Hardware optimization method based on SM3 password hash algorithm
A technology of hash algorithm and optimization method, applied in the field of information security, can solve problems such as user and enterprise losses, achieve the effect of saving implementation costs, solving optimization conflicts, and ensuring computing efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
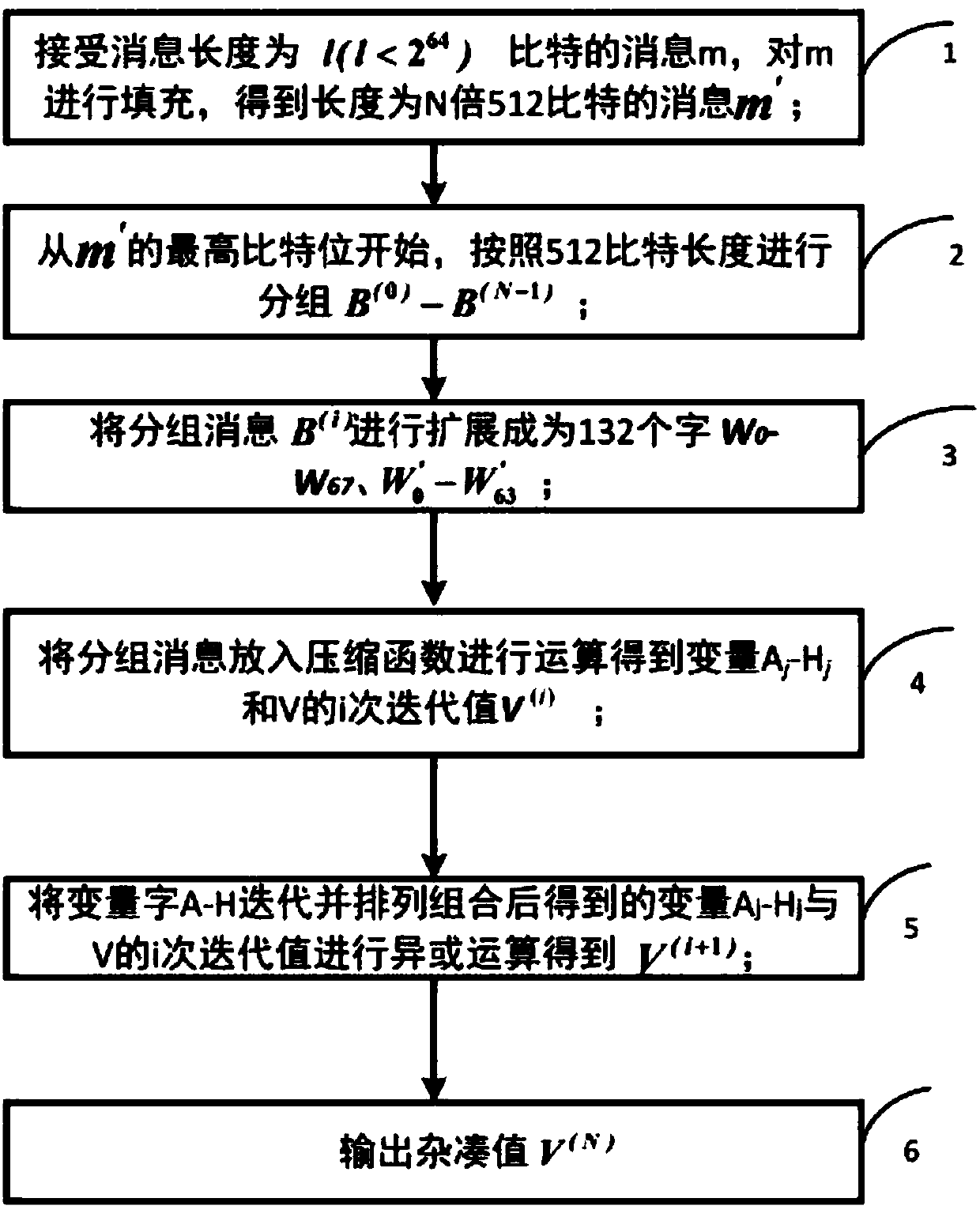
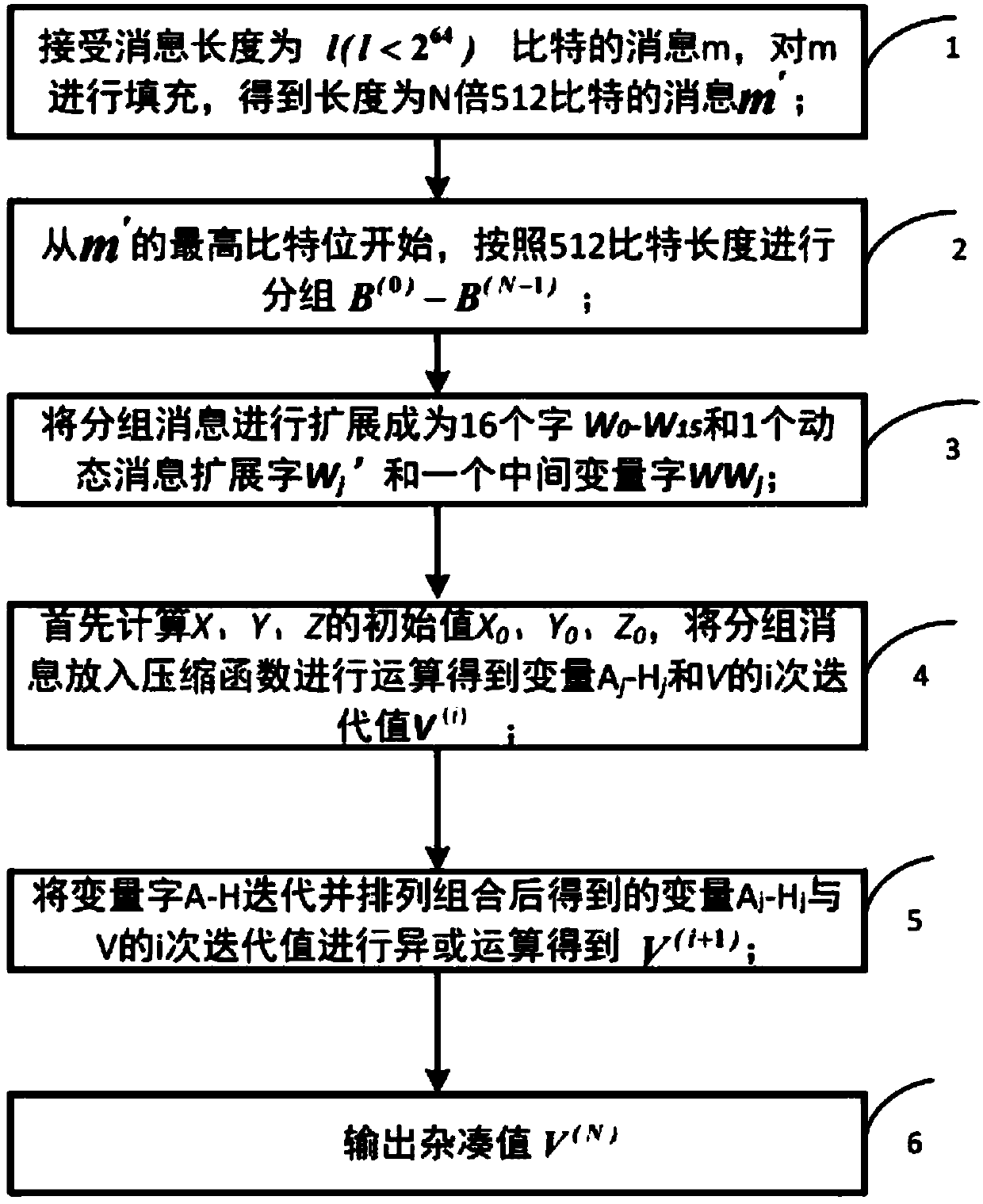
[0026] like figure 1 Shown, a kind of hardware optimization method based on SM3 cryptographic hash algorithm is characterized in that, comprises the following steps:
[0027] Step 1, receiving a message m with a message length of 1 bit, filling m to obtain a message m';
[0028] Step 2, starting from the highest bit of m', grouping according to the length of 512 bits,
[0029] m'=B (0) , B (1) ,···,B (n-1) ;
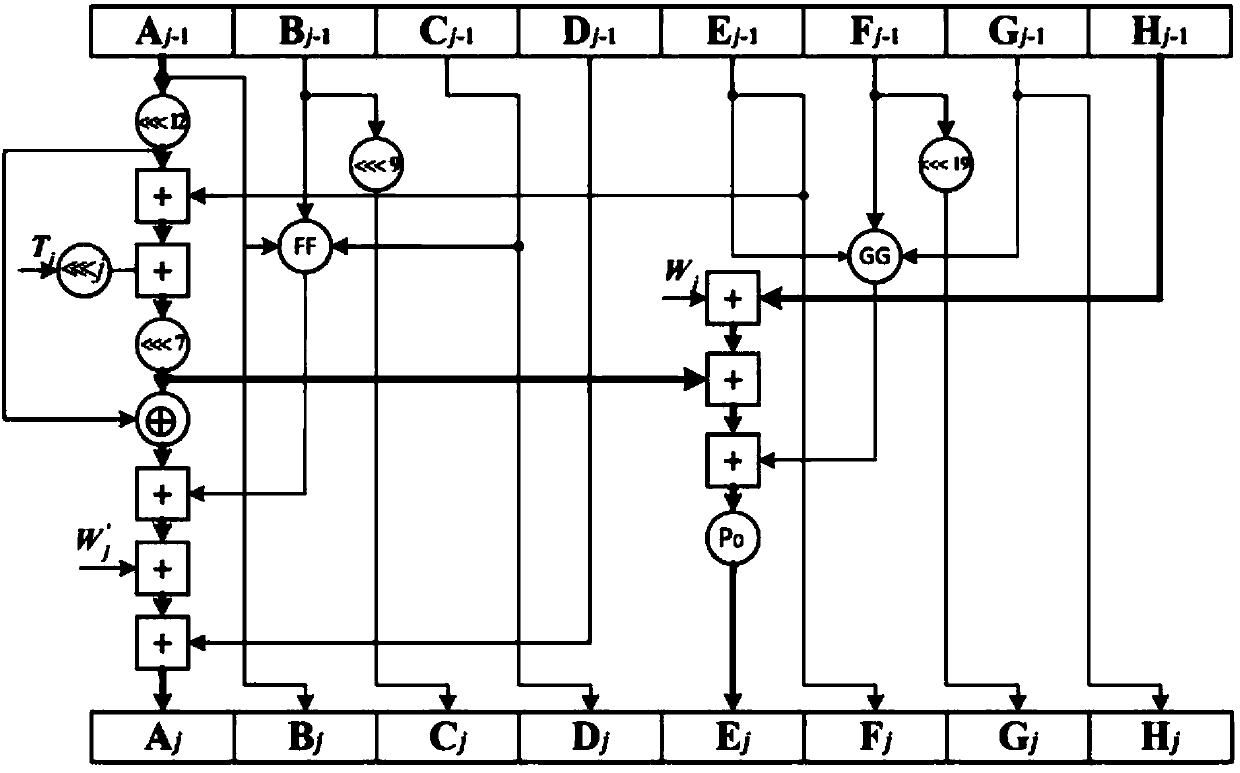
[0030] Step 3. Put the grouped message B (i) Extend according to the extension method to generate 16 32-bit extension words W 0 , W 1 ,···,W 15 , 1 dynamic message extension word W′ j and 1 intermediate variable word WW j ;
[0031] Step 4. Calculate the initial value X of the intermediate variables X, Y, and Z 0 , Y 0 ,Z 0 , put the grouped message into the compression function to get the variable A j -H j i iteration value V with V i ;
[0032] Step 5: Get the variable A by operation j -H j i iteration value V with V i Perform XOR operation to get ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com