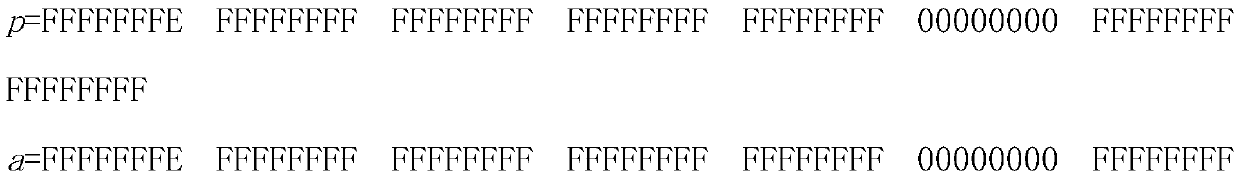Rapid Montgomery modular multiplier optimization component suitable for national cryptographic sm2p256v1 algorithm
An algorithm and fast technology, applied in the field of information security, can solve problems such as high time complexity, high power consumption, and high hardware design complexity, and achieve the effects of improving computing efficiency, reducing manufacturing costs, and reducing multiplier resources
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0022] The present invention will be further described, but the protection scope of the present invention is not limited to the following.
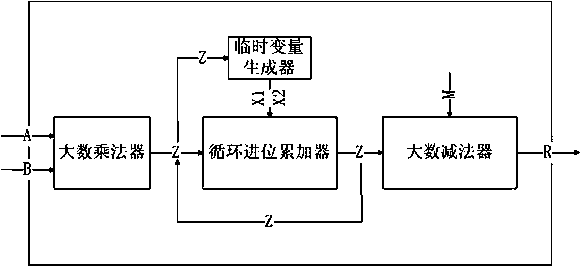
[0023] Such as figure 1 As shown, the fast Montgomery modular multiplier optimization components suitable for the national secret sm2p256v1 algorithm include: large number multiplier, temporary variable generator, circular carry accumulator and large number subtractor, input bit width of 256bit large integer A and B obtains a large integer Z with a bit width of 512bit through the large number multiplier, generates temporary variables X1 and X2 through Z, and performs 8 carry-accumulation operations with Z. The result Z obtained by each carry-accumulation is then used as a carry accumulator and The input of the temporary variable generator, after the completion of 8 carry-accumulation operations, if Z is greater than or equal to the large integer constant M, then M is subtracted from Z with a large number, otherwise the result of the 8-fold c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com