Image encryption method and image decryption method with visual security and data security based on compressed sensing
A technology of compressed sensing and data security, which is applied in the field of decryption and image addition, can solve the problems of anti-chosen plaintext attack and poor known plaintext attack, improve the secret key space, enhance the ability to resist violent attacks, and improve the ability to attack Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
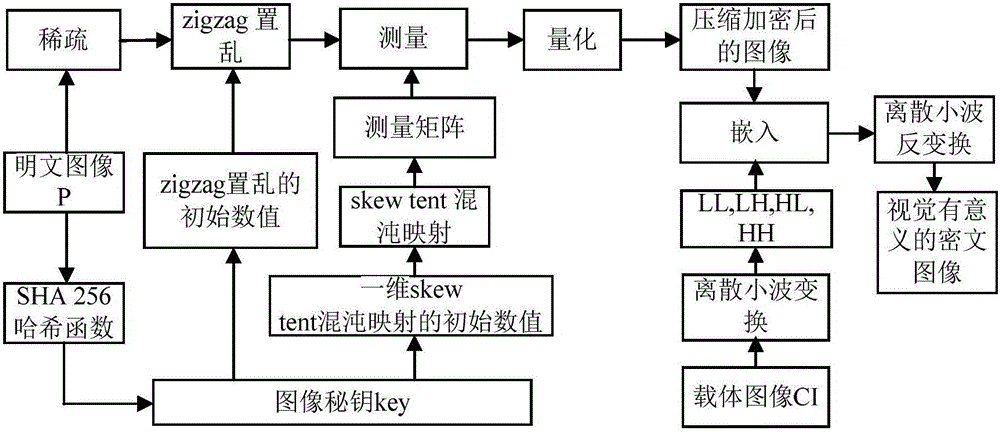
[0078] Example 1, see figure 1 As shown, an image encryption method based on compressed sensing for visual security and data security includes the following steps:
[0079] Step 1. Use the SHA 256 hash function to calculate the plaintext image P of size m×n to obtain the image secret key, and calculate the initial value of the one-dimensional skew tent chaotic map and zigzag scrambling;
[0080] Step 2. Use discrete wavelet transform to sparse the plaintext image P to obtain the coefficient matrix P1; scramble the coefficient matrix P1 according to the zigzag path to obtain the scrambled matrix P2; modify the matrix P2 by preset threshold TS , Get the corrected matrix P3;
[0081] Step 3. Use one-dimensional skew tent chaotic mapping to generate a measurement matrix Φ for compressed sensing, and measure matrix P3 to obtain a measurement value matrix P4, where the compression rate of the plaintext image P is expressed as CR, and the size of the measurement matrix Φ Is M×N, then M=CR×...
Embodiment 2
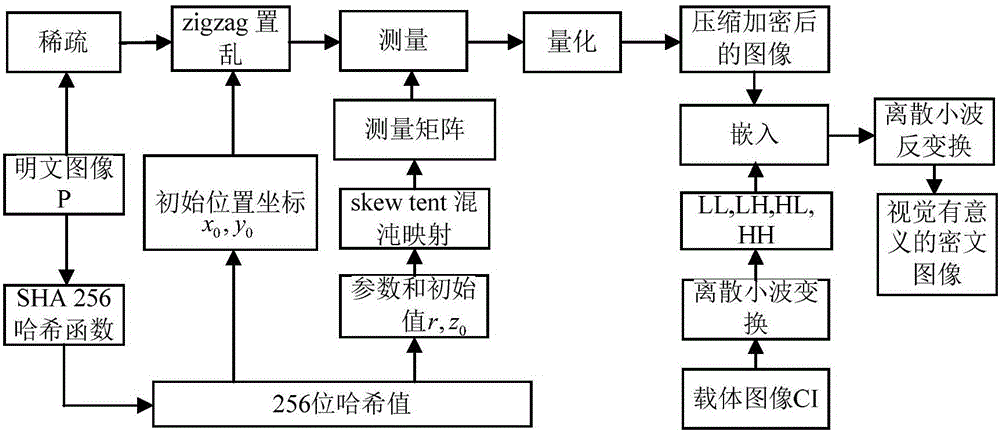
[0085] Example two, see figure 2 As shown, an image encryption method based on compressed sensing for visual security and data security includes the following contents:
[0086] 1. Use the SHA 256 hash function to calculate the plaintext image P of size m×n to obtain the image secret key, and calculate the initial value of the one-dimensional skew tent chaotic map and zigzag scrambling; calculate the one-dimensional skew tent chaotic map And the initial value of zigzag scrambling, including: converting the image secret key key to 32 decimal numbers k 1 , K 2 ,..., k 32 , And calculate the parameters and initial values of the one-dimensional skew tent chaotic map, and the initial position coordinates of the zigzag scrambling.
[0087] Preferably, the one-dimensional skew tent chaotic map is expressed as:
[0088]
[0089] Among them, r∈(0,1) is the system parameter, z∈(0,1) is the state variable of the chaotic system; and according to the formula:
[0090]
[0091] To calculate the ...
example 1
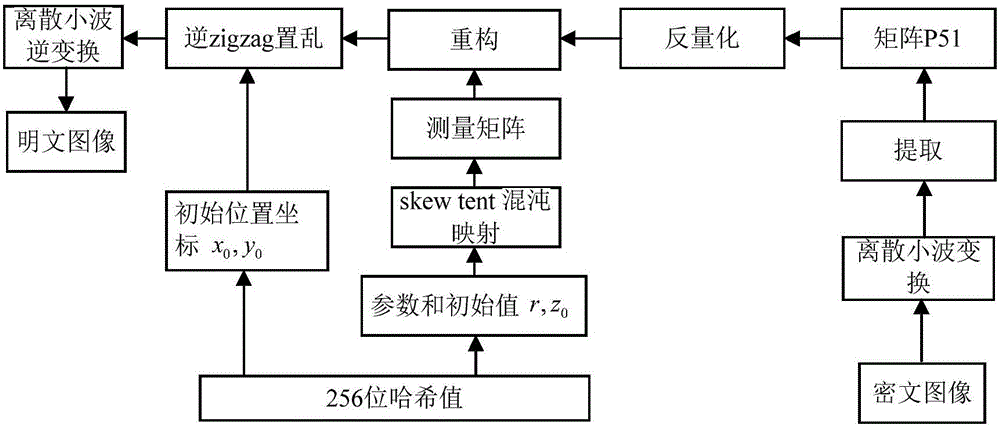
[0135] Example 1, see Figure 4~7 As shown, in this embodiment, the programming software used is Matlab R2014a, and a Lena gray image with a size of 512×512 is selected as the experimental object. The specific encryption process is as follows: Step 1: Input the Lena gray with the original size of 512×512 Use P=imread('Lena.bmp') to read the image information, and use the SHA 256 hash function to calculate the plaintext image P to obtain a set of 256-bit hash values and use it as the image secret key. Then convert the 256-bit key into 32 decimal numbers k 1 , K 2 ,..., k 32 , And then calculate the parameters and initial values of the one-dimensional skew tent chaotic map, and the specific steps of the initial position coordinates required for zigzag scrambling are as follows:
[0136] 1.1) The expression of the one-dimensional skew tent chaotic map used in the present invention is:
[0137]
[0138] Among them, r∈(0,1) is the system parameter, z∈(0,1) is the state variable of ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com