Natural language semantic key generation method based on deep neural network coding
A deep neural network and natural language technology, which is applied in the field of semantic feature extraction based on deep neural network and key generation based on semantic features, and semantic key generation based on natural language semantic similarity, which can solve the difficulty of guaranteeing user privacy and security, etc. problems, to achieve the effect of improving security strength, increasing security, and reducing difficulty
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0022] The technical solution of the present invention will be described in detail below with reference to the accompanying drawings.
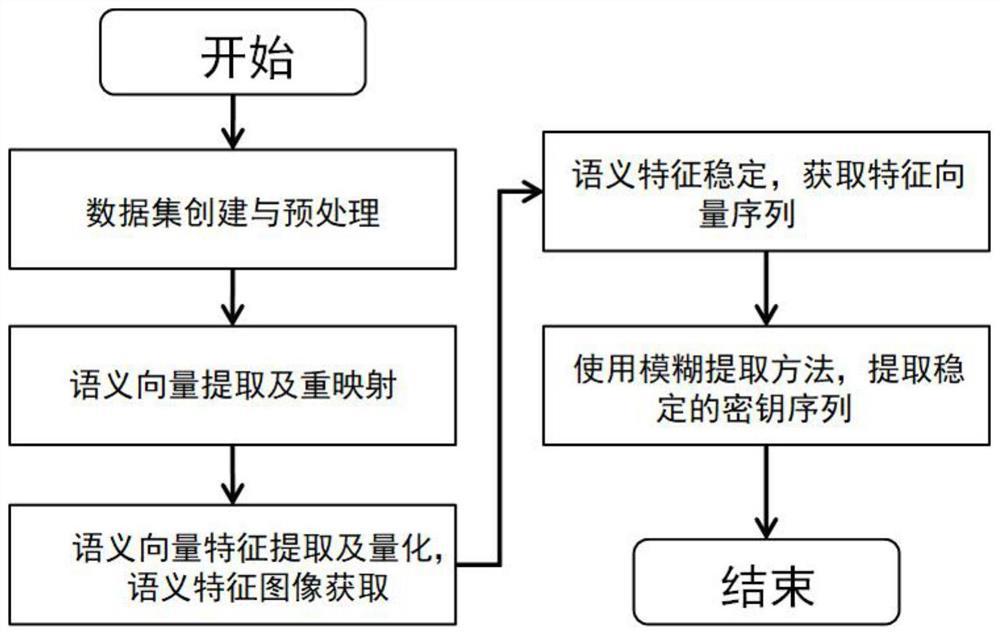
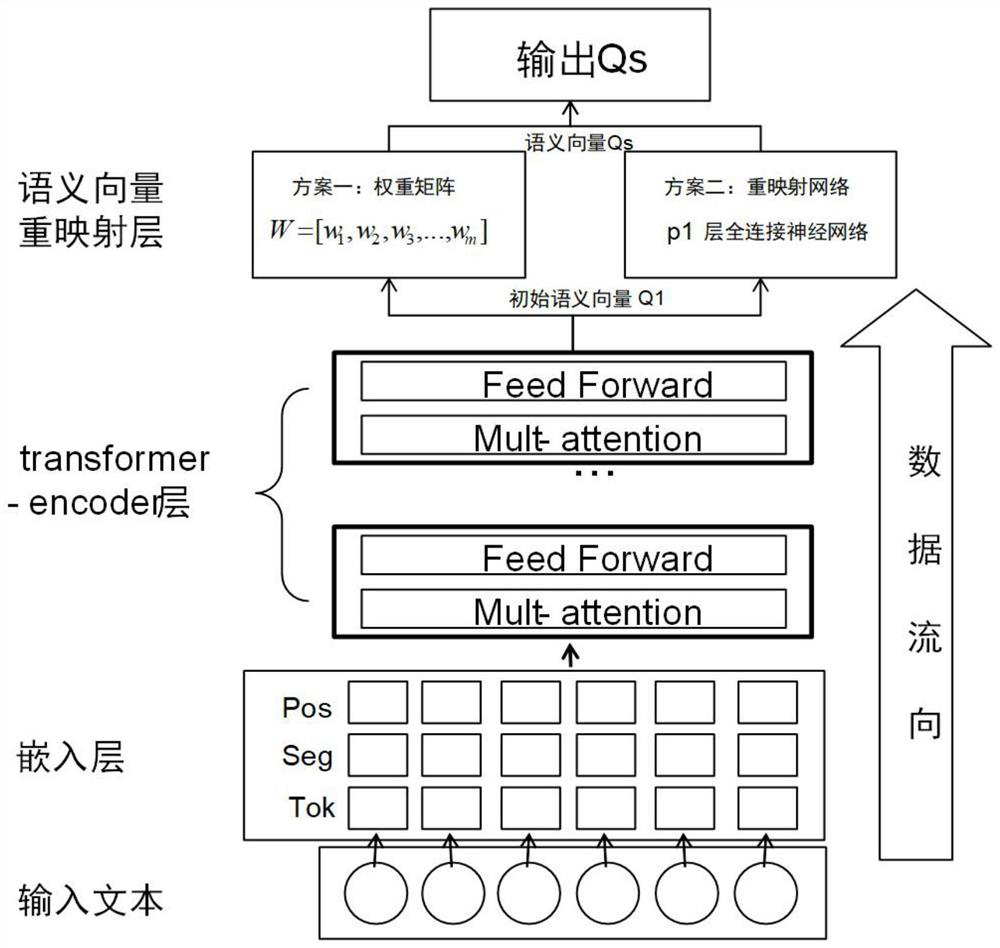
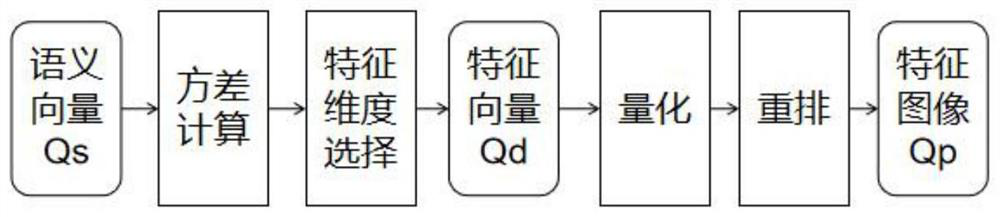
[0023] Refer figure 1 , figure 2 with image 3 , A text-semantic key generation technology, including the following steps:
[0024] Step (1), construct a natural language short-key training language library with a category tag, as the training data set L1.
[0025] Traditional semantic classification tasks are simply similar, or the statements of the same topics are used as the same class. In order to be able to more accurately separate semantically unsatisfactory statements, it is necessary to construct a textual key training data set. Each category is different but the semantics is the same, and the number of each category statement reaches N1, N1 ≥ 50; Semantic key training data sets each statement is labeled with the category tag. During the training, enter the statement in the data set, and output the category belonging to this statement.
[0...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com