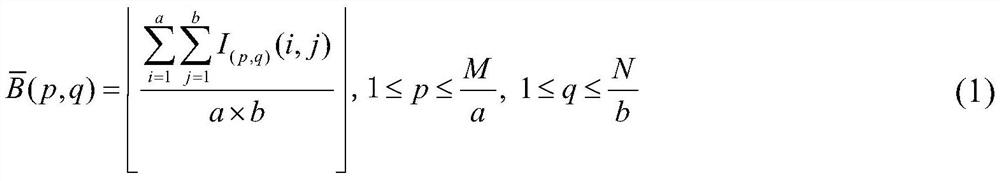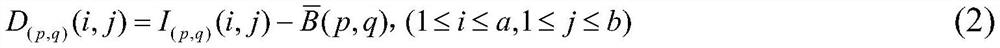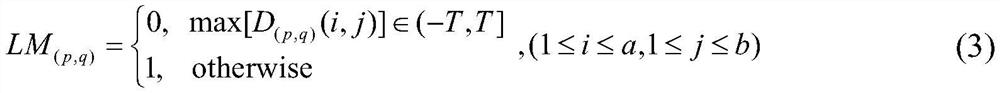Separable ciphertext domain reversible data hiding method
A technology of data hiding and secret data, applied in the field of information hiding, which can solve the problems of large decryption distortion and insufficient guarantee of reversibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0067] Now in conjunction with embodiment the present invention will be further described:
[0068] Select Matlab as the software platform, and program to realize the design of the scheme of the present invention. The implementation process selects the 512×512 standard test image “Lena” as the carrier image, assuming the threshold T=8.
[0069] The specific operation steps are:
[0070] Ⅰ. The owner of the content preprocesses the carrier image to make room for hiding secret data, which specifically includes the following steps:
[0071] The first step is to read in a carrier image I with a size of 512×512;
[0072] In the second step, the carrier image is divided into non-overlapping blocks of 2×2 size, and the average value of each block is calculated, such as: but
[0073] The third step is to calculate the difference between each pixel in the current block and the average value of the block, for the first block: such as: D (1,1) (1,1)=163-163=0,D (1,1) (1,2)=163...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com