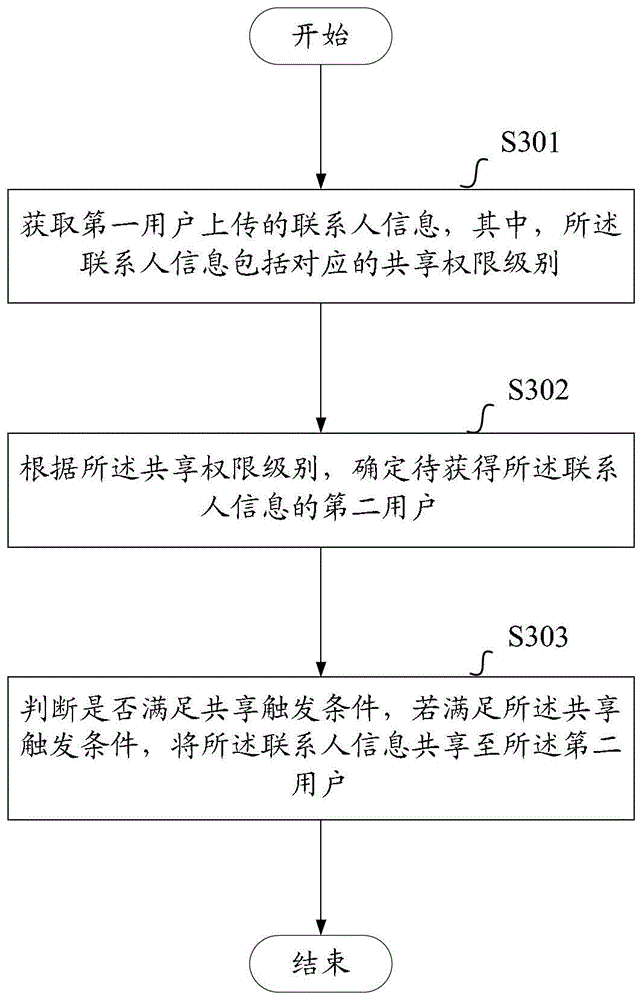
Contact person information sharing method and equipment based on sharing permission level
ActiveCN103327013AIncrease stickinessLow costData switching networksInformation sharingCommunications software
The invention provides a contact person information sharing method and equipment based on a sharing permission level. The method includes obtaining contact person information uploaded by a first user, wherein the contact person information includes the corresponding sharing permission level; confirming a second user to obtain the contact person information according to the sharing permission level; judging whether sharing triggering conditions are met, and if the answer is positive, sending the contact person information to the second user. Compared with the prior art, the contact person information sharing method and equipment confirms the second user to obtain the contact person information on the basis of the sharing permission level of the contact person information uploaded by the first user, sends the contact person information to the second user when the sharing triggering conditions are met, achieves safe interaction of the contact person information, improves information sharing efficiency and improves use experience of users, and the users of communication software can mutually share contact information safely.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
Safety human-computer interactive interface system and implementation method thereof
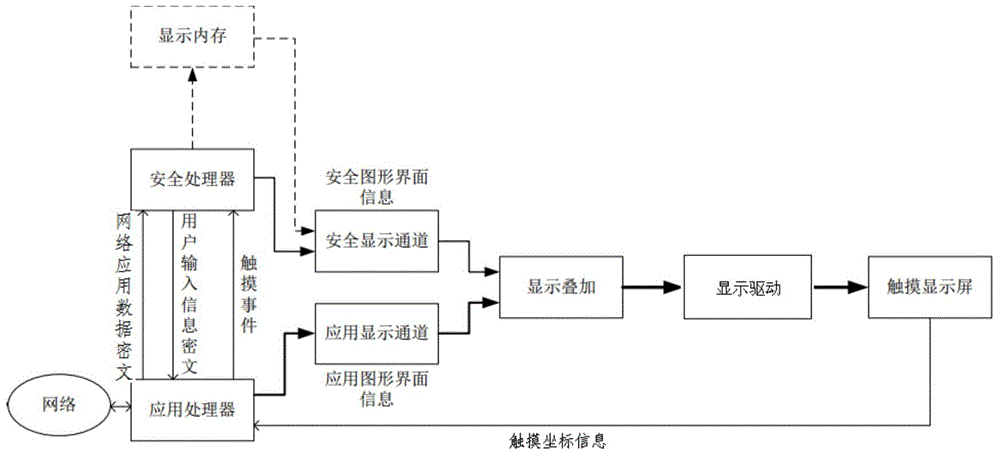
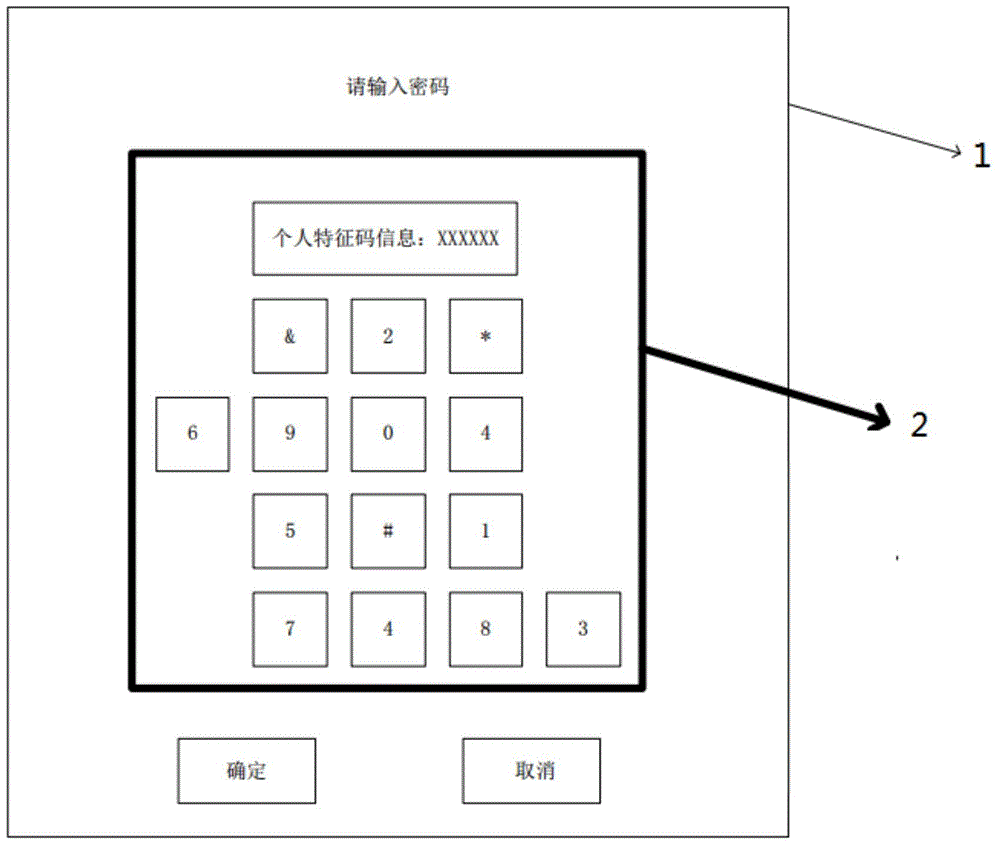
InactiveCN104820573AGuaranteed credibilityEnable secure interactionsDigital data protectionDigital data authenticationGraphicsSafe handling
The invention relates to a safety human-computer interactive interface system which comprises an application processor module, a safety processor module, an application display channel module, a safety display channel module, a display memory module, a display overlaying module, a display driving module and a touch display module. The invention further relates to an implementation method for a safety human-computer interactive interface. Keyboard display information generated by a protected safety processing module and display information generated by a universal processor undergo isolation operation and combined display. Through the overlaid display of separated safety graphical interfaces and application graphical interfaces, an application processor cannot obtain safety graphical interface information; users can obtain personal characteristic information through the safety graphical interfaces and make a comparison with preset personal characteristic information, so as to guarantee the credibility of input information interfaces; and a safety processor analyzes the interaction of the users and safety interfaces, so as to achieve safety interaction of sensitive data.
Owner:南京芯度电子科技有限公司
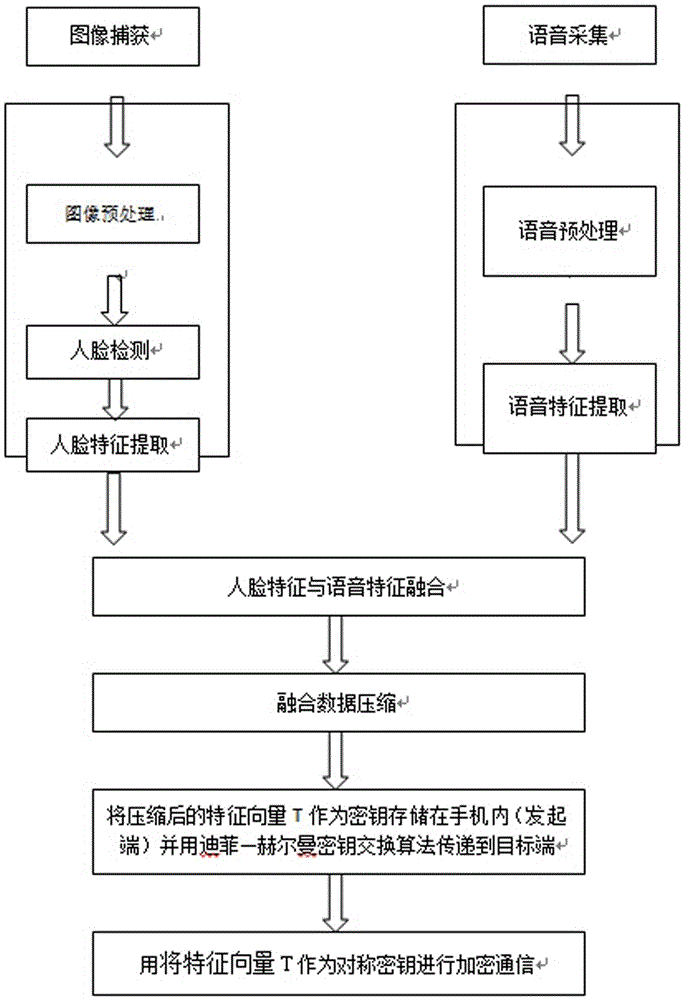
Handset NFC safety payment method based on integrated voiceprint and face characteristic encryption
The invention discloses a handset NFC safety payment method based on integrated voiceprint and face characteristic encryption. The method is characterized by comprising steps that, image acquisition and voice acquisition are carried out; the acquired image and the acquired voice are respectively processed; integrated processing on a face characteristic vector and a voice characteristic vector is carried out to acquire a characteristic vector P; the characteristic vector P is compressed to be in 256-bit bytes, and a characteristic vector T is acquired; the characteristic vector T is taken as a secret key and is stored in a handset as an initiation end, and the characteristic vector T is transmitted by utilizing a Diffie-Hellman key exchange algorithm to a target end; the characteristic vector T is taken as a symmetric secret key by two communication parties to carry out encryption communication. The method is carried out in an NFC point-to-point mode, and through the method, information safety interaction during handset NFC payment can be realized.
Owner:GUILIN UNIV OF AEROSPACE TECH
Man-machine safety protection system and safety protection method
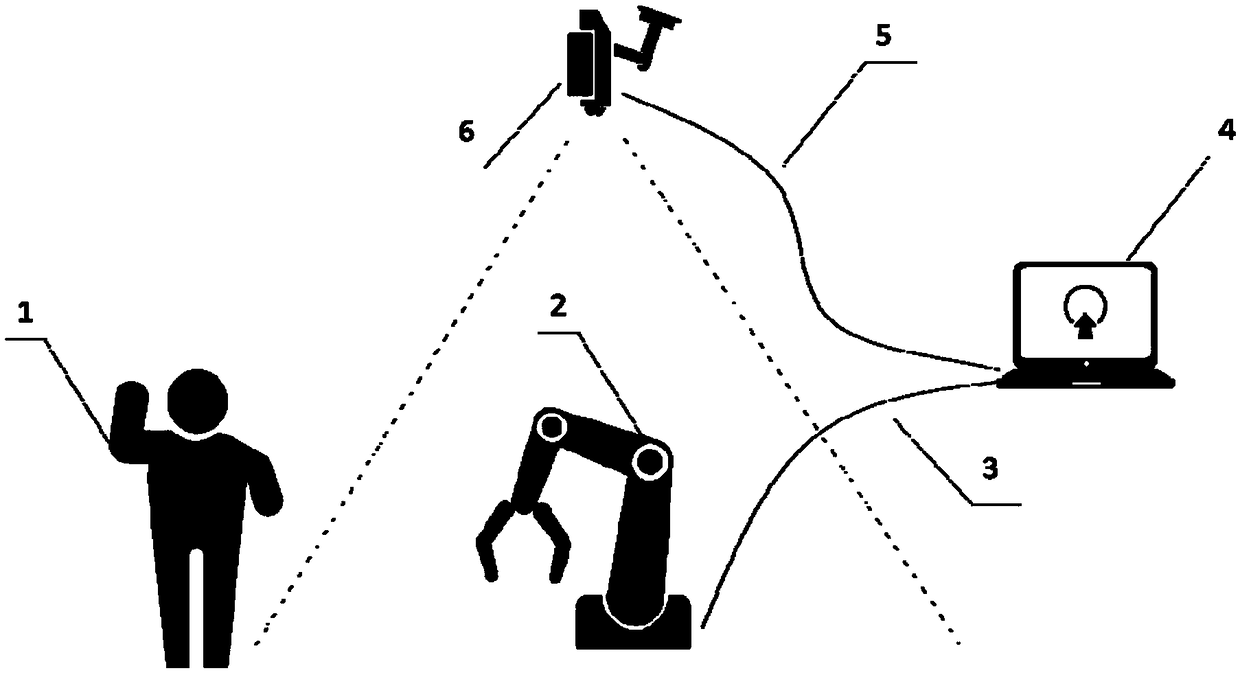
ActiveCN108789500AEnable secure interactionsLow costCharacter and pattern recognitionManipulatorMan machineEngineering
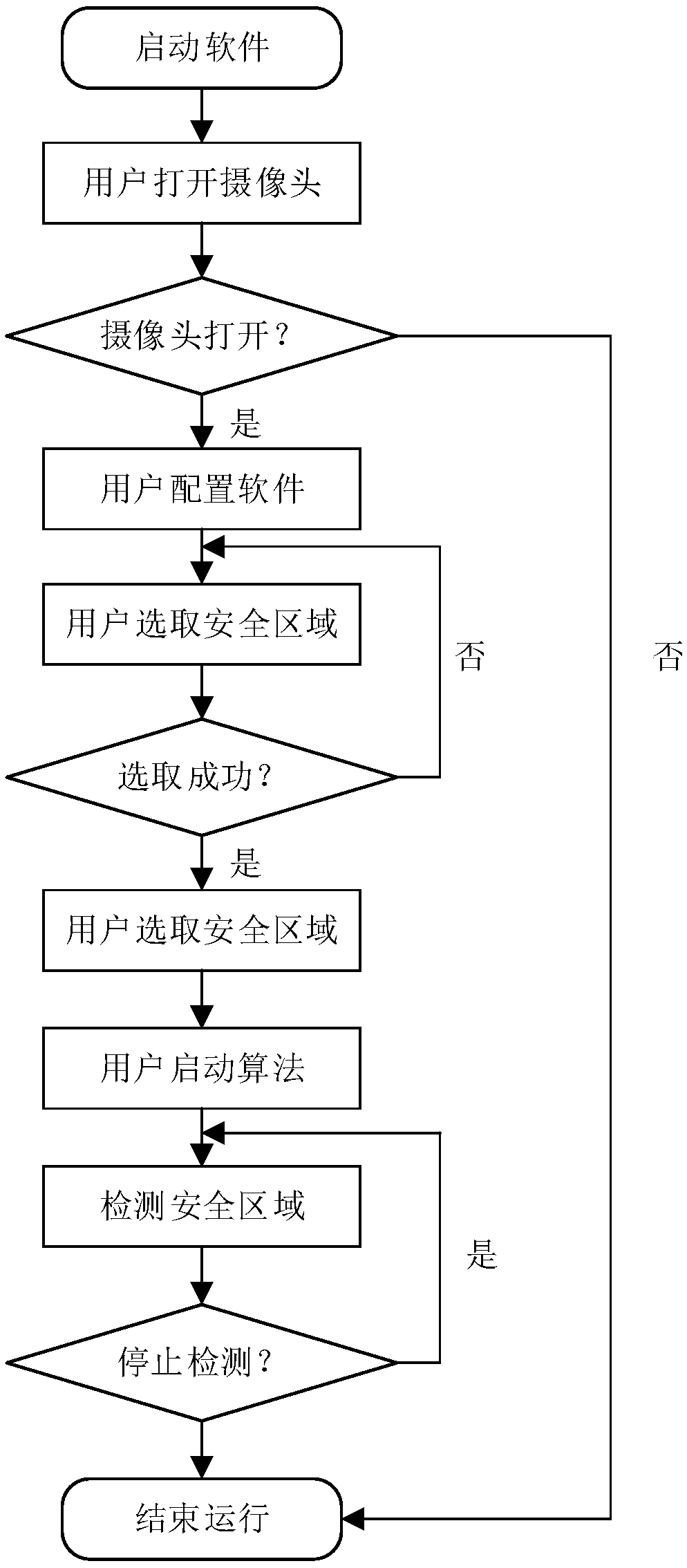
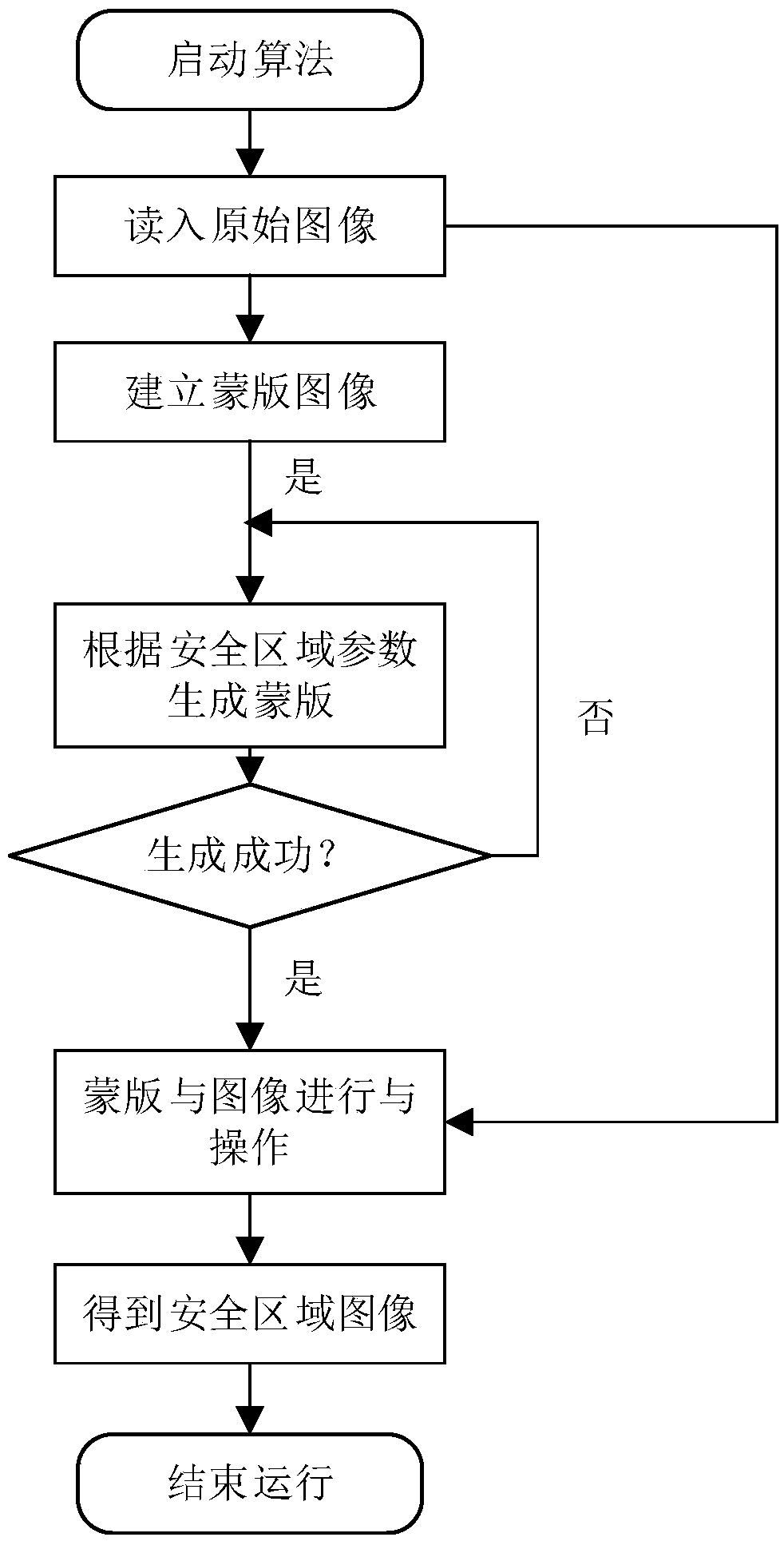
The invention provides a man-machine safety protection system and a safety protection method. A common camera is adopted and arranged at the top end of a robot, whether an object enters the detectionrange specified by a user is judged through a foreground extraction method by filtering out pixels of a robot body, if a moving object appears, the robot is slowed down or stopped, and safety of the robot and operators is ensured. The common RGB camera is adopted, and the cost is low; and the camera does not need to be calibrated, the detection range can be specified according to the user requirements, maintenance is convenient, configuration is flexible, and efficiency is high.
Owner:SHANGHAI JIEKA ROBOT TECH CO LTD
PDC data interface system oriented to multiple applications
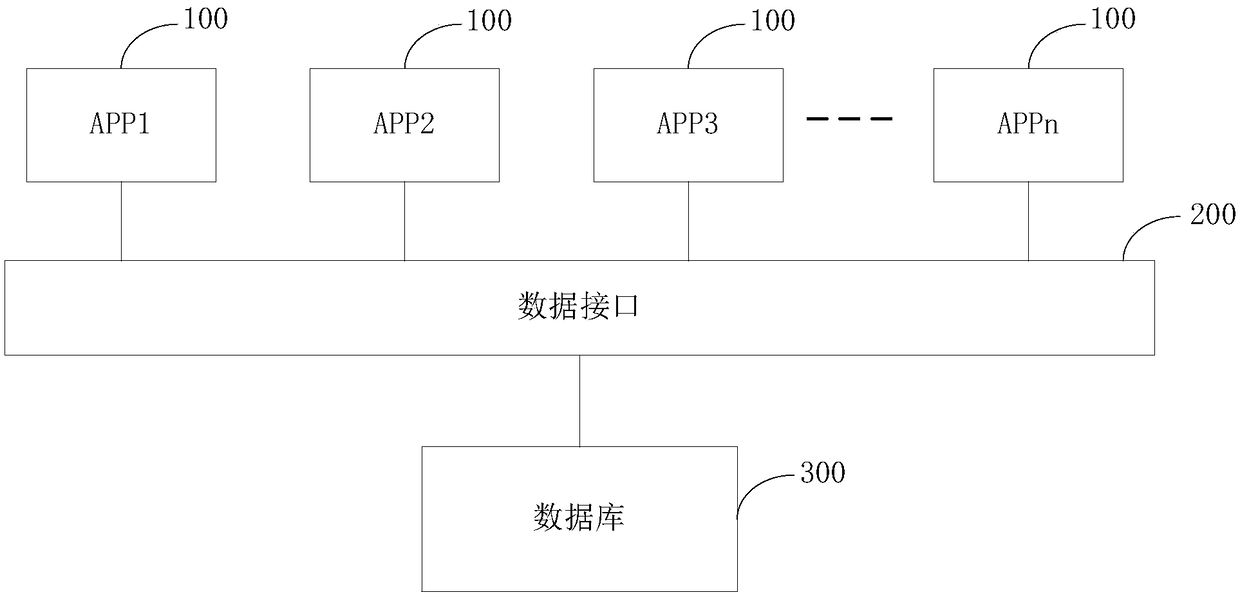
InactiveCN108920972AEnable secure interactionsSolve data interaction problemsDigital data protectionDigital data authenticationInteraction problemData storing
The application provides a PDC data interface system oriented to multiple applications. The system comprises at least one application, a database used for storing personal data and a data interface located between the at least one application and the database. The data interface is concretely used for receiving data request information sent by a first application and authenticating the first application according to the data request information. The data interface is used for acquiring target data requested by the data request information from the database after authentication is successful and returning the target data to the first application. The first application is any one application from the at least one application. Through the data interface, a data interaction problem between different applications and the database can be effectively resolved. Safe interaction is achieved between the multiple applications and the personal data stored in the database, thereby effectively protecting the personal data.
Owner:湖南岳麓山数据科学与技术研究院有限公司
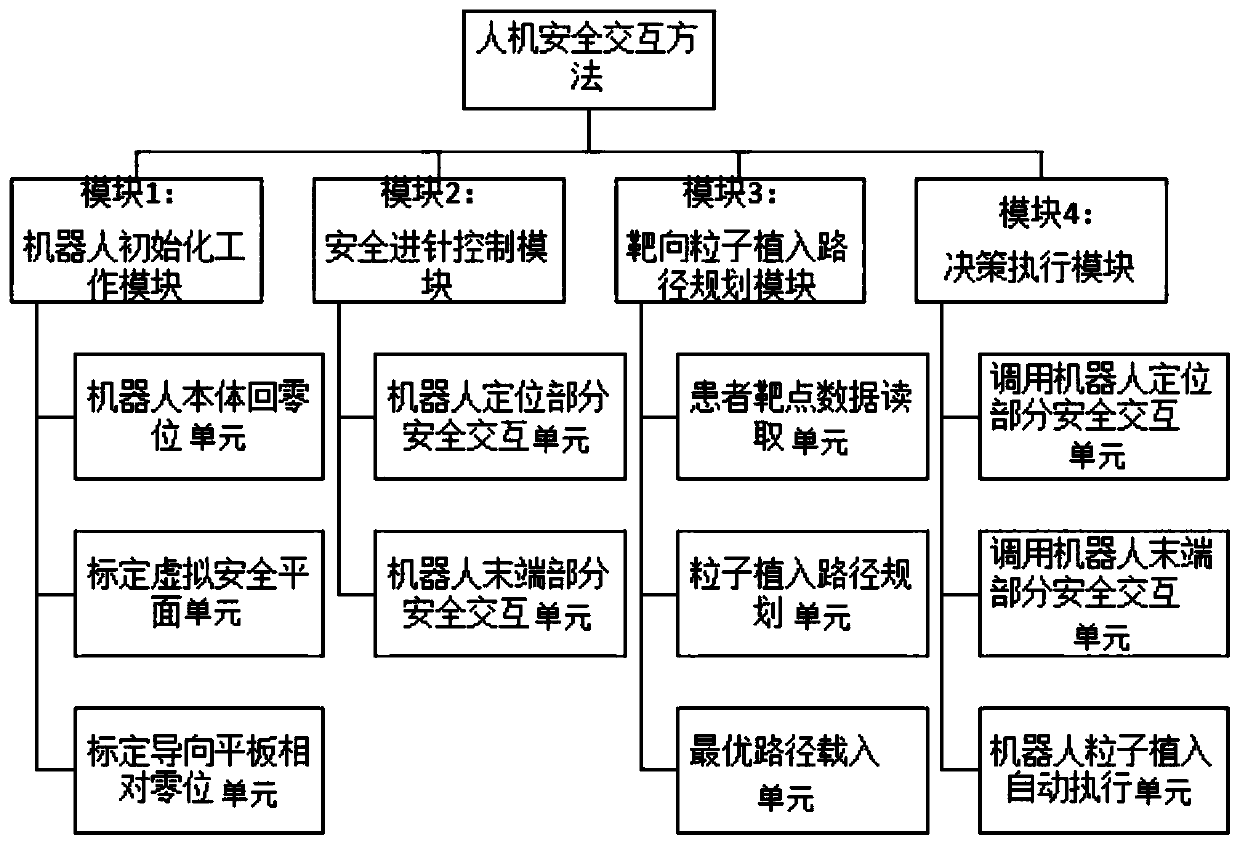
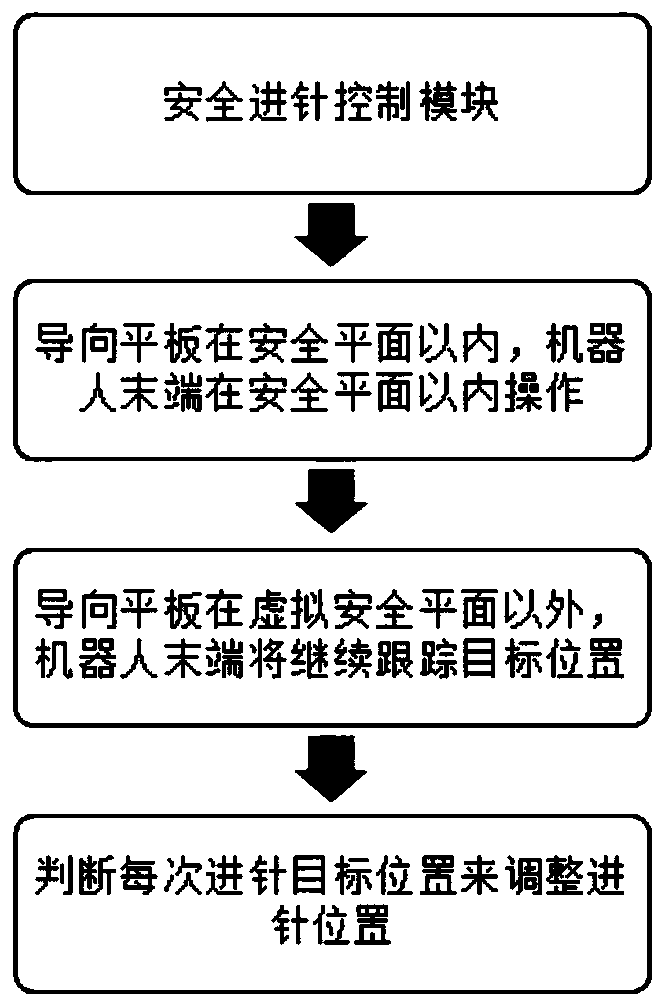
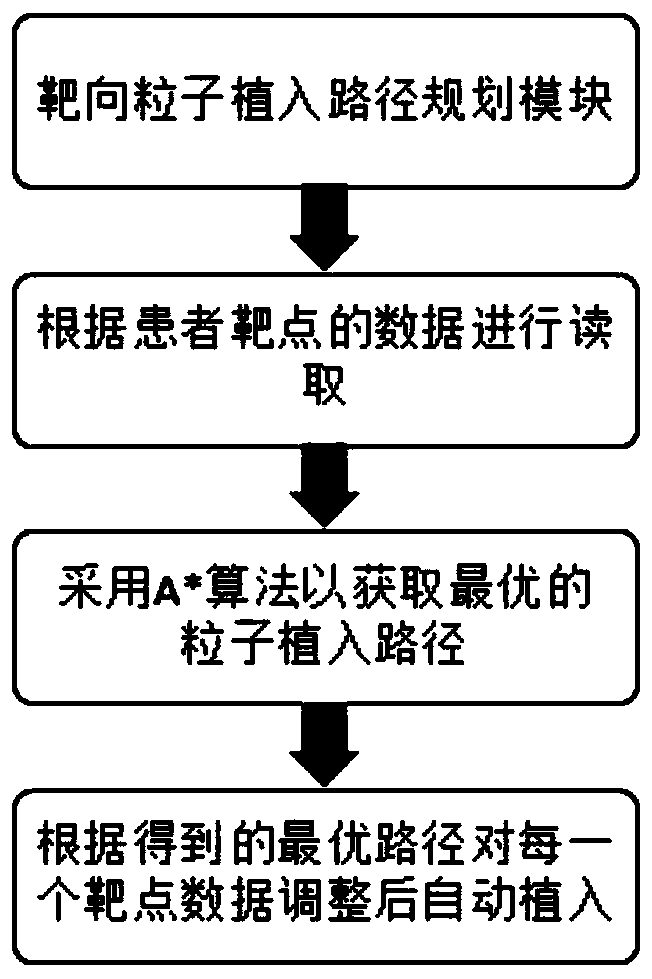
Human-computer safety interaction system and method of clinical lithotomy position target particle implantation robot
InactiveCN110478628AEnable secure interactionsGuaranteed stabilitySurgical navigation systemsSurgical systems user interfaceInteraction systemsExecution unit
The invention relates to the field of use methods of medical devices, and in particular, relates to a human-computer safety interaction system and method of a clinical lithotomy position target particle implantation robot, wherein the system includes a robot initialization work module, a safe needle feeding control module, a target particle implantation path planning module, and a decision-makingexecution module. The method comprises the following specific use steps: S1, robot initialization; S2, displacement; S3, needle feeding control; S4, operation; S5, target position determination; S6, needle feeding; S7, patient target data reading; S8, optimal path; S9, automatic implantation; S10, obtaining of an optimal path loading unit; S11, plane movement; S12, detection; S13, target confirmation; and S14, execution of the unit. Through joint use of the robot initialization work module, the safe needle feeding control module, the target particle implantation path planning module and the decision-making execution module, the safe interaction, safety, stability and high accuracy of the particle implantation process of the target particle implantation robot can be achieved.
Owner:ANHUI POLYTECHNIC UNIV +1
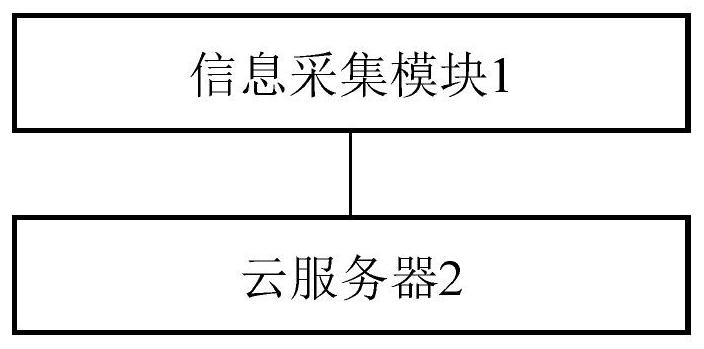
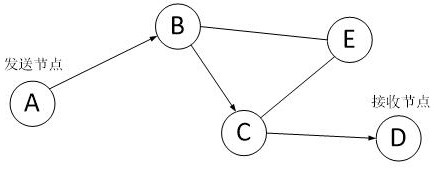
Information security collection and interaction system based on cloud server
InactiveCN111818083APrevent tamperingPrevent peepingParticular environment based servicesTransmissionThe InternetEngineering
The invention provides an information security collection and interaction system based on a cloud server. The system comprises an information collection module and a cloud server, the information collection module comprises an aggregation node, cluster heads and sensor nodes, each sensor node collects sensing information of a monitored position and sends the sensing information to the corresponding cluster head, and the aggregation node transmits the sensing information collected by the cluster heads to the cloud server; the cloud server is provided with a database with a plurality of databasepartitions, and the cloud server allocates corresponding access permission levels to the perception information collected by the cluster heads according to the identifiers of the cluster heads and stores the perception information collected by the cluster heads in the database partitions corresponding to the access permission levels of the cluster heads. Collection of the perception information is achieved through the Internet-of-Things technology, the corresponding access permission levels are distributed to the perception information of the different cluster heads through the cloud server,it is guaranteed that the perception information is only transmitted to a user with access permission or checked by a user with permission, and safety is high.
Owner:广州路昌科技有限公司
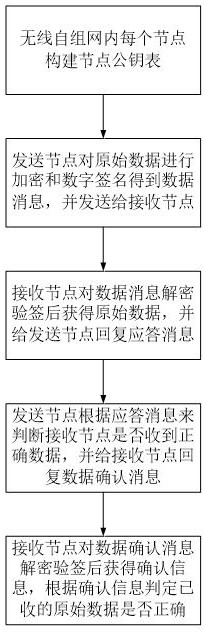
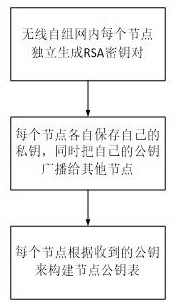
Method for safely transmitting data between wireless ad hoc networks
PendingCN112714507AEnable secure interactionsNo need to increase hardware resourcesEncryption apparatus with shift registers/memoriesUser identity/authority verificationNetwork architectureMessage type
The invention discloses a method for safely transmitting data between wireless ad hoc networks. The method comprises the following steps that: a node constructs a node public key table; a sending node sends a data message to a receiving node; the receiving node sends a response message to the sending node after receiving the data message and carrying out security check; the sending node sends a data confirmation message to the receiving node after receiving the response message and carrying out security check and data comparison; and the receiving node receives the data confirmation message and selects to reserve or discard the data according to the type of the data confirmation message. According to the method, on the basis of a network architecture of the wireless ad hoc network, a hash algorithm, a public key cryptographic algorithm and an encryption authentication technology are fused, and a brand-new data security transmission method is designed, so that security interaction of data between internal nodes of the wireless ad hoc network is realized. The method is wide in application range, easy to implement, safe and reliable, and can be used in some network environments with extremely high security requirements.
Owner:JIANGSU ZHENGHETONG INFORMATION TECH CO LTD
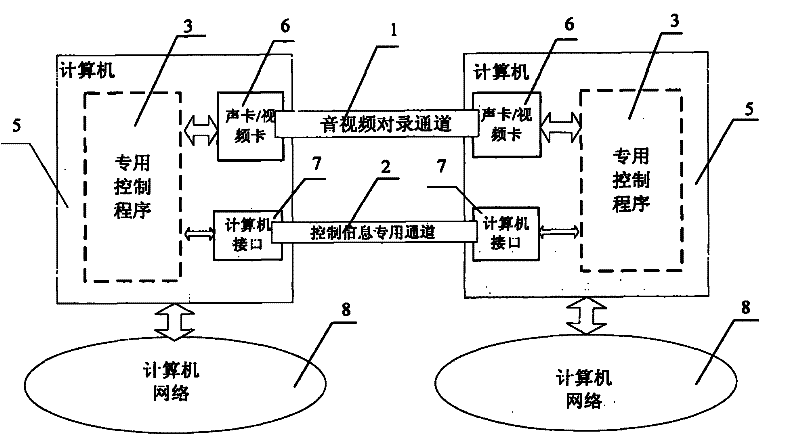
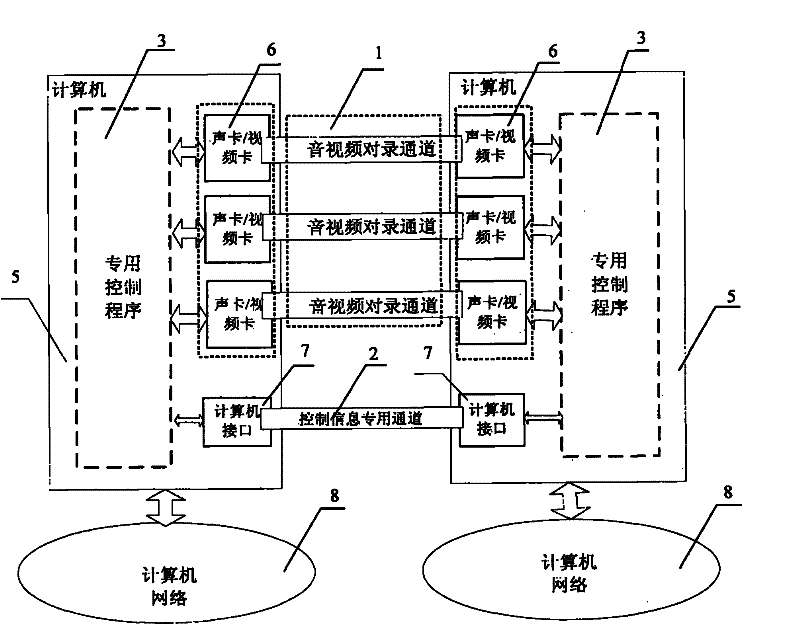
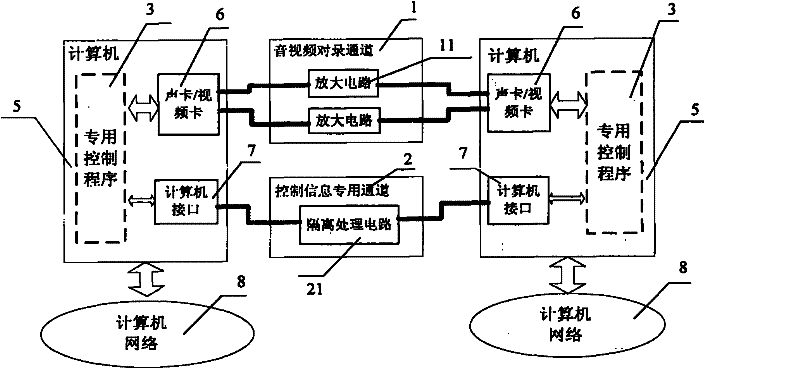
Method and device for realizing secure transfer of audio/video files among computers of different networks
InactiveCN102202068AAchieve securityEnable secure interactionsSound input/outputTransmissionWork periodControl signal
The invention discloses a method and device for realizing secure transfer of audio / video files among computers of different networks. The method transfers an audio / video signal through mutual record of a sound card or video card, realizes automatic mutual record through program linkage control, realizes coordination of program linkage control through special data interaction, and realizes security of the special data interaction through a limiting method of data format fixation and circuit isolation. The implementation device transfers the audio / video files through butt joint of the sound card or video card, performs interaction of control signal through butt joint of computer interfaces, and controls the mutual record of the sound card or video card in a linkage manner on two computers by use of a special program. The method and device disclosed by the invention can solve the problem that current exchange among the computers of different networks cannot be secure and simple at the same time, and can liberate workers of the broadcast television field from fussy manual re-recording, thereby saving precious working time.
Owner:陈麟华
Data presentation-based continuation type power grid intelligent monitoring and auditing platform and application thereof
ActiveCN113157776AEnable secure interactionsReal-time monitoringData processing applicationsDigital data information retrievalApplication serverSoftware engineering
The invention discloses a data presentation-based continuation type power grid intelligent monitoring and auditing platform and application thereof. The intelligent monitoring and auditing platform comprises an object database module based on special transformer user power energy consumption data, an application server module and a man-machine interaction and comprehensive display module. According to the intelligent monitoring and auditing platform developed by the invention, the potential value of the electric power energy consumption data is fully explored, and real-time, visual, accurate and convenient supervision and examination are realized for a control target in practical application.
Owner:STATE GRID HEBEI ELECTRIC POWER CO LTD
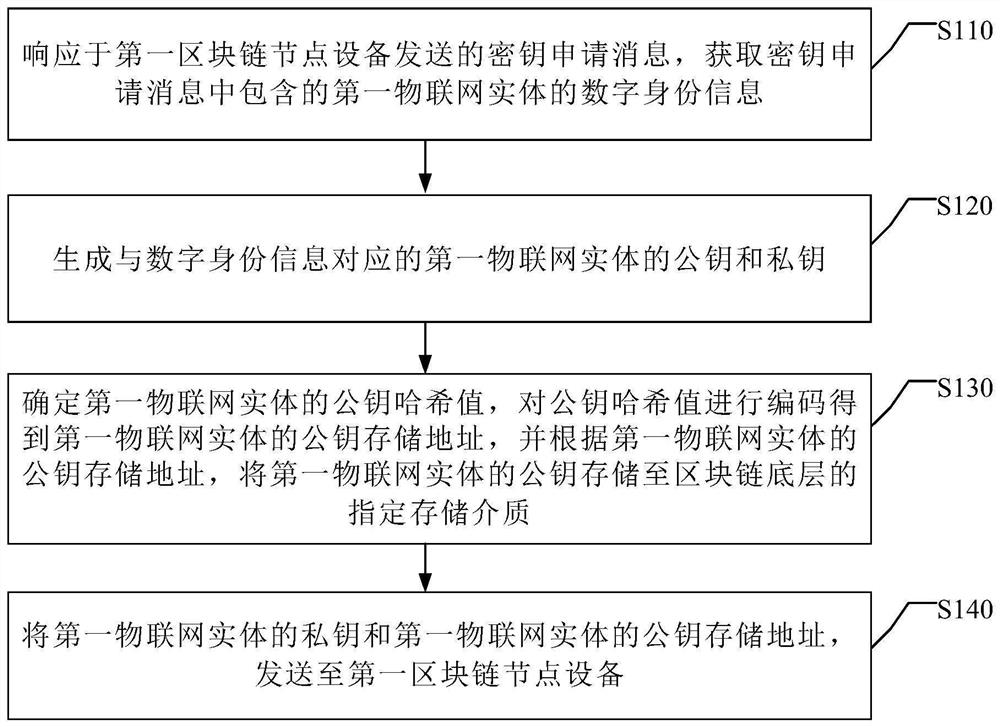
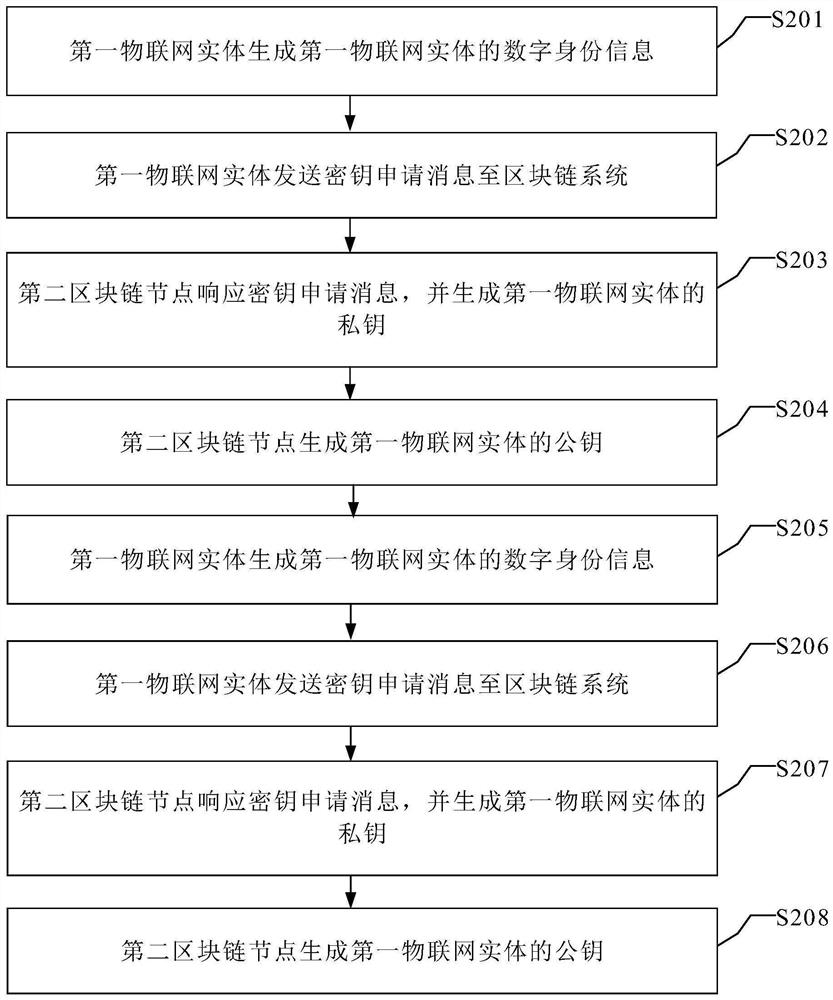
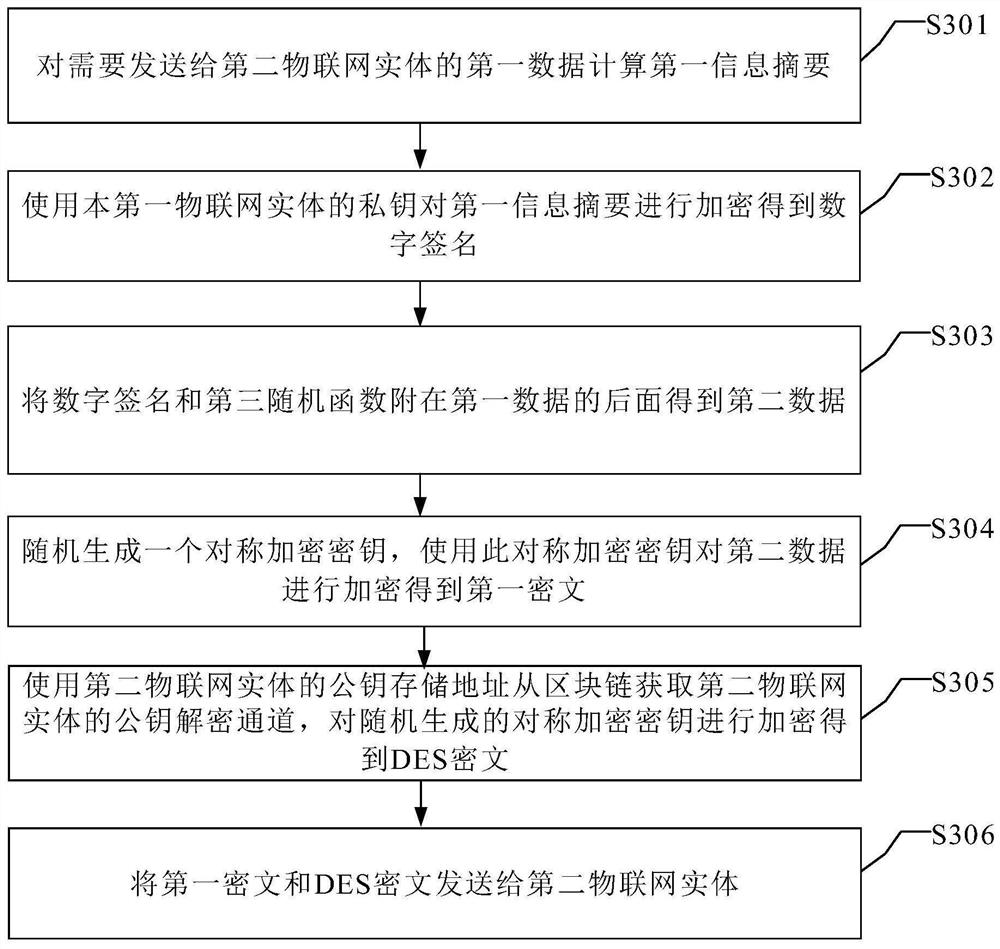
Key management method, system and device
ActiveCN112118245AEnable secure interactionsAchieving Fraud PreventionKey distribution for secure communicationDigital identityComputer network
The invention discloses a secret key management method, system and device. The method comprises the following steps: in response to a key application message sent by a first blockchain node device, obtaining digital identity information of a first Internet of Things entity included in the key application message; generating a public key and a private key of the first Internet of Things entity corresponding to the digital identity information; determining a public key hash value of the first Internet of Things entity, encoding the public key hash value to obtain a public key storage address ofthe first Internet of Things entity, and according to the public key storage address of the first Internet of Things entity, storing a public key of the first Internet of Things entity to a specifiedstorage medium at the bottom layer of the blockchain; and sending the private key of the first Internet of Things entity and the public key storage address of the first Internet of Things entity to the first blockchain node device. According to the method provided by the embodiment of the invention, the security of the Internet of Things entity and the Internet of Things data can be ensured.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
A method and device for sharing contact information based on sharing authority level
ActiveCN103327013BImprove user experienceEnable secure interactionsData switching networksInformation sharingCommunications software
The invention provides a contact person information sharing method and equipment based on a sharing permission level. The method includes obtaining contact person information uploaded by a first user, wherein the contact person information includes the corresponding sharing permission level; confirming a second user to obtain the contact person information according to the sharing permission level; judging whether sharing triggering conditions are met, and if the answer is positive, sending the contact person information to the second user. Compared with the prior art, the contact person information sharing method and equipment confirms the second user to obtain the contact person information on the basis of the sharing permission level of the contact person information uploaded by the first user, sends the contact person information to the second user when the sharing triggering conditions are met, achieves safe interaction of the contact person information, improves information sharing efficiency and improves use experience of users, and the users of communication software can mutually share contact information safely.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
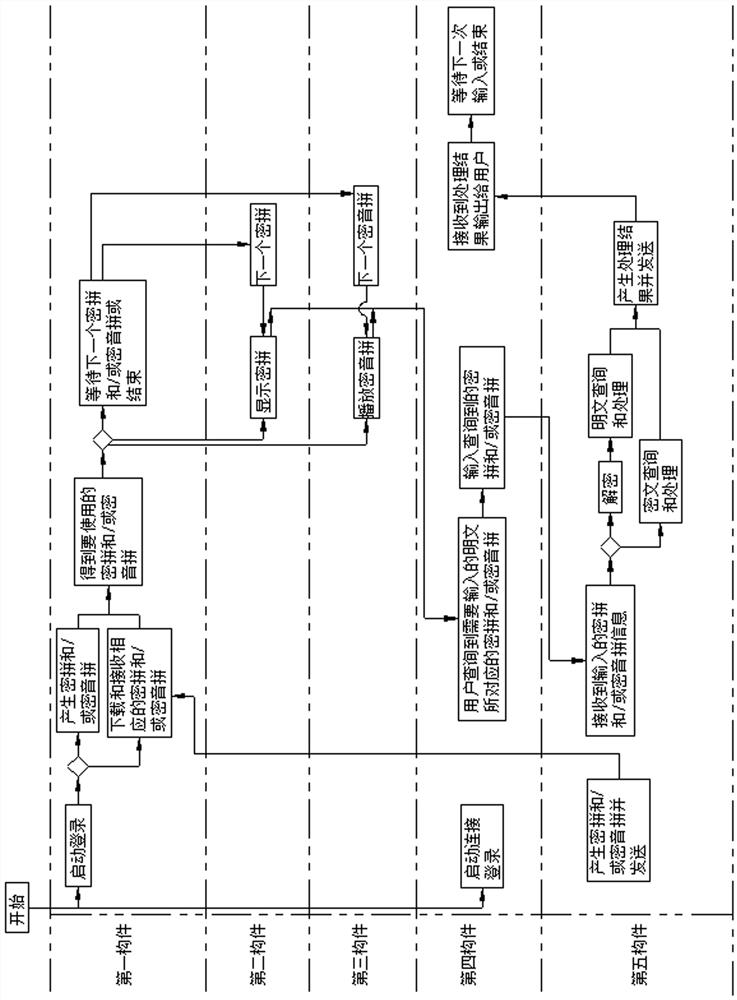
Security interaction system and method, electronic equipment and storage medium
PendingCN114528580AUnlimited interaction time and information volumeEnable secure interactionsDigital data protectionInteraction deviceElectronic equipment
The invention relates to a safety interaction system, which comprises a man-machine interaction system and a man-machine interaction device, the man-machine interaction system comprises a safety application and a safety service, and the safety application generates or receives corresponding secret spelling and / or secret sound spelling between one-time plaintext and ciphertext generated by the safety service. The method comprises the following steps: displaying and / or playing to a user or an administrator, and enabling the user or the administrator to carry out autonomous, unlimited and unlimited man-machine security interaction in a contact or non-contact manner through a standard keyboard, mouse, voice or gesture manner under the condition that the existing man-machine interaction equipment and application software and a security mechanism thereof are not changed at all; and the security of the interacted plaintext information is protected. The invention further discloses a secure interaction method, electronic equipment and a storage medium. According to the invention, through one-time man-machine security interaction, no plaintext appears in the whole process, and the leakage risk that sensitive information is secretly shot, eavesdropped, screenshot, secretly recorded, intercepted and the like in the man-machine interaction process is effectively avoided.
Owner:浙江智贝信息科技有限公司
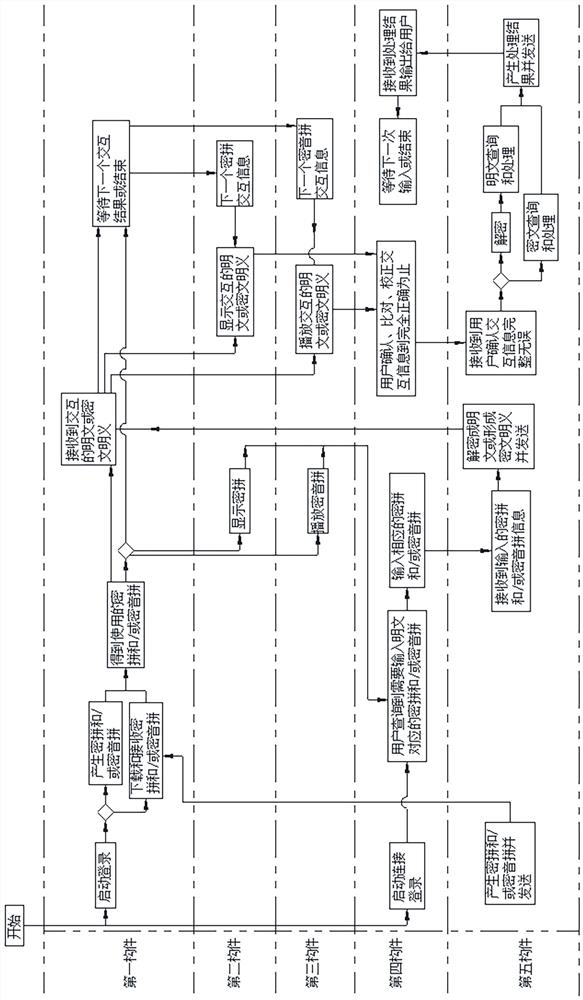
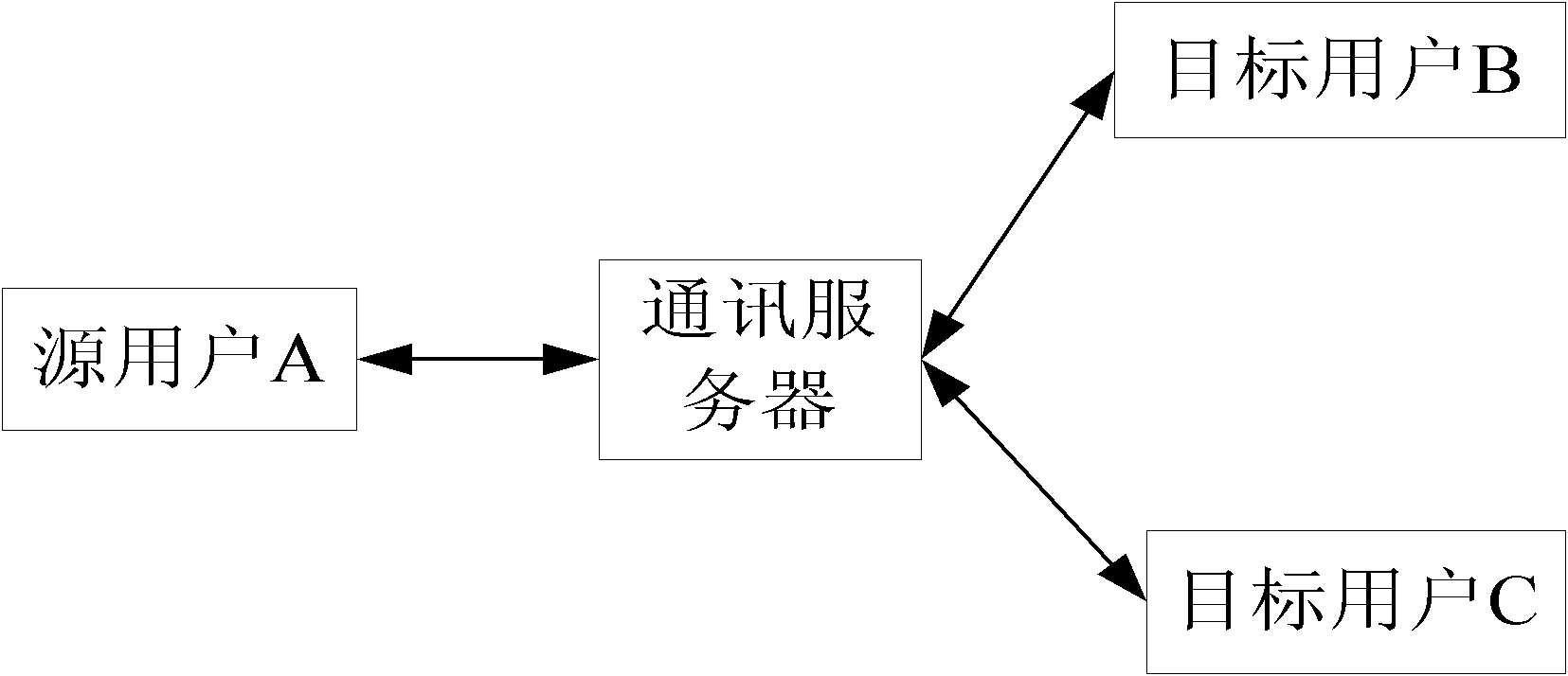
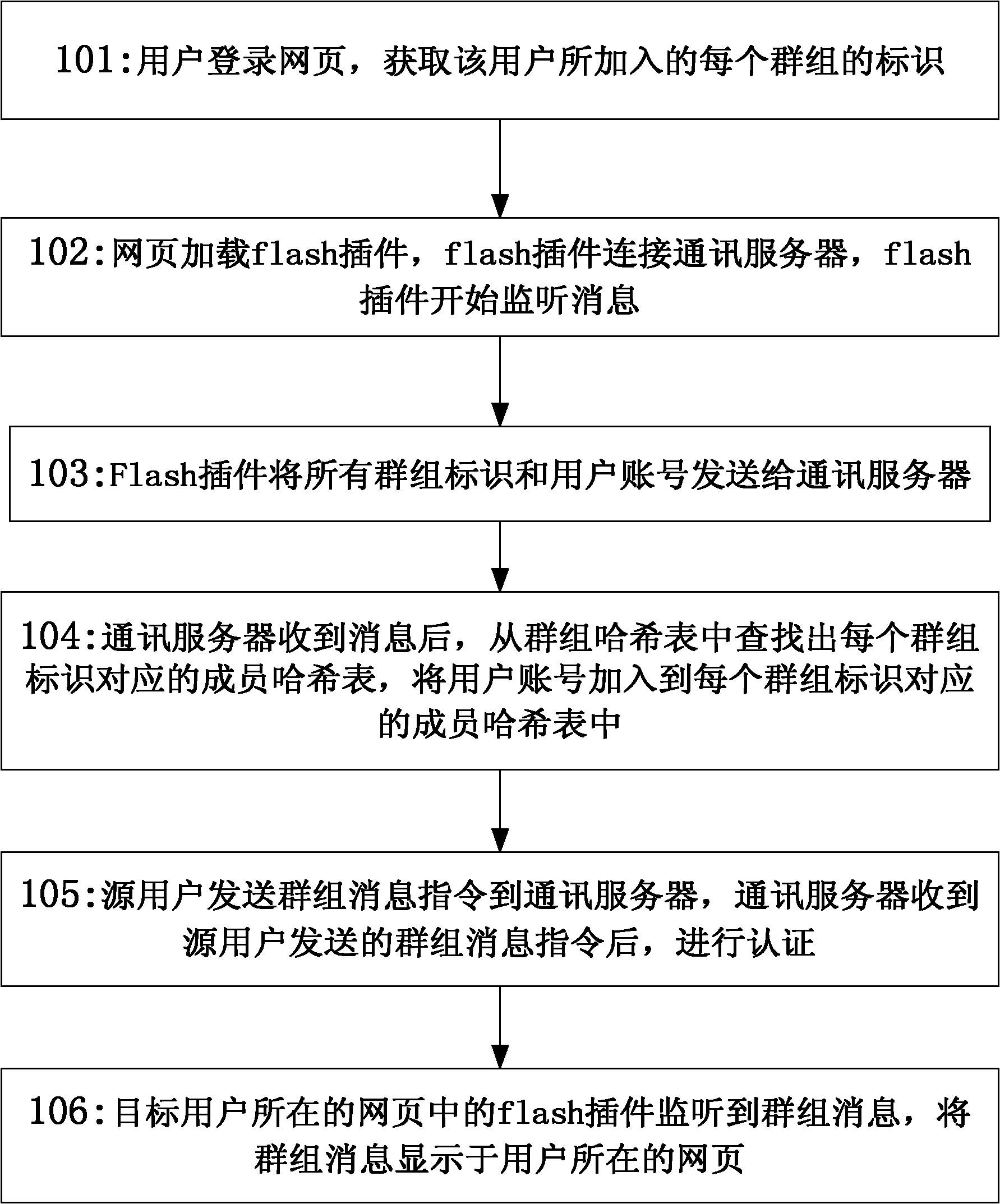
Webpage-based Method and system for realizing secure interaction of group information
The invention discloses a webpage-based method for realizing the secure interaction of group information, comprising the steps that a communication server authenticates the authority of a received group information instruction which is sent by a source user; after the authority is approved, the communication server authenticates the authority of a target user receiving the group information instruction; and after the authority of the target user is approved, the communication server authenticates sends the group information instruction to the target user. The invention also discloses a webpage-based system for realizing the secure interaction of group information, comprising the source user, the communication server and the target user, wherein the communication server authenticates the authority of the received group information instruction which is sent by the source user; after the authority is approved, the communication server authenticates the authority of a target user receiving the group information instruction; and after the authority of the target user is approved, the communication server sends the group information instruction to the target user. By the method and the system, the secure interaction of group information can be realized without installing and downloading any software.
Owner:SUZHOU CODYY NETWORK SCI & TECH
Business processing method and system
ActiveCN103942093BRealize data interactionEnable secure interactionsMultiprogramming arrangementsCommerceThird partyApplication server
The present application discloses a business processing method and system, wherein the method may include: determining the third-party application programs respectively used in each functional module; The identity of the third-party application program, and obtain the callback address of the target third-party application program from the server; the callback address is generated according to the information written into the URL scheme field of the target third-party application program code, and the The target third-party application has registered the information of the URL scheme field in the server; call the target third-party application according to the callback address of the target third-party application, and perform corresponding business processing . Through this application, data interaction between applications can be realized, helping to open up the e-commerce process of multiple applications at different stages.
Owner:ALIBABA GRP HLDG LTD
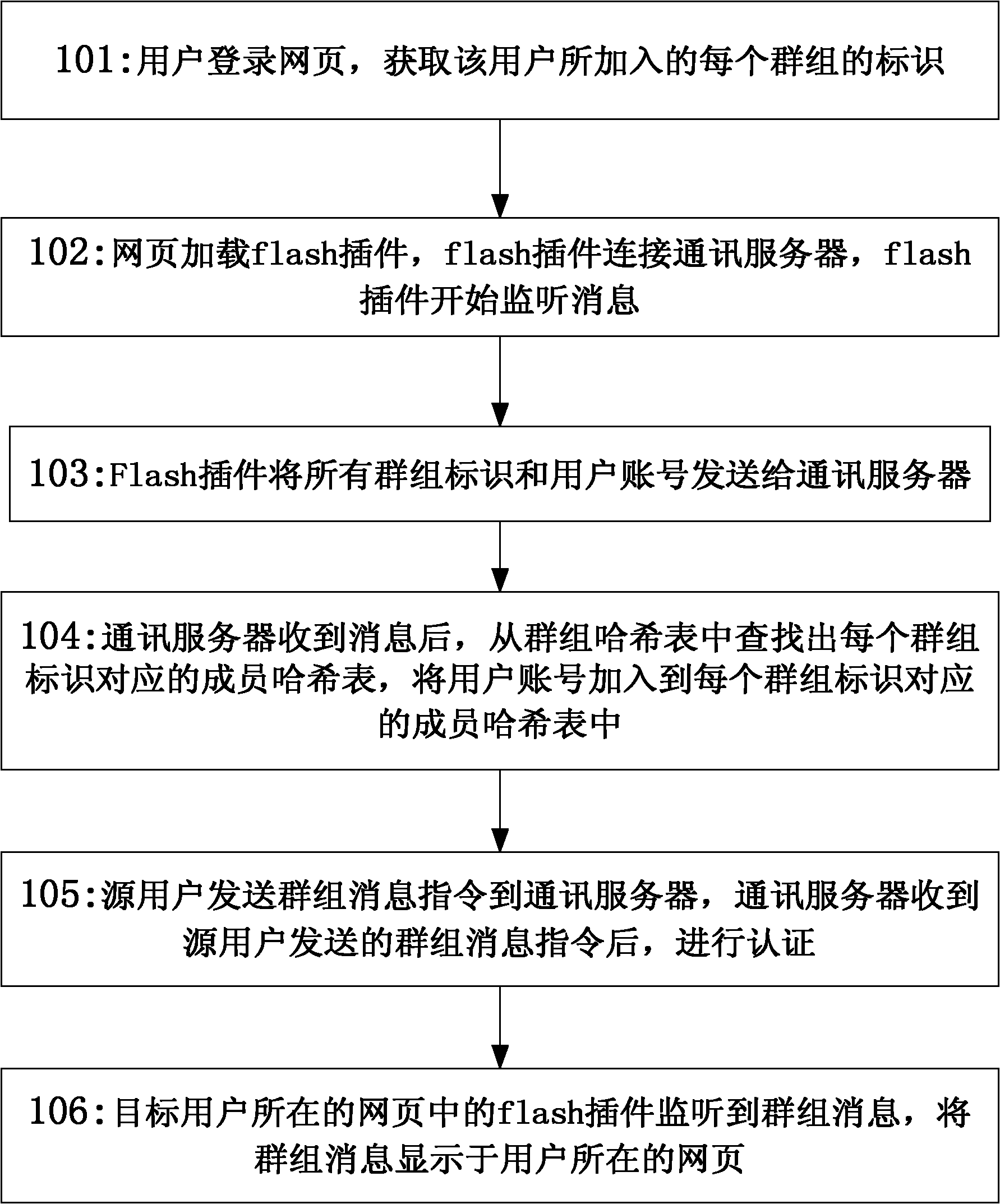
A download method and terminal
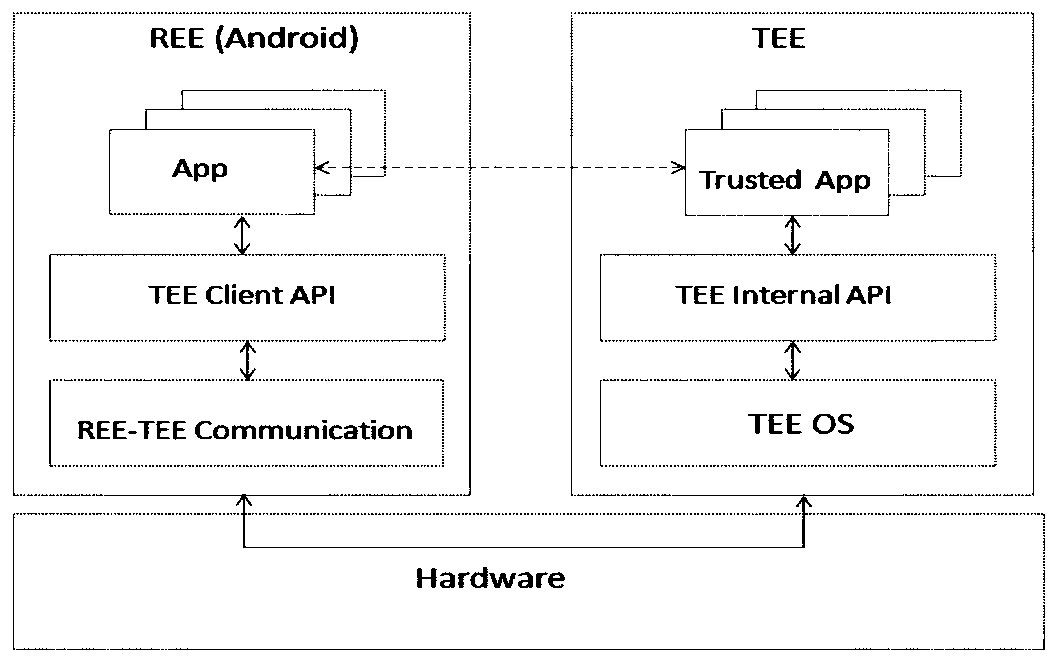
ActiveCN107995230BRealize dynamic downloadEnable secure interactionsInternal/peripheral component protectionPlatform integrity maintainanceComputer terminalSecurity validation
The invention discloses a downloading method applied to a terminal, wherein the terminal supports a rich execution environment (REE) and a trusted execution environment (TEE), the method comprises thefollowing steps: receiving a downloading command sent by a server in the REE, wherein the downloading command comprises first data of a trusted application; transmitting the downloading command to the TEE through a data channel between the REE and the TEE; performing security verification on the downloading command in the TEE, and decrypting the first data after the pass of the verification to obtain second data; performing security processing on the second data to obtain third data; and storing the third data.
Owner:CHINA MOBILE COMM LTD RES INST +1
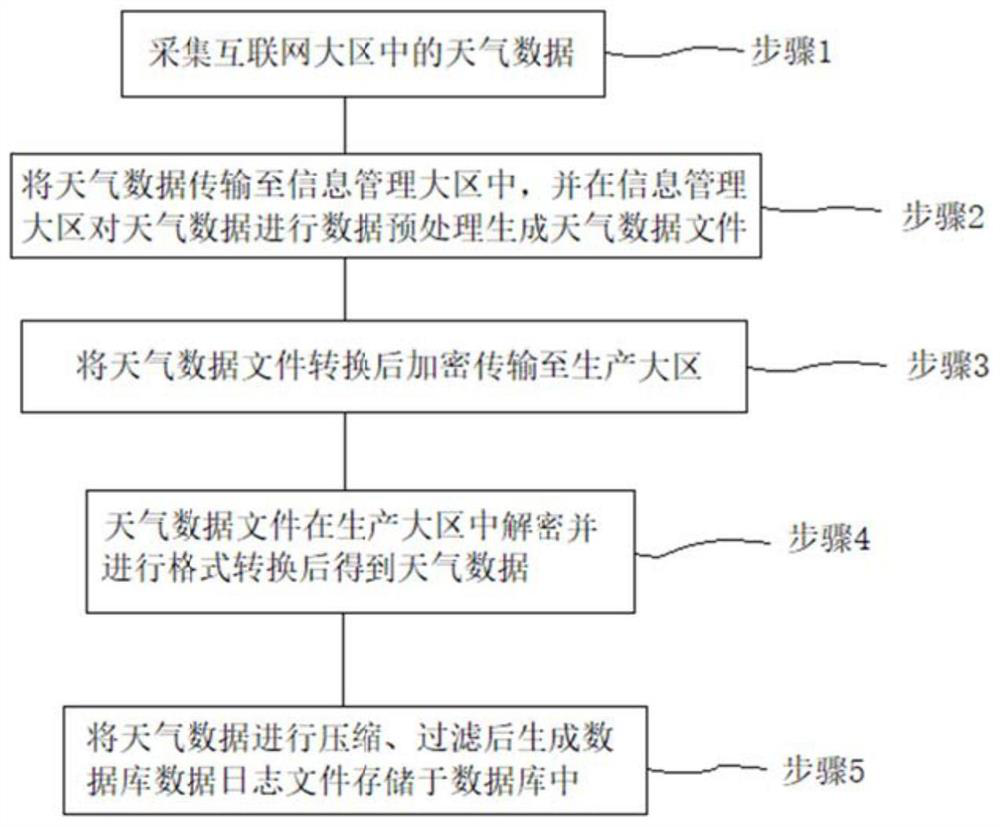
Power plant production region weather data acquisition method, system, equipment and medium
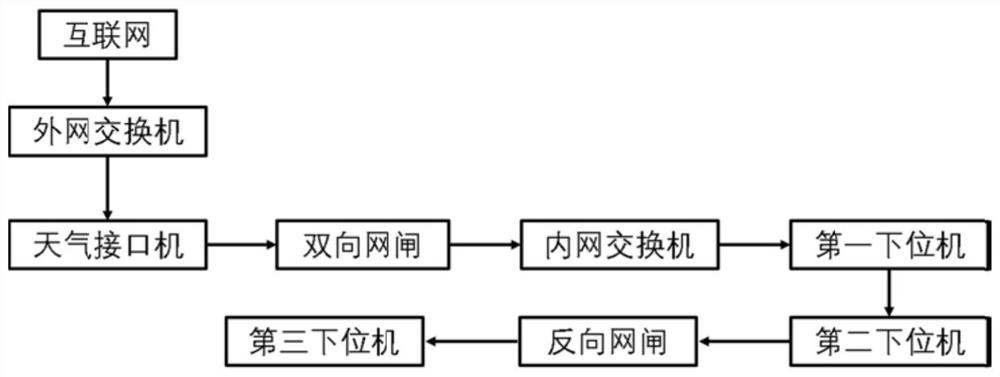
PendingCN114647616AEnable secure interactionsThe degree of structural modification is smallData processing applicationsDigital data protectionEnvironmental resource managementThe Internet
The invention provides a power plant production region weather data acquisition method, system, equipment and medium, weather forecast data from an internet region is transmitted to a production region through a reverse gatekeeper after format conversion and certificate encryption, and then certificate verification and decryption are performed, so that secure interaction of internal and external network data can be realized, and the safety of the data is improved. And the potential safety hazard during data interaction is greatly reduced. Operators in a large production area can adjust boiler output in time according to real-time weather data, energy conservation and emission reduction are achieved, economic benefits are improved, and the goals of carbon peak reaching and carbon neutralization are promoted. The method has high application value in the actual production process of a thermal power plant, and has the potential of large-scale popularization and application.
Owner:XIAN THERMAL POWER RES INST CO LTD
A secure network data interaction system and method
ActiveCN110830760BEnable secure interactionsDoes not change network securityClosed circuit television systemsSelective content distributionComputer hardwareComputer architecture
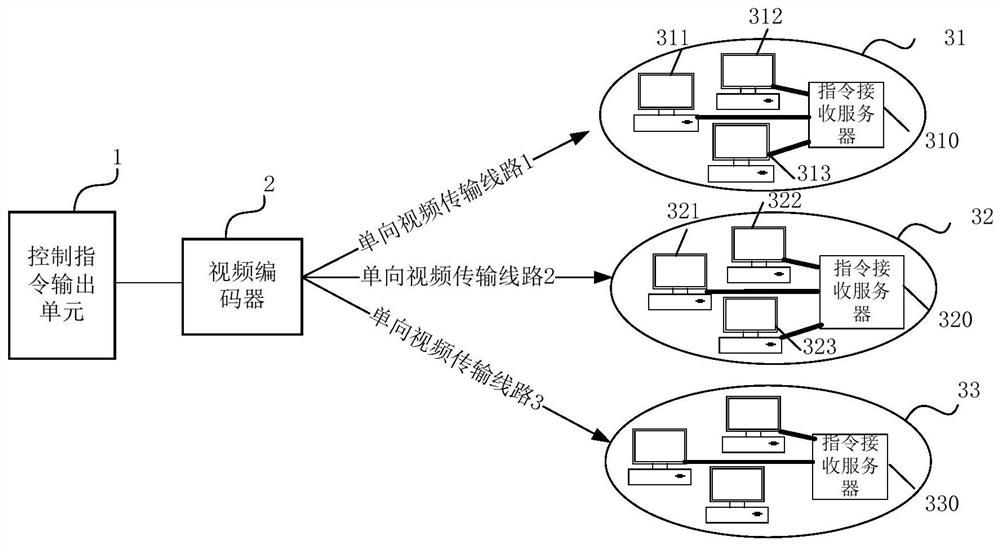
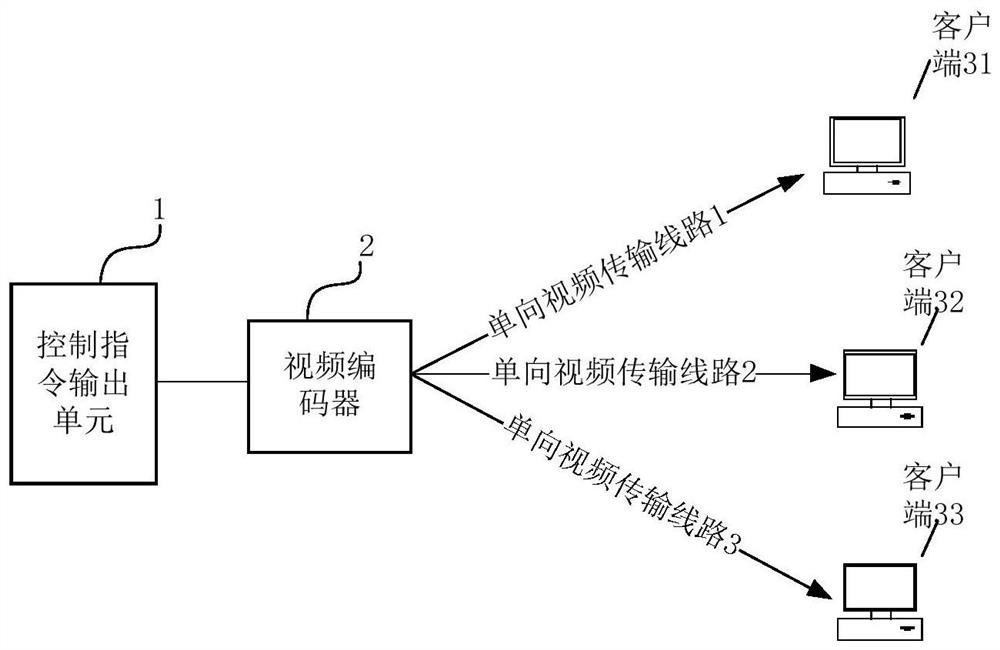
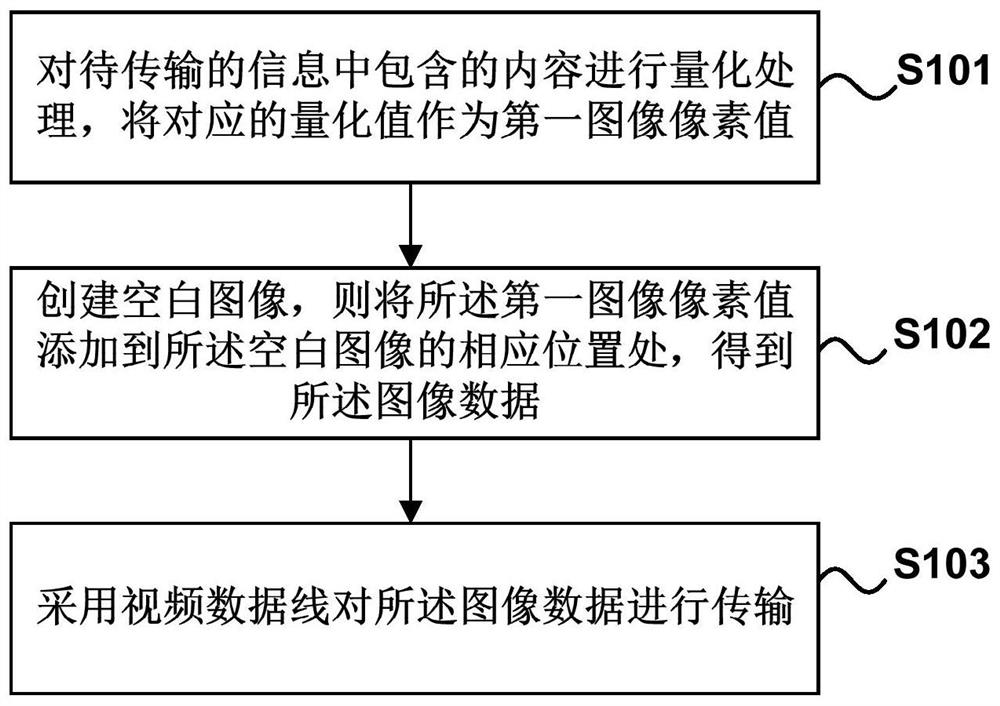
The invention discloses a safe network data interaction system, comprising: a control instruction output unit, a video encoder, and at least two subnets with mutual data isolation; each of the subnets includes an instruction receiving server and at least one client; The control instruction output unit is used to output the control instruction; the video encoder is used to encode the control instruction into image data; the image data is transmitted to the instruction receiving server of the subnet through a one-way video transmission line; The instruction receiving server in the subnet is used to receive the image data and decode the image data into the control instruction, and transmit the image data to the client corresponding to the control instruction. The present invention can realize the safe interaction of clients in multiple subnets, the whole interaction process will not change the original network security of each subnet, and avoid the interaction of each subnet due to receiving the same interactive terminal (or control command output unit) resulting in data leakage.
Owner:北京仁光科技有限公司
Data interaction method between different networks
InactiveCN107846354ATo achieve mutual switchingEnable secure interactionsNetwork connectionsInput/output processes for data processingHigh performance computationSoftware design
The invention relates to a data interaction method between different networks. The method comprises the following steps: 1, human engineering design of a design platform; 2, hardware appearance structure design of the design platform, the platform is a of a C-shaped semi-closed structure for the convenient entry and exit of personnel, and meanwhile effectively shielding the noise and external interference factors; 3, the hardware configuration of the platform: a variety of electronic devices are integrated in the platform, mainly comprising three high-performance computers, a KVM, a switch, aportable control terminal, a radio, an IP phone, a short message cat, a keyboard and a mouse; 4, platform software design: ensuring the automatic start of three machine boot software, and a corresponding touch screen system is deployed on the computer 1; and a window switching program is used for collecting a path of video signals on the computer.
Owner:CHINA CHANGFENG SCI TECH IND GROUPCORP
Secret key devices for supporting anonymous authentication, generation method and unlocking method thereof
ActiveCN101958796BBreak through application bottlenecksEnable secure interactionsKey distribution for secure communicationUser identity/authority verificationAnonymous authenticationComputer science
The invention provides identification authentication-based technology, and relates to secret key devices for supporting anonymous authentication. Identification secret keys generated by anonymous identifiers are stored in the secret key devices. The generation method of the secret key devices for supporting the anonymous authentication comprises the following steps of: defining and generating at least one anonymous identifier; defining a seed secret key pair, wherein the seed secret key pair consists of a seed public key and a seed private key; allowing the anonymous identifiers to generate identification private keys corresponding to the anonymous identifiers respectively through the seed private key; and writing the generated identification private keys into each secret key device. The invention also provides a back-up unlocking method of the dual secret key devices. The devices and the method can support requirements of social and publics on anonymous safety service, and reduce the application threshold of the authentication technology greatly.
Owner:北京联合智华微电子科技有限公司
Identity authentication method, device and system
ActiveCN106656481BImplement identity authenticationMaintain securityKey distribution for secure communicationComputer terminalEncryption
The invention brings forward an identity authentication method, apparatus and system. The identity authentication method comprises the following steps: an intelligent terminal generating a first randomized number and generating a terminal public key and terminal private key which form a pair; the intelligent terminal encrypting the first randomized number by use of a prestored cloud public key so as to obtain first encryption data; the intelligent terminal sending the first encryption data and the terminal public key to a cloud server; the intelligent terminal receiving second encryption data sent by the cloud server and decrypting the second encryption data by use of the terminal private key; and if a decryption result comprises the first randomized number, the intelligent terminal confirming that the cloud server succeeds in identity authentication. The identity authentication method simplifies operation steps, reduces operation resources, at the same time, maintains more secure data channels, promotes development of Internet of things and improves user experience.
Owner:MIDEA SMART TECH CO LTD +1
Communication mechanism and method of using same to implement safety guidance for windows embedded system
ActiveCN108536641AEnsure safe interactionHighlight substantive featuresMultiple digital computer combinationsPlatform integrity maintainancePersonal computerComputer terminal
The invention provides a communication mechanism and a method of using the same to implement safety guidance for a windows embedded system. A mobile terminal serves as a storage device shared storageregion; when a first application detects first communication information present in a first hidden sector of the mobile terminal, second communication information is written into the second hidden sector of the mobile terminal; when a personal computer detects, through a second application, the second communication information present in the second hidden sector of the mobile terminal, corresponding processing is performed according to the type of the second communication information. The communication mechanism and the method implement communication information interaction between a personalcomputer and a mobile terminal; the communication mechanism can be used to implement safety guidance and communication information interaction for an operating system through the mobile terminal whenthe personal computer has no operating system.
Owner:ZHENGZHOU XINDA JIEAN INFORMATION TECH
A secure interactive system
ActiveCN110830744BEnable secure interactionsDoes not change network securitySelective content distributionElectrical cable transmission adaptationComputer hardwareInteraction systems
The invention discloses a security interaction system, comprising: a control instruction output unit, a video encoder, and at least two clients; the control instruction output unit is used to output control instructions; the video encoder is used to convert the control instruction Instructions are encoded into image data; the image data is transmitted to each client through a one-way video transmission line; the client is used to receive the image data and decode the image data into the control instruction. Through the above-mentioned embodiments of the present invention, secure interaction to multiple clients can be realized, and the entire interaction process will not change the original network security of each client, avoiding that each client receives the same interaction terminal (or control instruction output unit) ) The problem of data leakage on the network or between clients caused by the interaction.
Owner:北京仁光科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com