Implement method of elliptic curve cipher system coprocessor
A technology of elliptic curve cryptography and coprocessor, which is applied in the field of public key cryptography, can solve problems such as ineffective results, and achieve the effects of convenient initialization, improved work efficiency, and fast processing speed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0058] 1) Reference standard
[0059] The international standards mainly referred to in this implementation method are [ANSI X9.62], [IEEE P1363], [SEC1], [SEC2] and the coprocessor design idea of SUN Company.
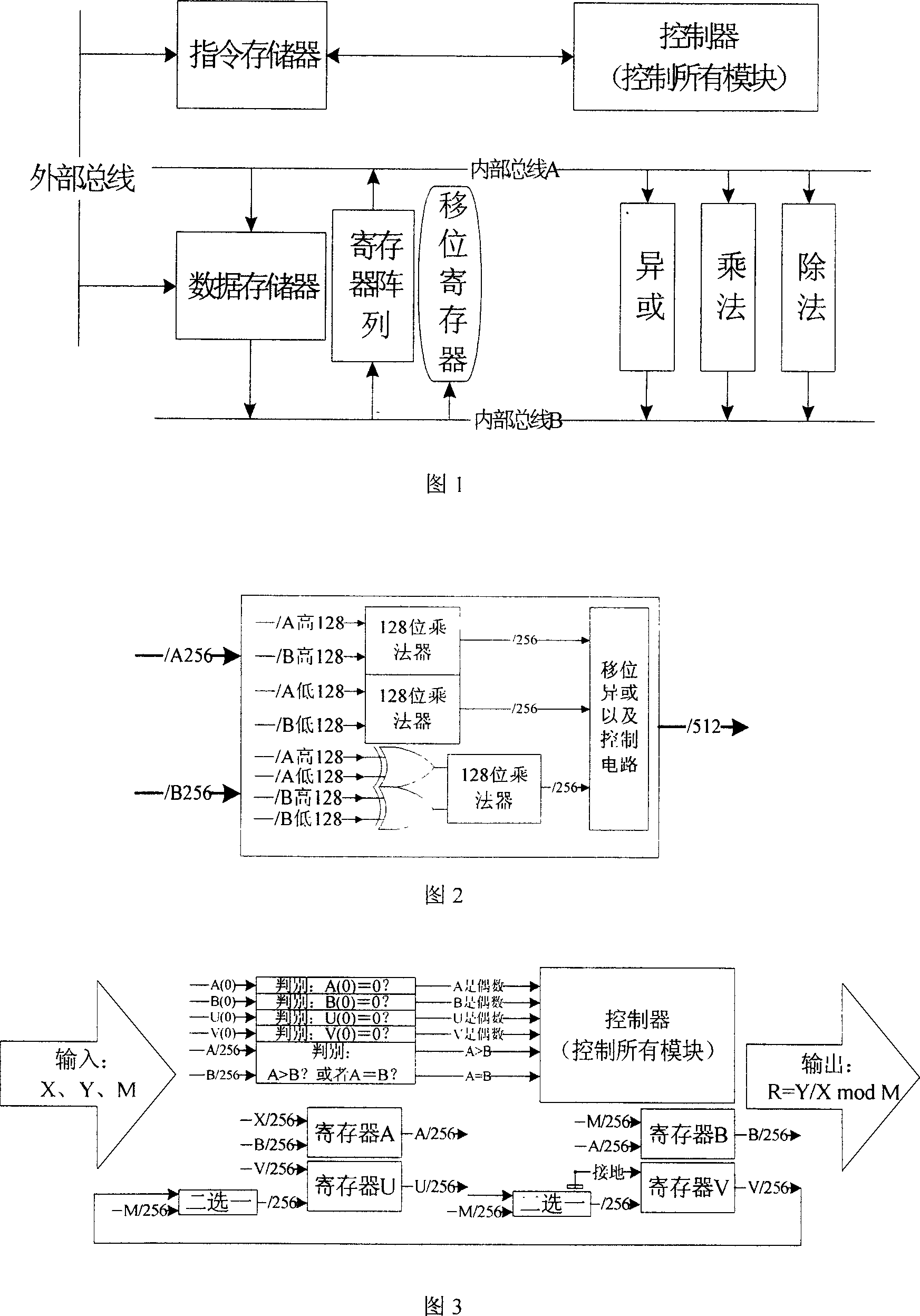
[0060] 2) Hardware structure
[0061] We borrowed the ideas of general computer processors, combined with the operation mode of ECC background domain, designed the ECC coprocessor on the binary domain.
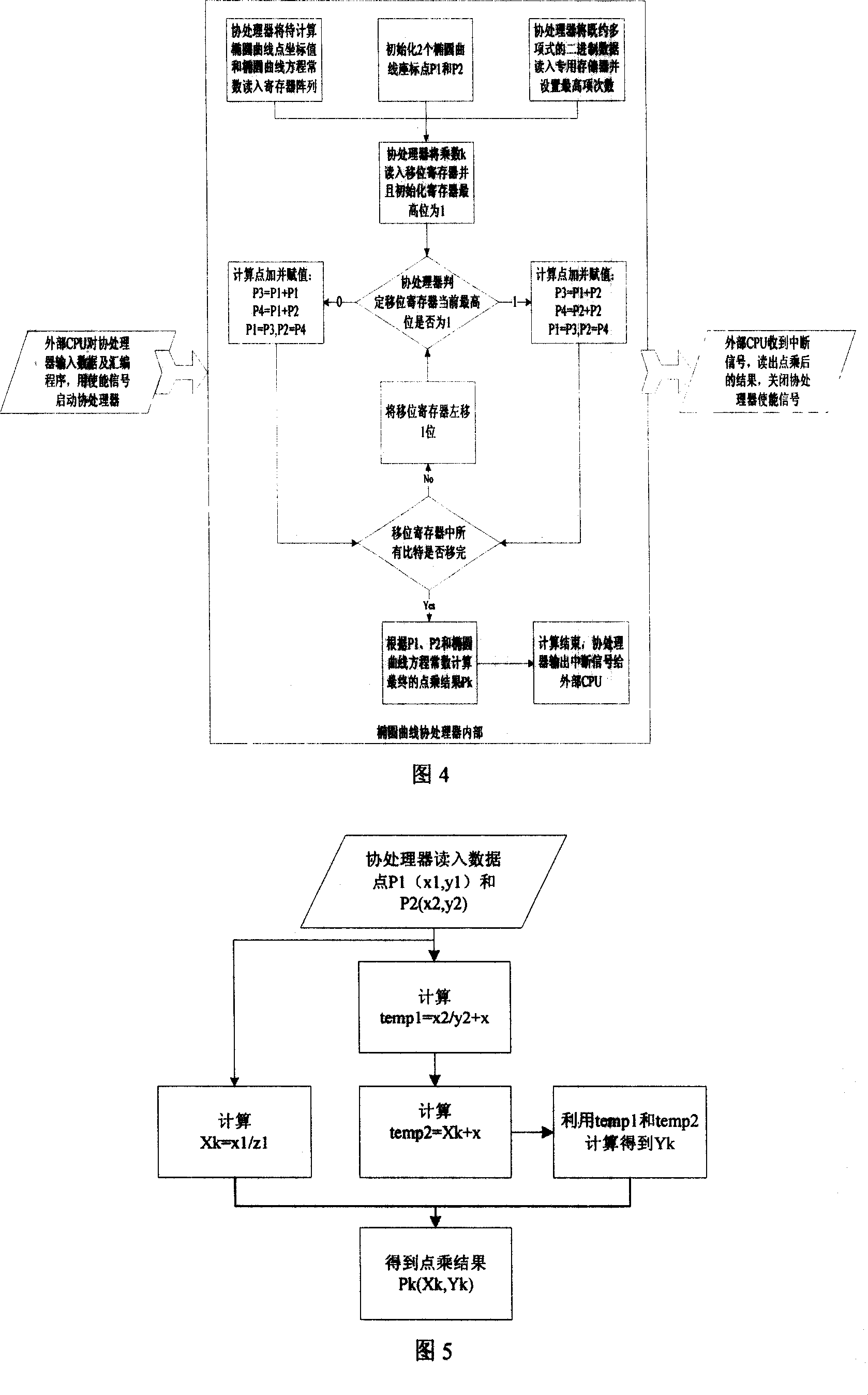
[0062] The coprocessor is composed of two dual-terminal memories, two 256-bit internal buses, 16 256 registers, a shift register, a controller, and a binary domain bottom operation module; among them, the binary field bottom operation module is an exclusive OR module , multiplication module and division module. The core module of the ECC coprocessor is the controller part, which is responsible for reading instructions from the instruction memory and parsing instructions, and then reading, processing, storing and jumping instructions according to the instructions. ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com