Security interaction system and method, electronic equipment and storage medium
An interactive system and interactive method technology, applied in the field of electronic equipment, storage media, and secure interactive systems, can solve the problems that users cannot change and participate freely, and the amount of information is limited, so as to achieve the effect of unlimited interaction time and information.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
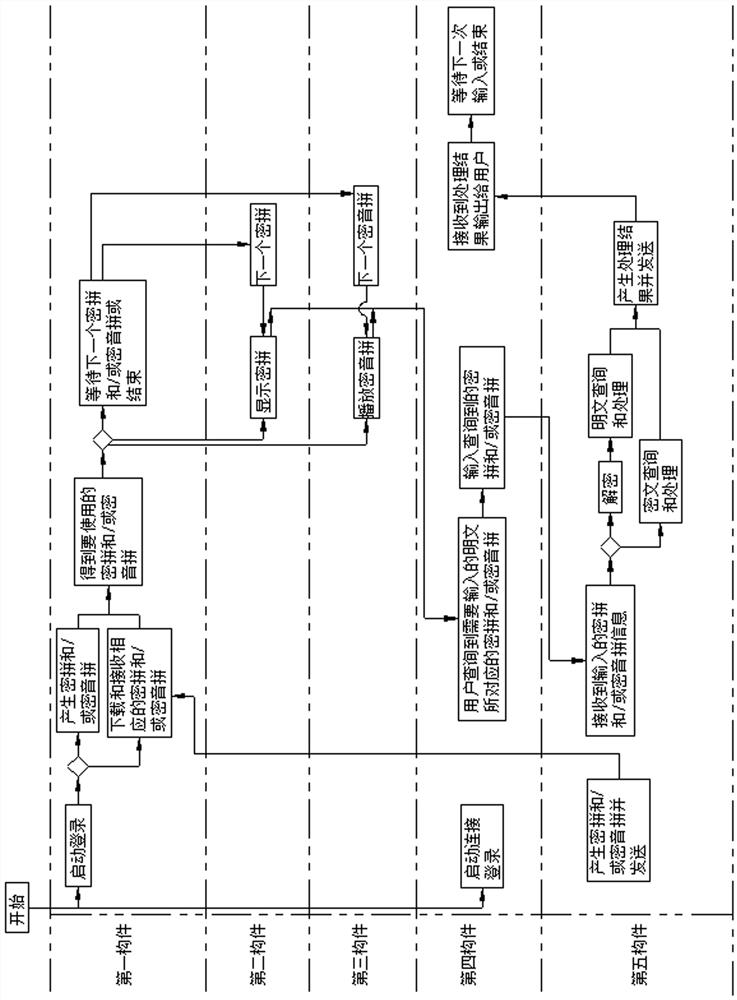
[0066] Please refer to figure 1 As shown, the first embodiment of the security interaction method of the present invention, taking the human-computer security interaction system of the telephone as an example, includes the following steps:
[0067] Step 11. After the user or administrator starts the first component at the same time or successively and logs in, picks up the phone of the fourth component and dials and connects to the telephone service of the fifth component, this time is generated in the first component or the fifth component. Mipin and / or Miyin for human-computer interaction, if Mipin and / or Miyin are generated by the fifth component, the first component downloads or receives the corresponding Mipin and / or Miyin from the fifth component Pin, the first component gets the Mi Pin and / or Mi Yin Pin to be used.
[0068] Step 12: The first component outputs the Mipin to be used this time to the second component, or outputs the Miyin Pin to be used this time to the t...
Embodiment 2
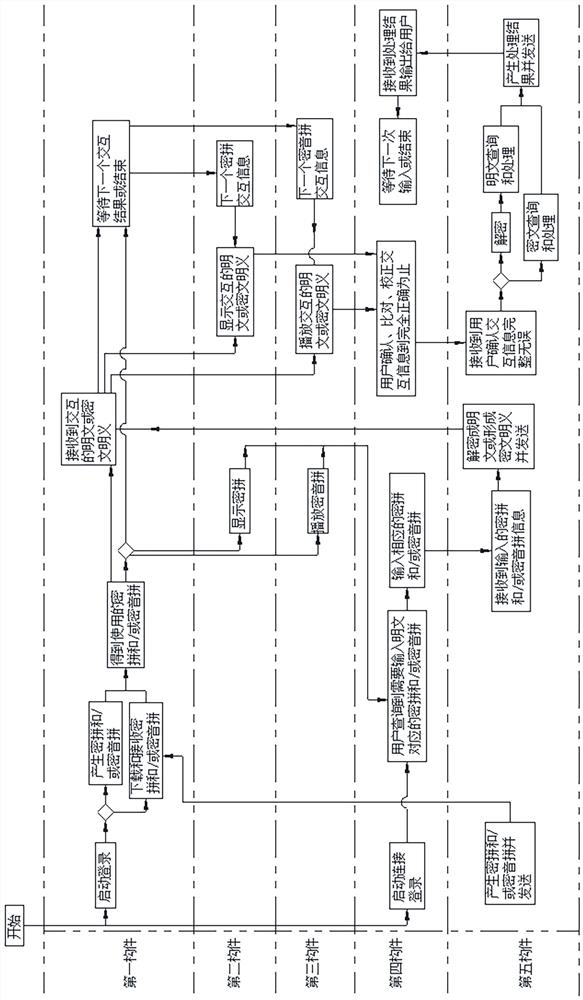
[0075] Please refer to figure 2 As shown, the second embodiment of the security interaction method of the present invention, taking the security interaction system of the ATM machine as an example, includes the following steps:
[0076] Step 21. The user or administrator starts the first component at the same time or successively and logs in. After the ATM machine of the fourth component is connected to the ATM machine service of the fifth component, the human-computer interaction is generated in the first component or the fifth component. Mi Pin and / or Mi Yin Pin, if Mi Pin and / or Mi Yin Pin are generated by the fifth component, the first component downloads or receives the corresponding Mi Pin and / or Mi Yin Pin from the fifth component, the first The component gets the Mipin and / or Miyin to use.
[0077] Step 22: The first component outputs the cipher to be used this time to the second component, or outputs the cipher to be used this time to the third component.
[0078] ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com