Physical layer secure transmission method for resisting information eavesdropping of eavesdropping node
A physical layer security and eavesdropping node technology, applied in the field of physical layer security, can solve the problems of eavesdropping node interference, security cannot be guaranteed, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0035] The present invention is described in further detail below in conjunction with accompanying drawing:
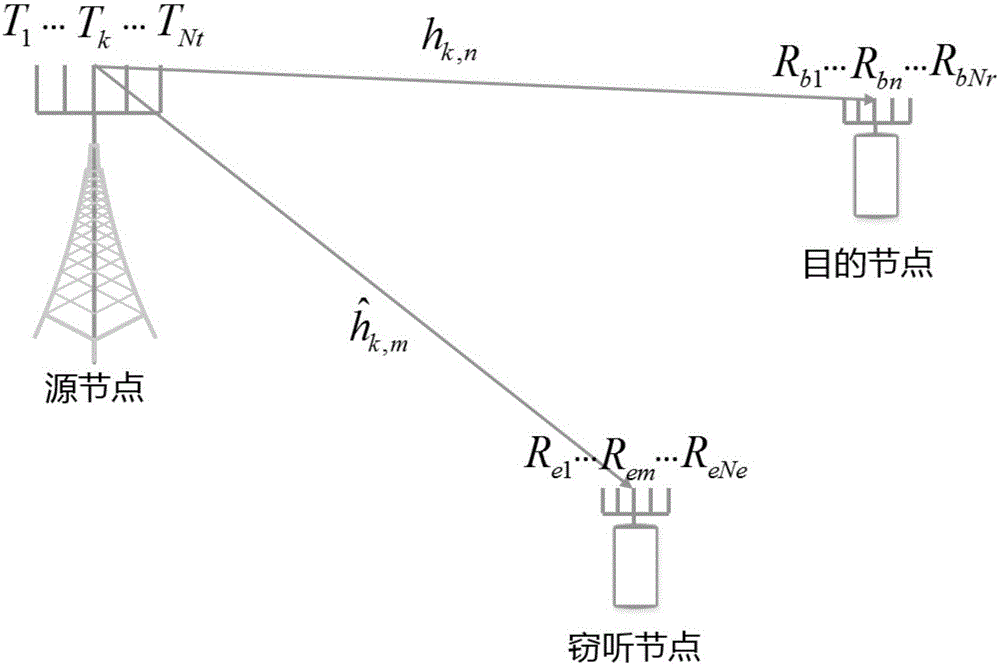
[0036] refer to figure 1 , the physical layer secure transmission method against eavesdropping nodes stealing information described in the present invention comprises the following steps:
[0037] 1) Before the information transmission starts, both the source node and the destination node send the training sequence sequentially, so that the source node and the destination node can estimate the equivalent channel information h from the source node to the destination node n,k , where n∈{1,...,N r}, k ∈ {1,...,N t}, N t The number of antennas set for the source node, N r is the number of antennas of the destination node;
[0038] 2) The source node encodes the data to be sent, obtains the symbol to be sent and the serial number of the antenna that sends the symbol to be sent, then adds artificial noise to the symbol to be sent, and then sends the symbol to be sent af...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com