Secure transmission method using fountain code for multiple feedbacks
A technology of secure transmission and fountain code, which is applied in the field of communication, can solve the problems of reducing the decoding rate of input symbols at the eavesdropper's end and the high quality requirements of legitimate channels, and achieve the goal of expanding the advantages of legal channels, low requirements for channel conditions, and realizing safe transmission Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
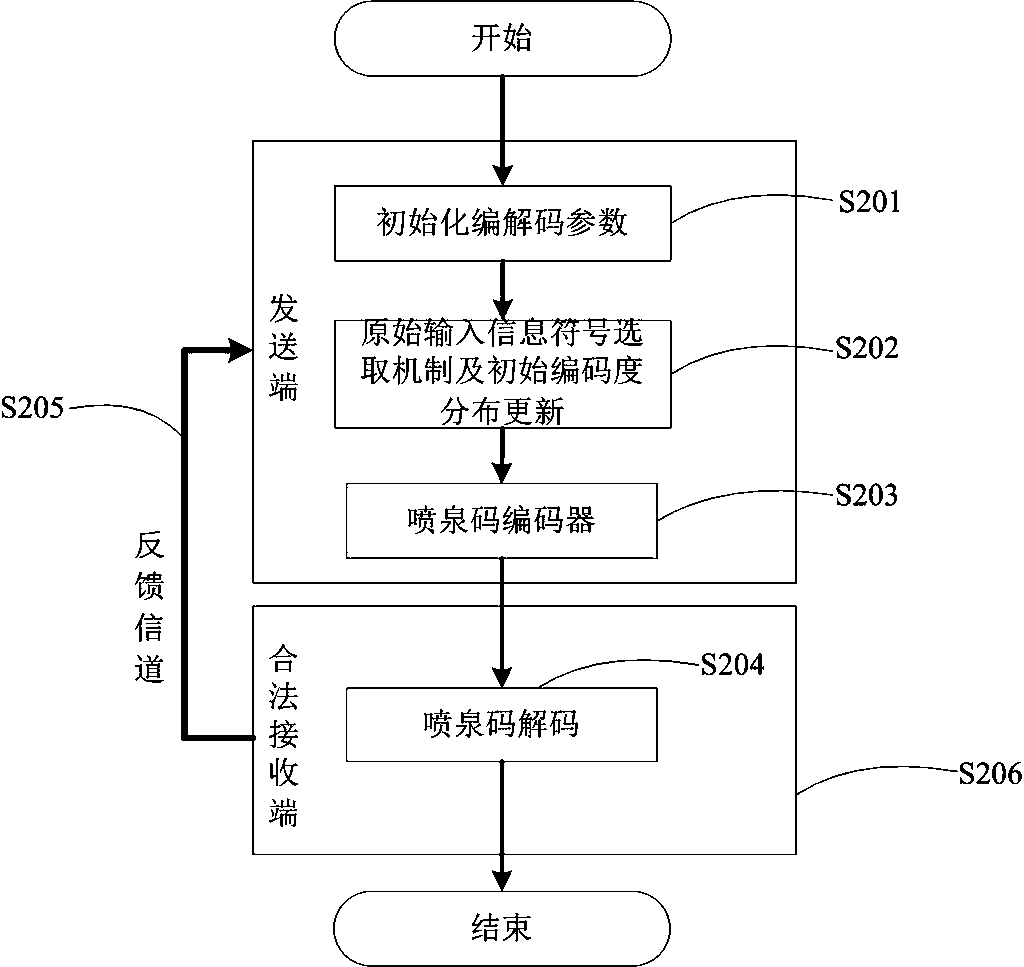
[0050] Such as figure 1 As shown, a secure transmission method using multiple feedbacks of fountain codes according to an embodiment of the present invention includes the following steps:
[0051] Step S101: Initialize an original input information symbol set and a coding degree distribution at the sending end, where the original input information symbol set includes a plurality of original input information symbols.
[0052] Step S102: The sending end optimizes and updates the original input information symbol selection mechanism and encoding degree distribution in the encoding and decoding process according to the decoding situation of the legal receiving end. Adjustment of distribution value range.
[0053]Step S103: The sending end divides the encoding and decoding process into multiple encoding and decoding stages based on the time when the feedback information sent by the legal receiving end is received, and in each encoding and decoding stage, the symbol selection mech...
Embodiment 2
[0058] Such as figure 2 As shown, another embodiment of the present invention provides a secure transmission method utilizing multiple feedbacks of fountain codes, comprising the following steps:
[0059] Step S201: Initialize an original input information symbol set and a coding degree distribution at the sending end, where the original input information symbol set includes a plurality of original input information symbols.
[0060] Step S202: The sending end optimizes and updates the original input information symbol selection mechanism and encoding degree distribution in the encoding and decoding process according to the decoding situation of the legal receiving end. Adjustment of distribution value range.
[0061] The step S202 includes:
[0062] Step S2021: Change the value range of the coding degree distribution to the number of original input information symbols that have not yet been decoded by the legal receiving end.
[0063] Step S2022: Remove the original input...
Embodiment 3
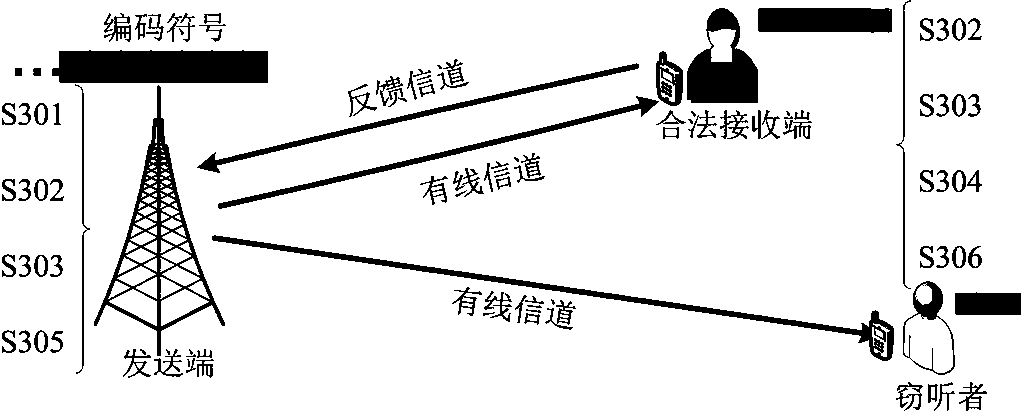
[0086] Such as image 3 As shown, the application of a secure transmission method using fountain code multiple feedbacks in the wired communication scenario according to the embodiment of the present invention. The channel quality of the wired network is better, and the transmission channel can be regarded as a deletion channel. The user may receive the correct data, or may not receive the data packet due to network congestion and other reasons. Based on the method of the present invention, the reliability and security of communication can be guaranteed simultaneously, and the method includes the following steps:
[0087] Step S301: Initialize the original input information symbol set and the encoding degree distribution, where the original input information symbols can be randomly generated, and the encoding degree distribution adopts the classic Robust Soliton Distribution (RSD).
[0088] Step S302: According to the feedback mechanism of the present invention, calculate the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com