A full-duplex cooperative scrambling secure transmission method based on optimal user selection of a direct path
A direct path, safe transmission technology, applied in the direction of transmission system, interference to communication, radio transmission system, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
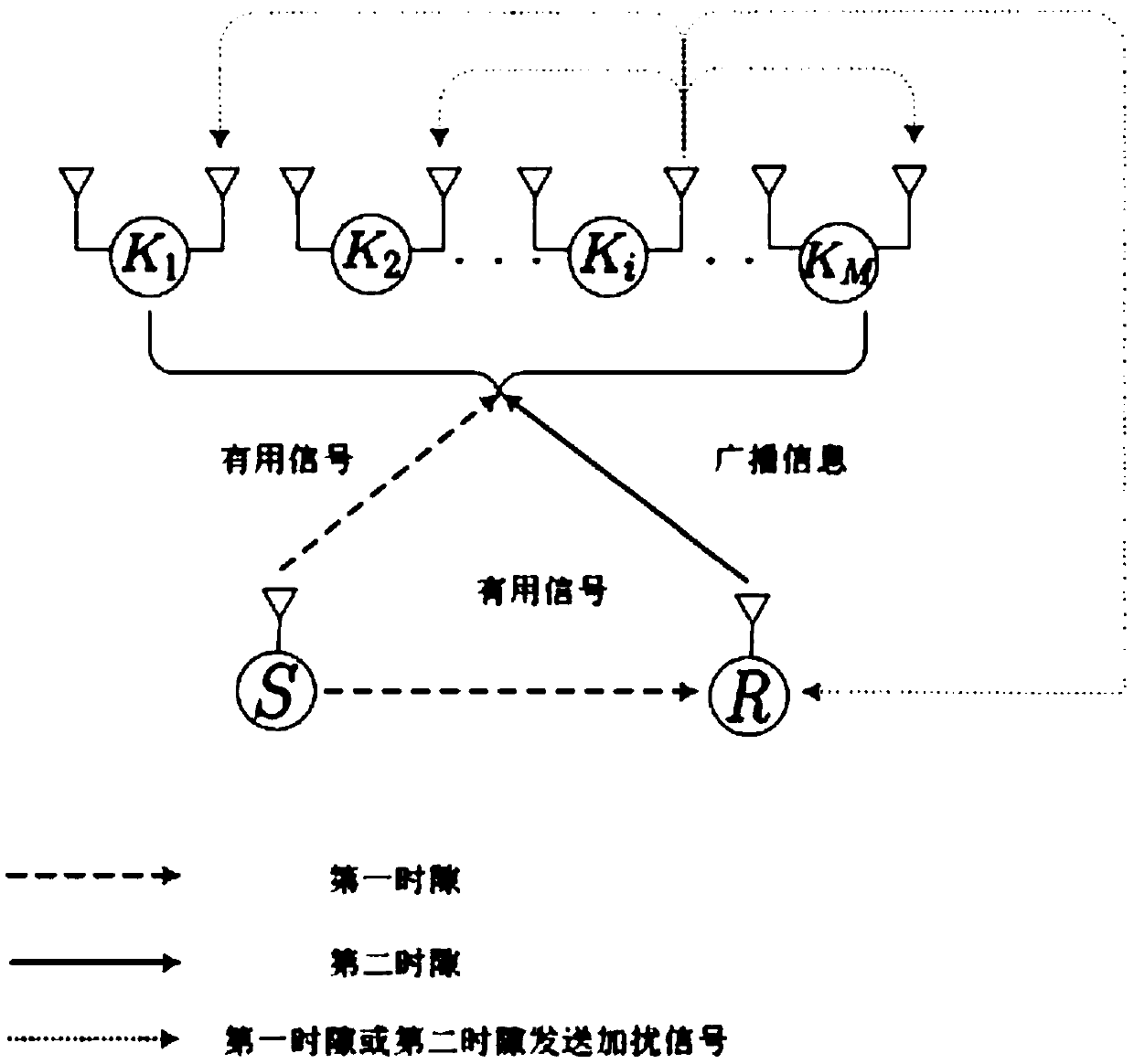
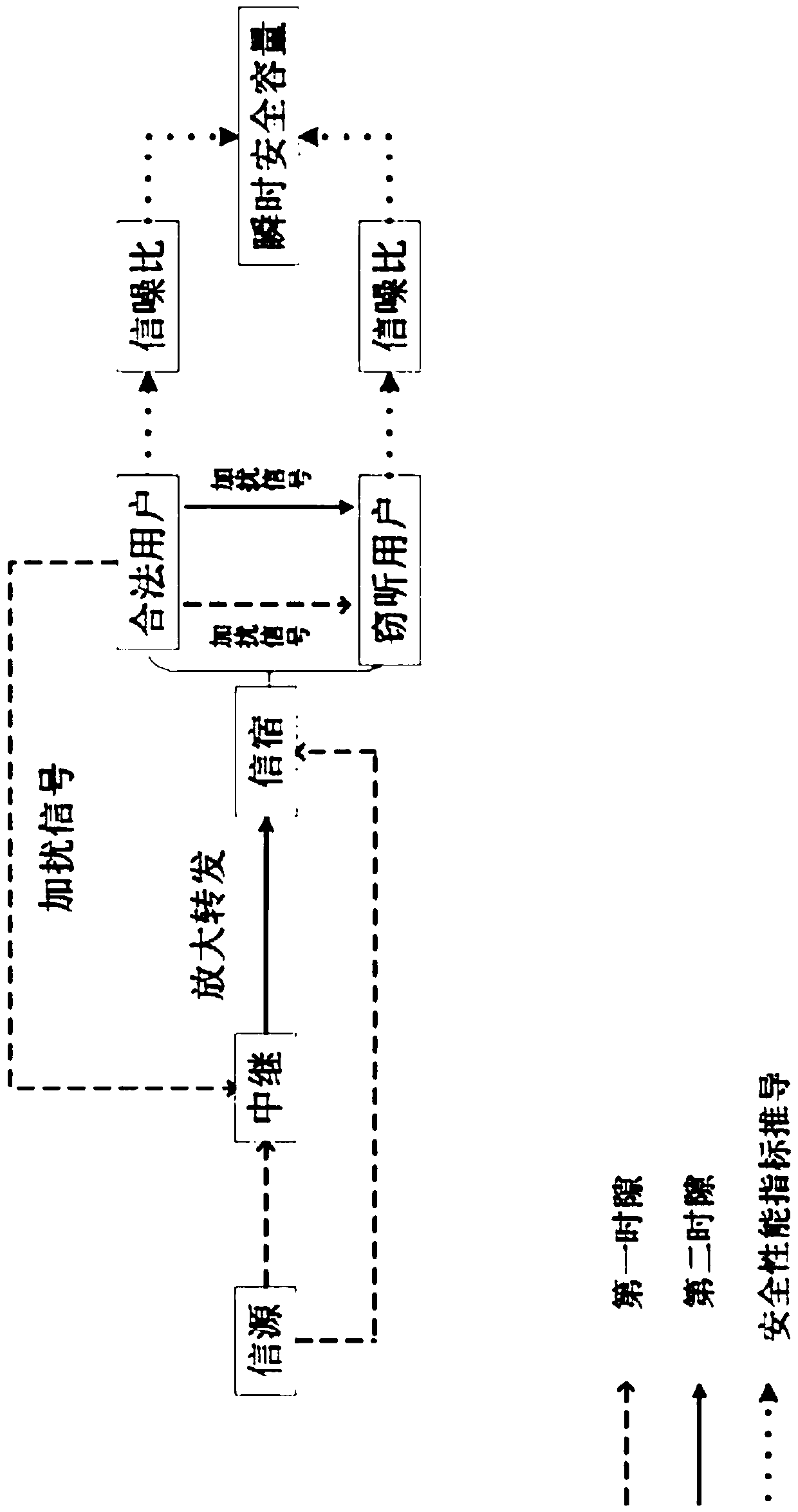
[0048] Such as figure 1 with figure 2 As shown, the present invention discloses a full-duplex cooperative scrambling secure transmission method based on the optimal user selection of the direct path, which is applied to a multi-user relay network, and the multi-user relay network includes a source node, a relay node and multiple destination user nodes (sinks), all nodes are single-antenna, and the relay node is a passive node, the destination user node adopts full-duplex working technology, and there is a direct path.
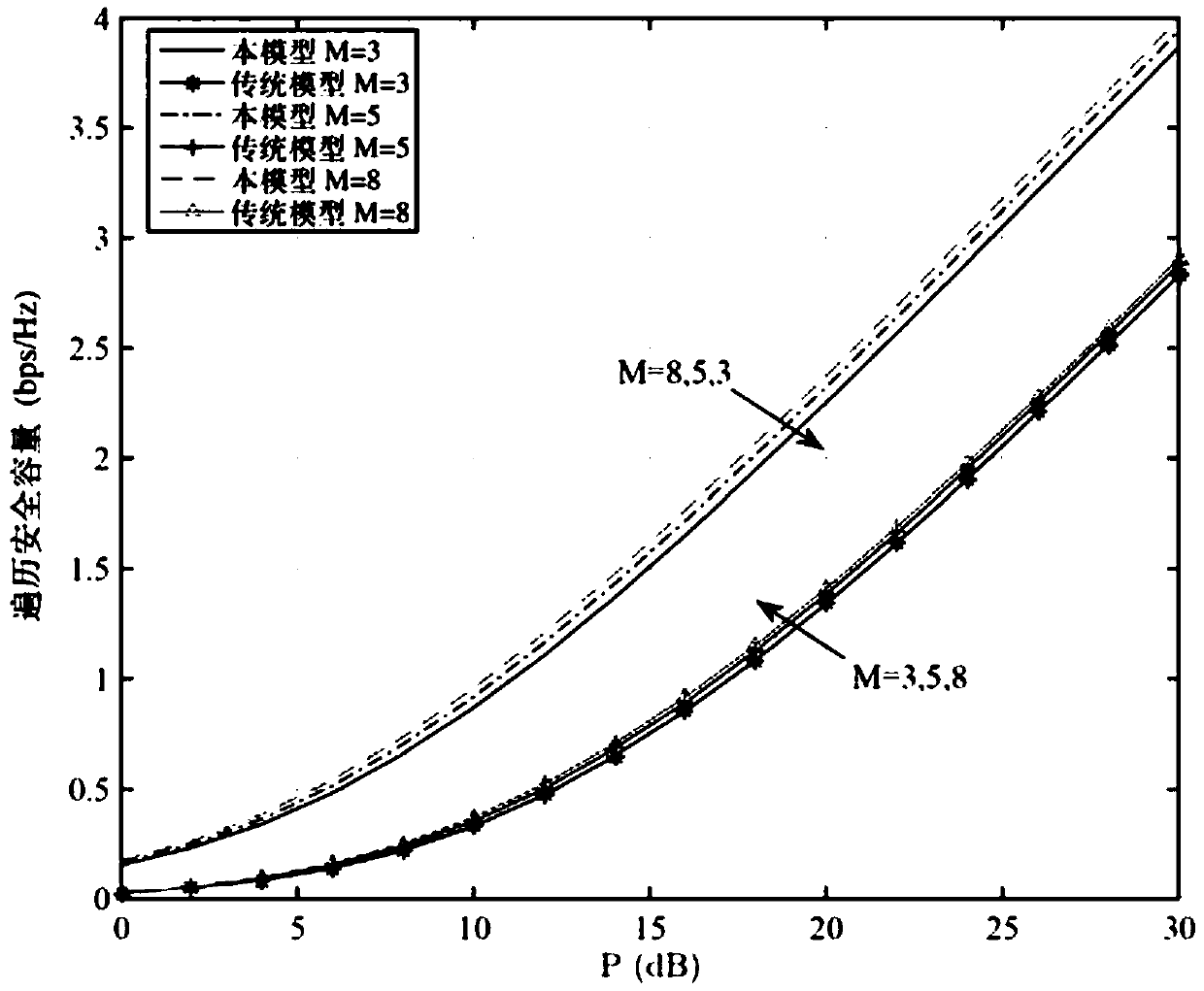
[0049] The entire secure transmission process of information is divided into two time slots. In the first time slot, the source node sends information to the relay node and the destination user node, and at the same time selects a user with the largest receiving signal-to-noise ratio from all destination user nodes. Nodes are legal user nodes, and eavesdropping user nodes are eavesdropping user nodes. Since the destination node is in full-duplex mode, the le...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com