Pipelined Montgomery modular multiplication method and pipelined Montgomery modular multiplication calculation device
A pipeline-type, computing method technology, applied in the field of data encryption algorithms, can solve problems such as increased hardware resources, area and energy consumption, difficulty in increasing the number of modular multiplication operations, and decreased cost performance of the system to achieve improved throughput and high performance /Resource ratio, the effect of increasing throughput
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0055] The present invention will be further described below in conjunction with specific embodiment:
[0056] The present invention has been implemented in the form of hardware RTL code and implemented into an FPGA-based product. It can also be integrated into asymmetric encryption algorithms and related security hardware ASIC products as IP.
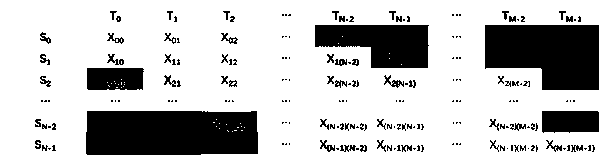
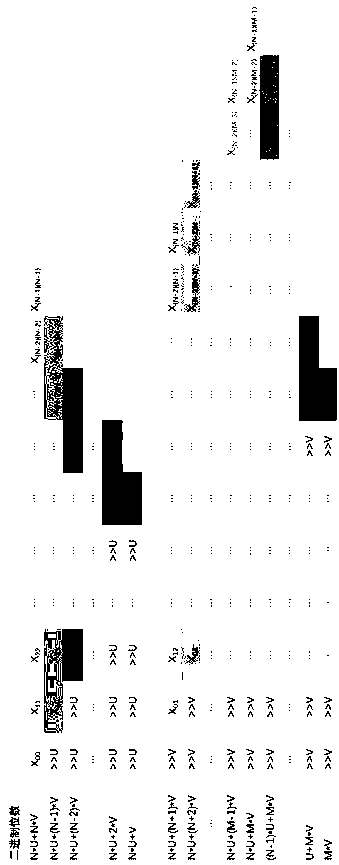
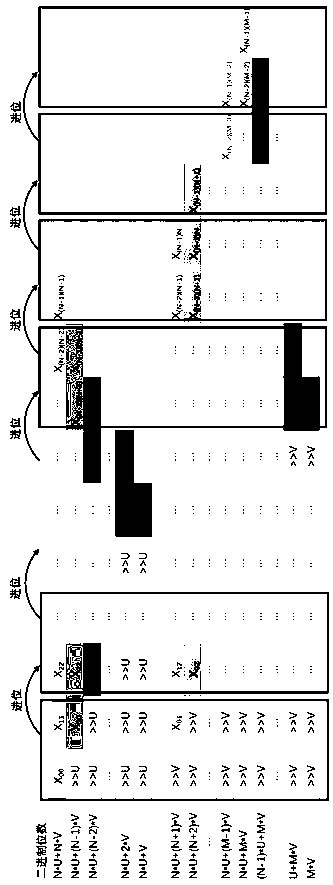
[0057] Montgomery modular multiplication mainly includes two parts. The first part is ordinary multiplication, but because the two numbers to be multiplied are very large (such as 256 or 512 bits), this multiplication must be divided into multiple smaller multiplications for execution.
[0058] Multiplication step 1: If the input bit width of an FPGA ADSP computing unit is U and V respectively, or the ASIC implements a multiplier with a smaller bit width, you can use multiple multipliers with a smaller bit width to implement this step. Assume that the input data (both are R-bit binary numbers) input data ,in , Indicates roundi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com