A Cooperative Congestion Strategy Method Based on Proximal Gradient Algorithm
A near-end gradient and strategy technology, applied in the field of wireless communication, can solve the problems of multi-relay quantity and relay power, ignore interference signals, etc., and achieve the effect of reducing total power consumption and improving relay efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
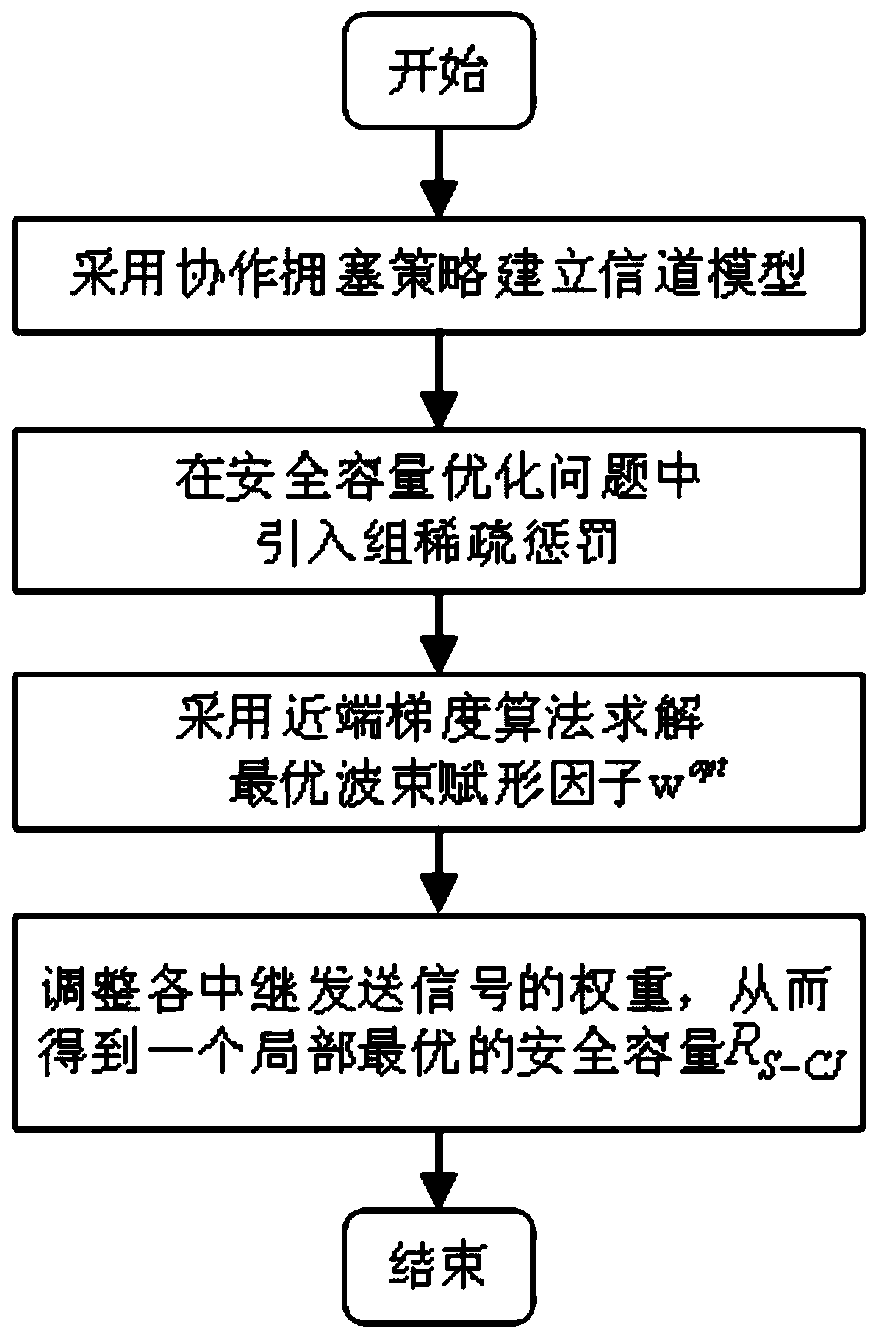
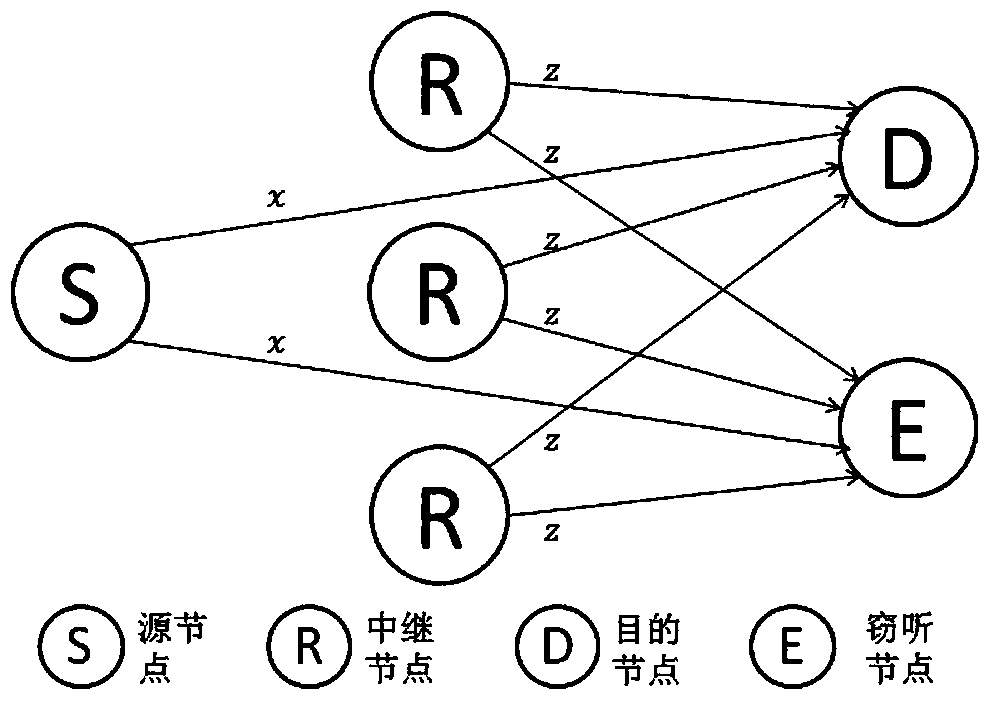
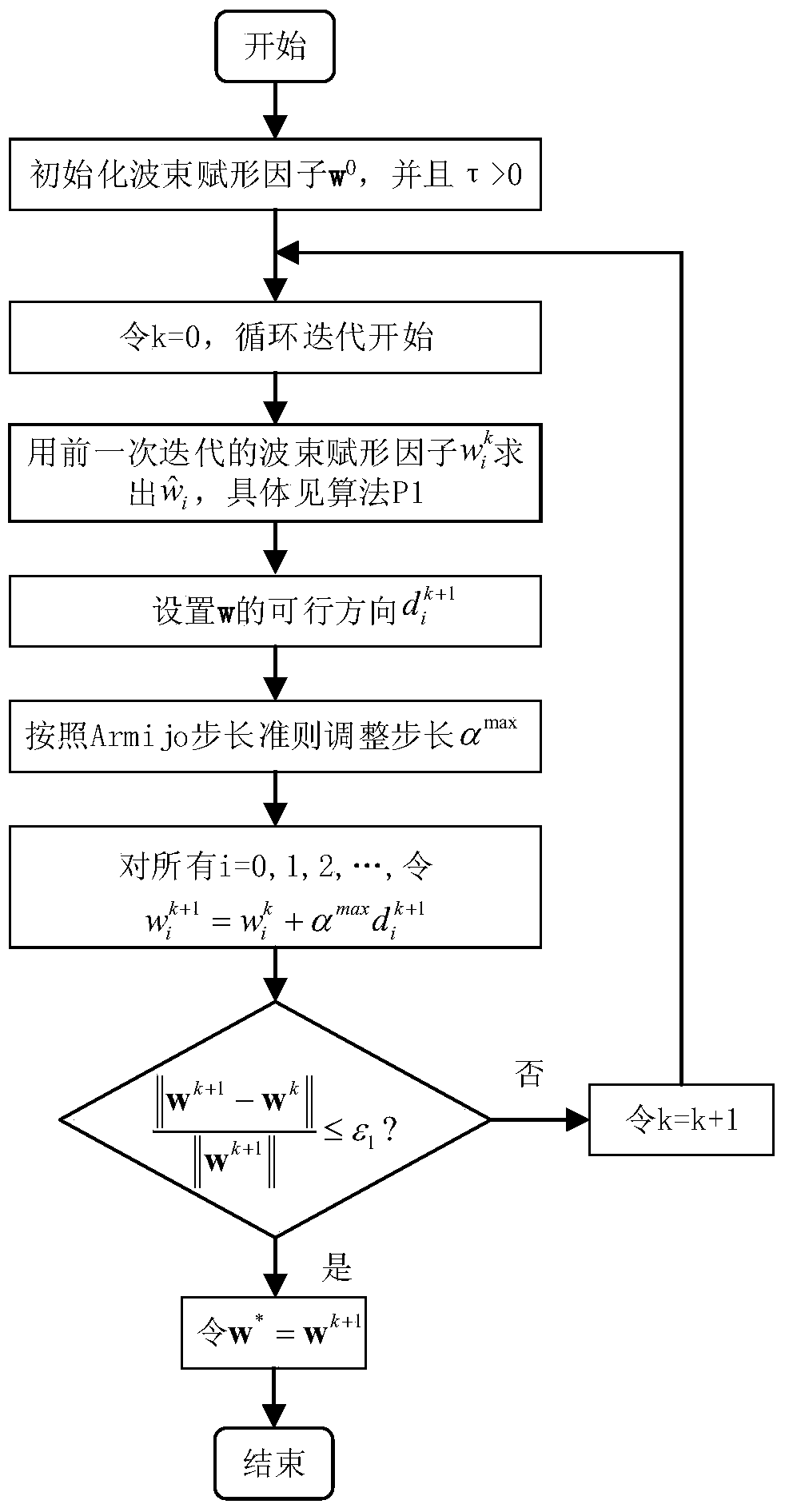
[0027] Such as figure 1 As shown, a cooperative congestion strategy method based on the near-end gradient algorithm for wiretapping channel systems, such as figure 2 As shown, the eavesdropping channel system includes a source node S, a destination node D, an eavesdropping node E and n relay nodes R, and the core step is to obtain the optimal beamforming factor w opt It is used to adjust the weight of n relay nodes R transmitting interference signal z, and the ultimate goal is to increase the safety capacity R S-CJ , to get a local optimum.
[0028] Specifically include the following steps:
[0029] S1 When the source node S broadcasts a complex signal x to the destination node D, n relay nodes transmit an interference signal z with a beamforming factor w independent of the complex signal x, so as to confuse the signal received by the eavesdropper E , get the safety capacity R S-CJ , the beamforming factor is w=(w 1 ,w 2 ,...,w n ) T , also represents the weight facto...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com