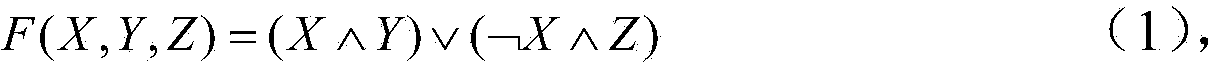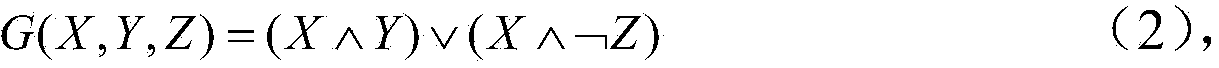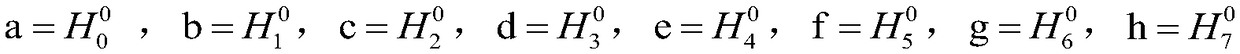Patents
Literature
96 results about "256-bit" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In computer architecture, 256-bit integers, memory addresses, or other data units are those that are 256 bits (32 octets) wide. Also, 256-bit CPU and ALU architectures are those that are based on registers, address buses, or data buses of that size.
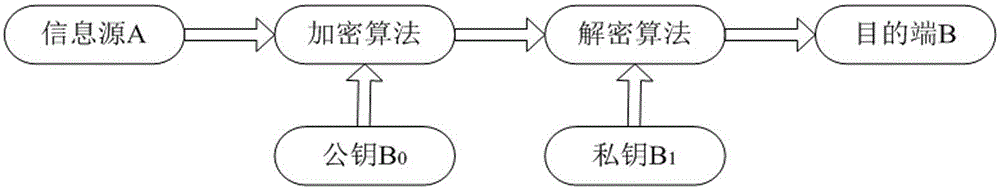
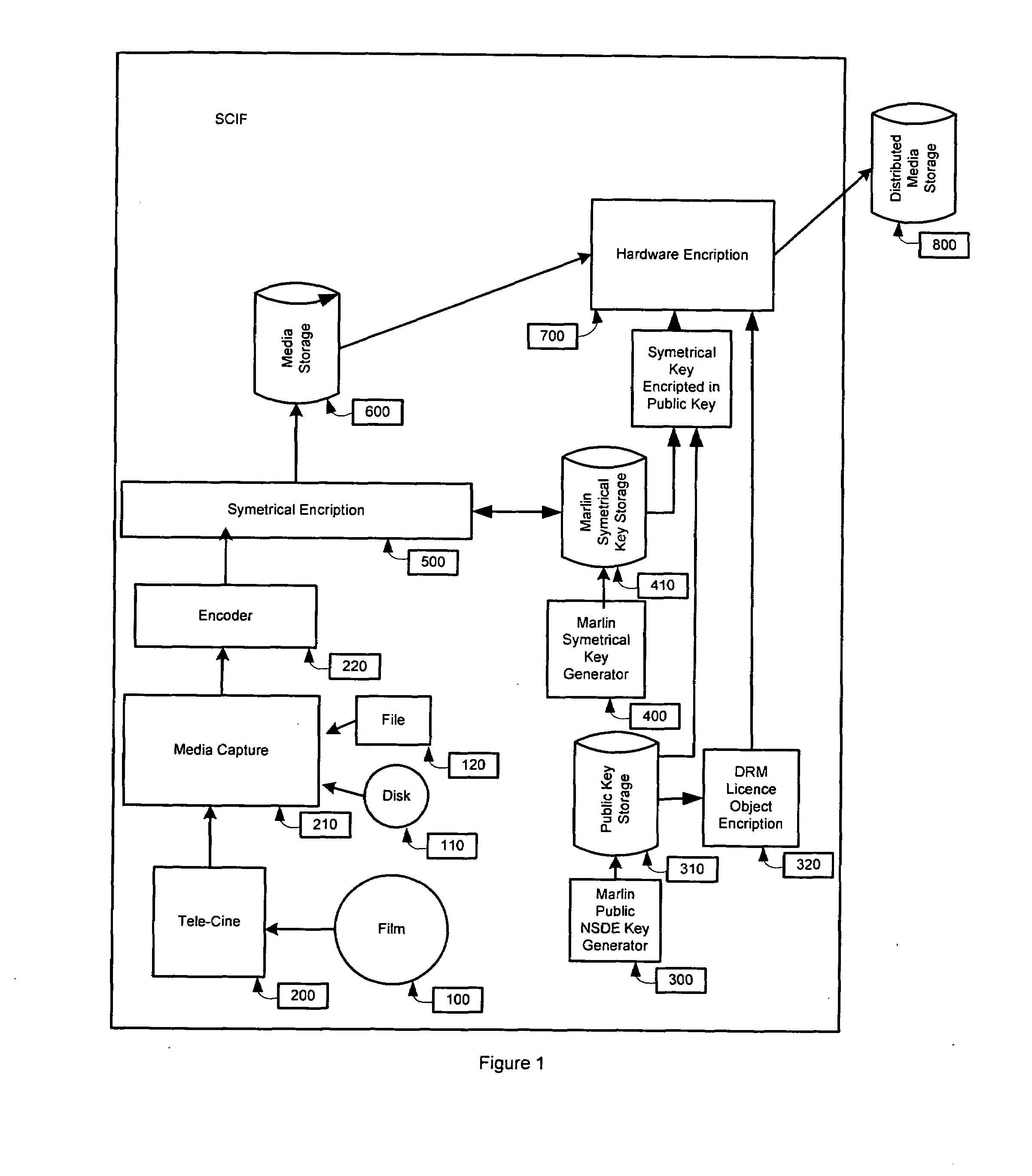
Method for generating cryptographic key from biometric data
InactiveUS20090310779A1Secret key can be re-generated efficientlyCharacter and pattern recognitionSecuring communicationBiometric dataTheoretical computer science
Data from biometric images such as minutiae of a fingerprint are represented in coordinates x- and y-, and the direction of the ridge flow of the minutia θ; in vector sets of (x1, y1, θ1) are used in generating a 256-bit secret key in a secure manner in enrolling the fingerprint in the Enrolment Phase. The key generation algorithm includes random key generation, threshold signature scheme using polynomial functions, generating random fake minutiae vector sets to form a locked representation of the fingerprint. In the Query Phase, the fingerprint image used to re-generate the secret key is matched against the locked template representation through automatic alignment process using geometric hash table to compare the enrolled minutiae (genuine and fake) with the vector set extracted from the query minutiae sets, and adjustable transform equation is used for adjusting for the minutiae direction, etc.
Owner:PRIVYLINK PRIVATE
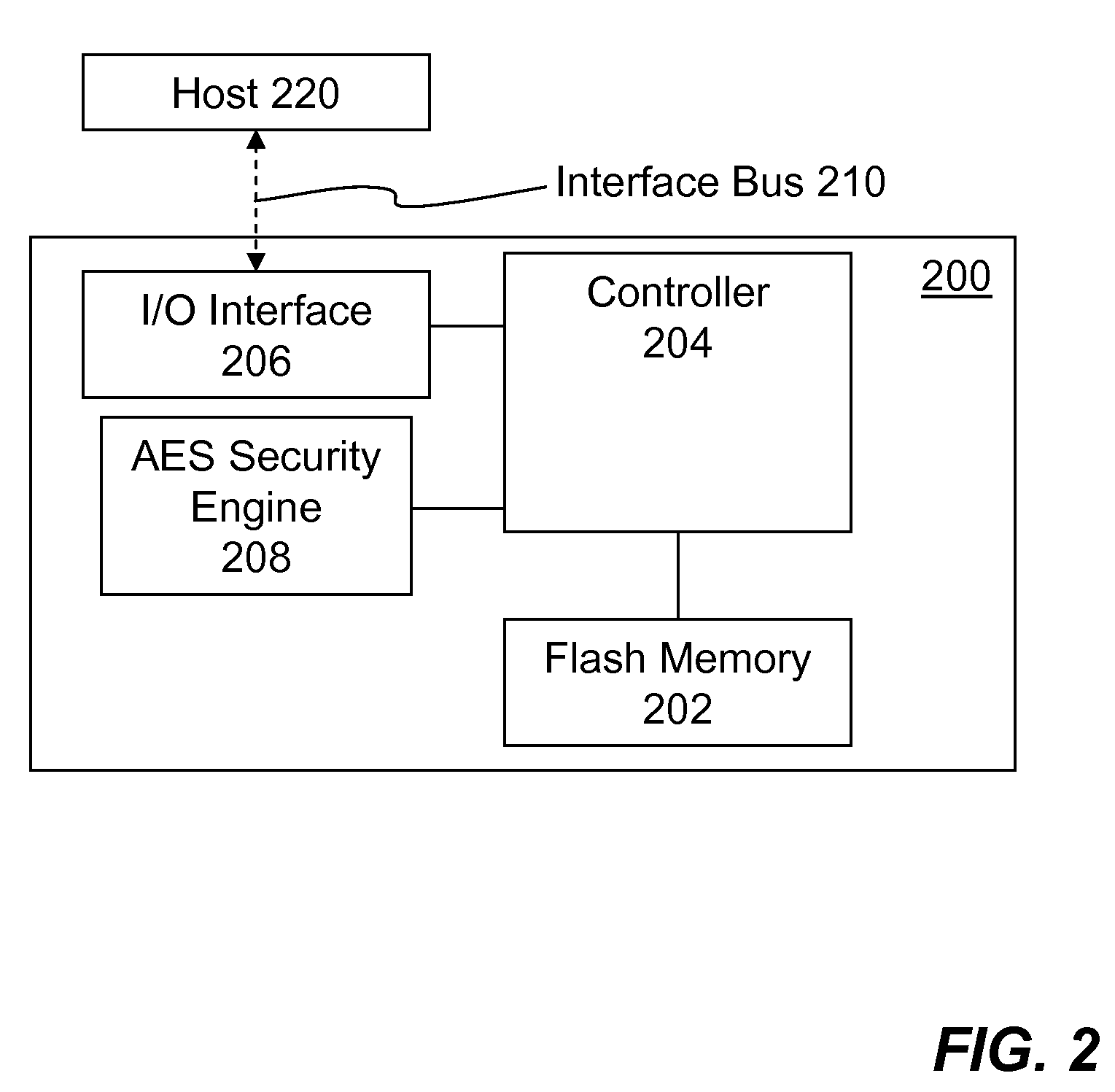
Portable Electronic Storage Devices with Hardware Security Based on Advanced Encryption Standard
InactiveUS20080192928A1Improve securityUnauthorized memory use protectionInternal/peripheral component protectionKey sizeAdvanced Encryption Standard
Portable electronic storage devices with hardware based security are described. According to one exemplary embodiment of the present invention, a portable electronic storage device (PESD) comprises a security engine integrated thereon. The security engine is configured to provide data encryption, data decryption, and encryption / decryption key (referred to as a key) generation according to a security standard (e.g., Advance Encryption Standard (AES)). AES is a symmetric encryption algorithm processing data in block of 128 bits. Under the influence of a key, a 128-bit data block is encrypted by transforming the data block in a unique way into a new data block of the same size. AES is symmetric sine the same key is used for encryption and the reverse transformation (i.e., decryption). The only secret necessary to keep for security is the key. AES may use different key-lengths (i.e., 128-bit, 192-bits and 256-bits).
Owner:SUPER TALENT ELECTRONICS
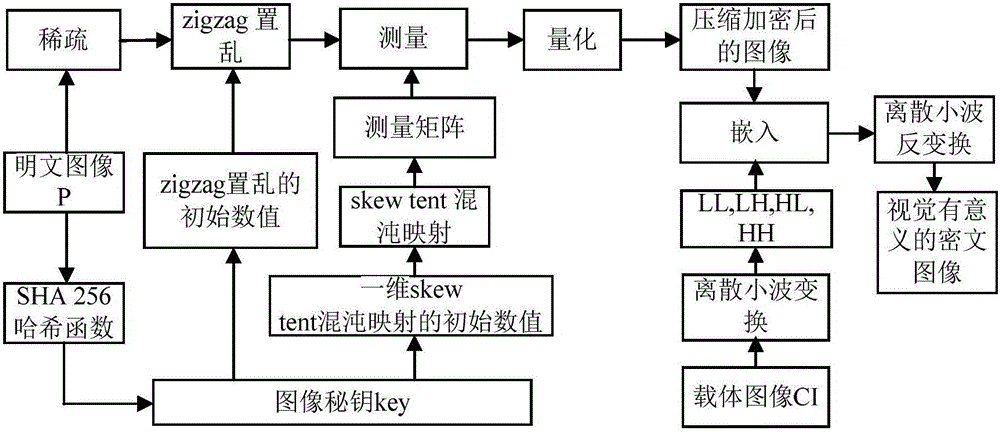
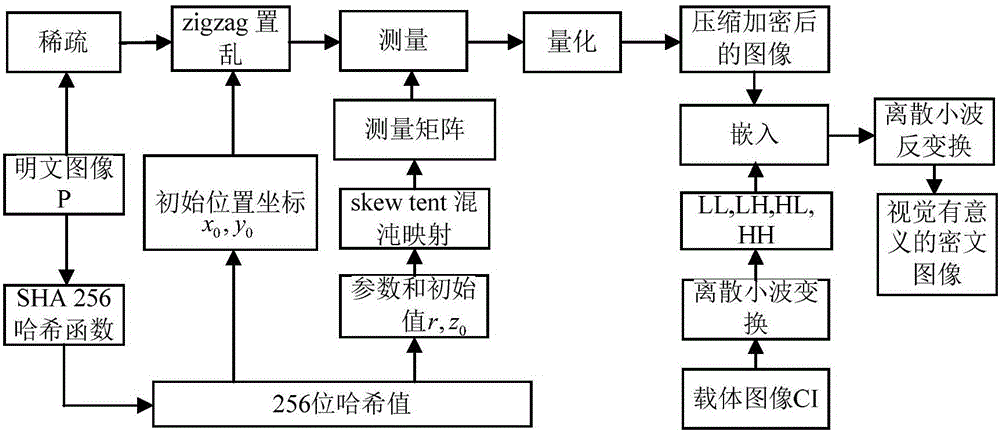
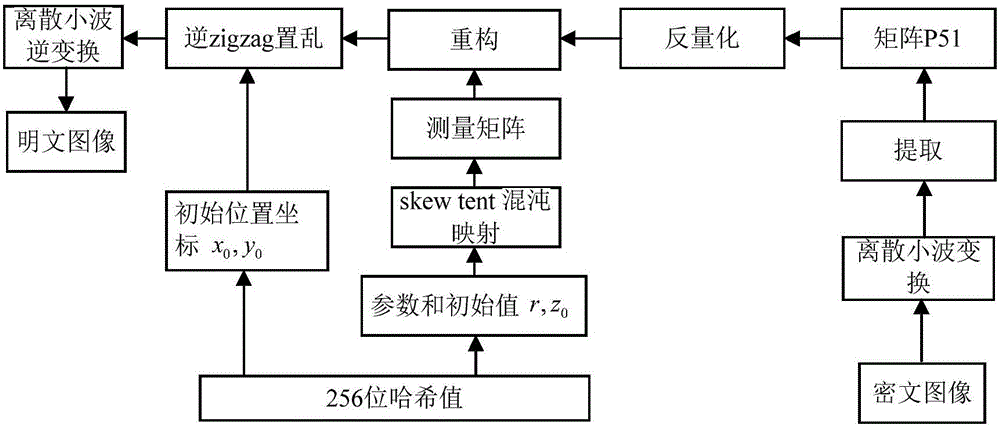
Image encryption method and image decryption method with visual security and data security based on compressed sensing
ActiveCN106600518AIncrease spaceEnhanced resistance to brute force attacksImage data processing detailsChosen-plaintext attackHash function
The invention relates to an image encryption method and an image decryption method with visual security and data security based on compressed sensing. The image encryption method comprises the steps of: firstly, utilizing an SHA 256 hash function to obtain a 256-bit hash value of a plaintext image as an image secret key, and calculating initial numerical values of one-dimensional skew tent chaotic mapping and zigzag scrambling; carrying out sparse processing on the plaintext image, and carrying out zigzag scrambling on a coefficient matrix; and then utilizing the one-dimensional skew tent chaotic mapping to generate a measurement matrix, measuring and quantifying a scrambling matrix to obtain a compressed and encrypted image, and embedding the image into a carrier image with visual significance to obtain a final ciphertext image with visual significance. The image encryption method realizes the visual security and data security of the plaintext image, has large secret key space, is highly sensitive to plaintext, has higher capacity of resisting brute-force attack, chosen-plaintext attack and known-plaintext attack, does not need an additional storage space, and can transmit and store the ciphertext image quickly and effectively.
Owner:HENAN UNIVERSITY
High speed arithmetic device and method of elliptic curve code
ActiveCN101782845AImprove hardware efficiencyReduced number of cycles for modular multiplicationPublic key for secure communicationComputations using residue arithmeticHardware structureModular multiplier
The invention relates to a high speed arithmetic device and a method of elliptic curve codes. The invention mainly aims to a master curve, the elliptic curve of which is 160-256 bit of die length and the prime field of which is on Fp. The high speed arithmetic device is a special hardware structure based on a water running pulsate double modular multiplier; the hardware structure comprises an operation part, a control part and a storage part, wherein the operation part comprises two parallel water running pulsate modular multipliers and two groups of adders. Based on the specific hardware structure, point addition and point double water running operation sequences of modified Jacobi coordinate projective joints are rearranged, and point addition and point double operations which sequentially appear in succession are connected end to end; and the vacant times of the double modular multipliers are mutually complemented, thus increasing the hardware efficiency of the water running pulsate modular multipliers and causing the point addition operation to only occupy seven modular multiplication operation cycles and the point double operation to occupy four modular multiplication operation cycles, and drastically reducing clock periodic numbers of the point addition and / or point double and point multiplication operation.
Owner:BEIJING HUADA INFOSEC TECH
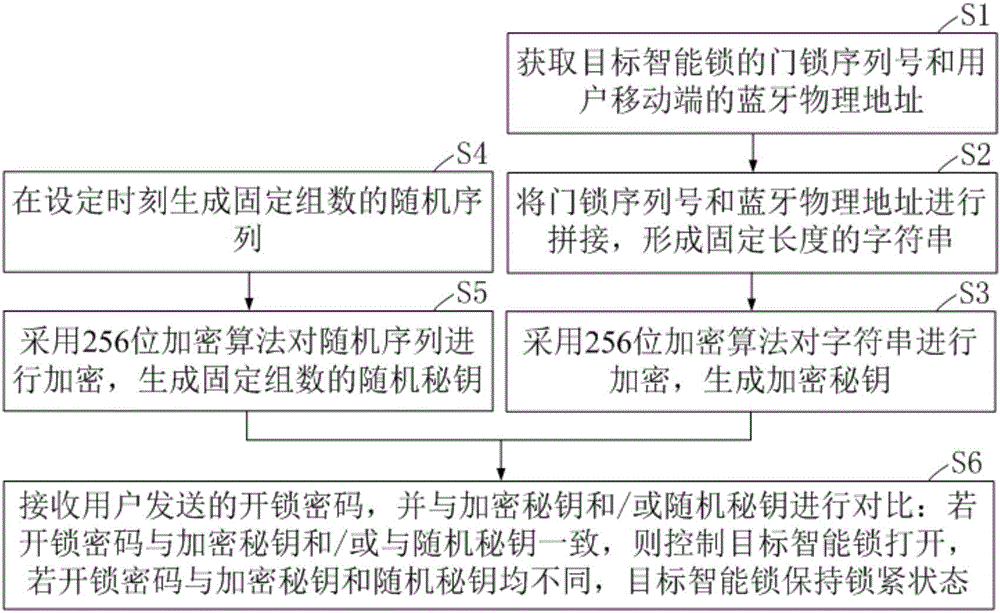
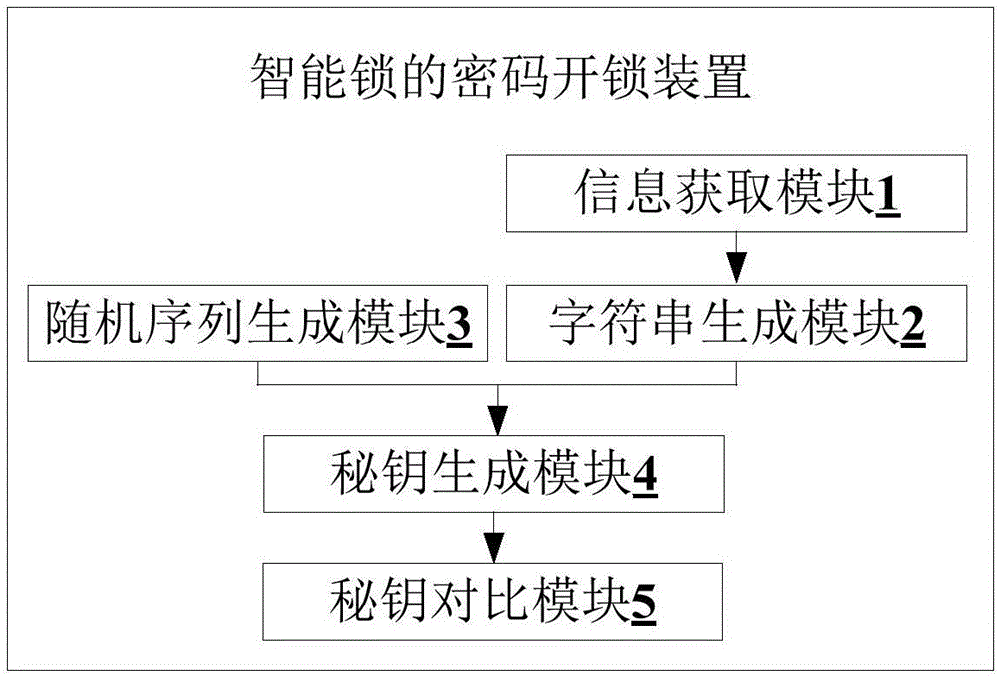
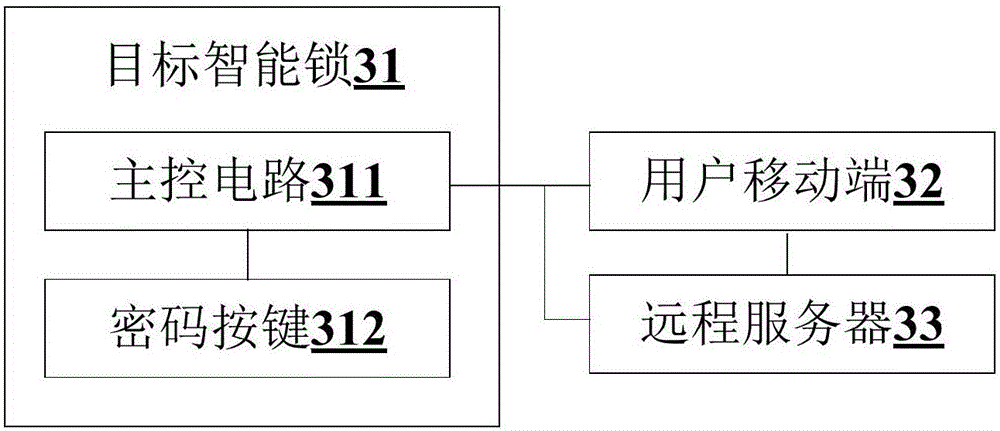
Password unlocking method, device and system for smart lock
InactiveCN106211048AImprove reliabilityIncreased complexityIndividual entry/exit registersWireless commuication servicesPasswordMobile end
The invention belongs to the technical field of smart locks, and provides a password unlocking method, device and system for a smart lock. The method comprises the following steps: acquiring a door lock serial number of a target smart lock and a Bluetooth physical address of a user mobile end; splicing the door lock serial number and the Bluetooth physical address to construct a fixed-length character string; encrypting the character string by adopting a 256-bit encryption algorithm to generate an encrypted key; generating a fixed number of groups of random sequences at a set moment; encrypting the random sequences by adopting the 256-bit encryption algorithm to generate a fixed number of groups of random keys; receiving an unlocking password transmitted by a user; and comparing the unlocking password with the encrypted key and / or the random keys: if the unlocking key is consistent with the encrypted key and / or the random keys, controlling the target smart lock to be unlocked. Through adoption of the password unlocking method, device and system for the smart lock, remote unlocking can be realized. Moreover, a complicated encryption algorithm is adopted, so that the security of the encrypted key and the random keys is enhanced.
Owner:重庆智城互盈科技发展有限公司
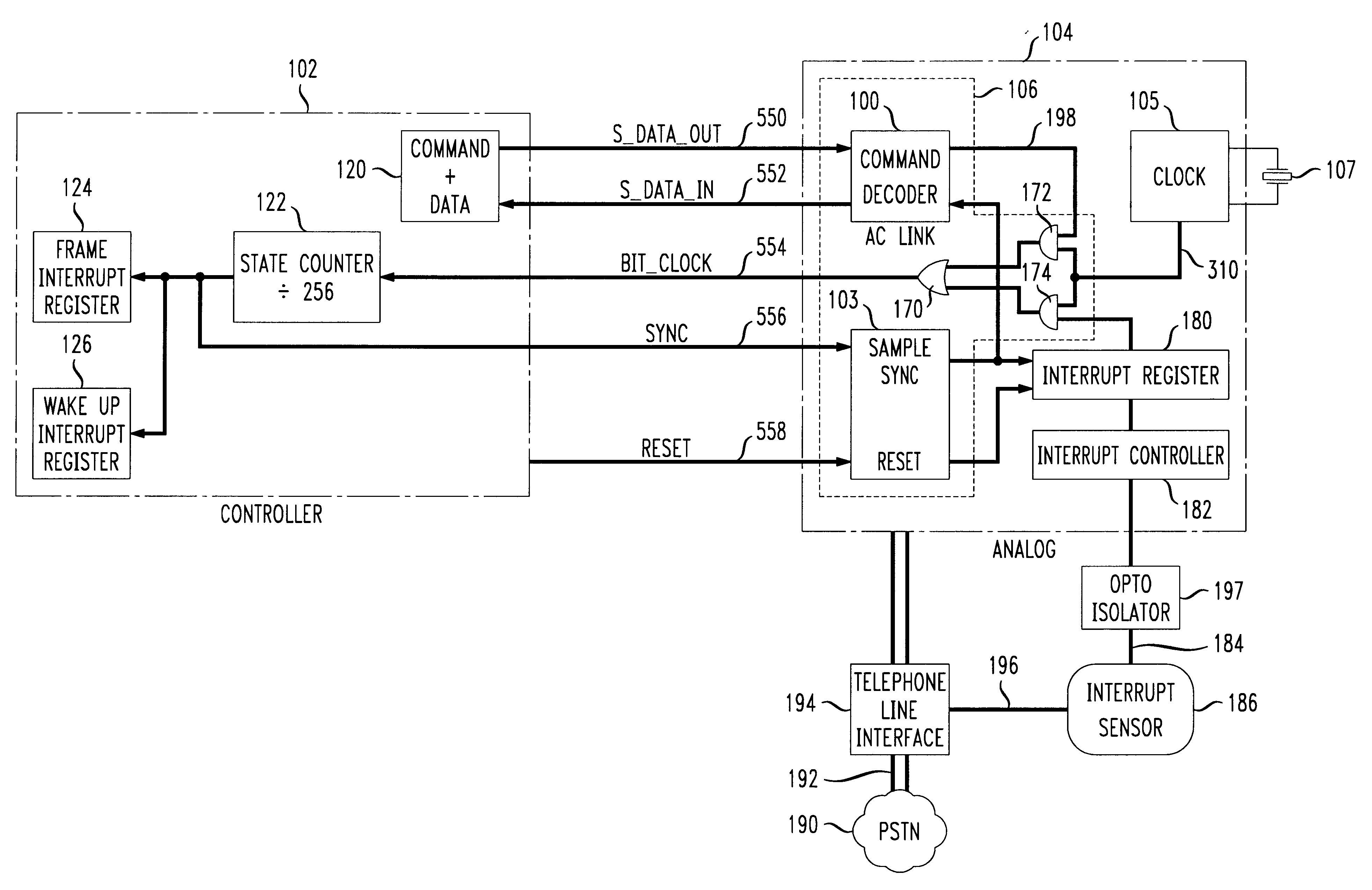
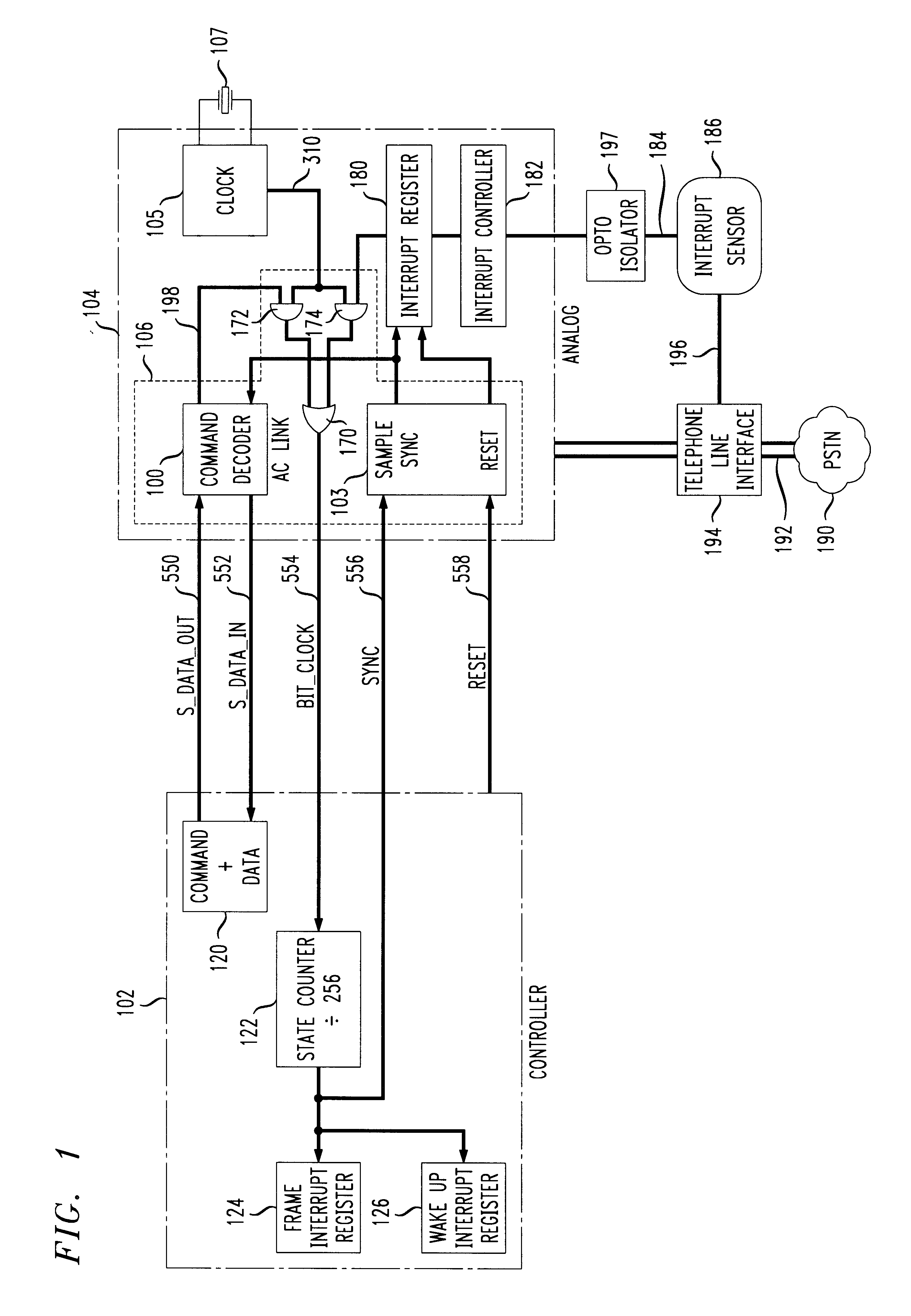
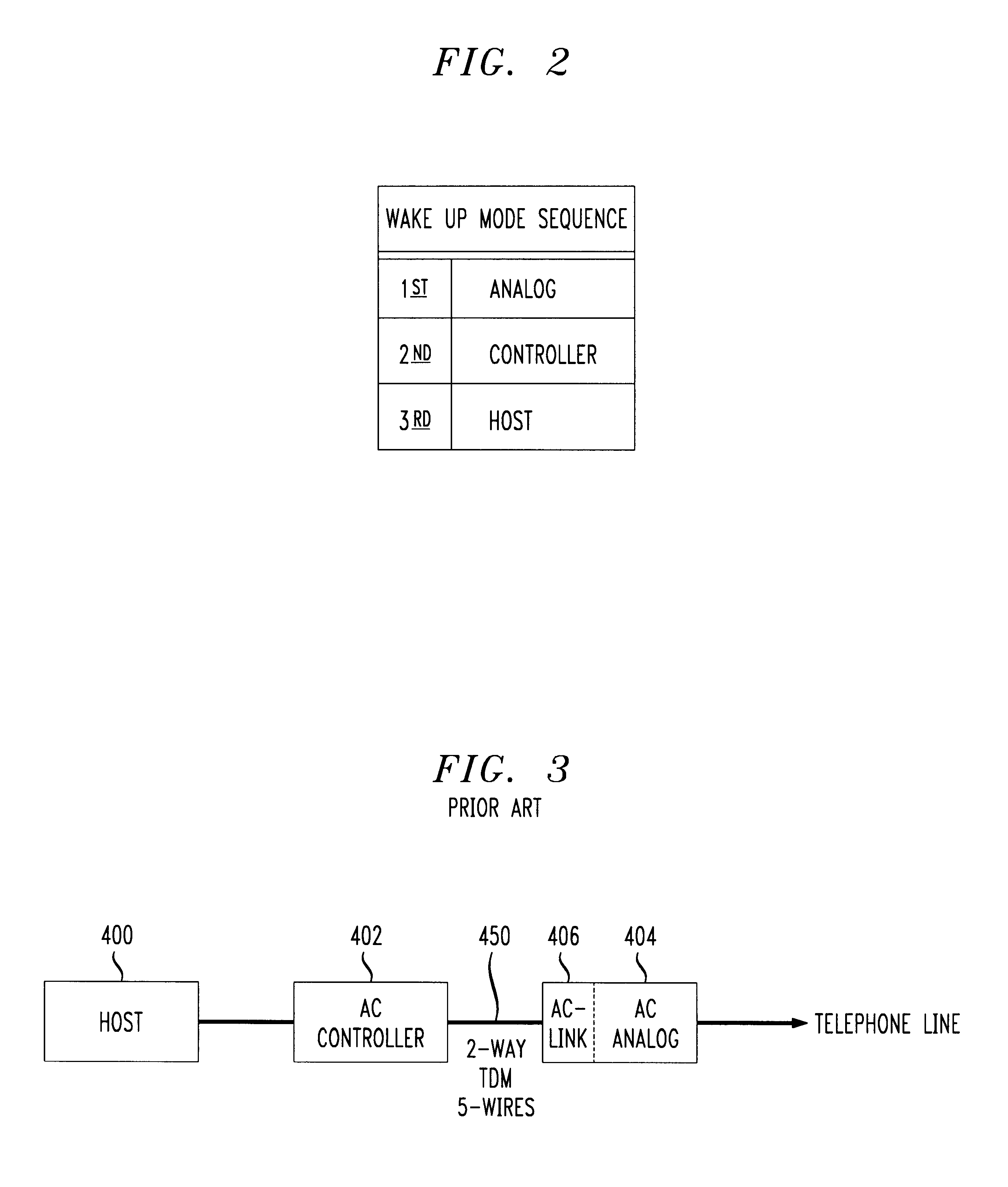
Interrupt mechanism using TDM serial interface
An improvement to split-architecture audio codecs such as those defined by the Audio Codec '97 specification (AC '97) includes an interrupt mechanism which allows an event at an analog peripheral device such as an incoming call to be sensed by the AC analog sub-system and initiate a wake up procedure in the split-architecture audio codec system. The interrupt mechanism includes a masked interrupt register which is responsive to an interrupt signal from an audio source, such as a ring detect from an incoming telephone line. Either the AC controller sub-system or the peripheral analog device via the AC analog sub-system can initiate a wake up procedure. The AC controller sub-system includes a static divide by 256 counter responsive to a bit clock signal. The bit clock signal is sensed at the AC controller sub-system to determine an operating mode. Upon detection of at least 256 bit clock cycles after a predetermined minimum time for the AC analog sub-system to be in a halted or sleep mode, a wake up interrupt register is enabled in the AC controller sub-system. The interrupt sensor is opto-coupled to the AC analog sub-system, and the interrupt signal from the interrupt sensor is communicated to the AC controller sub-system via the five-wire TDM serial bus between the AC analog sub-system and the AC controller sub-system.
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
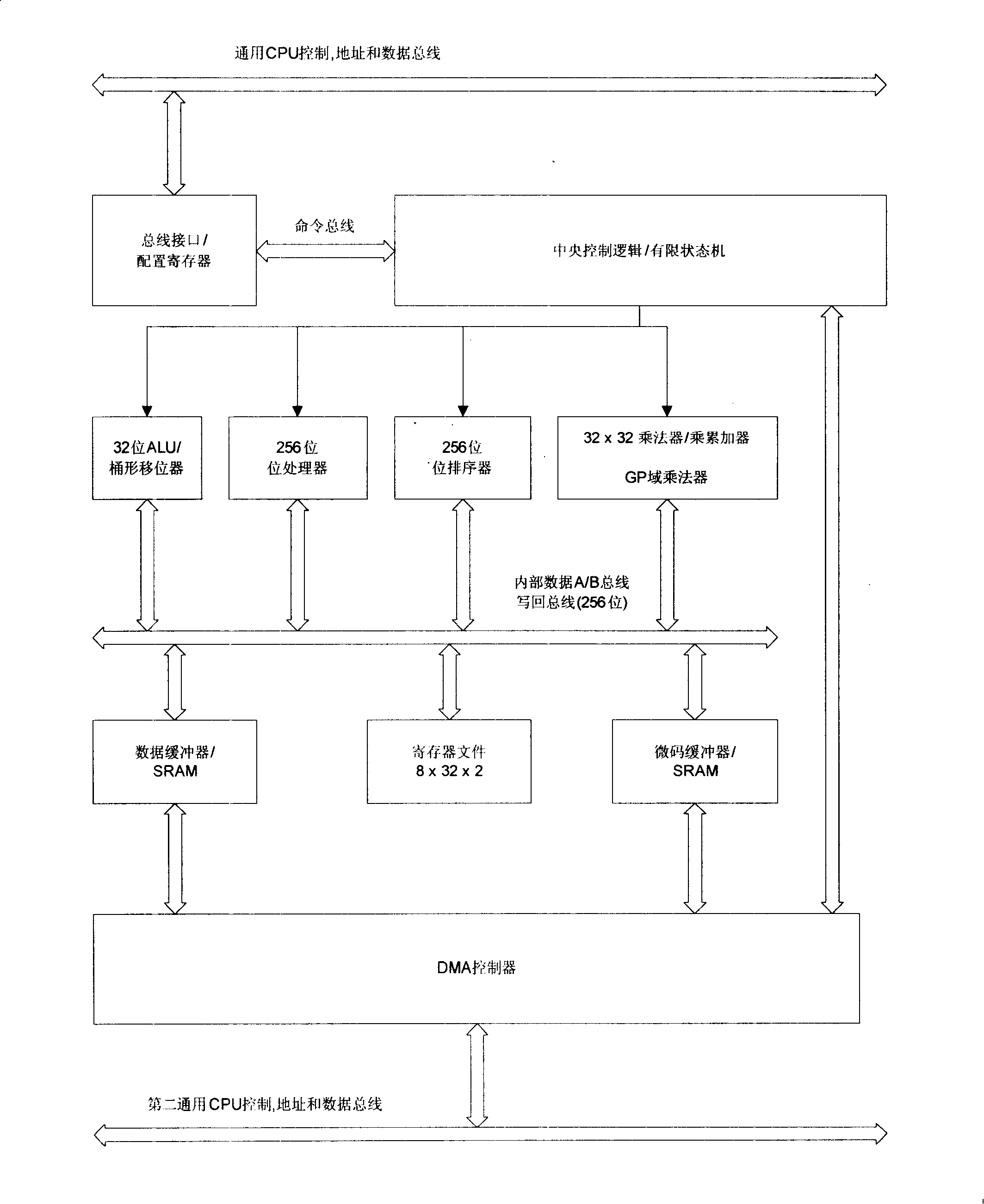
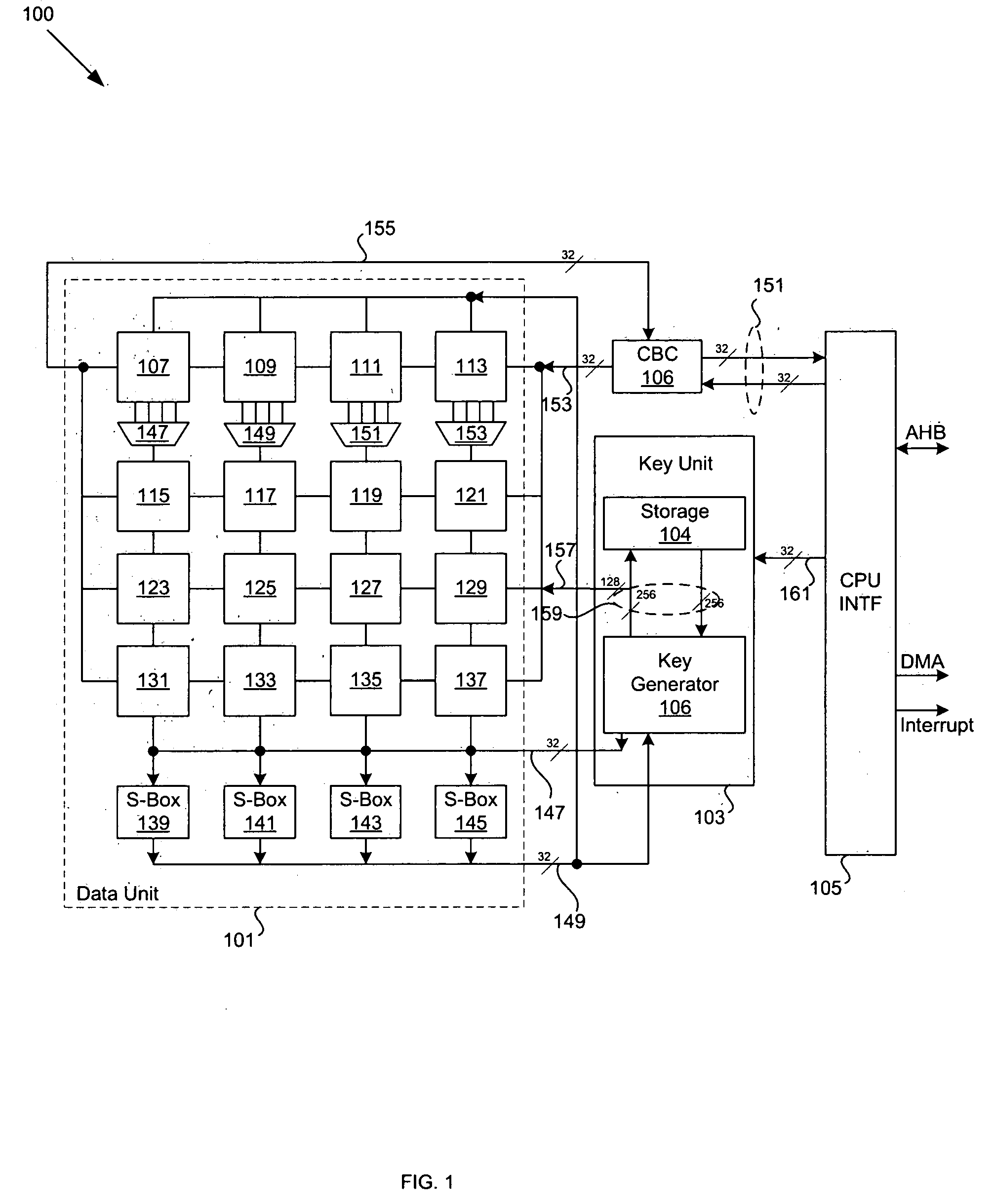
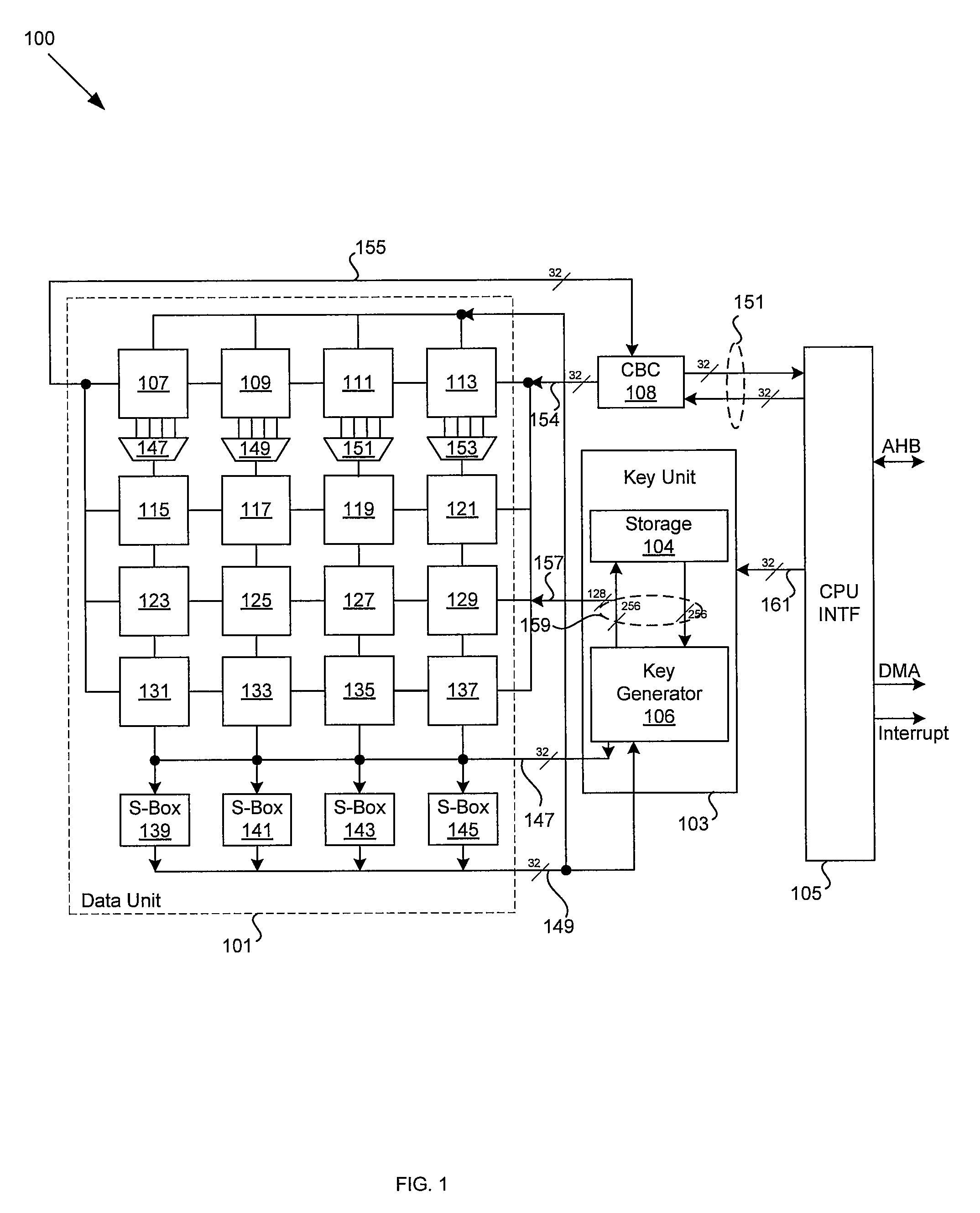
Encryption-decryption coprocessor for SOC, implementing method and programming model thereof
InactiveCN101201811AFlexible and economical realizationMeet the design requirementsArchitecture with single central processing unitCoprocessorData retrieval
The invention discloses a coprocessor used for decryption and encryption of an SOC, an accomplishing method and a programming model. A bus interface is connected with a general CPU bus and receives read-write order from the general CPU bus; a central control module is used for controlling the read-write order received by the bus interface and triggering the start, implementation and stop of the corresponding action of the coprocessor; a 256 bits bit processor implements the common data retrieval and hash algorithm in the encryption algorithm and the digital signature algorithm; a DMA controller is connected with a second general CPU bus and conducts data processing under the control of the central control module. The accomplishing method divides various encryption-decryption algorithms into various hardware arithmetic units which are controlled and dispatched by software. The programming model is the description of a register. The invention is more flexible and economic, can realize most known encryption-decryption algorithms and can meet the design requirements of most SOC chips.
Owner:边立剑 +1
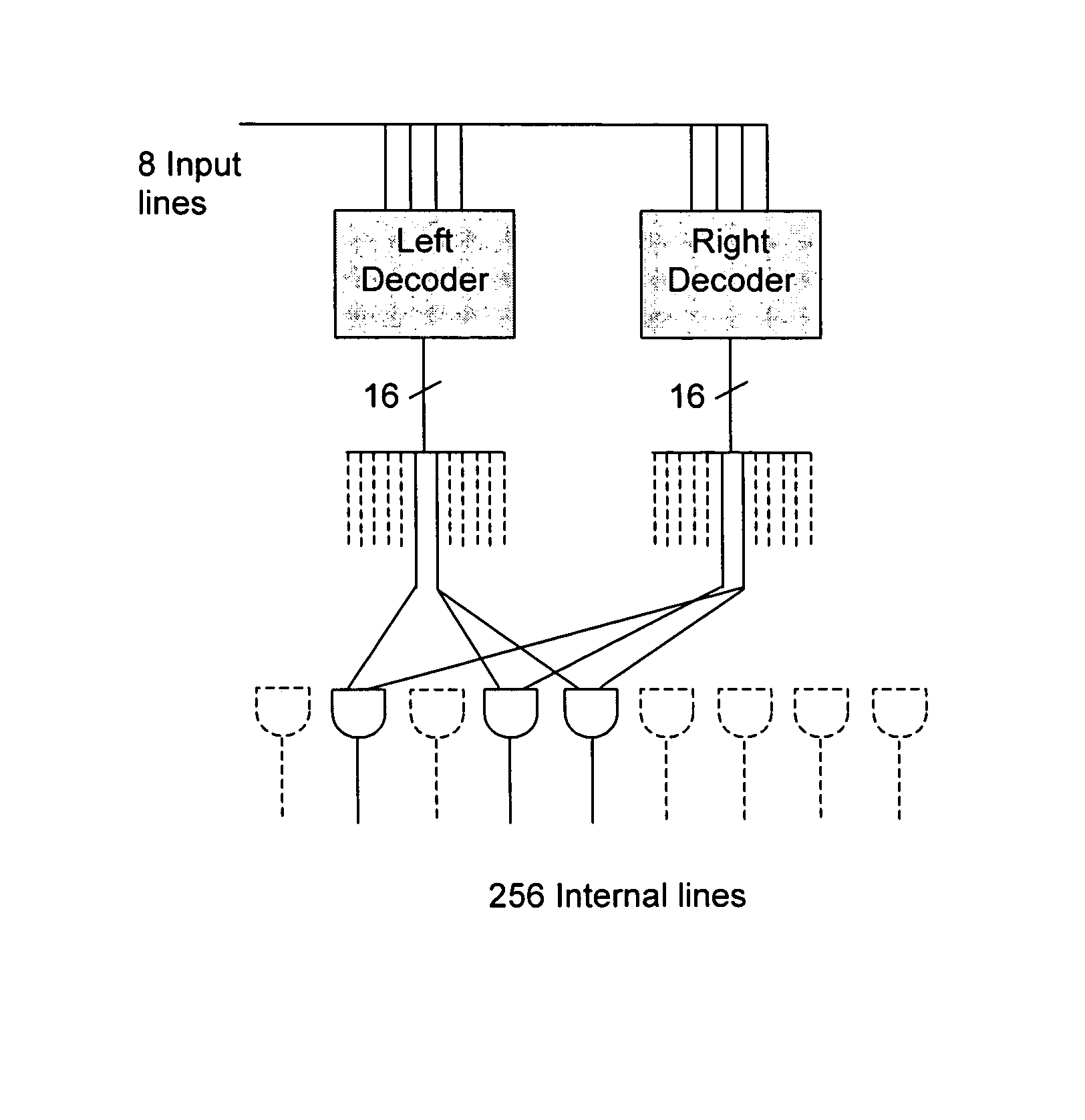
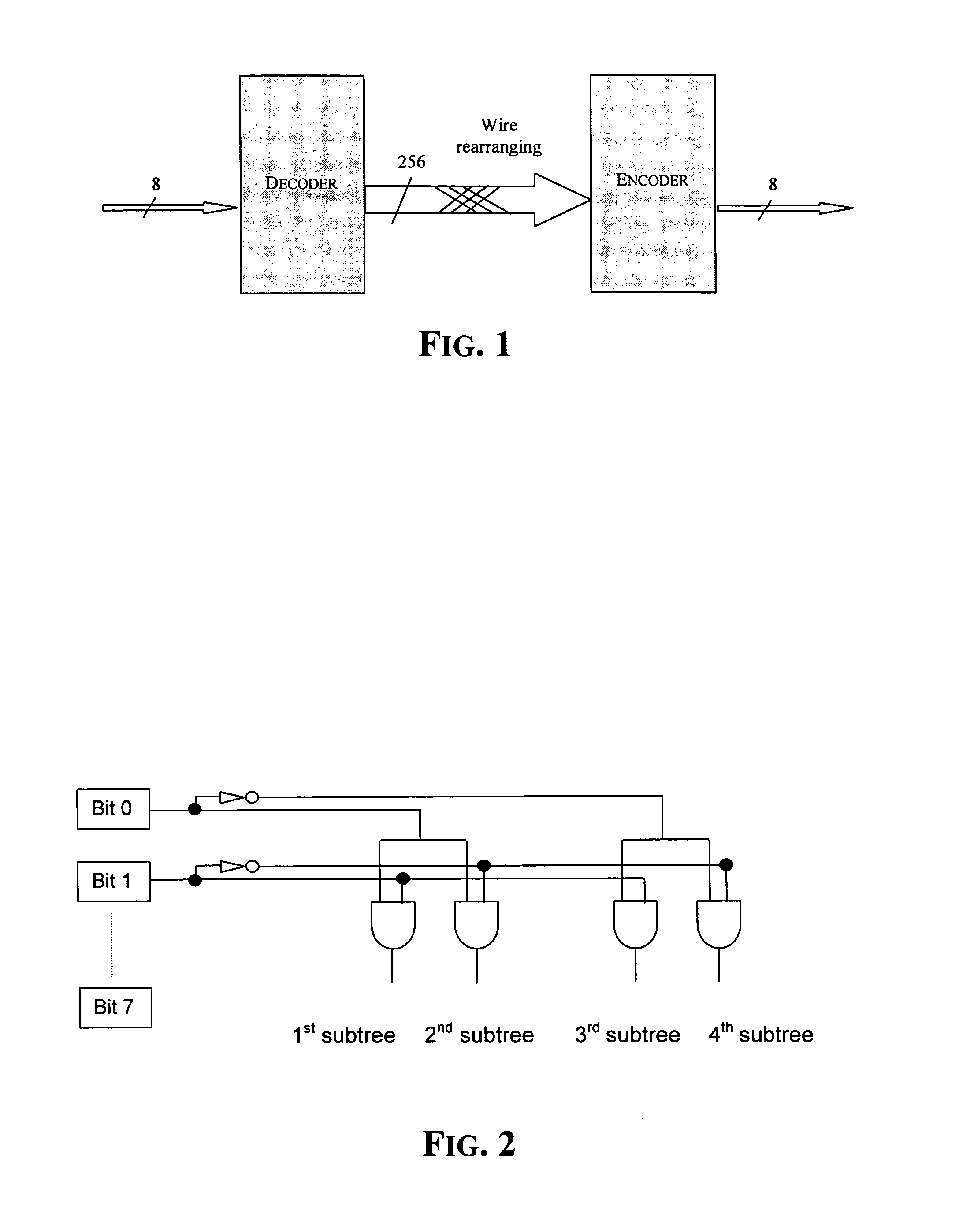
Method of implementing one-to-one binary function and relative hardware device, especially for a Rijndael S-box
InactiveUS7502464B2Encryption apparatus with shift registers/memoriesSecret communicationRijndael S-boxByte
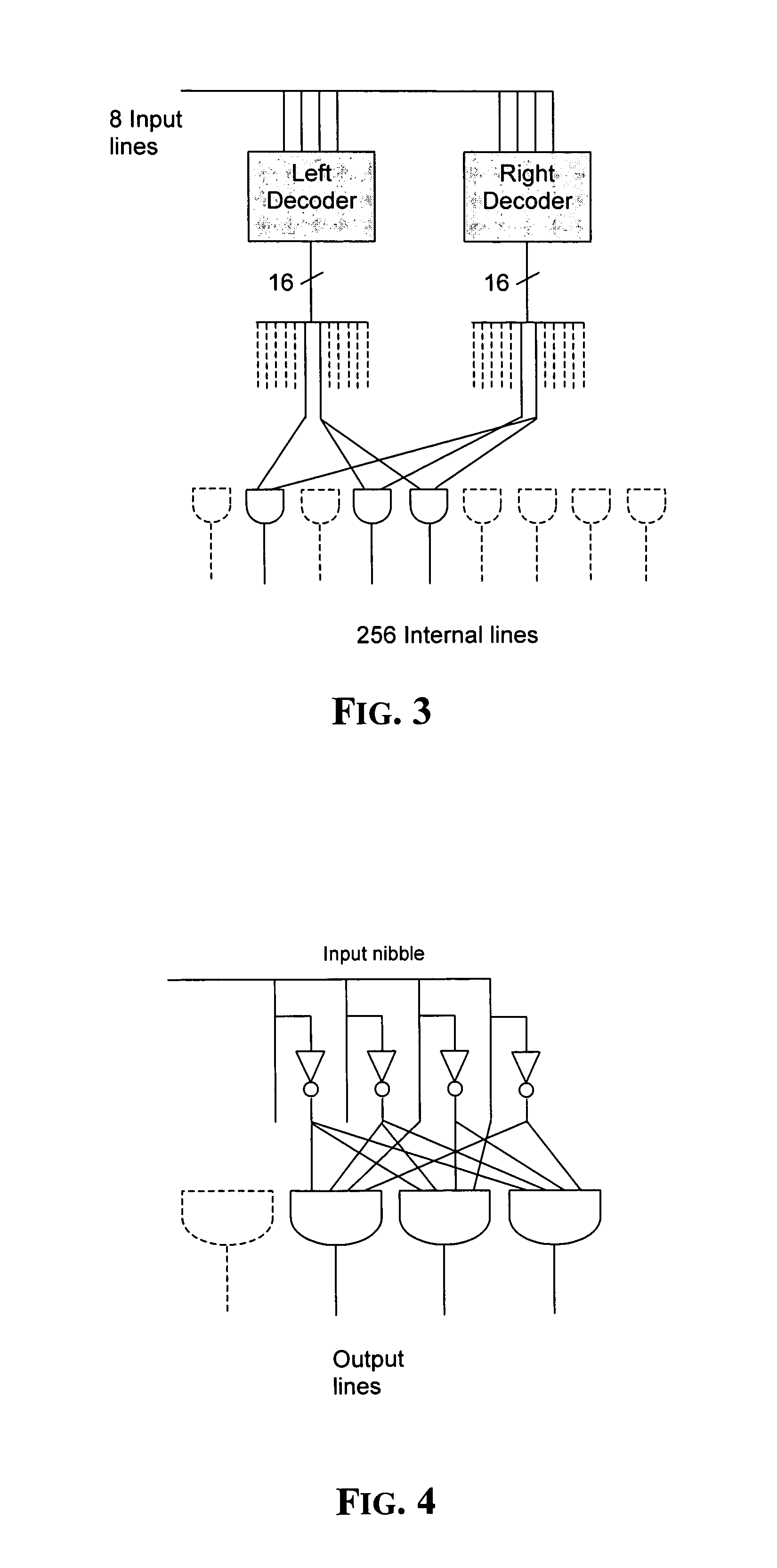
A method for implementing one-to-one binary functions defined on the Galois field GF(28) is very useful for forming fast and low power hardware devices regardless of the binary function. The method includes decoding an input byte for generating at least one bit string that contains only one active bit, and logically combining the bits of the bit string according to the binary function for generating a 256-bit string representing a corresponding output byte. The 256-bit string is then encoded in a byte for obtaining the output byte.
Owner:STMICROELECTRONICS SRL
Standalone hardware accelerator for advanced encryption standard (AES) encryption and decryption
InactiveUS20050271204A1Encryption apparatus with shift registers/memoriesS-boxAdvanced Encryption Standard
Systems and methods for accelerating AES encryption and decryption operations are provided. Aspects of the method may include time multiplexing a plurality of substitution boxes (S-boxes) for instantaneous key generation and byte substitution operations. Bytes may be substituted in at least a portion of a current security key information and at least a portion of a subsequent security key information within said plurality of S-boxes. The current security key may comprise 128 bits, 192 bits or 256 bits and the portion of the current security key may comprise 32 bits. The substituted portion of the security key information may be communicated to a key generator. The subsequent security key information may be generated utilizing the substituted portion of the current security key information. The current security key information may then be stored.
Owner:AVAGO TECH INT SALES PTE LTD
Implement method of elliptic curve cipher system coprocessor
InactiveCN101000538AImprove work efficiencyProcessing speedPublic key for secure communicationComputations using residue arithmeticCoprocessorInstruction set design
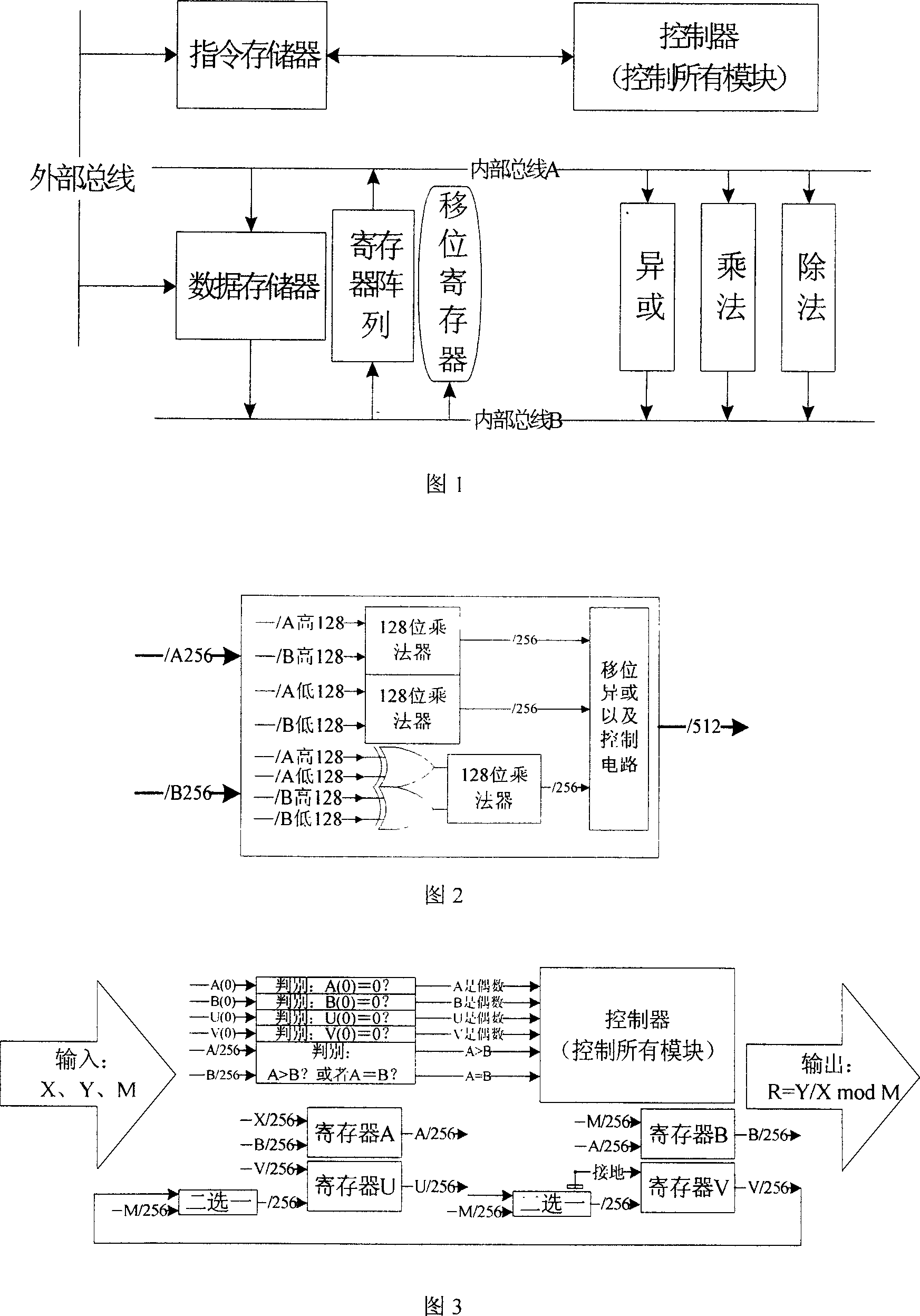
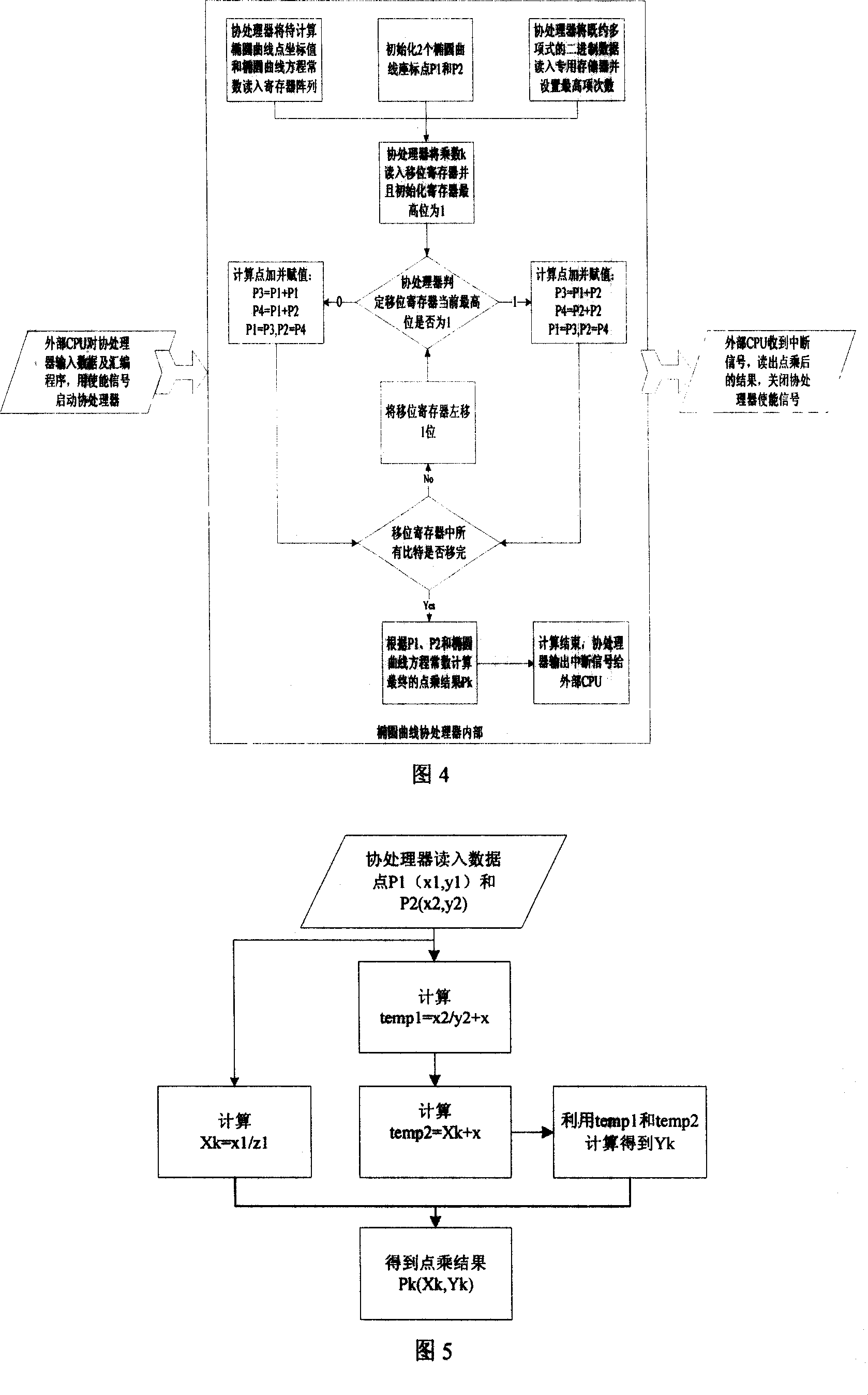
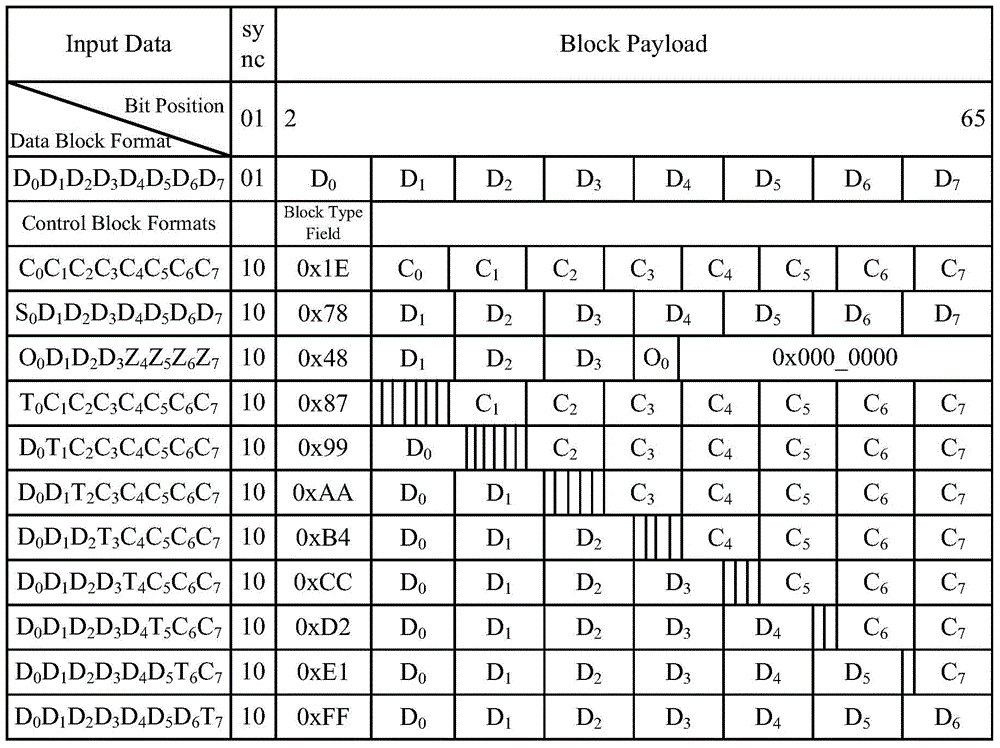
A method for realizing coprocessor of oval curve cipher system includes dividing functions of complete coprocessor first and then detailing divided functions to be each bottom layer module in design, realizing each bottom layer module first and testing then separately then integrating them to be complete ECC coprocessor in realization. The 256 position universal coprocessor for solving point multiplication problem in ECC calculation is also disclosed.
Owner:SOUTHEAST UNIV
Physical layer coding and decoding methods and devices
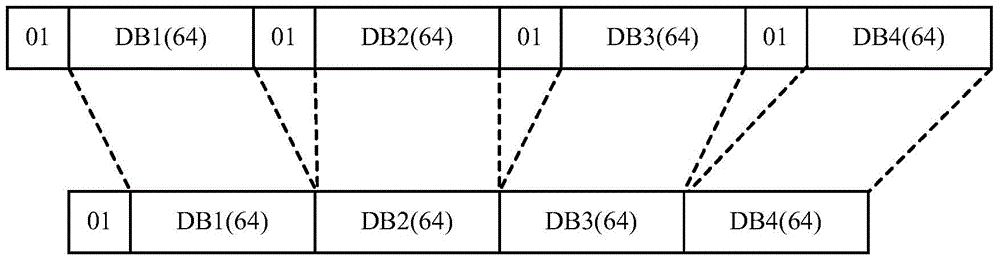
Disclosed are a physical layer coding / decoding method and an apparatus thereof, comprising: receiving inputted MII (Media Independent Interface) control code blocks and first 256-bit to-be-coded code blocks; determining control code blocks in the first 256-bit to-be-coded code blocks according to the MII control code blocks, and compressing the determined control code blocks; determining physical layer coding format, sync field value, the hierarchy of Block Type Field and the value of Block Type Field according to the MII control code blocks; mapping the compressed to-be-coded code blocks into data in a format of physical layer data according to the determined physical layer coding format, adding sync field to the data, the value of the added sync field being the determined sync field value, adding Block Type Field into a space obtained by compression according to the hierarchy of Block Type Field in order to obtain a coding result, and the value of the added Block Type Field being the determined value of Block Type Field. The physical layer coding / decoding method can be used to meet the demands of RS-FEC (Reed-Solomon Forward Error Correction) algorithm.
Owner:HUAWEI TECH CO LTD
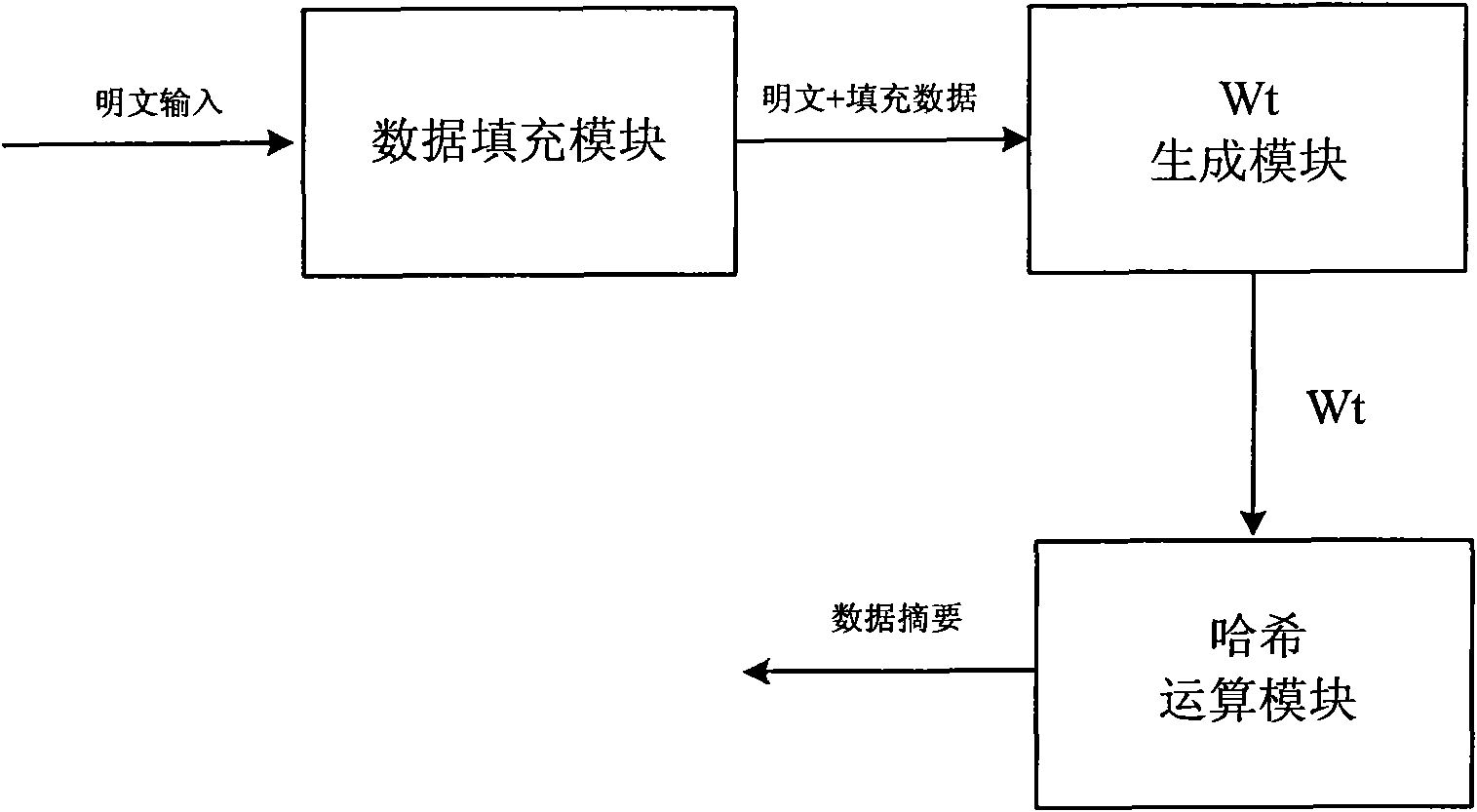
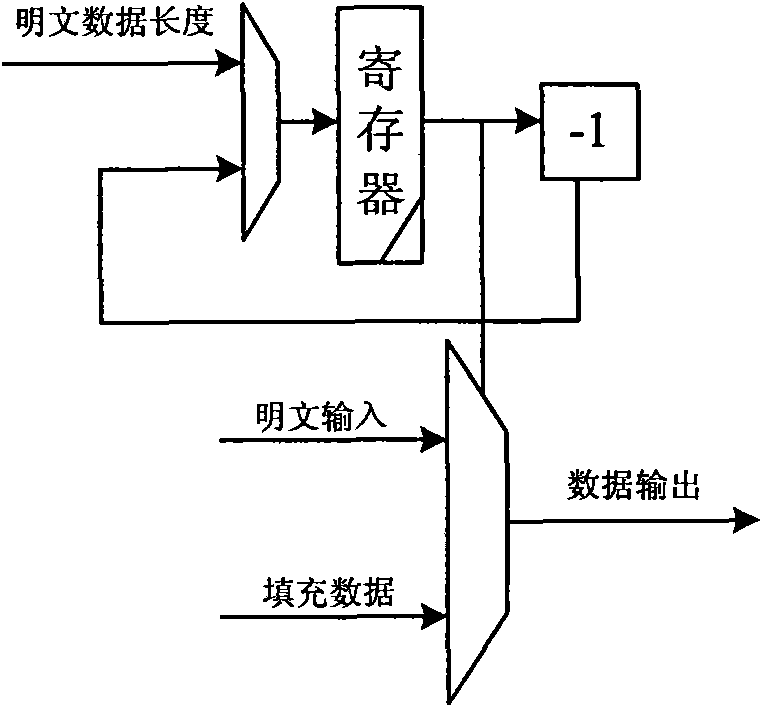
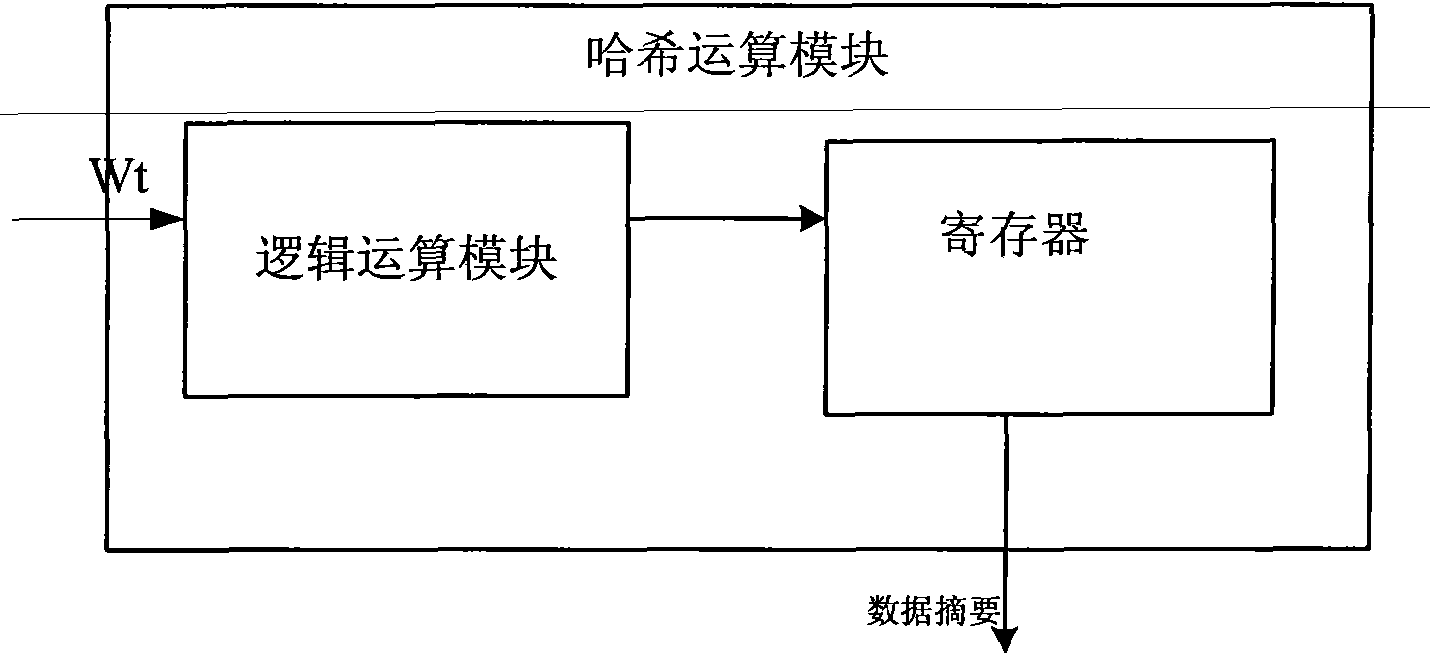
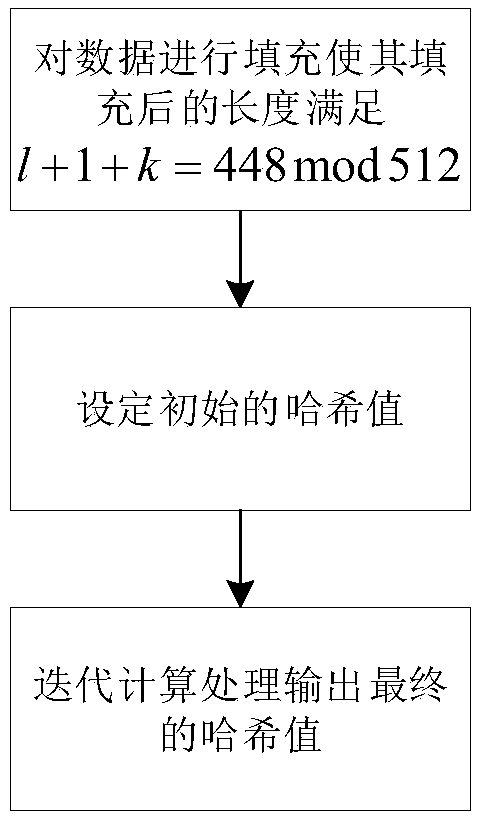
Device compatible with three SHA standards and realization method thereof
InactiveCN101894229AImprove compatibilityReduce consumptionInternal/peripheral component protectionComputer compatibilityData filling
The invention discloses a device compatible with three SHA standards, which comprises a data filling module, a Wt generation module and an Hash operation module, which are connected in order. The invention also discloses a realization method of the device compatible with three SHA standards, which comprises the following steps: (I) receiving cleartext data by the data filling module to generate filling data and outputting the data to the Wt generation module; (II) generating new Wt operators by the Wt generation module and inputting the new Wt operators into the Hash operation module; and (III) generating a data abstract with 160 bits under an SHA-a mode, generating a data abstract with 256 bits under SHA-256 mode or generating a data abstract with 512 bits under an SHA-512 mode by the Hash operation module. The invention has the advantages of common practicality, good compatibility, low power consumption, less occupation of extra resources and the like.
Owner:SOUTH CHINA UNIV OF TECH
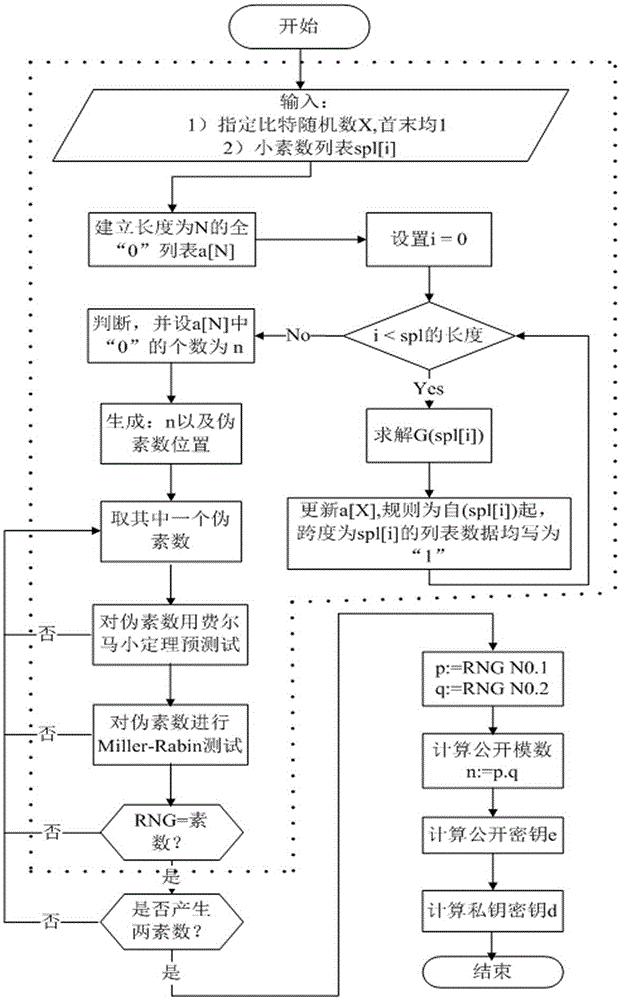
RSA key pair fast generation system and RSA key pair fast generation method
InactiveCN106487512AReduce build timeHigh speedKey distribution for secure communicationPublic key for secure communicationCoprocessorComposite number
The invention discloses an RSA key pair fast generation system and an RSA key pair fast generation method. The system comprises a CPU core, a cipher coprocessor, a prime number generator, and a memory. The prime number generator is used for filtering composite numbers, is implemented in hardware form, supports 256-bit, 512-bit, 1024-bit, 2048-bit and 4096-bit composite number filtering, and completes modular redundancy, calculation and identification table setting. According to the RSA key pair fast generation method, in order to realize fast key pair retrieving, filtering and judging in an asymmetric algorithm, a hardware-based composite number filtering scheme is adopted, optimized modular exponentiation and improved Montgomery modular multiplication are employed, and the existing prime number decision algorithm is optimized. Thus, efficient prime number screening is realized, the key pair generation speed is increased, and the problem that the generation of an RSA key pair takes long in the existing encryption and decryption technology is solved.
Owner:BEIJING TONGFANG MICROELECTRONICS
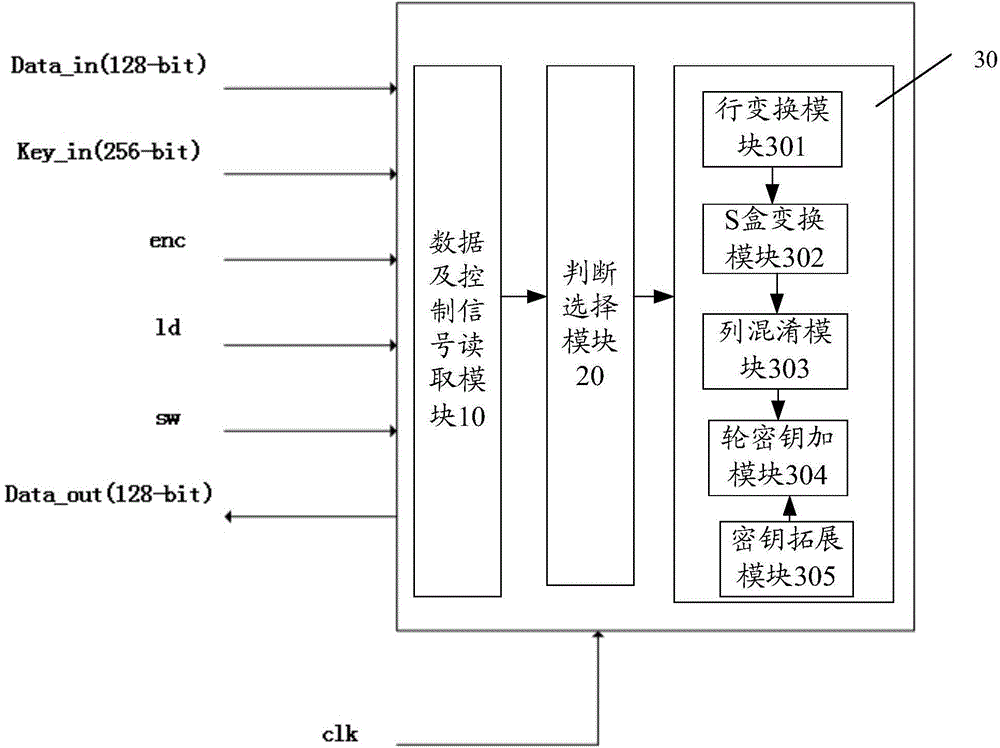
Light-weight dual-mode-compatible AES encryption and decryption module and method thereof
ActiveCN106034021AImplement encryption and decryption operationsThroughput equalizationEncryption apparatus with shift registers/memoriesMultiplexingControl signal
The invention discloses a light-weight dual-mode-compatible AES encryption and decryption module and a method thereof. The encryption and decryption module comprises a data and control signal reading module, a determination selection module, and an AES calculation module. The data and control signal reading module is used for reading a corresponding control signal and reading to-be-encrypted data and an encryption secret key after being triggered by a data reading-in control signal; the determination selection module is used for determining an encryption and decryption control signal and a mode selection control signal to select whether a current operation is an encryption operation or decryption operation and whether a current operation is a 256-bit secret key encryption and decryption operation or a 128-bit secret key encryption and decryption operation; and the AES calculation module is used for carrying out encryption and decryption on the to-be-encrypted / decrypted data by using round calculation based on selection by the determination selection module. According to the invention, under control of the control signal, the encryption and decryption operations with the 128-bit-length and 256-bit-length secret keys can be realized; and the partial structure multiplexing is realized. Therefore, the realization result of a ten-thousand equivalent gate level and the throughput capacity with the tens-of Mbps level can be realized.
Owner:SHANGHAI ADVANCED RES INST CHINESE ACADEMY OF SCI
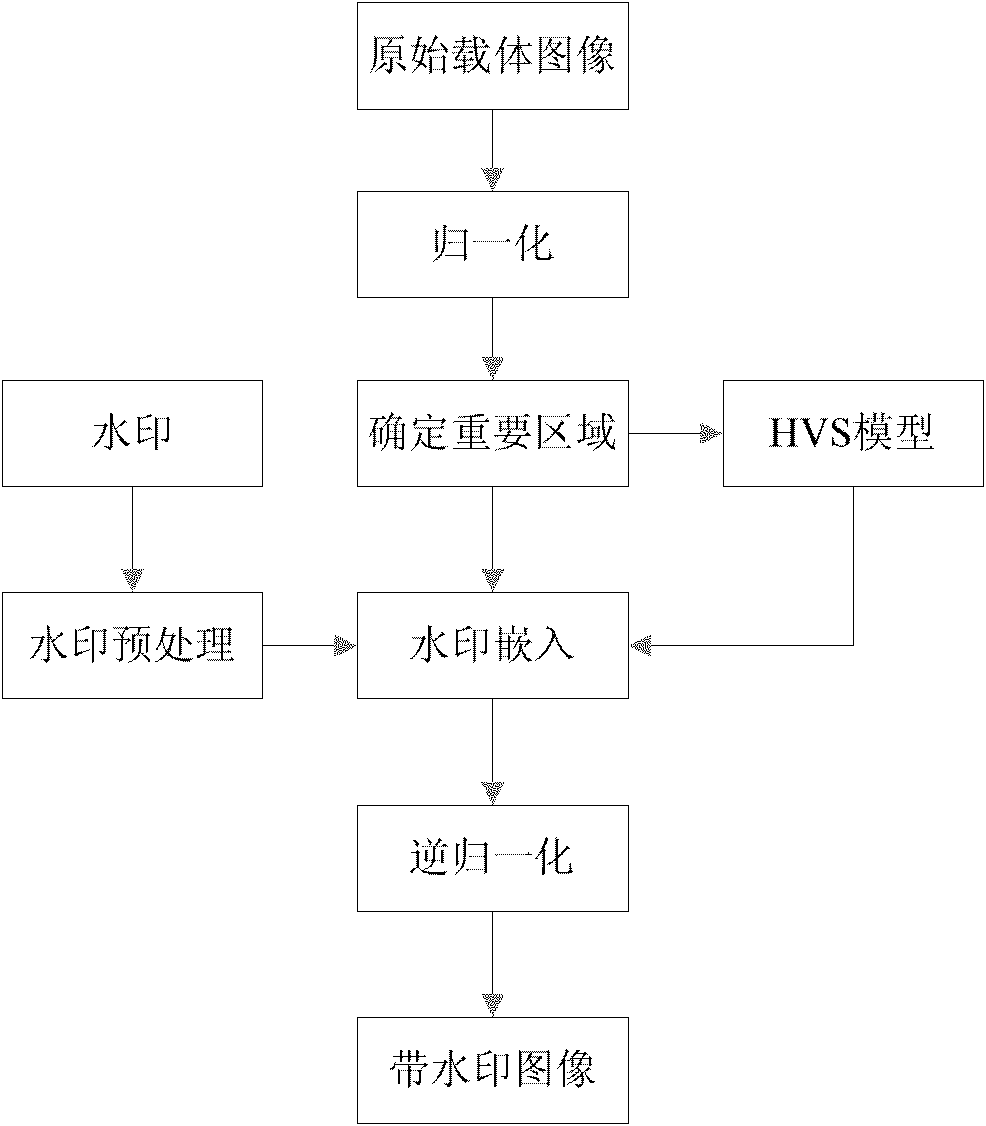
Digital image watermarking method based on visual perception characteristics
InactiveCN102024249ASimple calculationEasy to implementImage data processing detailsComputer visionInformation hiding
A digital image watermarking method based on visual perception characteristics provided by the invention relates to the technical field of information hiding and digital watermarking in multimedia information security, and mainly comprises the following five steps: preprocessing a digital image watermark; extracting an important region; creating a visual perceptual model; embedding the digital image watermark; and detecting the digital image watermark. A specific flow comprises the following steps: firstly, mapping a carrier image into a geometrical invariant space by using an image normalization method based on moment, and determining the important region in the normalized image by combining an invariant centroid theory; and then, establishing the visual perceptual model according to the visual perception characteristics; and finally, combining the visual perceptual model, and using a special adaptive quantization modulation policy to adaptively embed a 256-bit readable watermark in a DFT (discrete Fourier transformation) area of the important region. An original carrier is unnecessary for extracting out the watermark, so that blind detection is realized well. The method is not only good in transparency, but also has better robustness.
Owner:LIAONING NORMAL UNIVERSITY
Standalone hardware accelerator for advanced encryption standard (AES) encryption and decryption
InactiveUS8817979B2Random number generatorsEncryption apparatus with shift registers/memoriesS-boxAdvanced Encryption Standard
Systems and methods for accelerating AES encryption and decryption operations are provided. Aspects of the method may include time multiplexing a plurality of substitution boxes (S-boxes) for instantaneous key generation and byte substitution operations. Bytes may be substituted in at least a portion of a current security key information and at least a portion of a subsequent security key information within said plurality of S-boxes. The current security key may comprise 128 bits, 192 bits or 256 bits and the portion of the current security key may comprise 32 bits. The substituted portion of the security key information may be communicated to a key generator. The subsequent security key information may be generated utilizing the substituted portion of the current security key information. The current security key information may then be stored.
Owner:AVAGO TECH INT SALES PTE LTD
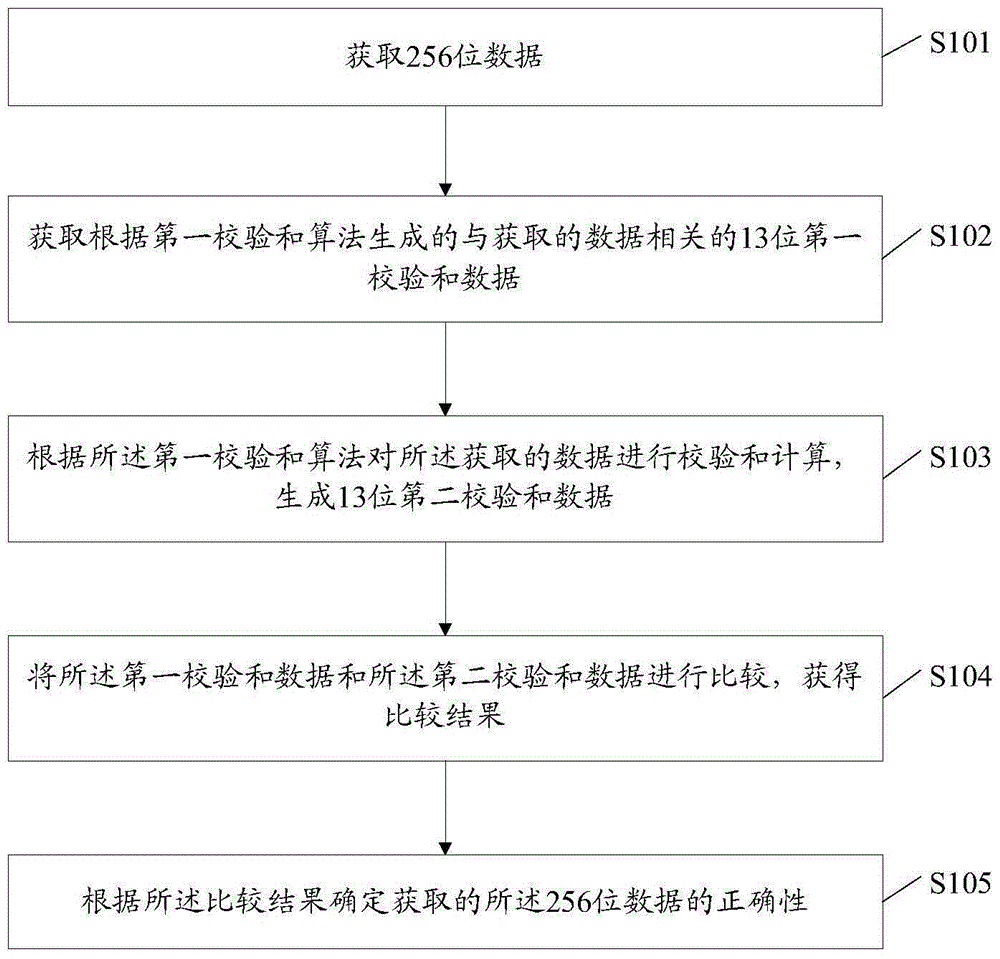
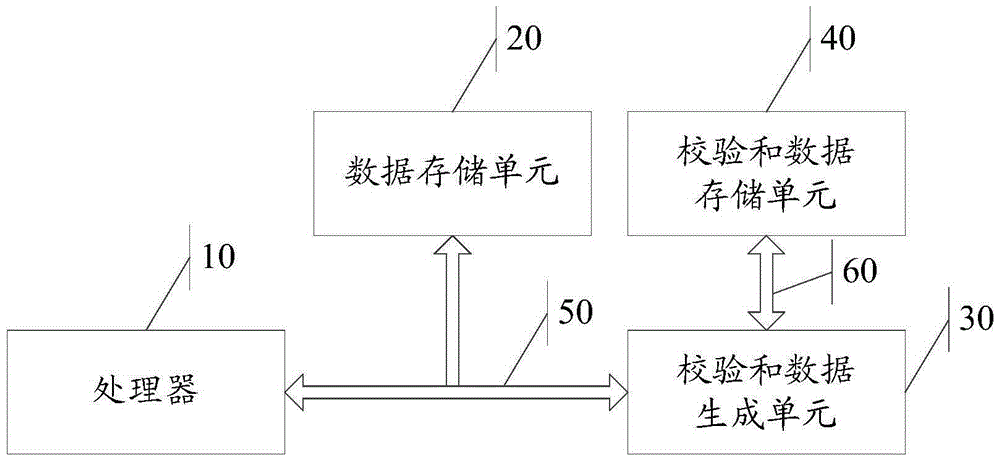
Data check method and device and electronic equipment
ActiveCN105183579AImprove experienceAvoid the disadvantages of longerRedundant data error correctionChecksum256-bit
The invention discloses a data check method and device and electronic equipment. The method includes the steps that 256-bit data are obtained; 13-bit first checksum data related to the obtained data and generated according to a first checksum algorithm are obtained; the obtained data are subjected to checksum calculation according to the first checksum algorithm, and 13-bit second checksum data are generated; the first checksum data and the second checksum data are compared, and a comparison result is obtained; the correctness of the obtained 256-bit data is determined according to the comparison result.
Owner:LENOVO (BEIJING) CO LTD
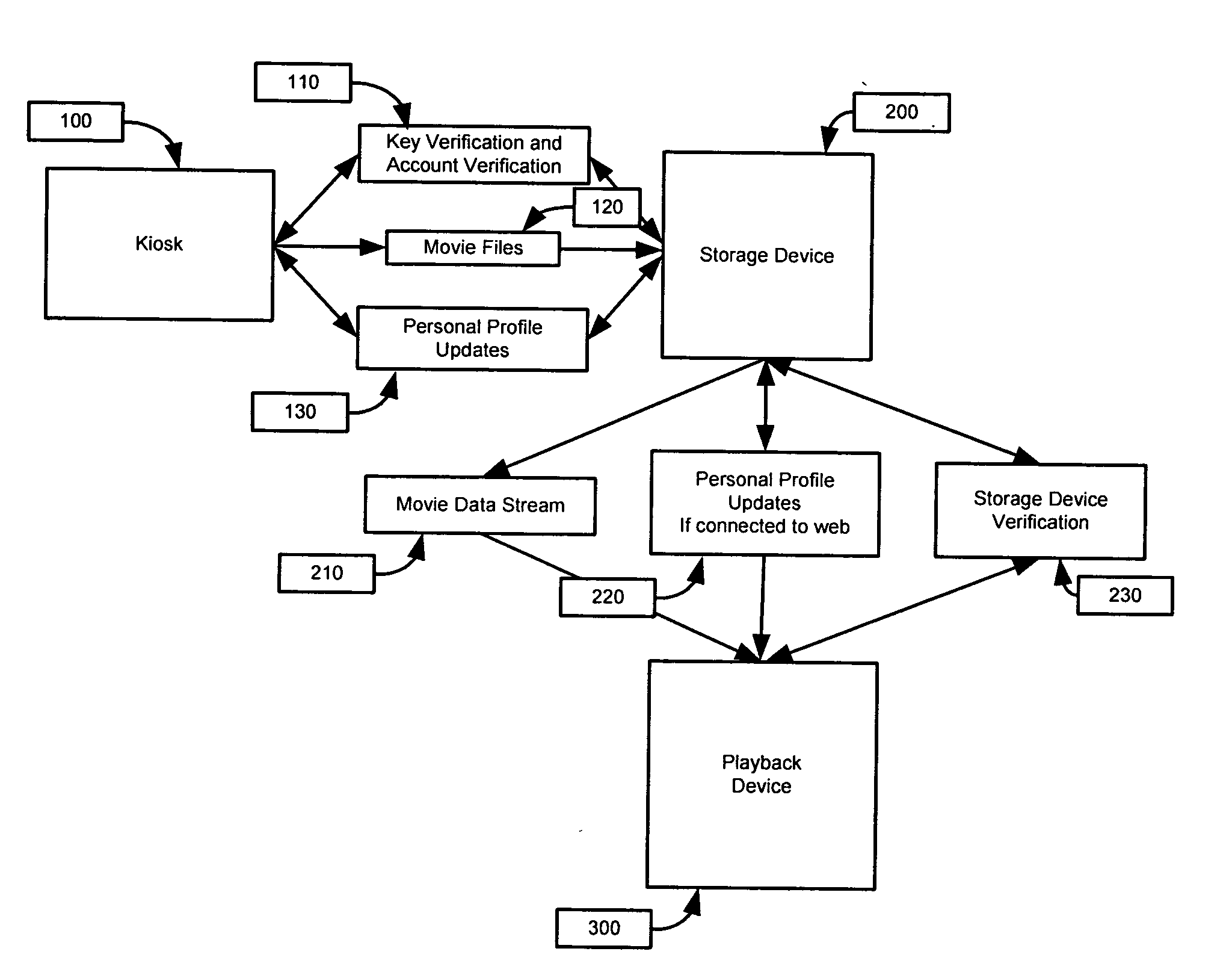
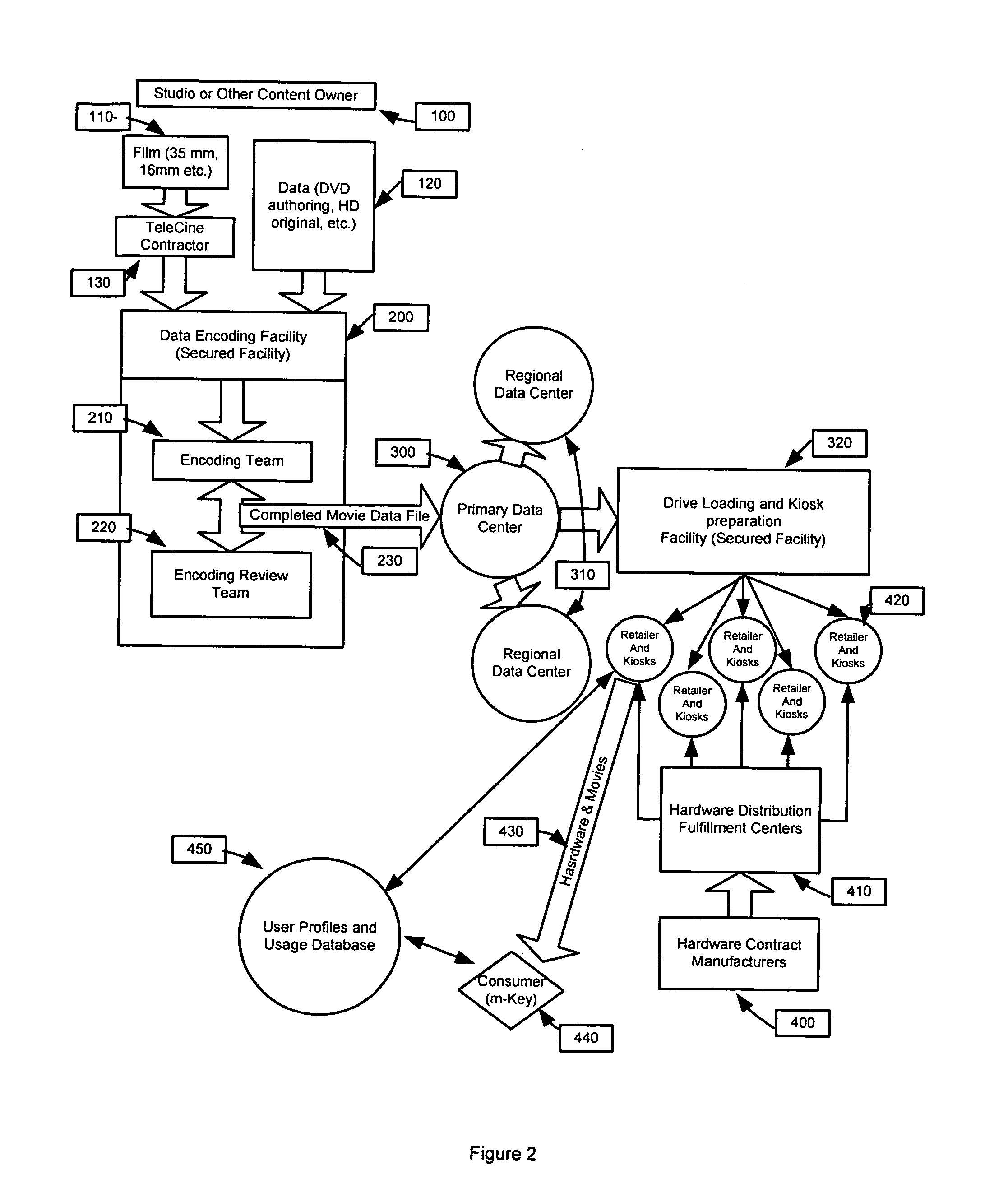
Process and apparatus for securing and retrieving digital data with a Portable Data Storage Device (PDSD) and Playback Device (PD)
InactiveUS20080279533A1Improve availabilityTelevision system detailsColor television signals processingDigital dataKey exchange
The invention is a process and apparatus for securing and retrieving digital data with a Portable Data Storage Device (PDSD) and Playback Device (PD). The PDSD-PD employs software and hardware security and encryption as barriers to those desiring illicit access to the stored data. Data is prepared with a Digital Rights Management (DRM) application which assigns a license object to the data and encrypts it using a Private Key managed Advanced Encryption Standard (AES) algorithm with 256-bit complexity. Private Keys are stored inside secured Field PGAs, PDSD, or PD. Another layer of AES encryption with 256-bit complexity is applied to the DRM license object using Public Key Infrastructure. Initial docking between a PDSD and PD initiates a sequence of routines and authentication. Interruption of the key exchange, authentication, or physical security measures may result in a lockout and / or the deletion of PDSD data. Potential applicable physical security measures are described.
Owner:BUTTARS DAVID B
Stream cipher based secure communication protocol
ActiveCN103812658AHigh encryption and decryption rateSmall footprintUser identity/authority verificationSecure communicationDigital signature
The invention relates to a stream cipher based secure communication protocol. The communication is one-time pad, keys are owned by both parties and are synchronous, the generation speed is fast, the fault-tolerant capacity is achieved, a 128-bit original text is processed every time, digital signature and data encryption are performed on the original text, and subsequently, 256-bit processed data are sent; firstly, original text grouping and hashed value calculation are performed, secondly, the data are encrypted, and finally, data decryption is achieved. According to the stream cipher based secure communication protocol, a method is designed on the basis of a stream cipher system, a grouping encryption processing structure is used for reference, the 256-bit data can be processed every time, high encryption and decryption efficiency is achieved, a random number generator is used for generating the keys which are owned by both communication parties and are synchronous, and the occupation space of the keys is small.
Owner:江苏参互延信息科技有限公司
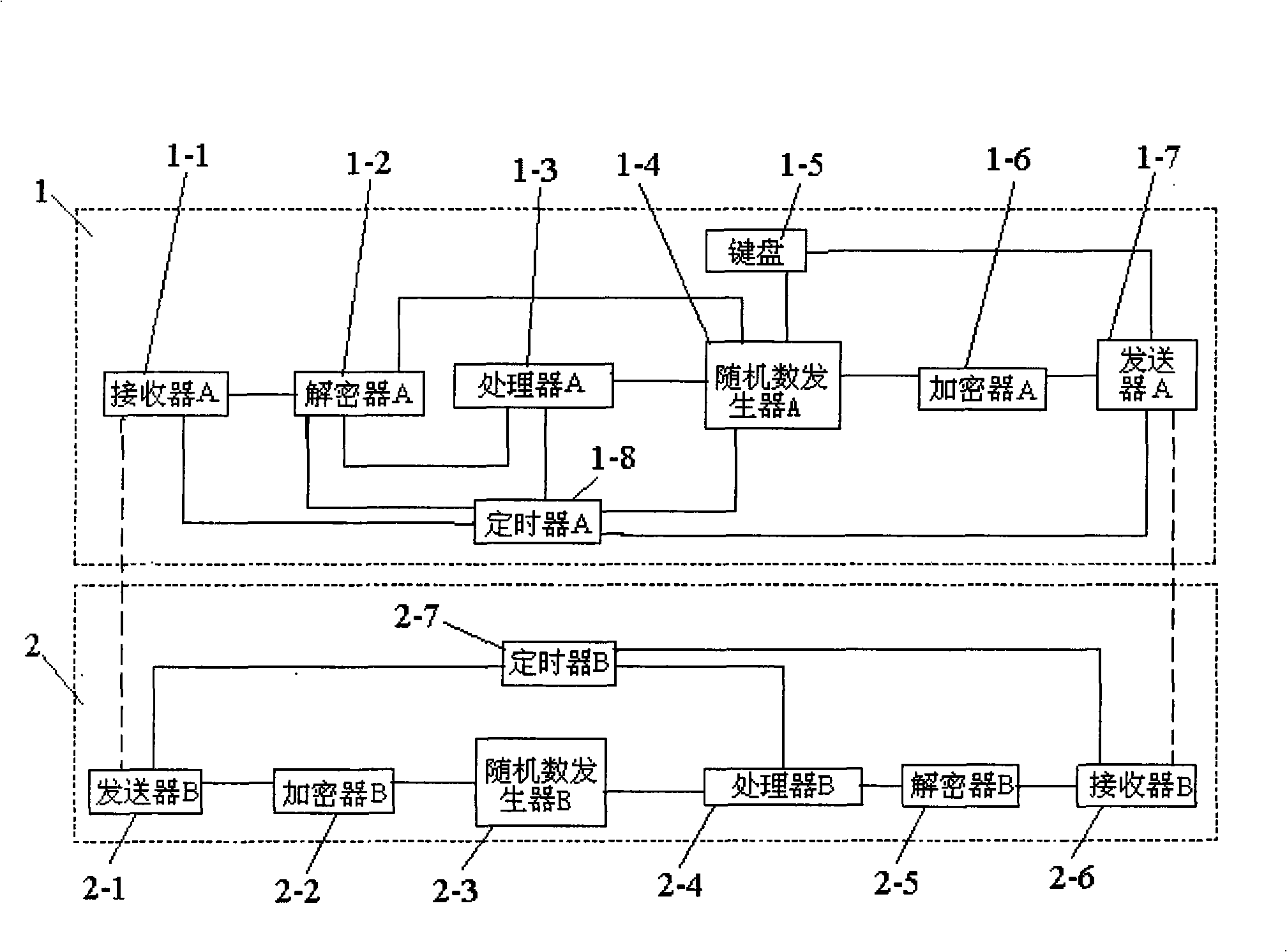
Password distant control lock control system based on AES cryptographic algorithm and control method
InactiveCN101265769AStrong EncryptionAvoid crackingEncryption apparatus with shift registers/memoriesElectric permutation locksControl systemPassword
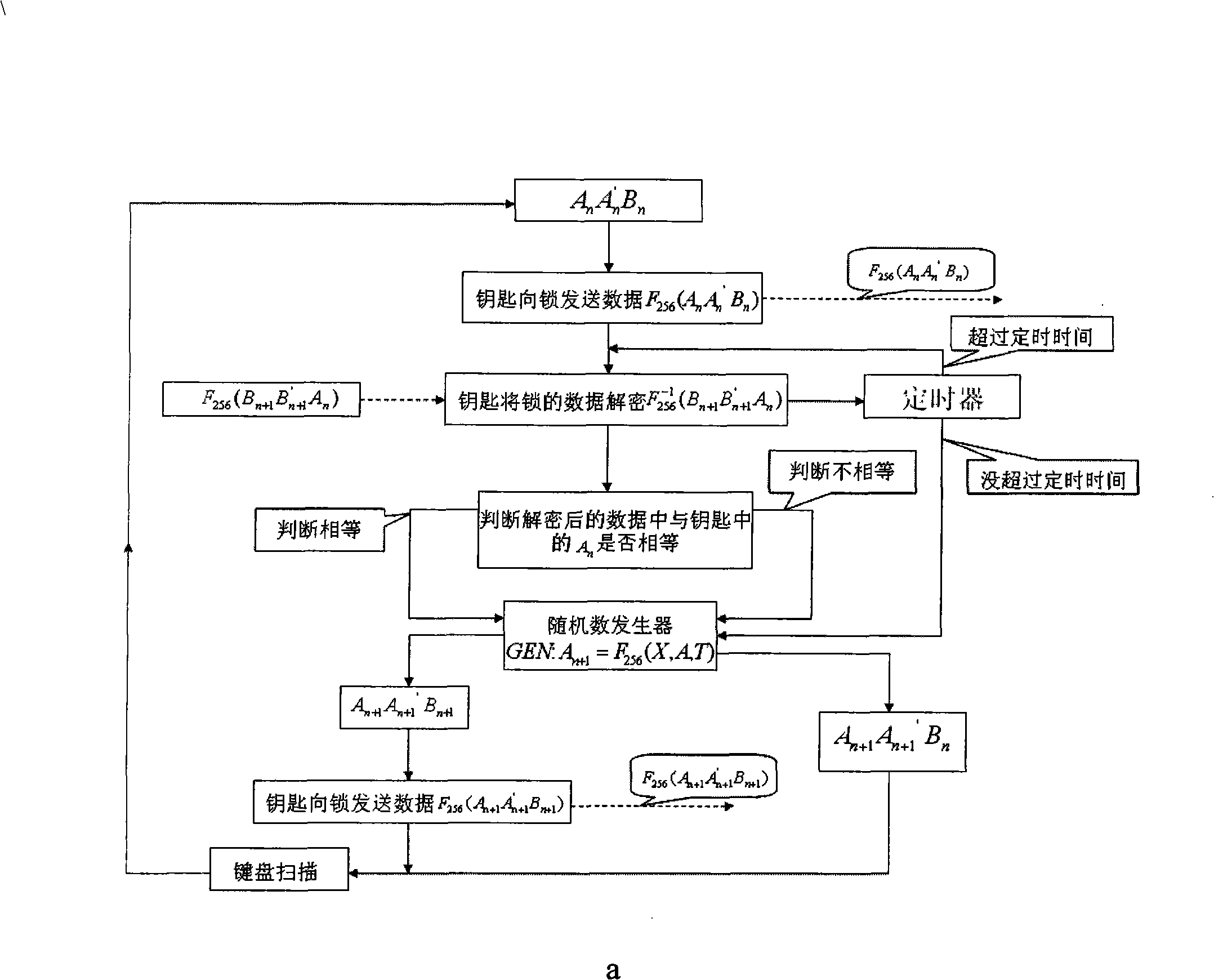
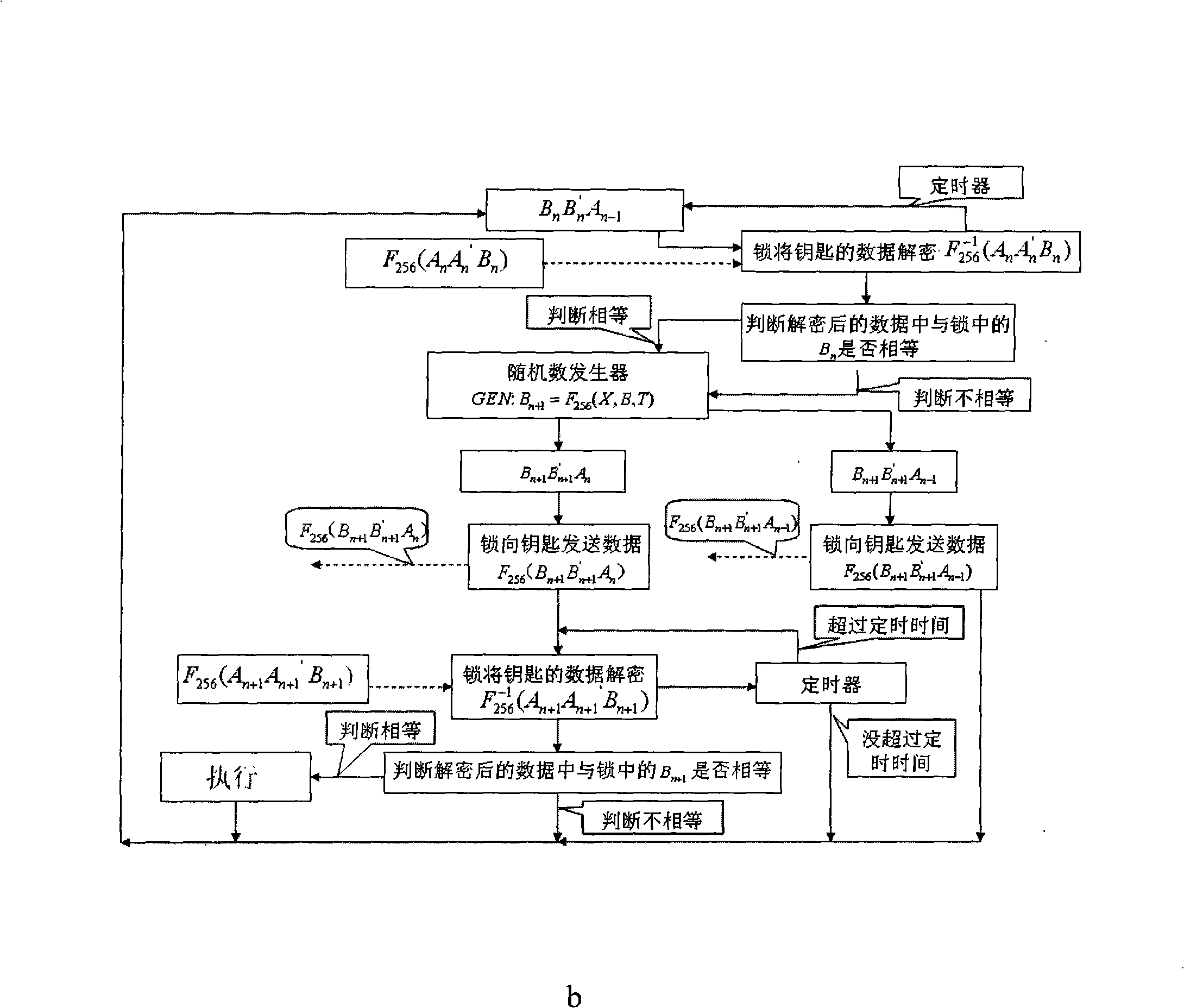
The invention discloses a password remote lock control system based on the AES cryptographic algorithm, which comprises a key unit and a lock unit. The key unit is composed of a timer A, a keyboard and a receiver A, a decoder A, a processor A, a random number generator A, an encipher A and a transmitter A connected in sequence; the lock unit is composed of a timer B and a transmitter B, an encipher B, a random number generator B, a processor B, a decoder B and a receiver B connected in sequence. By adopting the 256-bit key AES cryptographic algorithm, the password remote lock control system encrypts the time-variant random numbers and carries out the bidirectional communication transmission between the key and the lock, thereby avoiding being decoded by the prior various decoding manners, maximizing security, reliability and compatibility of the password remote lock and protecting a user's property.
Owner:余宁梅
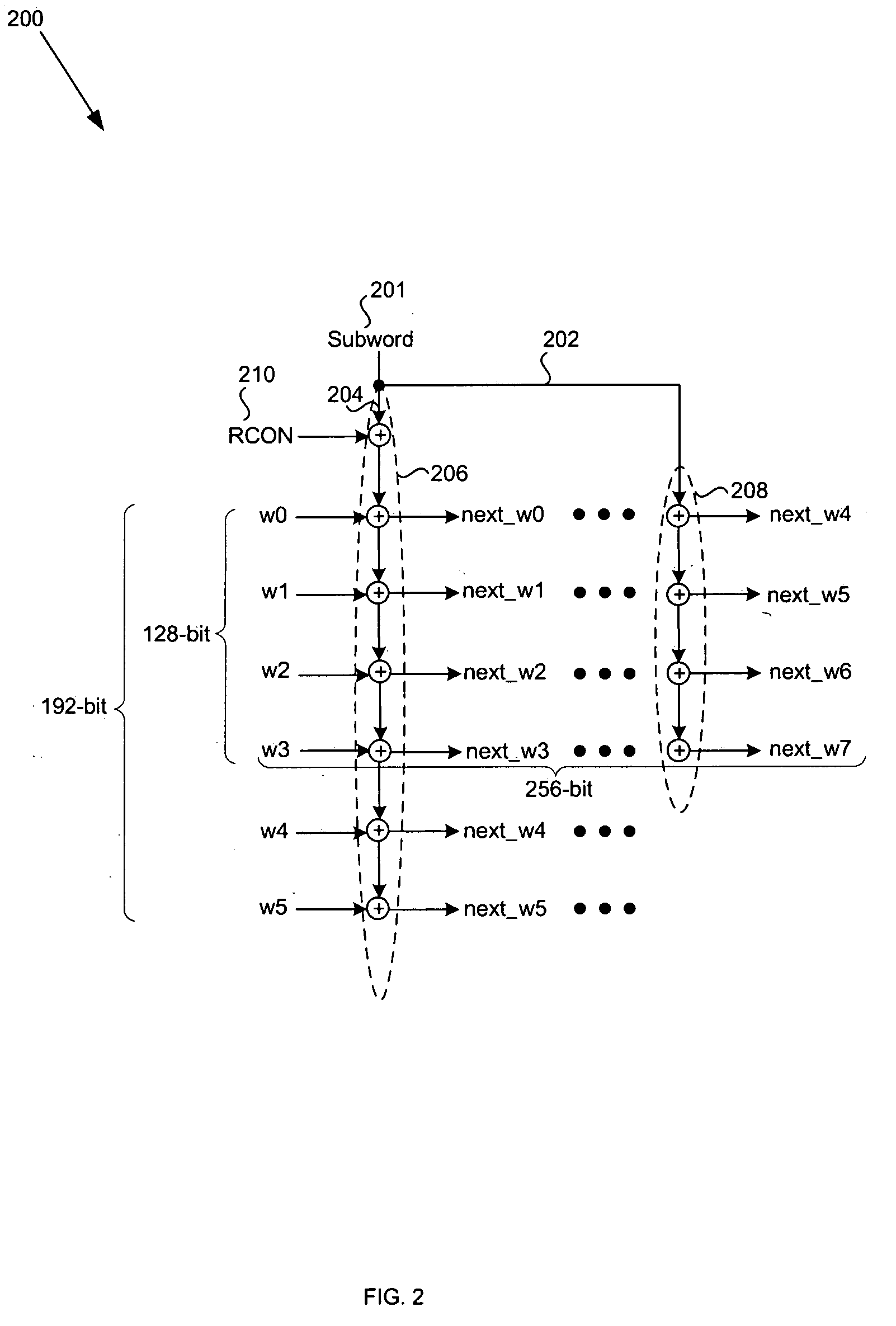
Fast key-changing hardware apparatus for AES block cipher
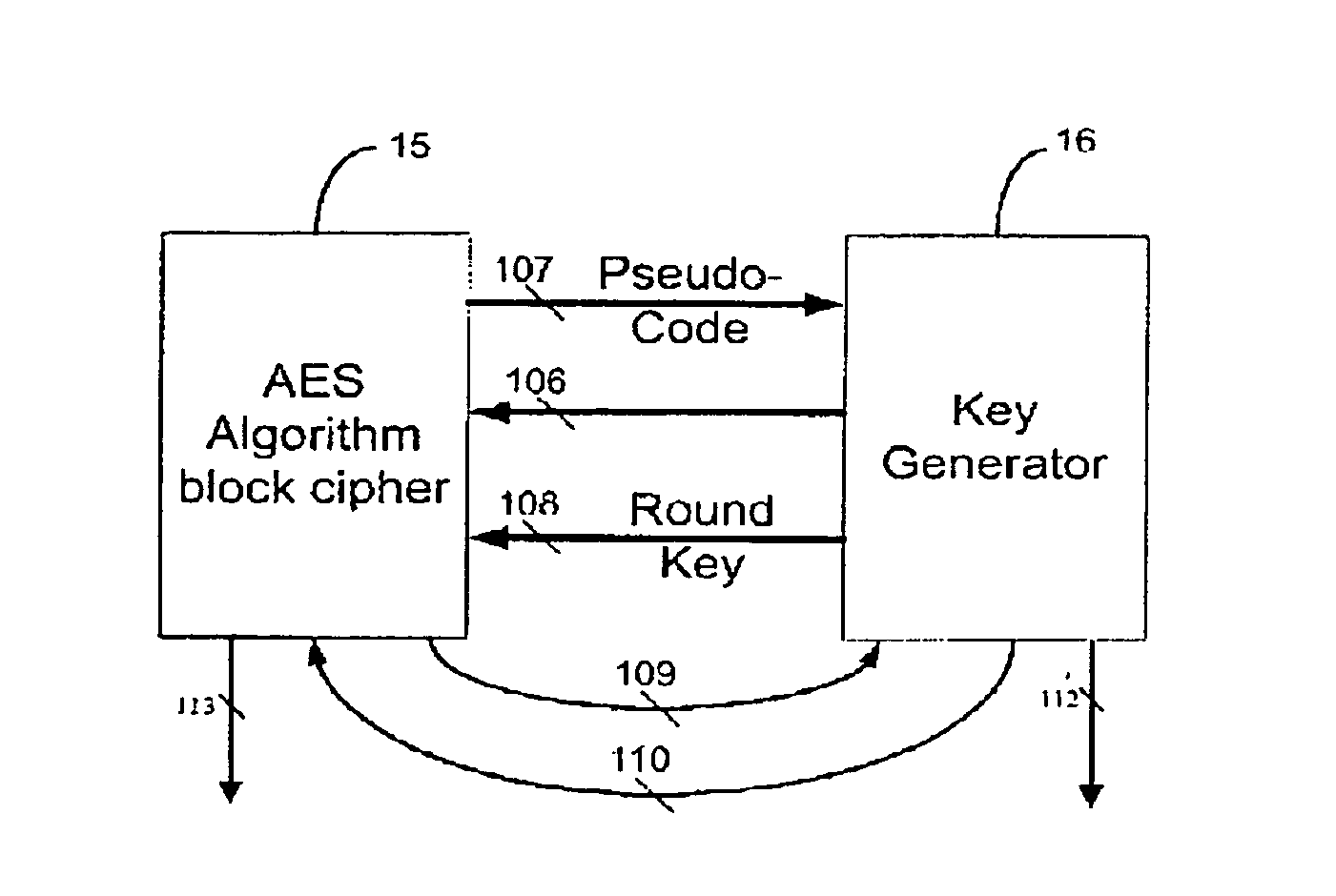
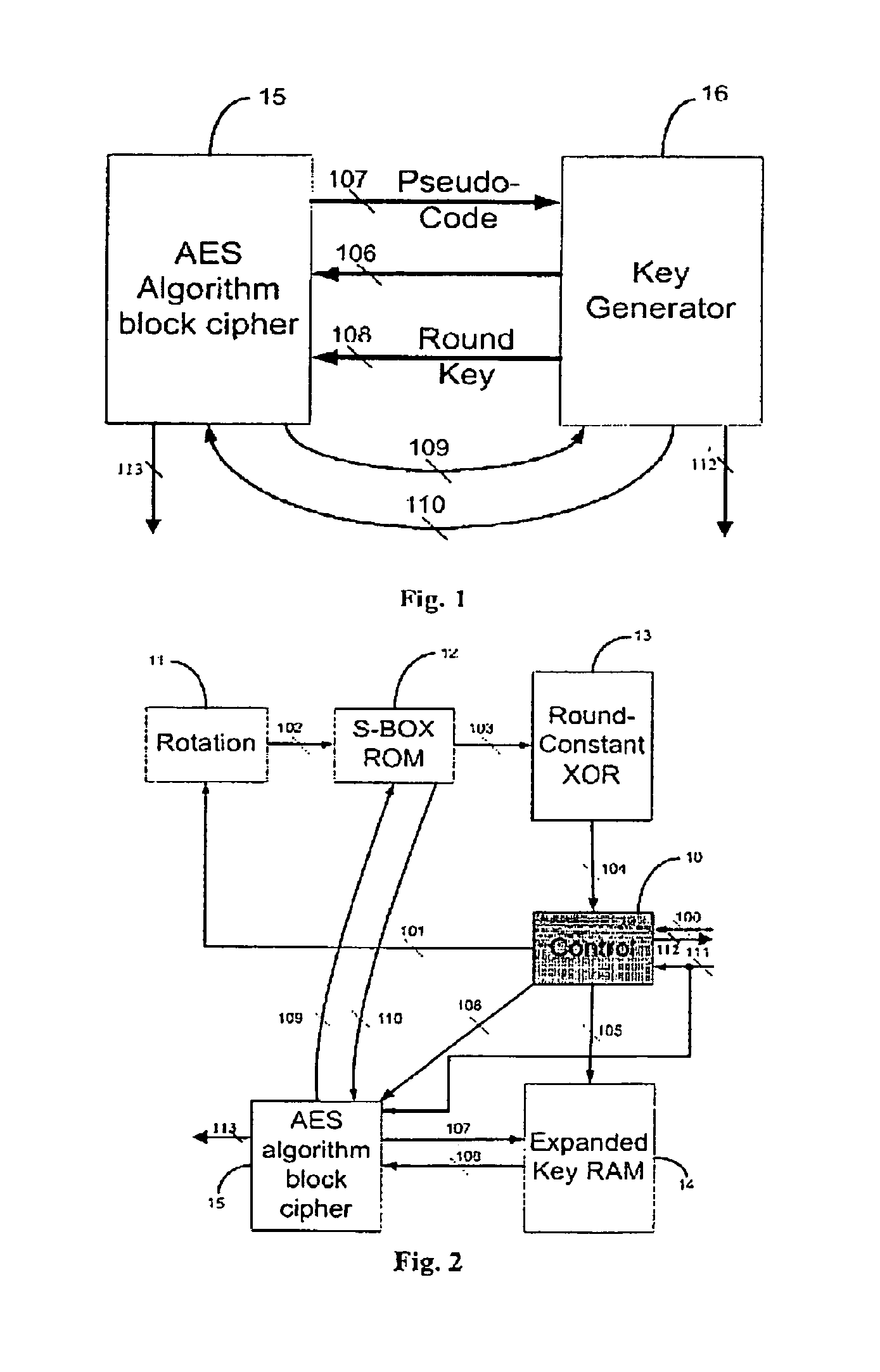
A fast key-changing hardware apparatus, which generates one sub-key each clock cycle, which is used by advanced encryption system (AES) algorithm block cipher, is independent from the AES algorithm block cipher. The invented apparatus automatically generate expanded keys from the input cipher key, store them in the key expanded RAM and ready to be used by the AES algorithm block cipher. If the key changing and the key expanding speed in the fast key-changing device is as fast as the data block (i.e. 128, 192, or 256 bits) processing speed in the AES algorithm block cipher, the cipher system has the characteristic of one-time pad perfect cryptography. When using this device with a fixed key cipher system, the original input cipher key can be detached or destroyed from the system and guarantees the safety of the cipher key.
Owner:DENG ANTE
AES (Advanced Encryption Standard) key extension method
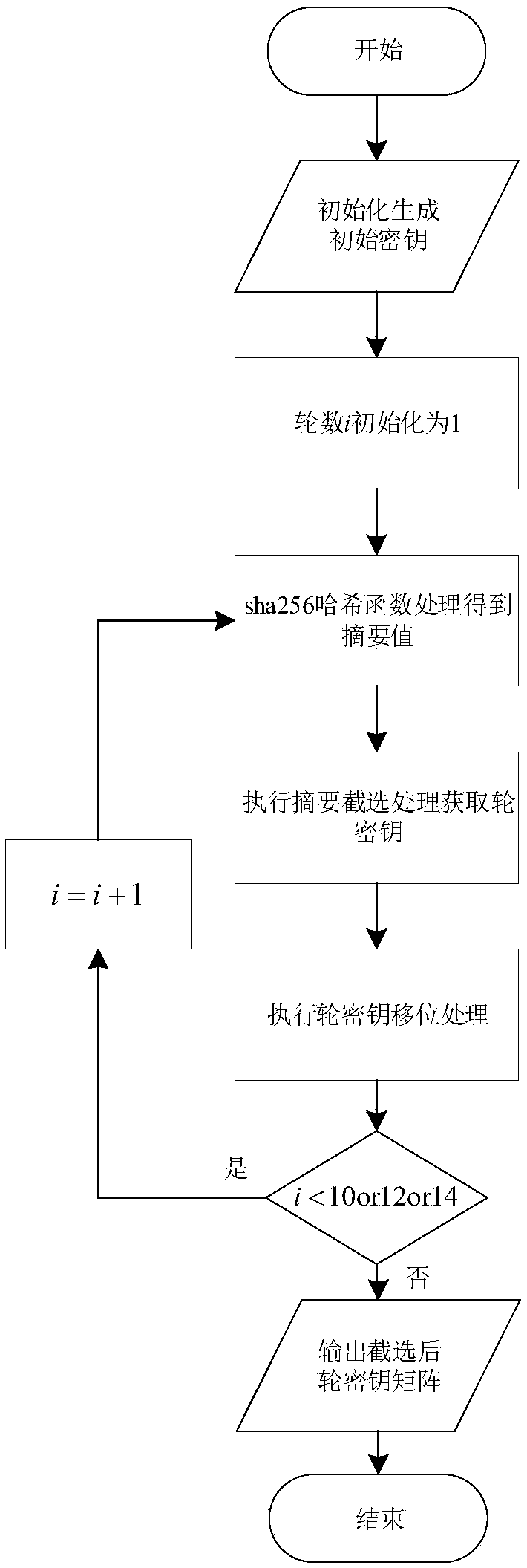
ActiveCN109302280AImprove securityAddress the Risk of Compromised KeysEncryption apparatus with shift registers/memoriesHash functionAdvanced Encryption Standard
The invention discloses an AES (Advanced Encryption Standard) key extension method, and belongs to the technical field of information security. Regarding a condition in which lengths of AES keys are 128 bits and 192 bits, a specific key interception rule is given; and by using the key interception rule, a key with a corresponding length can be intercepted from an output abstract of a sha256 hash function. Regarding an AES encryption algorithm for 128-bit, 192-bit and 256-bit keys, even though an attacker knows a corresponding interception rule, the attacker first needs to obtain an abstract generated by a key via a sha256 hash abstract function; and according to characteristics of the sha256, unless otherwise an output abstract is guessed by traversing, abstract information cannot be obtained by collision; and moreover, the complexity of the output abstract guessed by traversing is as shown in the specification and is obviously higher than the complexity of a 128-bit key and a 192-bitkey. By using the irreversibility of the sha256 hash abstract function, the unidirectionality of the AES key extension method is guaranteed; with the non-collision capability of the sha256, the difficulty of cracking a key violently is improved; and thus, the security of AES key extension is improved.
Owner:HARBIN ENG UNIV
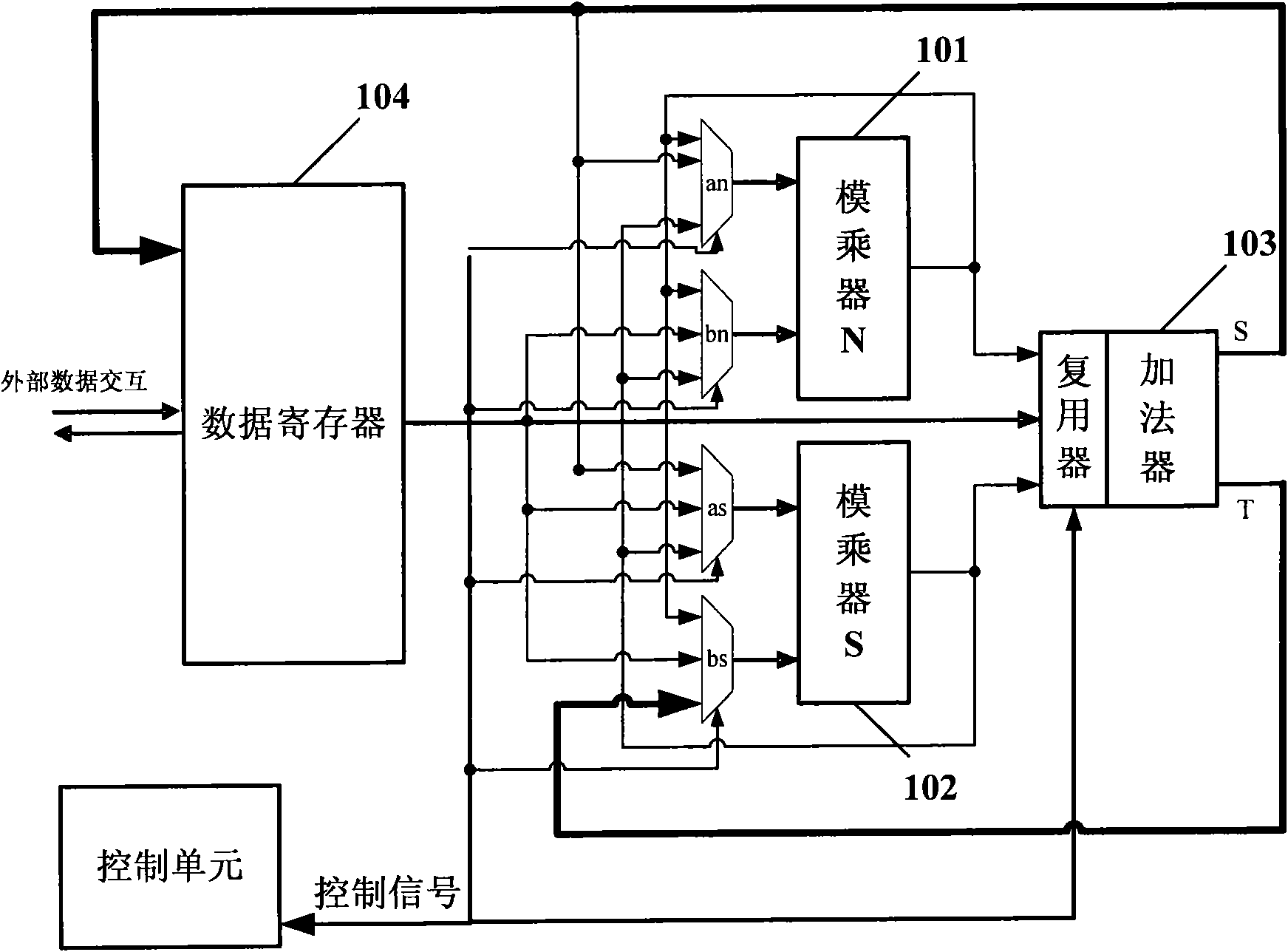
Digital in-memory computing array device
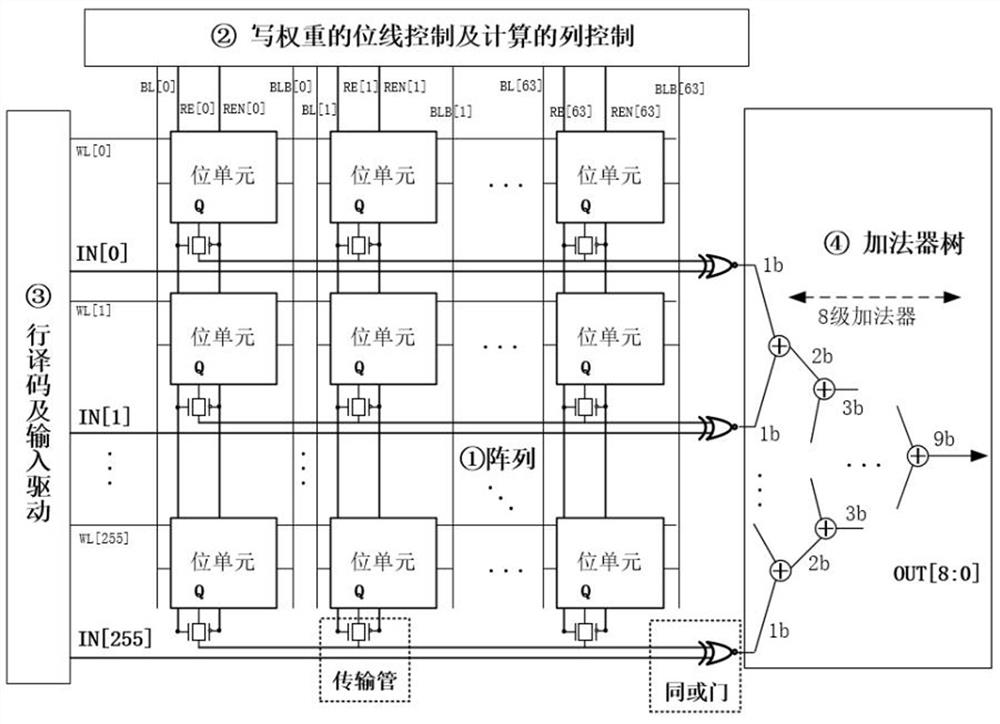
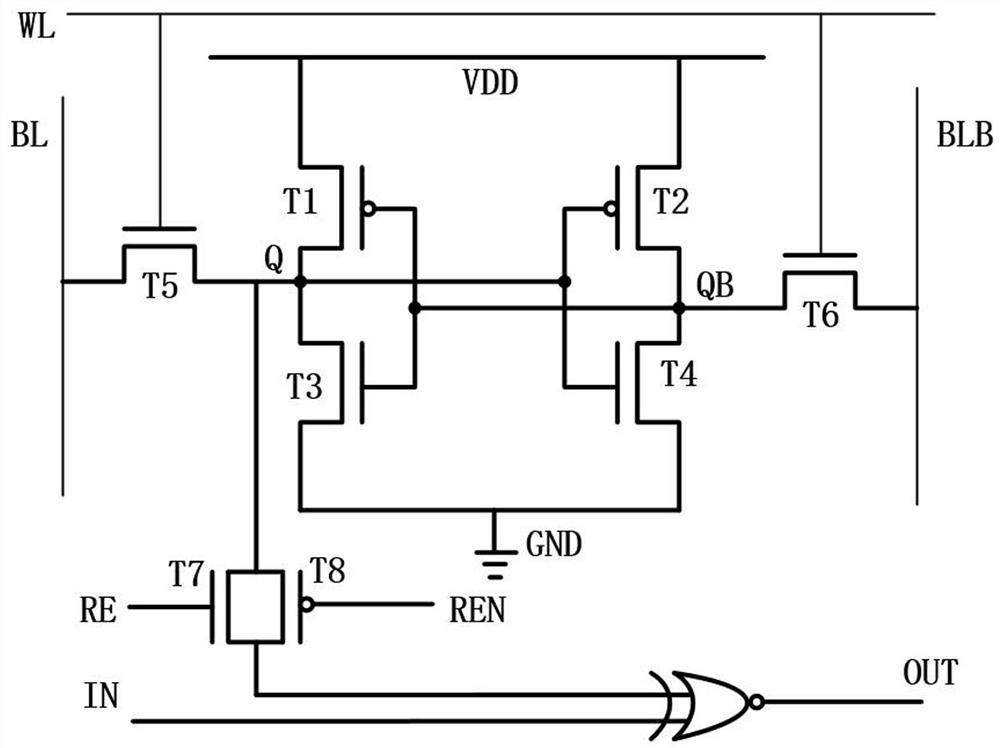
ActiveCN113035251ANo lossDigital data processing detailsDigital storageComputer architectureTransmission gate
The invention relates to a digital in-memory computing array device, which comprises 256 row * 64 column in-memory computing modules, each in-memory computing module comprises a bit cell, a tube T7, a tube 8 and an XNOR gate, and the tube T7 and the tube 8 form a transmission gate; the weight storage point Q of the bit cell is connected with the input end of the transmission gate, the output end of the transmission gate is connected with the first input end of the XNOR gate, the second input end of the XNOR gate is connected with an input signal, the output of the XNOR gate serves as the output of the bit cell, the grid electrode of the tube T7 is connected with a control signal RE, and the grid electrode of the tube T8 is connected with a control signal REN; an input signal input by each bit unit and the weight storage point Q are subjected to XNOR operation through an XNOR gate; and a column of bit cells is calculated each time, and thus accumulating 1bit outputs of 256 bit cells and then outputting a 9bit multiply-accumulate result. According to the invention, the calculation precision is improved.
Owner:中科南京智能技术研究院
Handset NFC safety payment method based on integrated voiceprint and face characteristic encryption
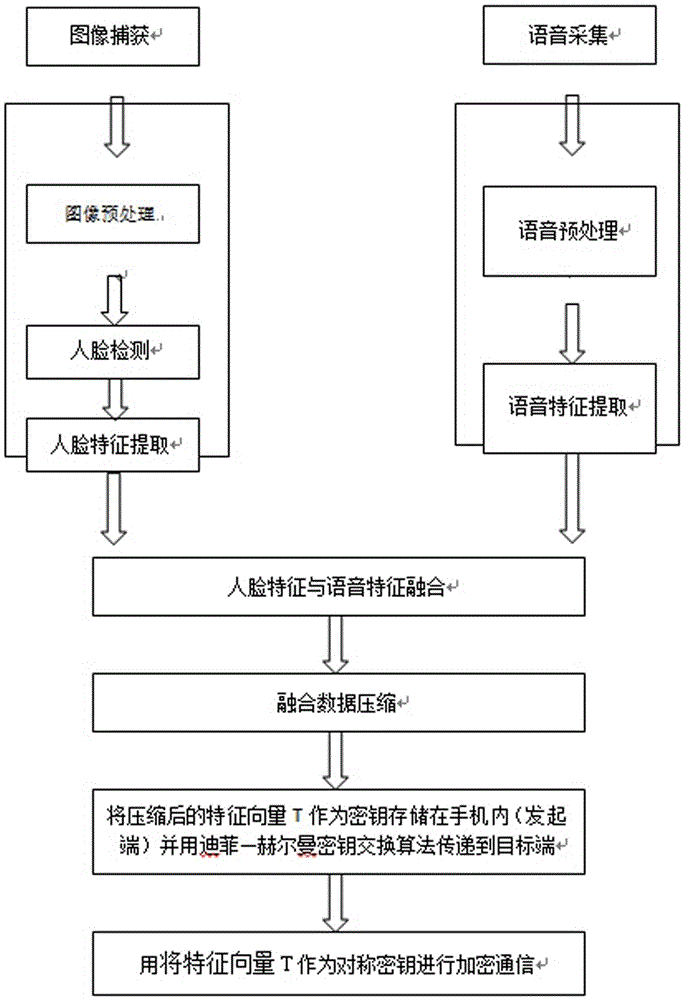
The invention discloses a handset NFC safety payment method based on integrated voiceprint and face characteristic encryption. The method is characterized by comprising steps that, image acquisition and voice acquisition are carried out; the acquired image and the acquired voice are respectively processed; integrated processing on a face characteristic vector and a voice characteristic vector is carried out to acquire a characteristic vector P; the characteristic vector P is compressed to be in 256-bit bytes, and a characteristic vector T is acquired; the characteristic vector T is taken as a secret key and is stored in a handset as an initiation end, and the characteristic vector T is transmitted by utilizing a Diffie-Hellman key exchange algorithm to a target end; the characteristic vector T is taken as a symmetric secret key by two communication parties to carry out encryption communication. The method is carried out in an NFC point-to-point mode, and through the method, information safety interaction during handset NFC payment can be realized.
Owner:GUILIN UNIV OF AEROSPACE TECH
Method for establishing channel in TLS1_3 protocol based on national cryptographic algorithm
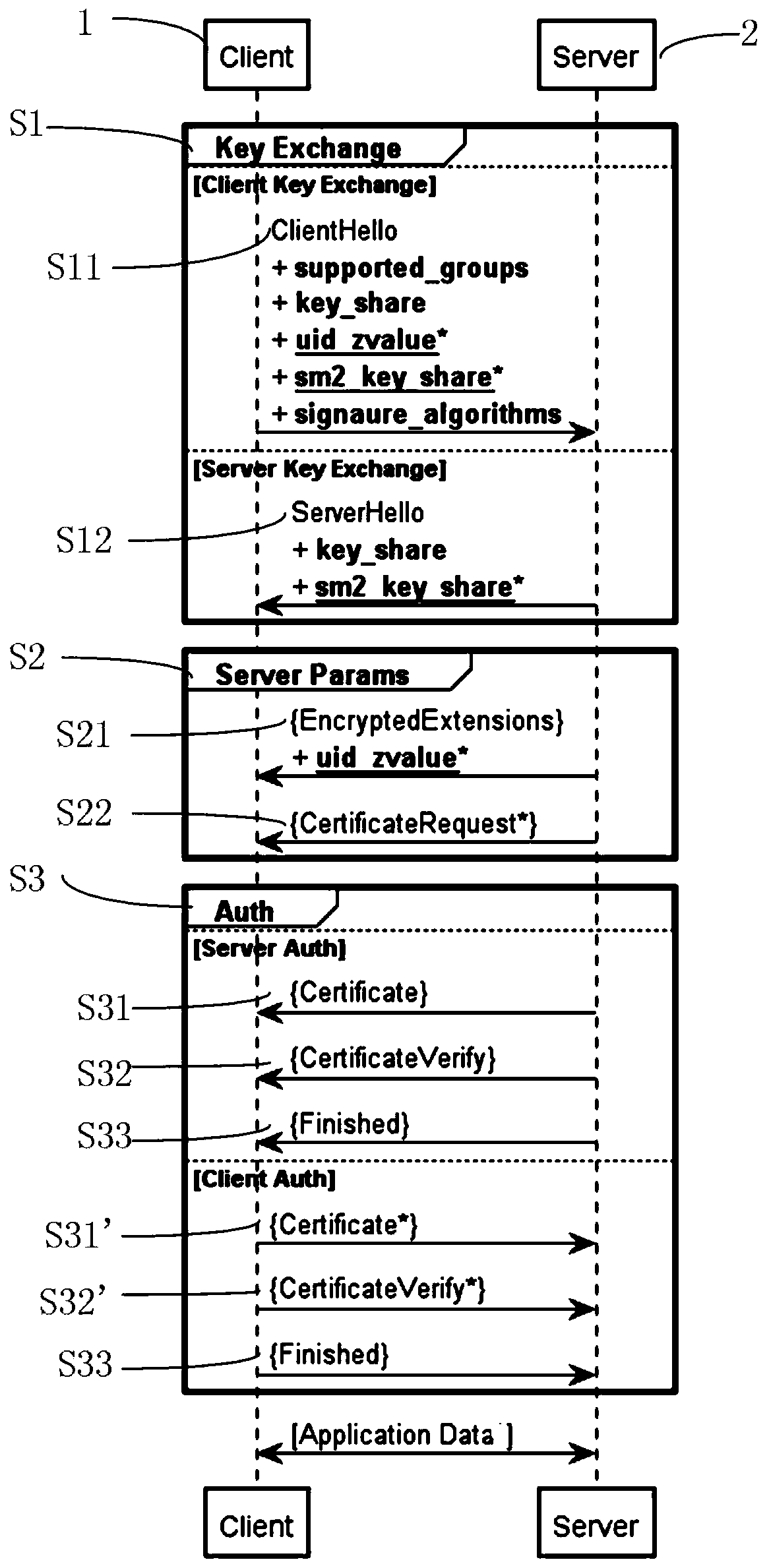
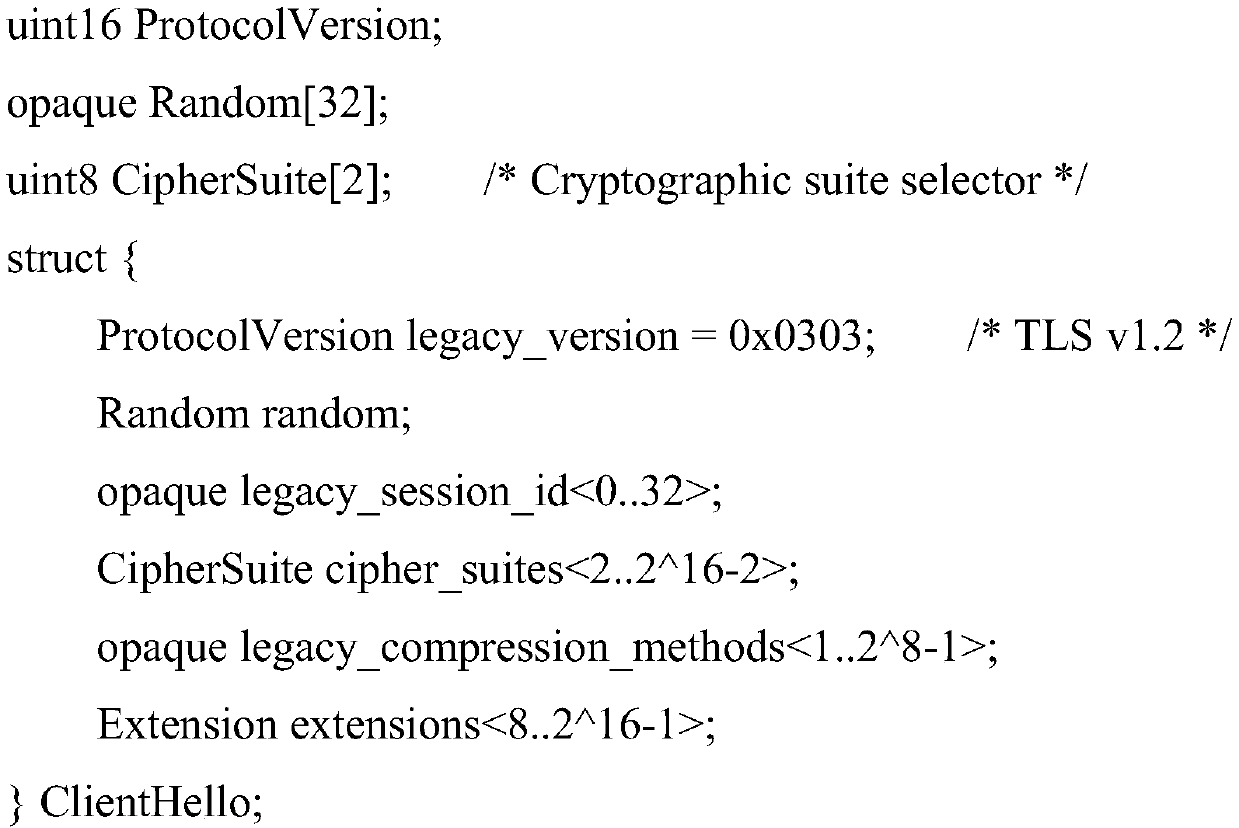
ActiveCN110995414AShorten the lengthPrevent theftEncryption apparatus with shift registers/memoriesPublic key for secure communicationKey exchangeKey size
The invention discloses a method for establishing a channel in a TLS1_3 protocol based on a national cryptographic algorithm. The method comprises a key exchange stage, a server parameter stage and anidentity authentication stage. In the key exchange phase, an SM2 key exchange algorithm is introduced to negotiate a shared key, and compared with international algorithms such as ECDH and ECDSA, a safer mechanism is adopted; in the identity authentication stage, compared with an RSA algorithm, the SM2 algorithm has the advantages that the encryption strength is similar to the safety performanceof a 3072-bit RSA algorithm when the key length of the SM2 algorithm is 256 bits, two message words are used in each round of a compression function of the SM3 algorithm, and the SM3 algorithm has higher word completeness than an existing SHA256 algorithm. In a symmetric encryption algorithm, an SM4 algorithm is introduced, a 32-round nonlinear iterative structure is adopted, the number of roundsof calculation is far larger than that of an AES algorithm, and safety is higher. According to the method, by improving the encryption algorithm serving as a data transmission safety core, secret keyleakage in the transmission process is avoided, and the safety of establishing a TLS1_3 channel is improved to a great extent.
Owner:CHINA FINANCIAL CERTIFICATION AUTHORITY
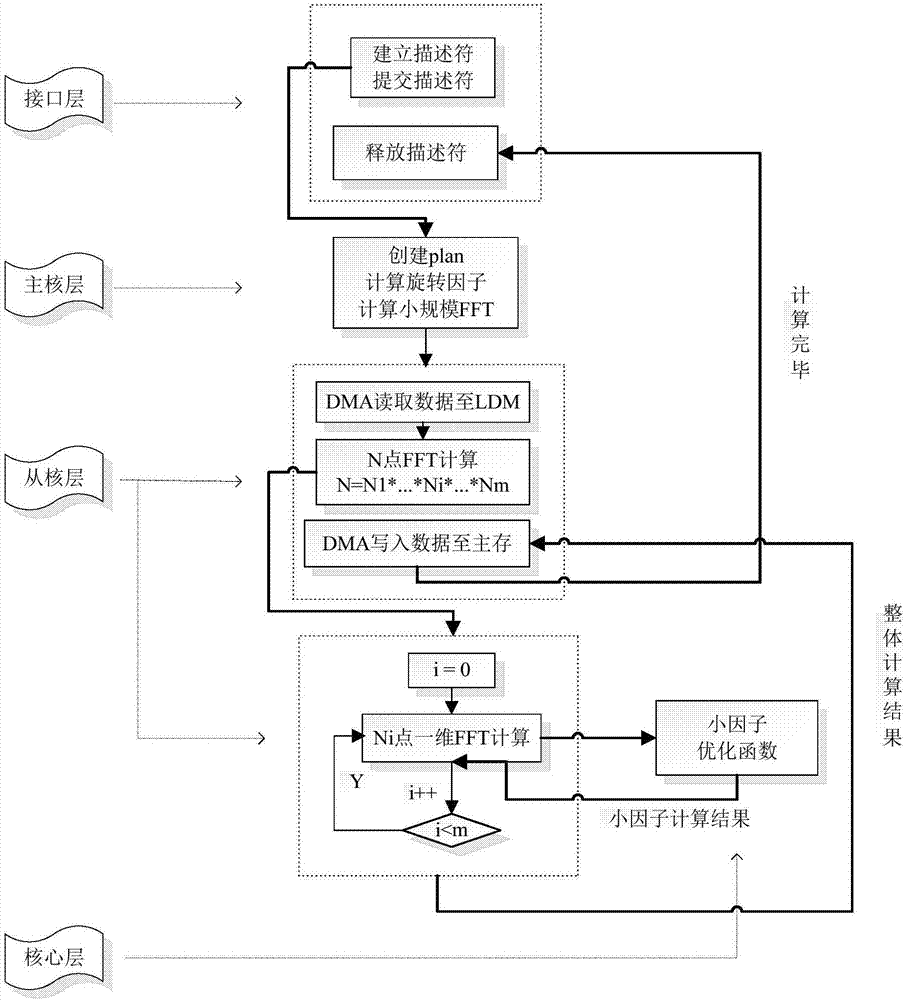
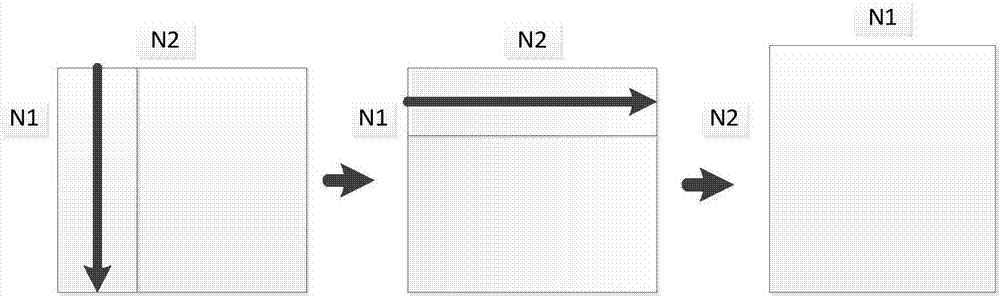
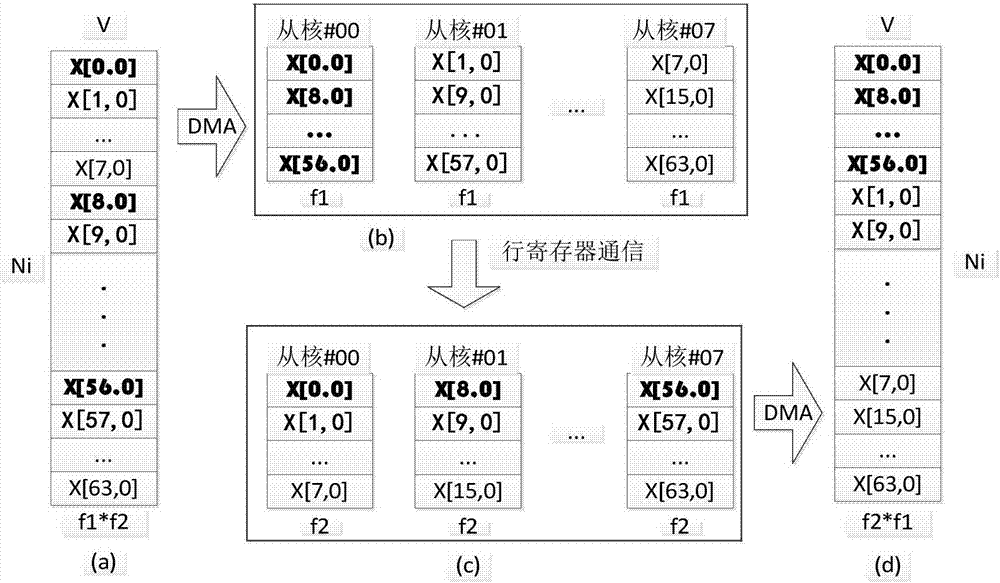
Method for realizing high performance of radix-2 one-dimensional FFT (Fast Fourier Transform) based on domestic SW 26010 processor
ActiveCN106933777AImprove performanceSolve the problem of limited memory access bandwidthComplex mathematical operationsData streamDecomposition
The invention provides a method for realizing high performance of a radix-2 one-dimensional FFT (Fast Fourier Transform) based on a domestic SW 26010 processor. Based on the domestic processor SW26010 platform, various optimization technologies such as a row or column register communication mechanism in an auxiliary core, an access memory-calculation overlapping double-buffer mechanism and a vector operation of a 256-bit single-instruction stream multiple-data stream are designed, meanwhile a two-layer decomposition-based Stockham FFT calculation framework is provided and a decomposition rule is a Cooley-Turkey algorithm, a four-layer structure framework of an interface layer, a main core layer, an auxiliary core layer and a kernel layer is designed for calculation of the radix-2 one-dimensional FFT, and thus the problem of limitation of an access memory bandwidth for the FFT calculation is effectively solved and the calculation performance of the radix-2 one-dimensional FFT is effectively improved. Compared with an open source FFTW (Fastest Fourier Transform in the West) library, the calculation performance of the radix-2 one-dimensional FFT based on the platform is rapidly improved; and a floating-point operation per second of the FFT calculation is taken as an example, an average speed-up ratio of the FFT calculation is 34.4 and a maximum speed-up ratio reaches 50.3.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI +1
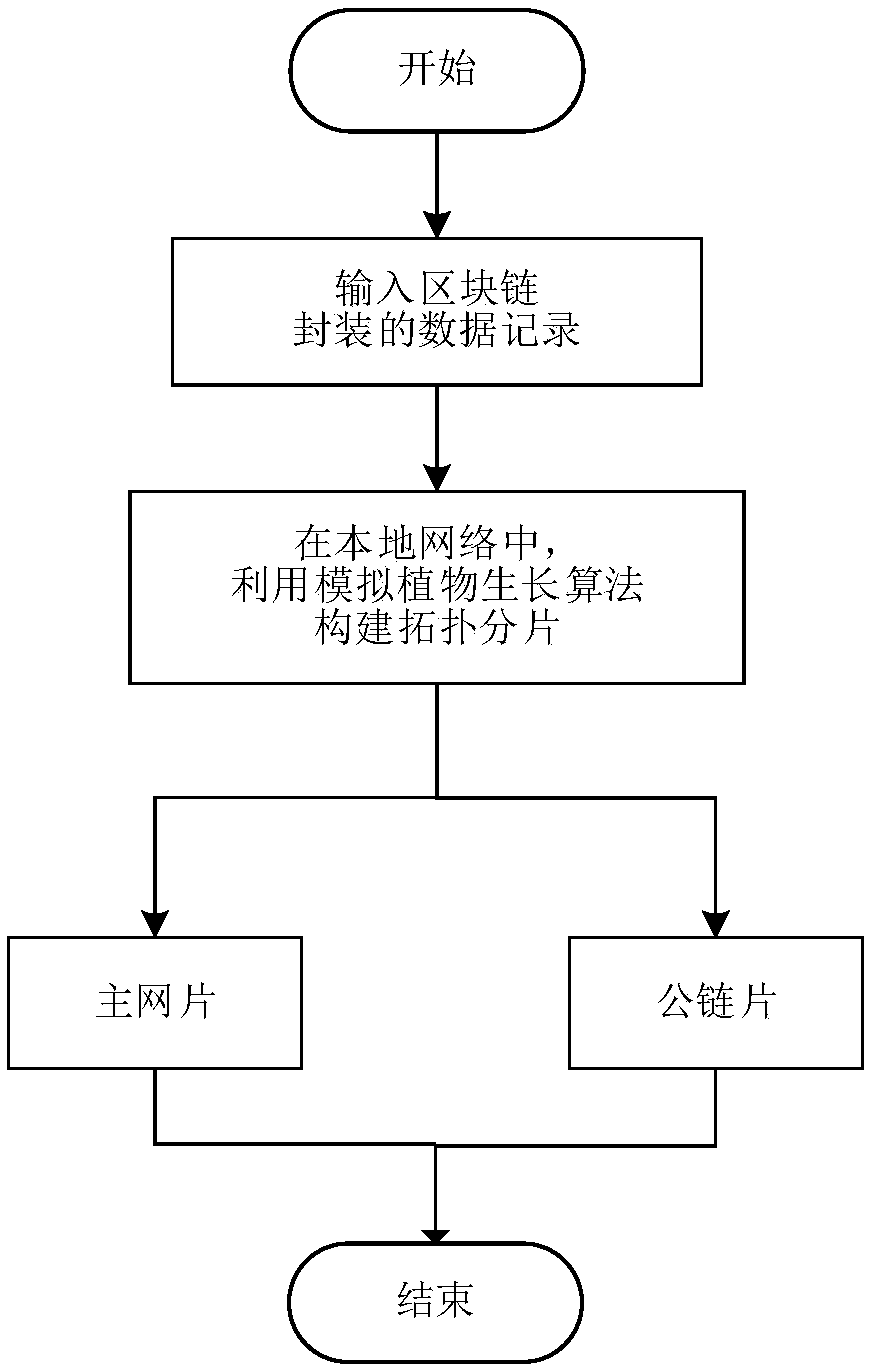
Block chain recording method based on hierarchical heterogeneous dynamic topology slicing
ActiveCN109040305AReduce the probability of illegal tamperingStrong GrowabilityData switching networksGrowth plantData recording
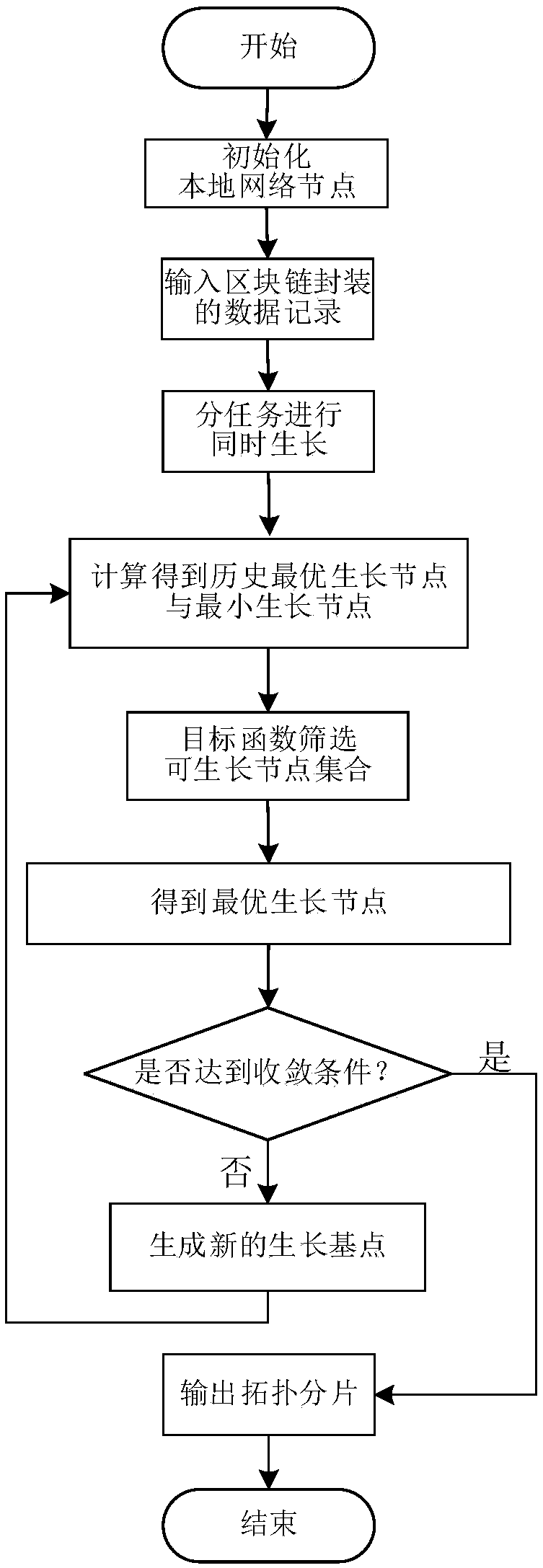
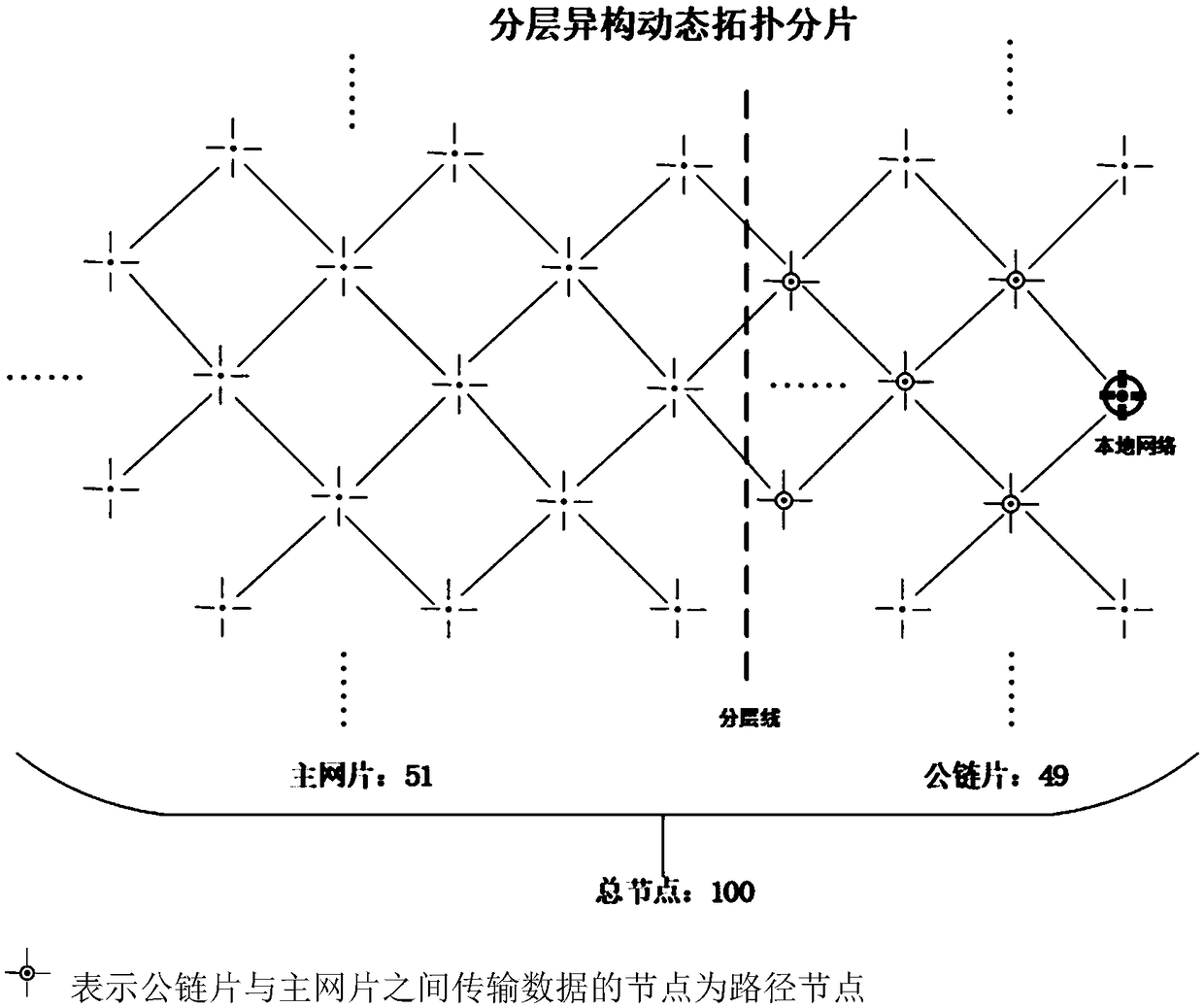
The invention discloses a block chain recording method based on hierarchical heterogeneous dynamic topology slicing, the method constructs a hierarchical heterogeneous dynamic topological slice for each block chain data record by using a simulated plant growth algorithm (PGSA) in a local network, the constructed two-layer heterogeneous dynamic topology consists of two parts, the common link and the main net, and the common link bears no more than 49% of the total number of nodes, and the main net bears no less than 51% of the total number of nodes. The nodes of the main network slice are usedto store data in a distributed manner, and the nodes of the common network slice are used to record the 256-bit Hash value after a specific encryption method (such as MD5, SHA 256, SHA 512, etc.). A layered heterogeneous dynamic topology slicing algorithm is combined with block chain recording to effectively solve that problem of 'ternary paradox' commonly faced by block chain data recording on the premise that the block chain technology is guarantee to be used for realizing the existing distributed recording technology.
Owner:湖北元村科技有限公司
Encrypted storage method of bank card information and encrypted storage system thereof
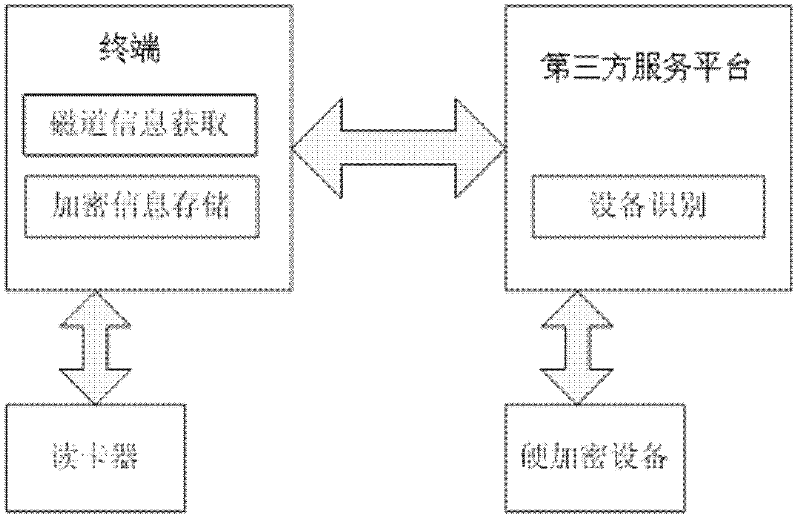
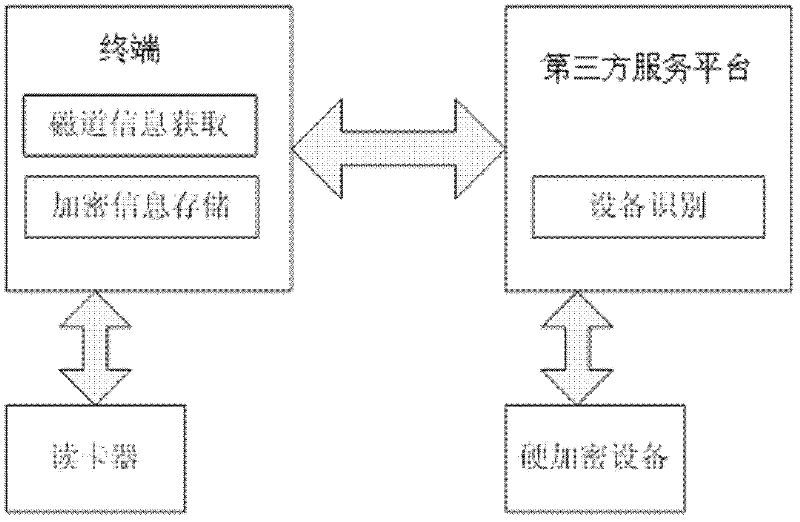
InactiveCN102496046AImprove payment experienceImprove securitySensing record carriersRecord carriers used with machinesThird partyPayment
The invention provides an encrypted storage method of bank card information and an encrypted storage system thereof. The system comprises: a terminal, which is used for initiating an encryption request and storing encrypted bank card information; a card reader, which is connected with the terminal and is used for reading magnetic track information of the bank card; a hardware encryption device, which is used for carrying out coding on the bank card information; and a third party service platform, which is used for reading the device number of the terminal, submitting the bank card information that applies for encryption to the hardware encryption device and carrying out association on the encrypted bank card information and the terminal device number and returning the information to the terminal. Therefore, according to the invention, a mobile phone user is helped to realize hardware encryption on the bank card information with low price, and a professional AES standard of over 256 bits is reached. Meanwhile, when the user carries out secondary payment, it is only needed to directly invoke the bank card information and there is no need to use a card reader or the bank card again. Therefore, payment experience and security of the user can be substantially enhanced.
Owner:快钱支付清算信息有限公司
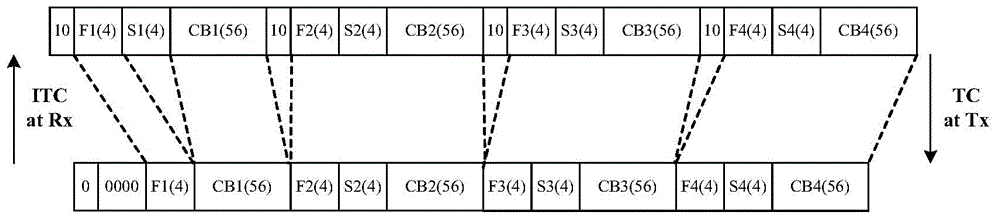
Synchronous digital multiplexer for on-frame multi plexing for multipath communication
InactiveCN1471251ALow costReduce technical difficultyTime-division multiplexTransmission path multiple useMultiplexerTime control
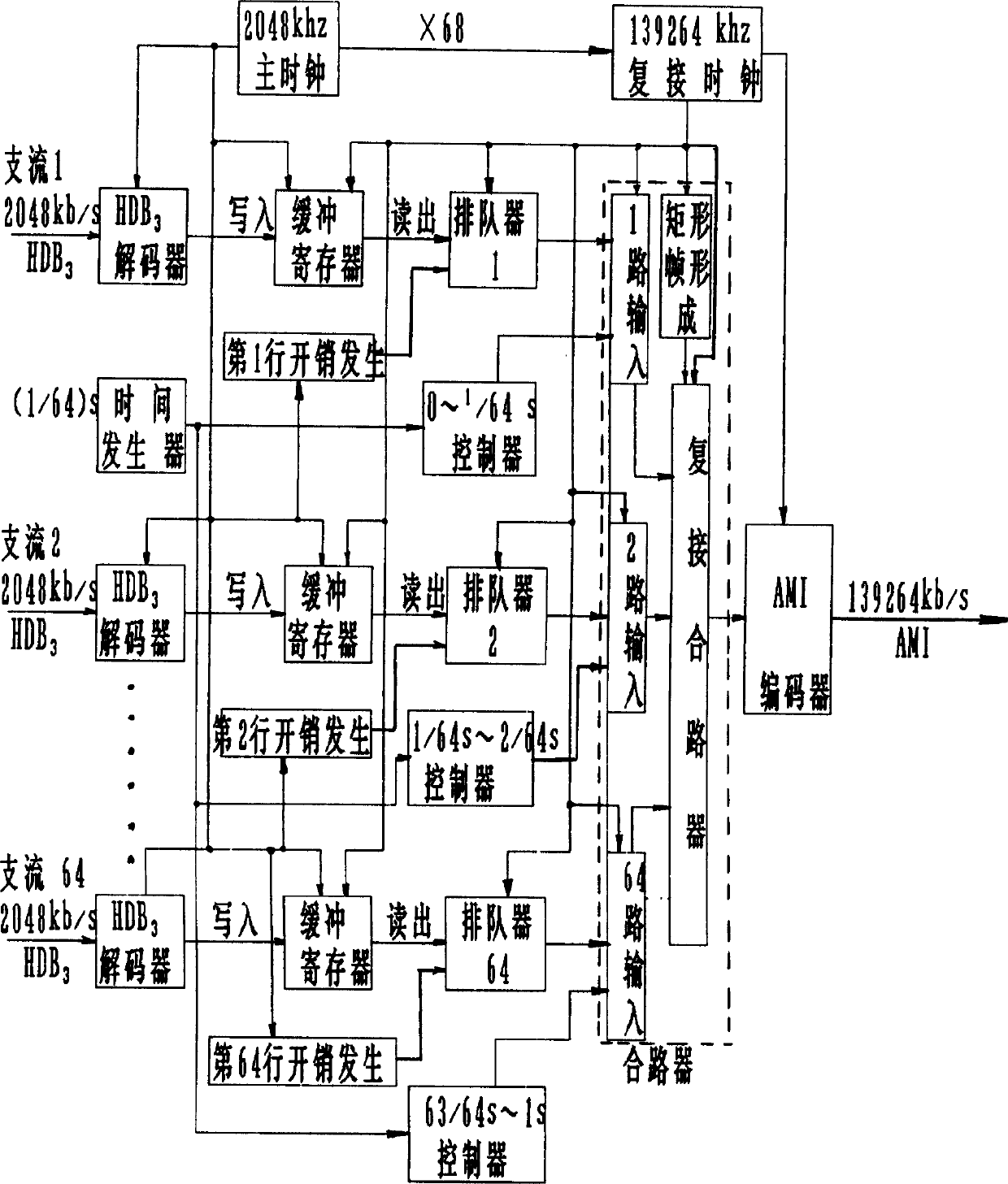
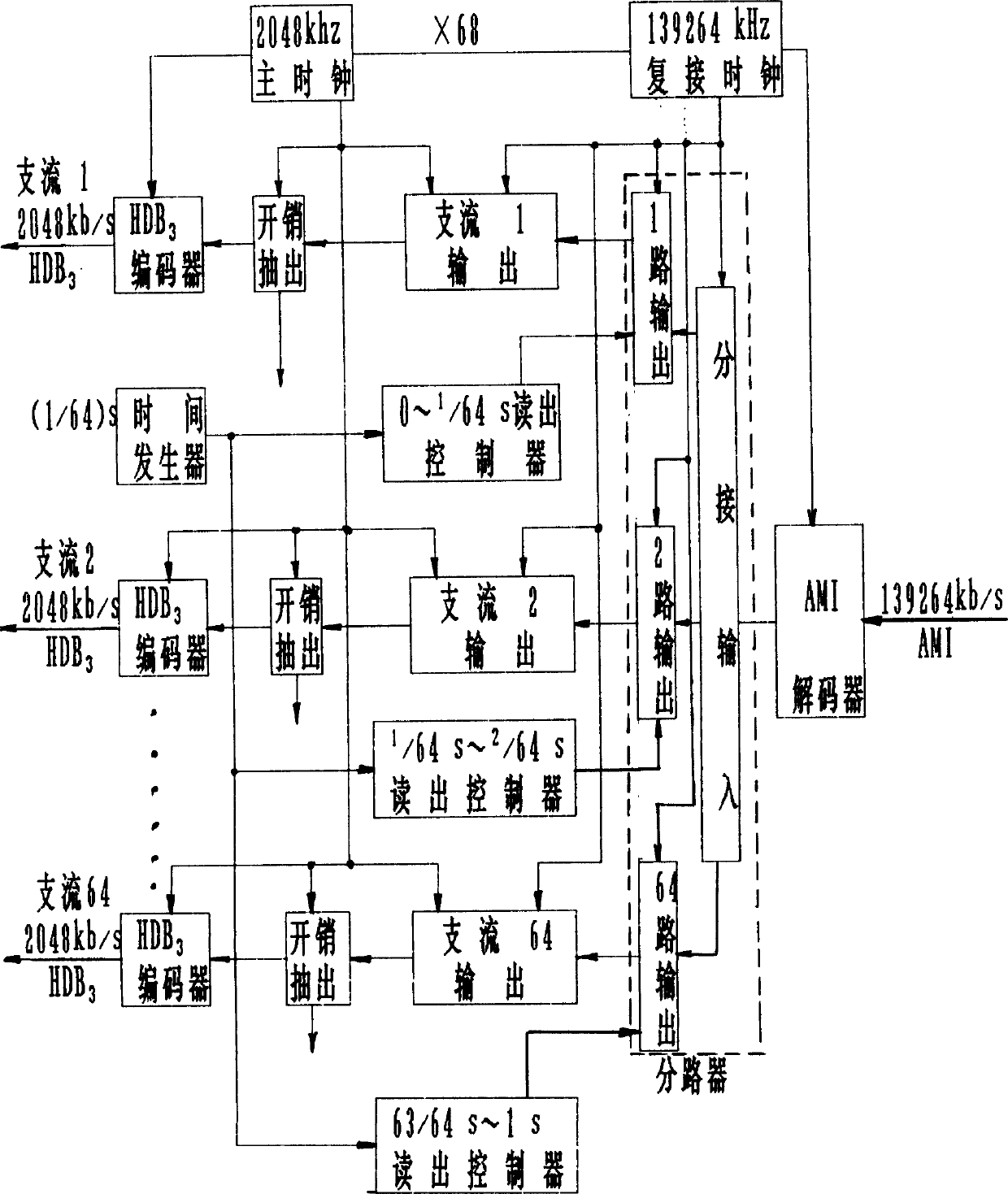
The frame structure is a rectangle structure: 64 rows / frame, 34 columns, 139264 kb / s. the first and second columns are the overhead. 3th-34th columns are affluent information. Under control of synchronous clock, each affluent is queuing. First row of first frame is written into 256 bits of first frame of first affluent, and second row of first frame is written into 256 bits of first frame of second affluent and so on. In multiple connection procedure, with decoded to NRZ code, under control of main clock, each affluent is written to own buffer register. Then, under control of synchronous multiple connection clock, the procedure is continued to enter each queue equipment, mixer and encoder to output codes. The method overcomes the shortcomings of PDH and is better than SDH, providing features of less investment, good compatibility and lower technical difficulties.
Owner:严尔林
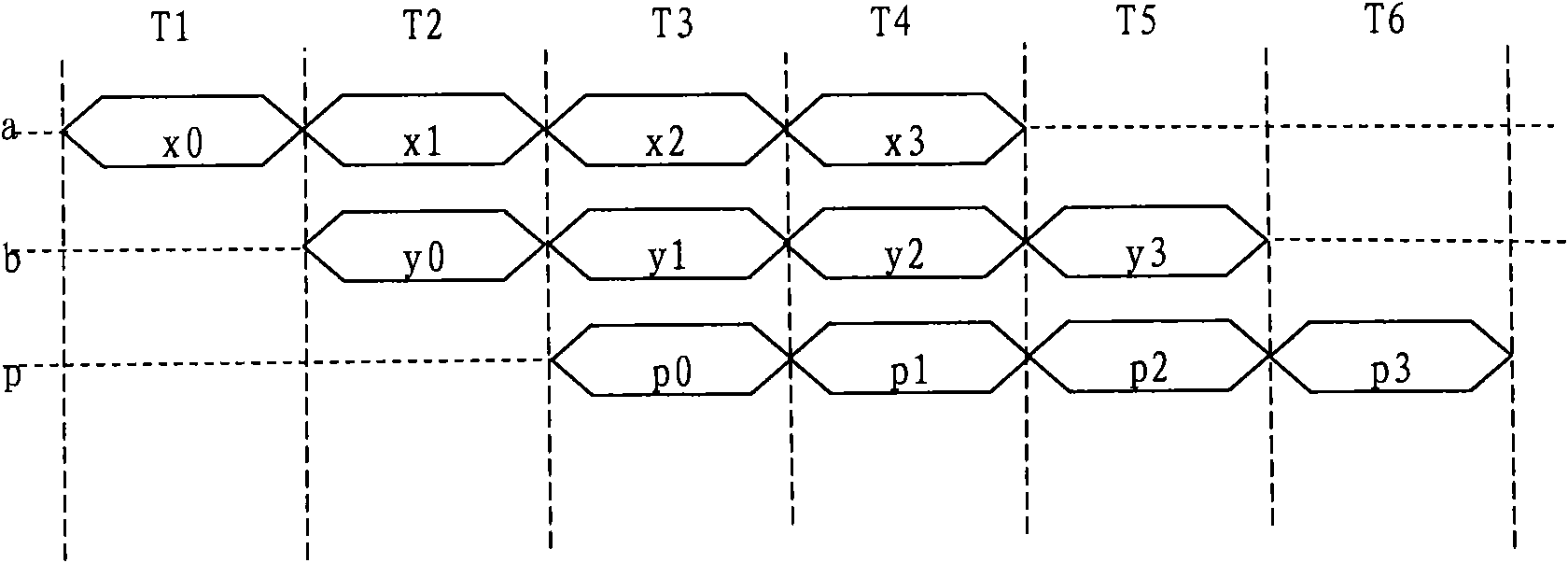
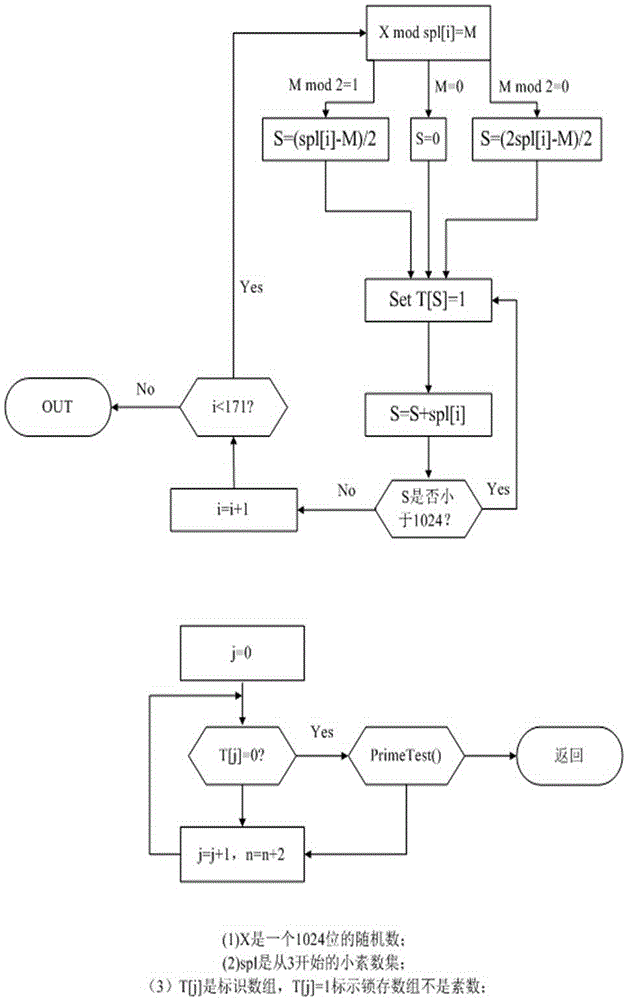
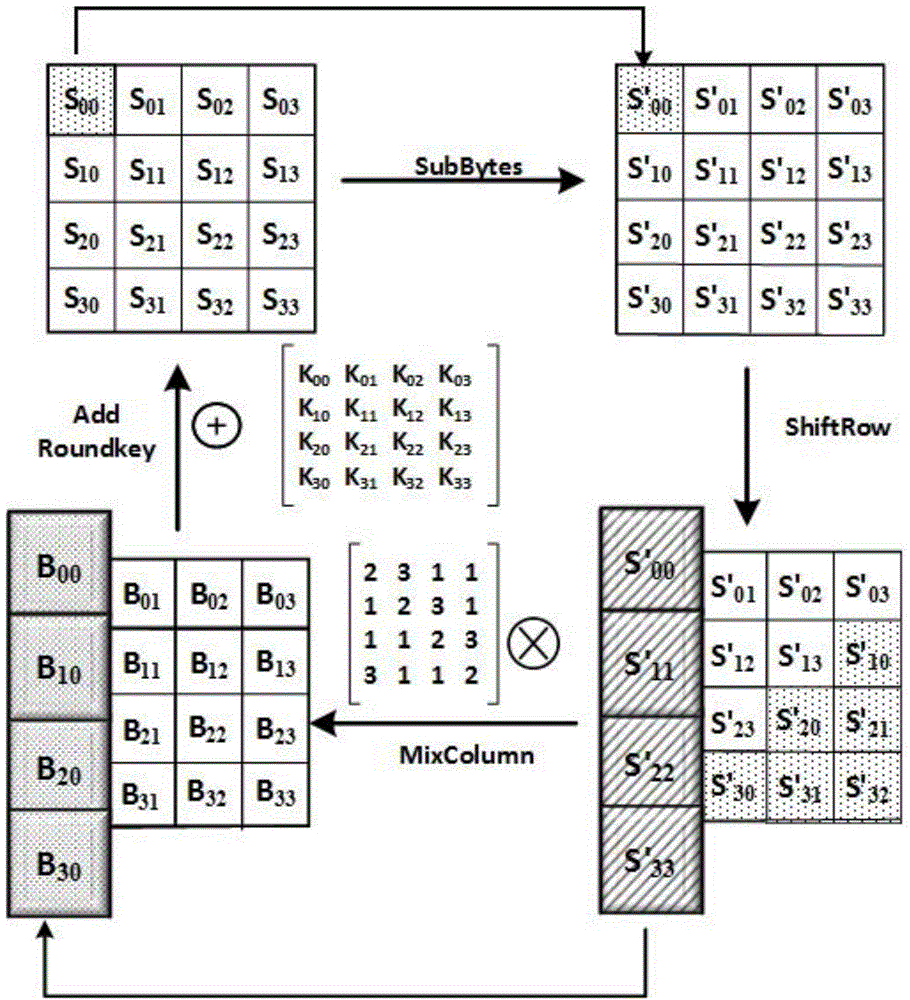
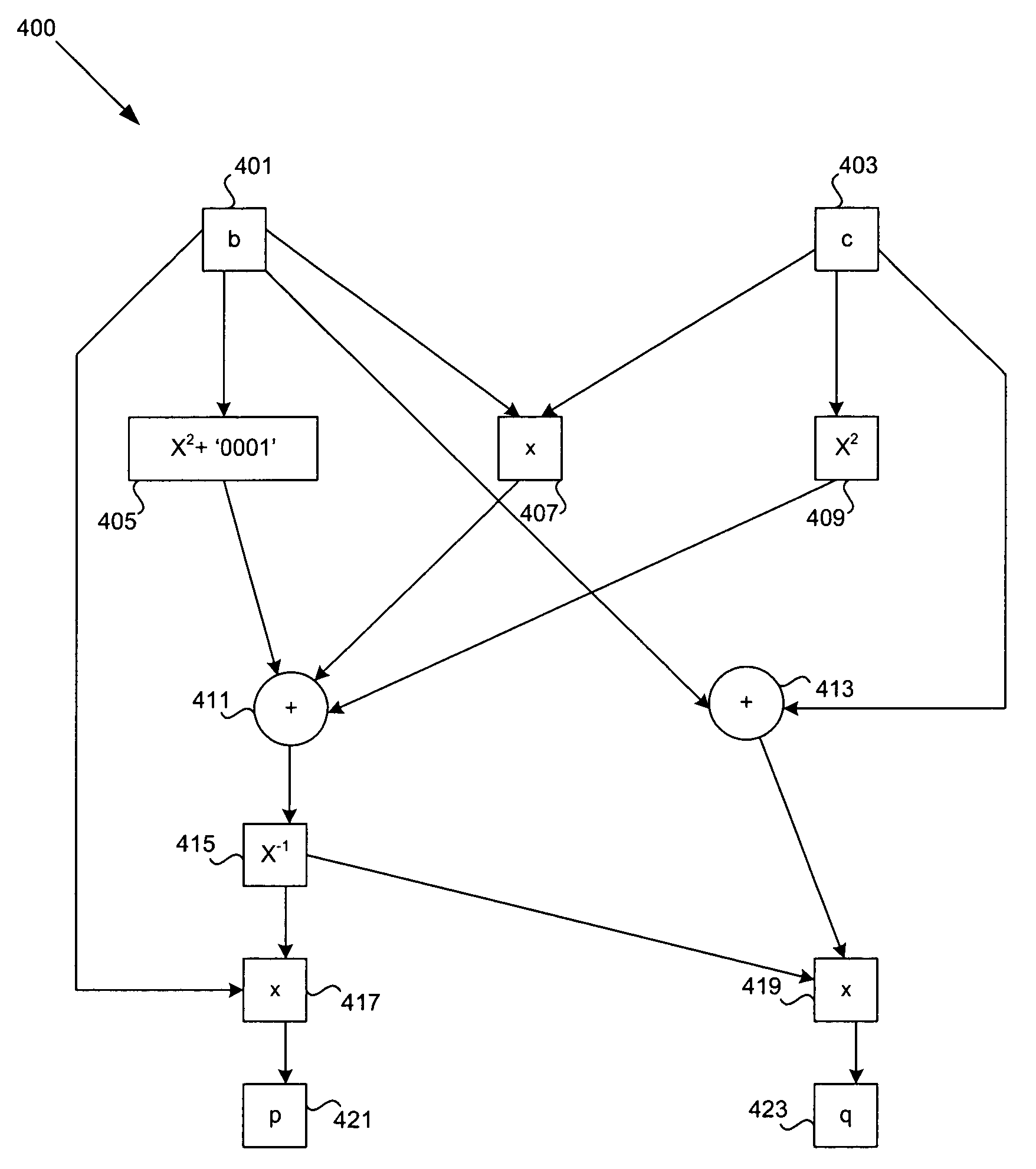
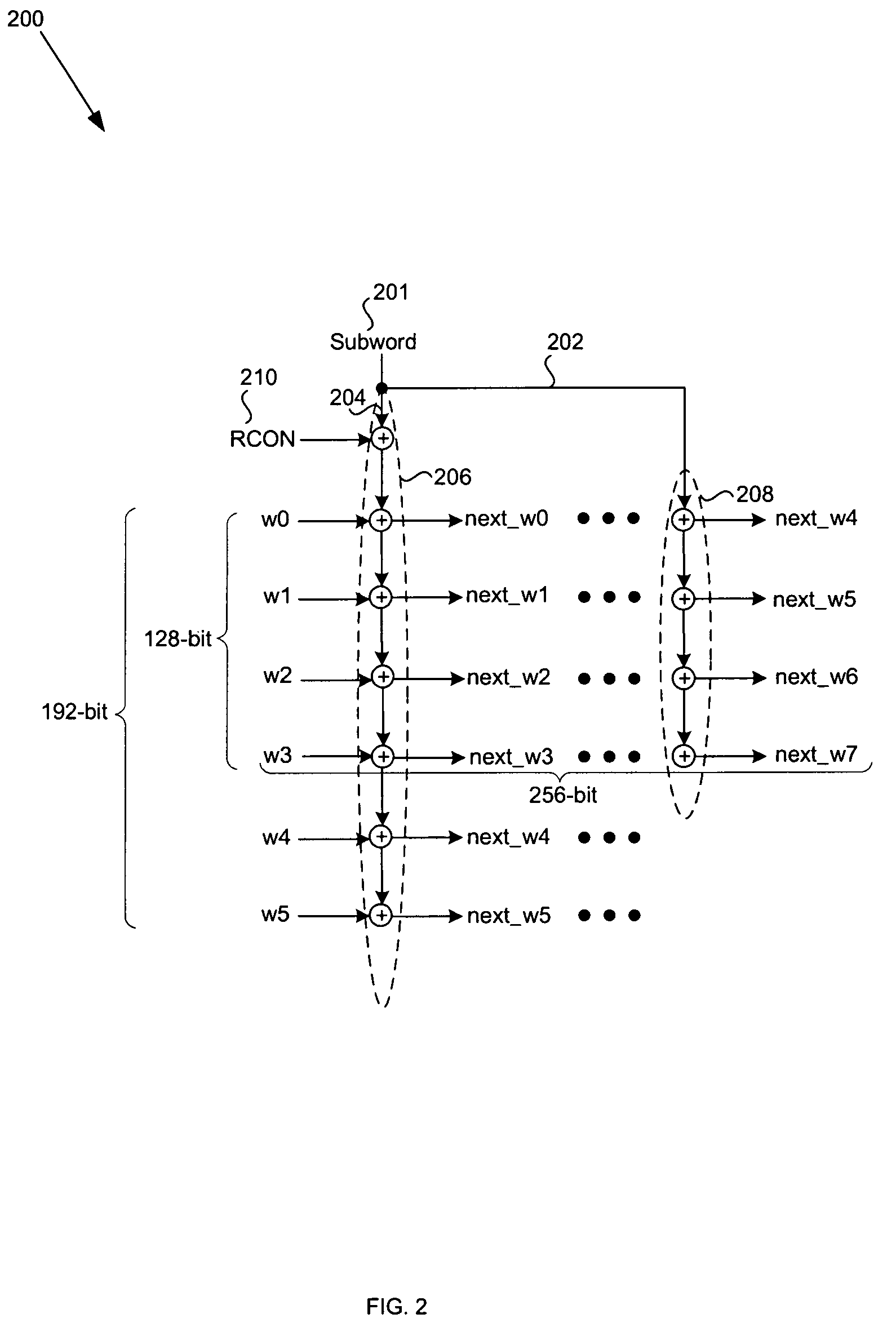
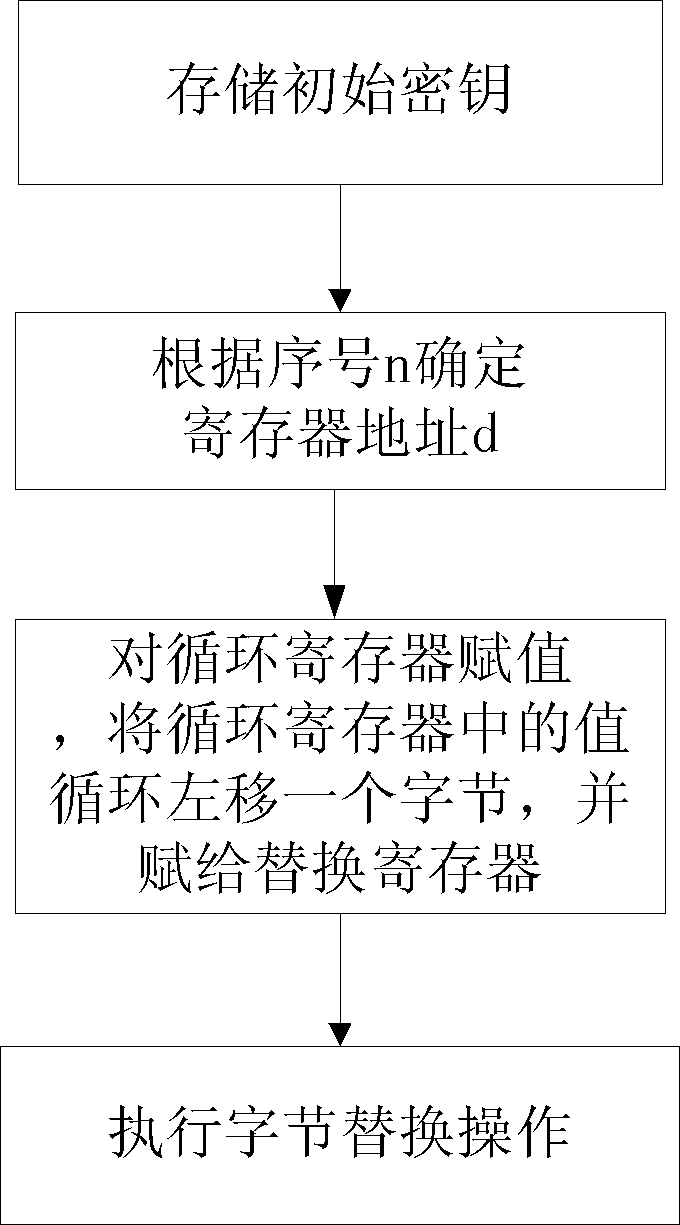
Expansion system and method for 256-bit keys
InactiveCN102647272AImprove scaling efficiencyImprove efficiencyEncryption apparatus with shift registers/memoriesExternal storageProcessor register
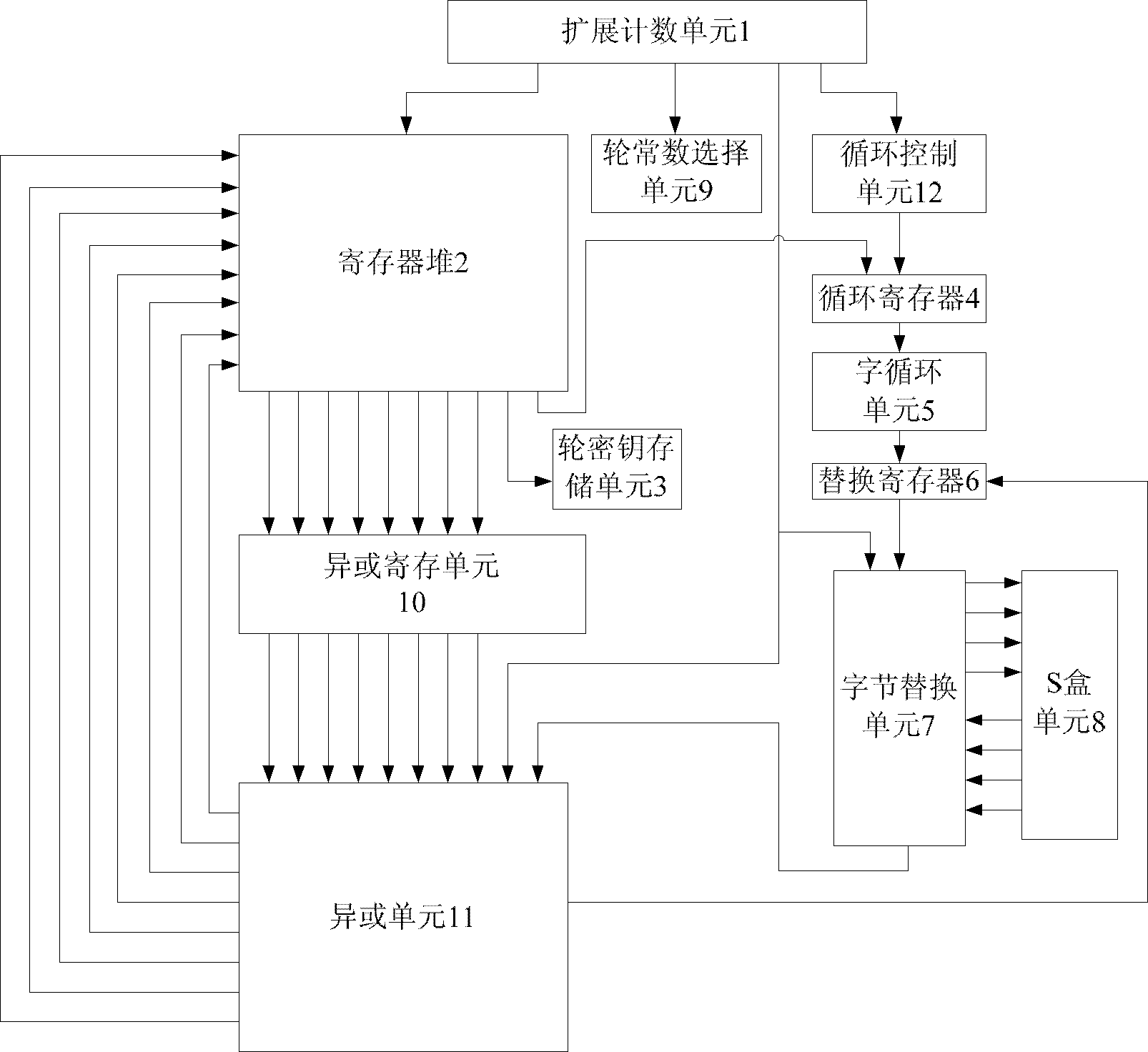
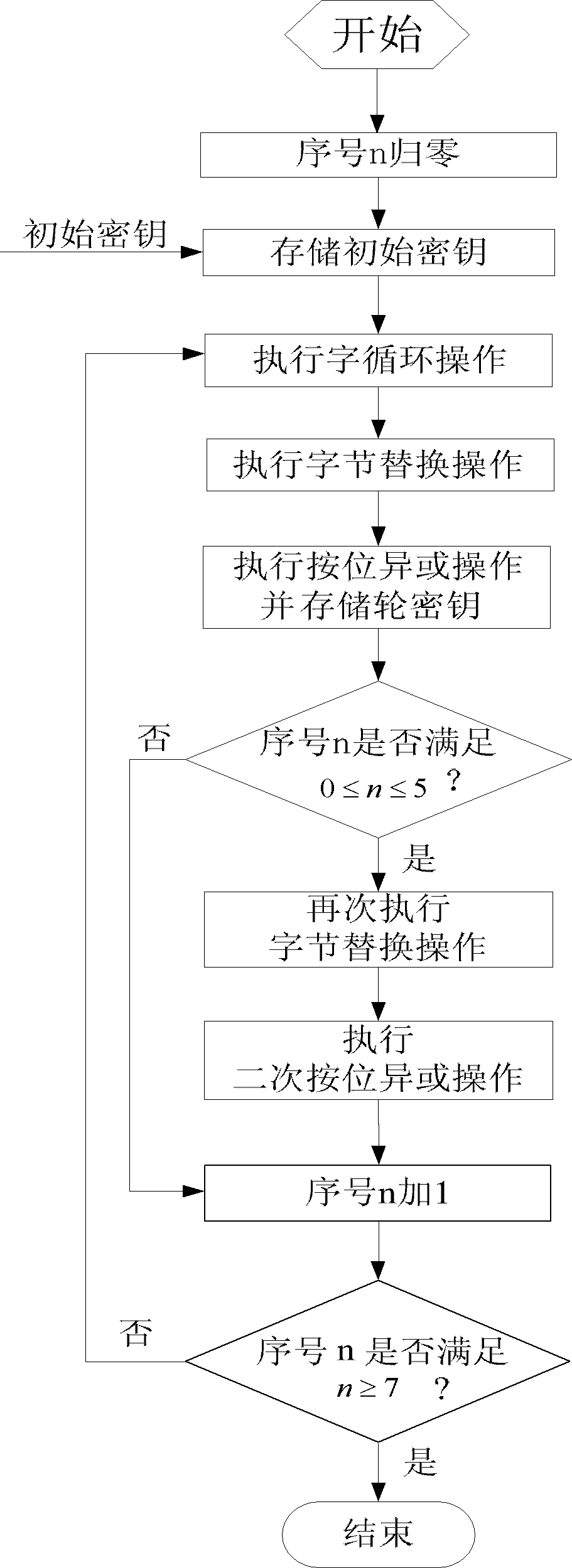
The invention discloses an expansion system and a method for 256-bit keys based on an advanced encryption standard (AES), and mainly solves the problems of low efficiency and high power consumption in a key expansion process in the existing 256-bit AES. The process includes storing an initial key in the first round of key expansion, taking the first four rows as a round key of the key expansion in the first round, and performing word cycle, byte replacement, and bitwise XOR operations; executing a new byte replacement and a secondary bitwise XOR operation according to serial number n; taking results of the two bitwise XOR operations as a round key and storing in a local register and an external storage cell for the usage of encryption process reading; and repeating the operations for round keys obtained in a former round in following rounds until 14 round keys are obtained, and finishing key expansion. According to the expansion system and the method for the 256-bit keys, instantaneity of key expansion and reusability of round keys are achieved simultaneously, key expansion with high efficiency and low power consumption is achieved, and the expansion system and the method are suitable for key expansion processes of the 256-bit AES.
Owner:XIDIAN UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com