Device compatible with three SHA standards and realization method thereof
An implementation method and technology of SHA-512, applied in the field of comprehensive design, can solve the problems of increasing the cost of replacing equipment, hidden dangers of TPM chip security, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
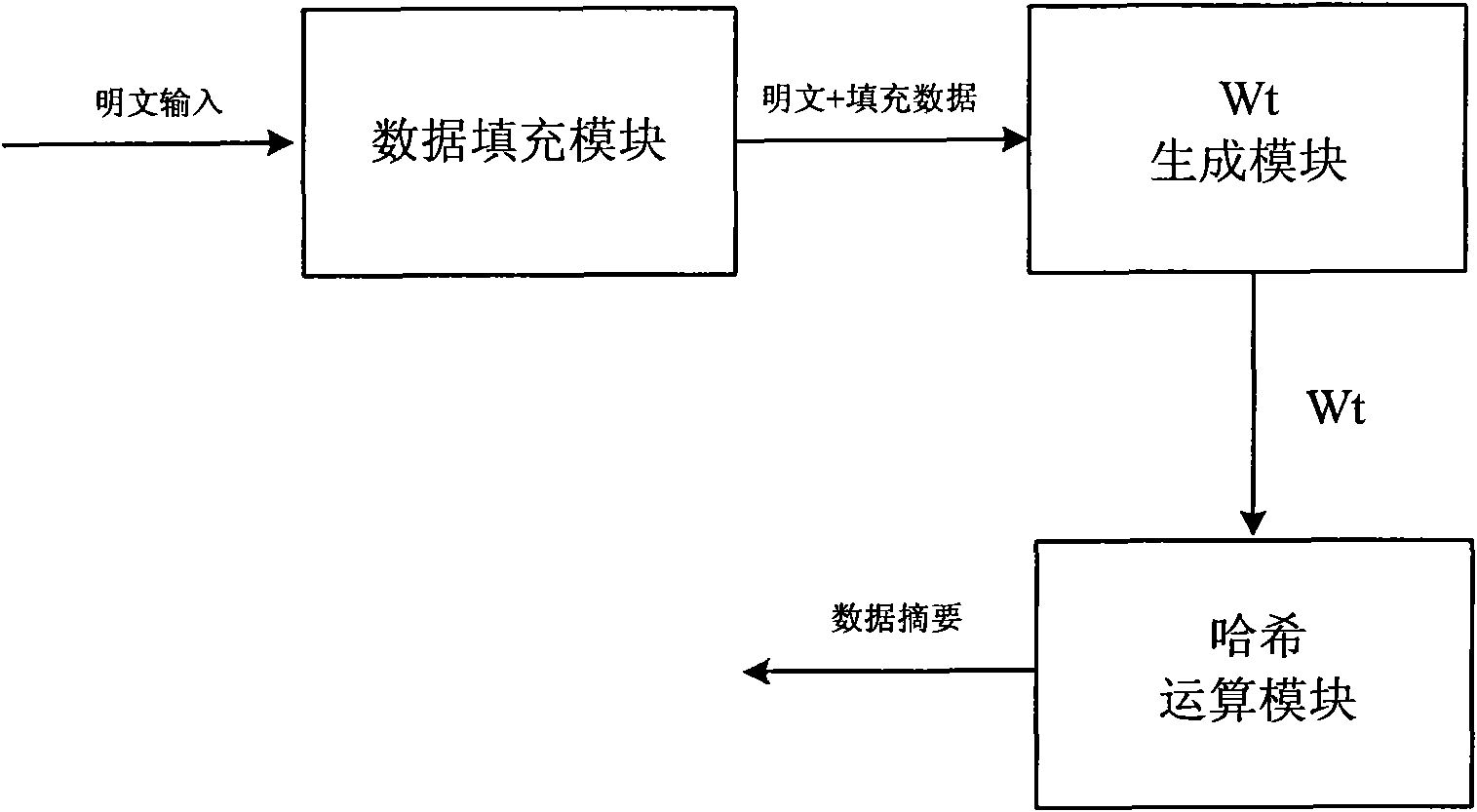
[0095] like figure 1 As shown, a device compatible with three SHA standards mainly includes a sequentially connected data filling module, Wt generation module and hash operation module.
[0096] The data filling module is used to receive plaintext data and generate filling data, and write the filling data of plaintext data to the Wt generation module;
[0097] The Wt generation module is used to receive the data output by the data filling module, connect each operand through exclusive OR operation in SHA-1 mode, and perform arithmetic addition operation on each operand in SHA-256 and SHA-512 mode Connect, generate a new Wt operator and input it to the hash operation module;
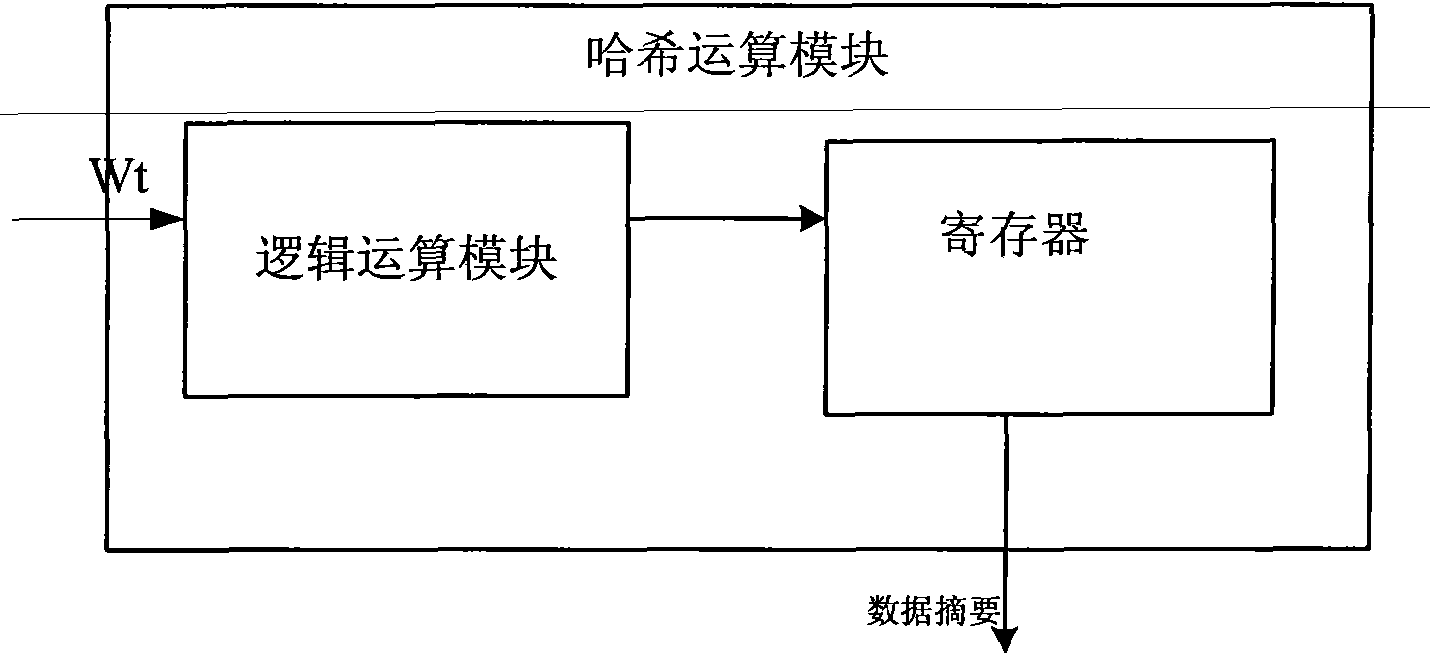
[0098] The hash operation module is used to receive the Wt operator of the Wt generation module, perform hash operation, and generate a 160-bit, 256-bit or 512-bit data summary.
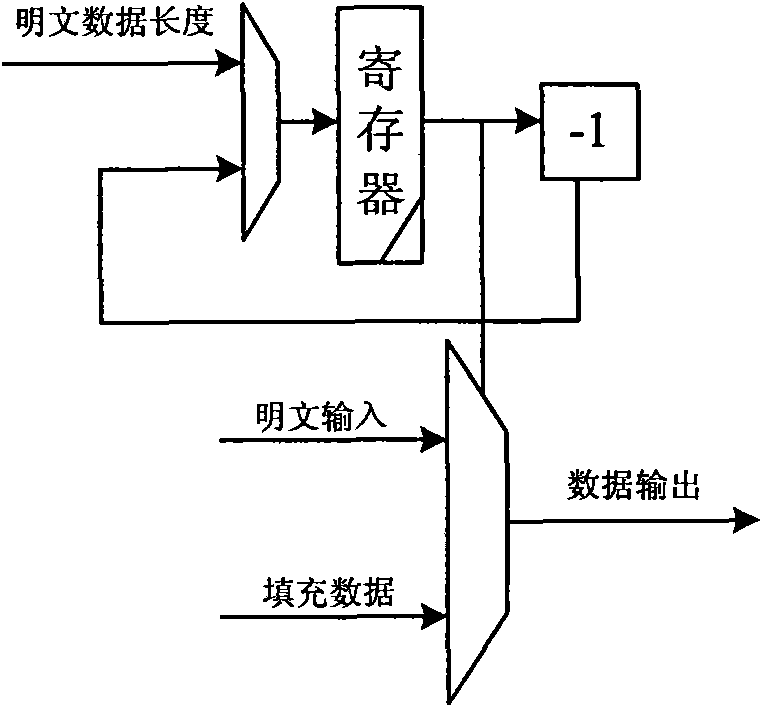
[0099] like figure 2 As shown, the data filling module mainly includes a register, a subtractor and a multiplexer;
[010...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com