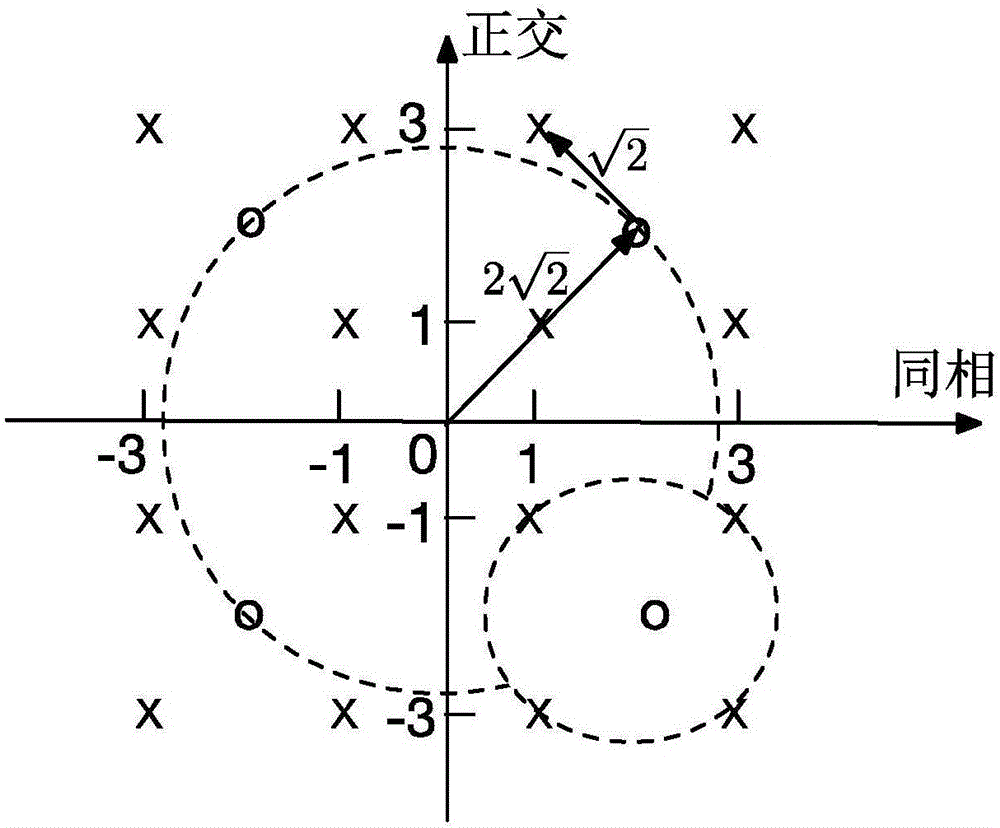Physical layer secret communication method based on modulation symbol phase rotation
A modulation symbol, phase rotation technology, applied in the field of wireless communication and information security, can solve the problems of reduced information transmission security, low key entropy, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0056] The present invention will be specifically described below in conjunction with the accompanying drawings.
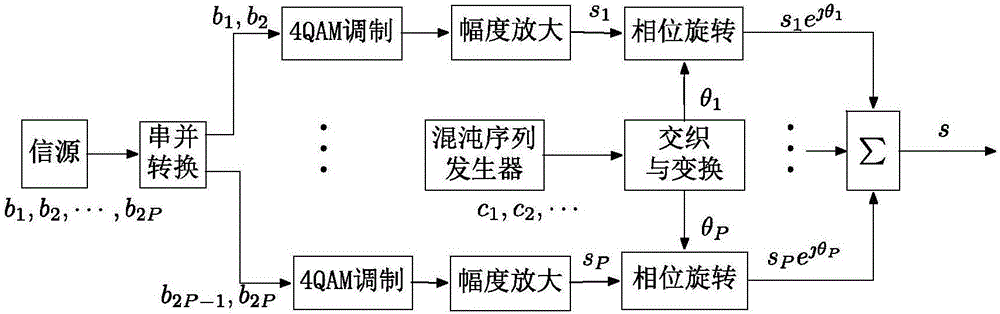
[0057] refer to Figure 1 to Figure 6 , a physical layer secure communication method based on modulation symbol phase rotation, including an encryption process and a decryption process of the physical layer;
[0058] The encryption process of the physical layer includes the following steps:
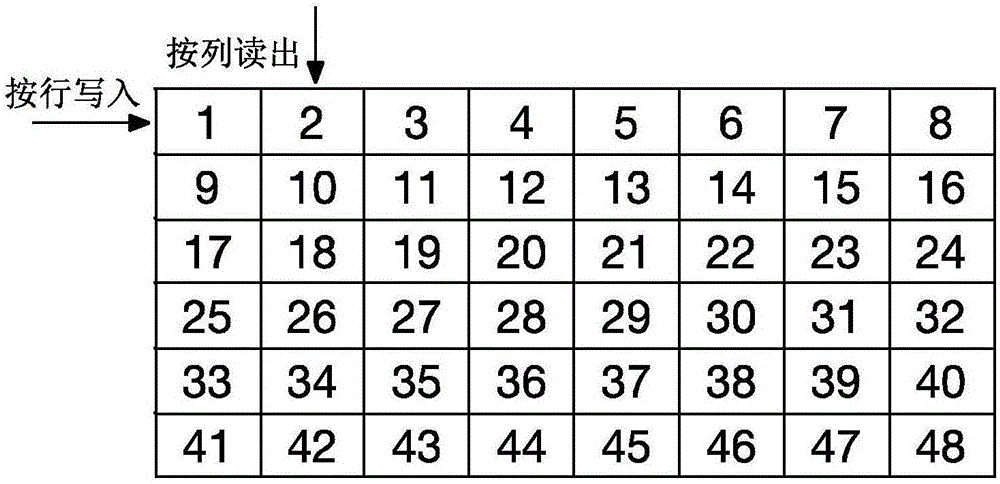
[0059] 1-1: Use the Tent mapping equation to generate a set of uniformly distributed chaotic sequences, and the number of seeds of the chaotic sequence is determined by the channel coefficient and the negotiation mechanism. A group of chaotic sequences are interleaved by an interleaver to generate P groups of chaotic sequences.
[0060] 1-2: Use the P sets of chaotic sequences obtained in step 1-1 to generate P sets of rotation phases, which are used to change the phase of 4QAM symbols, and each 4QAM symbol corresponds to a rotation phase.
[0061] 1-3: The bit information...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com