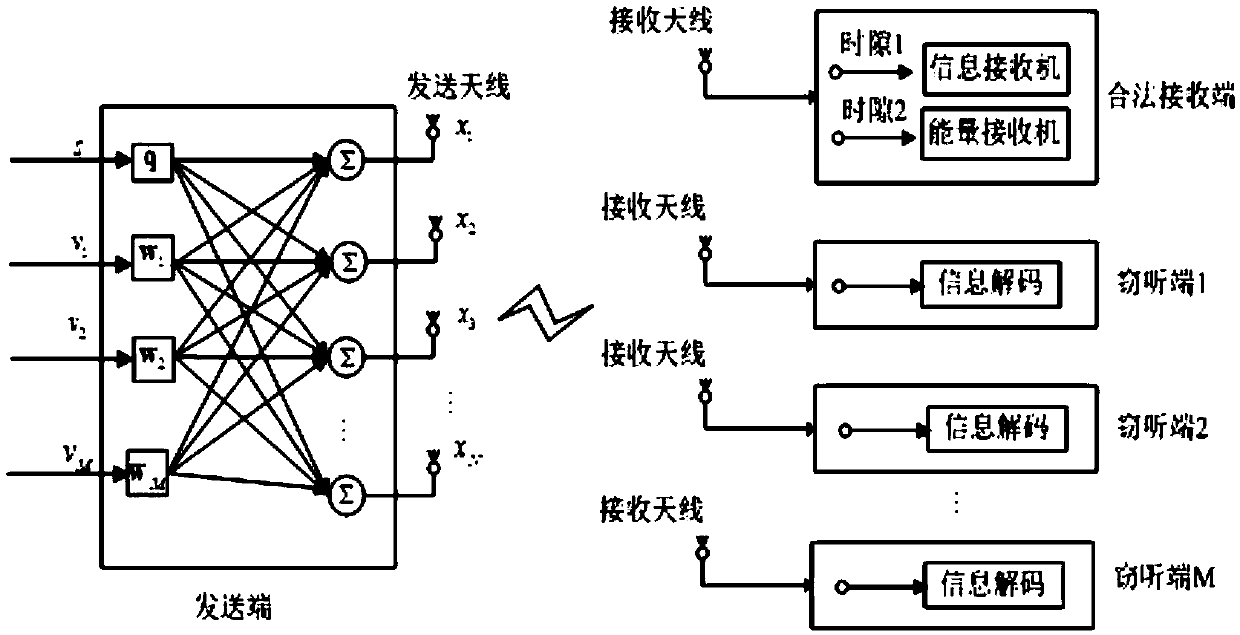
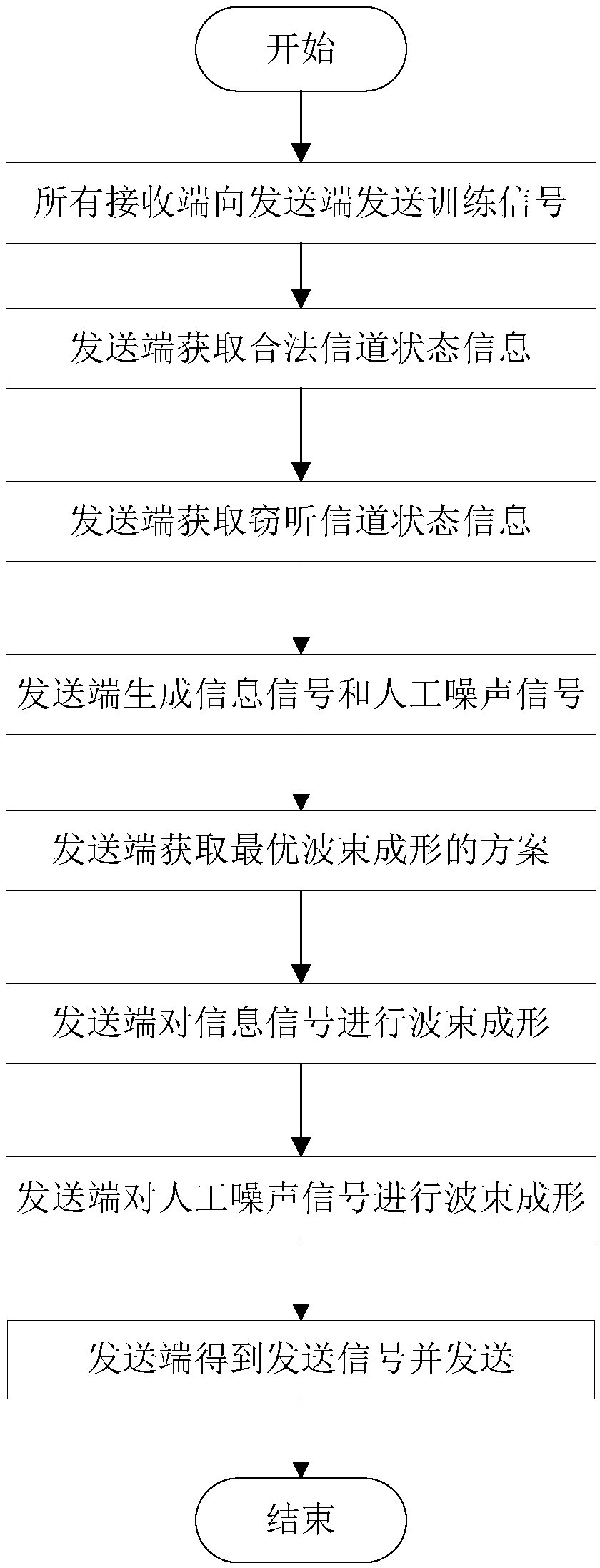
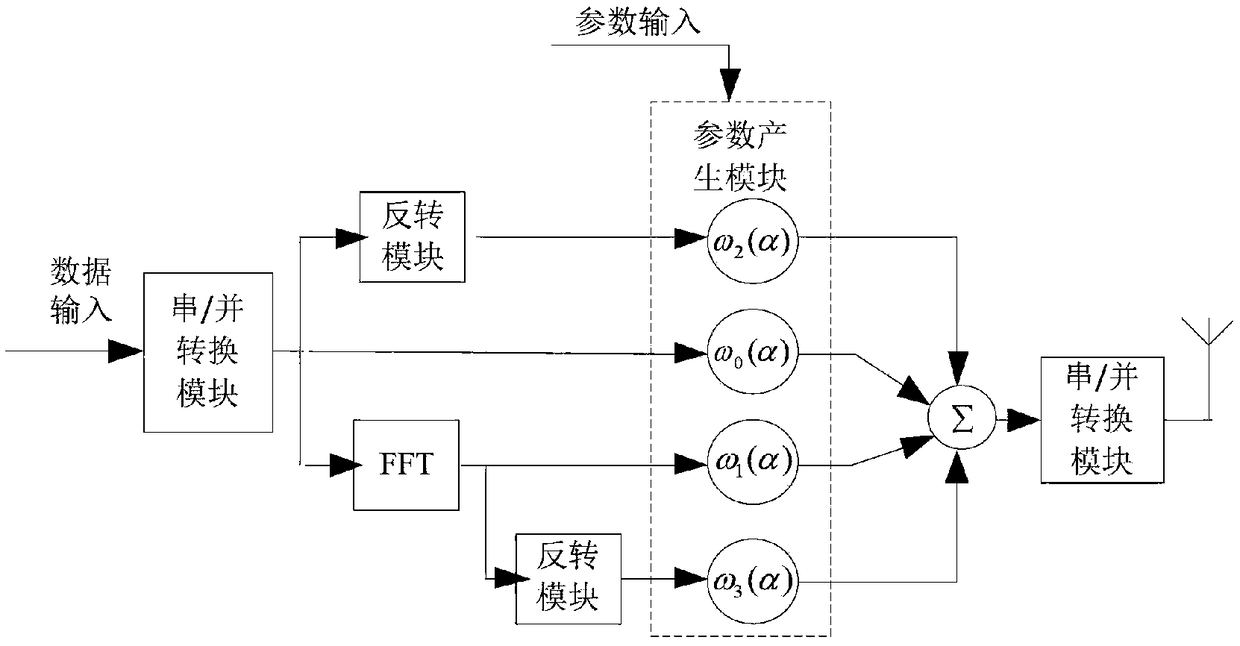
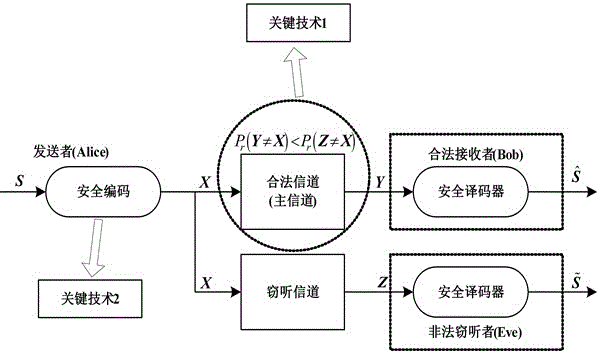
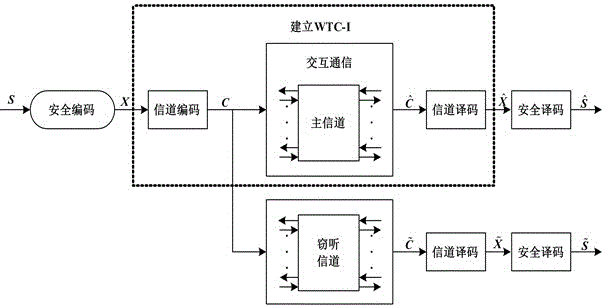
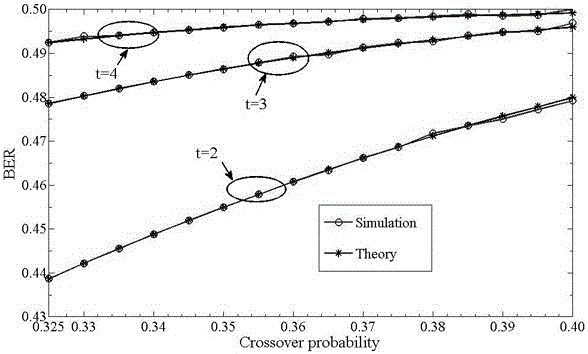
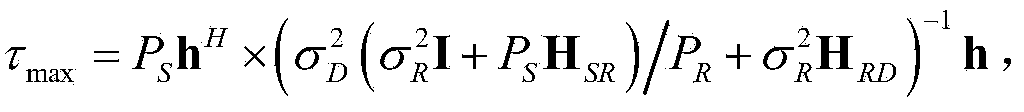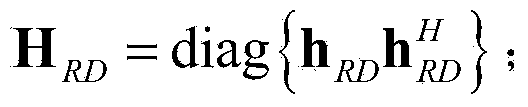Patents
Literature
47results about How to "Increase safety capacity" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
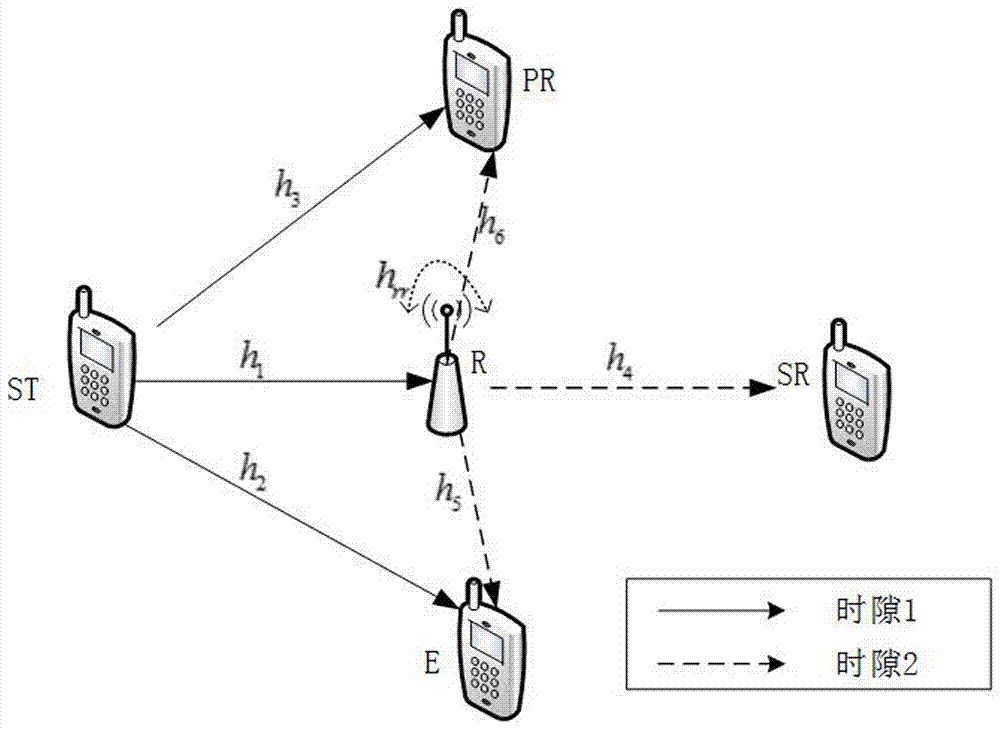
Degraded eavesdropping channel rate compatible method based on Polar code
InactiveCN103414540AIncrease safety capacityEnsure safetyError preventionEavesdroppingComputer science
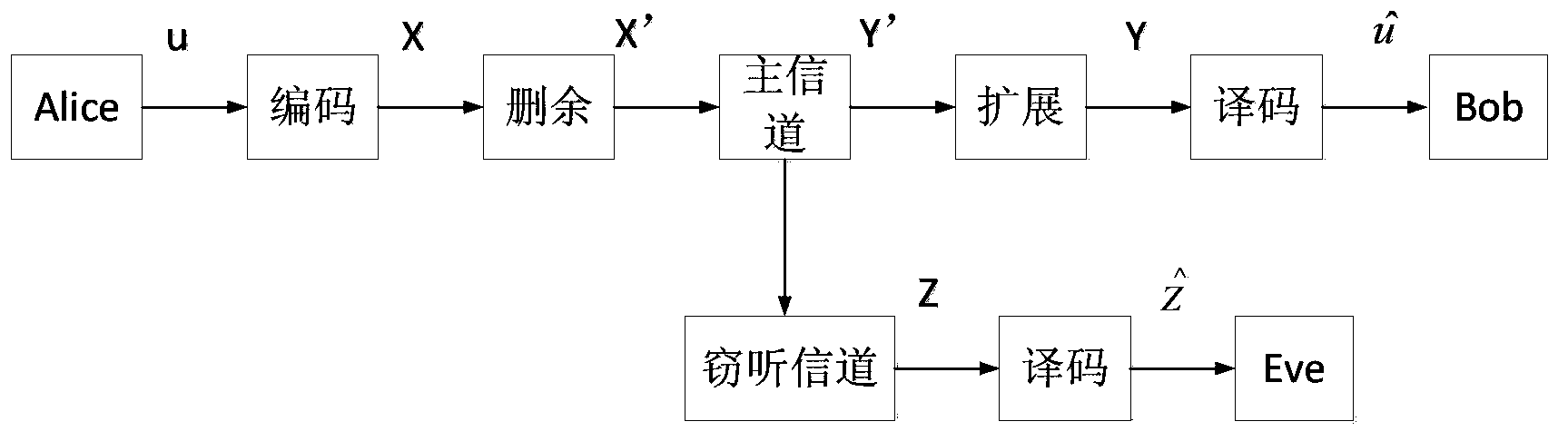
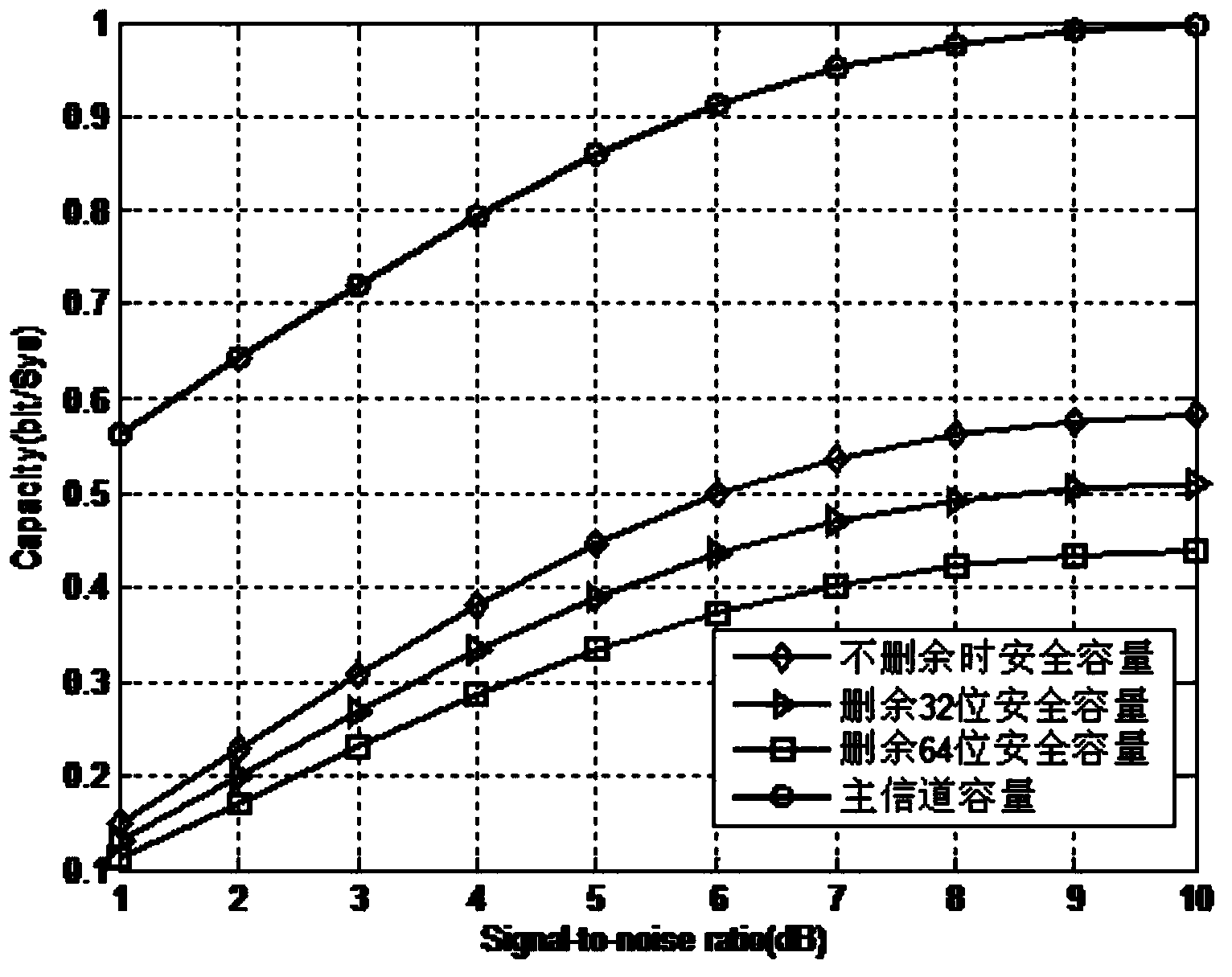
The invention discloses a degraded eavesdropping channel rate compatible method based on a punctured Polar code. According to the method, the punctured Polar code is combined with a degraded eavesdropping channel model; according to construction features of the Polar code, a safe bit-channel used for transmitting information is given; according to channel rate requirements of a degraded eavesdropping channel, a proper puncturing matrix is built, and the degraded eavesdropping channel rate compatible method based on the Polar code is achieved; because eavesdroppers do not know the puncturing matrix, the coded code word length is reduced through puncturing operation, information is hidden through the puncturing operation, the complexity that the eavesdroppers recover original information through code words received through wiretapping is increased, and system safety is guaranteed; furthermore, the puncturing method ensures that all codes in the same group of rate-compatible codes can be achieved through the same group of encoders, and therefore the complexity of emitters and receivers is greatly reduced.
Owner:NANJING UNIV OF POSTS & TELECOMM
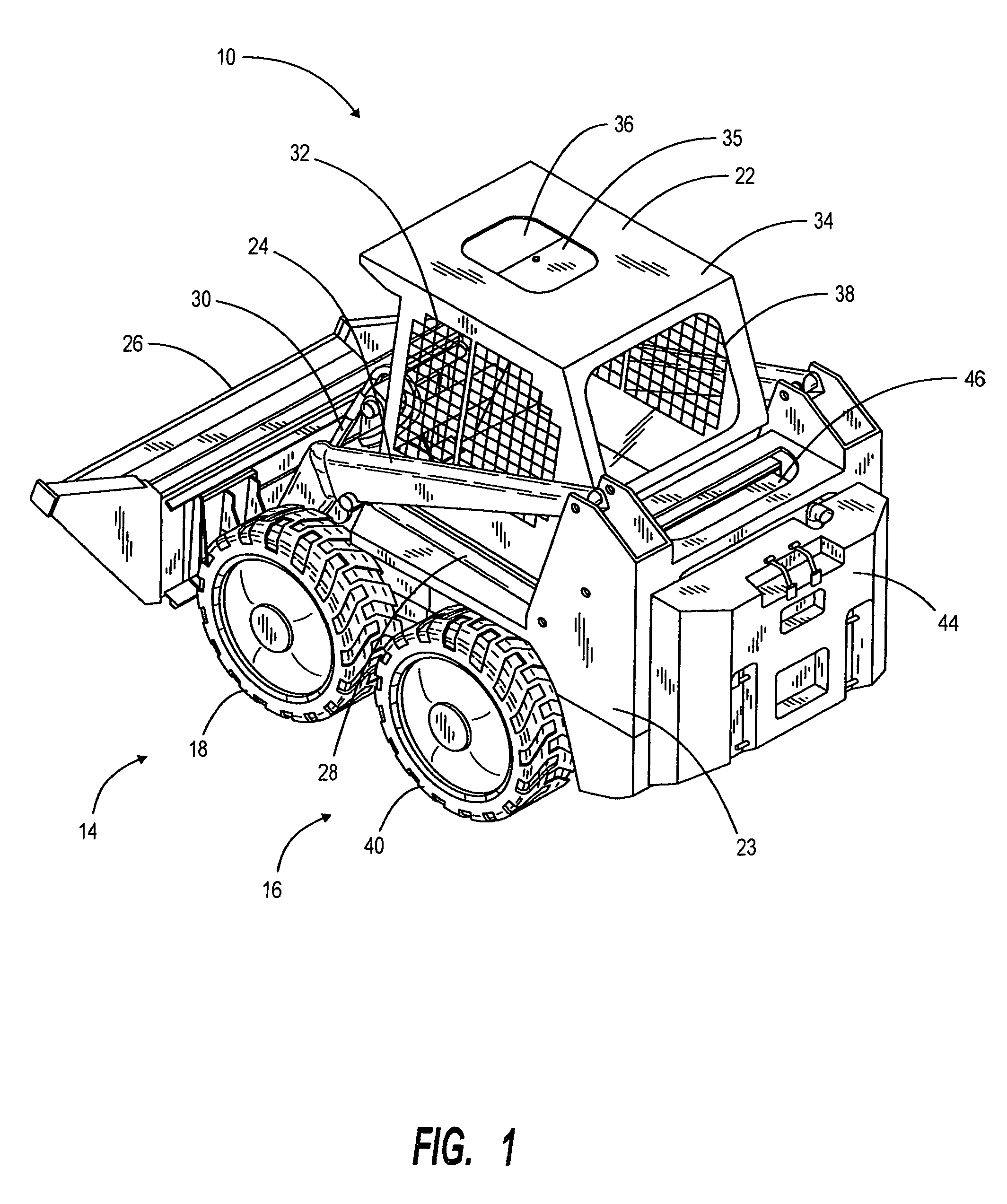
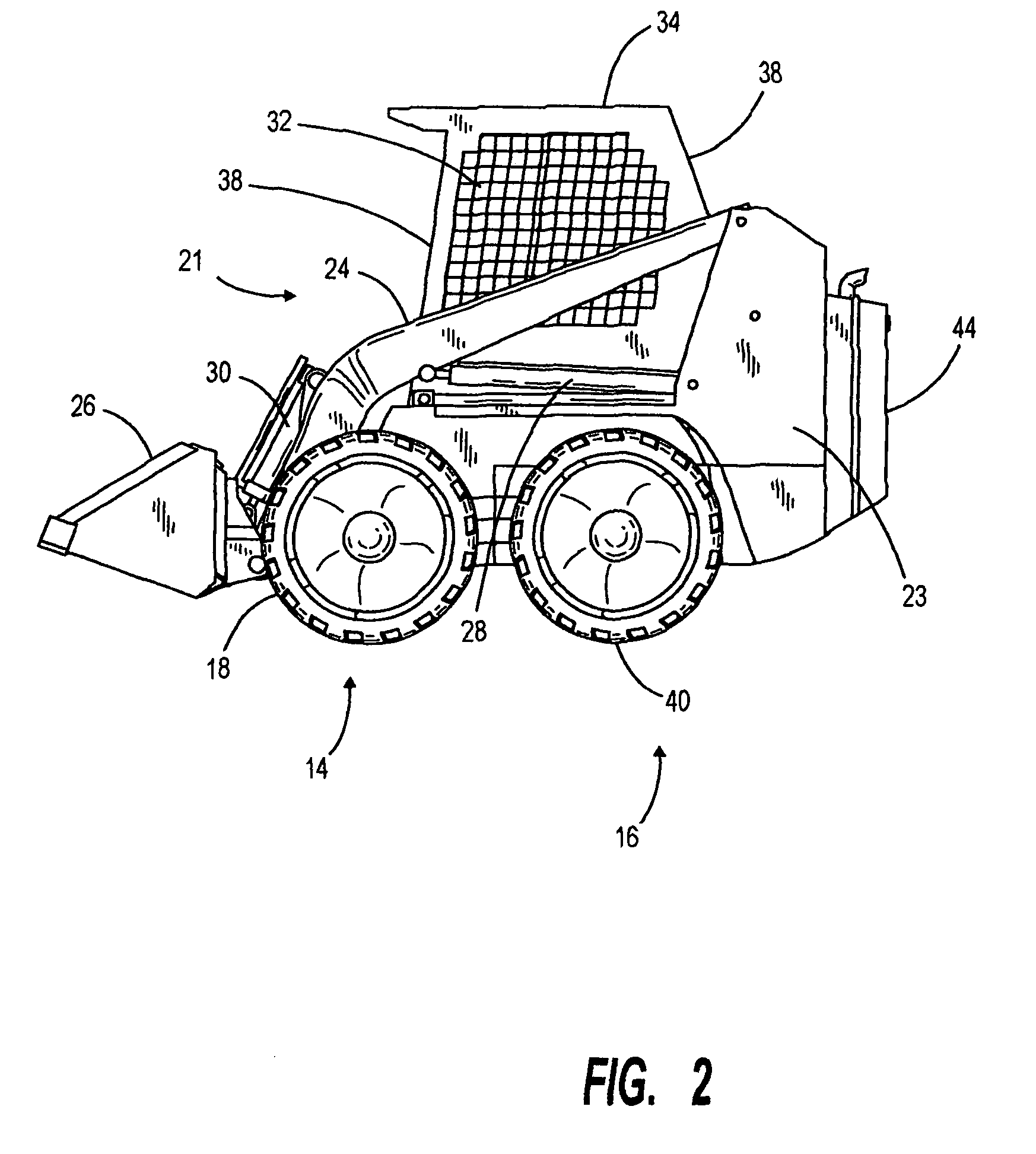
Extendable frame work vehicle
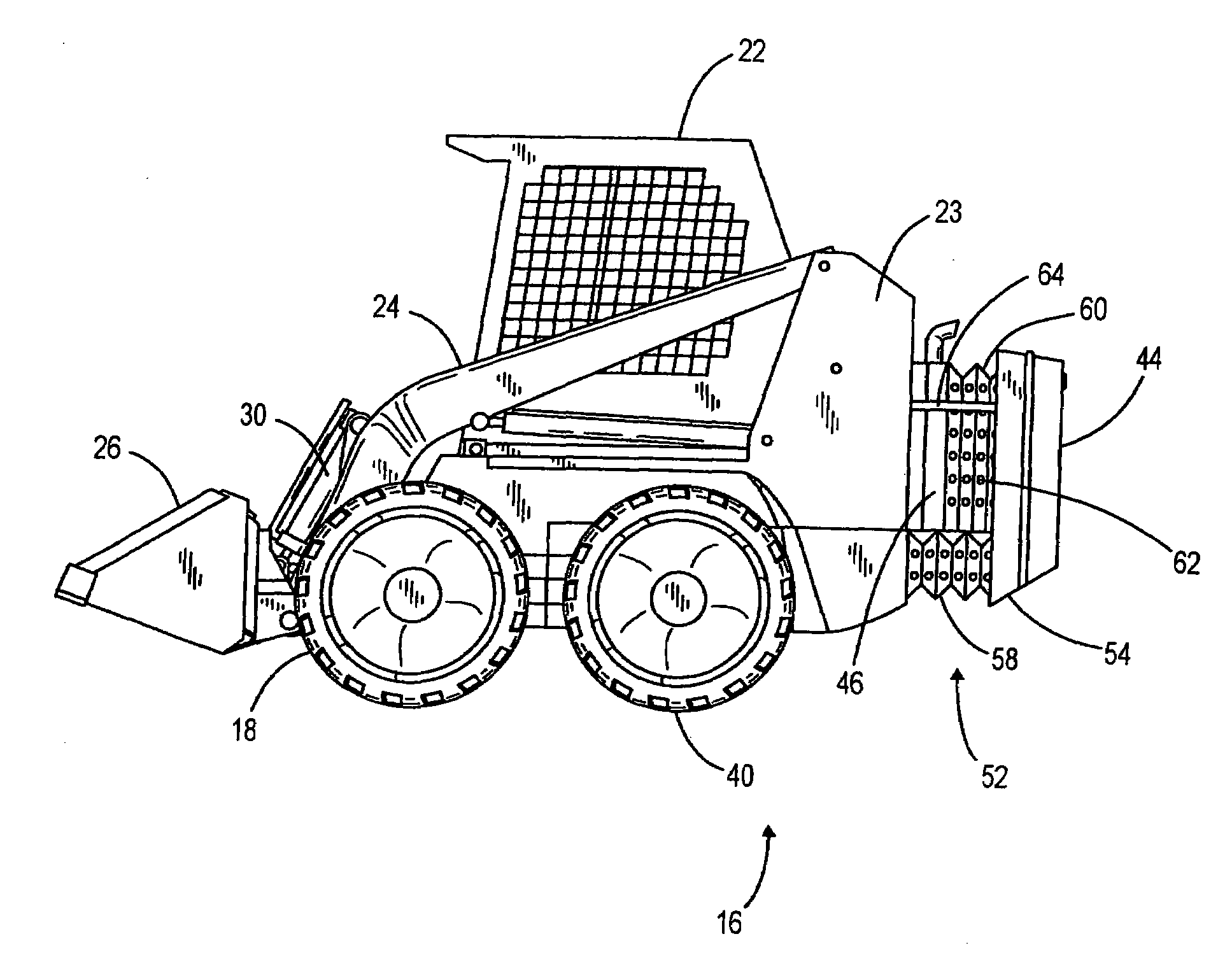
ActiveUS20090038186A1Improve versatilityImprove securitySafety devices for lifting equipmentsAuxillary drivesHydraulic motorVehicle frame
An extendable frame work vehicle offering enhanced versatility, safety and effectiveness. The vehicle includes an adjustable frame with front and rear portions that extend or retract with respect to each other. The front portion is supported by a first pair of wheels and said rear portion is supported by a second pair of wheels. Each wheel is independently driven and steered. The vehicle also includes an engine mounted on the rear portion of the frame. Incorporated into the vehicle is an electro-hydraulic assembly which enables extension and retraction of the adjustable frame. The assembly includes a sensor-responsive microprocessor controller, at least one hydraulic pump, at least one hydraulic drive motor, and at least one valve network.
Owner:EXTENDQUIP LLC
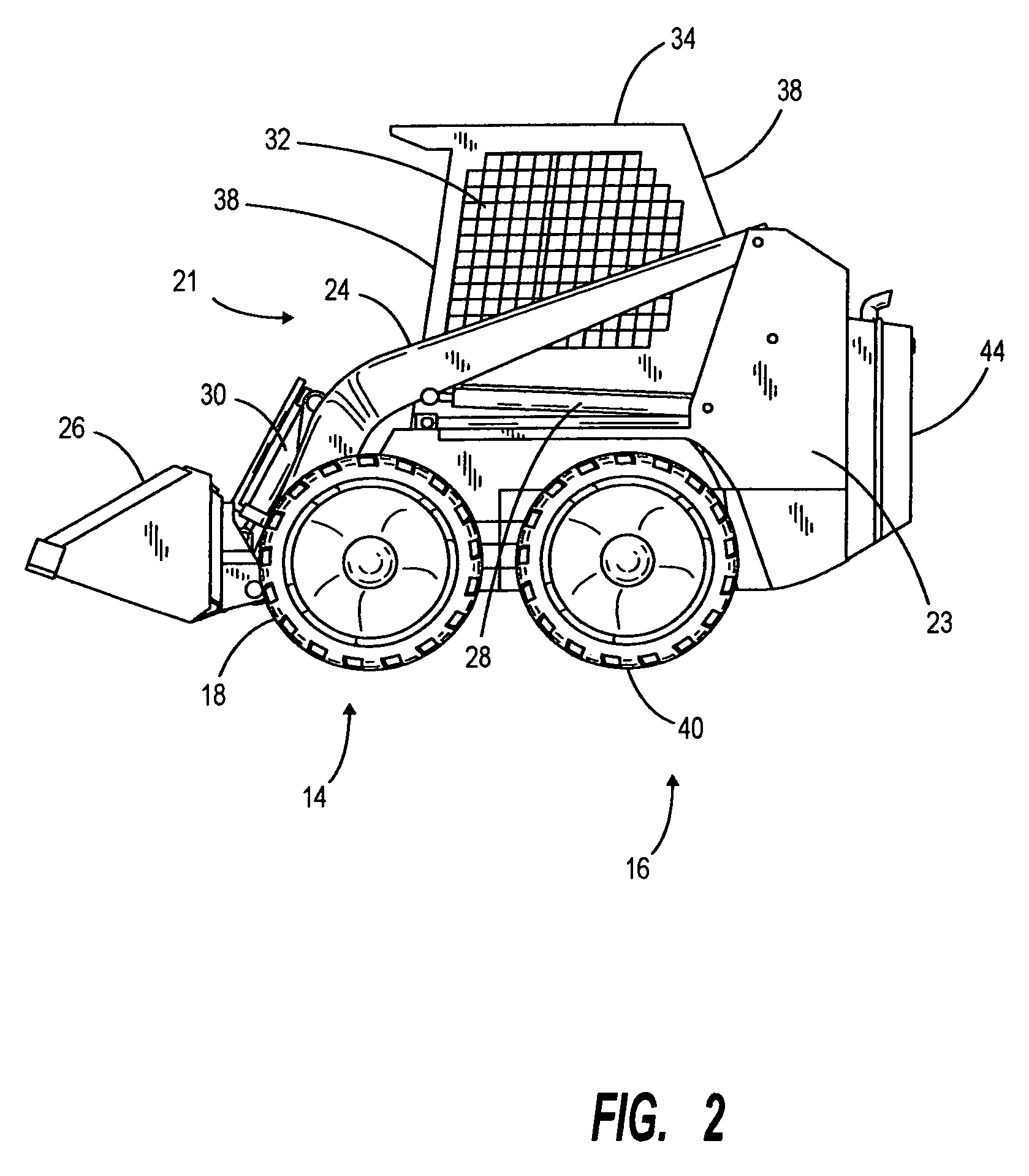
Extendable frame work vehicle having lift member movable in a true vertical fashion
ActiveUS20090206589A1Improve versatilityImprove effectivenessSafety devices for lifting equipmentsVehicle body stabilisationHydraulic motorVehicle frame
An extendable frame work vehicle offering enhanced versatility, safety and effectiveness. The vehicle includes an adjustable frame with front and rear portions that extend or retract with respect to each other. The front portion is supported by a first pair of wheels and said rear portion is supported by a second pair of wheels. Each wheel is independently driven and steered. The vehicle also includes an engine mounted on the rear portion of the frame. Incorporated into the vehicle is an electro-hydraulic assembly which enables extension and retraction of the adjustable frame. The assembly includes a sensor-responsive microprocessor controller, at least one hydraulic pump, at least one hydraulic drive motor and at least one valve network.
Owner:EXTENDQUIP LLC
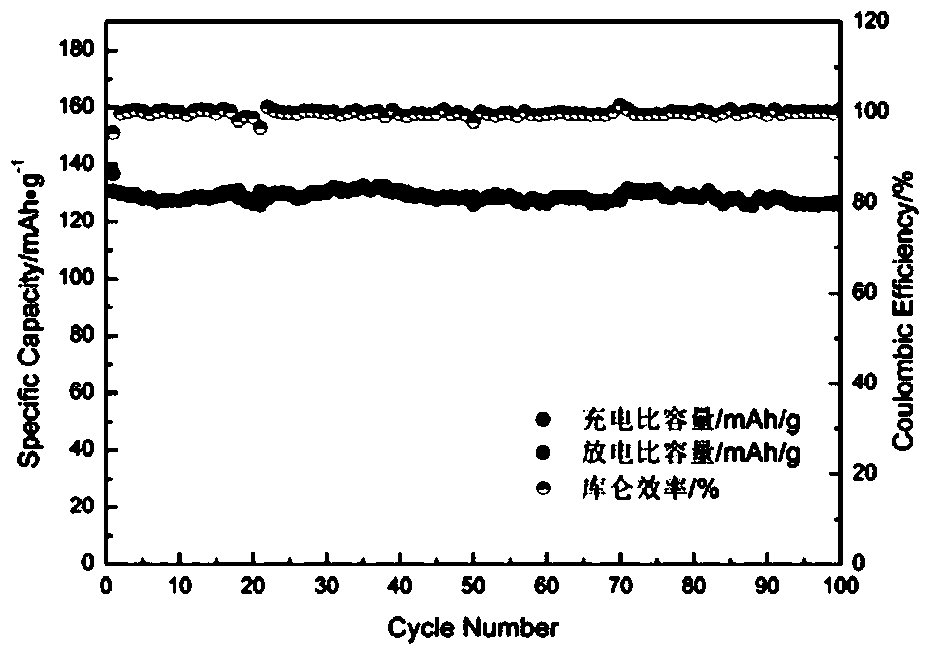
Nanostructured quasi-solid electrolyte applied to lithium ion batteries or lithium sulfur batteries and preparation method and application thereof
ActiveCN105070946AImprove conductivityImprove stabilitySolid electrolytesCell seperators/membranes/diaphragms/spacersSolid state electrolyteLithium sulfur
The invention discloses a nanostructured quasi-solid electrolyte applied to lithium ion batteries or lithium sulfur batteries and a preparation method and application thereof. The nanostructured quasi-solid electrolyte is a macro solid-state electrolyte material which is formed by an inorganic-organic hybrid framework material adsorbing ion conductive agent. The preparation method of the nanostructured quasi-solid electrolyte is as follows: in protective atmosphere, the inorganic-organic hybrid framework material is soaked in the ion conductive agent and sufficiently mixed, and redundant solvent is then volatilized. The prepared nanostructured quasi-solid electrolyte with high lithium ion conductivity can be substituted for both organic electrolyte and diaphragms in conventional lithium ion batteries, and thereby safety problems caused by the leakage of the organic electrolyte can be effectively prevented; a lithium battery assembled from the electrolyte can use a metal lithium plate as a cathode.
Owner:CENT SOUTH UNIV
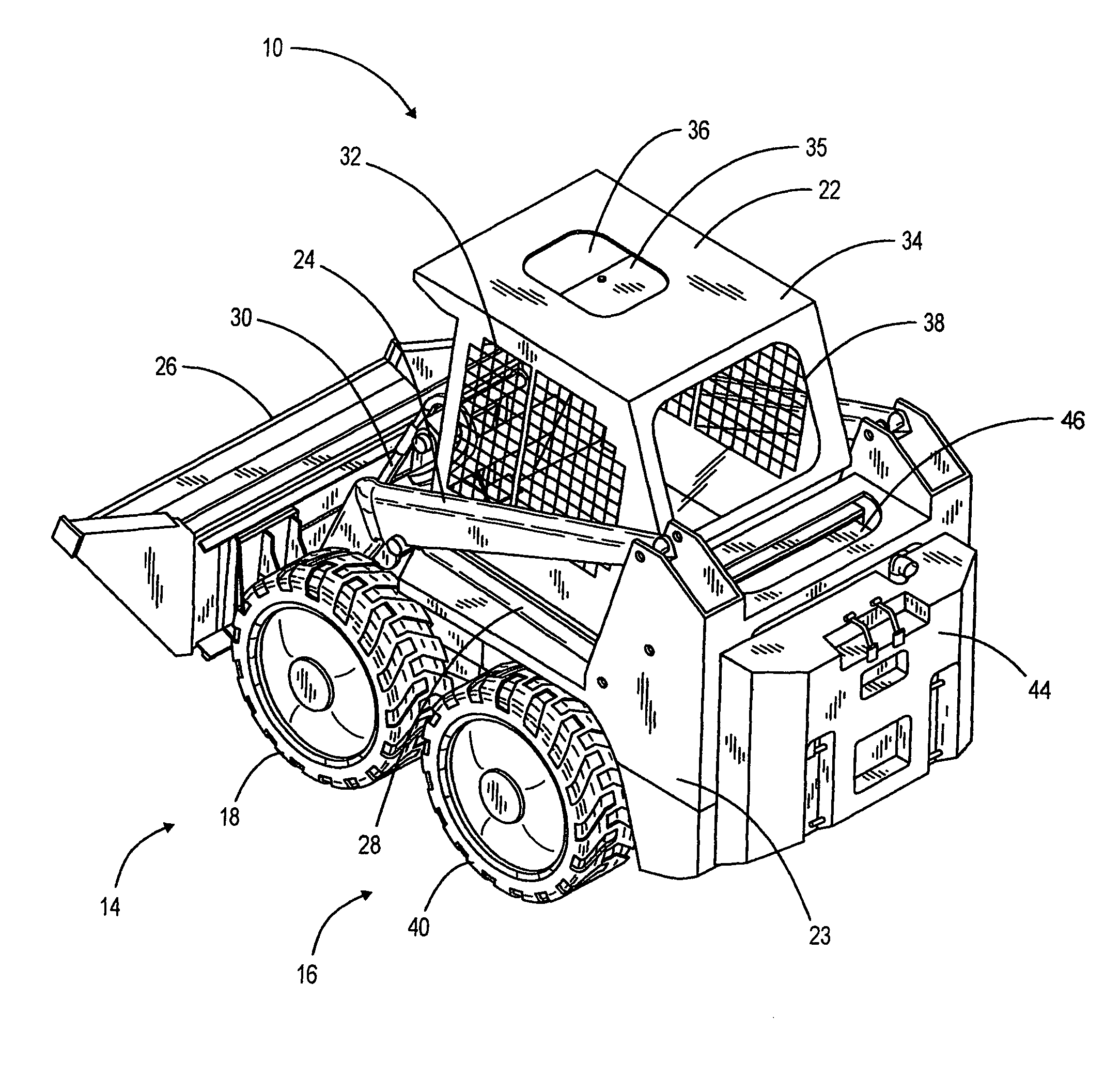
Extendable frame work vehicle having lift member movable in a true vertical fashion
ActiveUS8103418B2Improve effectivenessImprove securitySafety devices for lifting equipmentsVehicle body stabilisationVehicle frameHydraulic pump
An extendable frame work vehicle offering enhanced versatility, safety and effectiveness. The vehicle includes an adjustable frame with front and rear portions that extend or retract with respect to each other. The front portion is supported by a first pair of wheels and said rear portion is supported by a second pair of wheels. Each wheel is independently driven and steered. The vehicle also includes an engine mounted on the rear portion of the frame. Incorporated into the vehicle is an electro-hydraulic assembly which enables extension and retraction of the adjustable frame. The assembly includes a sensor-responsive microprocessor controller, at least one hydraulic pump, at least one hydraulic drive motor and at least one valve network.
Owner:EXTENDQUIP LLC
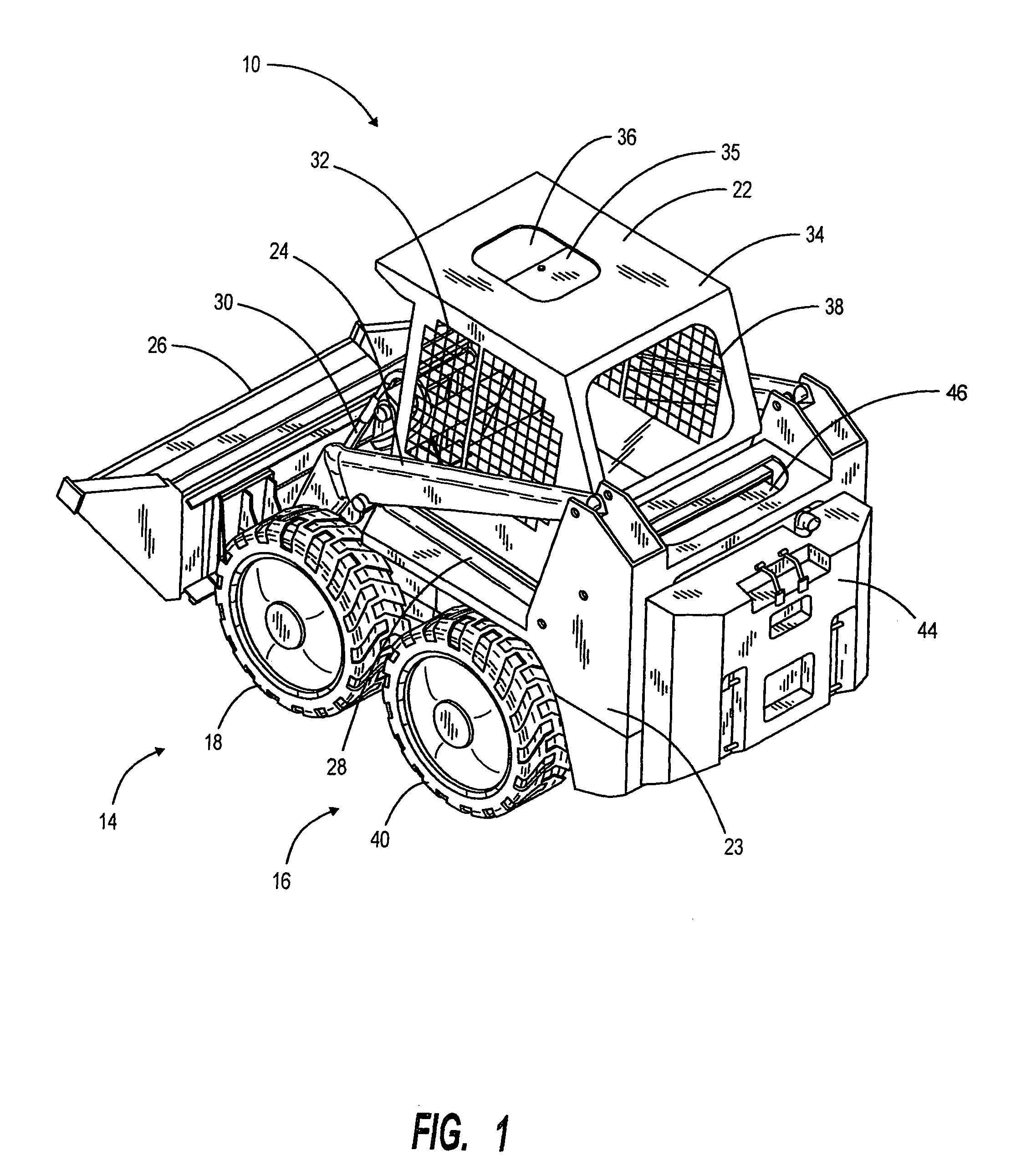
Extendable frame work vehicle
ActiveUS8602153B2Improve effectivenessImprove securitySafety devices for lifting equipmentsAuxillary drivesHydraulic motorVehicle frame
An extendable frame work vehicle offering enhanced versatility, safety and effectiveness. The vehicle includes an adjustable frame with front and rear portions that extend or retract with respect to each other. The front portion is supported by a first pair of wheels and said rear portion is supported by a second pair of wheels. Each wheel is independently driven and steered. The vehicle also includes an engine mounted on the rear portion of the frame. Incorporated into the vehicle is an electro-hydraulic assembly which enables extension and retraction of the adjustable frame. The assembly includes a sensor-responsive microprocessor controller, at least one hydraulic pump, at least one hydraulic drive motor, and at least one valve network.
Owner:EXTENDQUIP LLC
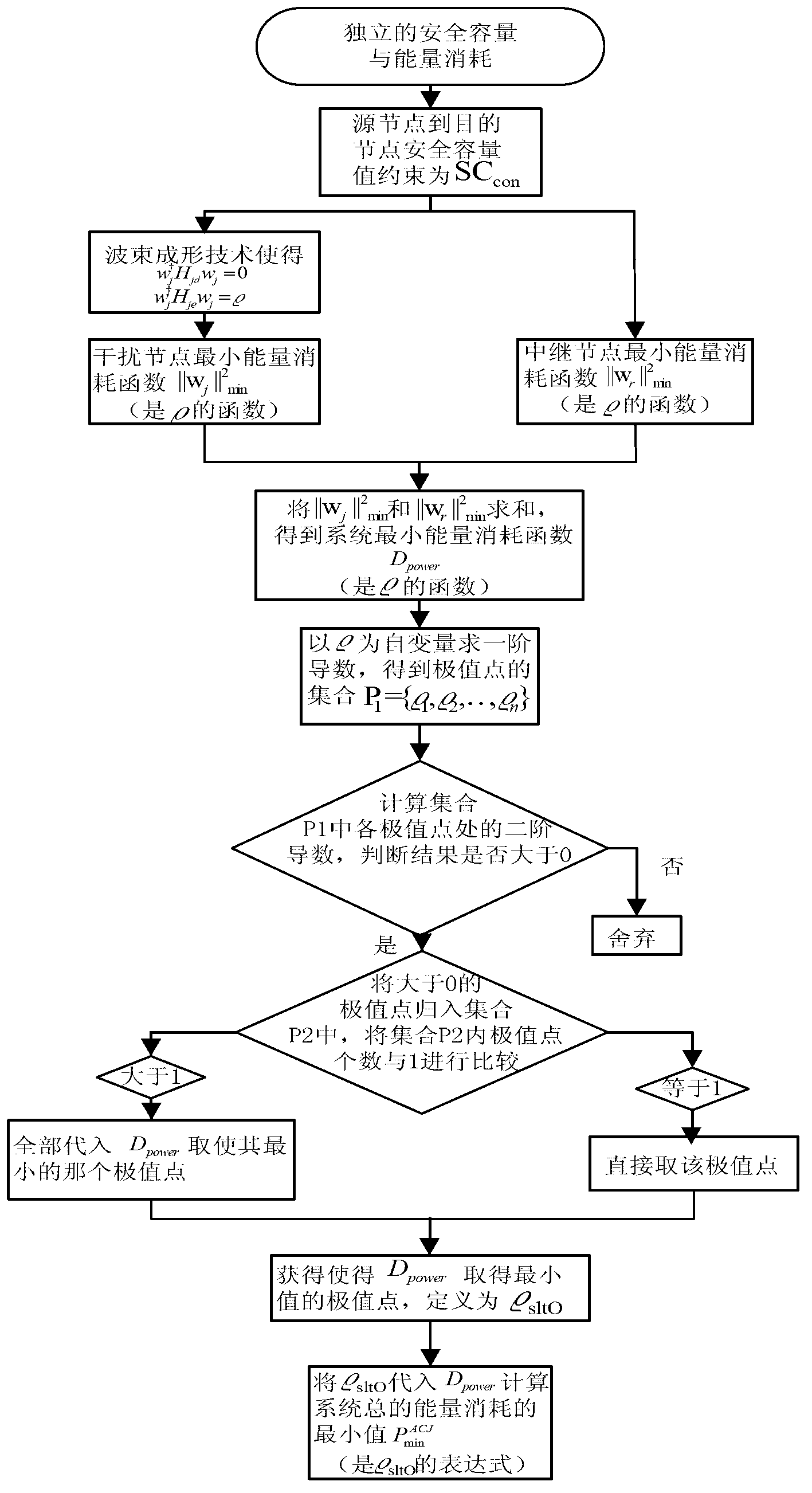
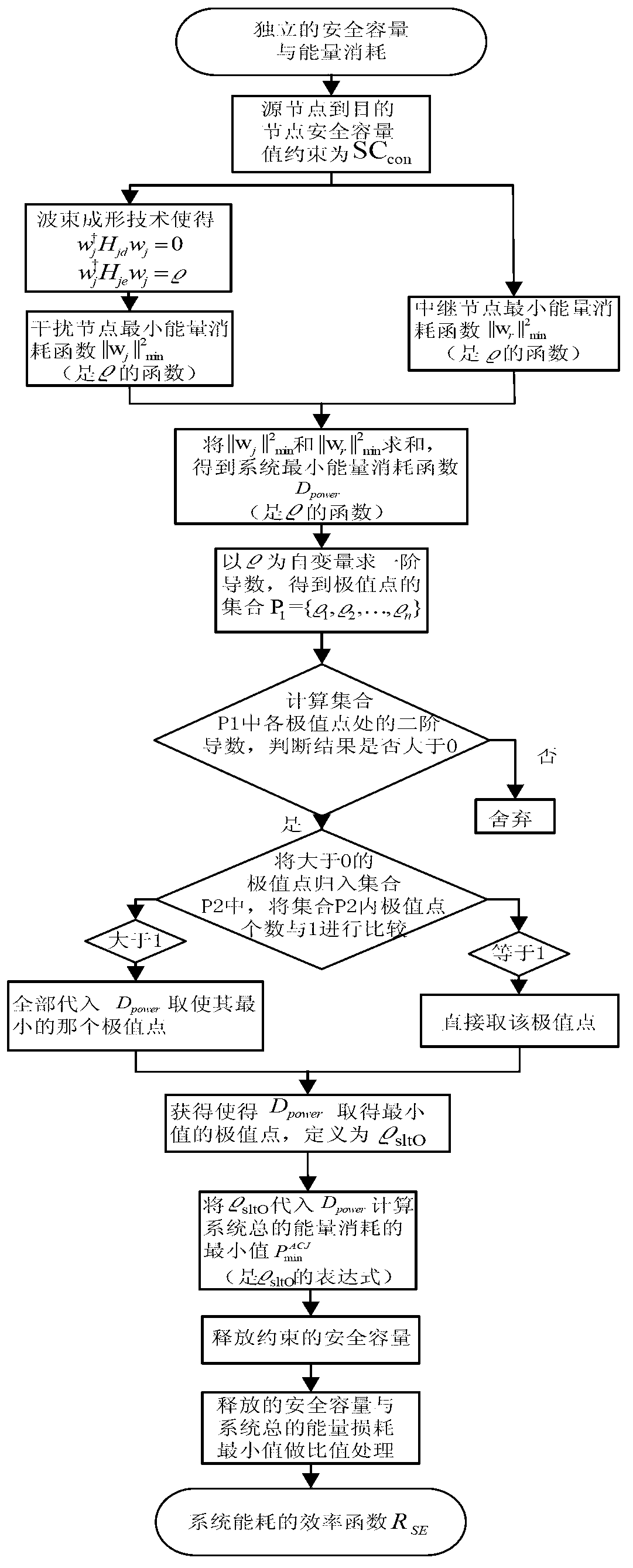
Joint optimization method of safety capacity and energy consumption in wireless relay network
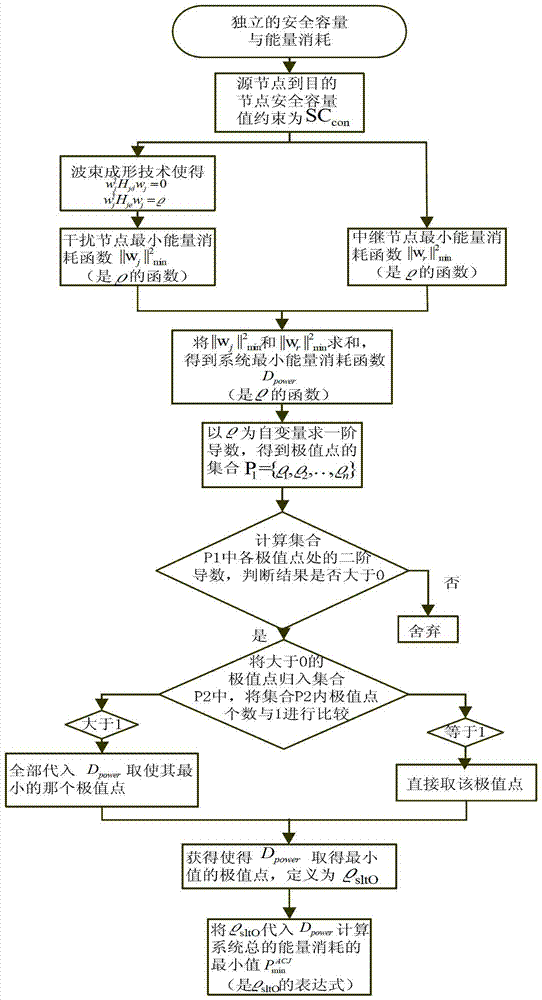
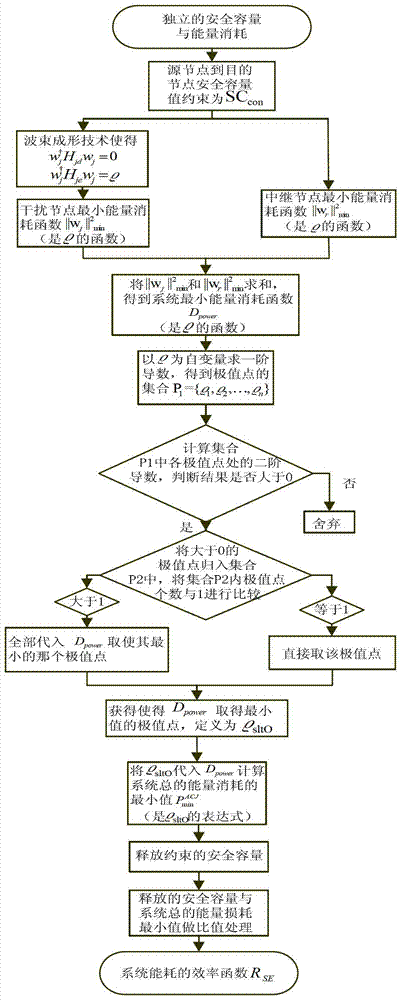
ActiveCN103227997AIncrease safety capacityFix security issuesEnergy efficient ICTPower managementWireless mesh networkCapacity value
The invention discloses a joint optimization method of safety capacity and energy consumption in a wireless relay network, and relates to the field of wireless relay network cooperative communication. The method comprises the steps as follows: a safety capacity value from a source node to a destination node is restrained to be SCcon; a minimum energy consumption function of an interference node is obtained by using a beam forming technology according to the SCcon; a minimum energy consumption function of a relay node is obtained according to the SCcon; a minimum energy consumption function Dpower of a system is obtained; a minimum energy consumption value of the system is obtained at an extreme point of a minimum value of the Dpower, and the restrained safety capacity is released; and an efficiency function RSE of the system energy consumption is calculated. The invention provides a joint optimization strategy of the relay node and the interference node, and an accurate expression of equivalent safety capacity maximization corresponding to the unit energy consumption of the system is obtained, so that each part of energy reaches the maximal usage value, and the problem of balance between the safety and the energy efficiency in the wireless relay network under a single sniffing node is effectively solved.
Owner:BEIJING UNIV OF POSTS & TELECOMM
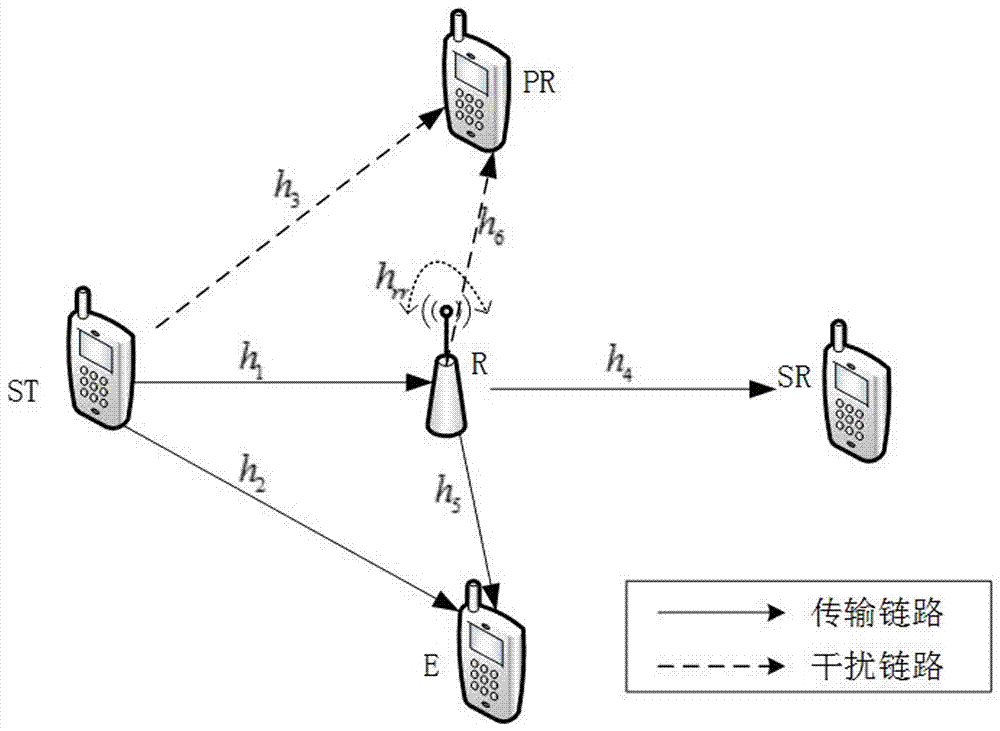
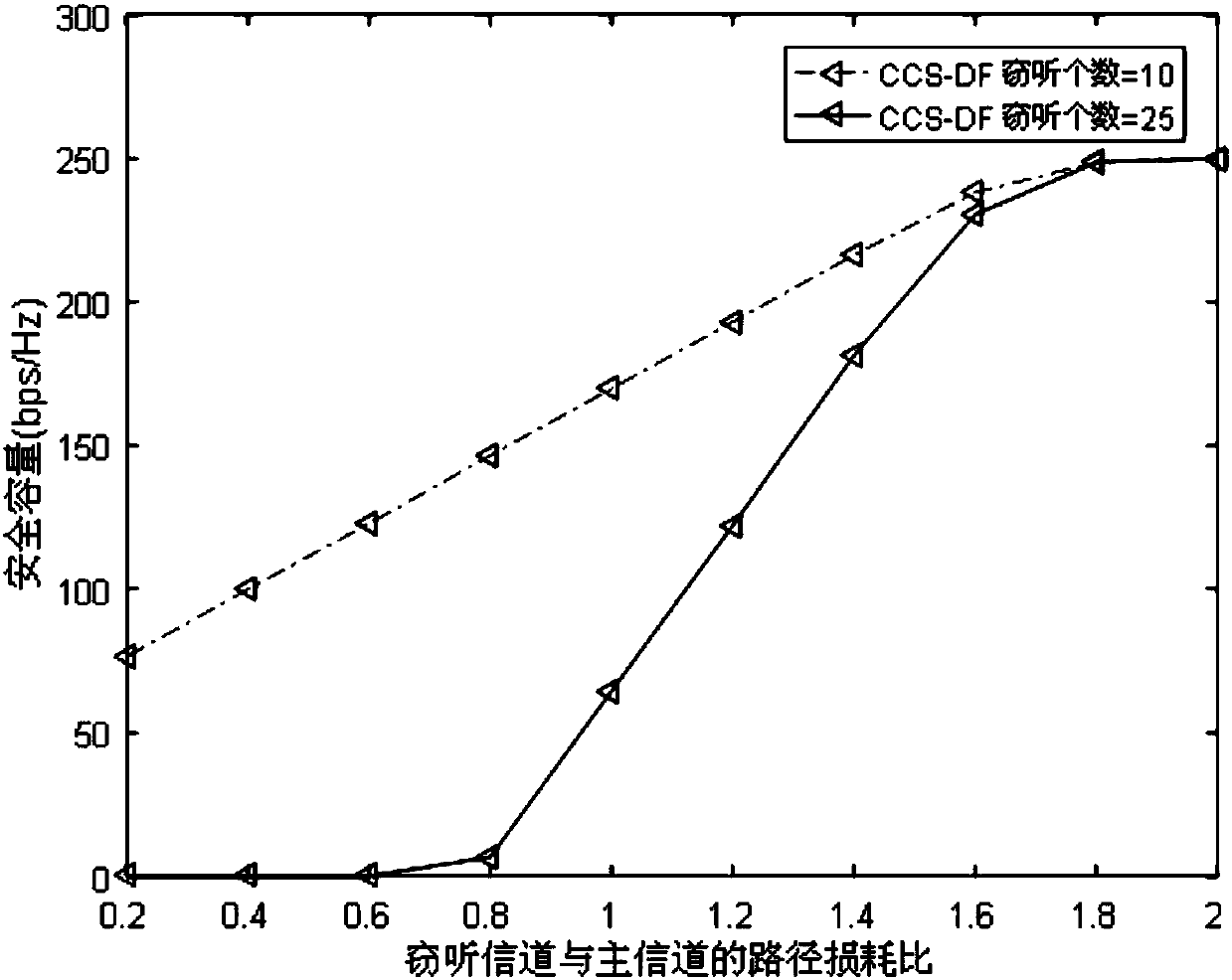
Relay link optimal user selection based collaboration scrambling secure transmission method
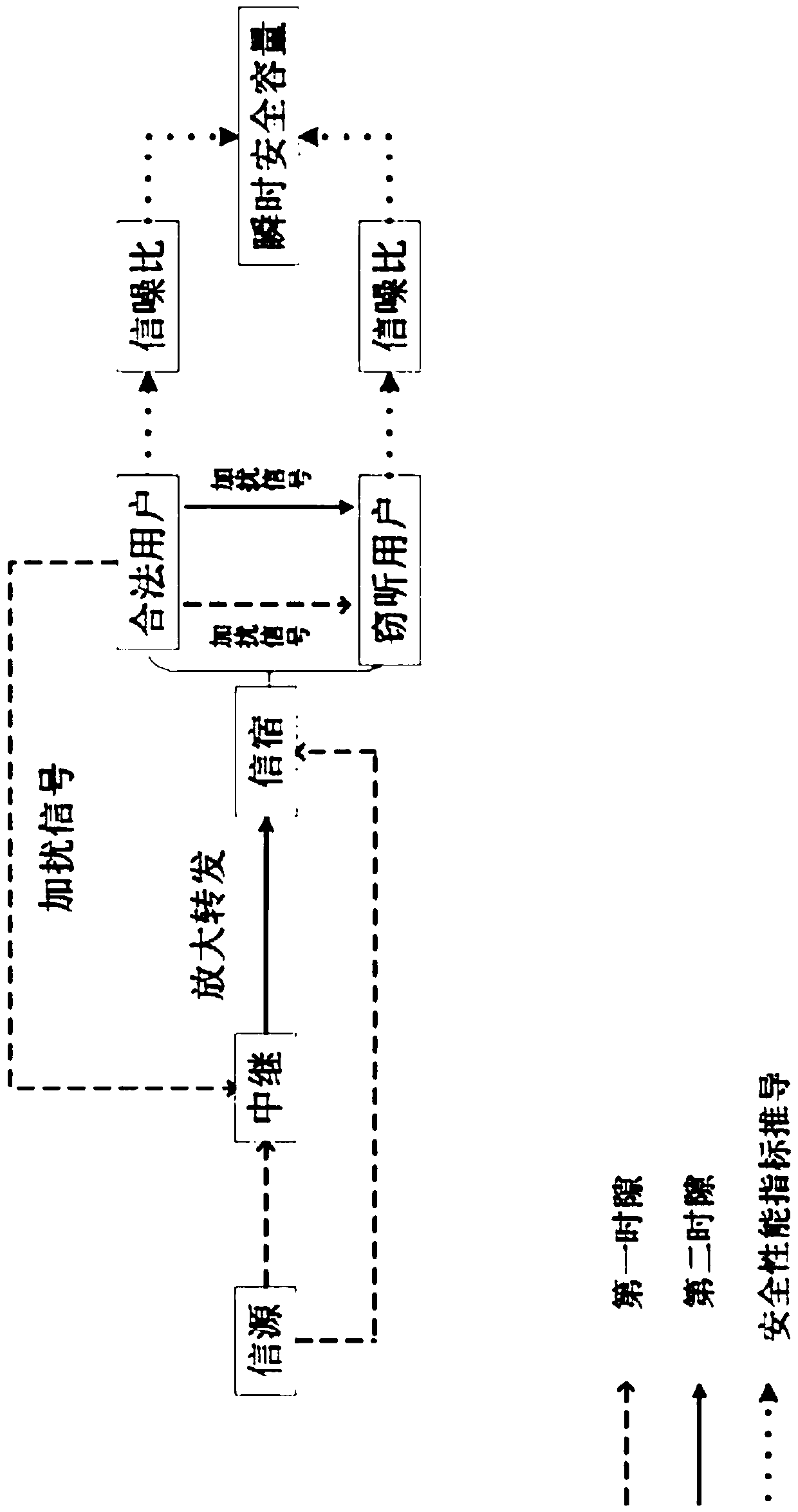
ActiveCN108809365AThe signal-to-noise ratio decreases or decreasesImprove securitySite diversityCommunication jammingSignal-to-noise ratio (imaging)Secure transmission
The invention relates to a relay link optimal user selection based collaboration scrambling secure transmission method. The method comprises the steps of selecting a target user node with the maximumreceiving SNR (Signal-to-Noise Ratio) as a legal user node and other user nodes as eavesdropping user nodes based on a link from a relay to a target user in a first time slot; sending information to arelay node and the target user node by a signal source node meanwhile sending an interference signal to the relay node and the eavesdropping user nodes by the legal user node; by the relay node, amplifying the information received in the first time slot by adopting a changeable grain amplification and forwarding protocol and forwarding the information to the target user node in a second time slot; and by the legal user node, carrying on sending the interference signal to the relay node and the eavesdropping user node. Through collaboration between the relay and the other nodes, the receivingSNR of an eavesdropping channel is reduced and the purpose of guaranteeing system secure transmission is realized.
Owner:HUAQIAO UNIVERSITY
Channel safety transmission method
ActiveCN104283629AIncrease safety capacityImprove anti-eavesdropping performancePower managementCommunication jammingPhysical layerPre treatment
The invention discloses a channel safety transmission method and belongs to the technical field of communication technologies. The channel safety transmission method comprises the steps of determining signal weight factors v and man-made noise nJ of relay nodes when signals are forwarded, based on maximized optimization processing of corresponding safe capacities of the relay nodes in the information forwarding process during preprocessing; respectively multiplying received source information by the signal weight factors v of the relay nodes and then adding the man-made noise nJ to products to serve as signals to be transmitted in the next step when a system works, namely the man-made noise is sent while the relay nodes collaboratively forward signals. The channel safety transmission method is mainly applied to physical-layer safety communication, the maximum reachable safety speed of the system is improved, and the purpose of improving the safety performance of the system is achieved.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Physical layer safety communication method for multi-input and single-output wireless energy-carrying communication system
ActiveCN109617590ATargeted interference effect is goodIncrease safety capacitySpatial transmit diversityChannel estimationMulti inputCommunications system
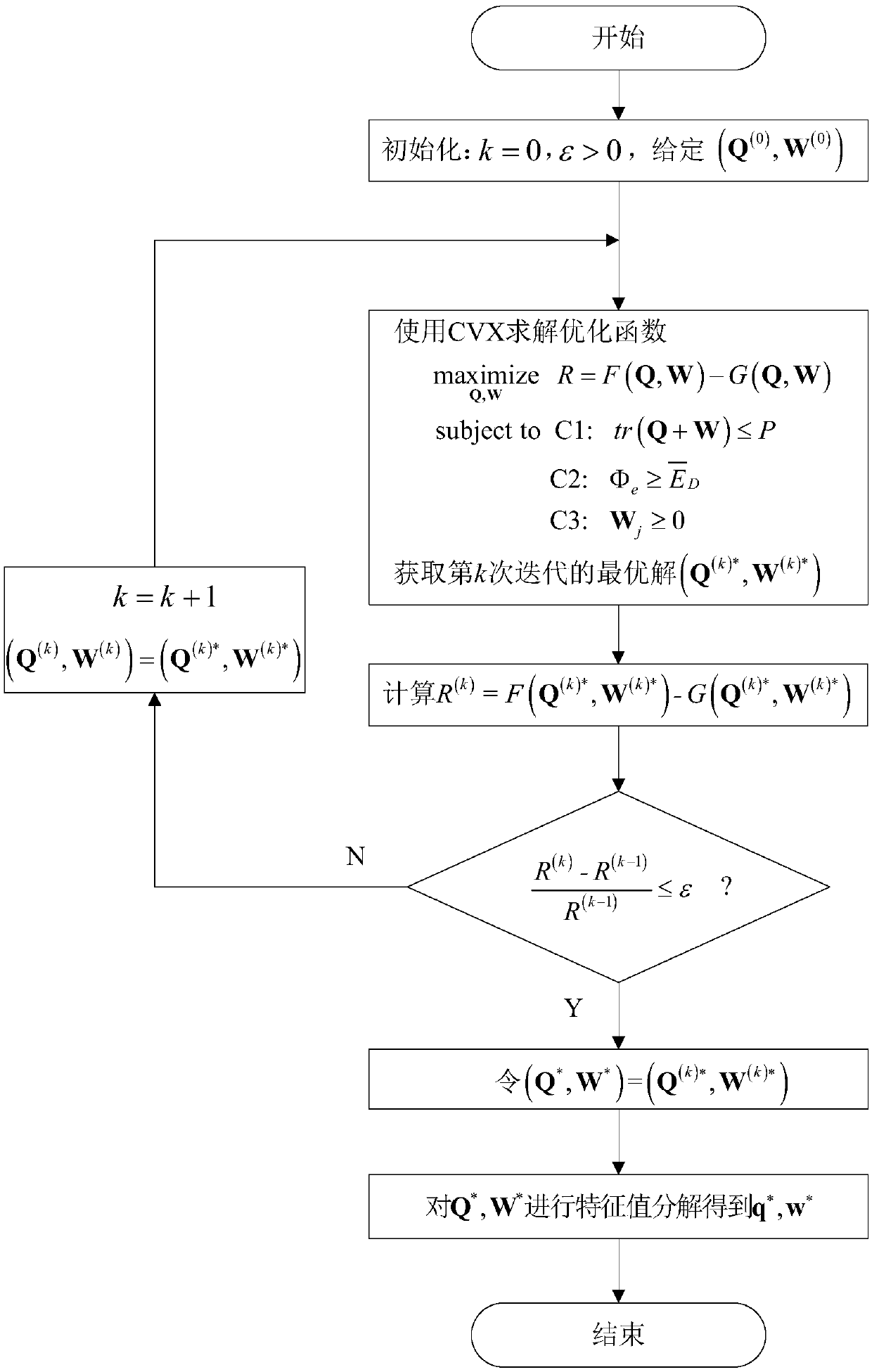
The invention discloses a physical layer safety communication method for a multi-input and single-output wireless energy-carrying communication system. The method has the advantages that a transmitting end carries out the optimal beam forming on artificial noises through channel status information of wiretap channels, so that the artificial noises in a specific direction can be generated in a space, targeted interference effects for wiretap terminals can be improved, and the system safety capacity can be remarkably increased; a continuous convex approximation method in a CVX tool kit is used to calculate the optimal value, second-order Taylor expansion and approximation is carried out on an optimization function at each iteration starting point of the optimization function, and the local close approximation of the optimization function is calculated under strictly convex restrictions of restriction conditions, so that a high algorithm convergence speed is achieved; and in considerationof the nonlinearity of an actual energy receiver internal circuit structure, a nonlinear energy receiver model is adopted, which is more practical and avoids mismatching in resource allocation and system performance declines caused by the mismatching.
Owner:SOUTH CHINA UNIV OF TECH
Secure transmission scheme based on time reversal technology
InactiveCN109379154AIncrease safety capacityReduce bit error rateSpatial transmit diversityTransmission monitoringMulti inputBeamforming
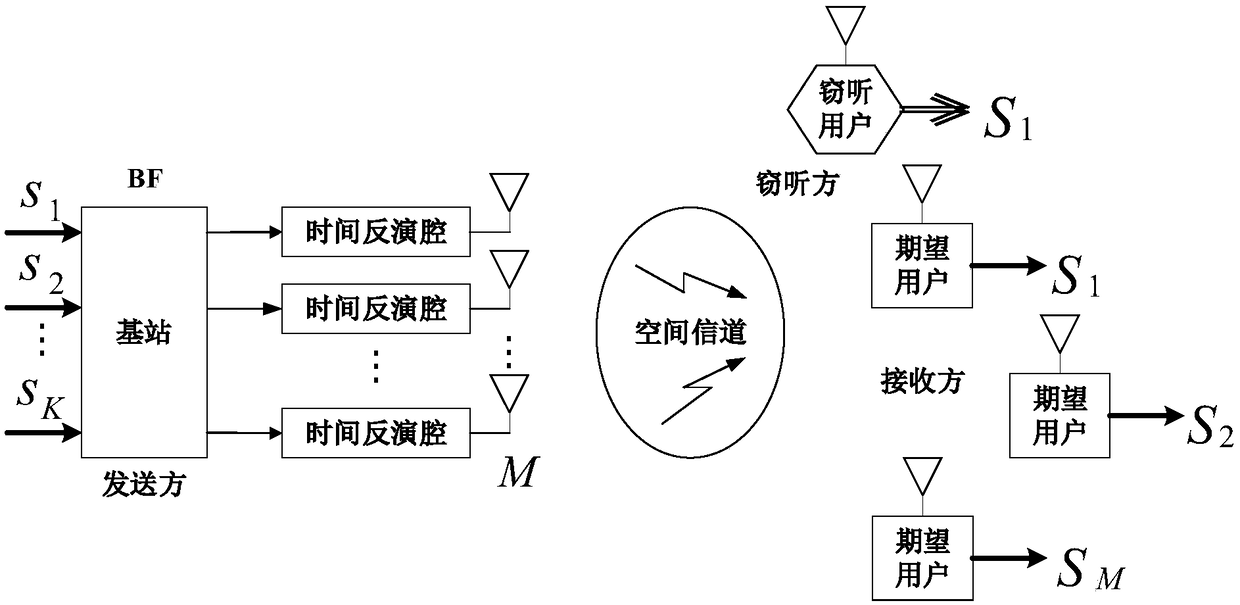
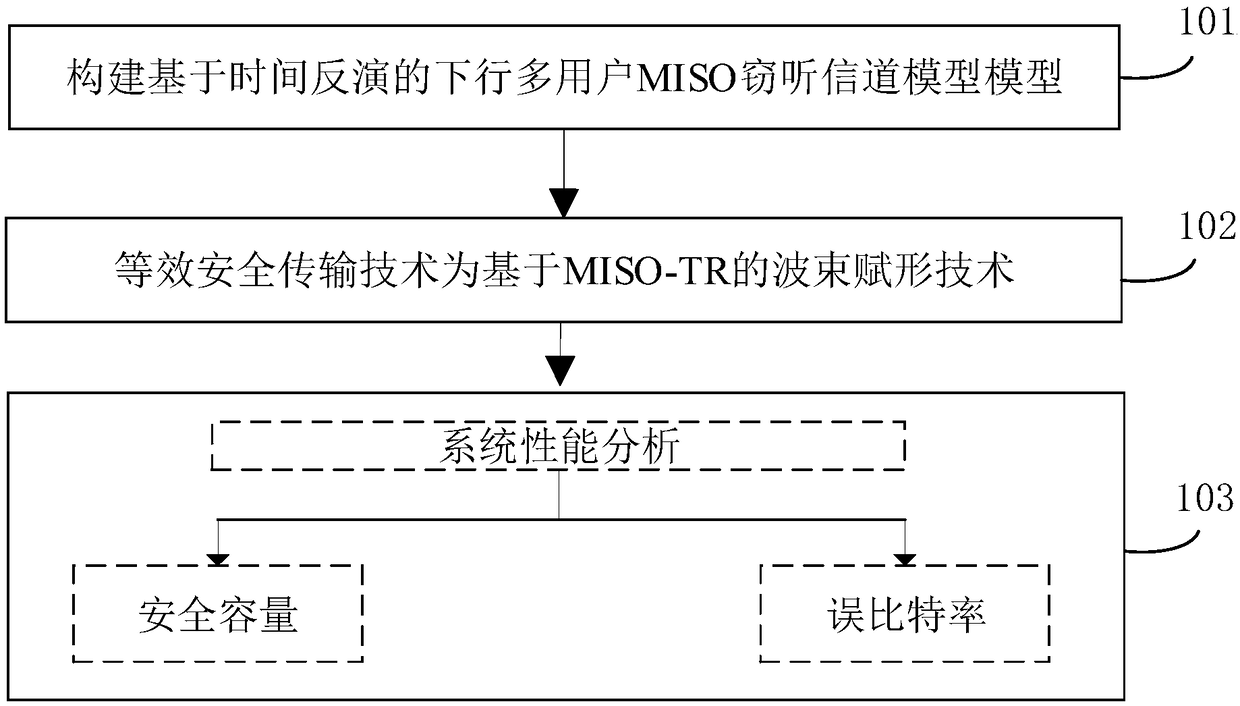
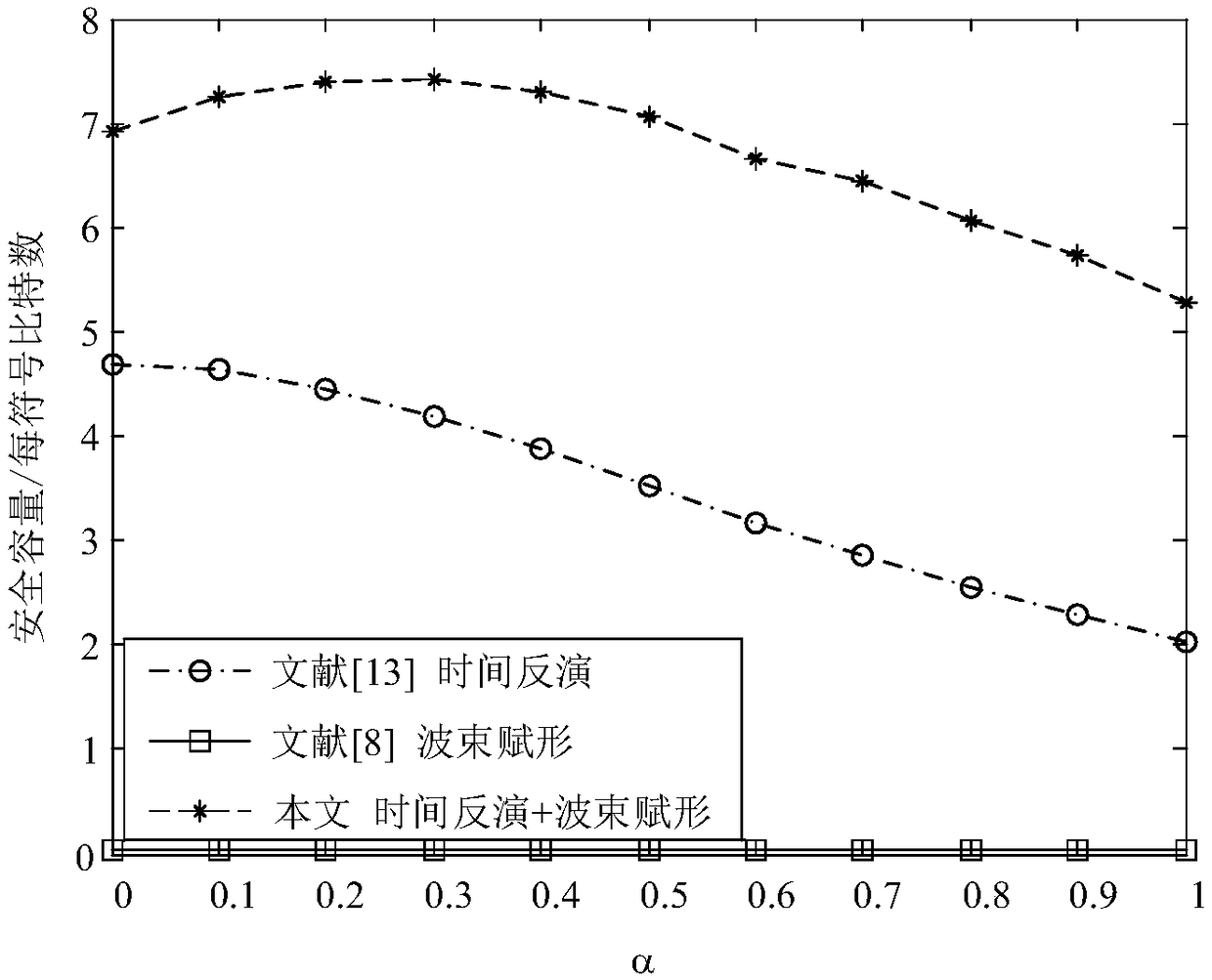
Wireless communication depends on open free space, and an interception user may steal information in a communication process. Aiming at a problem of information leakage of a multi-user downlink, a secure transmission scheme based on a time reversal (TR) technology and optimized with a beam forming (BF) technology is provided. In the scheme, maximizing secure capacity is taken as a multi-user communication criterion, and a multi-input single-output (MISO) interception channel model is built. On one hand, a base station enhances signals in a specified direction through the beam forming technology, and sends needed signals for expected users; and on the other hand, since the time reversal technology is adaptive to environment, the signals of the base station all pass through a time reversal chamber before being transmitted, spatial and temporal focusing property of the time reversal chamber enables energy to be focused at a legal receiving party, and thus, secrecy performance is more excellent. Theoretical analysis and simulation results show that, compared with the existing physical layer security scheme, the scheme provided by the invention has higher secure capacity and lower bit error rate
Owner:CHONGQING UNIV OF POSTS & TELECOMM
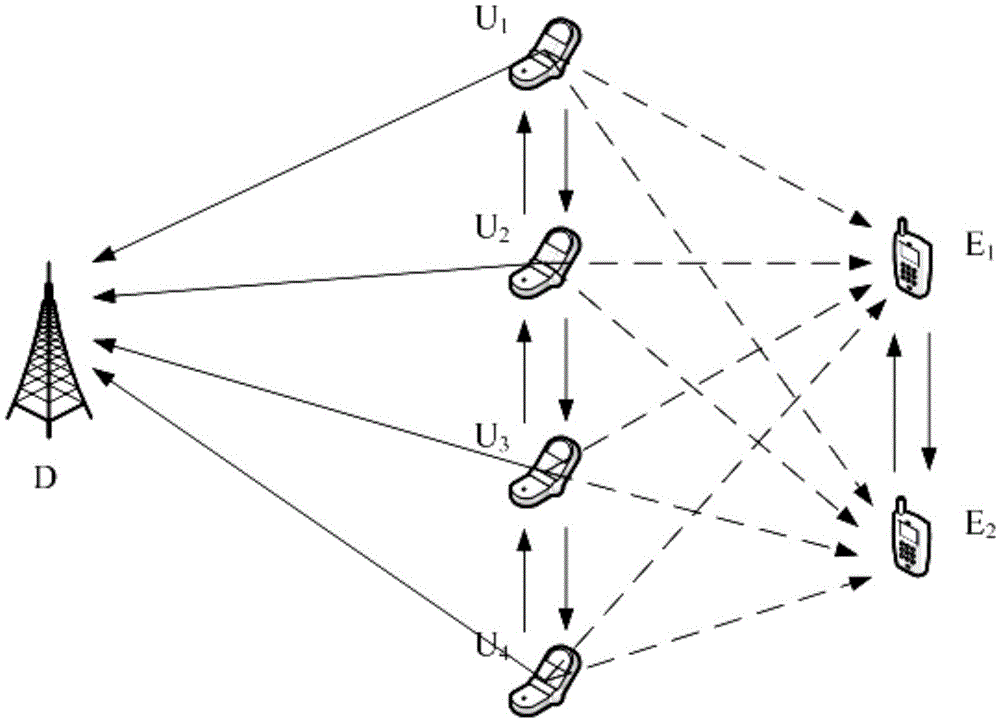
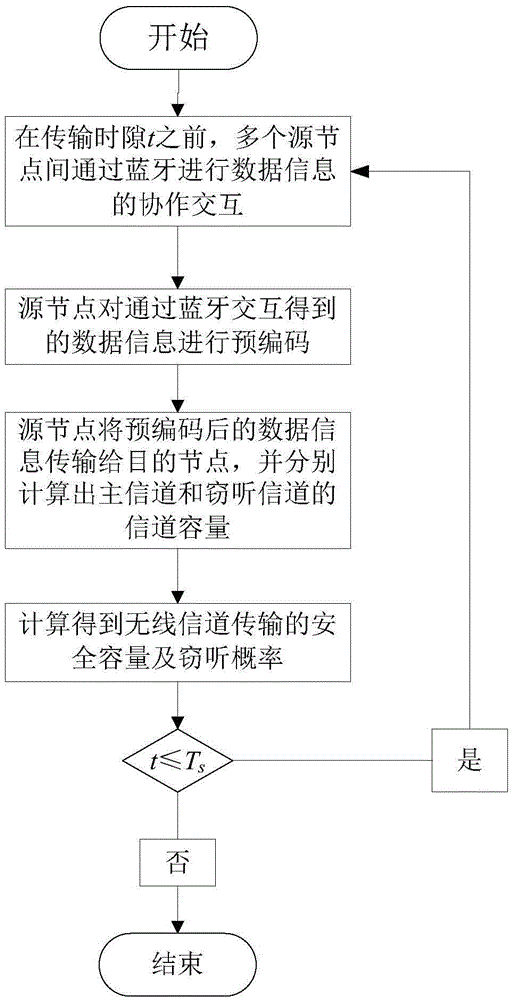
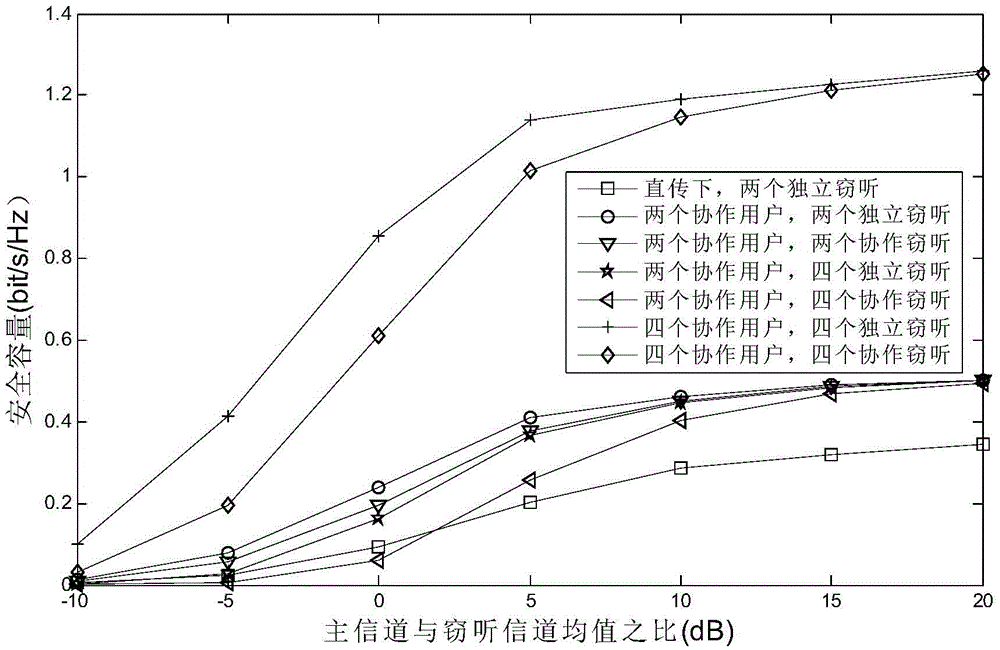
Wireless anti-eavesdropping communication method based on cooperation of multiple source nodes
ActiveCN105657700AAvoid illegal acquisitionIncrease safety capacityWireless commuication servicesTransmissionPrecodingTelecommunications
The invention discloses a wireless anti-eavesdropping communication method based on cooperation of multiple source nodes. The method includes the steps that data interaction is conducted on all the source modes in a Bluetooth mode, so that all the source nodes synchronously transmit the same data information to a target node; according to main channel state information, all the source nodes conduct precoding on the data information to be transmitted; all the source nodes synchronously transmit respective precoded information to the target node, then the target node and an eavesdropping node calculate capacity of the main channel and capacity of an eavesdropping channel respectively, and safety capacity and eavesdropping probability of wireless channel transmission are obtained further. In the mode of cooperation and precoding of the source nodes, the safety capacity of wireless transmission is remarkably improved, and the eavesdropping probability of wireless transmission is effectively reduced, which is beneficial for solving the safety problem caused by multiple eavesdropping nodes existing in an actual wireless communication scene.
Owner:NANJING UNIV OF POSTS & TELECOMM
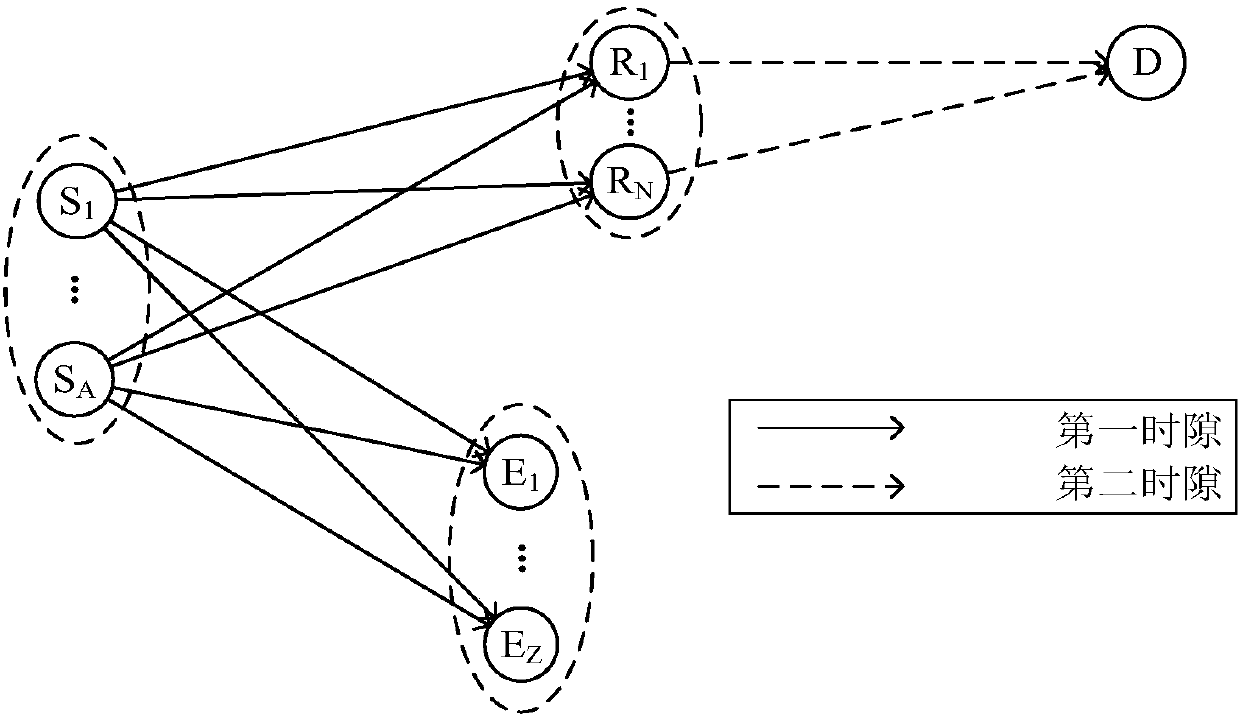
A full-duplex cooperative scrambling secure transmission method based on optimal user selection of a direct path
ActiveCN109067437AImprove securityReduced or reduced securitySite diversityCommunication jammingSignal-to-noise ratio (imaging)Amplify and forward
The invention relates to a full-duplex cooperative scrambling secure transmission method based on optimal user selection of direct path. In the first time slot, the source node sends information to the relay node and the destination user node. At the same time, one user node with the largest signal-to-noise ratio is selected from all the destination user nodes as the legal user node, and the otherdestination user nodes are eavesdropping user nodes. The legal user node sends interference signals to the relay node and destination user node. In the second time slot, the relay node amplifies theinformation received in the first time slot by using the variable gain amplification and forwarding protocol, and forwards the information to the destination user node. The legitimate user continues to send the scrambling signal to the eavesdropping user node. The invention can reduce the receiving signal-to-noise ratio of the eavesdropping channel and ensure the safe transmission of the information.
Owner:HUAQIAO UNIVERSITY
Satellite anti-parametric scanning communication method based on ML-WFRFT and AN assistance
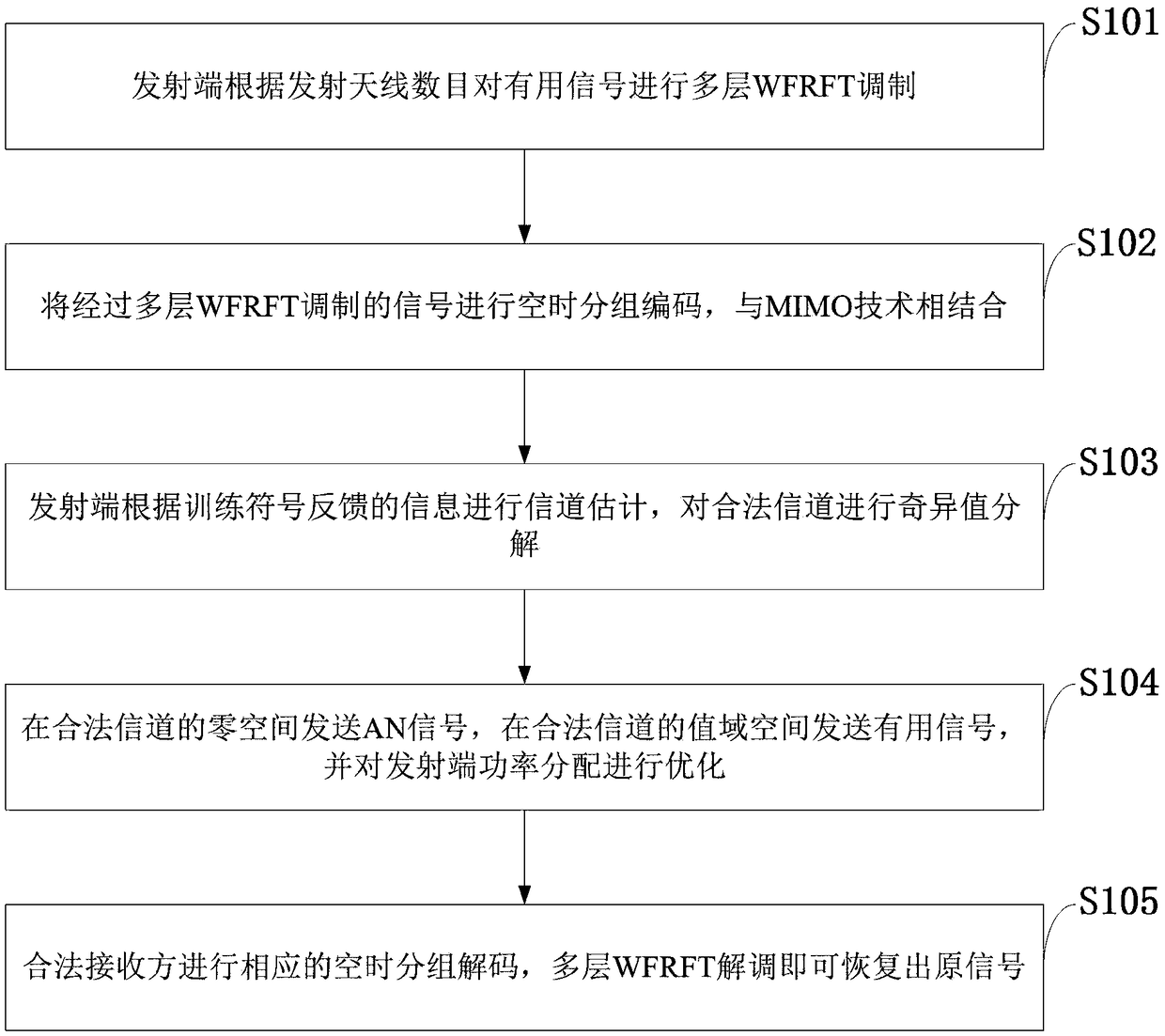
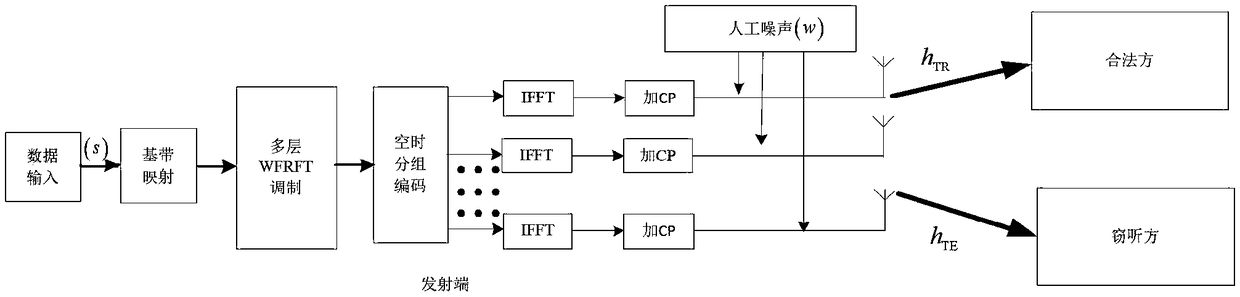
InactiveCN109150368AImprove capacity utilizationImprove spectrum utilizationSecret communicationCommunication jammingEavesdroppingMultiple input
The invention, which belongs to the field of satellite communication technology, discloses a satellite anti-parametric scanning communication method based on multilayer weighted fractional fourier transform (ML-WFRFT) and artificial noise (AN) assistance. According to the method disclosed by the invention, an ML-WFRFT modulation signal is employed and the ML-WFRFT is combined with the AN assistance technology. On the basis of modification of the traditional WFRFT, the ML-WFRFT is put forward to modulate signals; and the ML-WFRFT is combined with the multiple input multiple output (MIMO) technology, so that the modulated signal has multiple modulation parameters and high encryption; and parameter scanning is carried out by suppressing the eavesdropping side and the ML-WFRFT is combined withthe AN assistance technology. Therefore, the receiving performance of the AN assistance technology is suppressed greatly while the communication requirement of the legal receiving side is met; and thus the signal can not be demodulated correctly basically.
Owner:达新宇
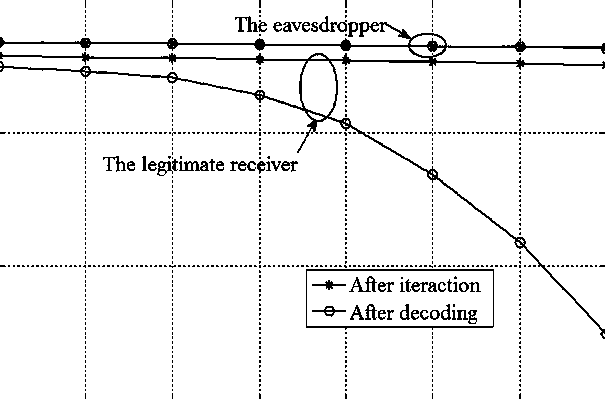
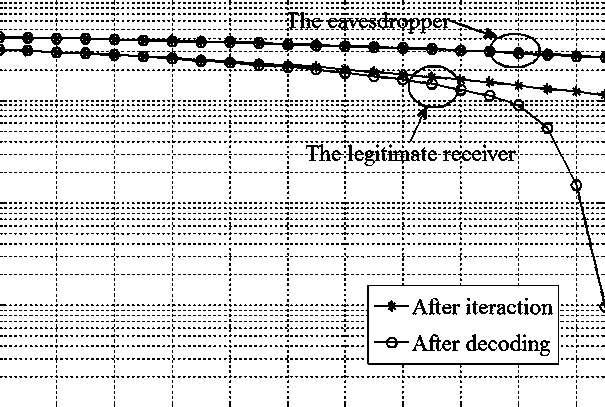
Method for constructing first-class wiretap channel through BSBC (Binary Symmetric Broadcast Channel)
InactiveCN106059713AImprove reliabilityEnhanced channel quality advantageChannel coding adaptationTransmitter/receiver shaping networksBroadcast channelsWiretap channels
The invention discloses a method for constructing a first-class wiretap channel through a BSBC (Binary Symmetric Broadcast Channel). The method comprises the following steps that: a legitimate receiver transmits feedback information to a legitimate transmitter through the BSBC; the legitimate transmitter and a wire tapper receive the feedback information interfered by noise of the legitimate receiver respectively, and the legitimate transmitter processes encoded information to be transmitted according to the received feedback information and then transmits the processed information through an error-free common channel; the legitimate receiver extracts bit log-likelihood ratio information needed by soft-decision decoding in a specific way firstly, and then decodes the received information in a soft-decision decoding way in order to lower the bit error rate of a main channel, enhance the channel reliability, enlarge a quality difference between the main channel and the wiretap channel and increase the security capacity of the first-class wiretap channel; and the wire tapper passively wiretaps the information transmitted by the legitimate transmitter, and decodes the received information in the soft-decision decoding way. The method is easy to implement, and high channel security capacity and good communication quality are achieved.
Owner:HENAN UNIV OF SCI & TECH
Physical layer secure communication method based on multi-radio cooperative precoding
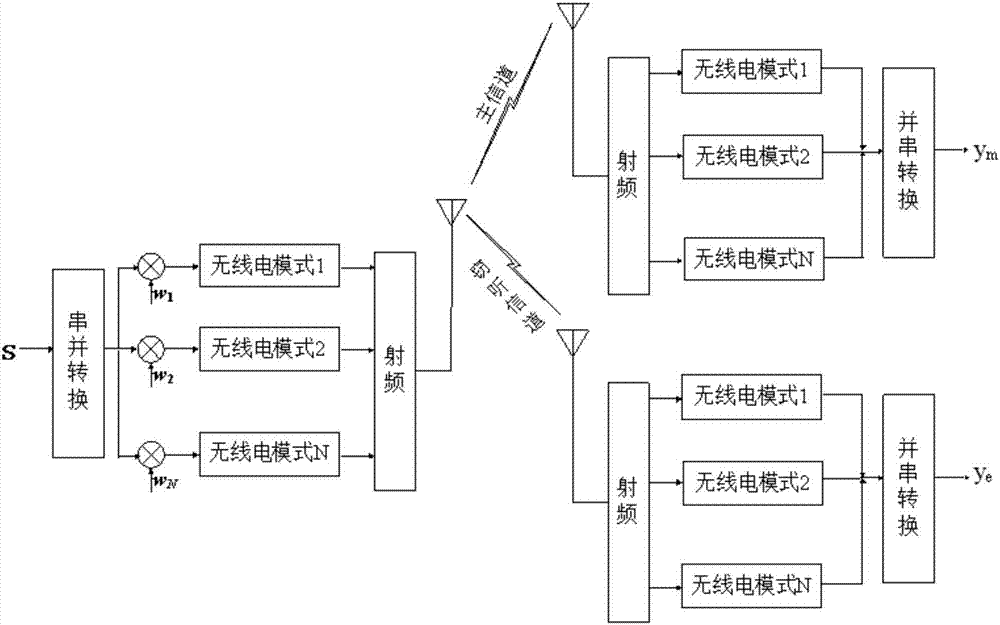
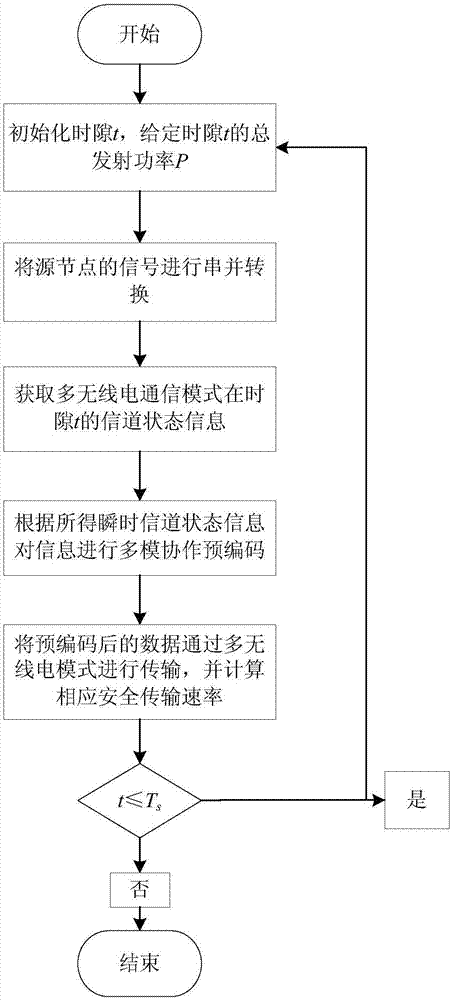
ActiveCN106953819AImprove securityAvoid illegal acquisitionTransmitter/receiver shaping networksSecurity arrangementData informationEavesdropping
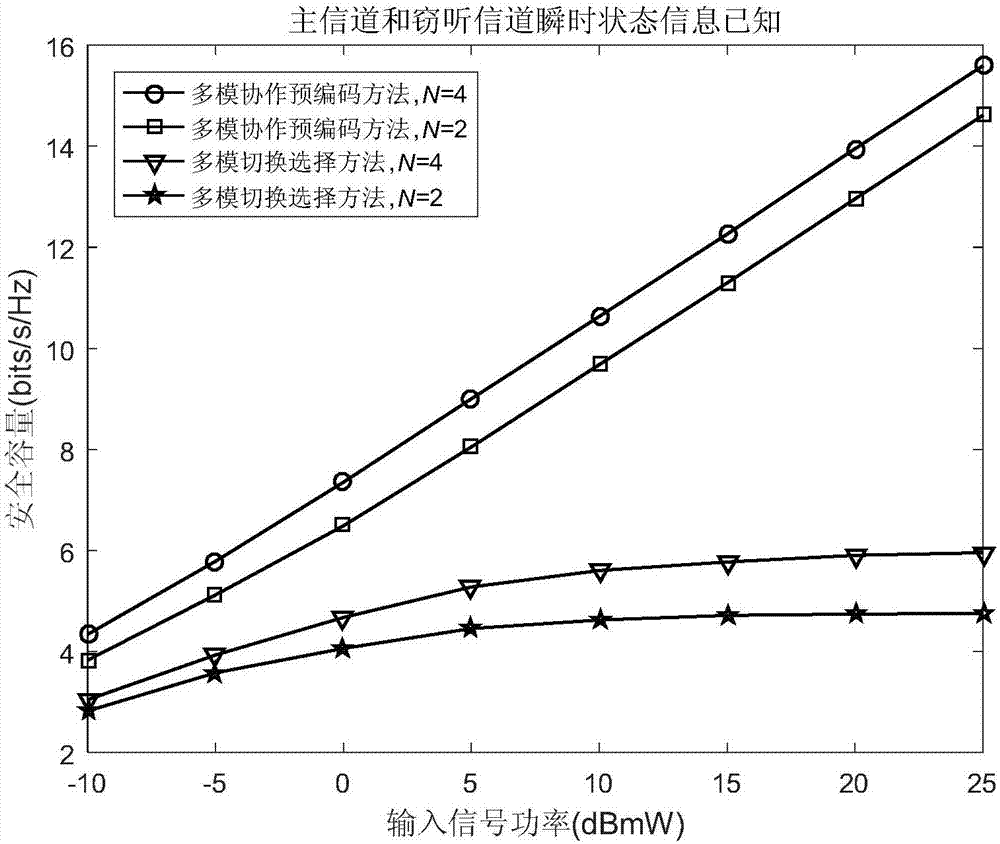
The invention discloses a physical layer secure communication method based on multi-radio cooperative precoding, which is suitable for secure information transmission between a user terminal and a base station in a heterogeneous wireless network. In the heterogeneous wireless network environment, the user terminal fully utilizes the multi-radio access technology to realize the cooperative secure information transmission between different communication modes. The physical layer secure communication method considers two situations that instantaneous channel state information of an eavesdropping channel between a source node and an eavesdropping node is known and unknown separately, preprocesses a source node signal by means of multi-mode cooperative precoding, and transmits data information after precoding to a destination node. Compared with the traditional multi-mode switching selection method, the multi-mode cooperative method provided by the invention significantly improves the secure transmission rate of wireless transmission, and is conductive to solving the security problem caused by the eavesdropping node existing in the multi-mode communication scene.
Owner:NANJING UNIV OF POSTS & TELECOMM
Mixed duplex transmission method for improving physical layer security in cognitive relay network
ActiveCN107171775AIncrease safety capacity situationDetrimental effects of weakening transmission capacity performanceAllocation timingSecurity arrangementSelf interferencePhysical layer
The invention discloses a mixed duplex transmission method for improving physical layer security in a cognitive relay network. The mixed duplex transmission method comprises the steps of, by a pair of unauthorized users, sharing a frequency band resource with an authorized user in the cognitive relay network with an illegal eavesdropper under the assistance of a cooperative relay and under the interference limitation to a main user; and by the relay, playing a role of confusing the illegal eavesdropper through adding man-made noise while assisting to decode and forward information. One relay transmission frame is divided into two equal time slots during half-duplex transmission. The relay transmission frame is not subjected to time slot division during the full-duplex transmission. When the full-duplex self-interference power is lower than a threshold value, the full-duplex transmission is adopted; otherwise, the half-duplex transmission is adopted. Switching between the half-duplex transmission and full-duplex transmission is realized based on the full-duplex self-interference power, respective advantages of the half-duplex mode and the full-duplex mode are utilized, and the physical layer security of the cognitive relay network is finally improved by increasing the total transmission capacity of the cognitive relay network.
Owner:GUILIN UNIV OF ELECTRONIC TECH
Method for establishing first side channel under BI-AWGN broadcast channel
ActiveCN106209710AImprove reliabilityEnhanced channel quality advantageDc level restoring means or bias distort correctionCodes simulation/testingBroadcast channelsTelecommunications
A method for establishing a first side channel under a BI-AWGN broadcast channel includes the steps that a legal receiver sends feedback information through a binary input additive white Gaussian noise broadcast channel, and a legal sender and an eavesdropper receive the feedback information influenced by noises respectively; the legal sender encodes to-be-sent information according to the received feedback information and sends the to-be-sent information through an error-free public channel, wherein the complexity degree of system obtaining is reduced; after the legal receiver receives the information of the legal sender, bit logarithm likelihood ratio information is extracted and is then decoded in a soft decision decoding mode, and a soft decision decoding algorithm with high reliability is selected for use, wherein the reliability of a main channel is improved, the quality difference of the main channel and the side channel is expanded, and the security capacity of the first side channel is further improved; the eavesdropper passively eavesdrops the information of the legal sender and conducts decoding in a soft decision decoding mode. The method is low in difficulty, high in channel security capacity and high in transmission rate.
Owner:HENAN UNIV OF SCI & TECH
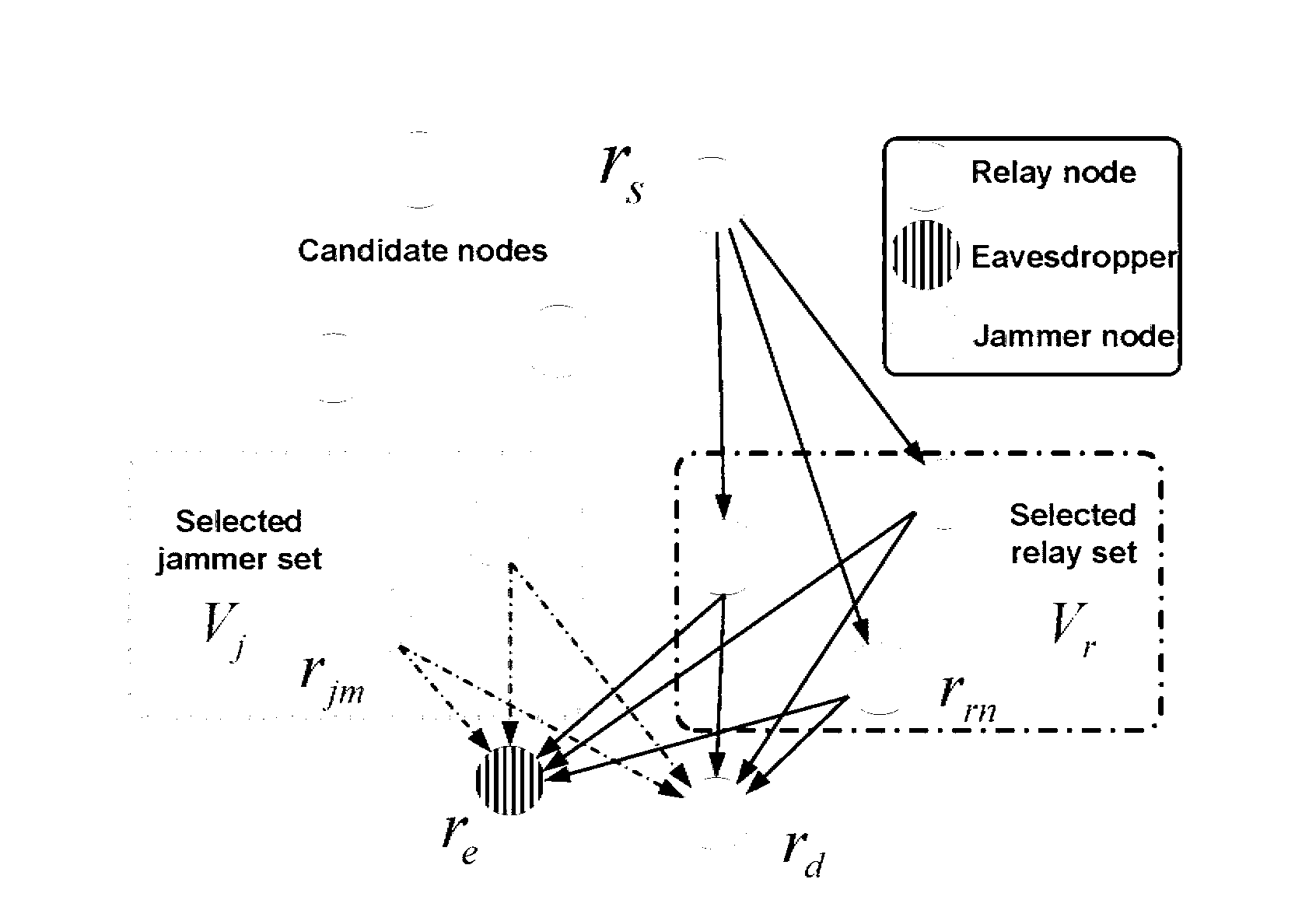
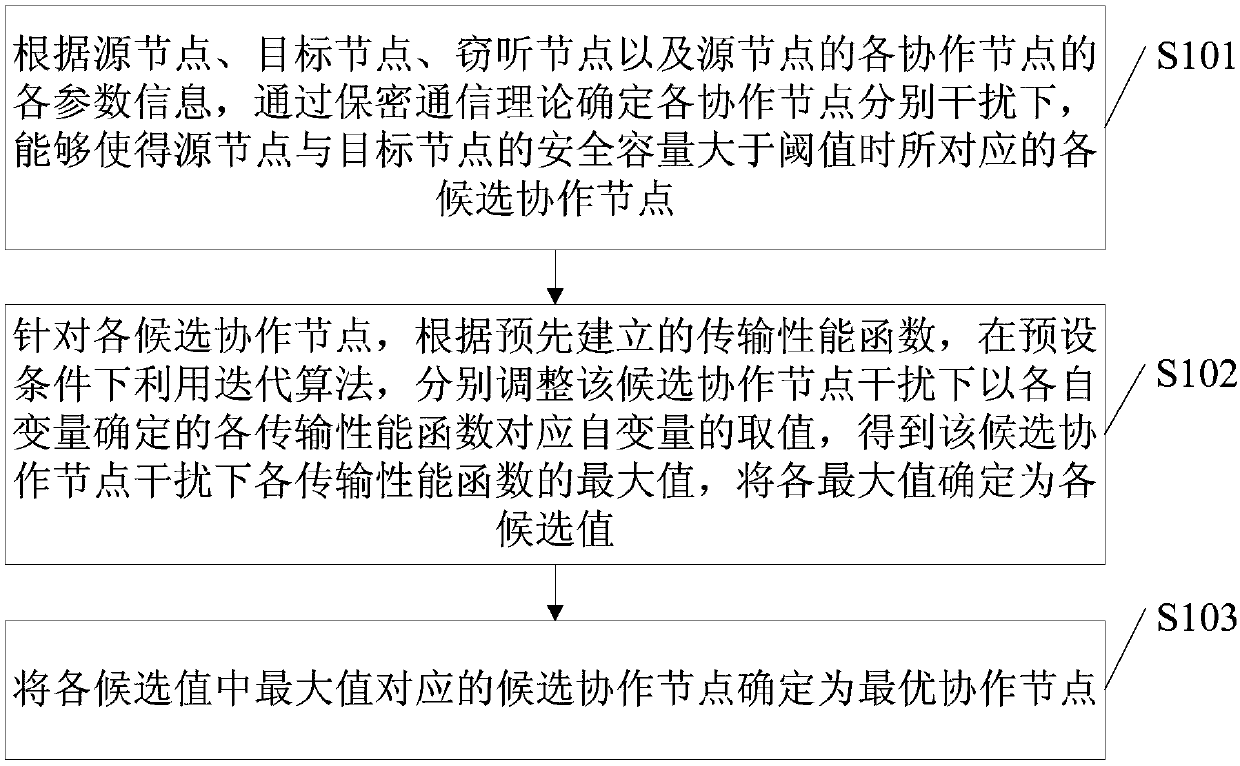
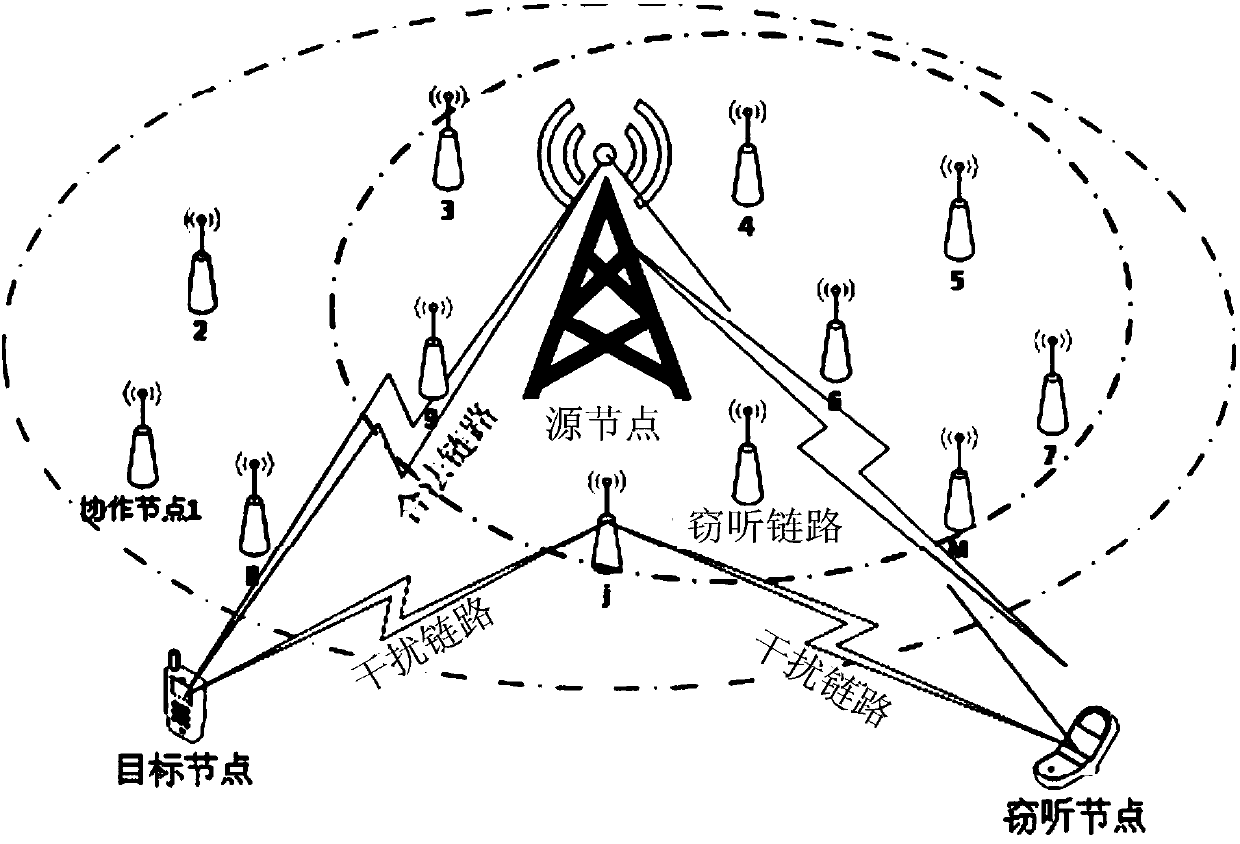
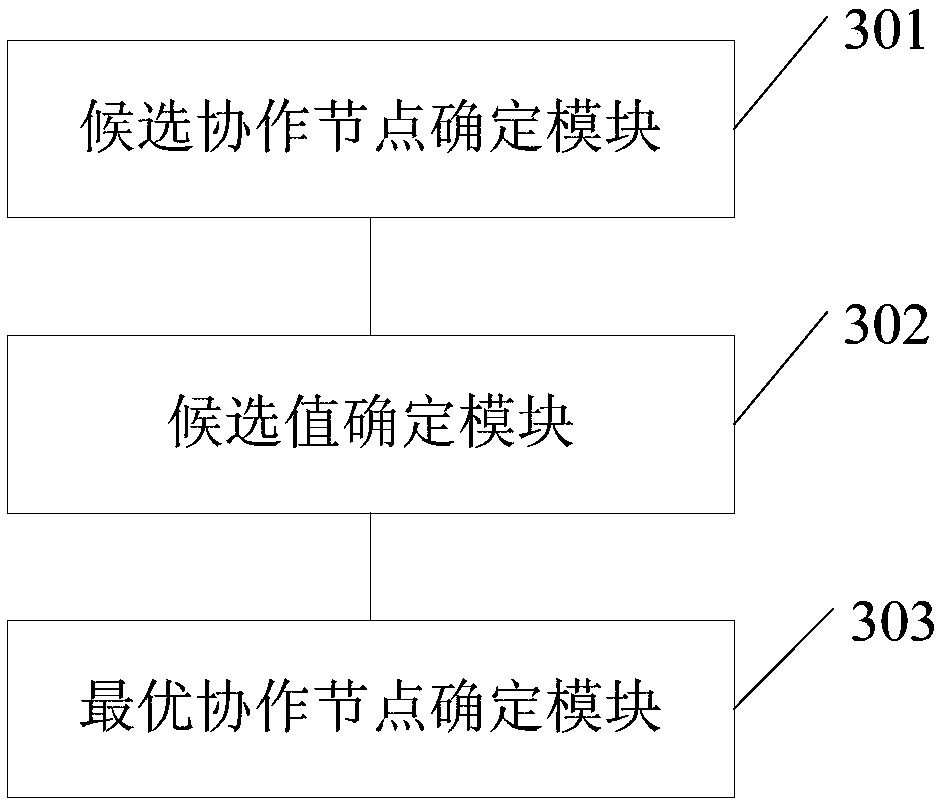
Cooperative node determination method and device of source node, electronic equipment and medium
ActiveCN110248306AAccurately determineIncrease safety capacityDistributed allocationLocation information based serviceEavesdroppingCo operative
The embodiment of the invention provides a cooperative node determination method and device of a source node, electronic equipment and a medium. The cooperative node determination method comprises the following steps: according to a source node, a target node, an eavesdropping node and parameter information of each cooperative node of the source node, determining each candidate cooperative node corresponding to the source node and the target node when the security capacity of the source node and the target node is greater than a threshold value under the respective interference of each cooperative node through a secret communication theory; for each candidate cooperative node, according to a pre-established transmission performance function, respectively adjusting values of independent variables corresponding to the transmission performance functions determined by respective variables under the interference of the candidate cooperative node by utilizing an iterative algorithm under a preset condition to obtain a maximum value of each transmission performance function under the interference of the candidate cooperative node, and determining each maximum value as each candidate value; and determining the candidate cooperative node corresponding to the maximum value in the candidate values as the optimal cooperative node. According to the embodiment of the invention, the optimal cooperative node of the source node can be accurately determined.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Unmanned aerial vehicle safety communication method based on multi-user scheduling
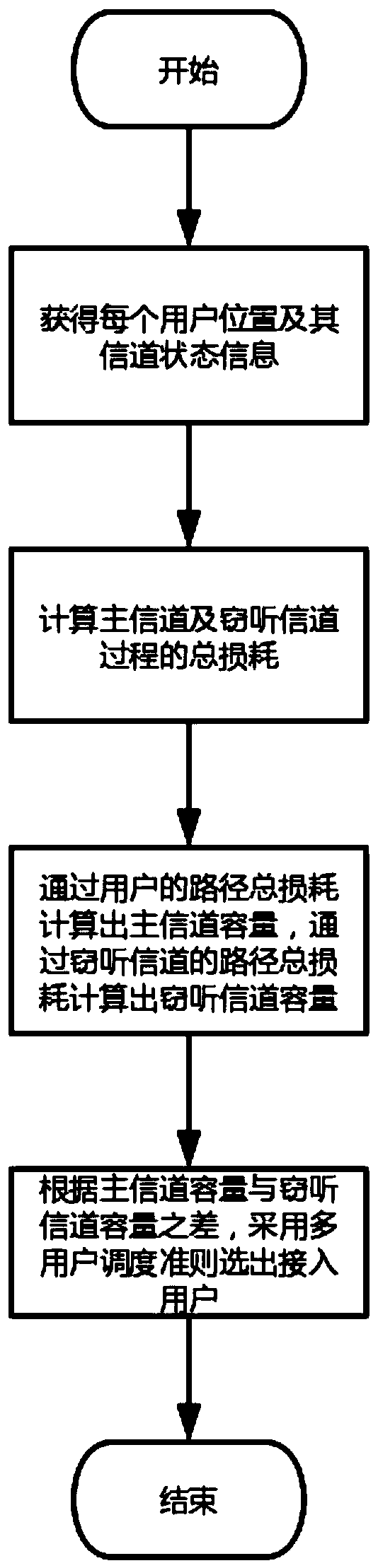
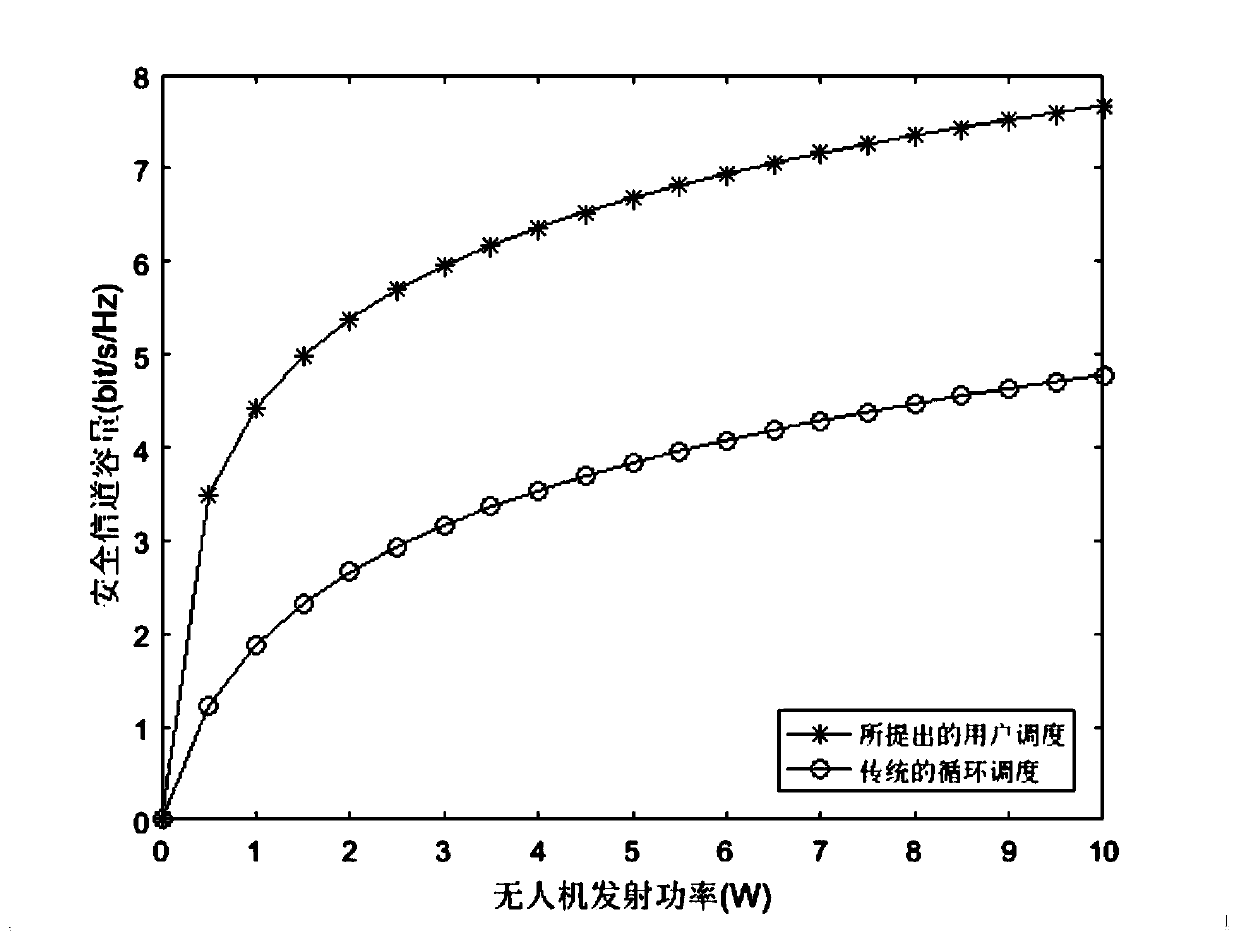
ActiveCN110912604AImprove system security capacityEnsure communication securityRadio transmissionWireless communicationData transmissionCommunication quality
The invention discloses an unmanned aerial vehicle safety communication method based on multi-user scheduling. The method is suitable for data transmission between a base station and users in an emergency scene. Network coverage is provided for users by using an unmanned aerial vehicle base station, and access users are selected through a multi-user scheduling criterion by taking maximization of security capacity as a target. According to the method, multi-user scheduling is carried out by jointly considering path loss and small-scale fading, so that the safety capacity of an unmanned aerial vehicle communication system is improved to the greatest extent, and the communication quality from the unmanned aerial vehicle to a user terminal is effectively guaranteed.
Owner:NANJING UNIV OF POSTS & TELECOMM
Joint optimization method of safety capacity and energy consumption in wireless relay network
ActiveCN103227997BIncrease safety capacityFix security issuesEnergy efficient ICTPower managementWireless mesh networkCapacity value
The invention discloses a joint optimization method of safety capacity and energy consumption in a wireless relay network, and relates to the field of wireless relay network cooperative communication. The method comprises the steps as follows: a safety capacity value from a source node to a destination node is restrained to be SCcon; a minimum energy consumption function of an interference node is obtained by using a beam forming technology according to the SCcon; a minimum energy consumption function of a relay node is obtained according to the SCcon; a minimum energy consumption function Dpower of a system is obtained; a minimum energy consumption value of the system is obtained at an extreme point of a minimum value of the Dpower, and the restrained safety capacity is released; and an efficiency function RSE of the system energy consumption is calculated. The invention provides a joint optimization strategy of the relay node and the interference node, and an accurate expression of equivalent safety capacity maximization corresponding to the unit energy consumption of the system is obtained, so that each part of energy reaches the maximal usage value, and the problem of balance between the safety and the energy efficiency in the wireless relay network under a single sniffing node is effectively solved.
Owner:BEIJING UNIV OF POSTS & TELECOMM
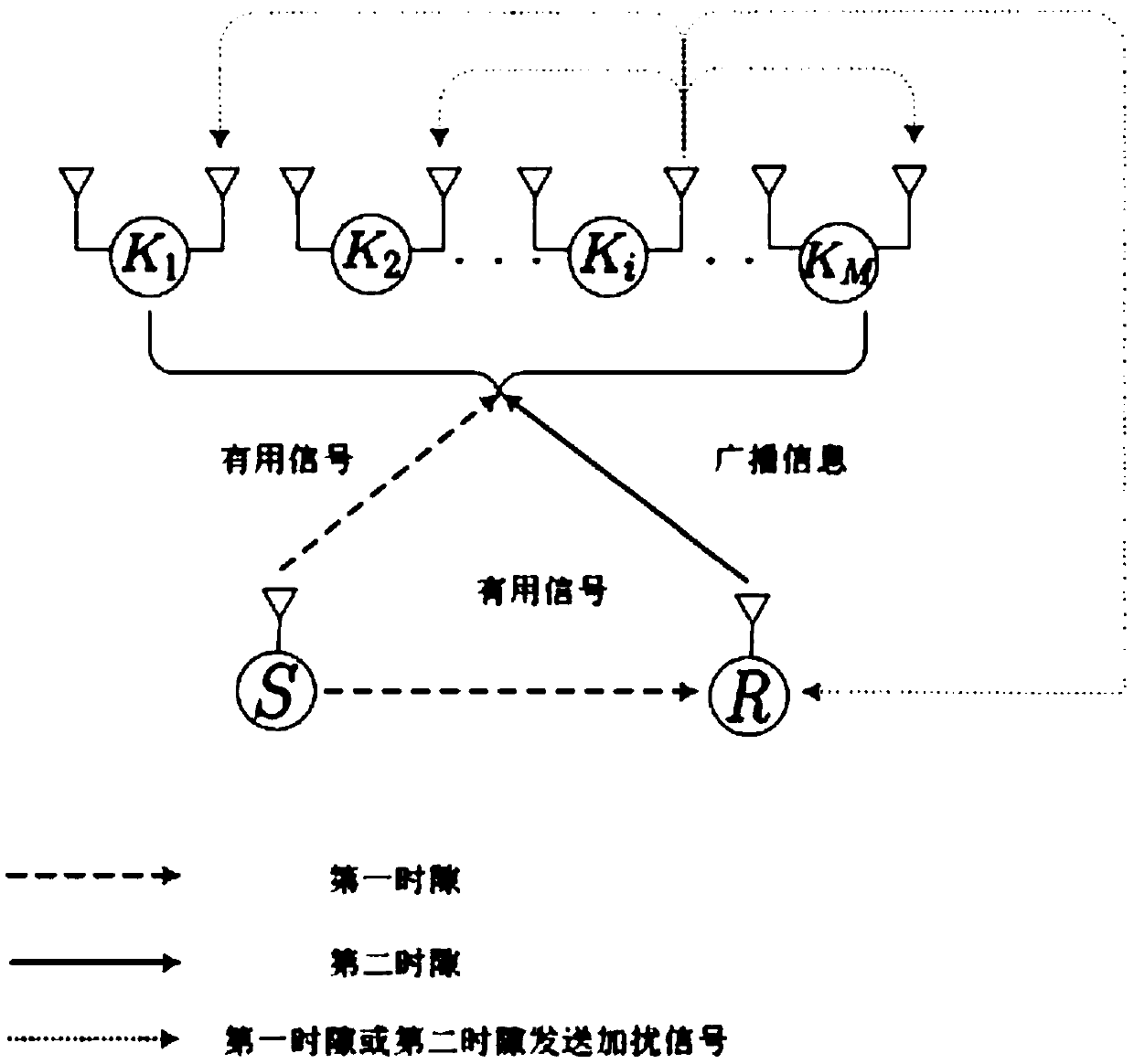
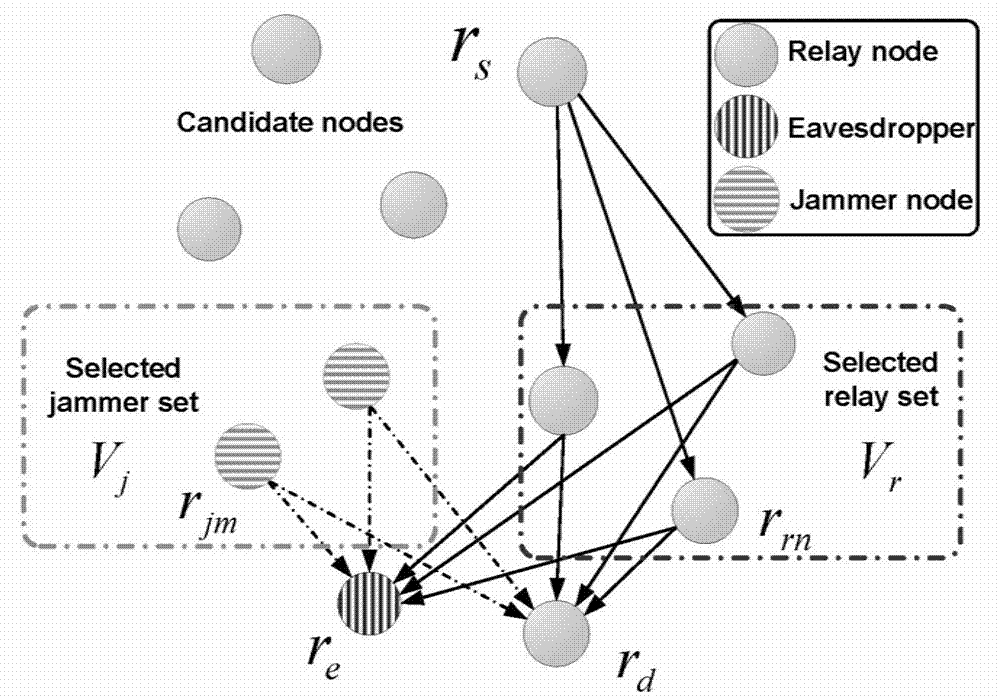
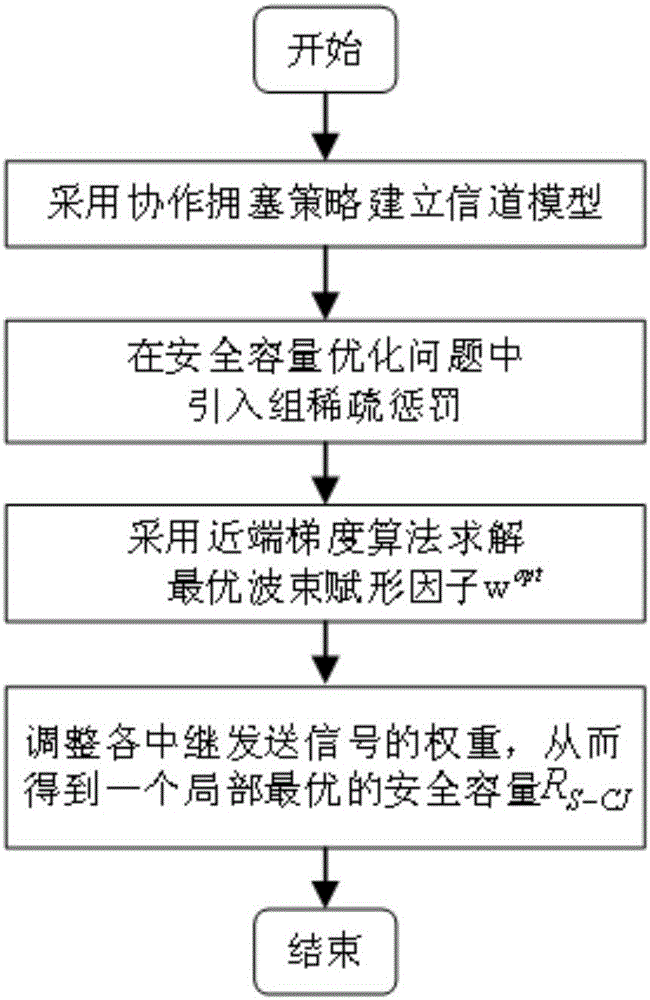
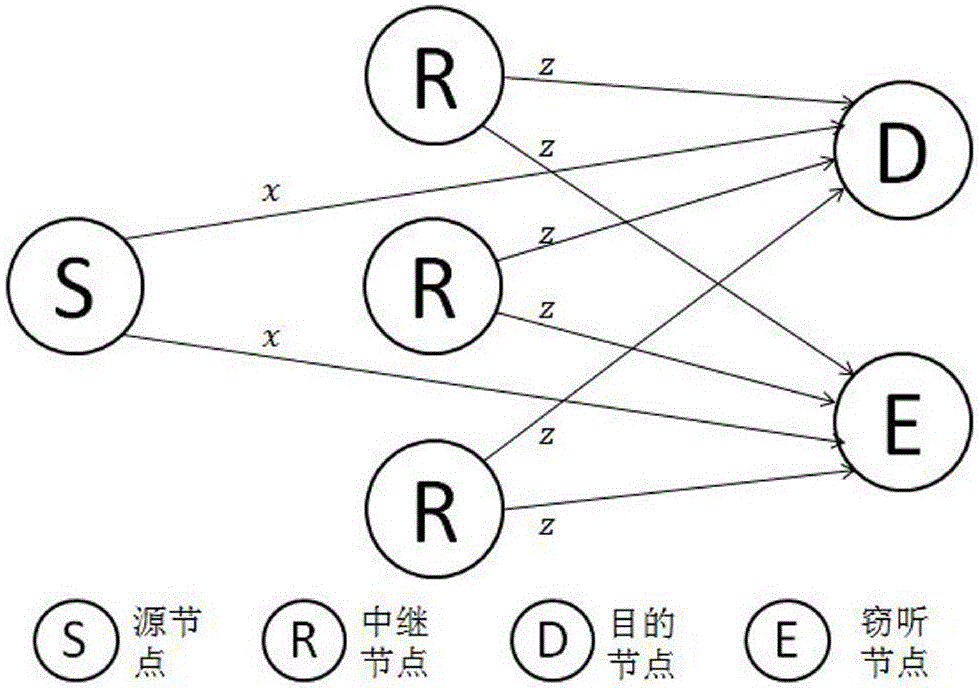
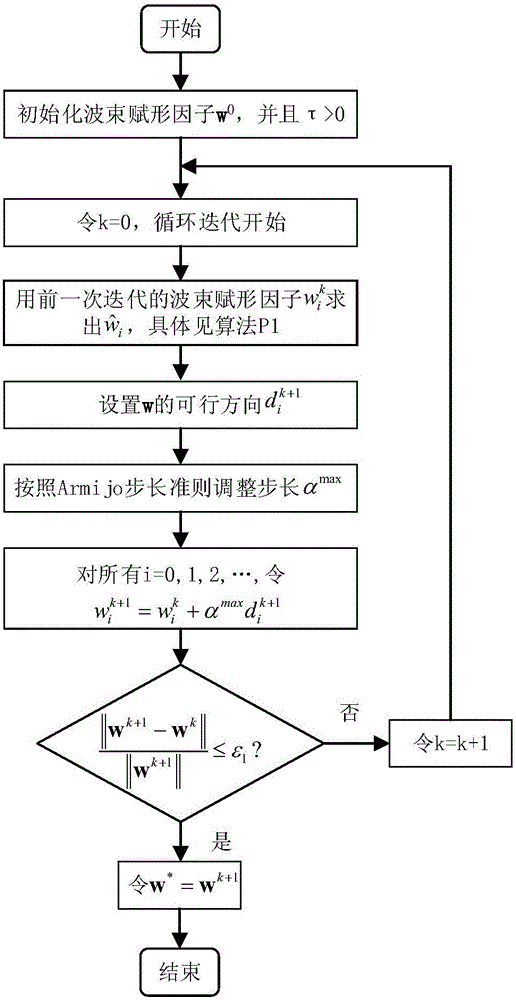
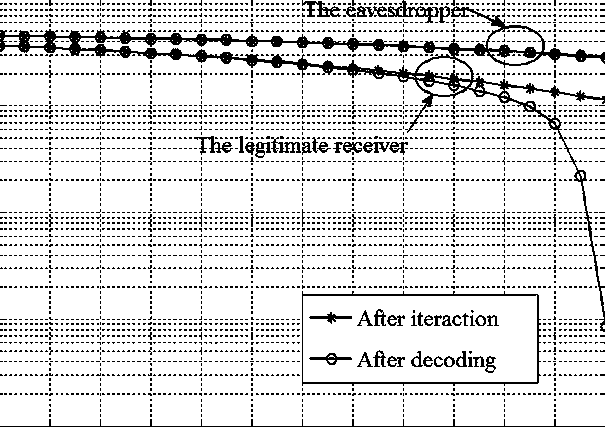
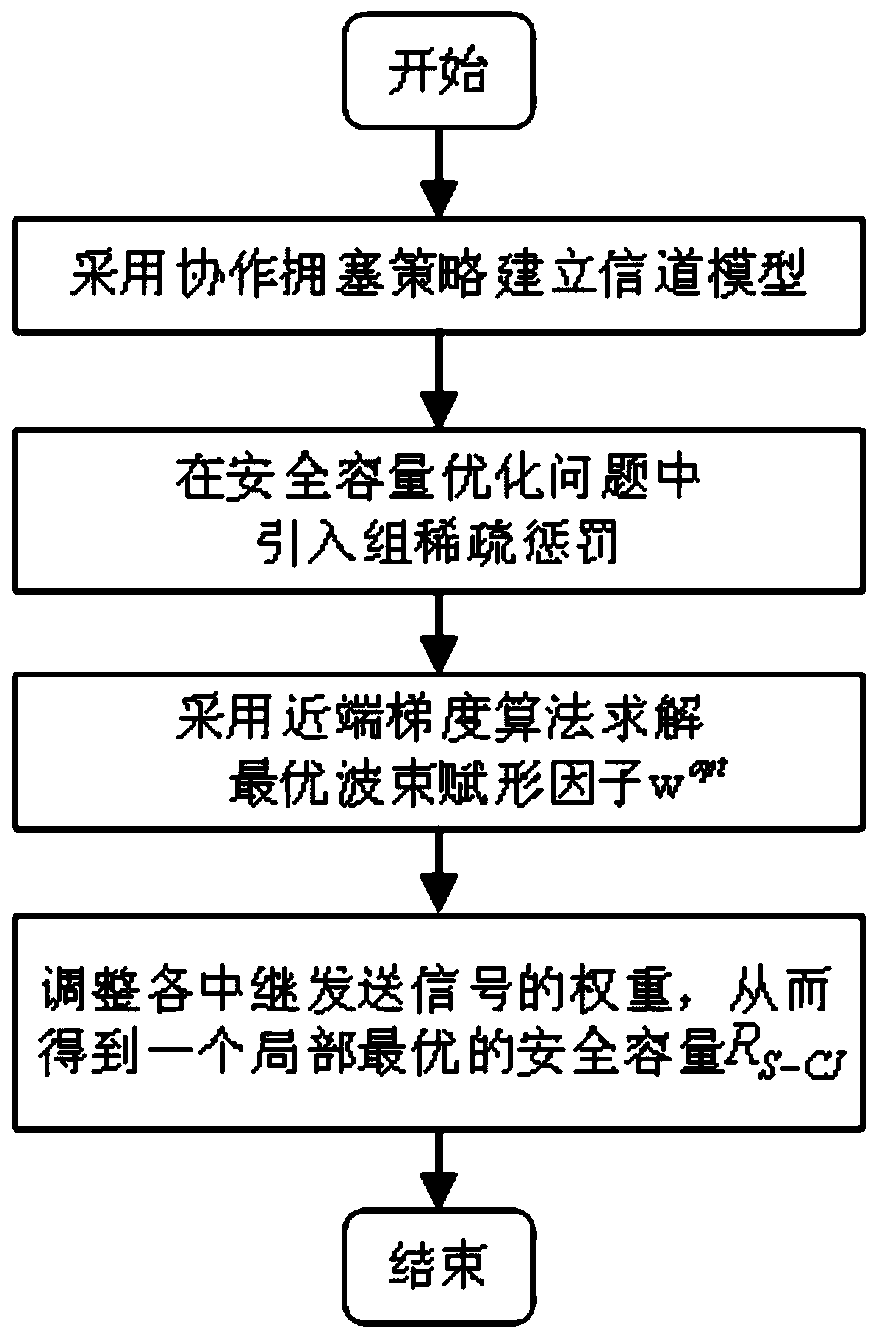
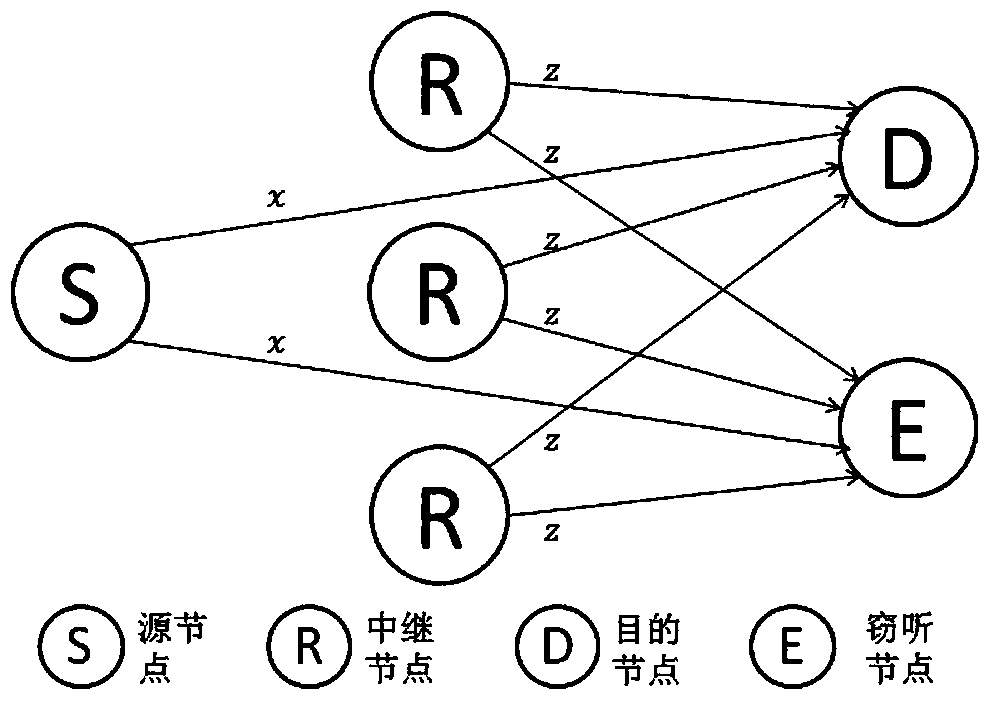
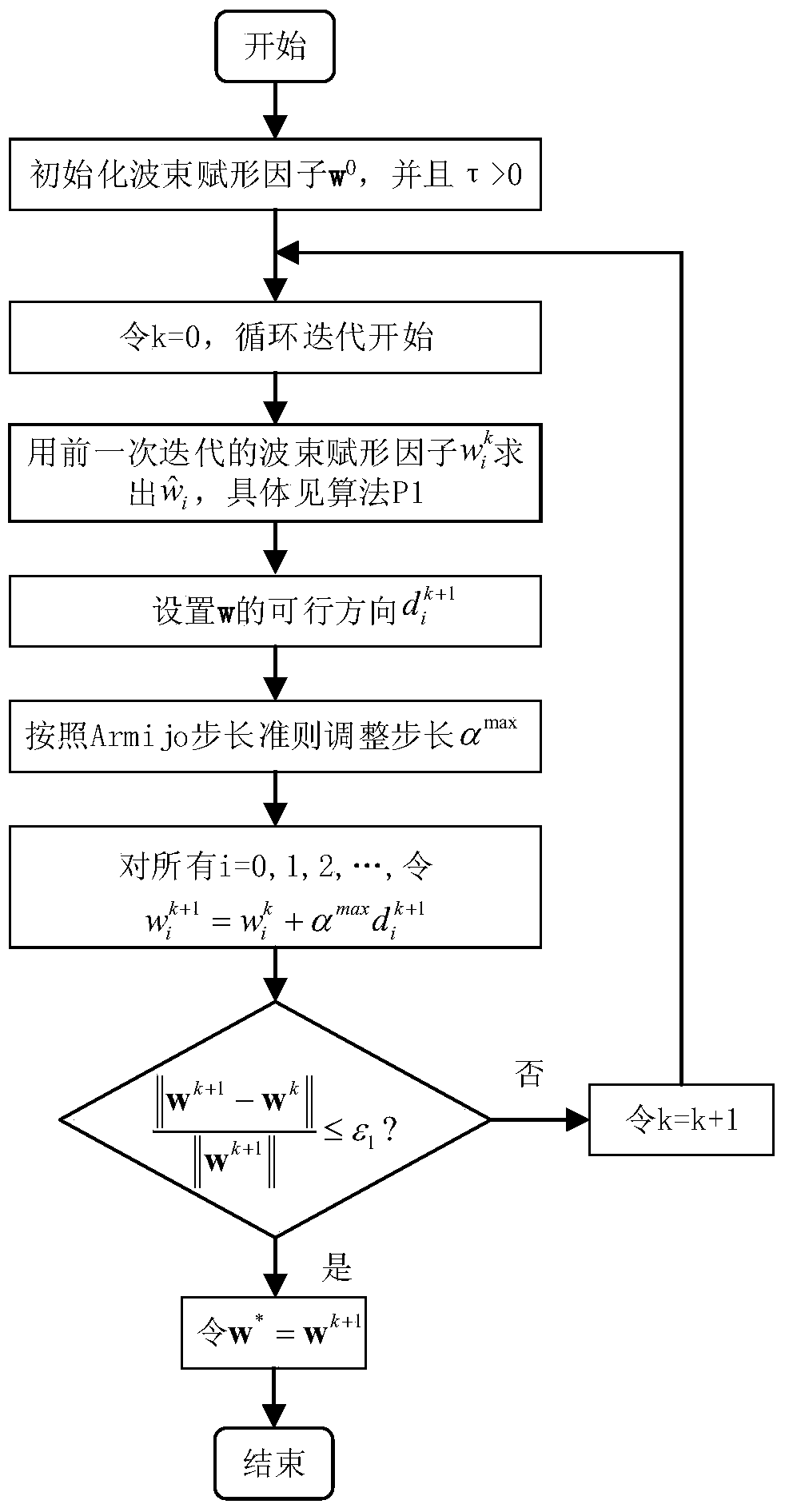
Cooperation congestion strategy method based on near-end gradient algorithm
InactiveCN105848195AIncrease safety capacityReduce power consumptionPower managementHigh level techniquesWiretap channelsComputer science
The invention discloses a cooperation congestion strategy method based on a near-end gradient algorithm, used for a wiretap channel system. The wiretap channel system comprises a source node, a destination node, a wiretap node and relay nodes; n relay nodes transmit interference signals of a band beam forming factor independent of complex signals while the source node broadcasts the complex signals to the destination node, such that the safety capacity is obtained; group sparse penalty is introduced into a safety capacity objective function; the optimal band beam forming factor is obtained according to the safety capacity, into which the group sparse penalty is introduced; then, weights of sending signals of various relay nodes are adjusted; power limitation conditions of the relay nodes are satisfied; and thus, the maximum safety capacity is obtained. According to the cooperation congestion strategy method disclosed by the invention, in the event that the relatively high safety capacity is kept, the total power consumption of relays and the use number of the relays are greatly reduced; and the relay efficiency is increased.
Owner:SOUTH CHINA UNIV OF TECH
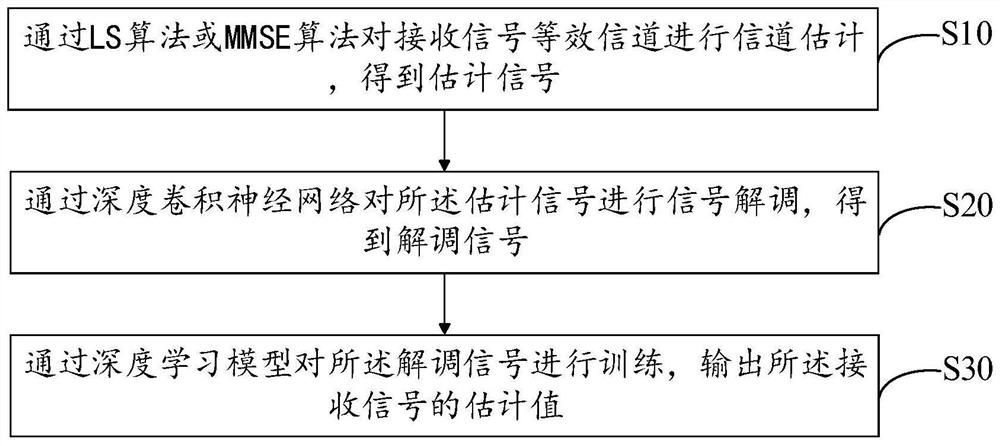
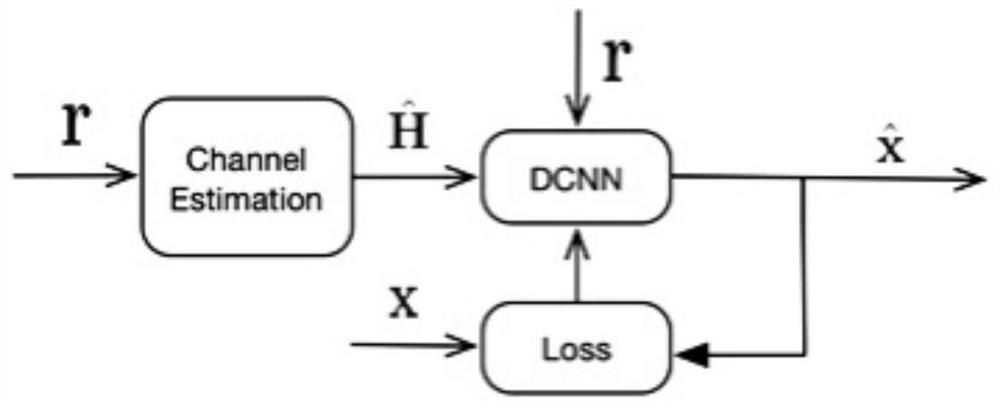
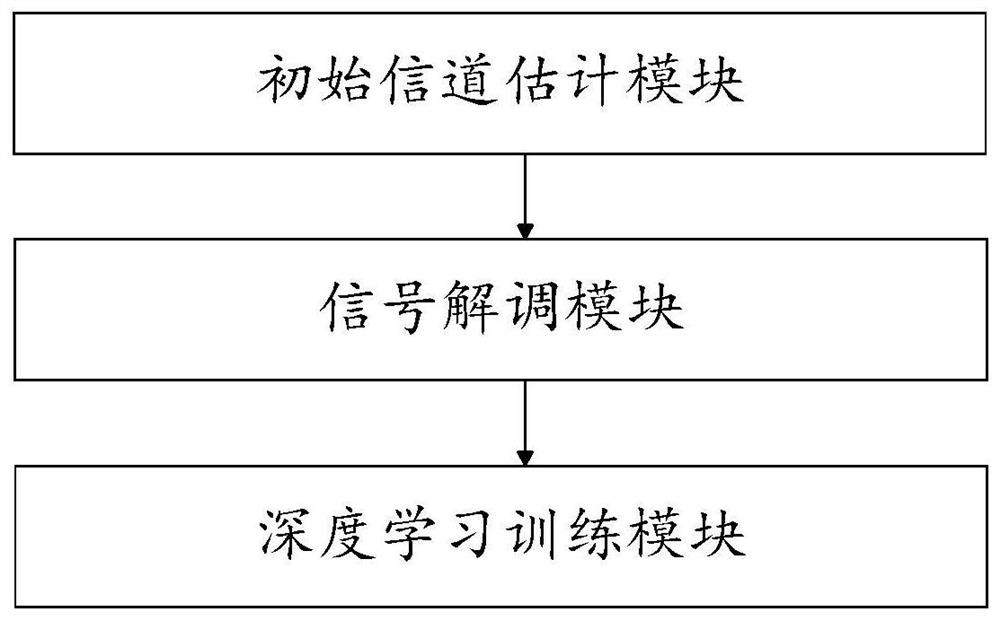
Wireless communication method and system based on deep learning under nonlinear distortion condition
ActiveCN111786915AIncrease safety capacitySpatial transmit diversityChannel estimationNonlinear distortionData set
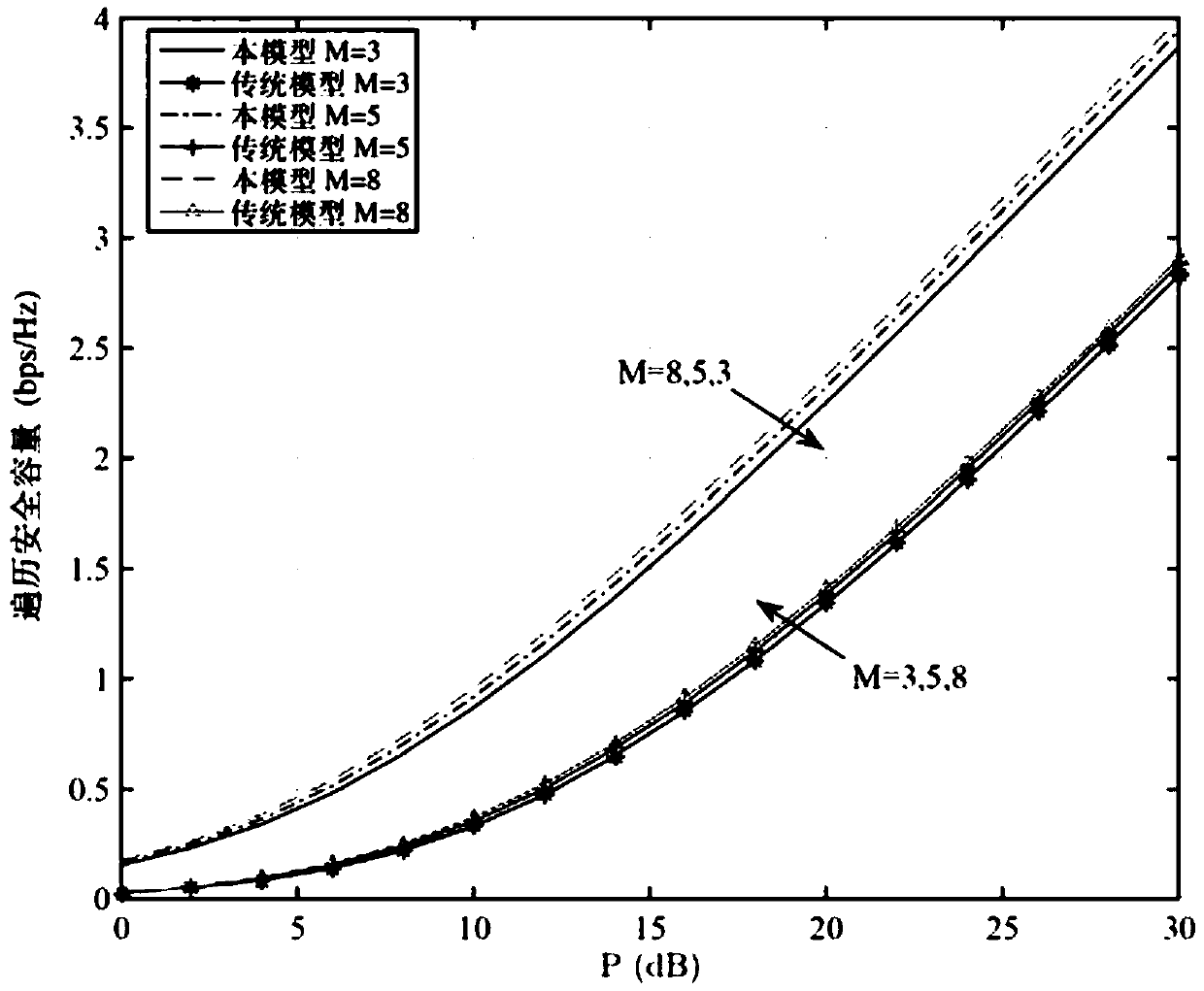
The invention discloses a wireless communication method and system based on deep learning under a nonlinear distortion condition, and the method comprises the steps: carrying out the channel estimation of an equivalent channel of a received signal through an LS algorithm or an MMSE algorithm, so as to obtain an estimated signal; demodulating the estimated signal through a deep convolutional neuralnetwork to obtain a demodulated signal; and training the demodulated signal through a deep learning model, and outputting an estimated value of the received signal. According to the method, a receiver architecture based on deep learning is adopted, and an initial channel estimation matrix is corrected through a large number of training data sets; and meanwhile, a deep learning network model is used for matching nonlinear distortion factors, so that the safety capacity of the system is improved.
Owner:GUANGZHOU PANYU POLYTECHNIC
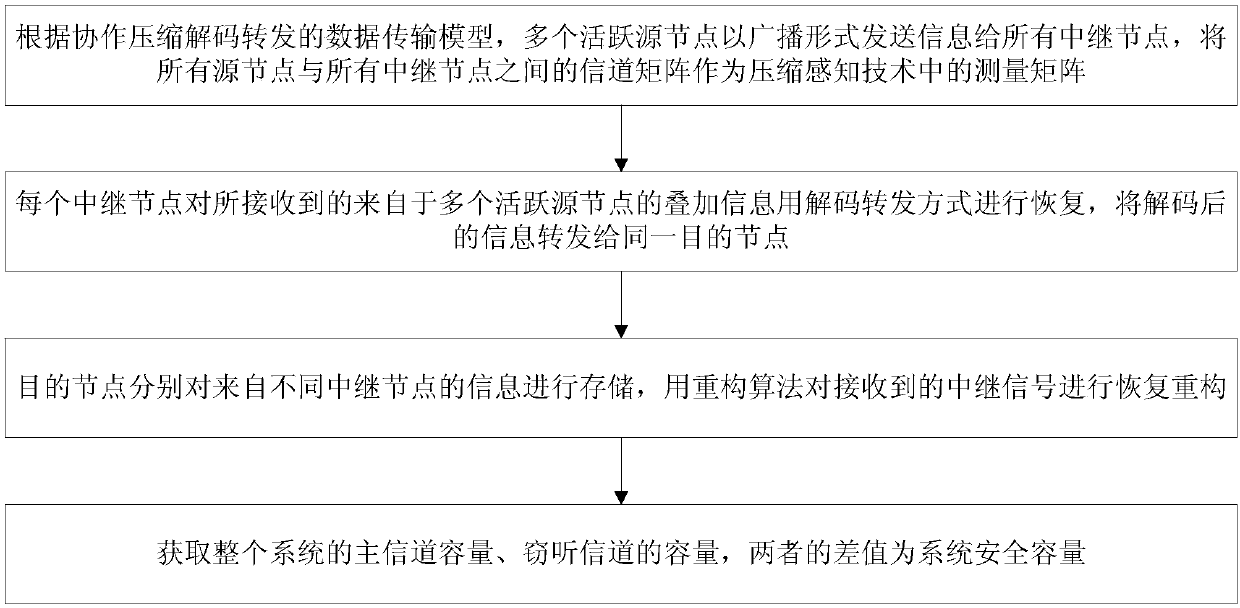
Data transmission method based on compressed sensing and decoding and forwarding
InactiveCN107612605AIncrease safety capacityAccurate reconstructionError preventionRadio transmissionComputer networkMain channel
The invention discloses a data transmission method based on compressed sensing and decoding and forwarding. The method comprises the following steps: a plurality of active source nodes send information to all relay nodes in a broadcast form according to a data transmission mode of cooperative compression decoding and forwarding, and channel matrixes among all source nodes and all relay nodes are used as measurement matrixes in the compressed sensing technology; each relay node restores the superposed information from the plurality of active source nodes and forwards the decoded information tothe same destination node; the destination node separately stores the information from different relay nodes, and restores and reconstructs the received relay signals by using a reconstructing algorithm; and the main channel volume of the whole system, the volume of an eavesdropping channel and the difference value of the two volumes are obtained to serve as secure volumes of the system. by adoption of the data transmission method, the security of the system is effectively ensured, the secure volume is improved, and the data can be ensured to be transmitted to the destination node effectivelyand securely.
Owner:TIANJIN UNIV
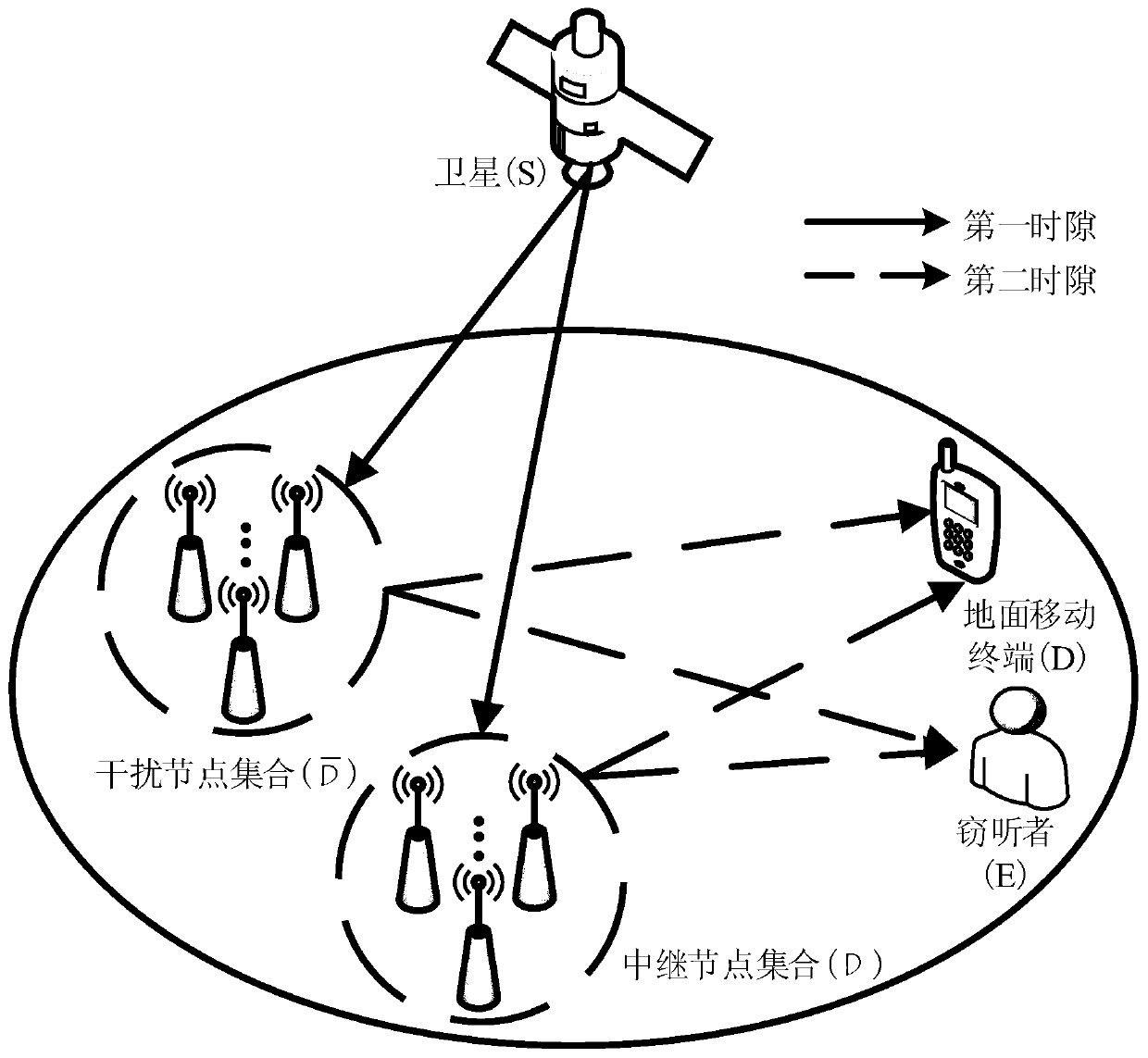
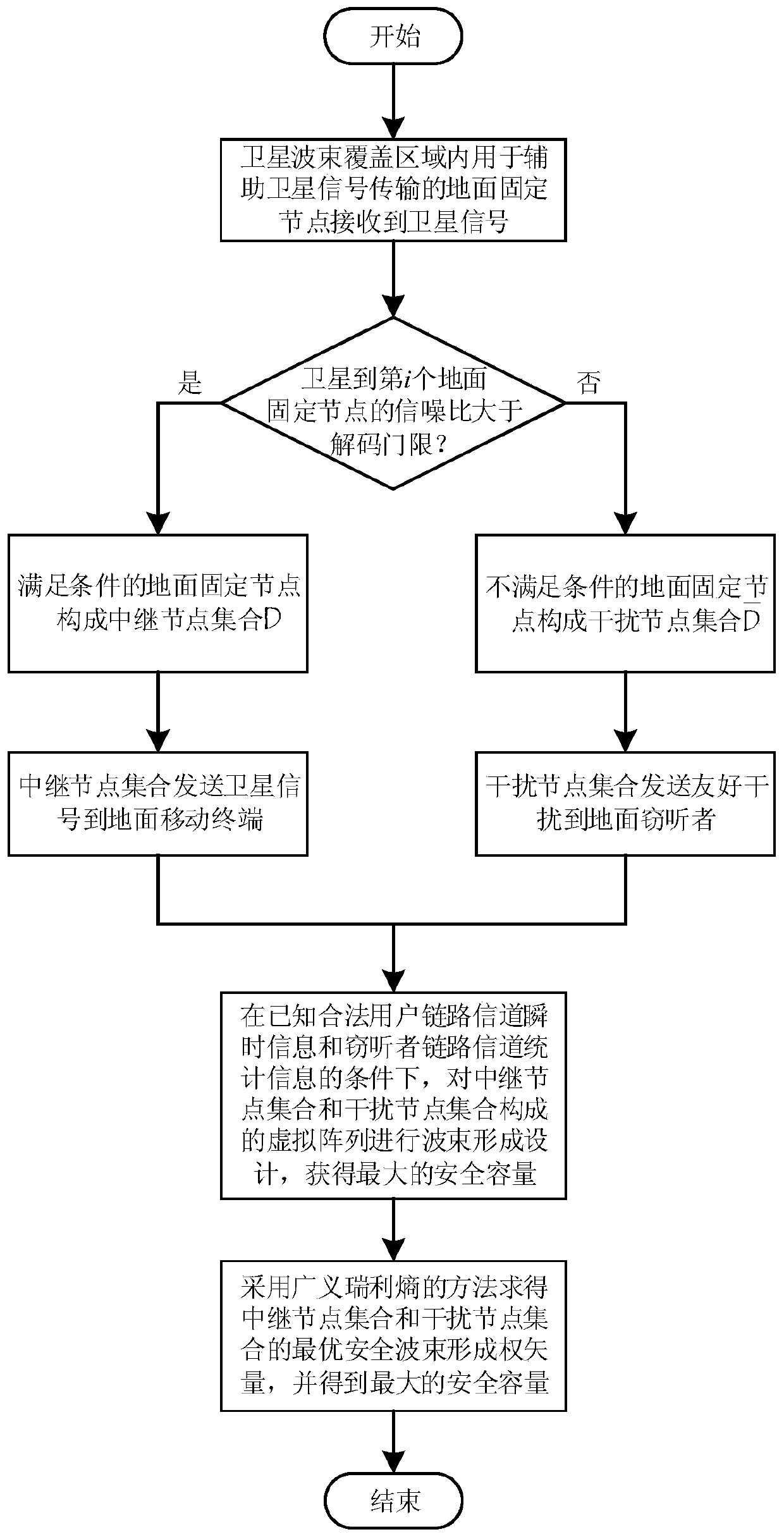
Satellite-ground fusion cooperative communication physical layer secure transmission method based on friendly interference
ActiveCN110086524AIncrease safety capacityImprove signal-to-noise ratioSpatial transmit diversityWireless communicationSignal-to-noise ratio (imaging)Communications system
The invention discloses a satellite-ground fusion cooperative communication physical layer secure transmission method based on friendly interference, and the method comprises the steps of calculatingthe output signal-to-noise ratio of a satellite to each ground fixed node according to a satellite signal received by each ground fixed node; enabling the ground fixed nodes of which the output signalto noise ratios are greater than a decoding threshold to form a relay node set used for decoding and forwarding the satellite signals; and enabling ground fixed nodes of which the output signal to noise ratios are smaller than the decoding threshold to form an interference node set used for sending the friendly interference to a ground eavesdropper so as to realize the safe transmission of the satellite information. Under the condition that the instantaneous information of a legal user link channel and the statistical information of an eavesdropper link channel are known, a virtual array formed by the relay node set and the interference node set is subjected to beamforming design, so that the maximum system security capacity is obtained. Compared with an existing relay selection method, the method has the advantage that the physical layer safety transmission performance of a satellite-ground fusion cooperative communication system can be remarkably improved.
Owner:NANJING UNIV OF POSTS & TELECOMM
A two-way full-duplex mimo relay antenna selection security transmission method
ActiveCN108900225BIncrease channel capacityWeakened receiving signal to interference and noise ratioSite diversitySpatial transmit diversitySecure transmissionTrunking
The invention discloses a bidirectional and duplex MIMO (Multiple Input Multiple Output) relay antenna selection and safety transmission method. A duplex MIMO relay system comprises a user A, a user B, a relay and an eavesdropper, wherein the user A, the user B, the relay R and the eavesdropper E are provided with a plurality of antennas; the method comprises the following steps: acquiring a transmitting antenna of the user A, a transmitting antenna of the user B and a receiving antenna of the relay; acquiring a receiving antenna of the user A, a receiving antenna of the user B and a transmitting antenna of the relay; acquiring a receiving signal-to-noise ratio of the user A, a receiving signal-to-noise ratio of the user B and a receiving signal-to-noise ratio of the eavesdropper E based on the transmitting antenna and the receiving antenna of the user A, the transmitting antenna and the receiving antenna of the user B and the receiving antenna and the transmitting antenna of the relay; acquiring an instantaneous safety capacity of the duplex MIMO relay system based on the receiving signal-to-noise ratio of the user A, the receiving signal-to-noise ratio of the user B and the receiving signal-to-noise ratio of the eavesdropper E. According to the bidirectional and duplex MIMO relay antenna selection and safety transmission method, optimal transmitting and receiving antennas areselected and the safety capacity of the whole system can be effectively improved.
Owner:HUAQIAO UNIVERSITY
A kind of nanostructure quasi-solid electrolyte for lithium-ion battery or lithium-sulfur battery and its preparation method and application
ActiveCN105070946BImprove thermal stabilityImprove electrochemical stabilitySolid electrolytesCell seperators/membranes/diaphragms/spacersMetallic lithiumElectrolytic agent
The invention discloses a nanostructure quasi-solid electrolyte for lithium-ion batteries or lithium-sulfur batteries and its preparation method and application. The nanostructure quasi-solid electrolyte is a macroscopic solid electrolyte formed by absorbing an ion-conducting agent from an inorganic-organic hybrid frame material material; its preparation method is to soak the inorganic-organic hybrid frame material in the ion-conducting agent and fully mix it under a protective atmosphere, and then volatilize the excess solvent; the prepared nanostructure quasi-solid electrolyte has higher lithium ion conductivity, which can At the same time, it replaces the organic electrolyte and separator in the traditional lithium-ion battery, which can effectively avoid the safety problems caused by the leakage of the organic electrolyte; the lithium battery assembled with the electrolyte can use metal lithium sheets as the negative electrode.
Owner:CENT SOUTH UNIV
Cloud wireless access network system and security scheduling method of physical layer thereof
InactiveCN106454840AMaximize safe capacityIncrease safety capacityAssess restrictionSecurity arrangementAccess networkCommunications system
The invention discloses a cloud wireless access network system comprising a central processor, base stations, legitimate users and eavesdropping users, one central processor is arranged, more than one base stations are arranged, the central processor is connected with the base stations, and the base stations are respectively connected with the legitimate users and the eavesdropping users. The invention further discloses a security scheduling method of a physical layer of the cloud wireless access network system. According to the security scheduling method disclosed by the invention, the maximum safe capacity of a cloud wireless access network is achieved by a simple base station selection algorithm; the optimal base station can be selected by the comparison of chain gains of legitimate links and eavesdropping links in active set base stations, the active set base stations are selected by a predetermined selection criterion, so the maximum safe capacity of the system can be guaranteed under different channel conditions, and the safe capacity of the system is improved by real-time link control without affecting the original communication system.
Owner:GUANGZHOU PANYU POLYTECHNIC
A method for constructing the first type of eavesdropping channel under the bi-awgn broadcast channel
ActiveCN106209710BImprove reliabilityEnhanced channel quality advantageDc level restoring means or bias distort correctionCodes simulation/testingBroadcast channelsTelecommunications
A method for establishing a first side channel under a BI-AWGN broadcast channel includes the steps that a legal receiver sends feedback information through a binary input additive white Gaussian noise broadcast channel, and a legal sender and an eavesdropper receive the feedback information influenced by noises respectively; the legal sender encodes to-be-sent information according to the received feedback information and sends the to-be-sent information through an error-free public channel, wherein the complexity degree of system obtaining is reduced; after the legal receiver receives the information of the legal sender, bit logarithm likelihood ratio information is extracted and is then decoded in a soft decision decoding mode, and a soft decision decoding algorithm with high reliability is selected for use, wherein the reliability of a main channel is improved, the quality difference of the main channel and the side channel is expanded, and the security capacity of the first side channel is further improved; the eavesdropper passively eavesdrops the information of the legal sender and conducts decoding in a soft decision decoding mode. The method is low in difficulty, high in channel security capacity and high in transmission rate.
Owner:HENAN UNIV OF SCI & TECH
A Cooperative Congestion Strategy Method Based on Proximal Gradient Algorithm
InactiveCN105848195BIncrease safety capacityReduce power consumptionPower managementHigh level techniquesNODALWiretap channels
The invention discloses a cooperation congestion strategy method based on a near-end gradient algorithm, used for a wiretap channel system. The wiretap channel system comprises a source node, a destination node, a wiretap node and relay nodes; n relay nodes transmit interference signals of a band beam forming factor independent of complex signals while the source node broadcasts the complex signals to the destination node, such that the safety capacity is obtained; group sparse penalty is introduced into a safety capacity objective function; the optimal band beam forming factor is obtained according to the safety capacity, into which the group sparse penalty is introduced; then, weights of sending signals of various relay nodes are adjusted; power limitation conditions of the relay nodes are satisfied; and thus, the maximum safety capacity is obtained. According to the cooperation congestion strategy method disclosed by the invention, in the event that the relatively high safety capacity is kept, the total power consumption of relays and the use number of the relays are greatly reduced; and the relay efficiency is increased.
Owner:SOUTH CHINA UNIV OF TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com