Patents
Literature
852 results about "Safety standards" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Safety standards are standards designed to ensure the safety of products, activities or processes, etc. They may be advisory or compulsory and are normally laid down by an advisory or regulatory body that may be either voluntary or statutory. China has recently experienced trouble with some of the post listed associations.
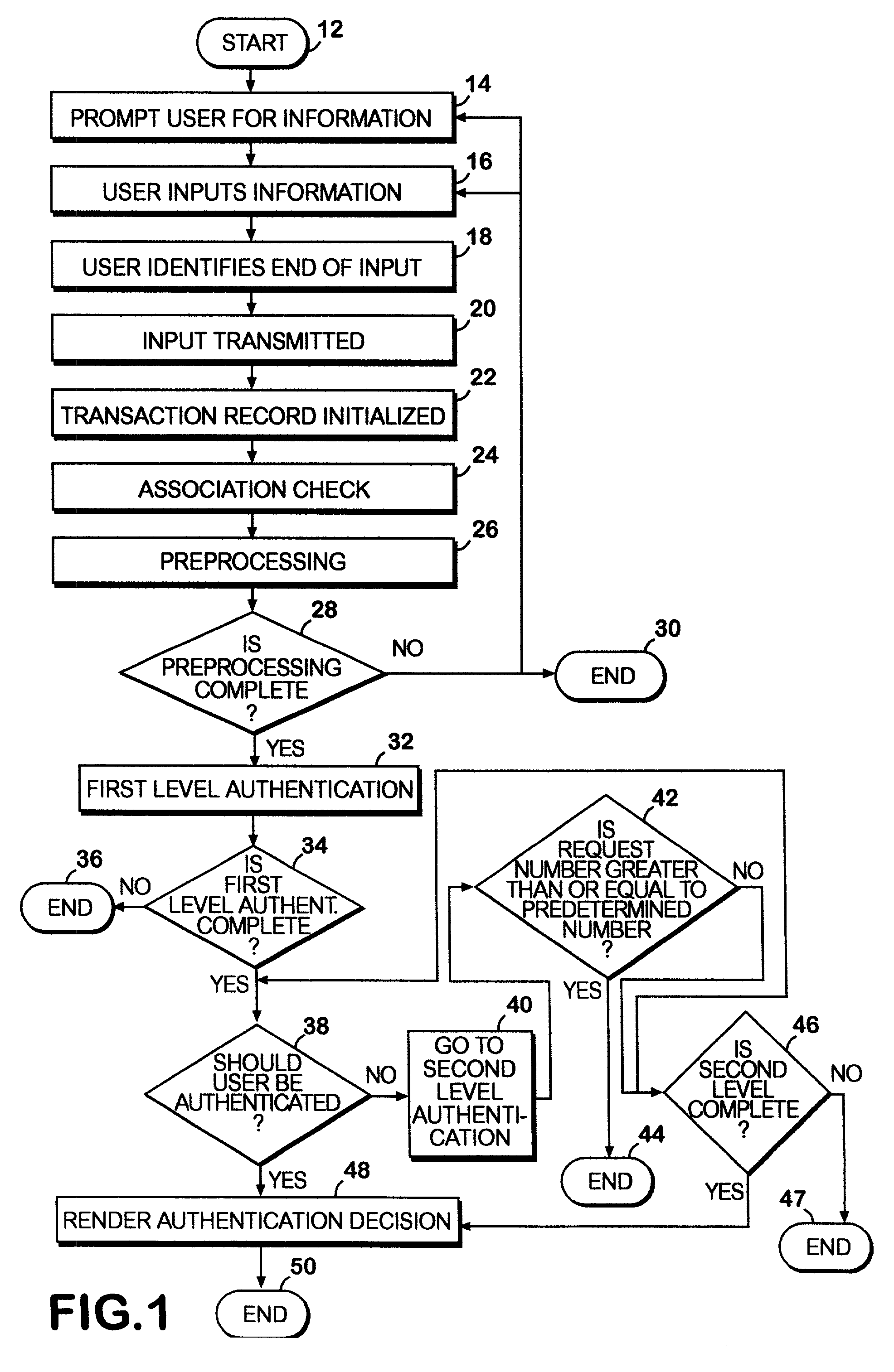
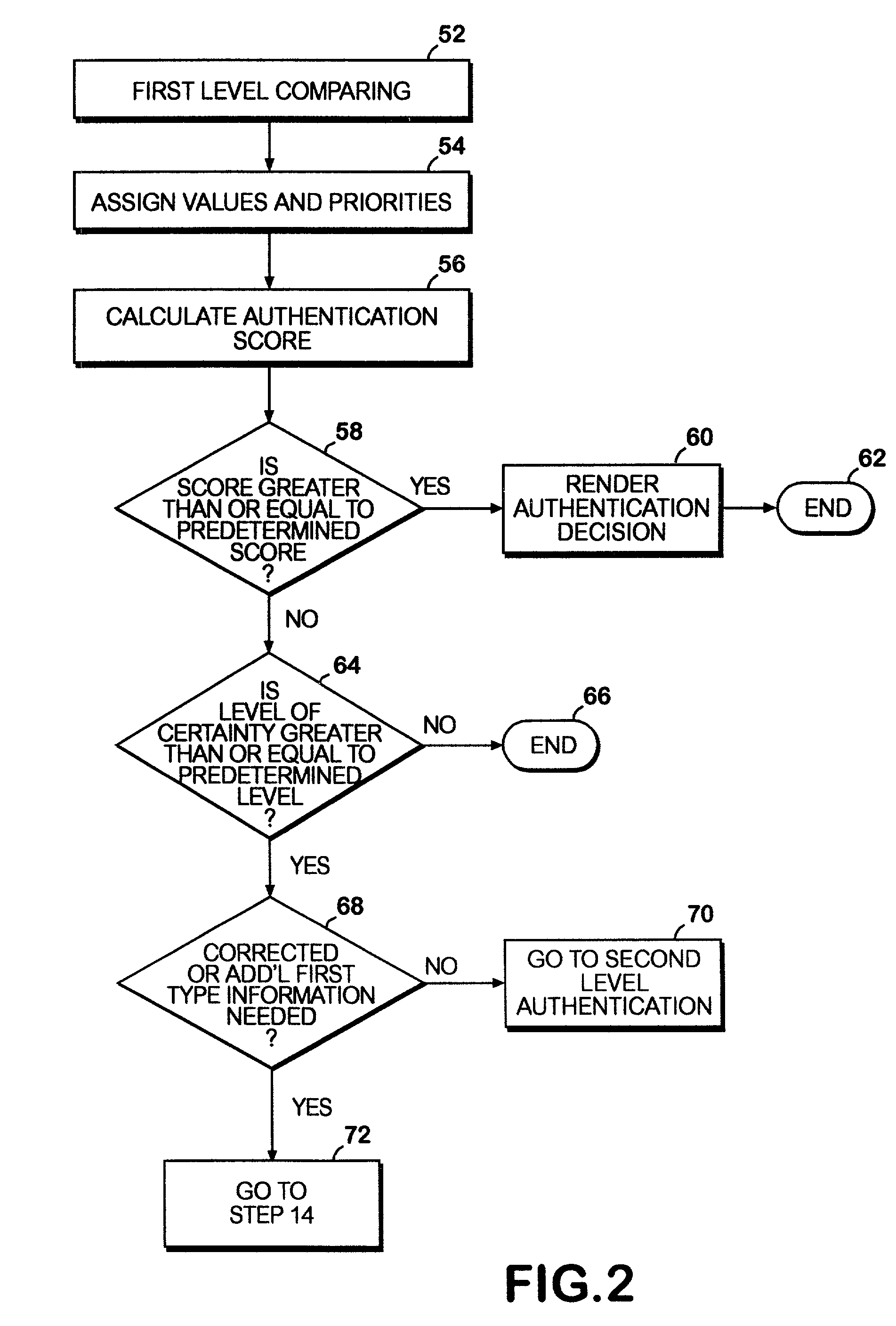
System and method for authentication of network users
InactiveUS6857073B2Avoiding terminationReducing cost and unnecessary useDigital data processing detailsUser identity/authority verificationInternet privacyInformation design
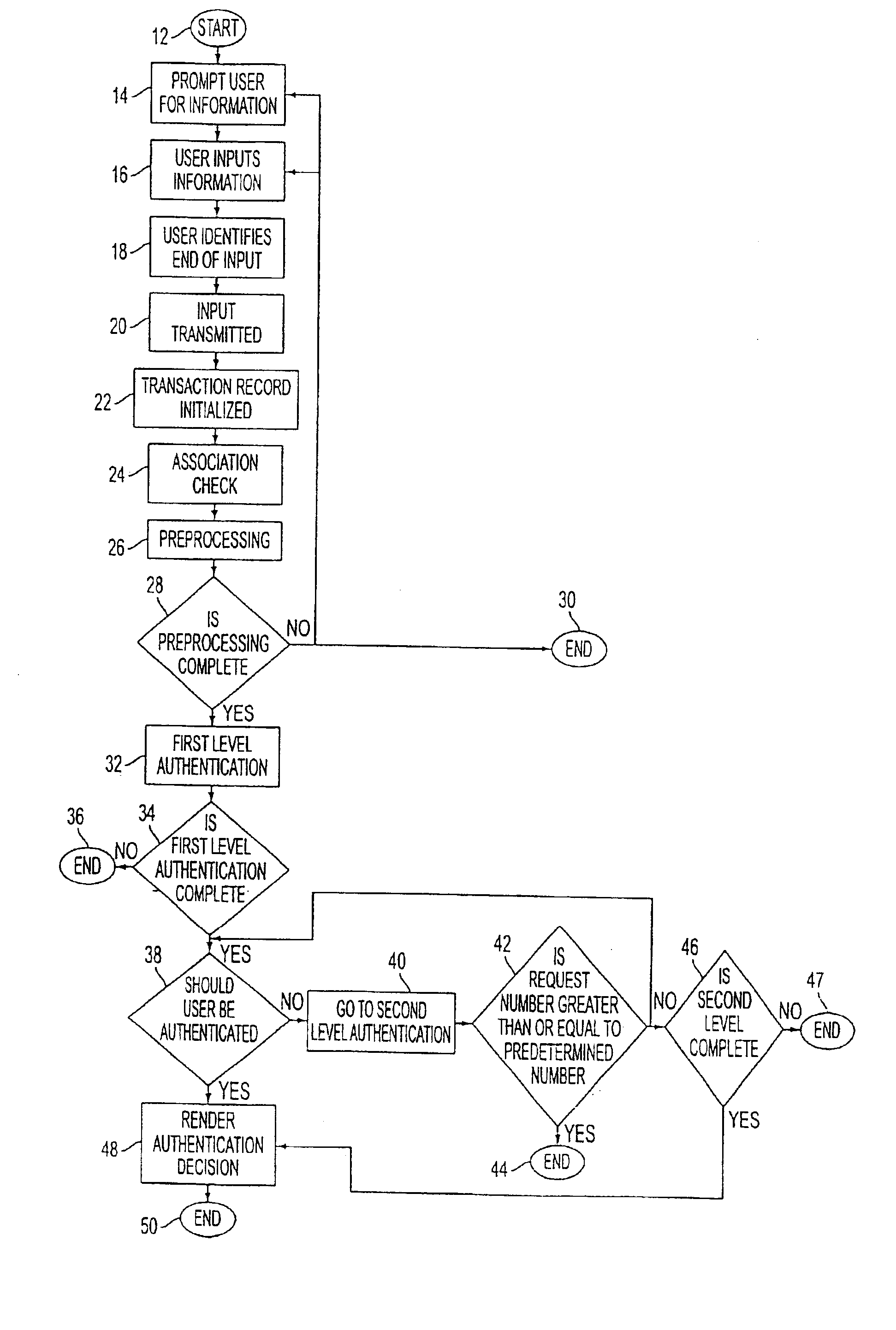
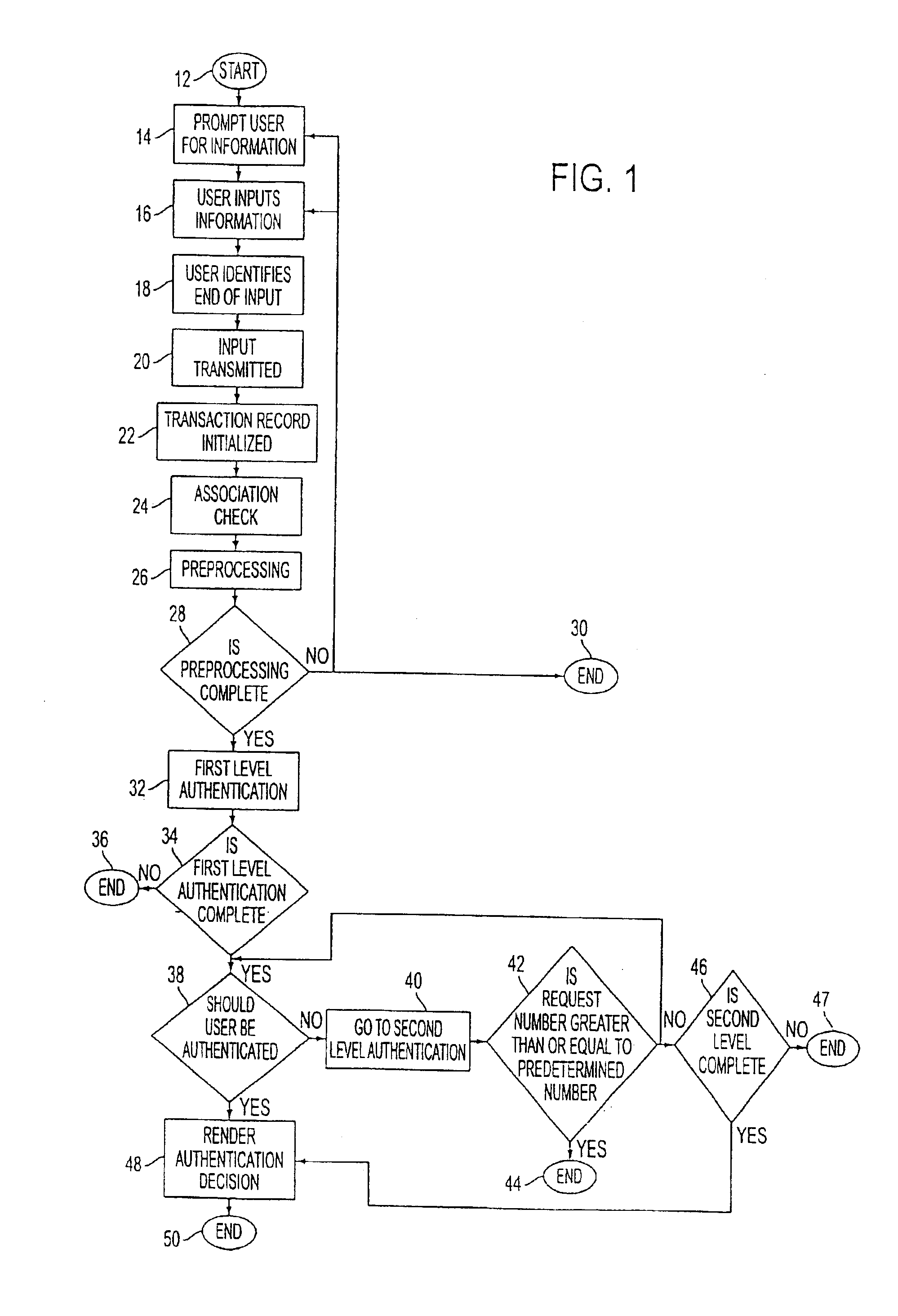
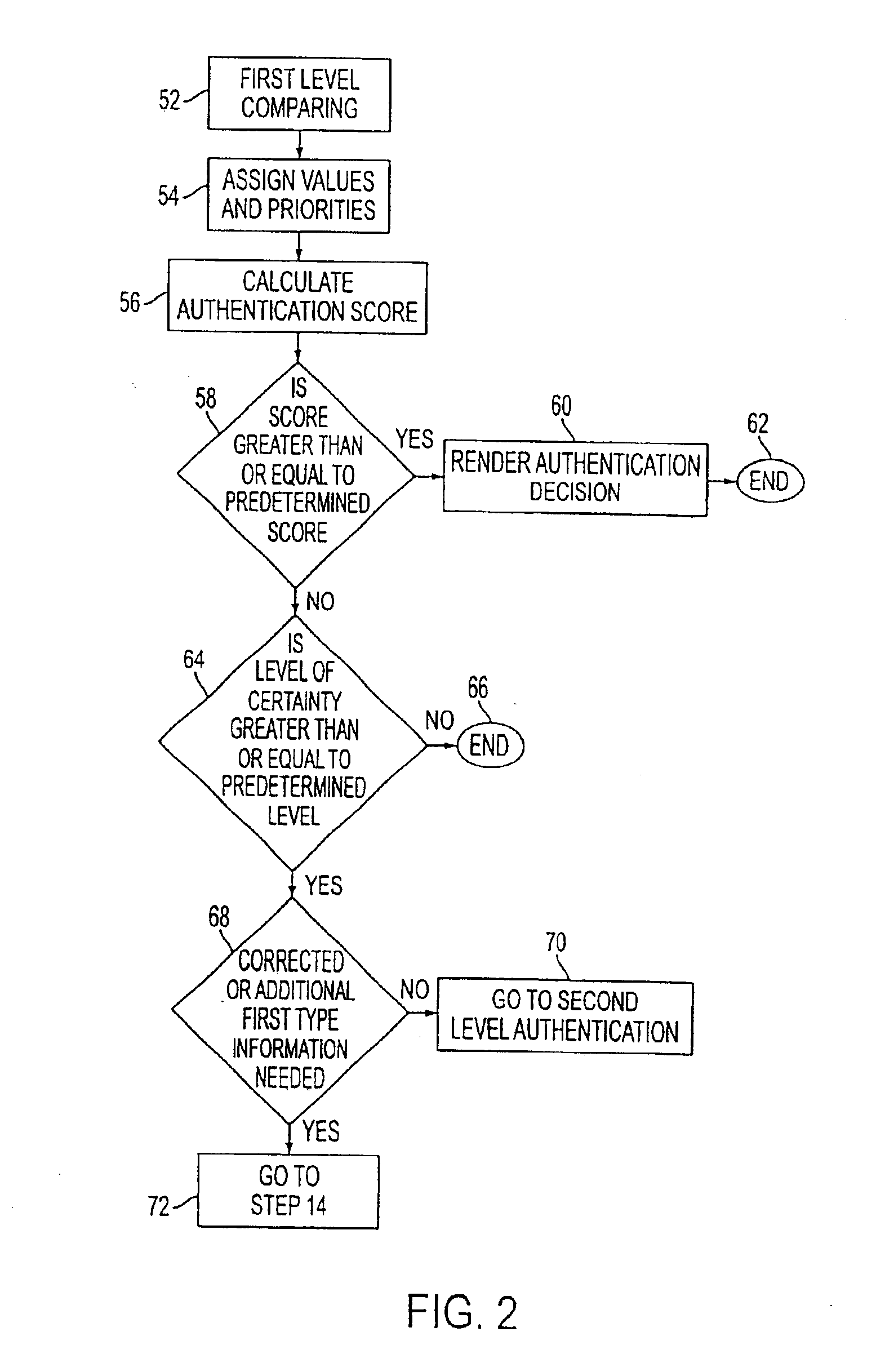
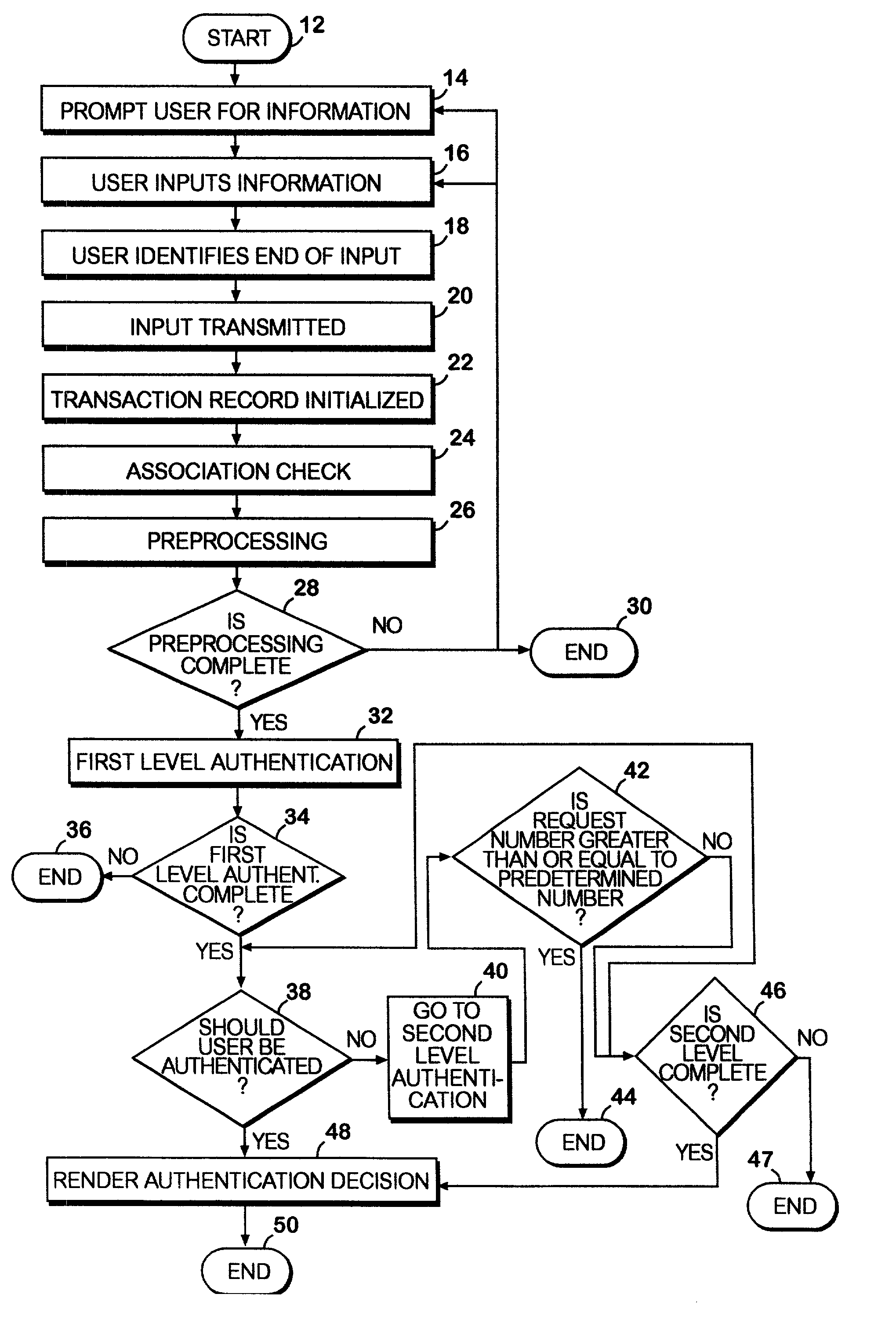
A network authentication system provides verification of the identity or other attributes of a network user to conduct a transaction, access data or avail themselves of other resources. The user is presented with a hierarchy of queries based on wallet-type (basic identification) and non-wallet type (more private) information designed to ensure the identity of the user and prevent fraud, false negatives and other undesirable results. A preprocessing stage may be employed to ensure correct formatting of the input information and clean up routine mistakes (such as missing digits, typos, etc.) that might otherwise halt the transaction. Queries can be presented in interactive, batch processed or other format. The authenticator can be configured to require differing levels of input or award differing levels of authentication according to security criteria.
Owner:EQUIFAX INC
System and method for authentication of network users
InactiveUS7234156B2Reducing cost and unnecessary useChanceDigital data processing detailsUser identity/authority verificationBatch processingInformation design
A network authentication system provides verification of the identity or other attributes of a network user to conduct a transaction, access data or avail themselves of other resources. The user is presented with a hierarchy of queries based on wallet-type (basic identification) and non-wallet type (more private) information designed to ensure the identity of the user and prevent fraud, false negatives and other undesirable results. A preprocessing stage may be employed to ensure correct formatting of the input information and clean up routine mistakes (such as missing digits, typos, etc.) that might otherwise halt the transaction. Queries can be presented in interactive, batch processed or other format. The authenticator can be configured to require differing levels of input or award differing levels of authentication according to security criteria.
Owner:EQUIFAX INC
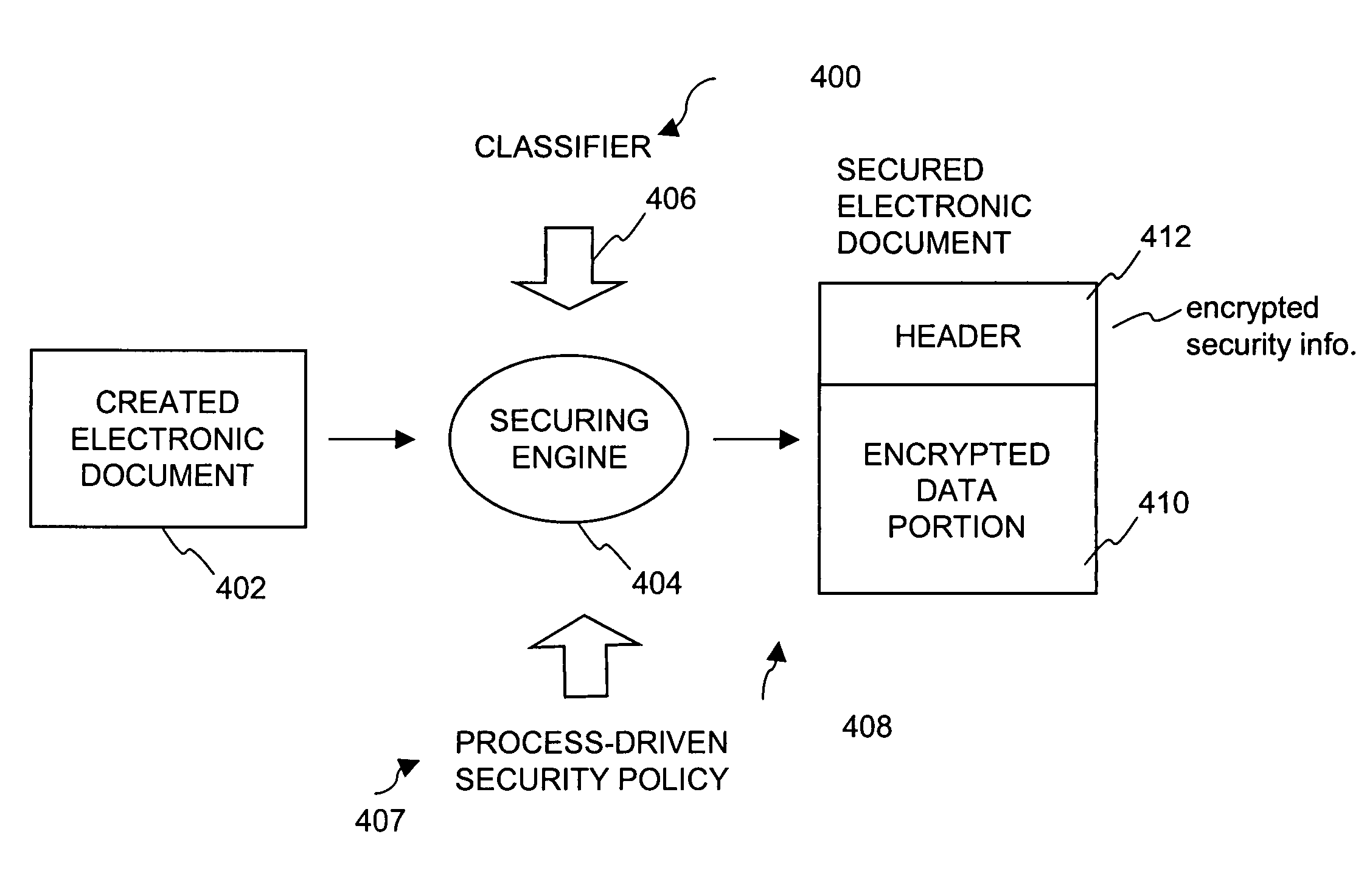
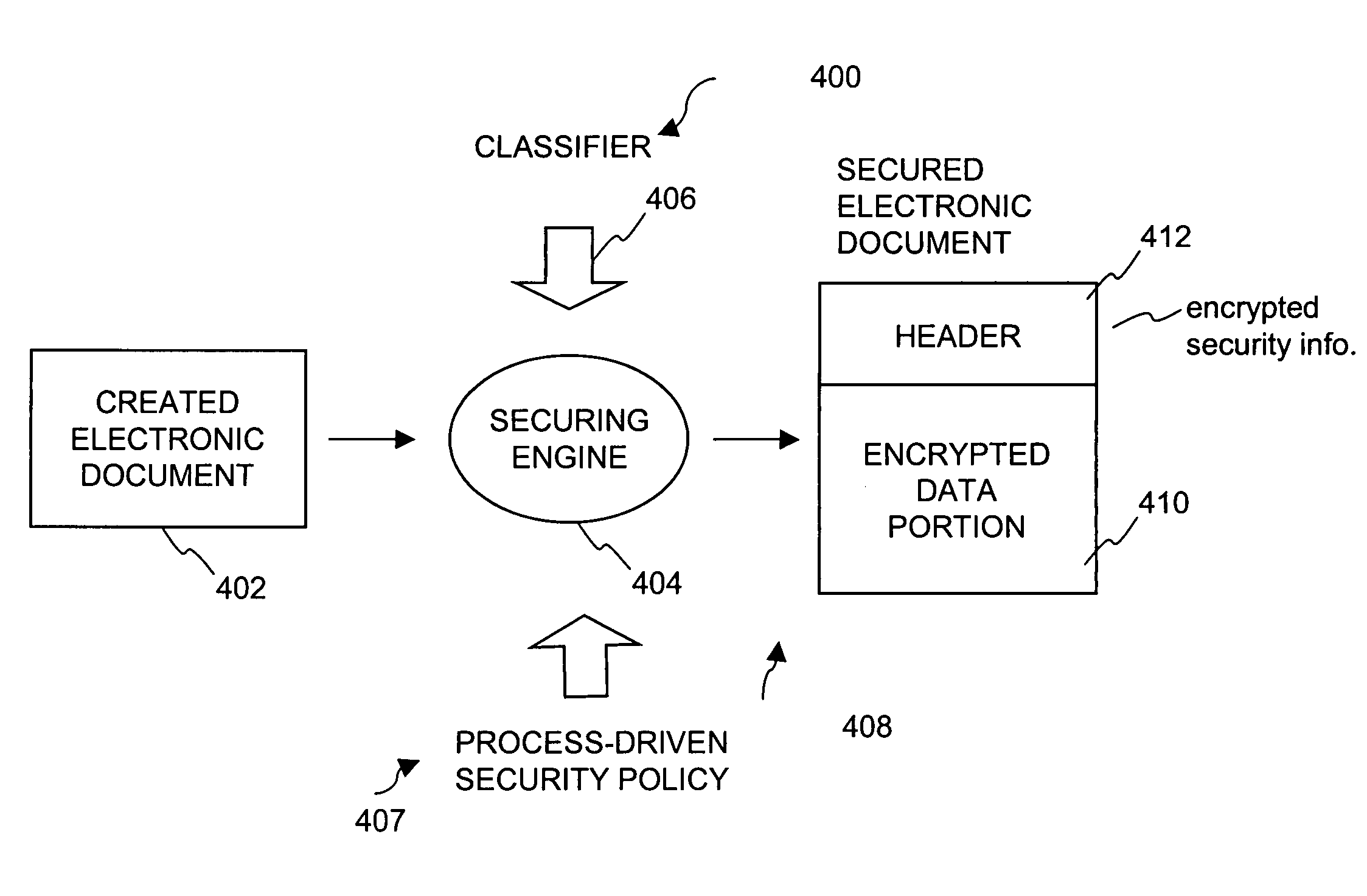
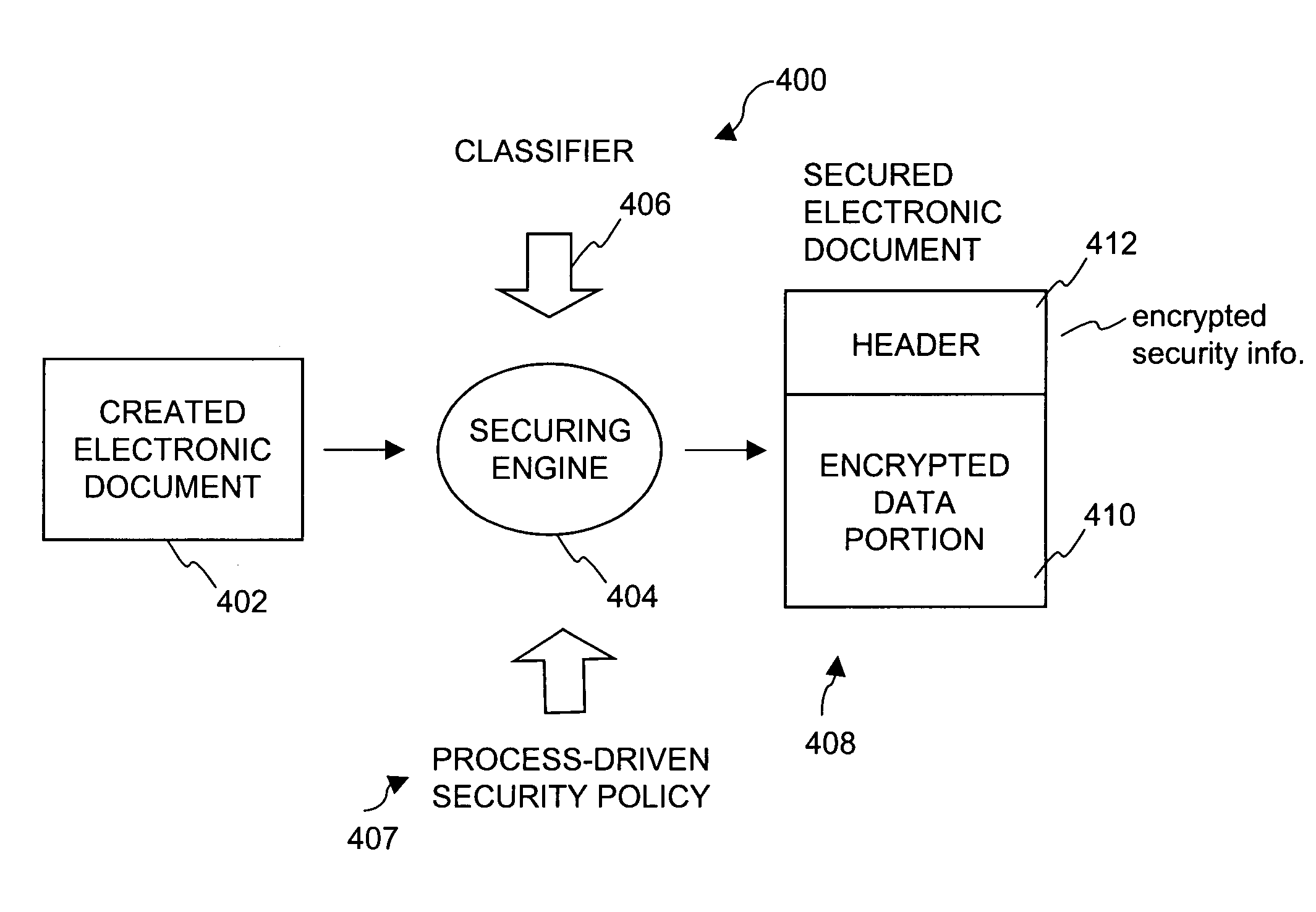
Method and system for securing digital assets using process-driven security policies
ActiveUS7703140B2More burdensomeGood flexibilityKey distribution for secure communicationPublic key for secure communicationSecurity policySecurity system
Techniques for dynamically altering security criteria used in a file security system are disclosed. The security criteria pertains to keys (or ciphers) used by the file security system to encrypt electronic files to be secured or to decrypt electronic files already secured. The security criteria can, among other things, include keys that are required to gain access to electronic files. Here, the keys can be changed automatically as electronic files transition between different states of a process-driven security policy. The dynamic alteration of security criteria enhances the flexibility and robustness of the security system. In other words, access restrictions on electronic files can be dependent on the state of the process-driven security policy.
Owner:INTELLECTUAL VENTURES I LLC
Dynamically and customizably managing data in compliance with privacy and security standards
InactiveUS9049314B2Preserving professional confidencesAvoid identificationDigital data protectionOffice automationDocumentation procedureRecordset
Owner:VERISMA SYST
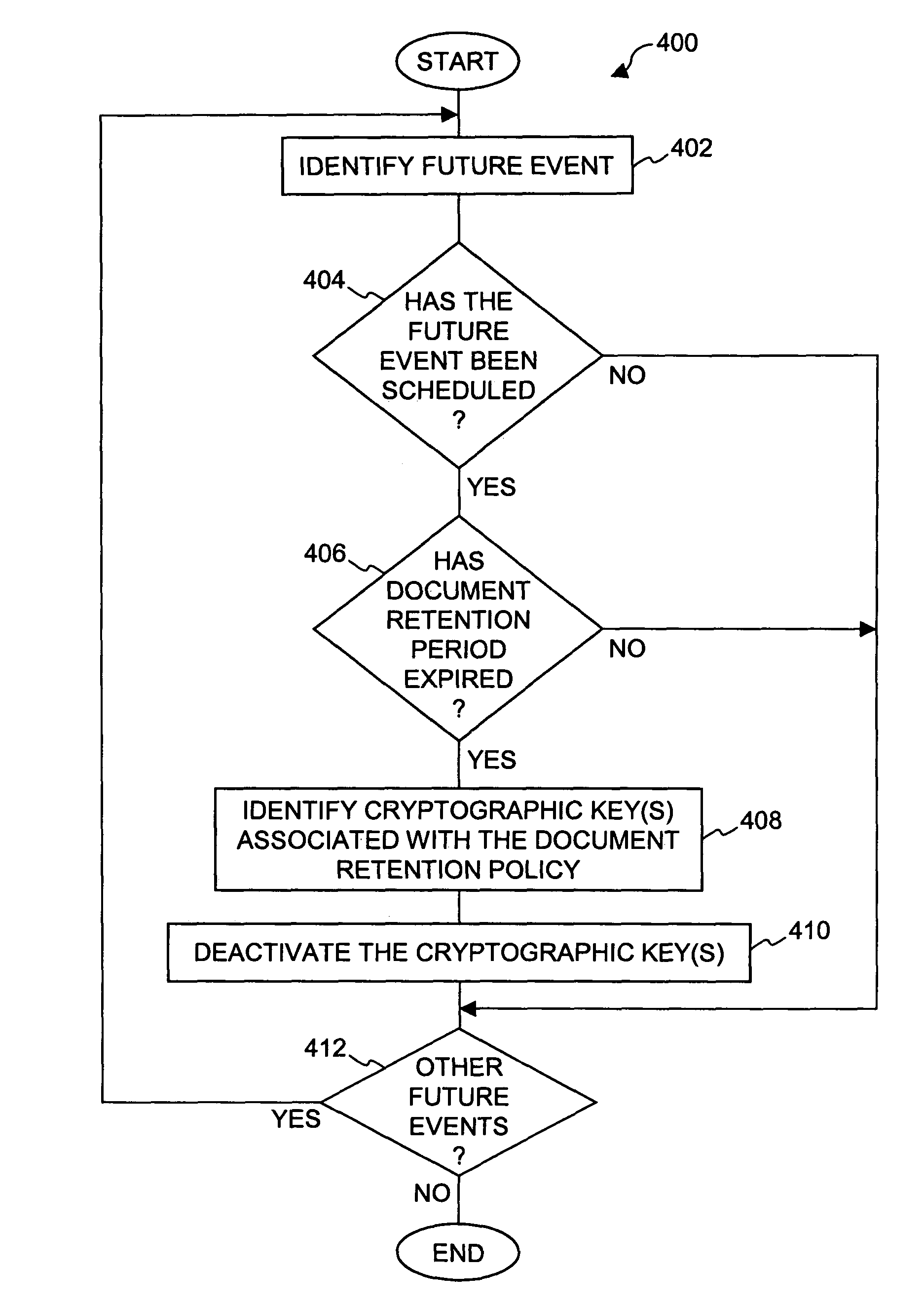
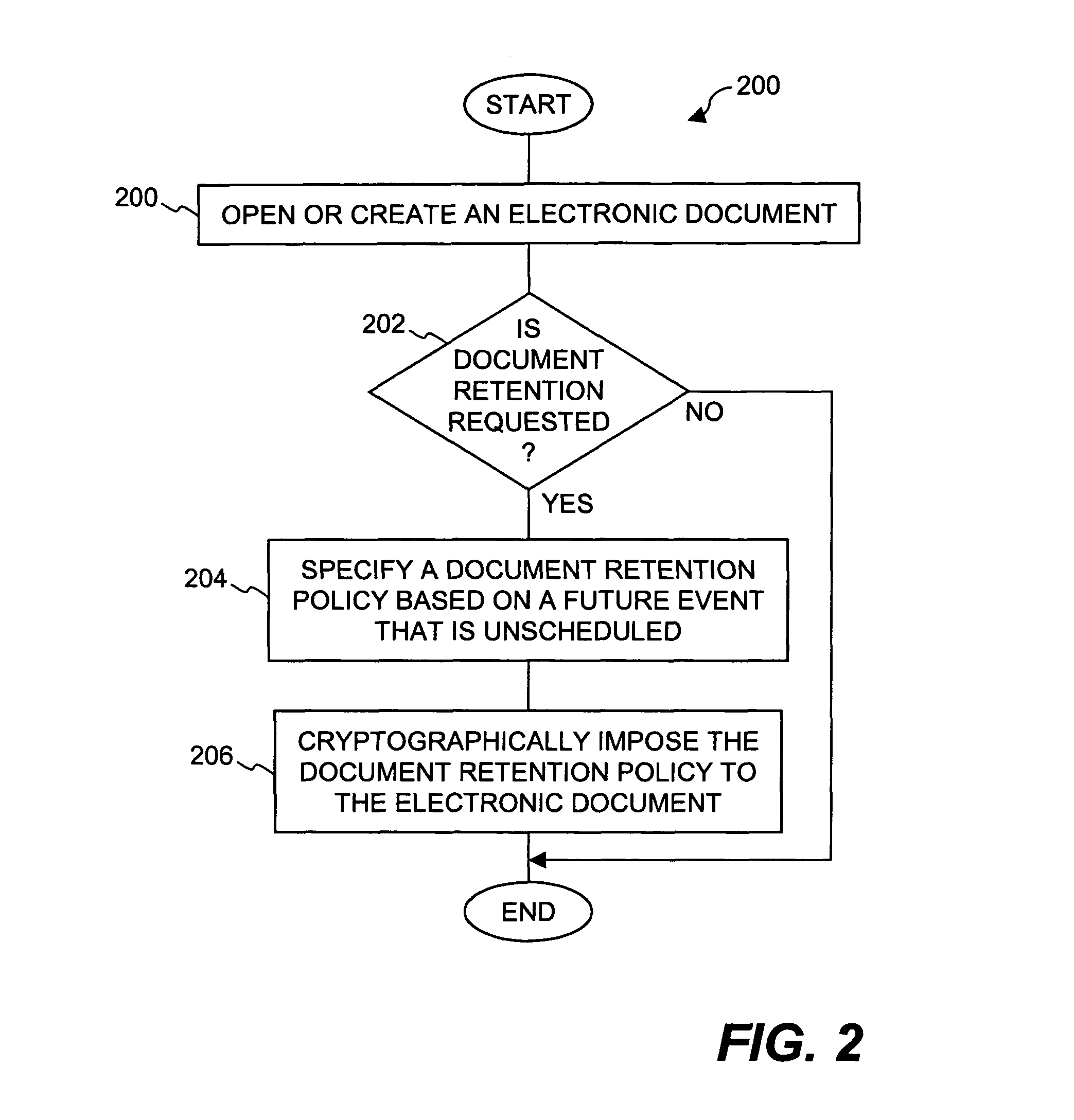
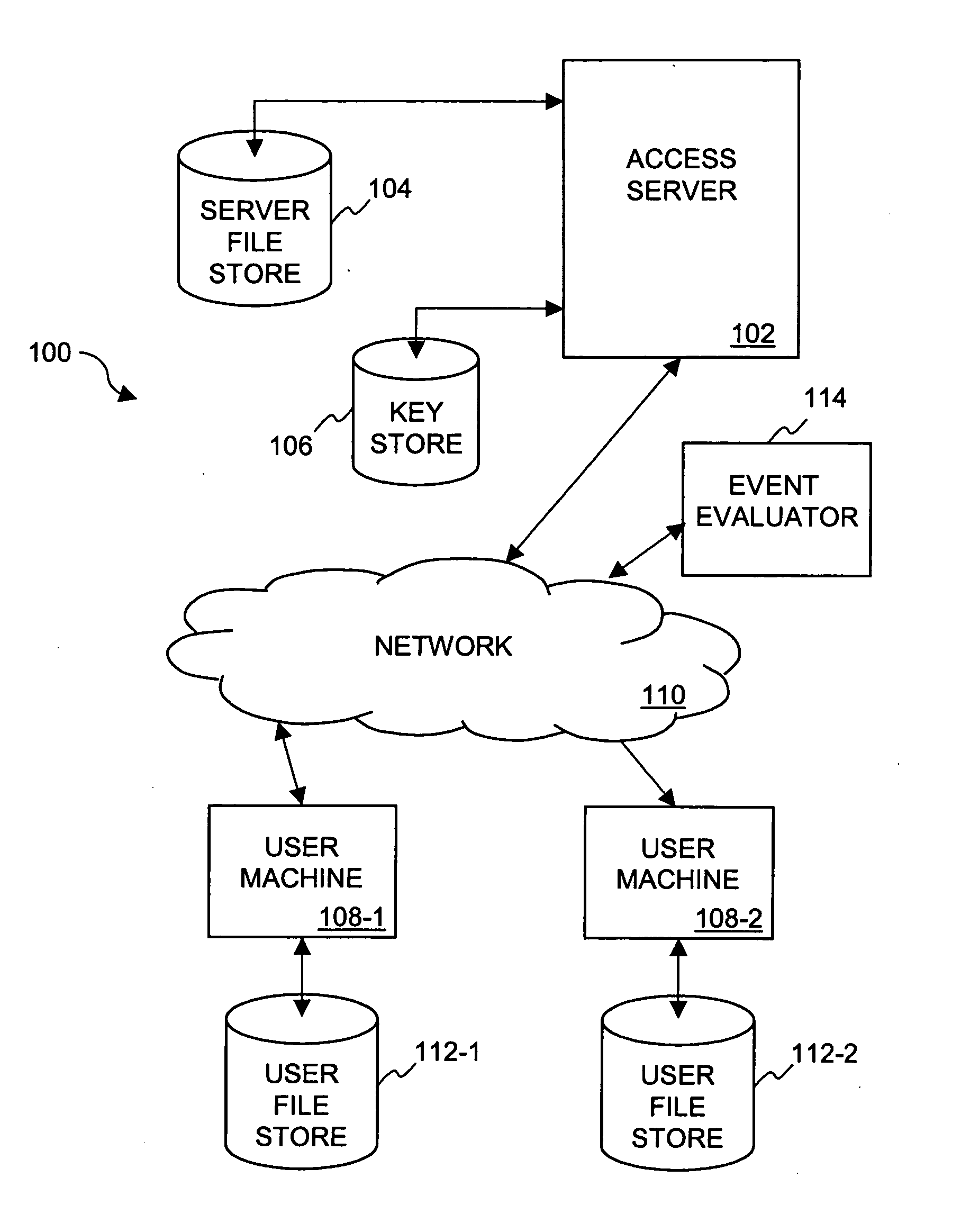
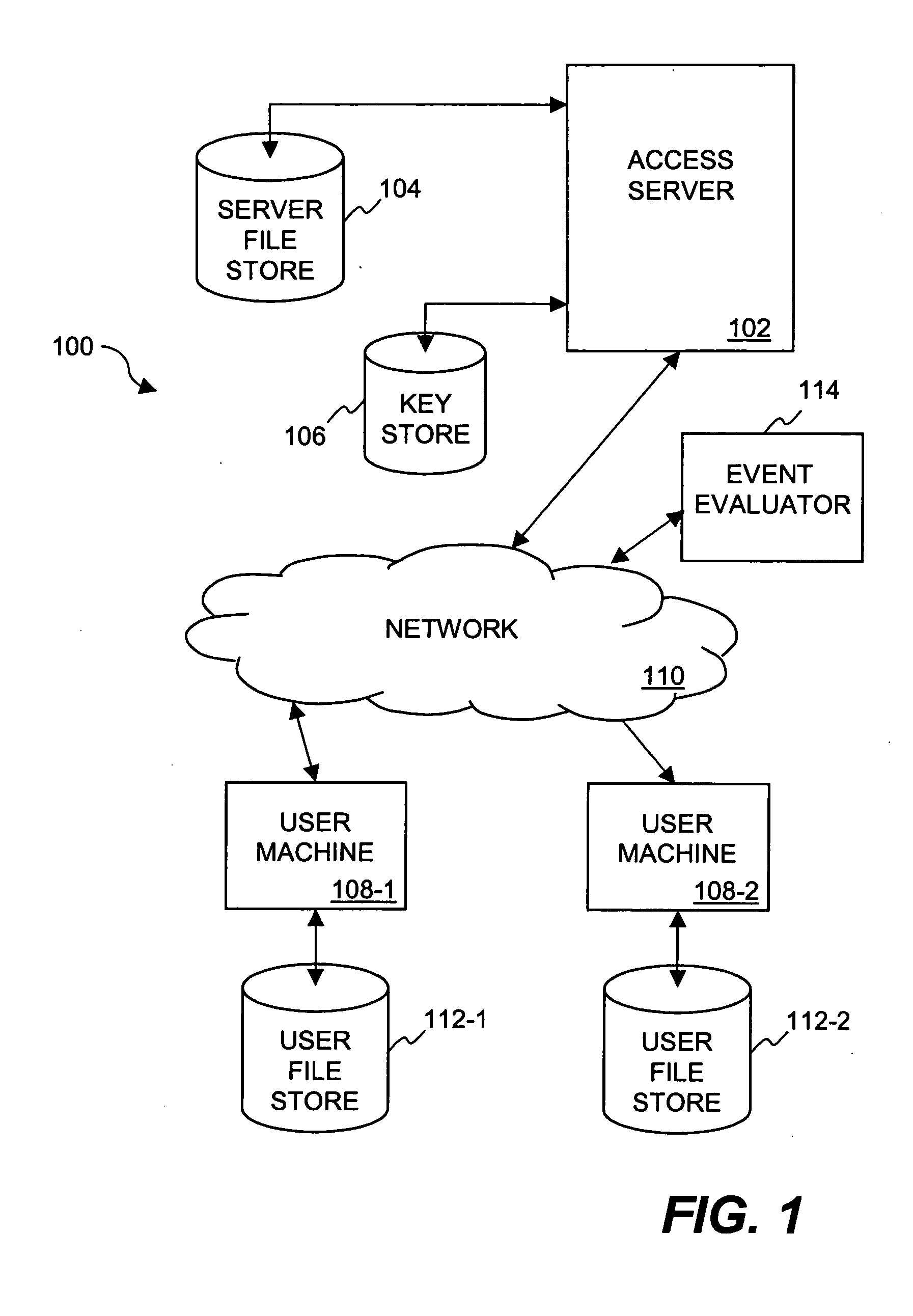
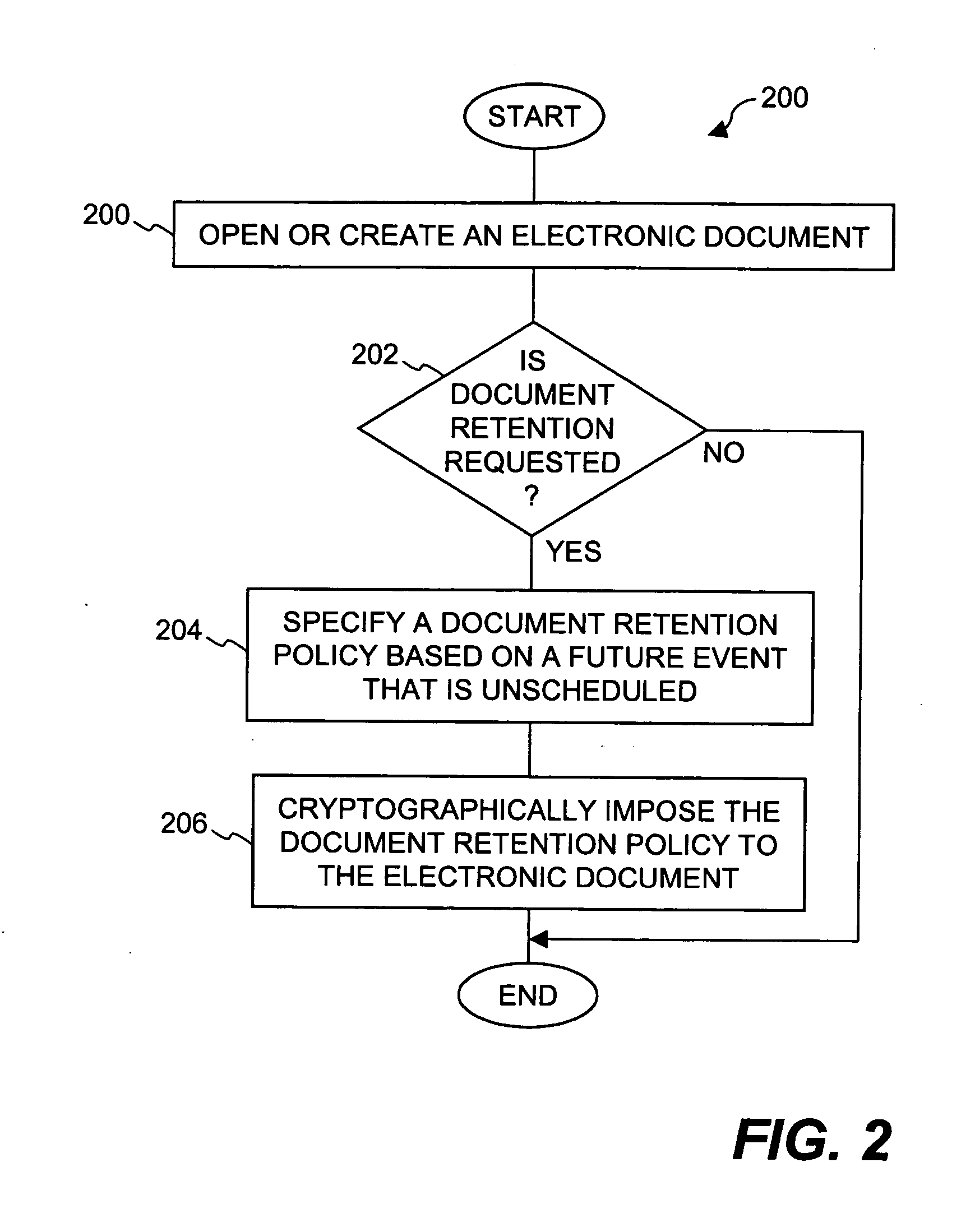
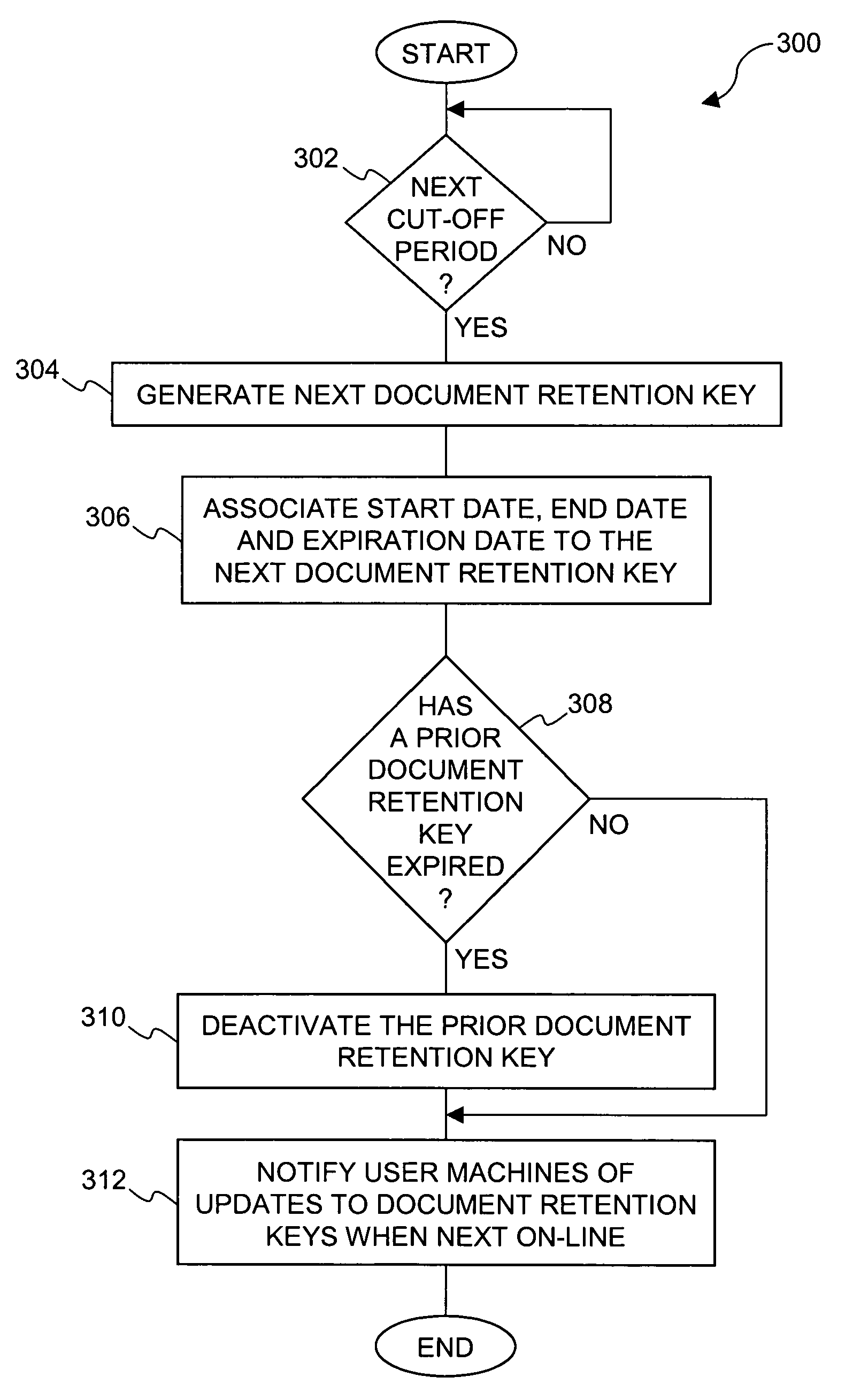
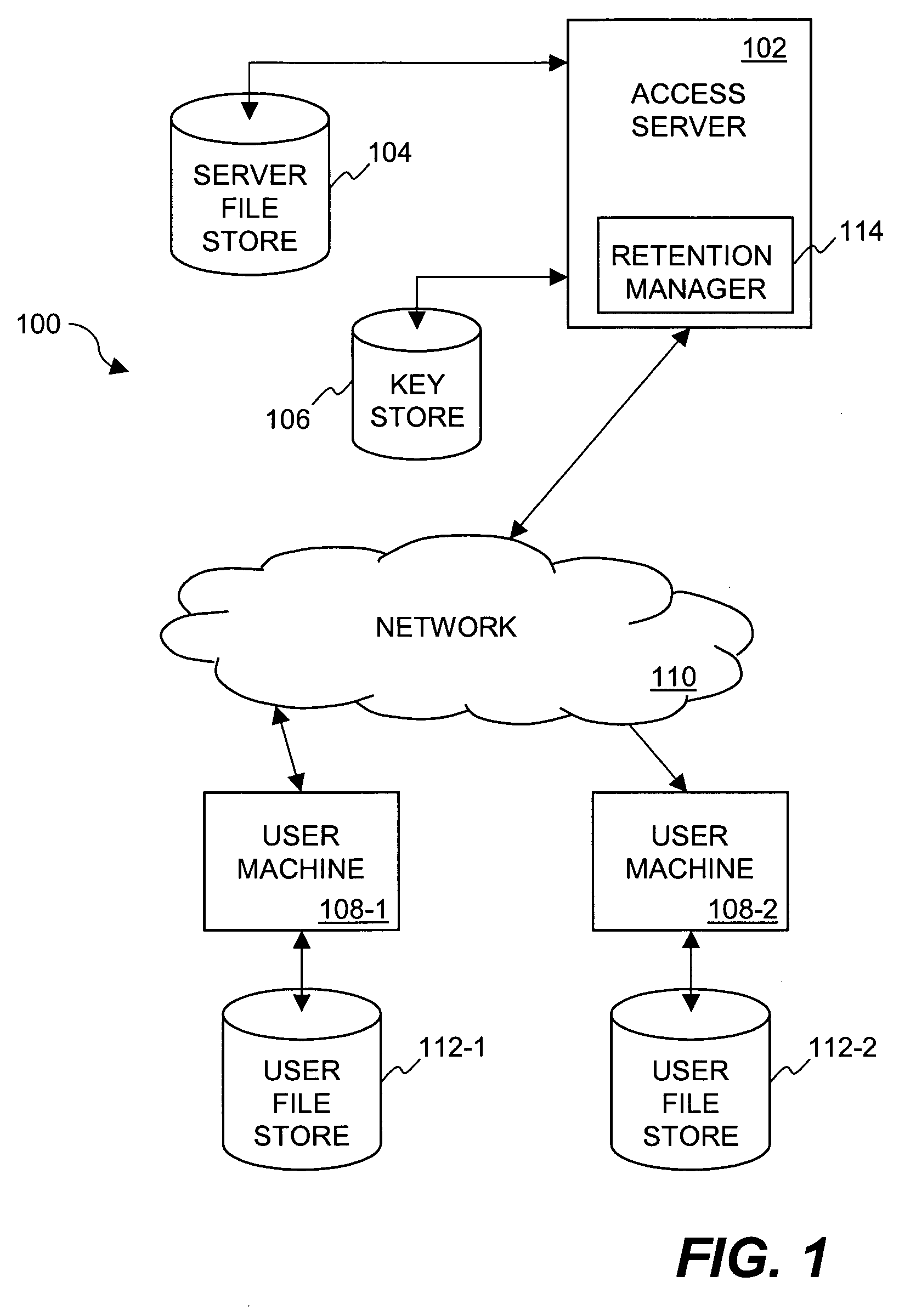
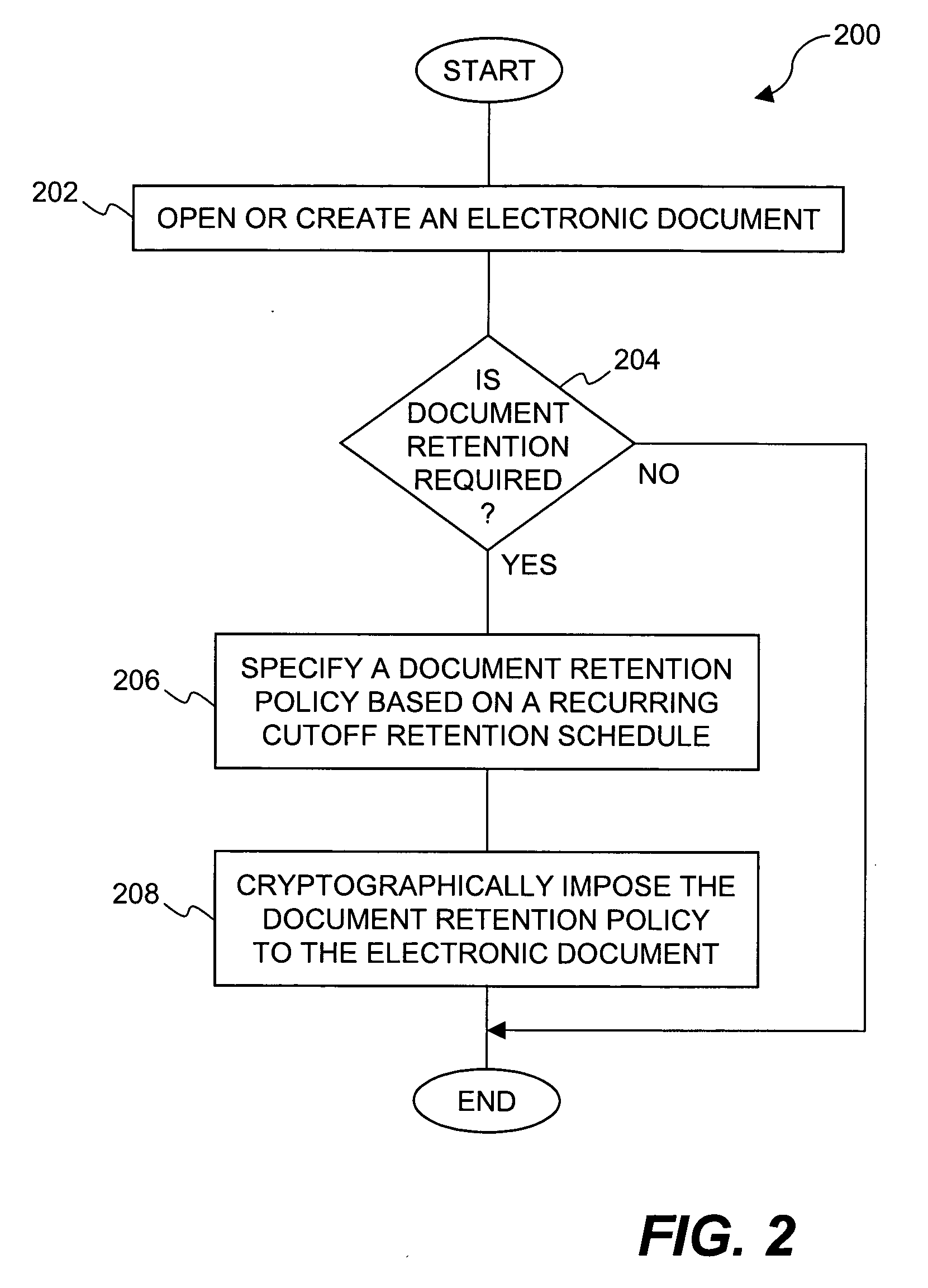
Method and system for providing document retention using cryptography
ActiveUS8613102B2Effectively and properly disposingDigital data processing detailsUser identity/authority verificationElectronic documentDocumentation procedure
Techniques for utilizing security criteria to implement document retention for electronic documents are disclosed. The security criteria can also limit when, how and where access to the electronic documents is permitted. The security criteria can pertain to keys (or ciphers) used to secure (e.g., encrypt) electronic files (namely, electronic documents), or to unsecure (e.g., decrypt) electronic files already secured. At least a portion of the security criteria can be used to implement document retention, namely, a document retention policy. After a secured electronic document has been retained for the duration of the document retention policy, the associated security criteria becomes no longer available, thus preventing subsequent access to the secured electronic document. In other words, access restrictions on electronic documents can be used to prevent access to electronic documents which are no longer to be retained.
Owner:CITRIX SYST INC
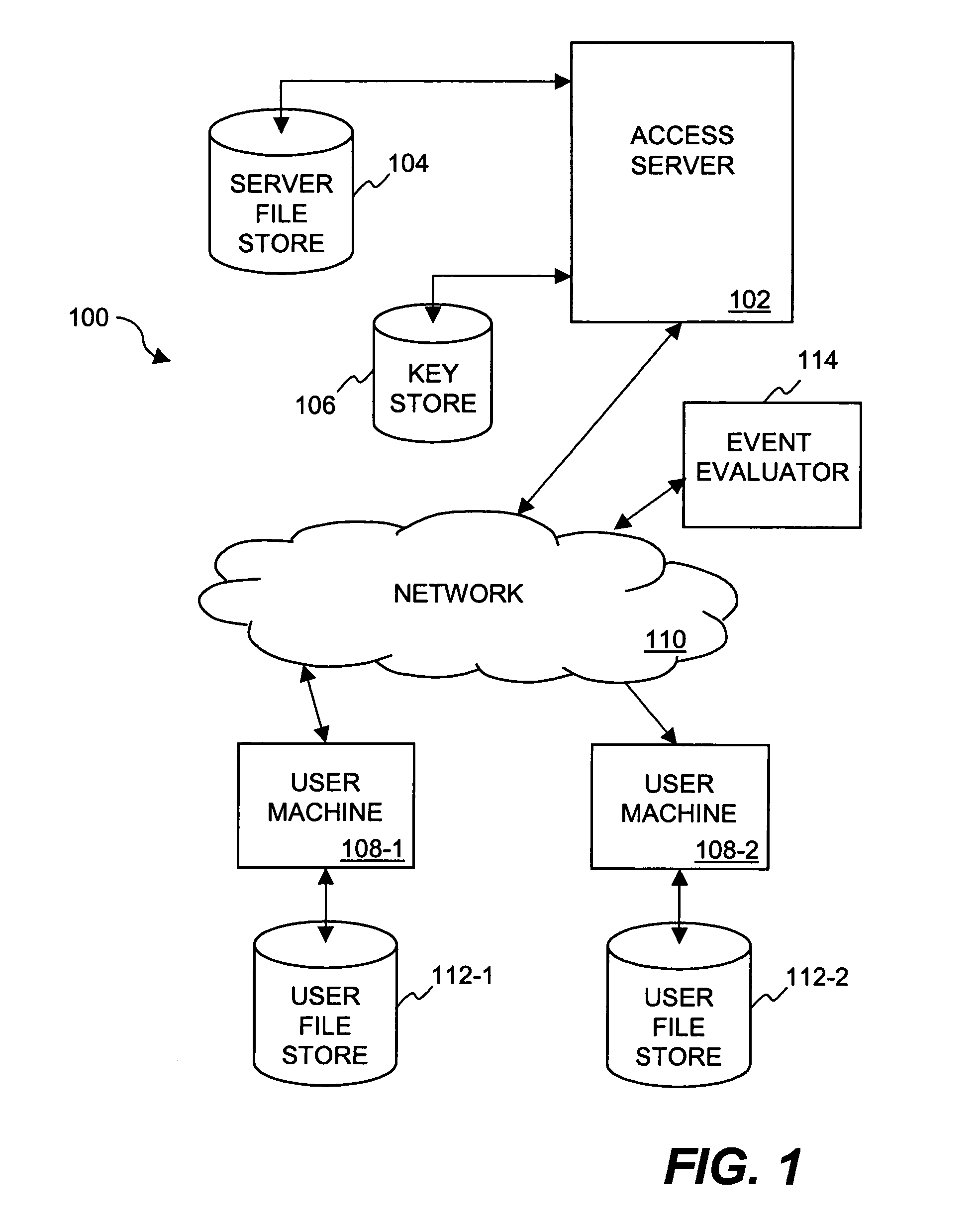
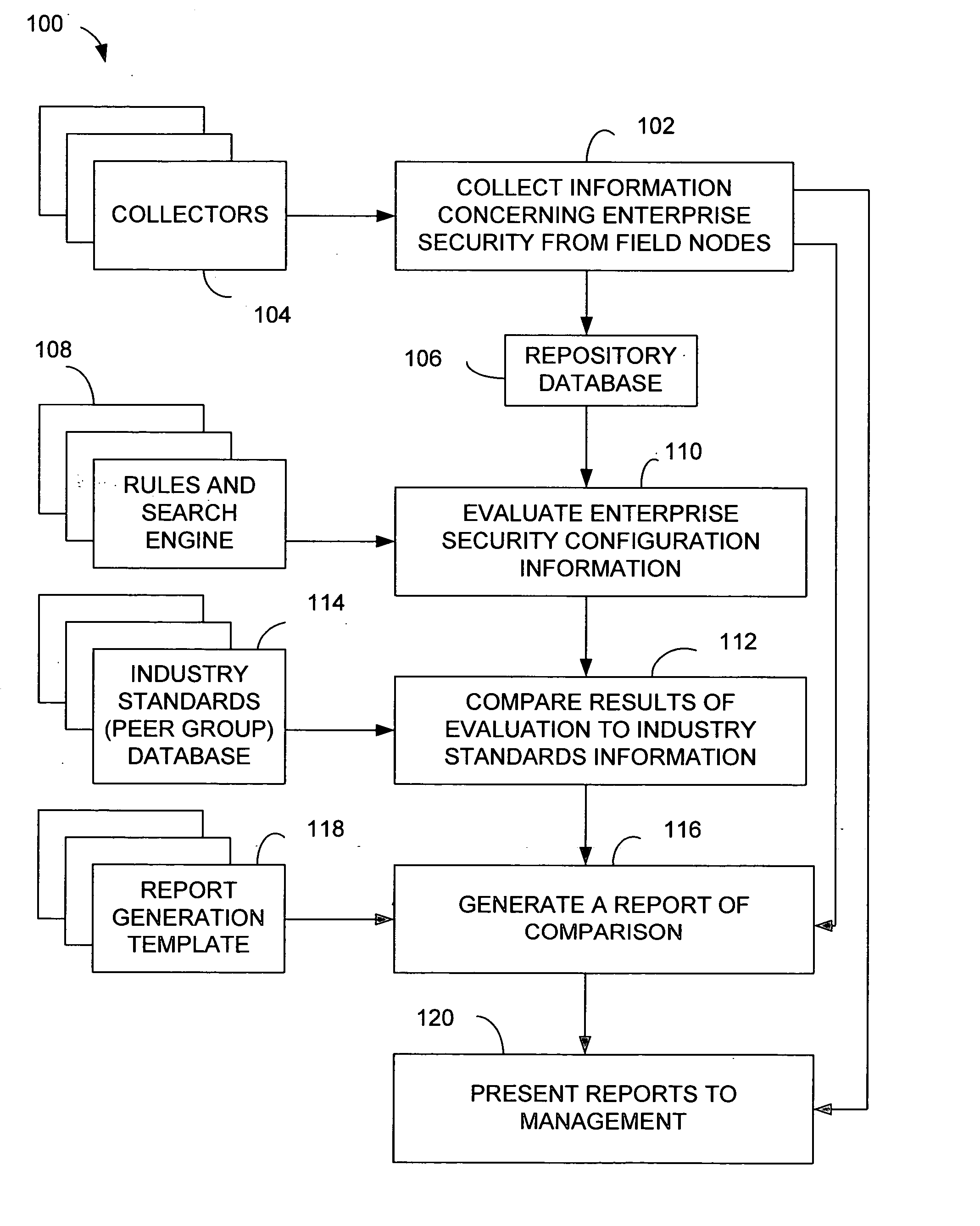
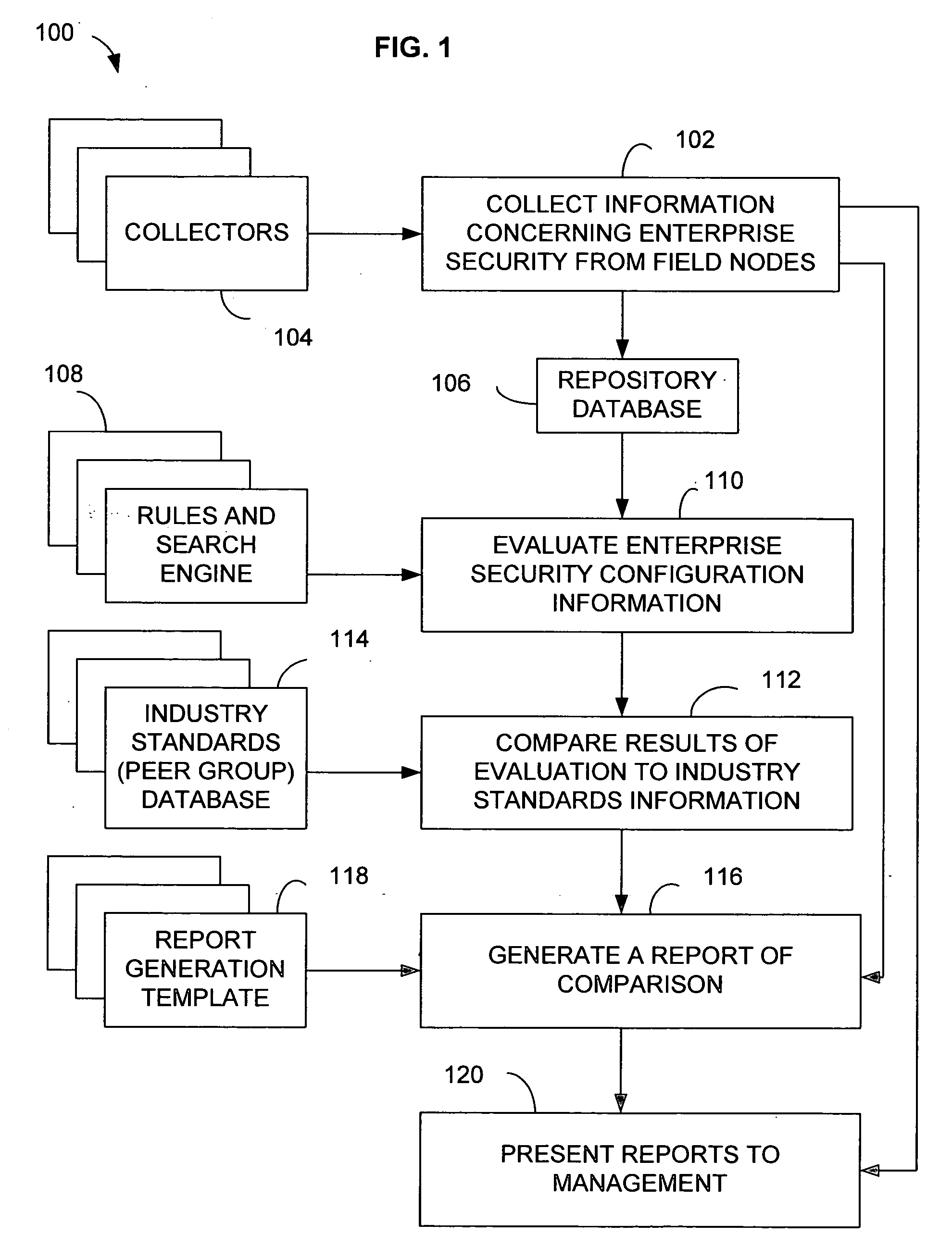
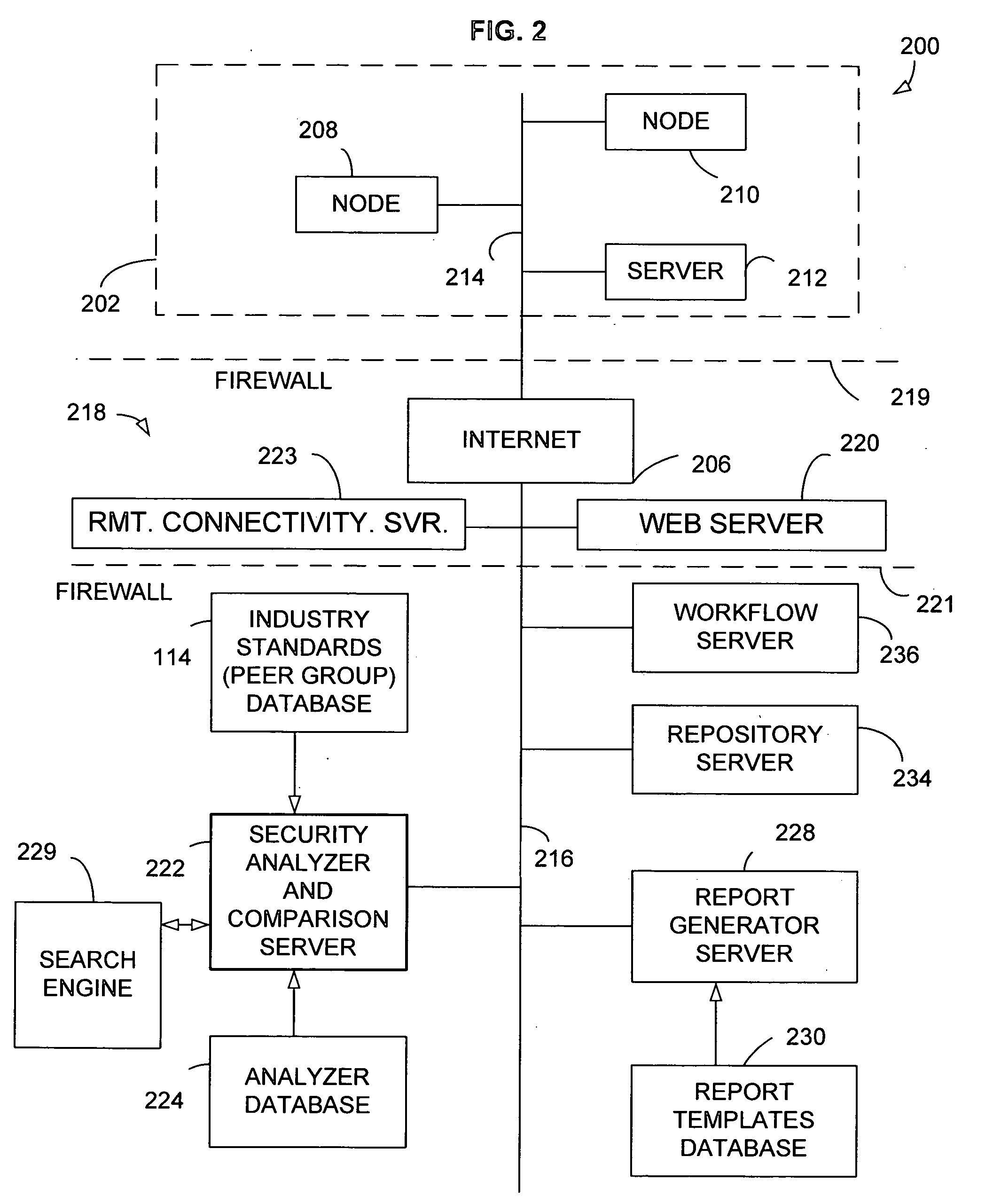
System and method for auditing the security of an enterprise
InactiveUS20050102534A1Digital data processing detailsComputer security arrangementsSecurity informationSafety standards
A method and apparatus is provided for auditing the security configuration of an enterprise having plural nodes. The method comprises collecting security information from the nodes of the enterprise under audit, analyzing the security information and providing a first result of this analysis; and then comparing this first result with a second result comprising security standards applicable to the enterprise under audit and one or more other enterprises that together form a relevant peer group, the result of this comparing step indicating the security of the enterprise under audit relative to that of the peer group of enterprises. The apparatus comprises an apparatus that carries out these same steps.
Owner:HEWLETT PACKARD DEV CO LP
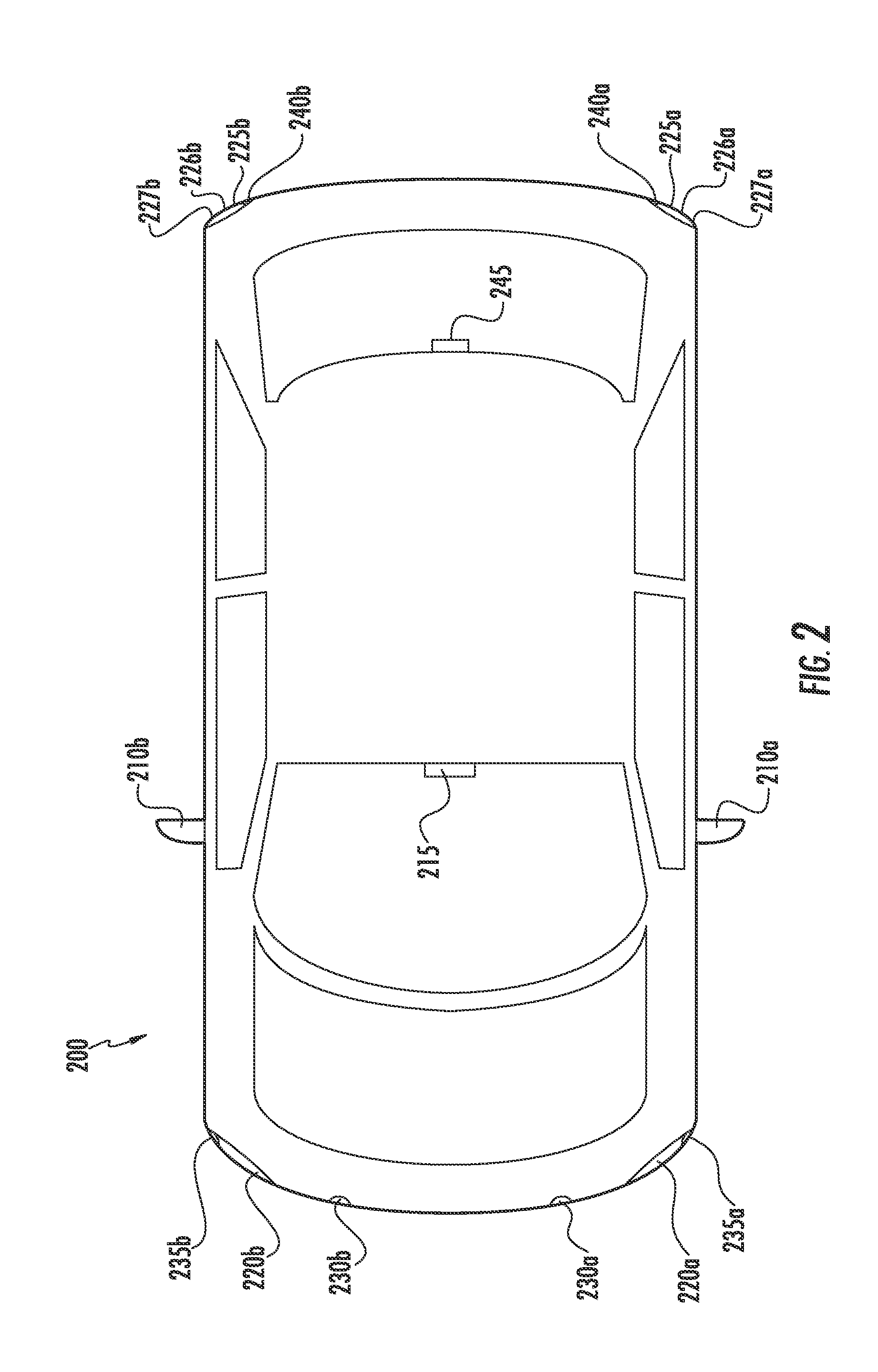
Automotive rearview mirror with capacitive switches
A vehicular rearview assembly that has a rounded outer perimeter edge to satisfy safety standards and contains an EC element having a complex peripheral ring, a front surface that is fully observable from the front of the assembly, and a user interface with switches and sensors that activate and configure, in cooperation with electronic circuitry of the assembly, pre-defined function(s) or device(s) of the assembly in response to the user input applied to the user interface. A complex peripheral ring may include multiple bands the structures of which is adapted to provide for specified optical characteristics of light, reflected off of the ring. Electrical communications between the electronic circuitry, the mirror element, and the user interface utilize connectors configured to exert a low contact force, onto the mirror element, limited in part by the strength of adhesive affixing the EC element to an element of the housing of the assembly.
Owner:GENTEX CORP
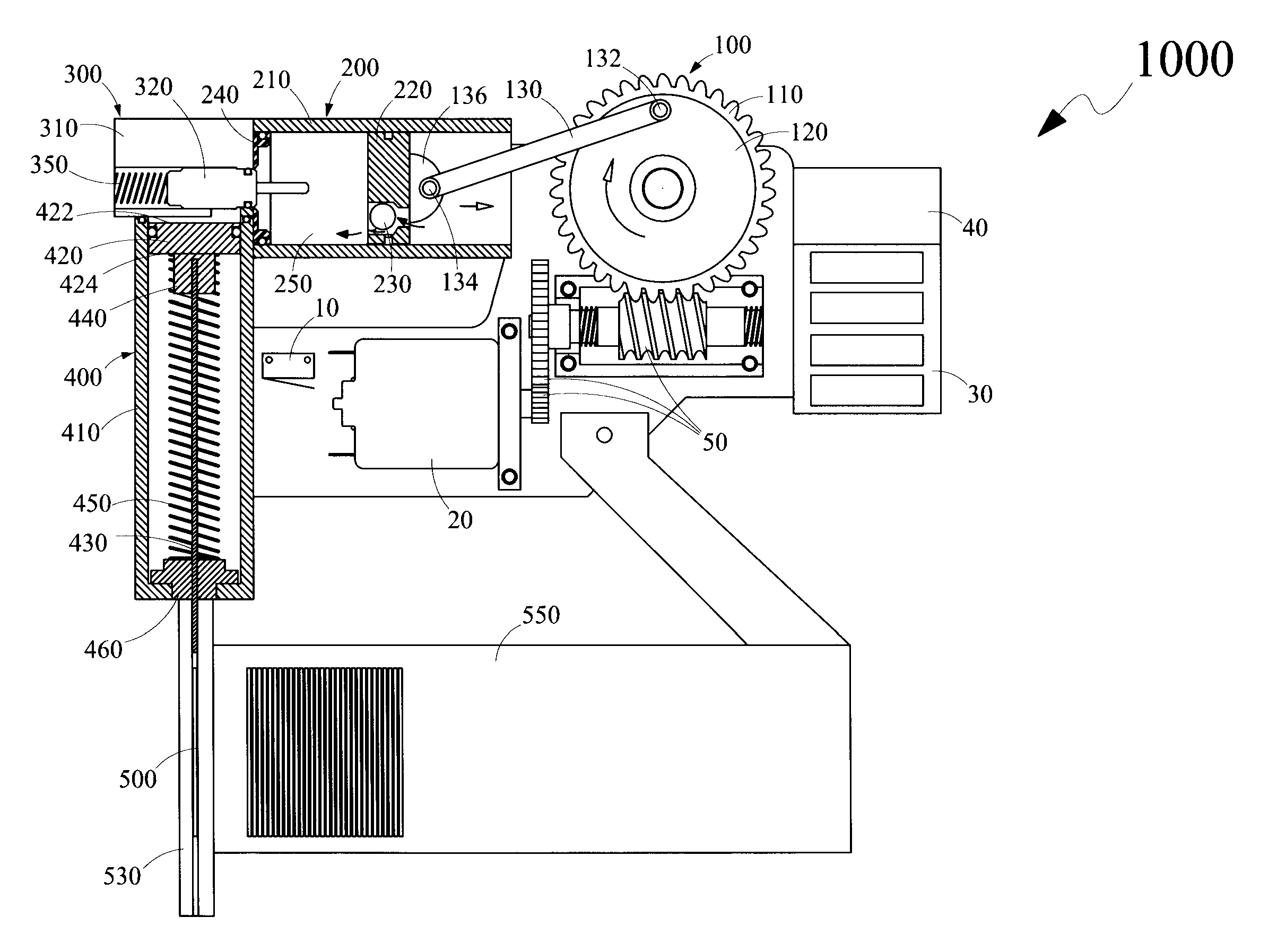
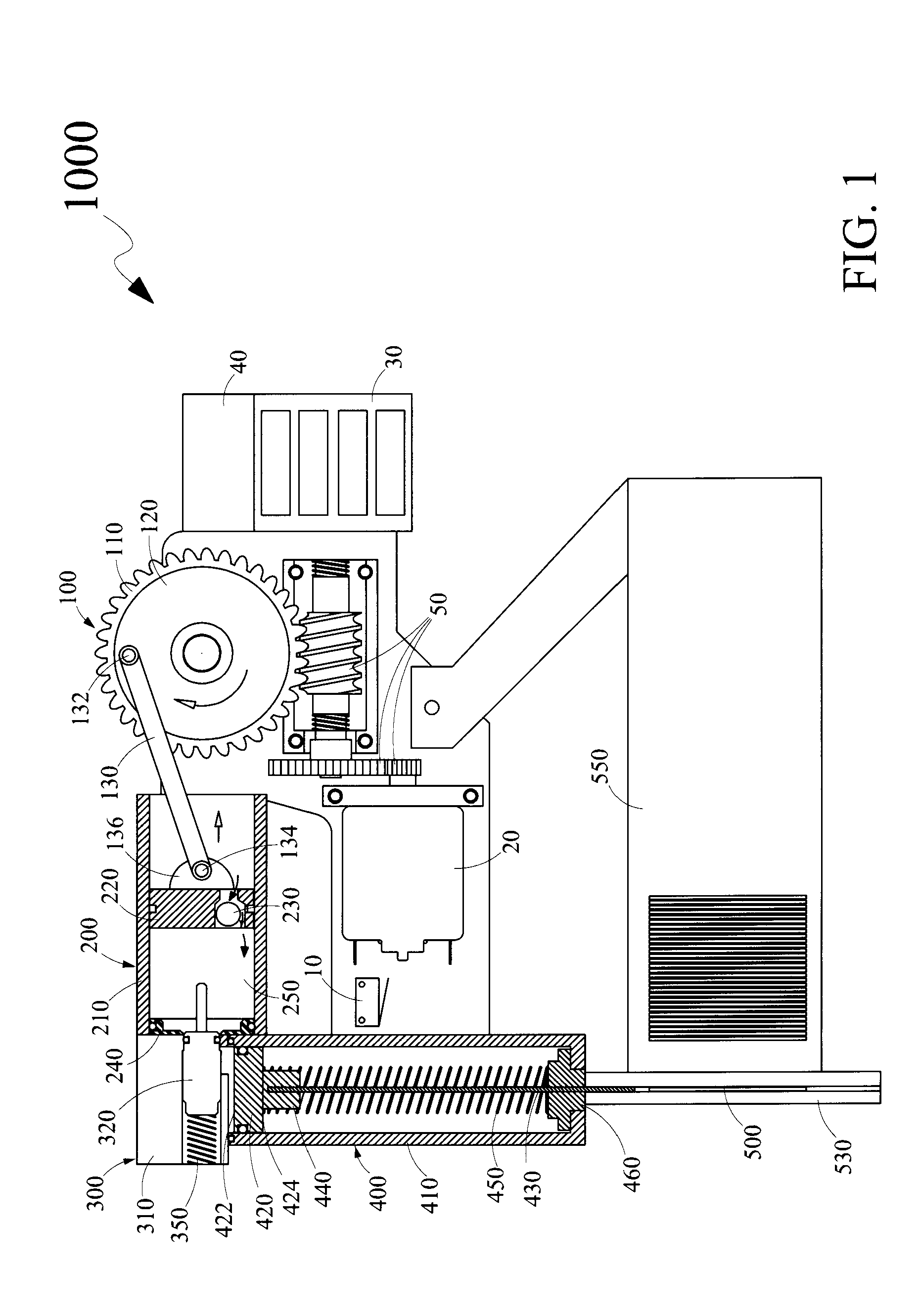
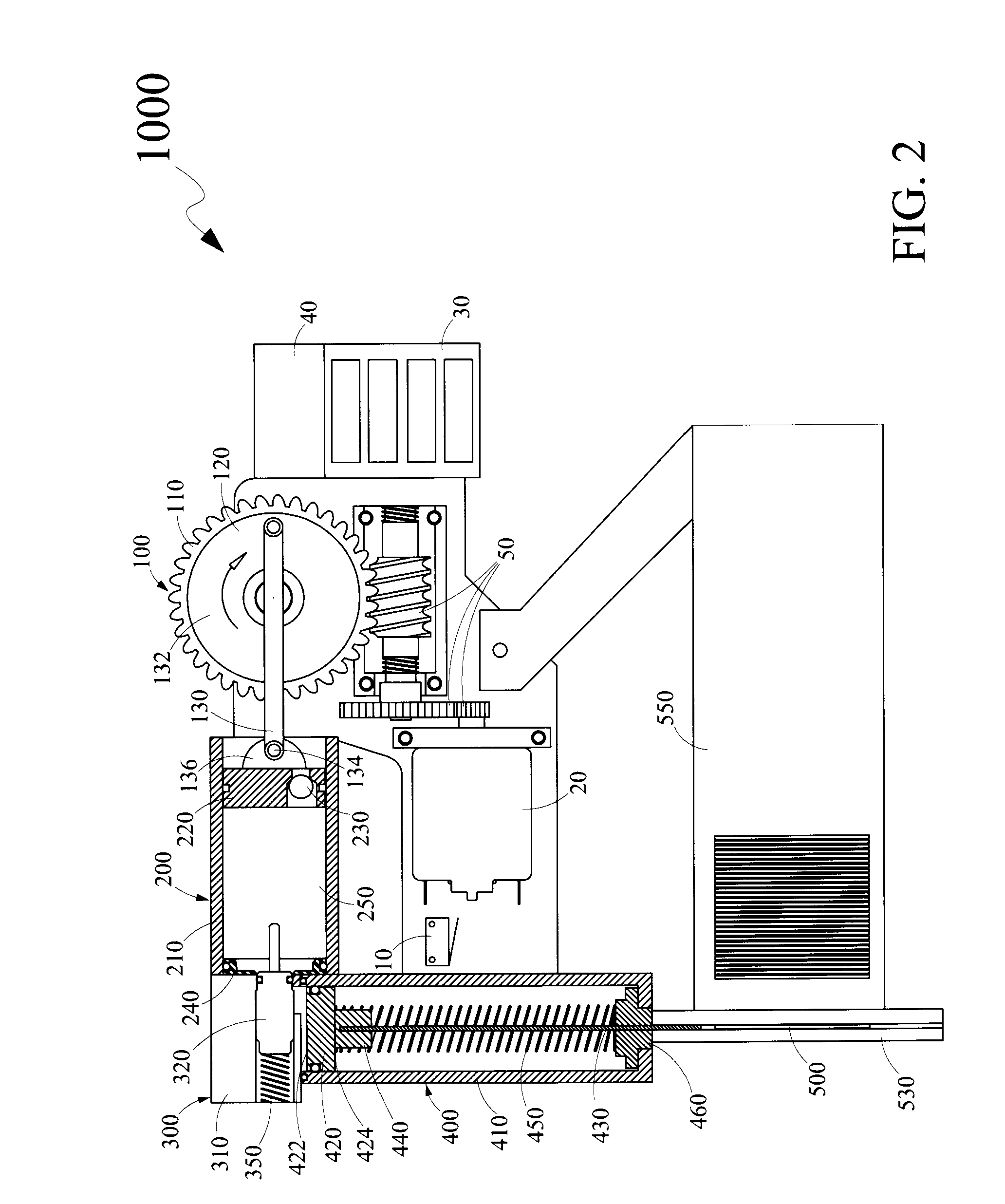
Fastener Driving Apparatus
Disclosed is a fastener driving apparatus for driving fasteners into a substrate. The fastener driving apparatus is a combination of a motor driven linear motion converter; a compression cylinder; an expansion cylinder and a valve arrangement. The linear motion converter converts a rotational motion of a motor to a linear motion of a compression piston within the compression cylinder causing a gas within the compression cylinder to be compressed. The compressed gas is communicated to the expansion cylinder through the valve arrangement wherein the compressed gas expands causing an anvil coupled to an expansion piston within the expansion cylinder to move axially. The axial movement of the anvil causes a fastener to be driven into the substrate. The fastener driving apparatus is an ergonomically designed portable hand held tool providing comfort to a user, meeting safety standards and performance efficiency requirements.
Owner:TRICORD SOLUTIONS
Method and system for providing document retention using cryptography
ActiveUS20050223242A1Effectively and properly disposingDigital data processing detailsUser identity/authority verificationElectronic documentPaper document
Techniques for utilizing security criteria to implement document retention for electronic documents are disclosed. The security criteria can also limit when, how and where access to the electronic documents is permitted. The security criteria can pertain to keys (or ciphers) used to secure (e.g., encrypt) electronic files (namely, electronic documents), or to unsecure (e.g., decrypt) electronic files already secured. At least a portion of the security criteria can be used to implement document retention, namely, a document retention policy. After a secured electronic document has been retained for the duration of the document retention policy, the associated security criteria becomes no longer available, thus preventing subsequent access to the secured electronic document. In other words, access restrictions on electronic documents can be used to prevent access to electronic documents which are no longer to be retained.
Owner:CITRIX SYST INC
Method and system for providing cryptographic document retention with off-line access
ActiveUS20050223414A1Digital data processing detailsUnauthorized memory use protectionElectronic documentPaper document
Techniques for utilizing security criteria to implement document retention for electronic documents are disclosed. The security criteria can also limit when, how and where access to the electronic documents is permitted. The security criteria can pertain to keys (or ciphers) used to secure (e.g., encrypt) electronic files (namely, electronic documents), or to unsecure (e.g., decrypt) electronic files already secured. At least a portion of the security criteria can be used to implement document retention, namely, a document retention policy. After a secured electronic document has been retained for the duration of the document retention policy, the associated security criteria becomes no longer available, thus preventing subsequent access to the secured electronic document. In other words, access restrictions on electronic documents can be used to prevent access to electronic documents which are no longer to be retained.
Owner:CITRIX SYST INC
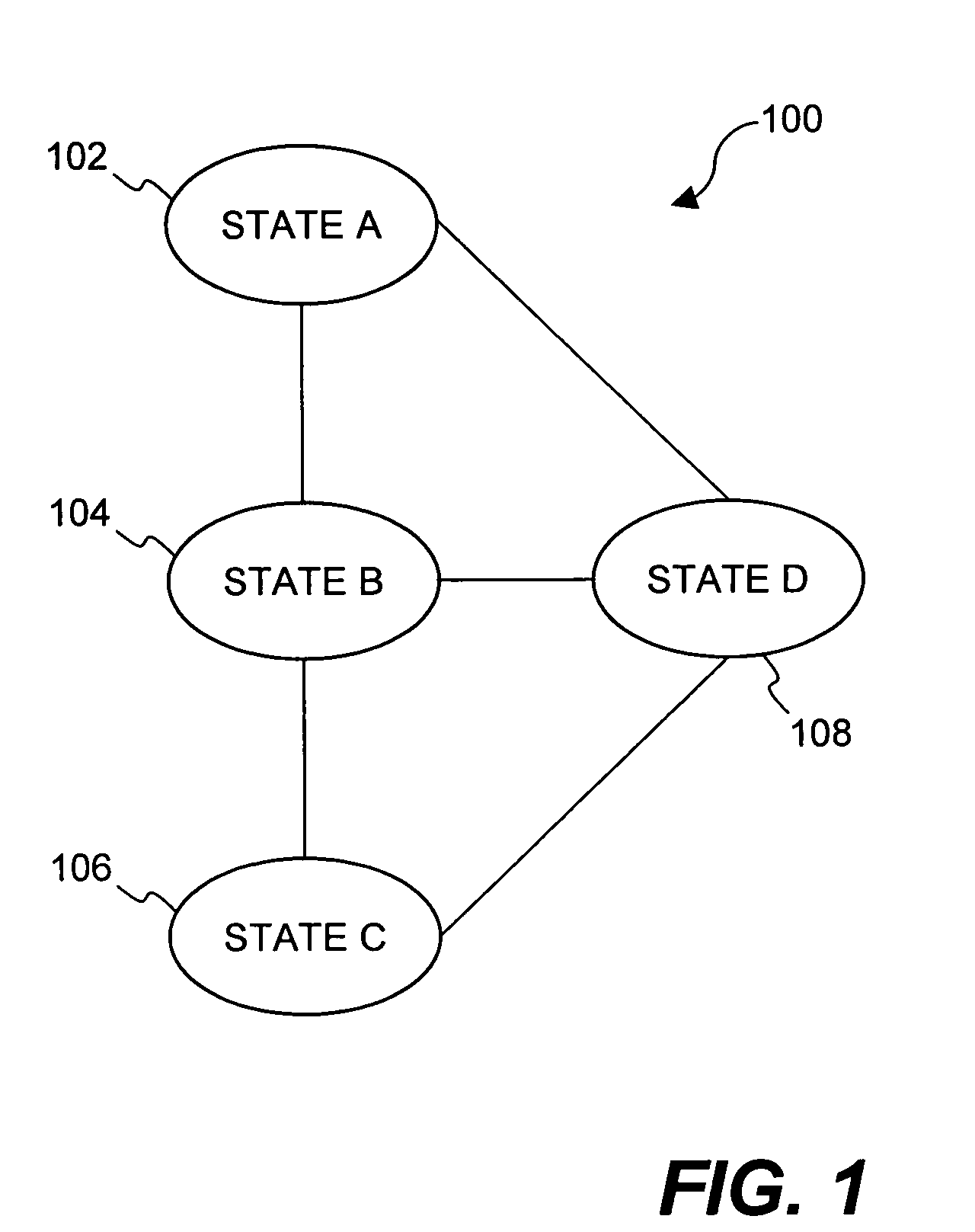
Method and system for securing digital assets using process-driven security policies
ActiveUS20050071658A1More burdensomeGood flexibilityKey distribution for secure communicationPublic key for secure communicationSecurity policySafety standards
Techniques for dynamically altering security criteria used in a file security system are disclosed. The security criteria pertains to keys (or ciphers) used by the file security system to encrypt electronic files to be secured or to decrypt electronic files already secured. The security criteria can, among other things, include keys that are required to gain access to electronic files. Here, the keys can be changed automatically as electronic files transition between different states of a process-driven security policy. The dynamic alteration of security criteria enhances the flexibility and robustness of the security system. In other words, access restrictions on electronic files can be dependent on the state of the process-driven security policy.
Owner:INTELLECTUAL VENTURES I LLC
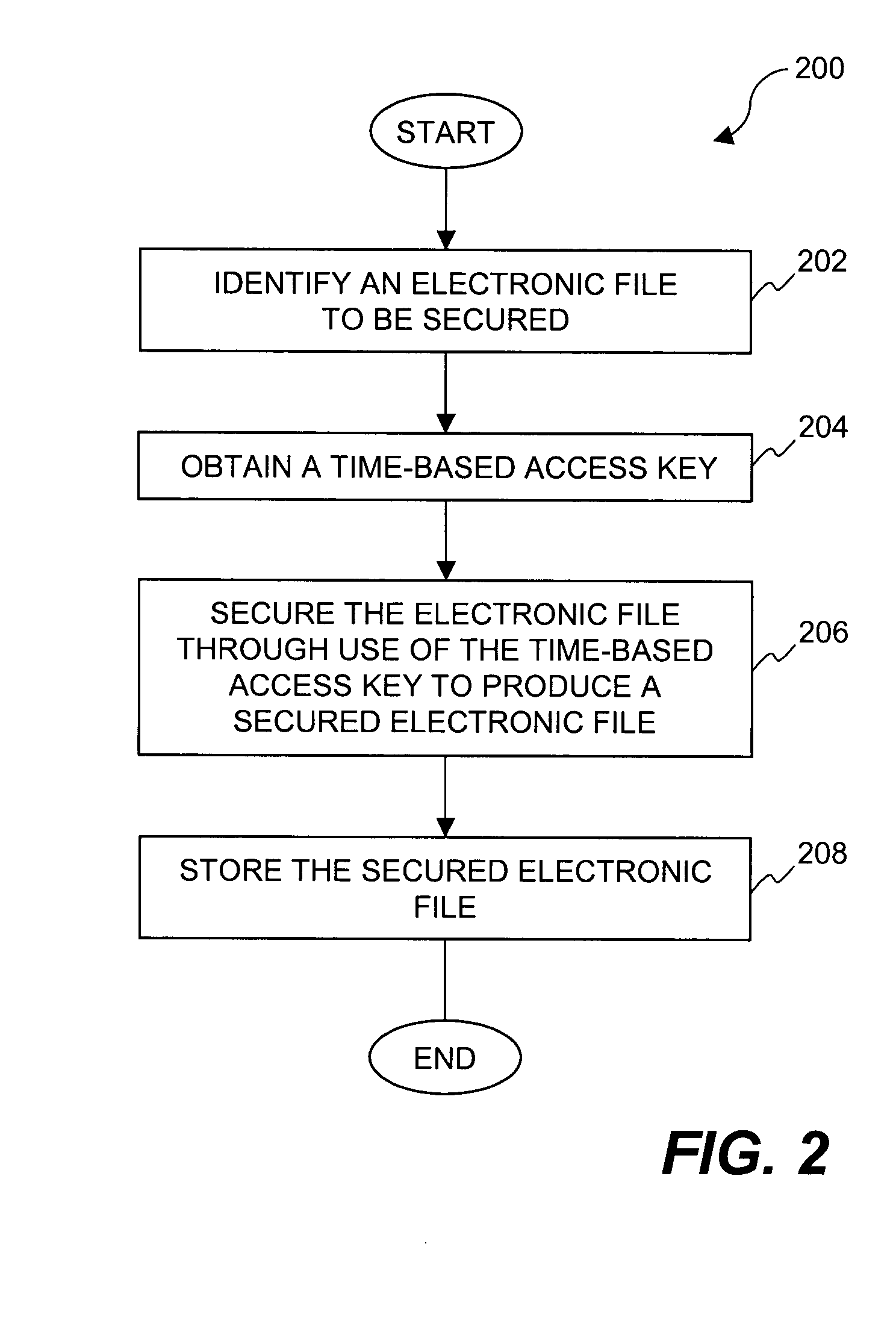
Method and system for securing digital assets using time-based security criteria
InactiveUS20050071657A1Key distribution for secure communicationUser identity/authority verificationSecurity systemSafety standards
Techniques for utilizing time-based security criteria in a file security system are disclosed. At least a portion of the security criteria can have a time associated therewith (i.e., time-based security criteria) that serves as a time-based restriction on the ability to gain access to electronic files. If the time-based restriction is not satisfied, then the associated security criteria is not made available and thus access to a secured electronic file is prevented. In other words, access restrictions on electronic files can be dependent on the time at which access to the electronic files is attempted. The security criteria can pertain to keys (or ciphers) used by the file security system to secure (e.g., encrypt) electronic files to be secured, or to unsecure (e.g., decrypt) electronic files already secured.
Owner:GUARDIAN DATA STORAGE
Enteromorpha potato chips and processing method thereof
InactiveCN105795395AGuaranteed qualityReduce moisture contentFood ingredient as taste affecting agentFood ingredient as mouthfeel improving agentMonosodium glutamateHazardous substance
The invention relates to the field of food, in particular to enteromorpha potato chips and a processing method thereof.The potato chips are full of seafood flavor, tasty in sour and sweet taste and slightly salty.The potato chips are golden matched with emerald green, and the color is very attractive and promotes appetite.The potato chips are unique in flavor, and have rich enteromorpha fresh flavor, and with the aromatic odor of orange juice, the potato chips can enable people to be full of energy and enhance appetite.Crisping of the potato chips is matched with flexibility of syrup, softness and hardness of the crisping sense are combined, and innovation and interest are added.The potato chips are safe and healthy, aginomoto and other hazardous substances are not added, and all indexes of enteromorpha powder conform to national safety standards.The potato chips are abundant in nutrition, and malnutrition, obesity and hazardous substance intake and other negative health problems caused when people eat a large number of potato chips are relieved.The potato chips have the healthcare function.
Owner:SHANGHAI OCEAN UNIV
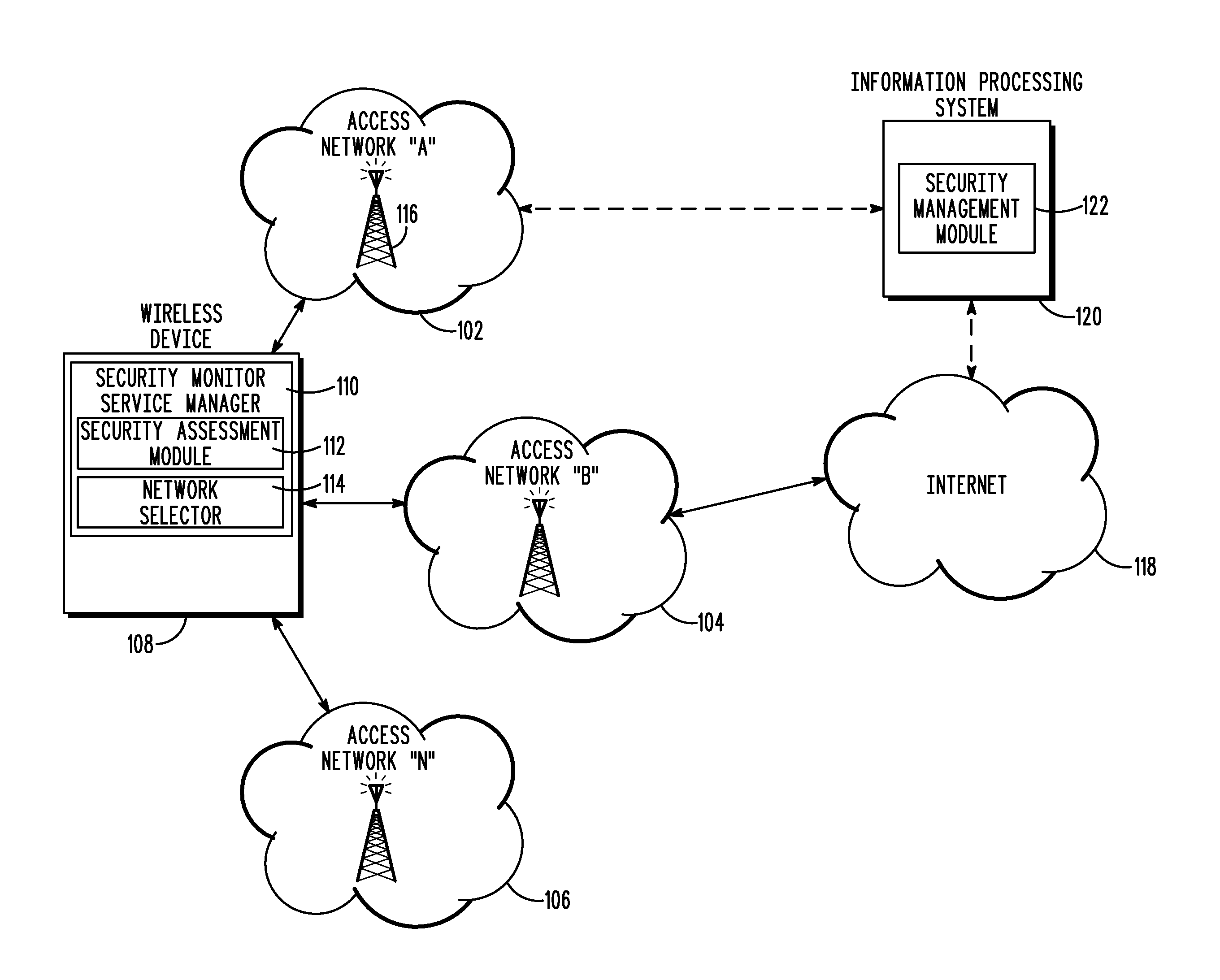
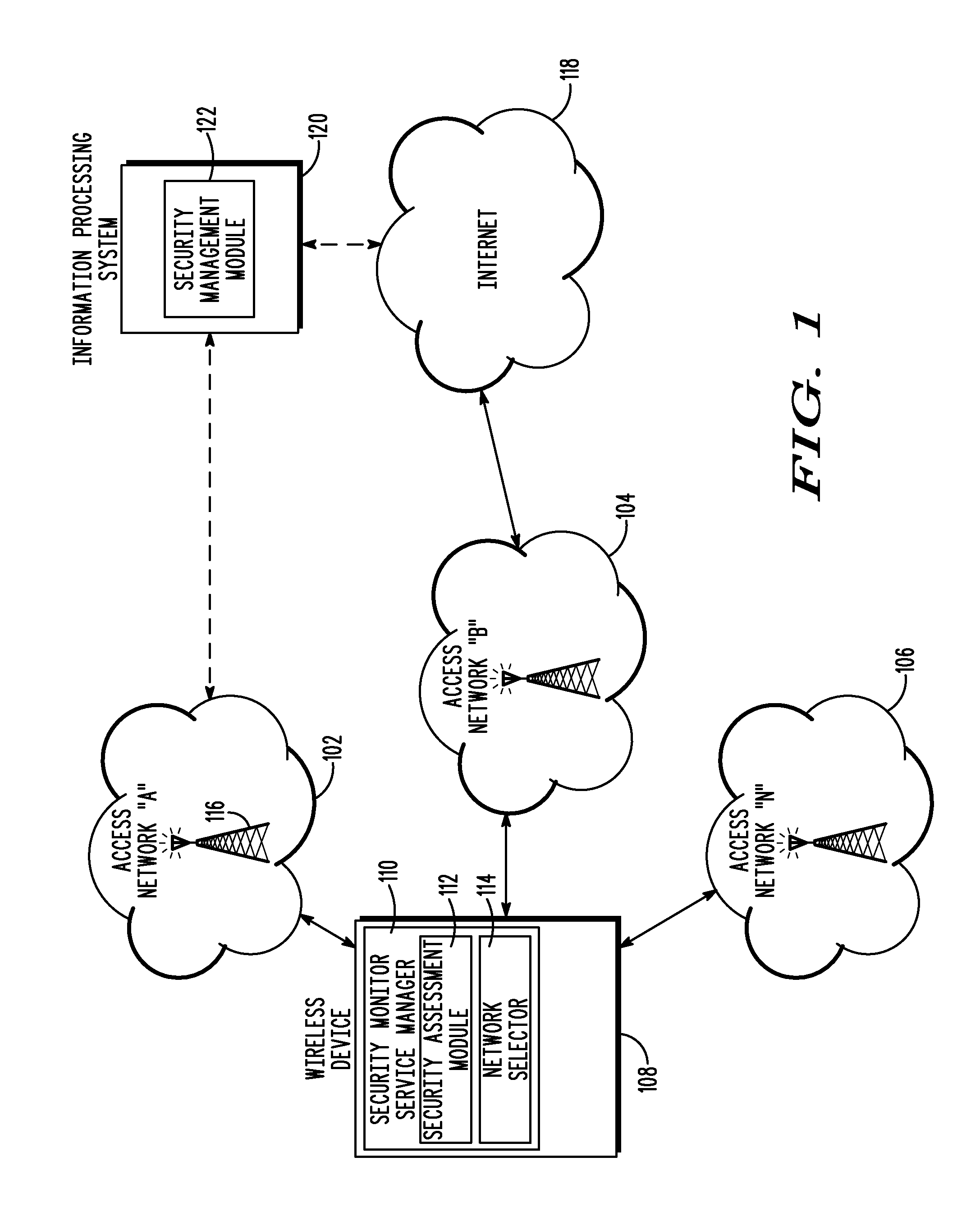
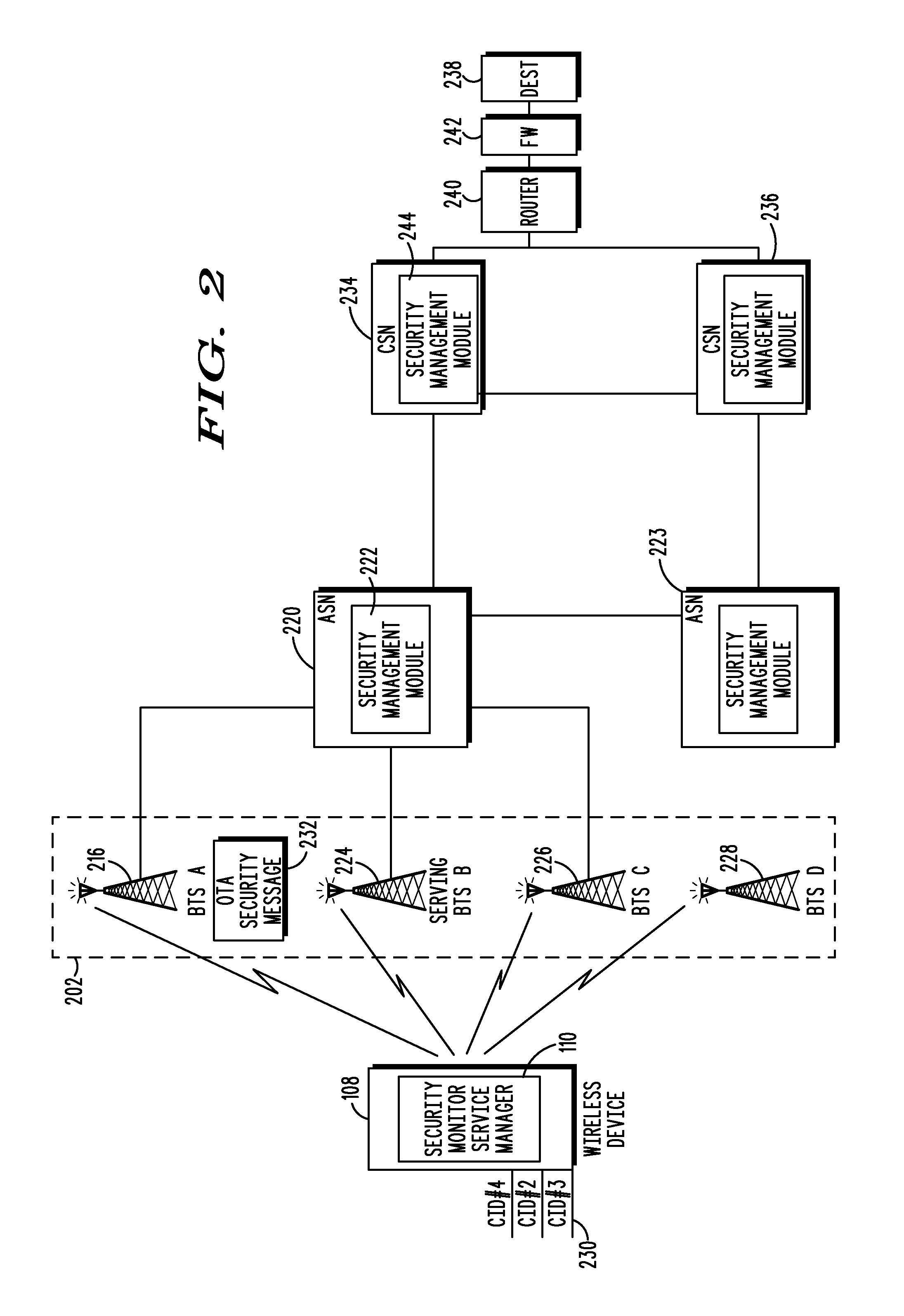
Security based network access selection
ActiveUS9325737B2Digital data processing detailsMultiple digital computer combinationsCommunications systemNetwork connection
A method and wireless device select a set of secure network connections (230) between a wireless device (108) in a wireless communication system and a target destination system (238). A first security assessment (708) associated with each of a plurality of base station connections associated with respective each of a plurality of base stations (116) available for wireless communications with the wireless device (108) is performed. A second security assessment (716) associated with each of a plurality of subsequent network connections available between the plurality of base stations (116) and a target destination system (238) is performed. A set of base station connections from the plurality of base station connections are prioritized according to predetermined security criteria associated with the wireless device (108). A set of subsequent network connections from the plurality of subsequent network connections (230) are prioritized according to predetermined security criteria associated with the wireless device (108).
Owner:MOTOROLA SOLUTIONS INC
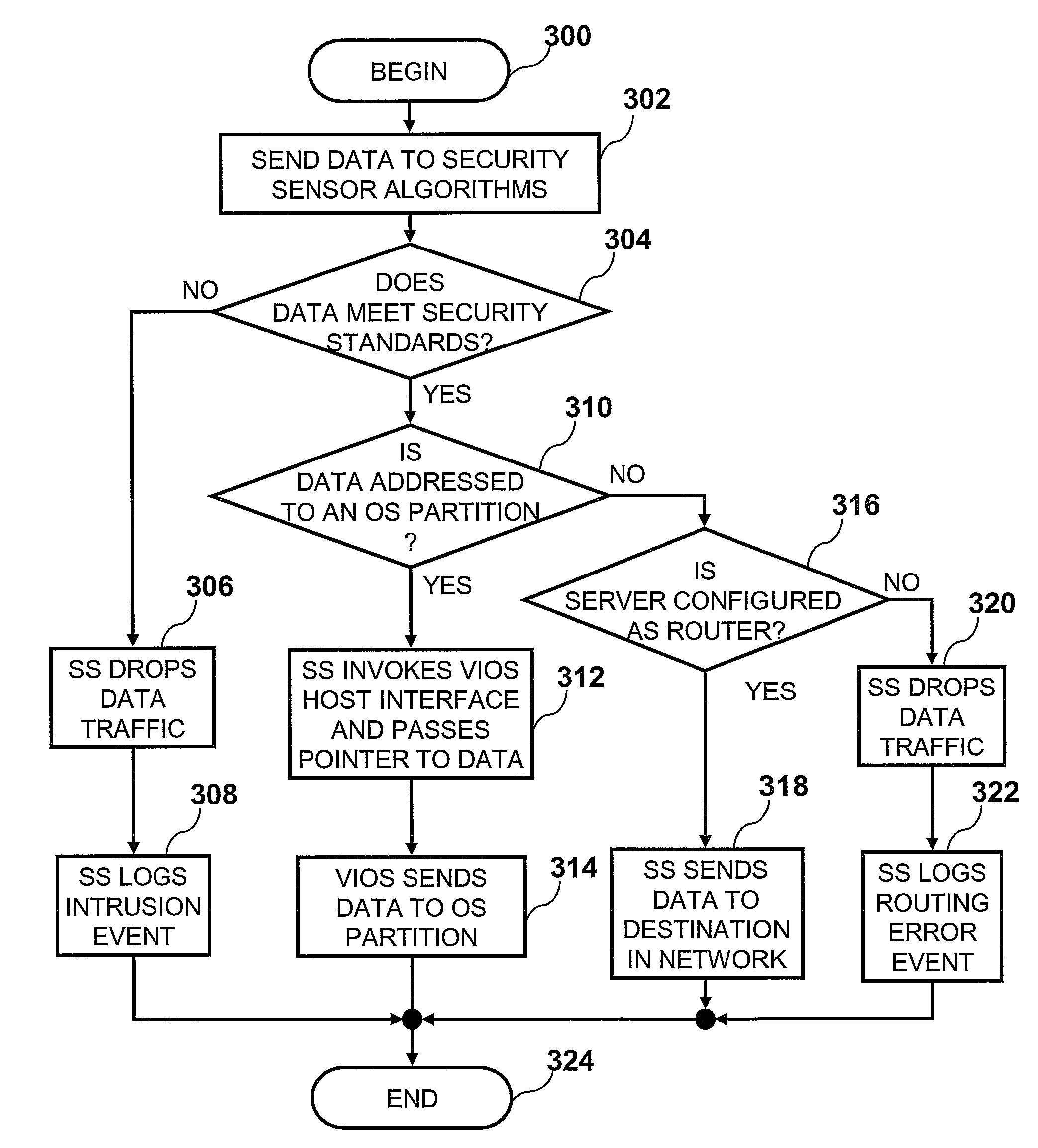
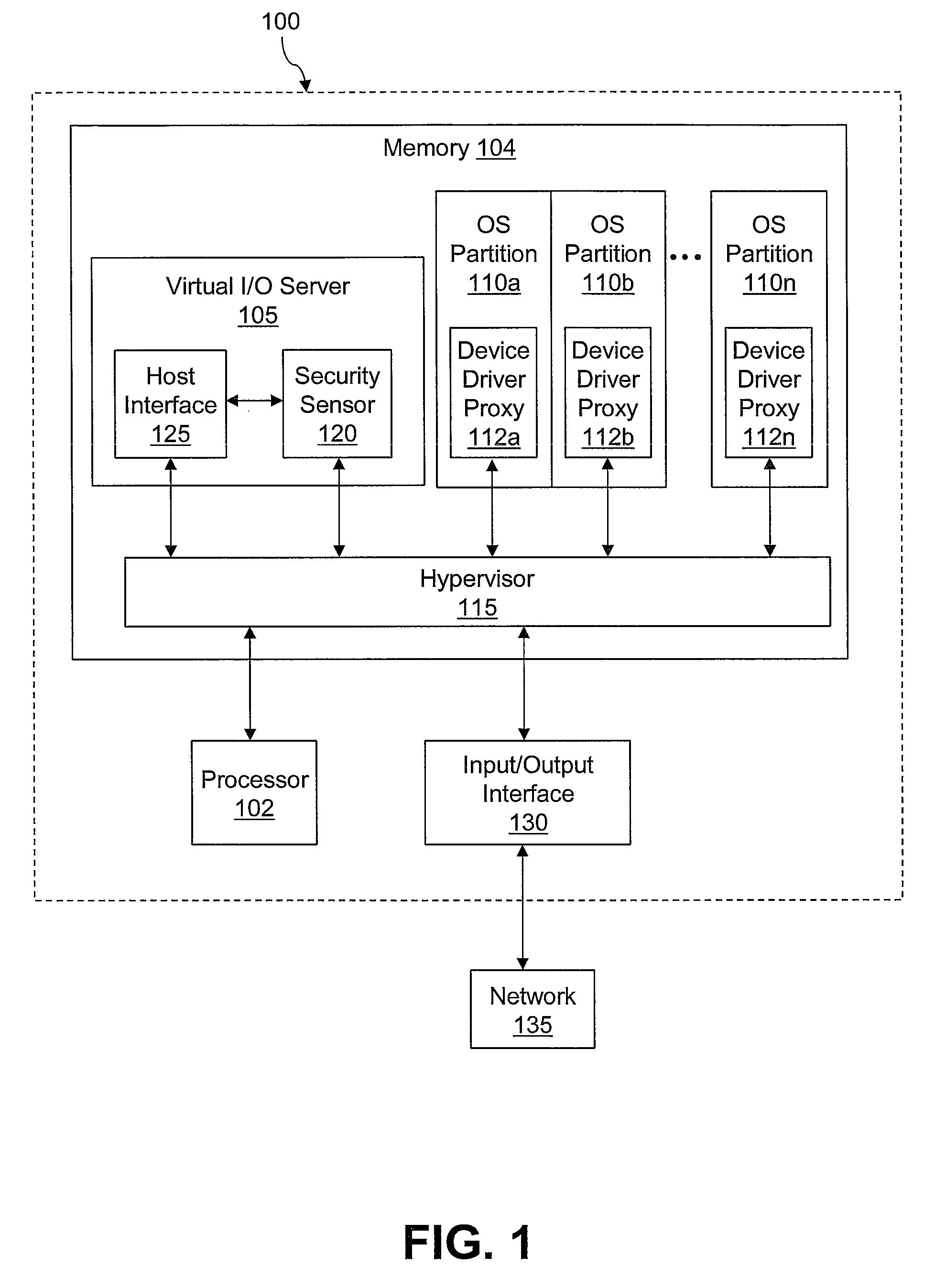
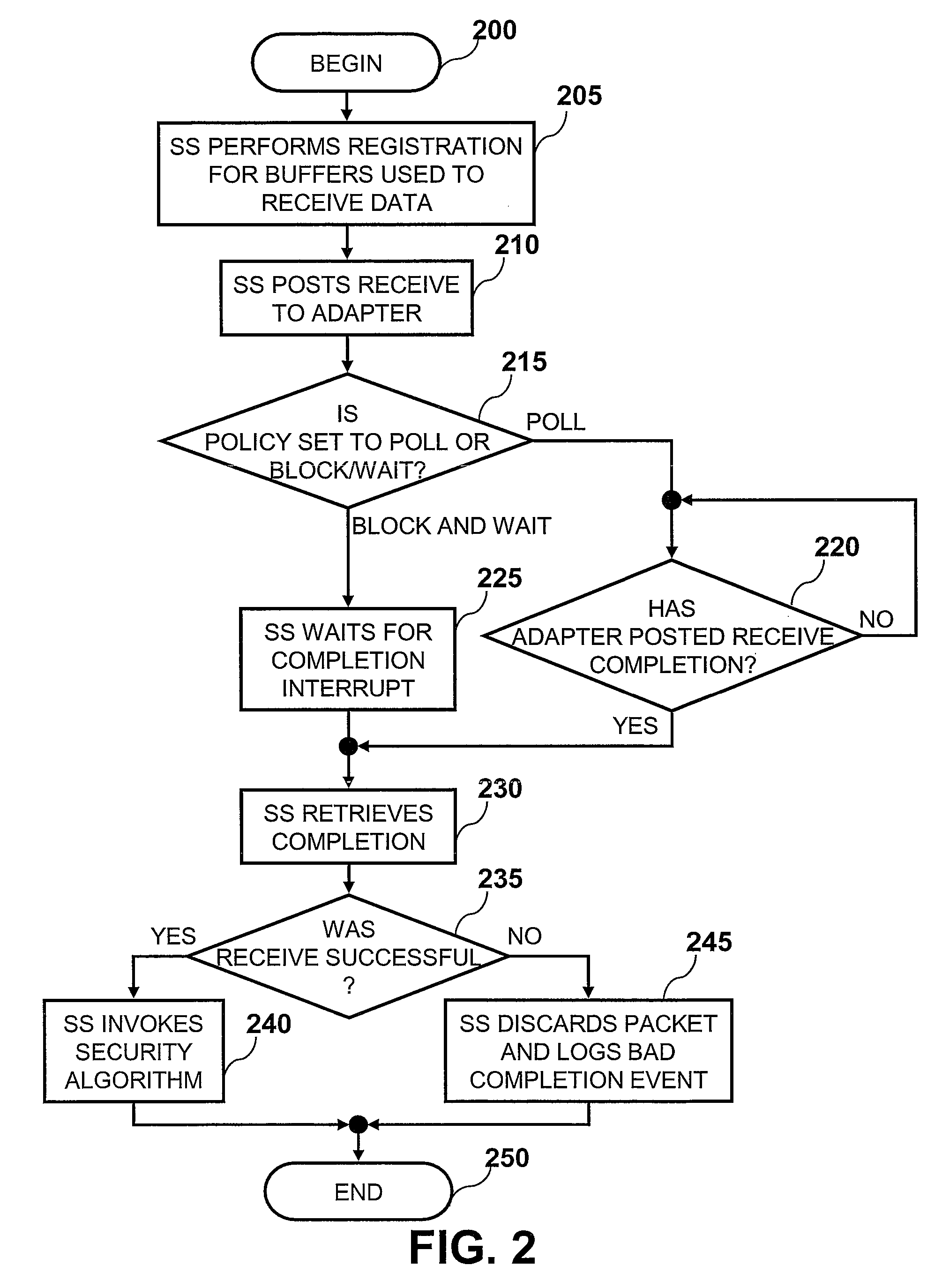
Providing server security via a security sensor application shared by multiple operating system partitions
InactiveUS7844744B2Digital data processing detailsAnalogue secracy/subscription systemsTraffic capacityOperational system
Owner:INT BUSINESS MASCH CORP
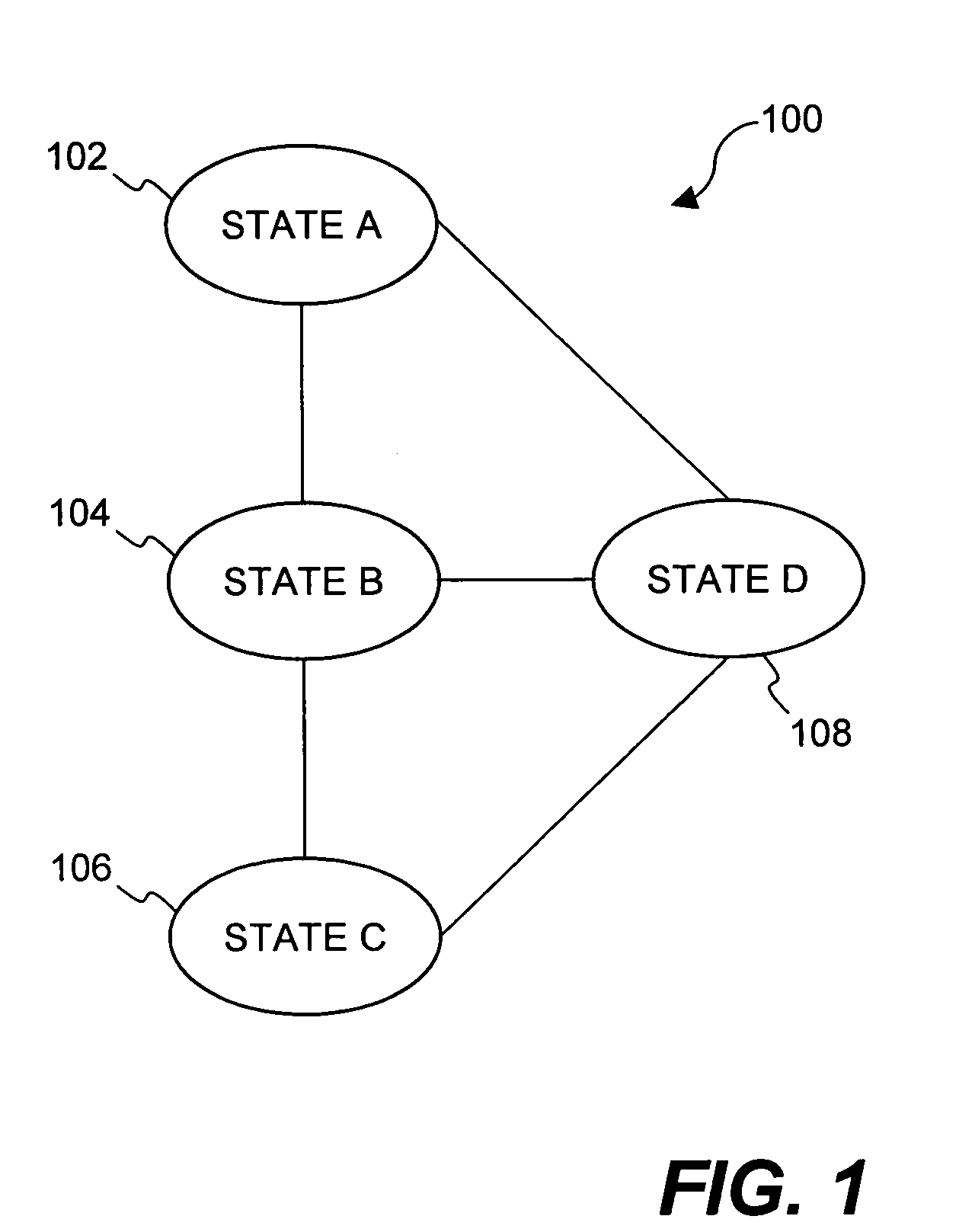
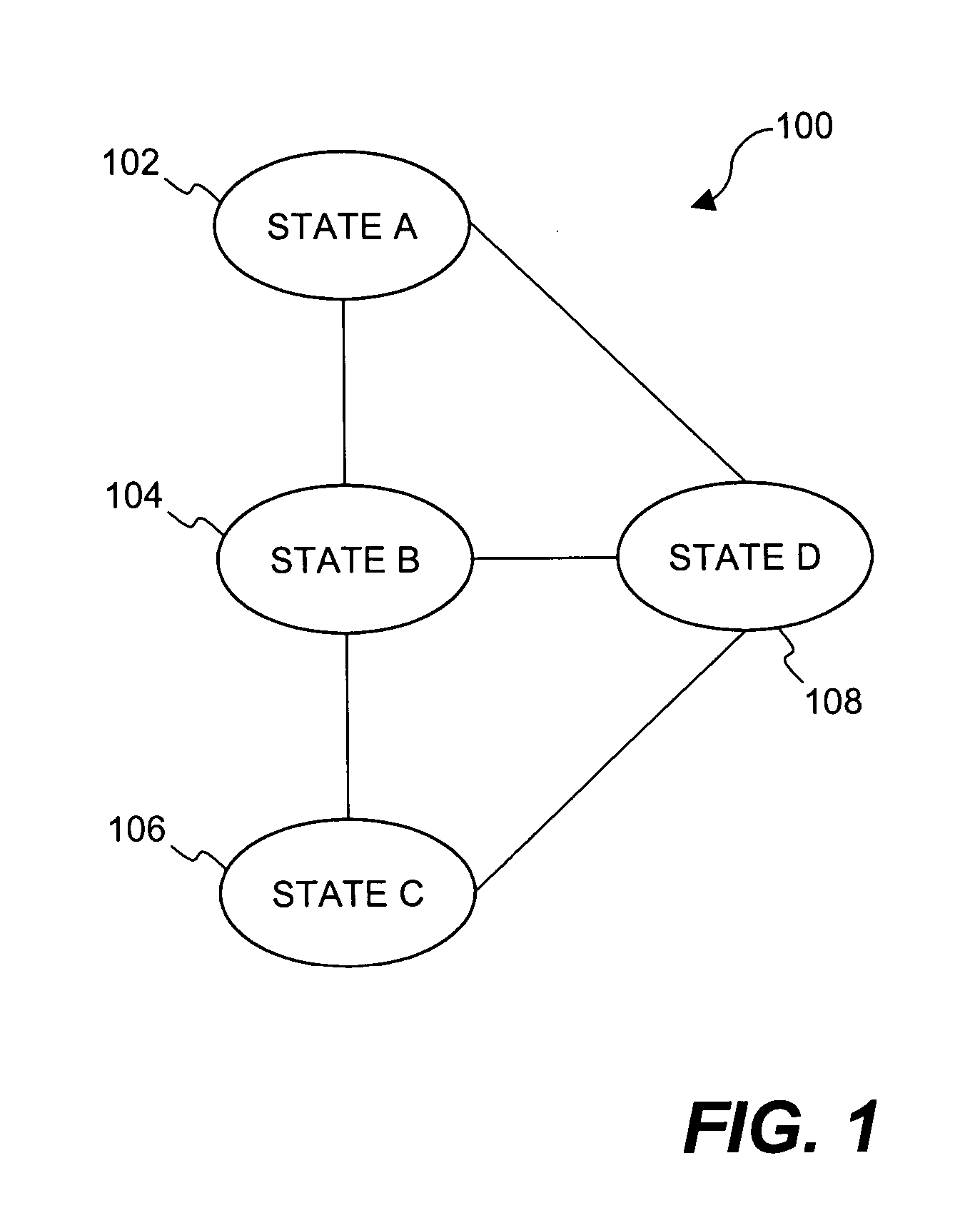
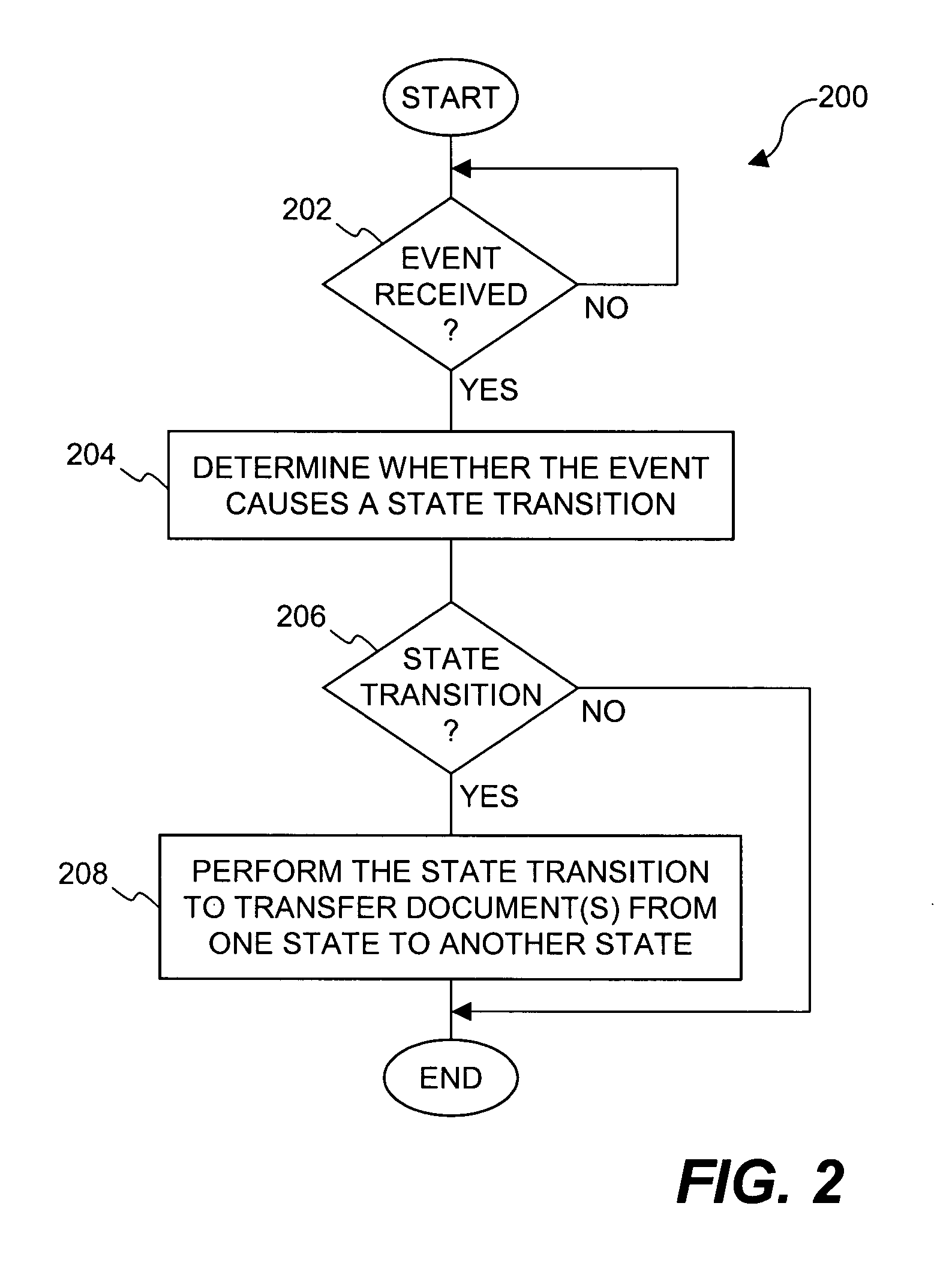
Method and apparatus for transitioning between states of security policies used to secure electronic documents
ActiveUS20050071275A1More burdensomeGood flexibilityKey distribution for secure communicationDigital data processing detailsElectronic documentSecurity policy
Techniques for dynamically altering security criteria used in a file security system are disclosed. The security criteria pertains to keys (or ciphers) used by the file security system to encrypt electronic files to be secured or to decrypt electronic files already secured. The security criteria can, among other things, include keys that are required to gain access to electronic files. Here, the keys can be changed automatically as electronic files transition between different states of a process-driven security policy. The dynamic alteration of security criteria enhances the flexibility and robustness of the security system. In other words, access restrictions on electronic files can be dependent on the state of the process-driven security policy and enforced in conjunction with one or more cryptographic methods.
Owner:INTELLECTUAL VENTURES I LLC
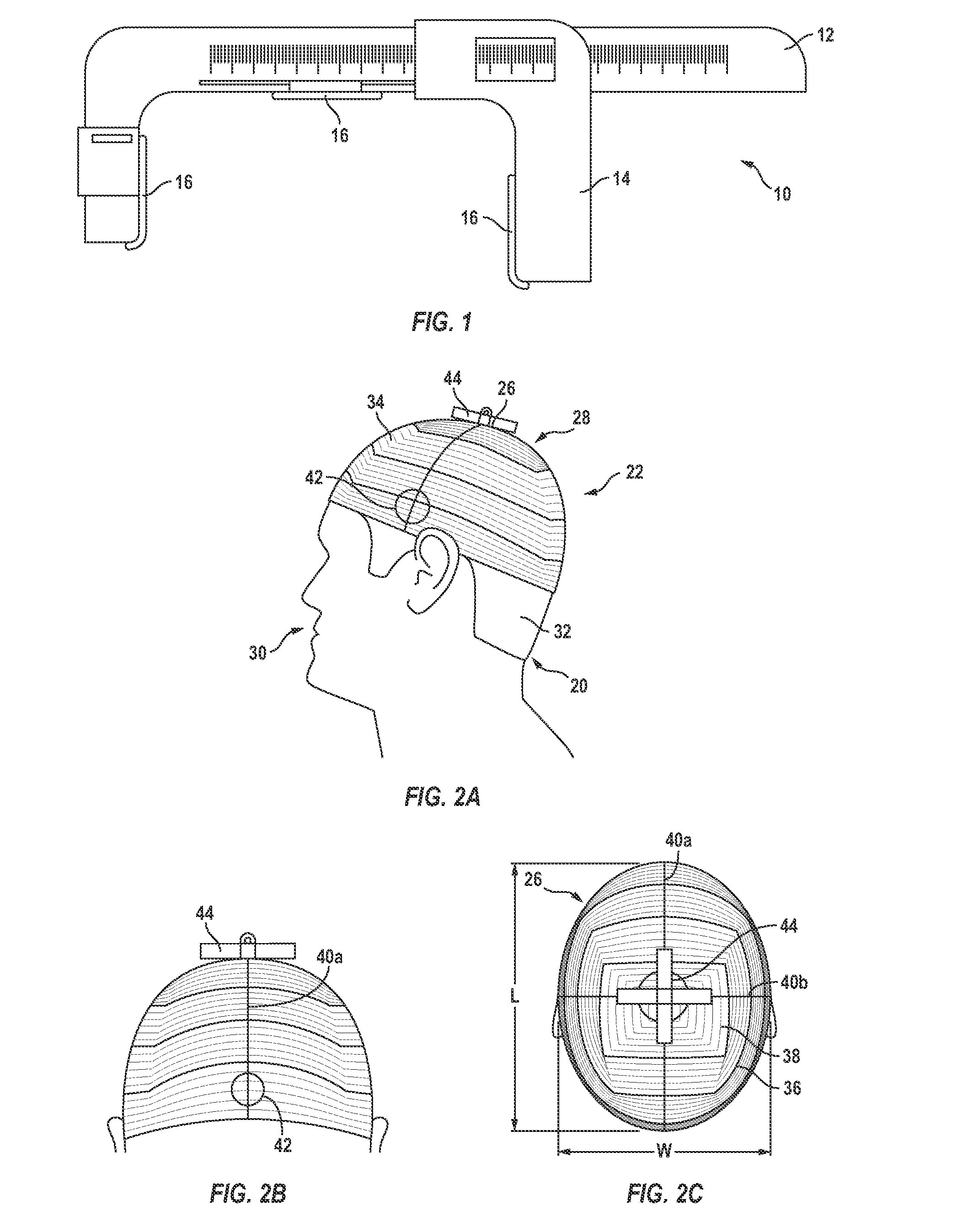
System and method for custom forming a protective helmet for a customer's head
ActiveUS20140201889A1Easy to viewProgramme controlAdditive manufacturing apparatusHead shapeTopography
A custom-fitted helmet and a method of making the same can comprise, at a first location, obtaining head data for a customer's head comprising a length, a width, and at least one head contour. With at least one processor, generating a computerized three-dimensional (3D) headform matching the customer's head length, width, and head contour from the head data. The 3D headform can be compared to a helmet safety standard. At a second location different from the first location, a custom-fitted helmet based on the 3D headform can be formed, wherein the custom-fitted helmet satisfies the safety standard and comprises an inner surface comprising a topography that conforms to the length, width, and at least one contour of the customer's head. The first location can be a home or a store. Obtaining the head data from photographic images of a deformable interface member disposed on the customer's head.
Owner:BELL SPORTS INC
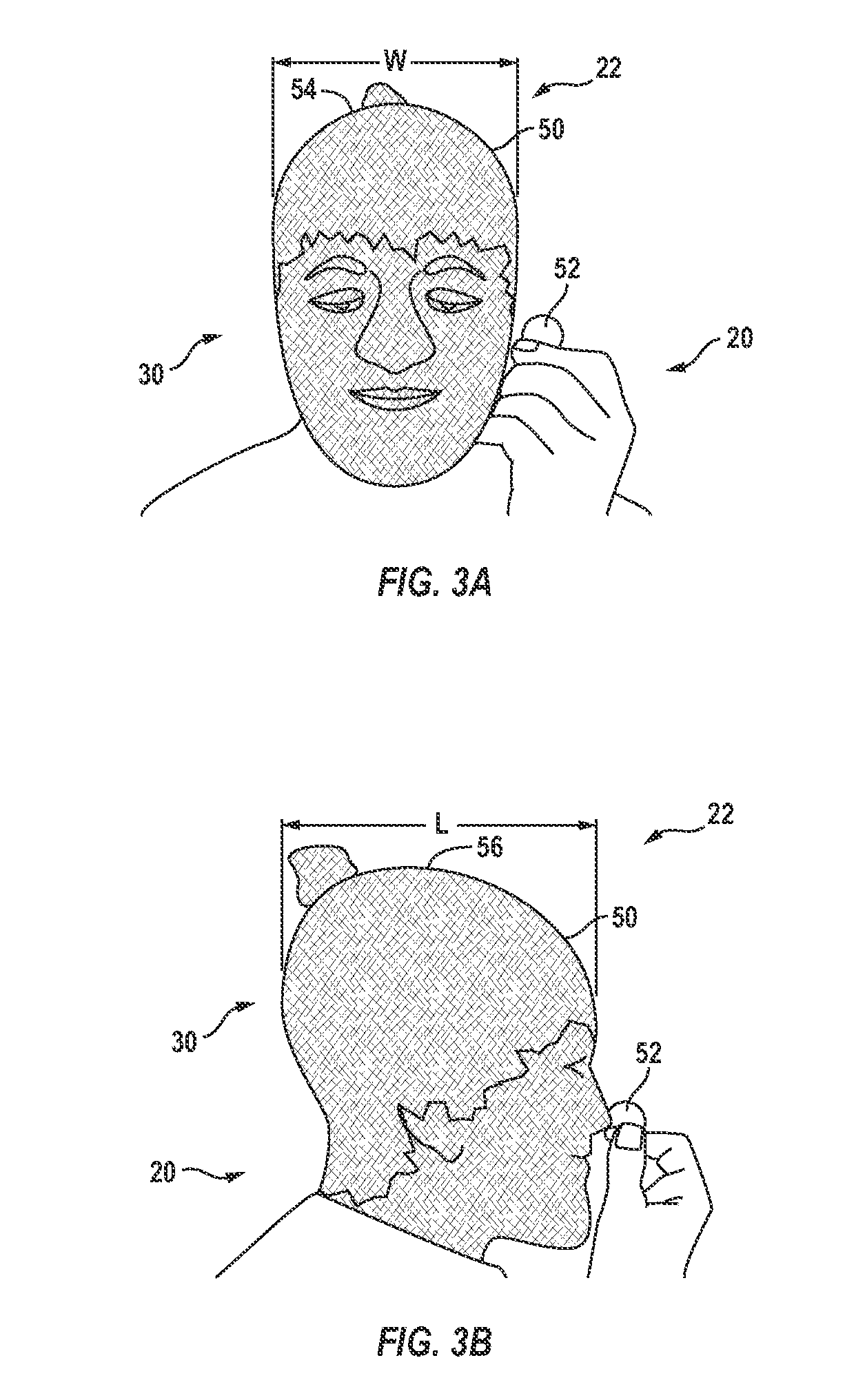
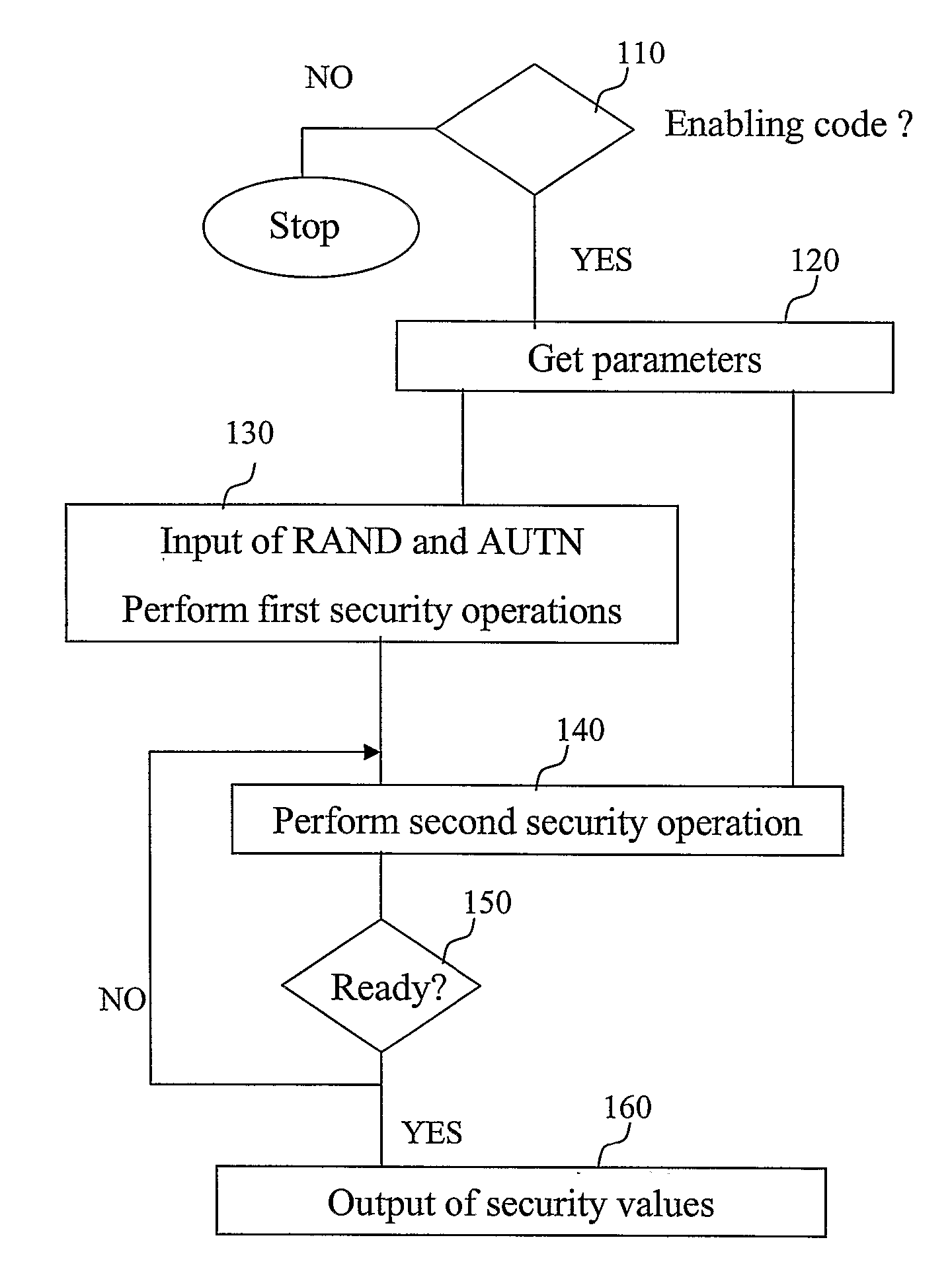
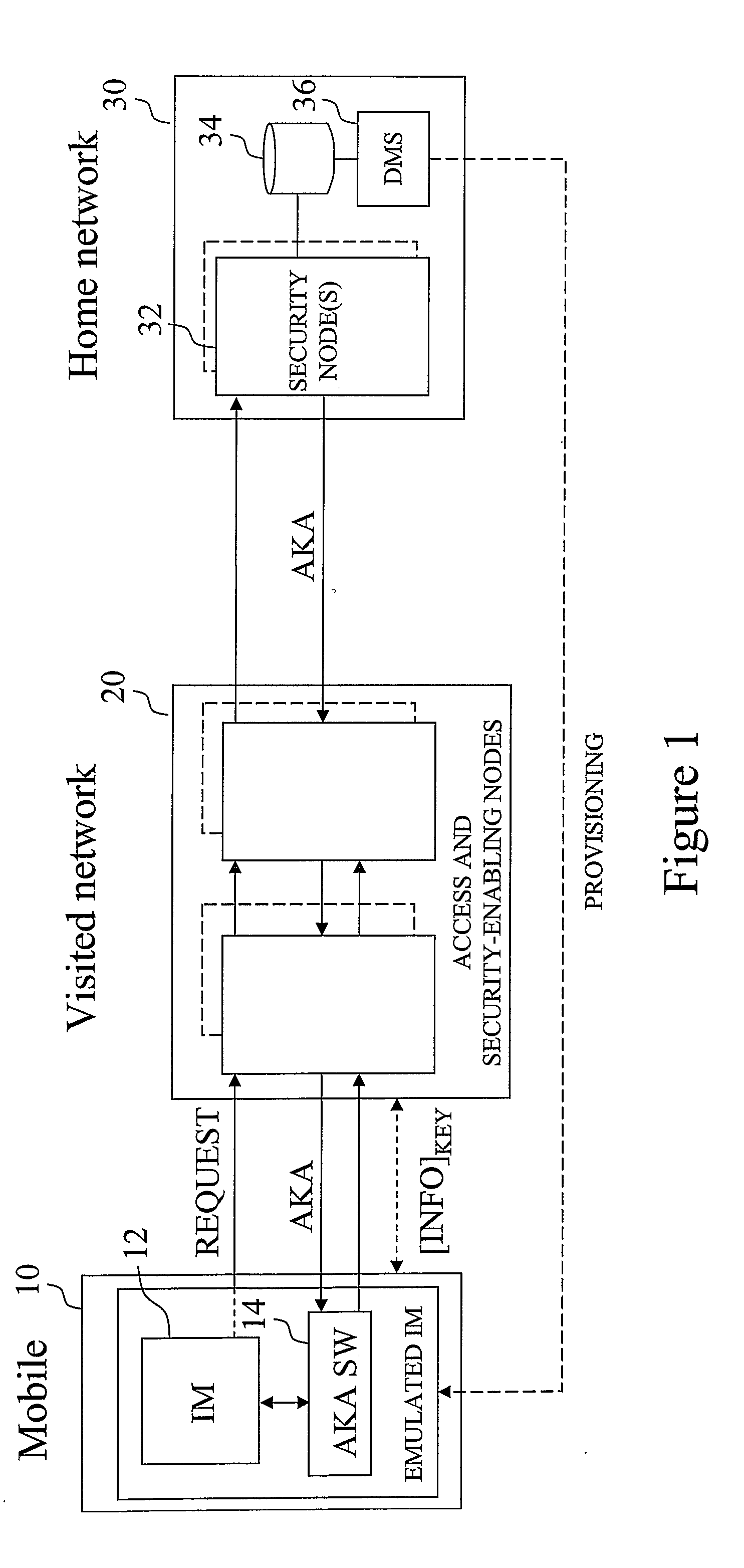
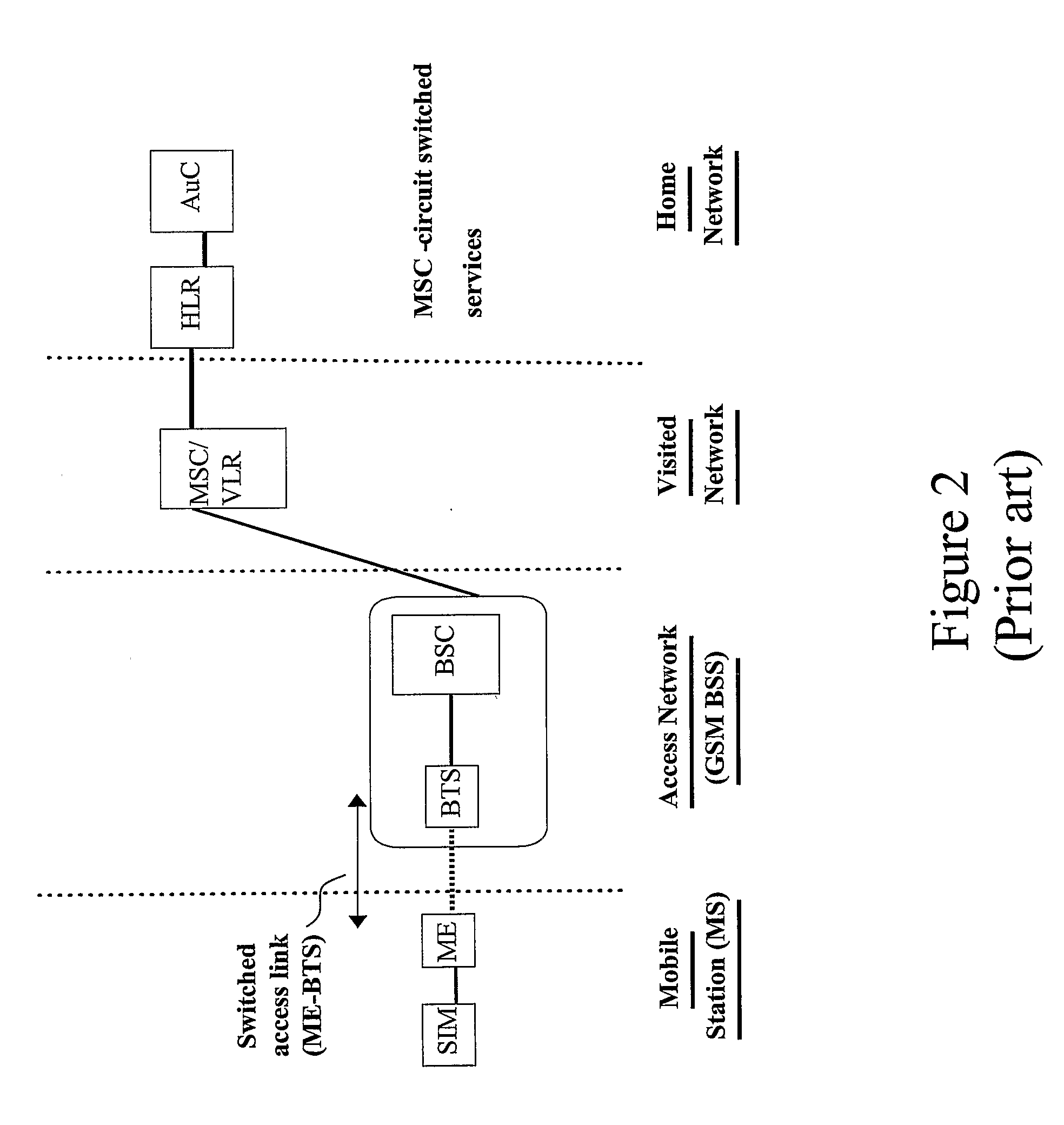
Security in a mobile communications system
ActiveUS20070157022A1Improve securityUnauthorised/fraudulent call preventionEavesdropping prevention circuitsCommunications systemThird generation
When a mobile terminal (10), having a basic identity module (12) operative according to a first security standard, initiates a service access, the home network (30) determines whether the mobile terminal has an executable program (14) configured to interact with the basic identity module for emulating an identity module according to the second security standard. If it is concluded that the mobile terminal has such an executable program, a security algorithm is executed at the home network (30) to provide security data according to the second security standard. At least part of these security data are then transferred, transparently to a visited network (20), to the mobile terminal (10). On the mobile terminal side, the executable program (14) is executed for emulating an identity module according to the second security standard using at least part of the transferred security data as input. Preferably, the first security standard corresponds to a 2G standard, basically the GSM standard and the second security standard at least in part corresponds to a 3G standard such as the UMTS standard, and / or the IP Multimedia Sub-system (IMS) standard.
Owner:TELEFON AB LM ERICSSON (PUBL)
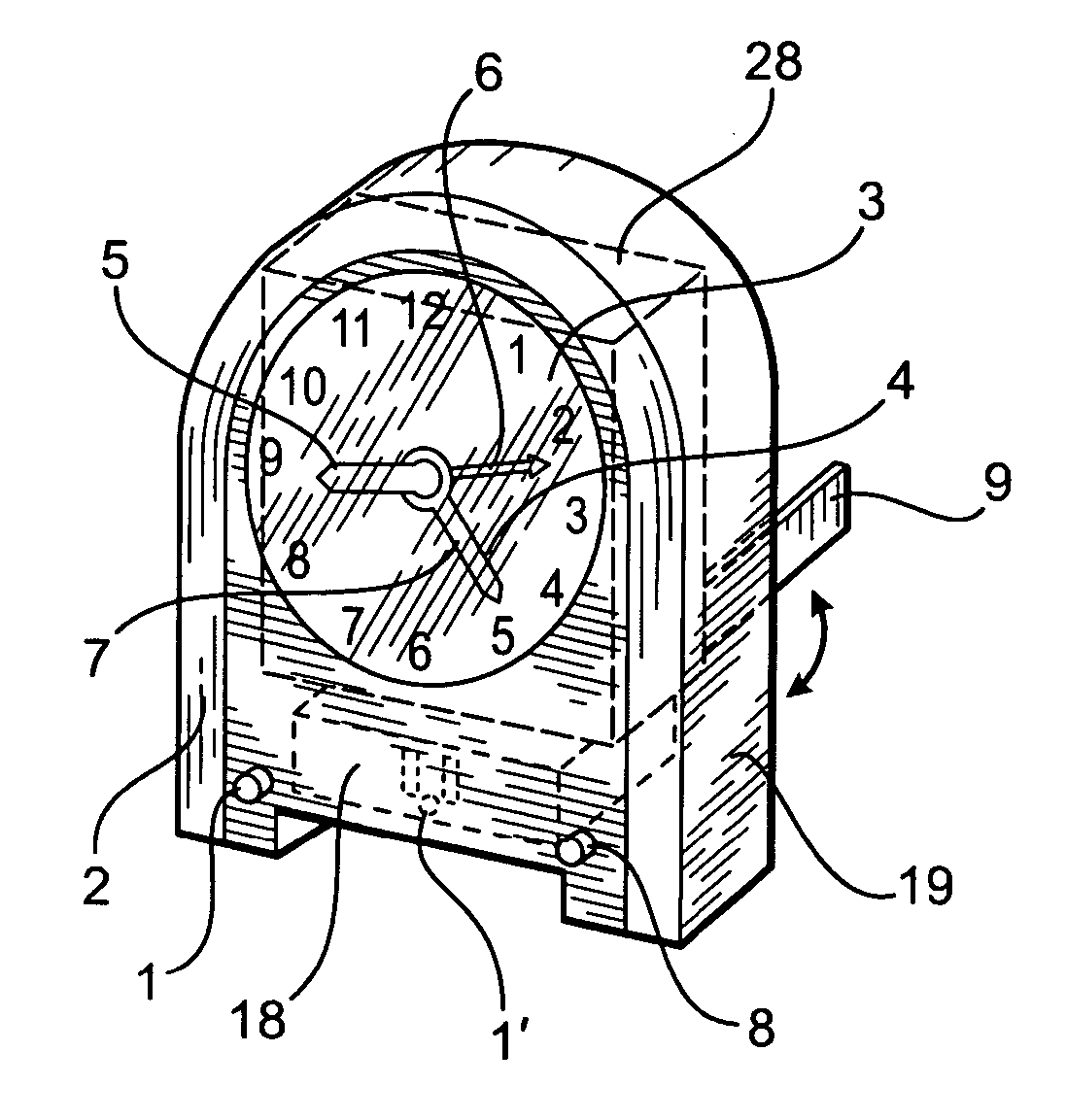
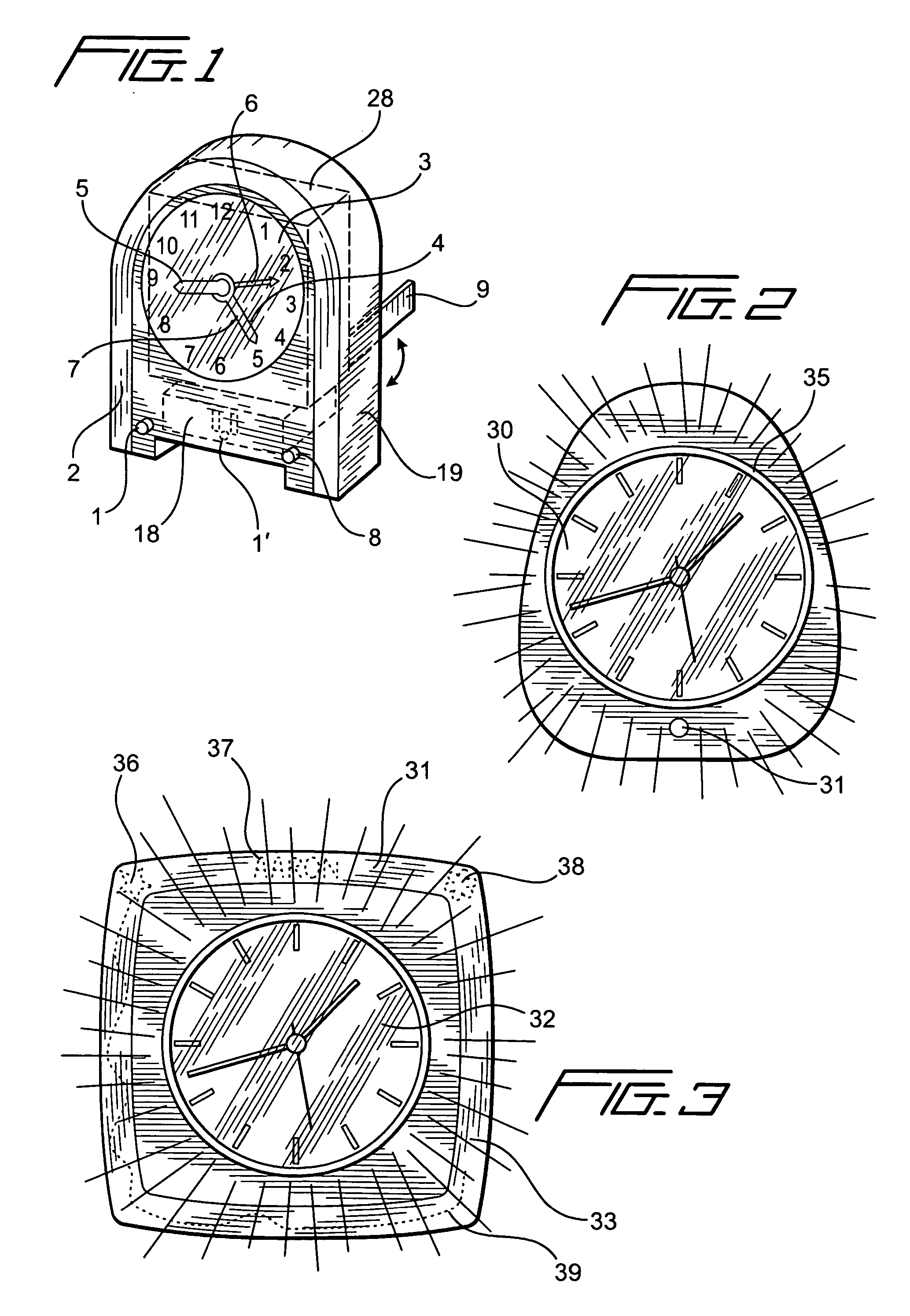
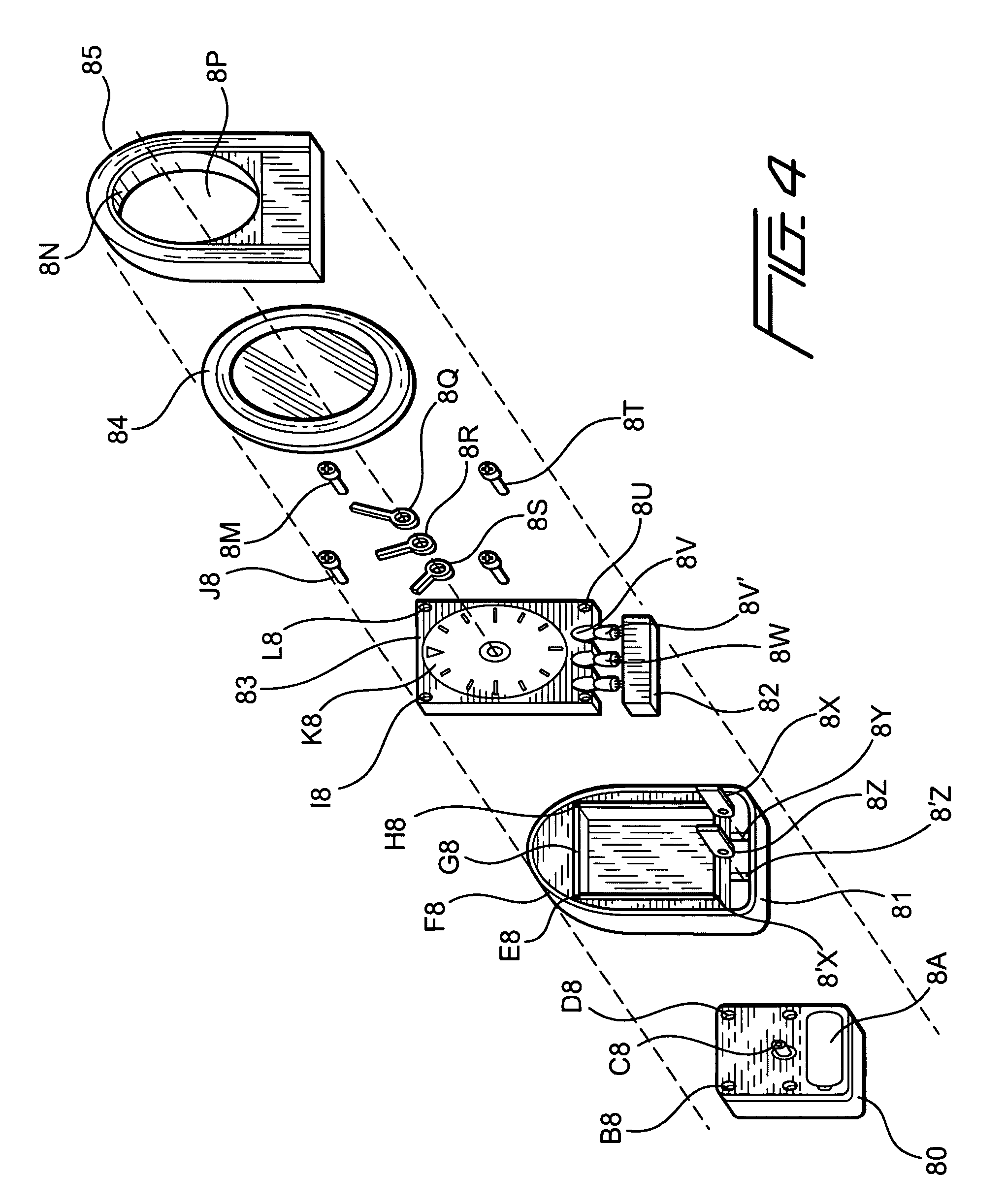
Time piece with LED light means
A time piece with LED light means adapted a simple light-medium body with very rough finish to allow the LED(s) pass though the input-end(s) and make majority light beams travel within the body to get very even brightness on all surface of the said light medium to be seen by viewer. Incorporating with milky / frosted front sheet overlay the said light-medium surface can get perfect photometric effects. The movement for time display for analog time piece with build-in light-medium on top cover of the said movement will get super slim LED illumination for time piece. For night light application, the sealed-unit consist of prong-means and LED related circuit to seal within a safety standard plastic material and assembly with night light body can save a lot of cost and may use all kind materials to do rest part of night light to increase the big flexibility for eye-catching design. Same as LCD display time piece.
Owner:CHIEN TSENG LU
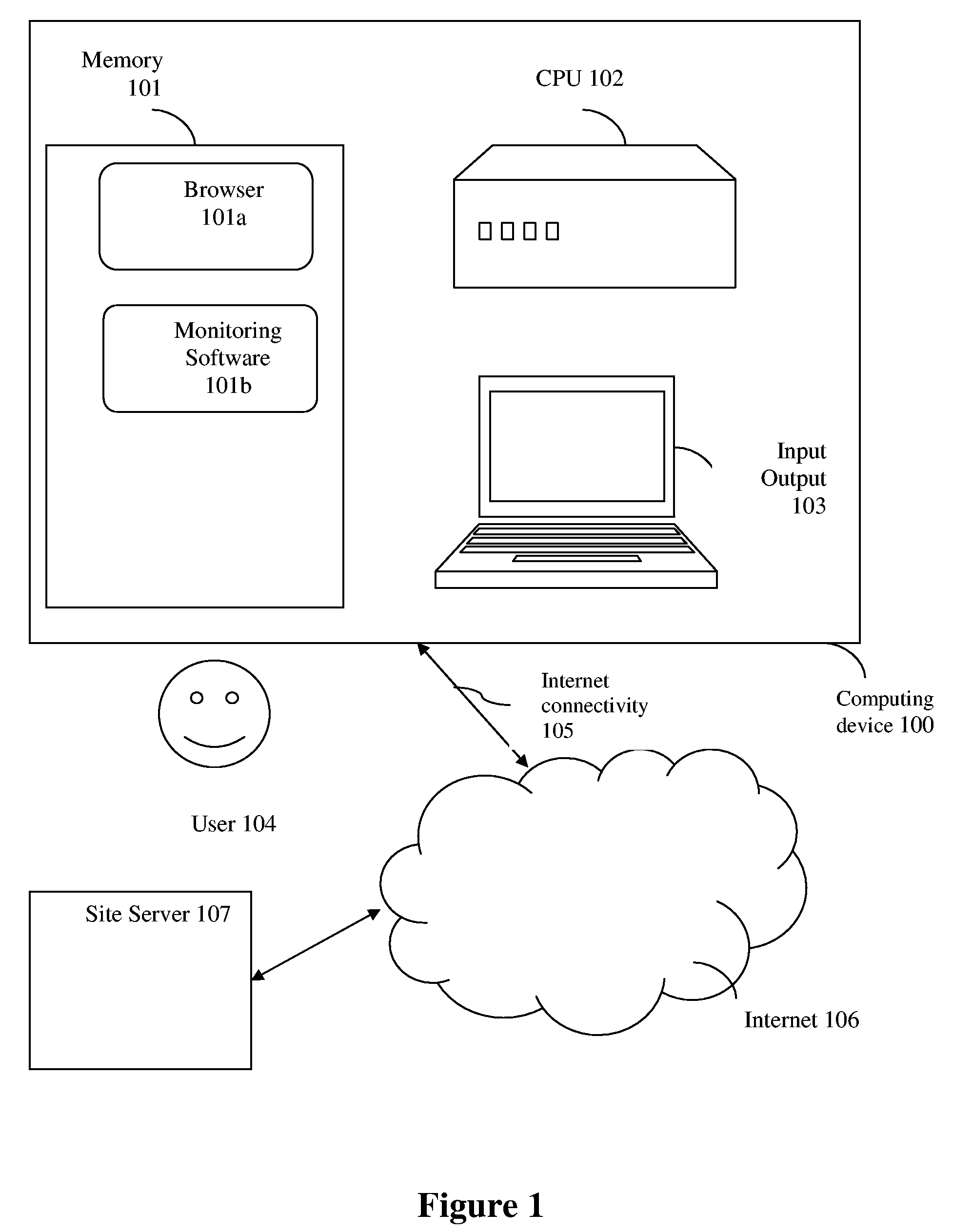
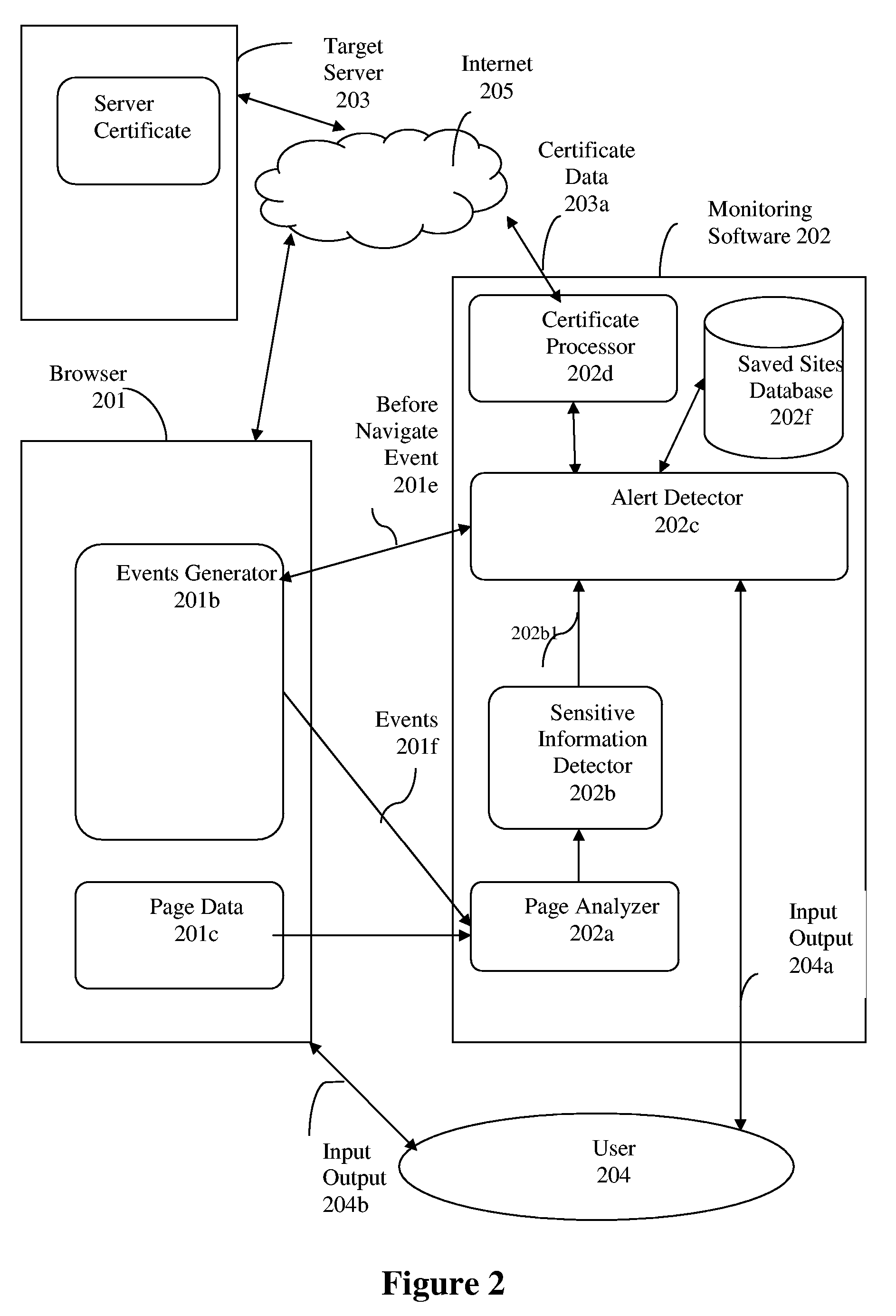
A system and methods for blocking submission of online forms.
InactiveUS20060070126A1Memory loss protectionError detection/correctionWeb siteUniform resource locator
A system and methods for blocking submission of online forms to suspicious web sites comprising detection of sensitive form fields before a form is submitted, analysis of URL and certificate target sites against security criteria to generate an alert codes and matching alert code with blocking criteria to generate a block submission message.
Owner:GRYNBERG AMIRAM
Farmland soil heavy metal pollution restoration method through coupling activating and passivating
ActiveCN104550208AReduce concentrationImprove repair efficiencyContaminated soil reclamationRestoration methodCoupling
The invention provides a farmland soil heavy metal pollution restoration method through coupling activating and passivating, belonging to the technical field of environmental technology. According to a technical scheme adopted by the invention, the farmland soil heavy metal pollution restoration method comprises the following steps: a step I, planting heavy metal hyper-accumulation plant, applying a heavy metal activator into the soil, collecting plant which is enriched with heavy metals; a step II, applying a heavy metal passivator into the soil, planting and harvesting crops with heavy metal content reaching the safety standard. By two different coupling technologies in the two government stages, on one hand, the concentration of heavy metals in the farmland soil is lowered with high efficiency, on the other hand, the farmland can be put into safety production as early as possible, so that the heavy metal pollution farmland soil restoration efficiency is improved generally, and the method can be applied to farmland soil with large-area heavy metal pollution.
Owner:中环循环境技术有限责任公司
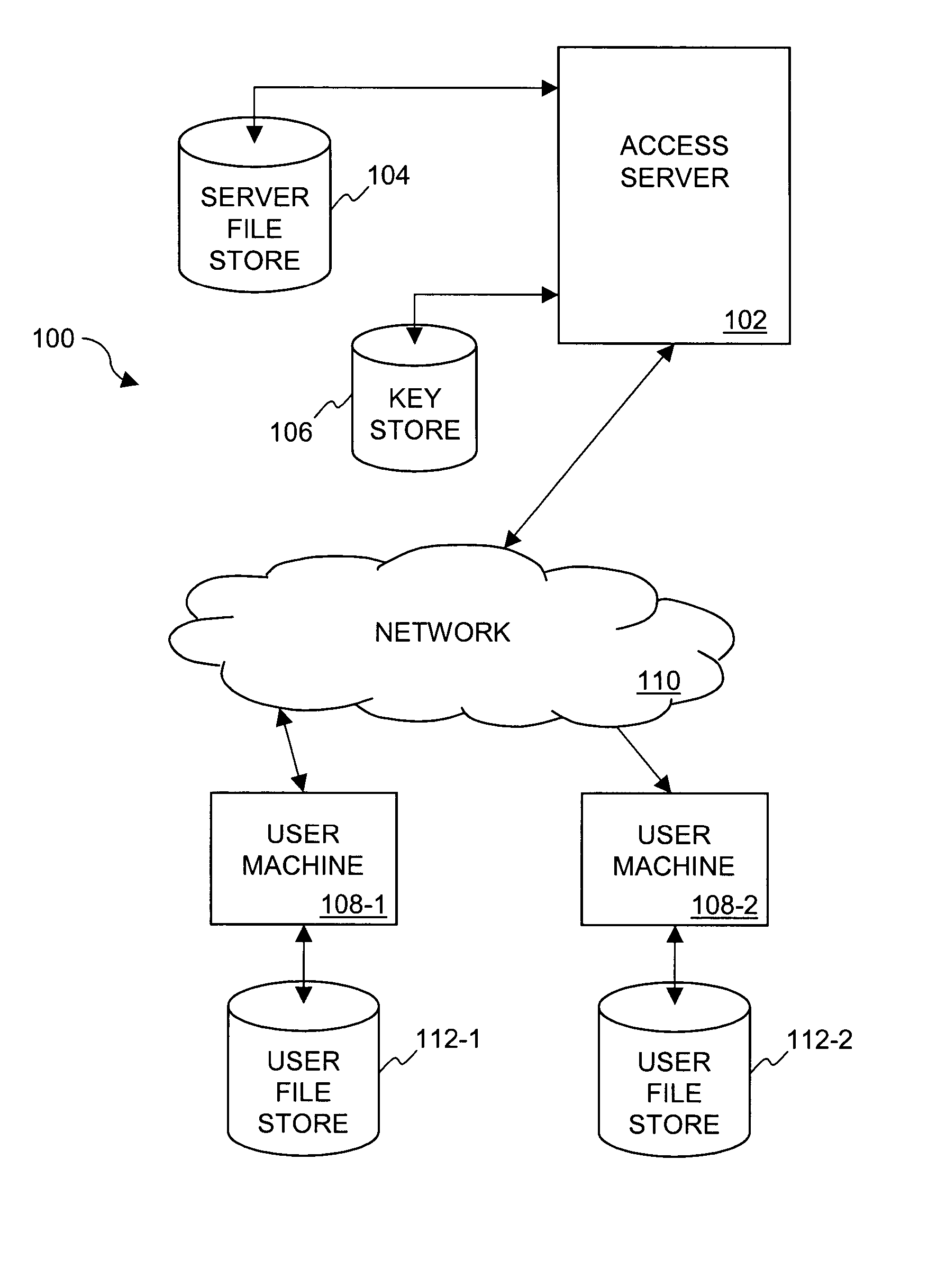
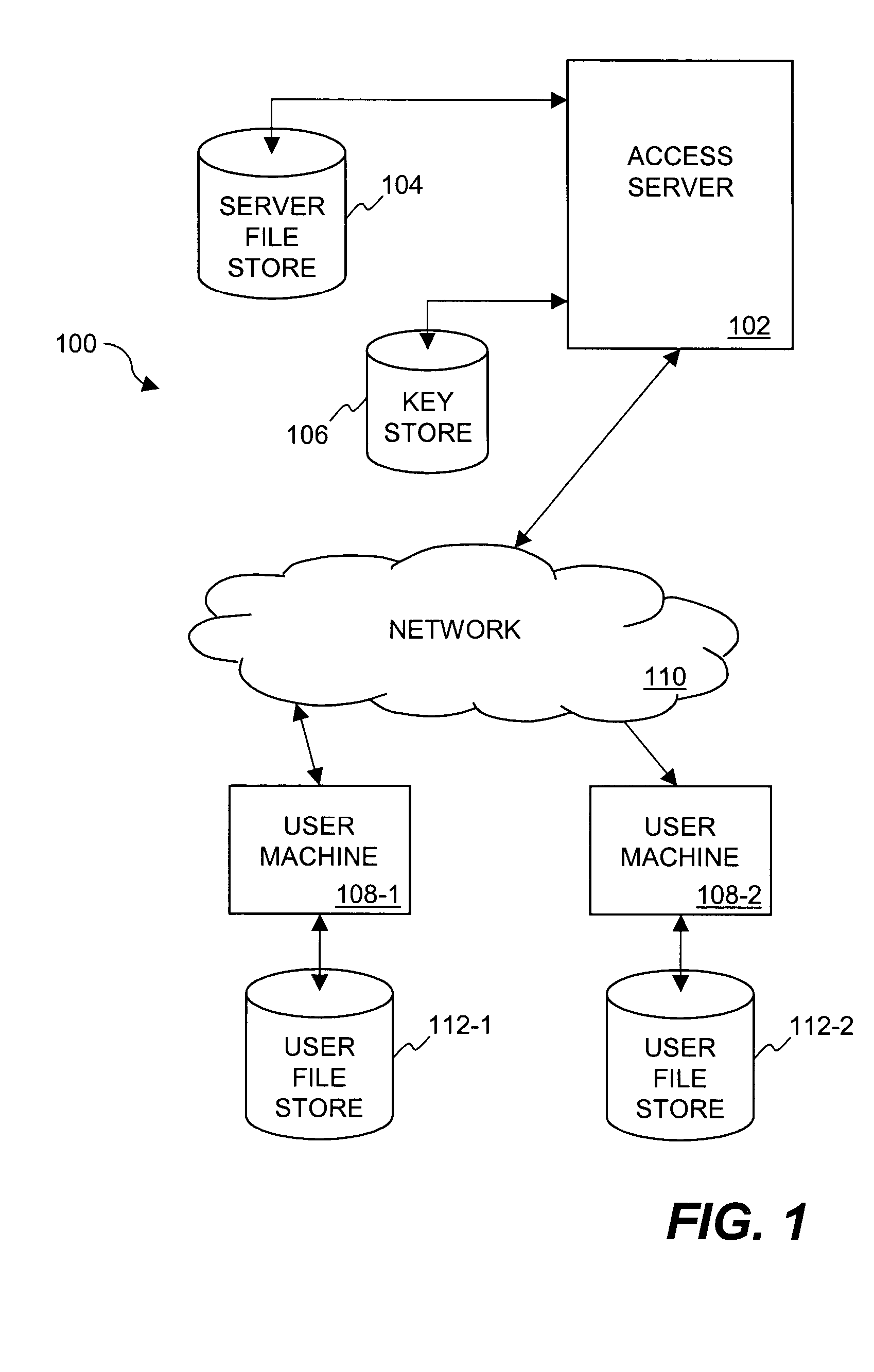
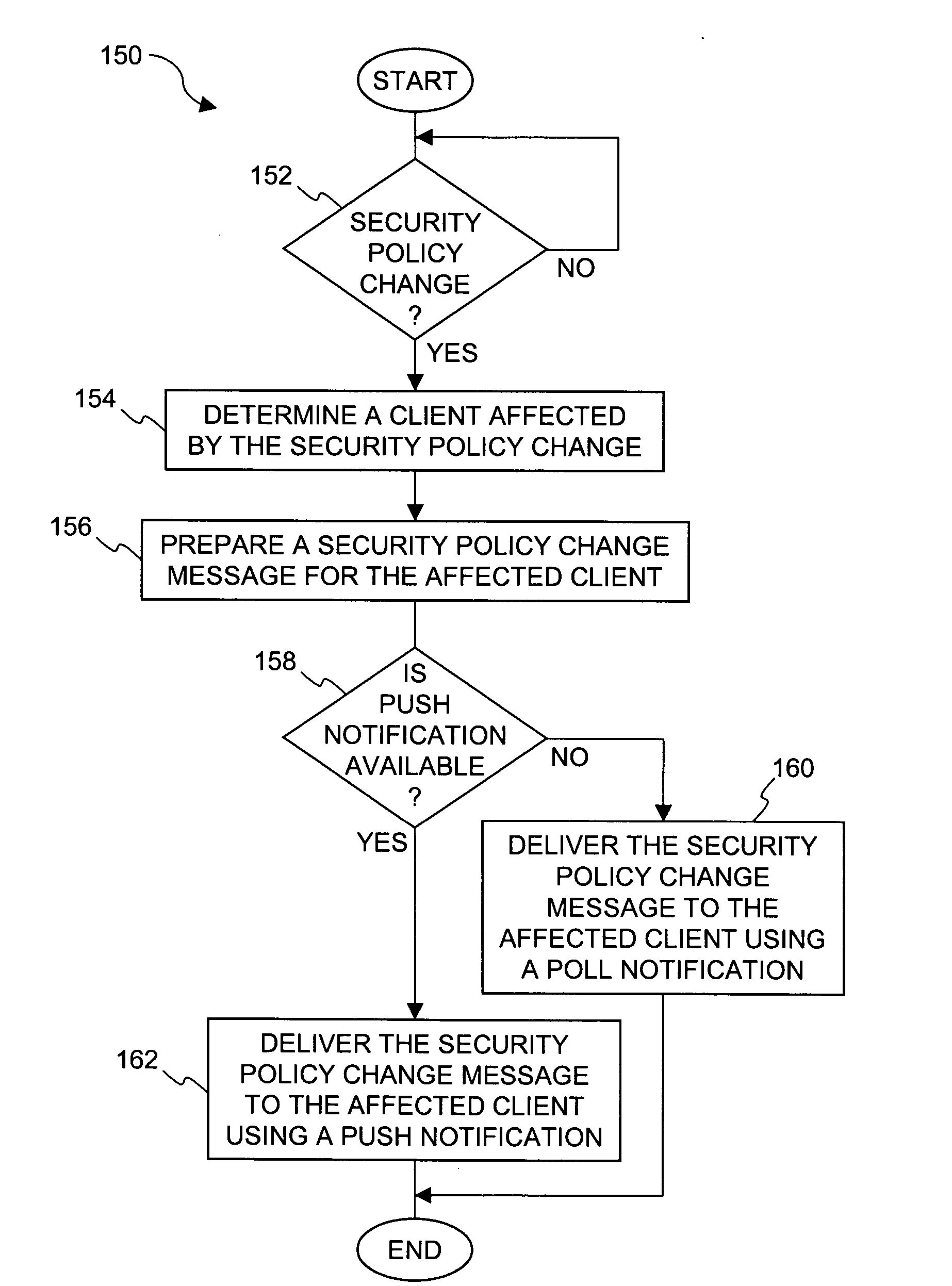
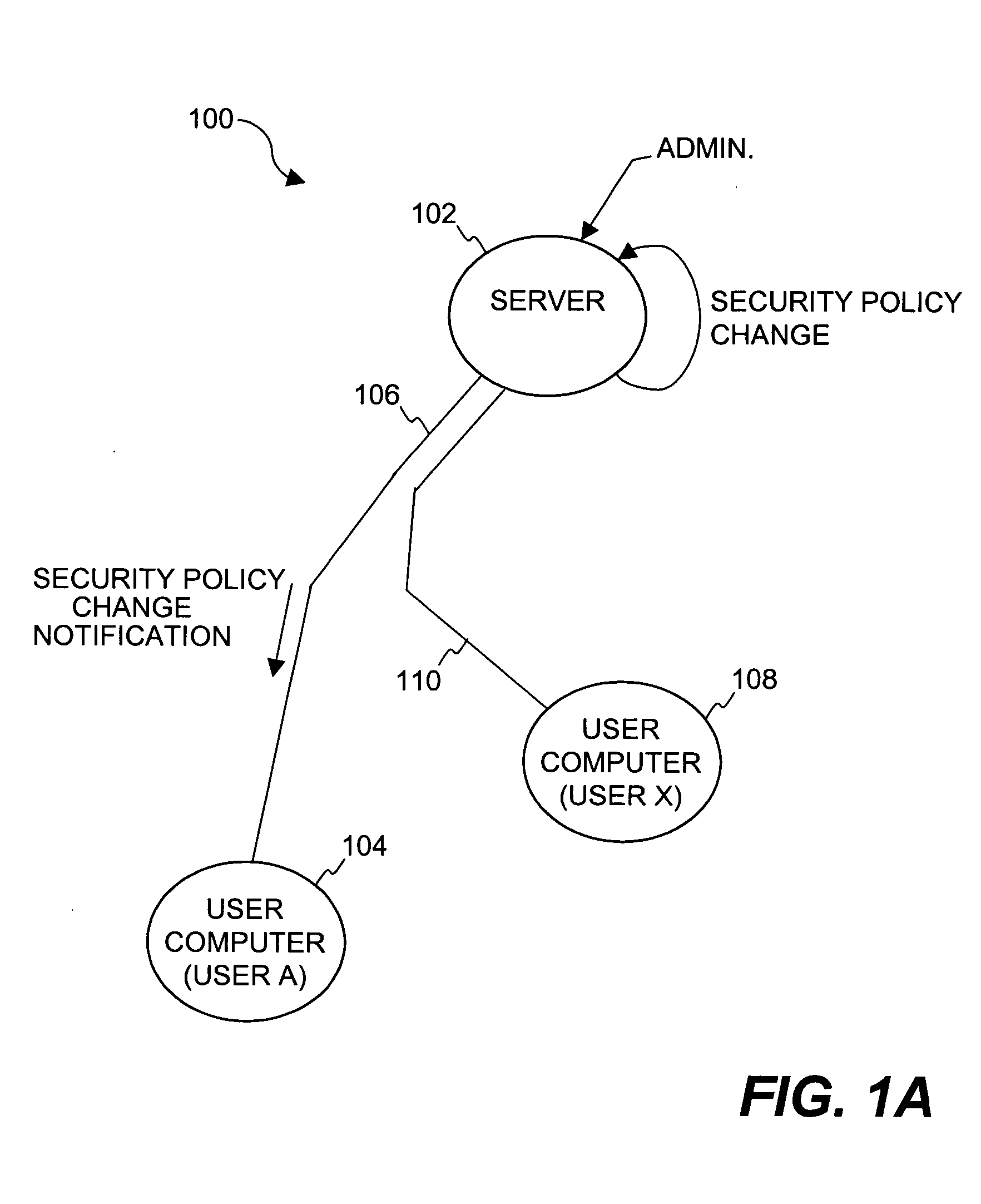
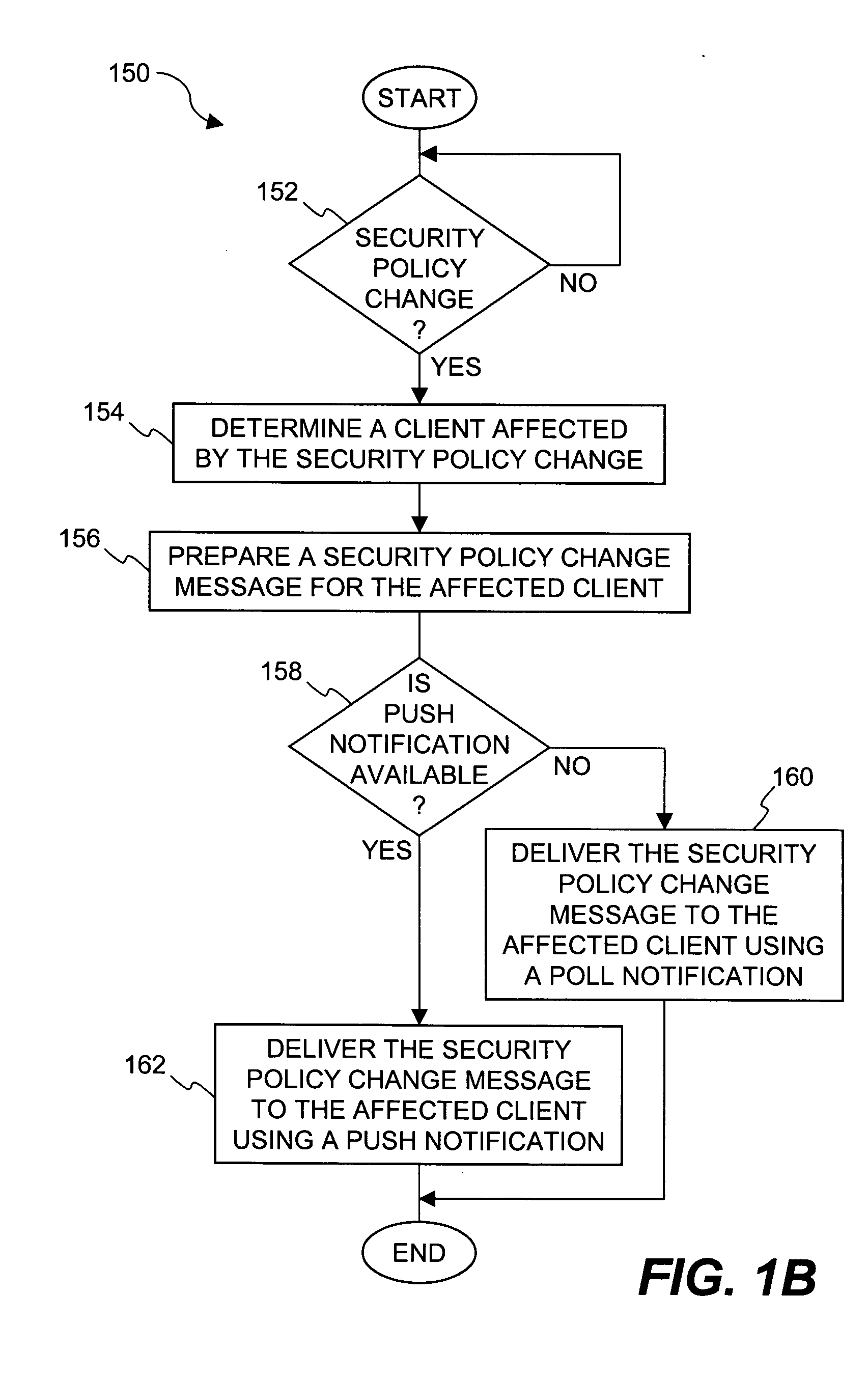
Method and system for distribution of notifications in file security systems
Improved approaches for providing notifications in a distributed file security system are disclosed. The file security system includes a file security server that manages file security for a plurality of clients. When security criteria (e.g., security policies or rules) change at the file security system, typically the clients need to be notified so that they operate in accordance with the correct security criteria. The security criteria impacts whether a particular client (or its user) are able to access certain files being protected by the file security system. A client can be notified in different ways depending on network characteristics. In one embodiment, an appropriate way to perform notifications between the file security server and clients can be automatically determined, thus advantageously minimizing user impact and allowing the system to transparently adapt to different networks.
Owner:INTELLECTUAL VENTURES I LLC
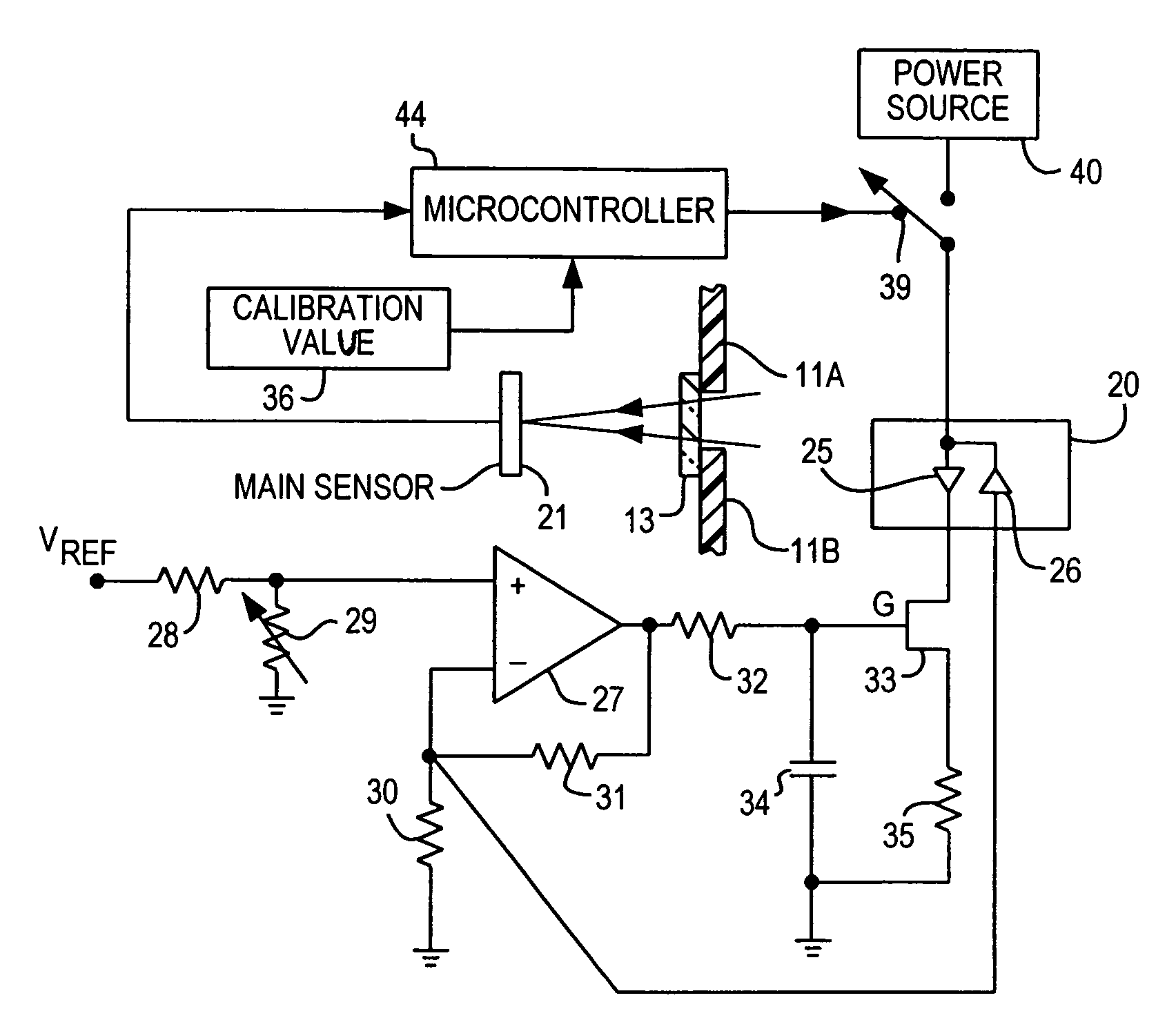
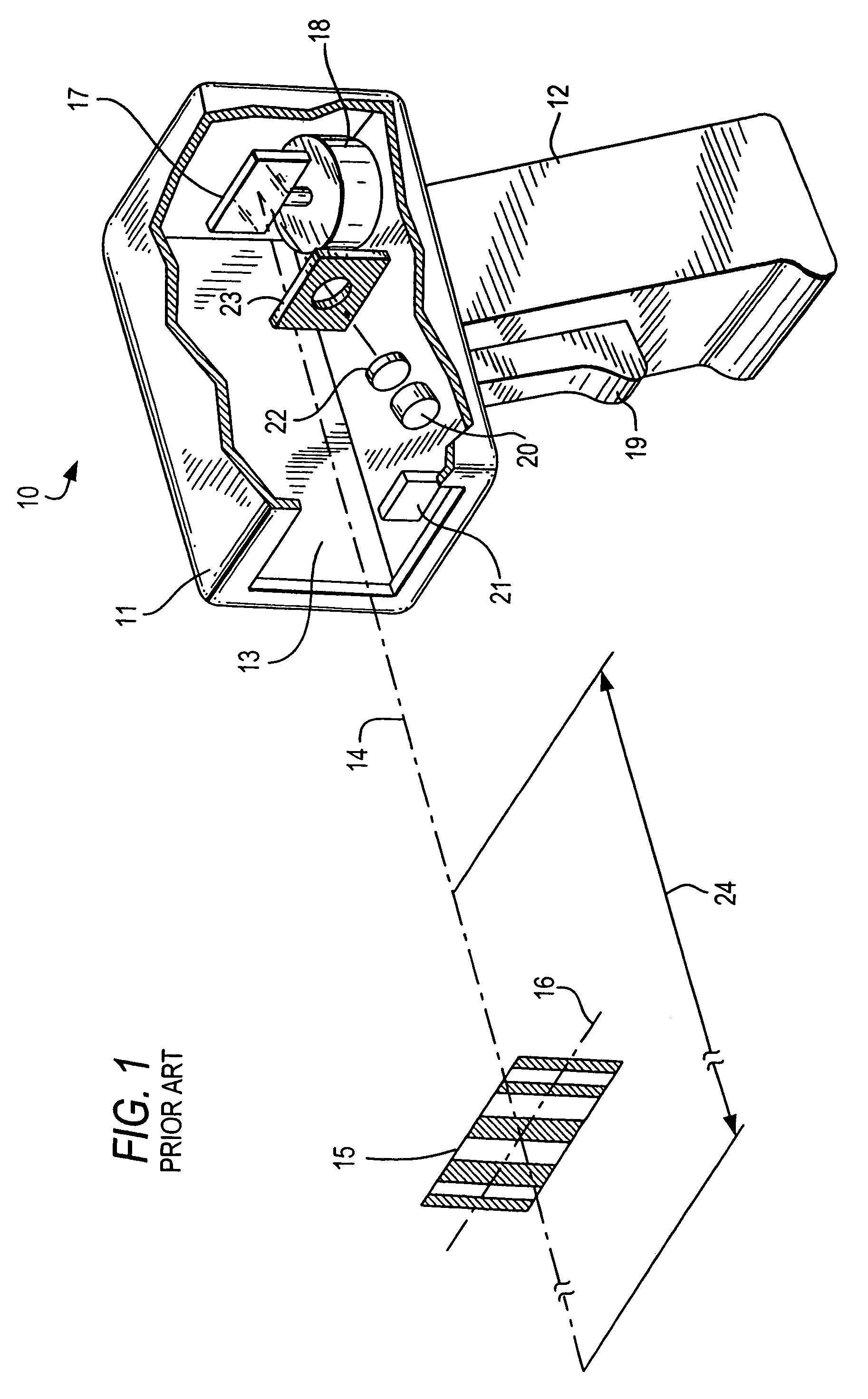
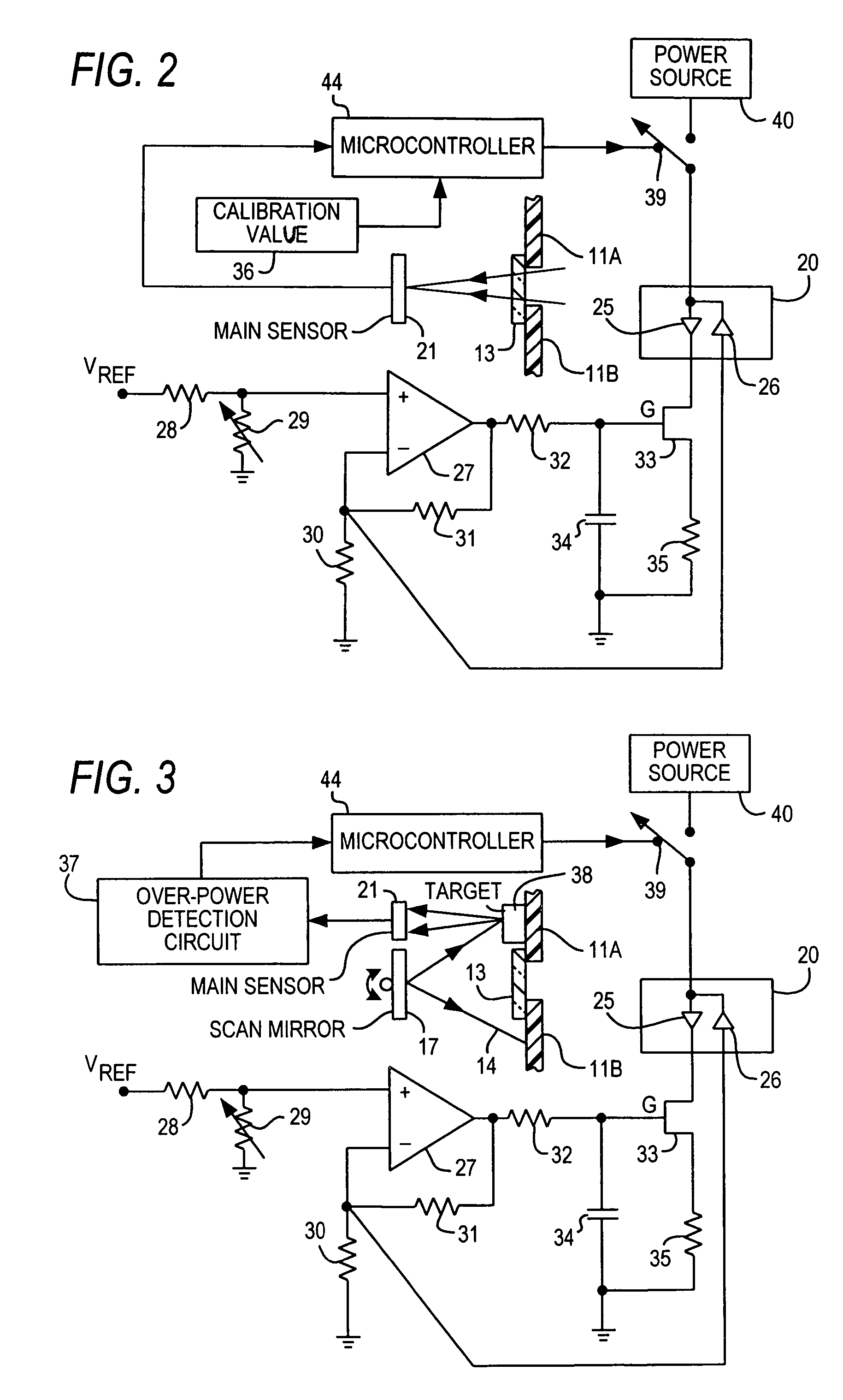
Laser power control arrangements in electro-optical readers
ActiveUS7255275B2Increase safety without adversely impacting on reader performanceSensing by electromagnetic radiationEngineeringSafety standards
Laser power control arrangements interrupt power to a laser used in electro-optical readers upon detection of an over-power condition not conforming to preestablished standards to meet prevalent safety standards.
Owner:SYMBOL TECH LLC
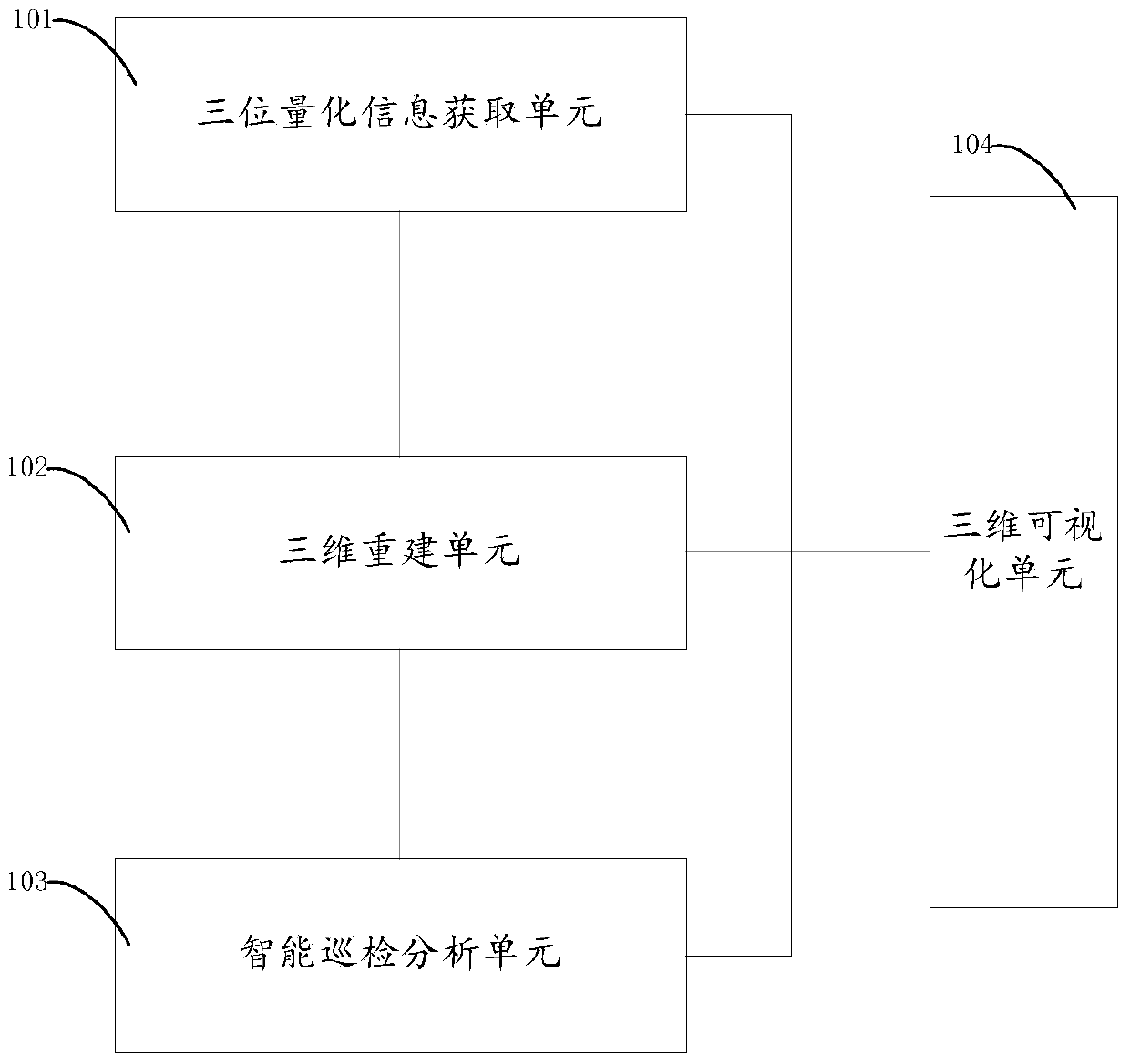
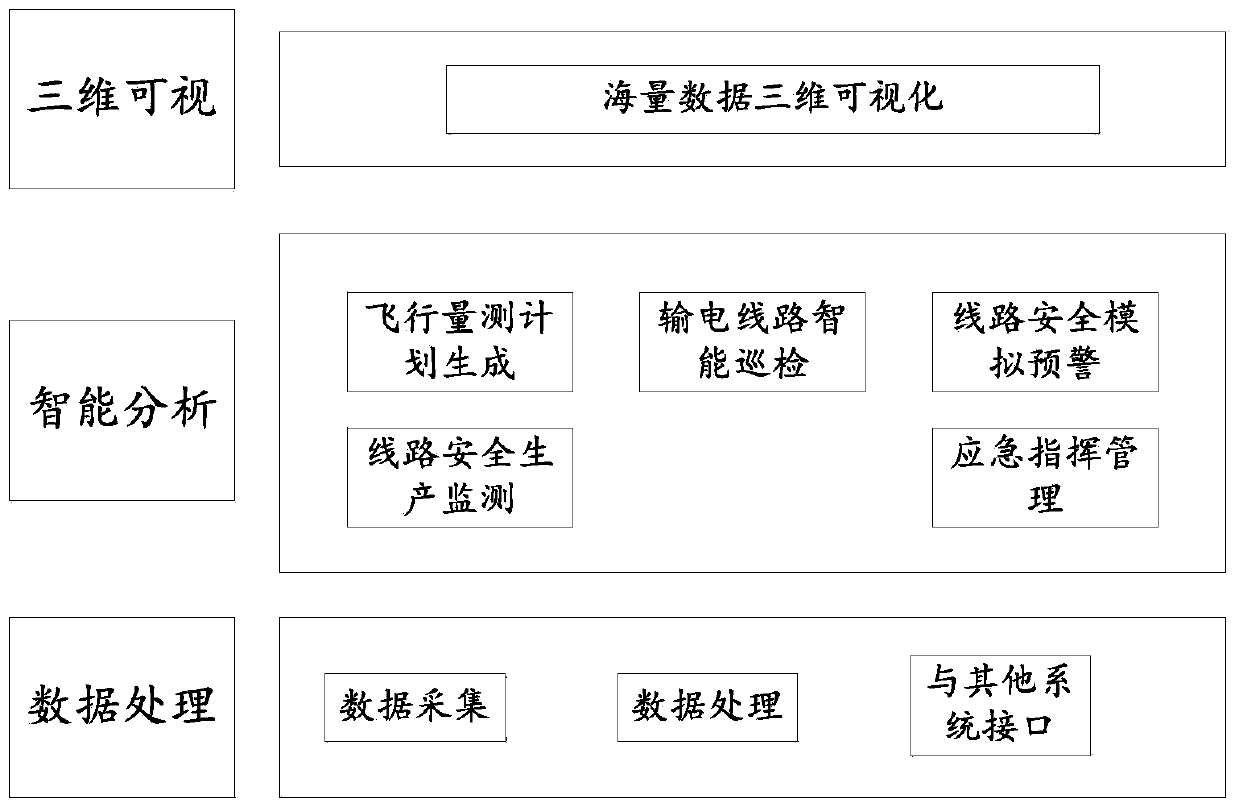
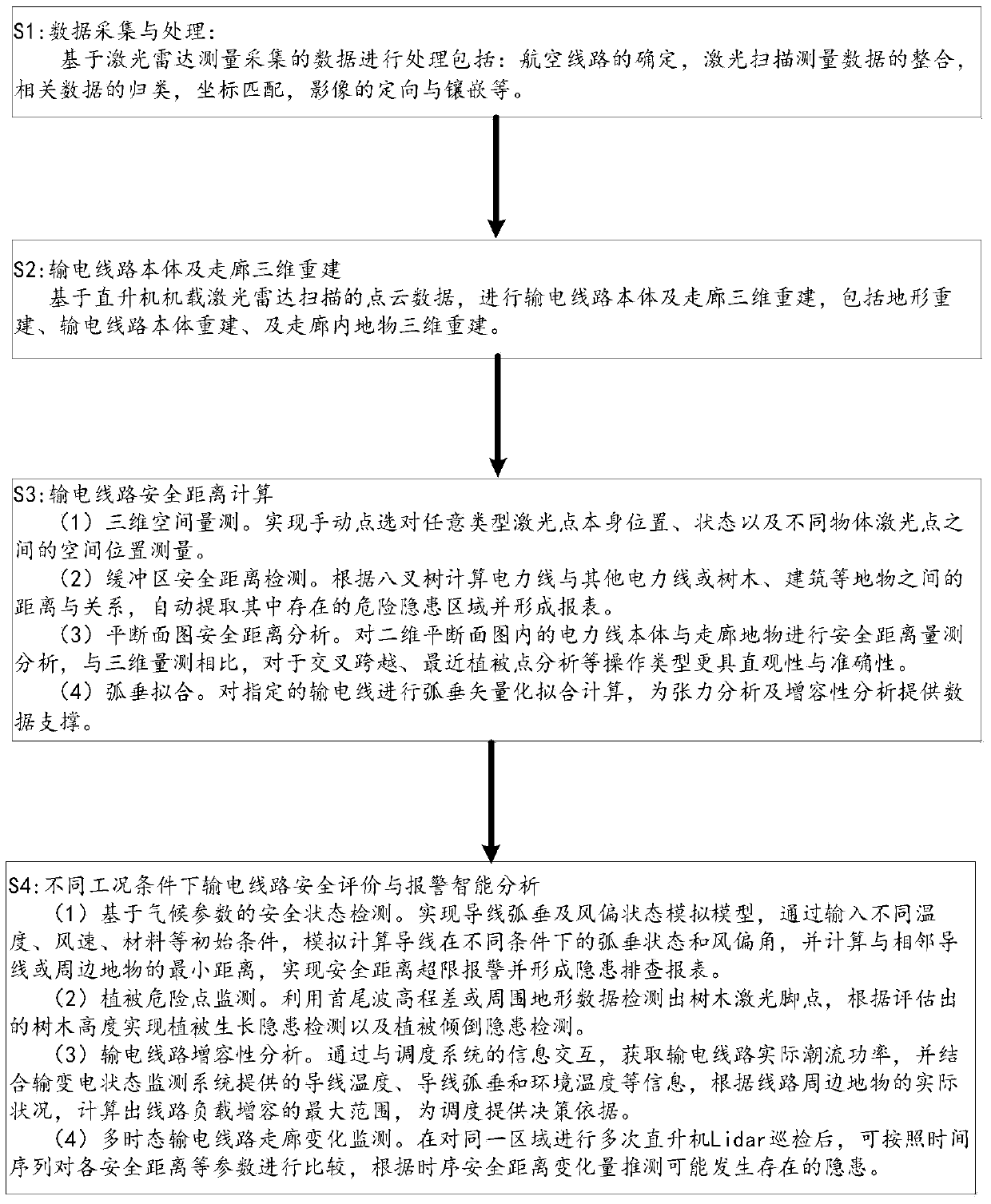
Power transmission line intelligent inspection system based on LiDAR
InactiveCN103779808ARealize automated detectionImprove management levelApparatus for overhead lines/cablesPoint cloudDistance analysis
The invention provides a power transmission line intelligent inspection system based on LiDAR and further provides a power transmission line intelligent inspection method based on LiDAR. The power transmission line intelligent inspection system comprises a three-dimensional quantifying information acquiring unit, a three-dimensional rebuilding unit and an intelligent inspection analysis unit. The three-dimensional quantifying information acquiring unit is suitable for acquiring power transmission equipment actual space three-dimensional quantifying information and power transmission line peripheral environment ground feature three-dimensional quantifying information, namely, point cloud data provided by LiDAR; the three-dimensional rebuilding unit is suitable for three-dimensional rebuilding of a power transmission line body and a corridor based on power transmission equipment actual space three-dimensional quantifying distribution information and power transmission line peripheral environment ground feature actual three-dimensional quantifying information; the intelligent inspection analysis unit is suitable for carrying out safety distance detection based on three-dimensional rebuilding results, carrying out safety distance analysis according to safety distance detection results and power transmission line safety standards and pointing out power transmission lines not catering to the safety standards or giving an alarm about the power transmission lines not catering to the safety standards. By means of the power transmission line intelligent inspection system and the power transmission line intelligent inspection method, requirements for line inspection data and function digitalization, standardization and visualization are achieved.
Owner:STATE GRID CORP OF CHINA +1
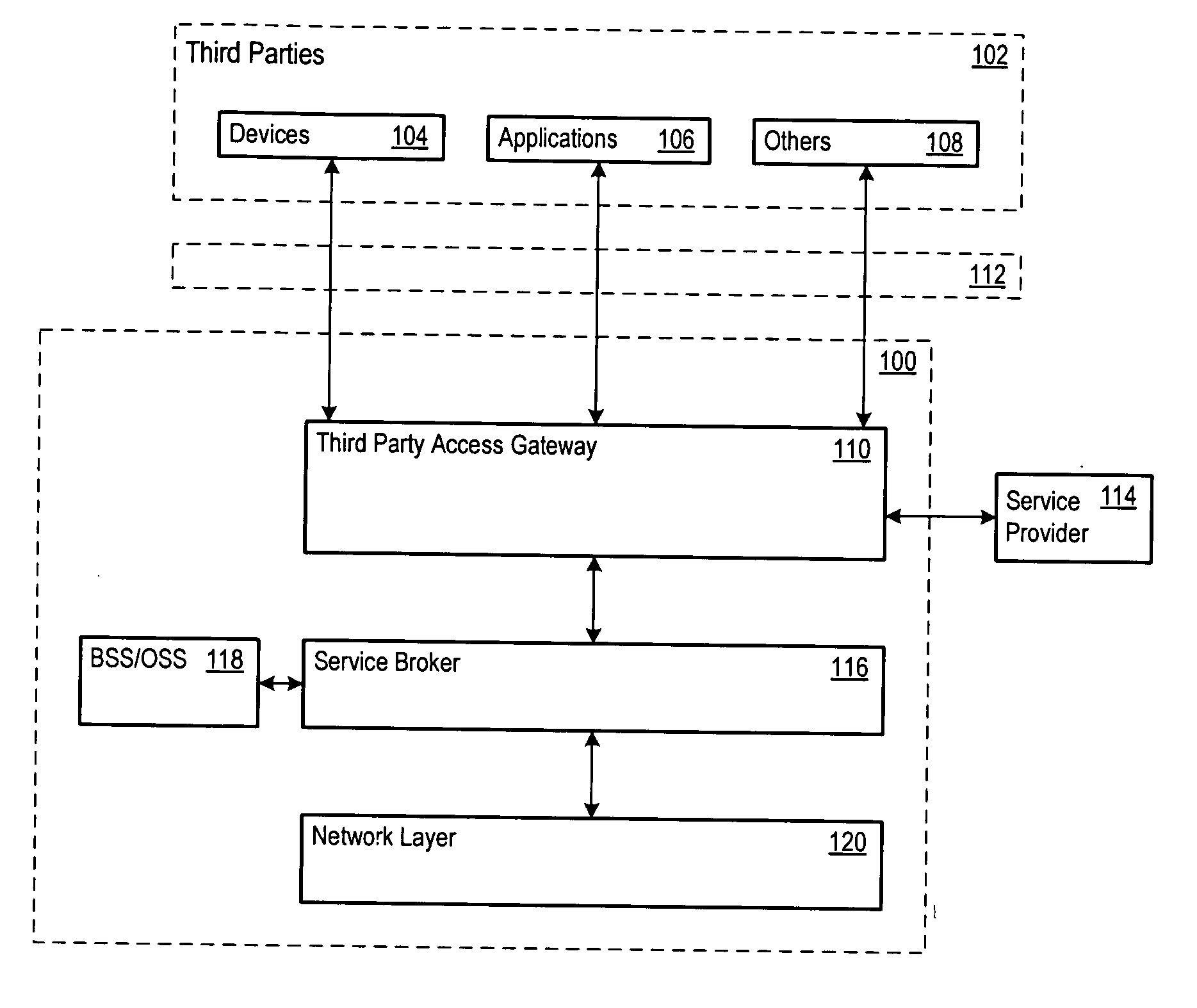
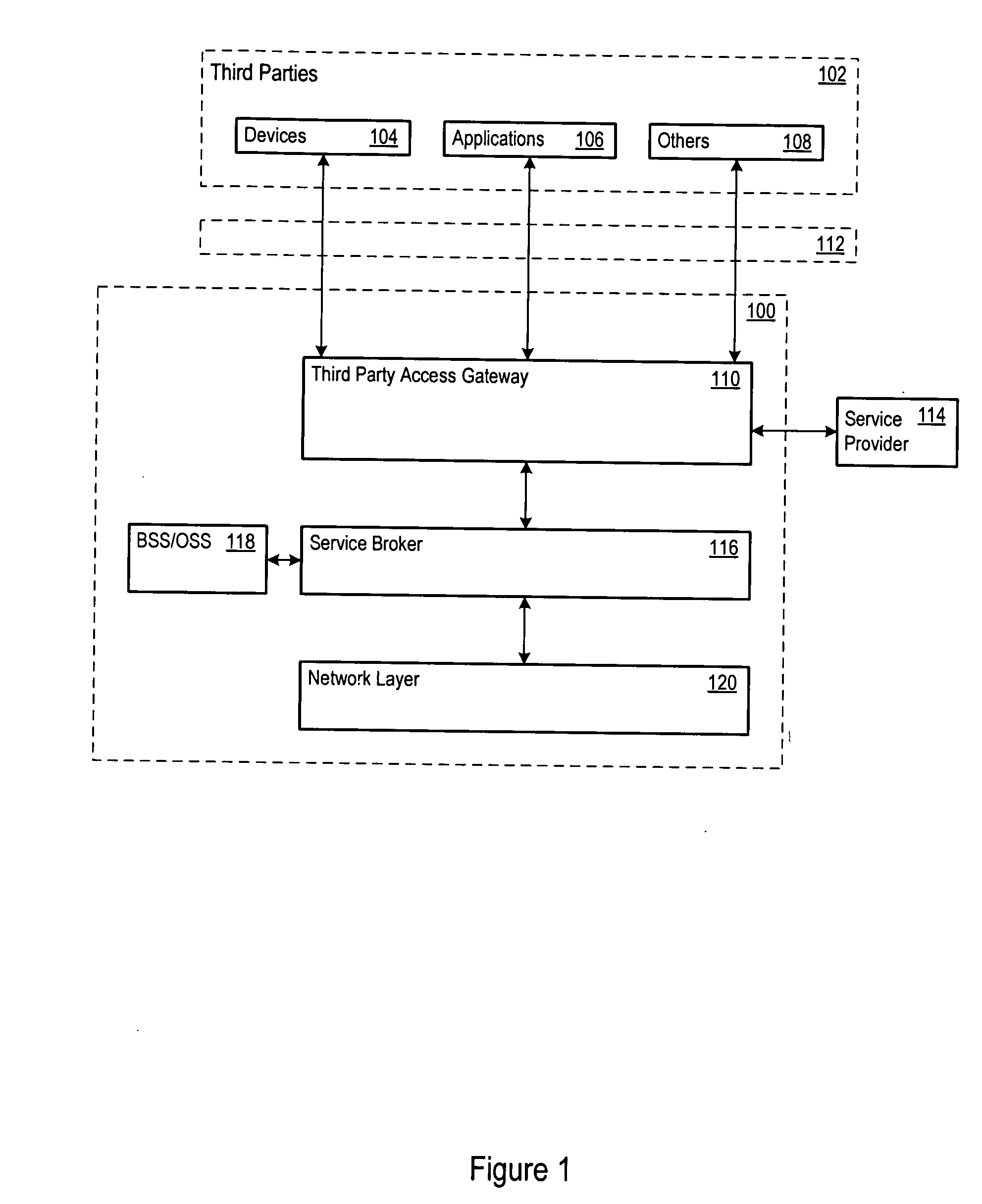
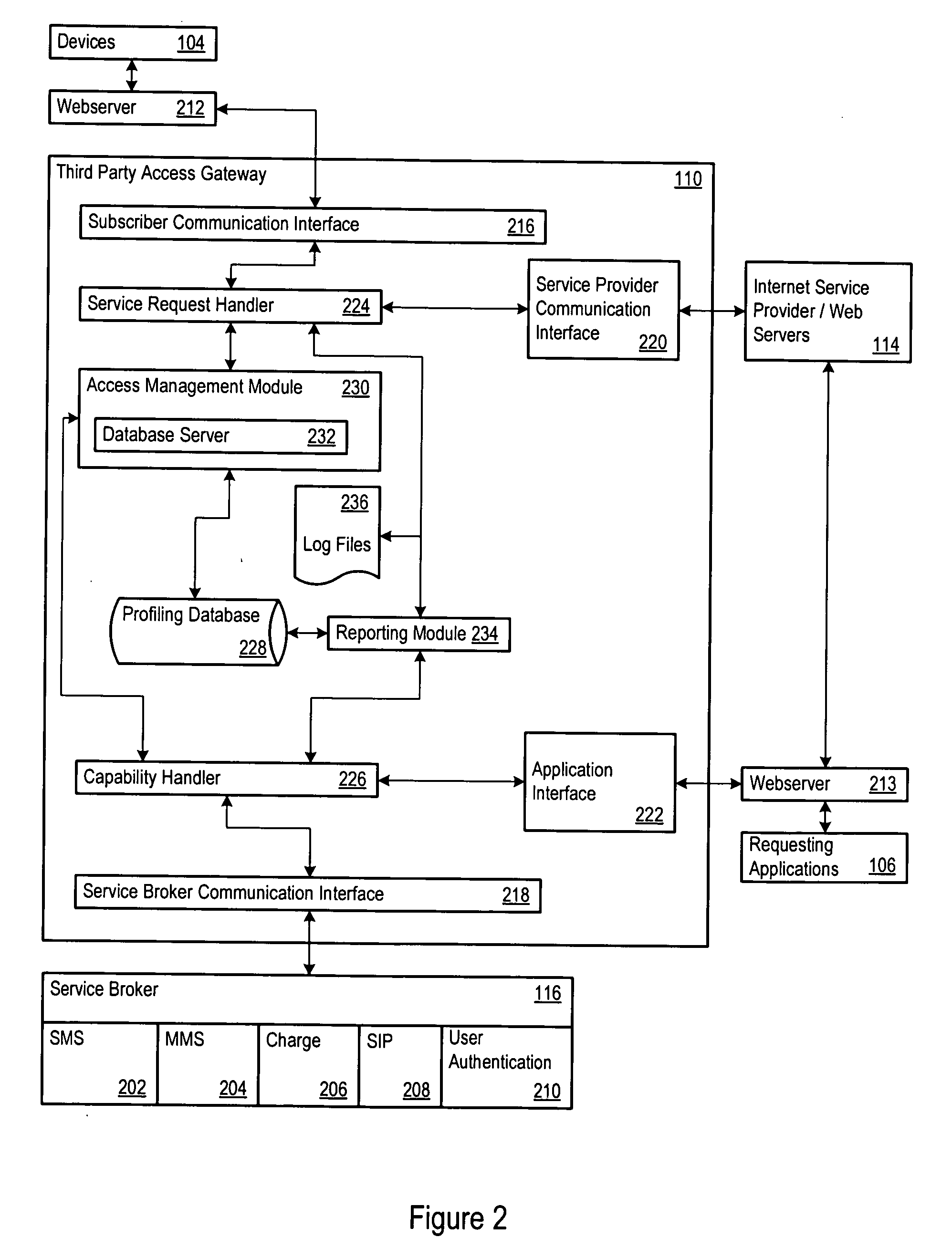
Authentication and authorization architecture for an access gateway
A telecommunications architecture exposes telecommunications services to third parties through a secure access gateway. The third parties may be other telecommunications service providers who employ the services to support their own products and services. The access gateway provides a secure, standardized, and controlled access platform for the exposed services, and addresses the technical problems associated with such access. In addition to providing technical solutions for efficient and secure access to exposed services, the architecture also provides an additional revenue channel for existing telecommunication service providers.
Owner:ACCENTURE GLOBAL SERVICES LTD
Laminate body and display device using the laminated body
InactiveUS20030176124A1Reduce deteriorationWeak elasticityCathode ray tubes/electron beam tubesMagnetic/electric field screeningDisplay deviceYoung's modulus
A laminate which can easily attain safety standards such as impact resistance, while cost reduction is aimed for, for example, when the laminate is provided on a display viewing surface, and a display apparatus using this laminate are provided. By using a filter for a display having a specified parameter and a specified thickness, the impact resistance is enhanced. By using the filter for the display containing a transparent adhesive layer having a specified Young's modulus and a specified thickness, the impact resistance is enhanced. By using the filter for the display containing a transparent resin layer having a specified Young's modulus and a specified thickness, the impact resistance is enhanced. By using the filter for the display containing an impact absorption layer having a specified penetration and a specified thickness, the impact resistance is enhanced.
Owner:MITSUI CHEM INC
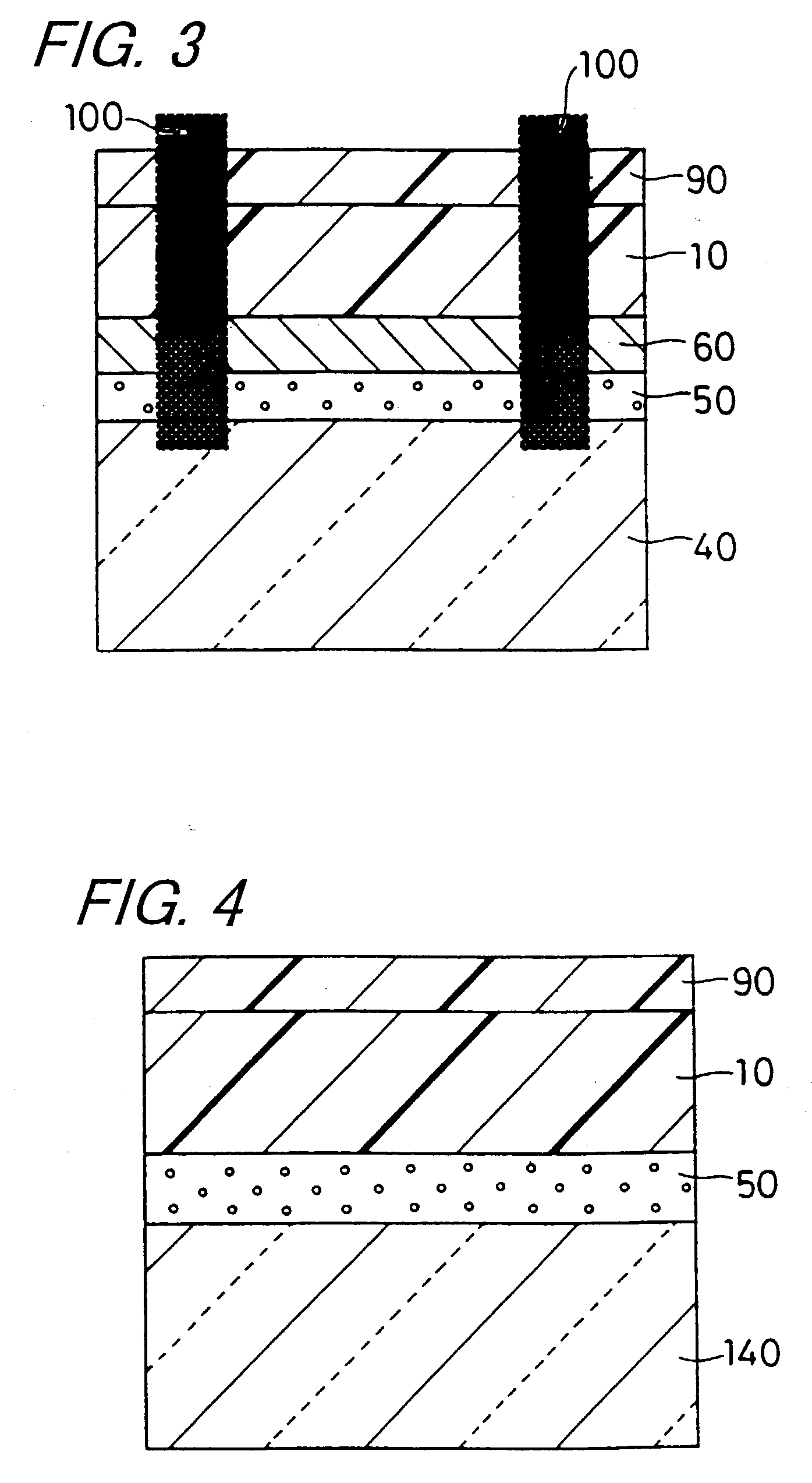
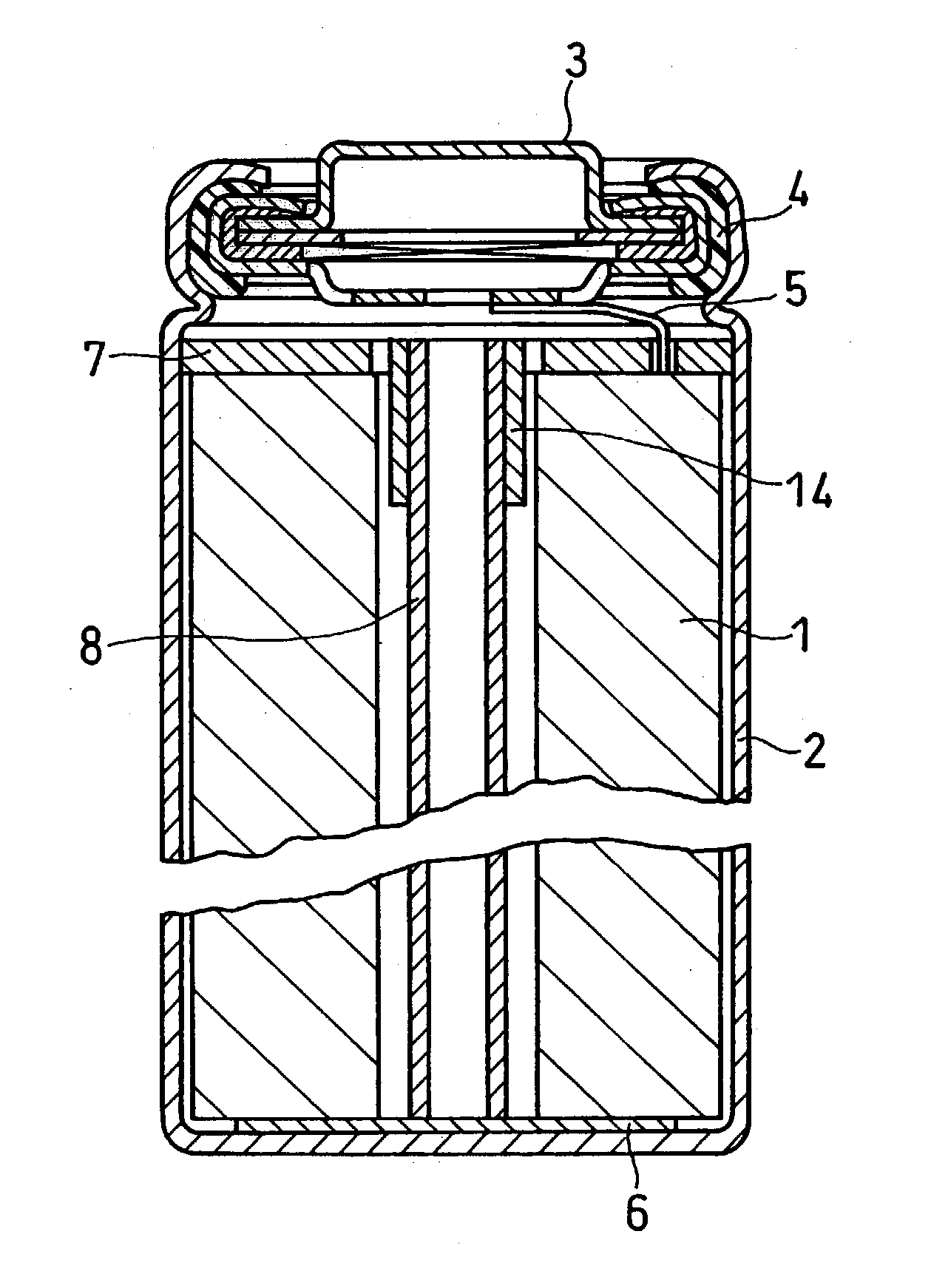
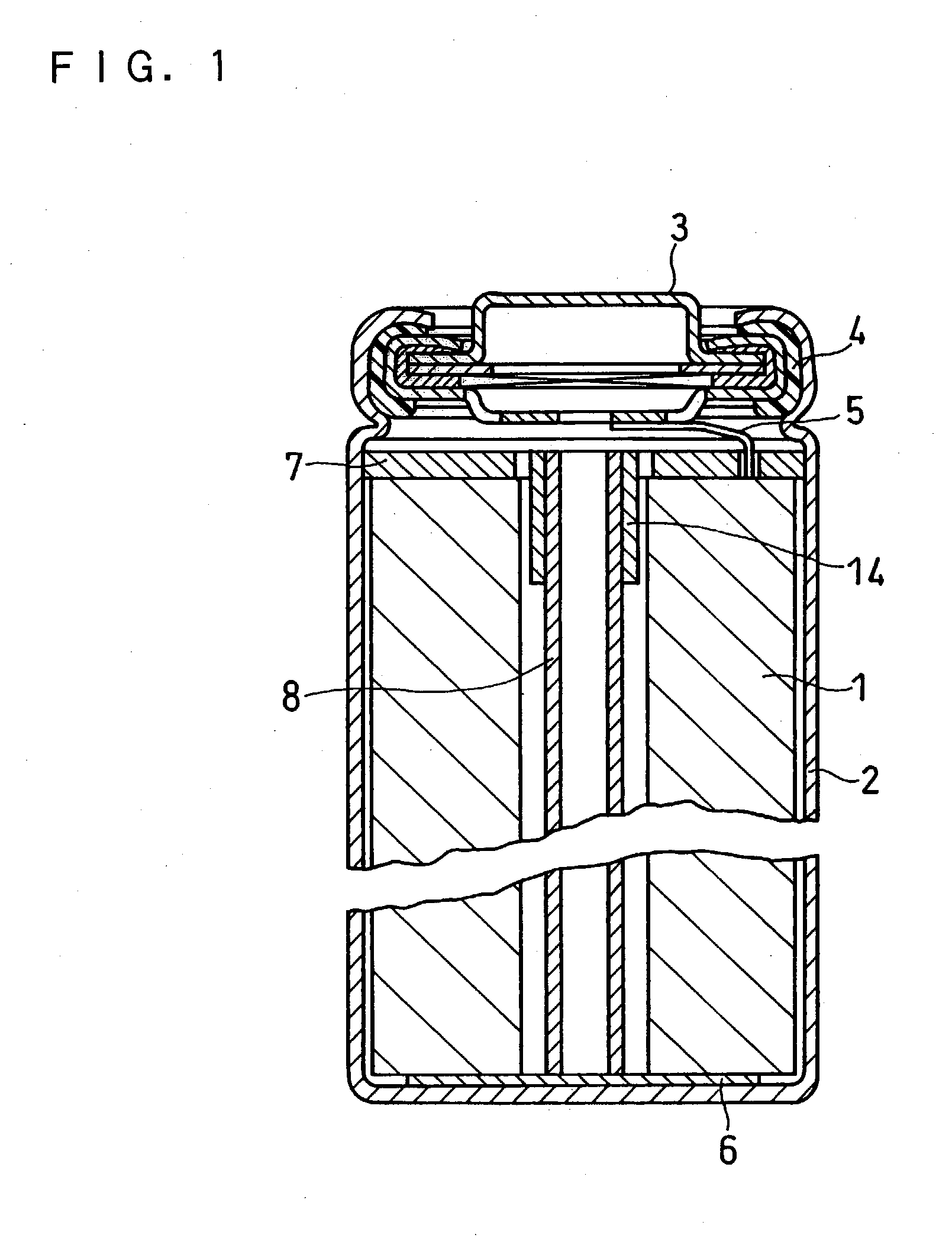
Cylindrical lithium ion secondary battery and fabrication method thereof
InactiveUS20030198863A1Non-aqueous electrolyte accumulatorsFinal product manufactureLithiumBand shape
A lithium ion secondary battery is so designed as to facilitate the insertion of the top insulator plate and to secure the fixation of the electrode group. This structure can reduce the probability of the electrode group moving around in the battery case to be damaged when the battery is dropped or shocked, thereby maintaining high safety standards even when a high pressure is applied from outside the battery. In a lithium ion secondary battery provided with a safety valve and composed of an electrode group which consists of a band-shaped positive electrode plate and a band-shaped negative electrode plate wound together with a separator disposed therebetween and which is housed in a cylindrical metal battery case with a bottom, together with a top insulator plate, the top insulator plate is designed to be elastic and is provided in its center with a through hole into which a center core member is press-fitted.
Owner:PANASONIC CORP
Proximity detection and communication mechanism and method
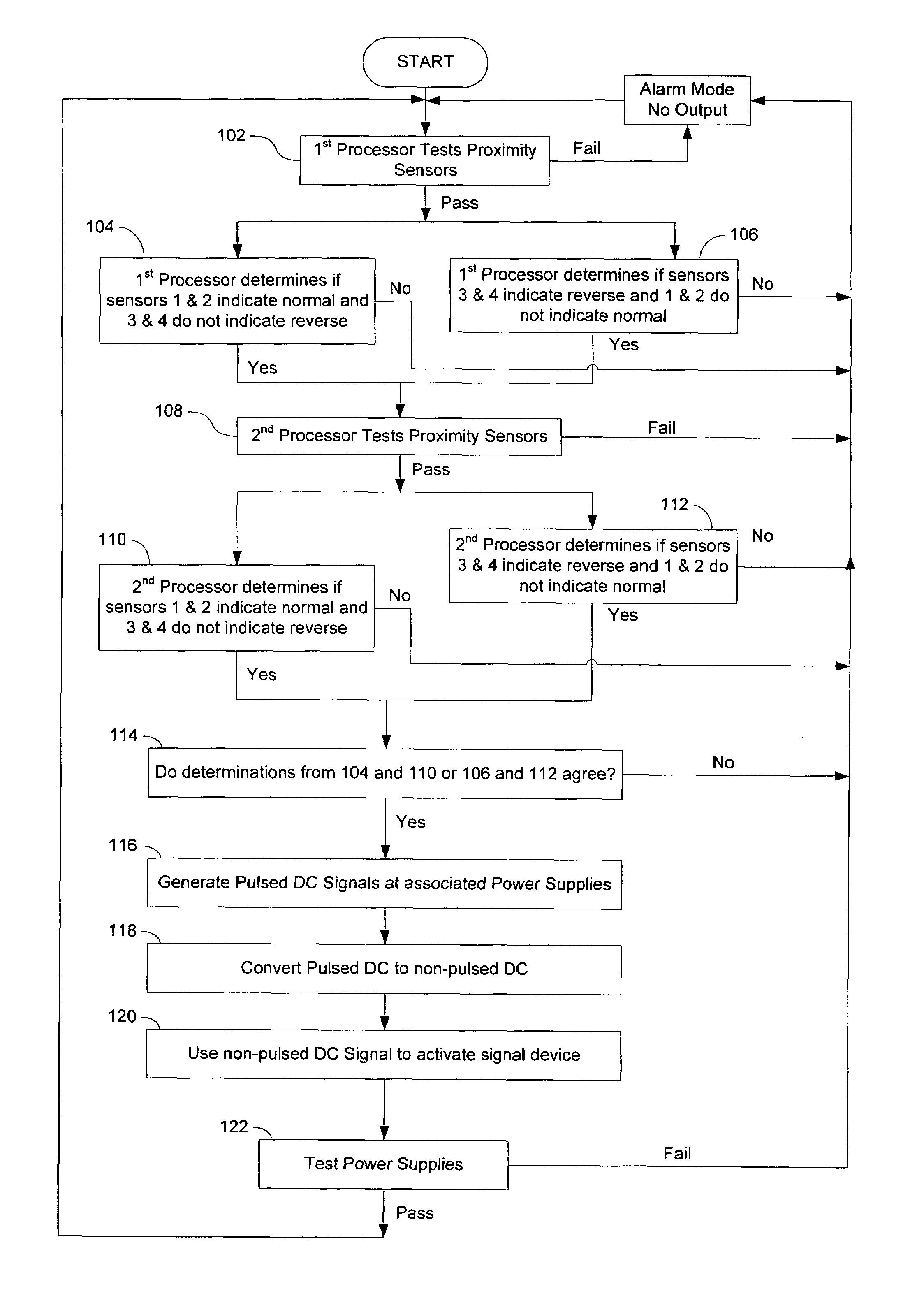
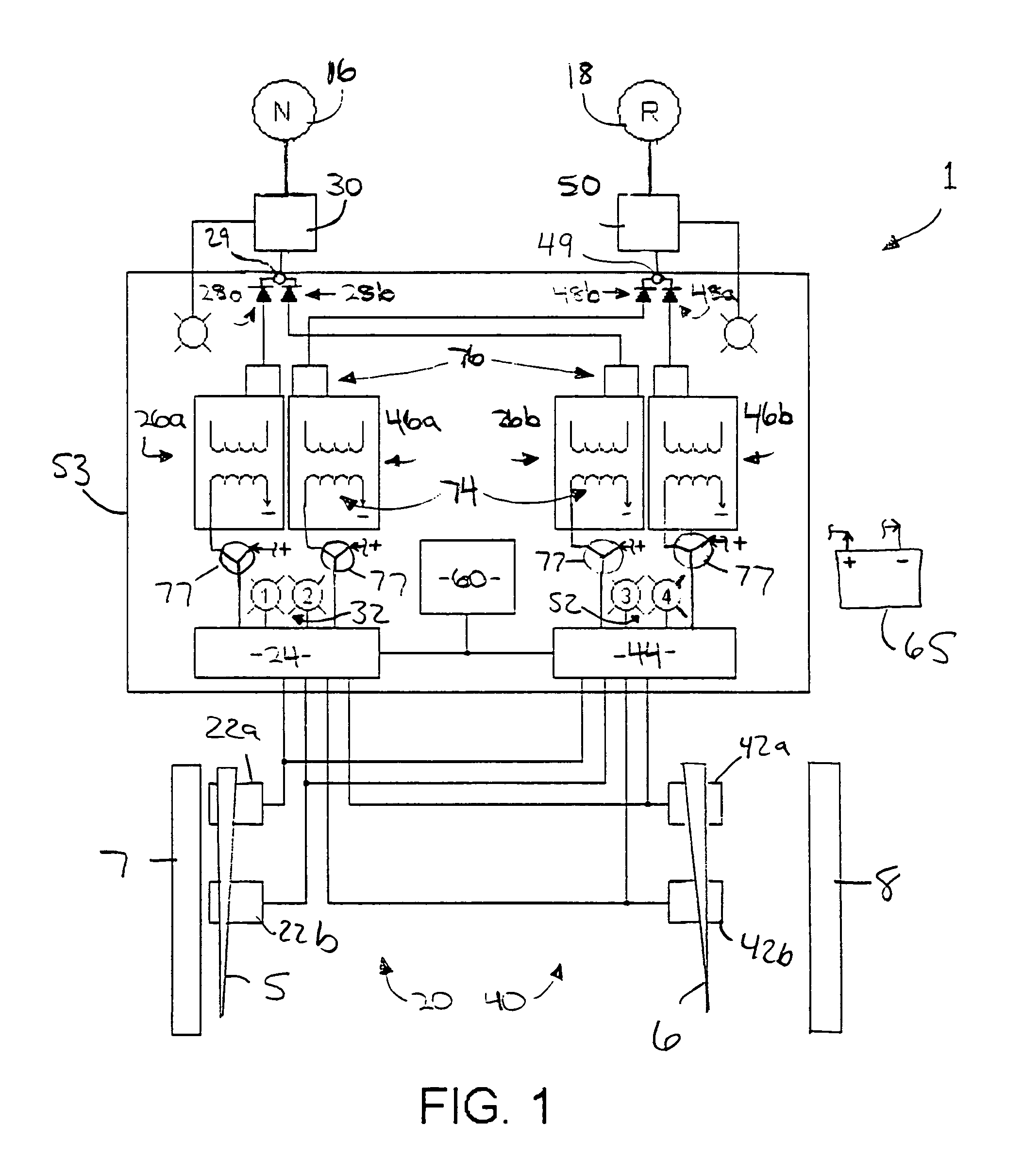
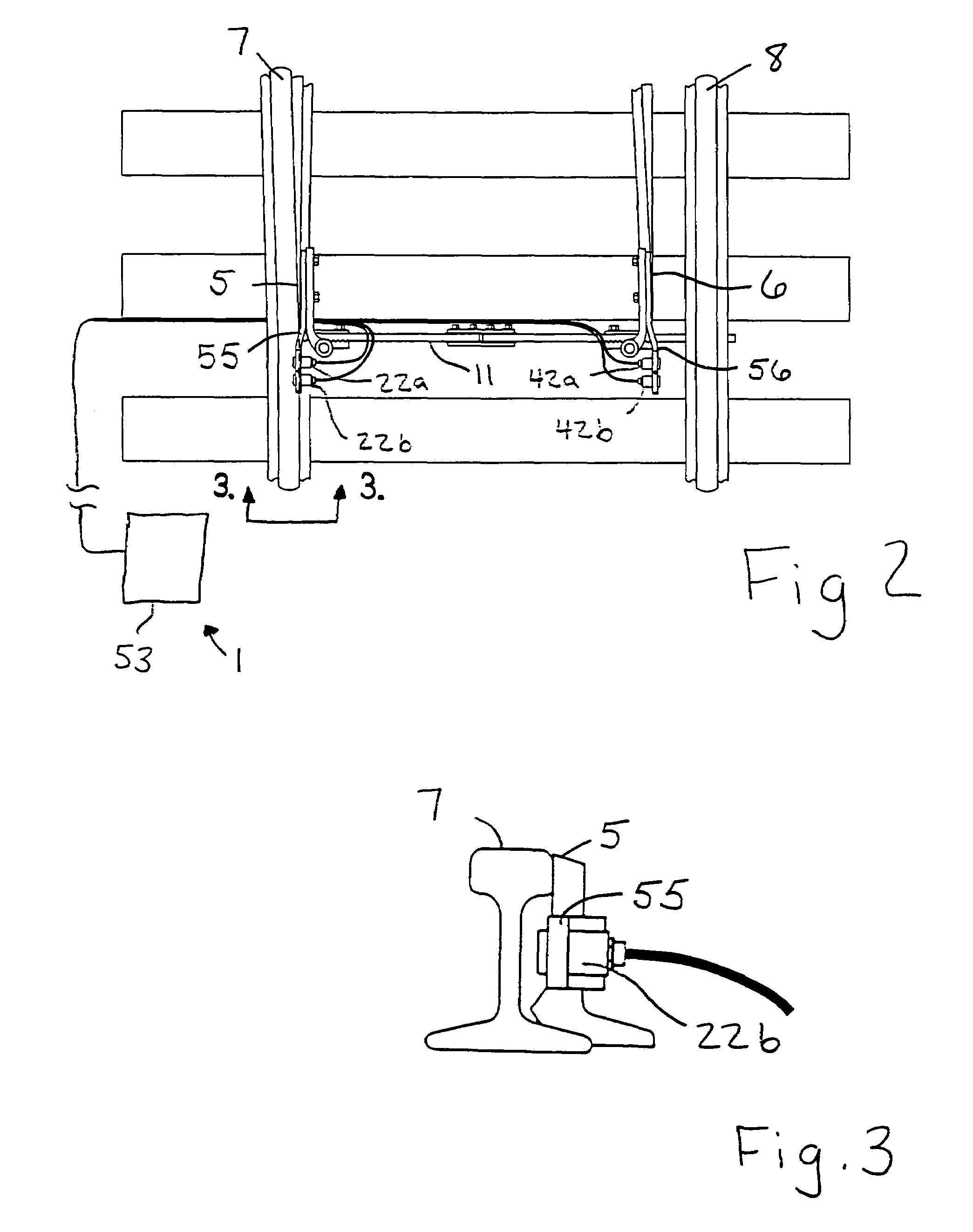
ActiveUS7577502B1Improve reliabilityAvoid feedbackRail switchesDigital data processing detailsProximity sensorEngineering
A vital proximity detection mechanism and method for reliably determining and communicating the position of a railroad switch point relative to a normal fixed track and a reverse fixed track, wherein the mechanism includes substantial component redundancy and fault-checking features and otherwise meets promulgated safety standards for vital componentry. The mechanism includes an RF transmitter and remote status indicator unit to allow for remote adjustments of proximity sensors while monitoring the effects of such adjustments.
Owner:C D L ELECTRIC CO INC
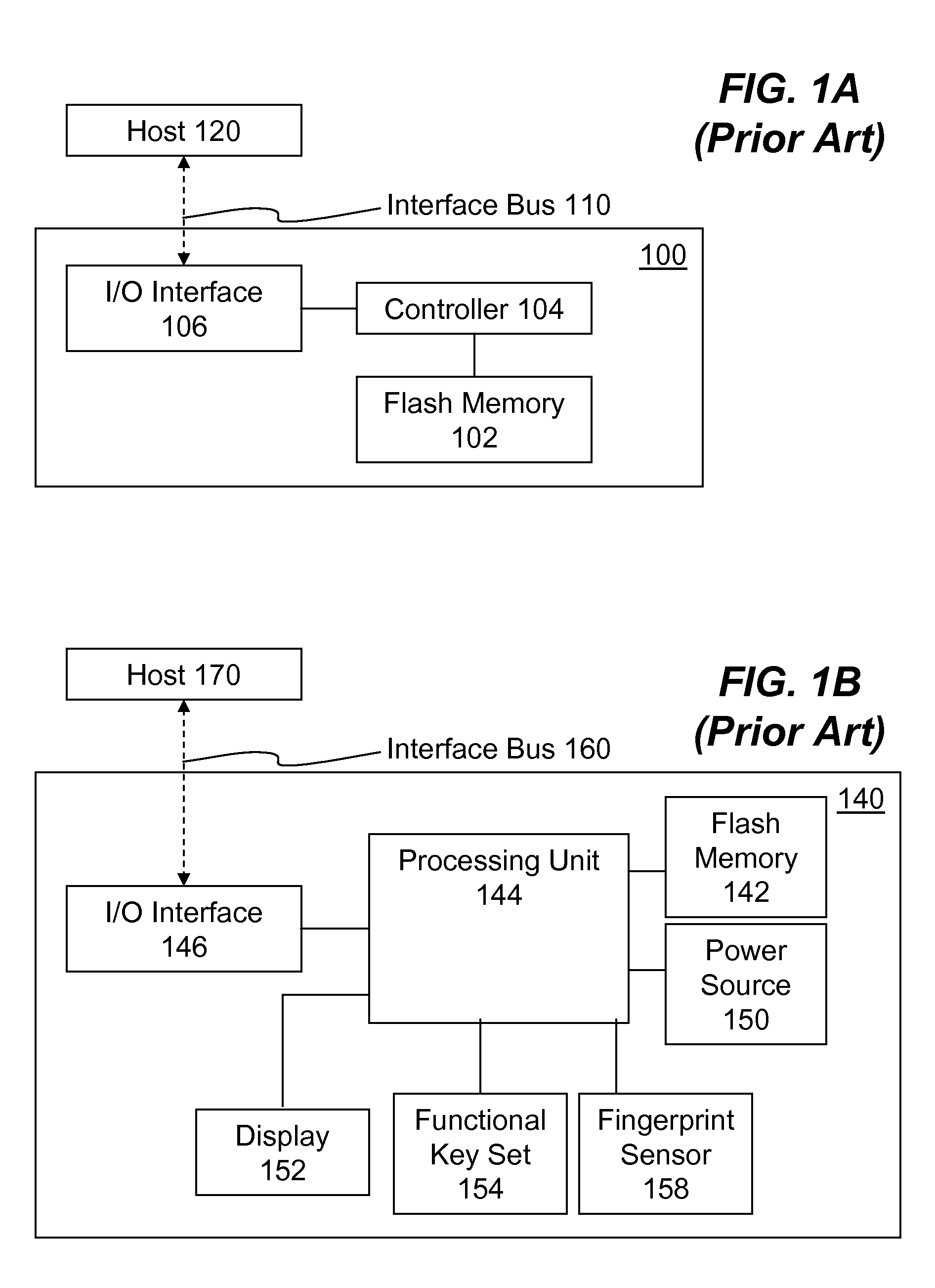
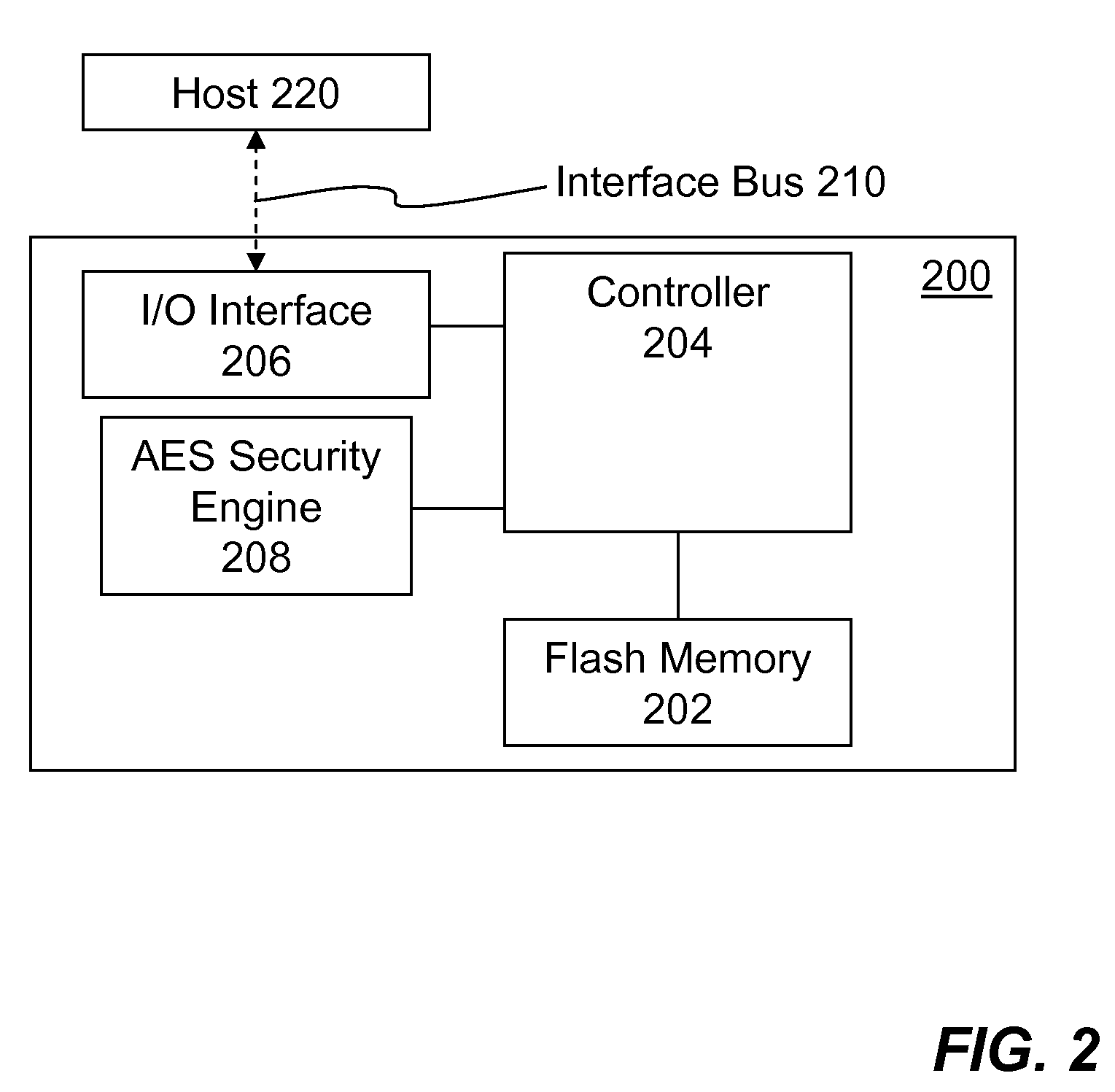
Portable Electronic Storage Devices with Hardware Security Based on Advanced Encryption Standard
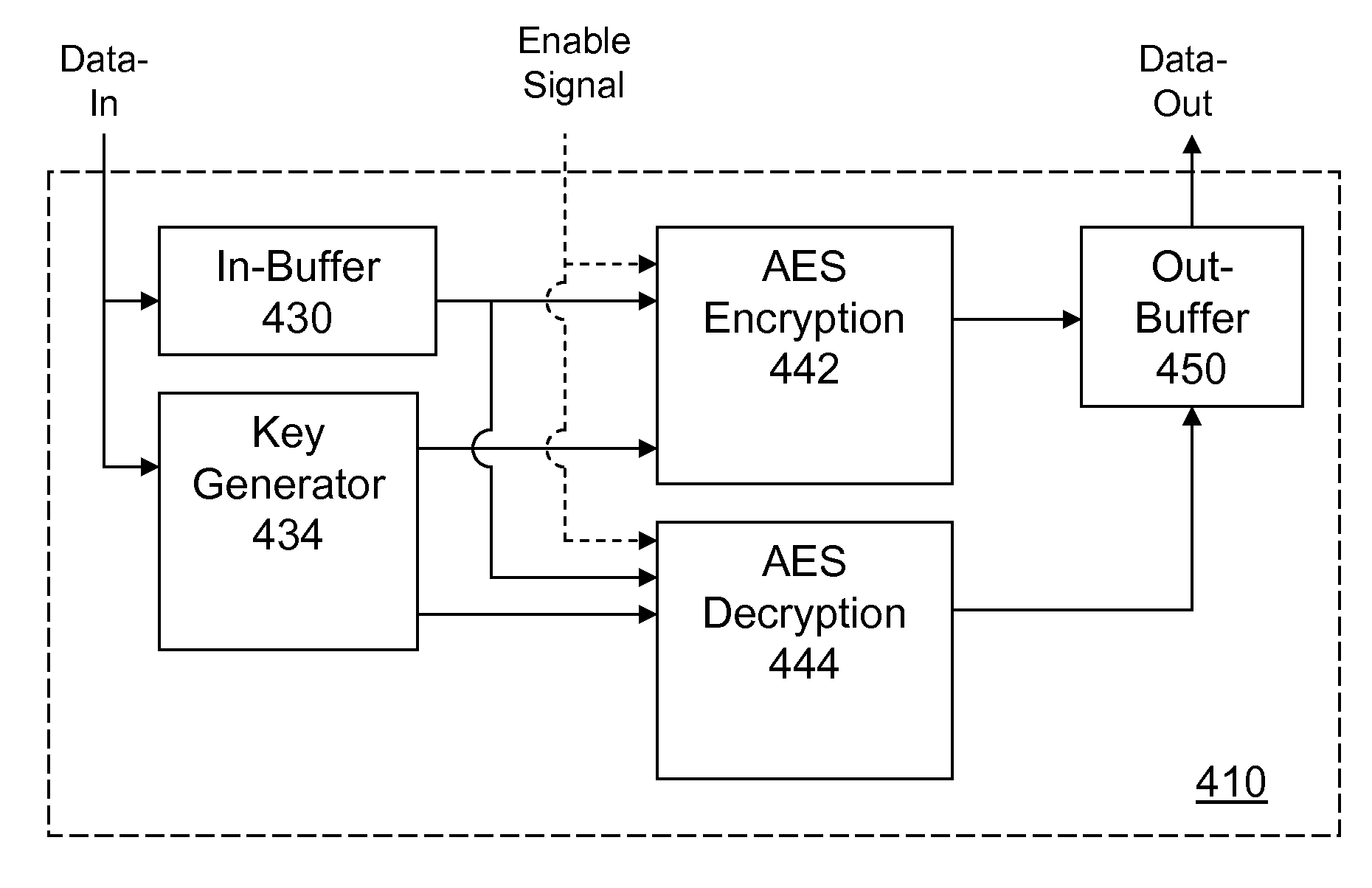
InactiveUS20080192928A1Improve securityUnauthorized memory use protectionInternal/peripheral component protectionKey sizeAdvanced Encryption Standard
Portable electronic storage devices with hardware based security are described. According to one exemplary embodiment of the present invention, a portable electronic storage device (PESD) comprises a security engine integrated thereon. The security engine is configured to provide data encryption, data decryption, and encryption / decryption key (referred to as a key) generation according to a security standard (e.g., Advance Encryption Standard (AES)). AES is a symmetric encryption algorithm processing data in block of 128 bits. Under the influence of a key, a 128-bit data block is encrypted by transforming the data block in a unique way into a new data block of the same size. AES is symmetric sine the same key is used for encryption and the reverse transformation (i.e., decryption). The only secret necessary to keep for security is the key. AES may use different key-lengths (i.e., 128-bit, 192-bits and 256-bits).
Owner:SUPER TALENT ELECTRONICS
Warning system
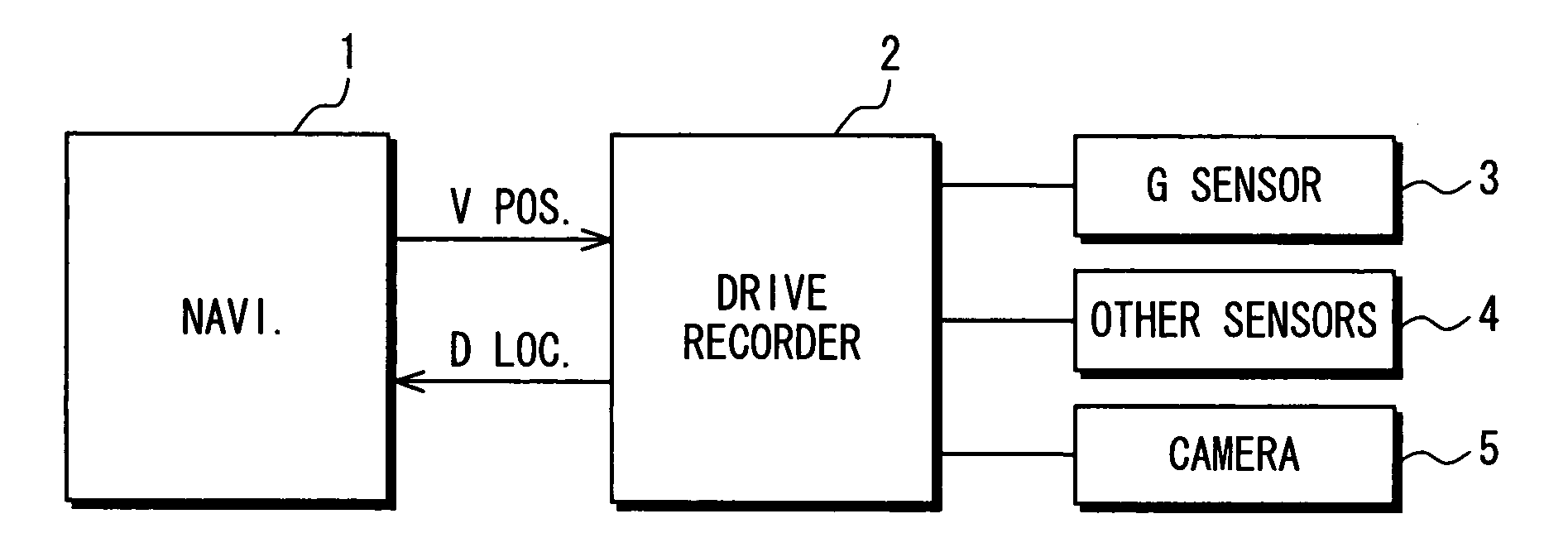
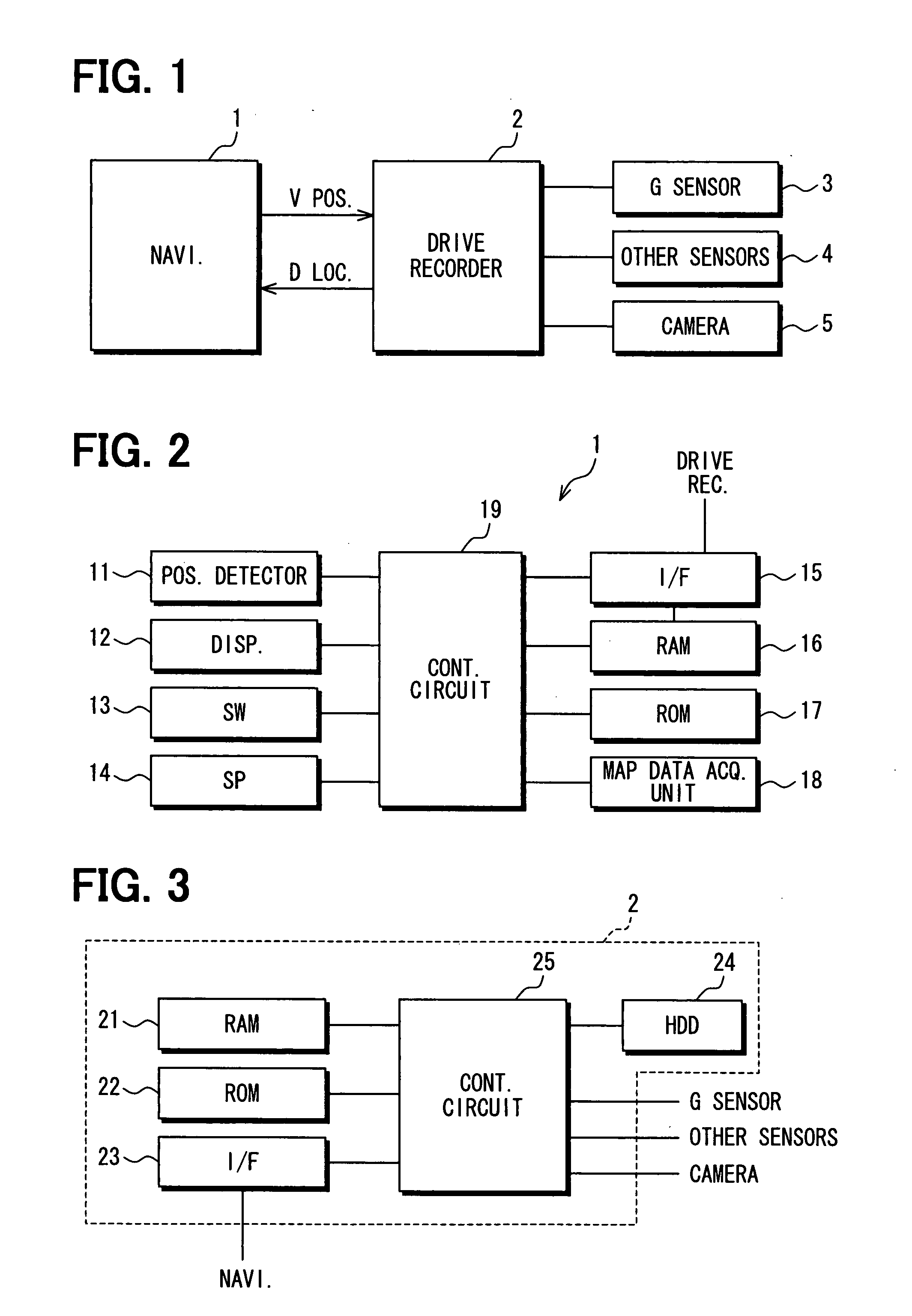
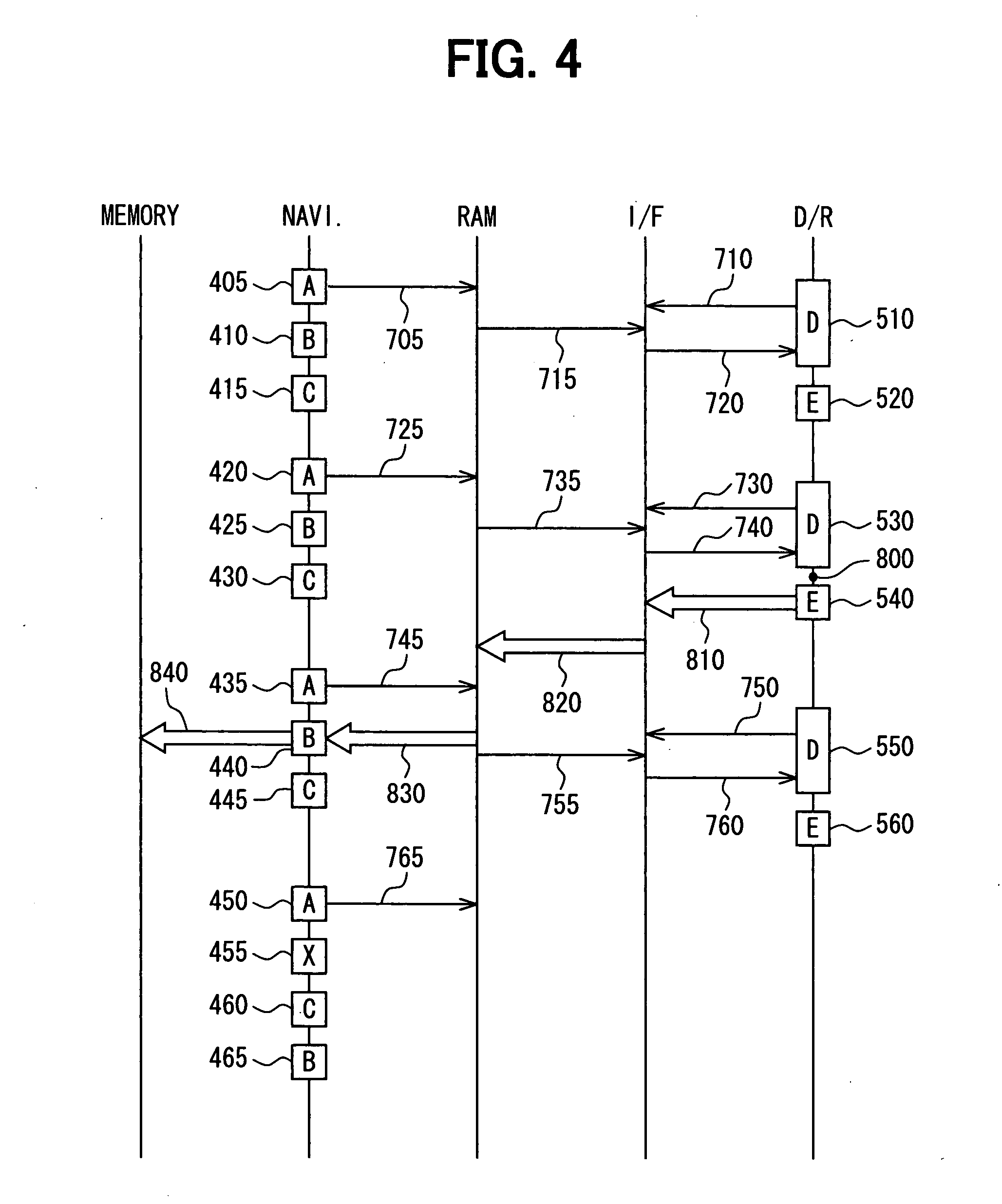
InactiveUS20080048850A1Reduce processing loadInstruments for road network navigationPedestrian/occupant safety arrangementLocation detectionDriver/operator
A warning system warns a driver of a vehicle that a vehicle location in a record of previously detected drive operation that indicates a violation of a safety standard and a current position of the vehicle are determined to be within a predetermined distance from each other based on repeated detections of a current vehicle position by a detector and a detection of the drive operation that indicates the violation of the safety standard transmitted through an interface from a drive recorder. In this manner, the warning system for warning the driver lightens a process load of a unit that performs a position detection process and a unit that performs a record keeping process.
Owner:DENSO CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com