Big data implementation system and method based on network security
A technology of network security and big data, which is applied in the field of big data implementation system based on network security, can solve problems such as heavy workload, data loss, and network congestion during data, to reduce cost investment, ensure safety and integrity, and improve Effect of data security input level
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
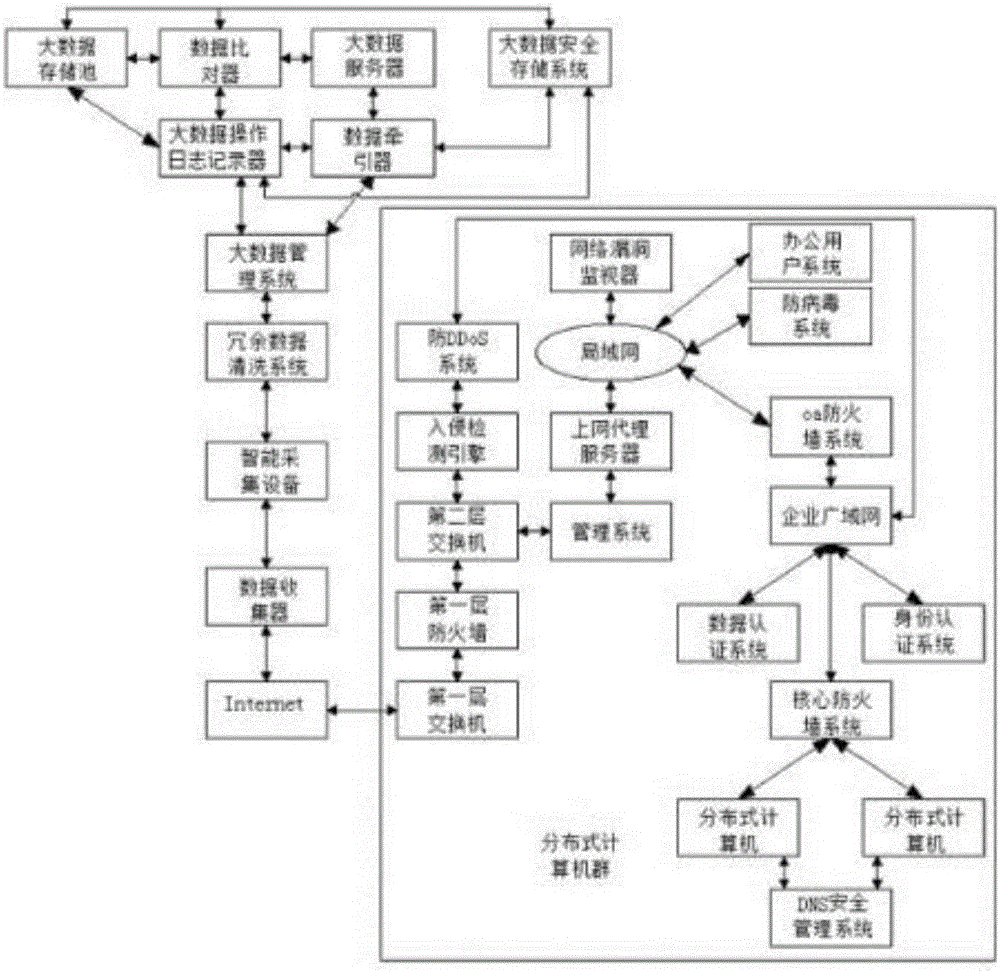
[0069] A big data implementation system and method based on network security, such as figure 1 As shown, a big data processing platform and a distributed computer group connected to the big data processing platform are provided, and a data collector, an intelligent collection device, a redundant data cleaning system, and a big data management system are arranged in the big data processing platform , a data tractor, a big data server, a data comparator, a big data storage pool, a big data operation log recorder and a big data safe storage system, the distributed computer group and the data collector are all connected to the Internet, and the data collection The device is sequentially connected to the intelligent acquisition equipment, the redundant data cleaning system and the big data management system, the big data management system is connected to the big data server through the data tractor, and the big data server is connected to the big data storage pool through the data c...
Embodiment 2
[0076] This embodiment is further optimized on the basis of the above embodiments, further to better realize the network security implementation system of the present invention, such as figure 1 As shown, the following structure is particularly arranged: the distributed computer group is provided with a first-layer switch, a first-layer firewall, a second-layer switch, an intrusion detection engine, an anti-DDoS system, and an enterprise network architecture, and the first The layer switch is connected to the first layer firewall, the second layer switch, the intrusion detection engine and the anti-DDoS system in turn, the second layer switch and the anti-DDoS system are connected to the enterprise network architecture, and the first layer switch is connected to the Internet.
[0077] The architecture of the distributed computer group has the following characteristics:
[0078] It can protect against DDoS attacks, hackers, viruses, worms and other common security threats on th...
Embodiment 3
[0082] This embodiment is further optimized on the basis of the above embodiments, further to better realize the network security implementation system of the present invention, such as figure 1 As shown, it is specially set to the following structure: a local area network user architecture and a wide area network user architecture are arranged in the enterprise network architecture, and the local area network user architecture is connected with the second-layer switch and the wide area network user architecture respectively, and the said wide area network user architecture is connected with the Anti-DDoS system is connected.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com