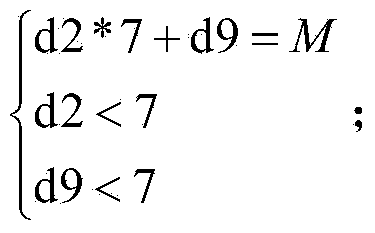Patents
Literature
65results about How to "Ensure secure transmission" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
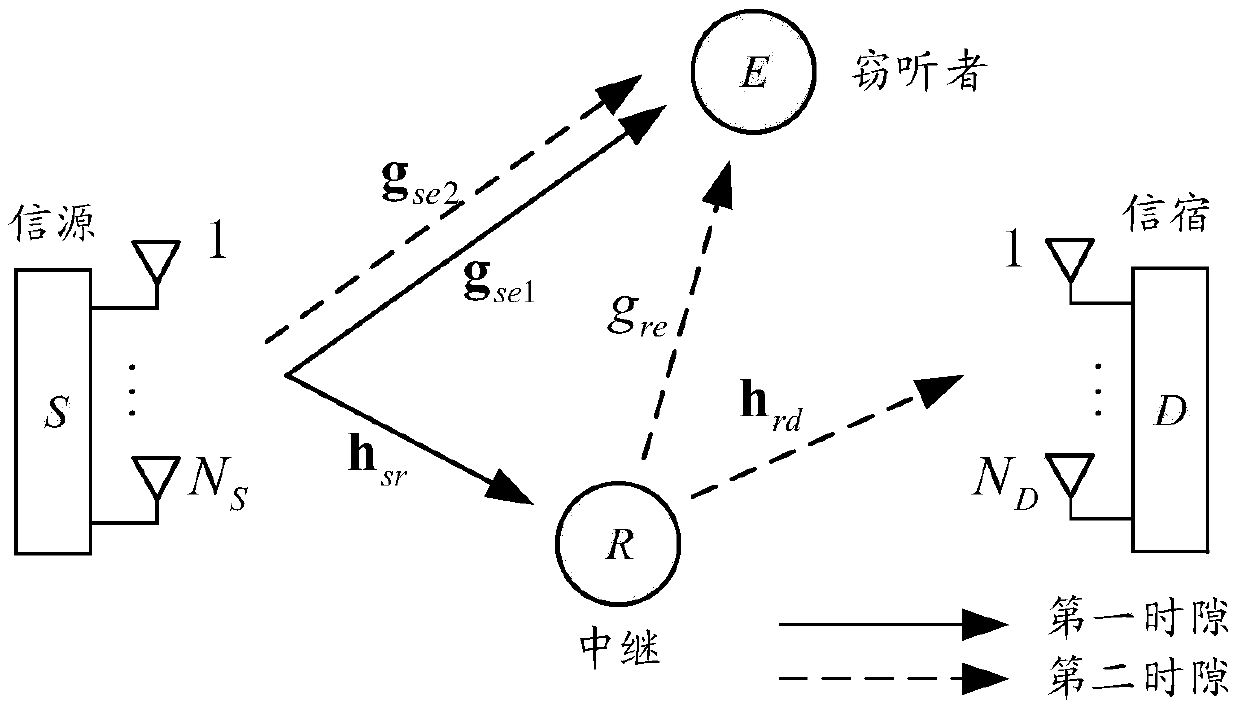
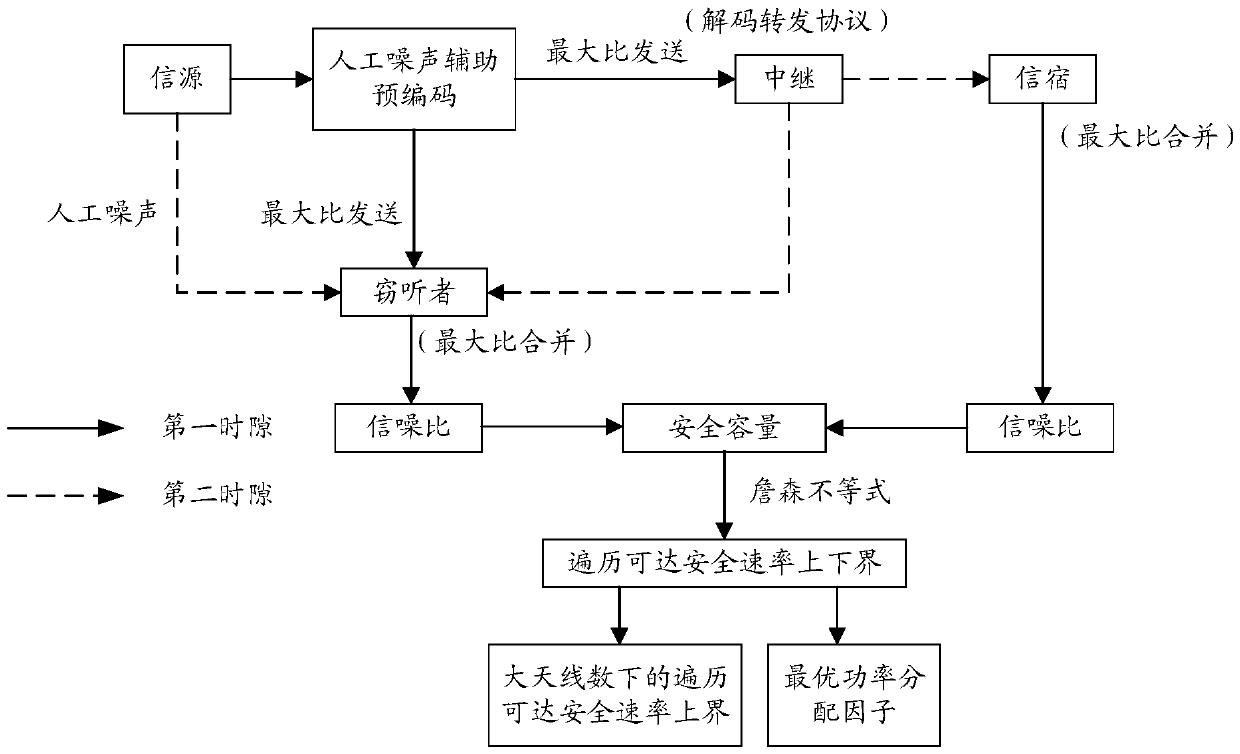
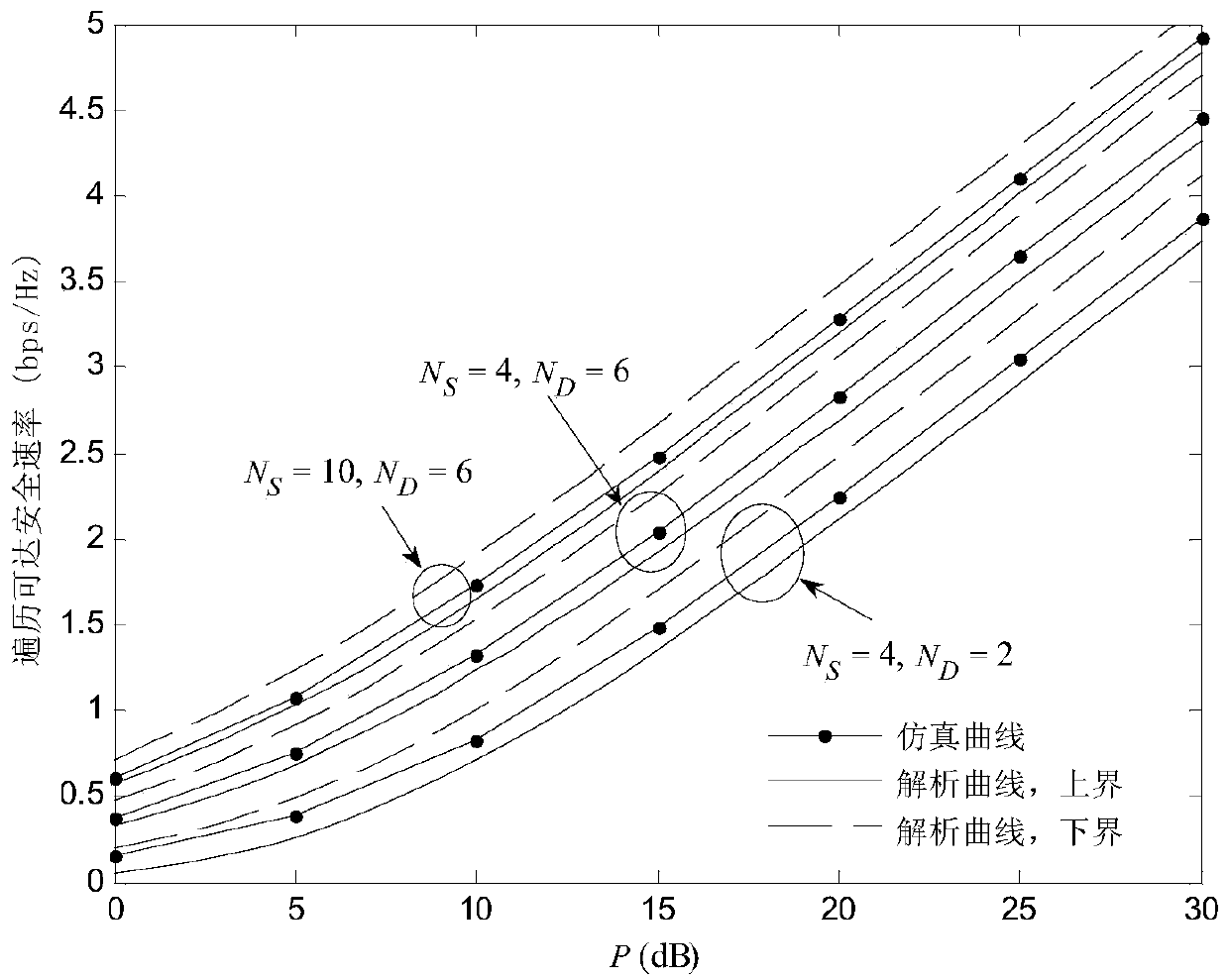
Cooperative relay security transmission method based on artificial noise interference
ActiveCN105515717AEnsure secure transmissionReduce the received signal to interference and noise ratioCommunication jammingSecure transmissionTransfer procedure
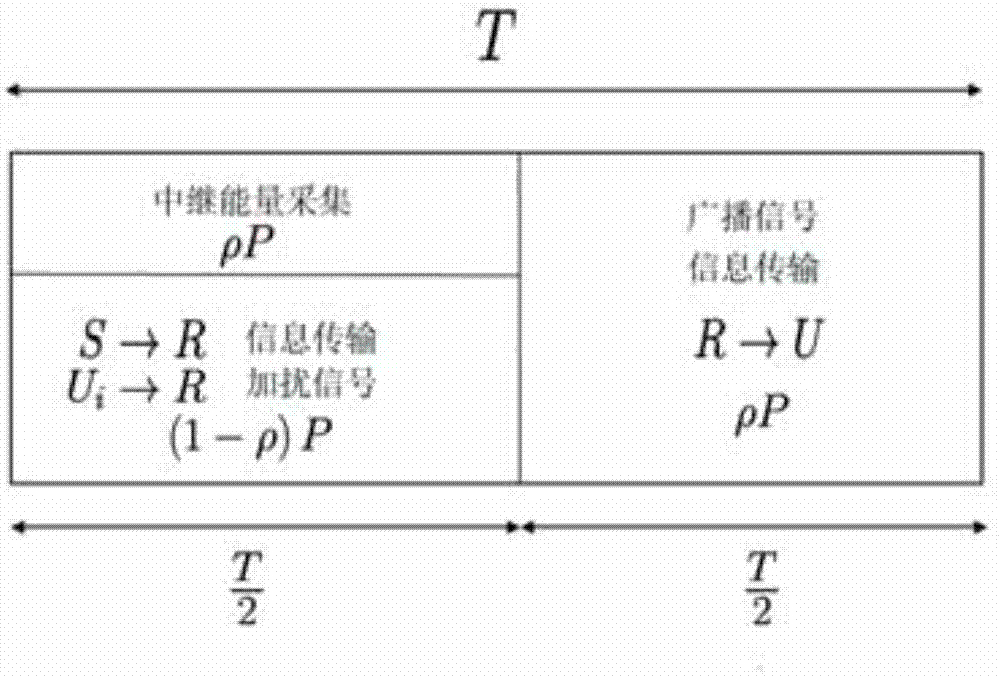
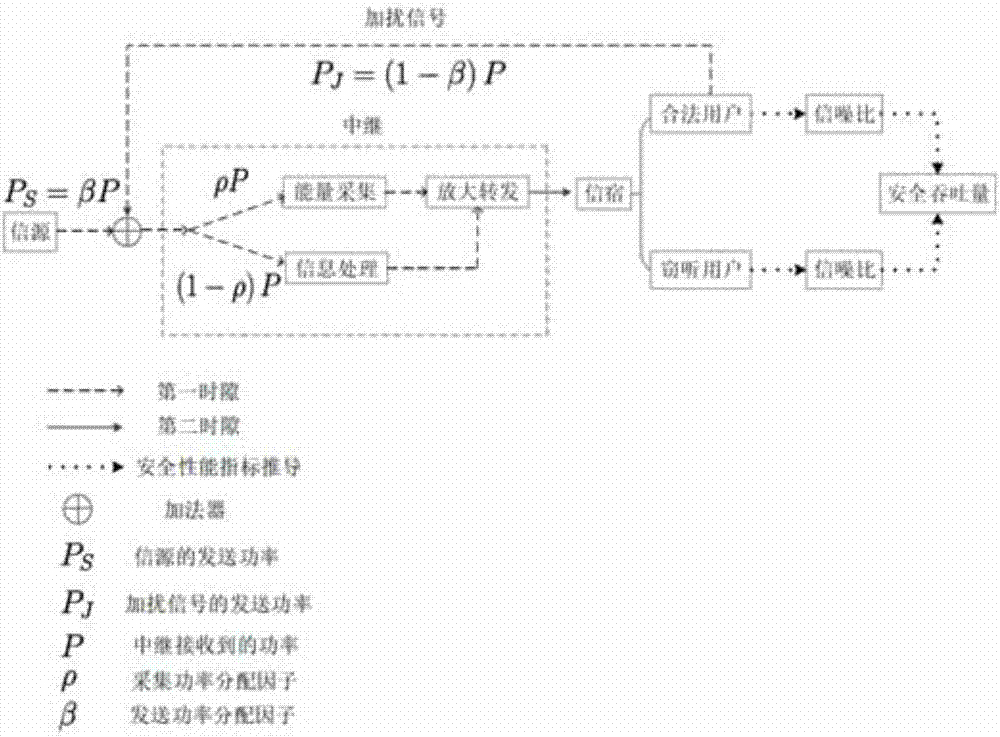
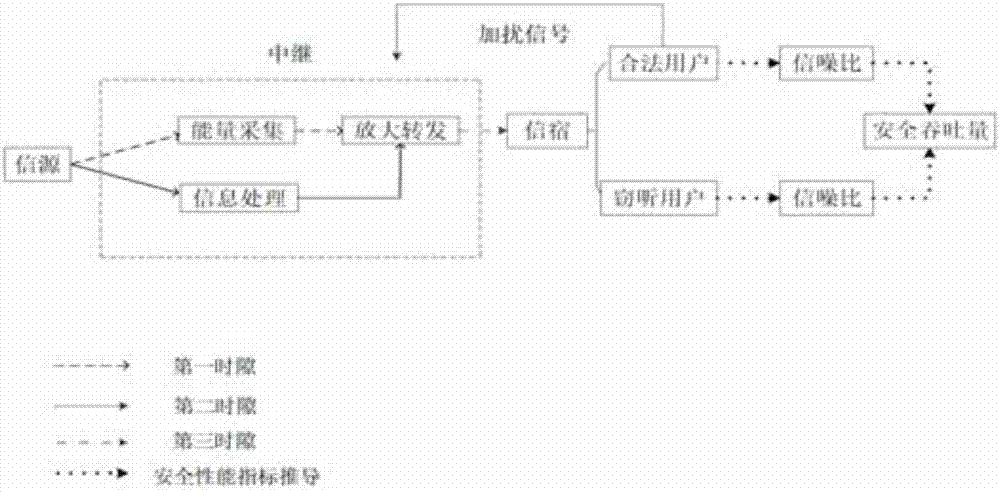
The invention discloses a cooperative relay security transmission method based on artificial noise interference, wherein the whole transmission process is completed in two time slots; in the first time slot, an information source broadcasts available information fused with artificial noise to a relay and an eavesdropper, and before broadcasting, the artificial noise is pre-coded by a null space orthogonal base of a channel from the information source to the relay, and the available information is pre-coded by using a maximal ratio transmission strategy; and in the second time slot, the relay decodes and transmits the received information, and meanwhile the information source sends the artificial noise to interfere the receiving of the eavesdropper. According to the cooperative relay security transmission method based on artificial noise interference, as interferences are implemented in both the two transmission time slots for the eavesdropper, the reception signal-to-interference-and-noise-ratio of the eavesdropper can be effectively reduced, thereby the system security performance is enhanced, and the security transmission of the information is ensured; in addition, in order to improve the use ratio of the system power, the power can be set through working out the optimal power distribution factor of the system, and thereby the optimal system security performance can be achieved with the lowest power consumption.
Owner:HUAQIAO UNIVERSITY
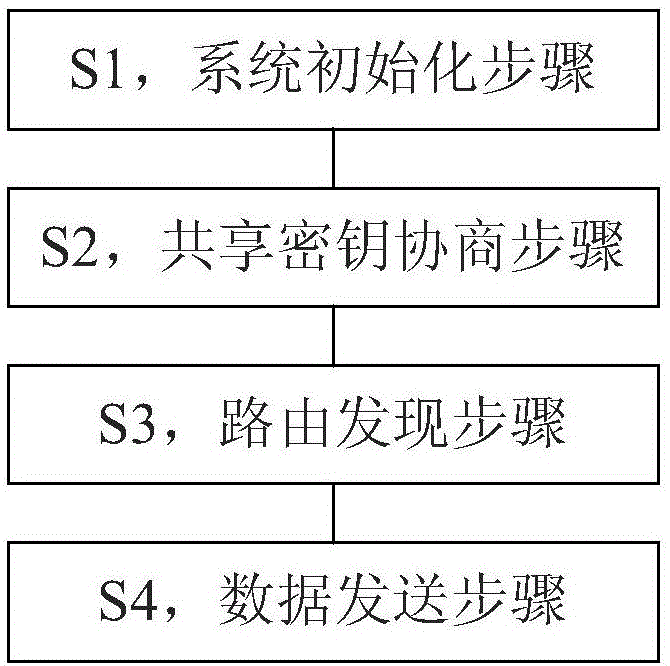
Anonymous safety communication method applicable to MANET (mobile ad-hoc network) network layer
InactiveCN106453428AProtect Identity Information SecurityProtection securityTransmissionSecurity arrangementMaster keyData transmission
The invention provides an anonymous safety communication method applicable to an MANET (mobile ad-hoc network) network layer. The anonymous safety communication method includes a system initializing step, a shared-key negotiation step, a route discovery step and a data sending step. In the system initializing step, a PKG (private key generator) generates a master key and network public parameters, the master key is kept by the PKG, and the network public parameters are published to all nodes in a network; the PKG generates a public key and a private key both corresponding to each node according to ID (identification) of each node, publishes the public keys to all the nodes and publishes the private keys to the corresponding nodes. In the shared-key negotiation step, negotiation on a shared key and a communication sequence number between a source node and a target node is achieved according to an IBE (identity-based encryption) protocol, and the shared key is a symmetrical key. In the route discovery step, an anonymous route path between the source node and the target node is established according to the negotiated shared key and the negotiated communication sequence number on the basis of an onion encryption protocol. In the data sending step, data transmission from the source node to the target node along the anonymous route path is achieved by the onion encryption protocol. By the anonymous safety communication method, identity information safety, position information safety and route information safety of the nodes in the network can be protected effectively.
Owner:SHANGHAI INST OF MICROSYSTEM & INFORMATION TECH CHINESE ACAD OF SCI
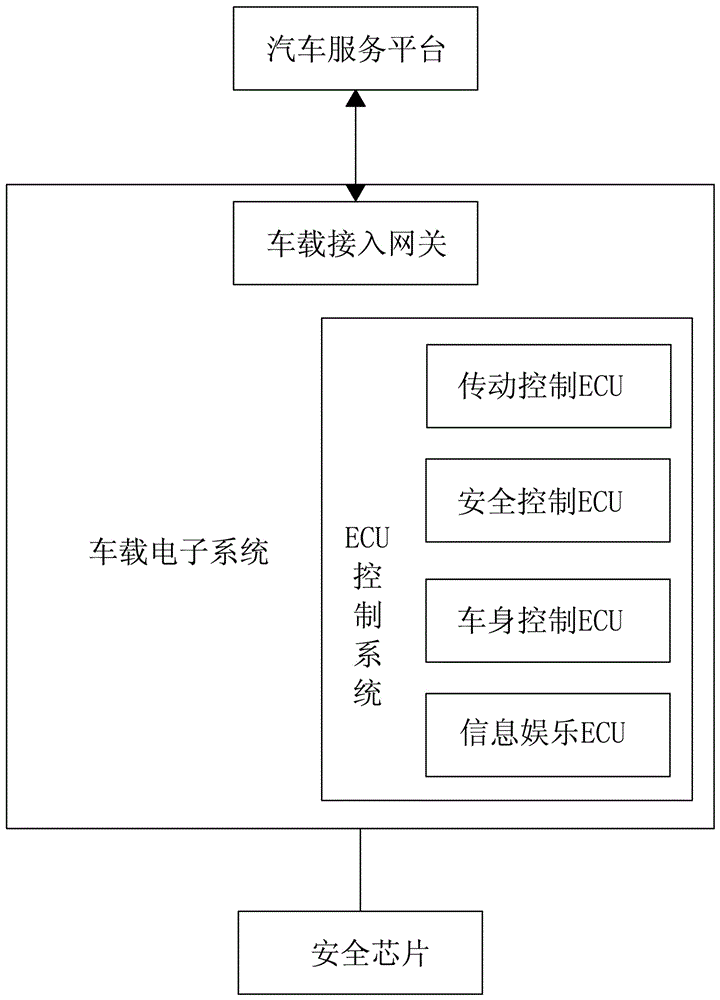
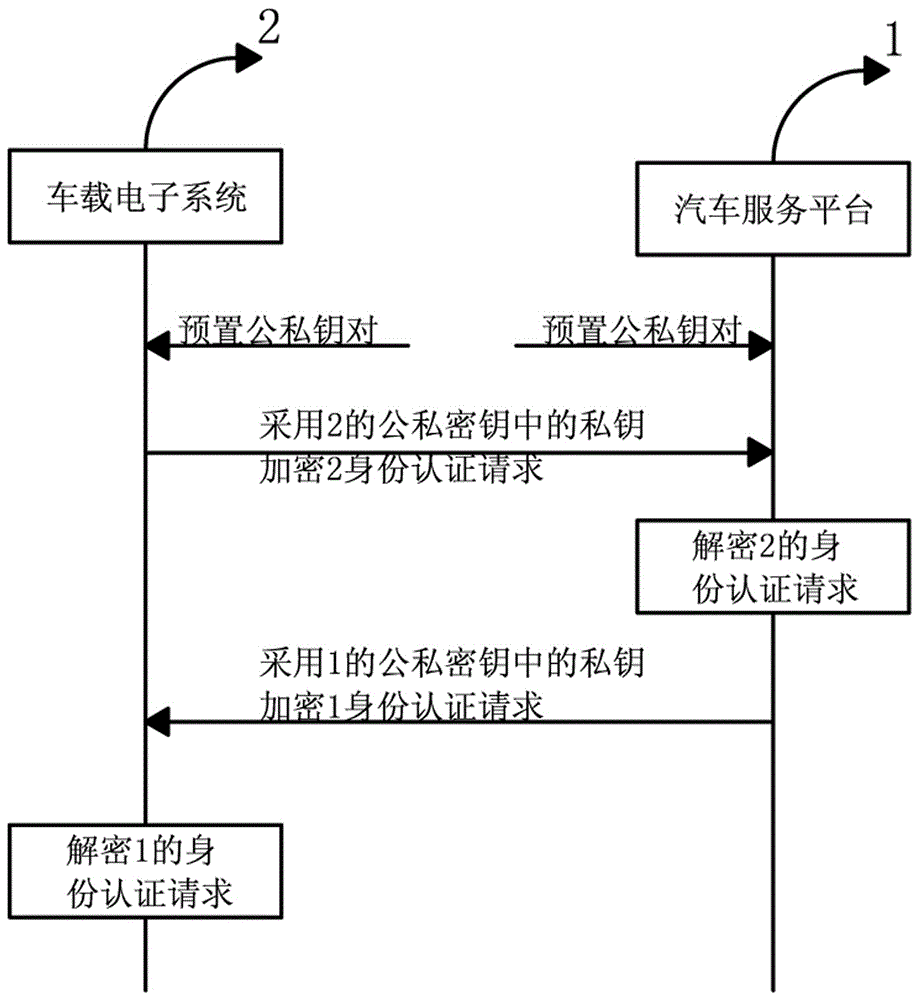
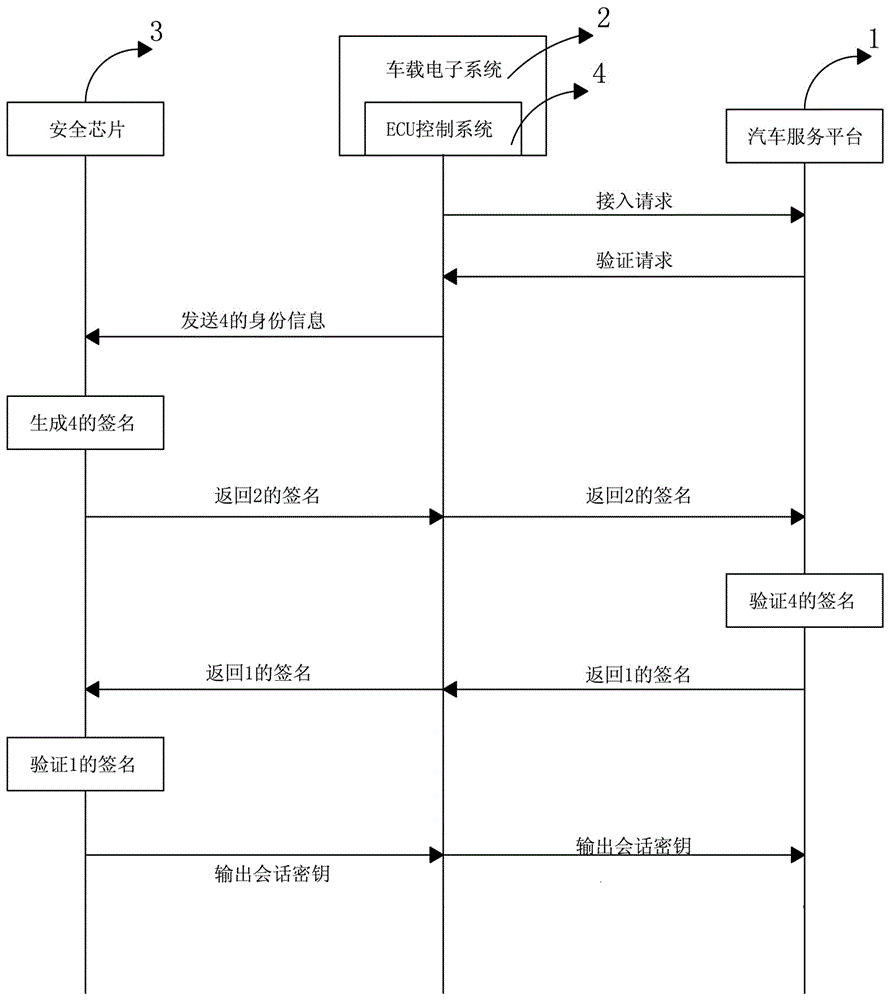
Vehicular electronic secure communication system and communication method
ActiveCN106101111AImprove securityImplement security authenticationTransmissionSecure communication systemEngineering
The invention provides a vehicular electronic secure communication system. The vehicular electronic secure communication system comprises a secure chip, a vehicular electronic system and an automobile service platform; the vehicular electronic system and the automobile service platform perform bidirectional identity authentication; the vehicular electronic system comprises an ECU control system; the ECU control system and the automobile service platform perform bidirectional signature authentication through the secure chip; and, after bidirectional signature is successfully verified, the automobile service platform and the ECU control system are in encrypted communication. The invention further provides a communication method of the vehicular electronic secure communication system. The communication method comprises the following steps that: (1), the vehicular electronic system and the automobile service platform perform bidirectional identity authentication; (2), after verification is successful, the ECU control system of the vehicular electronic system and the automobile service platform perform bidirectional signature authentication through the secure chip; and (3), after verification is successful, the automobile service platform and the ECU control system are in encrypted communication through a session key output by the secure chip.
Owner:ZHENGZHOU XINDA JIEAN INFORMATION TECH
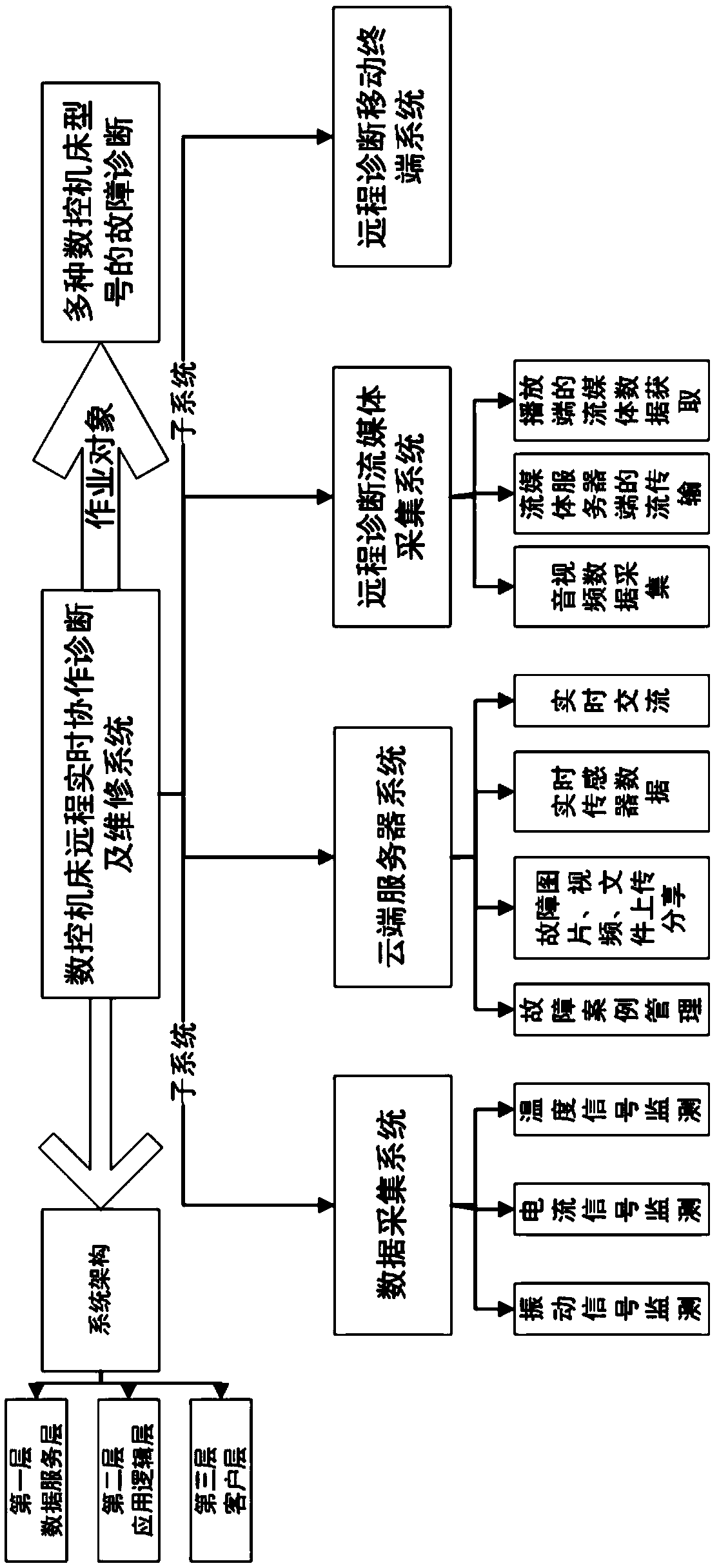
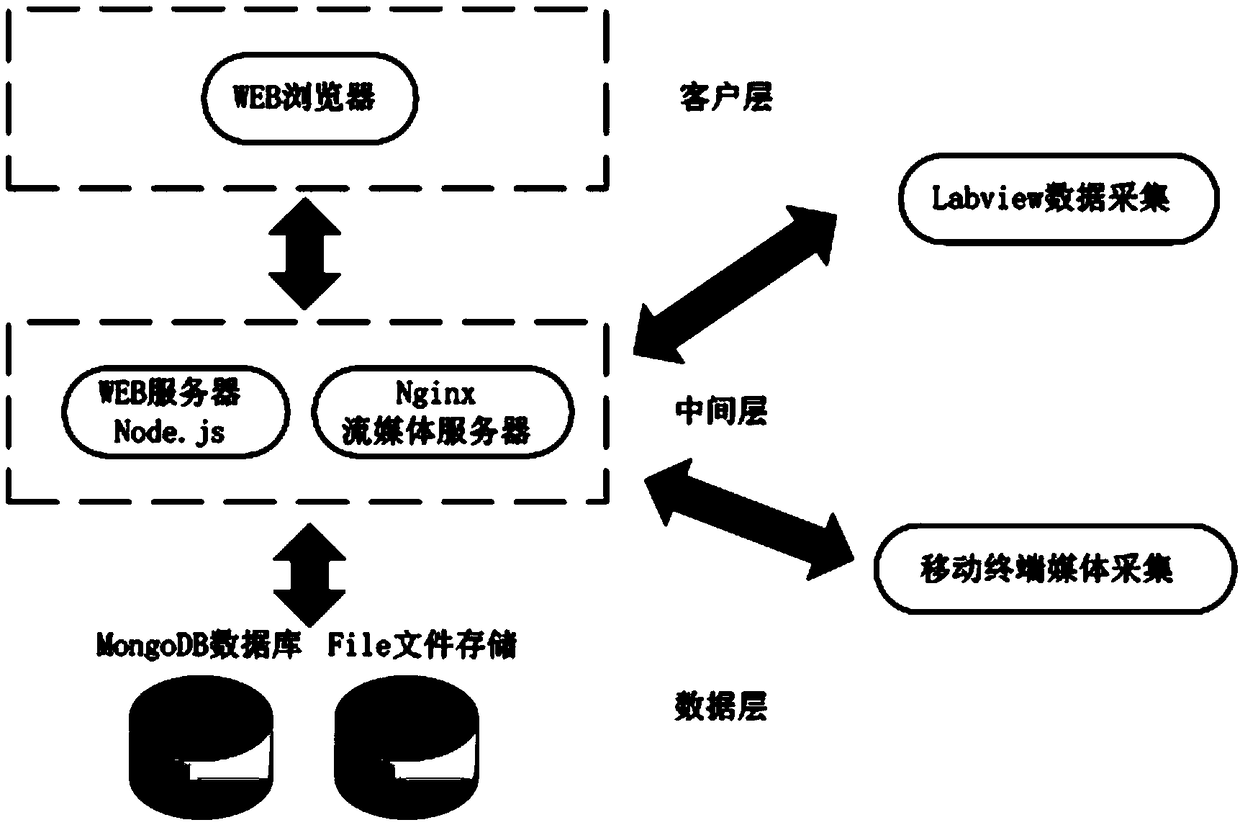
Numerical control machine tool remote real-time cooperation fault diagnosis and maintenance system
The invention relates to a numerical control machine tool remote real-time cooperation fault diagnosis and maintenance system. According to the system, a LabVIEW virtual instrument technology, a Node.js background server technology, a streaming media technology and an iOS mobile terminal technology are utilized to establish a remote fault diagnosis system, data collection, transmission and processing are integrated on one shared platform, the work of a fault diagnosis expert gets rid of limitations of spatial positions and conditions, collected data is sent to a remote cloud server in real time through a network, and then the data is stored and distributed through the cloud server. For real-time cooperation, a cooperation exchange platform is set up, and real-time online text exchange andpicture and file sharing between a field engineer and the remote expert are supported. Meanwhile, mobile equipment is utilized to collect fault field pictures, videos and other multimedia data and send the data to the cloud server during field engineering so that the remote expert can view all types of multimedia data in real time. Besides, the system adopts an HTTPS encryption technology, so thatsecure transmission of the data is guaranteed.
Owner:UNIV OF SHANGHAI FOR SCI & TECH
Secure transmission method adopting information source and relay-combined transmitting antenna selection
ActiveCN105933040ADecrease the receive signal-to-noise ratioImprove the receiving signal-to-noise ratioSite diversitySpatial transmit diversityChannel state informationSignal-to-noise ratio (imaging)
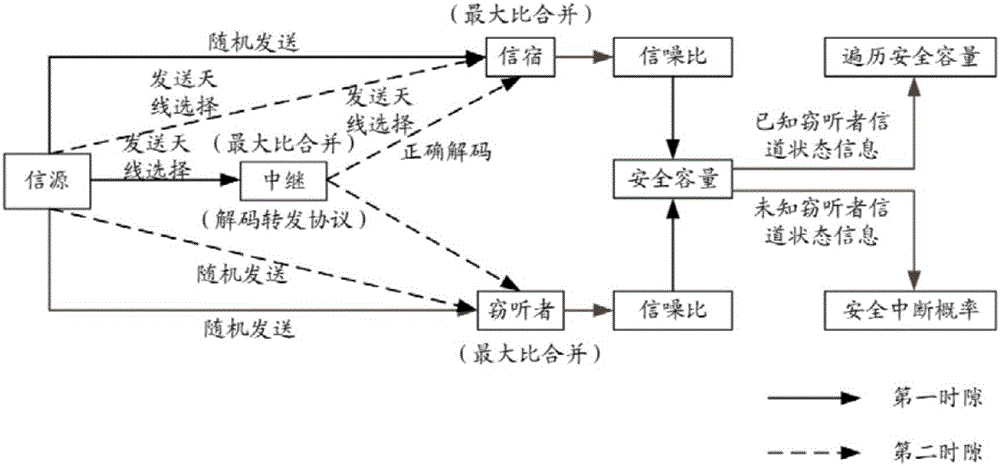
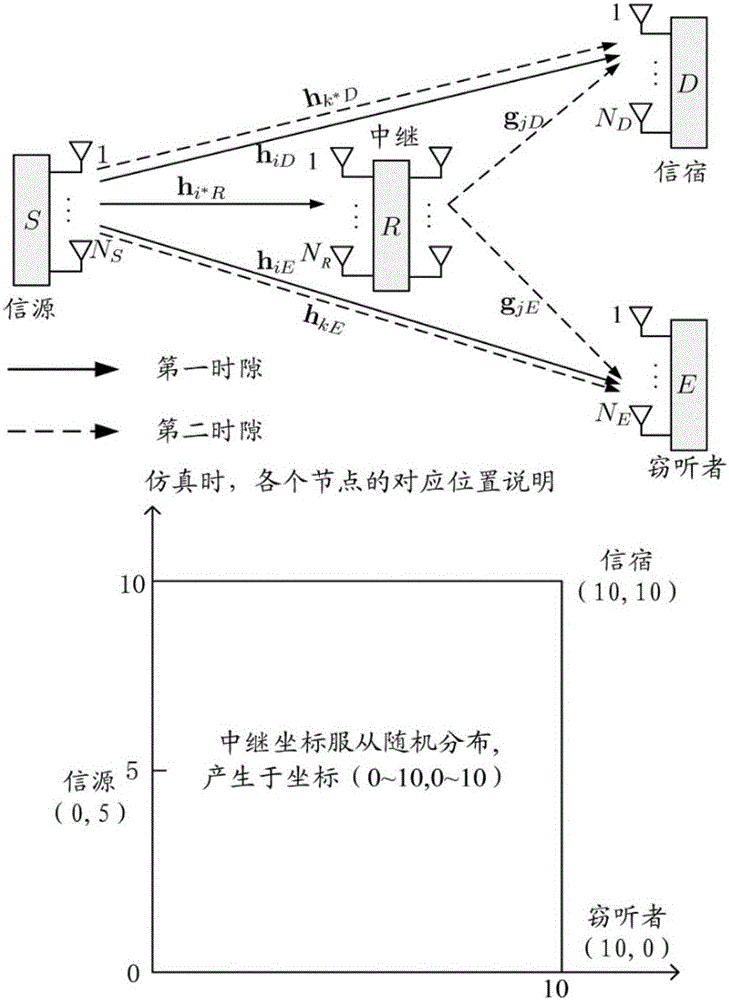
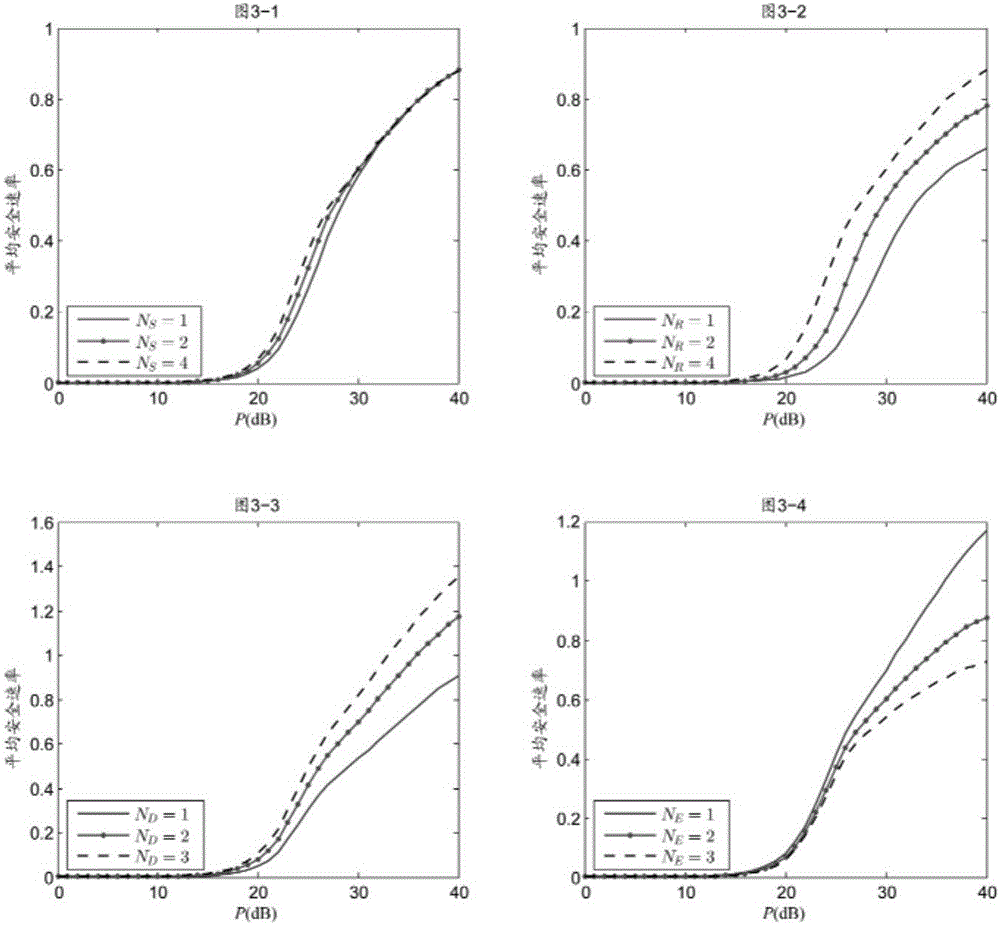
The invention relates to a secure transmission method adopting information source and relay-combined transmitting antenna selection. The method includes the following steps that: in a first time slot, and an information source obtains channel state information from a relay and selects an antenna which makes the received signal to noise of the relay maximum to broadcast confidential signals according to the channel state information, and other three nodes receive signals through adopting maximal-ratio combining; in a second time slot, the relay adaptively decodes a forwarding protocol, when the relay can correctly decode the forwarding protocol, the relay obtains channel state information from an information sink and selects one antenna which makes the received signal to noise of the information sink maximum to forward confidential signals according to the channel state information from the information sink; and when the relay cannot correctly decode the forwarding protocol, the information source obtains the channel state information from the information sink and selects an antenna which makes the received signal to noise of the information sink maximum to retransmit the confidential signals in the first time slot, and the information sink and the relay receive the signals with maximal-ratio combining. According to the method of the invention, transmitting antenna selection technology is adopted to maximize the received signal to noise ratio of the relay or the information sink, and the received signal to noise ratio of an eavesdropper can be decreased, and low complexity and high security can be achieved.
Owner:HUAQIAO UNIVERSITY
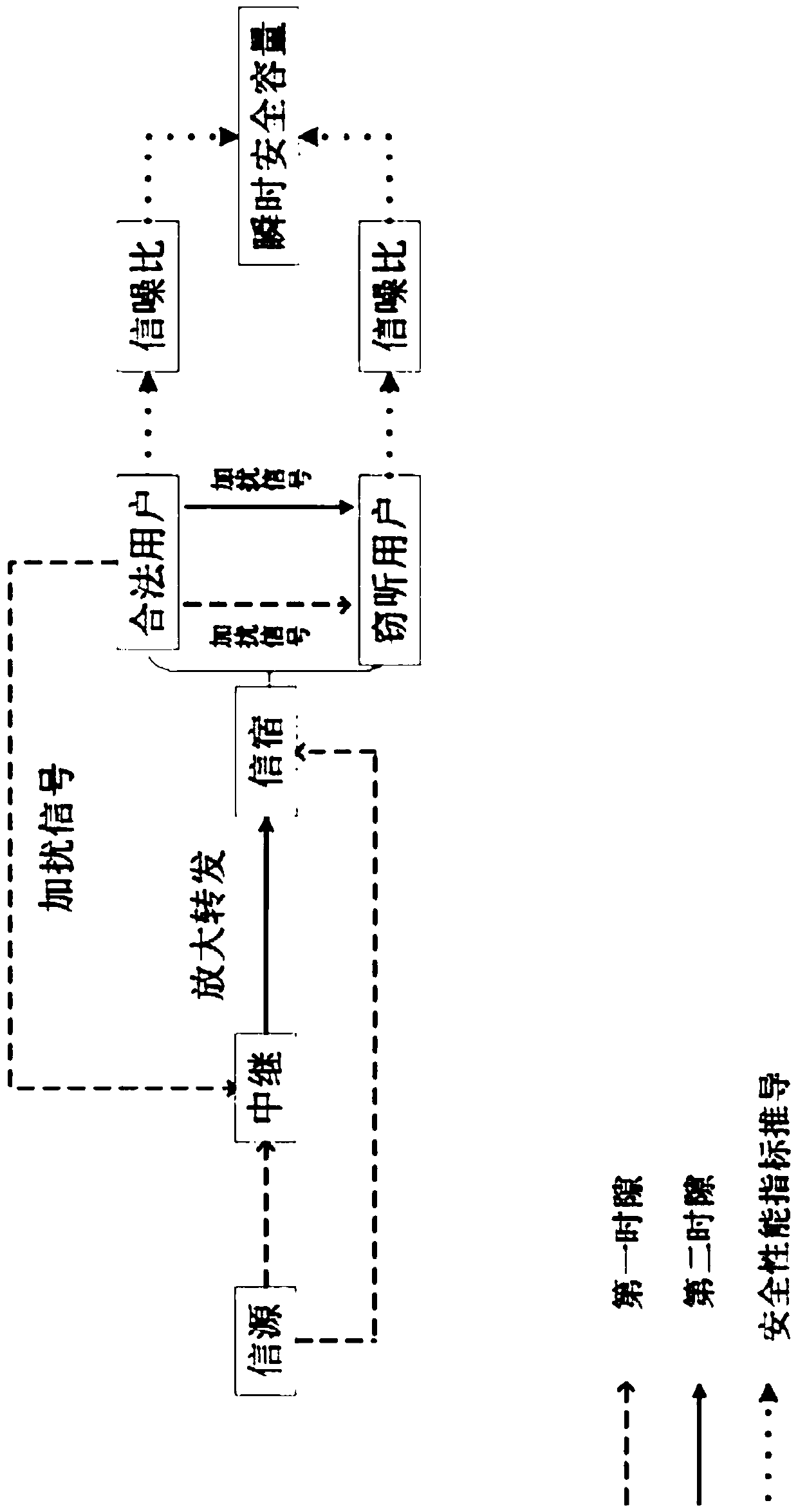
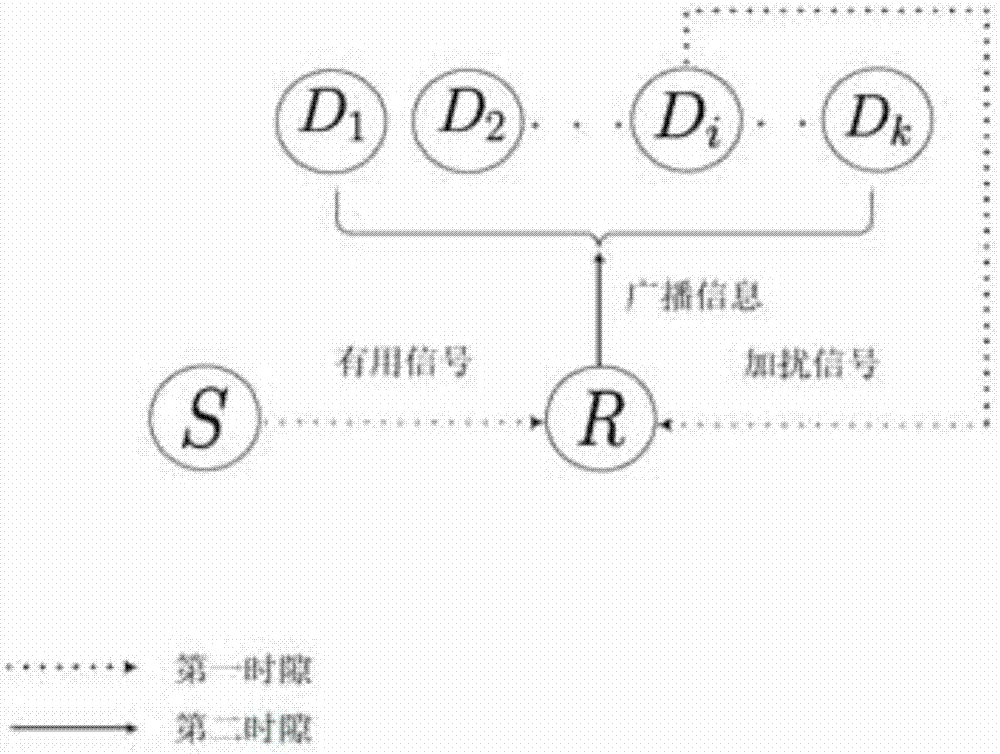
Relay link optimal user selection based collaboration scrambling secure transmission method
ActiveCN108809365AThe signal-to-noise ratio decreases or decreasesImprove securitySite diversityCommunication jammingSignal-to-noise ratio (imaging)Secure transmission
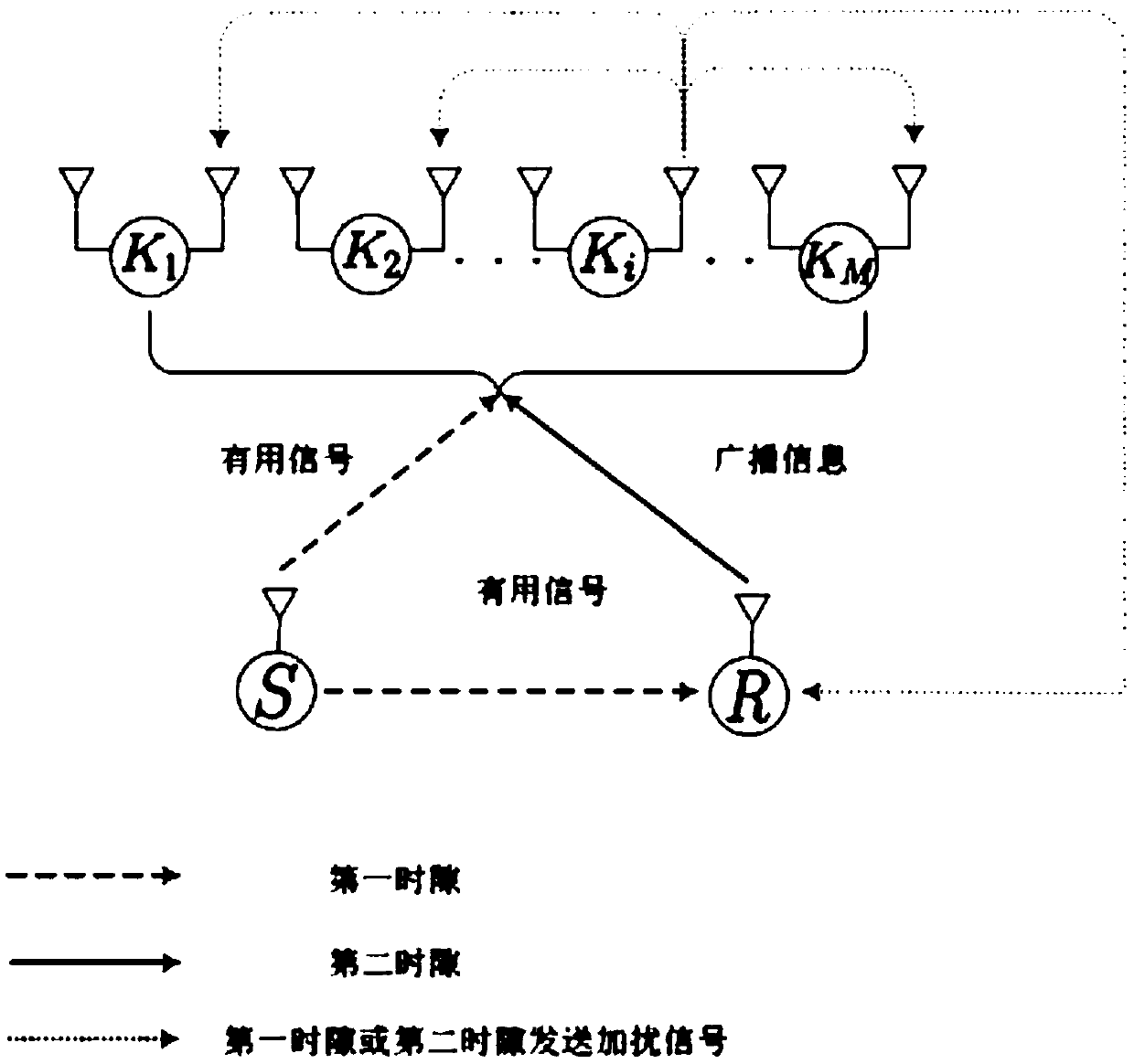
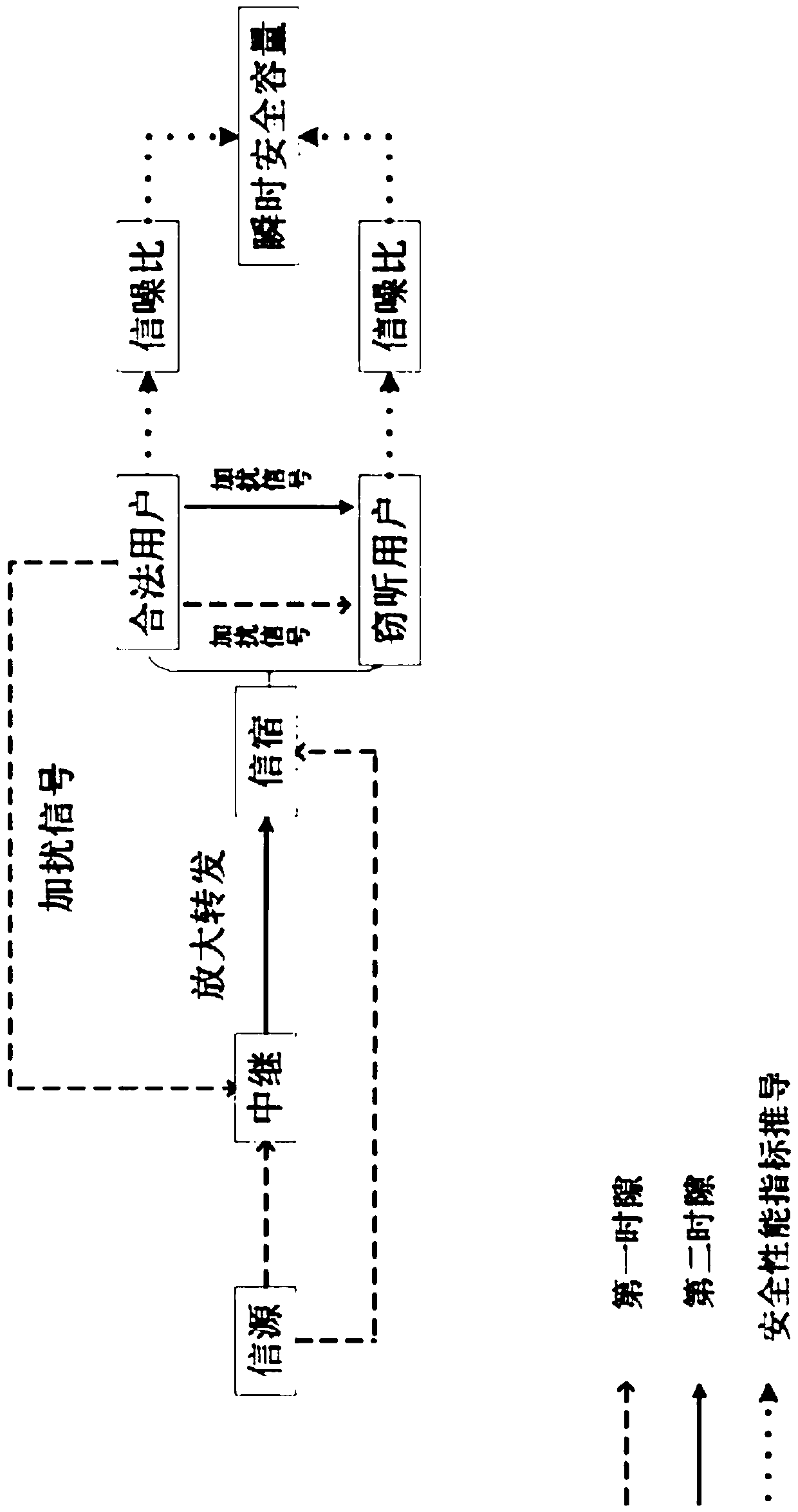
The invention relates to a relay link optimal user selection based collaboration scrambling secure transmission method. The method comprises the steps of selecting a target user node with the maximumreceiving SNR (Signal-to-Noise Ratio) as a legal user node and other user nodes as eavesdropping user nodes based on a link from a relay to a target user in a first time slot; sending information to arelay node and the target user node by a signal source node meanwhile sending an interference signal to the relay node and the eavesdropping user nodes by the legal user node; by the relay node, amplifying the information received in the first time slot by adopting a changeable grain amplification and forwarding protocol and forwarding the information to the target user node in a second time slot; and by the legal user node, carrying on sending the interference signal to the relay node and the eavesdropping user node. Through collaboration between the relay and the other nodes, the receivingSNR of an eavesdropping channel is reduced and the purpose of guaranteeing system secure transmission is realized.
Owner:HUAQIAO UNIVERSITY
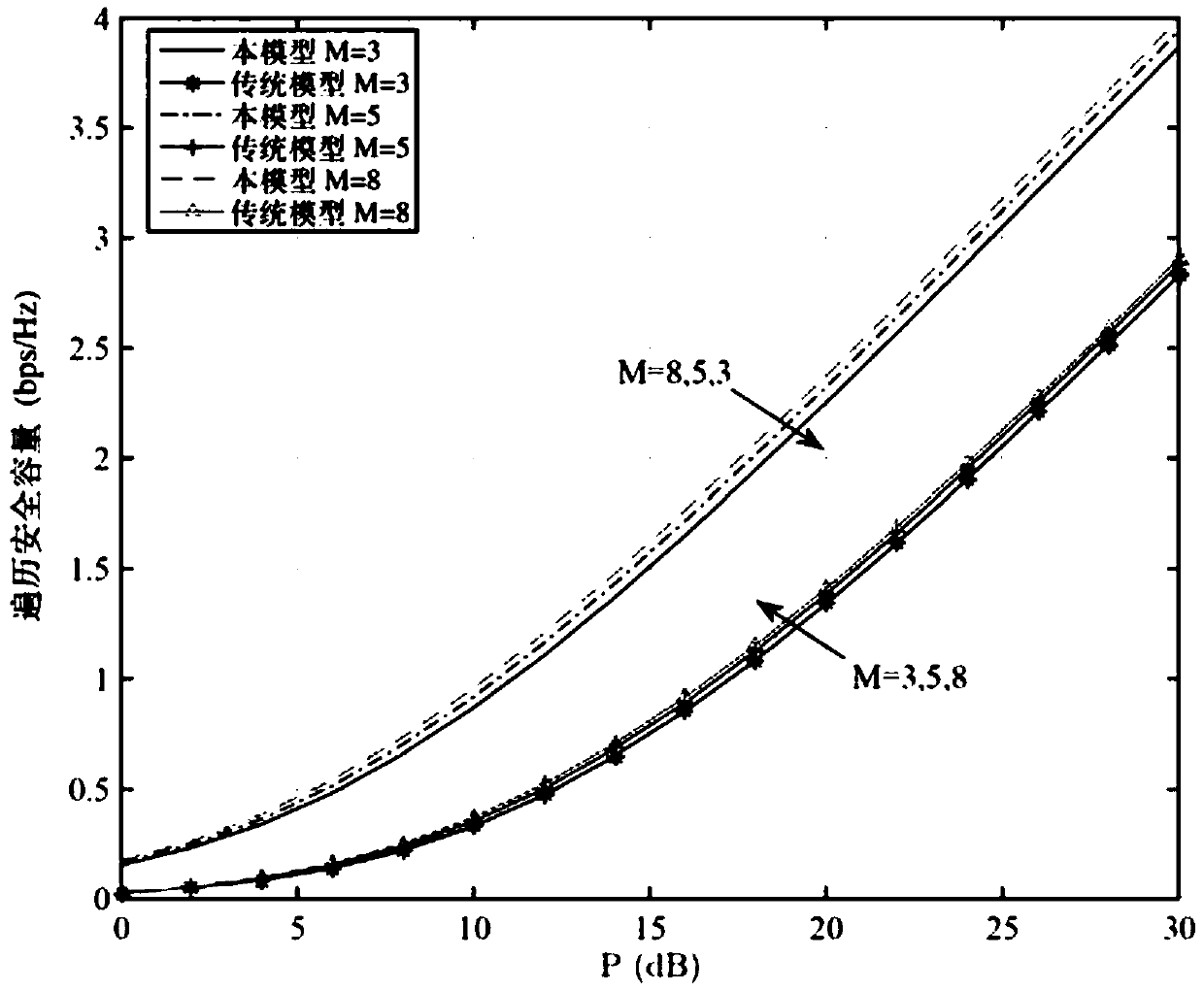
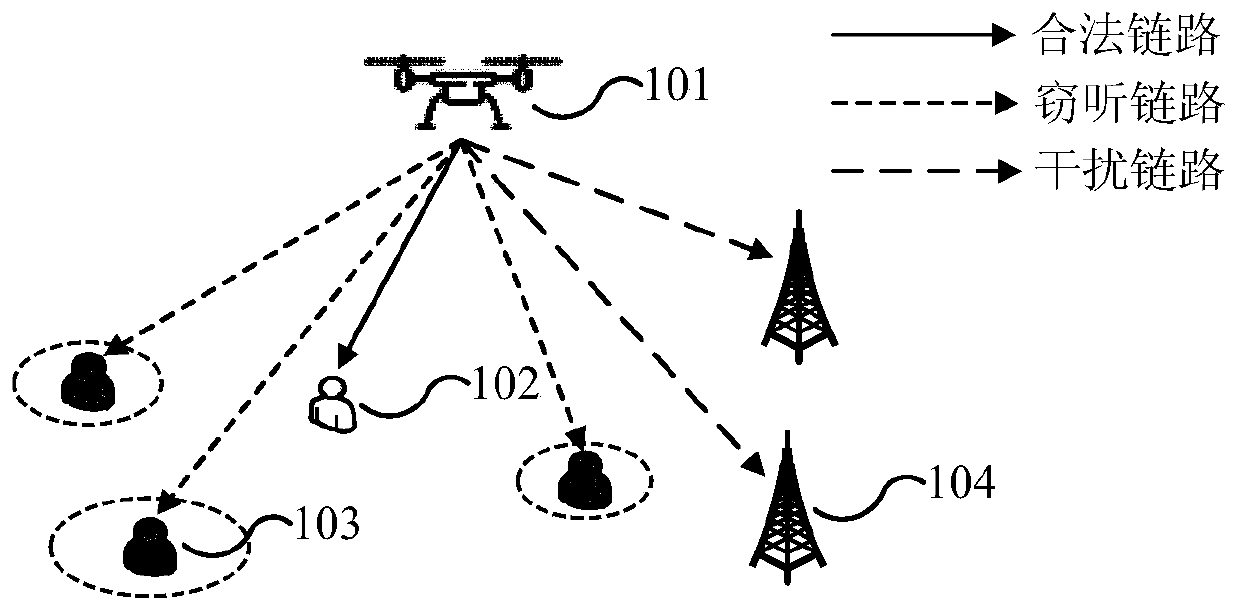
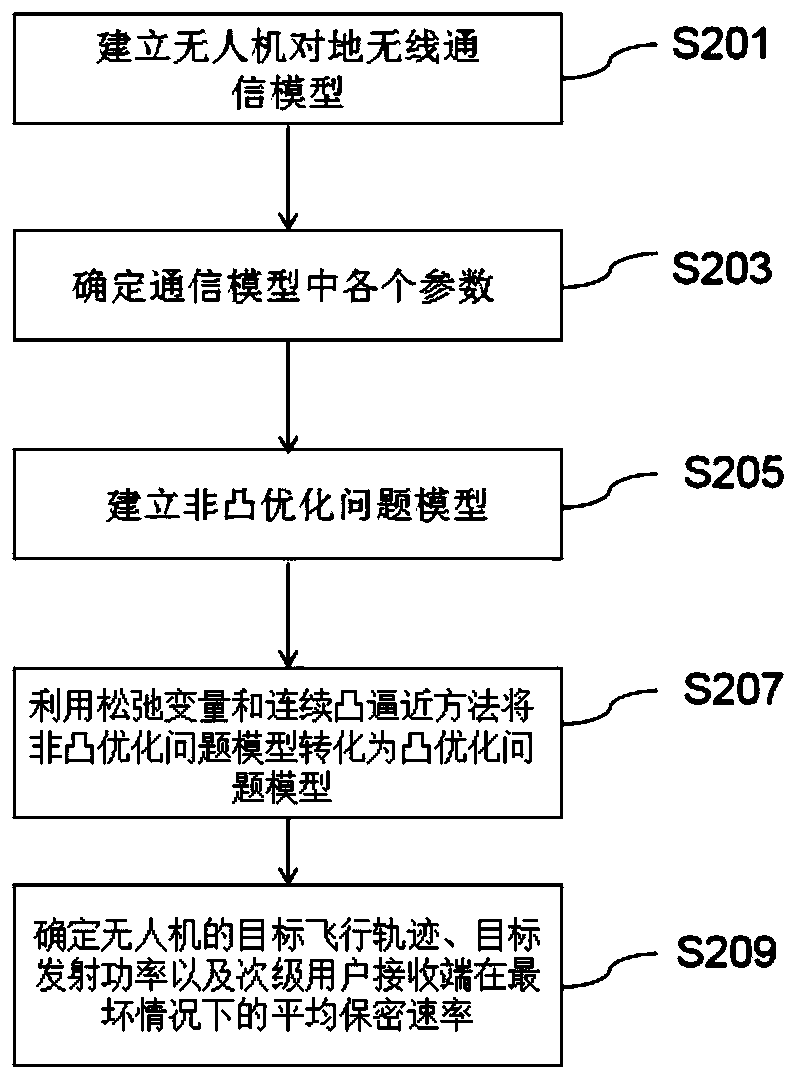
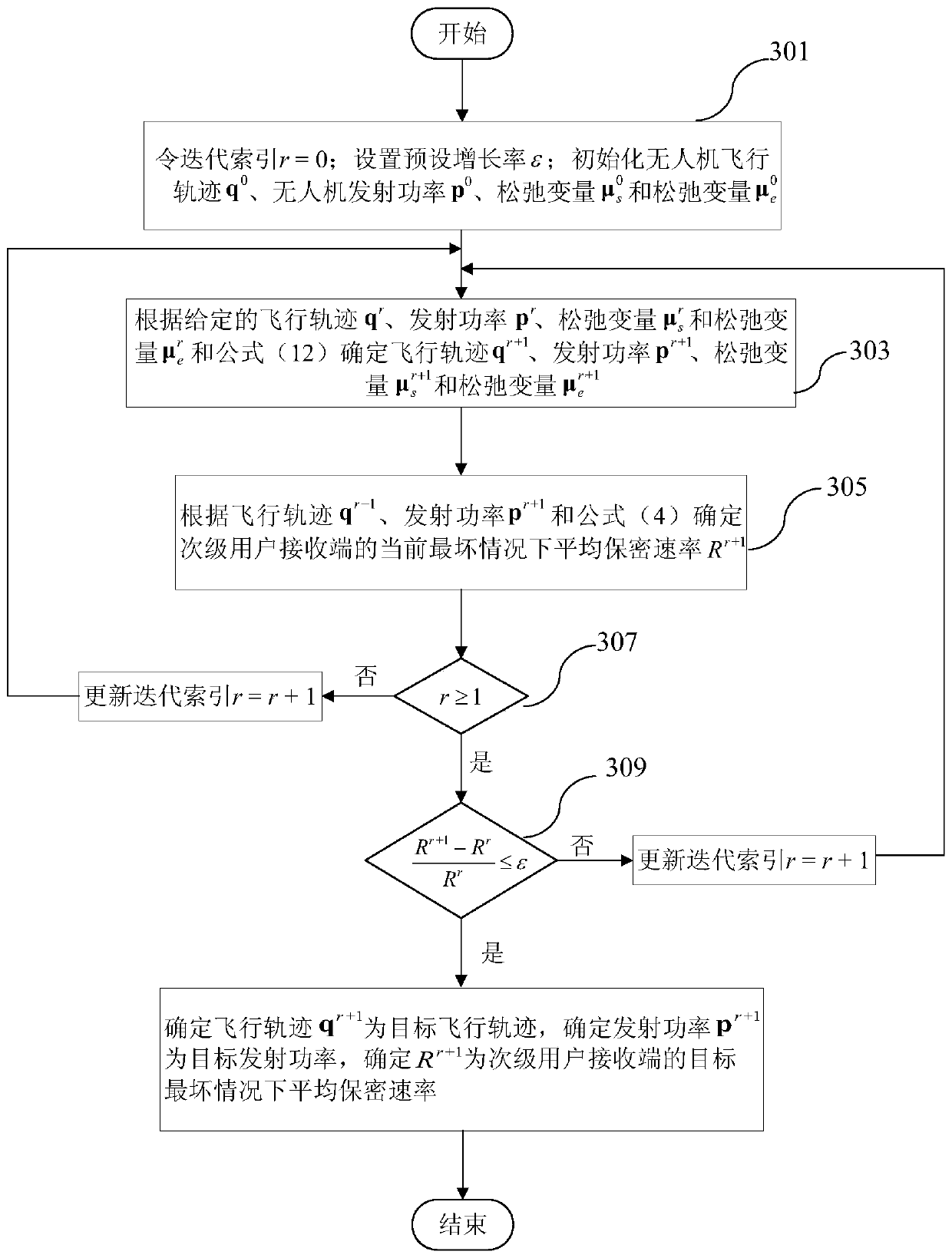
Method for controlling communication security of unmanned aerial vehicle assisted cognitive radio network
InactiveCN111343712AEnsure secure transmissionPower managementInternal combustion piston enginesCommunications securityTransmitted power
The invention relates to a method for controlling the communication security of an unmanned aerial vehicle assisted cognitive wireless network. The method comprises the following steps: step S201, establishing a communication model of unmanned aerial vehicle-to-ground wireless communication; step S203, determining each parameter in the communication model; s205, establishing a non-convex optimization problem model according to each parameter in the communication model; s207, converting the non-convex optimization problem model into a convex optimization problem model by using a slack variableand a continuous convex approximation method; and S209, according to the convex optimization problem model, determining the target flight path and the target transmitting power of the unmanned aerialvehicle and the average secrecy rate of the secondary user receiving end under the worst condition. According to the method, the average secrecy rate of the secondary user receiving end under the worst condition is maximized by jointly optimizing the flight path and the transmitting power of the unmanned aerial vehicle within the given flight time, so that safe transmission of information is effectively guaranteed.
Owner:SHANGHAI INST OF MICROSYSTEM & INFORMATION TECH CHINESE ACAD OF SCI
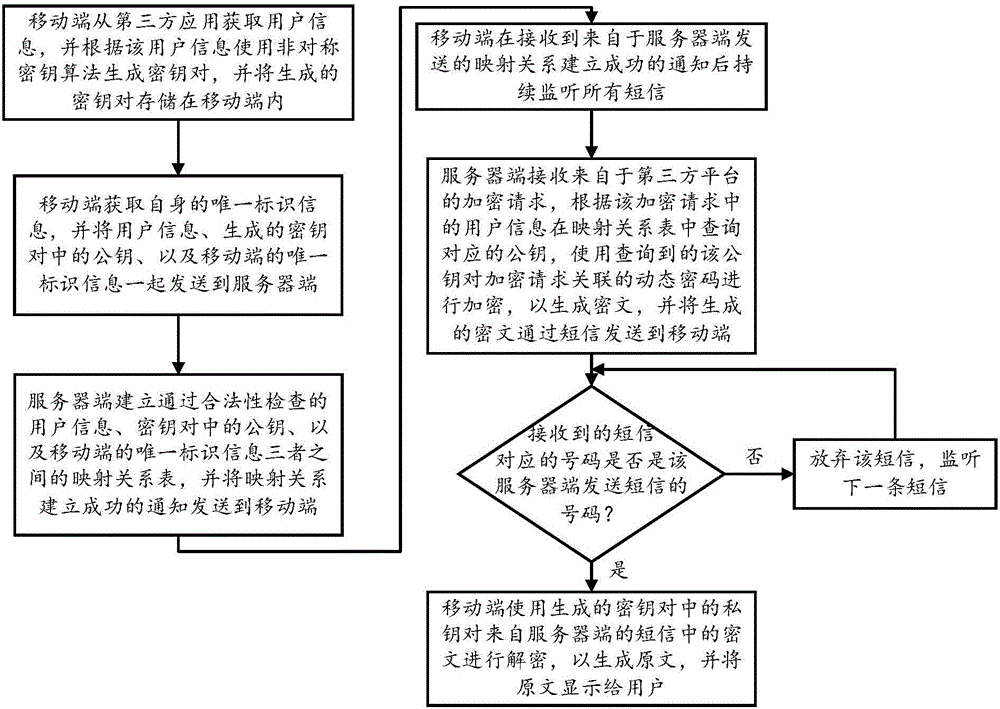
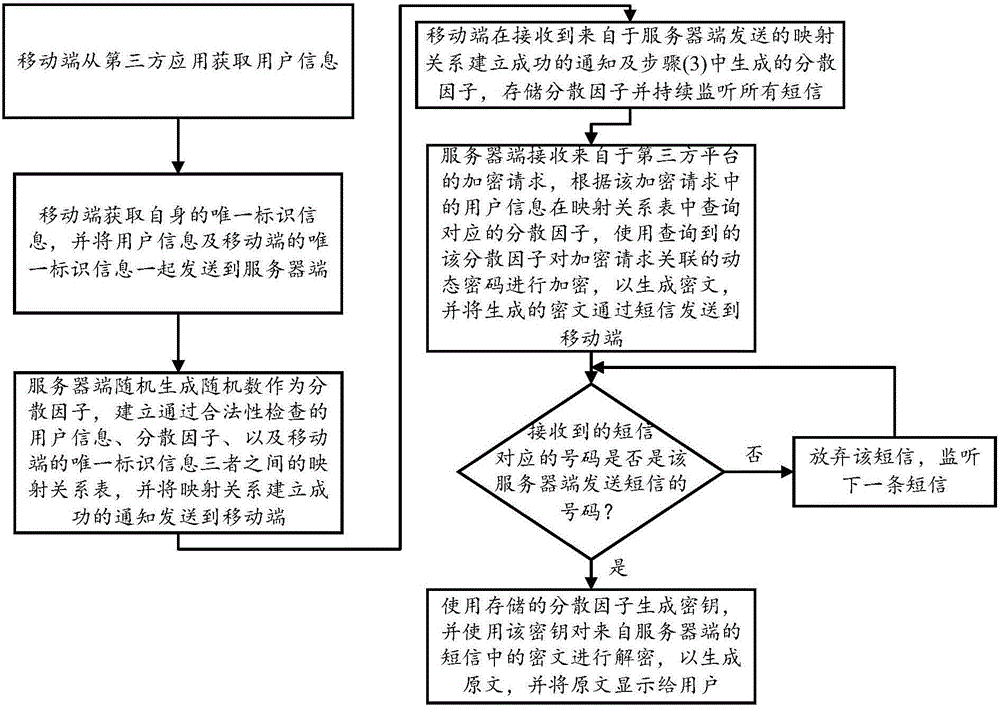
Secure transmission method and system for dynamic password
InactiveCN106330862AEnsure secure transmissionAchieve protectionMessaging/mailboxes/announcementsTransmissionThird partyPassword
The invention discloses a secure transmission method for a dynamic password. The method comprises the steps: a mobile terminal obtains user information from a third party application, uses the asymmetric key algorithm to generate a key pair according to the user information, and stores the generated key pair in the mobile terminal; the mobile terminal obtains its own unique identification information and sends the user information, the public key of the generated key pair, and the unique identification information of the mobile terminal to a server; the server establishes a mapping relationship table among the user information, the public key of the generated key pair, and the unique identification information of the mobile terminal that all pass the validity check, and sends a notice of success of mapping relationship establishment to the mobile terminal; and the mobile terminal receives the notice of success of mapping relationship establishment and continues to monitor all the short messages. The method and the system can overcome the technical problems that the dynamic password is easily intercepted, acquired, received or eavesdropped by the third party in the existing dynamic password encryption transmission process.
Owner:WUHAN ARGUSEC TECH
Power distribution energy collection delay secure transmission scheme of target user scrambling
ActiveCN107426792ADecrease the receive signal-to-noise ratioEnsure secure transmissionPower managementHigh level techniquesChannel powerSignal-to-noise ratio (imaging)
The invention discloses a power distribution energy collection delay secure transmission scheme of target user scrambling. The scheme comprises: the relay selects a user node having the maximum channel power gain from all target user nodes to serve a legal user in a first time slot, and uses the residual unselected user nodes as potential eavesdropping users, a signal source sends useful information to the relay, the legal user sends a scrambled signal to the relay, a relay node applies the power of the received signal to energy collection and uses the residual power for receiving the useful information sent by the signal source and the scrambled signal sent by the legal user; and in a second time slot, the relay broadcasts the received signal to a host, and the host contains the legal user and the potential eavesdropping users. The power distribution energy collection delay secure transmission scheme combines the cooperative scrambling technology with the information simultaneous interpretation technology reasonably, so that the receiving signal to noise ratio of an eavesdropping channel is reduced, the security performance of the network is improved, and thus the secure transmission of information is ensured.
Owner:HUAQIAO UNIVERSITY
Time-division energy harvesting relay secure transmission scheme based on destination user scrambling
ActiveCN107404743ADecrease the receive signal-to-noise ratioEnsure secure transmissionPower managementHigh level techniquesChannel powerSignal-to-noise ratio (imaging)
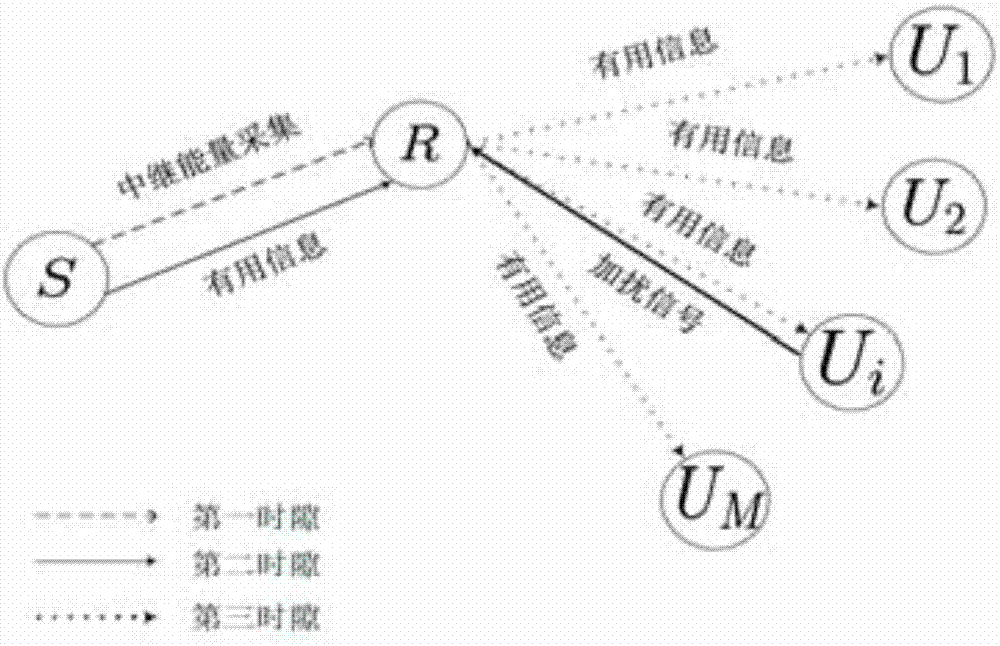
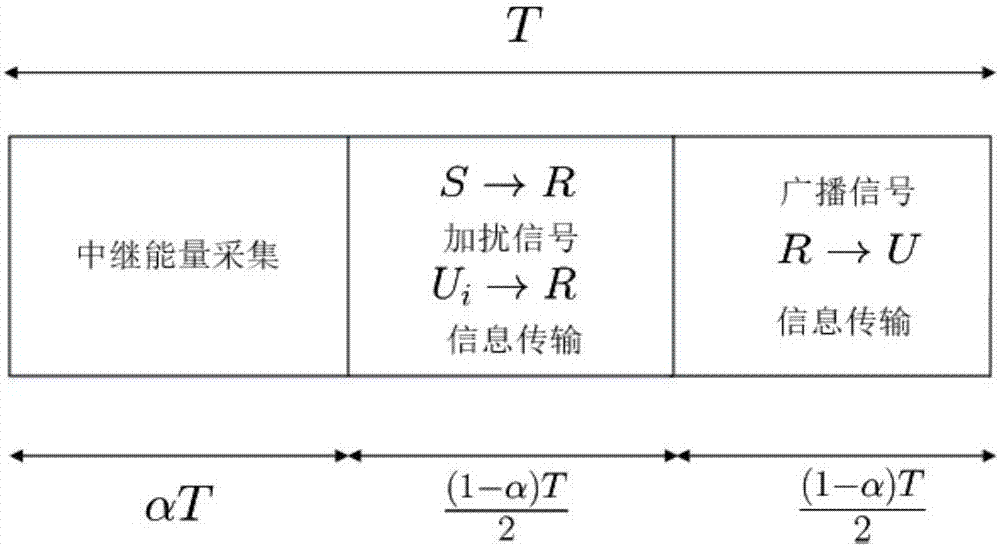
The invention discloses a time-division energy harvesting relay secure transmission scheme based on destination user scrambling. The scheme comprises the following steps: in a first time slot, a relay converts a received radio frequency signal into energy through an energy harvesting technology; in a second Time slot, the relay selects one destination user with the largest channel power gain from multiple destination users as a legal user and serves the legal user, remaining unselected destination users serve as potential eavesdropping users, a source sends useful information to the relay, and the legal destination user sends a scrambled signal to the relay; and in a third time slot, after the signal received by the relay is amplified, the signal is broadcast to a destination by use of energy obtained in the first time slot, wherein the destination includes the selected legal user and the potential eavesdropping users. According to the invention, by combining a cooperative scrambling technology with a time-division energy harvesting technology reasonably, the receiving signal-to-noise ratio of an eavesdropping channel is reduced, the network security performance is improved, and safe transmission of the information is guaranteed.
Owner:HUAQIAO UNIVERSITY
Remote proving method applicable to emergency rescue platform
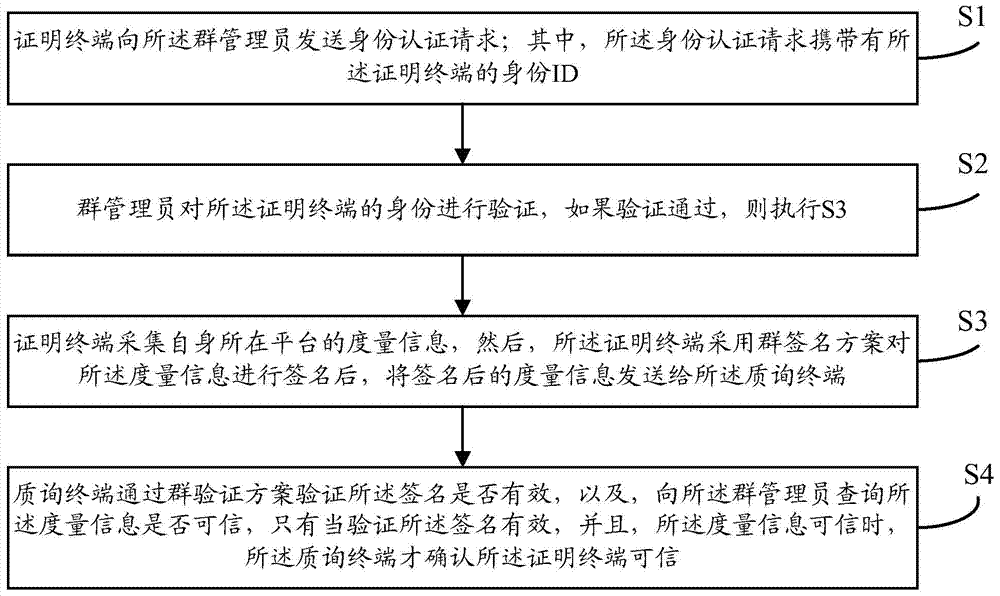
InactiveCN104506532ASolve the credible proof problemGuarantee authenticitySecuring communicationSecure transmissionEmergency rescue
The invention provides a remote proving method applicable to emergency rescue platform. The remote providing method comprises the steps that a proving terminal sends an identity authentication request to a cluster administrator; the cluster administrator verifies the identity of the proving terminal; if passing the verification, the proving terminal acquires measurement information of a platform where the proving terminal is positioned, signs the measurement information by adopting a cluster signing scheme and sends the signed measurement information to an inquiry terminal; the inquiry terminal verifies whether the signature is effective according to a cluster verification scheme and inquires whether the measurement information is credible from the cluster administrator; only if the signature is effective and the measurement information is credible, the inquiry terminal confirms that the proving terminal is credible. The remote proving method has the advantages that the problem of credibility proving of a terminal can be effectively resolved, and the authenticity of data and secure transmission of the data are guaranteed; meanwhile, the remote proving method has the characteristic of proving traceability, and identity forgery attack and malicious fraud attack can be effectively resisted.
Owner:BEIJING BUSINESS INTELLIGENCE & COMM TECH +1
Wireless communication encryption method based on angular momentums
InactiveCN106899970AEnsure secure transmissionAchieve securityError preventionEncryption apparatus with shift registers/memoriesSpin angular momentum of lightComputer hardware
The invention relates to a wireless communication encryption method based on angular momentums. According to wireless spin angular momentum and orbital angular momentum channel parameter characteristics, cross-layer password negotiation is realized by utilizing the difference due to the randomness and the independence of the spin angular momentum in different polarization or polarization states, the orbital angular momentum in different characteristic quantum numbers, signal strength indication and the bit error rate, so that an expected user and an eavesdropper receive not exactly same password packets in a password negotiation stage; therefore, the eavesdropper cannot obtain a password among normal communication users; and thus, the purpose of ensuring security data transmission is achieved.
Owner:NORTHWESTERN POLYTECHNICAL UNIV +1
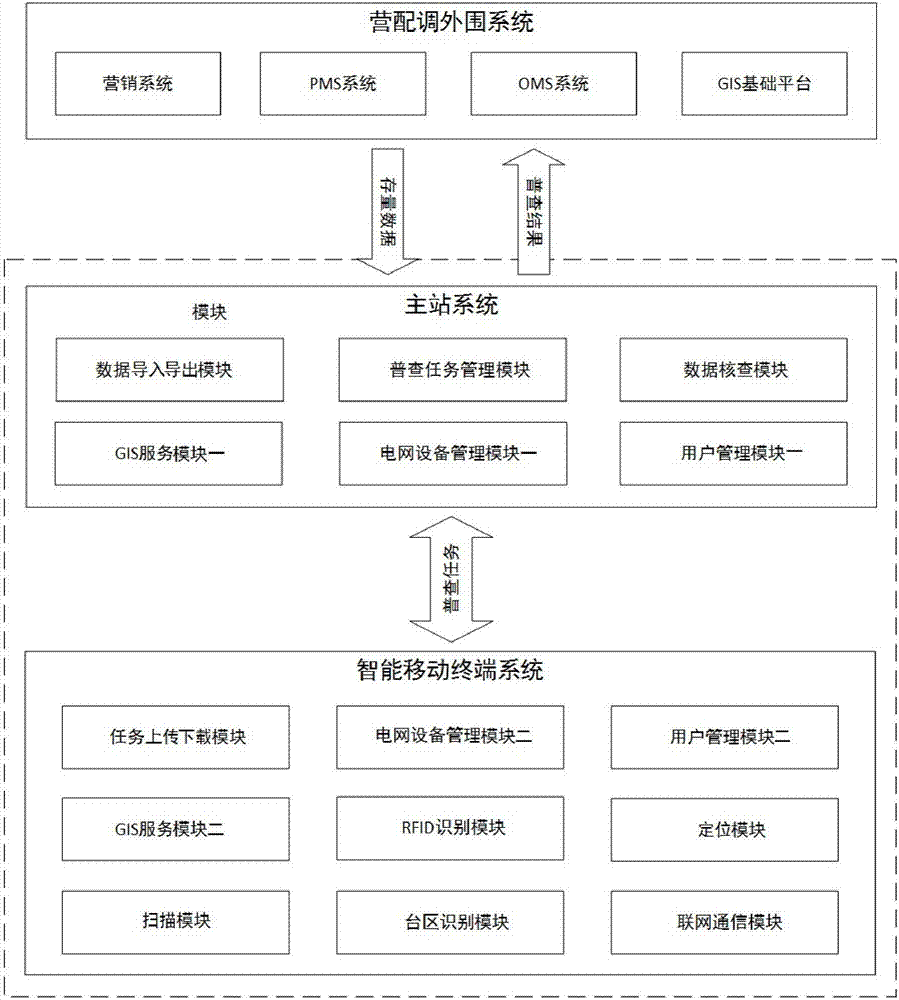
Mobile internet-based data general-survey system and general-survey method of marketing, distribution and dispatching integration
ActiveCN107315774AOvercome dataOvercoming time lagDatabase distribution/replicationGeographical information databasesData acquisitionData quality
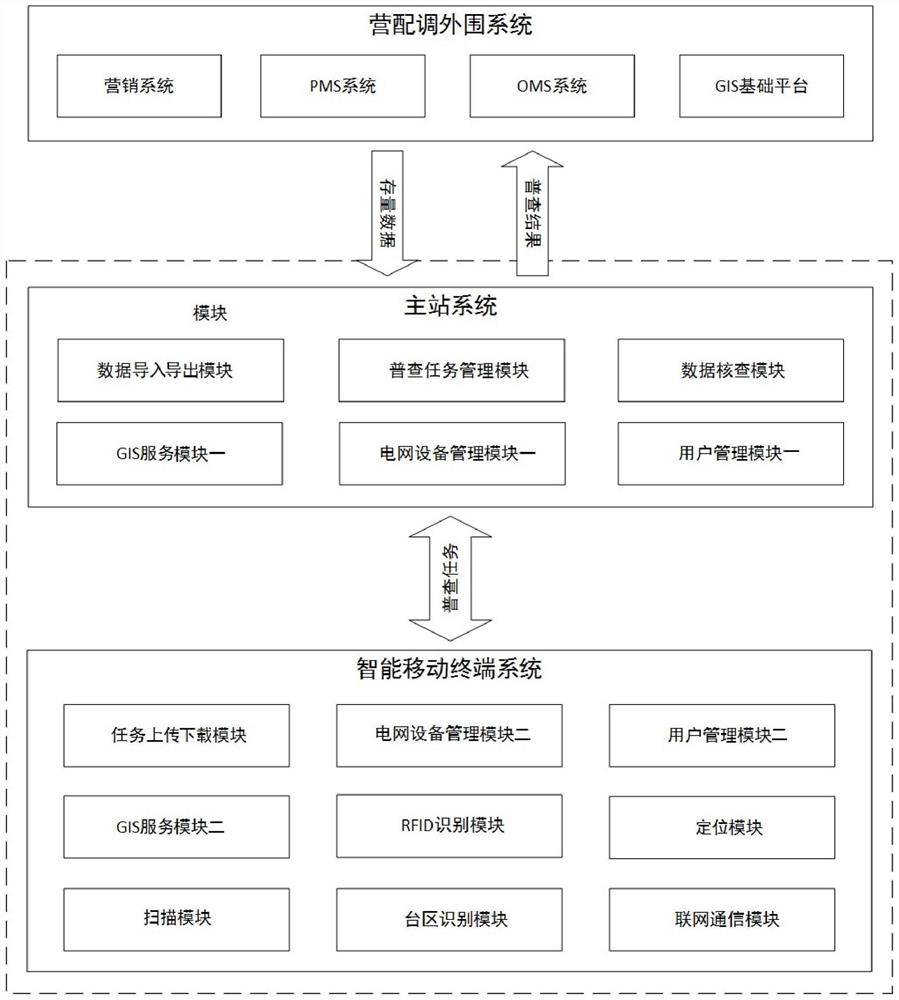
The invention discloses a mobile internet-based data general-survey system and general-survey method of marketing, distribution and dispatching integration, and belongs to the technical field of data general-surveys. The system includes a main station system carrying out data communication with a peripheral system of marketing, distribution and dispatching, and an intelligent mobile terminal system carrying out data communication with the main station system. The general-survey method includes the five steps of stock data extraction, general-survey task generation, data collection, data quality checking and general-survey result generation. The system and method overcome the shortcomings of poor data timeliness, low efficiency, poor quality, high costs and the like existing in prior data general-survey methods, have the advantages of good topology integrity, true data and high quality, and can improve a refinement management level of a whole life cycle of equipment, realize refinement management of equipment and user resources, and provide true and accurate basic data support and guarantees for all business fusion of marketing, distribution and dispatching.
Owner:STATE GRID CORP OF CHINA +1
A full-duplex cooperative scrambling secure transmission method based on optimal user selection of a direct path
ActiveCN109067437AImprove securityReduced or reduced securitySite diversityCommunication jammingSignal-to-noise ratio (imaging)Amplify and forward
The invention relates to a full-duplex cooperative scrambling secure transmission method based on optimal user selection of direct path. In the first time slot, the source node sends information to the relay node and the destination user node. At the same time, one user node with the largest signal-to-noise ratio is selected from all the destination user nodes as the legal user node, and the otherdestination user nodes are eavesdropping user nodes. The legal user node sends interference signals to the relay node and destination user node. In the second time slot, the relay node amplifies theinformation received in the first time slot by using the variable gain amplification and forwarding protocol, and forwards the information to the destination user node. The legitimate user continues to send the scrambling signal to the eavesdropping user node. The invention can reduce the receiving signal-to-noise ratio of the eavesdropping channel and ensure the safe transmission of the information.
Owner:HUAQIAO UNIVERSITY
An improved solution for increasing safety of RSSP-II protocol
ActiveCN104135469AAvoid destructionImprove securitySecuring communicationBlock cipher mode of operationSignaling system
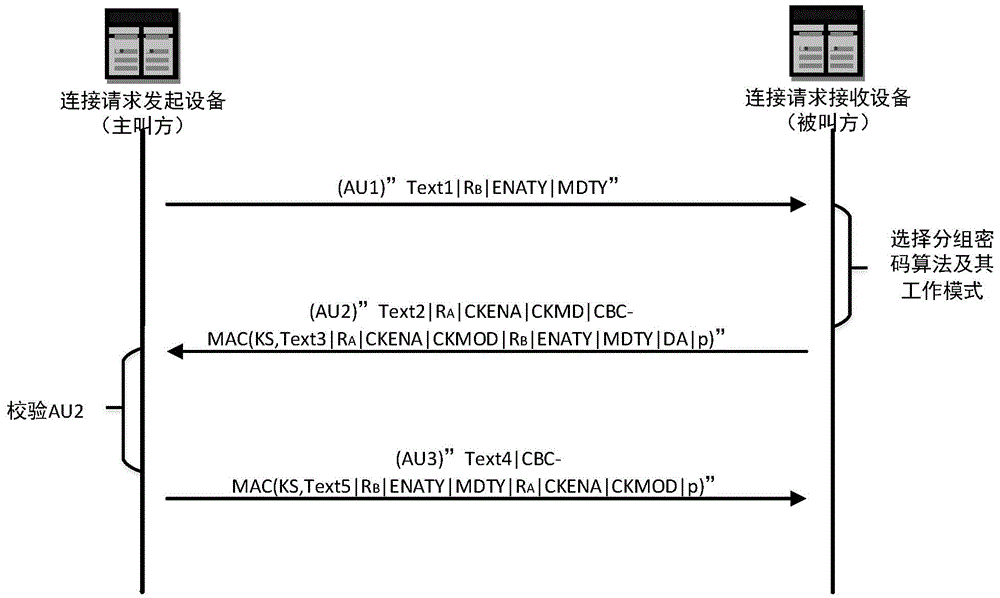
The present invention relates to an improved solution for increasing the safety of an RSSP-II protocol of a railway communication signal system, and the solution mainly includes the following aspects: introducing a block cipher algorithm and a block cipher working mode selection and negotiation mechanism; adding a block cipher algorithm list and a block cipher working mode list; in the block cipher working mode, besides an authentication mode, further introducing an authentication and encryption mode with associated data as an enhanced safe mode; restricting a maximum allowable message number for a single safe connection; and enhancing the judgment of contents of a received package. The solution of the present invention may hopefully improve the safety of the current railway system.
Owner:安捷光通科技成都有限公司 +1
A method and a system for generating an electronic format file by utilizing printable data of a bill
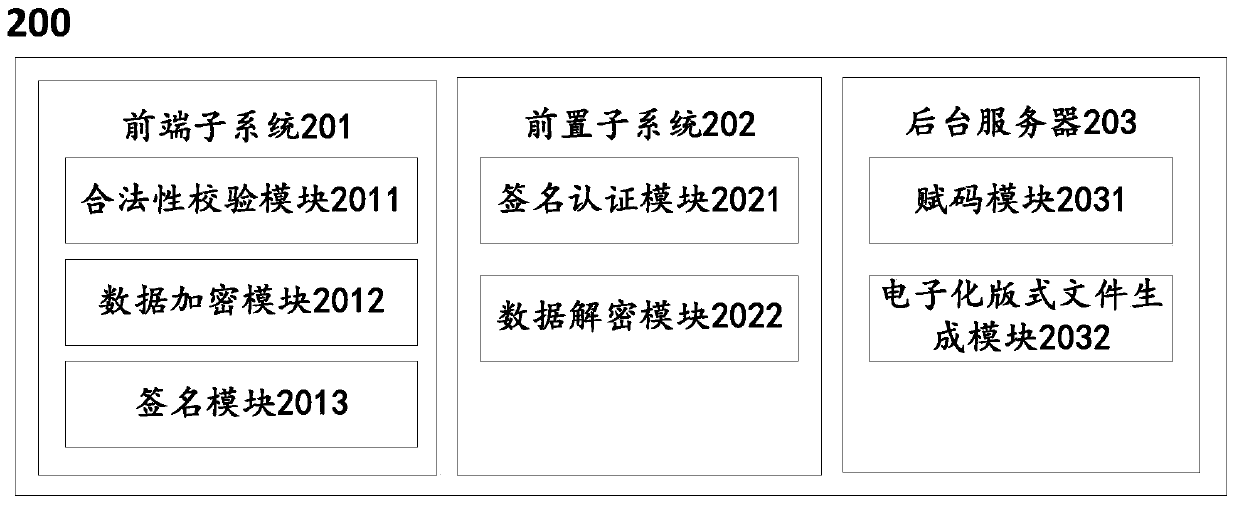
InactiveCN109948369ATimely deliveryStatistically accurateFinanceUser identity/authority verificationData transmissionDatabase
The invention discloses a method and a system for generating an electronic format file by utilizing printable data of a bill. The method comprises the following steps: carrying out legality verification on bill printing structured data; after the bill printing structured data passes legality verification, carrying out encryption and signature to obtain signed bill information; performing signatureauthentication and decryption on the received signed bill information to obtain decrypted bill information; and carrying out code assignment operation on the decrypted bill information to generate acomplete legal bill, and carrying out template assignment according to a preset template to generate an electronic format file corresponding to the bill printing structured data. According to the technical scheme of the invention, the technical advantages of paperless office, timely bill data transmission and accurate statistics can be fully realized while the data accuracy is ensured; the socialproblems and technical problems that the long-term storage cost of the paper bills is high and the paper bills need to be manually verified and signed are solved.
Owner:AEROSPACE INFORMATION
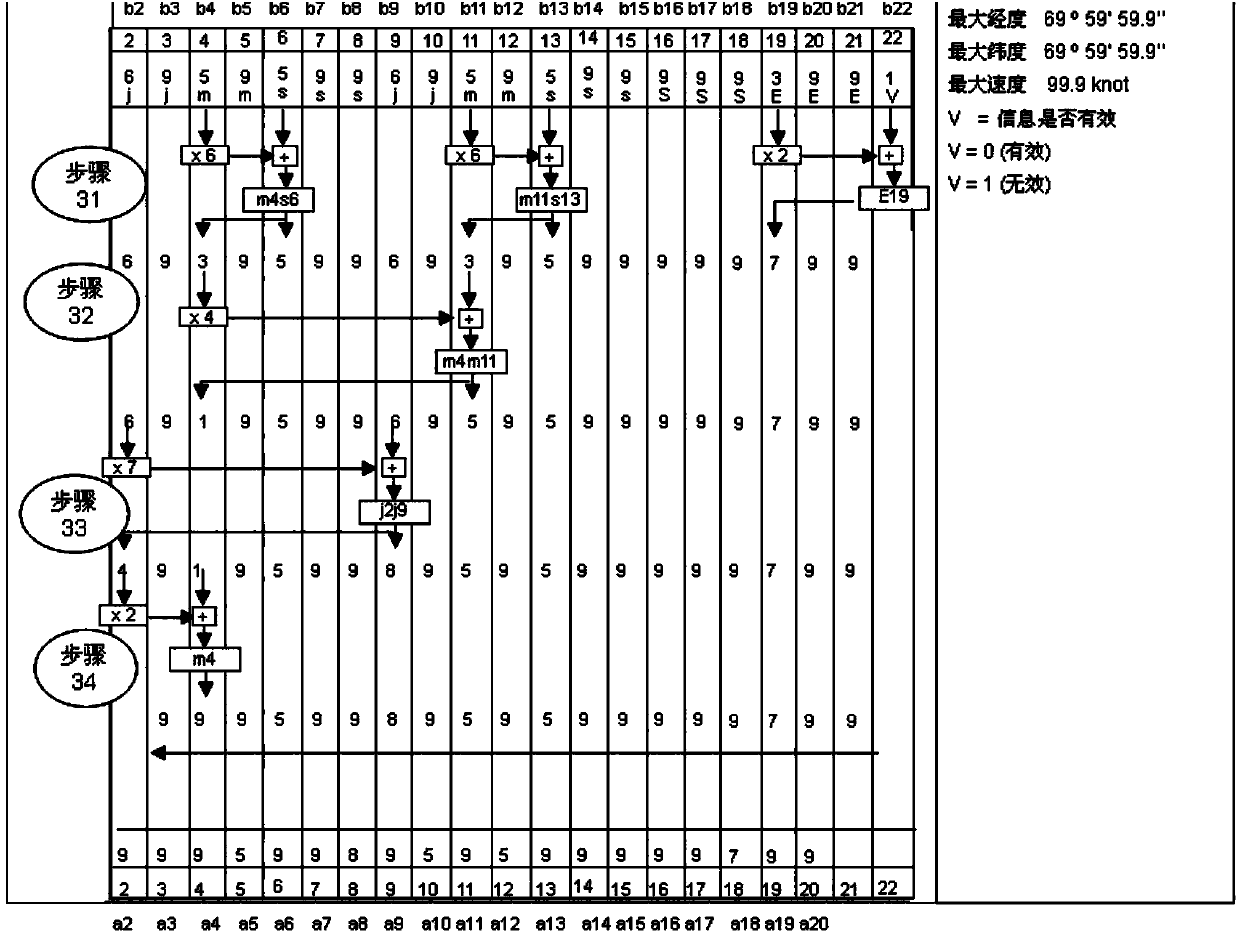
Satellite mobile communication system data processing method
The invention discloses a satellite mobile communication system data processing method which includes the steps of 1, converting longitude and latitude for representing an original location into forms of degree, minute and second, performing shifting process to the longitude and the latitude and editing shifted location information into location data composed of 22 numbers b1-b22; 2, removing a message type b1 from the 22 numbers to obtain the location data composed of 21 numbers; 3, encoding the location data composed of 21 numbers and converting the location data composed of 21 numbers into location data composed of 19 numbers; 4, by a receiver, receiving the location data composed of 19 numbers and solving the location data composed of 21 numbers through inverse operation; 5, supplementing the message type to obtain the location data composed of 22 numbers; and 6, performing inverse process to the longitude and latitude of the location data composed of 22 numbers so as to obtain information of the original location. The satellite mobile communication system data processing method can solve the problem of low channel utilization caused by high data volume, improve performance of a tracking system and further guarantee safety transmission of user data.
Owner:CHENGDUSCEON TECH
Physical layer secure transmission method based on noise distribution
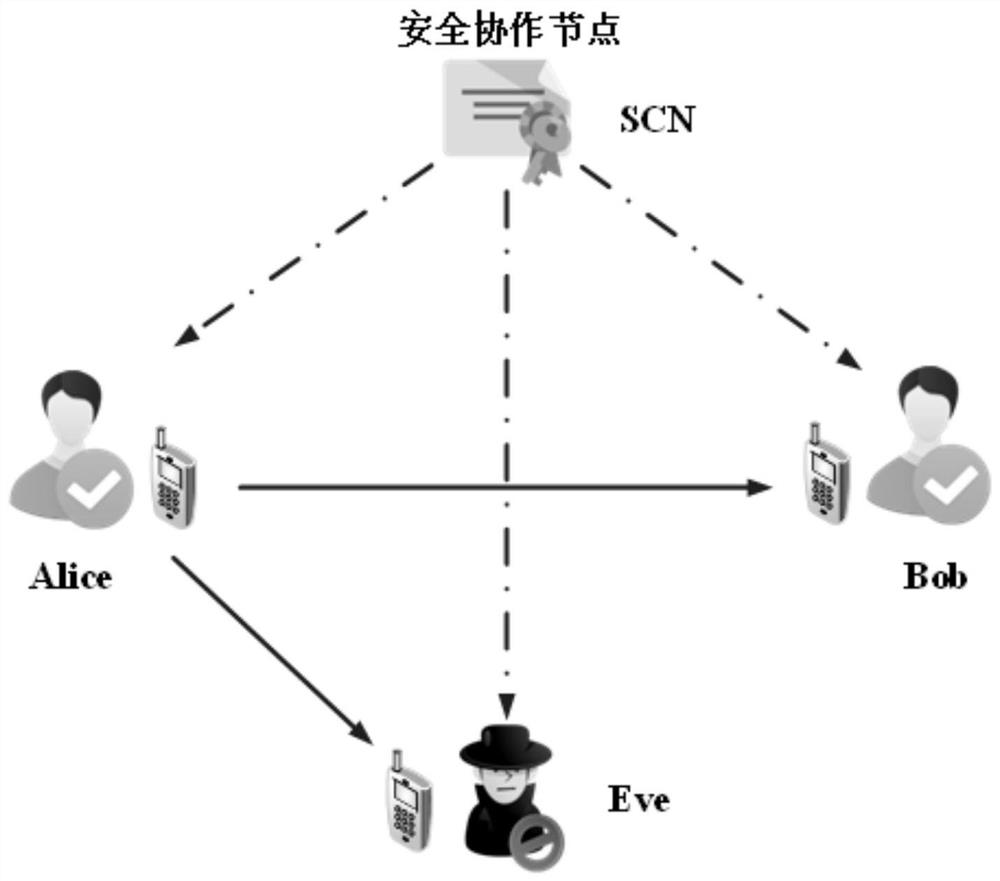
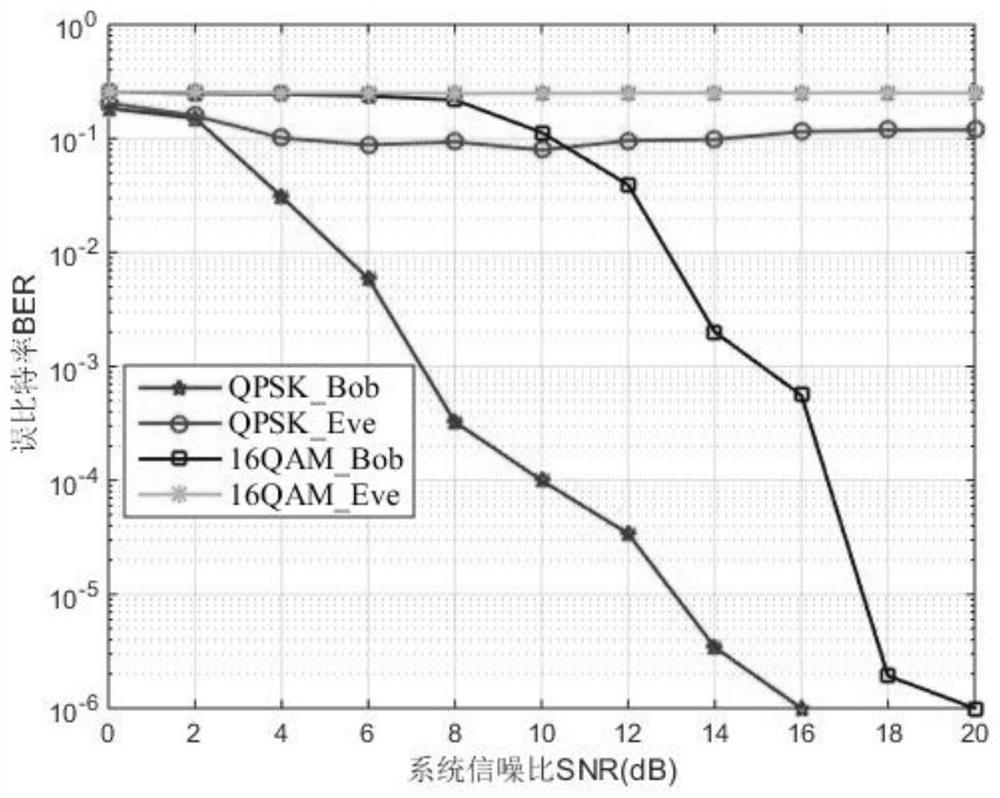
ActiveCN111901794AEnsure secure transmissionEnsure mutual independenceTransmissionSecurity arrangementInformation transmissionInterference elimination
The invention discloses a physical layer secure transmission method based on noise distribution. A security cooperation node SCN is introduced to distribute an artificial noise signal to a legal user;the SCN combines the local secret key with the random secret key of the legal user and then generates a random interference noise signal in a Hash mapping mode; an interference noise signal and an artificial noise signal used for confidential information transmission are sent to the legal user at the same time; the legal user can eliminate the influence of interference noise to obtain an artificial noise signal required by safe transmission. According to the method, the fact that an eavesdropper cannot eliminate noise interference is guaranteed, so that the eavesdropper generates an error code platform, and then safe transmission of a wireless system is guaranteed.
Owner:XI AN JIAOTONG UNIV
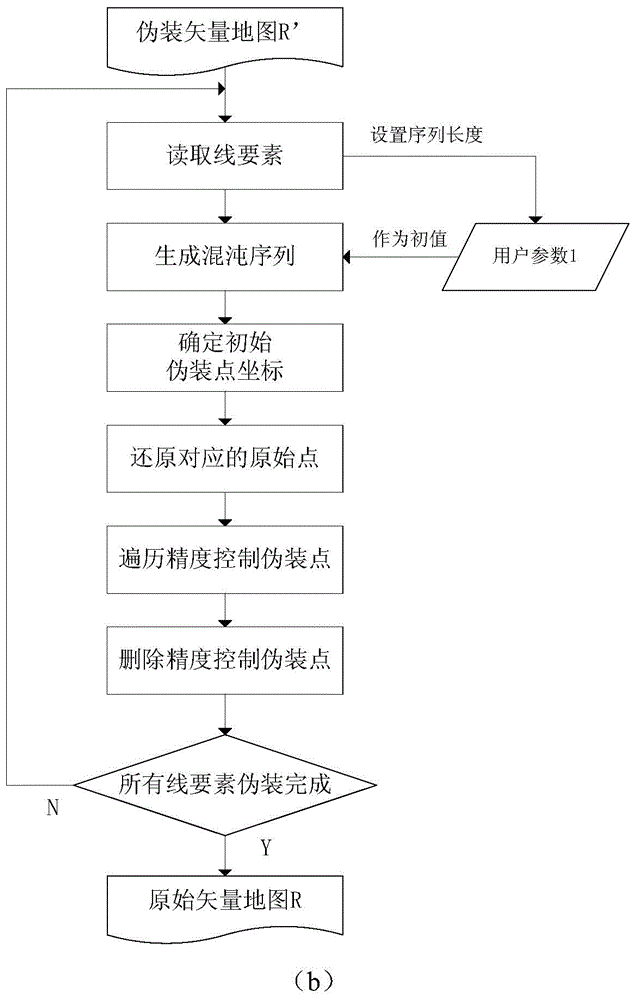
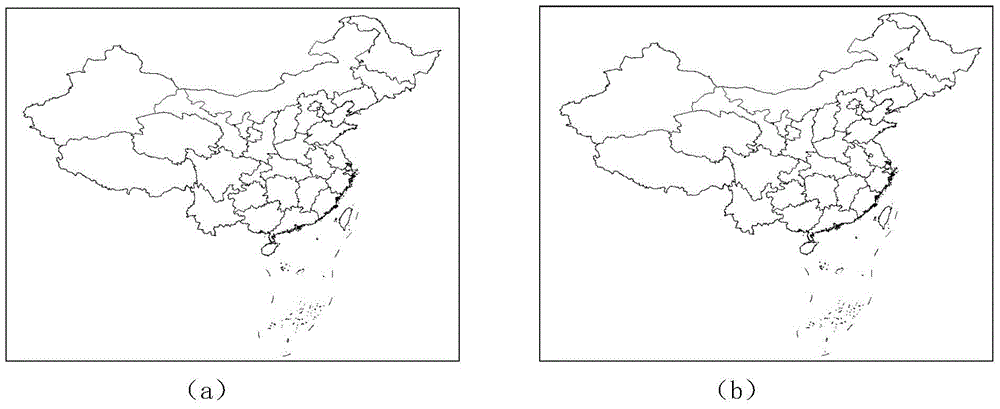
Precision controllable line and plane geographic element information disguising and restoring method
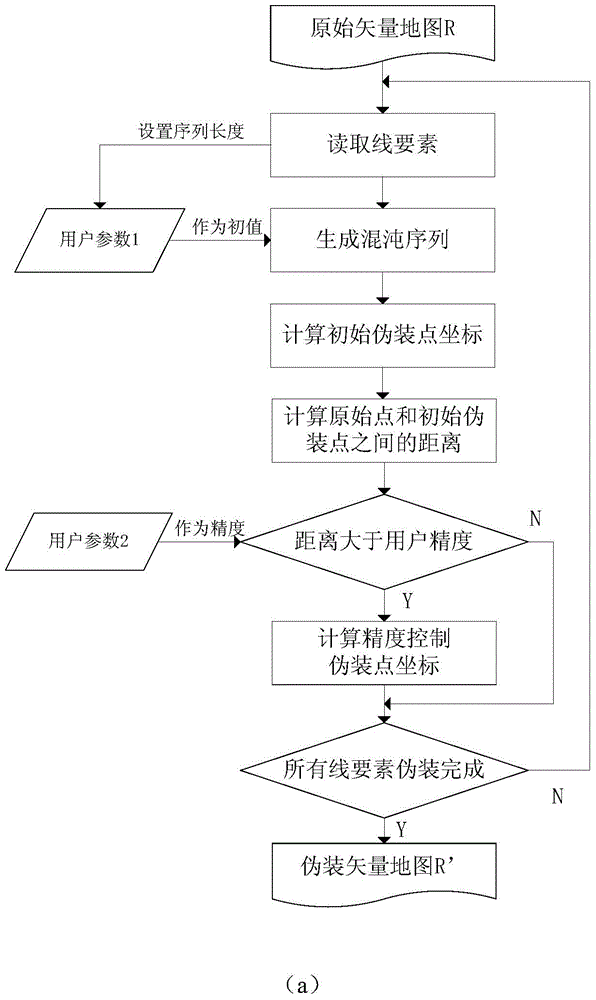
InactiveCN104657669AImprove concealmentAvoid the problem of too low embedding capacityDigital data protectionGeographical information databasesGlobal information systemAlgorithm
The invention discloses a precision controllable line and plane geographic element information disguising and restoring method. The method comprises the following steps: (1) calculating an initial disguising point, calculating a control disguising point and the like aiming at a line and plane type GIS (Global Information System) vector data disguising process; (2) restoring the disguising point, traversing a precision control disguising point, deleting and the like aiming at a line and plane type GIS vector data restoring process. The method has the advantages that the elusiveness is higher and the method is not limited by capacity; the safety of secret data in data transmission and elusive communication can be effectively guaranteed on the basis of hiding the existence of the secret information.
Owner:NANJING NORMAL UNIVERSITY
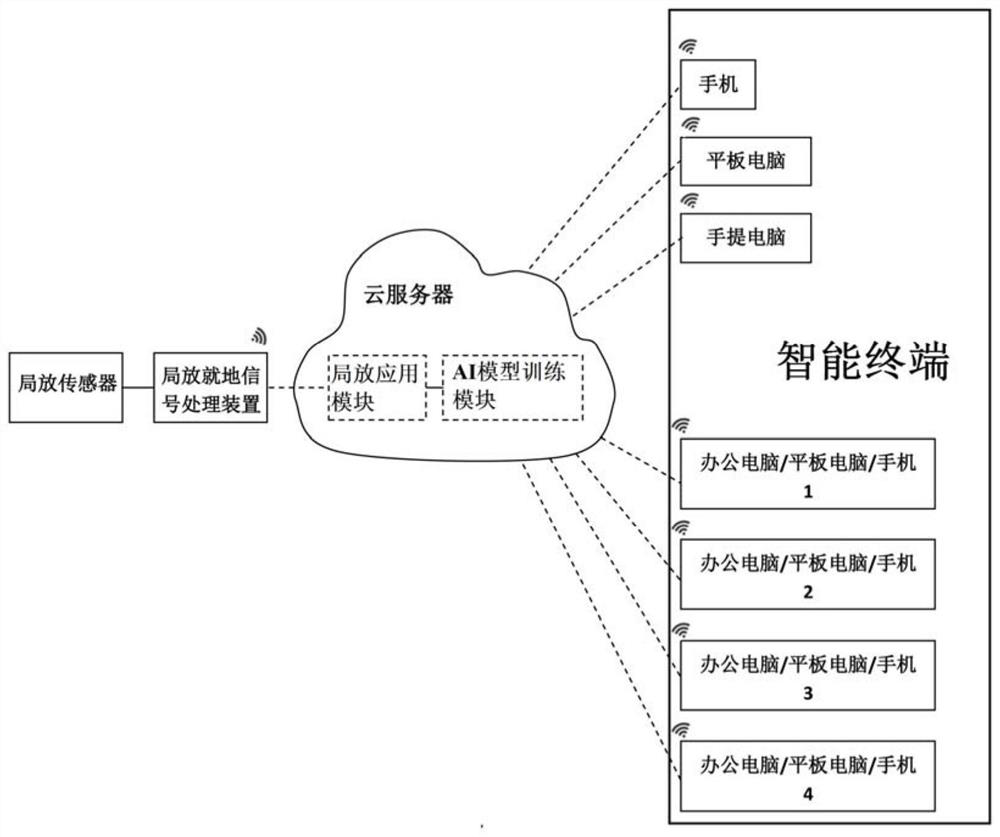
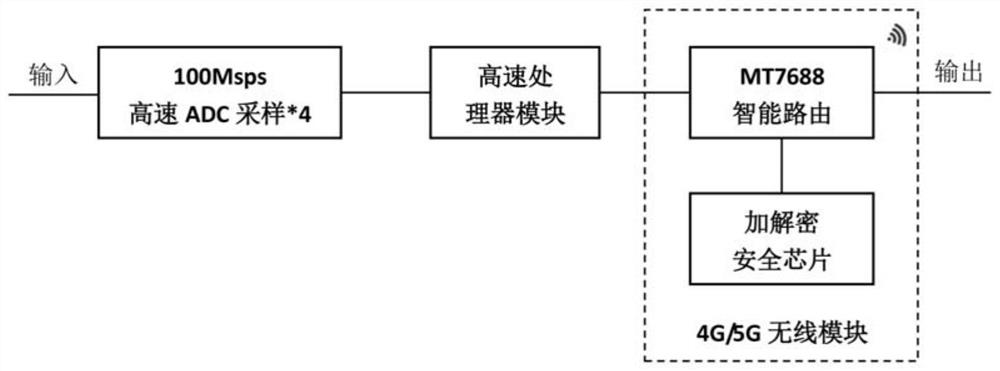
Artificial intelligence partial discharge monitoring and distinguishing system and method based on cloud technology
InactiveCN112462212AAchieve sharingLower requirementTesting dielectric strengthMachine learningWireless transmissionSignal on
The invention provides an artificial intelligence partial discharge real-time monitoring and distinguishing method based on a cloud technology. The method comprises the following steps: S1, detectinga partial discharge signal on a cable line in real time through a partial discharge sensor; s2, a partial discharge on-site signal processing device acquires a partial discharge signal and processes the partial discharge signal to form intermediate data; s3, obtaining the intermediate data through a cloud server, carrying out the safety processing to form test data, and then carrying out the storage analysis; and S4, acquiring test data through the intelligent terminal and displaying the test data. The invention further provides an artificial intelligence partial discharge monitoring and distinguishing system based on the cloud technology utilizing the method. The system comprises the partial discharge sensor, the partial discharge on-site signal processing device, the cloud server and theintelligent terminal. According to the invention, sharing of test data is realized based on a cloud technology and a wireless transmission technology, partial discharge test experts in different areas can remotely support and judge partial discharge at any time, and the requirement on test personnel is not high.
Owner:GUANGDONG POWER GRID CO LTD +1
Wireless single-input single-output vector synthesis secure transmission method based on RIS
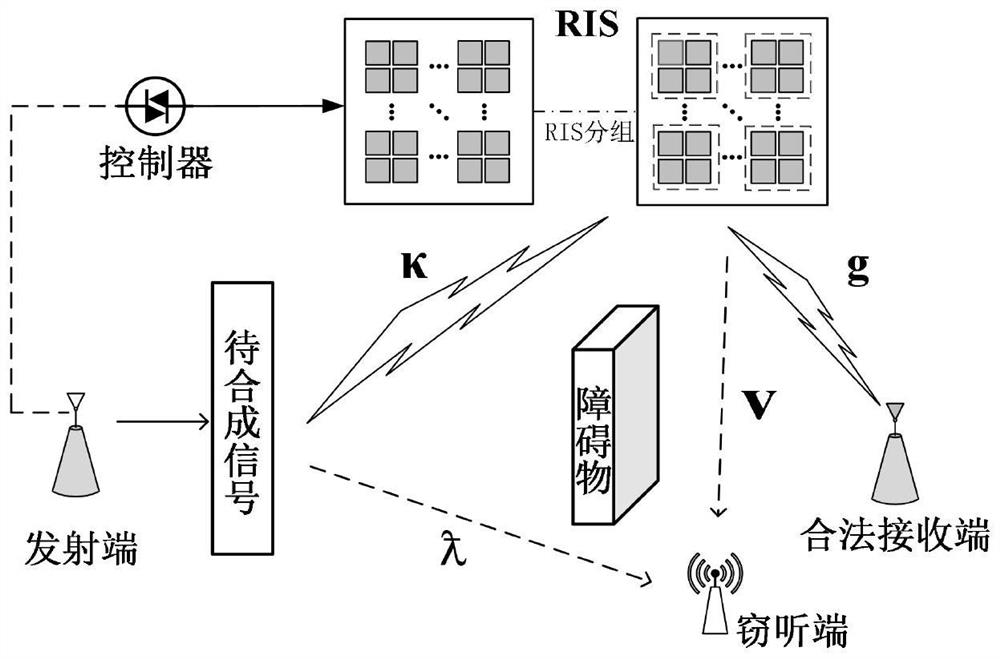
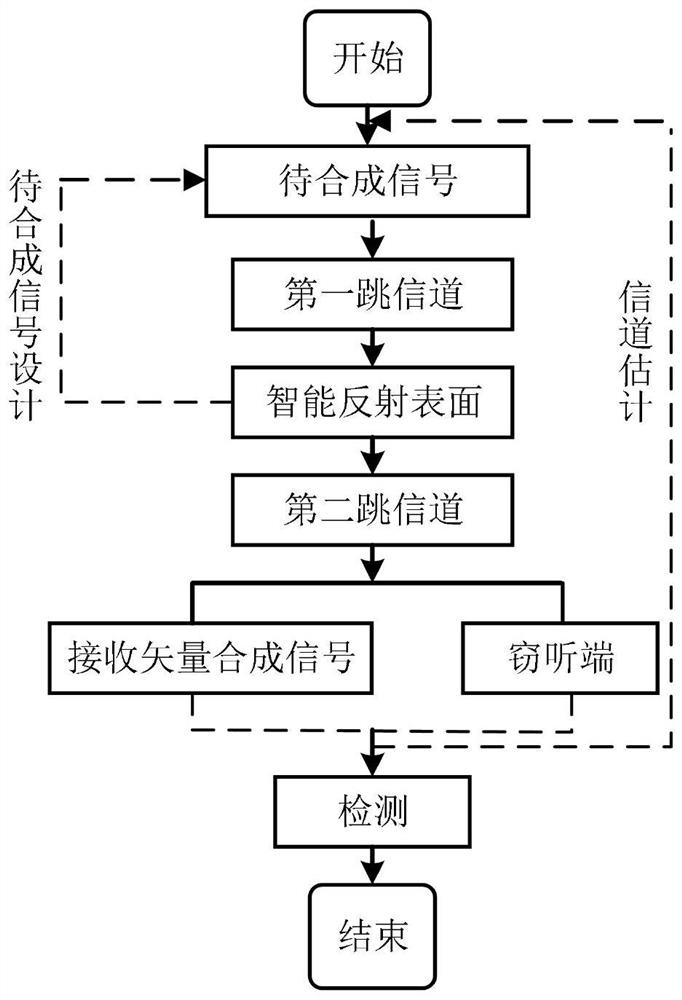
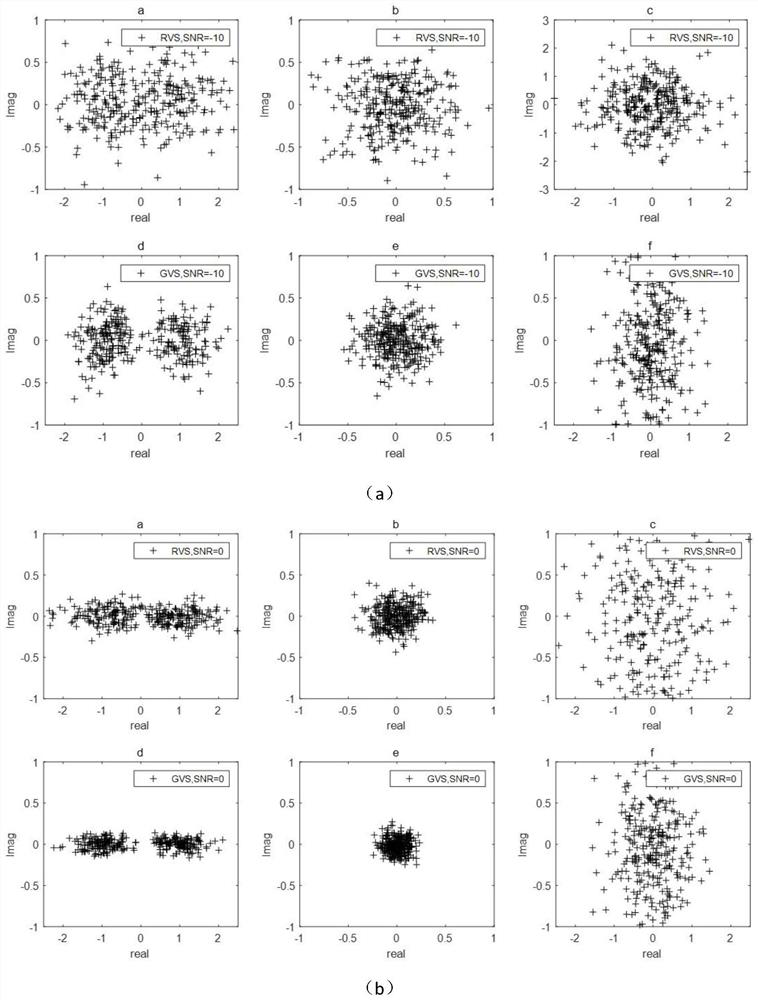
PendingCN114205048AReduce complexityEnsure transmission securitySecret communicationSecurity arrangementChannel state informationWireless transmission
The invention discloses a wireless single-input single-output vector synthesis secure transmission method based on an RIS (Radio Information System), which mainly solves the problem of ensuring the information security of a physical layer of a single-input single-output system in the existing RIS-assisted wireless transmission technology. Comprising the steps that a single-antenna transmitting end transmits a signal to be synthesized, and the signal is designed according to known channel state information; then, for randomly selecting RIS array element reflection coefficients, respectively designing two RIS reflected signal vector synthesis signal transmission schemes with different implementation complexity so as to realize vector synthesis of received signals by a legal receiving end and obtain regular receiving constellation symbols, but the received signals at an eavesdropping end keep random disturbance, and ideal synthesis processing cannot be realized; and finally, the legal receiving end and the eavesdropping end respectively detect and decode the received signals obtained by the legal receiving end and the eavesdropping end. According to the invention, the security of information transmission can be guaranteed, the reliability of information transmission is effectively improved, and the hardware implementation cost of the RIS control end is low.
Owner:XIAN UNIV OF POSTS & TELECOMM
Dental system
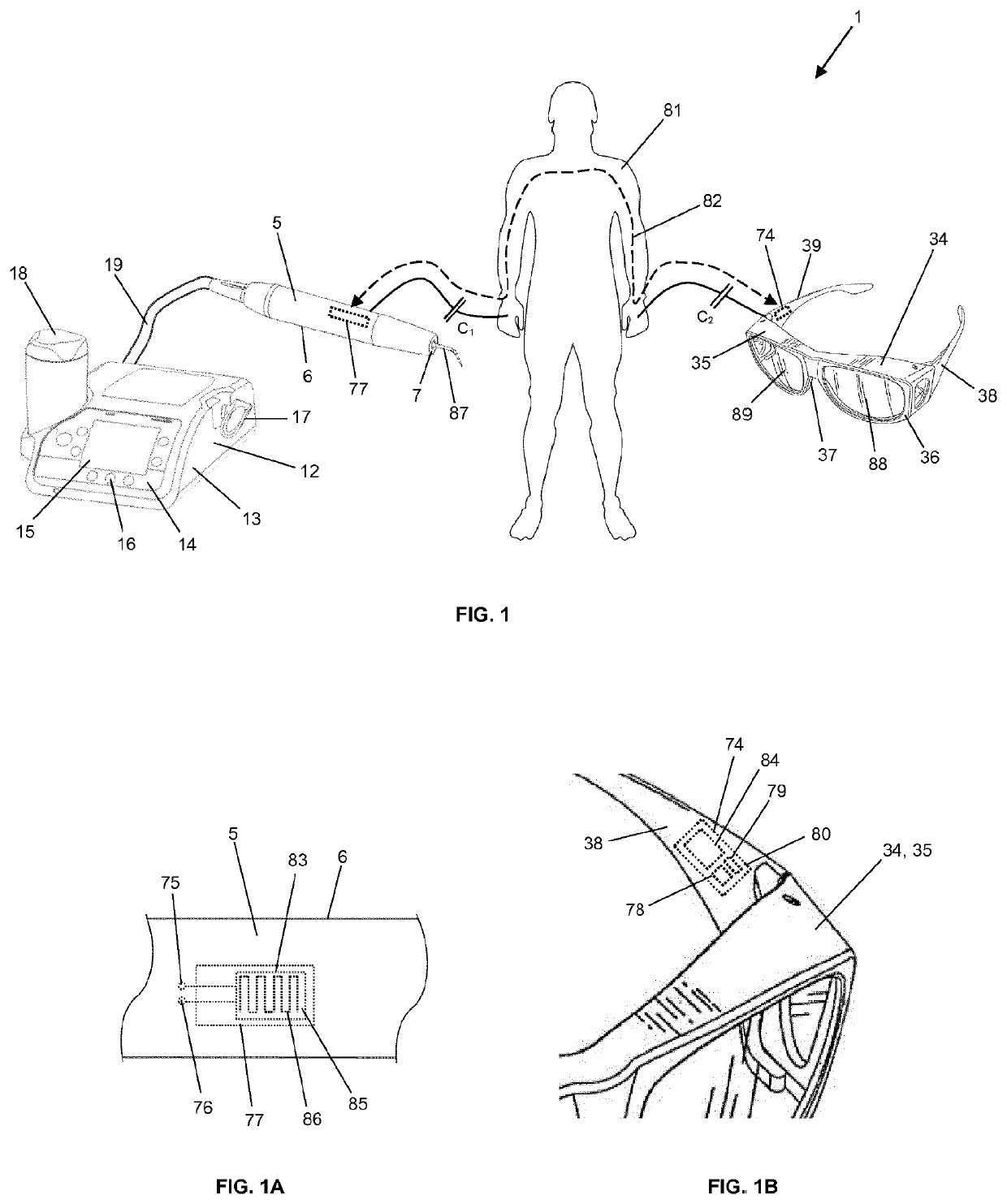
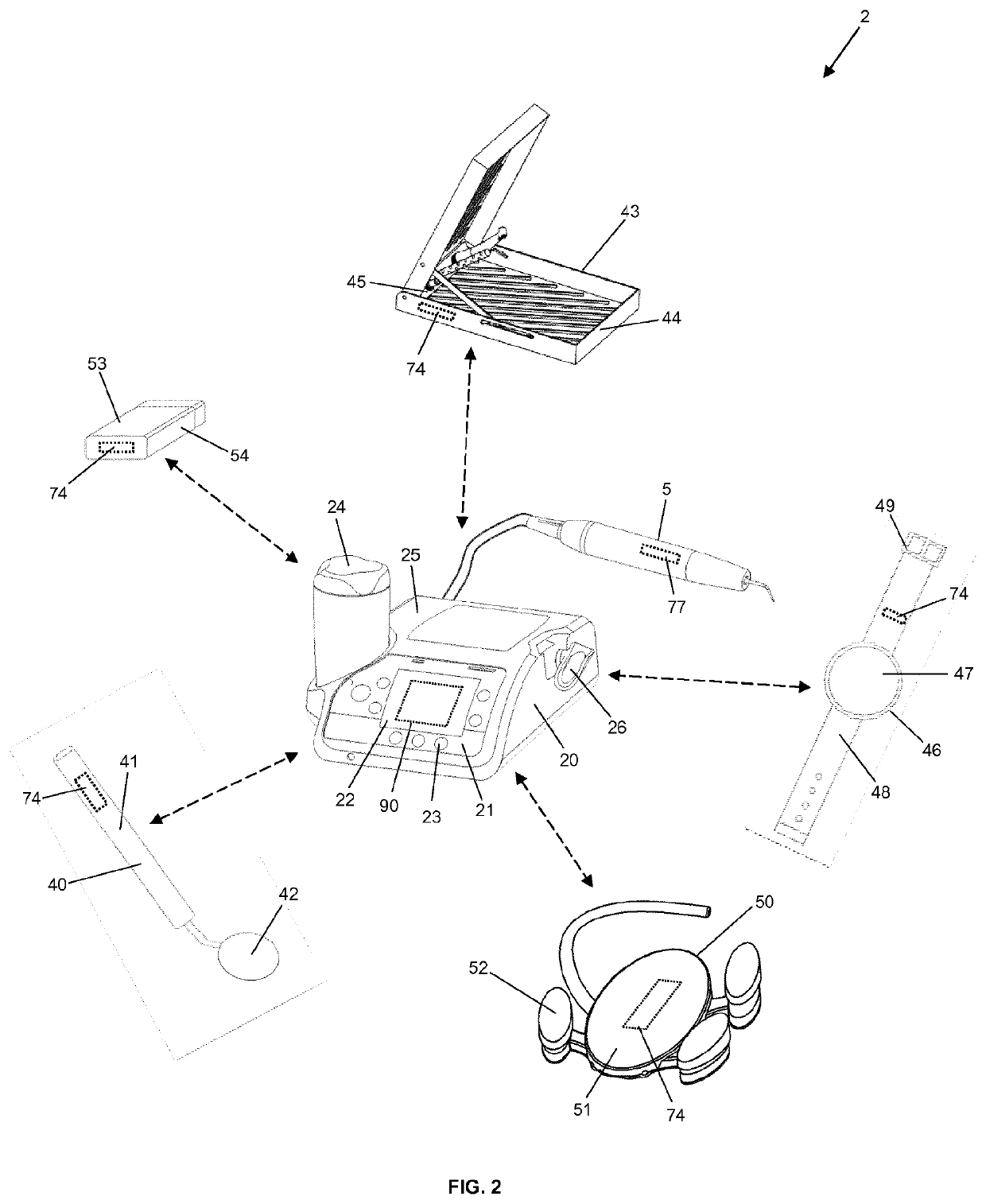
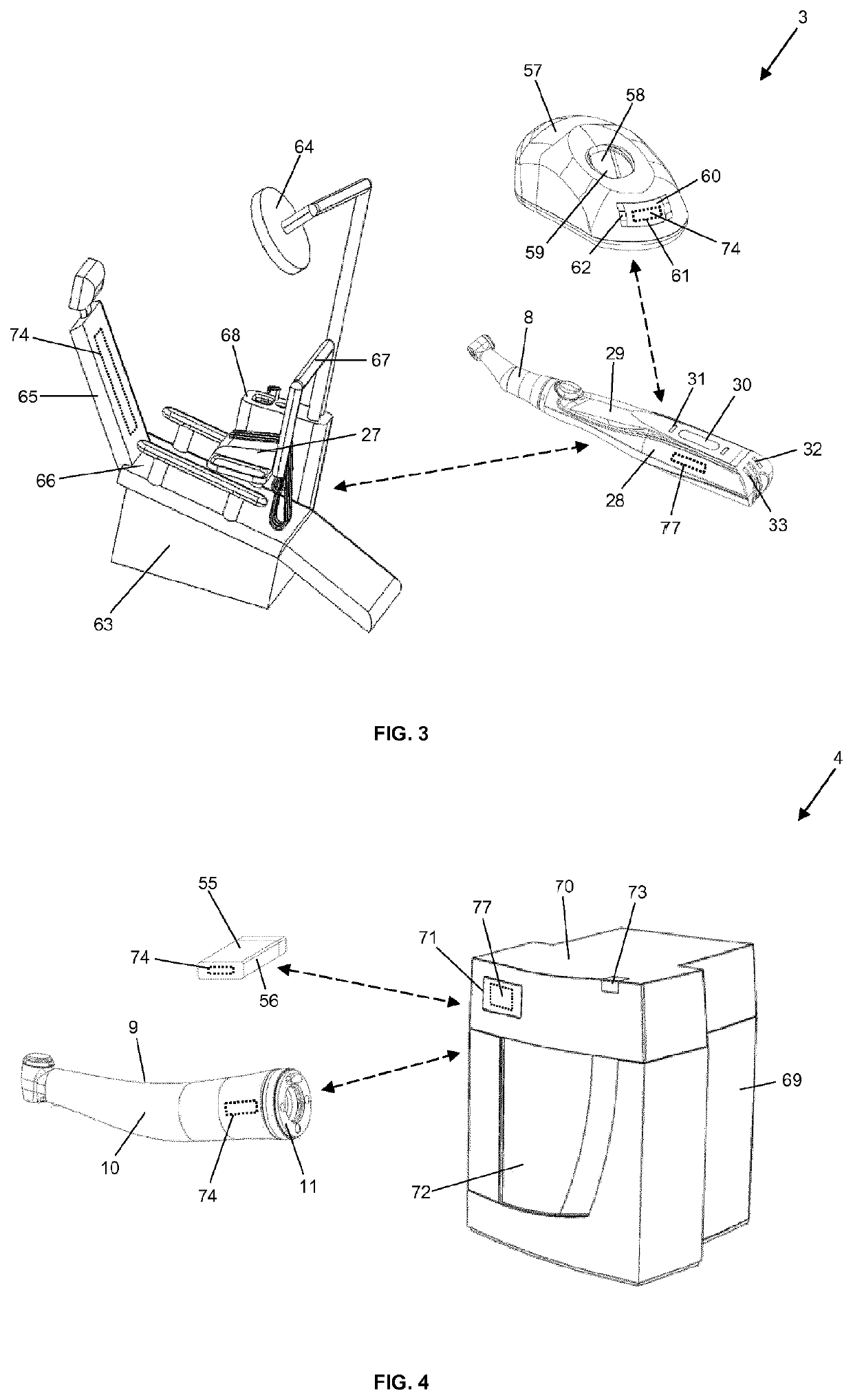
ActiveUS10610309B2Ensure secure transmissionSecure transmissionDiagnosticsSurgical systems user interfaceHuman bodyCapacitive coupling
A medical or dental system with at least one first transmitting and / or receiving unit and at least one second transmitting and / or receiving unit, wherein the at least two transmitting and / or receiving units are designed for the capacitive coupling of electric signals into and / or out of a human body, so that an electric path which extends through the human body of the user and / or of the person to be treated can be established for the transmission of electric signals between the at least one first transmitting and / or receiving unit and the at least one second transmitting and / or receiving unit, in order to transmit data between the at least two transmitting and / or receiving units.
Owner:W&H DENTALWERK
Big data implementation system and method based on network security
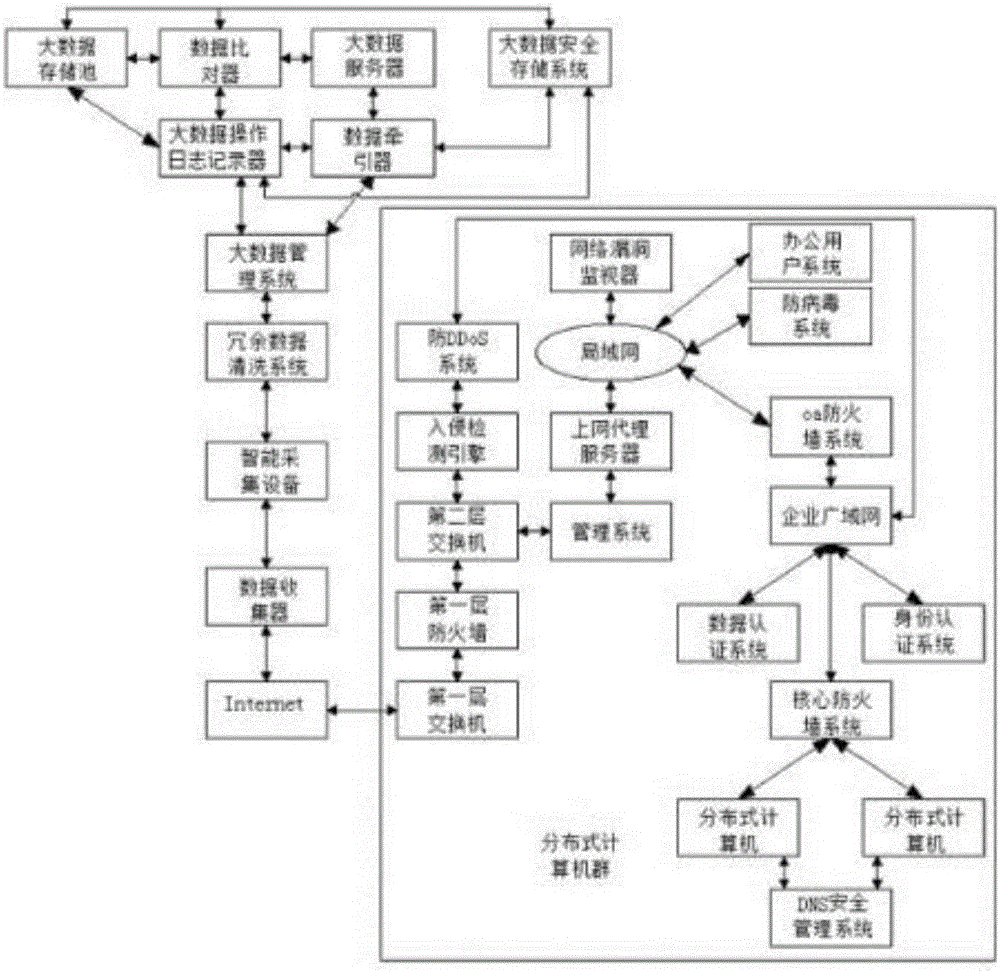
InactiveCN105871877AEnsure safetyIntegrity guaranteedTransmissionBig data securityBig data management
The invention discloses a big data implementation system and method based on network security. A big data processing platform and a distributed computer group connected with the big data processing platform are arranged. The big data processing platform is internally provided with a data collector, an intelligent acquisition device, a redundant data cleaning system, a big data management system, a data traction device, a big data server, a data comparator, a big data storage pool, a big data operation log recorder and a big data secure storage system. The big data server transmits small class big data into the big data storage pool to be stored through the data comparator with the hardware security protection function, and in the process that the small class big data is uploaded to the big data storage pool through the data comparator, the data comparator calls data stored in the big data security storage system to be compared with the small class big data which is uploaded. Cost investment is reduced, the level of data security transmission can be further improved, and integrity of data is ensured during uploading or issuing.
Owner:云神科技投资股份有限公司
Geological disaster monitoring data transmission method and system, electronic equipment and storage medium
InactiveCN113038562AResolve detectionSolve the problem of selectivityTransmission systemsParticular environment based servicesGeneral Packet Radio ServiceDisaster monitoring
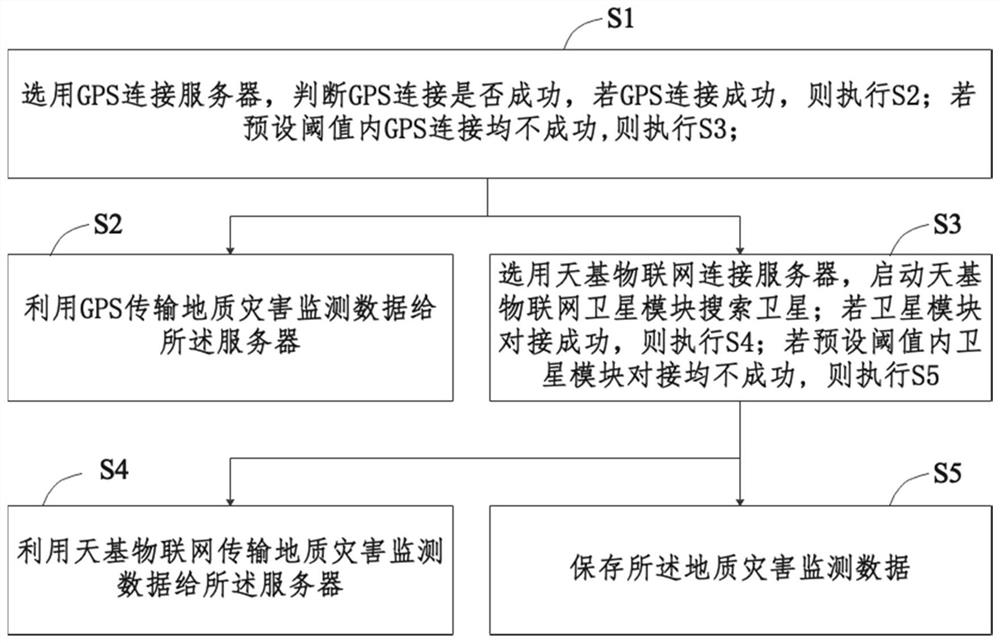
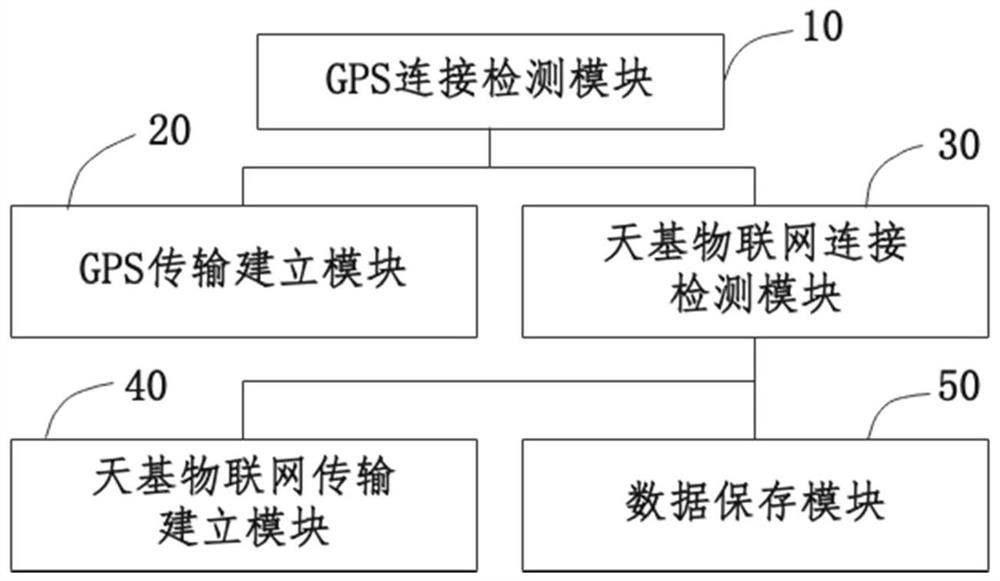
The invention provides a geological disaster monitoring data transmission method and system, electronic equipment and a storage medium, and the method comprises the steps: S1, selecting a GPRS connection server, judging whether the GPRS connection is successful, and if the GPRS connection is successful, executing S2; if the GPRS connection is not successful within the preset threshold value, executing S3; S2, transmitting the geological disaster monitoring data to the server by using GPRS (General Packet Radio Service); S3, selecting the space-based Internet of Things to be connected with the server, and starting a space-based Internet-of- Things satellite module to search satellites; if the satellite modules are successfully docked, executing S4; if the docking of the satellite modules is not successful within the preset threshold value, executing S5; S4, geological disaster monitoring data are transmitted to the server through the space-based Internet of Things; and S5, storing the geological disaster monitoring data. According to the invention, safe transmission of monitoring data under different network conditions can be guaranteed, and mutual intelligent switching of two communication modes is supported.
Owner:中国地质环境监测院
Integrated data census system and census method based on mobile Internet
ActiveCN107315774BRealize full path grid data censusEnsure secure transmissionDatabase distribution/replicationGeographical information databasesData ingestionPrimary station
Owner:STATE GRID CORP OF CHINA +1
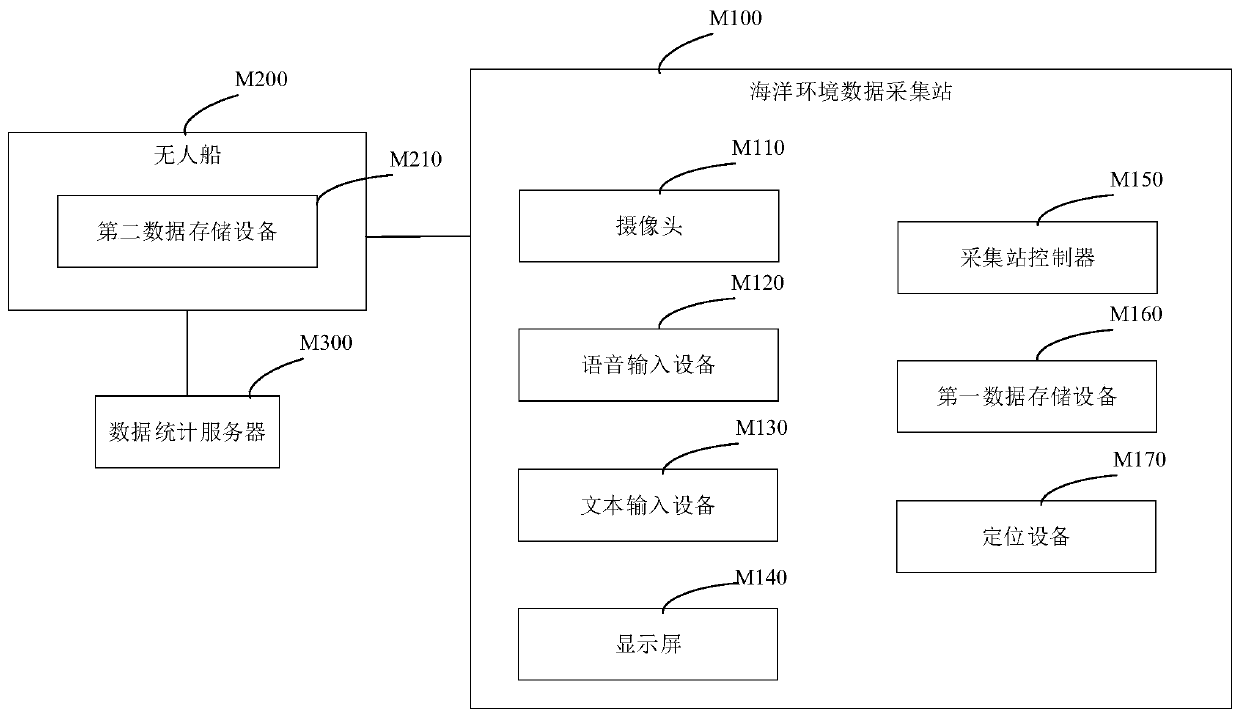
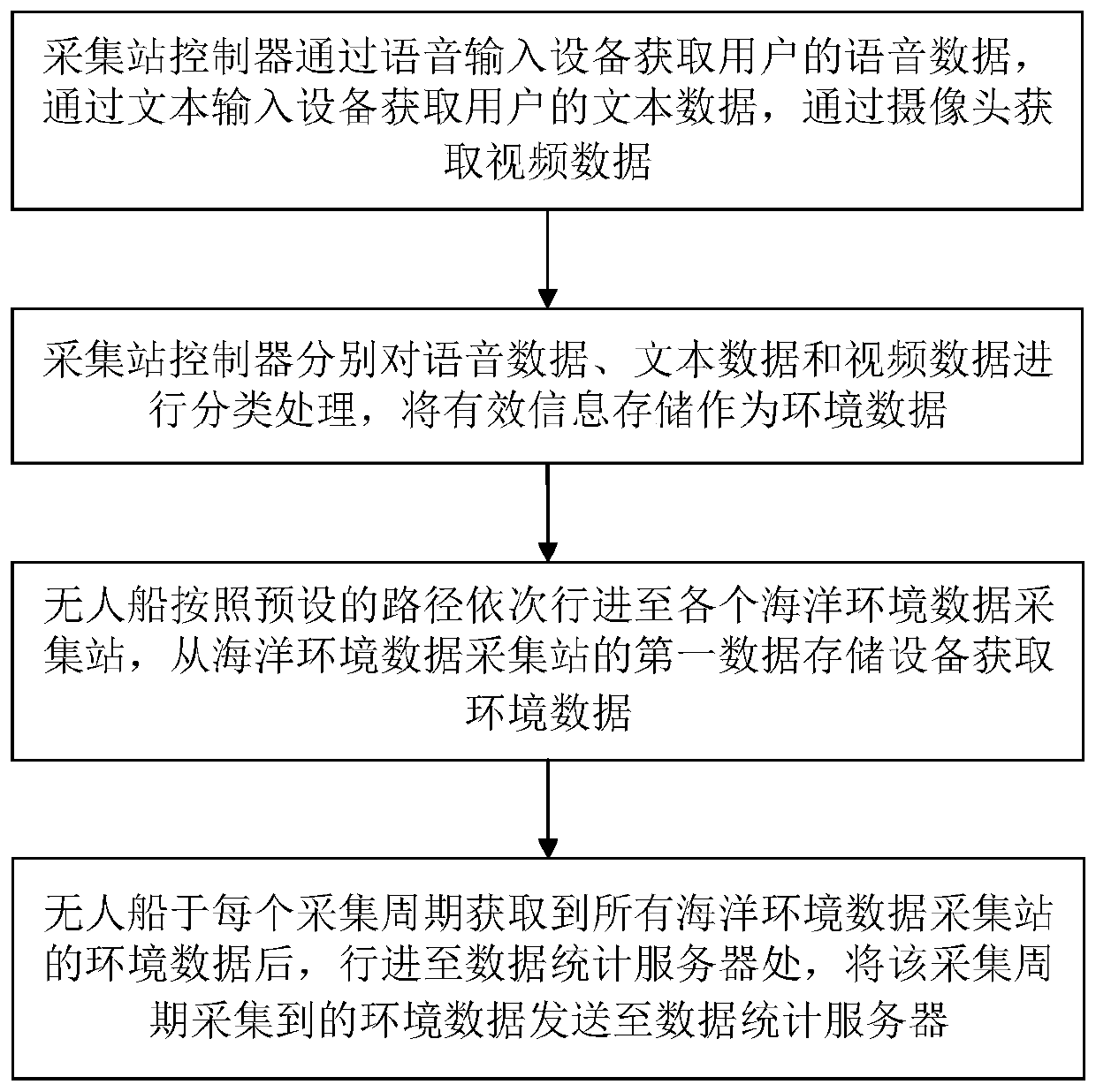
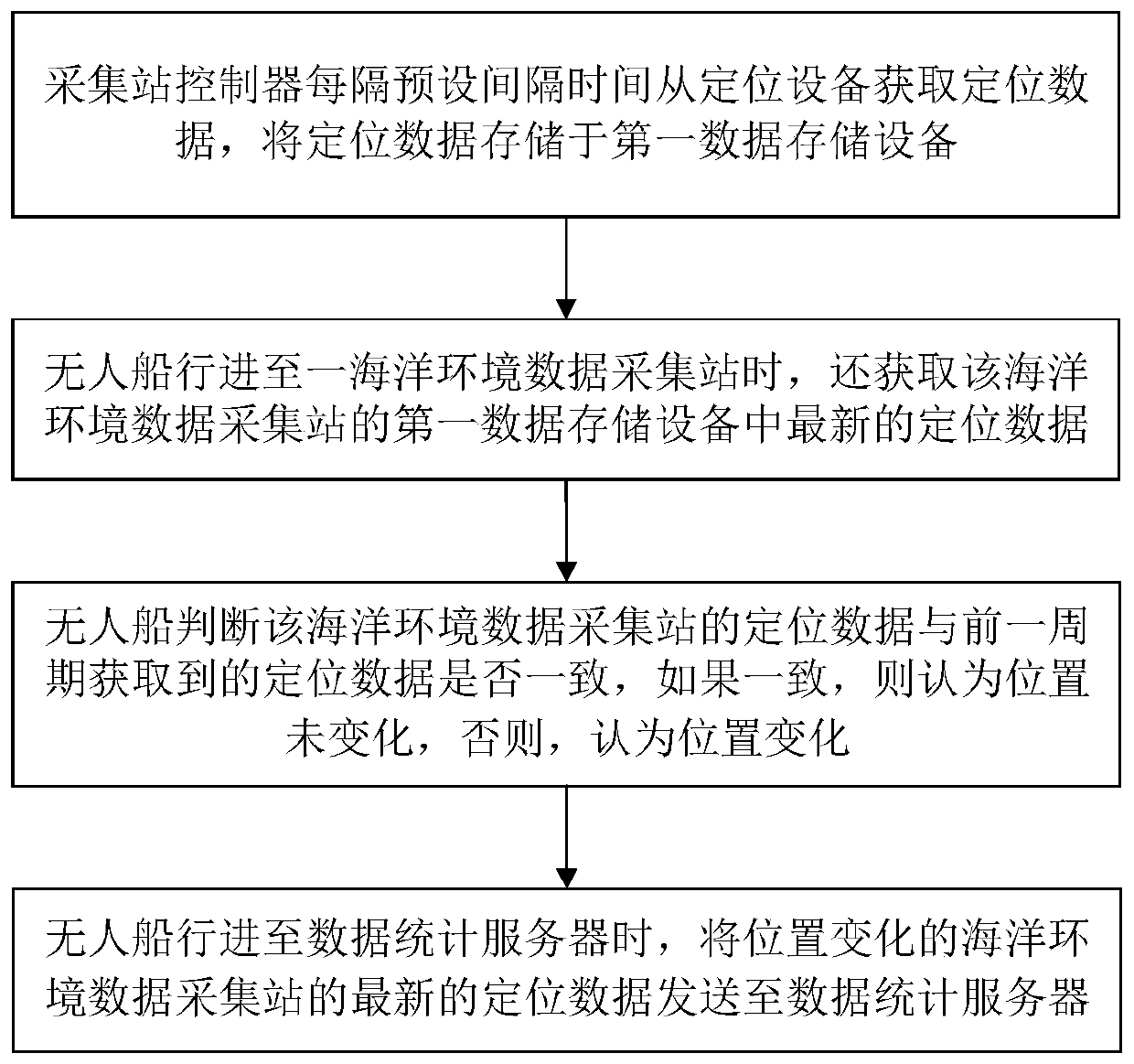
Multi-modal marine environment data fusion acquisition system and method
ActiveCN110674245AImprove collection efficiencyIncrease transfer rateMetadata text retrievalData processing applicationsData acquisitionEngineering
The invention relates to a multi-modal marine environment data fusion acquisition system and method. The multi-modal marine environment data fusion acquisition system comprises a plurality of marine environment data acquisition stations, an unmanned ship and a data statistics server, wherein the marine environment data acquisition stations are distributed at marine data acquisition points, and thedata statistics server stores acquisition positions of the marine data acquisition points and ID numbers of the corresponding marine environment acquisition stations; the marine environment acquisition station comprises a camera, a voice input device, a text input device, a display screen, an acquisition station controller and a first data storage device; the camera is arranged on a rotating support, and the rotating support drives the camera to continuously rotate according to a preset rotating speed, and the camera collects video data, and the voice input device is used for collecting voicedata of a user; and the text input device is used for collecting text data of the user. The invention provides a multi-modal data acquisition form, capable of improving the data acquisition efficiency, and being richer in the acquired data types.
Owner:ZHOUSHAN OCEAN UNIV SCI & TECH RES INST CO LTD
Control system and control method for wet-type electrostatic dust collector of coal conveying system
PendingCN113117891AMeet the protection requirementsDoes not affect dust removal effectExternal electric electrostatic seperatorElectric supply techniquesThermodynamicsControl system
The invention relates to a control system and a control method for a wet-type electrostatic dust collector of a coal conveying system. Existing electrostatic dust collectors mostly adopt a one-supporting-one design on site, that is, a set of complete dust collector control system is only used by one belt, and meanwhile, a traditional wet type electrostatic dust collector can only meet the requirement for on-site dust suppression and cannot feed back on-site conditions in the first time. The control system for the wet type electrostatic dust collector of the coal conveying system comprises a dust collector (26), an induced draft fan (23), a belt air suction cover A (24) and a belt air suction cover B (25), wherein the belt air suction cover A is connected with an A-path belt drawer type filter (1), the belt air suction cover B is connected with a B-path belt drawer type filter (2), the A-path belt drawer type filter is connected with an A-path belt electric butterfly valve (3), and the B-path belt drawer type filter is connected with a B-path belt electric butterfly valve (4). The system and the method are applied to the electrostatic dust collector.
Owner:GUANGDONG DATANG INT CHAOZHOU POWER GENERATION
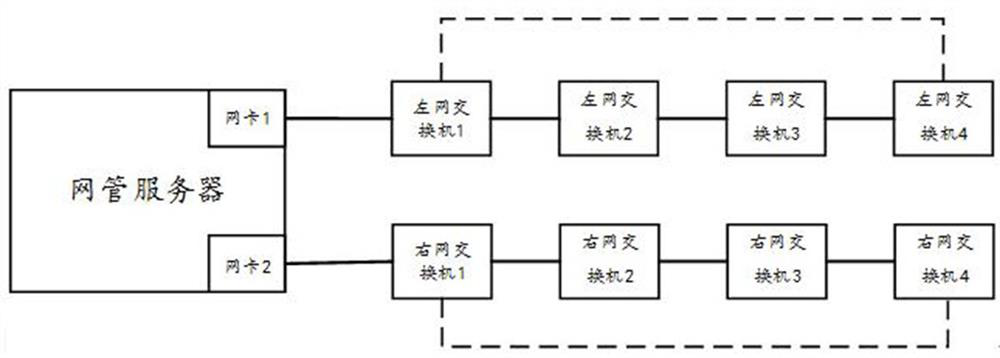
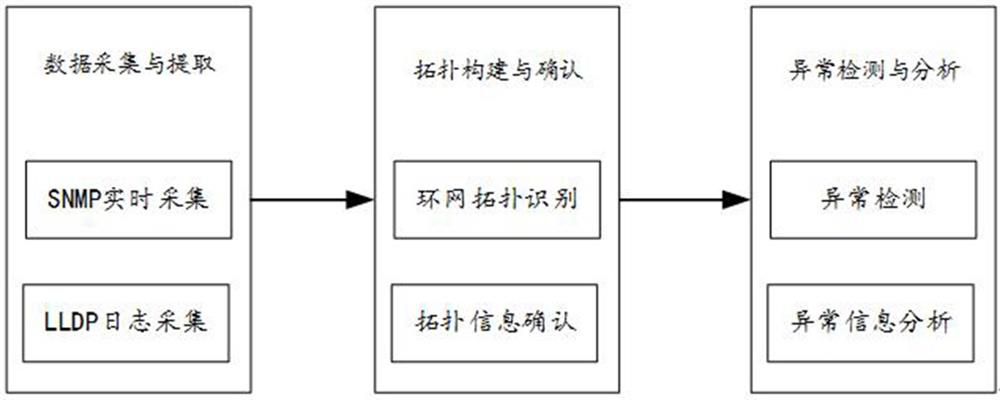
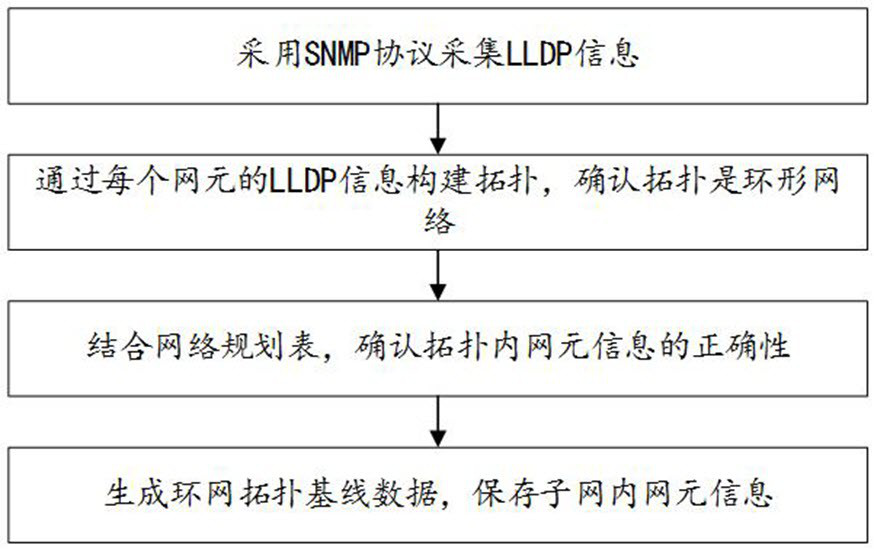
Dual-network interleaving anomaly detection method and system
ActiveCN113098725AImplementing Anomaly Interleaving DetectionReduce consumptionData switching networksHigh level techniquesBaseline dataEngineering
The invention provides a dual-network interweaving anomaly detection method and system, and the method comprises the steps: obtaining network topology baseline data of dual networks, storing the network element information of each subnetwork of the dual networks, and enabling the dual networks to be ring networks which are redundant to each other; and monitoring network element information change and producing change information, and determining whether dual-network interleaving abnormity occurs according to the change information and the network topology baseline data. Network changes are dynamically monitored based on network topology baseline data, and dynamic abnormal interleaving detection for an existing signal security data network networking scheme is achieved.
Owner:CRSC RESEARCH & DESIGN INSTITUTE GROUP CO LTD +1
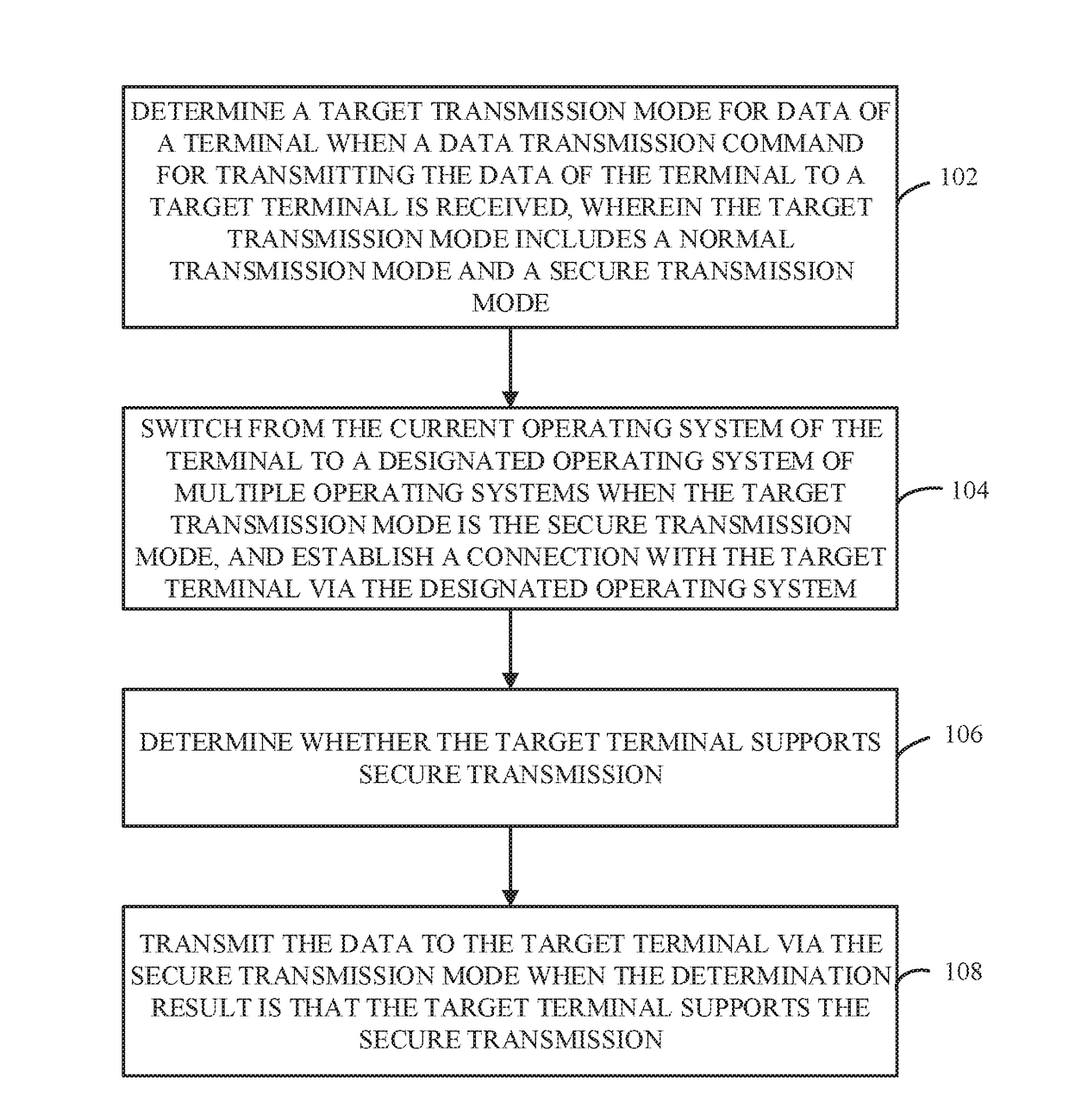
Data Transmission Method, Apparatus, and System
ActiveUS20170193242A1Malicious attack be avoidEnsure safetyConnection managementDigital data protectionData transmissionEngineering
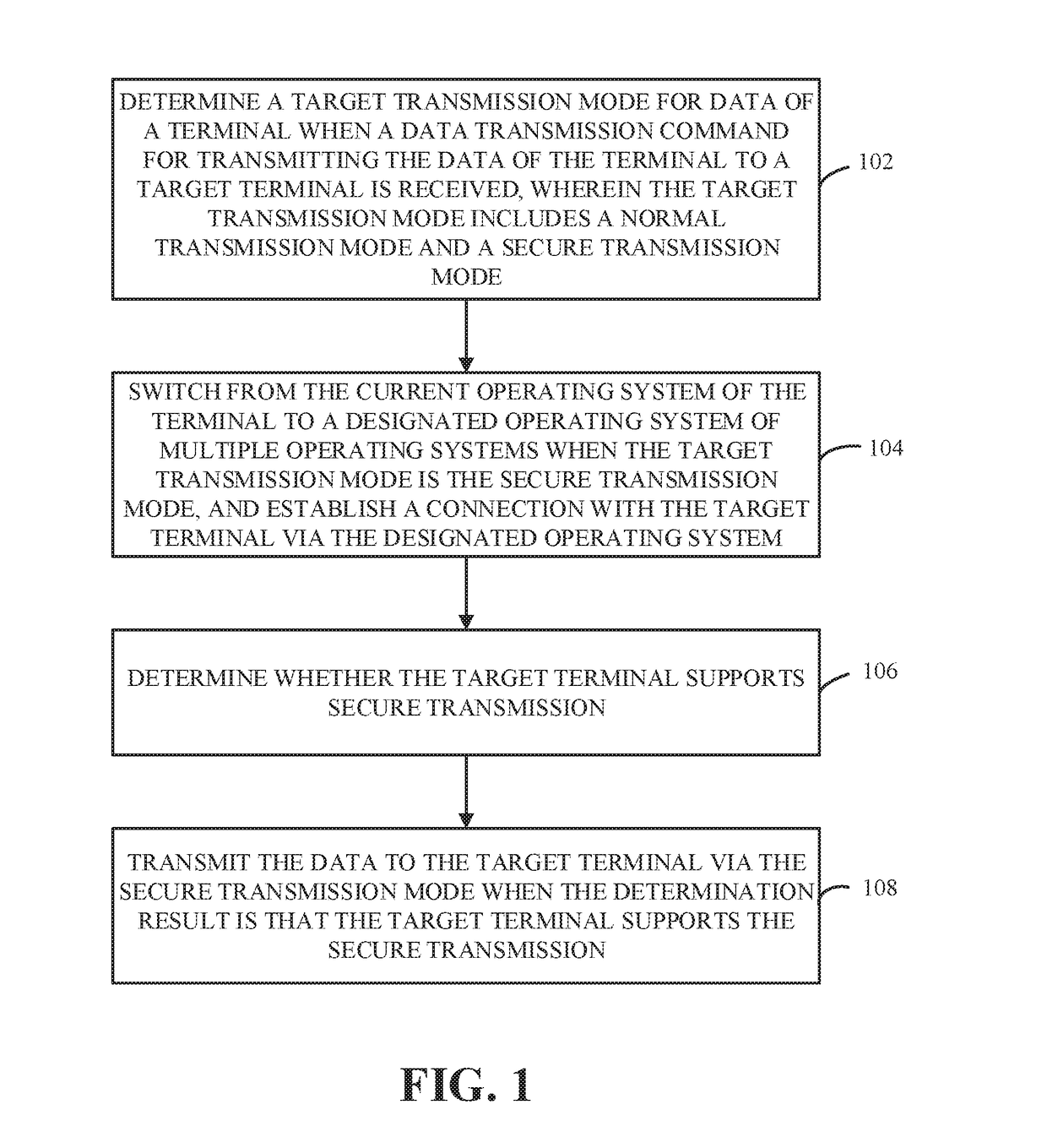
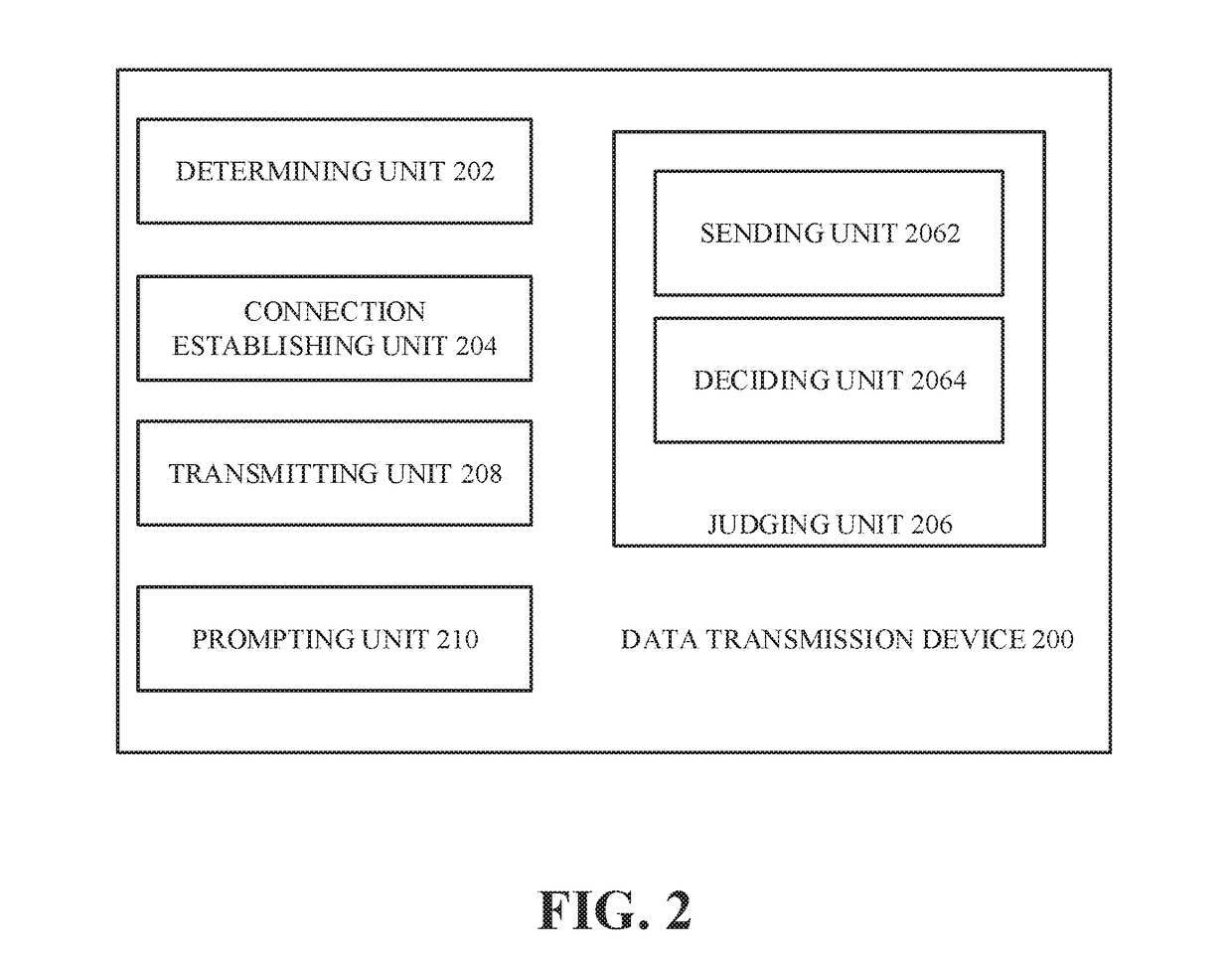
A data transmission method and a terminal include multiple operating systems, and each operating system corresponds to a transmission module. The terminal determines a target transmission mode for data of the terminal when a data transmission command for transmitting the data of the terminal to a target terminal is received, and the target transmission mode includes a normal transmission mode and a secure transmission mode. The terminal switches to a designated operating system of the multiple operating systems when the target transmission mode is the secure transmission mode, establishes a connection with the target terminal via the designated operating system, determines whether the target terminal supports secure transmission, and transmits the data to the target terminal via the secure transmission mode when the determination result is that the target terminal supports the secure transmission.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
Secure network establishment method and system based on secure module
InactiveCN108809888AGood technical effectEnsure secure transmissionEncryption apparatus with shift registers/memoriesPublic key for secure communicationClient-sideInternet security
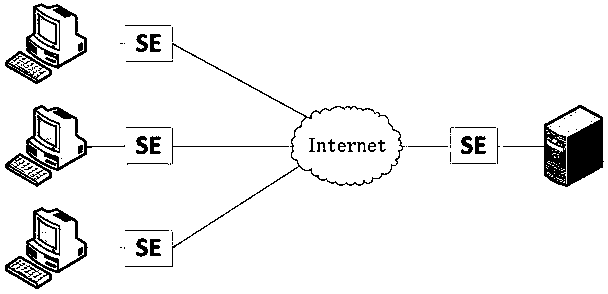
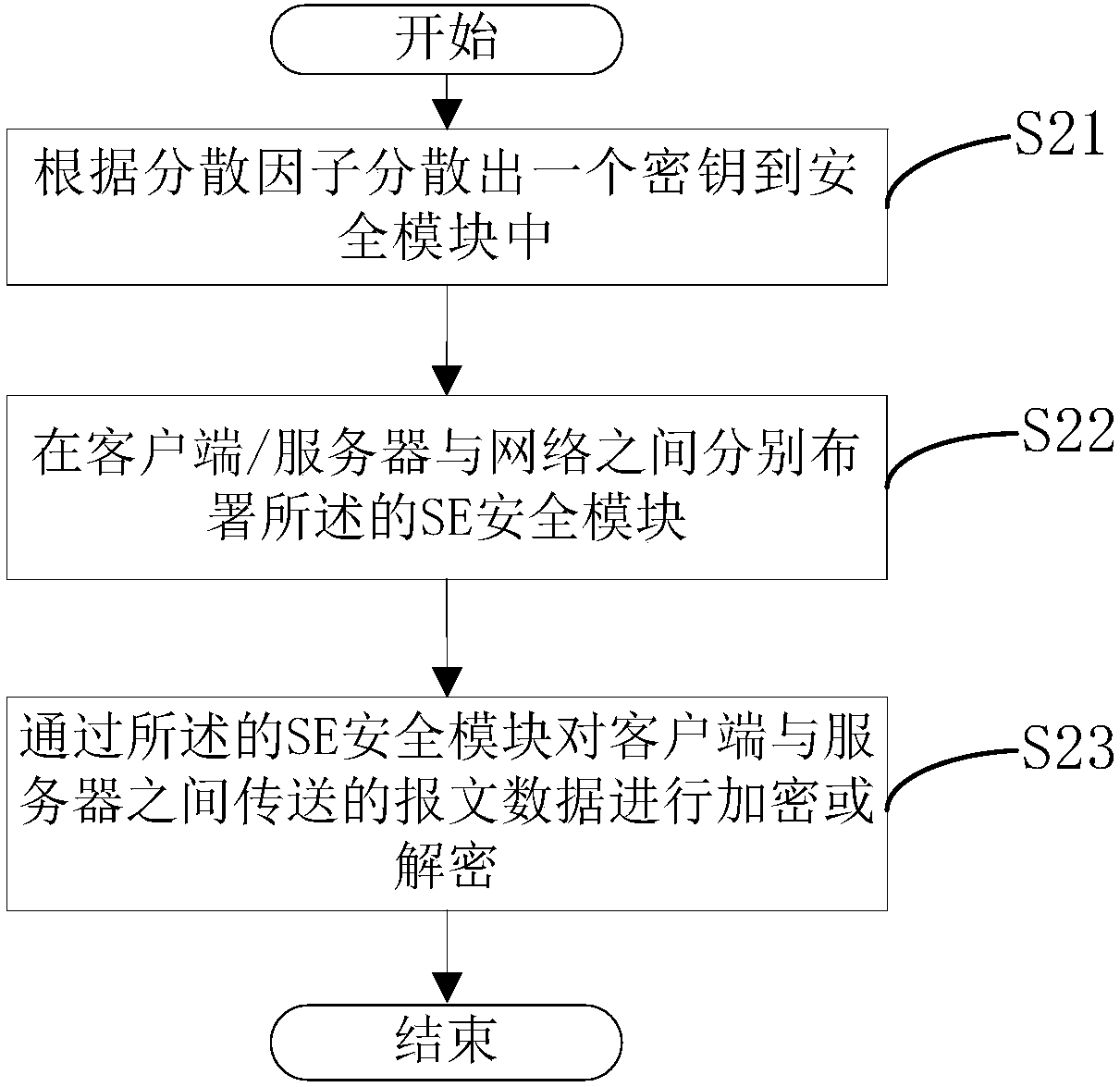
The invention relates to a secure network establishment method and system based on a secure module and belongs to the technical field of Internet security. The method provided by the invention comprises the following steps of (1), scattering a key to the secure module according to a scattering factor; (2), deploying the secure module between a client / server and a network; and (3), encrypting or decrypting message data transmitted between the client and the server through the secure module. Through adoption of the method and the system provided by the invention, on the basis of an encryption / decryption function of the secure module, the security of the data in network transmission is ensured, and the cost for establishing a transitional VPN (Visual Private Network) is reduced.
Owner:WATCHDATA SYST +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com