Method and terminal for provision and loading of executable module
A technology of execution module and target end, which is applied in the direction of instrumentation, calculation, electrical digital data processing, etc., and can solve problems such as kernel security issues
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
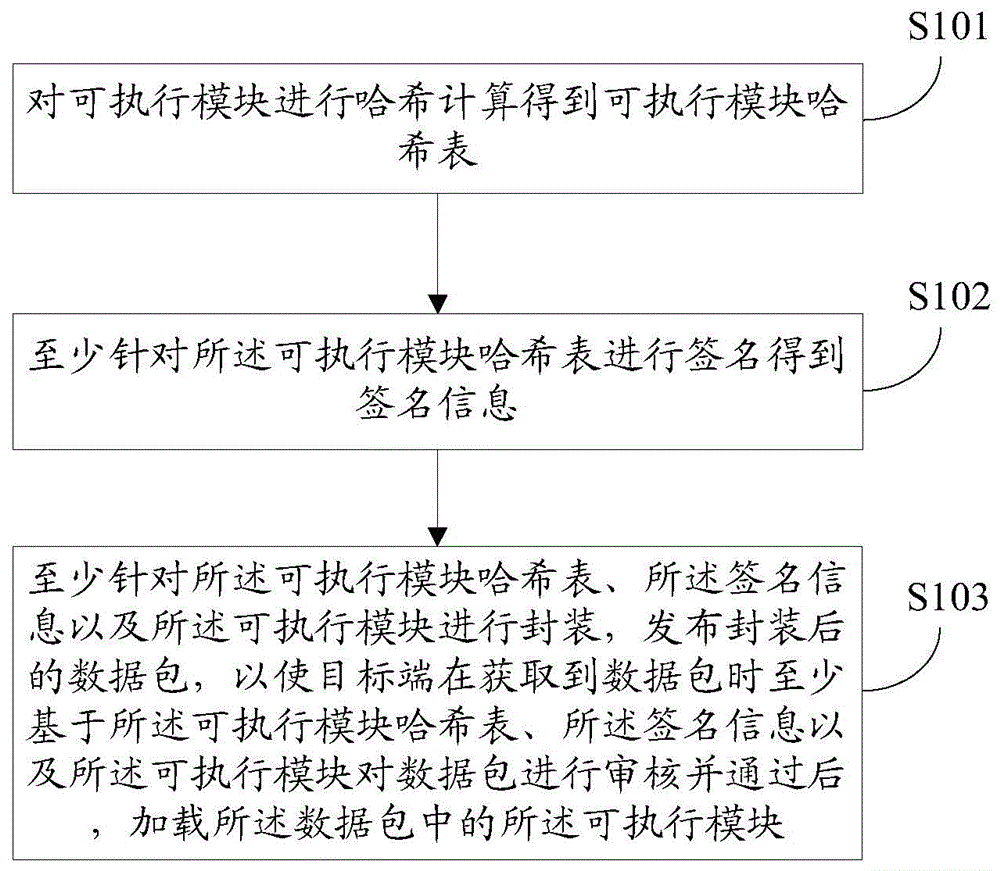
[0057] In the first embodiment of the present invention, a method for providing an executable module, such as figure 1 As shown, the process executed on the host side includes the following specific steps:
[0058] Step S101, perform hash calculation on the executable module to obtain the executable module hash table.
[0059] Specifically, as is well known in the art, hash calculation is performed on binary values of program modules or files to obtain a hash table.
[0060] Step S102, signing at least the hash table of the executable module to obtain signature information.
[0061] Specifically, the format of the signature information includes the following two sections: a signature section and an authentication section.
[0062]Step S103, encapsulating at least the executable module hash table, the signature information, and the executable module, and publishing the encapsulated data package, so that the target end obtains the data package based on at least the executabl...
no. 2 example
[0067] The second embodiment of the present invention is a method for providing an executable module. The method described in this embodiment is substantially the same as that in the first embodiment, except that the component part of the data packet further includes: a segment table. The hash table segment also includes: segment table hash table, and / or, hash table segment hash table. And, the signature information in step S102 of this embodiment is also somewhat different.
[0068] Specifically, in this embodiment, the components of the packet include the following sections: packet header, segment table, hash table segment, and executable module segment, which are similar to the ELF format; wherein, the segment table includes: hash Hash table segment header and executable module segment header, the content of the hash table segment header is the offset of the hash table segment relative to the starting position of the data packet, and the content of the executable module seg...
no. 3 example
[0073] The third embodiment of the present invention corresponds to the method for providing an executable module run by the host terminal in the first embodiment. This embodiment introduces a method for loading an executable module, such as figure 2 As shown, the processes performed on the target side include:
[0074] Step S301, acquiring data packets.
[0075] Specifically, the components of the obtained data packet include the following sections: data packet header, hash table segment and executable module segment, wherein, the total file size of the data packet, the hash table segment header and the executable module segment are placed in the data packet header. Module segment header, the content of the hash table segment header is the offset of the hash table segment relative to the starting position of the data packet, and the content of the executable module segment header is the offset of the executable module segment relative to the starting position of the data pac...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com