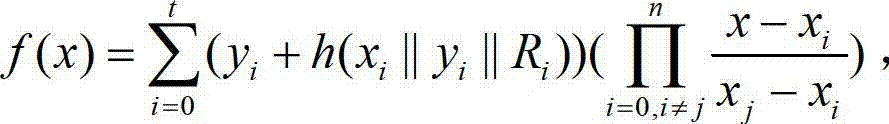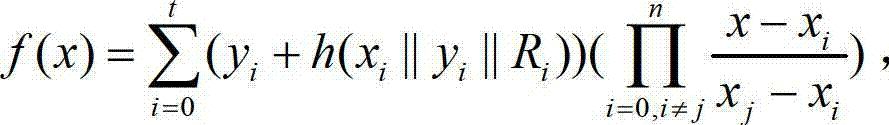Patents
Literature
36 results about "512-bit" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In computer architecture, 512-bit integers, memory addresses, or other data units are those that are 512 bits wide. Also, 512-bit CPU and ALU architectures are those that are based on registers, address buses, or data buses of that size.
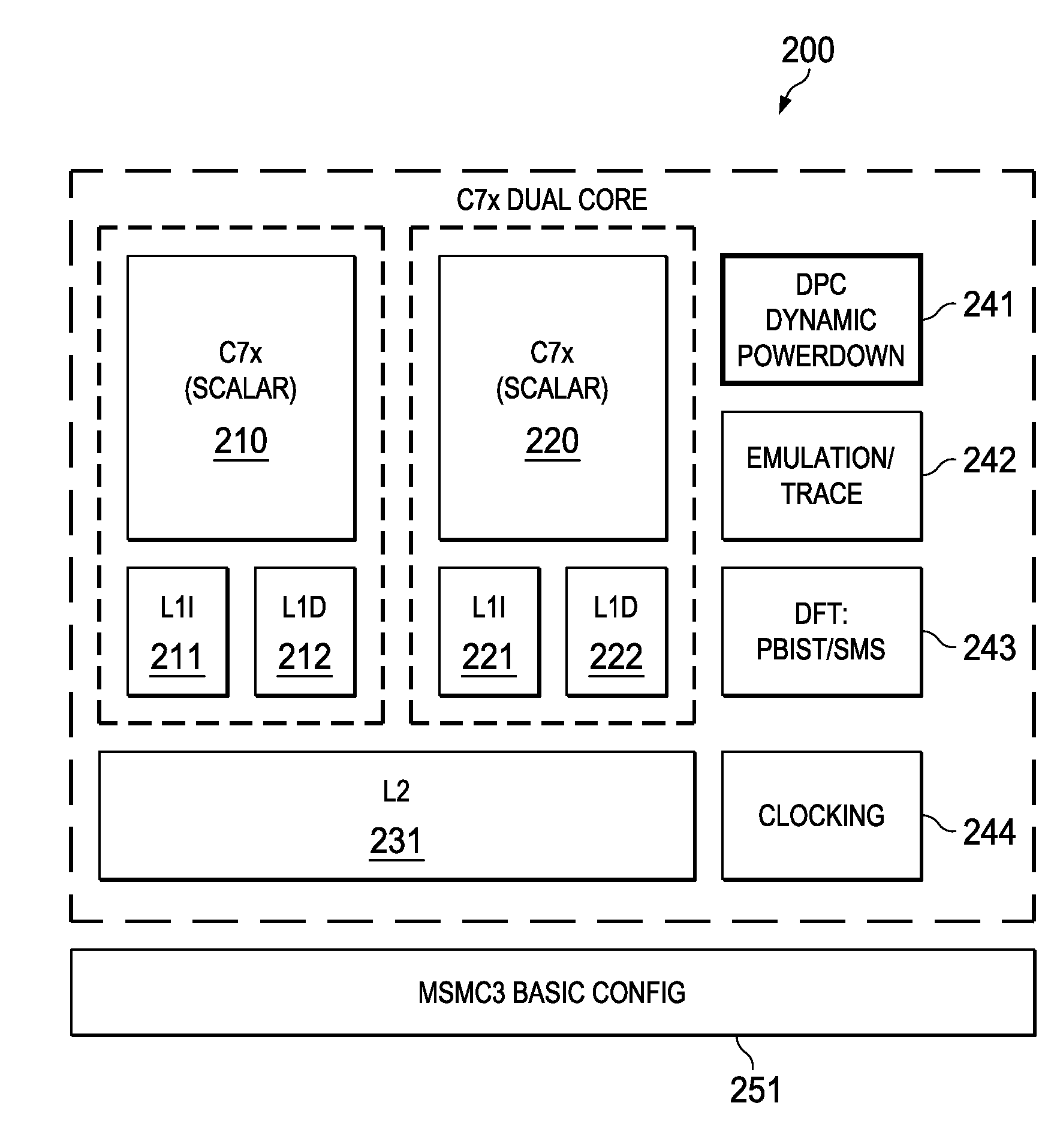
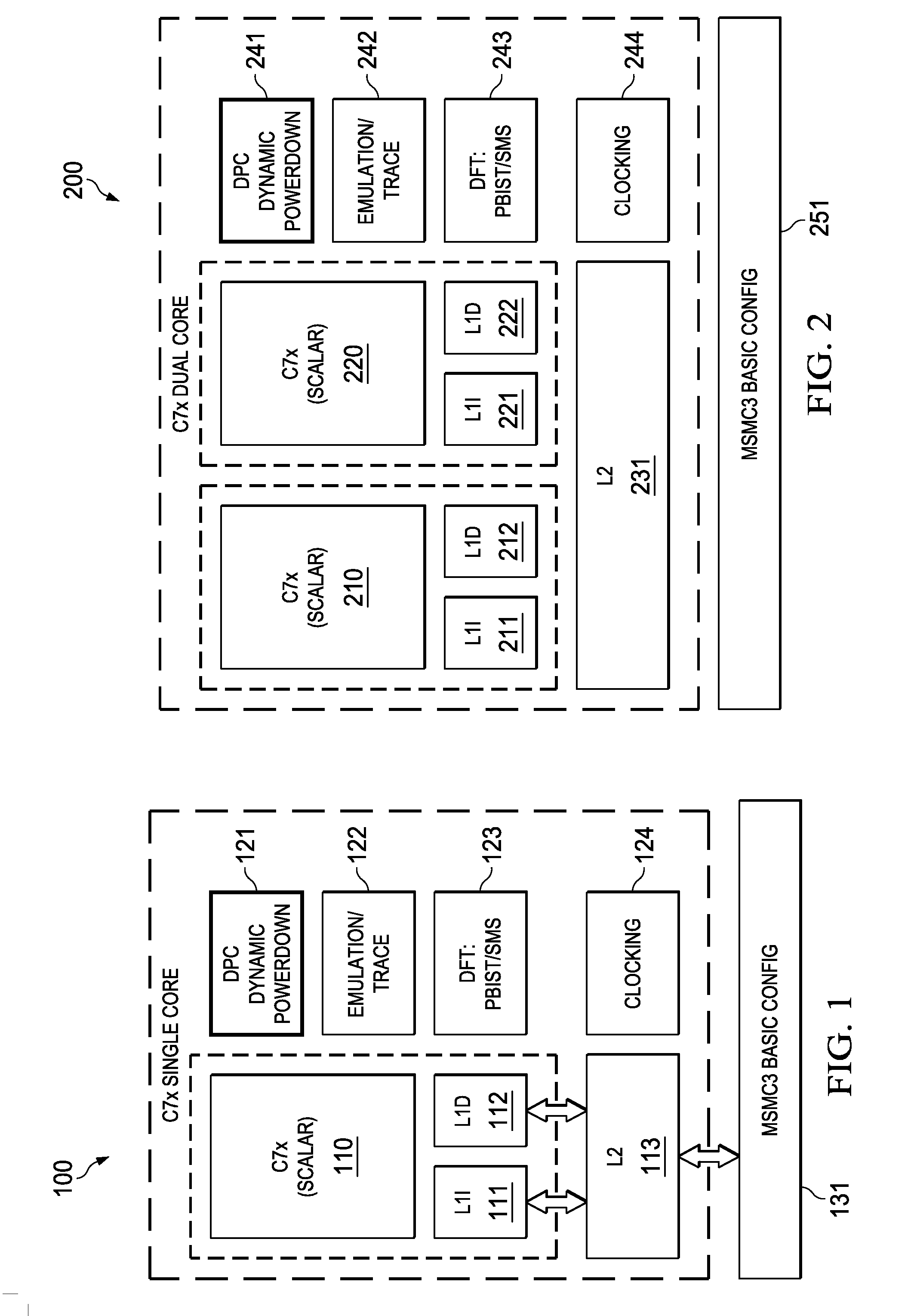
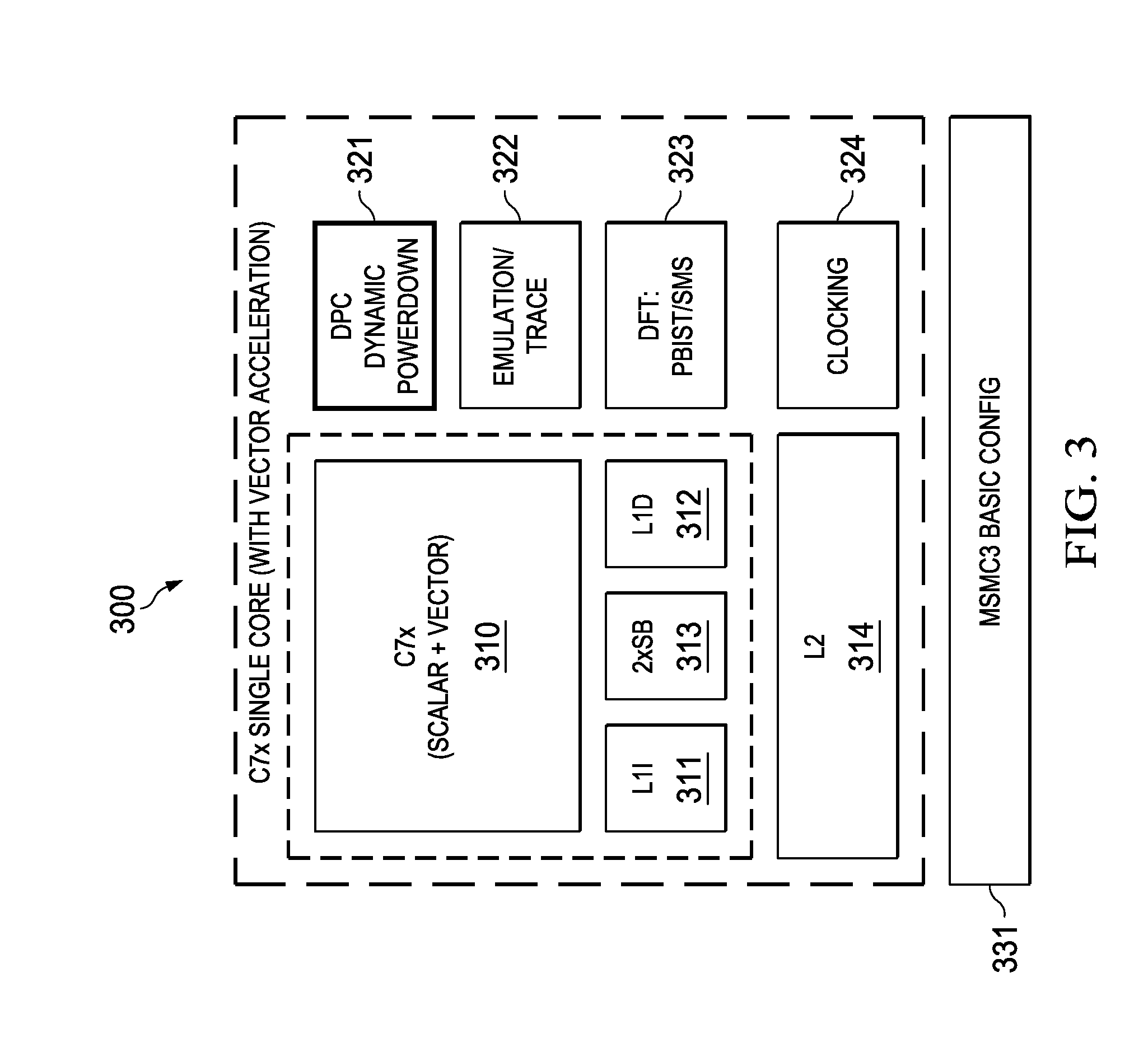
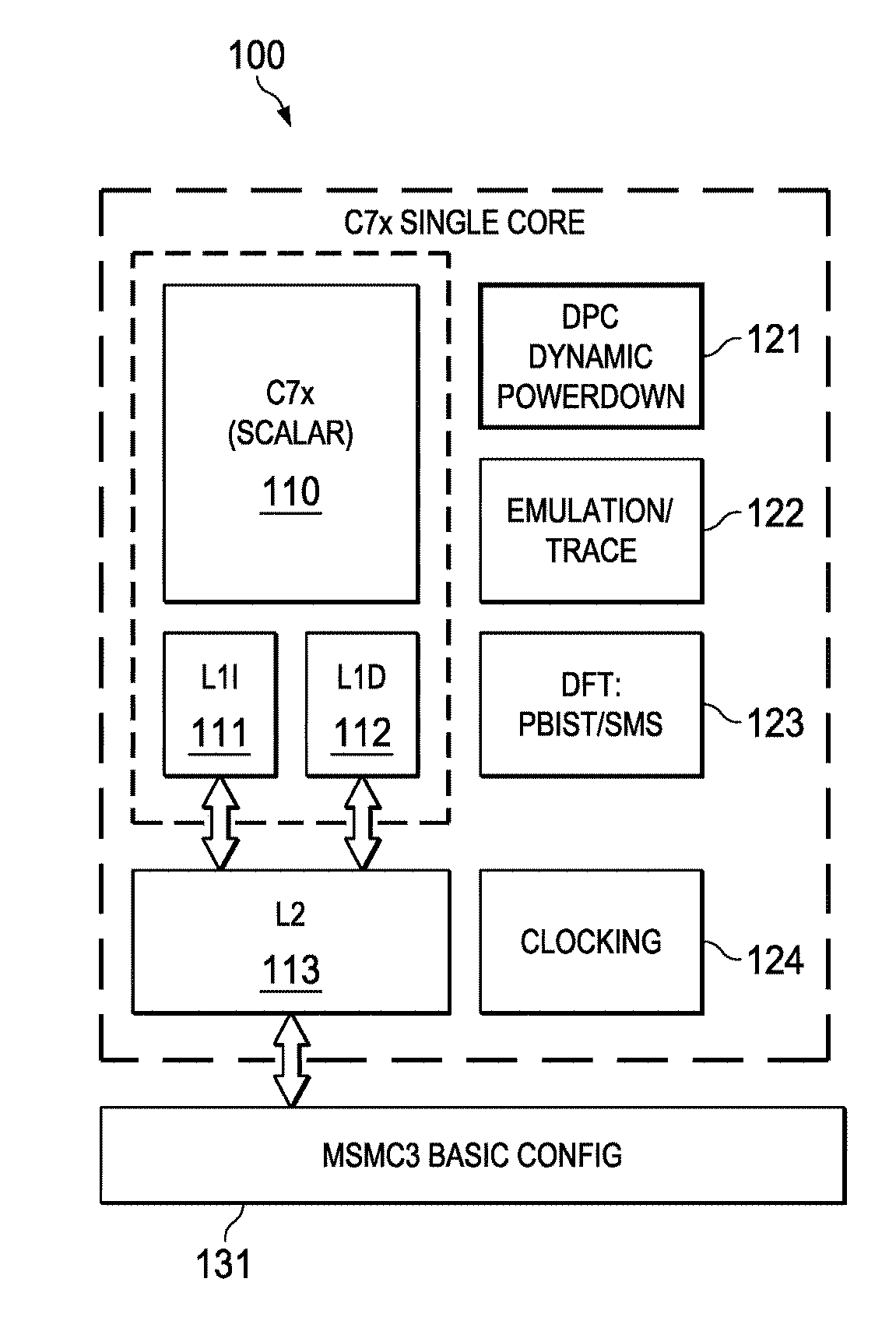
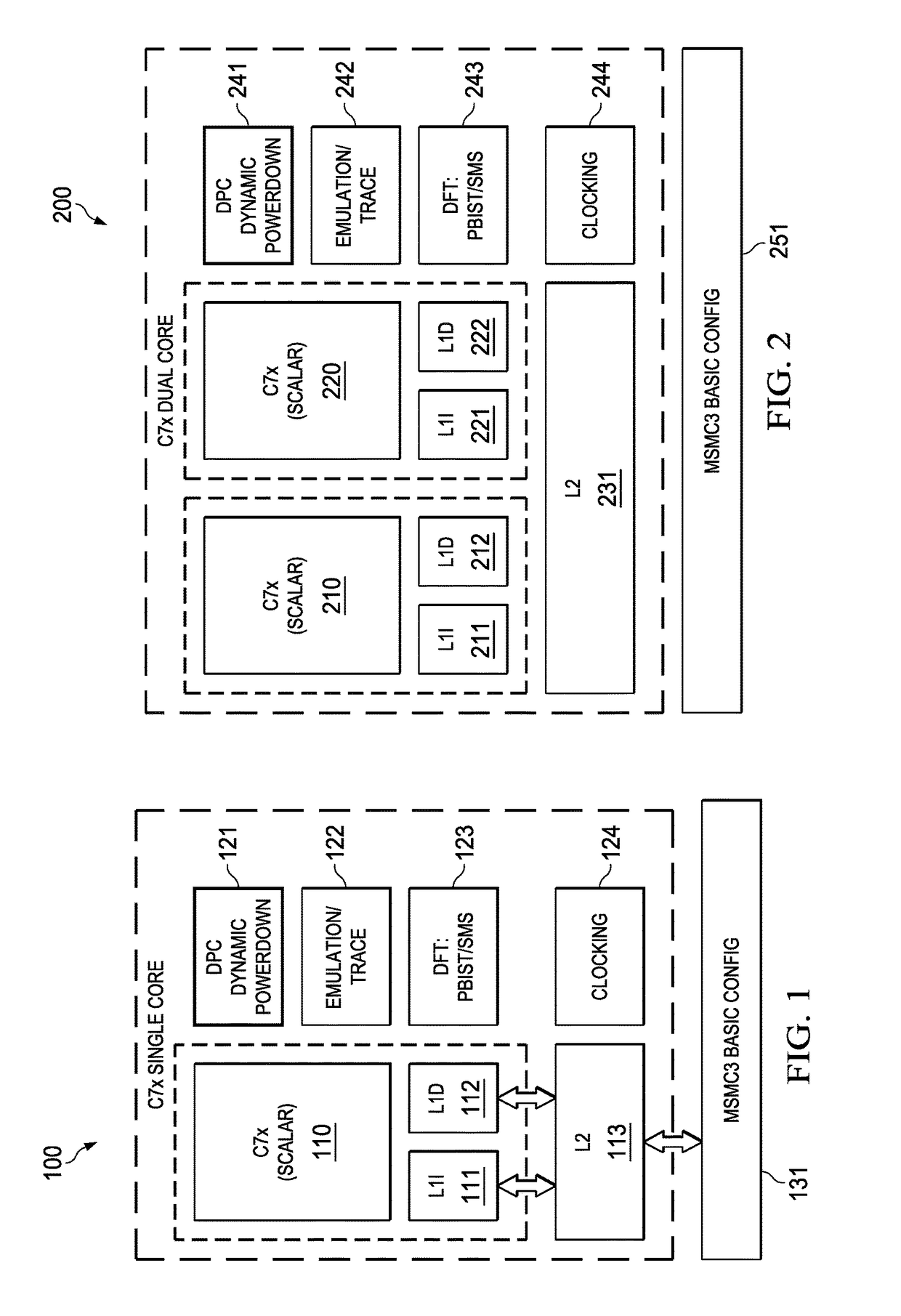
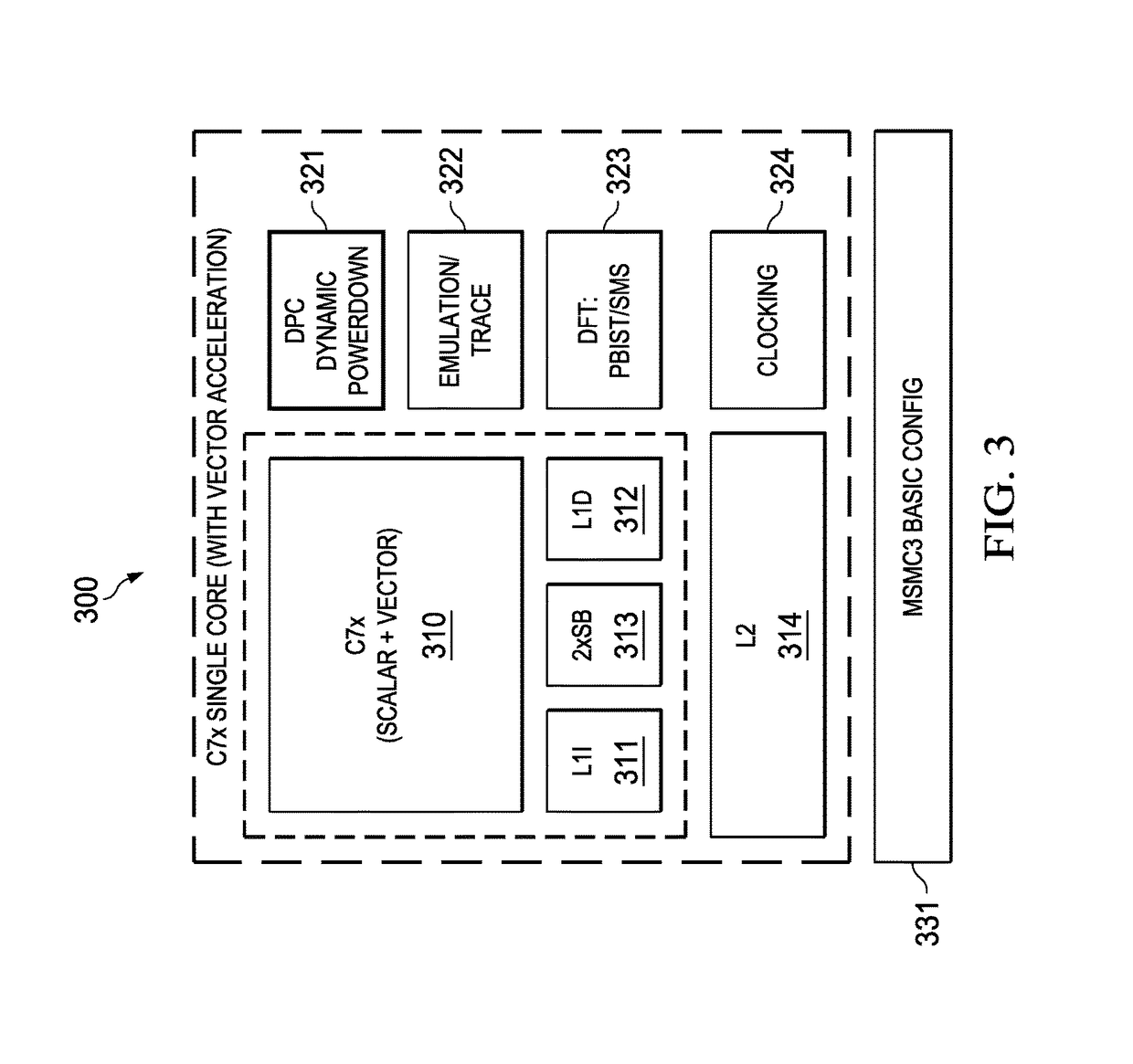
Highly Integrated Scalable, Flexible DSP Megamodule Architecture
ActiveUS20150019840A1High compute to bandwidth ratioExcessive latencyMemory architecture accessing/allocationProgram initiation/switchingSemi automaticData error
This invention addresses implements a range of interesting technologies into a single block. Each DSP CPU has a streaming engine. The streaming engines include: a SE to L2 interface that can request 512 bits / cycle from L2; a loose binding between SE and L2 interface, to allow a single stream to peak at 1024 bits / cycle; one-way coherence where the SE sees all earlier writes cached in system, but not writes that occur after stream opens; full protection against single-bit data errors within its internal storage via single-bit parity with semi-automatic restart on parity error.
Owner:TEXAS INSTR INC
Highly integrated scalable, flexible DSP megamodule architecture
ActiveUS9606803B2Excessive latencyImprove bus utilizationProgram initiation/switchingComputation using non-contact making devicesInternal memorySemi automatic
This invention addresses implements a range of interesting technologies into a single block. Each DSP CPU has a streaming engine. The streaming engines include: a SE to L2 interface that can request 512 bits / cycle from L2; a loose binding between SE and L2 interface, to allow a single stream to peak at 1024 bits / cycle; one-way coherence where the SE sees all earlier writes cached in system, but not writes that occur after stream opens; full protection against single-bit data errors within its internal storage via single-bit parity with semi-automatic restart on parity error.
Owner:TEXAS INSTR INC
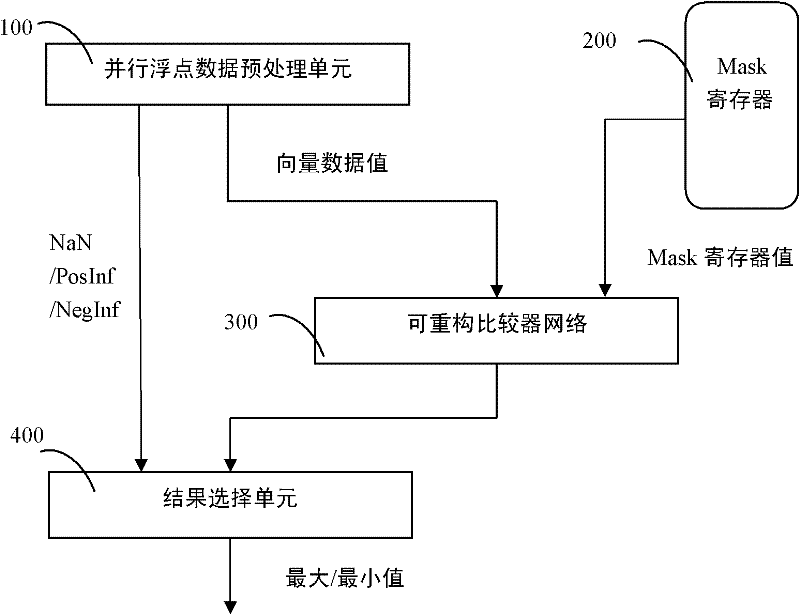
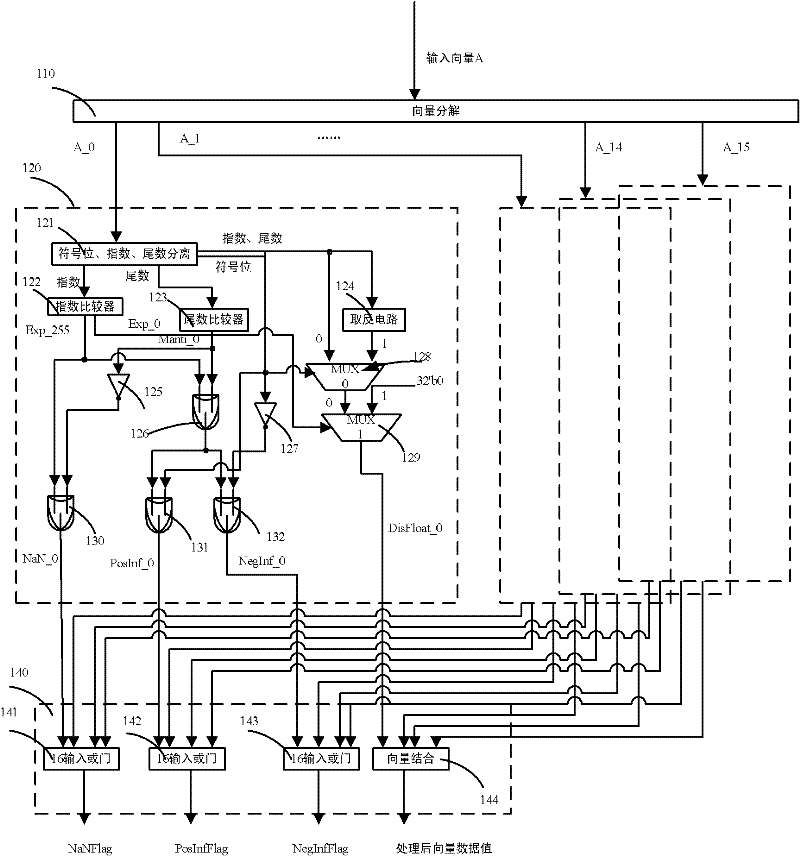
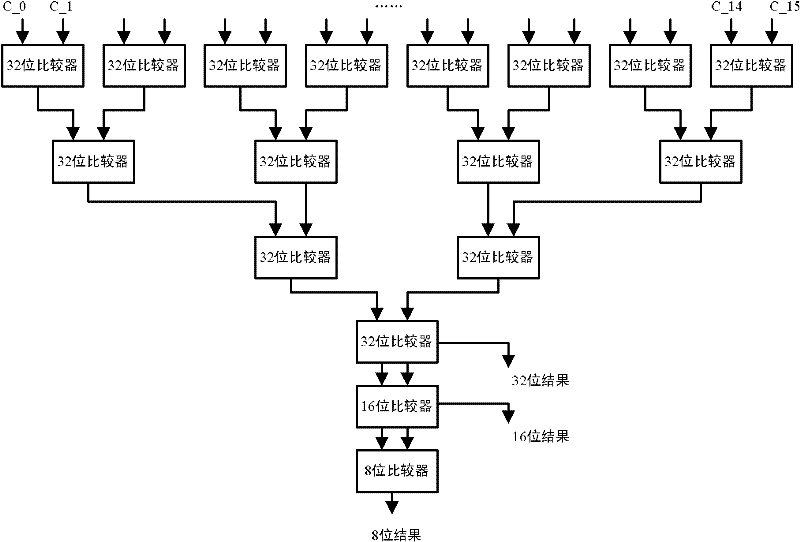
Length-configurable vector maximum/minimum network supporting reconfigurable fixed floating points
ActiveCN102520903AFast executionSimplify programming complexityComparison of digital valuesFloating pointEuclidean vector
The invention discloses a length-configurable vector maximum / minimum network supporting reconfigurable fixed floating points, which comprises a parallel floating point data preprocessing unit, a Mask register, a reconfigurable comparator network and a result selecting unit. The parallel floating point data preprocessing unit is used for analyzing formats of received 512 bit vector data, respectively processing the data according to different data formats, outputting floating point data obtained after processing to the reconfigurable comparator network and outputting various zone bits obtained after processing to the result selecting unit. The Mask register is used for controlling data involved in maximum / minimum. The reconfigurable comparator network is used for inputting the floating point data received from the parallel floating point data preprocessing unit and values received from the Mask register, sequentially comparing the vector data and outputting obtained maximum / minimum results to the result selecting unit. The result selecting unit is used for receiving output of the reconfigurable comparator network and obtaining the final vector maximum / minimum results according to output of the various zone bits received from the parallel floating point data preprocessing unit.
Owner:BEIJING SMART LOGIC TECH CO LTD
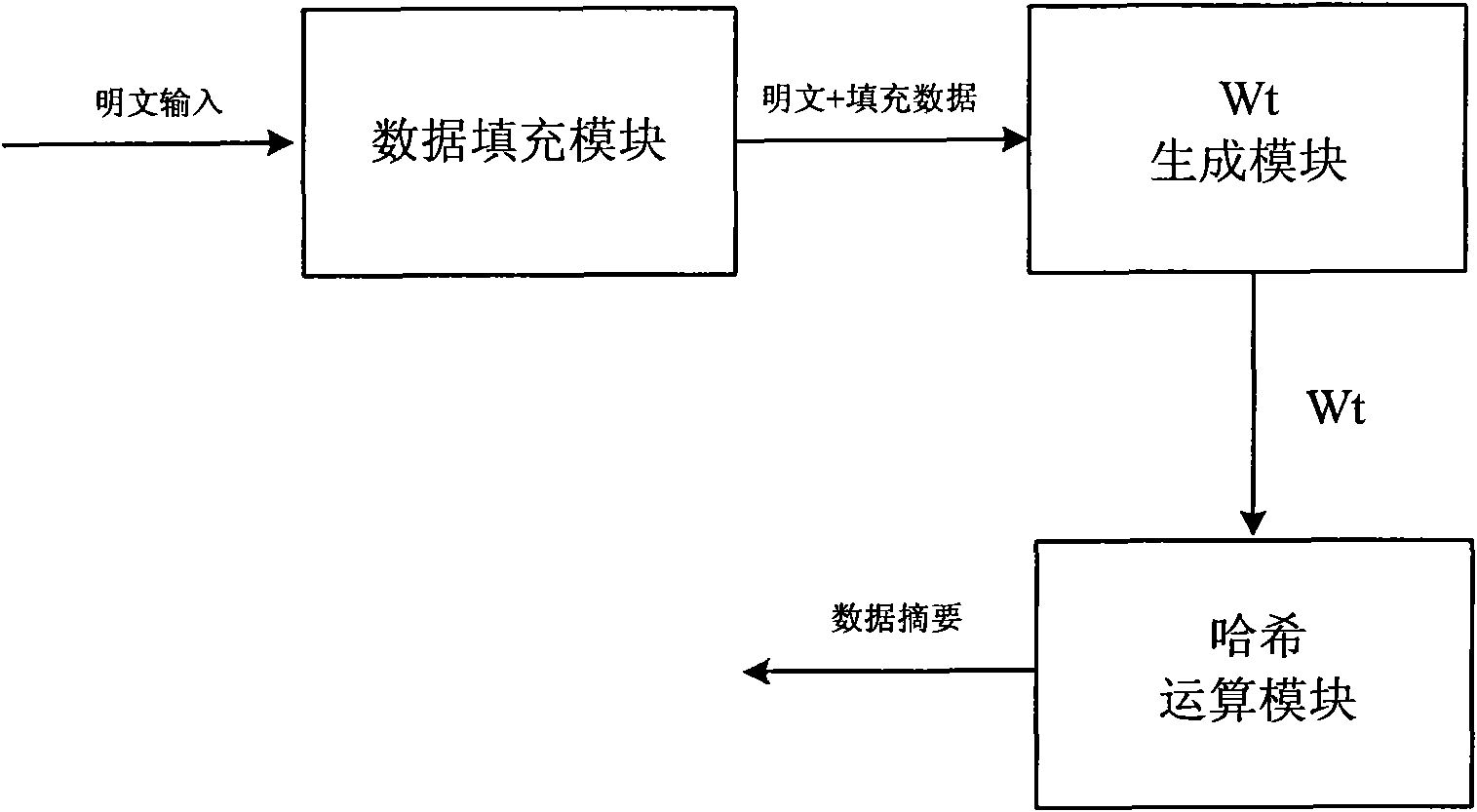
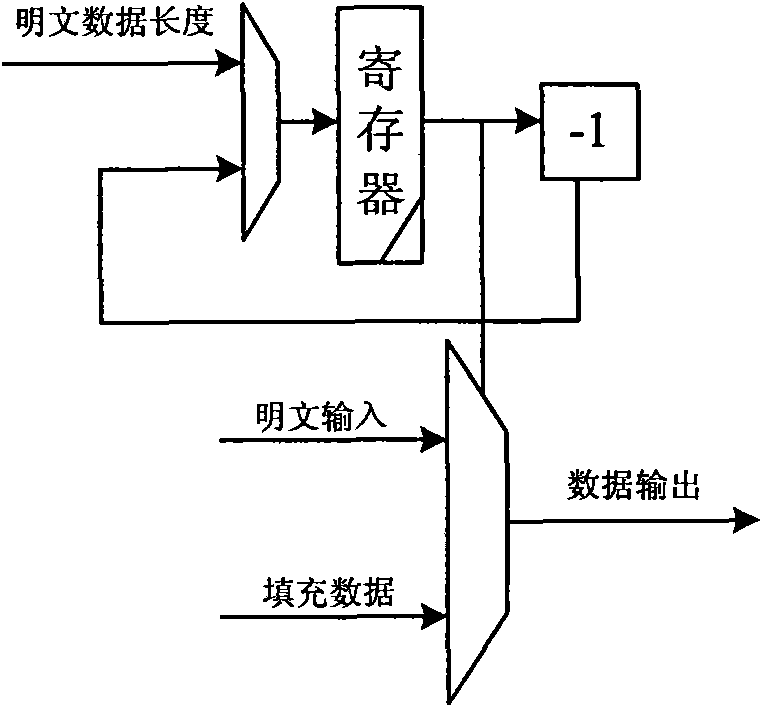
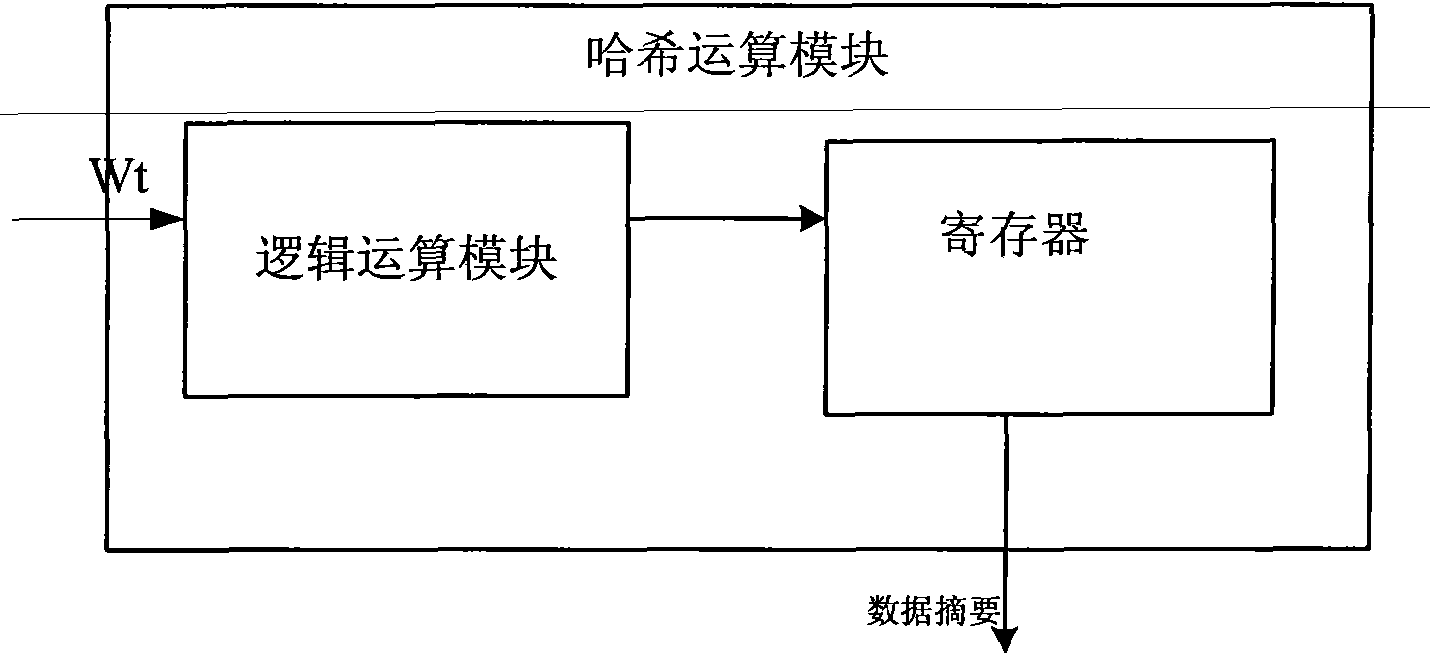
Device compatible with three SHA standards and realization method thereof
InactiveCN101894229AImprove compatibilityReduce consumptionInternal/peripheral component protectionComputer compatibilityData filling
The invention discloses a device compatible with three SHA standards, which comprises a data filling module, a Wt generation module and an Hash operation module, which are connected in order. The invention also discloses a realization method of the device compatible with three SHA standards, which comprises the following steps: (I) receiving cleartext data by the data filling module to generate filling data and outputting the data to the Wt generation module; (II) generating new Wt operators by the Wt generation module and inputting the new Wt operators into the Hash operation module; and (III) generating a data abstract with 160 bits under an SHA-a mode, generating a data abstract with 256 bits under SHA-256 mode or generating a data abstract with 512 bits under an SHA-512 mode by the Hash operation module. The invention has the advantages of common practicality, good compatibility, low power consumption, less occupation of extra resources and the like.
Owner:SOUTH CHINA UNIV OF TECH
Modified SHA-1 hash algorithm
InactiveCN101872338AImprove efficiencyImprove securityTransmissionComplex mathematical operationsMessage processingMessage passing
The invention relates to a modified SHA-1 hash algorithm. The existing SHA-1 harsh algorithm has low security. The invention firstly adds a 1, a plurality of 0 and a 64-bit binary string after the information to be processed, then enlarges and groups the information, so the original 512-bit group is changed into a 1024-bit group and a register value is initialized; then a main cycle is utilized to sequentially process each group, the main cycle totally has four operations, and each operation contains logical function and compression function processing; and finally, after the processing of all the groups is completed, 160-bit message digest is output, and when the message digest is transferred, the message to be transferred is added with a safety hashed value. Through the algorithm of the invention, the original SHA-1 algorithm has more safety on message processing, and through modifying the logical function expression and the compression function logical structure of the algorithm, the efficiency of the SHA-1 algorithm is improved.
Owner:HANGZHOU DIANZI UNIV
Hardware optimization method based on SM3 password hash algorithm
InactiveCN107579811AReduce in quantityImprove computing efficiencyEncryption apparatus with shift registers/memoriesPasswordIntermediate variable
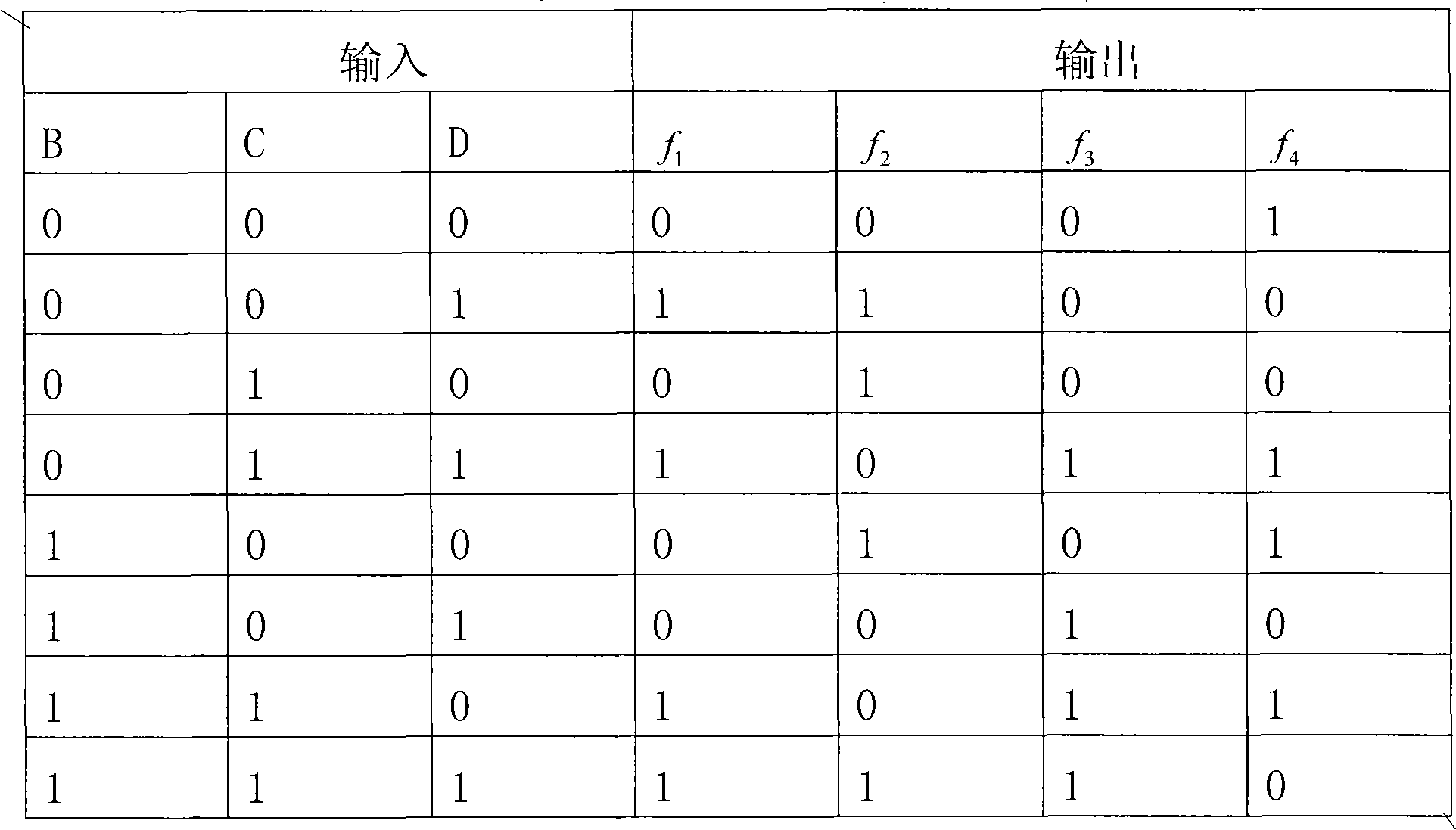
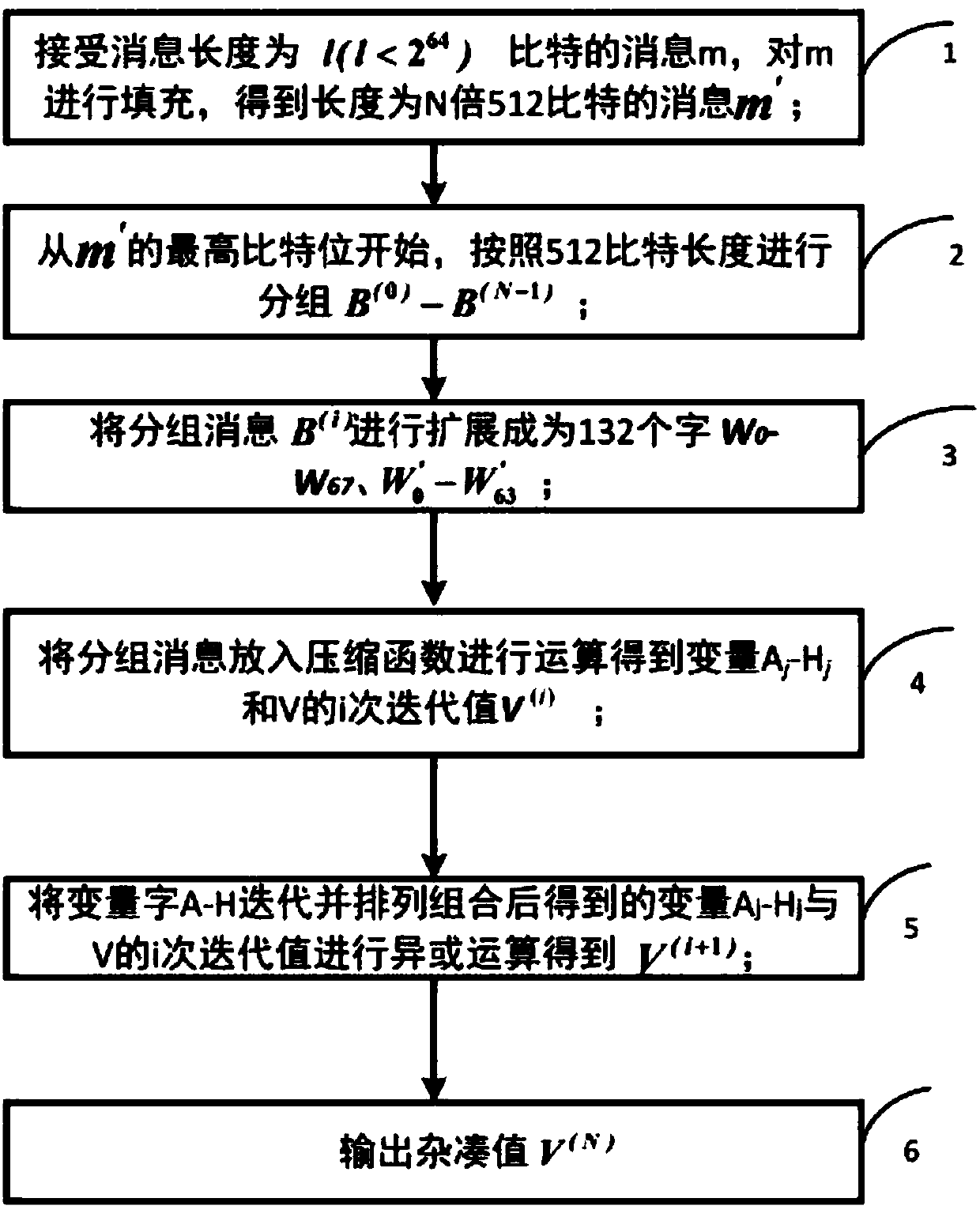
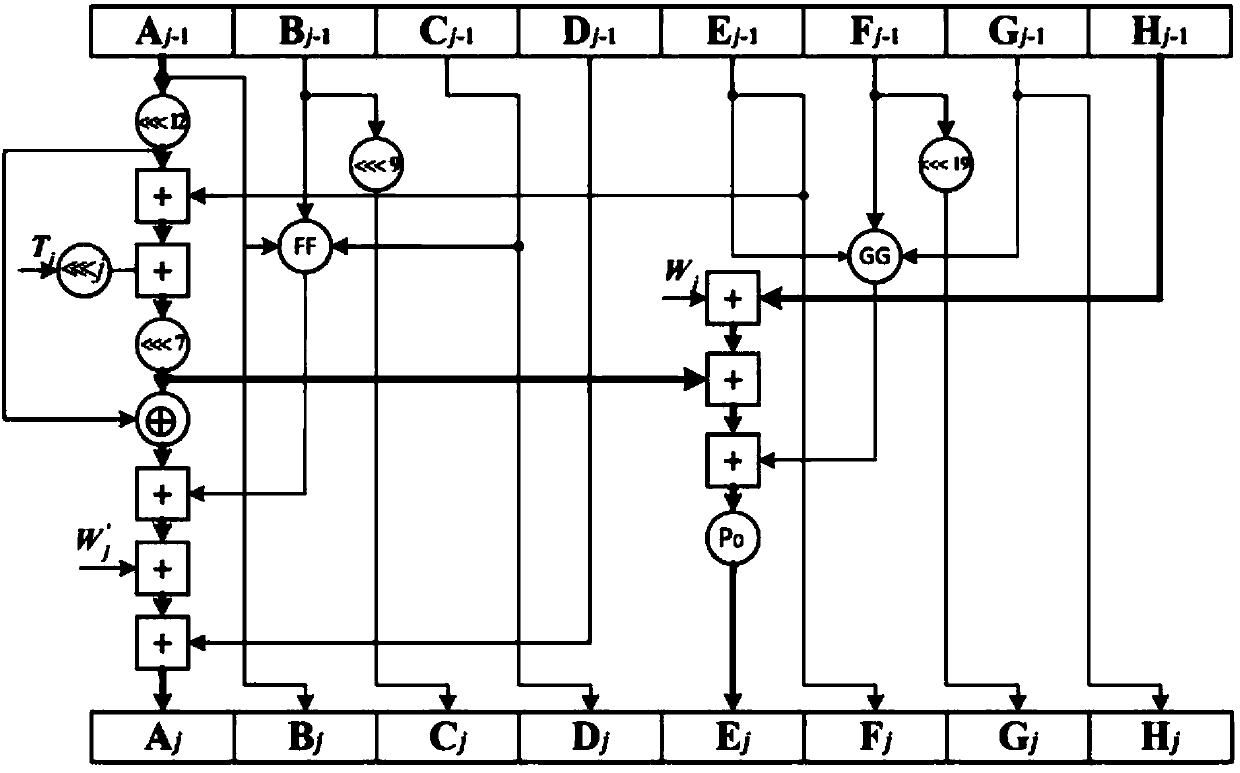
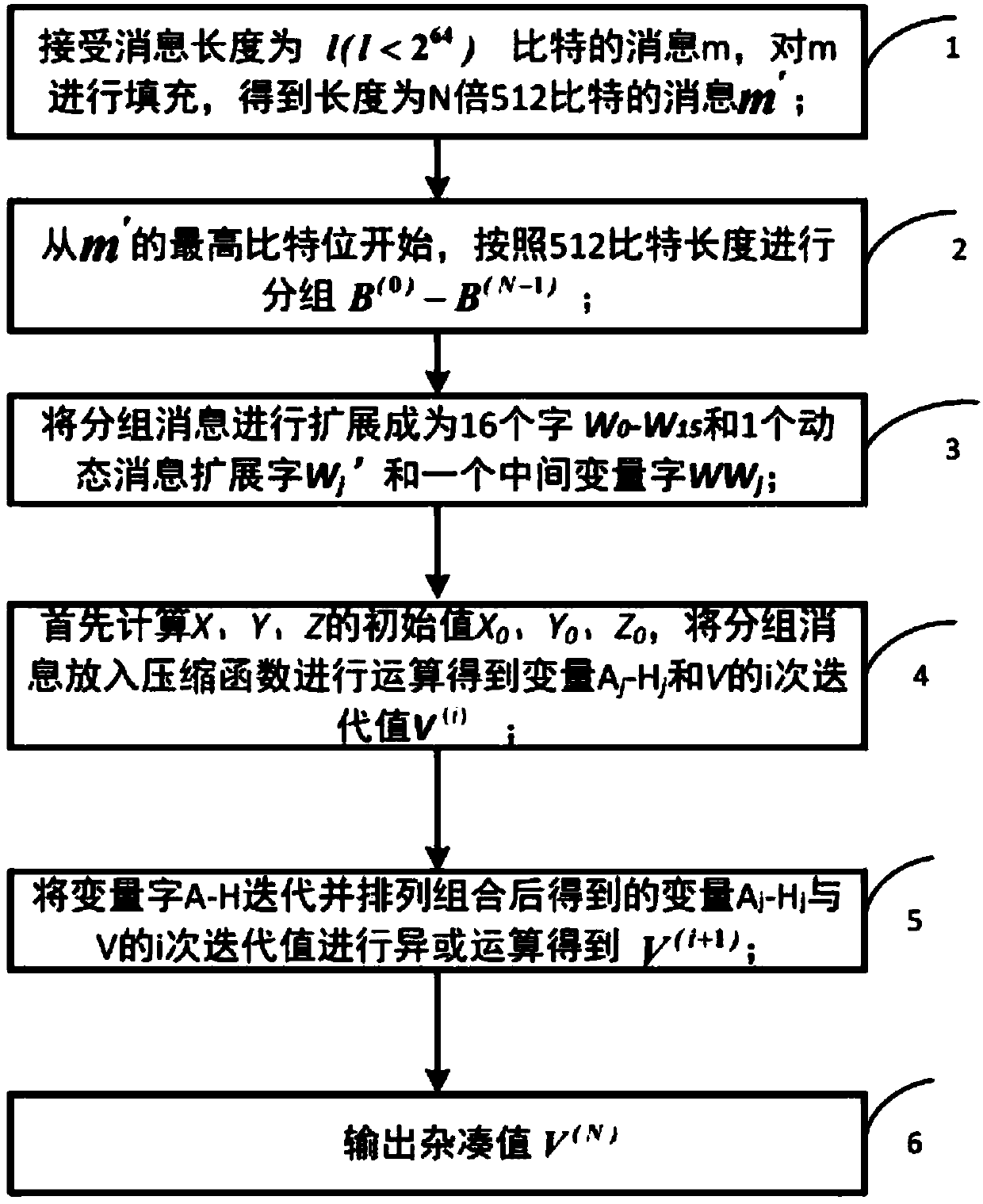
The invention discloses a hardware optimization method based on an SM3 password hash algorithm. The method includes receiving a message m with the length of l bits , and filling m to obtain a messagem'; starting from the highest bit of m', and grouping according to the length of 512 bits, m'= B (0), B (1),..., B (n-1); expanding the grouped message B (i) according to an extension method, and generating 16 32-bit extension words W0, W1, ..., W15, one dynamic message extension word Wj' and one intermediate variable word WWj; and placing the grouped message into a compression function for operation to obtain variables Aj-Hj and the i-time iteration value Vi of V; subjecting the variables Aj-Hj and the i-time iteration value Vi of V obtained by operation to the exclusion operation to obtain V(i+1); and outputting a hash value V(N). According to the method, the operation efficiency of the SM3 password hash algorithm is effectively improved, and the software and hardware implementation costof the SM3 password algorithm is greatly saved, the calculation amount of the algorithm is not increased, and the calculation efficiency of the algorithm is guaranteed.
Owner:广州星海集成电路基地有限公司
Method for generating a secure cryptographic hash function
InactiveUS20150215114A1Readily apparentKey distribution for secure communicationCryptographic hash functionMerkle–Damgård construction
A method for generating a secure cryptographic hash function supporting 256-512 bit digests is provided. A compression function based on a block cipher in the Davies-Meyer mode is used. A hash function is developed from this compression function using an iterative compression function with the Merkle-Damgård construction, finally resulting in a wide pipe construction in which the intermediate chaining value is at least twice the length of the output hash.
Owner:ALAHMAD MOHAMMAD A +1
RSA key pair fast generation system and RSA key pair fast generation method
InactiveCN106487512AReduce build timeHigh speedKey distribution for secure communicationPublic key for secure communicationCoprocessorComposite number
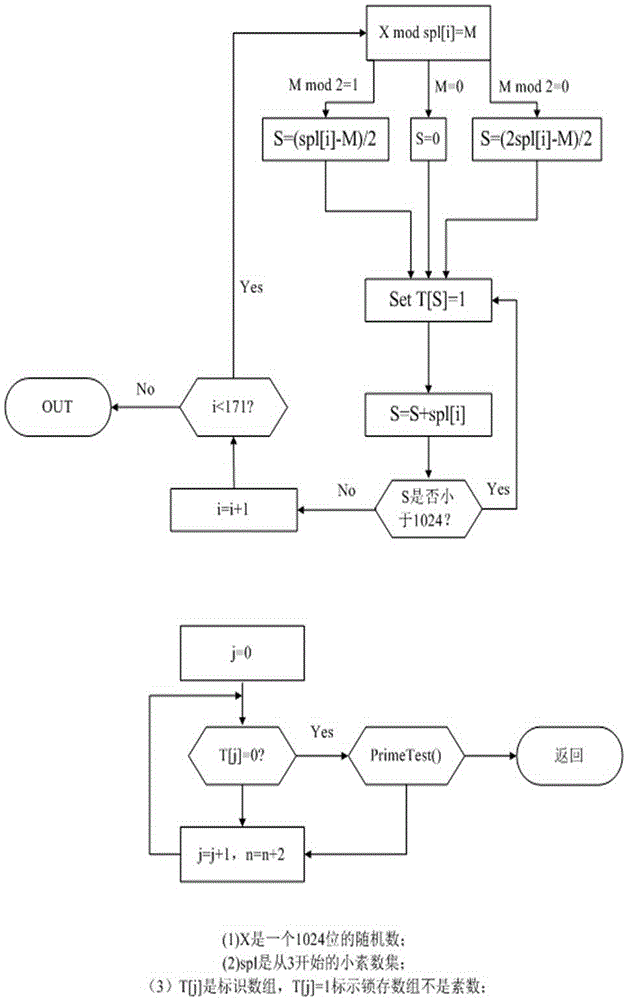
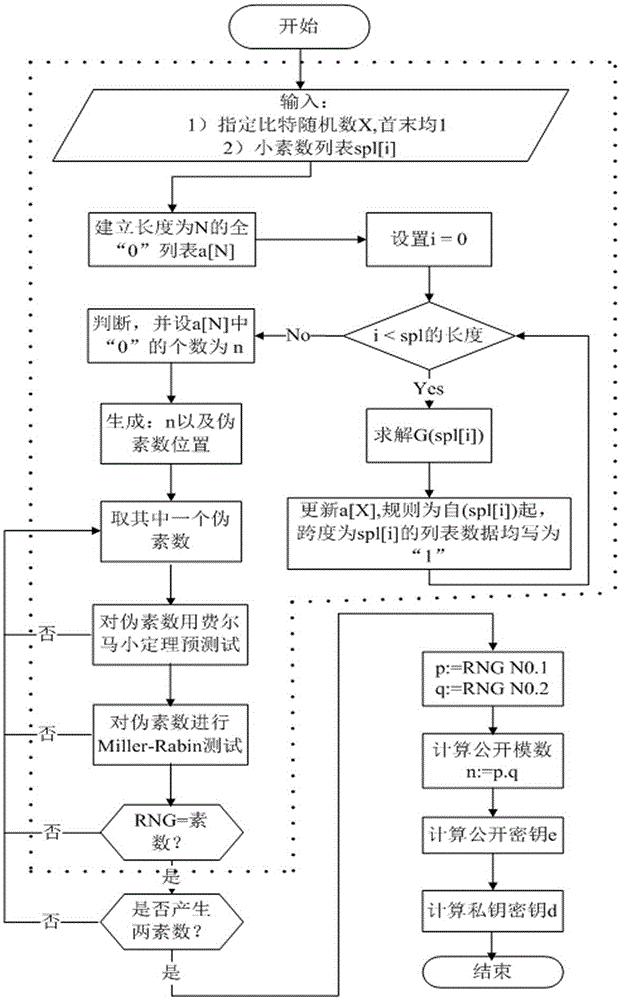
The invention discloses an RSA key pair fast generation system and an RSA key pair fast generation method. The system comprises a CPU core, a cipher coprocessor, a prime number generator, and a memory. The prime number generator is used for filtering composite numbers, is implemented in hardware form, supports 256-bit, 512-bit, 1024-bit, 2048-bit and 4096-bit composite number filtering, and completes modular redundancy, calculation and identification table setting. According to the RSA key pair fast generation method, in order to realize fast key pair retrieving, filtering and judging in an asymmetric algorithm, a hardware-based composite number filtering scheme is adopted, optimized modular exponentiation and improved Montgomery modular multiplication are employed, and the existing prime number decision algorithm is optimized. Thus, efficient prime number screening is realized, the key pair generation speed is increased, and the problem that the generation of an RSA key pair takes long in the existing encryption and decryption technology is solved.
Owner:BEIJING TONGFANG MICROELECTRONICS
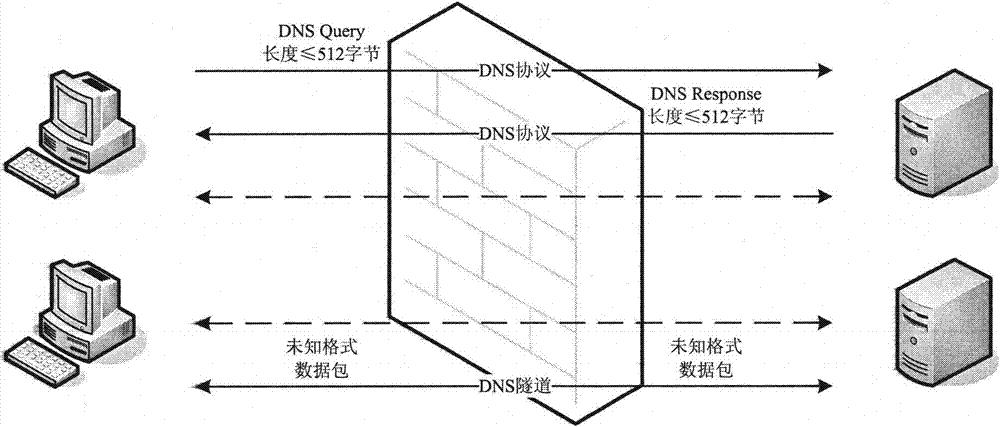
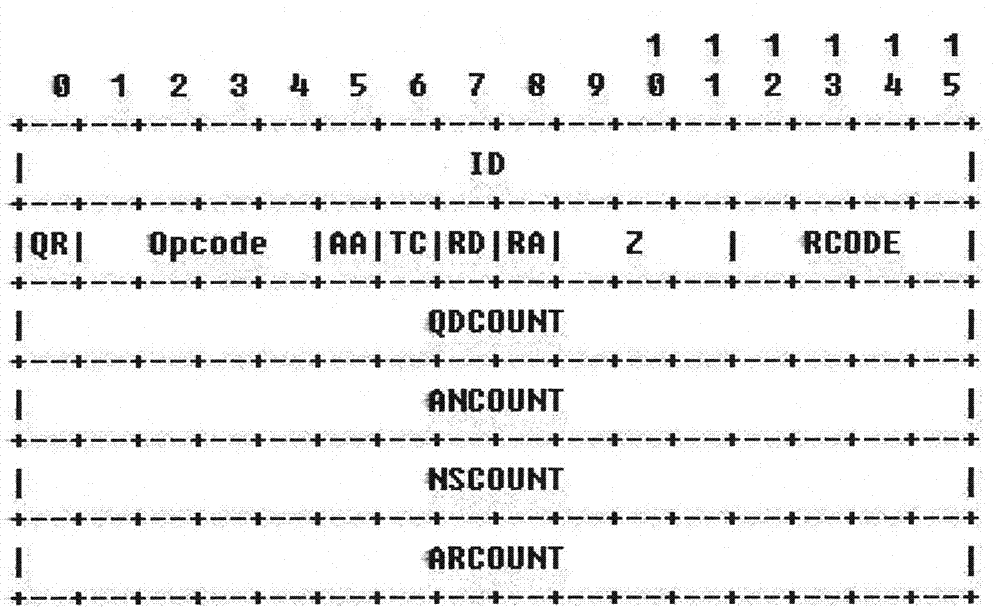
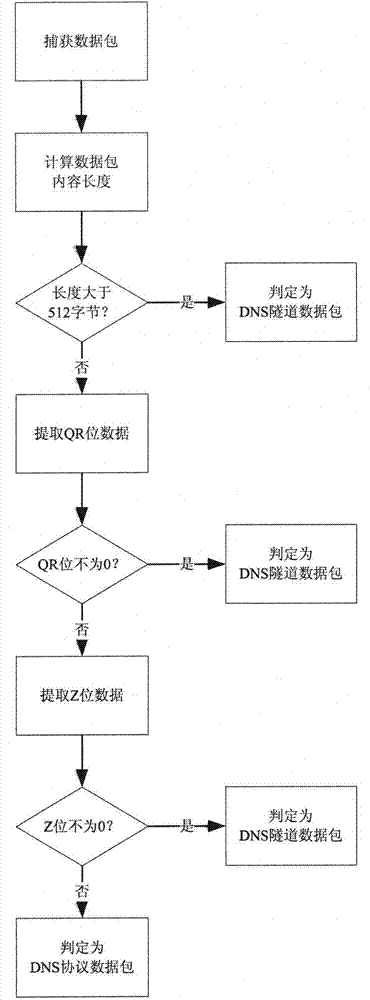
Method for detecting DNS (Domain Name-implementation and Specification) tunnel data based on DNS protocol standard
The invention belongs to the technical field of computer networks, and discloses a method for distinguishing standard DNS (Domain Name-implementation and Specification) protocol data and DNS tunnel data. The system acquires a data packet of a DNS port. When the data packet reaches a detection system, 1, the system examines the length of data packet content and considers that the data is the DNS tunnel data if the length is greater than 512 bits; 2, the system examines the content of the data packet and judges whether the standard DNS protocol is met (for example, a client transmits DNS Query, and a server responds DNS Response). If the standard DNS protocol is met, the system considers that the data is the DNS protocol data, and otherwise considers that the data is the DNS tunnel data. By using the method, the DNS tunnel data can be recognized and differentiated service is performed, or the non-DNS protocol data is stopped from penetrating through the DNS port.
Owner:金琥
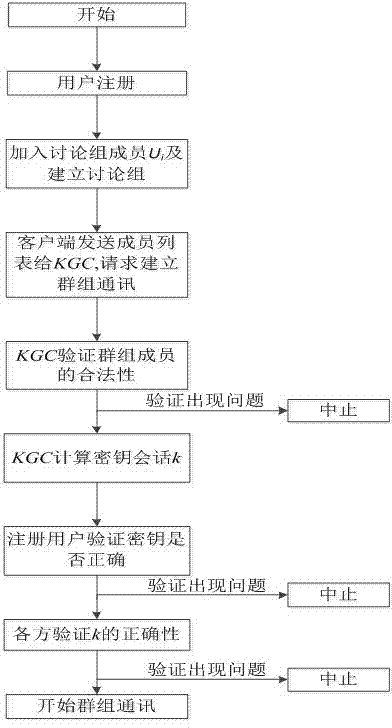
Method for establishing safety communication of network groups
InactiveCN103051457AEnsure safetyPrevent attack and stealSpecial service provision for substationUser identity/authority verificationSecure communicationHash function
The invention discloses a method for establishing safety communication of network groups. The method comprises the following steps of: processing long-term secret data and authentication information of group communication members by using an SHA (Secure Hash Algorithm) safety hash function which is 512 bits in length; and distributing a key by using an interpolation polynomial according to a secret partition threshold scheme of Shamir to keep a group key fresh, confidential and authenticable and effectively resist external attacks and internal attacks. According to the invention, all information is transmitted on a public channel, so that the method has the characteristics of low calculation amount, high running speed and high server calculation efficiency.
Owner:GUILIN UNIV OF ELECTRONIC TECH
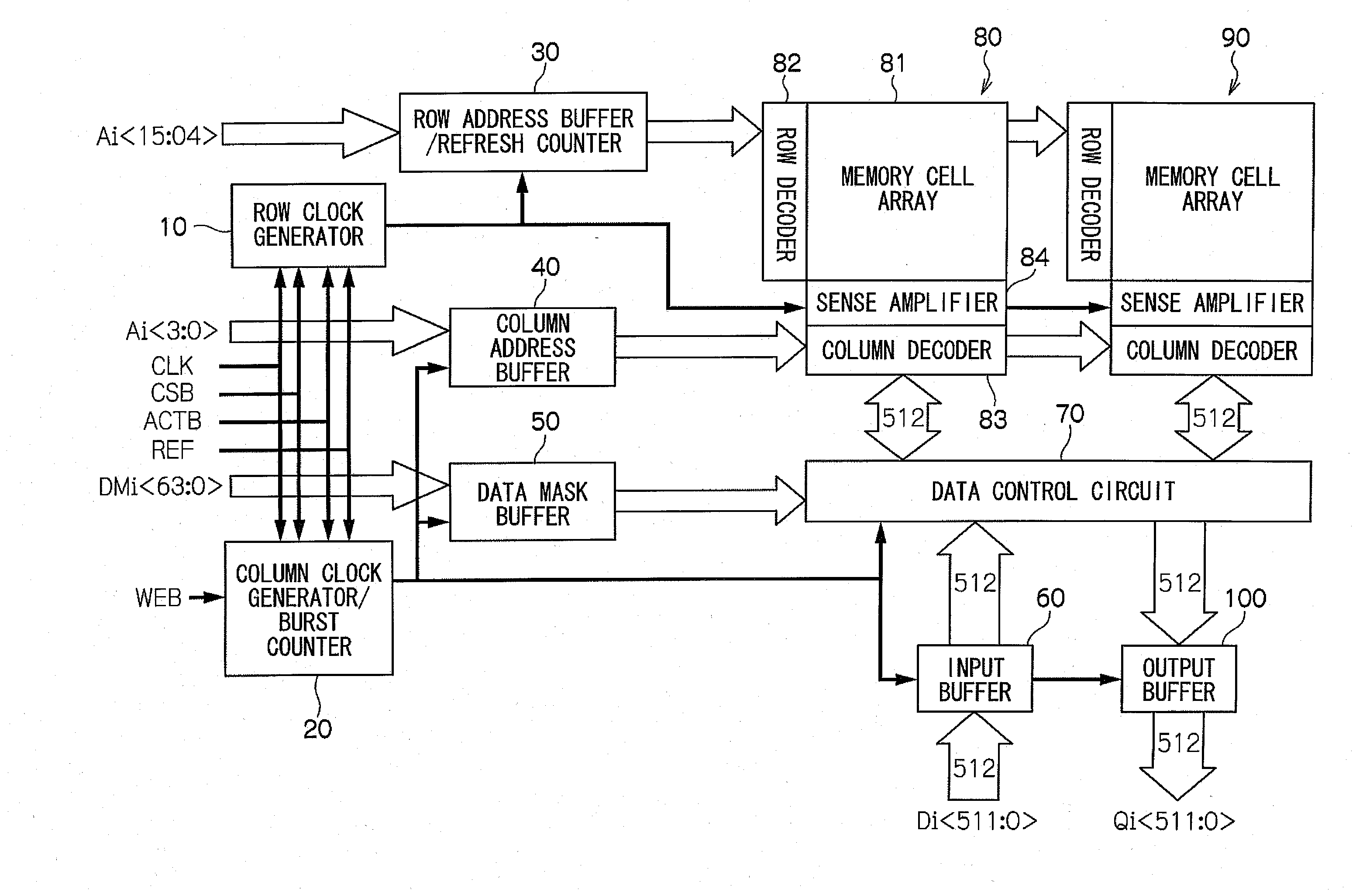
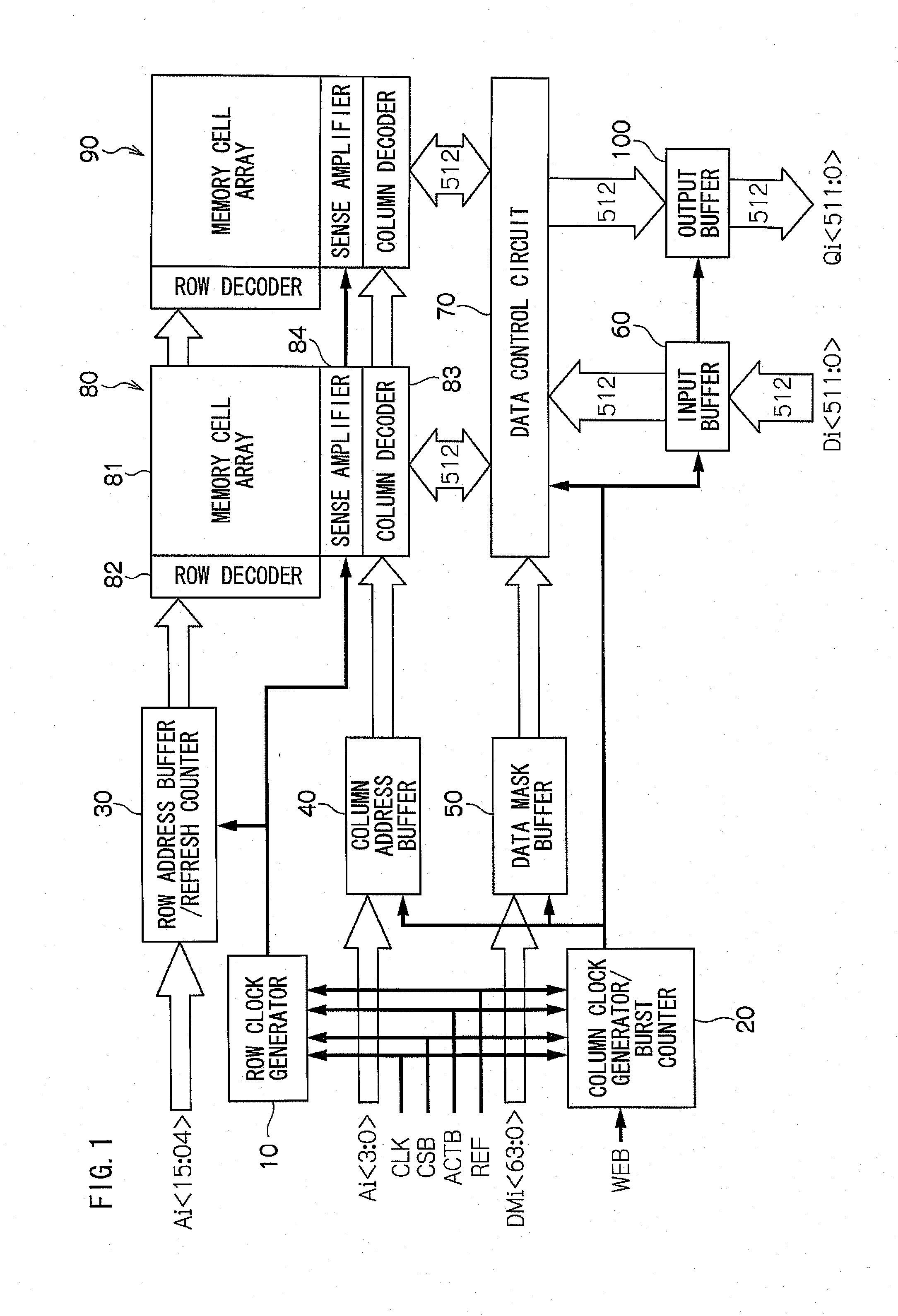
Semiconductor memory device
InactiveUS20100110747A1Enhances random accessHigh-speed writingDigital storageMemory bankHemt circuits
The semiconductor memory device proposed in the present invention comprises memory cells disposed in the row direction and the column direction, a plurality of first lines by which supply voltages are supplied in order to select memory cells disposed in the row direction among the plurality of cells, a plurality of second lines by which supply voltages are supplied in order to select memory cells disposed in the column direction among the plurality of cells, the data lines which input and output the data to the selected memory cells, the first power voltage supply circuit which supplies the predetermined supply voltages to the first lines corresponding with the externally input row address synchronizing with an act command, and the second power voltage supply circuit which supplies the predetermined supply voltages to the second lines corresponding with the externally input column address synchronizing with an act command. It also comprises m pieces of memory banks (m is a natural number larger than 2) which write or read the data into or from the memory cells which are selected one after another in the row or column directions, data input circuits in which multiple bits of serial data which is larger than 512 bits to be written in the m pieces of memory banks, data output circuits which reads the data from the m pieces of memory banks and output in a form of multiple bits of serial data which is larger than 512 bits, and data conversion circuits which convert the serial data input in the data input circuits to parallel data so that it can be written in each memory bank or to convert each parallel data read from each memory bank to serial data so that such data are supplied to the data output circuits.
Owner:RAMBUS INC
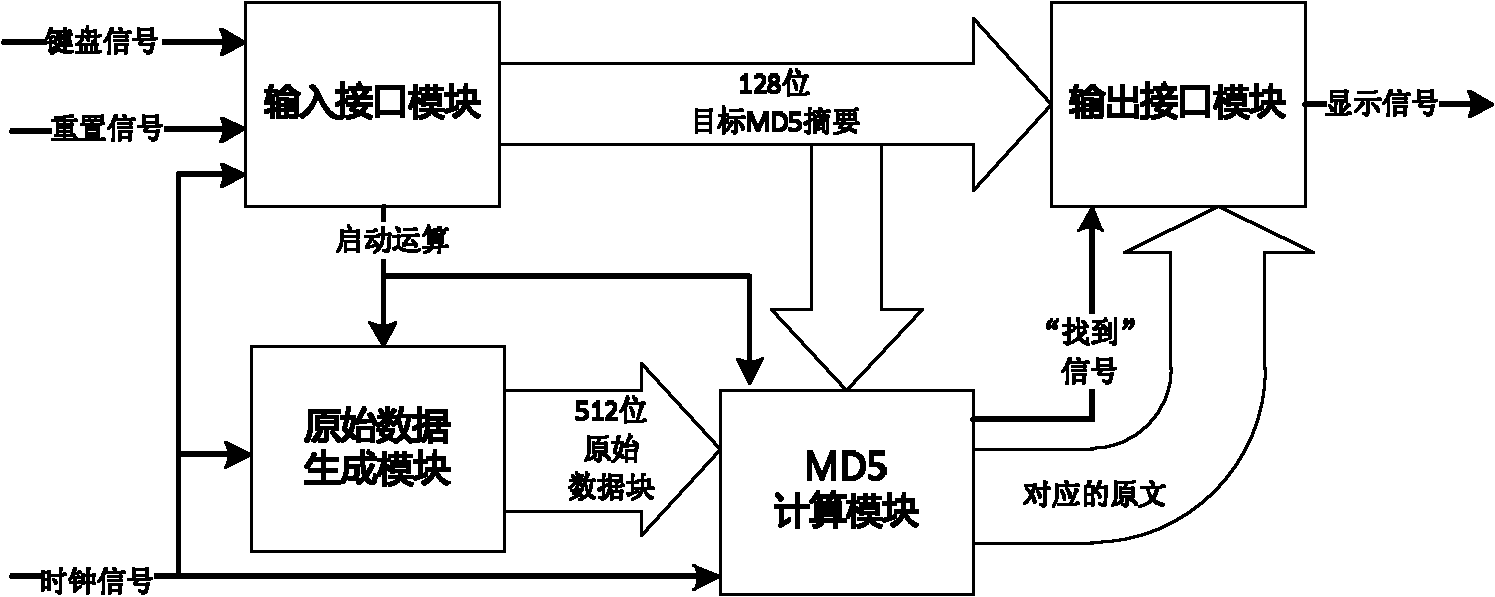
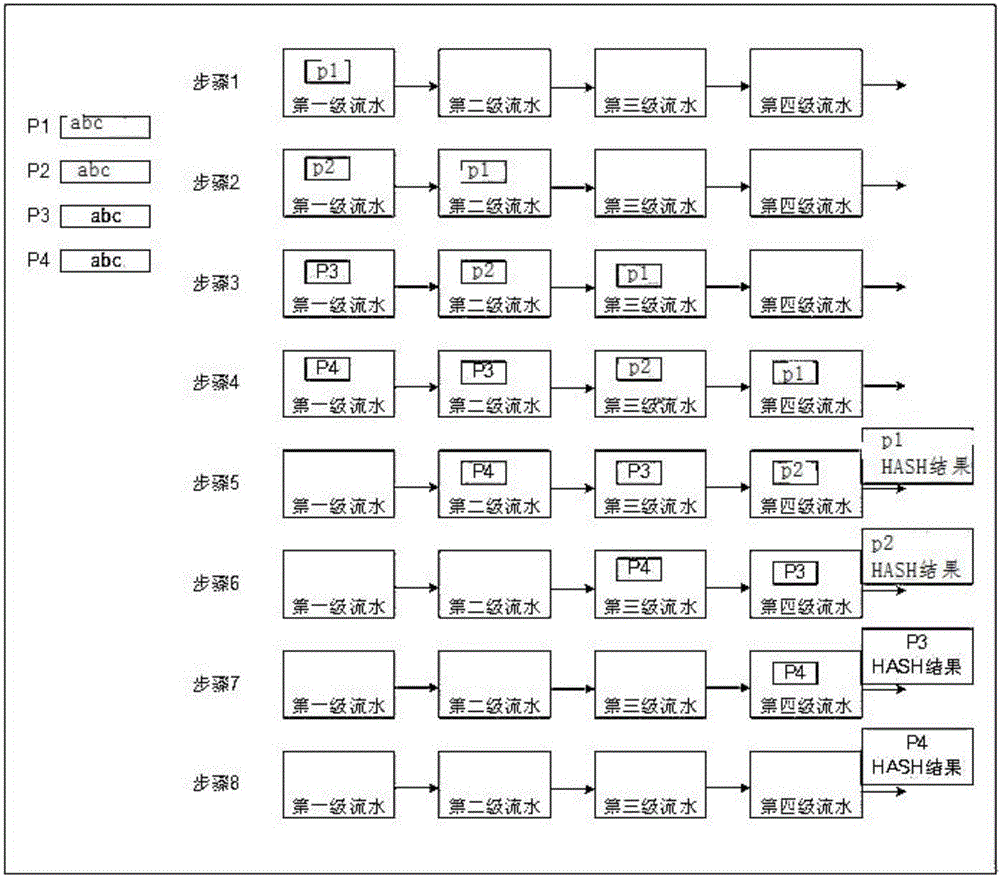
Ultrahigh-throughput MD5 brute-force cracking device implemented based on FPGA
InactiveCN102156434AClock upImprove throughputProgramme control in sequence/logic controllersInformation processingBrute force
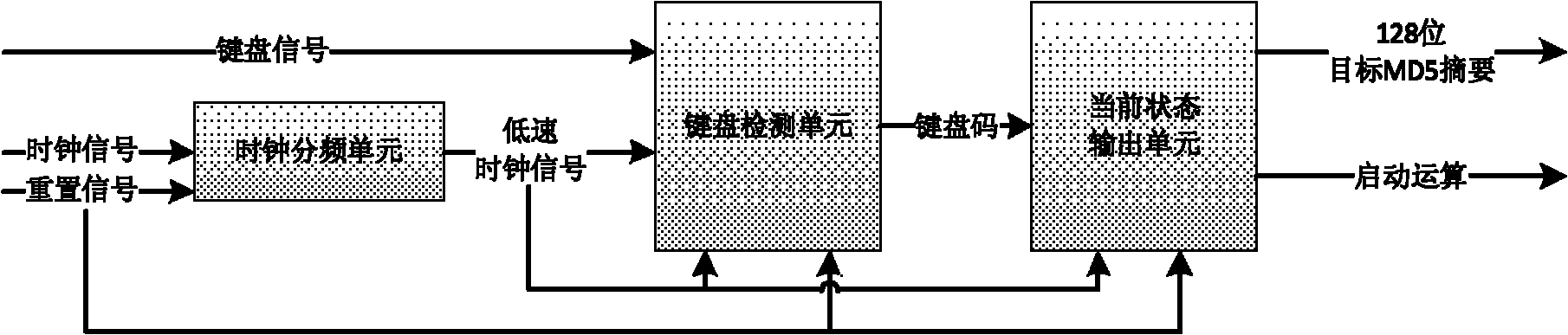
The invention discloses an ultrahigh-throughput MD5 brute-force cracking device implemented based on a FPGA (Field Programmable Gate Array) in the technical field of digital information processing. The ultrahigh-throughput MD5 brute-force cracking device comprises an input interface module, a raw data generation module, a MD5 computation module and an output module implemented in the FPGA, and a keyboard input device and a display interface device connected to the FPGA; the input interface module is connected with the keyboard input device and transmits a target MD5 value and control computation information input by a user, the raw data generation module is connected with the input interface module and the MD5 computation module and transmits 512-bit raw data block information to the MD5 computation module under the control of a clock signal, the MD5 computation module is connected with the input interface module, the raw data generation module and the output interface module and transmits computation result to the output interface module, and the output interface module is connected with the display interface device and transmits the computed target MD5 value and the computation result. In the ultrahigh-throughput MD5 brute-force cracking device implemented based on the FPGA, information is stored in a FIFO (First in First out) memory so as to cooperate with the computation of the whole pipeline architecture, and computation efficiency is improved.
Owner:SHANGHAI JIAO TONG UNIV
High-throughput SHA-1 (Secure Hash Algorithm) based on FPGA
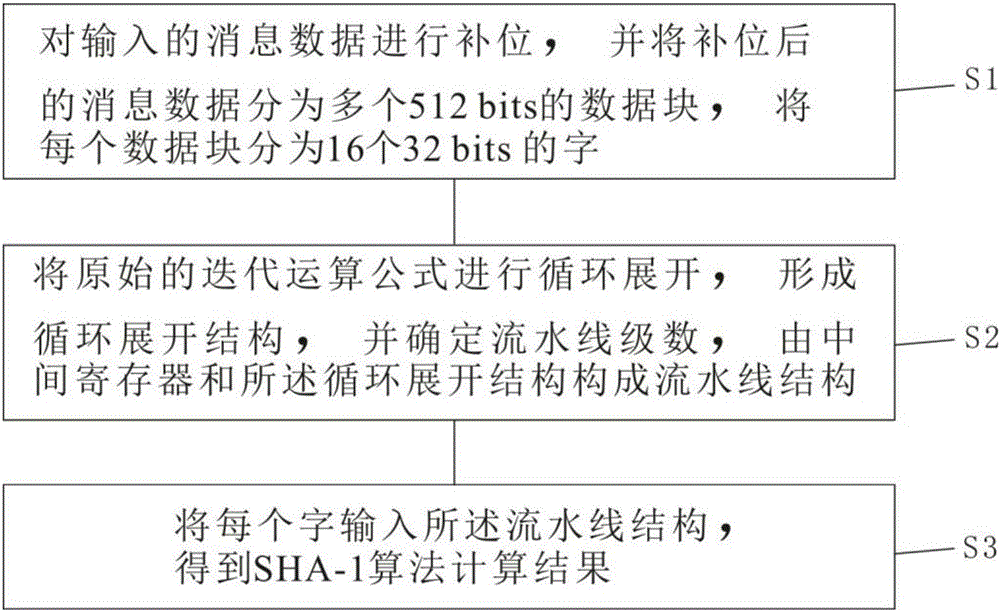
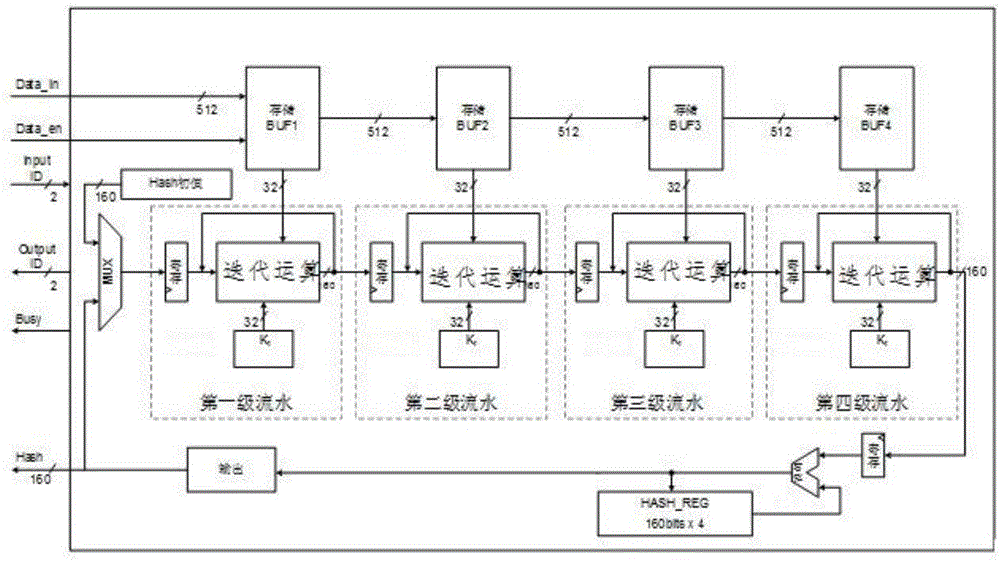
InactiveCN106100825AReduce clock cyclesCalculation speedEncryption apparatus with shift registers/memoriesProcessor registerCritical path method
The invention provides a high-throughput SHA-1 (Secure Hash Algorithm) based on an FPGA. The method comprises the steps of S1, judging whether length of input message data exceeds 512 bits or not; S2, carrying out bit compensation on the message data until the length is integer multiples of the 512 bits if the length of input message data exceeds 512 bits; S3, segmenting the message data after bit compensation into multiple data blocks, wherein each data block is 512 bits, and segmenting each data block into 16 characters, wherein each character is 32 bits; S4, carrying out loop unrolling on an original iteration operation formula, thereby forming a loop unrolling structure; S5, determining pipeline series, and forming a pipeline structure by an intermediate register and the loop unrolling structure; and S6, inputting each character into the pipeline structure, thereby obtaining a SHA-1 calculation result. According to the algorithm, the iteration operation is simplified, an intermediate variable is added, therefore, a key path is shortened, and a calculation speed is improved. Moreover, through adoption of a pipeline processing mode, the data processing quantity is increased, and the throughput is improved.
Owner:SHENZHEN FORWARD IND CO LTD
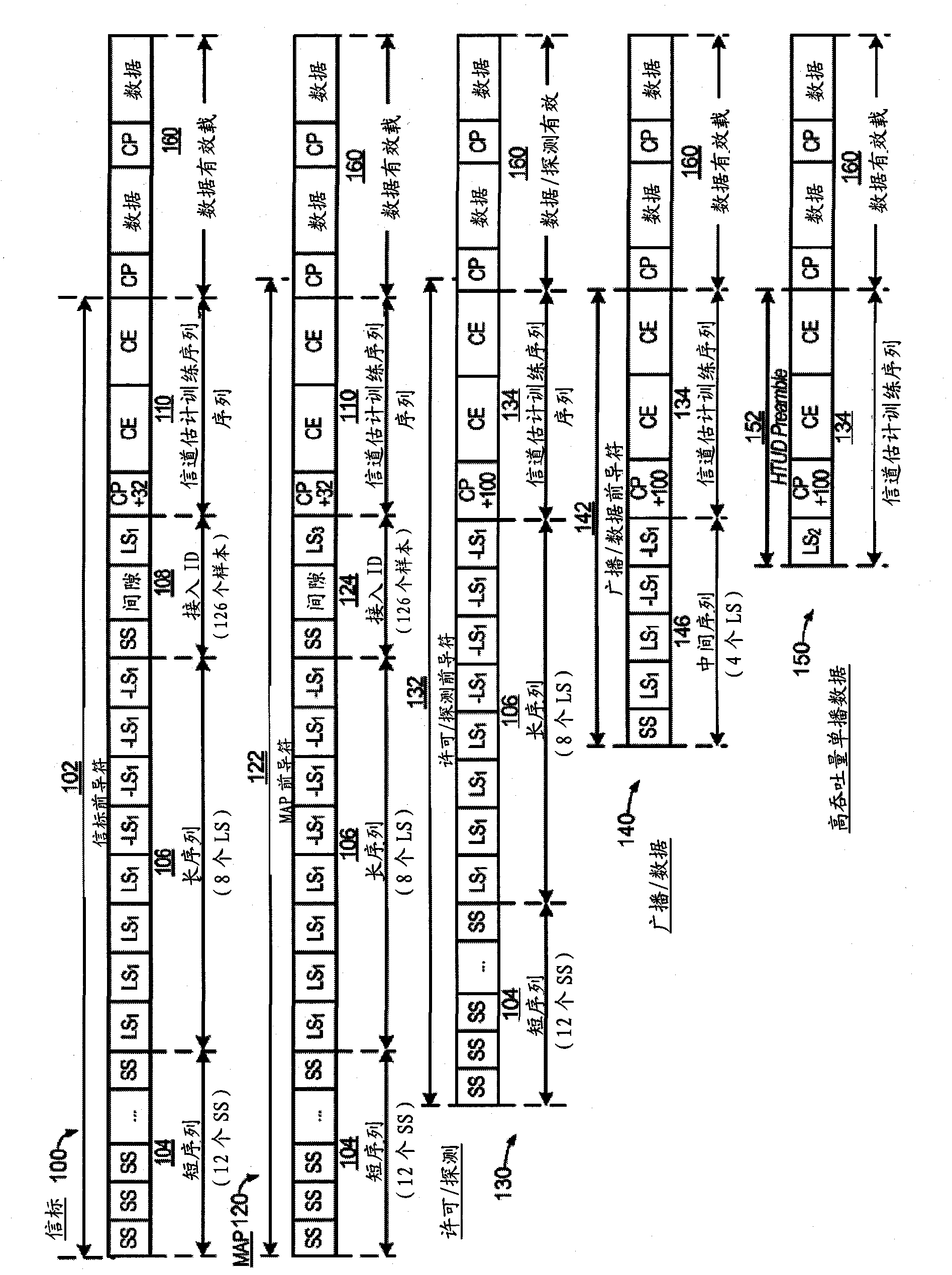
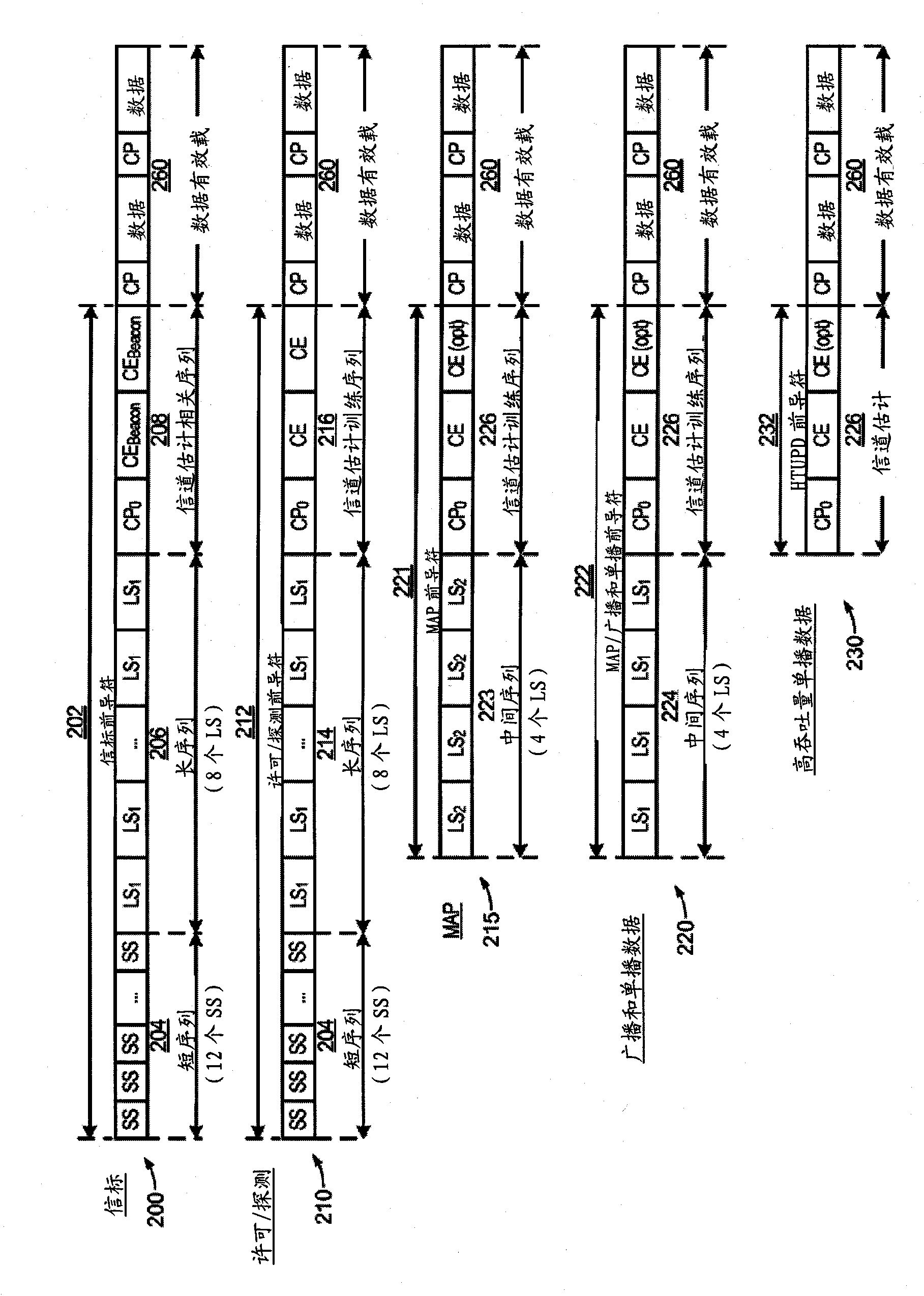
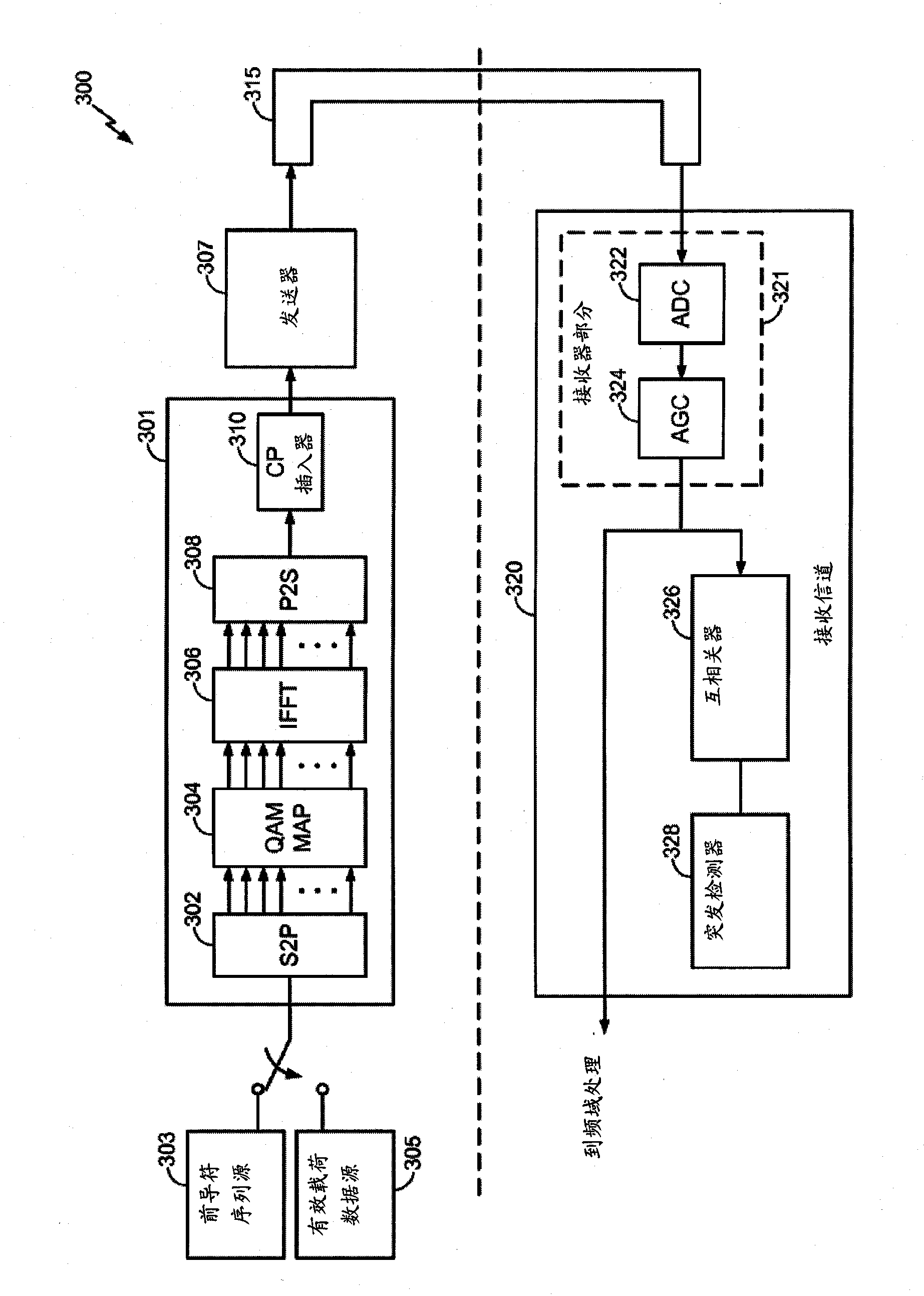
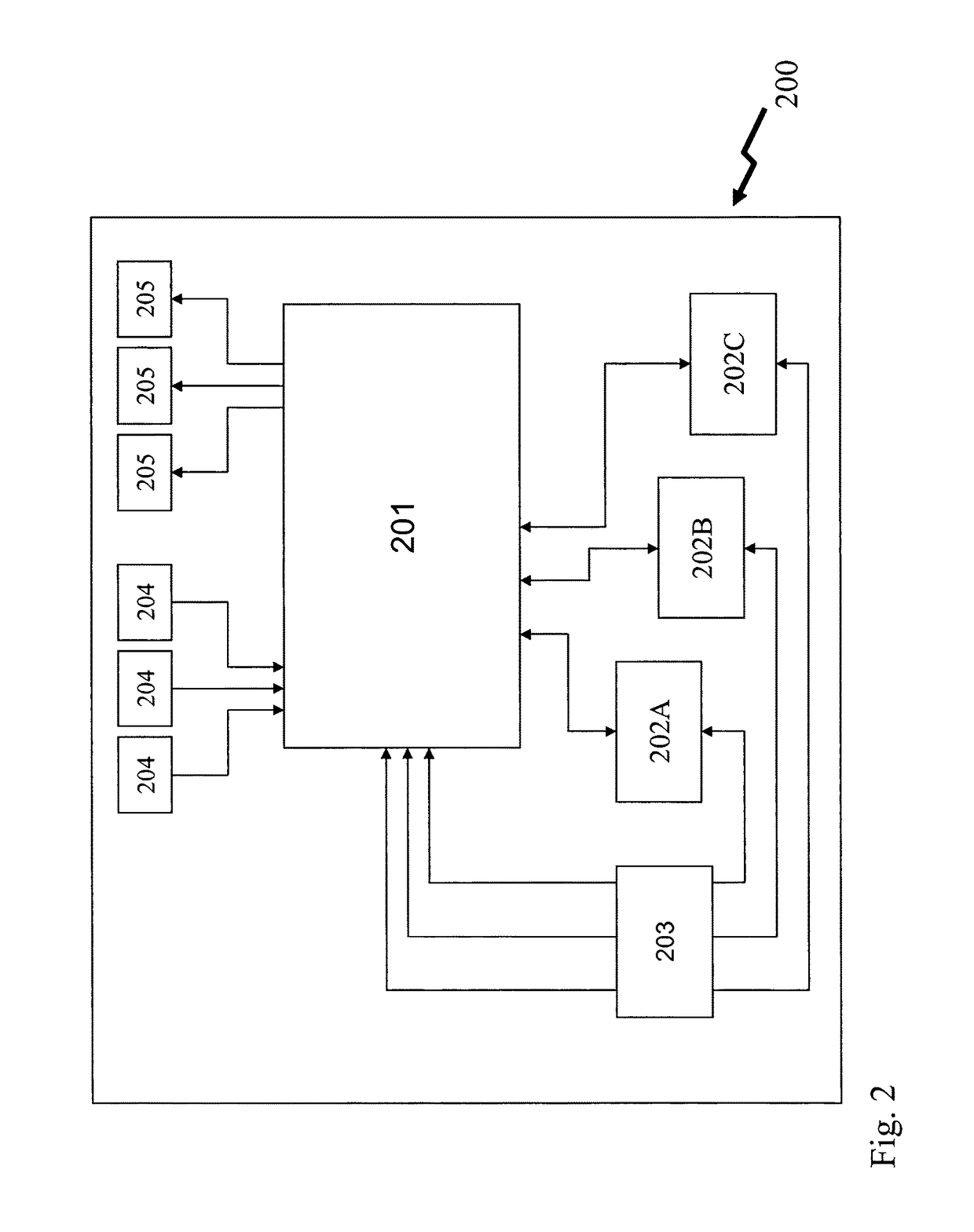
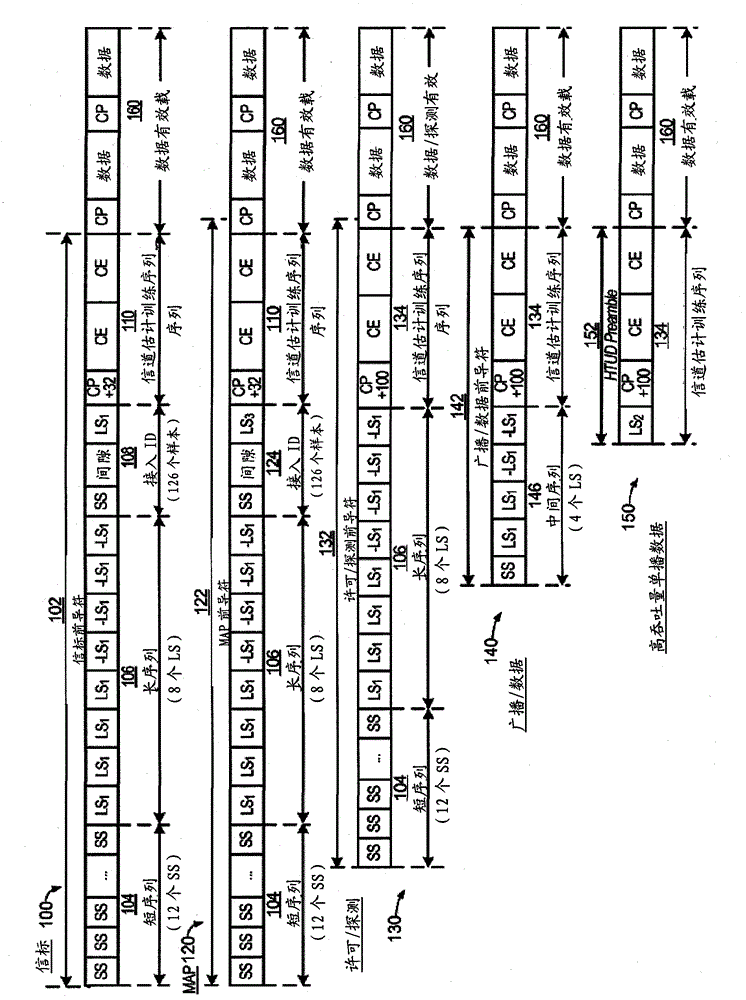
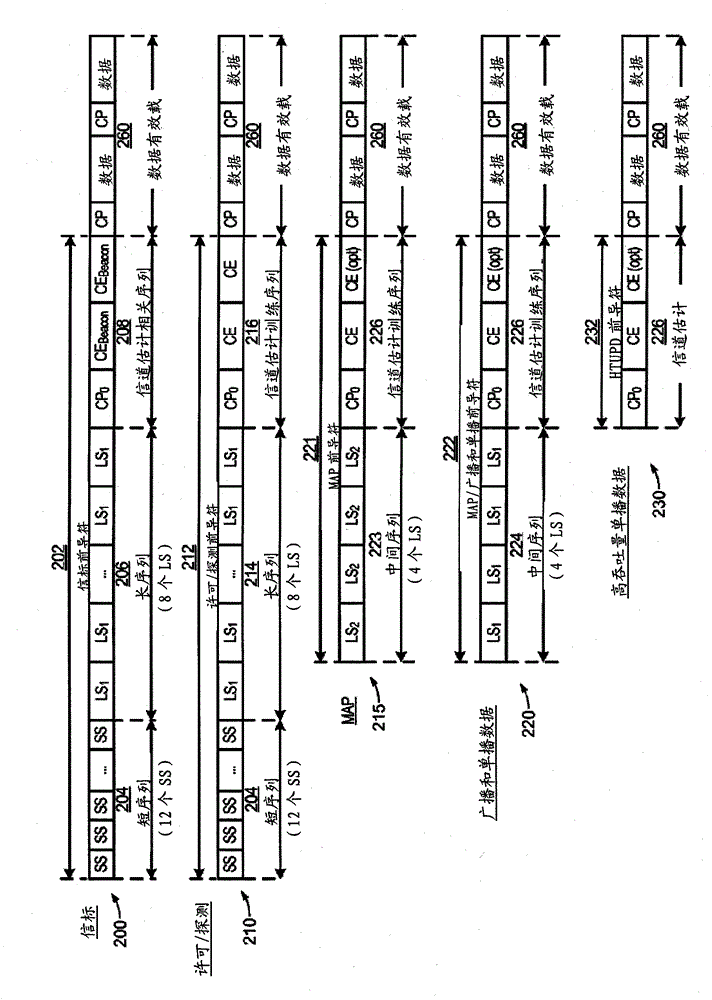
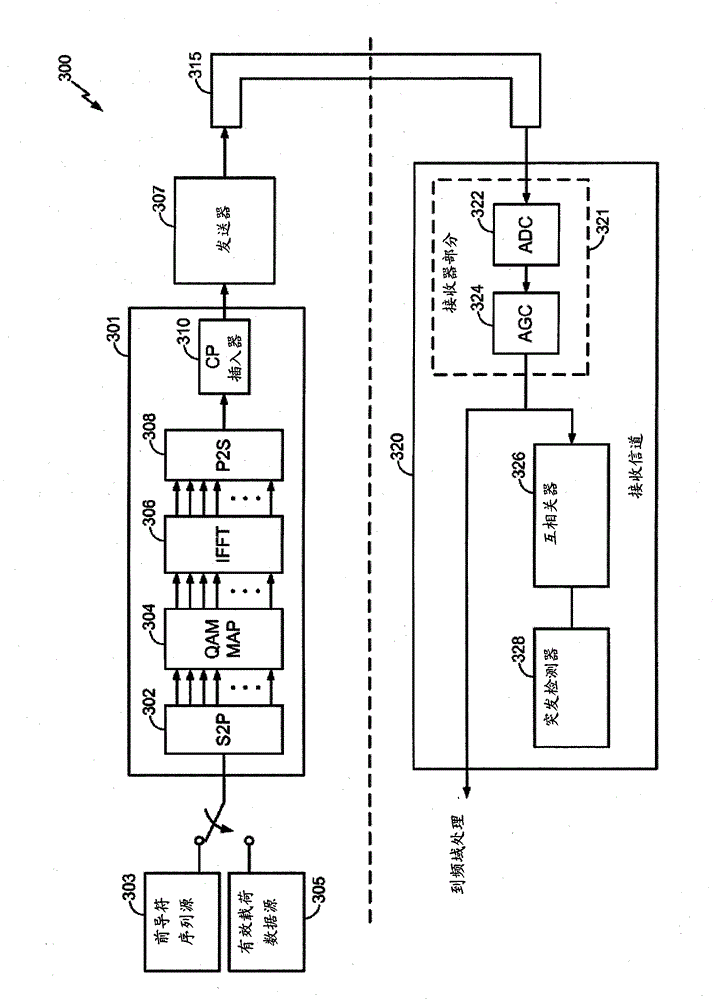
High efficiency preambles for communications systems over pseudo-stationary communication channels
InactiveCN102150403ABaseband system detailsBroadband local area networksCommunications systemBroadcasting
A method includes appending a preamble to a data packet and transmitting the preamble and data packet over a communication channel in the network. The preamble may be a Beacon, Admission, Broadcast, or High-Throughput Preamble. The Beacon Preamble includes the following symbols SS, SS, SS, SS, SS, SS, SS, SS, SS, SS, SS, SS, LS1, LS1, LS1, LS1, LS1, LS1, LS1, LS1, CP0, CEBeacon, CEBeacon. The Admission Preamble includes the following symbols SS, SS, SS, SS, SS, SS, SS, SS, SS, SS, SS, SS, LS1, LS1, LS1, LS1, LS1, LS1, LS1, LS1, CP0, CE, CE. The Broadcast Preamble includes the following symbols LS1, LS1, LS1, LS1, CP0, CE, CE. The high-throughput preamble includes the following symbols CP0, CE. The SS symbol includes 64 bits, the LS1, LS2, and CP0 symbols include 192 bits, the CE symbol includes 512 bits, and the CEBeacon symbol is a subset of CE.
Owner:ENTROPIC COMM INC
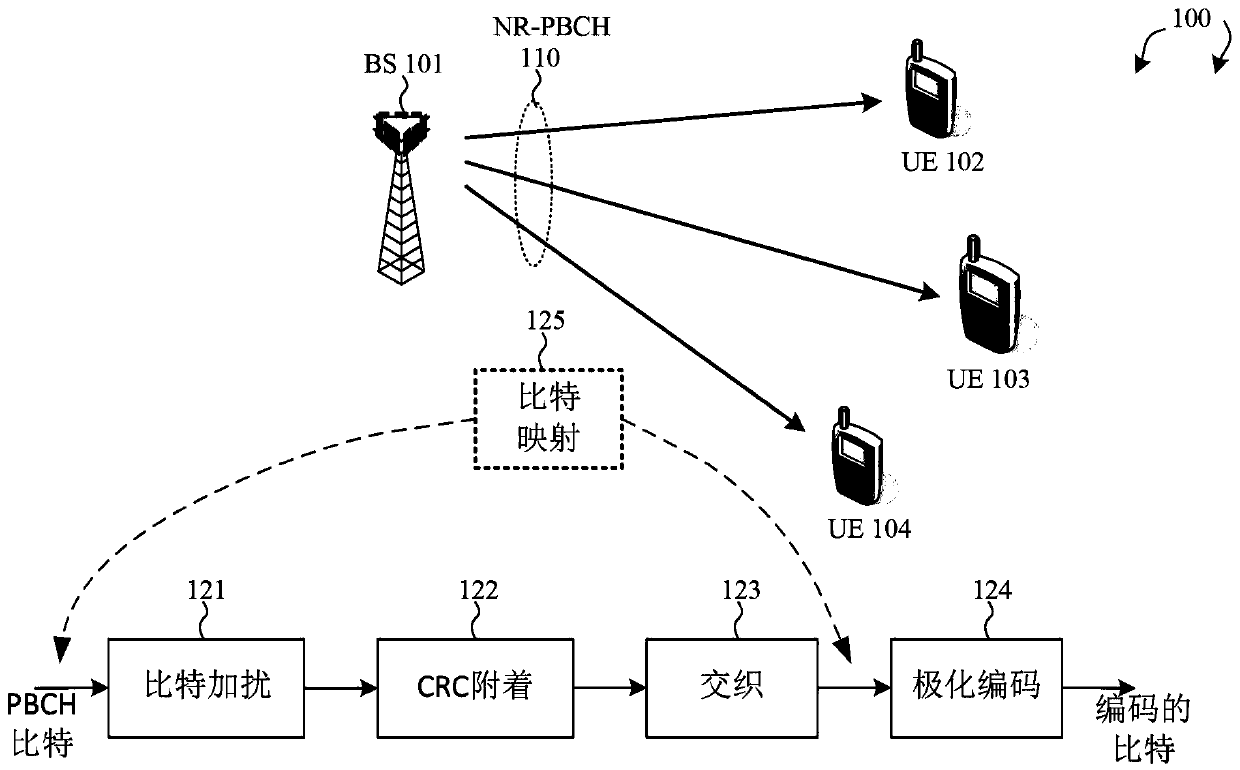
Broadcast channel enhancement with polar code
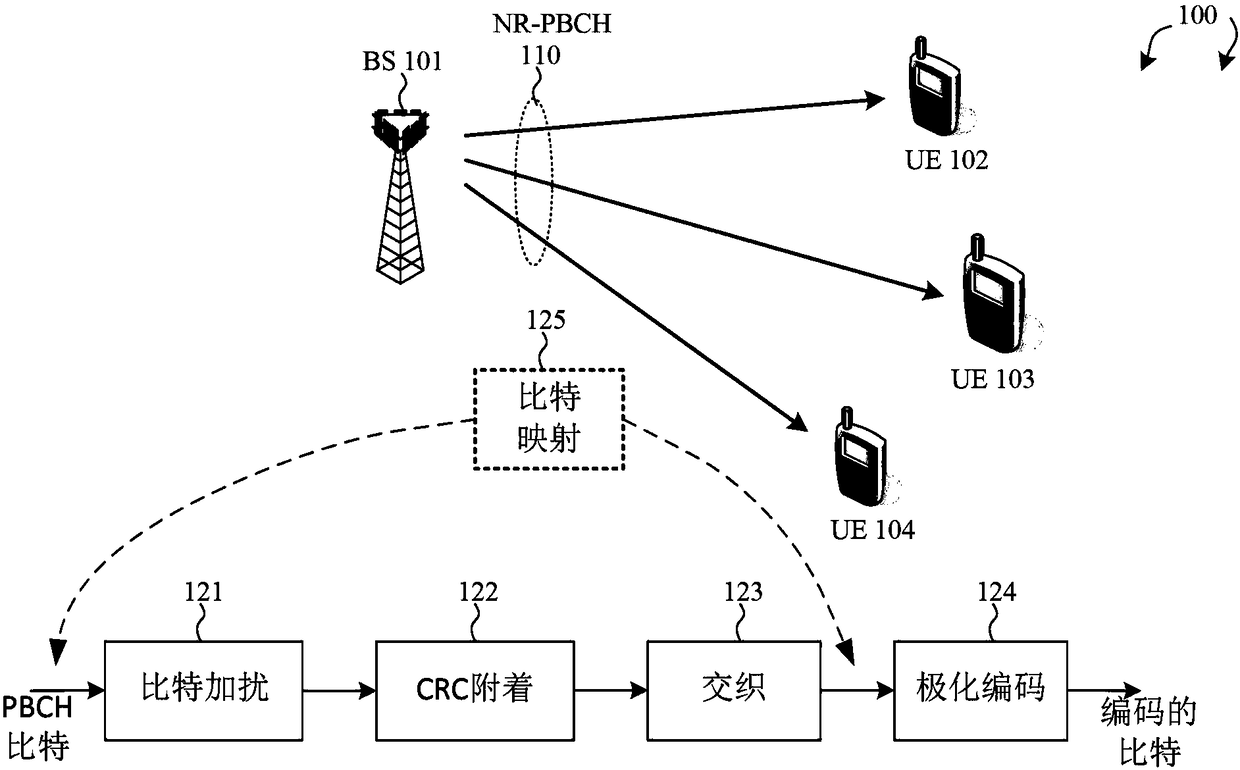
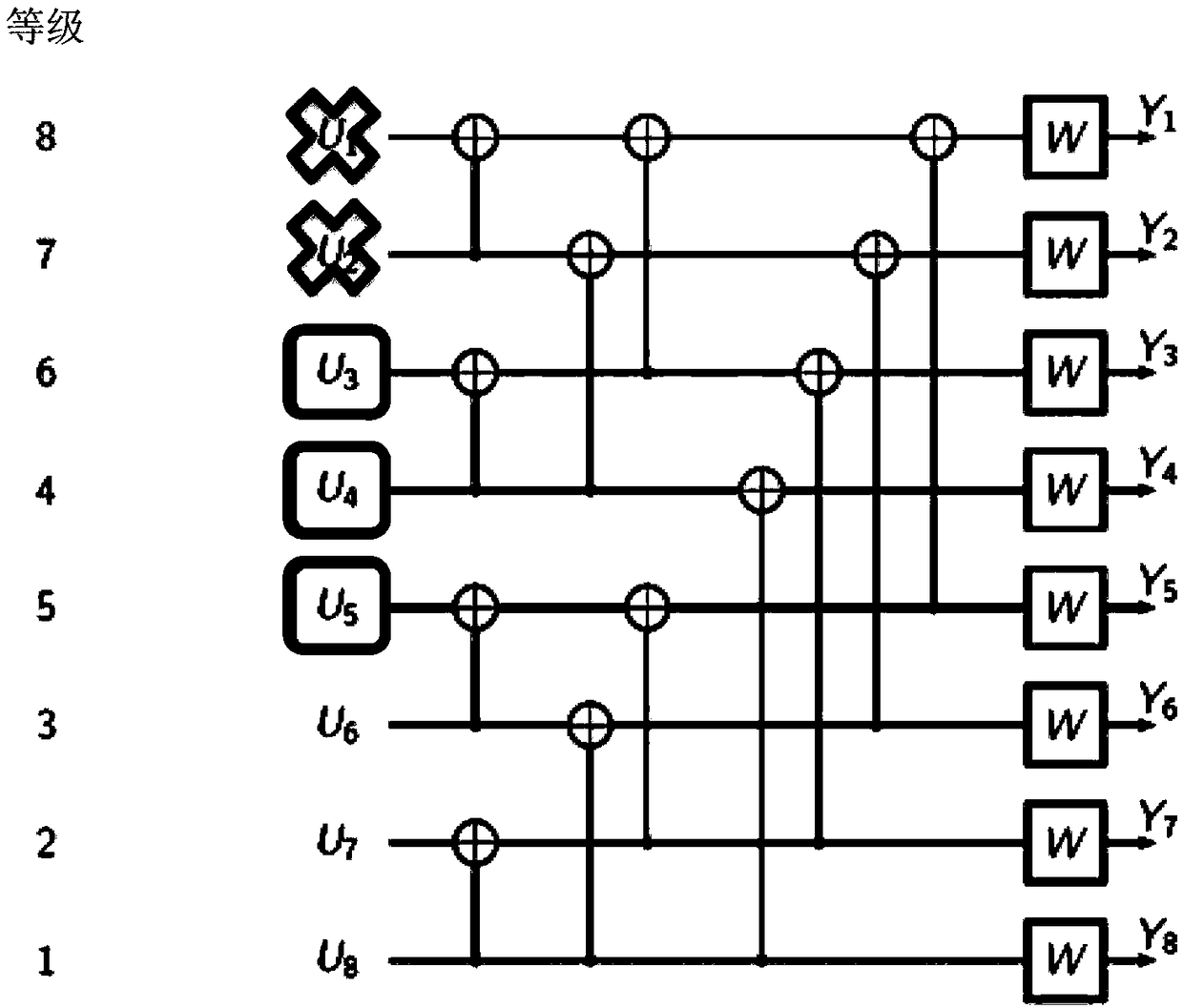
A method of new radio physical broadcast channel (NR-PBCH) bit mapping is proposed to improve for NR-PBCH decoding performance under Polar codes. NR-PBCH carries 32 information bits and 24 CRC bits. Specifically, NR-PBCH uses 512-bit Polar codes to carry total 56 data bits. Different Polar code bit channels have different channel reliability. As a general rule, the most reliable Polar code bit channels are used for the 56 data bits. In accordance with a novel aspect, within the 32 NR-PBCH information bits, some of the information bits that can be known to the decoders under certain conditionsand therefore are placed at the least reliable Polar code bit positions. As a result, by mapping the NR-PBCH data bits properly at the input bit positions of Polar codes, the NR-PBCH decoding performance is improved when the known bits a priori can be exploited.
Owner:MEDIATEK INC
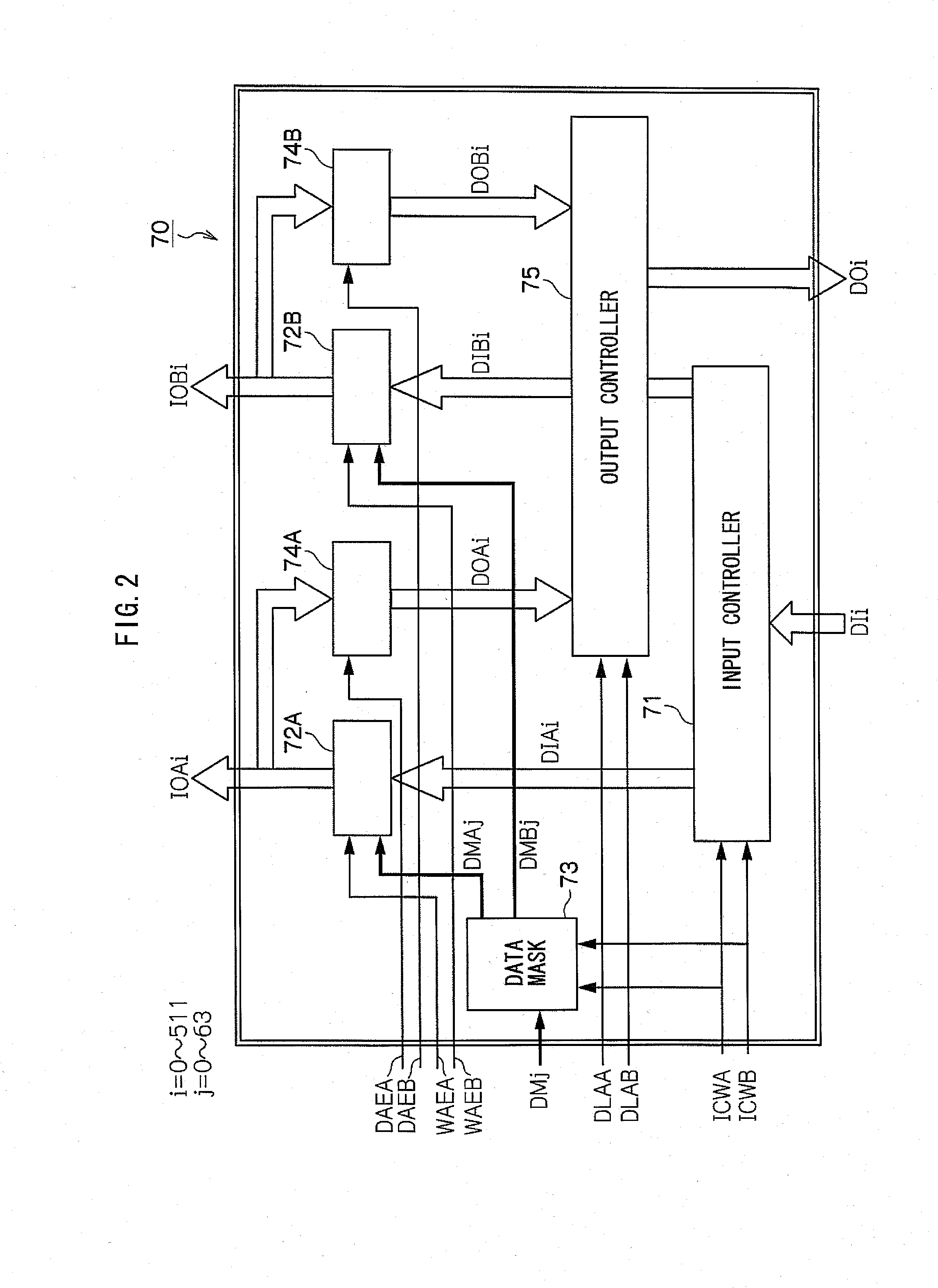
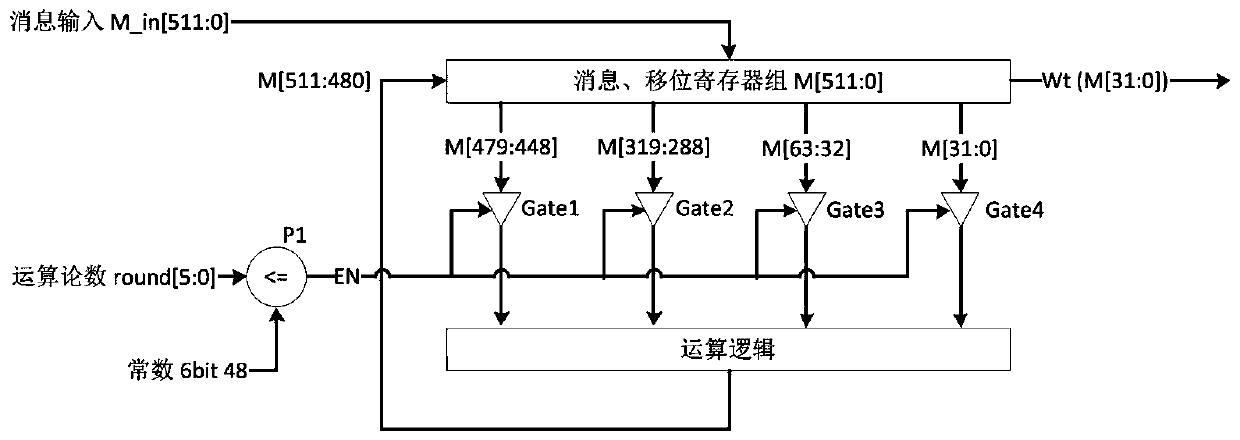
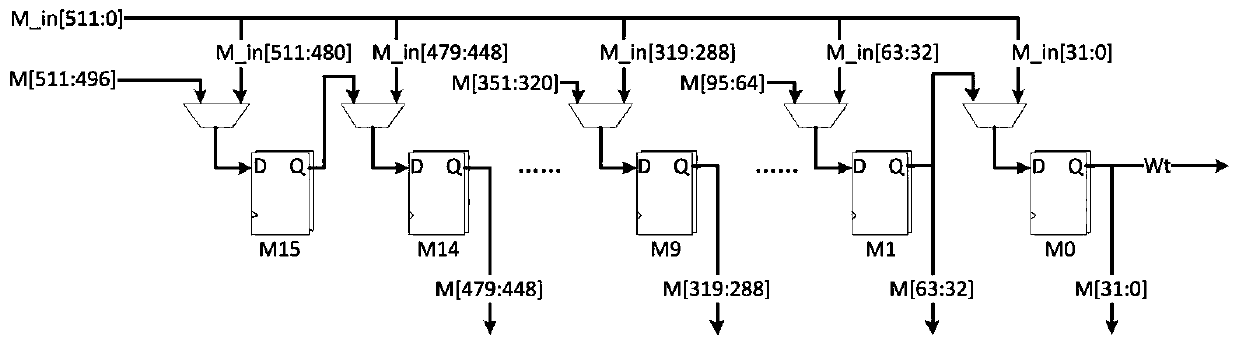
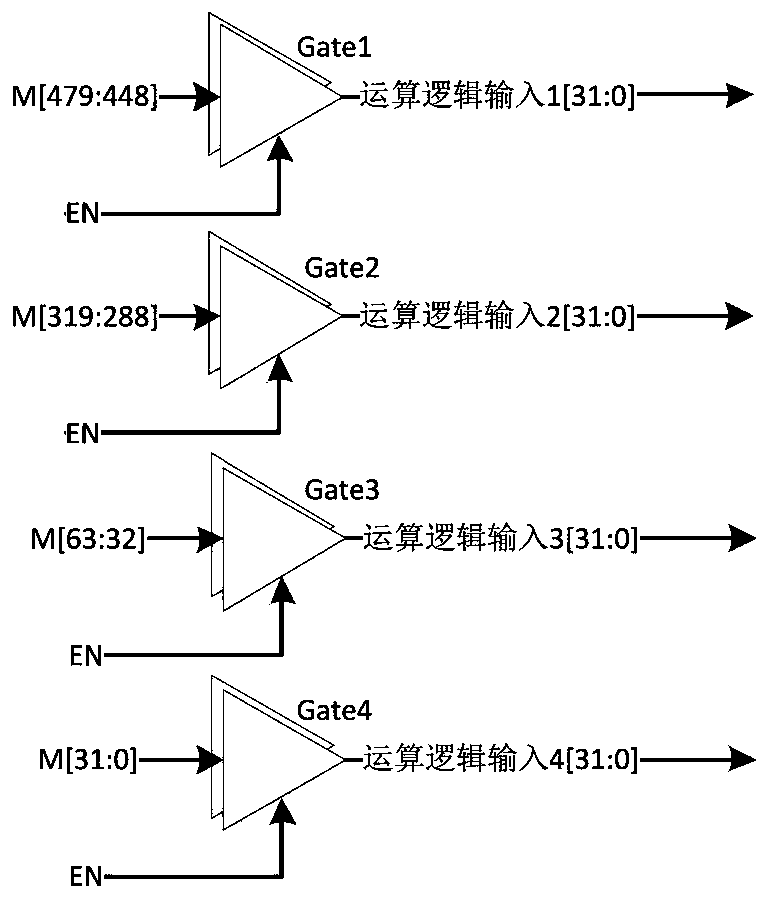
Message expansion circuit in low-power-consumption SHA256 algorithm
PendingCN110430040AReduce power consumptionReduce dynamic power consumptionLogic circuits characterised by logic functionEncryption apparatus with shift registers/memoriesMultiplexingComputer science
The invention provides a message expansion circuit in a low-power-consumption SHA256 algorithm, and belongs to the technical field of digital integrated circuits. The problem that a message expansioncircuit in an SHA256 circuit is too high in power consumption is solved. The technical scheme is as follows: the circuit comprises a message expansion circuit in a low-power-consumption SHA256 algorithm. The message expansion circuit comprises a group of 512-bit message and shift multiplexing registers M, four groups of three-state gates Gate1, Gate2, Gate3 and Gate4, a group of operational logiccircuits and a group of 6-bit comparators P1. The beneficial effects of the invention are that the comparator and the three-state gate turn-off operation circuit are used for input, thereby saving thepower consumption, and achieving the purpose of saving the power consumption.
Owner:WUHAN XINCHANG TECH CO LTD
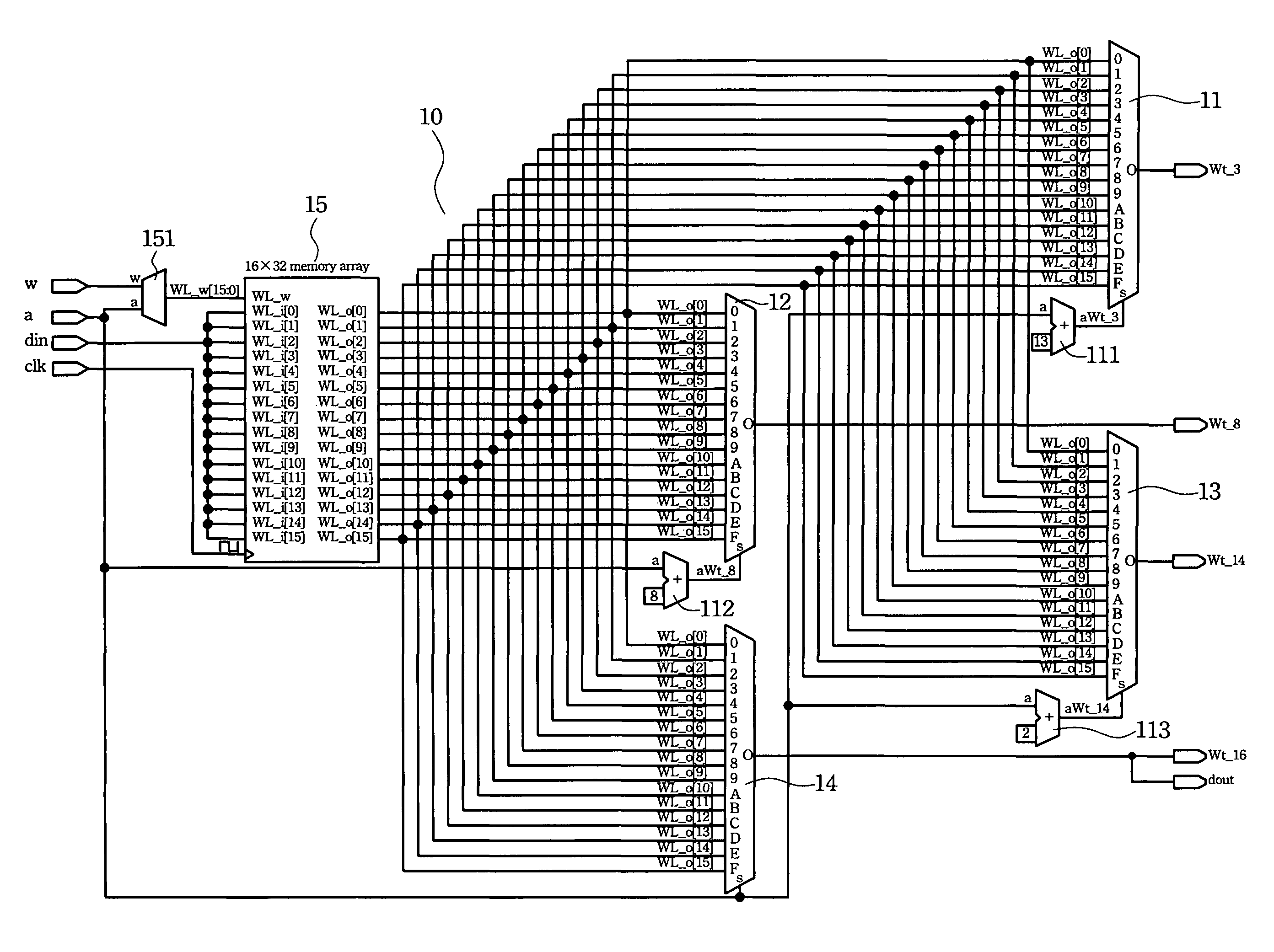
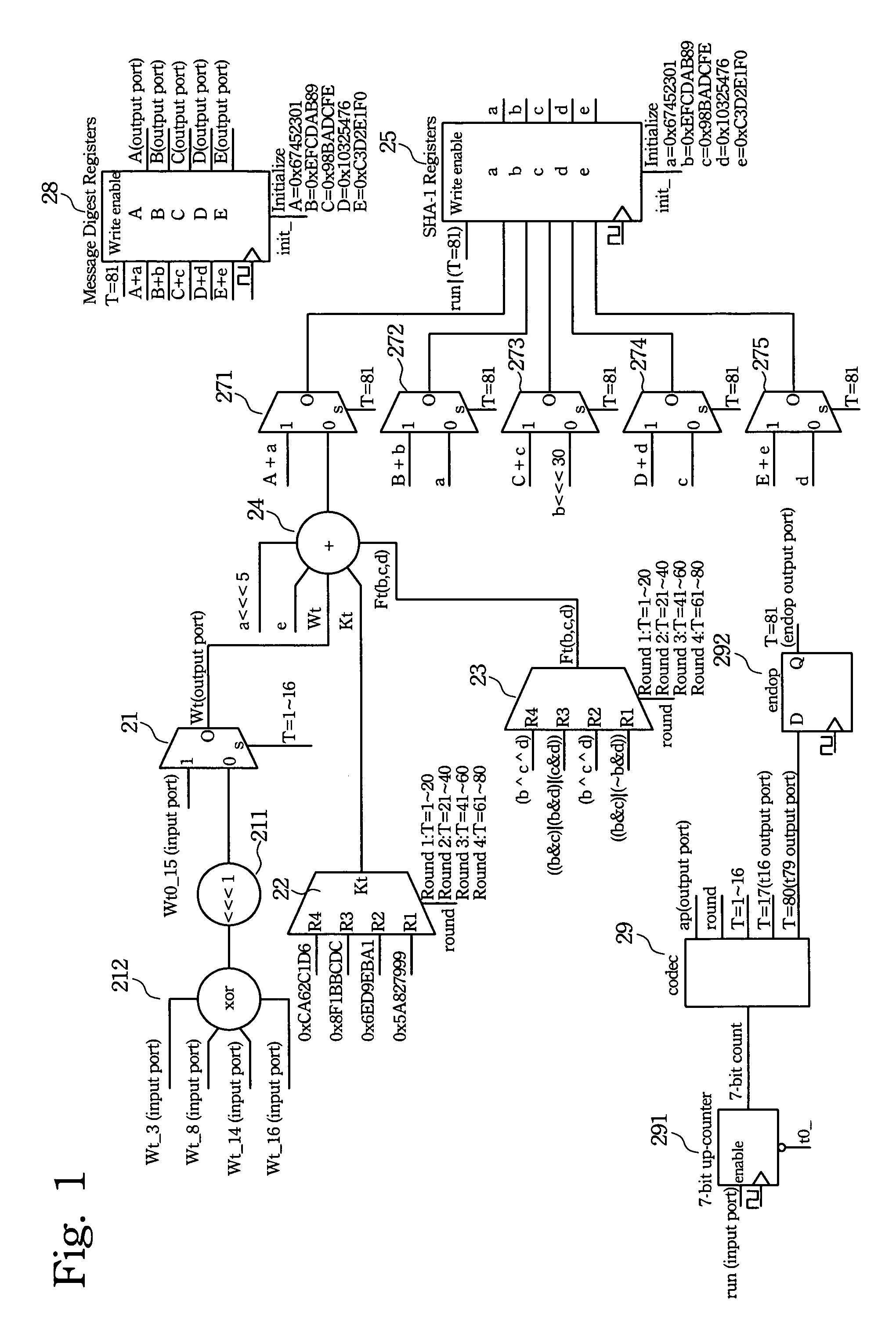
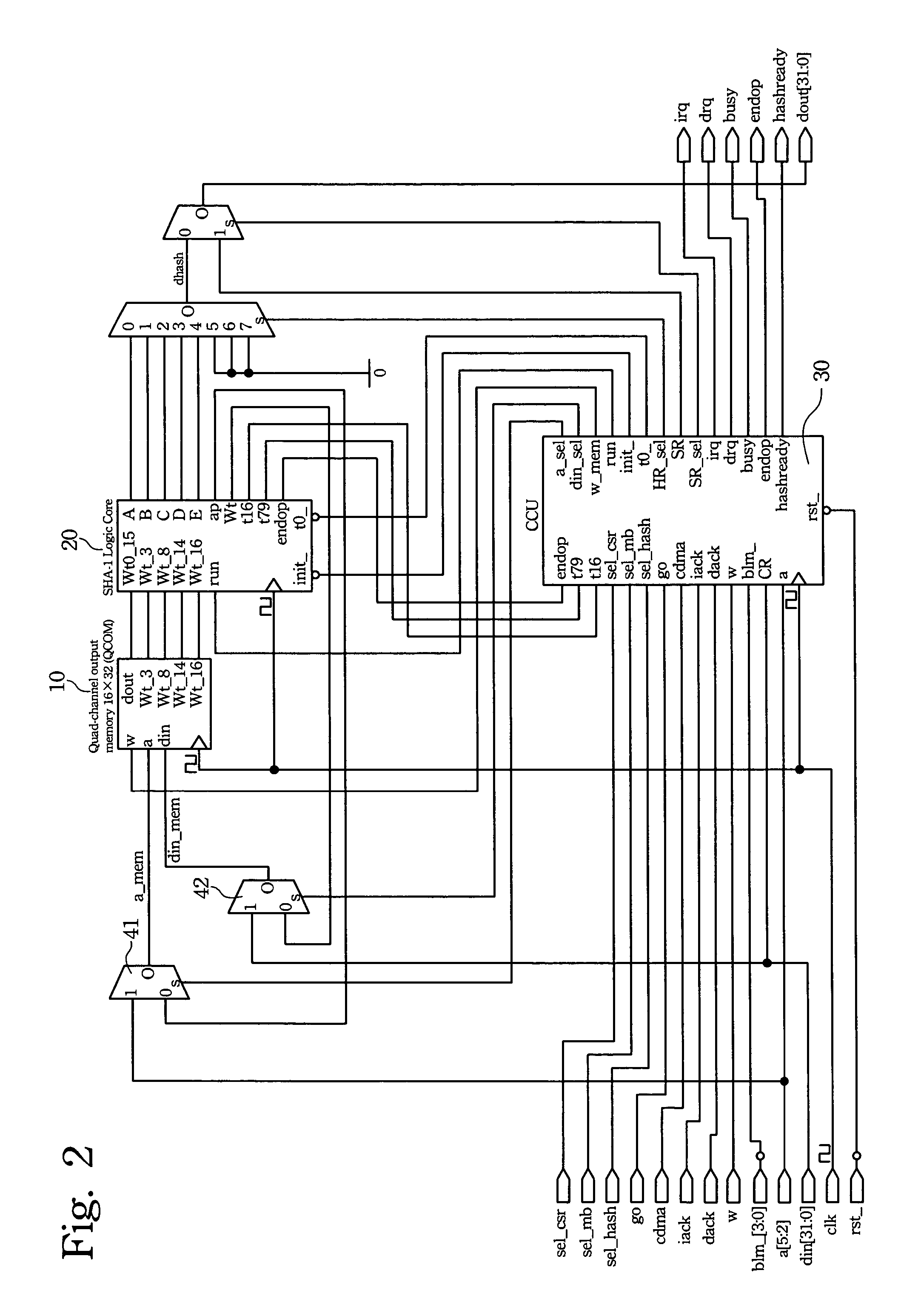
System of efficiently implementing secure hash algorithm (SHA-1) in digital hardware that accomplishes optimal computation speed using minimal hardware resources
ActiveUS8045706B2MinimalMaximum performance of algorithmPublic key for secure communicationUser identity/authority verificationAsynchronous circuitControl selection
A method of completing the Secure Hash Algorithm (SHA-1) computation in exactly 81 clock cycles with digital hardware. The general implementation techniques include: using a combination of synchronous storage elements to store the required computation values and asynchronous circuits to perform all the logic and mathematic operations of each step of the 81-step SHA-1 computation within a single clock cycle; using a quad-output-channel 16×32-bit circular queue memory to store the 512-bit message segment (block), as a computation buffer of the Wt parameter, and to supply the Wt-3, Wt-8, Wt-14, and Wt-16 data parameters simultaneously; using a combination of a counter circuit and a decoder / encoder circuit to control selecting data parameters and sequencing the 81-step SHA-1 computation; and using an automated controller to control internal units that perform SHA-1 and allowing external systems to access the SHA-1 computation service. The robust architecture allows for a highly efficient digital hardware implementation.
Owner:LIU YEN FU
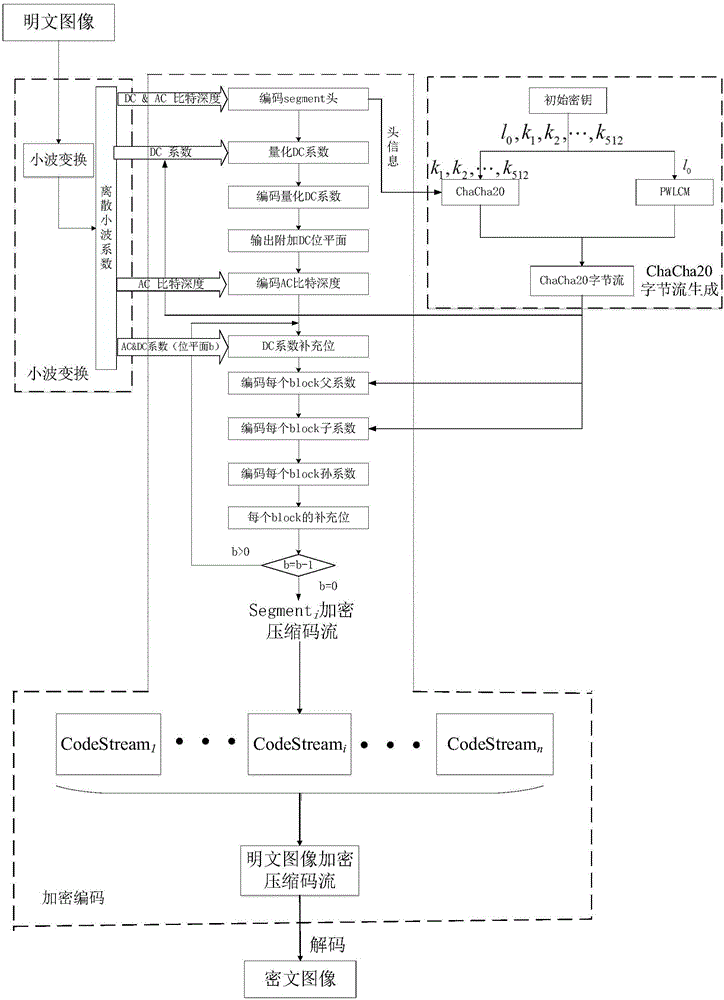
Selective satellite image compression encryption method based on Chacha20 and CCSDS
InactiveCN105704499AIncreased sensitivityHigh encryption strengthDigital video signal modificationPlaintextAc coefficient
The invention provides a selective satellite image compression encryption method based on Chacha20 and CCSDS. Aiming the characteristics of a satellite image, the method comprises the steps: firstly carrying out the three-stage two-dimensional discrete wavelet transformation through employing a 9 / 7 integral wavelet in a CCSDS image compression algorithm, and obtaining a DC coefficient and an AC coefficient after transformation; secondly generating a ChaCha20 initial byte stream through the head information in a coding item and a 512-bit initial secret key and ChaCha20 Hash; thirdly carrying out the summation and modular operation of a chaos initial secret key and a plaintext image normalization value through the byte stream generated by PWLCM (Piecewise Linear Chaotic Map) and the ChaCha20 initial byte stream, and generating a ChaCha20 byte stream; fourthly carrying out the XOR encryption of the ChaCha20 byte stream and the DC coefficient and AC coefficient (the father and son coefficients in each block) and all AC coefficient symbol bites; finally enabling the encrypted DC and AC coefficients to be coded and compressed, and completing the compression and encryption of the satellite image. The generation of the ChaCha20 byte stream is related with the to-be-encrypted satellite image and a compression coding parameter, thereby improving the encryption adaptability.
Owner:NORTHWESTERN POLYTECHNICAL UNIV
BMC-based random number generation method and system
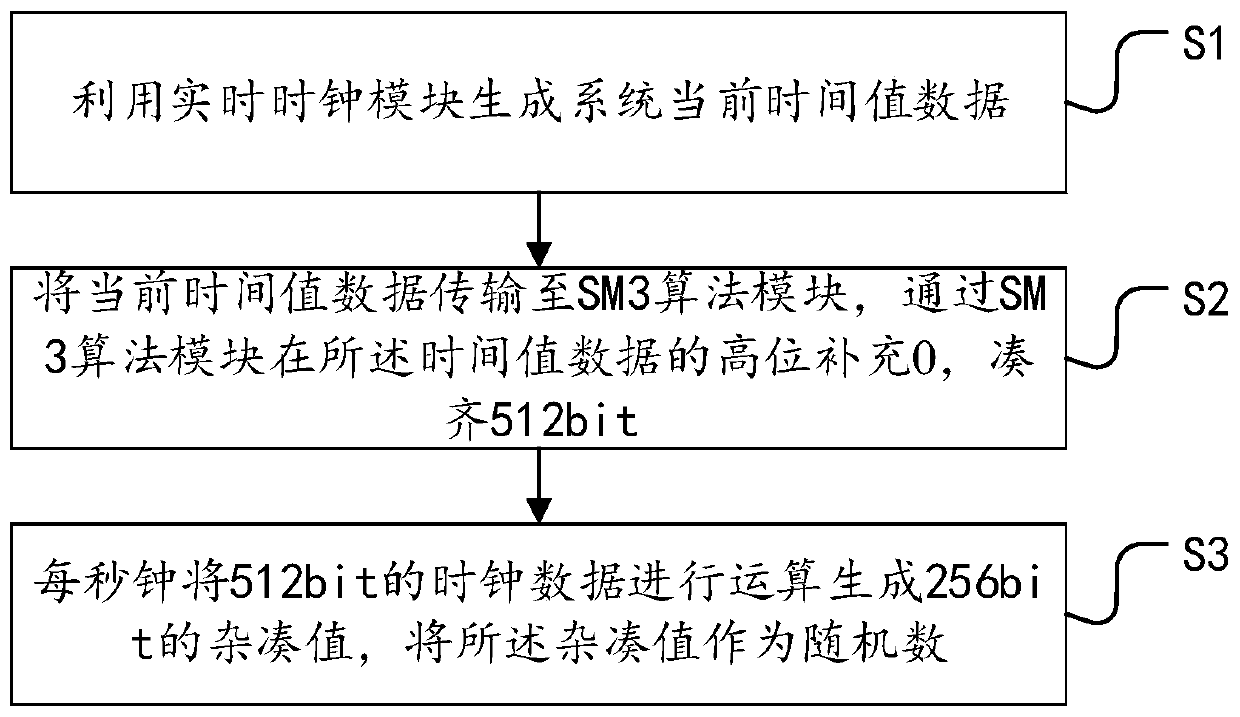
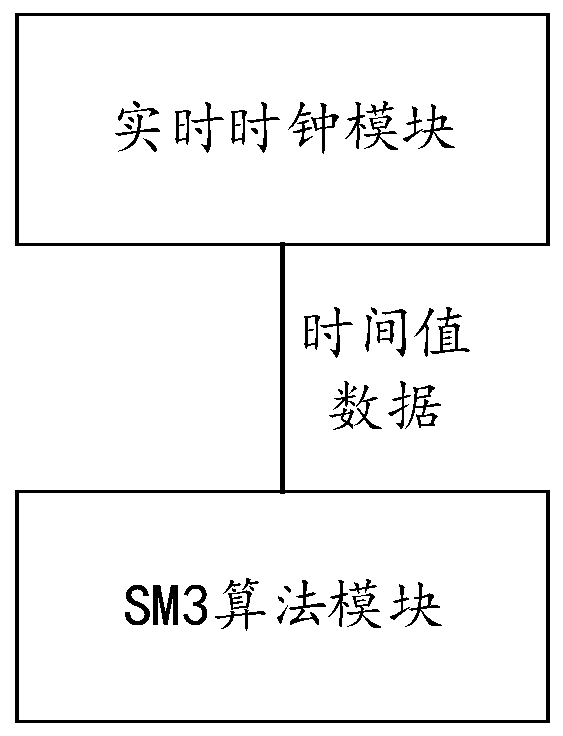
ActiveCN110071793AImprove stabilityMeet the needs of using random numbersKey distribution for secure communicationRandom number generatorsReal-time clockOperability
The invention provides a BMC-based random number generation method and system. The method comprises: S1, generating system current time value data by using a real-time clock module; S2, transmitting the current time value data to an SM3 algorithm module, supplementing 0 at a high position of the time value data through the SM3 algorithm module, and enabling the time value data to reach 512 bits; and S3, carrying out operation on 512-bit clock data per second to generate a 256-bit hash value, and taking the hash value as a random number. According to the method and the system, a random number generation function is realized through a software mode. The system current time value data generated per second by the real-time clock module is transmitted to the SM3 algorithm module. The SM3 algorithm module generates a 32-byte hash value per second as a random number, so that generation of random number is realized, and requirement of using random number by BMC is effectively met. According tothe technical scheme, the generated random number is high in stability, hardware resources of a server mainboard is not occupied, and the system is free of additional cost and is high in operability,and the design flexibility is improved.
Owner:SUZHOU LANGCHAO INTELLIGENT TECH CO LTD
Natural language semantic key generation method based on deep neural network coding
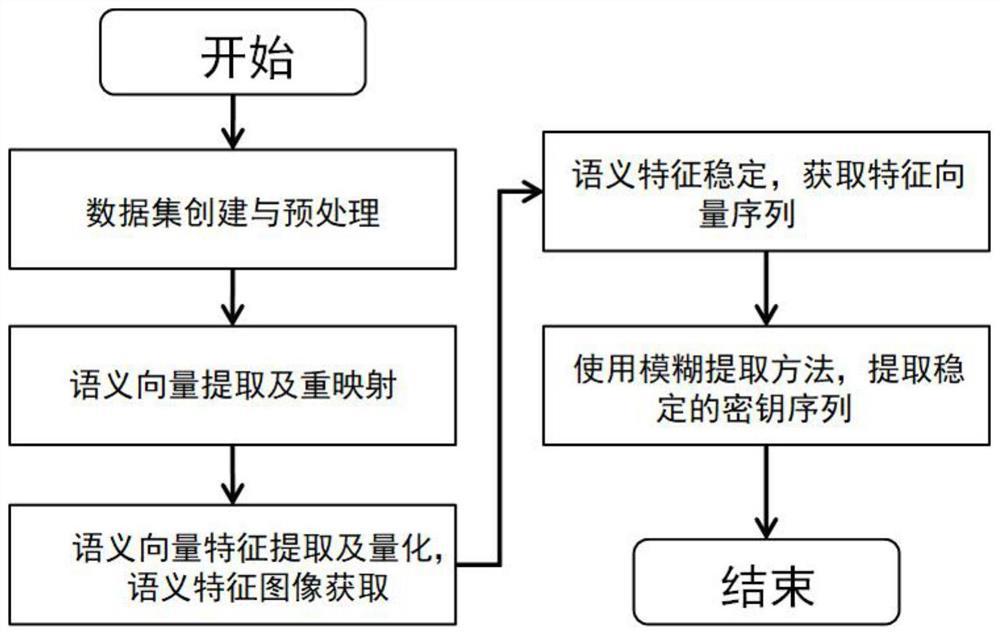
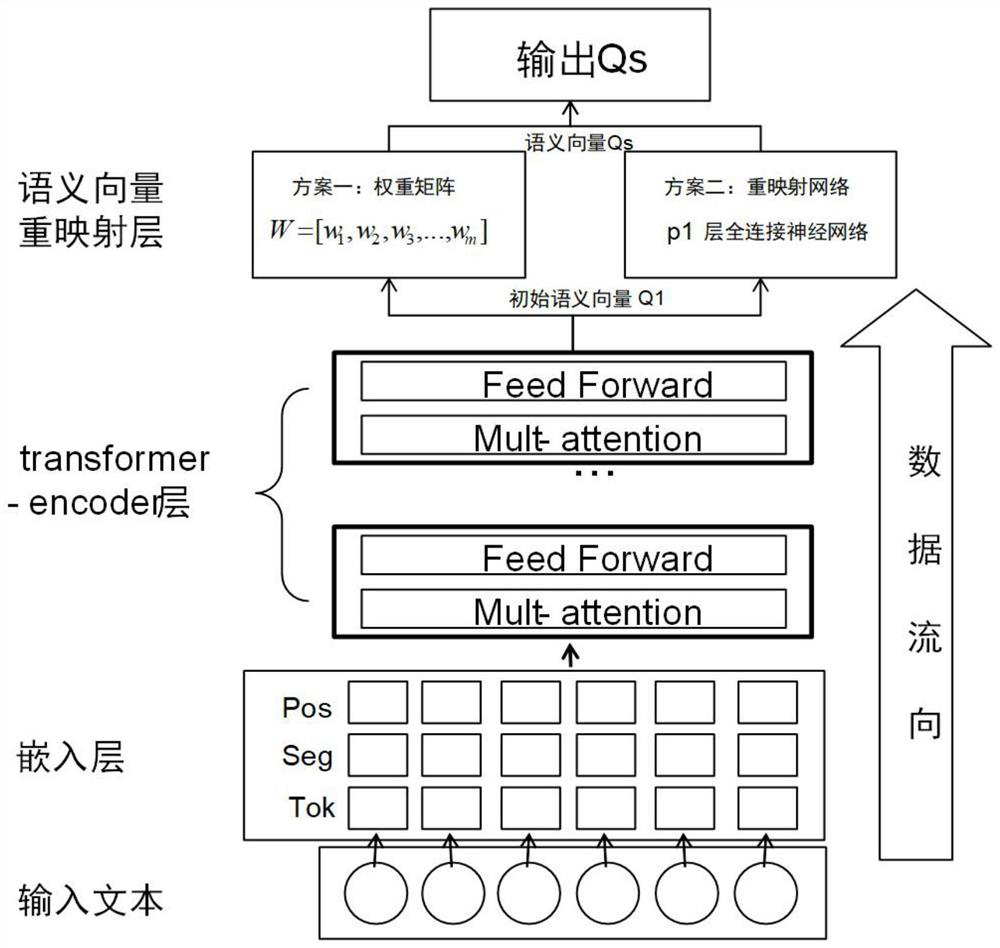
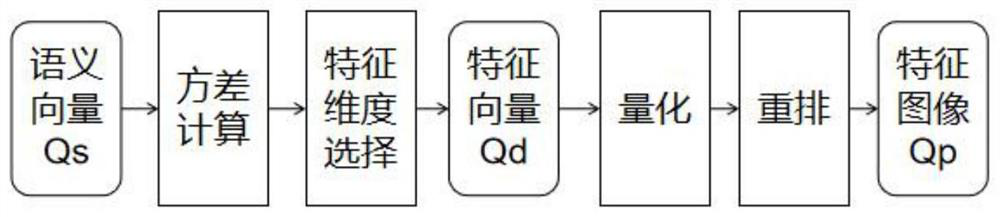
ActiveCN112905991AStability is not affectedImprove security strengthSemantic analysisDigital data authenticationSemantic vectorKey size
The invention discloses a semantic key generation method based on natural language semantic similarity. According to the method, a text with a certain elastic range is used as a password, a text semantic vector is extracted by using a deep neural network model, and the semantic vector is recoded through a deep neural network to generate a key. In the authentication process, the input natural language text does not need to be matched with the original text one by one, and the same key can be generated to complete the authentication process as long as the semantics of the input natural language text is similar to that of the original text. In the process, a user does not need to memorize an original text in a one-word-free manner, and only needs to basically memorize short text semantics and formats, the memories can be described through a natural language, a secret key is generated, and authentication is completed. According to the method, the risk of privacy leakage of biological feature template authentication does not exist, and meanwhile, a user can generate a high-security key (>512 bit length) and the security and the flexibility of the authentication process are improved.
Owner:HANGZHOU DIANZI UNIV
Amplitude phase precision adjustable attenuation phase shift architecture
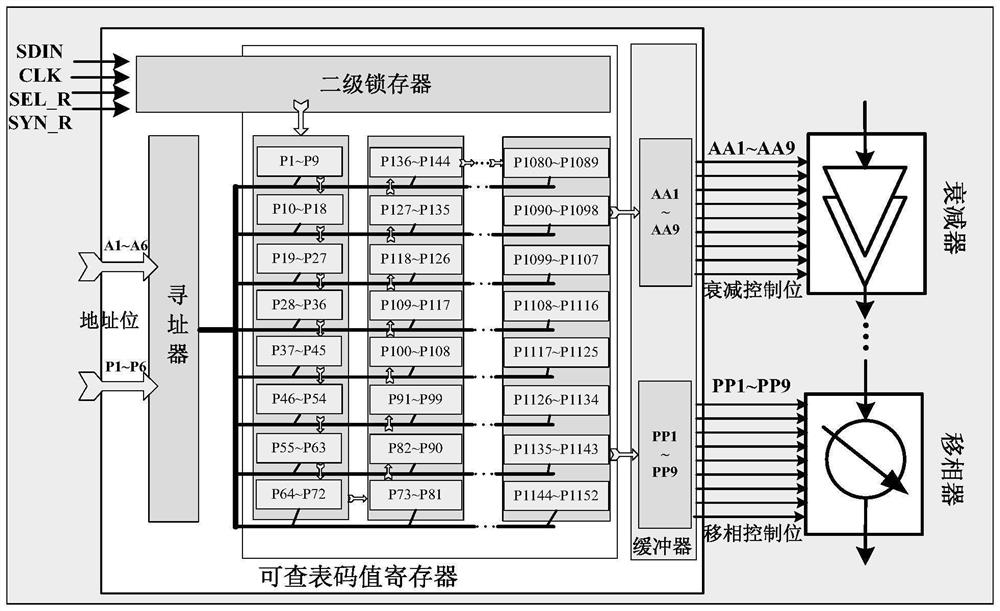
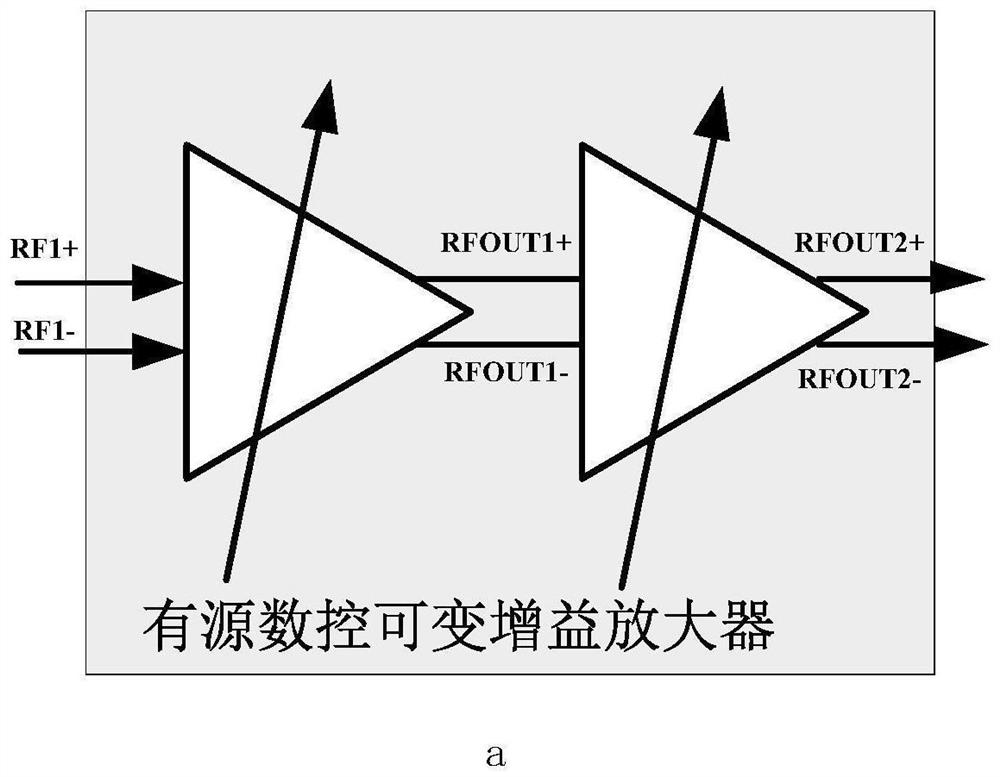
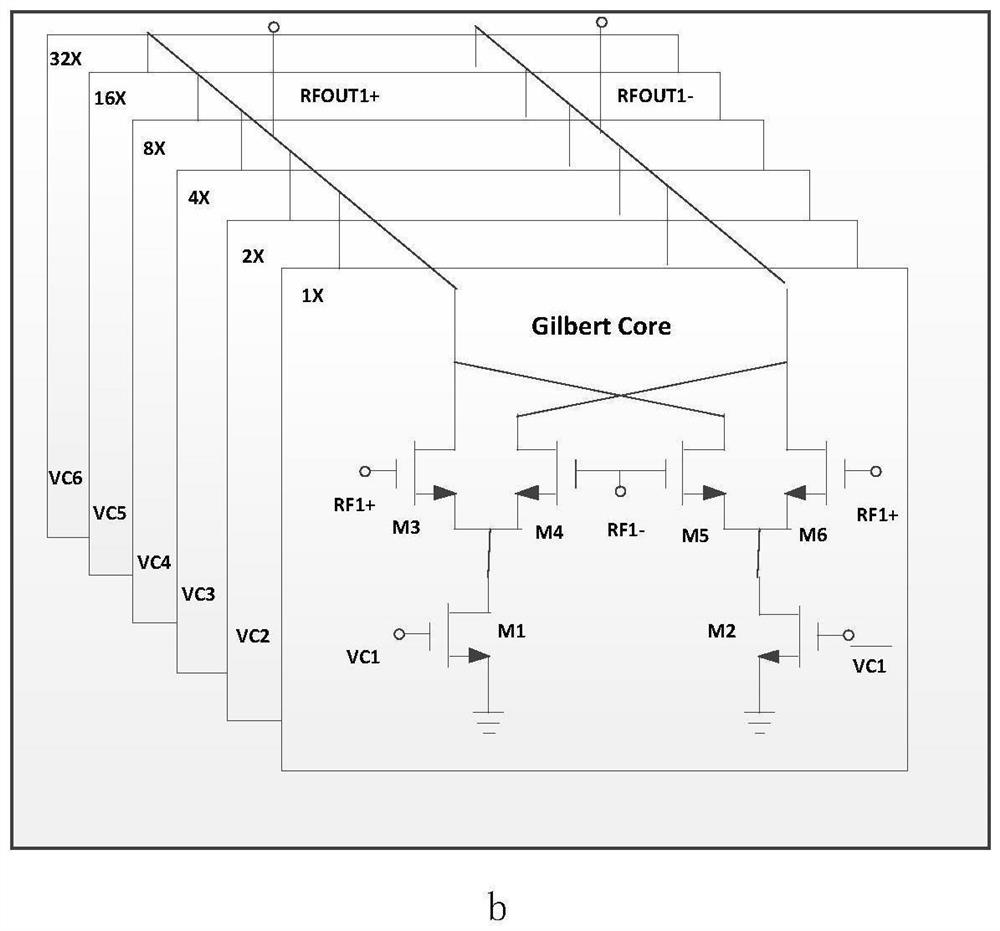
ActiveCN114665908ARealize tuning optimizationImproved amplitude and phase accuracyTransmissionHigh level techniquesNumerical controlSystem requirements
The invention, which belongs to the technical field of chip circuit design, discloses an amplitude-phase precision adjustable attenuation phase shift architecture comprising an active numerical control attenuator, an active numerical control phase shifter, and a table look-up code value register. According to the invention, under the background that an external system requires 6-bit attenuation and 6-bit phase shift, the direct attenuation bit number and the phase shift bit number are respectively increased to 9 bits, so that further improvement of the amplitude-phase precision becomes possible; in addition, based on the architecture, under the condition that the system complexity and the write-in data time of the power-on table look-up code value register are allowed, the 9-bit direct control bit can still be further increased; along with the increase of direct control bits, corresponding attenuation and phase shift phases are respectively increased to 512 bits from original 64 bits, and each attenuation state and each phase shift state can be selected from a plurality of states under the condition that external 6-bit control bits are not changed. Different code values can be written into a table look-up code value register to realize on-chip adjustment and optimization of an amplitude-phase multifunctional chip according to index requirements of different attenuation phase shift precisions of a system.
Owner:CHINA ELECTRONIC TECH GRP CORP NO 38 RES INST
A web resource encryption method, device and storage medium
The invention discloses a webpage resource encryption method, device and storage medium. The method includes: receiving a webpage resource request instruction sent by a browser; according to the webpage resource request instruction, converting the webpage resource corresponding to the webpage resource request instruction into a first waiting Encrypt the sequence, and add a random number before the first sequence to be encrypted to obtain the second sequence to be encrypted as a binary sequence; perform source processing on the second sequence to be encrypted to obtain the third sequence to be encrypted; based on the weighted probability model Encode the encrypted sequence three times to obtain the ciphertext, and the weight coefficient of the weighted probability model is implanted with a binary password and the binary password is greater than or equal to 512 bits; the ciphertext is sent to the browser so that the browser can process the ciphertext according to the weighted probability model The ciphertext is decoded, and the browser can detect the decoding result based on the result of the information source processing. The invention can not only realize encryption and decryption of webpage resources, but also effectively protect the security of encrypted webpage resources.
Owner:HUNAN YAOSHENG COMM TECH CO LTD
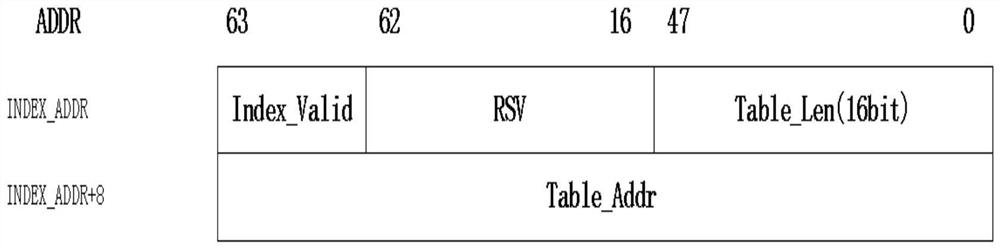
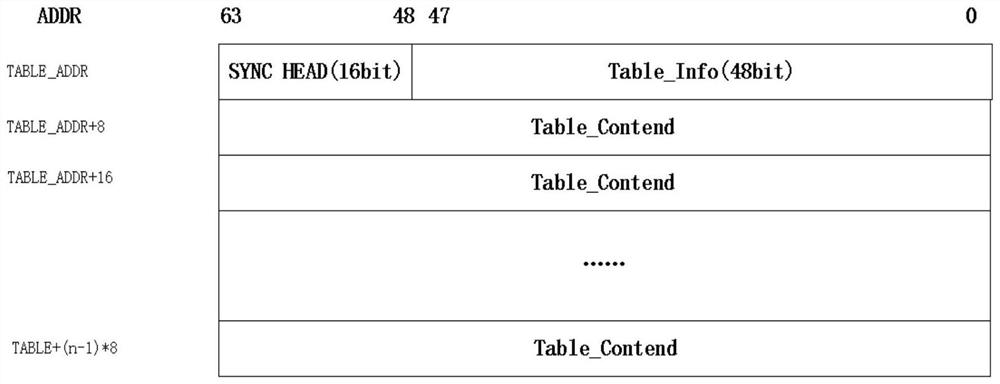
Rapid table refreshing method based on hardware DMA
PendingCN114679381ASolve the shortcoming of long power-on initialization timeQuick refreshTransmissionEnergy efficient computingDatasheetDirect memory access
The invention relates to the related technical field of network exchange, in particular to a rapid table refreshing method based on hardware DMA (direct memory access), which comprises the following steps: firstly, constructing a descriptor space and a data space in a memory, filling descriptor table items in the descriptor space, filling data table items in the data space in a message manner, and storing information of the data table items in the descriptor table items; then informing the DMA of the index address of the descriptor table item, initiating a read operation by the DAM through the index address to obtain the descriptor table item, and extracting a corresponding data table item message according to information in the descriptor table item; and finally, analyzing the data table item message to obtain configuration information, recombining the configuration information, and writing the recombined configuration information into a corresponding table item RAM (Random Access Memory) through a configuration interface to complete table item configuration. According to the method and the device, the burden of a CPU (Central Processing Unit) can be reduced, table entries with any bit width of 64-512 bits can be flexibly configured through setting, and the table refreshing time is greatly saved due to the adoption of a pure hardware mode.
Owner:芯河半导体科技(无锡)有限公司
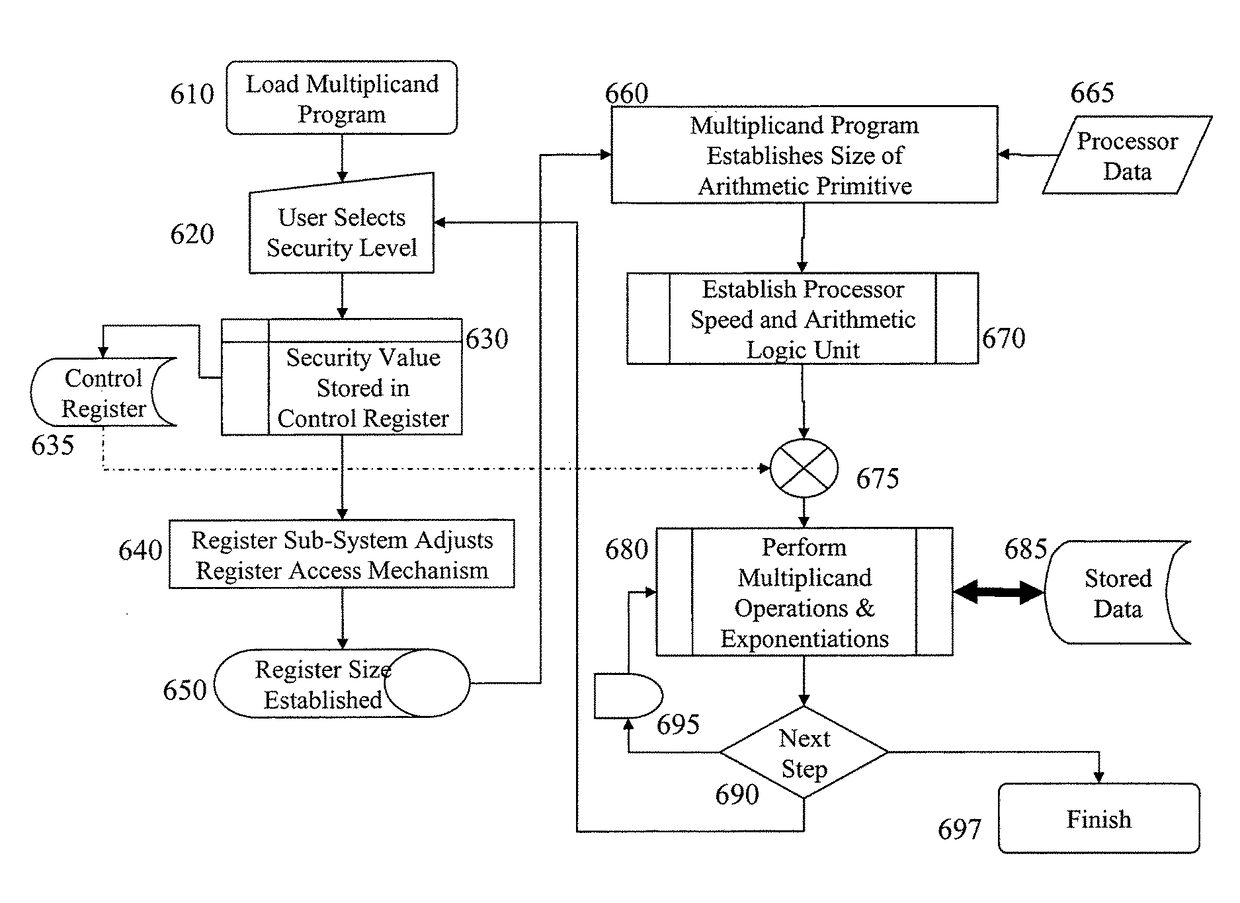
Flexible architecture for processing of large numbers and method therefor
ActiveUS9860055B2Encryption apparatus with shift registers/memoriesPublic key for secure communicationGeneral purposeProcessor register
A method of implementing large number multiplication and exponentiation is provided upon a general purpose microprocessor. These large number multiplication and exponentiation processes being common to cryptography standards such as RSA and AES that typically employ numbers with 512-bits, 1024-bits, and 2048-bits. According to the invention the method establishes the size of the large number processes according to value stored within a control register, this control register and other registers storing data are configured according to this value and accessed as N-bit registers (i.e. as 1024-bit registers for 1024-bit encryption. Additionally, the multiplication and exponentiation processes are handled according to the size of an arithmetic primitive, which is established according to the hardware configuration upon which the process is operating. As such the invention allows for an encryption process to adjust both to the configuration of the host microprocessor and supporting hardware / firmware and dynamically according to degree of security determined from the value stored within the control register.
Owner:SYNOPSYS INC
High efficiency preambles for communications systems over pseudo-stationary communication channels
InactiveCN102150403BBaseband system detailsBroadband local area networksCommunications systemPreconditioner
One method includes appending a preamble to a data packet and sending the preamble and data packet over a communication channel in a network. The preamble can be a beacon, permission, broadcast or high-throughput preamble. The beacon preamble includes the following symbols SS, SS, SS, SS, SS, SS, SS, SS, SS, SS, SS, SS, LS1, LS1, LS1, LS1, LS1, LS1, LS1, LS1, CP0, CEBeacon , CE Beacon. The License Preamble includes the following symbols SS, SS, SS, SS, SS, SS, SS, SS, SS, SS, SS, SS, LS1, LS1, LS1, LS1, LS1, LS1, LS1, LS1, CP0, CE, CE. The broadcast preamble includes the following symbols LS1, LS1, LS1, LS1, CP0, CE, CE. The high-throughput preamble includes the following symbols CP0, CE. SS symbols consist of 64 bits, LS1, LS2 and CP0 symbols consist of 192 bits, CE symbols consist of 512 bits, and CEBeacon symbols are a subset of CE.
Owner:ENTROPIC COMM INC
Method for obtaining safe information abstract in authentication header
InactiveCN101872338BImprove efficiencyImprove securityTransmissionComplex mathematical operationsMessage processingBinary strings
The invention relates to a modified SHA-1 hash algorithm. The existing SHA-1 harsh algorithm has low security. The invention firstly adds a 1, a plurality of 0 and a 64-bit binary string after the information to be processed, then enlarges and groups the information, so the original 512-bit group is changed into a 1024-bit group and a register value is initialized; then a main cycle is utilized to sequentially process each group, the main cycle totally has four operations, and each operation contains logical function and compression function processing; and finally, after the processing of all the groups is completed, 160-bit message digest is output, and when the message digest is transferred, the message to be transferred is added with a safety hashed value. Through the algorithm of theinvention, the original SHA-1 algorithm has more safety on message processing, and through modifying the logical function expression and the compression function logical structure of the algorithm, the efficiency of the SHA-1 algorithm is improved.
Owner:HANGZHOU DIANZI UNIV
Rapid Montgomery modular multiplier optimization component suitable for national cryptographic sm2p256v1 algorithm
InactiveCN109933305AReduce Design ComplexityImprove computing efficiencyInternal/peripheral component protectionComputations using residue arithmeticTemporary variableModular multiplier
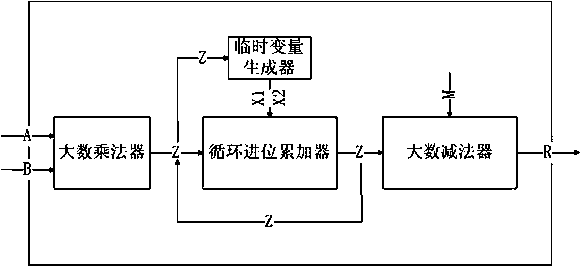
The invention discloses a rapid Montgomery modular multiplier optimization component suitable for a national cryptographic sm2p256v1 algorithm. The component includes a large number multiplier, a temporary variable producer, a cyclic carry accumulator and a large number subtracter. A large integer A and a large integer B with the bit width of 256 bit are input and processed by the large number multiplier to obtain a large integer Z with the bit width of 512 bit. Temporary variables X1 and X2 are generated through Z, and then the temporary variables X1 and X2 and Z are subjected to carry accumulation operation for eight times. A result Z obtained by carry accumulation of each time is used as an input of the carry accumulator and the temporary variable generator, if Z is greater than or equal to a large integer constant M after eight carry accumulation operations are completed, a large number subtraction operation is performed on M and Z once, otherwise, directly a result of eight timesof the cyclic carry accumulator is output.
Owner:成都三零嘉微电子有限公司
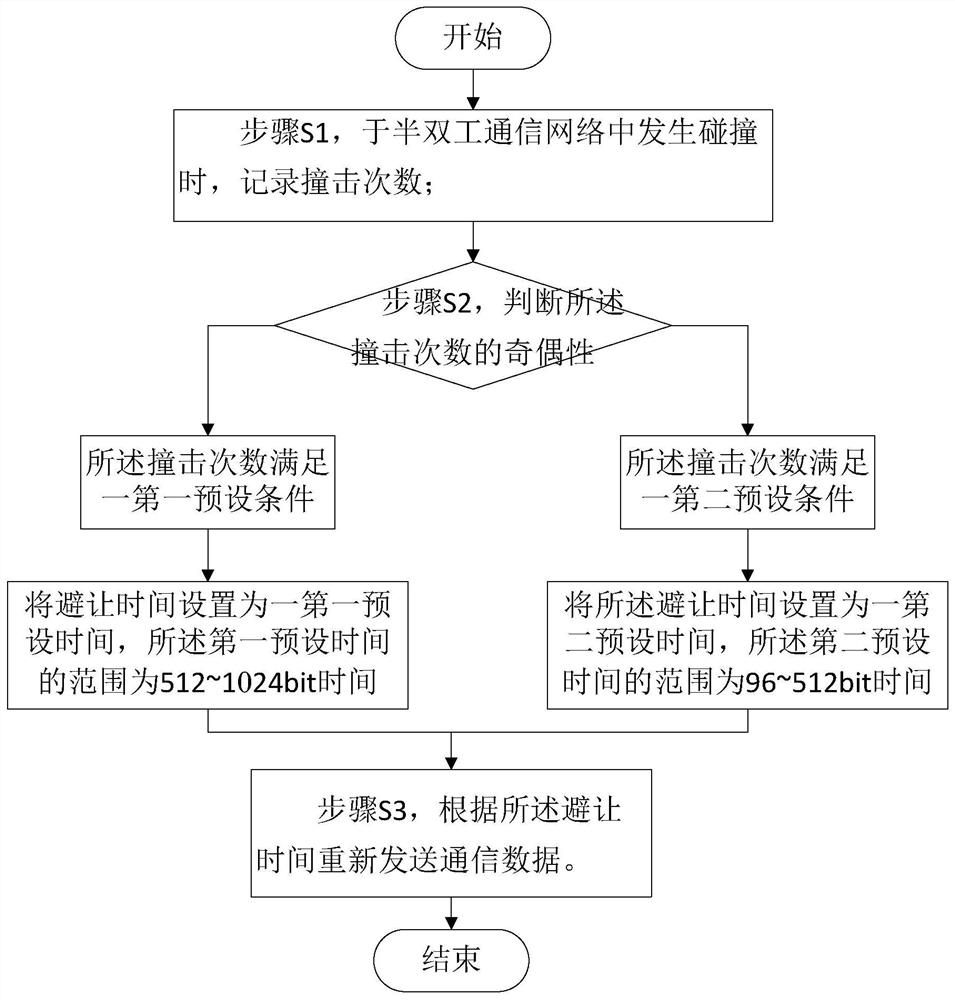
Ethernet half-duplex retransmission method and system
PendingCN113794546AIncrease profitReduce the number of collisionsError prevention/detection by using return channelDuplex signal operationEngineeringData transmission
The invention discloses an Ethernet half-duplex retransmission method and system, and belongs to the technical field of communication. The method comprises the steps of: S1, recording the number of collision times when collision occurs in a half-duplex communication network; S2, judging the parity of the impact times, namely if the impact times meet a first preset condition, setting avoidance time as first preset time and setting the range of the first preset time to be 512-1024 bit time, and if the number of impact times meets a second preset condition, setting the avoidance time to be second preset time and setting the range of the second preset time to be 96-512 bit time; and S3, resending communication data according to the avoidance time. The Ethernet half-duplex retransmission method has the beneficial effects that when collision occurs, through parity judgment of collision times and configuration of the avoidance time, the situation that a bus is continuously occupied by a certain end due to poor quality of a random mechanism of the certain end is avoided, the number of collision times is reduced, continuous data transmission on a communication line can be basically maintained, and the utilization rate of the line is improved.
Owner:SUZHOU MOTORCOMM ELECTRONICS TECH CO LTD
A method for establishing secure communication in a social network group
InactiveCN103051457BSpecial service provision for substationUser identity/authority verificationHash functionAttack
The invention discloses a method for establishing safety communication of network groups. The method comprises the following steps of: processing long-term secret data and authentication information of group communication members by using an SHA (Secure Hash Algorithm) safety hash function which is 512 bits in length; and distributing a key by using an interpolation polynomial according to a secret partition threshold scheme of Shamir to keep a group key fresh, confidential and authenticable and effectively resist external attacks and internal attacks. According to the invention, all information is transmitted on a public channel, so that the method has the characteristics of low calculation amount, high running speed and high server calculation efficiency.
Owner:GUILIN UNIV OF ELECTRONIC TECH
Bit mapping method and sending device thereof
The present invention proposes a New Radio Physical Broadcast Channel (NR-PBCH) bit mapping method to improve NR-PBCH decoding performance under polar codes. NR‑PBCH carries 32 information bits and 24 CRC bits. Specifically, NR‑PBCH uses a 512-bit polar code to carry a total of 56 data bits. Different polar code bit channels have different channel reliability. As a general rule, the most reliable polar code bit channel is used for the 56 data bits. According to a novel aspect, within the 32 NR‑PBCH information bits, some information bits are known to the decoder under certain conditions and are thus placed in the least reliable polar code bit positions. As a result, by correctly mapping NR‑PBCH data bits at the input bit positions of polar codes, NR‑PBCH decoding performance is improved when a priori known bits are available.
Owner:MEDIATEK INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com