Network secret key interaction system, device and method
A technology of network keys and interactive information, which is applied in transmission systems, digital transmission systems, secure communication devices, etc., can solve problems such as information leakage, poor wireless network communication security, and damage to the interests of multiple parties, and achieve the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach
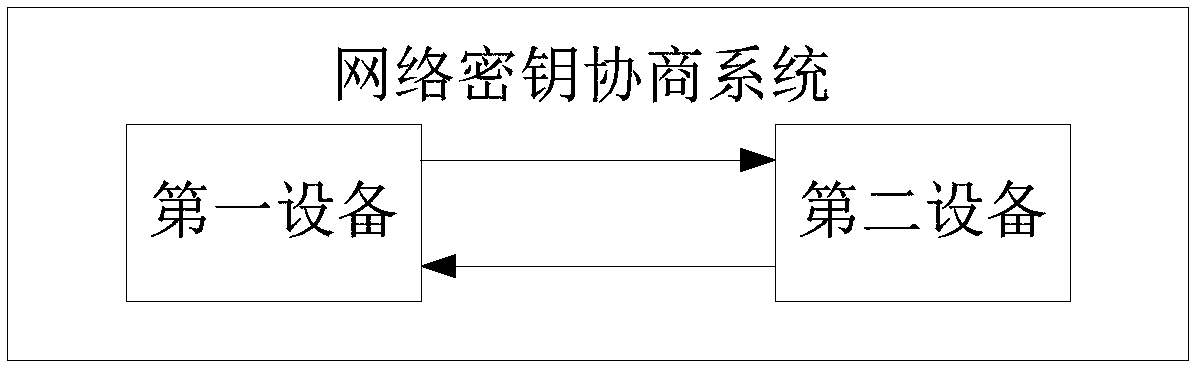
[0080] In the above process (1), the first interaction information also carries the first timestamp T encrypted with the security key ks i1 .
[0081] In process (2), the second device will use the security key ks to encrypt the first time stamp T i1 To decrypt, obtain and save T i1 .
[0082] In the process (4), the second device is also used to use the network key K NWK For the first timestamp T i1 Perform encryption to generate timestamp encrypted information; carry the timestamp encrypted information in the fourth interaction information ω, and send the fourth interaction information ω to the first device.
[0083] Wherein, the fourth mutual information ω satisfies the following formula: ω=(T i1 )K NWK .
[0084] In addition, the fourth interaction information ω may also be generated based on other information exchanged between the first device and the second device during the foregoing interaction process, such as first round information, second round information, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com