Cooperative vector secure transmission method and system for resisting pilot pollution attack
A pilot pollution and safe transmission technology, applied in the field of information communication, can solve the problems of complex detection scheme algorithm, reduced practicability, poor practicability, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
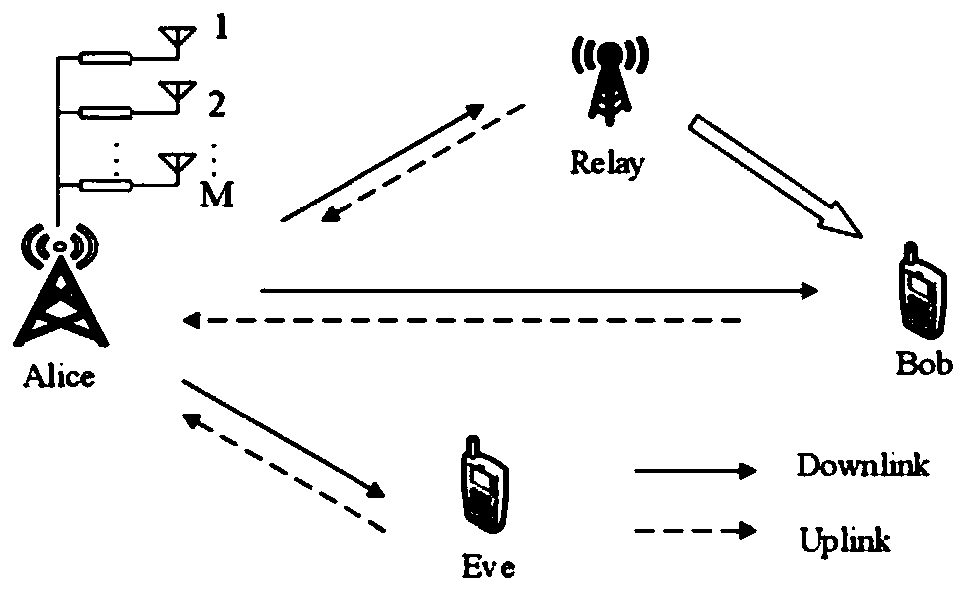
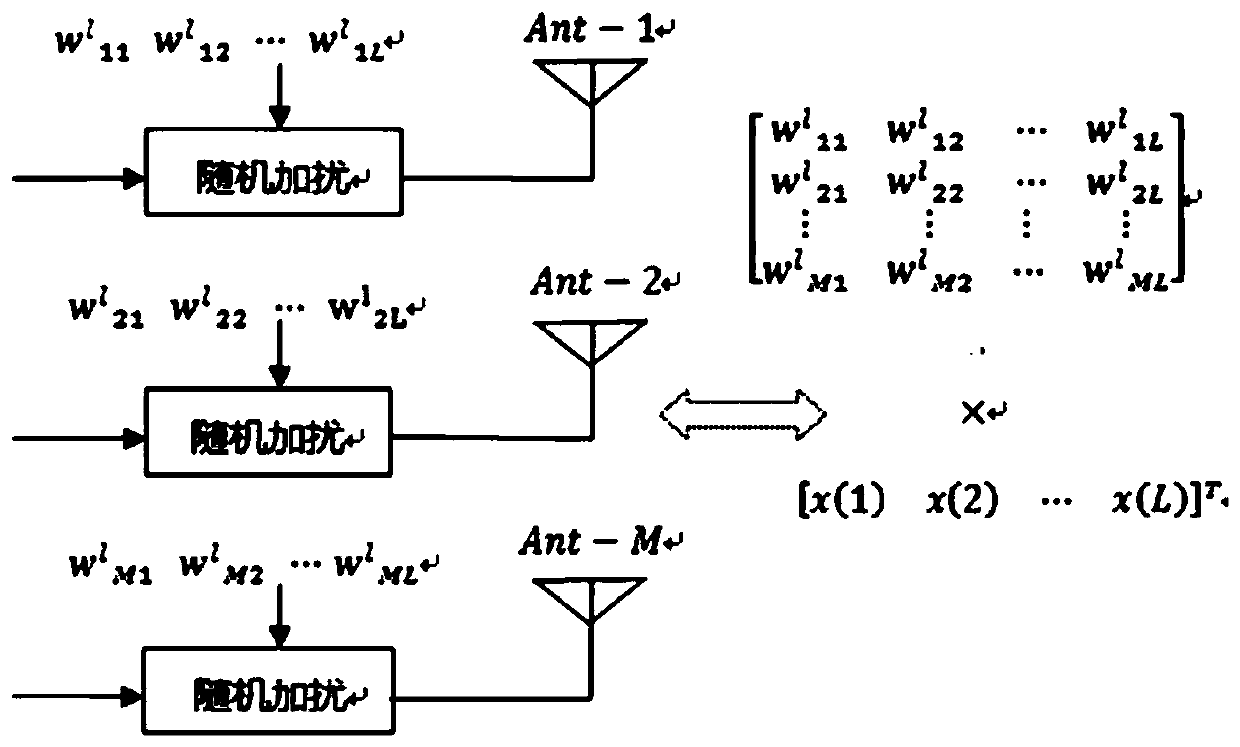
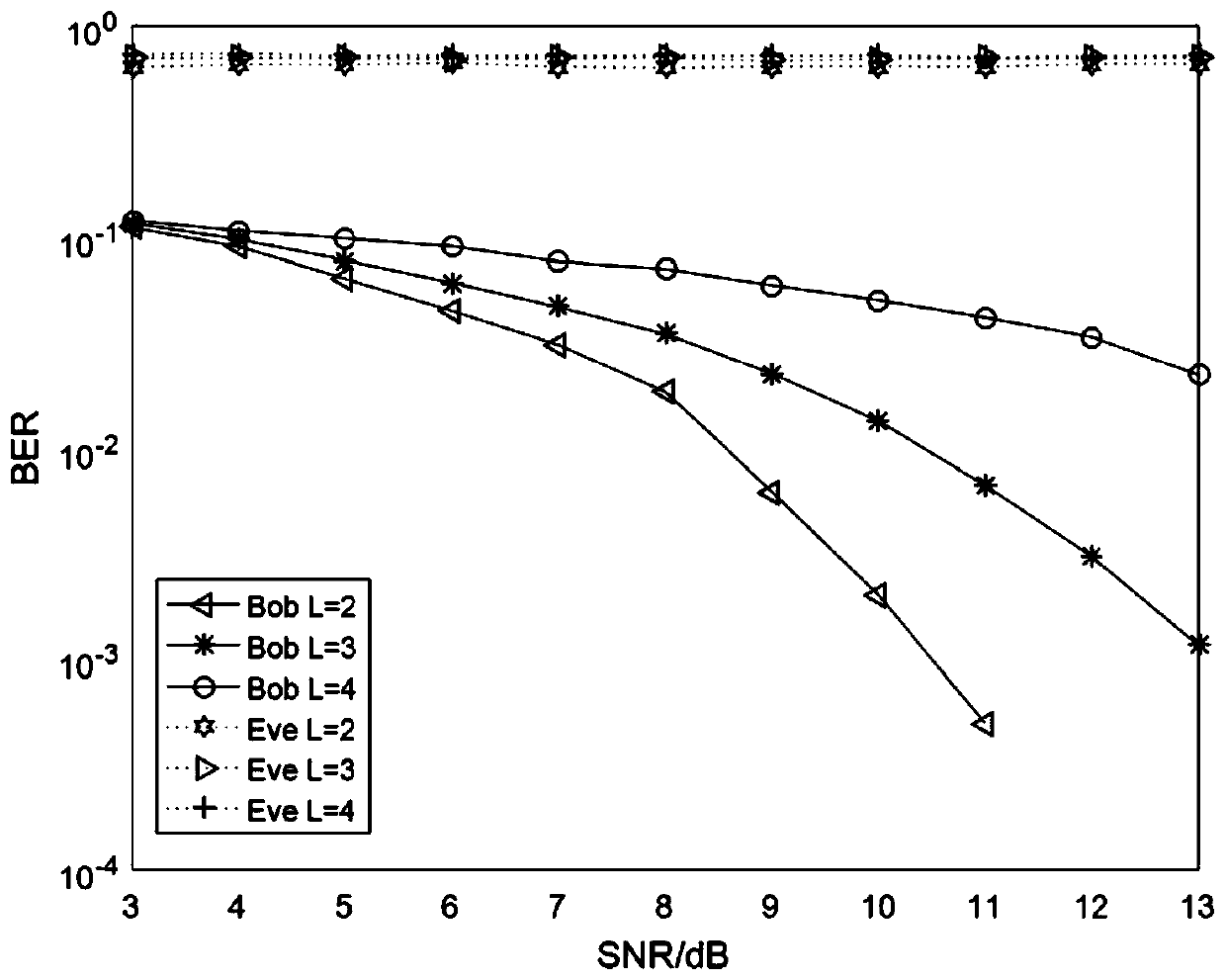
[0044] The communication model of the present invention is as figure 1 shown. Relay is a trusted auxiliary node (for example, the base station relay node deployed by the operator), and together with the legal receiver Bob, the sender Alice, and the attacker Eve, constitutes the sender-assistant node-receiver-attacker eavesdropping model. Without loss of generality, it is assumed that the sender Alice has M antennas, the auxiliary node Relay, the legal receiver Bob, and the attacker Eve all use a single antenna to transmit and receive. Assume that Eve has obtained in advance the reverse pilot sequence that Bob will send to Alice, and can send the same reverse pilot signal strictly synchronously with Bob through signal tracking. Therefore, Alice cannot tell which components of the received superimposed reverse pilot sequence signal come from the legal receiver Bob and which ones come from the attacker Eve. The channel from Alice to Bob is denoted as According to channel reci...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com