Method for safely transmitting data between wireless ad hoc networks
A wireless ad-hoc network and data security technology, applied in digital transmission systems, security devices, transmission systems, etc., can solve problems such as high complexity, legal node defection, and data packet loss, so as to prevent data tampering and facilitate Realize and apply a wide range of effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
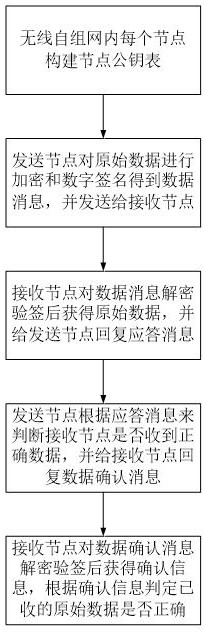
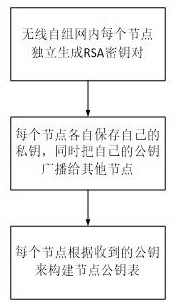
[0055] A method for secure data transmission between wireless ad hoc networks according to the present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments:
[0056] First of all, it should be explained that the precondition of the method for secure data transmission between ad hoc networks in the present invention is that the ad hoc network has been successfully established, and all nodes in the ad hoc network have realized interconnection.
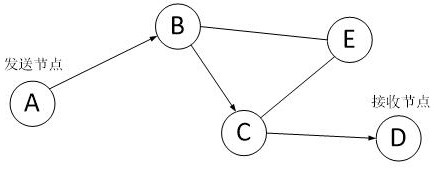
[0057] Such as figure 1 As shown, there are five online nodes in the wireless ad hoc network. Assume that node A is the sending node and node D is the receiving node. Node A needs to send the collected data to node D. According to the network topology diagram of the wireless ad hoc network, it can be seen Out, the data passes through node B, node C, and finally reaches node D. Then the data may be lost due to signal interference or network congestion when it is transm...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com