Security authentication method for realizing multi-cloud management and control across public network
A safety certification and control technology, applied to electrical components, transmission systems, etc., can solve problems such as large financial expenses, and achieve the effects of reduced operation and maintenance costs, high security, and low risk of certificate leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
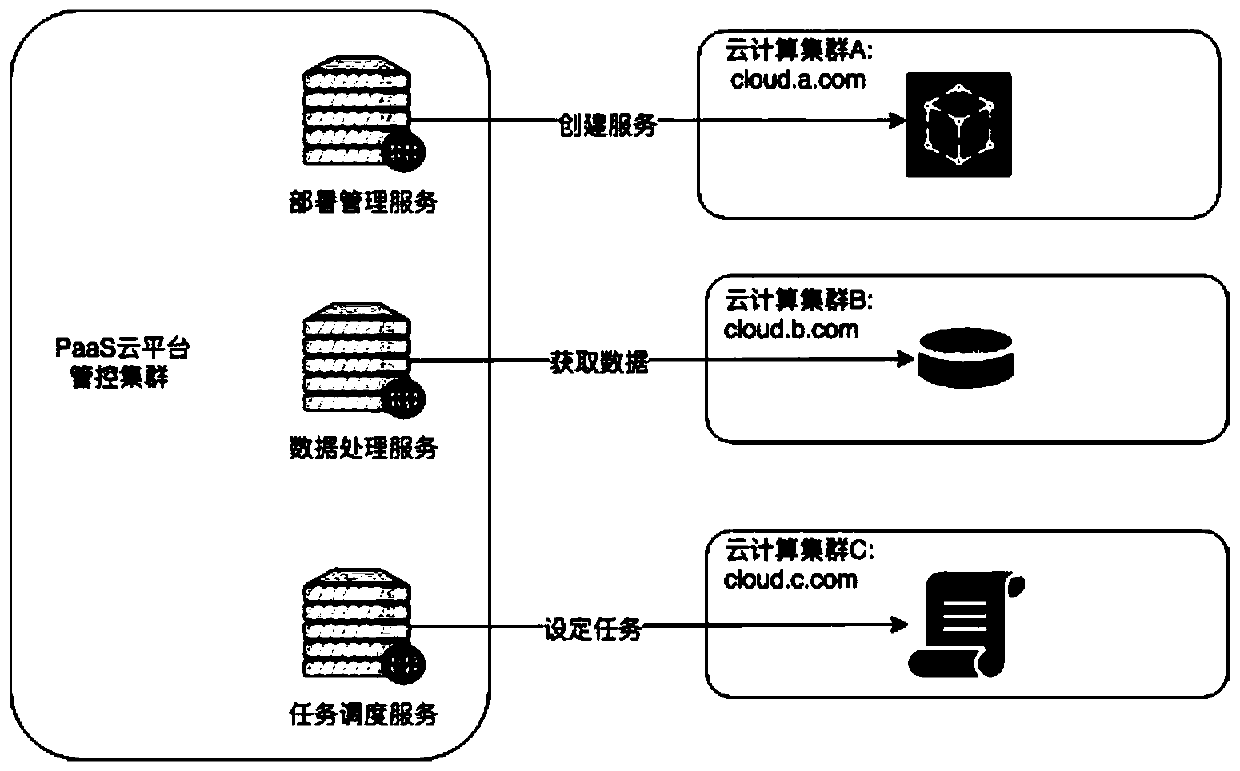
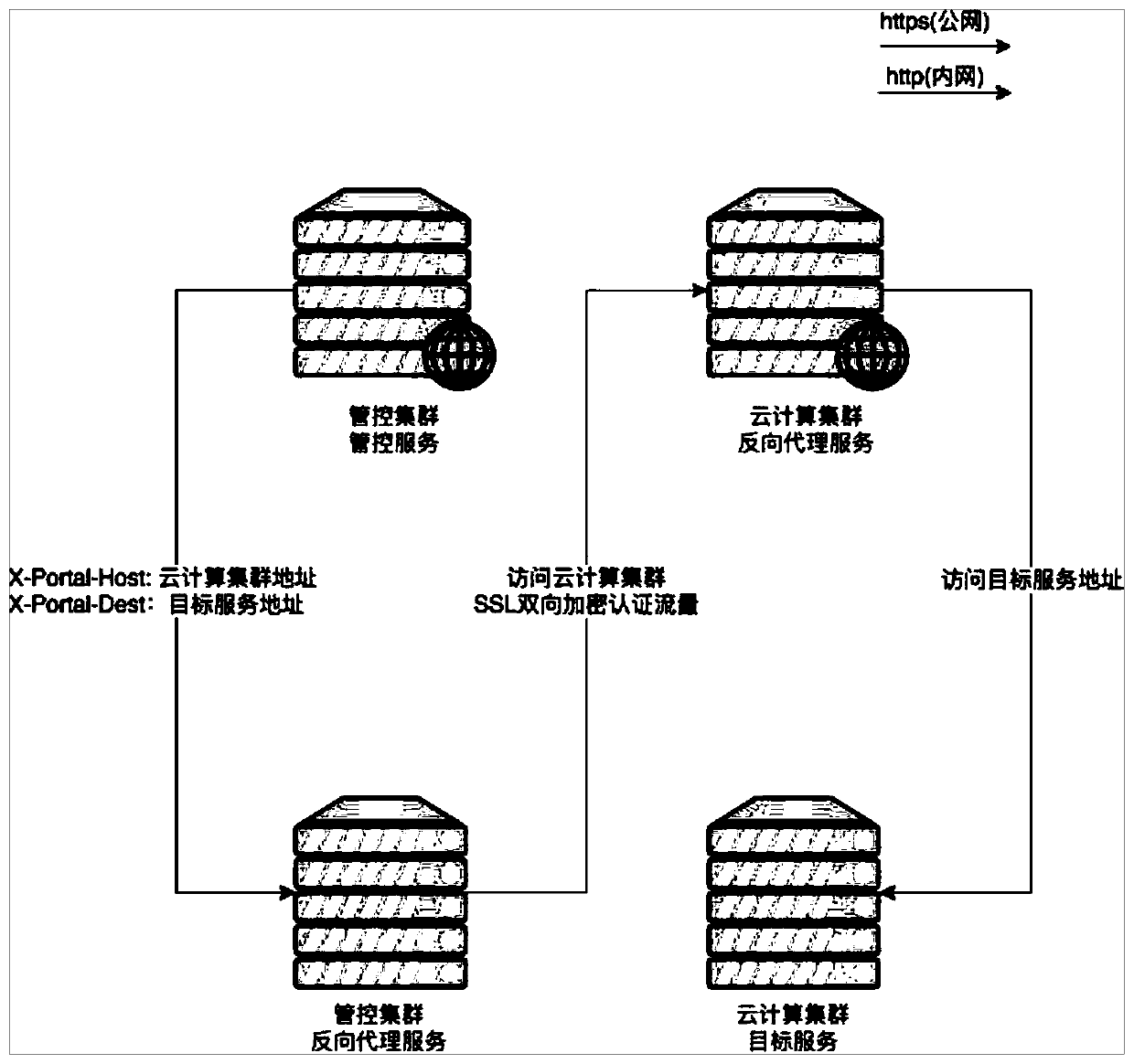
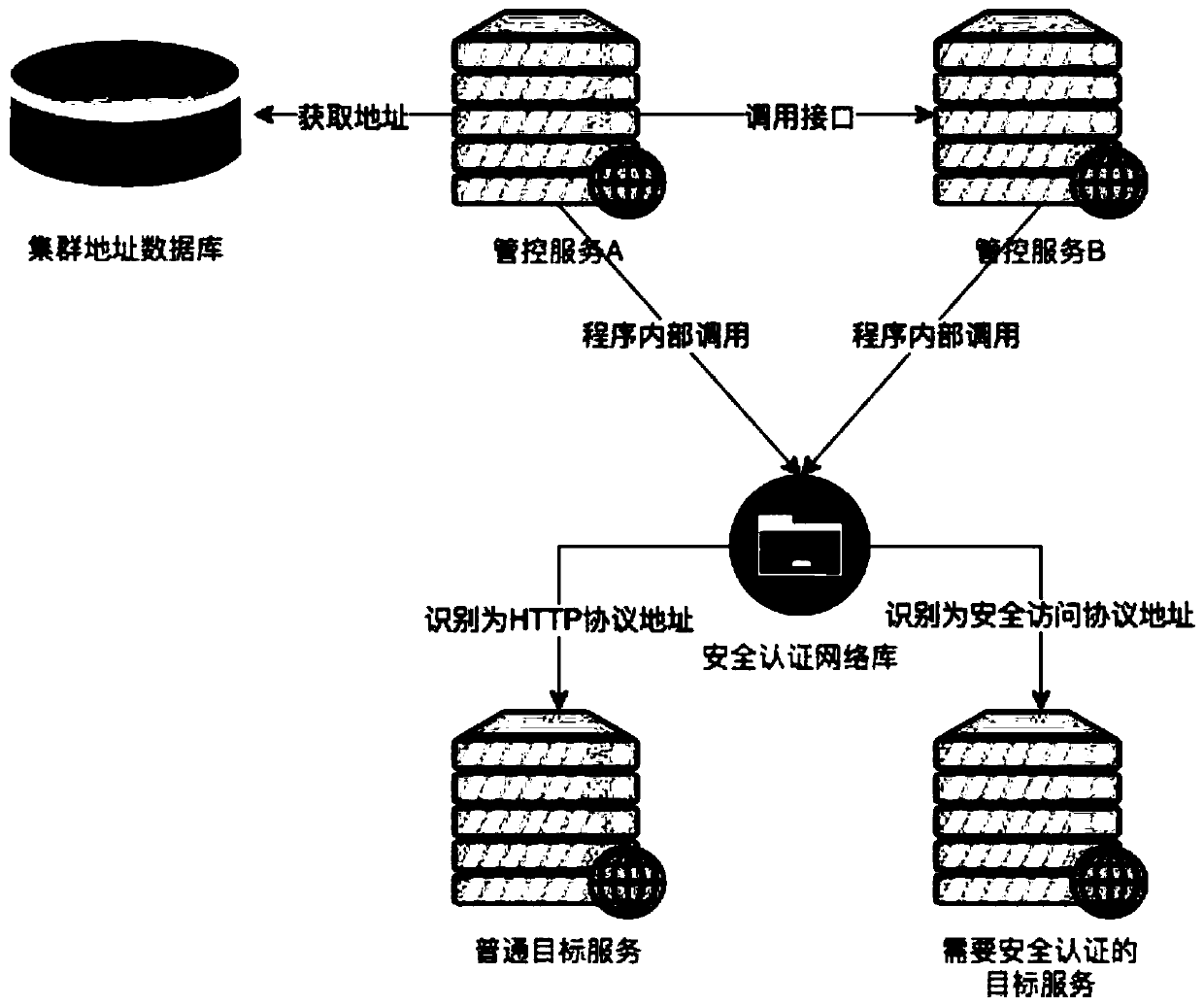
[0024] like figure 2 As shown, the present invention comprises management and control cluster and cloud computing cluster, is characterized in that, also comprises management and control cluster reverse proxy service and cloud computing cluster reverse proxy service, reverse server can be Nginx; Concrete steps include:
[0025] S1. Build a two-way authentication network channel between the network edge of the managed cluster and the network edge of the managed cloud computing cluster through a group of reverse proxy servers;
[0026] S2. In the management and control cluster, the management and control service directly uses the HTTP protocol on the intranet to access the reverse proxy service;
[0027] S3. After receiving the request, the reverse proxy server in the management and control cluster uses the self-signed SSL client certificate to access the reverse proxy server of the cloud computing cluster through the HTTPS protocol public network to complete the authentication...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com