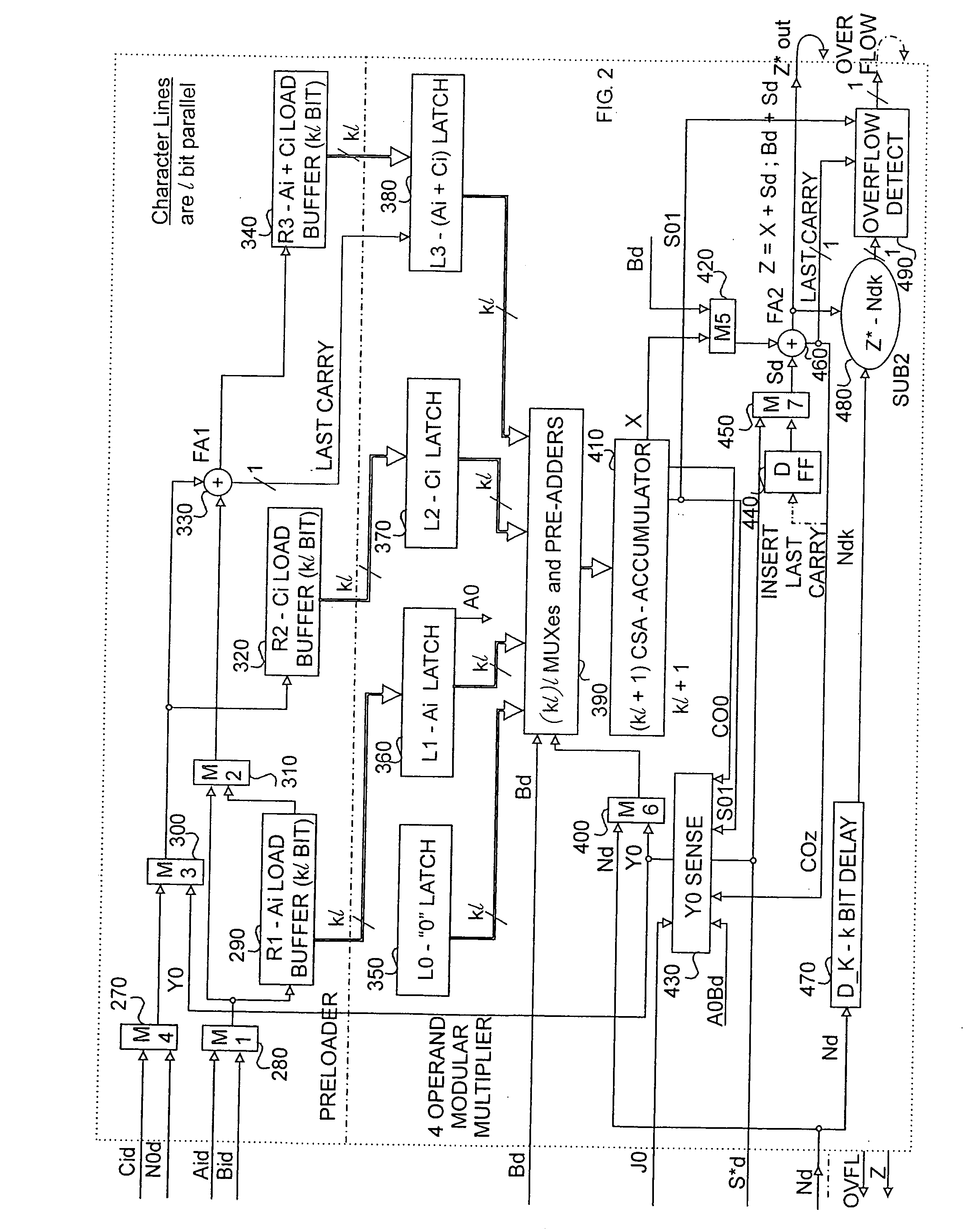
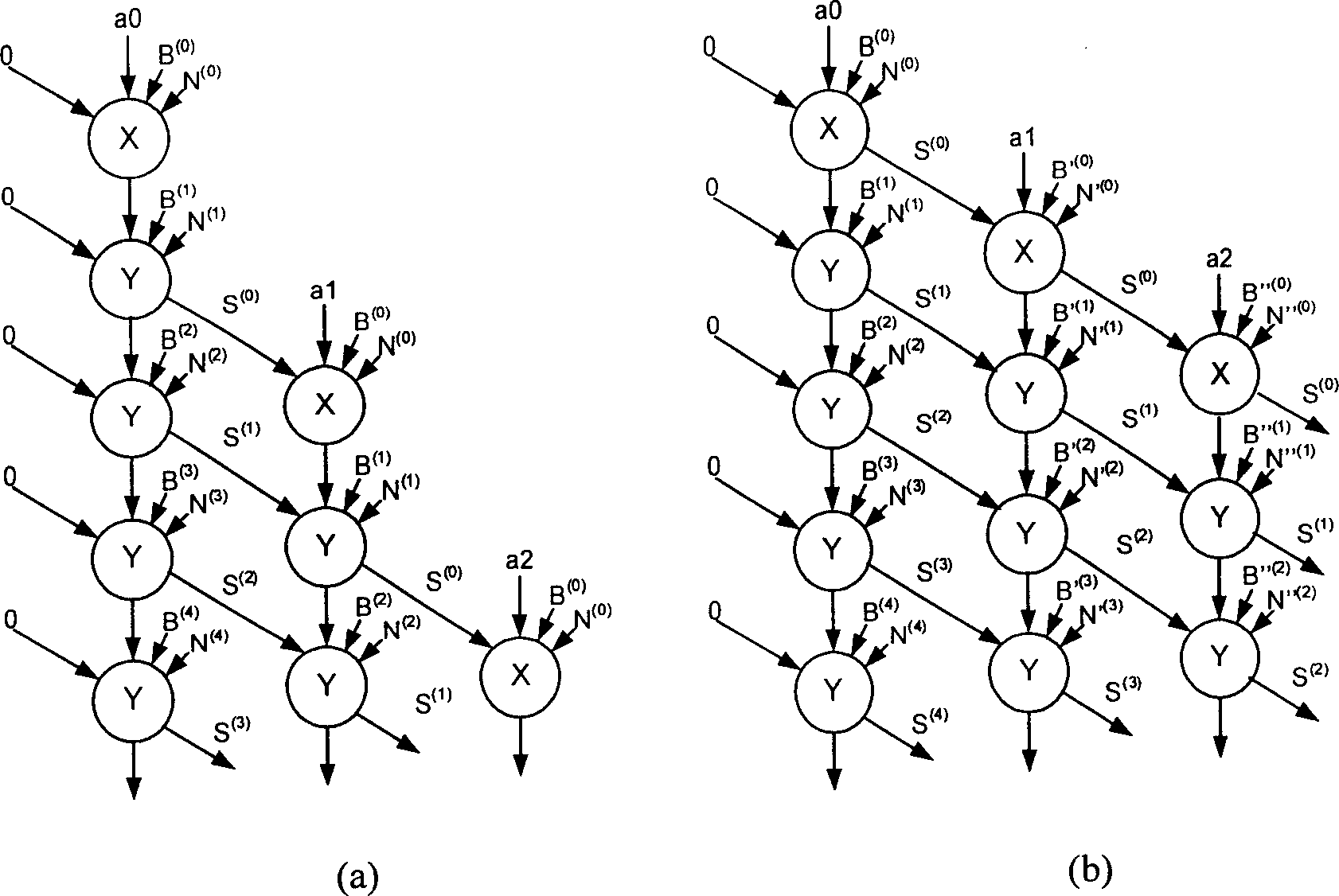
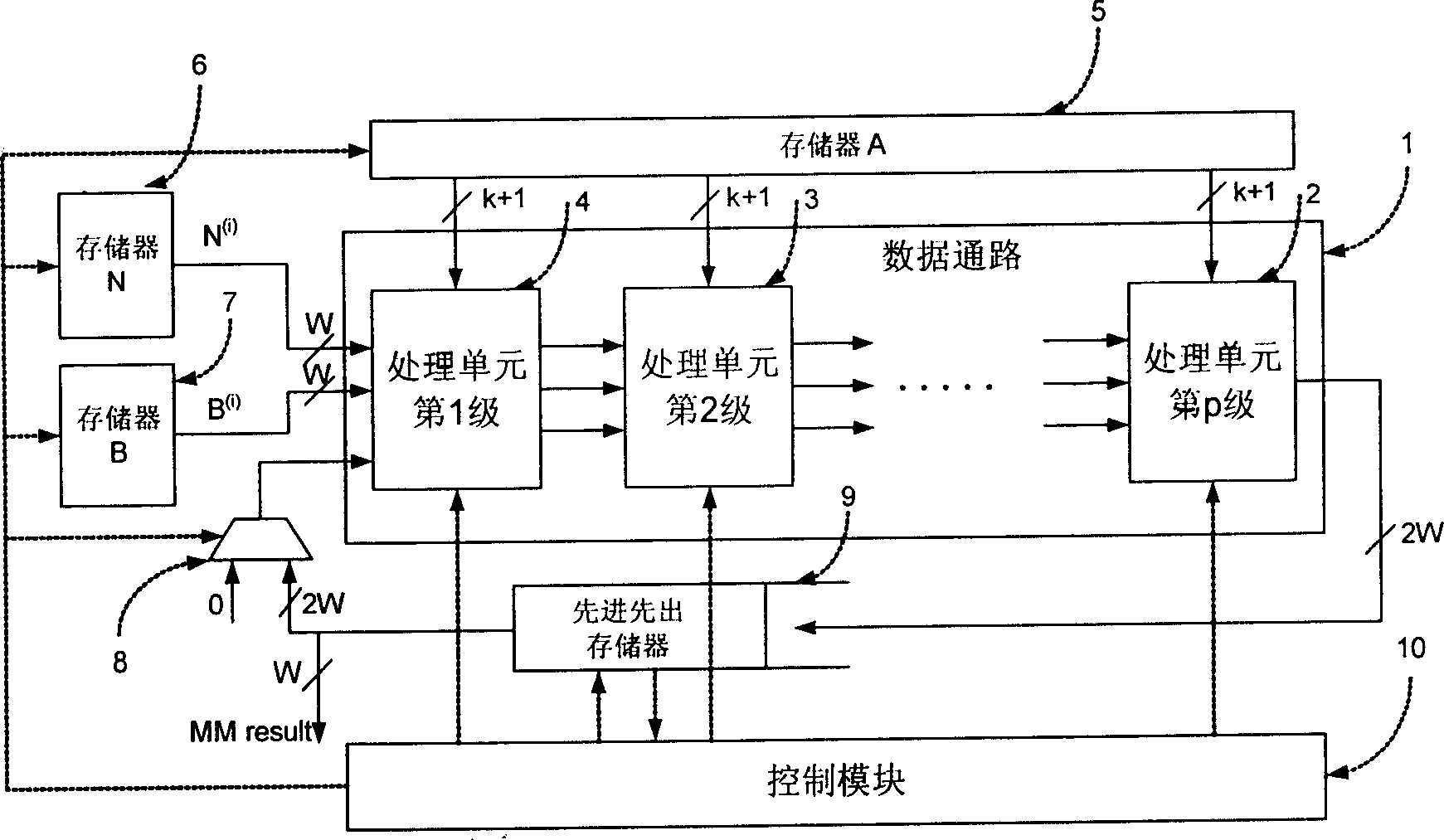
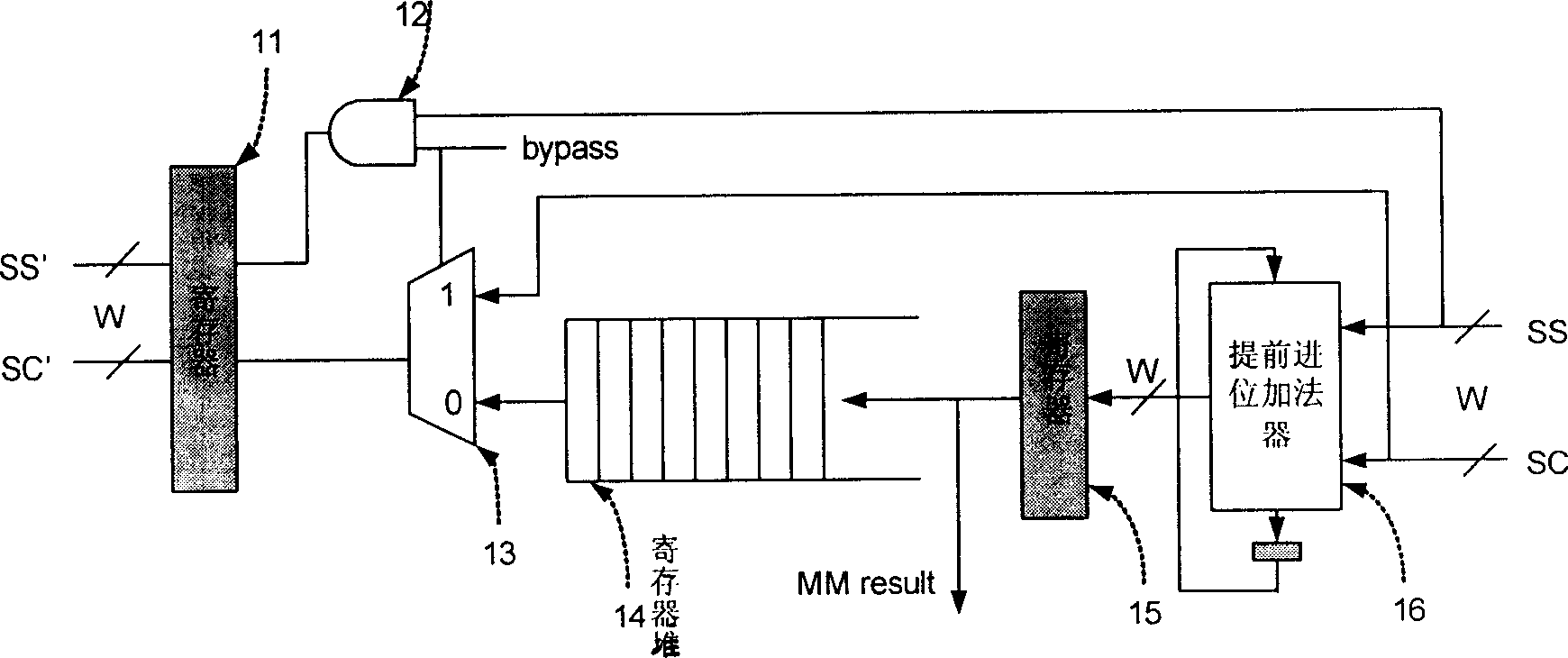
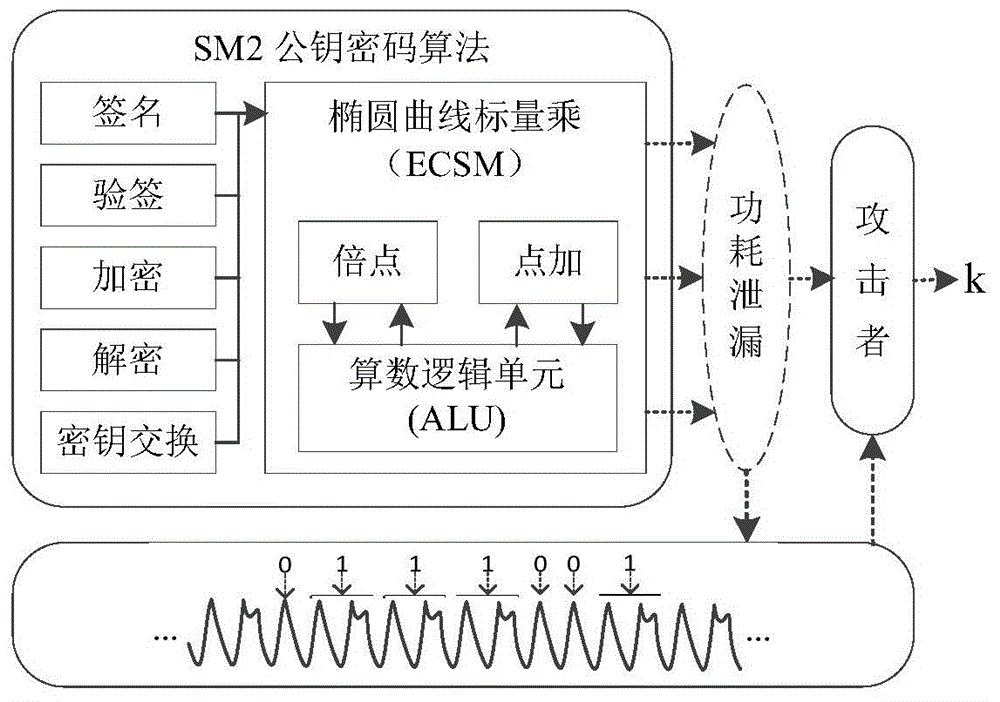
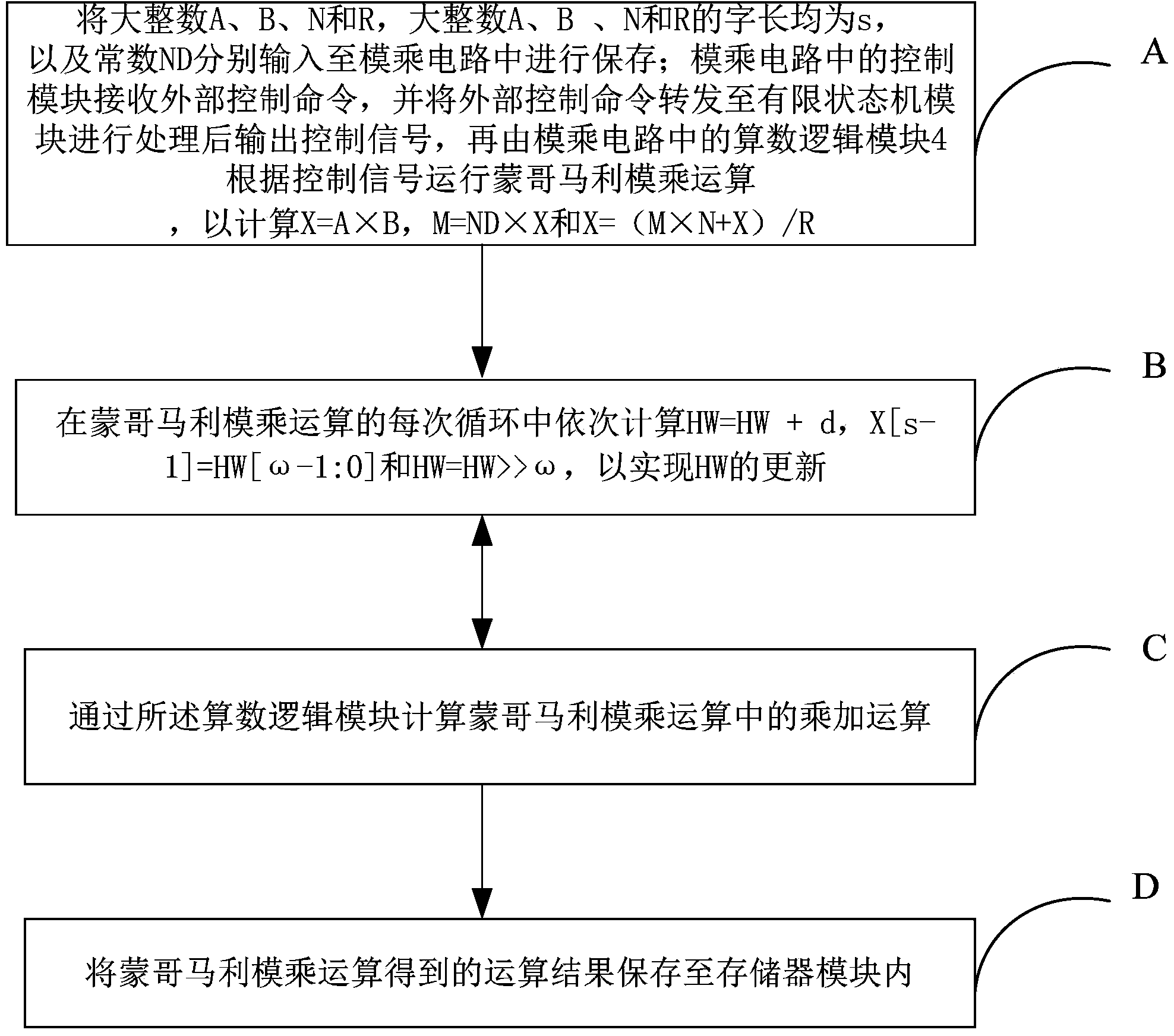
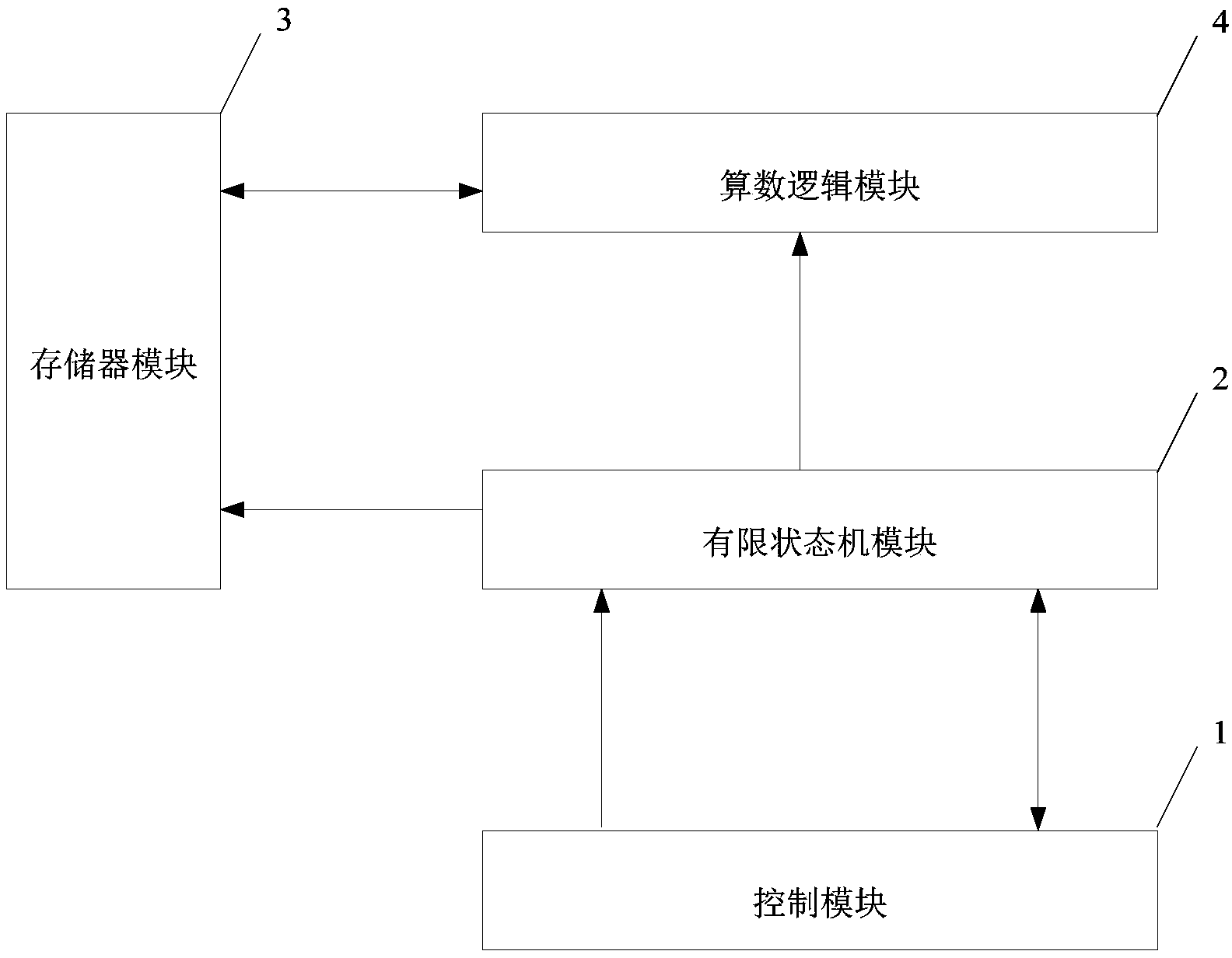
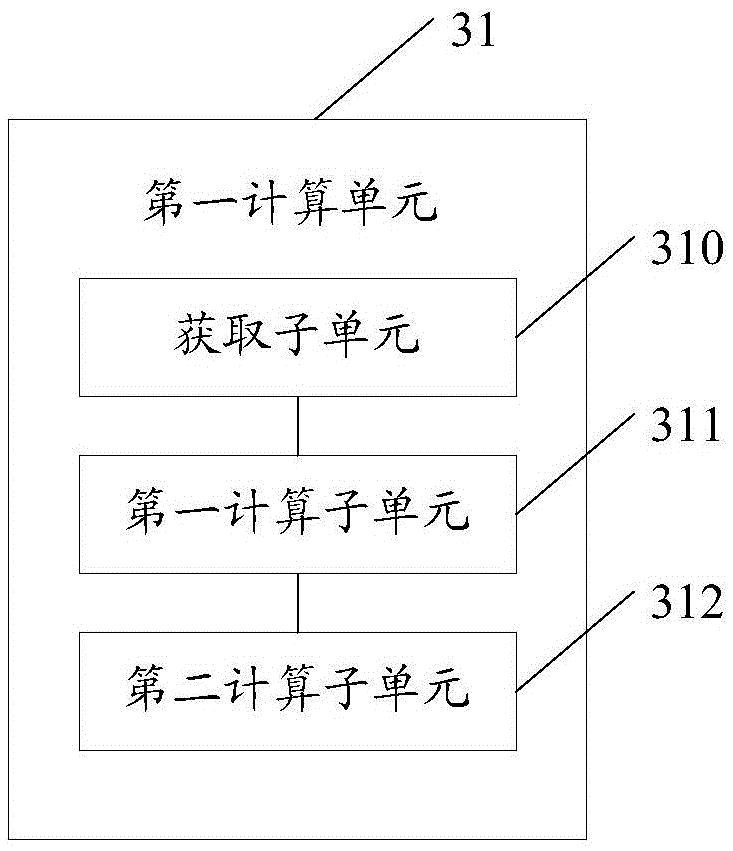
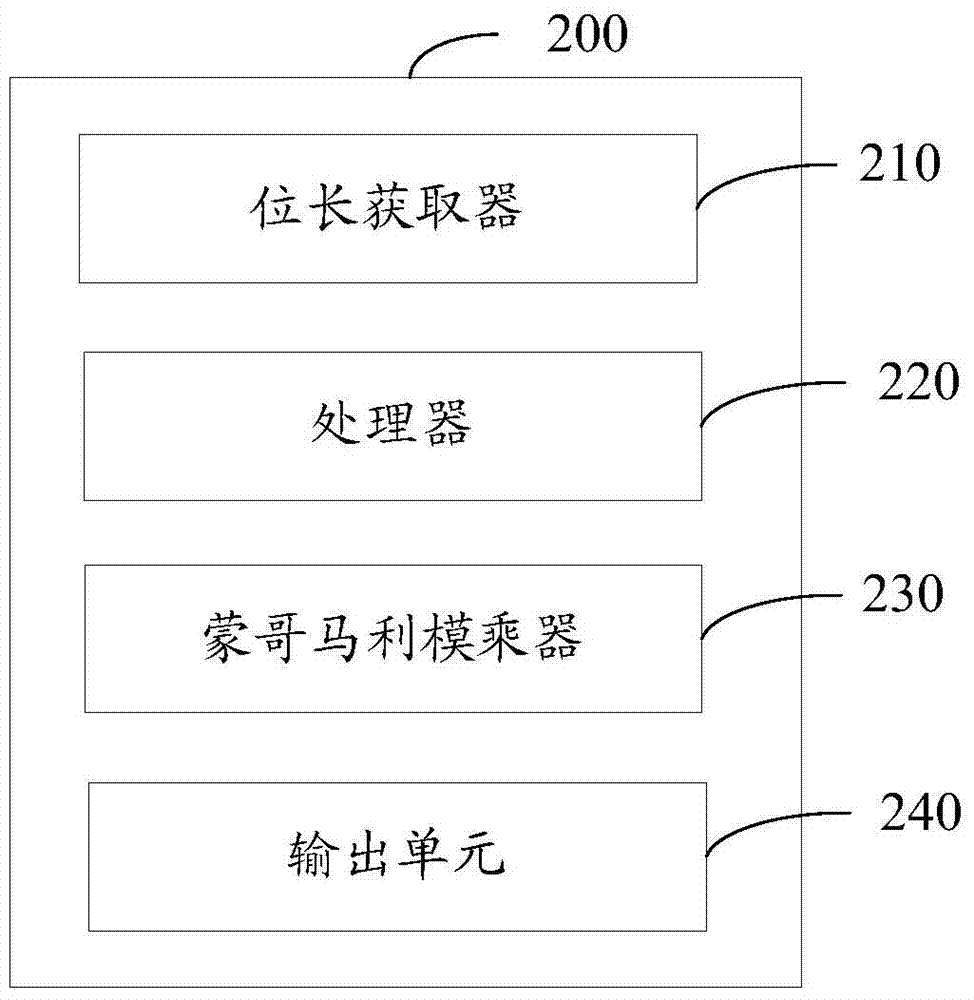
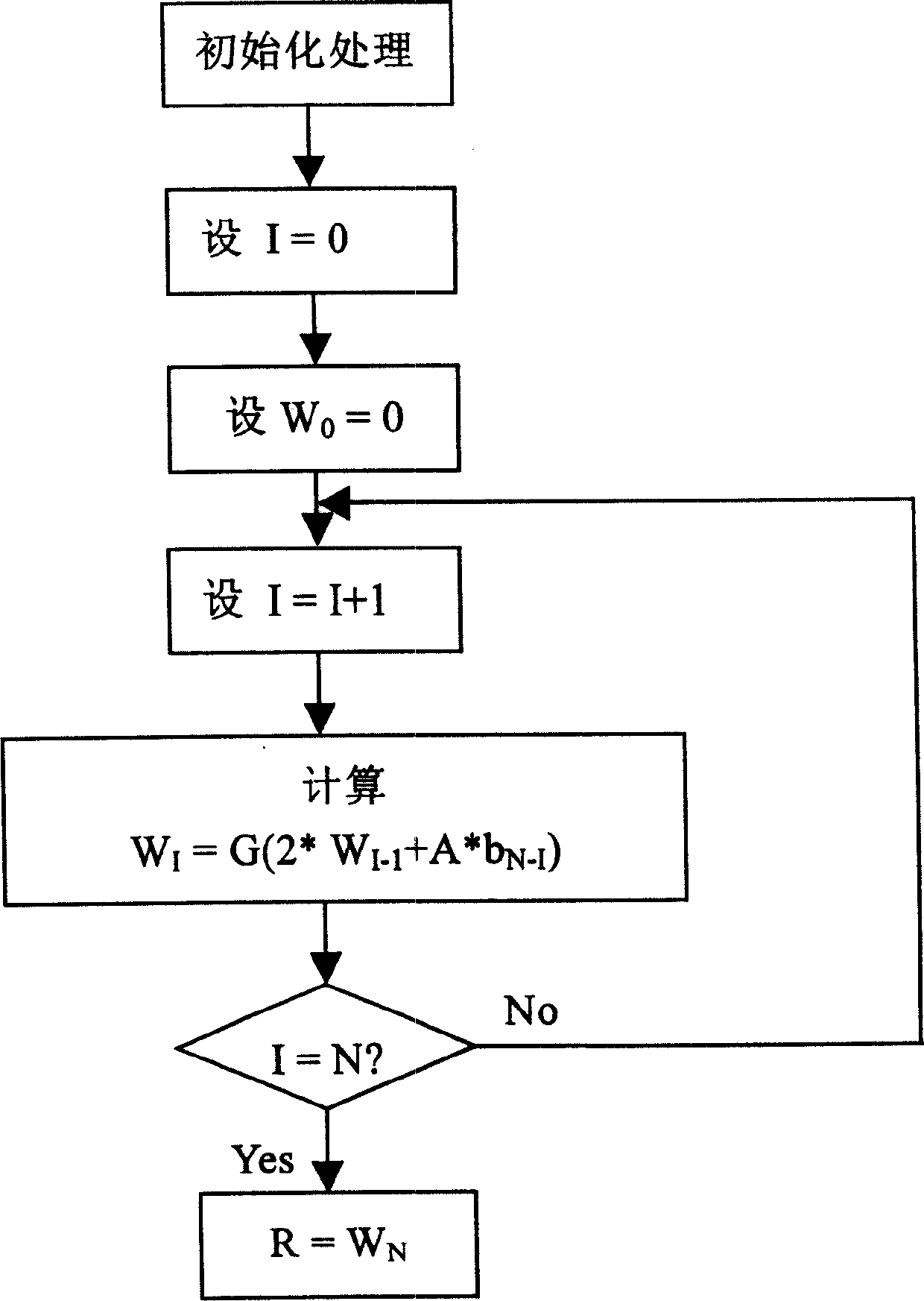
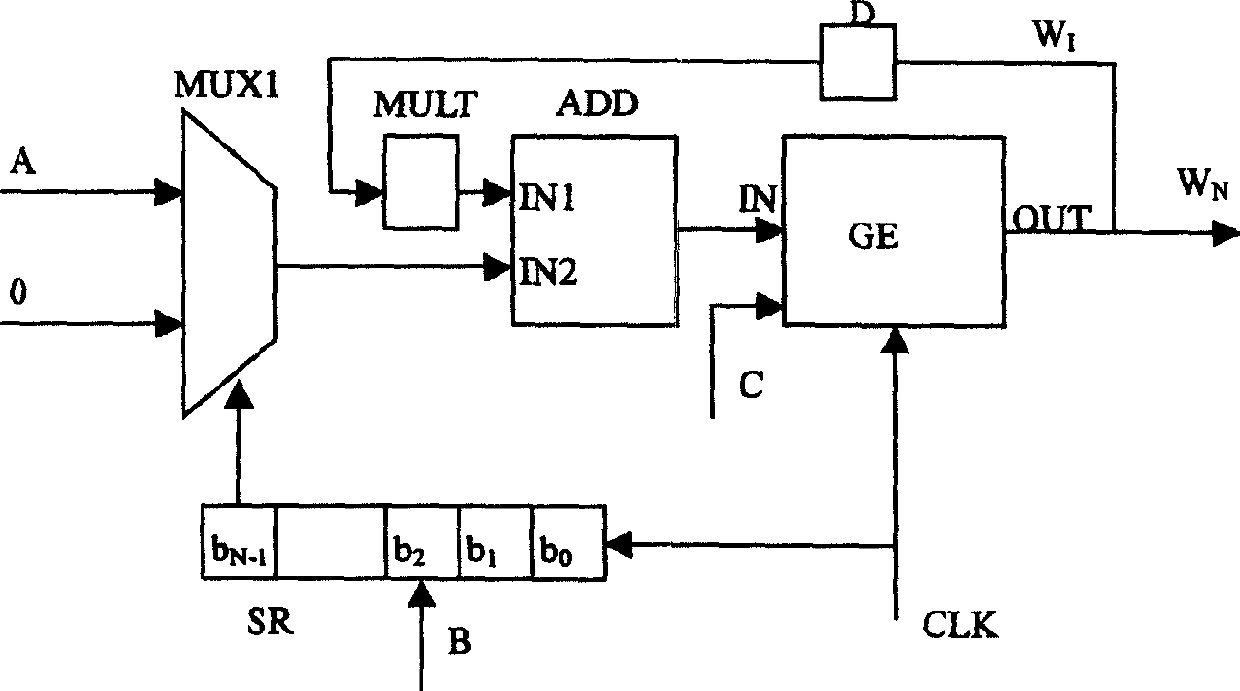
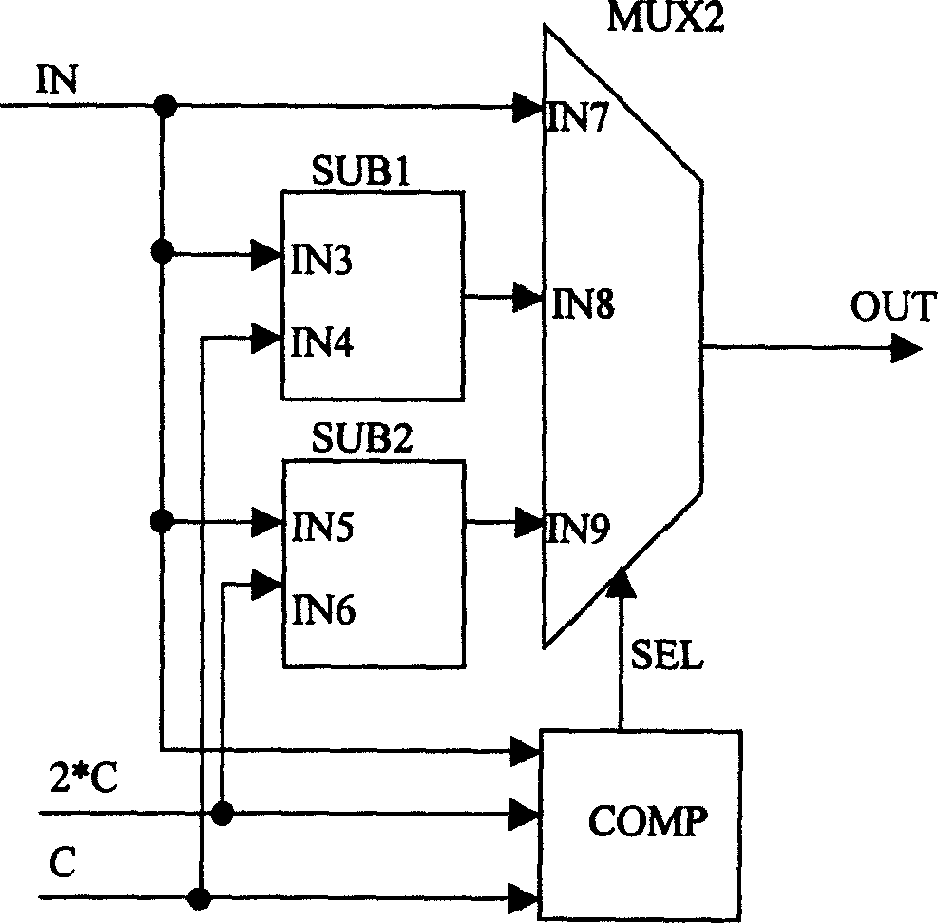
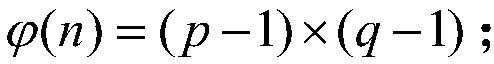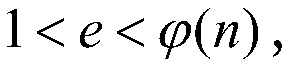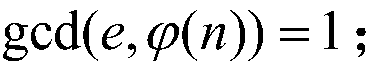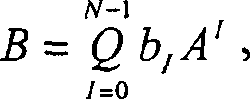Patents
Literature
98 results about "Montgomery reduction" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
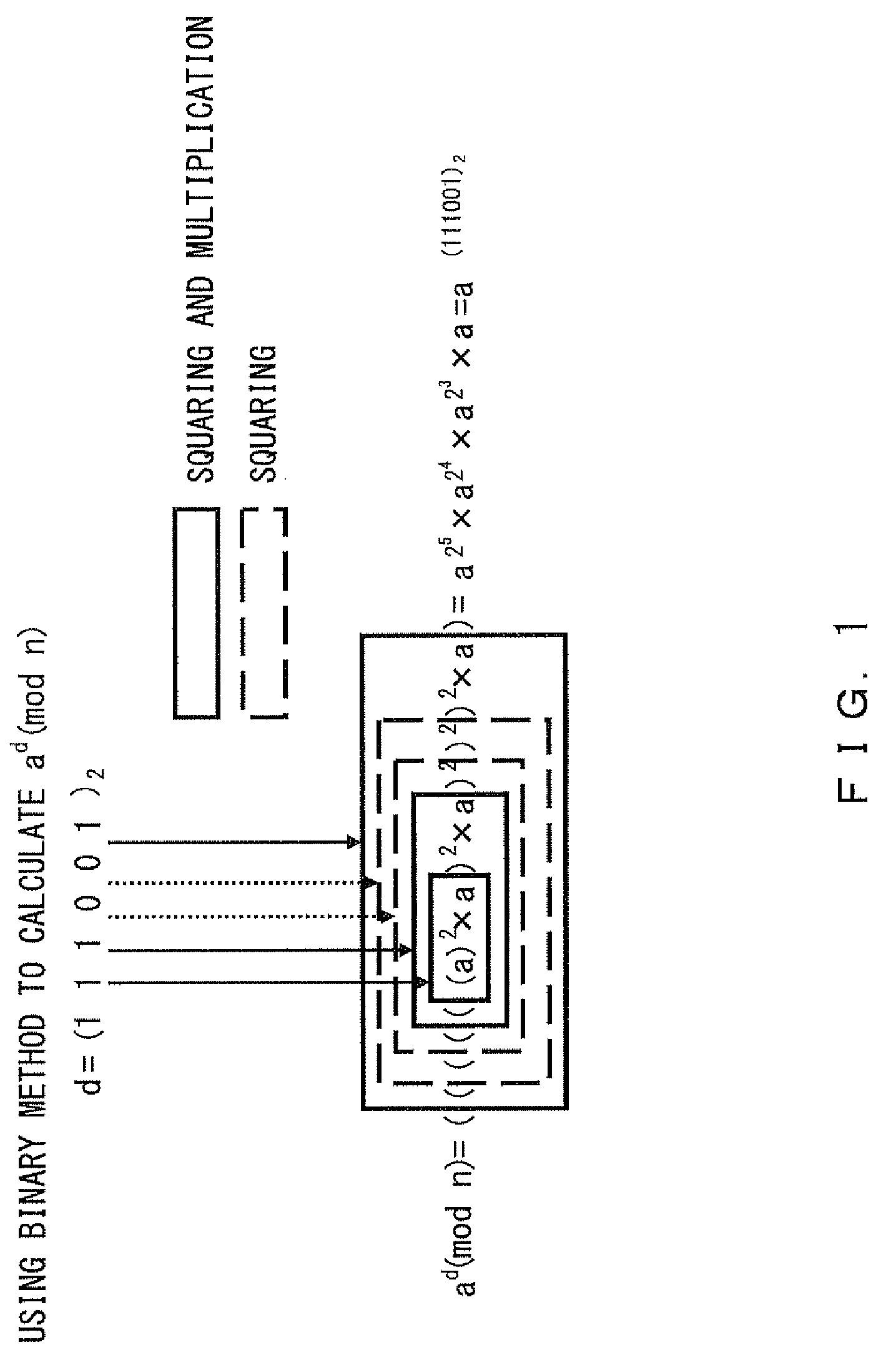
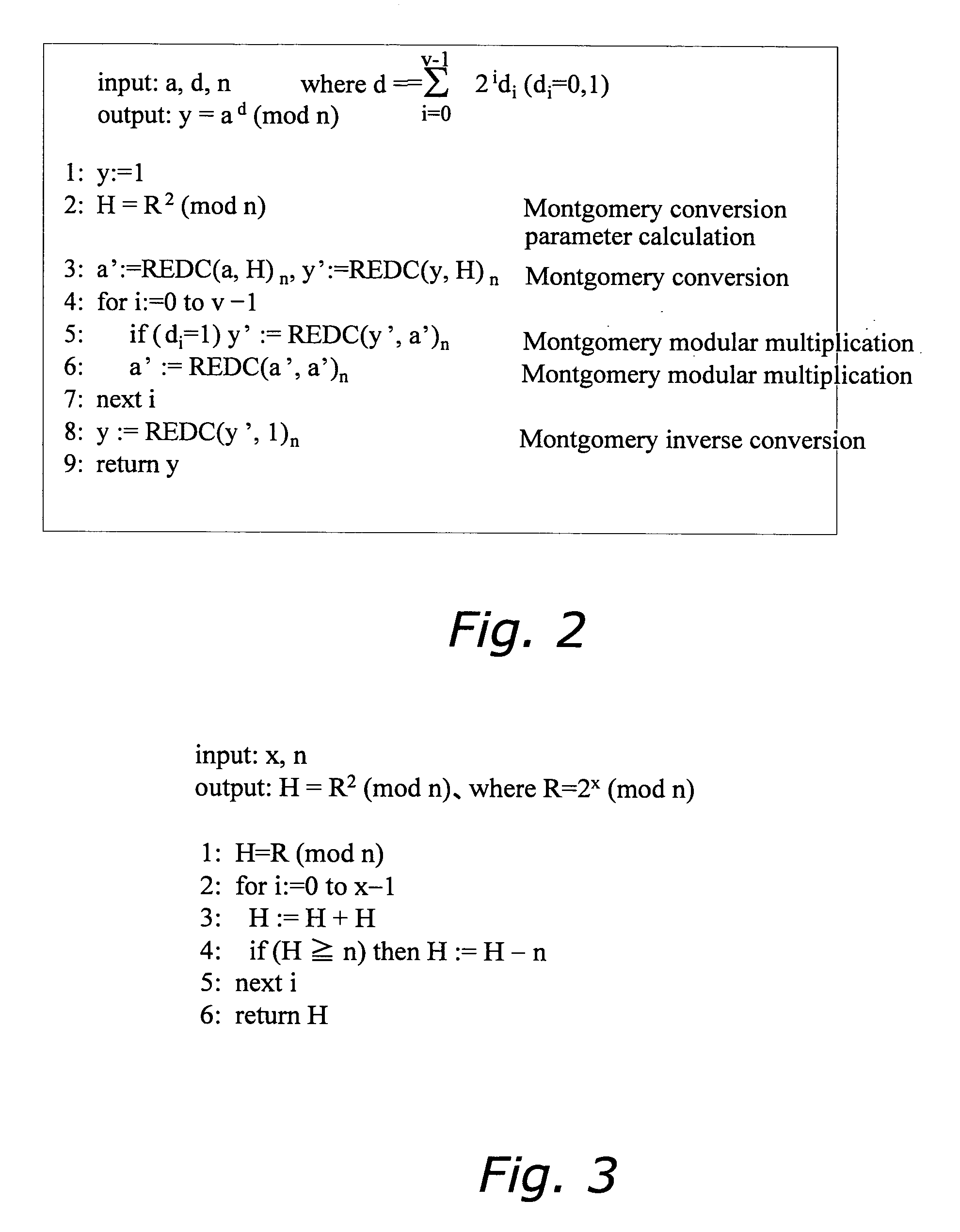
In modular arithmetic computation, Montgomery modular multiplication, more commonly referred to as Montgomery multiplication, is a method for performing fast modular multiplication. It was introduced in 1985 by the American mathematician Peter L. Montgomery.
Multi-word arithmetic device for faster computation of cryptosystem calculations
InactiveUS6963644B1Good flexibilityHigh-speed executionPublic key for secure communicationDigital computer detailsCryptosystemMontgomery reduction
Owner:PANASONIC CORP
Data encryption and decryption processing method and device based on Montgomery modular multiplication operation
InactiveCN102207847AReduce clock cyclesImprove efficiencyComputations using residue arithmeticComputer hardwareMontgomery reduction
The invention discloses a data encryption and decryption processing method and device based on Montgomery modular multiplication operation. During the data encryption or decryption processing, the modular exponentiation operation is transformed to the Montgomery modular multiplication operation which is divided into an external circulation part and an internal circulation part. The internal circulation part mainly performs the multiplication operation, while the external circulation part mainly conducts the reduction operation. After the external circulation operation and the internal circulation operation are completed, the operation result is reduced to a range smaller than a modulus P if the operation result is determined to be larger than the modulus P, and otherwise, the operation result is outputted directly. For the hardware implementation, the internal circulation and the external circulation are designed to a parallel processing pipeline architecture, which can reduce the clock period consumed by one modular multiplication operation and can improve the overall modular multiplication efficiency, thereby improving the efficiency and the speed for data encryption and decryption.
Owner:GCI SCI & TECH
Extending the range of computational fields of intergers
InactiveUS20060269054A1Increase the amount of calculationReduce silicon areaUser identity/authority verificationDigital computer detailsOperandMontgomery reduction
Owner:WESTERN DIGITAL ISRAEL LTD
Extensible high-radix Montgomery's modular multiplication algorithm and circuit structure thereof
InactiveCN1731345AHigh speedReduce overheadComputations using residue arithmeticMontgomery reductionAnalog multiplier
The invention relates to an extended high base Montgomery analog multiplying algorithm and the circuit structure in the field of integrated circuit technology. It improves multiply characters high base Montgomery analog multiplying algorithm, wherein each step dose left shift operation to the batch N and the multiplicand B but not to the result S so that the delay between the two data path lines can de reduced from two clock weeks to one clock week. The circuit structure comprises: three storages used to store A, B and N operation numbers, a line type data path module which is formed by first stage to p stage processing units, a control module used to control the entire analog multiplier computing course and first-in first-out storage.
Owner:上海微科集成电路有限公司 +1
Scalable methods and apparatus for Montgomery multiplication
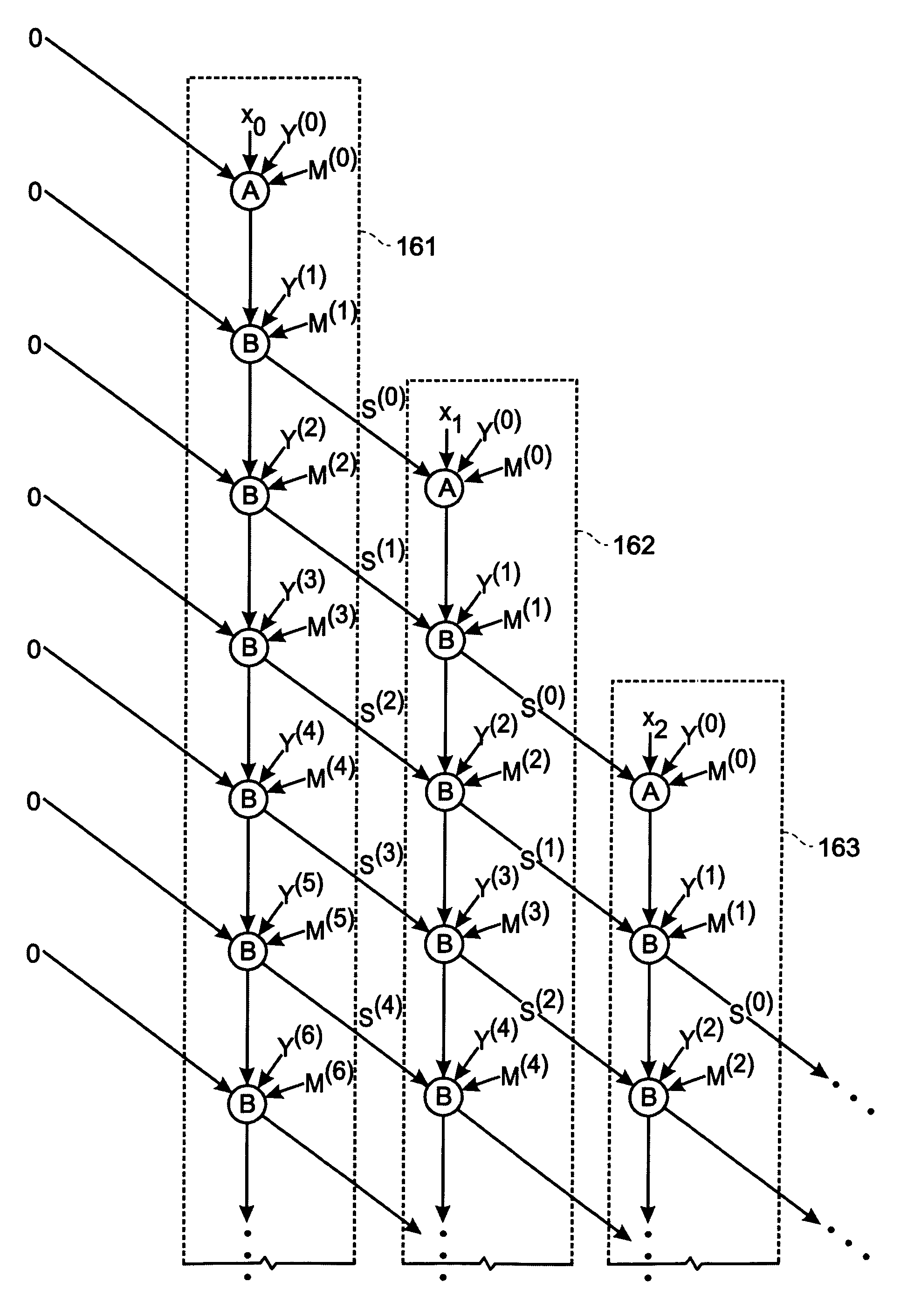
Scalable Montgomery multiplication methods and apparatus are provided that are reconfigurable to perform Montgomery multiplication on operands having arbitrary data precision. The methods perform Montgomery multiplication by combining bit-wise and word-wise operations and exhibit pipelined and parallel operation. Apparatus include a control unit that directs bits of an operand to processing elements that receive words of a second operand and a modulus, and produce intermediate values of a Montgomery product. After an intermediate value of a word of a Montgomery product is obtained in a first processing element based on a selected bit of the first operand, the intermediate value is directed to a second processing element and is updated based on another selected bit of the first operand.
Owner:THE STATE OF OREGON ACTING BY & THROUGH THE OREGON STATE BOARD OF HIGHER EDUCATION ON BEHALF OF OREGON STATE UNIV
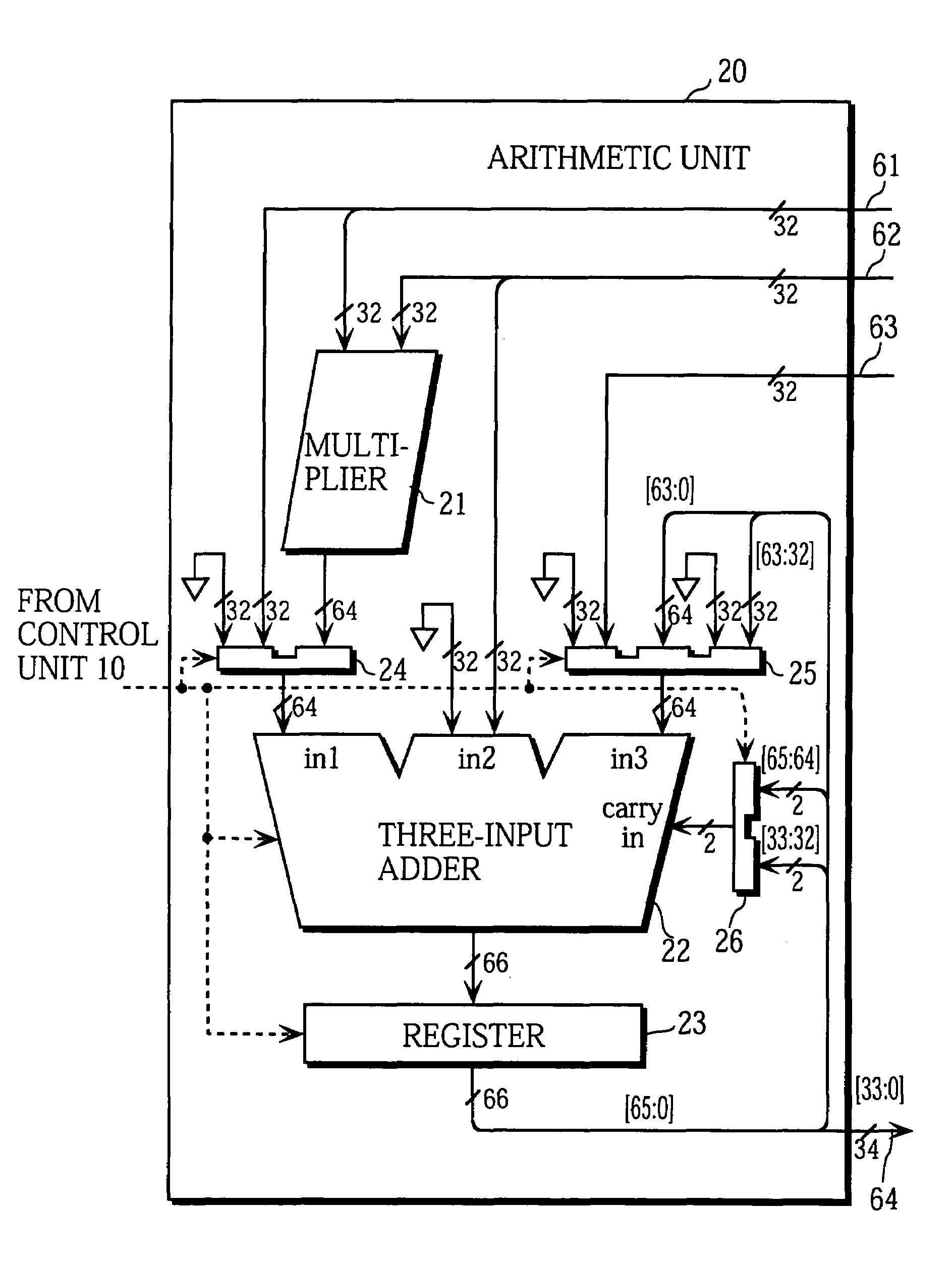
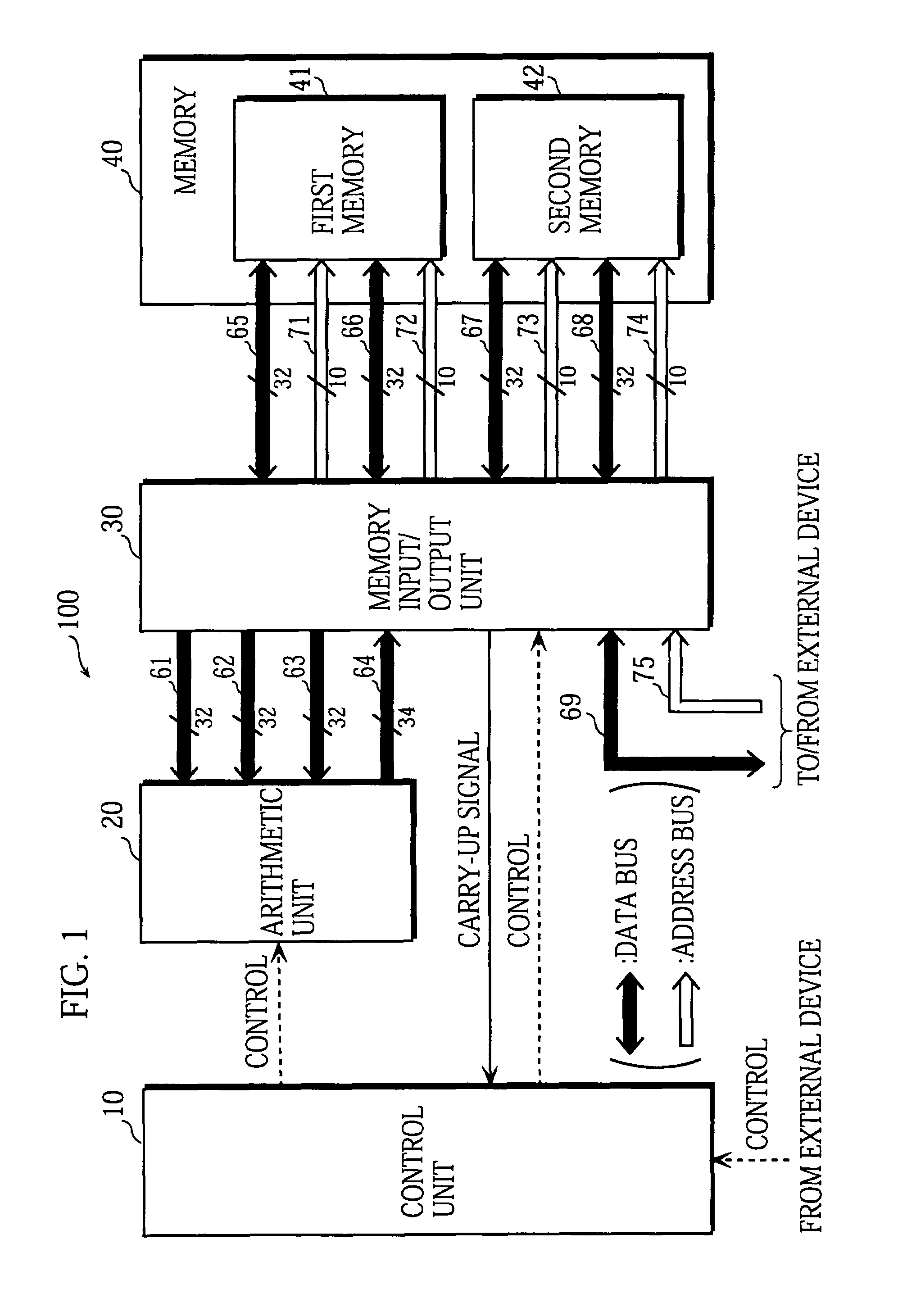
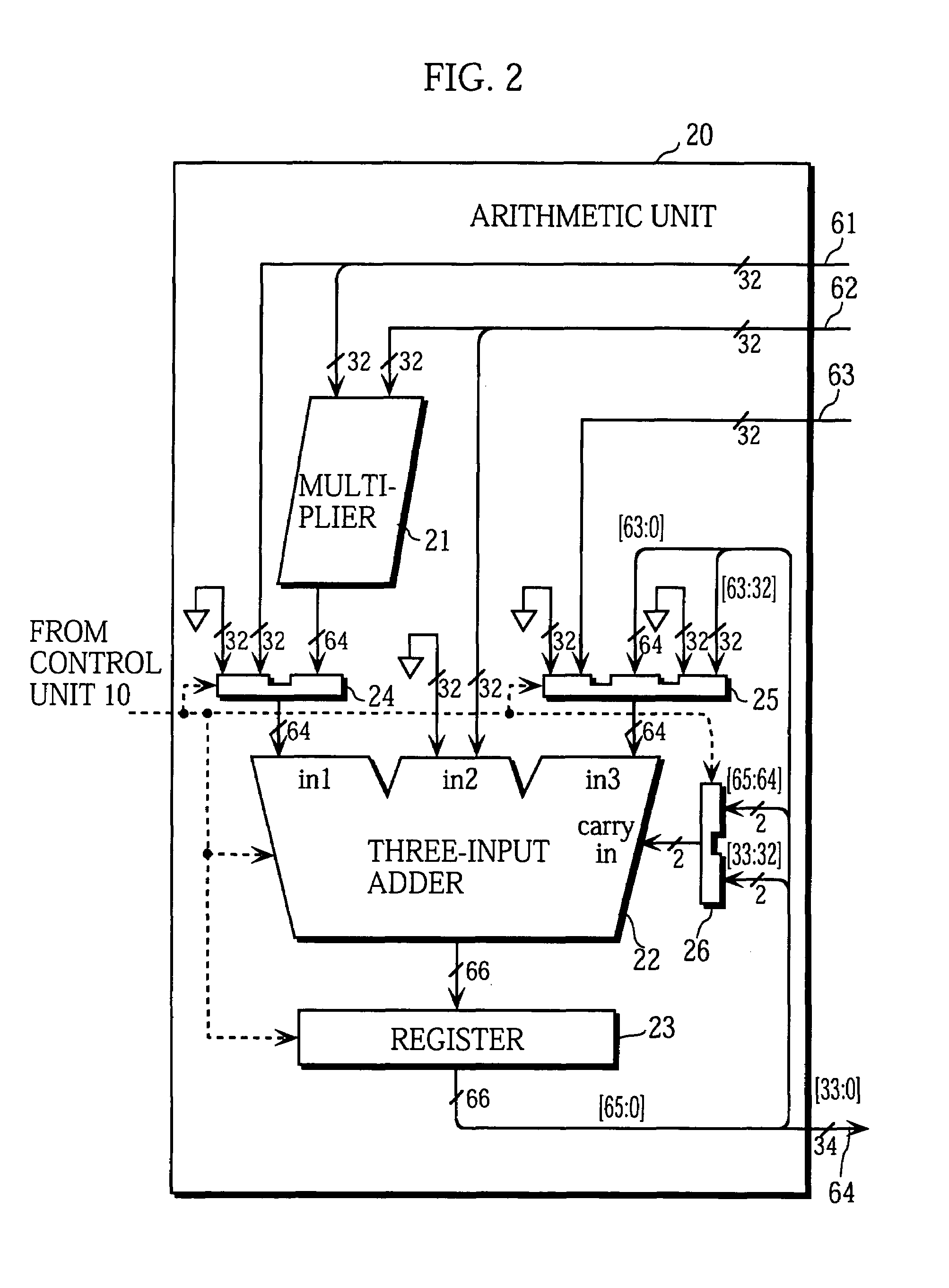
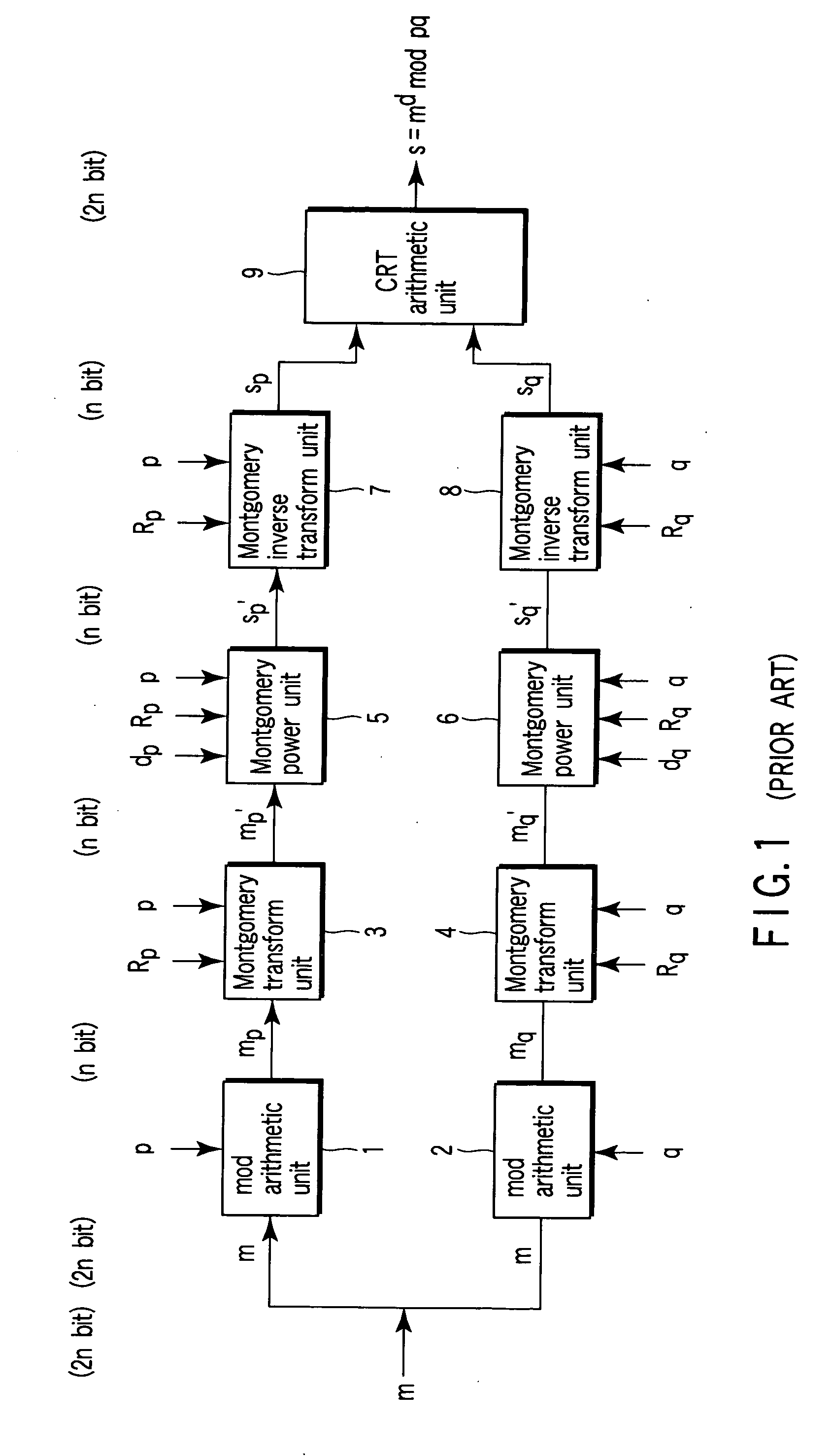
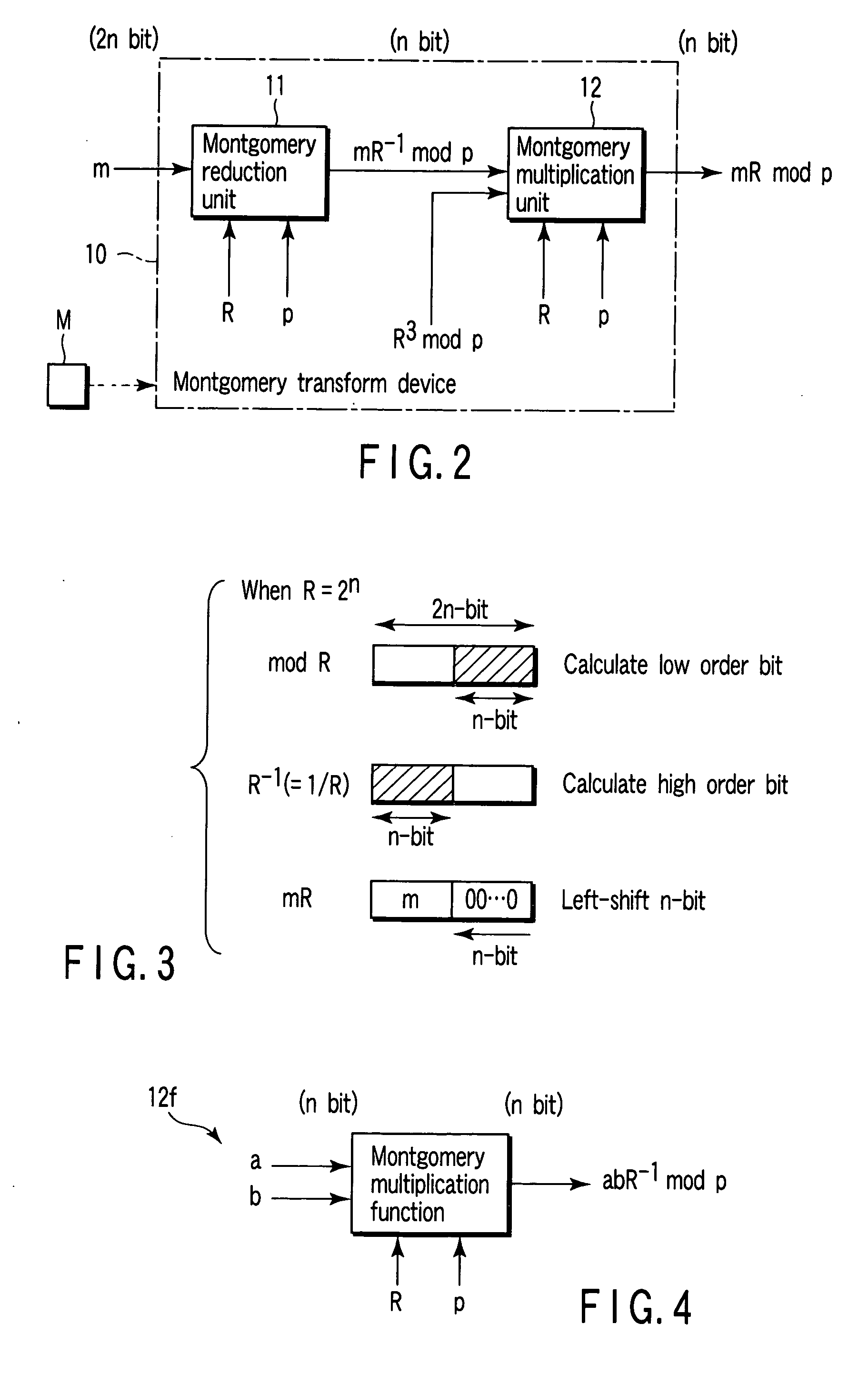
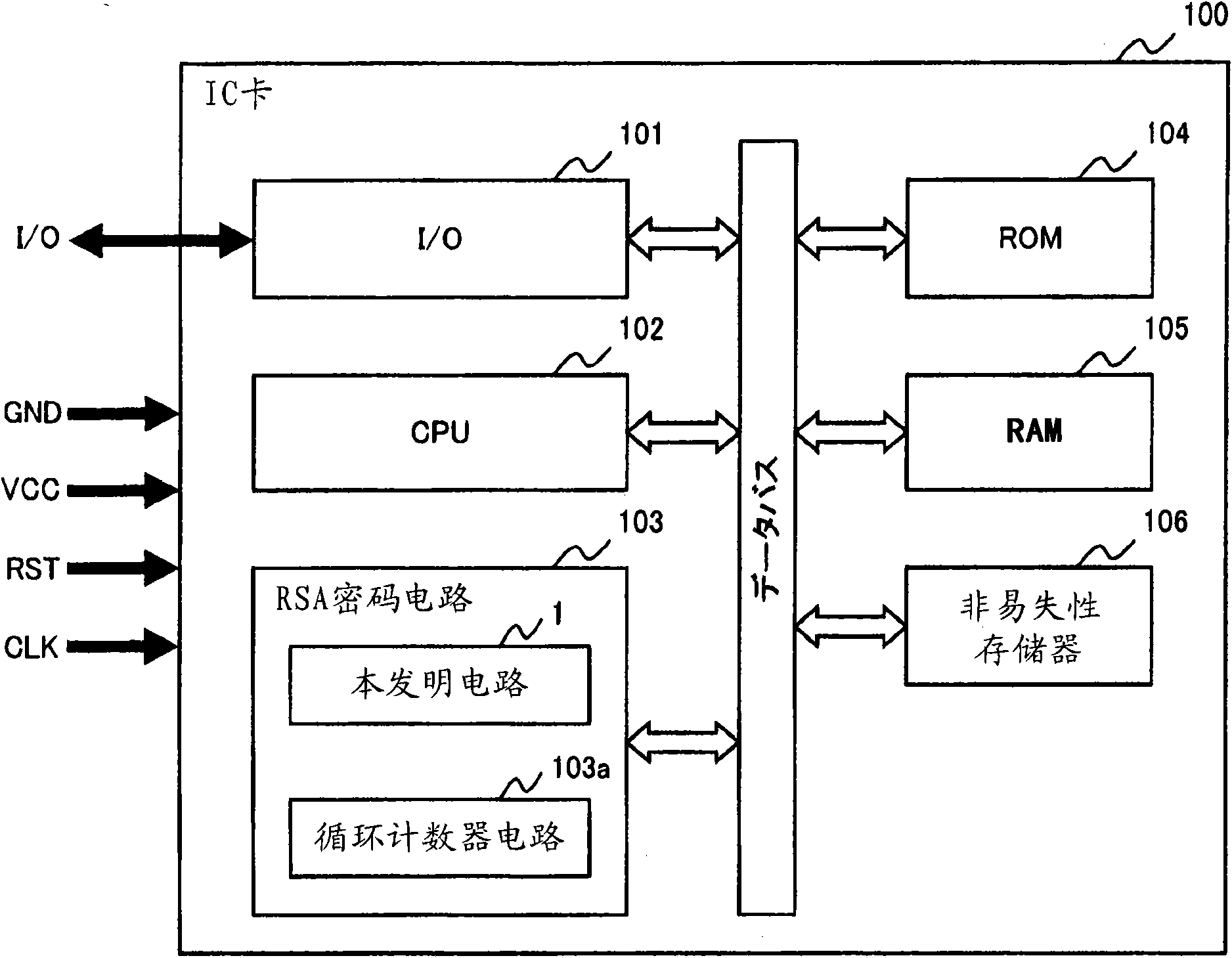
Montgomery transform device, arithmetic device, IC card, encryption device, decryption device and program
InactiveUS20060126830A1Digital data processing detailsUser identity/authority verificationComputer hardwareMontgomery reduction
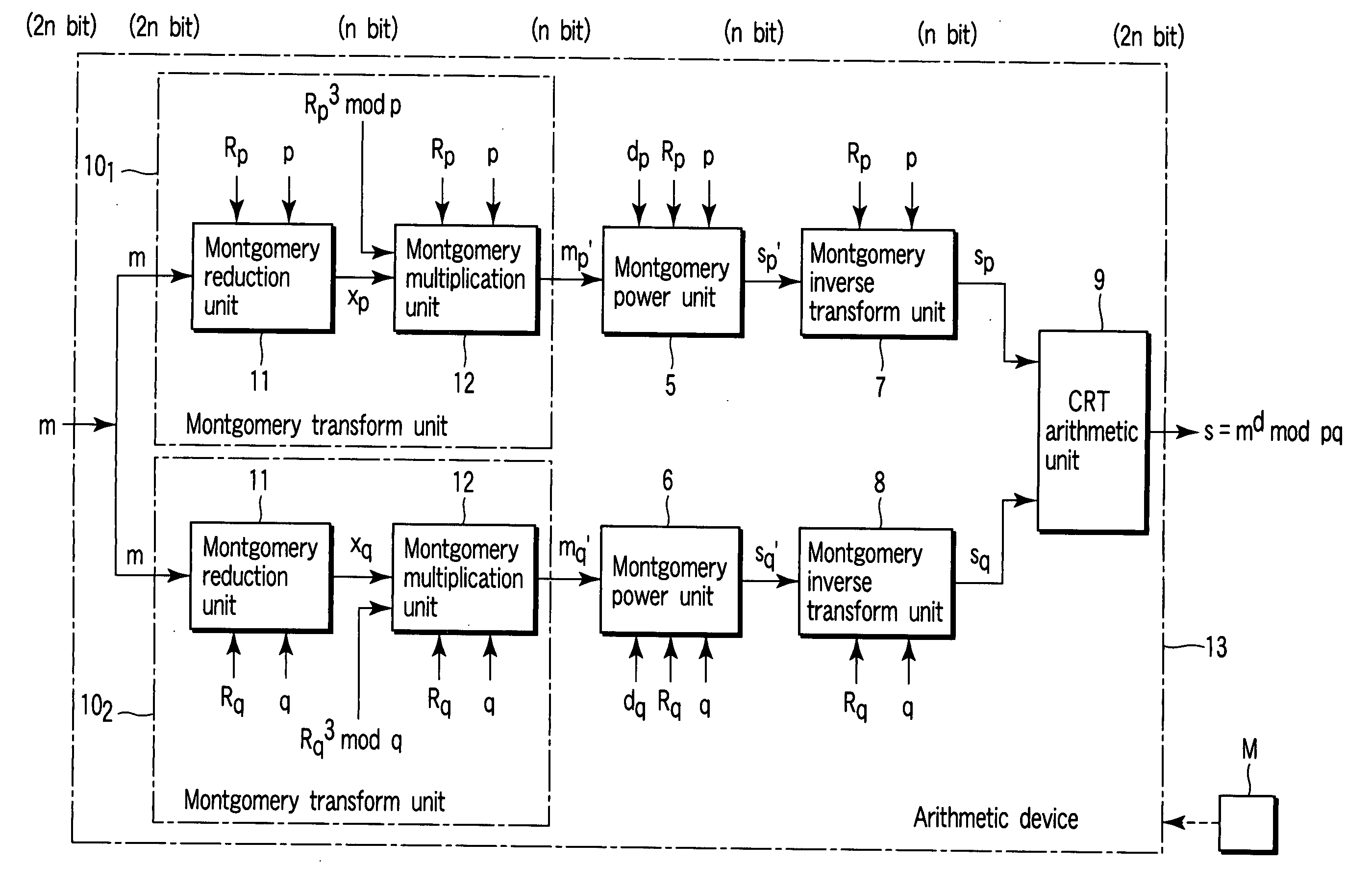
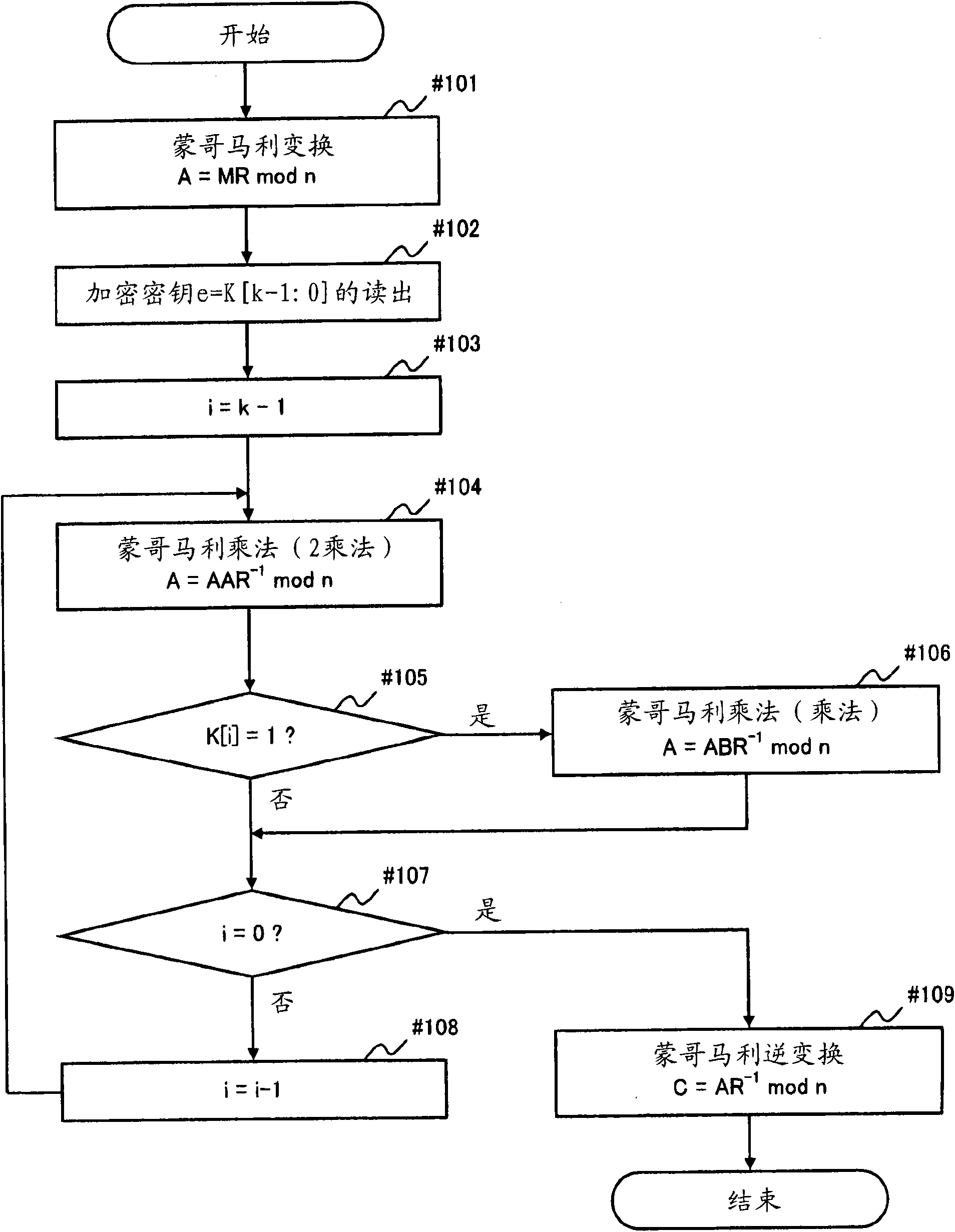
According to an aspect of the invention, Montgomery arithmetic can be achieved while omitting division in an input stage. That is, the aspect of the invention is configured to obtain a Montgomery transform result m′ (=mR mod p) of n-bit from an input m of 2n-bit without using the division, with using Montgomery reduction and Montgomery multiplication instead of conventional mod arithmetic and the Montgomery transform. Accordingly, Montgomery arithmetic can be achieved while omitting the division in the input stage.
Owner:KK TOSHIBA
Extending the range of computational fields of integers
ActiveUS7111166B2Increase the amount of calculationReduce silicon areaComputations using contact-making devicesComputation using non-contact making devicesModularityMontgomery reduction
Owner:WESTERN DIGITAL ISRAEL LTD
Optimized Montgomery modular multiplication method, optimized modular square method and optimized modular multiplication hardware
InactiveCN103761068AImprove computing powerReduce areaComputations using residue arithmeticBinary multiplierProcessor register
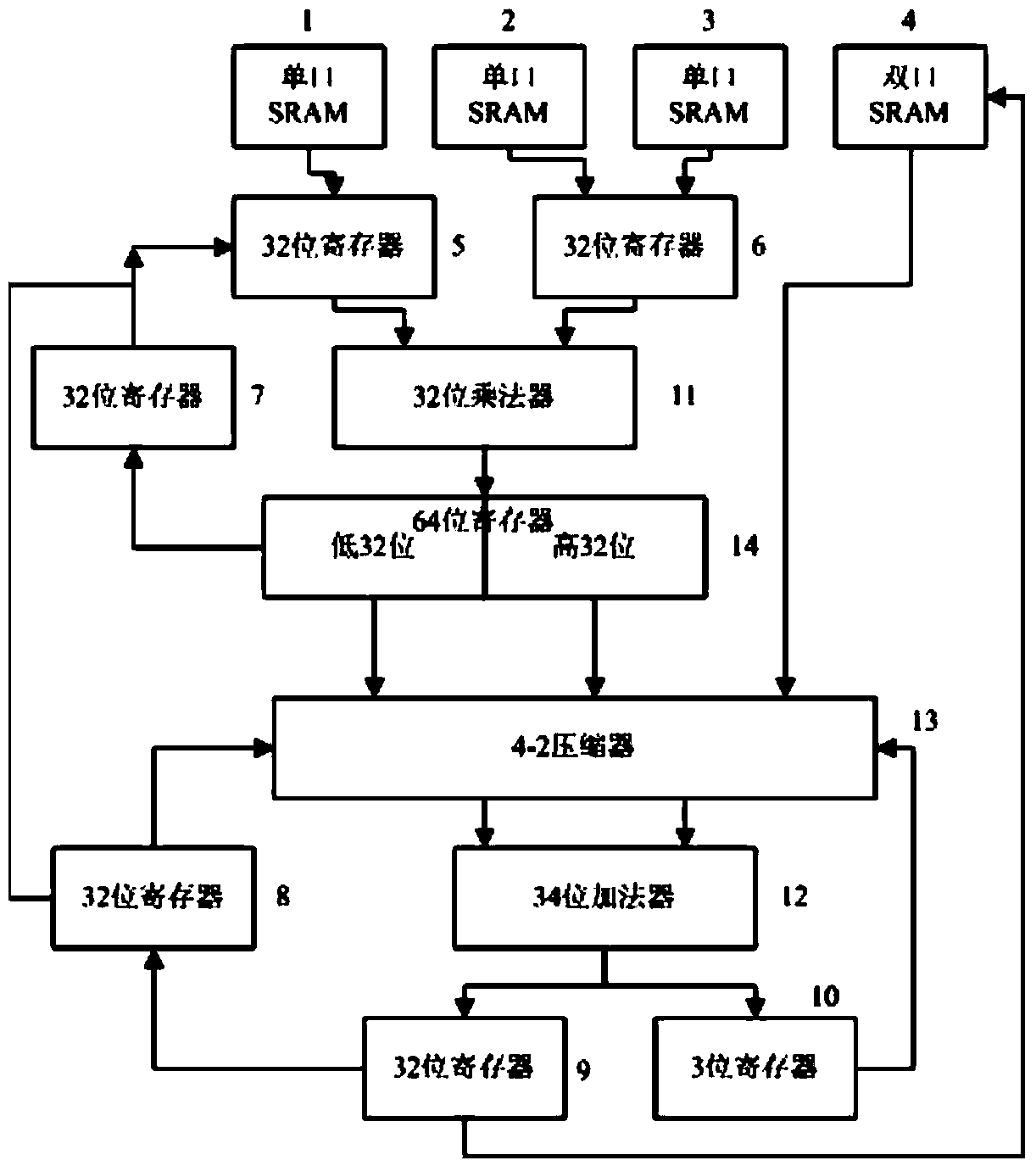
The invention discloses an optimized Montgomery modular multiplication method, an optimized modular square method and optimized modular multiplication hardware. The optimization is carried out based on an original FIOS (Finely integrated operand scanning) algorithm. The optimized modular multiplication hardware mainly comprises three single-port SRAMs, a double-port SRAM, a 32-bit multiplier, a 34-bit adder, a 4-2 compressor, a 64-bit register and six 32-bit registers. According to the optimized Montgomery modular multiplication method, the optimized modular square method and the optimized modular multiplication hardware, a high-radix modular multiplier of a two-stage parallel assembly line is adopted, the AB operation is completed through a first-stage 32-bit multiplier, the T+AB+C operation is completed through a second-stage adder, the 32-2048-bit modular multiplication operation is achieved, the area of a chip is reduced, and the modular multiplication operation performance is improved.
Owner:SHANGHAI JIAO TONG UNIV
Montgomery modular multiplication-based data processing method
ActiveCN102999313AIncrease processing rateImprove efficiencyComputations using residue arithmeticInput/output processes for data processingStatic random-access memoryProcessor register
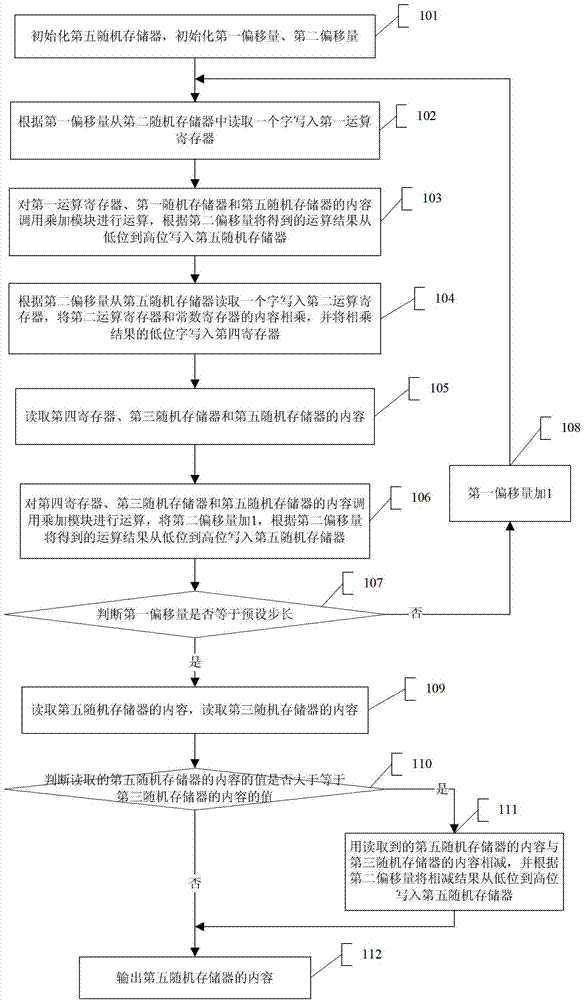
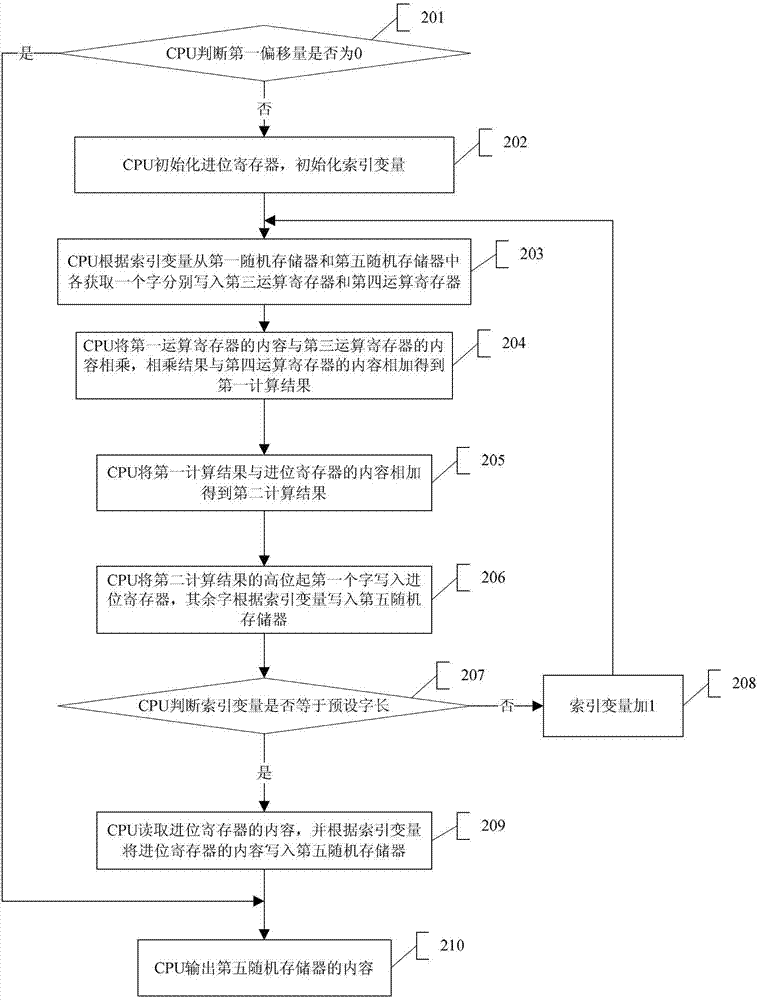
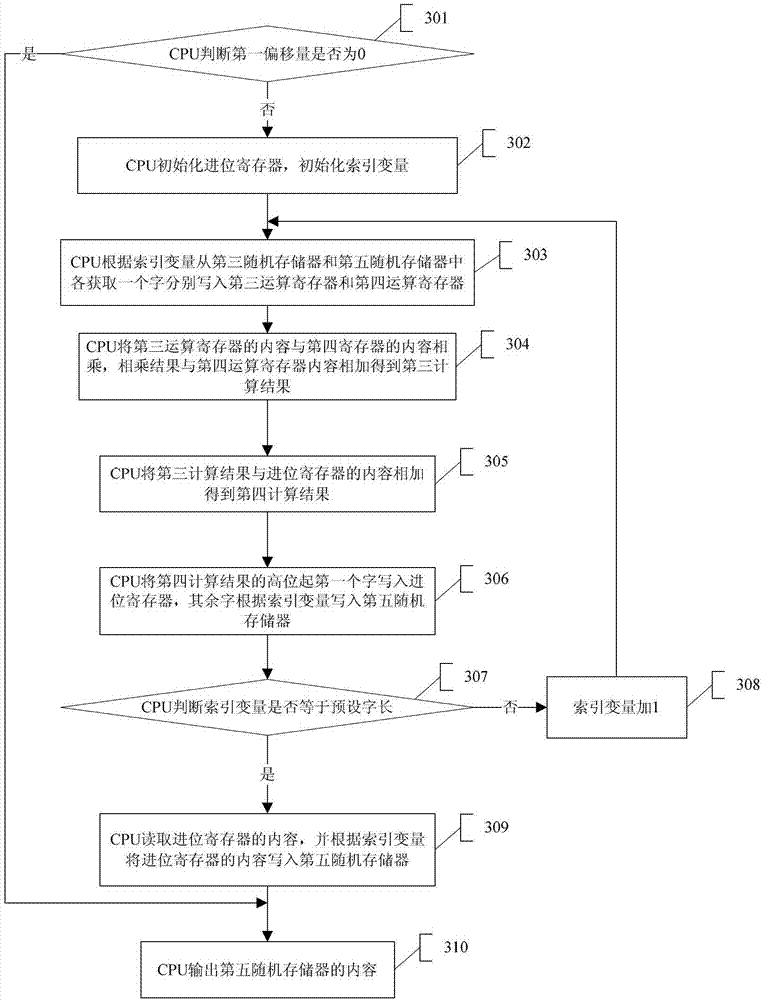
The invention discloses a Montgomery modular multiplication-based data processing method and belongs to the technical field of computers. The method comprises the following steps of: initializing a fifth random access memory through a central processing unit (CPU), and executing the following operations on the contents in a second random access memory by taking words as units, namely (1) calling a multiplying and adding module to multiply one word of the contents of the second random access memory and contents of a first random access memory and add the product with the contents of the fifth random access memory; (2) extracting one word from an operation result of the step (1) and multiplying the word with the contents of a constant register, and writing the low-order word of the multiplied result into a fourth register; and (3) calling the multiplying and adding module to multiply the contents of the fourth register with the contents of the third random access memory and add the product with the contents of the fifth random access memory; and finally, outputting the contents of the fifth random access memory according to the contents of the third memory.
Owner:BEIJING HONGSI ELECTRONICS TECH
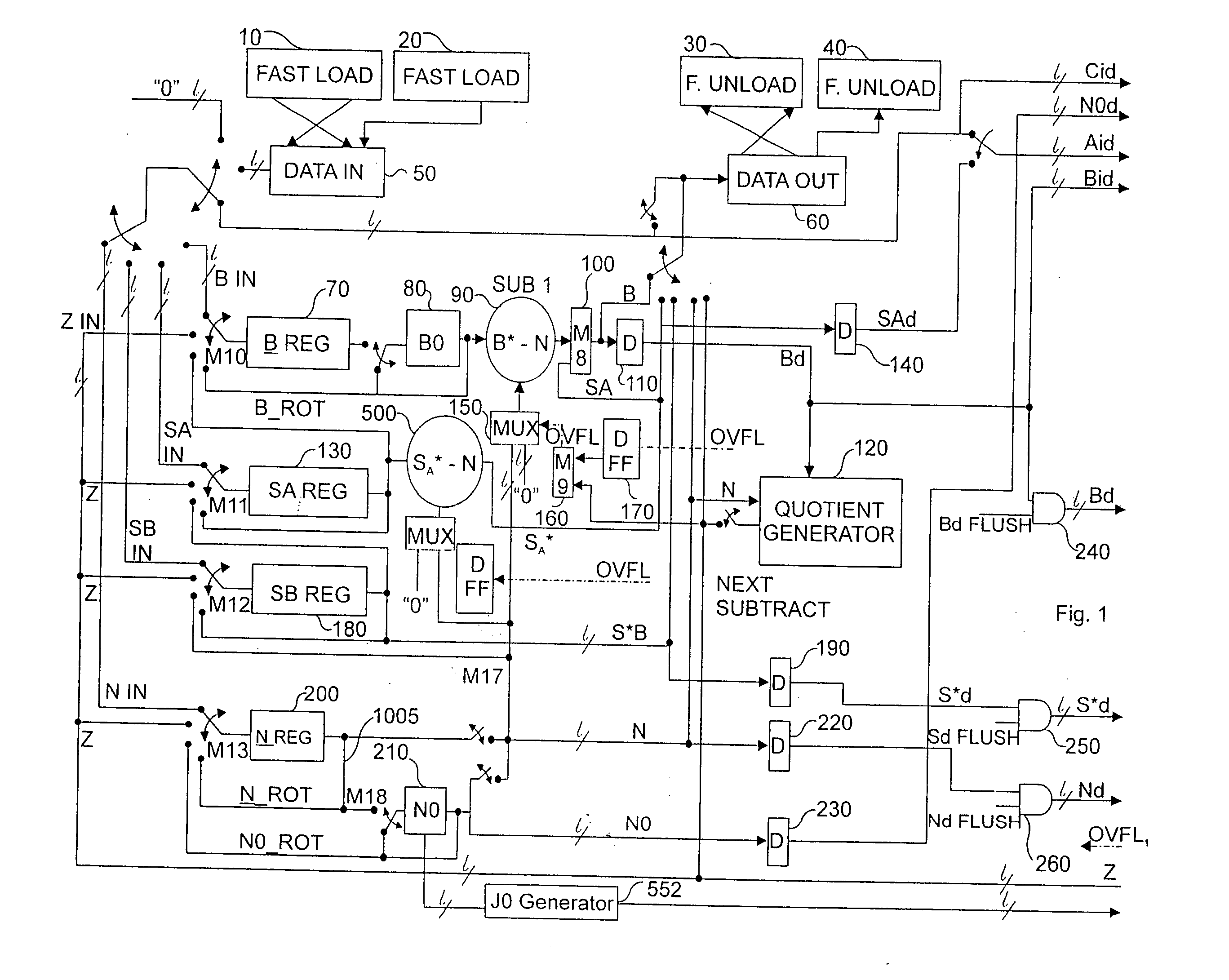
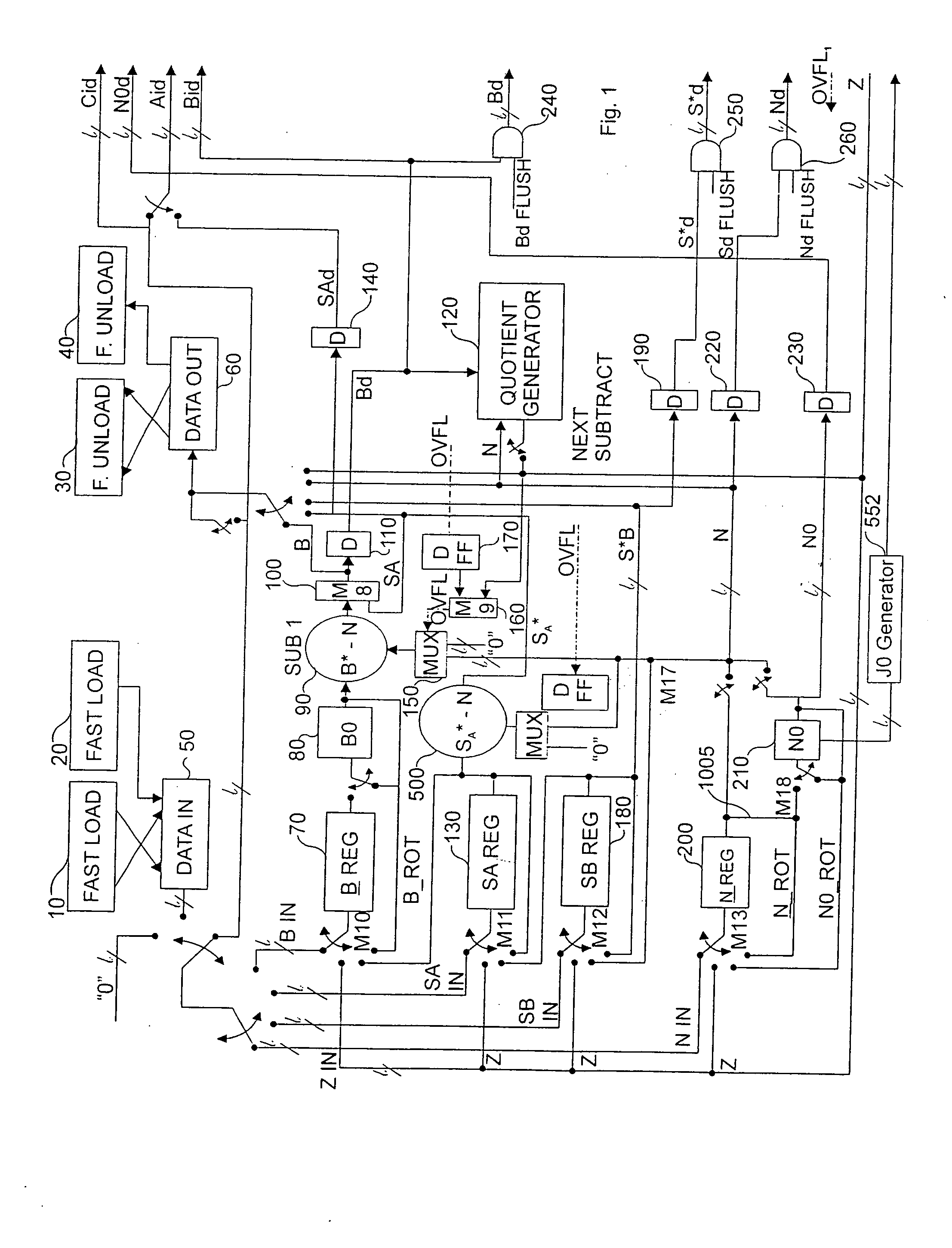
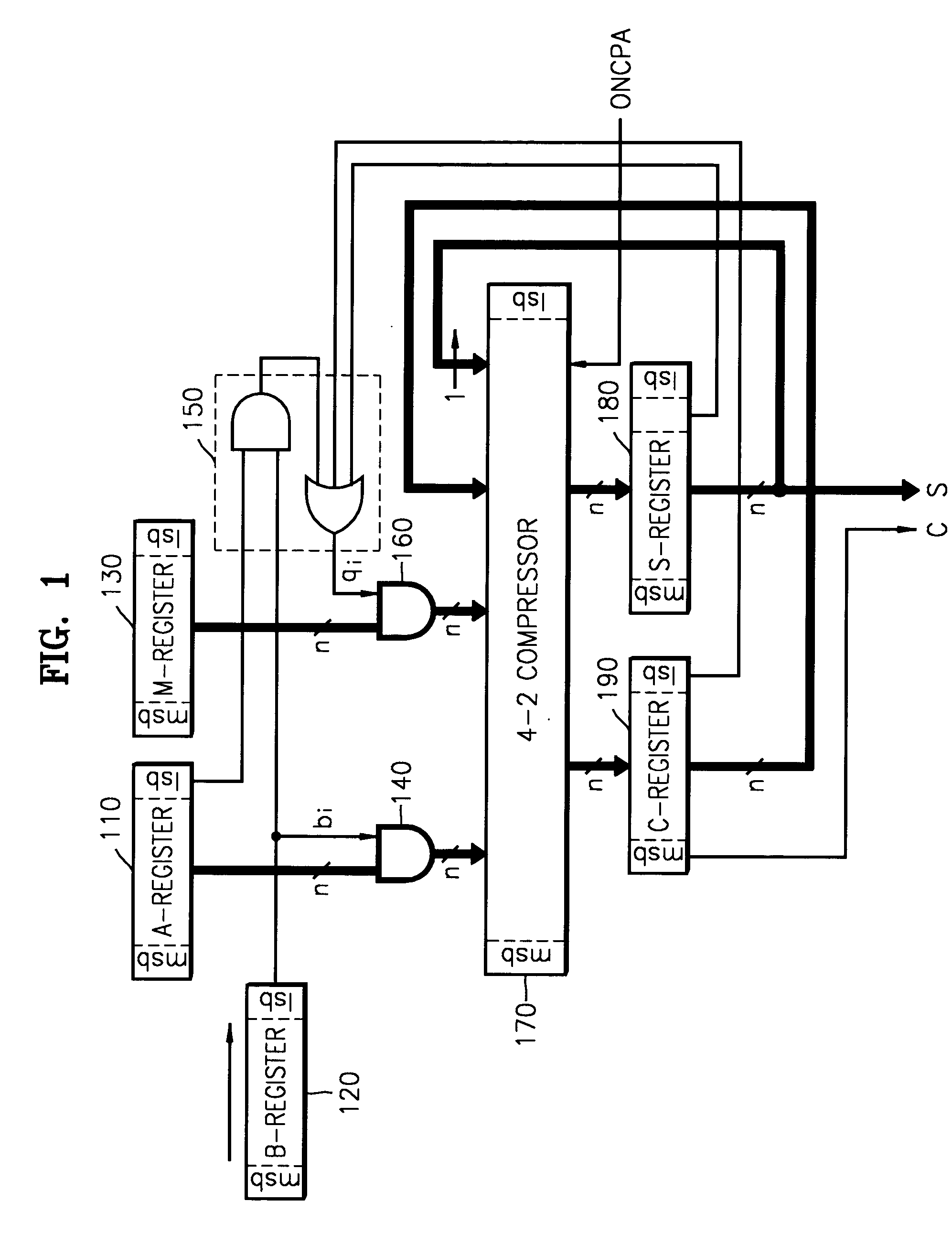
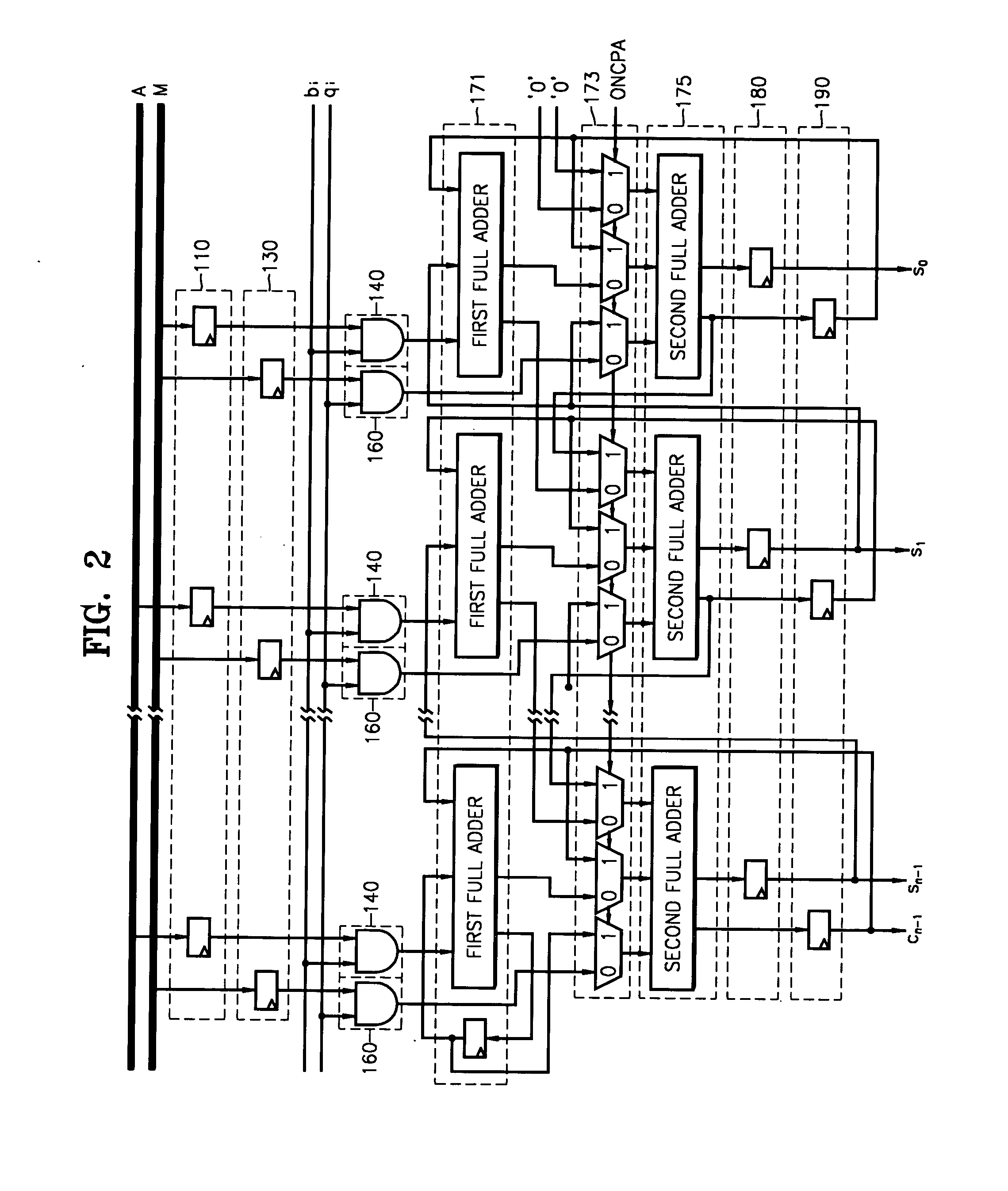
Montgomery modular multiplier using a compressor and multiplication method
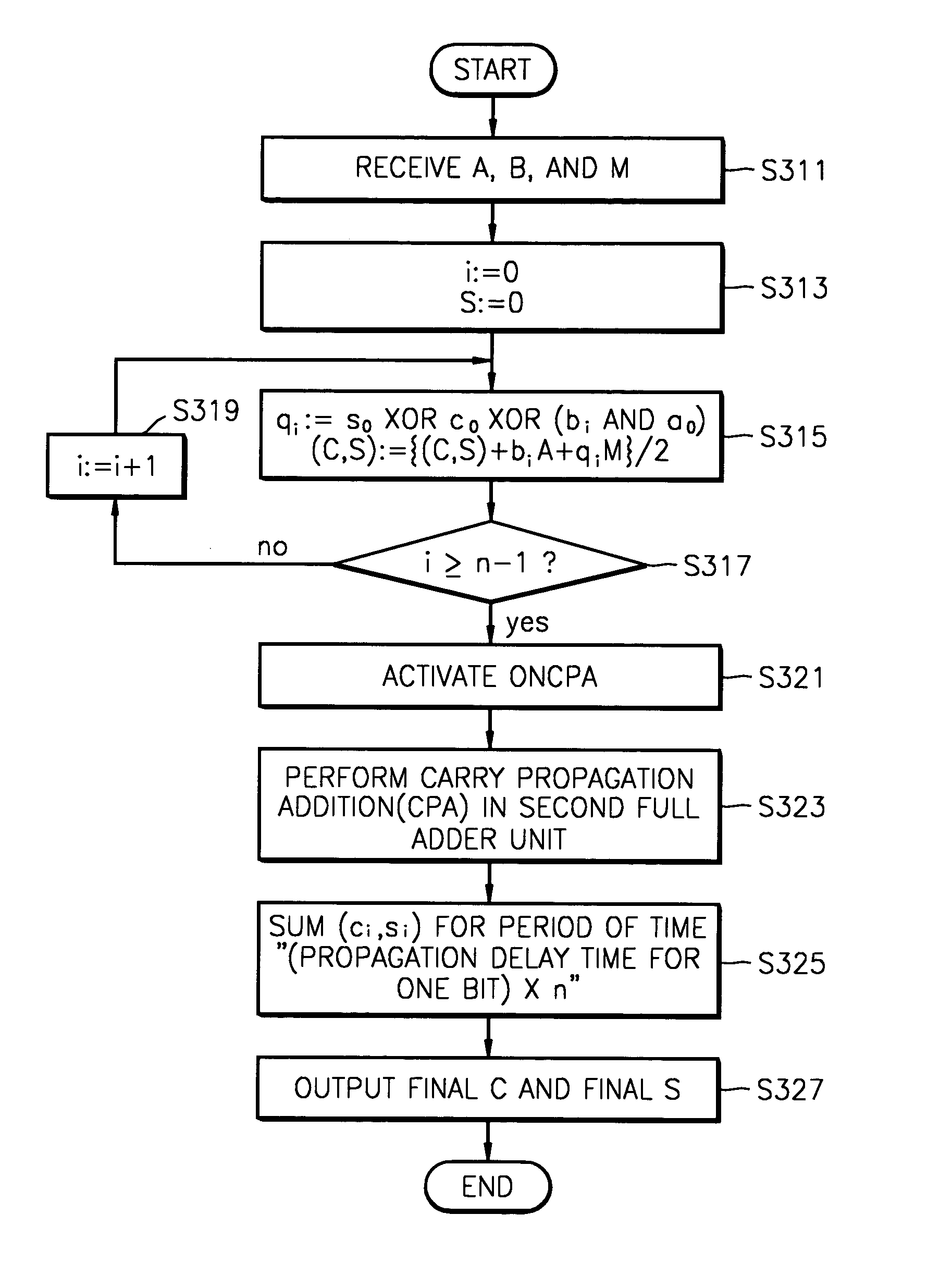
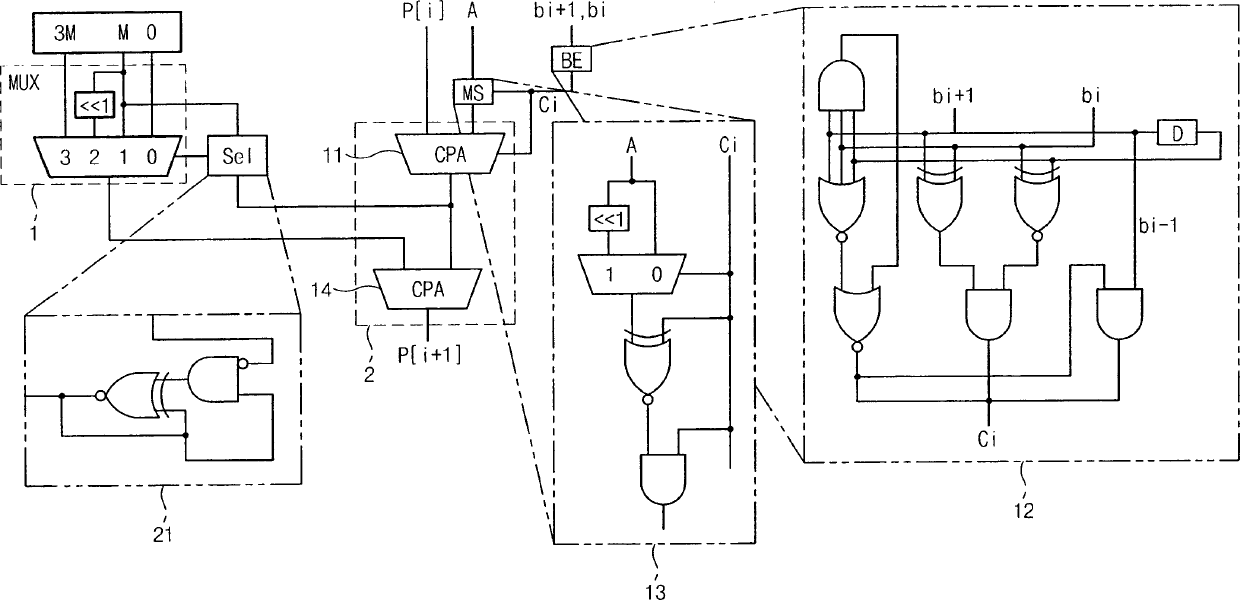
ActiveUS20040125948A1Easy to disassembleHigh speedPublic key for secure communicationComputation using non-contact making devicesCarry propagationModular multiplier
A Montgomery modular multiplier receiving a multiplicand (A), a modulus (M), and a multiplier (B), using a t-s compressor, where t>3 and s>1, and a multiplication method performed in the same. In response to a carry propagation adder signal, the t-s compressor performs additions on the carry C and the sum Sand obtains the final results in a carry propagation adder structure.
Owner:SAMSUNG ELECTRONICS CO LTD
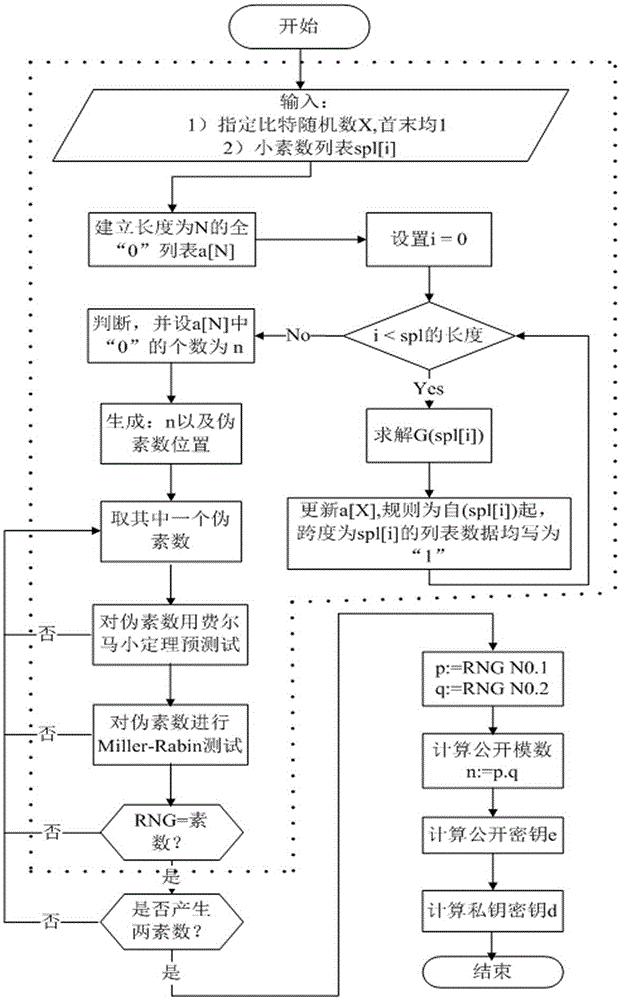
RSA key pair fast generation system and RSA key pair fast generation method
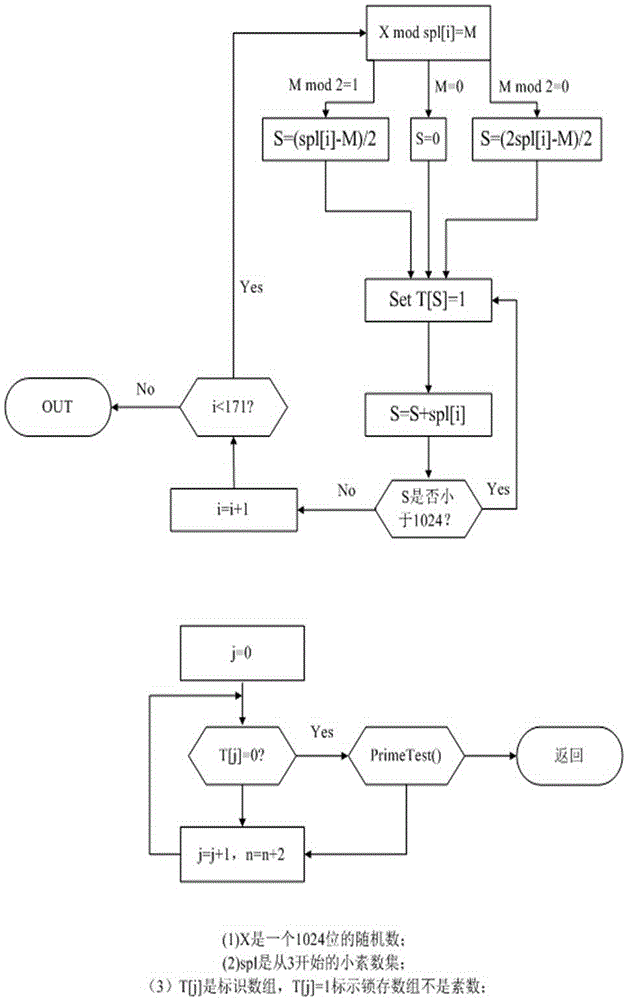
InactiveCN106487512AReduce build timeHigh speedKey distribution for secure communicationPublic key for secure communicationCoprocessorComposite number
The invention discloses an RSA key pair fast generation system and an RSA key pair fast generation method. The system comprises a CPU core, a cipher coprocessor, a prime number generator, and a memory. The prime number generator is used for filtering composite numbers, is implemented in hardware form, supports 256-bit, 512-bit, 1024-bit, 2048-bit and 4096-bit composite number filtering, and completes modular redundancy, calculation and identification table setting. According to the RSA key pair fast generation method, in order to realize fast key pair retrieving, filtering and judging in an asymmetric algorithm, a hardware-based composite number filtering scheme is adopted, optimized modular exponentiation and improved Montgomery modular multiplication are employed, and the existing prime number decision algorithm is optimized. Thus, efficient prime number screening is realized, the key pair generation speed is increased, and the problem that the generation of an RSA key pair takes long in the existing encryption and decryption technology is solved.
Owner:BEIJING TONGFANG MICROELECTRONICS
Pipelined Montgomery modular multiplication method and pipelined Montgomery modular multiplication calculation device
InactiveCN110351087AImprove throughputImprove performancePublic key for secure communicationComputations using residue arithmeticParallel computingModular multiplier
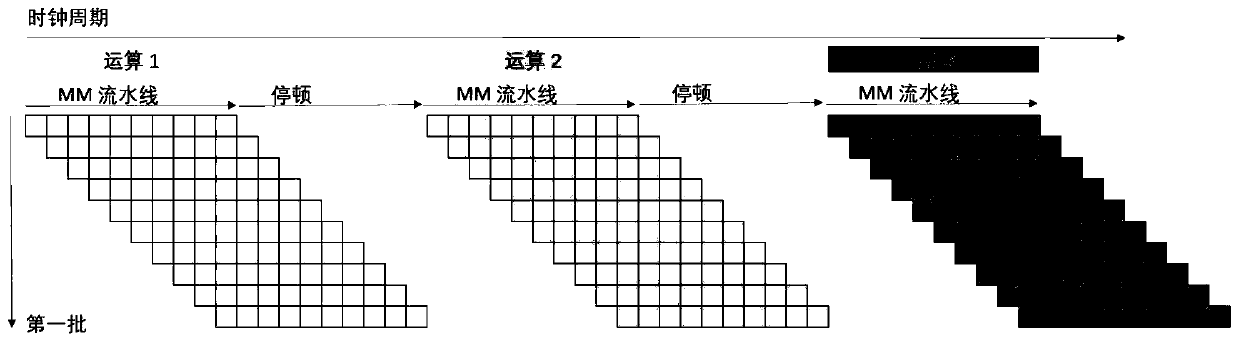
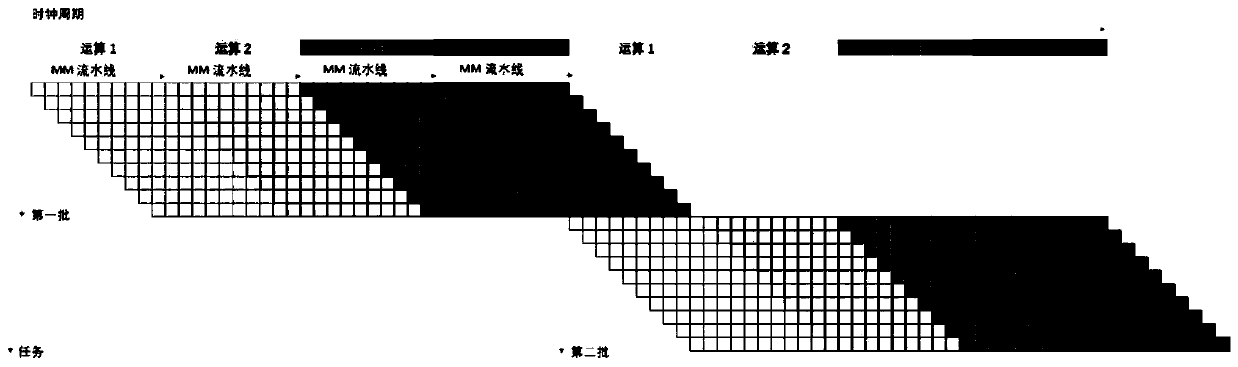
The invention discloses a pipelined Montgomery modular multiplication operation method and a pipelined Montgomery modular multiplication operation device, relates to the technical field of data cryptography algorithms, adopts a pipelined mode to improve Montgomery modular multiplication algorithm performance, increases throughput of a single Montgomery modular multiplier, and consumes less hardware resources and area than a traditional method using a plurality of Montgomery modular multipliers under the condition of the same throughput. Therefore, the modular multiplication number in unit timeis increased by dozens of times, and the Montgomery modular multiplier has higher performance / resource ratio than a non-pipelined Montgomery modular multiplier. Meanwhile, the asymmetric key algorithm hardware using the pipelined Montgomery modular multiplier can achieve higher performance with fewer hardware resources, and the throughput of Montgomery modular multiplication operation of any length is improved.
Owner:南京秉速科技有限公司
Key anti-power attack method
ActiveCN104917608AEasy to operateReduce computationKey distribution for secure communicationEncryption apparatus with shift registers/memoriesComputer hardwareInner loop
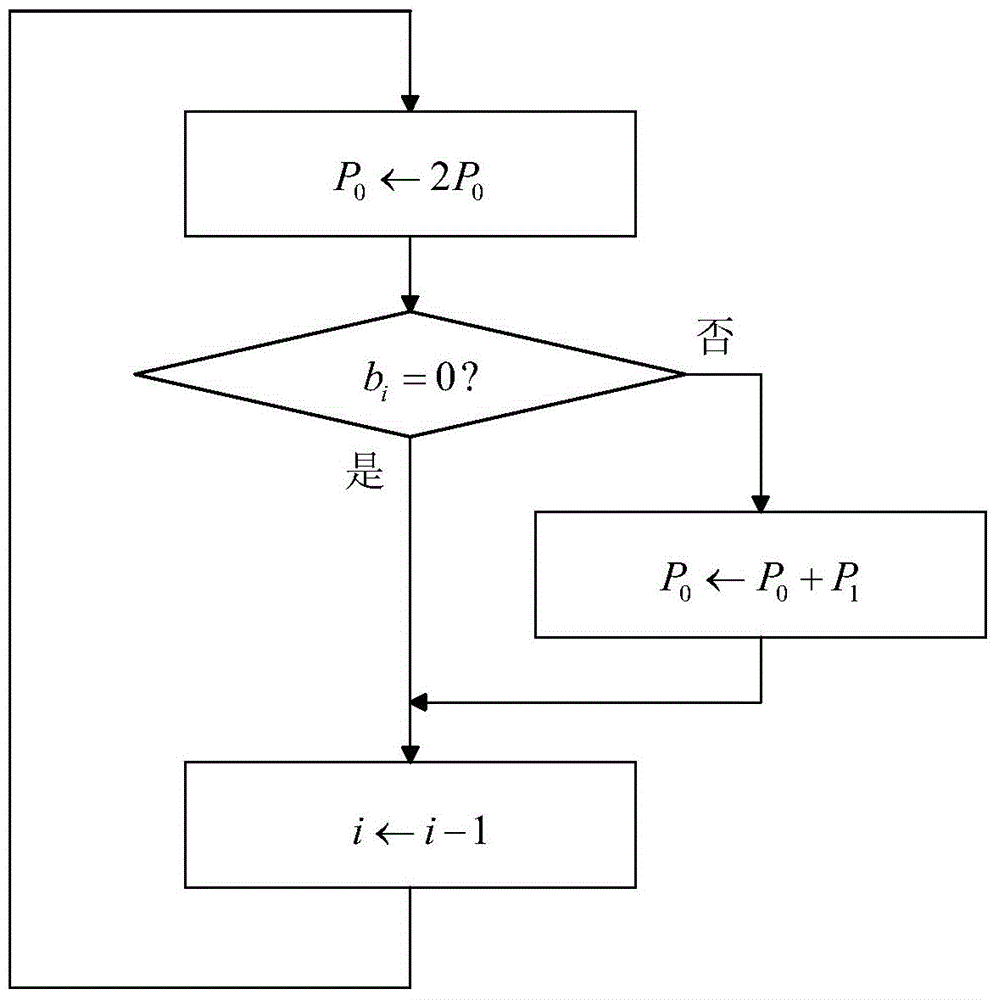
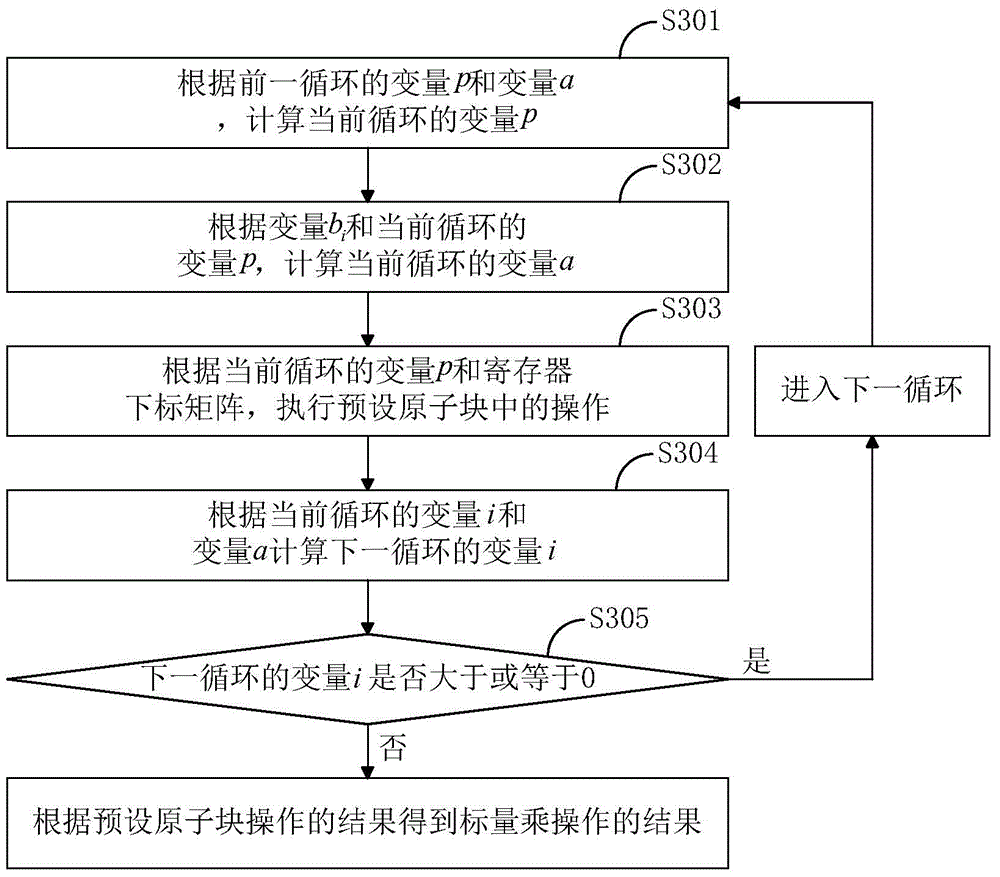
The invention discloses a key anti-power attack method. The method includes the step that a preset atomic block is utilized to perform point multiplying and / or point adding operation in scalar multiplication, wherein the preset atomic block contains modular multiplication operation, addition operation and subtraction operation. According to the method, the concept of the atomic algorithm is combined with the characteristics of a public key cryptographic algorithm, and therefore, the procedures of point adding operation and point multiplying operation can be optimized; an corresponding variables are adopted to control the internal loop of the scalar multiplication, and the scalar multiplication is converted to a modular multiplication-addition-subtraction atomic block loop. With the method of the invention adopted, computation burden required by the scalar multiplication can be greatly decreased, and the security of keys can be ensured, and the computation speed of the public key cryptographic algorithm can be improved.
Owner:TSINGHUA UNIV
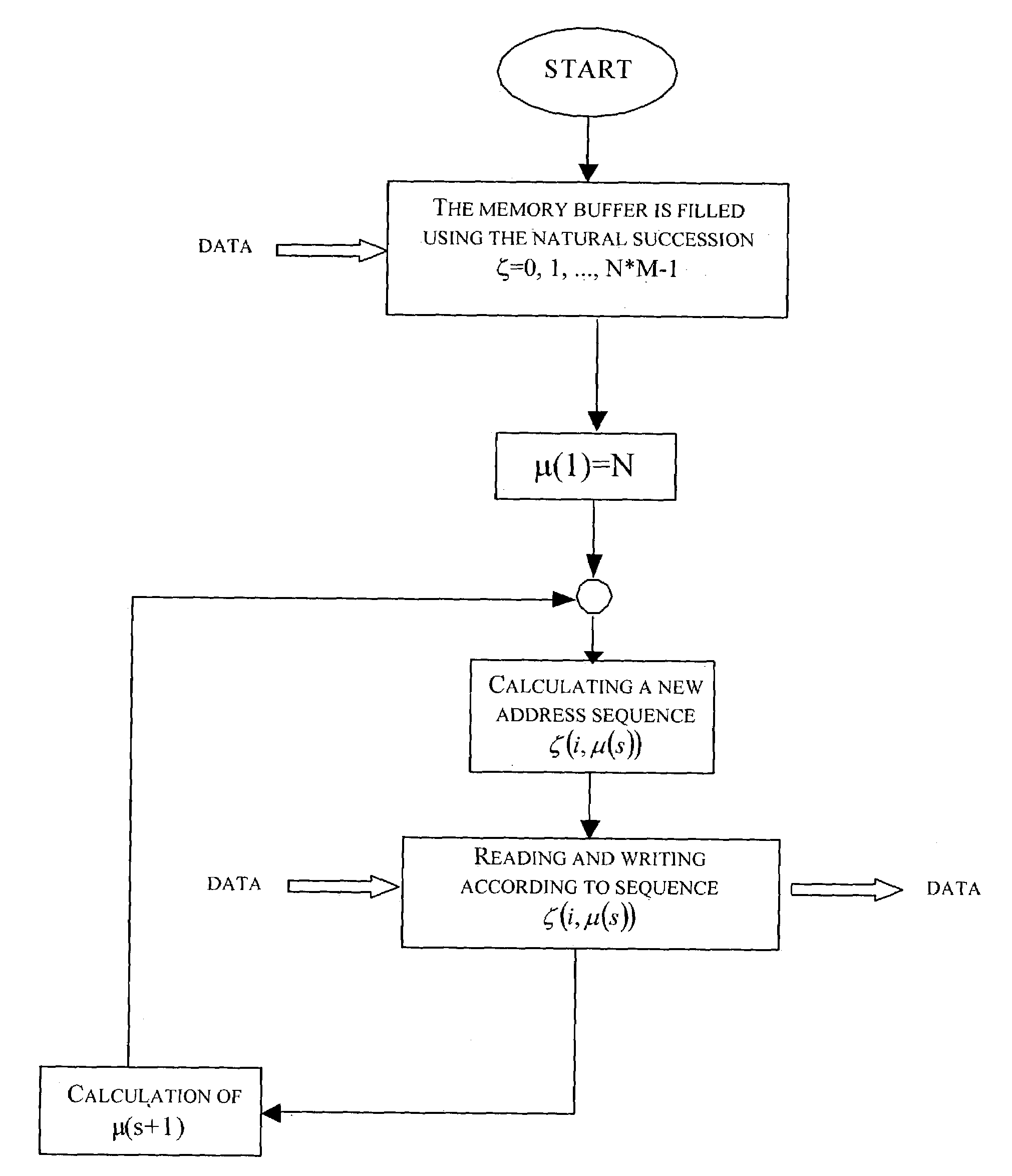
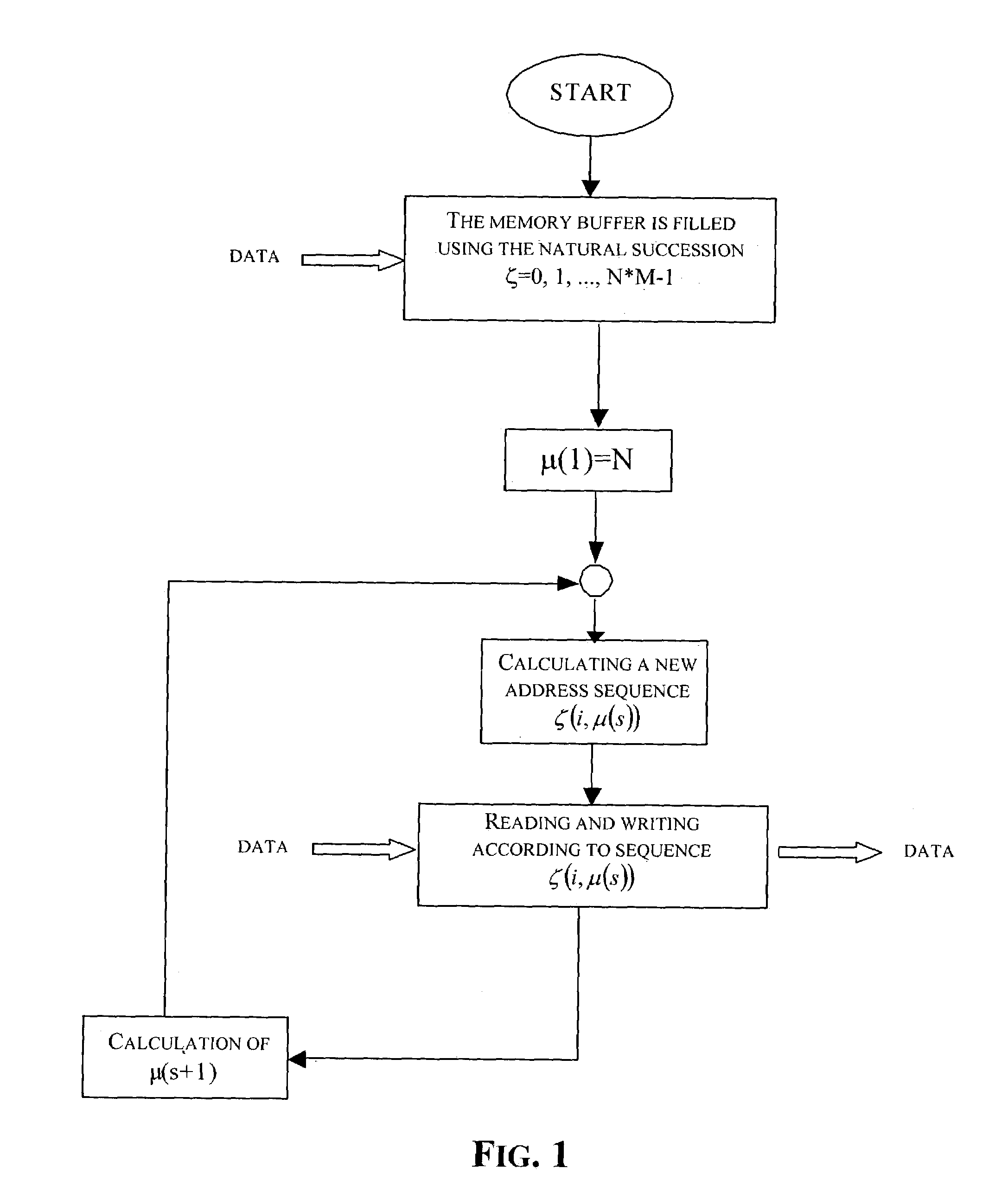
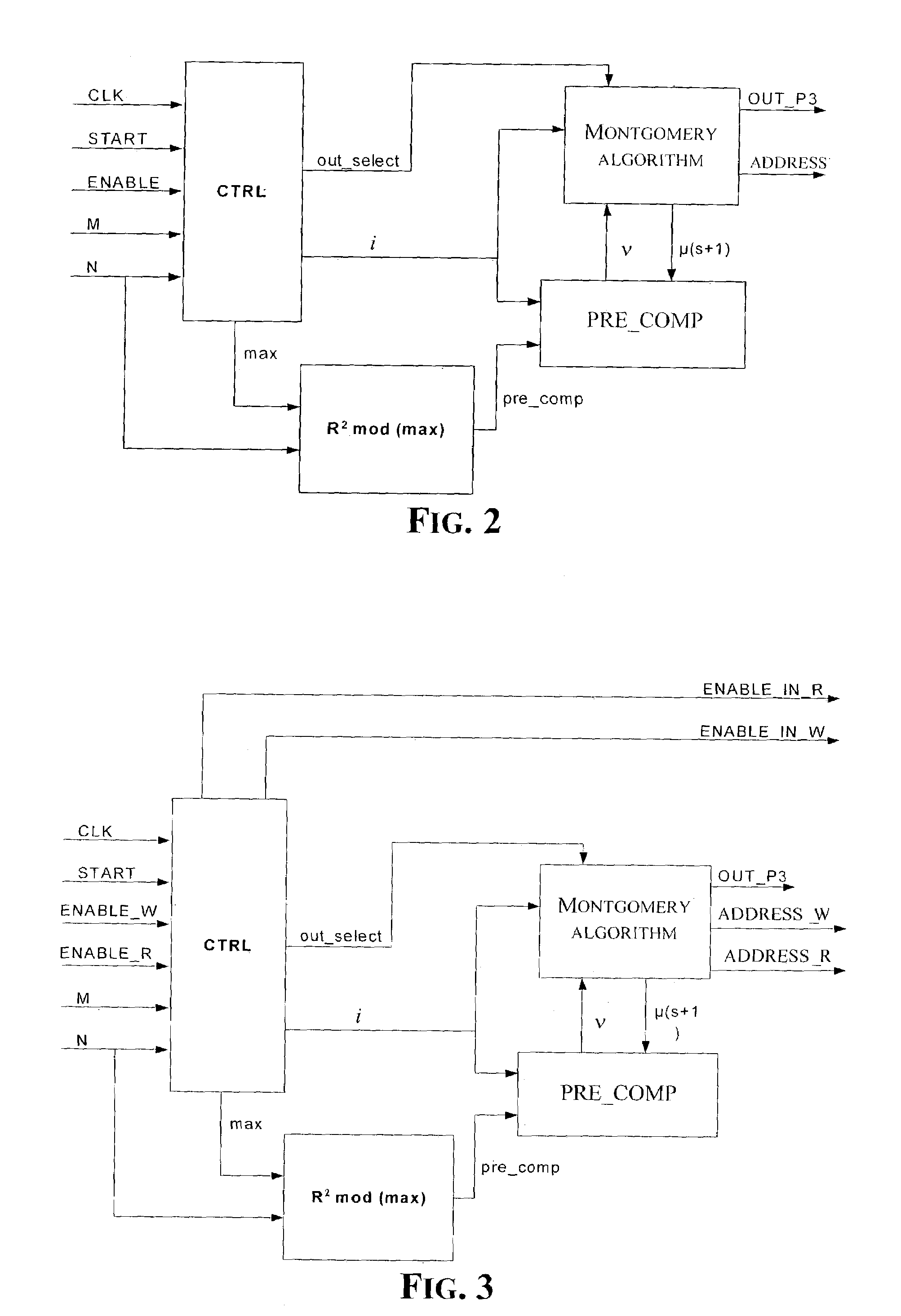
Method and circuit for generating memory addresses for a memory buffer
ActiveUS7058787B2Method is fastMemory adressing/allocation/relocationVisual presentation using printersMemory addressModular product
A method for generating sequences of memory addresses for a memory buffer having N*M locations includes making a first address and a last address of every sequence respectively equal to 0 and to N*M−1, assigning a first sequence of addresses, and each address but a last address of another sequence of addresses is generated by multiplying a corresponding address of a previous sequence by N, and performing a modular reduction of this product with respect to N*M−1. The method further includes calculating a greatest bit length of every address, and calculating an auxiliary constant as the modular reduction with respect to N*M−1 of the power of two raised to twice the greatest bit length. Each sequence of addresses includes storing an auxiliary parameter equal to an N+1th address of the current sequence, computing a first factor as the modular product with respect to N*M−1 of the auxiliary constant based upon a ratio between the auxiliary parameter and the power of two raised to the greatest bit length, and generating all addresses but the last of a sequence by performing the Montgomery algorithm using the first factor and an address index varying from 0 to N*M−2 as factors of the Montgomery algorithm, and with the quantity N*M−1 as modulus of the Montgomery algorithm, and the greatest bit length as the number of iterations of the Montgomery algorithm.
Owner:STMICROELECTRONICS SRL
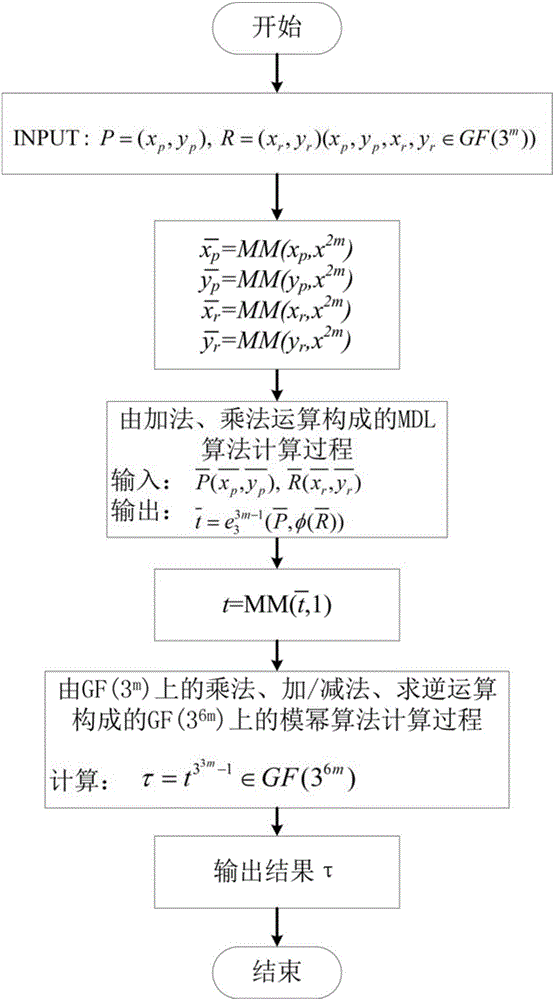
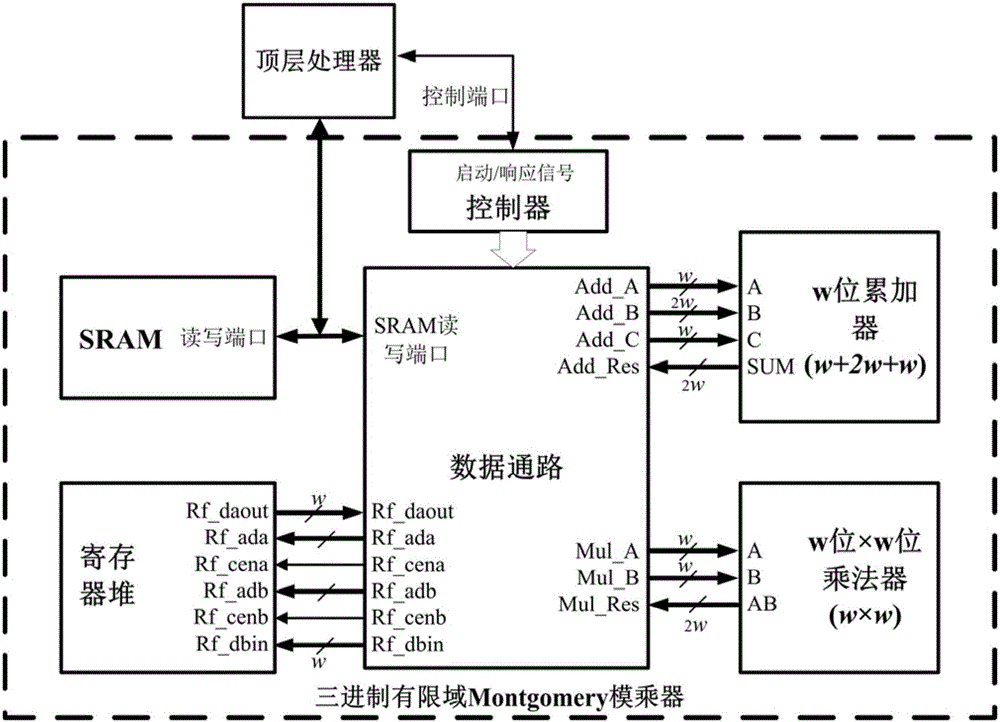
Montgomery modular multiplication based Tate pairing algorithm and hardware structure therefor
ActiveCN105068784AReduce hardware overheadReduce power overheadDigital data processing detailsHardware structureStatic random-access memory
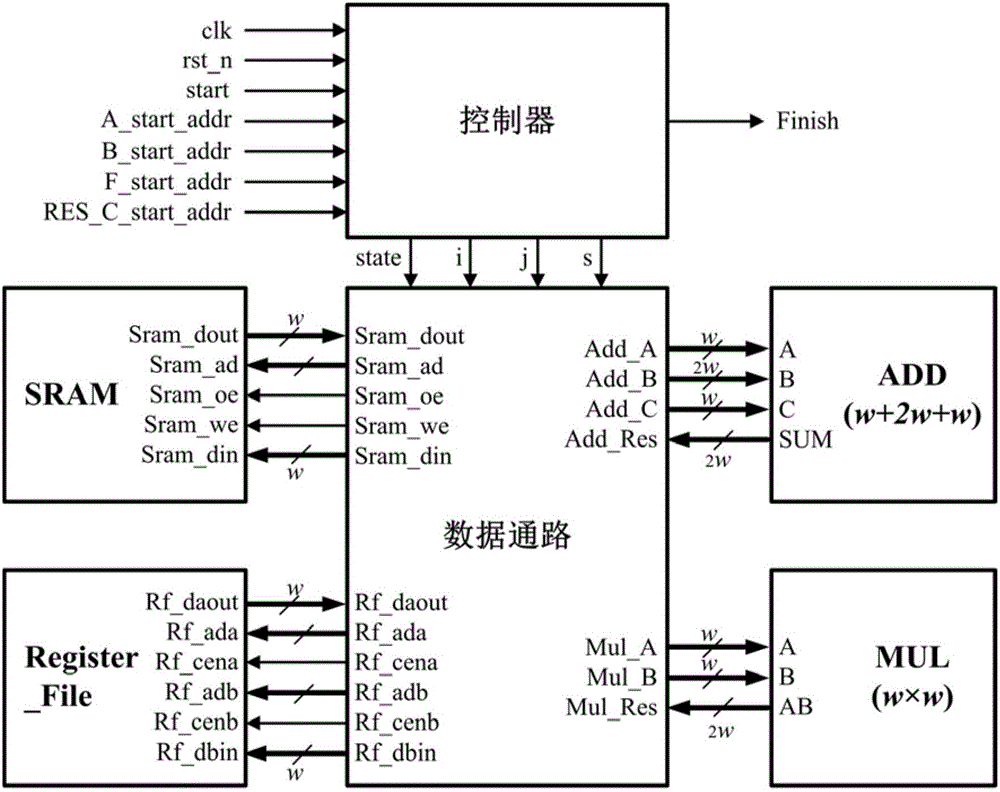
The invention belongs to the technical field of realization of cryptographic algorithms of embedded systems and particularly relates to a ternary finite field Montgomery modular multiplication based Tate pairing algorithm and a hardware structure for realizing the algorithm. The algorithm comprises: converting X coordinates and Y coordinates of two input points P and R on an elliptic curve to a Montgomery domain from a defined GF(3m) domain; according to an MDL (minimum description length) algorithm procedure taking multiplication, addition / subtraction and cubic operation on GF(3m) as basic operations, performing operation in the Montgomery domain; and converting a calculation result to the GF(3m) domain from the Montgomery domain, and performing 33m-1-power modular exponentiation on the calculation result. The hardware structure comprises a top-level processor, a controller, a ternary accumulator, a ternary multiplier, a register file and an SRAM (static random access memory), wherein the controller is used for controlling input of the ternary accumulator and the ternary multiplier and read-write operation of the SRAM and the register file so as to control data transmission of the whole circuit.
Owner:TSINGHUA UNIV
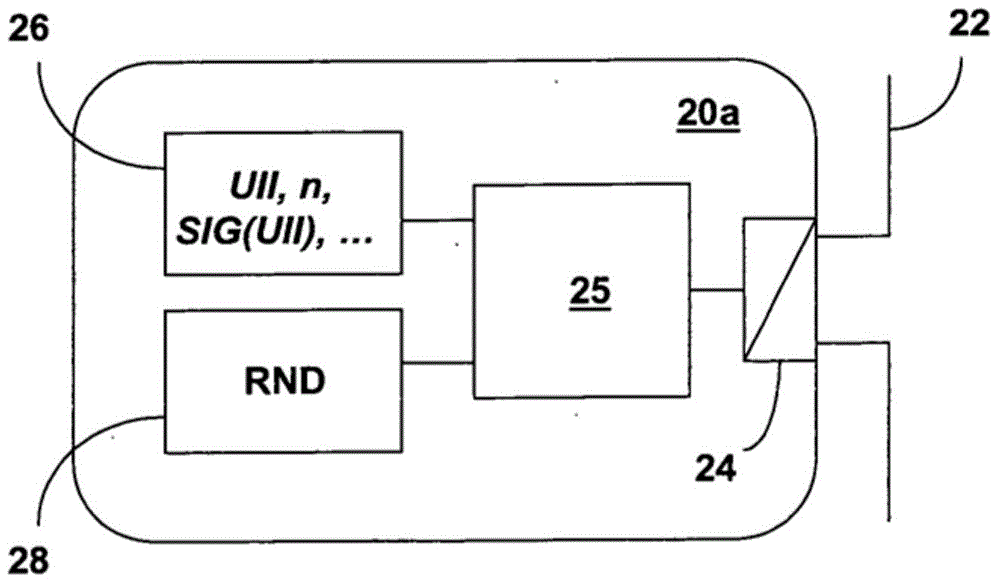
Methods and system for secure communication between an rfid tag and a reader
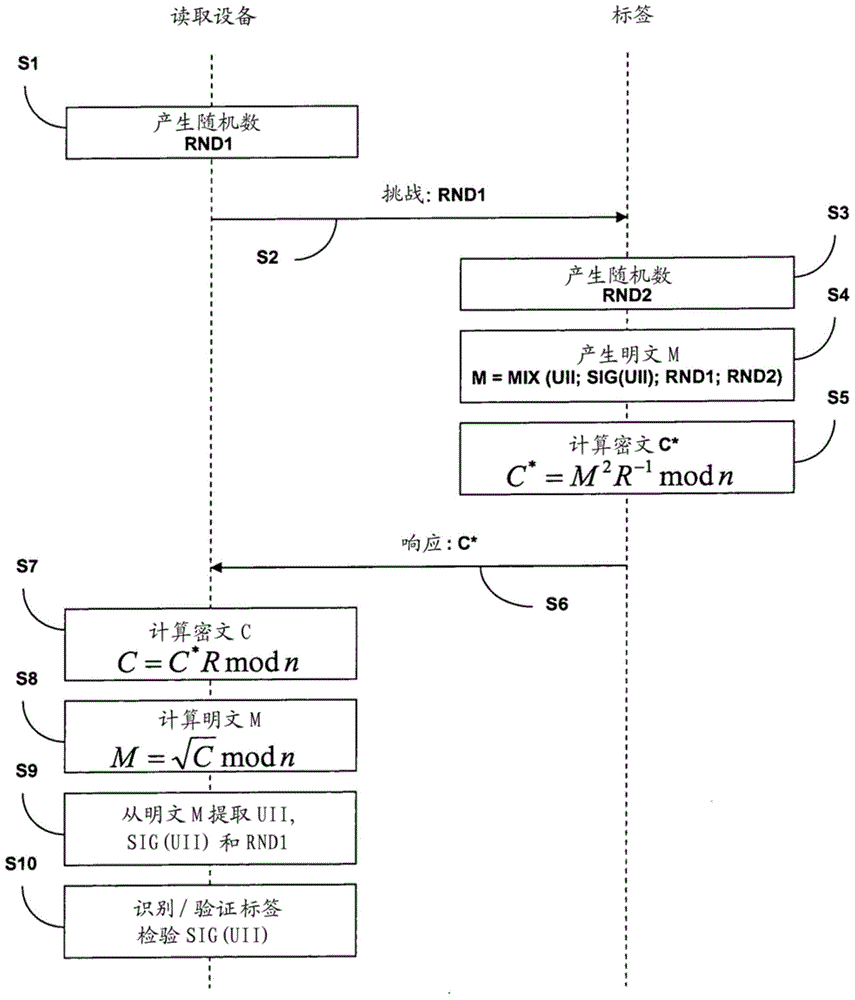
ActiveCN104488219AReduce processing timeSecurity is not compromisedPublic key for secure communicationUser identity/authority verificationPlaintextSecure communication
The invention relates to methods and a system for secure communication between an RFID tag and a reader via the air interface and to corresponding RFID tags and corresponding readers. The invention is based on the fundamental idea that, for the purpose of secure communication between an RFID tag and a reader, a modification of Rabin's method is used, in which, within the scope of encrypting plain text M, which includes an identification element of the RFID tag or of an object provided with the latter, the Montgomery residual ('Montgomery reduction') of the square of the plain text M modulo n with respect to a Montgomery base R, that is to say C* = Mu2 R-1mod n, is calculated from the RFID tag instead of the square of the plain text M modulo n, that is to say M2 mod n, and the resultant ciphertext C* is used to authenticate the RFID tag. In this case the modulus n = p.q is the public key of the reader, the prime numbers p, q are the private key of the reader and the Montgomery base R is an integer greater than the modulus n.
Owner:捷德移动安全有限责任公司
Embedded device having countermeasure function against fault attack
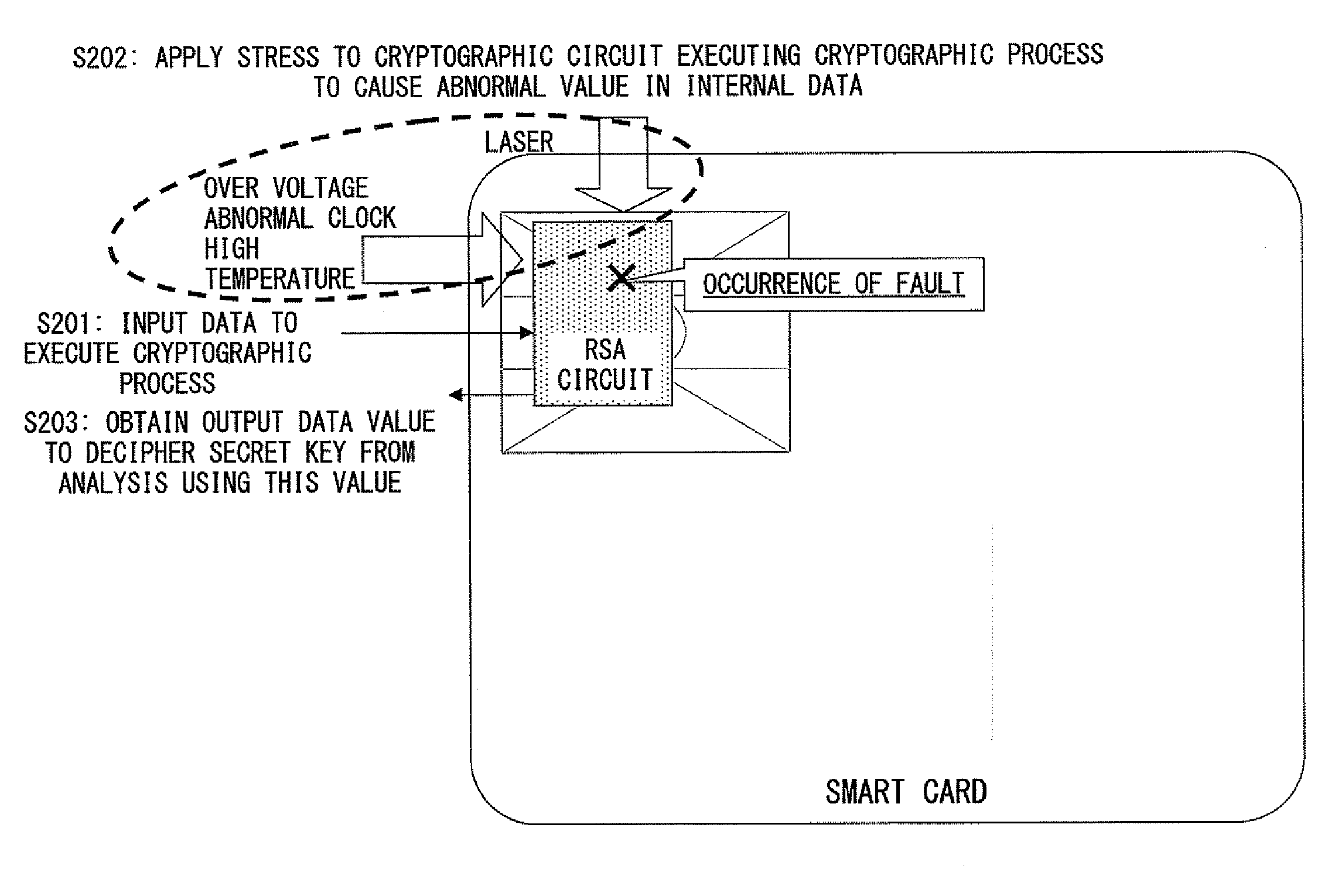
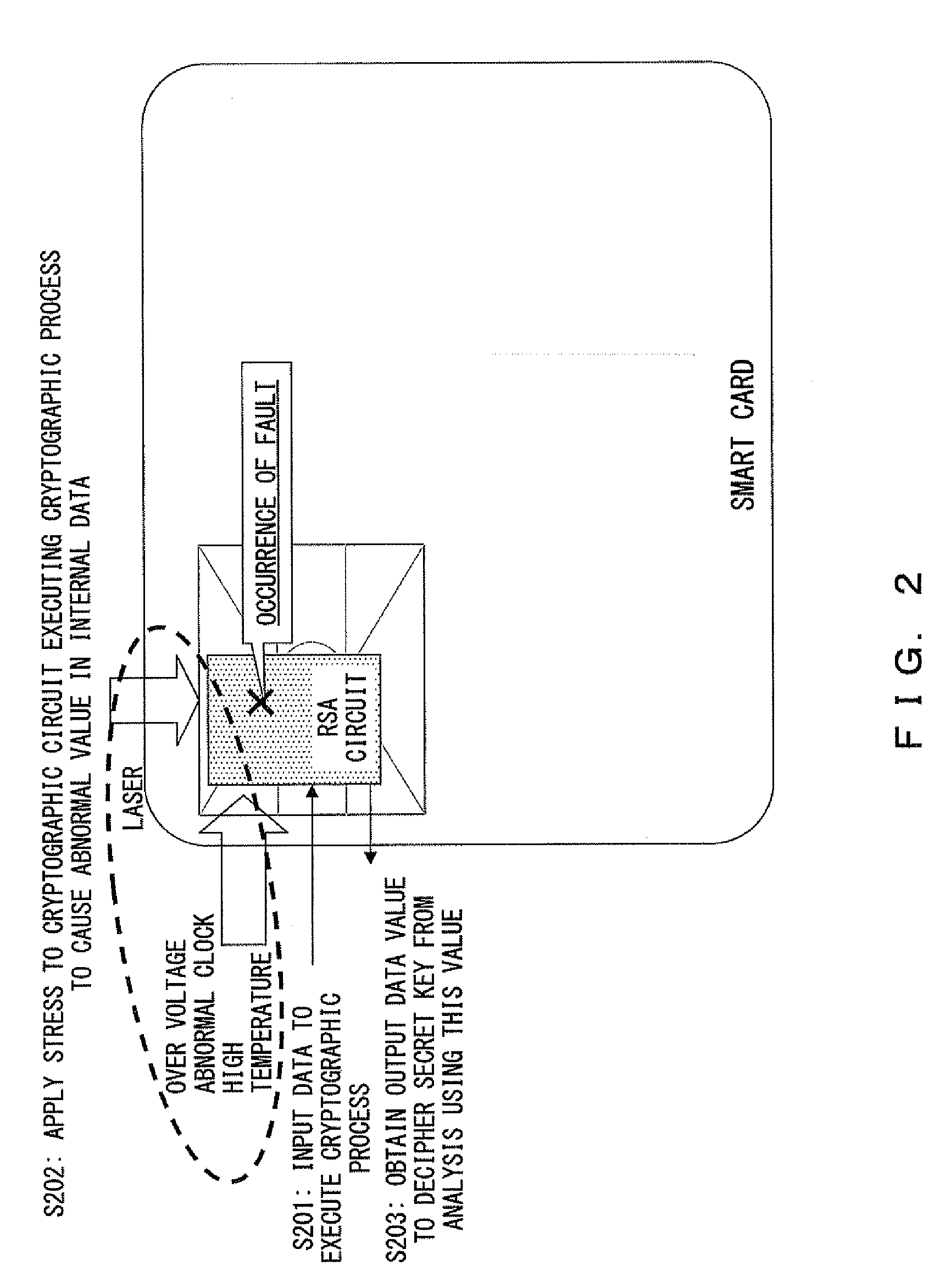
InactiveUS20100031055A1Improve securityAvoid crackingUnauthorized memory use protectionHardware monitoringCountermeasureValue set
A cryptographic processing device, comprising: a storage unit; initial setting unit for setting a value to be stored in the storage unit; Montgomery modular multiplication operation unit for performing a Montgomery modular multiplication operation plural times for a value set by the initial setting unit; and fault attack detection unit for determining whether or not a fault attack occurred for each of at least some parts of the Montgomery modular multiplication operations performed plural times.
Owner:FUJITSU LTD
High-speed point addition operation method and device for elliptic curve password
PendingCN110460443AAvoid Time to Improve Performance PitfallsImprove performancePublic key for secure communicationBatch processingMultiple point
The invention discloses a high-speed point addition operation method and a device for elliptic curve cryptography, which are realized by matching a pipelined Montgomery modular multiplier with a modular adder, and 16 modular multiplication operations are executed by one point addition operation; according to the point addition circuit using one or more modular multipliers, each modular multiplication operation executes an operation request of one batch, and the system can calculate N operations at the same time, so that the overall performance of the system is improved by N times. According tothe method, the pipelined characteristics of the pipelined Montgomery modular multiplier are utilized, a bottom pipelined hardware circuit is ingeniously multiplexed, multiple point addition operations are executed at the same time in a batch processing mode, and the throughput of the whole system is improved by several orders of magnitudes. Therefore, the performance / hardware resource ratio andthe performance / energy consumption ratio of the method are improved by several times or even dozens of times compared with those of the prior art. Meanwhile, the optimal number of Montgomery modular multipliers and modular adders is selected by analyzing the characteristics of the point addition algorithm, and the optimal configuration of performance and resource use is achieved.
Owner:南京秉速科技有限公司
An encryption and decryption hardware system and method based on RSA cryptographic algorithm
ActiveCN109039640AReduce computationHigh speedPublic key for secure communicationUser identity/authority verificationComputer hardwareMontgomery reduction
The invention discloses an encryption and decryption hardware system based on RSA cryptographic algorithm, comprises an RSA main control module, a key generation module, an encryption control module,a decryption control module, a modulo exponentiation module, a modulo multiplication operation module and a large number multiplier module, wherein, the RSA main control module is used for calling theencryption control module and the decryption control module; The key generation module is used for generating a public key {e, N} and a private key {d, N} needed for encryption and decryption; The invention aims at the problems of large calculation amount, slow encryption and decryption operation speed and large area realized by hardware in the prior RSA hardware system, and under the condition of giving consideration to the hardware area and the realization speed, the improved Montgomery modular multiplication algorithm and the L-R modulo exponentiation algorithm are combined. The hardware system and the method of RSA encryption and decryption are designed, so the hardware system and the method can reduce the calculation amount in the process of RSA encryption and decryption, improve thespeed of RSA encryption and decryption, and reduce the area of the chip.
Owner:GUANGDONG UNIV OF TECH
Elliptic curve cryptographic coprocessor
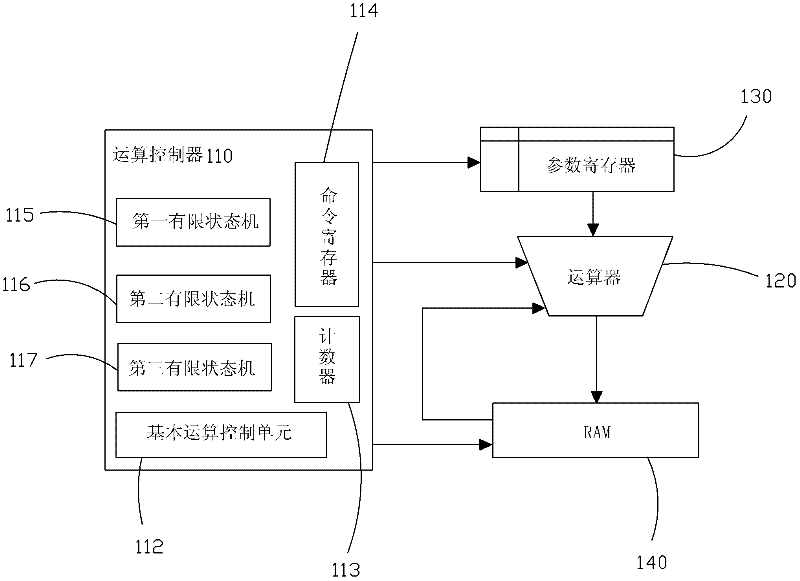
ActiveCN102412965ASimple structureReduce volumeUser identity/authority verificationCoprocessorControl signal
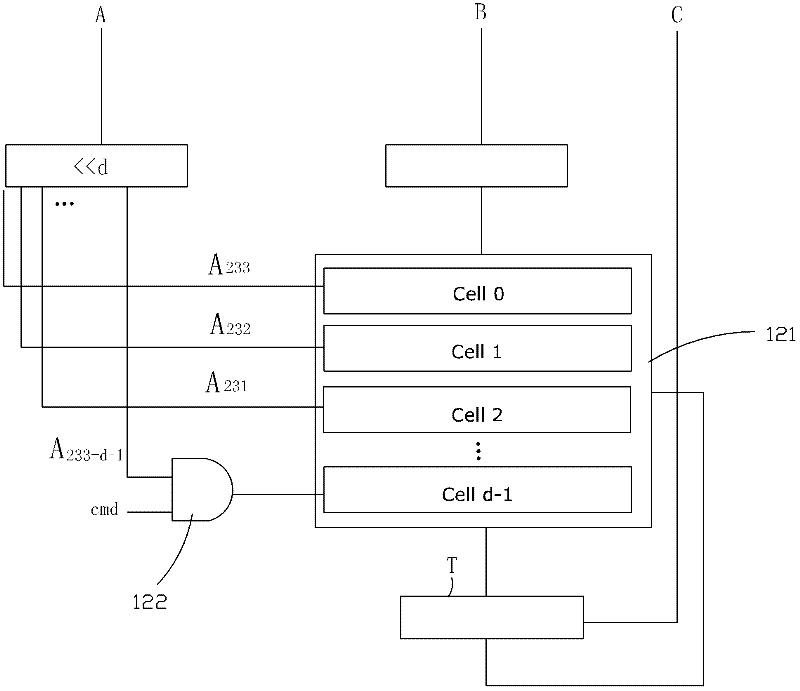
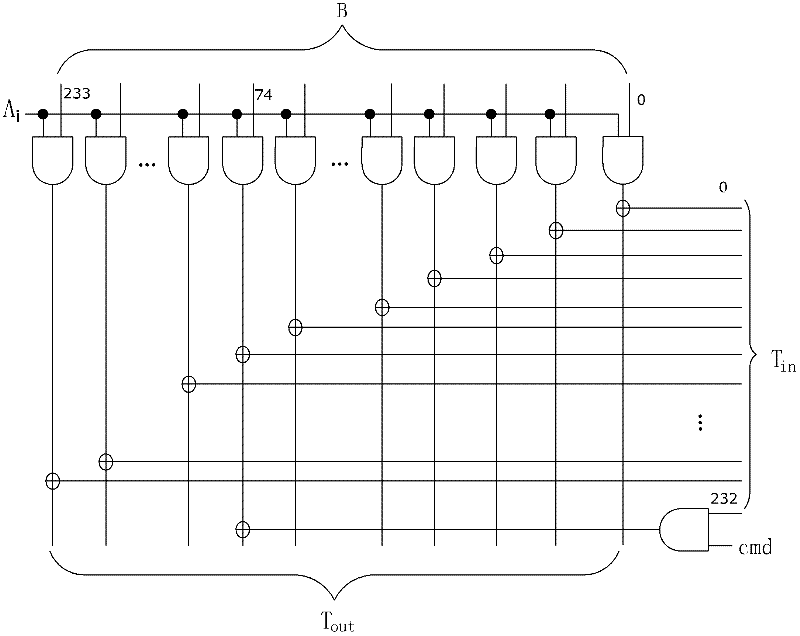
The invention provides an elliptic curve cryptographic coprocessor, comprising an arithmetic controller, an arithmetic device, a parameter register and a RAM (Random-Access Memory), wherein the arithmetic controller is respectively in electrical connection with the arithmetic device, the parameter register and the RAM, and is used for elliptic curve point multiplication and generating a control signal for the arithmetic device to finish modular addition and modular multiplication on a base field; the arithmetic device is respectively in electrical connection with the parameter register and the RAM, and is used for modular addition and modular multiplication on the base field; the parameter register is used for storing parameters of an elliptic curve equation and pre-computing the parameters; and the RAM is used for receiving the data transmitted from the outside and storing the computation result, and exchanging data with the outside. The elliptic curve cryptographic coprocessor has simple interface manners; the computation speed is increased greatly by means of a state machine; the elliptic curve point multiplication process is optimized, intermediate variables are reduced, and consequently, the number of registers is reduced; and a modular addition and modular multiplication circuit on the base field is reused to the greatest extent, so that the circuit area is reduced.
Owner:SHENZHEN DECARD SMART CARD TECH
Low-energy-consumption small-area data processing method and data processing device thereof
InactiveCN103888246AReduce the number of cyclesReduce power consumptionEncryption apparatus with shift registers/memoriesTemporary variableControl signal
Owner:CHINA VISION MICROELECTRONICS
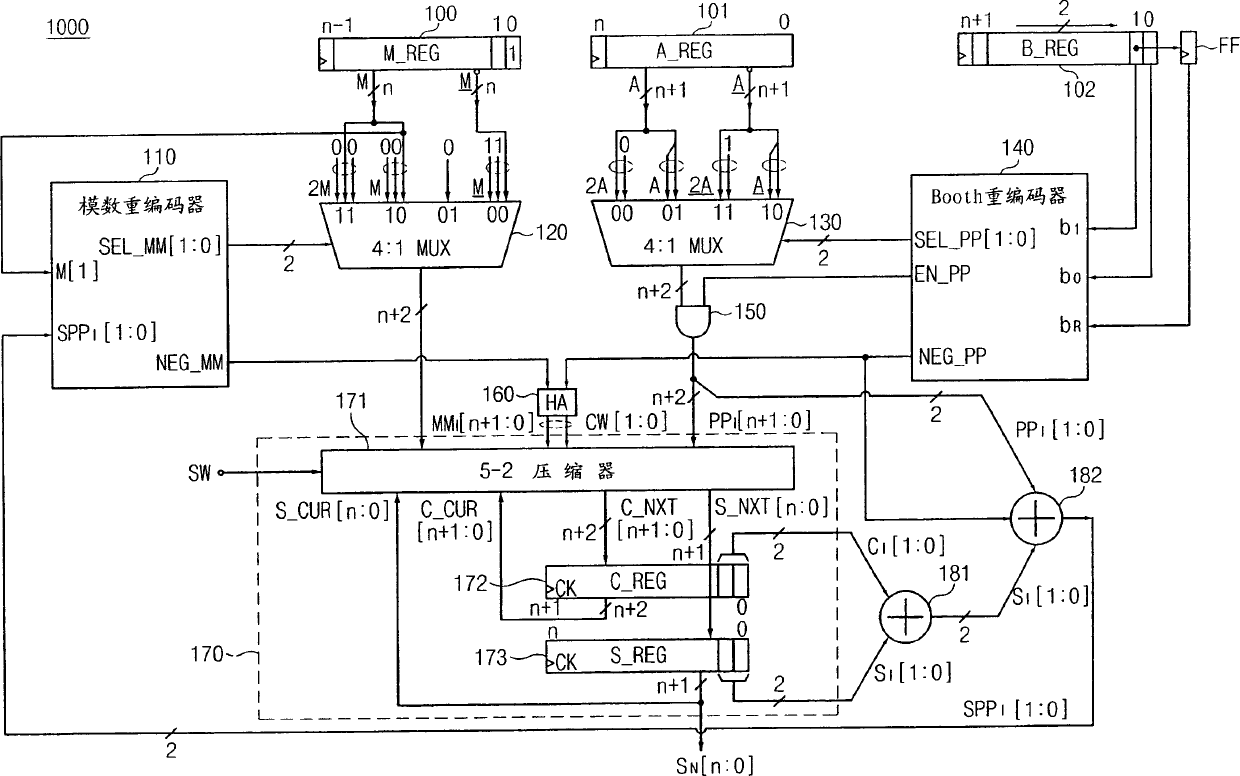
Data processing method and modular multiplication operation method and apparatus based on Montgomery modular-multiplication
ActiveCN106681691ASmall amount of calculationImprove computing efficiencyComputations using residue arithmeticSimulationModular multiplier
The invention provides a data processing method and a modular multiplication operation method and an apparatus based on the Montgomery modular-multiplication. The data processing method based on the Montgomery modular-multiplication comprises the steps of using the following steps to calculate a first value S2: acquiring an initial value s10 of a first memory, wherein the initial value s10 is an n-digit number, the digit n plus n-c is 0, the digit n-c is 1; the calculation is made to let s10 be subtracted by a modular number N, and the result is made to be added by 1 to get a result s11, which is written in the first memory; n-c times of modular addition is made to the s11 in the first memory to get a calculated result s1n-c+1; the calculated result s1n-c+1 takes a modular from N, the result s1 is written in the first memory, the Montgomery modular multiplier is called to implement n-1 times of modular multiplication to the initial value of a second memory, the result R2mod N of the n-1th time of modular multiplication is treated as a first value s2 to be exported. The data processing method and the modular multiplication operation method based on Montgomery modular-multiplication can be used for reducing the calculation amount of the Montgomery modular multiplier calculation, and enhance the calculation efficiency.
Owner:SHANGHAI FUDAN MICROELECTRONICS GROUP
Montgomery modular multiplier and method thereof using carry save addition
InactiveCN1570848AGuaranteed normal operationApplicability is clearComputation using non-contact making devicesComputations using residue arithmeticCarry propagationModular multiplier
A method of reducing power consumption and / or enhancing computation speed in the modulus multiplication operation of a Montgomery modulus multiplication module. A coding scheme reduces the need for an adder or memory element for obtaining multiple modulus values, and the use of carry save addition with carry propagation addition enhances the computational speed of the multiplication module.
Owner:SAMSUNG ELECTRONICS CO LTD
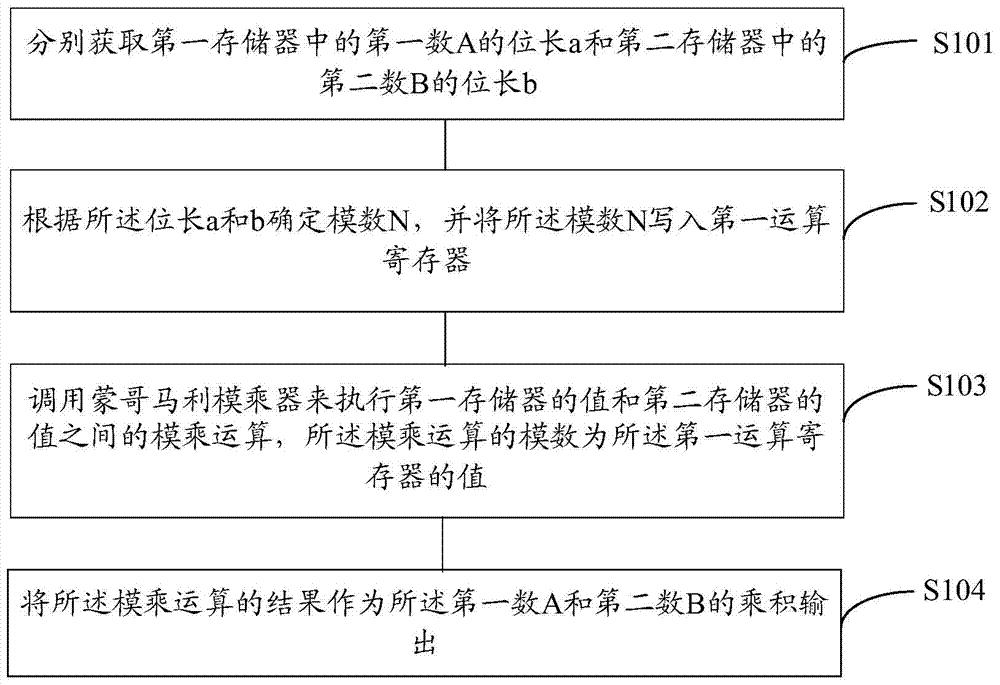
Method and device for processing data on basis of Montgomery modular multiplication
ActiveCN104750455AAvoid product operationsShorten the timeDigital data processing detailsProcessor registerModular multiplier
The invention provides a method and a device for processing data on the basis of Montgomery modular multiplication. The method includes respectively acquiring bit lengths a of first numbers A in first storages and bit lengths b of second numbers B in second storages; determining module numbers N according to the bit lengths a and b and writing the module numbers N into first arithmetic registers; calling Montgomery modular multipliers to execute modular multiplication on values of the first storages and values of the second storages; outputting products of the first numbers A and the second numbers B. Bit lengths n of the module numbers N are larger than or equal to the sums of the bit lengths a and b. Module numbers of modular multiplication are values of the first arithmetic registers. The products of the first numbers A and the second numbers B are results of modular multiplication. The method and the device have the advantage that the encryption processing efficiency can be improved by the aid of the method and the device.
Owner:SHANGHAI FUDAN MICROELECTRONICS GROUP
A method of module multiplication operation and apparatus and use thereof
InactiveCN1691580AReduce complexitySimplify Design ComplexitySecuring communicationRound complexityCommunications system
The invention relates to an apparatus and method for modular multiplying arithmetic and its usage. The inventive modular multiplying arithmetic method comprises the steps of: breaking up the modular multiplying operating formula to realize it by using the recursive solution which repeated applying a fixing algorithm (or function) on the result of the prior algorithm; get the wanted remainder. The invention provides a method for realizing the lower algorithm complexity of the Montgomery modular multiplying and a quick and low power consuming apparatus for the algorithm. It can be used in RSA encryption processing system and the interlace mode generation of the internal interlace device of the Bode coder-decoder in the third generation communication system.
Owner:上海明波通信技术股份有限公司
Chip and batch modular operation method for chip
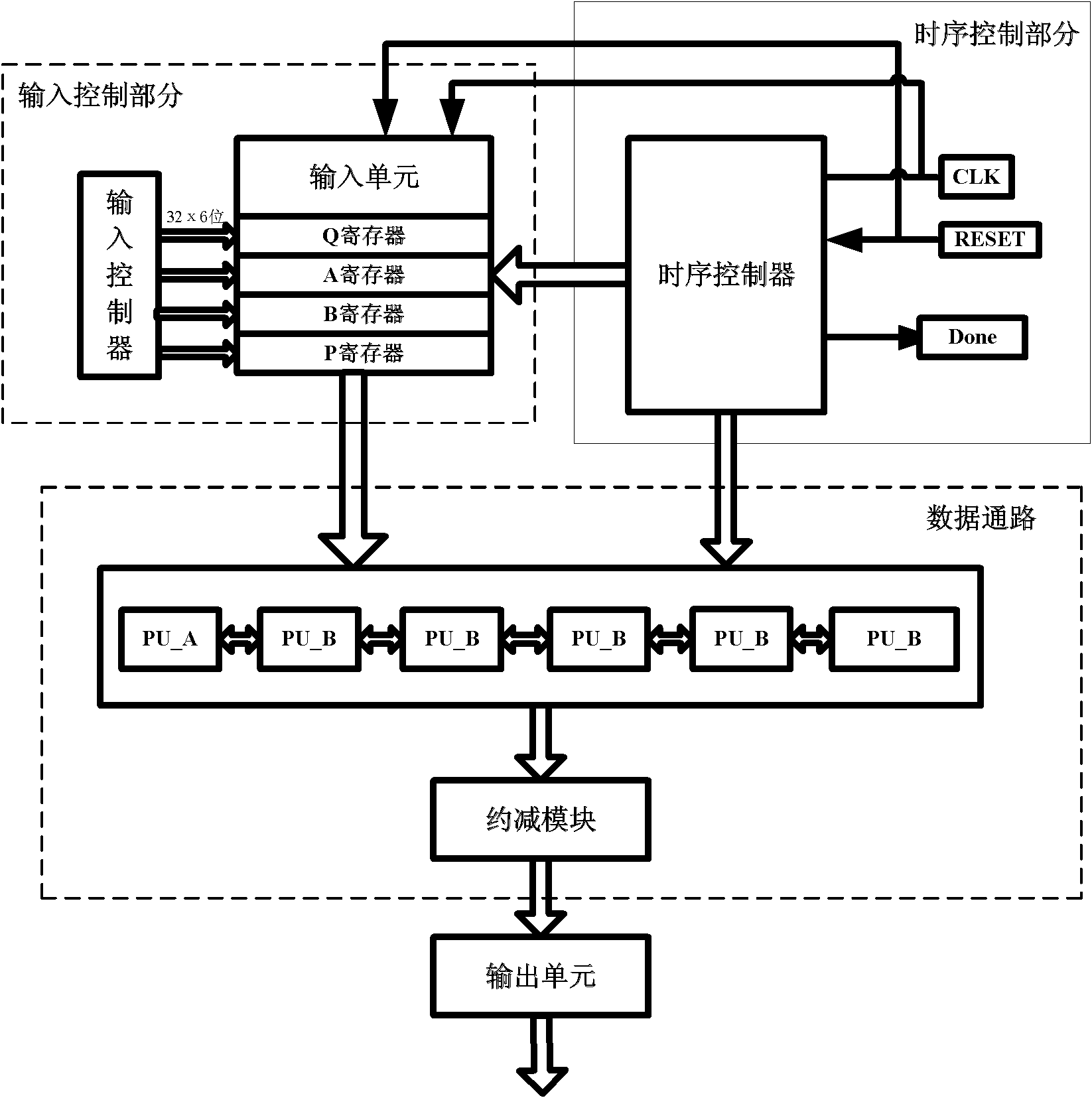
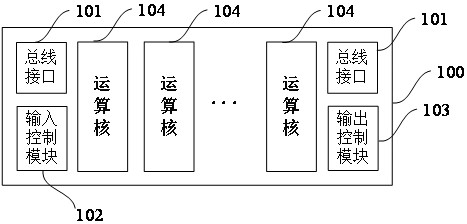
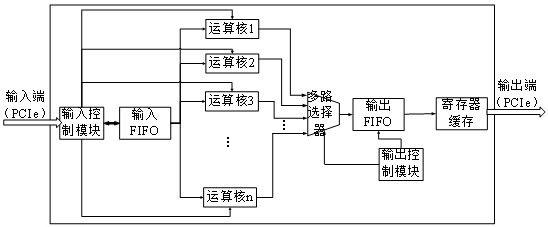
ActiveCN113031920AIncrease flexibilityImprove adaptabilityDigital data protectionComputations using residue arithmeticComputer architectureInput control
The embodiment of the invention provides a chip and a batch modular operation method for the chip. The chip is used for carrying out privacy calculation and comprises a bus interface, an input control module, an output control module and at least two operation cores; the bus interface is used for receiving n input data from a host side; the input control module is used for distributing n parts of input data to n operation cores for parallel modular operation based on a multi-core scheduling algorithm; the operation cores are used for performing modular operation on received input data based on a preset Montgomery modular multiplication algorithm, each operation core comprises an independent modular residue calculation unit or a plurality of operation cores share one modular residue calculation unit, and the modular residue calculation unit is used for performing modular residue calculation on a cyclic calculation result in the Montgomery modular multiplication algorithm so as to obtain a modular operation result; and the output control module is used for controlling n modular operation results calculated by the n operation cores to be sequentially output to a host side through the bus interface. According to the embodiment of the invention, the privacy calculation efficiency can be improved.
Owner:HUAKONG TSINGJIAO INFORMATION SCI BEIJING LTD
Arithmetic circuit for montgomery multiplication and encryption circuit
InactiveCN101782846AHigh computing speedPublic key for secure communicationComputations using residue arithmeticProcessor registerParallel computing
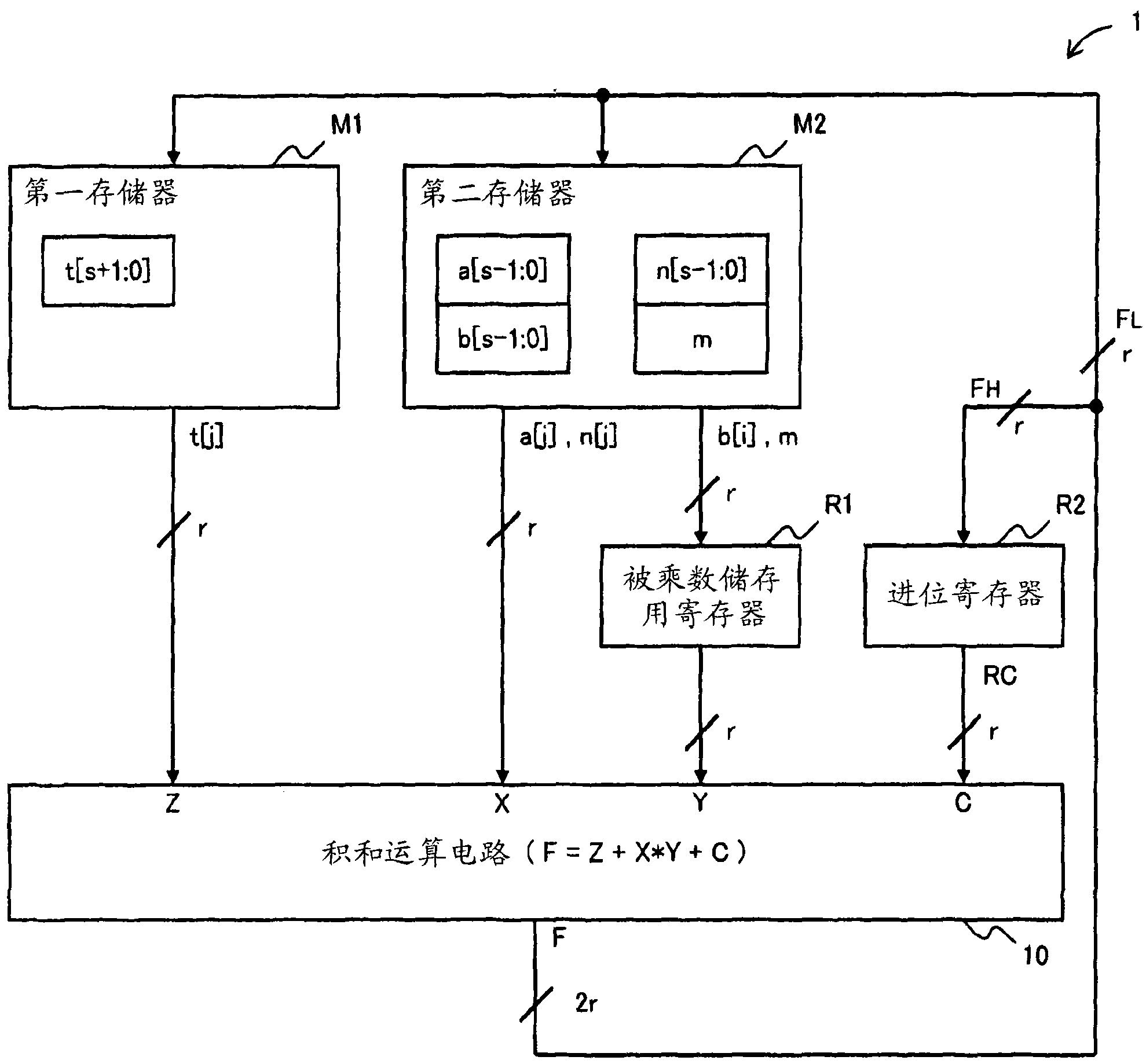
An arithmetic circuit capable of Montgomery multiplication using only a one-port RAM is disclosed. In a first read process, b[i] is read from a memory M2 of a sync one-port RAM for storing a[s-1: 0] and b[s-1: 0] and stored in a register R1. In a second read process, a[j] is read from the memory M2, t[j] from a memory M1 of a sync one-port RAM for storing t[s-1: 0], b[i] from the register R1, and a value RC from a register R2, and input to a sum-of-products calculation circuit 10 for calculating t[j]+a[j]*b[j]+RC. In a write process, the calculation result data FH is written in the register R2, and the calculation result data FL in the memory M1 as t[j]. A first subloop process for repeating the second read process, the sum-of-products calculation process and the write process is executed after the first read process.
Owner:SHARP KK
Device and method for calculating conversion parameter of montgomery modular multiplication and program therefor
InactiveUS20060235921A1Promote generationIncrease speedDigital computer detailsComputations using residue arithmeticMontgomery reductionComputer science
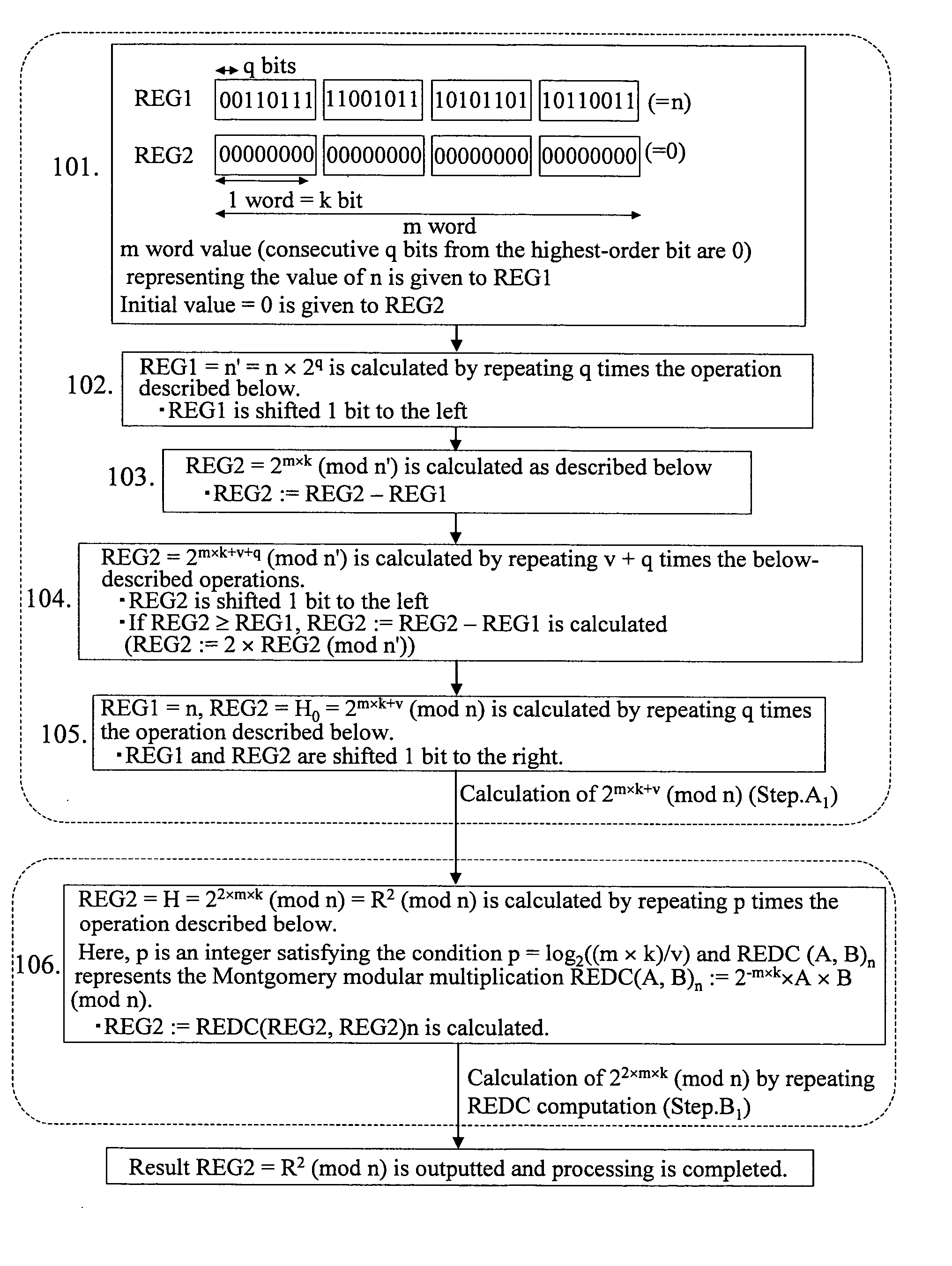
A method for calculating a conversion parameter of the Montgomery modular multiplication to improve the efficiency of software installation, comprising a first step for calculating H0=2v×R (mod n) (where v is an integer, v≧1, and (m×k) / v is an integer), a second step for calculating Hp=2v×2<?img id="custom-character-00001" he="3.13mm" wi="2.12mm" file="US20060235921A1-20061019-P00900.TIF" alt="custom character" img-content="character" img-format="tif" ?>p×R (mod n) from H0=2v×R (mod n) by repeating Hi=REDC(Hi-1, Hi-1)n with respect to i=1, 2, . . . , p (where p represents an integer satisfying the condition 2p≧(m×k) / v>2p−1, REDC represents the Montgomery modular multiplication REDC(a, b)n=a×b×R−1 (mod n), and xˆi represents exponential computation xi); and a third step for calculating Hp=R2 (mod n) by calculating Hp=REDC(Hp, g)n with respect to Hp obtained in the second step when 2p>(m×k) / v (where g=2k×E(p,m,k), E(p, m, k)=2×m−(v×2p) / k) and finally outputting Hp as R2 (mod n).
Owner:FUJITSU LTD
Montgomery modular multiplication device and embedded security chip with same
ActiveCN104793919AAvoid Calculating Conversion FactorsObvious advantagesEncryption apparatus with shift registers/memoriesComputations using residue arithmeticEmbedded securityConversion coefficients
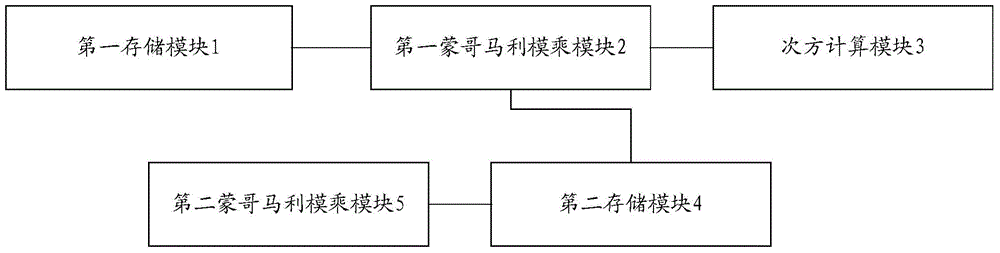
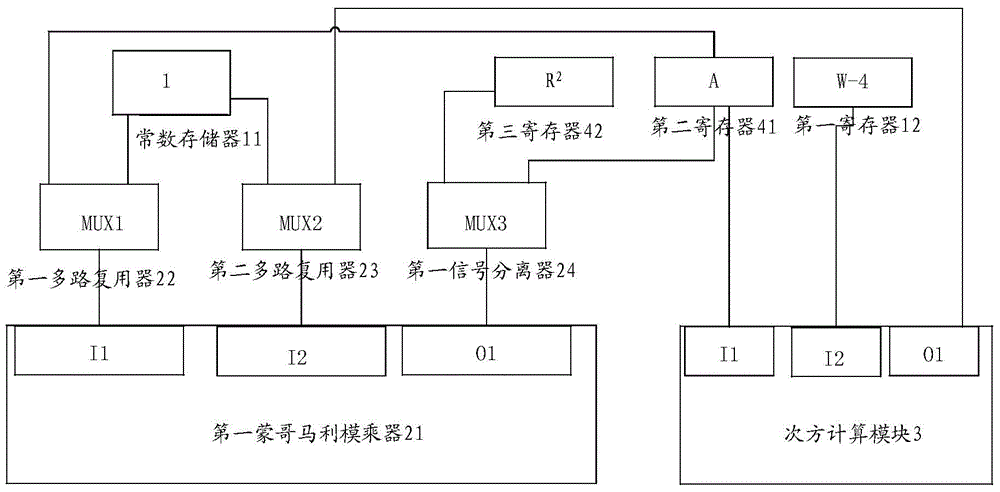
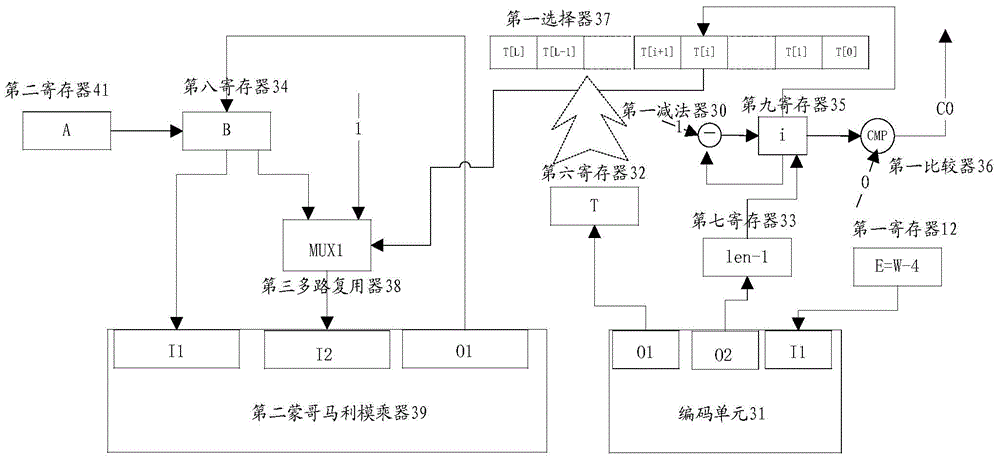
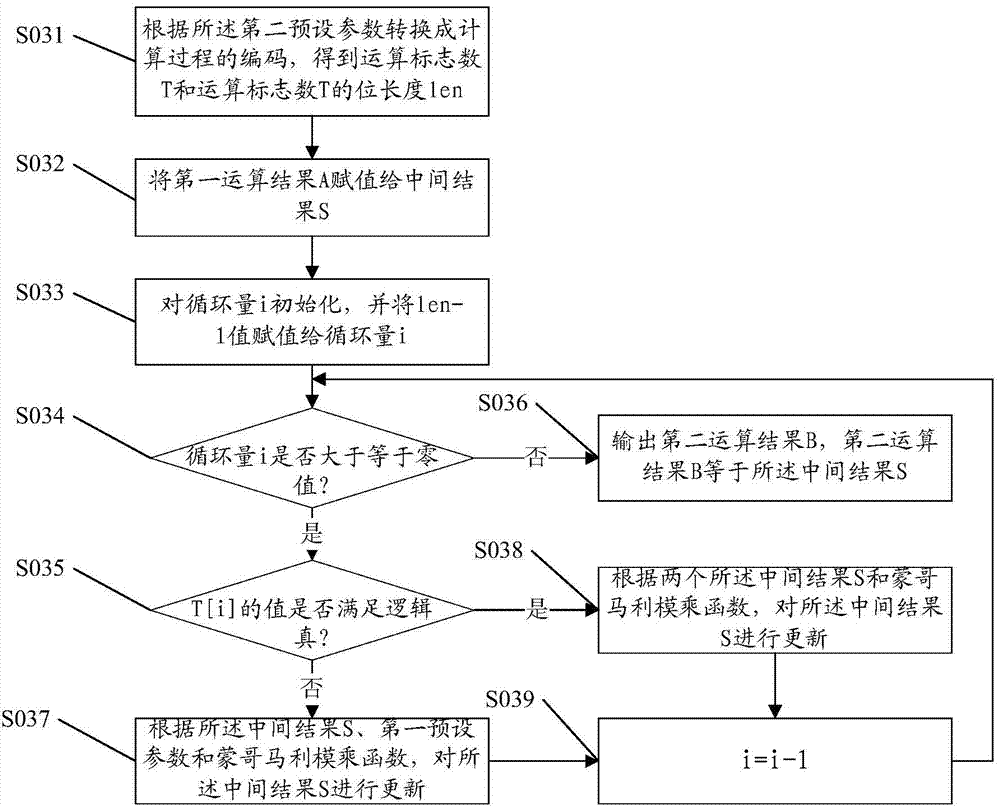
The invention provides a Montgomery modular multiplication device and an embedded security chip. The Montgomery modular multiplication device comprises a first Montgomery modular multiplication module, a power calculation module and a second Montgomery modular multiplication module, wherein the first Montgomery modular multiplication module is used for obtaining a first operation result A according to two first preset parameters, the power calculation module is used for obtaining a second operation result B according to the first operation result A output by the first Montgomery modular multiplication module, the first preset parameter, the second preset parameter and a power calculation function, the first Montgomery modular multiplication module is further used for obtaining a Montgomery modular multiplication conversion coefficient according to the first operation result A and the second operation result B, and the second Montgomery modular multiplication module is used for obtaining a final modular multiplication result according to a first input parameter NA, a second input parameter NB and the Montgomery modular multiplication conversion coefficient. By means of the Montgomery modular multiplication device and the embedded security chip, conversion coefficient calculation through a large modular power multiplication mode can be avoided, the coefficient does not need to be calculated in advance, and the memory space can be saved.
Owner:SHENZHEN STATE MICRO TECH CO LTD
Embedded security chip and Montgomery modular multiplication operational method thereof
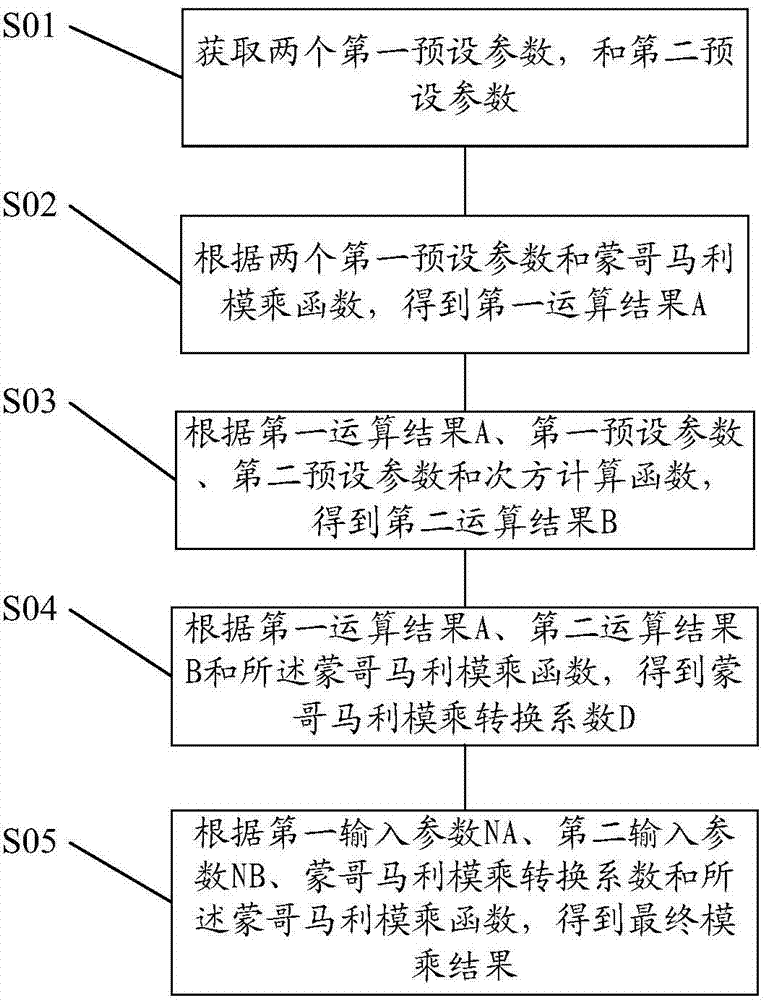
ActiveCN104765586AAvoid Calculating Conversion FactorsObvious advantagesComputations using residue arithmeticPower modeEmbedded security
The invention provides an embedded security chip and a Montgomery modular multiplication operational method thereof. The operational method comprises the steps that two first preset parameters and two second preset parameters are obtained, and the first preset parameters are constant one; according to the two first preset parameters and a Montgomery modular multiplication function, a first operation result A is obtained; according to the first operation result A, the first preset parameters, the second preset parameters and a power calculation function, a second operation result B is obtained; according to the first operation result A, the second operation result B and the Montgomery modular multiplication function, a Montgomery modular multiplication conversion coefficient D is obtained; according to a first input parameter NA, a second input parameter NB, the Montgomery modular multiplication conversion coefficient and the Montgomery modular multiplication conversion coefficient, the final modular multiplication result is obtained. According to the Montgomery modular multiplication operational method, a calculation conversion coefficient of a large module power mode can be avoided, the coefficient does not need to be calculated in advance, and the storage space can be saved.
Owner:SHENZHEN STATE MICRO TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com