Patents
Literature
57 results about "Grey list" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A gray list is a list of stocks that are ineligible for trade by an investment bank's risk arbitrage division. Securities on the gray list aren’t necessarily exceptionally risky or otherwise inherently flawed. The gray list is composed of firms working with the investment bank, often in matters of mergers and acquisitions.
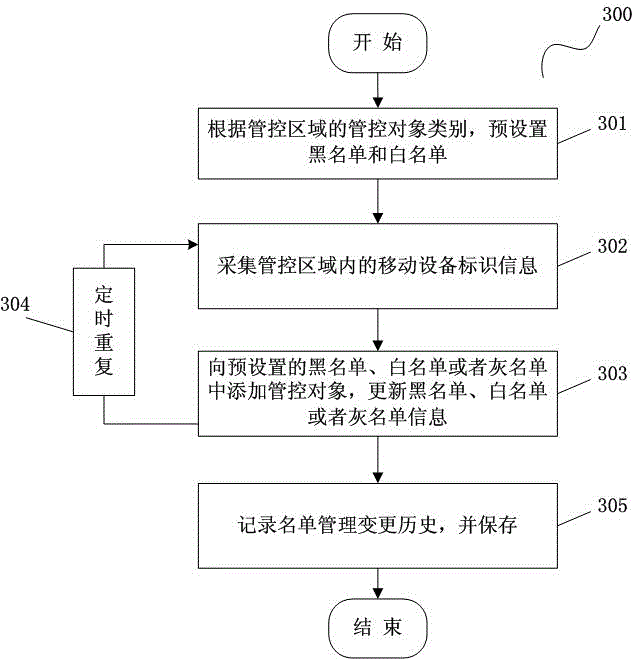
Community personnel file intelligent management method
ActiveCN108052925AImprove securityReduce work intensityCharacter and pattern recognitionCommunity managementIntelligent management
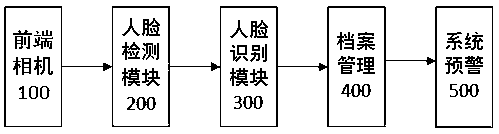
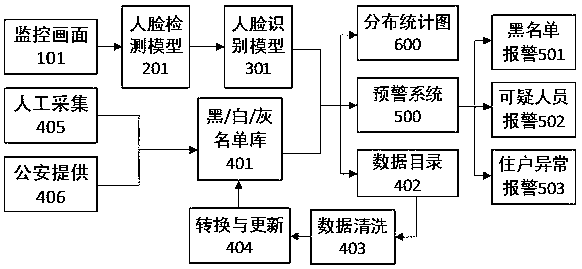
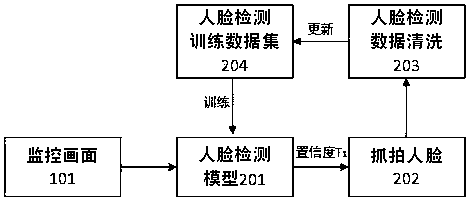
The invention relates to the field of community management, and provides a community personnel file intelligent management method. The method comprises the steps that faces are detected by using a deep learning model, and list database comparison is conducted; management and classification of community personnel are conducted by adopting a mechanism of black, white, and gray lists to achieve real-time alert of special personnel; cleaning of acquired image data is conducted to optimize and train the deep learning model; entry and exit time of the community personnel are analyzed to achieve advance warning of abnormal events; archive information of list database personnel is used for forming relevant statistical data and charts of the community. By means of a community management system, specification management of the community personnel and timely warning of the special personnel and the abnormal events are achieved to reduce work load of security personnel and effectively improve safety coefficient of the community, and community management is more intelligent.
Owner:GOSUN GUARD SECURITY SERVICE TECH
Abnormal electricity utilization user detection method based on semi-supervised learning
InactiveCN108805747AImprove accuracyImprove efficiencyData processing applicationsCharacter and pattern recognitionElectricitySupervised learning
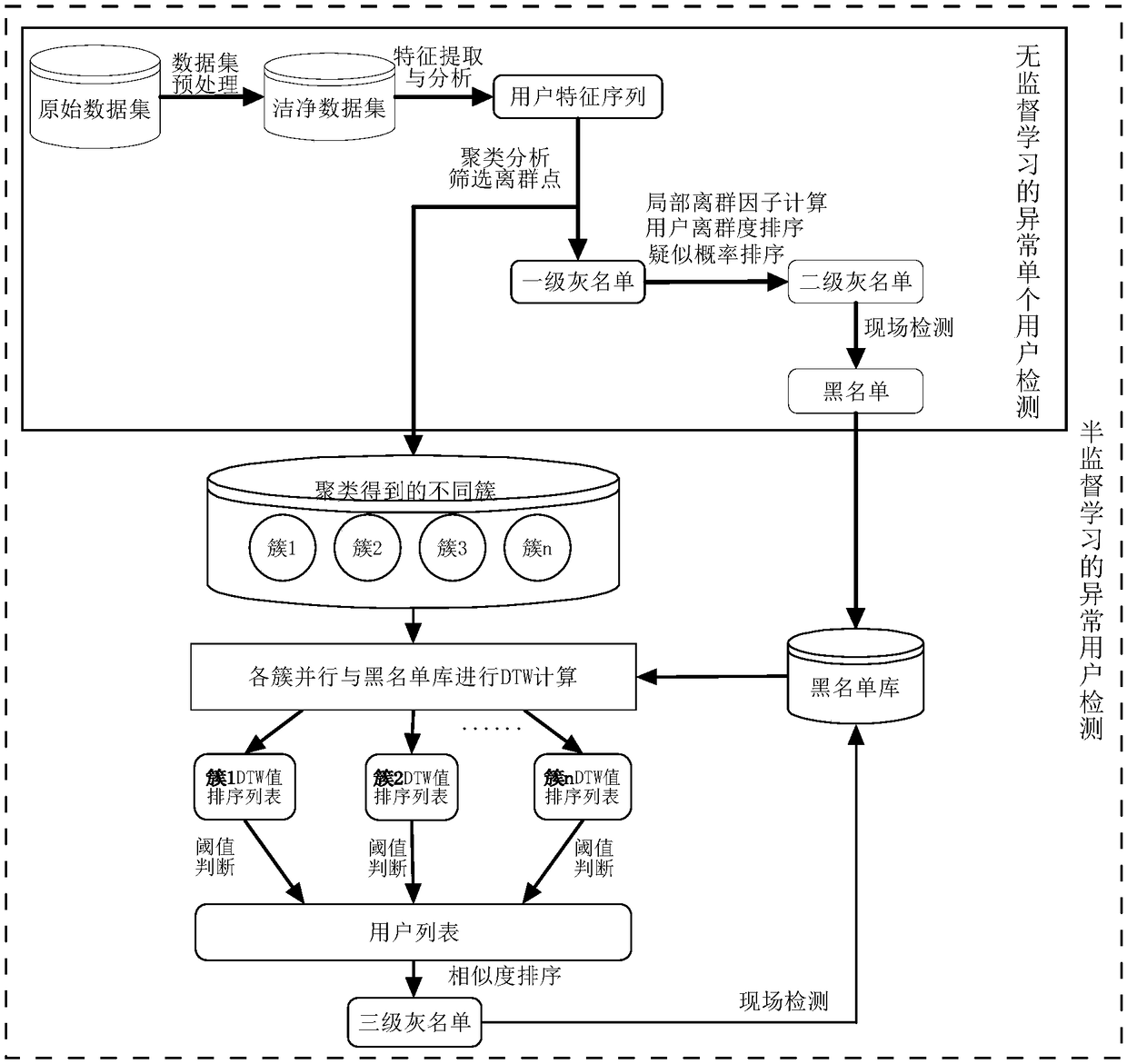
The invention discloses an abnormal electricity utilization user detection method based on semi-supervised learning, belonging to the technical field of detection. The method comprises the following steps: data preprocessing; generation of a first grade grey list based on clustering analysis; generation of a second grade grey list based on outlier degree calculation; and generation of a third grade grey list based on similarity calculation. An abnormal electricity utilization user detection model based on semi-supervised learning in the invention aims at forming a user dubiety degree ordered list, thus a key detection list is provided for manual detection, and accuracy and efficiency of on-site detection are improved.
Owner:SHANDONG UNIV OF SCI & TECH
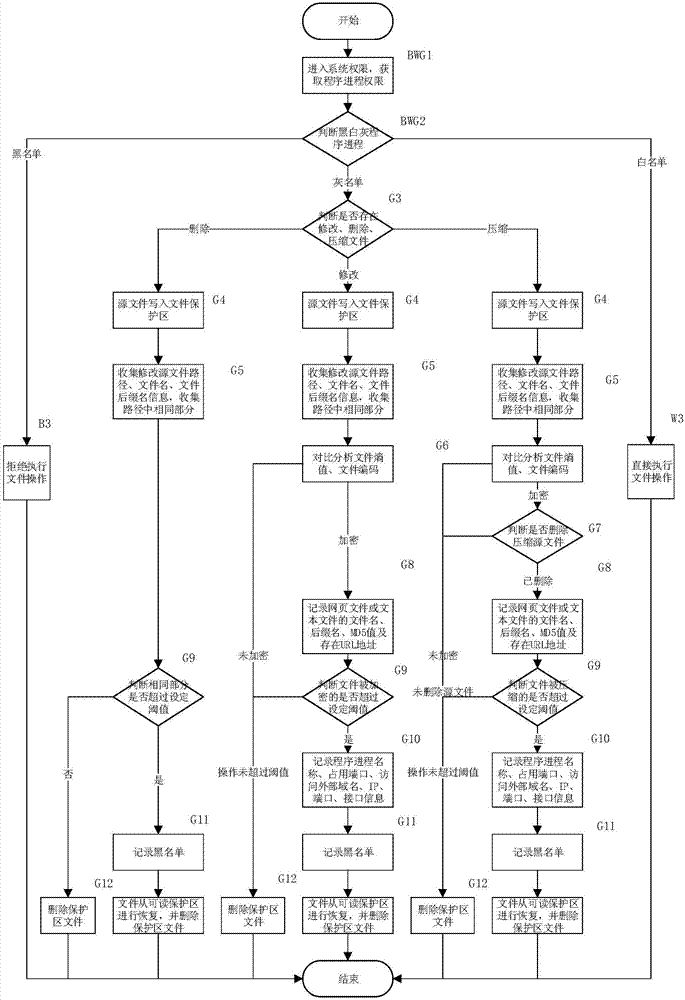
Method and system of preventing files from being damaged by malicious operation behaviors
InactiveCN107506642AReduce risk frequencyEffective identification of malicious operationsDigital data protectionPlatform integrity maintainanceBlack listEncryption
The invention discloses a method and a system of preventing files from being damaged by malicious operation behaviors. if a process of deleting the file exists, the process is released if the process is a white-list process, is directly blocked if the process is a black-list file reading or writing operation process, and is suspended if the process is a gray-list process, and released after backing up the file to a readable protected area is completed; if a process of modifying the file exists, the process is released if the process is a white-list process, is directly blocked if the process is a black-list process, and is suspended if the process is a gray-list process, and released after backing up the file to the readable protected area is completed; and if an encryption / compression encryption operation exists, whether operation frequency of a process for the file in a preset time exceeds a set threshold value is judged, and if yes, it is determined that the operation is a suspected malicious file operation behavior. According to the technical solution of the invention, the malicious file operation behaviors can be effectively identified, and risk frequency of maliciously deleting and modifying important files can be reduced at the same time.
Owner:SICHUAN CHANGHONG ELECTRIC CO LTD
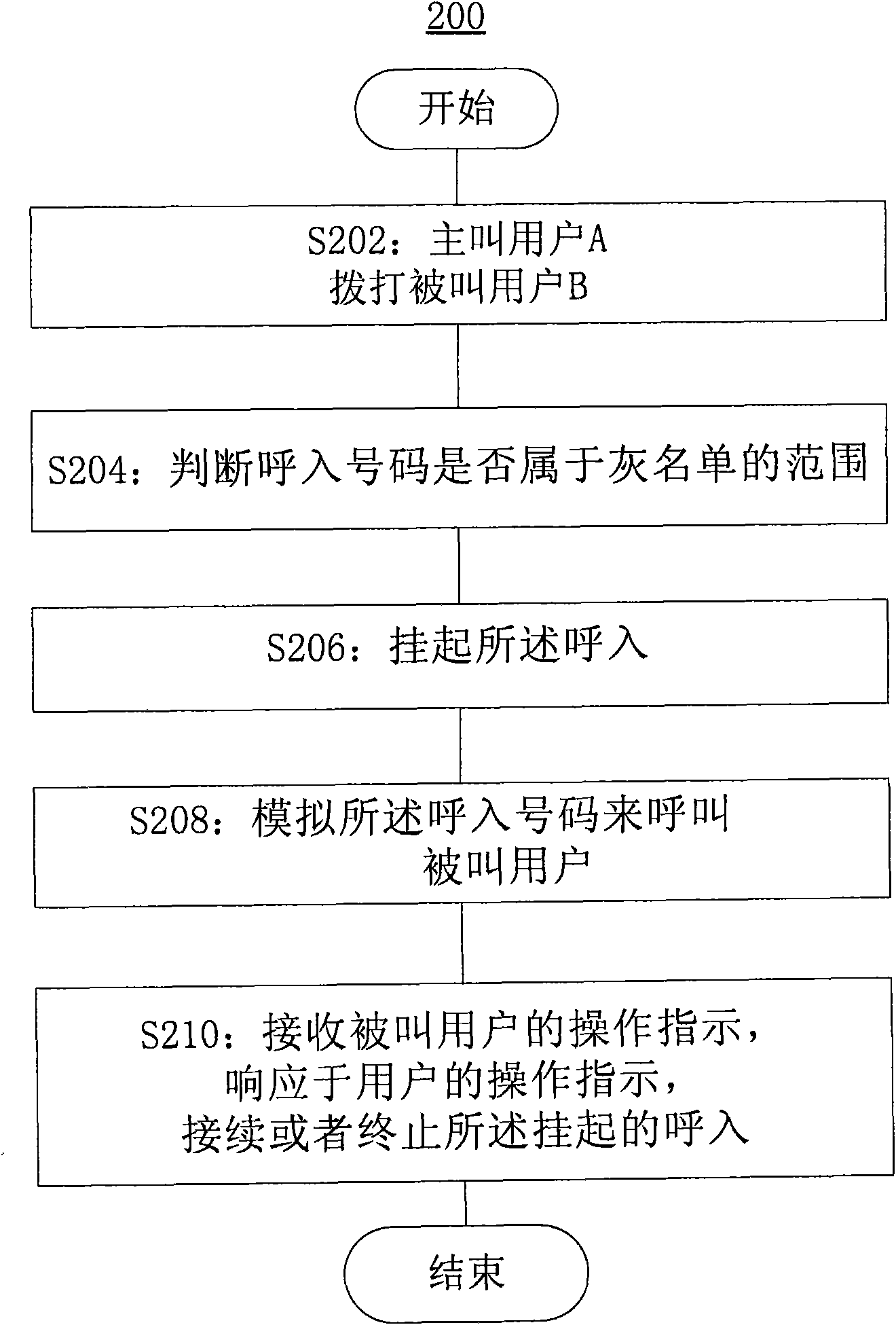
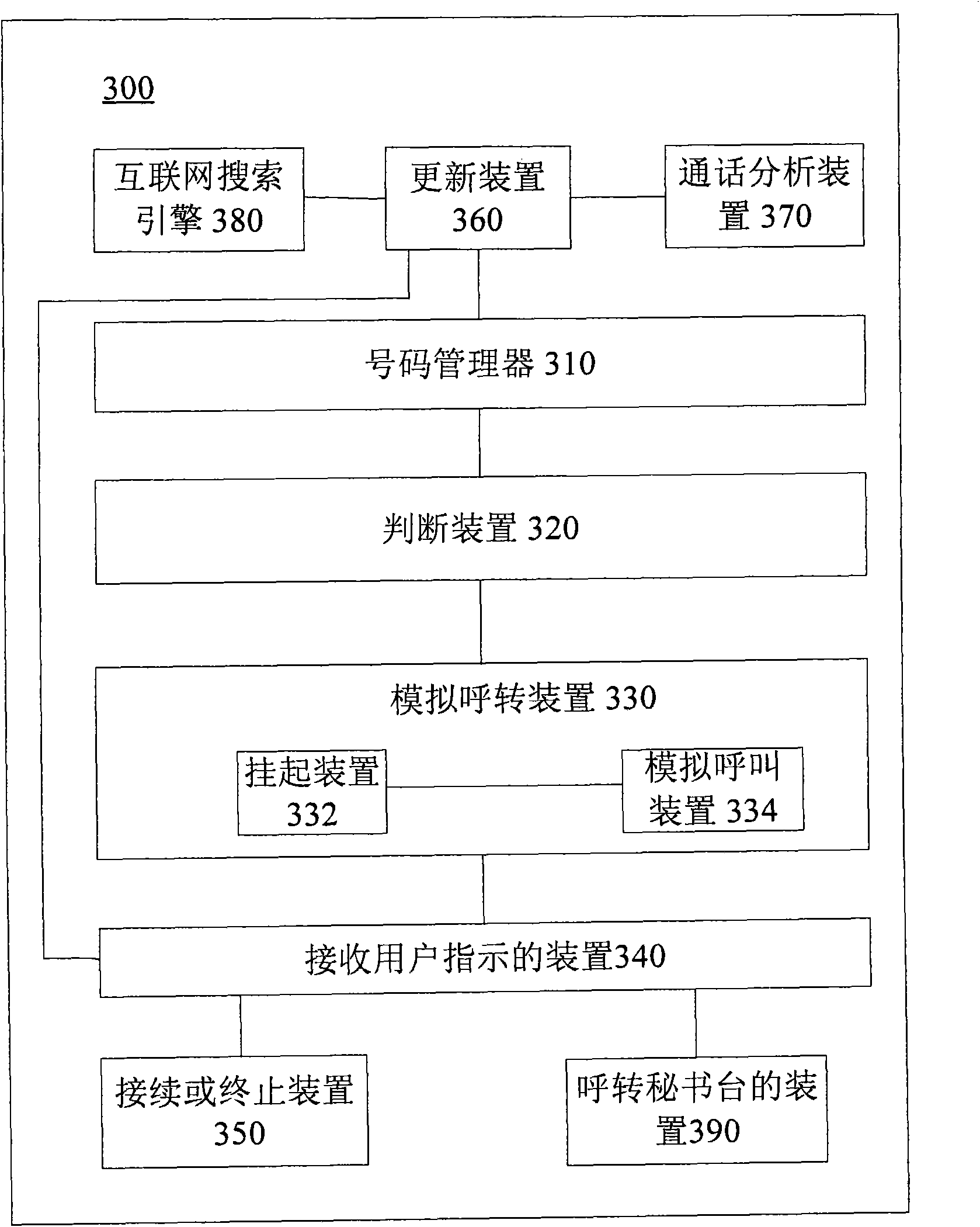
Intelligent call forwarding method and device
InactiveCN102143461AReduce stepsEffective interceptionSpecial service for subscribersCommmunication supplementary servicesGrey listCall forwarding
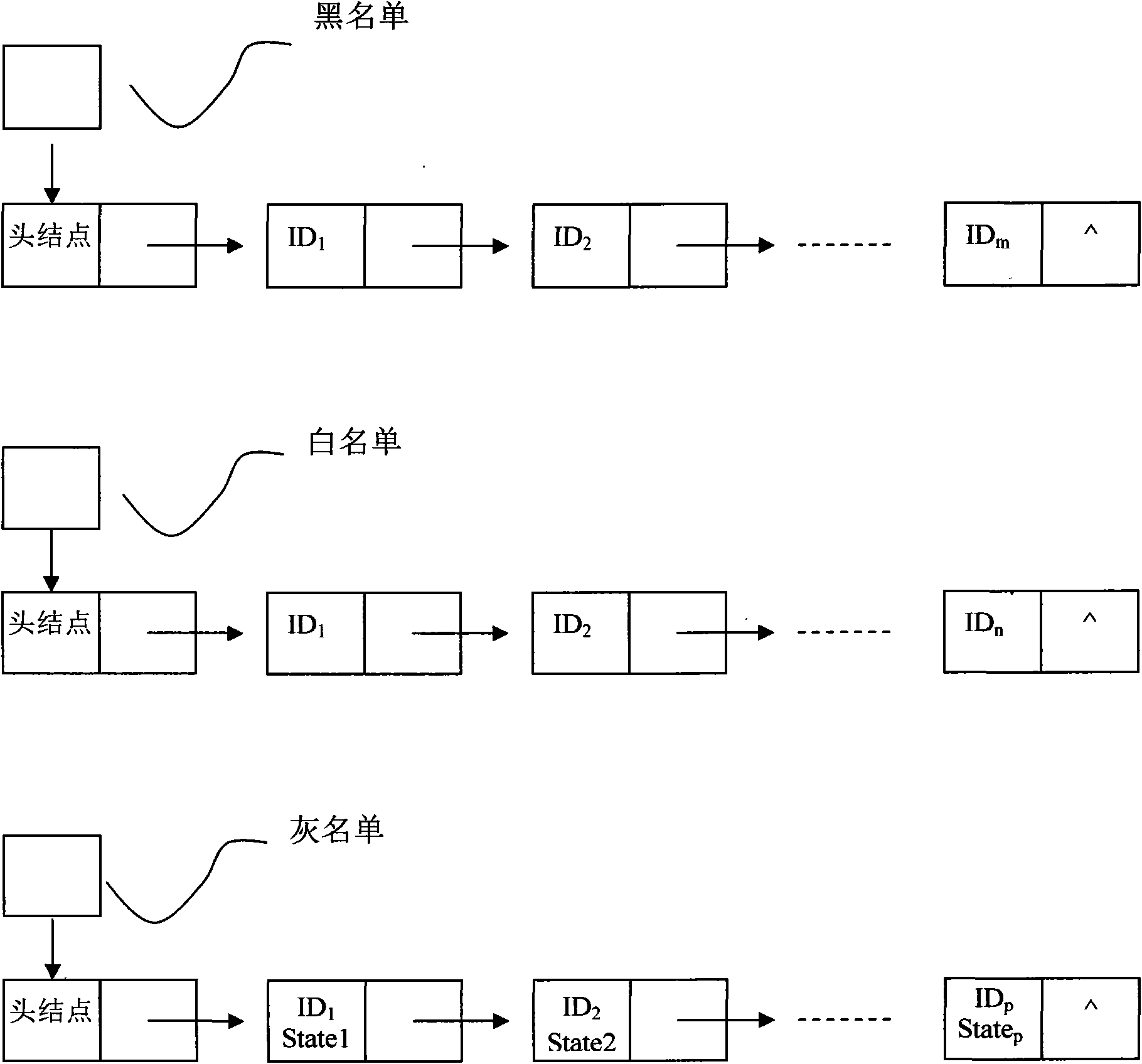
The invention discloses an intelligent call forwarding method and device. The intelligent call forwarding method comprises the following steps of: judging whether an incoming call belongs to the range of a grey list according to a white list and a black list; and performing simulation call forwarding responding to the situation that the incoming call belongs to the range of the grey list. According to the invention, a high efficient interception to annoyance calls is realized without missing useful calls of a user.
Owner:王滨
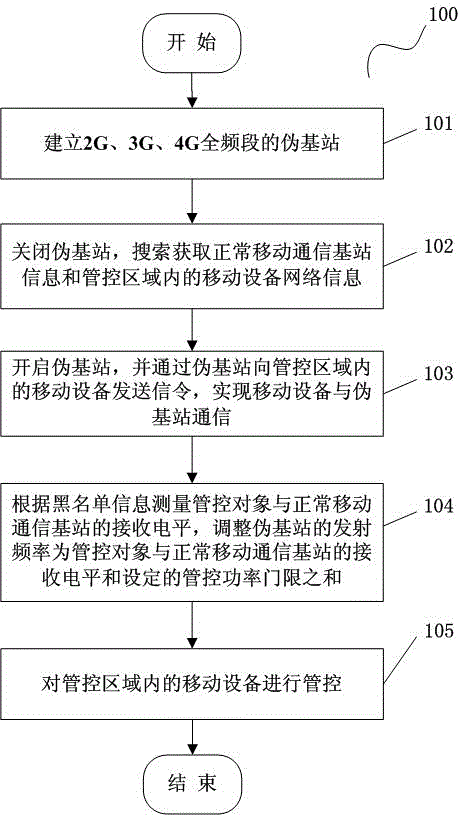
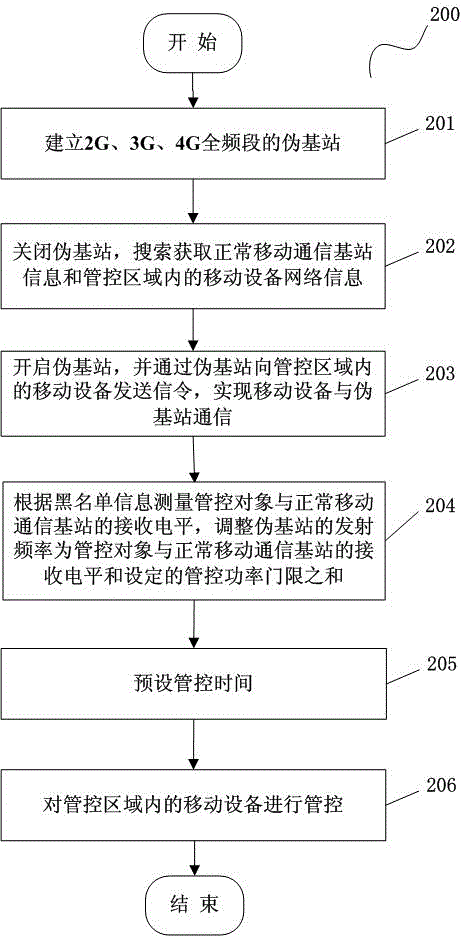
Regional control method and system of mobile device communication
InactiveCN103607730AEffective confidentiality controlOrderly managementPower managementAssess restrictionControl systemBlack list
The invention discloses a regional control method of mobile device communication. The method comprises the following steps: a pseudo base station is established, and communication between a mobile device in a control region and the pseudo base station is realized; and a black list, a white list and a grey list are preset according to the position of the mobile device relative to the control region, and the black list, the white list and the grey list are updated in real time. The invention also discloses a regional control system of the mobile device communication. The system comprises a shielding management module and an object management module. According to the technical scheme of regional control of mobile device communication, effective confidential control of full-standard and full-frequency range various mobile phones in the control region is realized via arrangement of 2G, 3G and 4G pseudo base stations.
Owner:CHENGDU SEEKCON MICROWAVE COMM
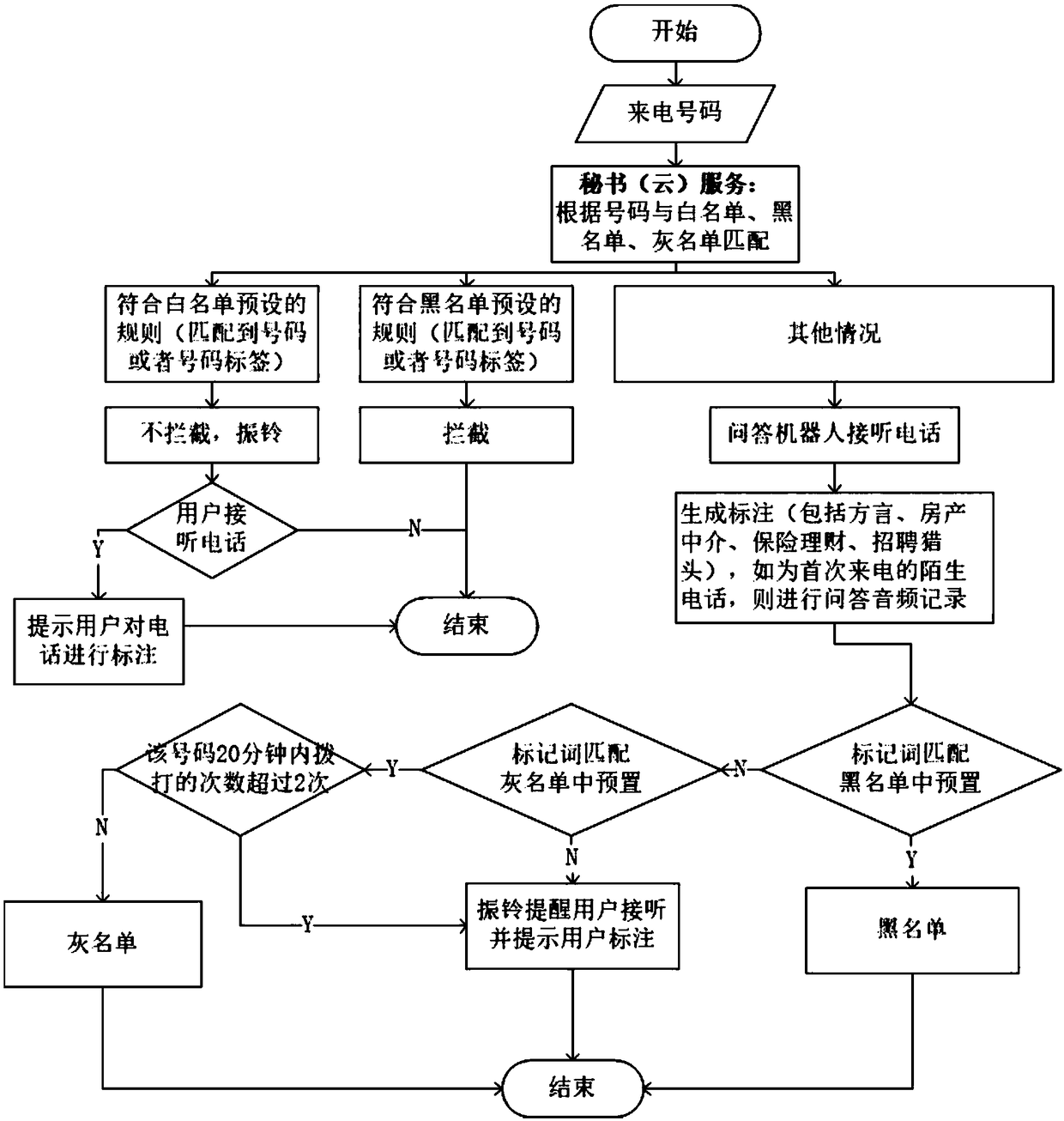
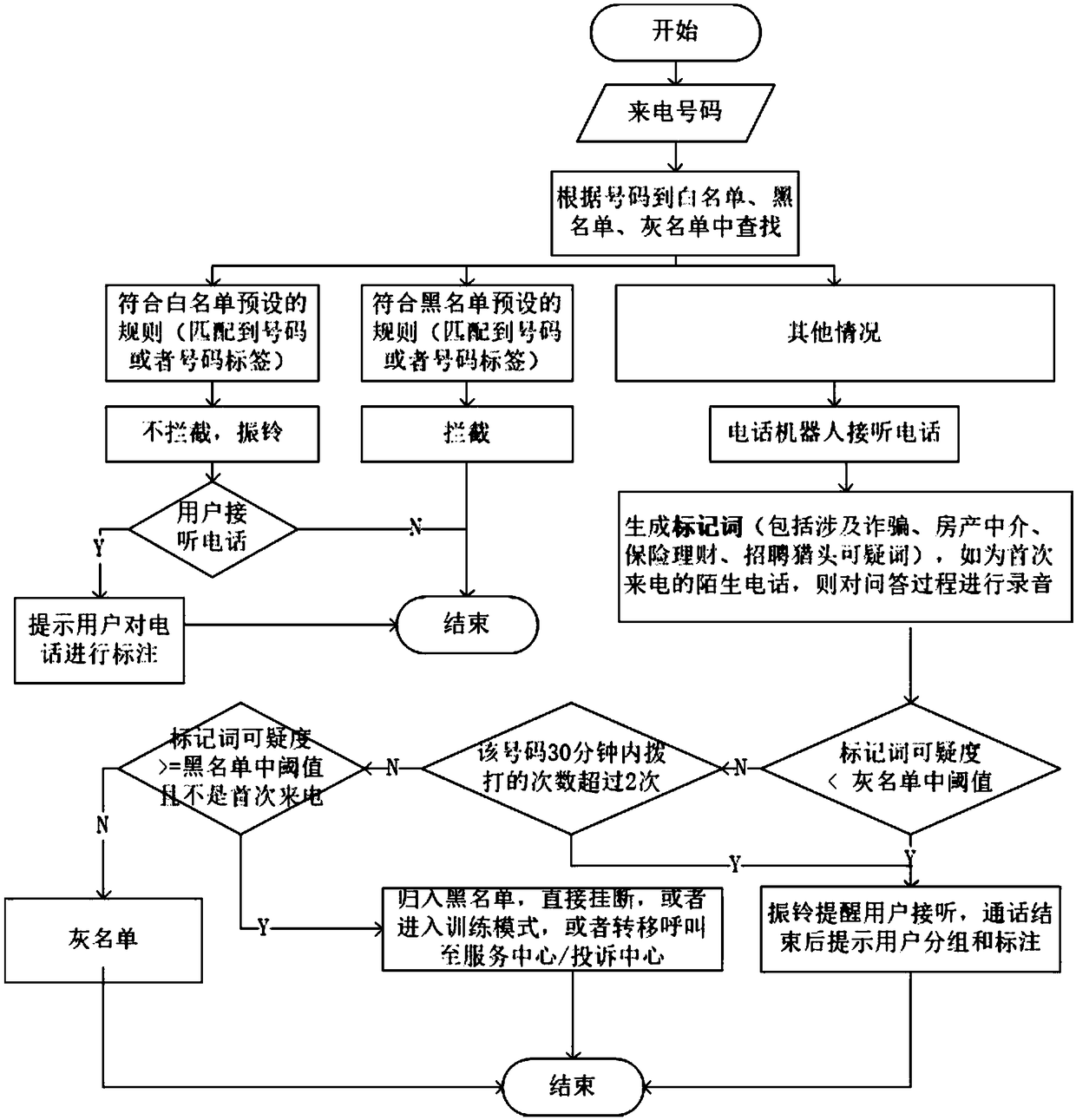
Harassment-resistant telephone secretary cloud service achieving method based on intelligent question answering
InactiveCN109474757AAvoid interferenceAvoid delaySpecial service for subscribersSupervisory/monitoring/testing arrangementsGrey listQuestions and answers
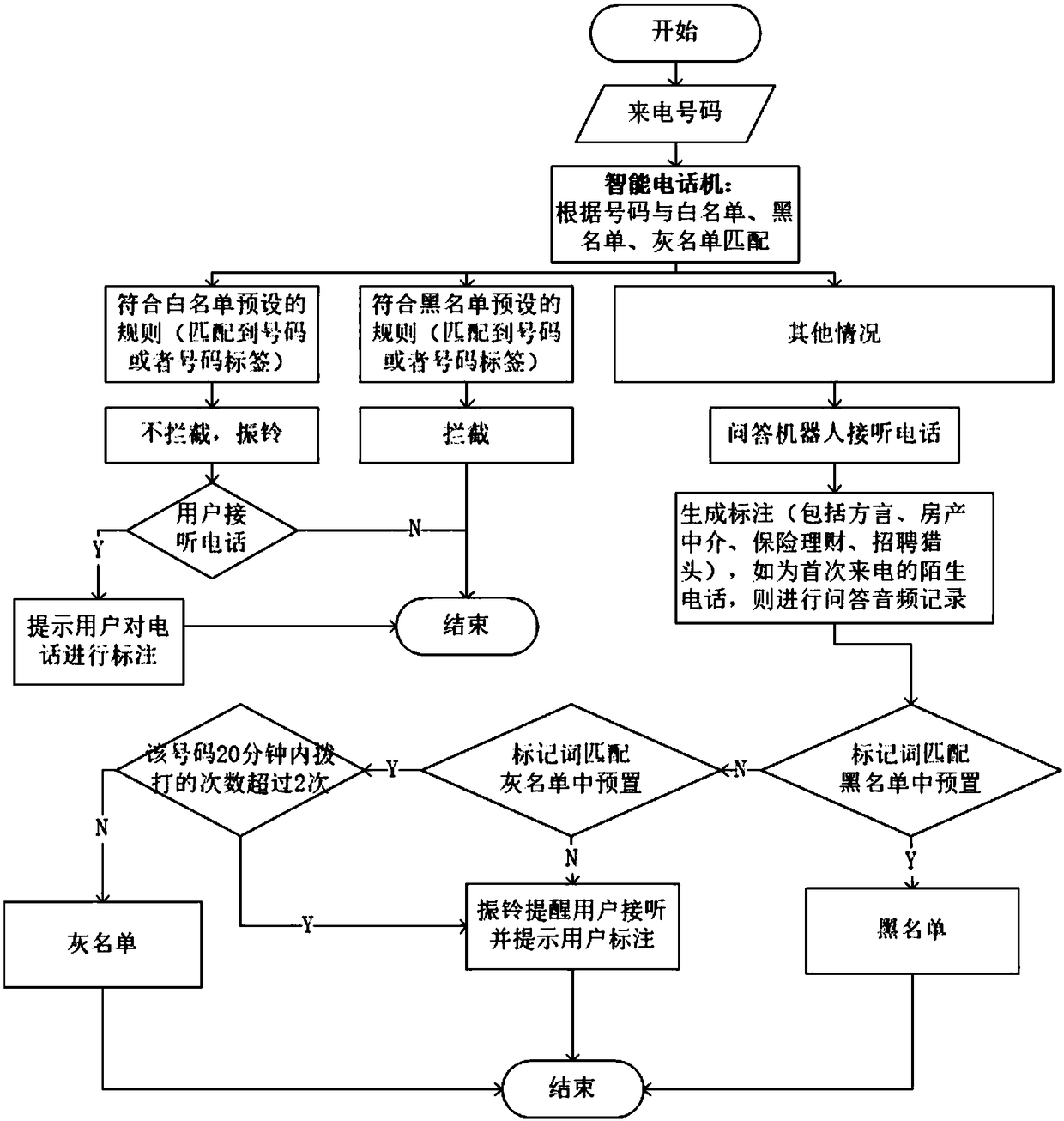
The invention relates to a harassment-resistant telephone secretary cloud service achieving method based on intelligent question answering. The method comprises the following steps that (1) a telephone secretary service is configured for an owner telephone, a telephone secretary service process judges each incoming call number, ringing is performed to notify an owner for incoming calls belonging to a white list, interception is performed for incoming calls belonging to a black list, and a robot is started to perform answering for incoming calls belonging to a grey list; (2) for strange incoming calls, the robot is started to carry out intelligent question answering with callers, and whether the ringing is performed or the grey list is accessed is decided according to question answering contents; (3) for the incoming calls in the grey list, the robot is started to carry out intelligent question answering with callers, the incoming calls can be directly hung up and are classified in theblack list in combination with owner settings according to re-judgment of the suspicious degree of the incoming calls; and (4) for the harassment / fraud calls belonging to the black list, a mode can beswitched to a training / punishment mode in addition to direct hang-up, so that a training tool of the question-and-answer robot is realized.
Owner:SOUTHEAST UNIV
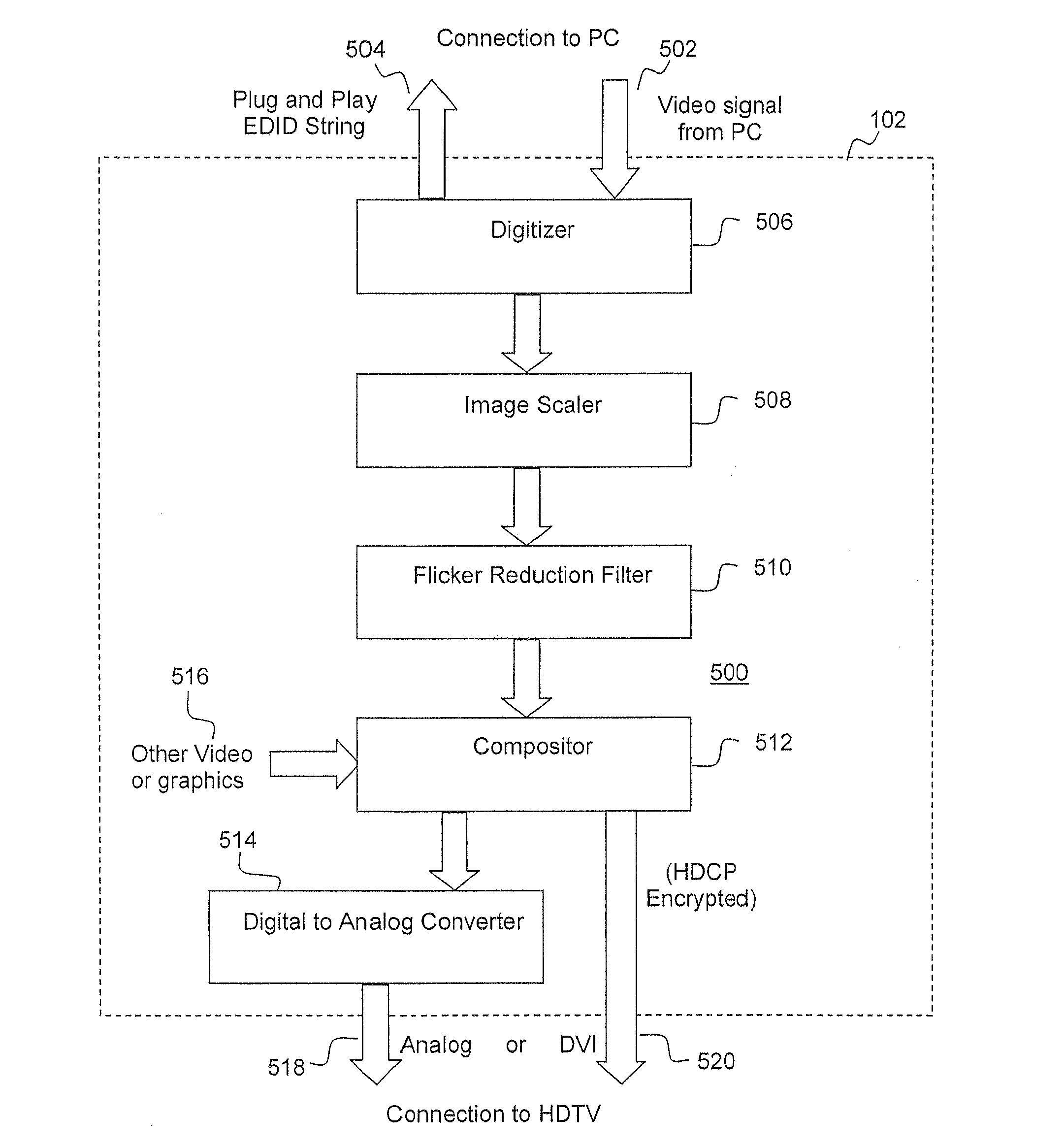
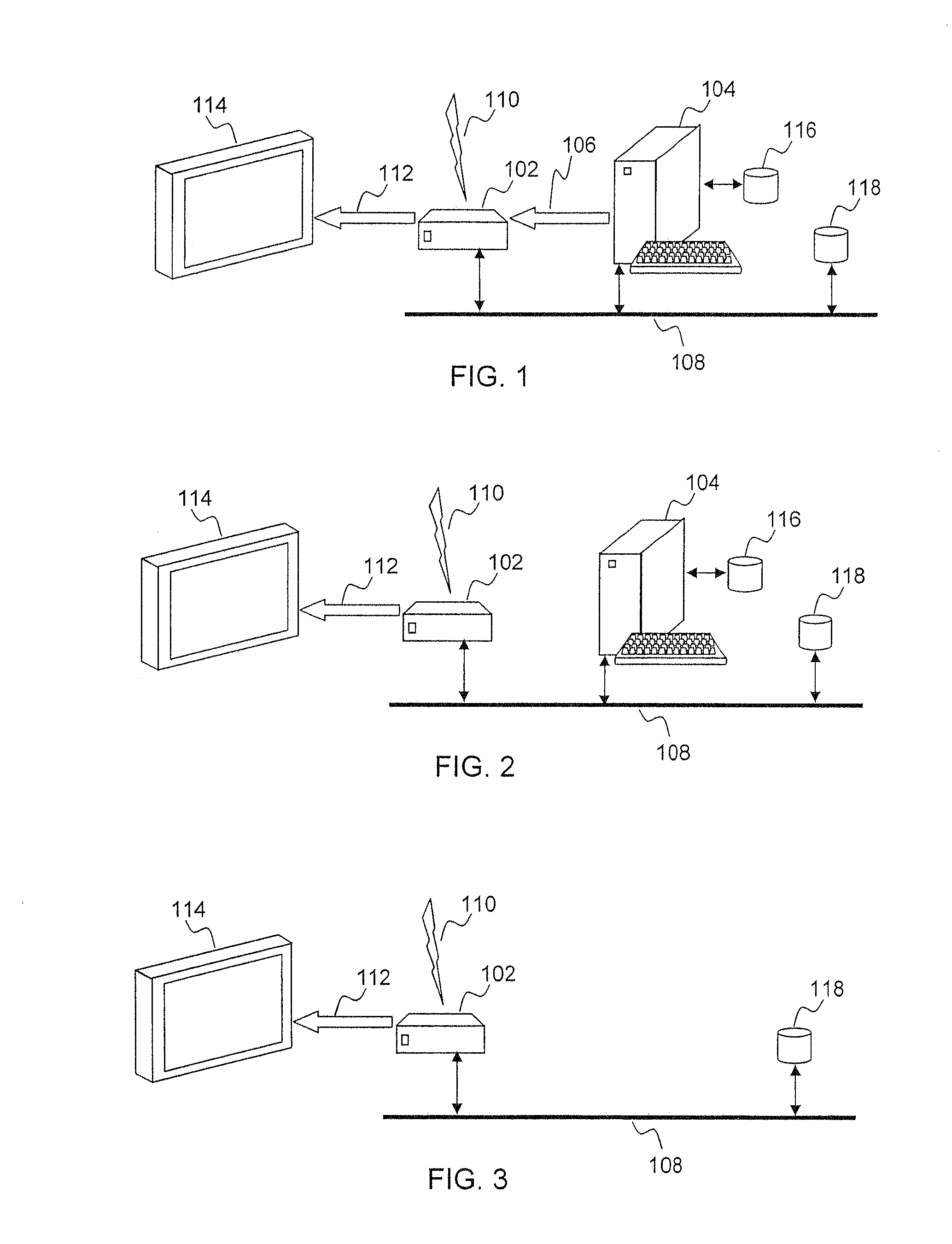
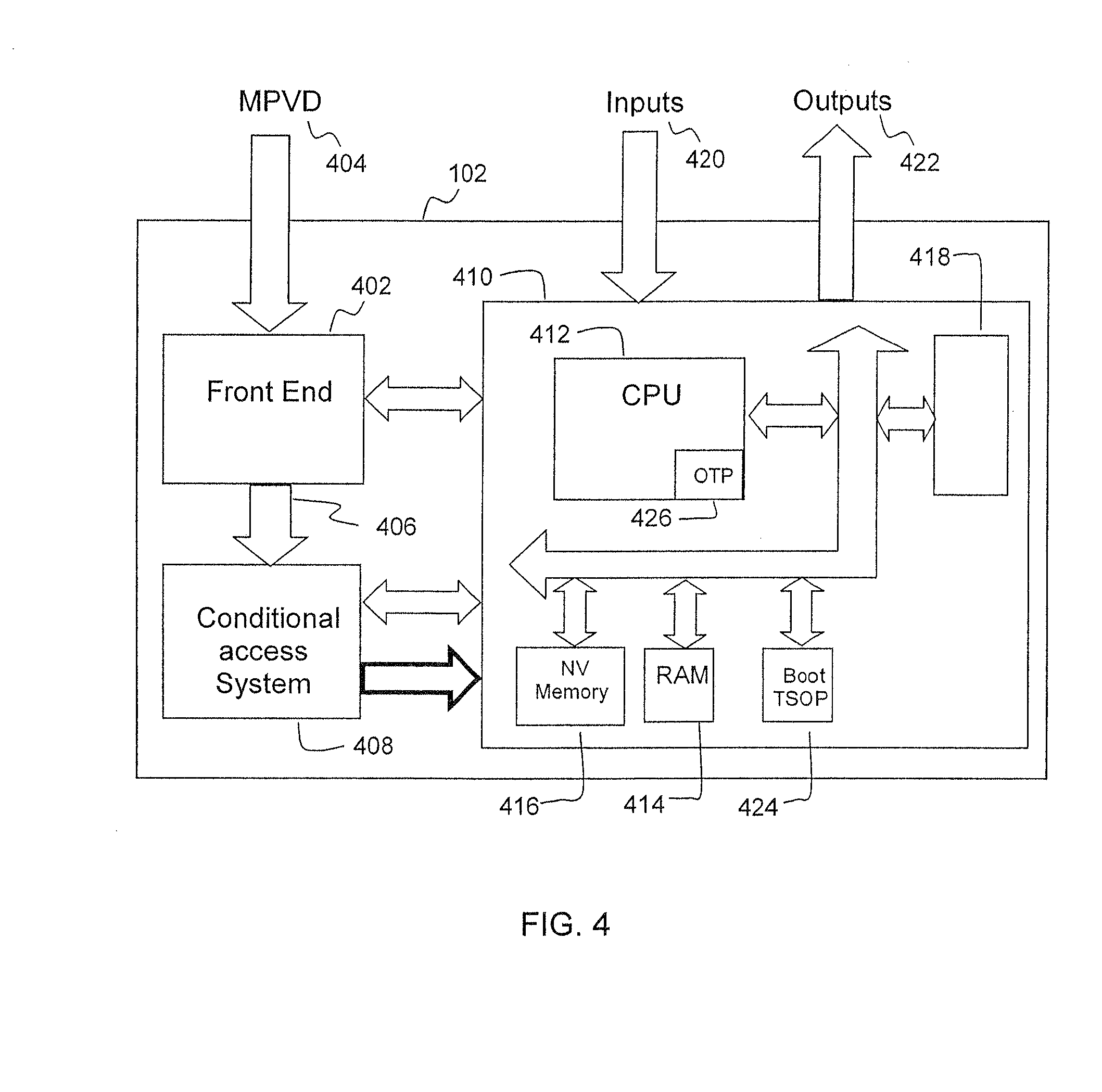
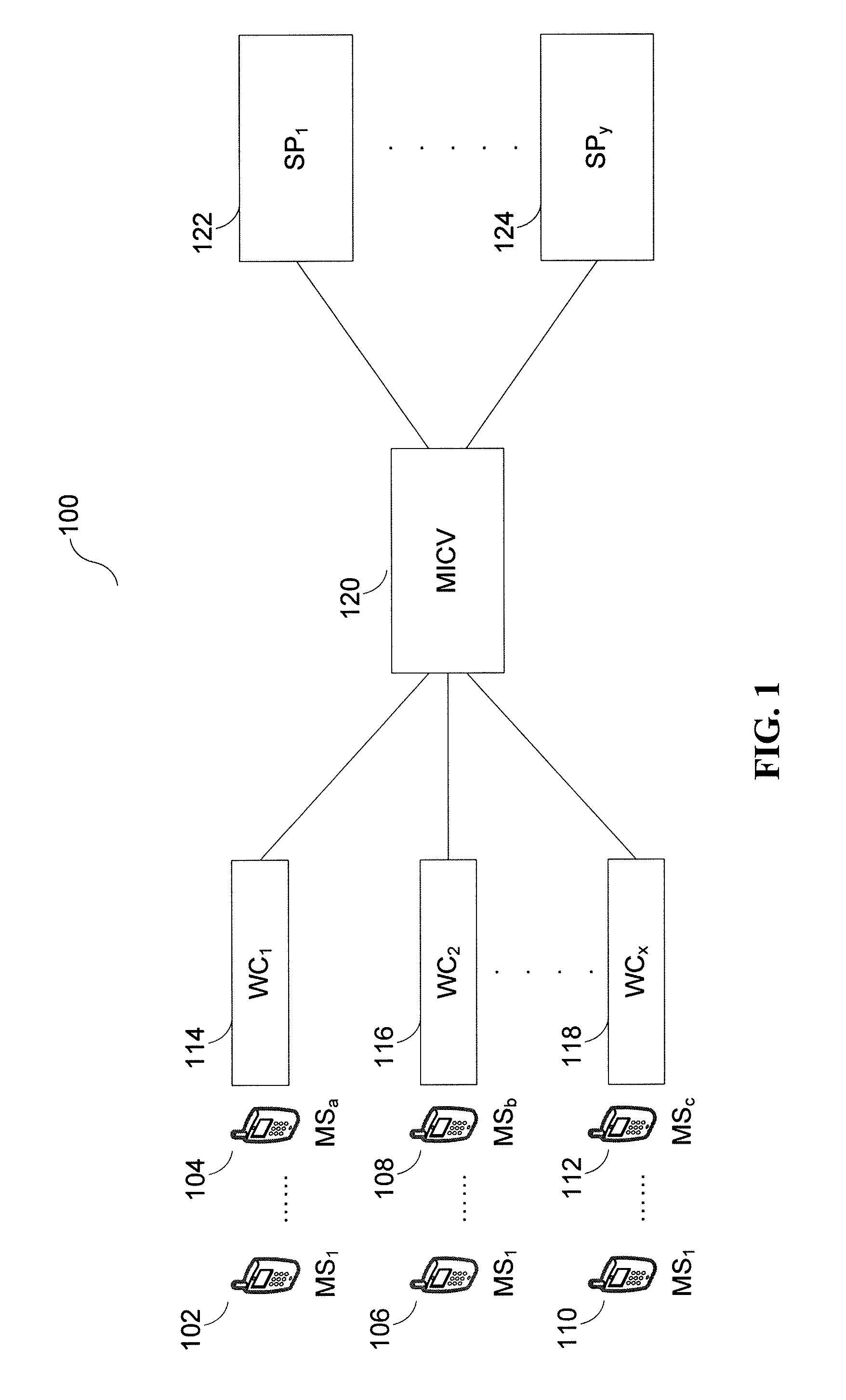
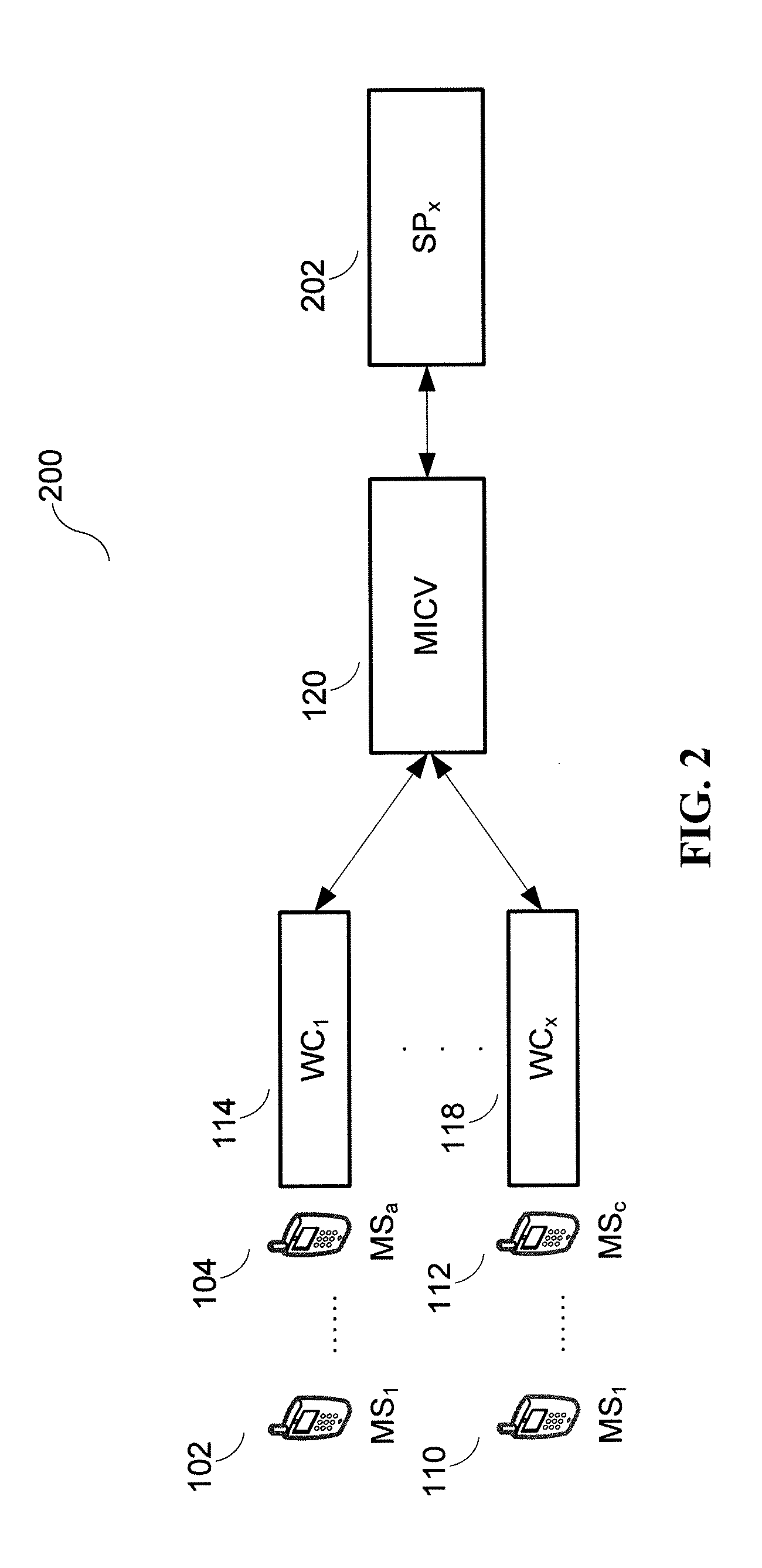
Secure Integrated Media Center
InactiveUS20100205648A1Safe storageTelevision system detailsEncryption apparatus with shift registers/memoriesHard disc driveHigh definition tv
A set-top media system is disclosed which can be combined with an open architecture personal computer (PC) to provide a feature-rich secure integrated media center while meeting security rules of most major conditional access and content protection industry rules such as Cable Labs DFAST and PHILA agreements; and DTLA agreements for 5C-DTCP for IEEE1394, USB, and IP. The set-top media center and PC share common resources such as high definition display, remote control, hard disk drive, and other external unsecure storage devices. All media content is available seamlessly using a PC user interface, including controlled-content media such as high definition TV, within a PC desktop window. All controlled-content media is manipulated and managed within the set-top media system in a seamless manner. A mechanism is disclosed to allow controlled-content media to be stored on unsecure devices in encrypted form while overcoming the disk cloning attack problem for move operations. One embodiment utilizes a “grey list” of available programs to keep track of controlled-content media which is allowed to be played, while another embodiment utilizes a “black list” of programs no longer available to keep track of controlled-content media which is forbidden from being played.
Owner:SAADAT ABBAS SASAN +1
Harassment call coping method and system based on smart question-answer_human-computer interaction mechanism
InactiveCN109348036AAvoid interferenceAvoid delayAutomatic call-answering/message-recording/conversation-recordingQuestion answerBlack list
The invention relates to a harassment call coping method and system based on a smart question-answer_human-computer interaction mechanism. The method comprises the steps of (1), increasing a grey liston the basis that an owner phone has a white / black list; (2), for stranger call, starting a robot to carry out question-answer on callers, and deciding to ring or enter the grey list according to question-answer content; (3), for the calls in the grey list, starting the robot to carry out question-answer on the callers, and directly hanging up the calls and putting the calls into the black list according to re-judgment of call suspicious degree through combination of settings of an owner, or putting the calls into the grey list again, or carrying out ringing to notify the owner to answer thecalls, thereby eliminating suspicion or preventing emergency calls from being omitted; and (4), for harassment / fraud calls which are judged to belong to the black list, directly hanging up the calls,or switching to a training / punishment mode. Time consumption and communication cost of harassment parties are increased, and the method and the system become a training tool for a question-answer-robot.
Owner:张力予
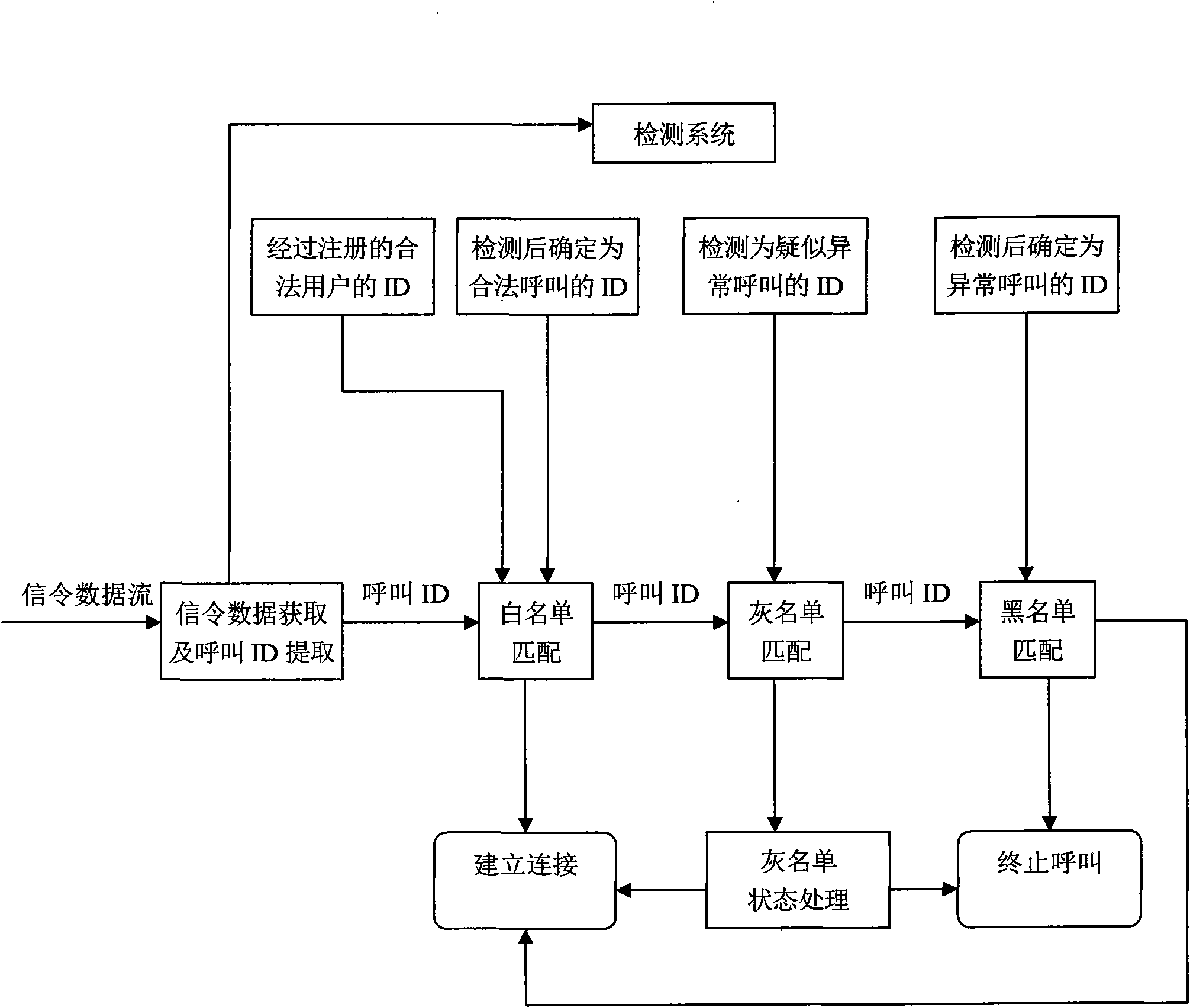
Method for filtering abnormal call based on multiple lists
InactiveCN101938583AImplement automatic updatesFree from harassmentInterconnection arrangementsUnauthorised/fraudulent call preventionProcess mechanismGrey list
The invention discloses a method for filtering an abnormal call based on multiple lists. The abnormal call can be timely interrupted and connection is quickly established for a legal user, namely a normal call by matched filtering based on multiple lists such as a white list, a grey list and a black list. In addition, the state processing mechanism of the grey list is adopted to realize automaticupdating of the state in the grey list. Meanwhile, multiple list-based matched filtering and the detection process are concurrently executed, so the abnormal call can be filtered on line, abnormalityis timely discovered and the connection is terminated to prevent a called user from being disturbed.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Anti-fraud and anti-harass fixed-line telephone based on intelligent question-answering system
InactiveCN109348037AAvoid interferenceAvoid delaySpecial service for subscribersSubstation equipmentGrey listTelephone network
The invention relates to an anti-fraud and anti-harass fixed-line telephone based on an intelligent question-answering system. A grey list and an intelligent question-answering module are arranged inthe fixed-line telephone, and the fixed telephone comprises the following operations: for each dialed-in number, performing matching on the numbers in the white list, the black list and the gray listaccording to the number through the intelligent question-answering module, if the matching is successful, judging the dialed-in number as the known number in the white list if the matching is successful, and ringing to notify a telephone owner to answer; judging the dialed-in number as the known telephone in the blacklist if the matching is successful, and directly rejecting the dialed-in number;judging the dialed-in number as the known telephone in the grey list if the matching is successful, or judging as the strange number if the matching is unsuccessful, and starting a robot to perform intelligent question-answering with a caller; extracting marker words according to the question-answering content, and judging whether rings to notify the owner or adds in the grey list or adds in the black list through marker words matching. The telephone disclosed by the invention can effectively judge whether the strange incoming call is a harass telephone, thereby avoiding the condition that theowner is harassed due to missed judgment or the normal telephone is missed due to misjudgment.
Owner:SOUTHEAST UNIV
Detection and analysis method for image emails
ActiveCN104270304AIncrease flexibilityQuick filterData switching networksPattern recognitionGrey list
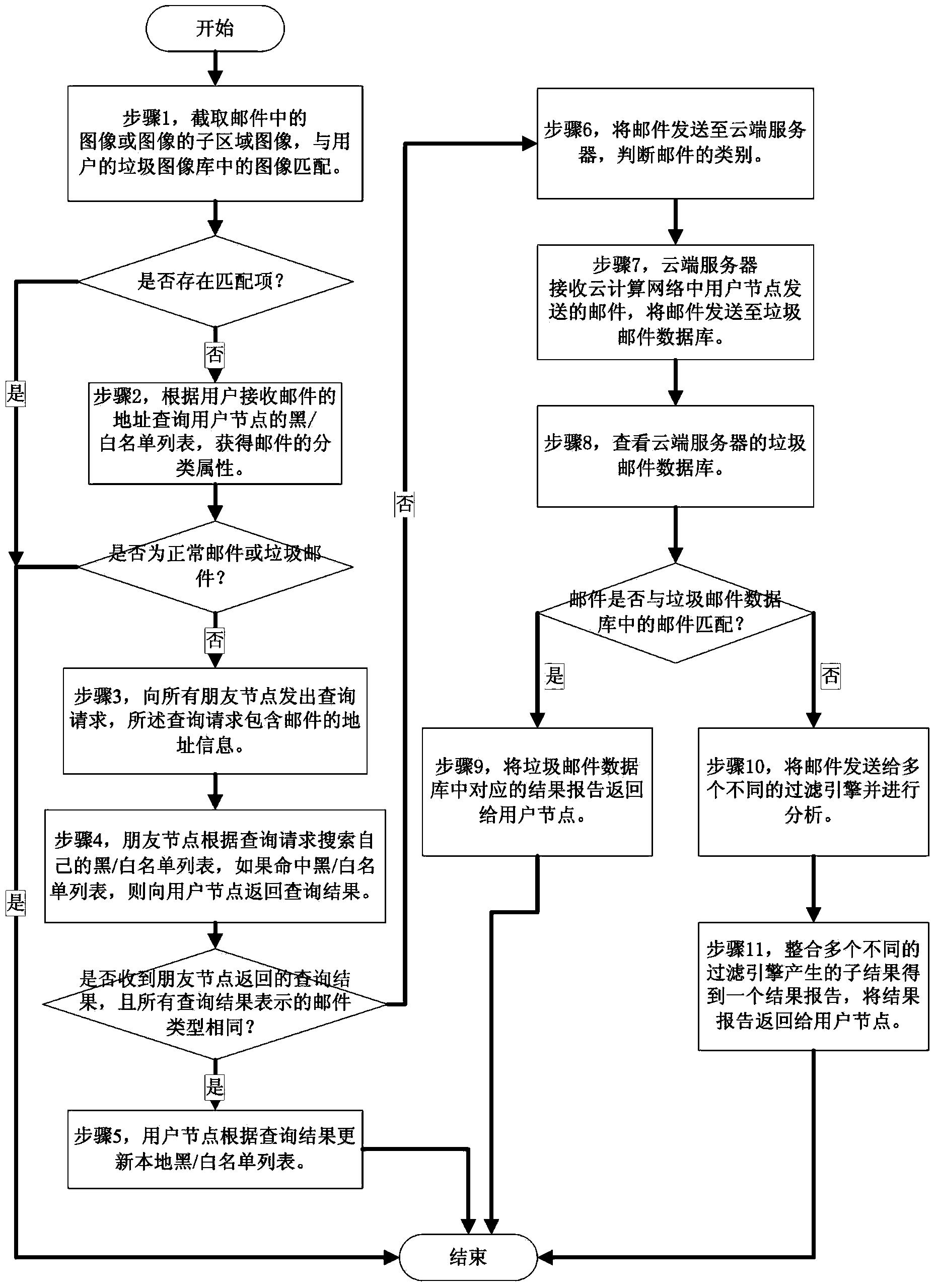
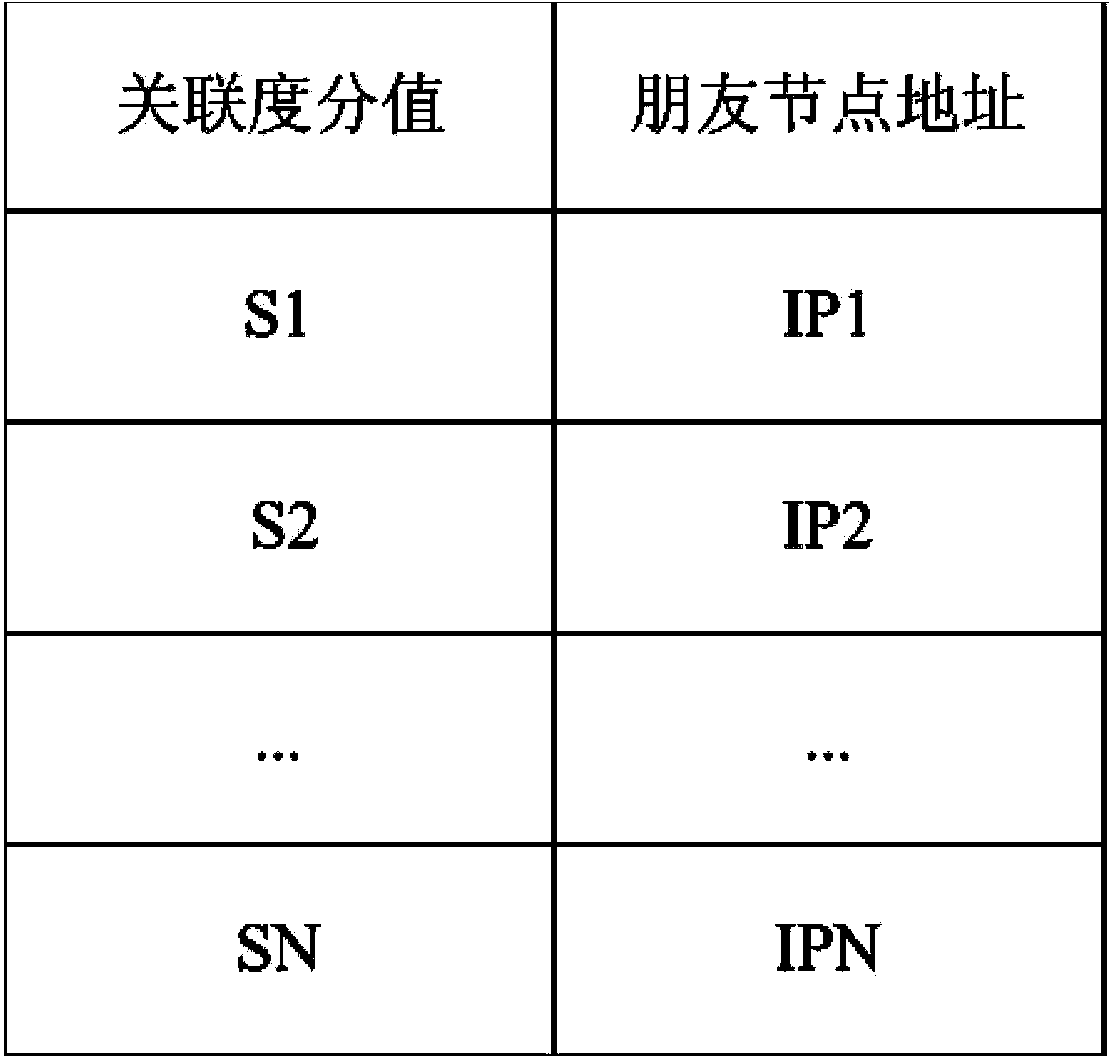
The invention relates to a detection and analysis method for image emails. The method is used for detection and analysis on the basis of images in the emails and other content attributes of the emails. The method comprises the steps that firstly, images or subdomain images in the emails are intercepted to be matched with a spam image library of a user, and if matching succeeds, the emails are regarded as spam emails, or a blacklist and a whitelist of the user and a grey list based on the credibility score are searched, and the categories of the emails are obtained; the categories of the emails of which the categories can not be determined are obtained by inquiring a blacklist and a whitelist of friend nodes in the network, wherein the friend nodes are the network nodes having higher email interaction frequency with the current user node; the emails can also be sent to a cloud server for category judgment. The method can effectively detect and filter spam images in the emails, and can carry out multilevel and multi-grade comprehensive detection and analysis on the emails.
Owner:四川神虎科技有限公司
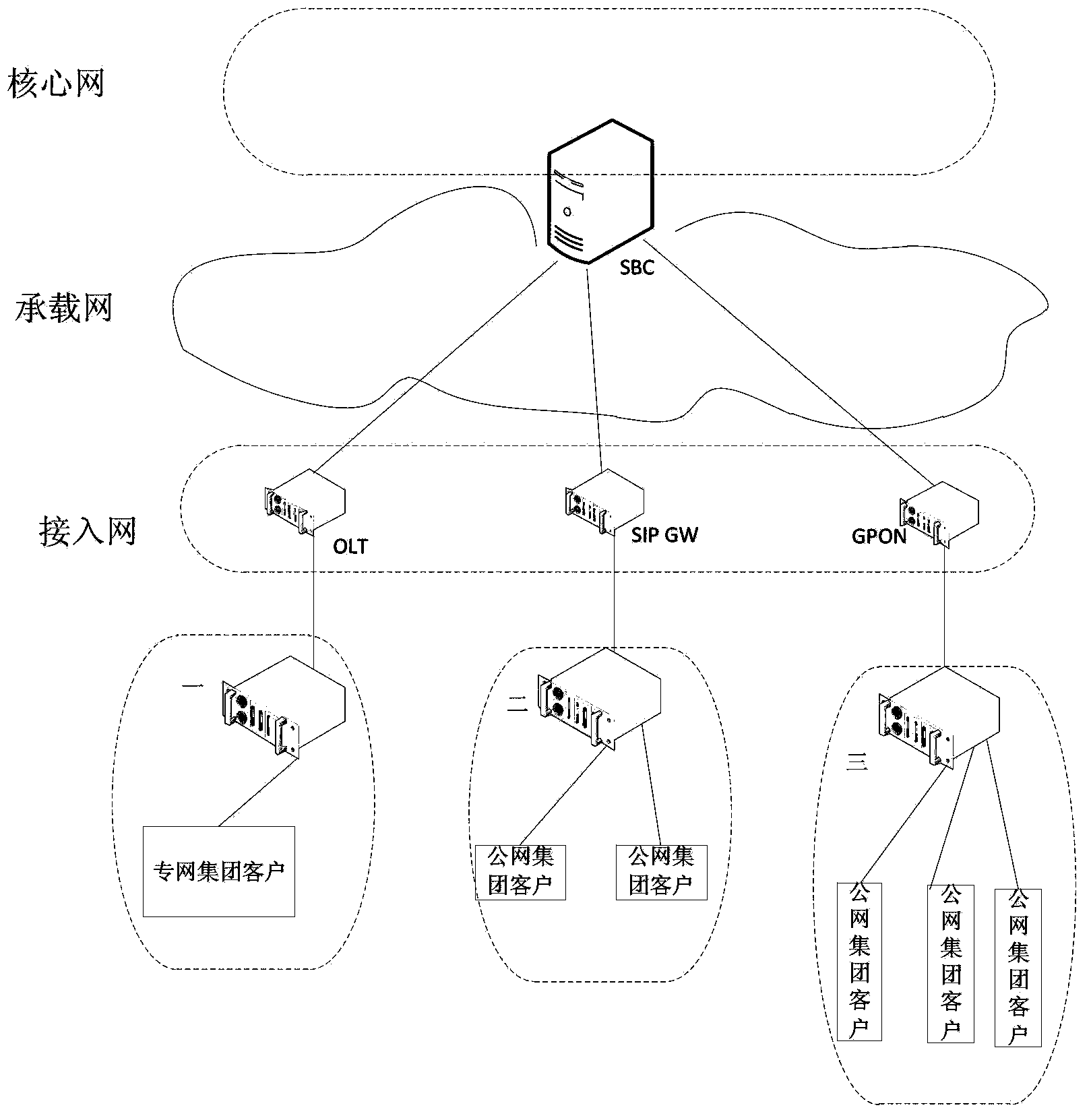
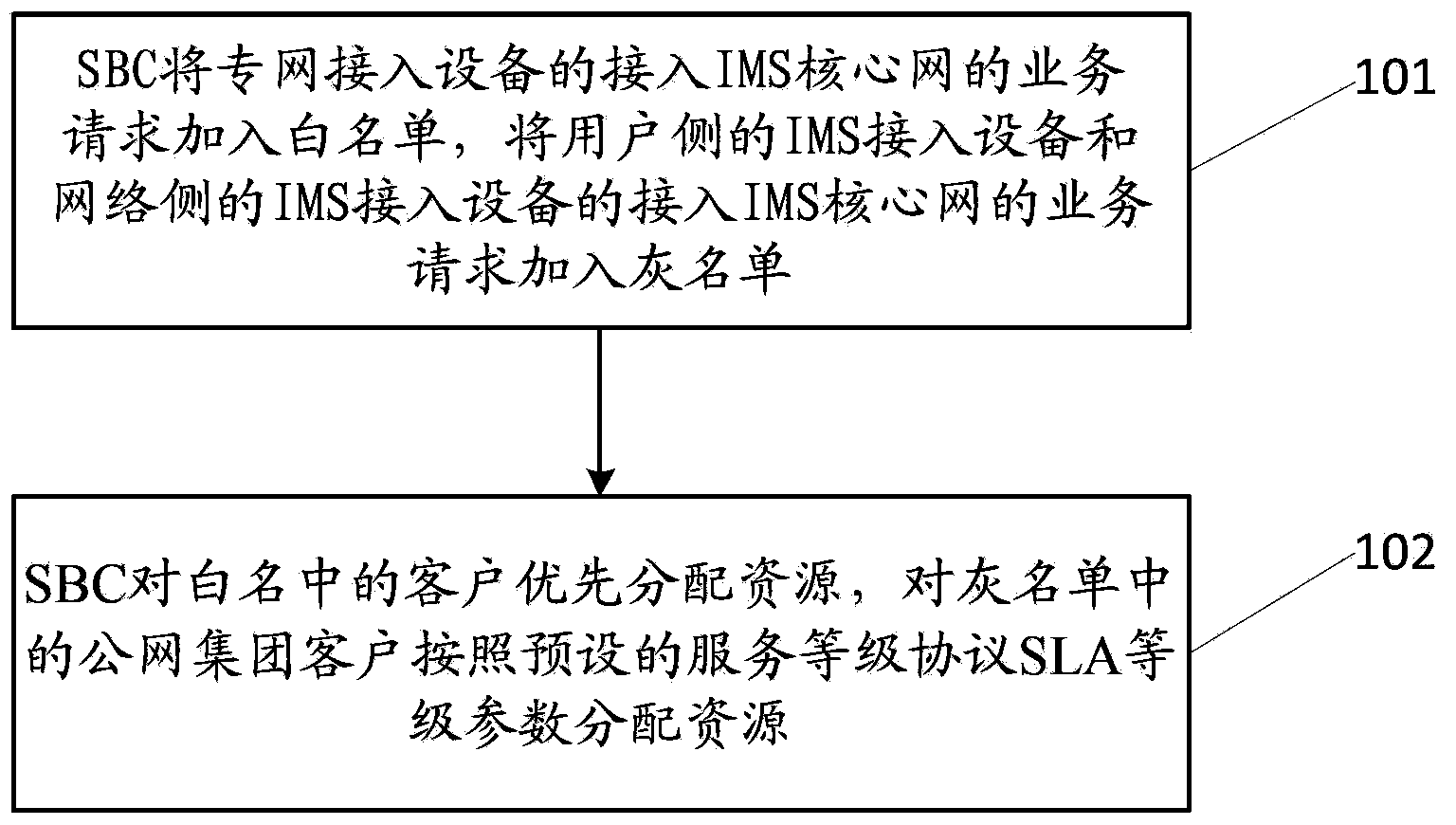
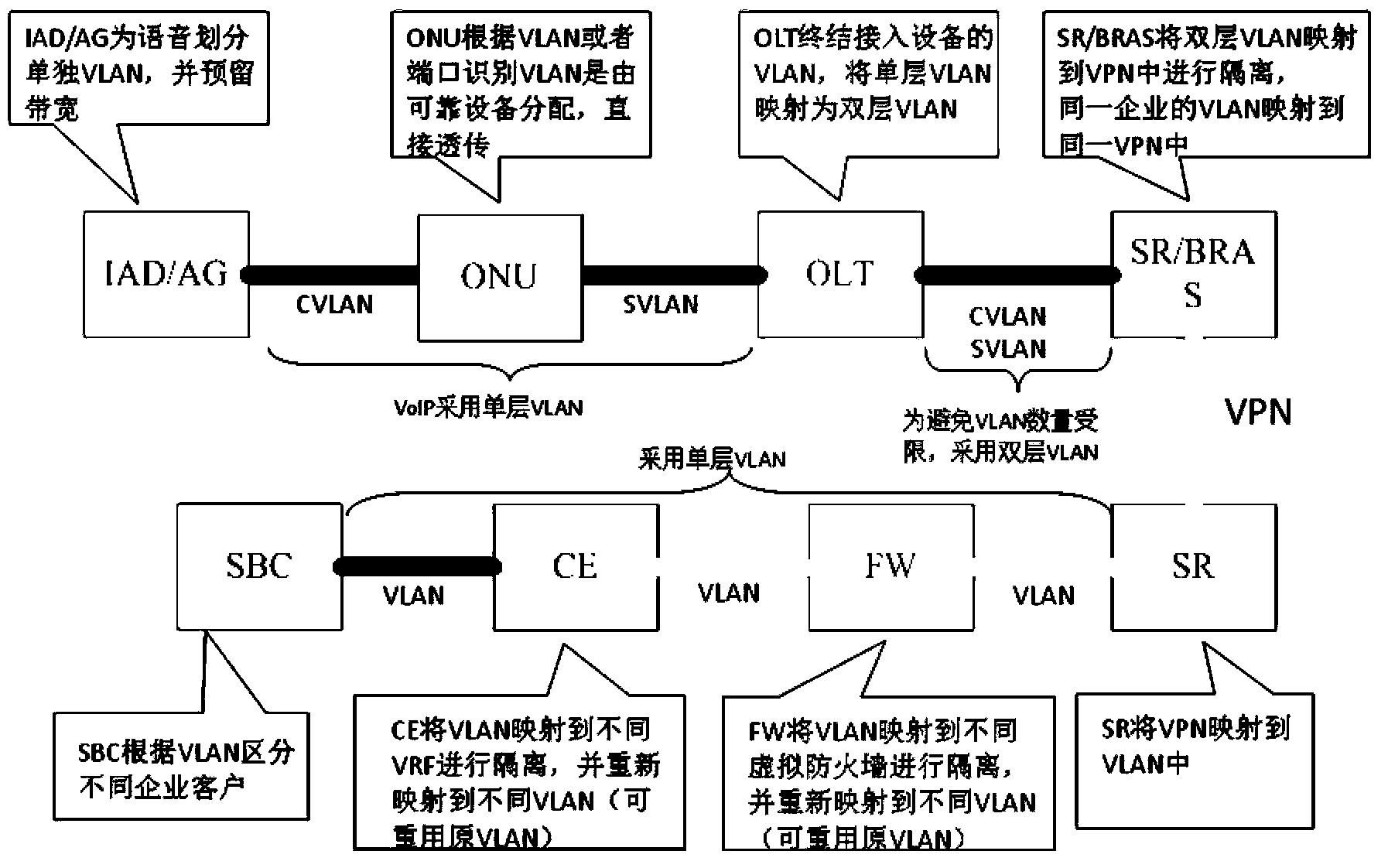
SLA level implement method and system for IMS service group customer
The invention discloses an SLA level implement method and system for an IMS service customer, relates to the field of communication technology, and solves the technical problem that different SLA levels cannot be provided to IMS service group customers according to customer needs in the prior art. In the method, an SBC receives a service request of an IMS core network accessed to a private network access device, and adds a group customer who sends the service request as a private network group customer into a white list; the SBC receives a service request of an IMS core network accessed to an access device other than a private network receiving device, and adds a group customer who sends the service request as a public network group customer into a gray list; and the SBC allocates resources first for the private network group customer in the white list, and then allocates resources for the public network group customer in the gray list according to set service level agreement (SLA) level parameters.
Owner:CHINA MOBILE GRP BEIJING
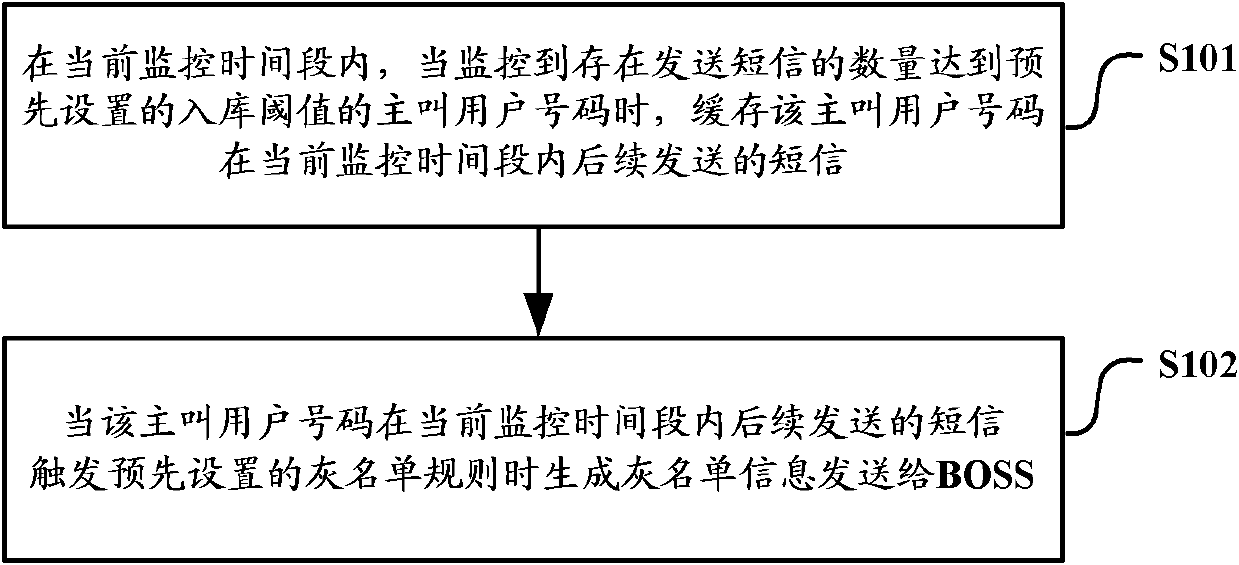
Method and system for monitoring junk short message
ActiveCN102572747AAccurately determine informationValid judgment informationMessaging/mailboxes/announcementsTime rangeTelecommunications
The invention discloses a method and a system for monitoring a junk short message, which are used for providing judging information of a sending source of a junk short message accurately and effectively for a business operation support system (BOSS). The method for monitoring the junk short message includes that in a current monitoring time range, when a calling party number sending short messages with quantity reaching a preset base-entering threshold is monitored to exist, following short messages sent by the calling party number are cached; when the following short messages sent by the calling party number in the current monitoring time range trigger a preset grey list rule, generated grey list information is sent to the BOSS. The grey list information comprises the calling party number and reason parameters determined according to the triggered grey list rule.
Owner:CHINA MOBILE GROUP JILIN BRANCH
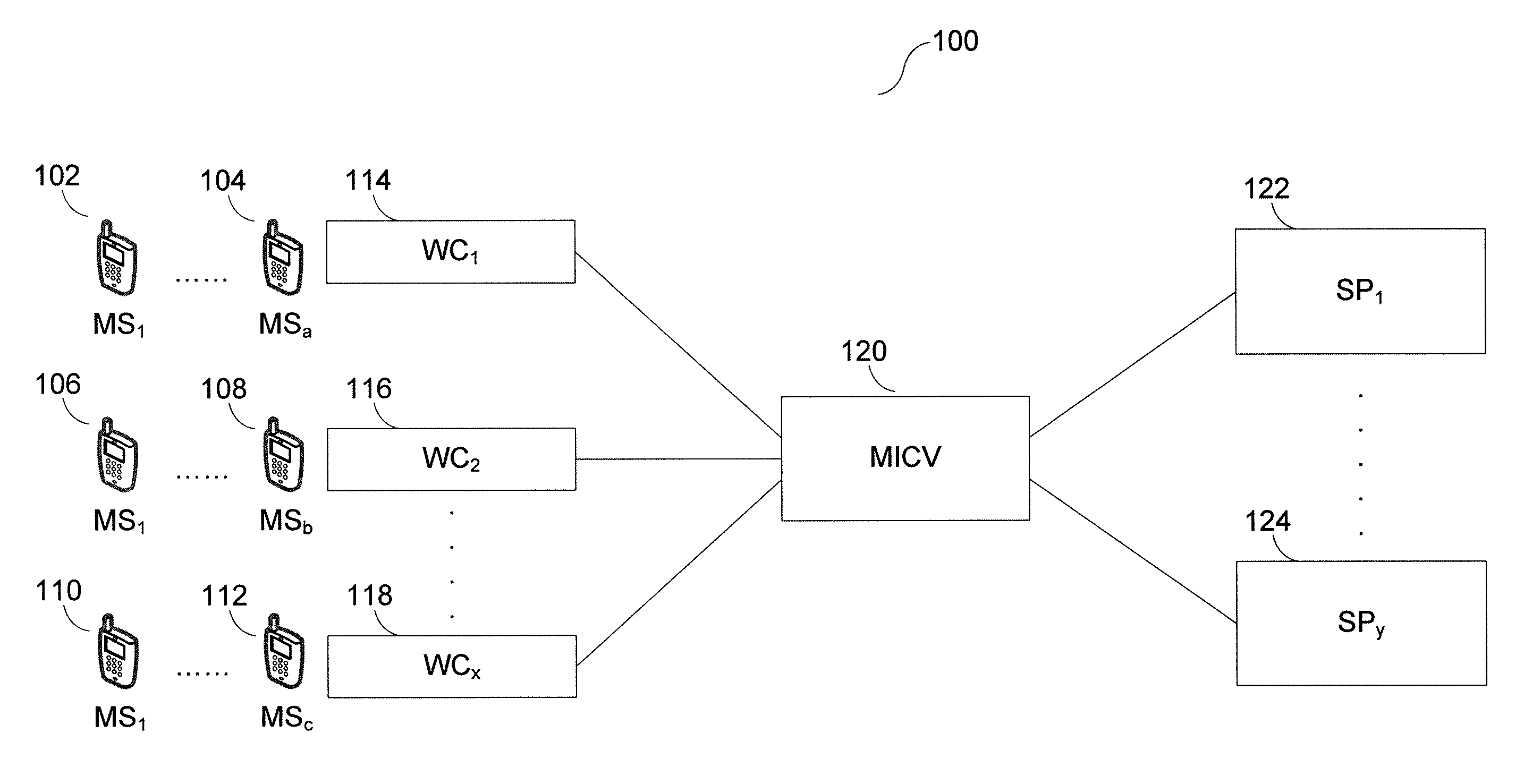
System and Method for Dynamic Spam Detection
ActiveUS20130303204A1Messaging/mailboxes/announcementsWireless commuication servicesProtocol for Carrying Authentication for Network AccessMessage service
A flexible, extensible, and dynamically configurable anti-spam facility that operates on a general quanta of data (such as for example a Short Message Service message, a Multimedia Message Service message, an Internet Protocol Multimedia Subsystem message, a Wireless Application Protocol stream, an Electronic Mail message, an Instant Messaging exchange, streaming (audio, video, etc.) data, etc.), innovatively analyzes various attributes of same (such as for example originating address and destination address), and—when an instance of spam is identified—performs one or more remediation activities (such as for example updating a blacklist, updating a greylist, dropping a message, issuing an alert, etc.). The facility may optionally leverage the capabilities of a centrally-located Messaging Inter-Carrier Vendor.
Owner:SYBASE 365 INC
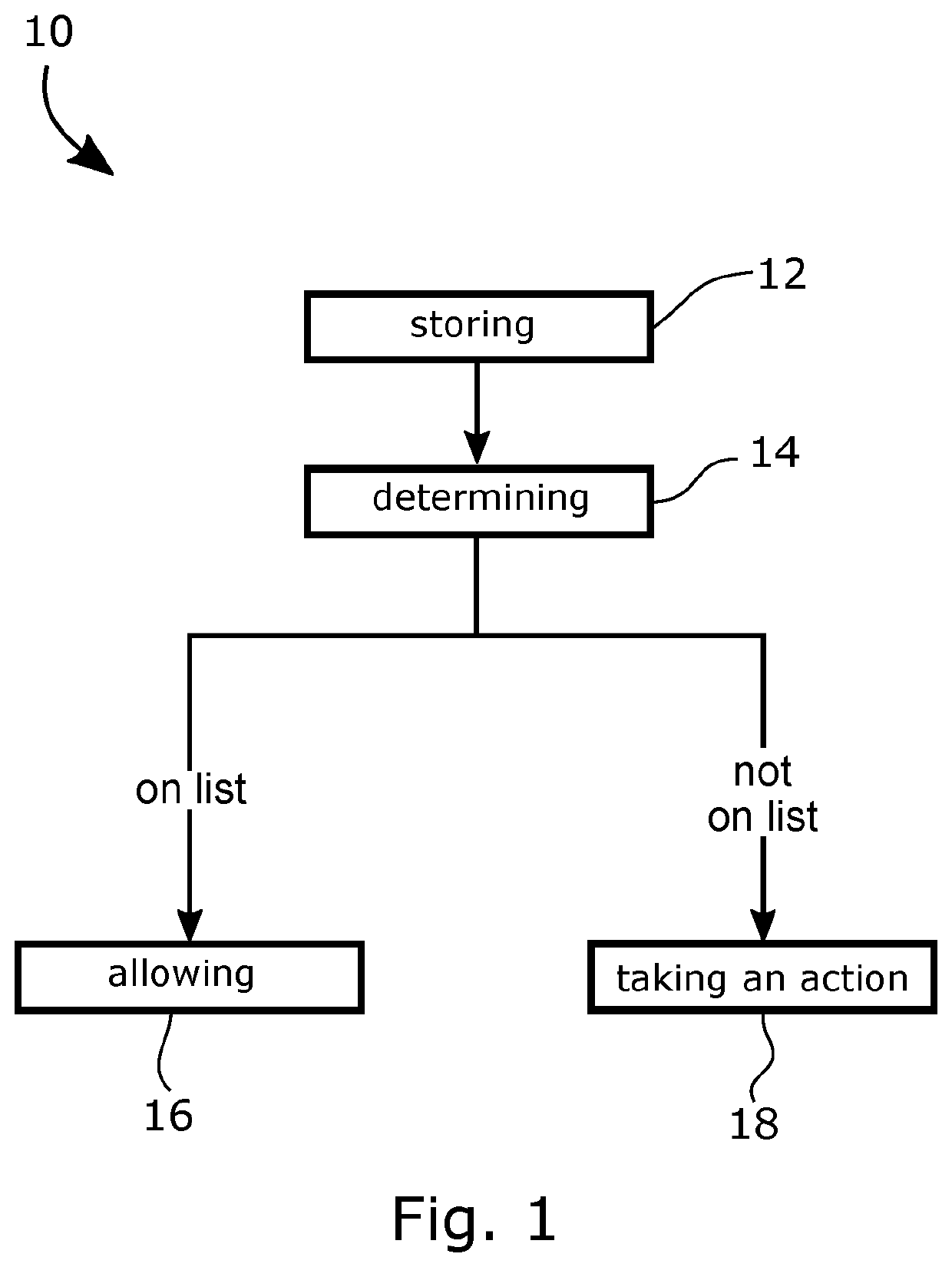
System and method for limiting incoming spam calls
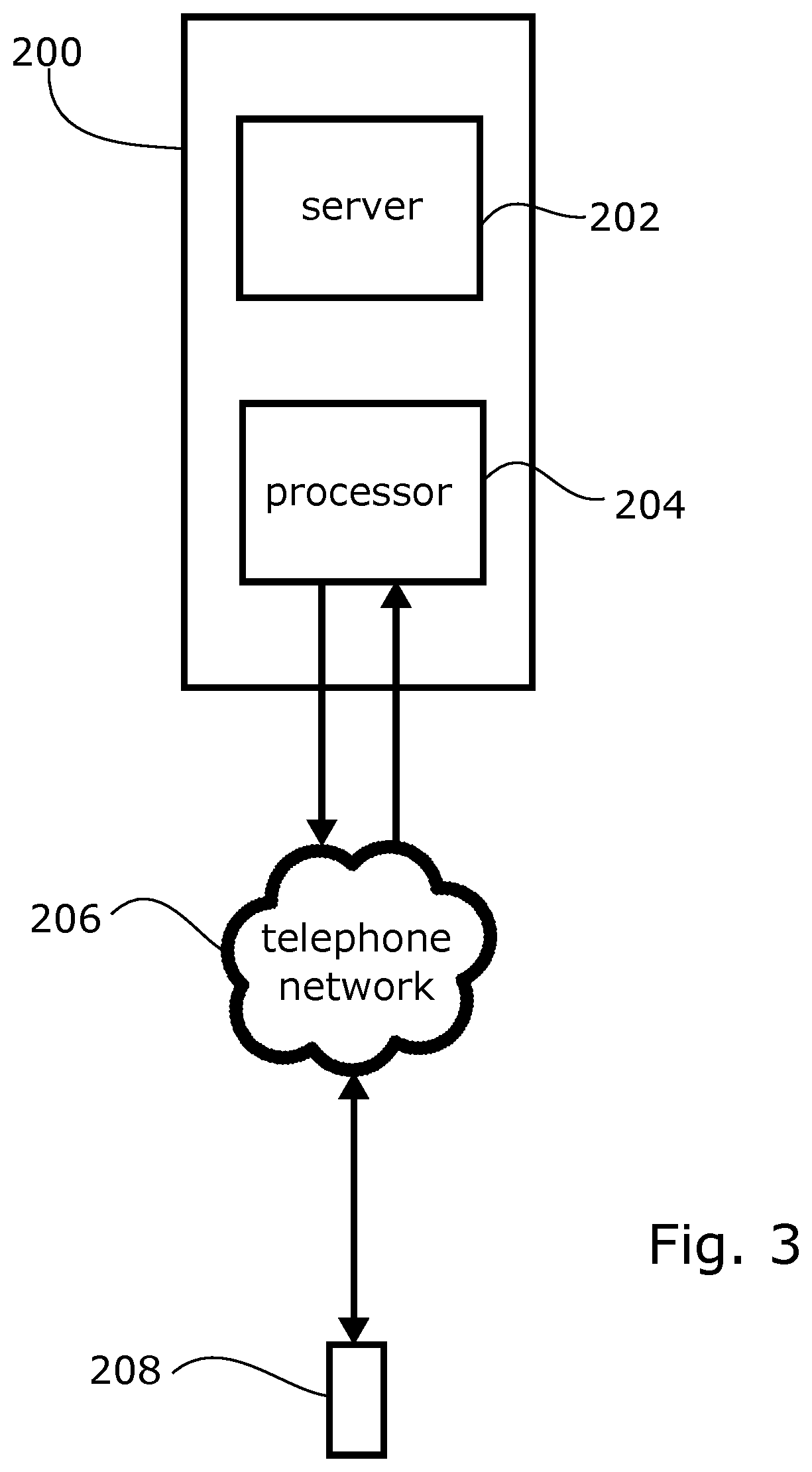
ActiveUS10523815B1Special service for subscribersCalled number recording/indicationGrey listSpamming
A system and method for maintaining a grey list for controlling incoming calls from numbers on a telephone network. Information associated with previous calls received by the telephone is stored in the form of a grey list. The stored information includes an indication of whether each of the previously received calls passed a previous challenge. Based on the stored information, when an incoming call is received, a determination is made whether the incoming call corresponds to a call that passed a previous challenge. The incoming call connected to the telephone if the stored information indicates that the incoming call previously passed a challenge. An action is taken if the stored information does not indicate that the incoming call previously passed the challenge. The action may include blocking the call, allowing the call or providing a current challenge to the call.
Owner:TELUS HLDG 2023 INC
System and method for limiting incoming spam calls
A system and method for maintaining a grey list for controlling incoming calls from numbers on a telephone network. Information associated with previous calls received by the telephone is stored in the form of a grey list. The stored information includes an indication of whether each of the previously received calls passed a previous challenge. Based on the stored information, when an incoming call is received, a determination is made whether the incoming call corresponds to a call that passed a previous challenge. The incoming call connected to the telephone if the stored information indicates that the incoming call previously passed a challenge. An action is taken if the stored information does not indicate that the incoming call previously passed the challenge. The action may include blocking the call, allowing the call or providing a current challenge to the call.
Owner:TELUS HLDG 2023 INC
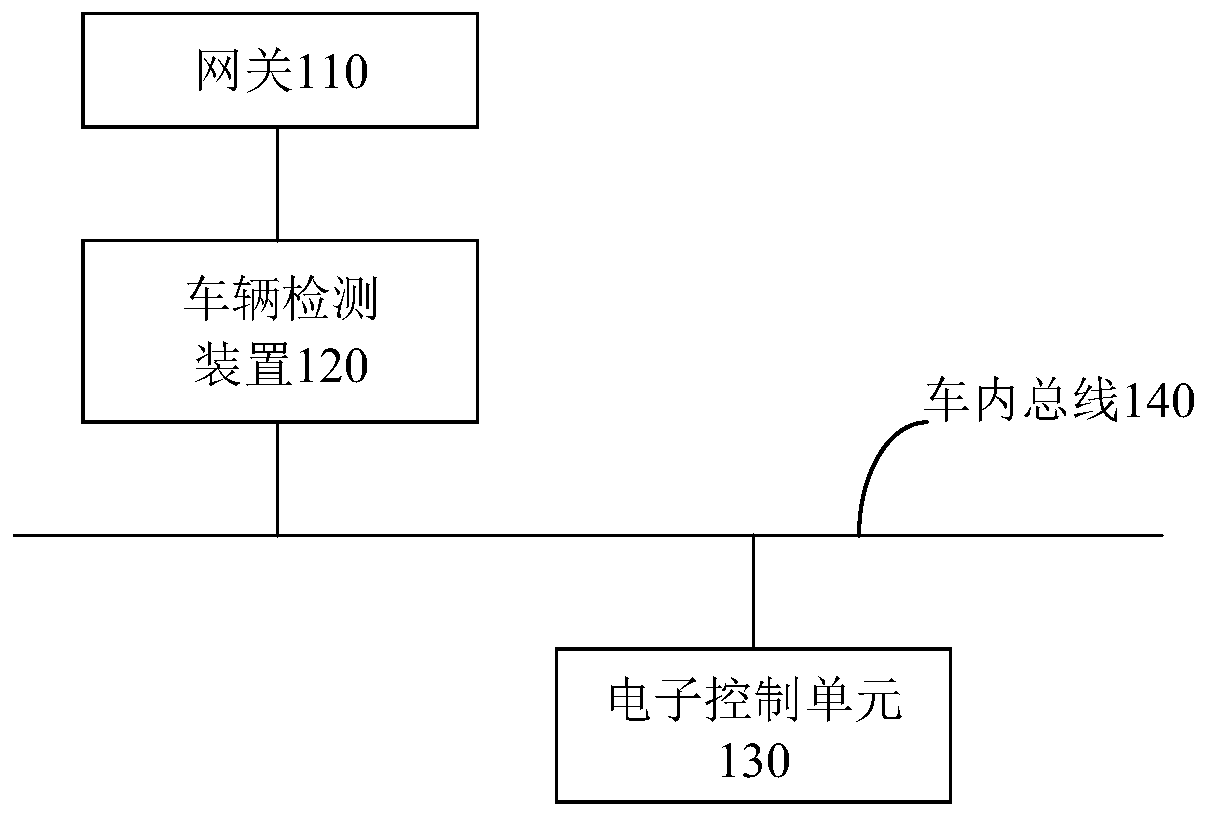
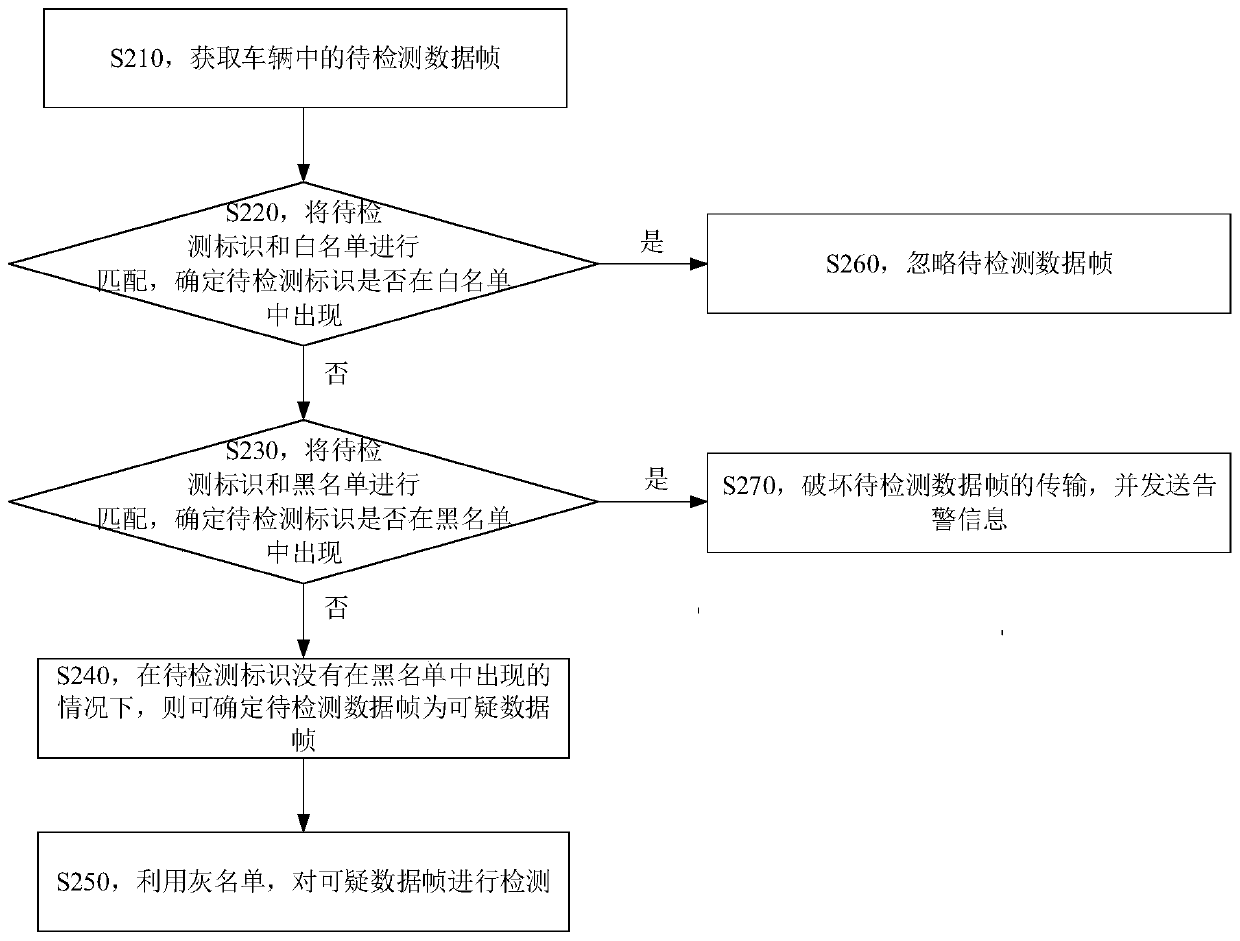
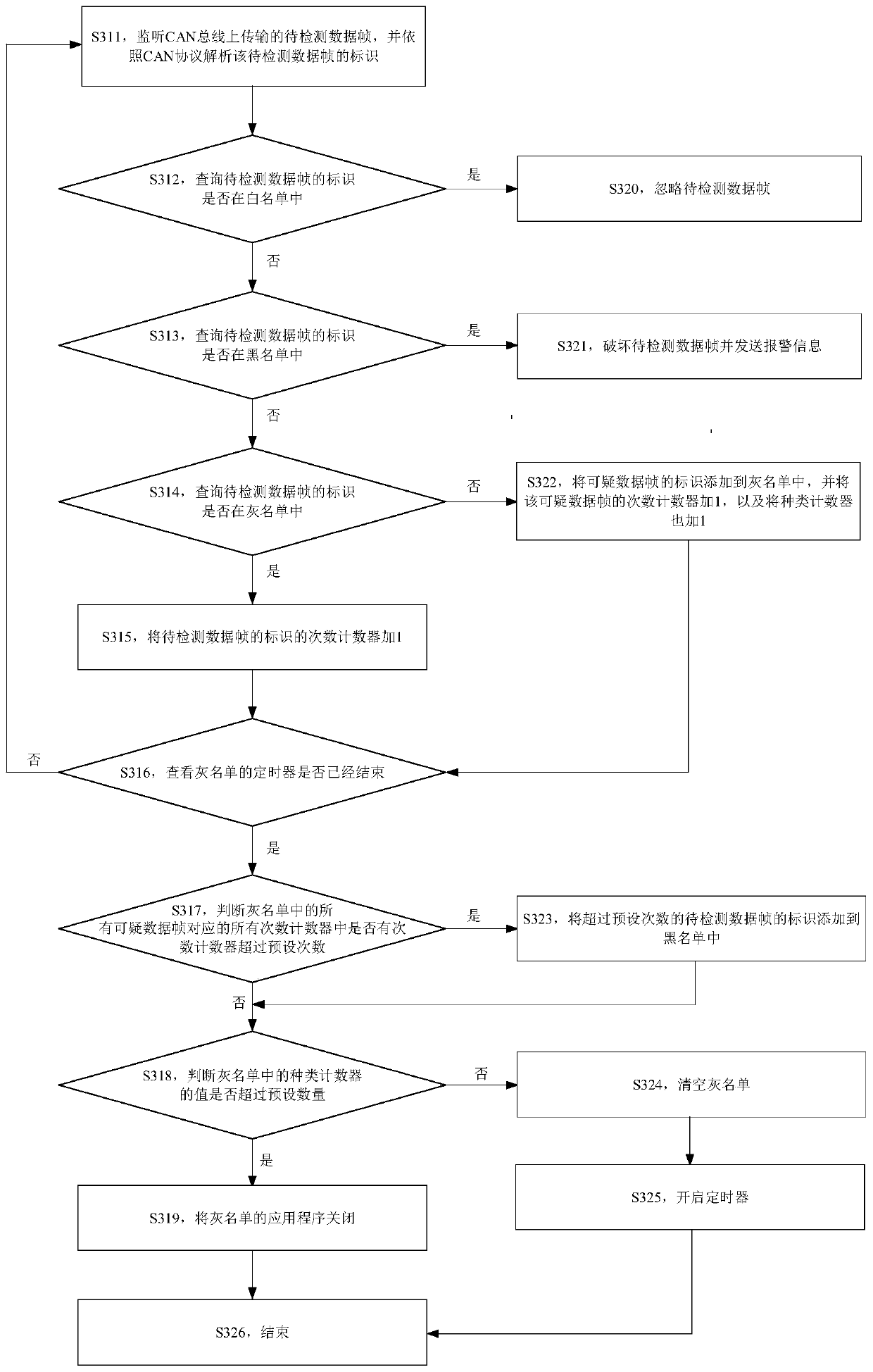
Vehicle detection method and device, storage medium and electronic equipment
ActiveCN111352761AExpand coverageDiversification of countermeasuresInternal combustion piston enginesFault responseGrey listEngineering
The embodiment of the invention provides a vehicle detection method and device, a storage medium and electronic equipment, and the method comprises the steps: obtaining a to-be-detected data frame ina vehicle, and obtaining a to-be-detected identification of the to-be-detected data frame; matching the to-be-detected identifier with the white list, and determining whether the to-be-detected identifier appears in the white list or not; when the to-be-detected identifier does not appear in the white list, matching the to-be-detected identifier with the blacklist, and determining whether the to-be-detected identifier appears in the blacklist or not; under the condition that the to-be-detected identifier does not appear in the blacklist, determining that the to-be-detected data frame is a suspicious data frame; and detecting the suspicious data frames by utilizing the grey list. According to the embodiment of the invention, black, white and gray three-level classification is carried out onthe identifier of the to-be-detected data frame on the in-vehicle bus, so the coverage range can be improved. Moreover, the to-be-detected data frame can be detected through the obtained white list,black list and grey list, so diversified measures can be taken.
Owner:BEIJING TOPSEC NETWORK SECURITY TECH +2
Method and device for controlling access to mobile telecommunications networks
ActiveUS20140128028A1Avoid equipmentUnauthorised/fraudulent call preventionAssess restrictionTelecommunications networkGrey list
To control access by any given mobile terminal to a mobile telecommunications network, a smartcard (i.e. a SIM) is arranged to include a list of device identifiers corresponding to one or more mobile terminals together with an indication of their respective access categories (i.e. black-list, grey-list or white-list). This list is constructed from an updated list of identifiers of mobile devices into which the smartcard has been inserted. This may be enhanced with a limited number of generic excluded identifiers. The smartcard thus maintains a local database of banned devices and / or devices that need to be monitored by the network.
Owner:VODAFONE IP LICENSING
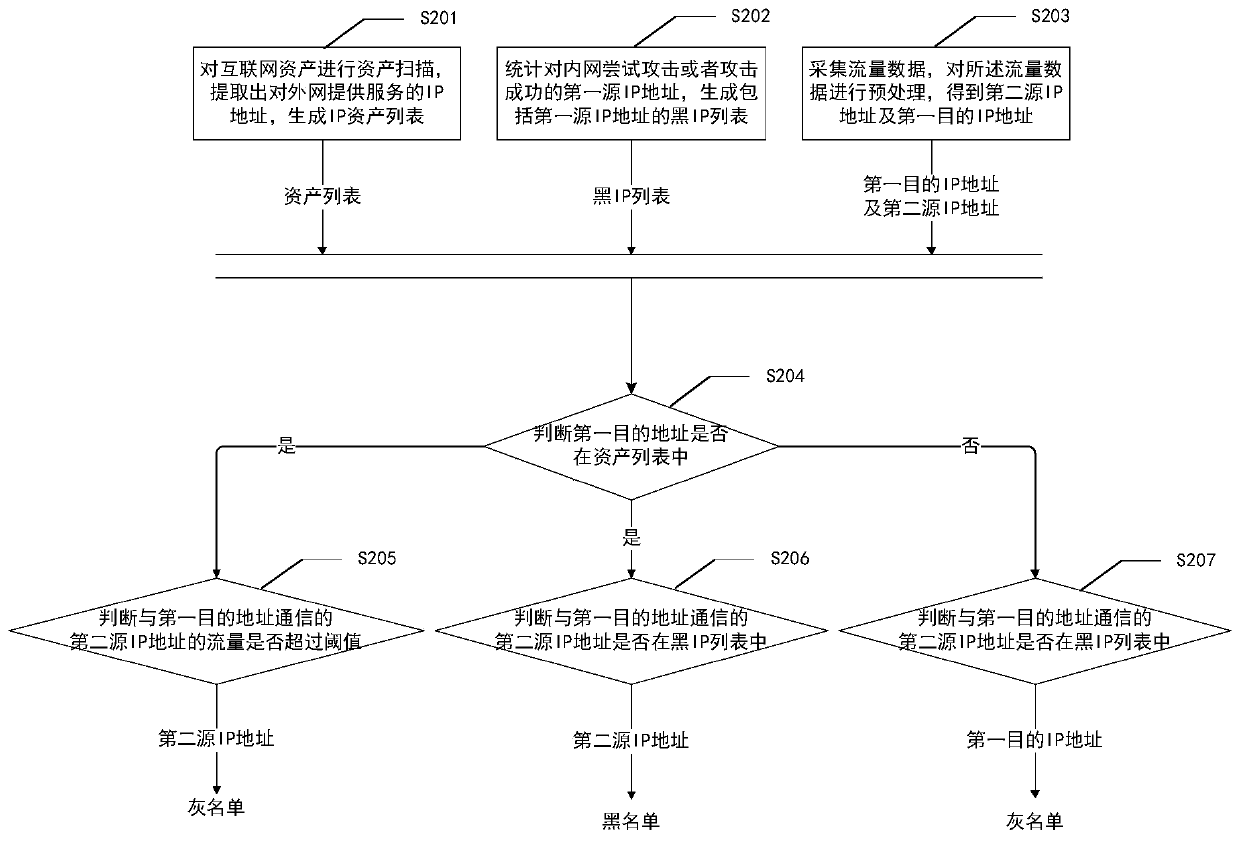
IP credit calculation method and device, electronic equipment and medium
The IP credit calculation method comprises the steps of performing asset scanning on Internet assets, extracting an IP address for providing service for an external network, and generating an IP assetlist; counting a first source IP address attempting to attack the intranet or successfully attacking the intranet, and generating a black IP list; collecting flow data, and preprocessing the flow data to obtain a second source IP address and a first destination IP address; when the first destination IP address does not exist in the IP asset list, judging whether a second source IP address communicating with the first destination IP address exists in a black IP list, and if yes, adding the first destination IP address into a grey list; when the first destination IP address exists in the IP asset list, determining that the first destination IP address exists, judging whether a second source IP address communicated with the first destination IP address exists in a black IP list, if yes, adding the second source IP address into a blacklist, judging whether the flow of the second source IP address communicated with the first destination IP address exceeds a threshold value, and if yes, adding the second source IP address into a grey list.
Owner:CERNET CORP
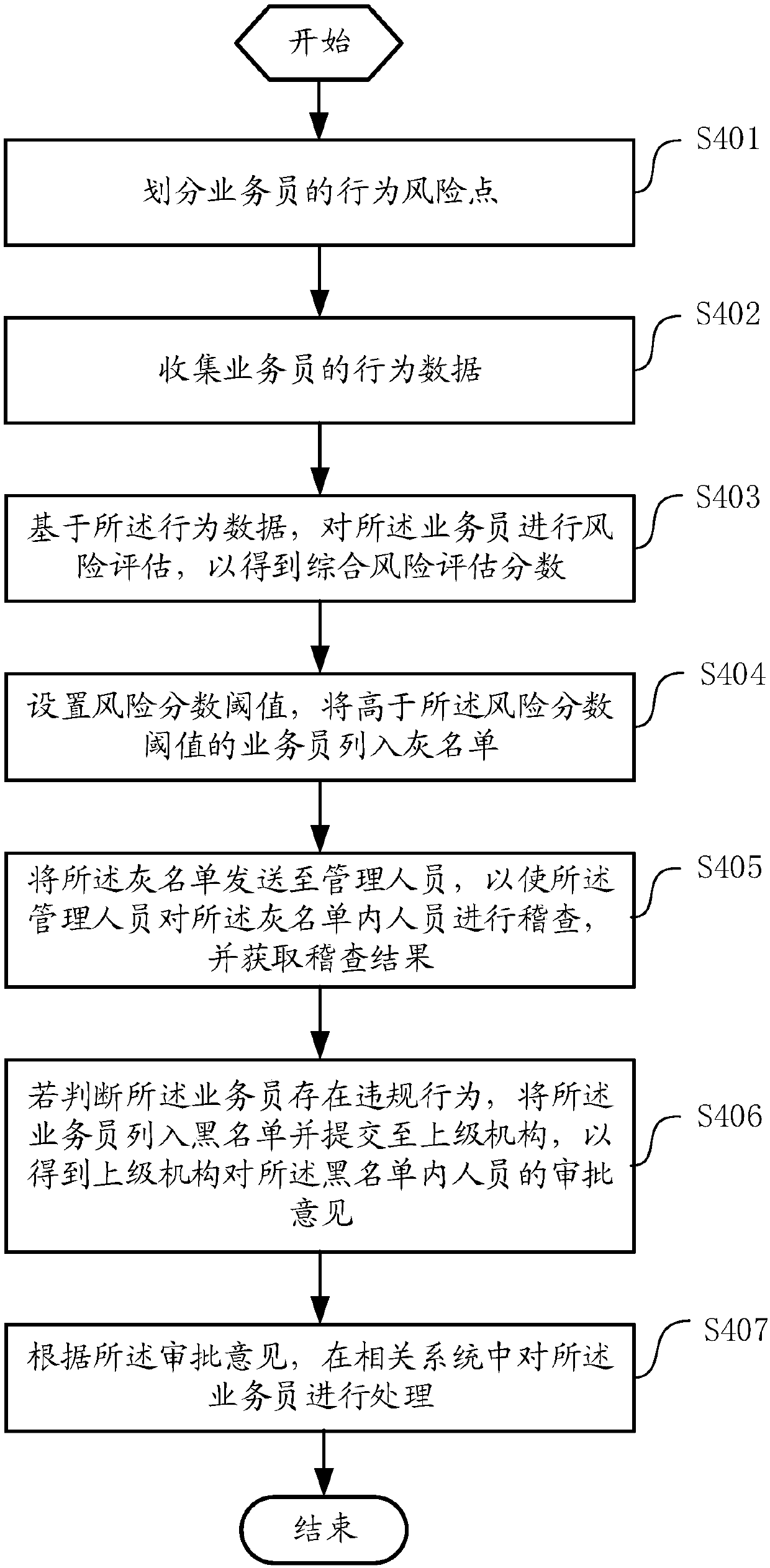
Salesman behavior risk discrimination management method, application server and computer readable storage medium
InactiveCN107871203ATimely processingPrevent proliferationFinanceResourcesApplication serverGrey list
The invention discloses a salesman behavior risk discrimination management method. The method comprises the following steps of: dividing behavior risk points of salesmen; collecting behavior data of the salesmen; carrying out risk assessment on the salesmen on the basis of the behavior data so as to obtain a comprehensive risk assessment scores; setting a risk score threshold value and enrolling the salesmen, the comprehensive risk assessment scores of which are higher than the risk score threshold value, into a grey list; sending the grey list to a manager and obtaining a processing result; if the salesmen have illegal behaviors, enrolling the salesmen into a black list and submitting the black list to a supervising authority so as to obtain approval opinions, for personnel in the black list, of the supervising authority; and processing the salesmen in a related system according to the approval opinions. The invention furthermore provides an application server and a computer readablestorage medium. According to the application server and the salesman behavior risk discrimination management method, risky salesmen can be timely recognized and processed, so that diffusion is prevented and company loss is reduced.
Owner:PING AN TECH (SHENZHEN) CO LTD
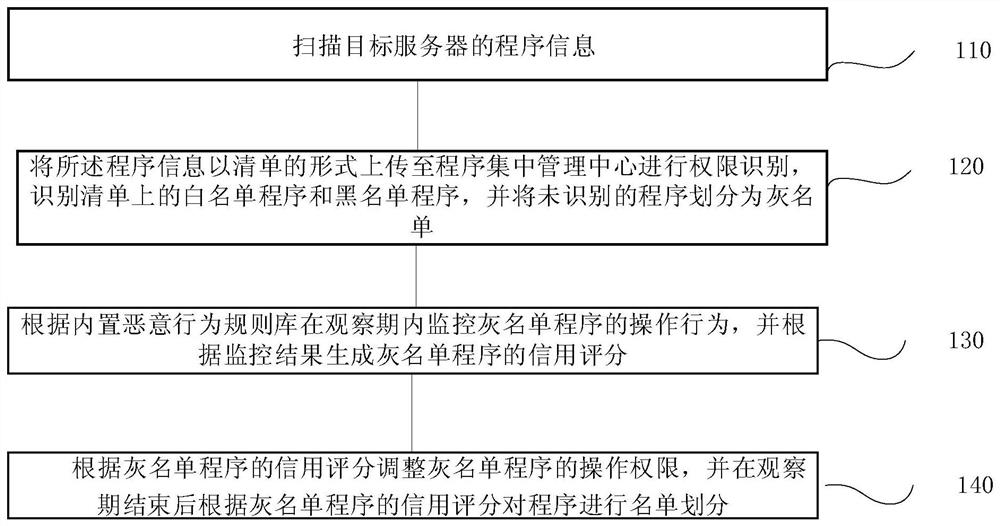
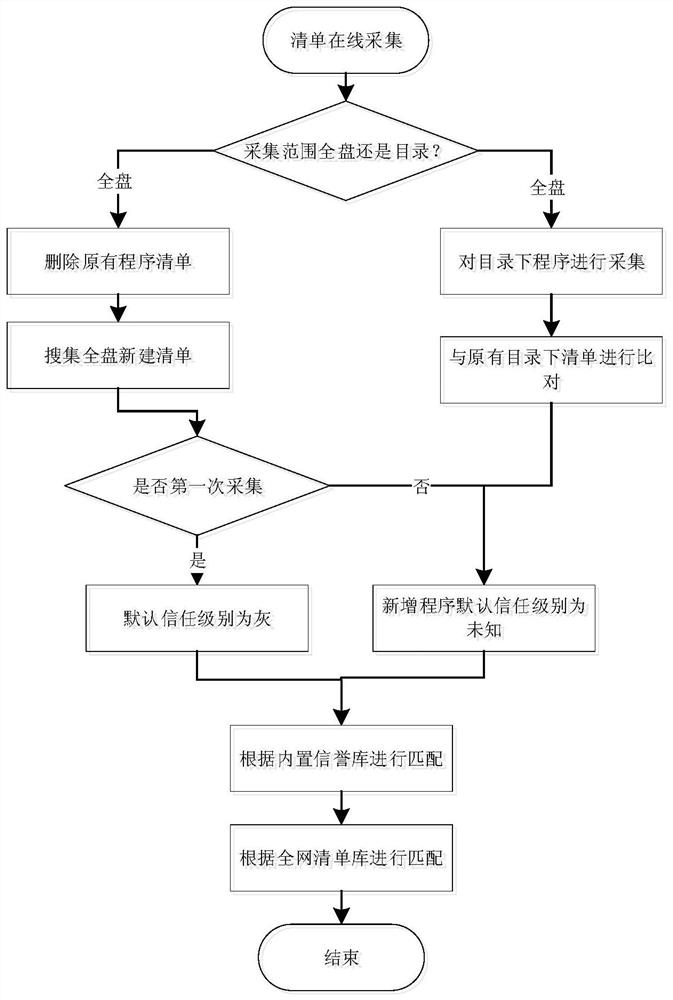
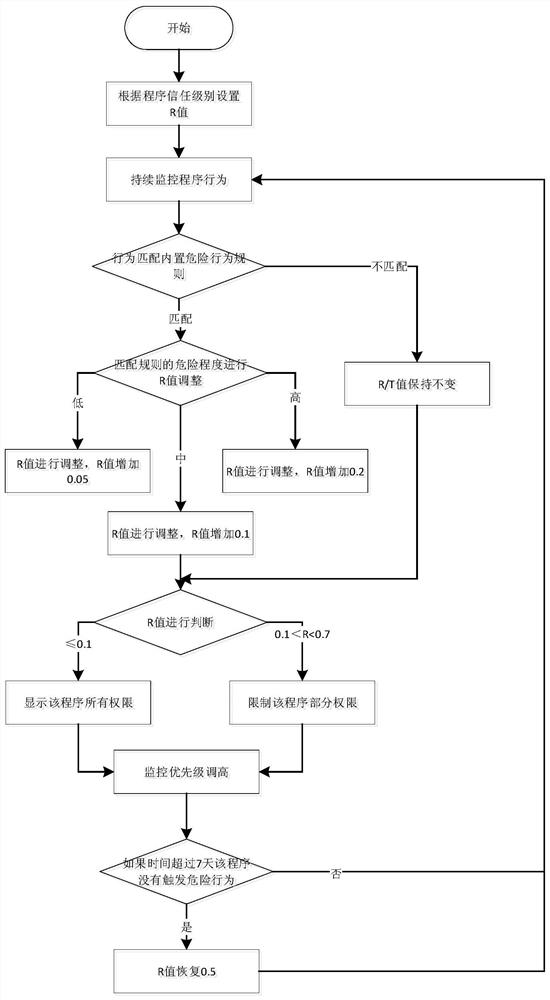
White list self-adapting program management method and system, terminal and storage medium
InactiveCN113722703AGuaranteed continuityEnsure safetyPlatform integrity maintainanceProgram managementGrey list
The invention provides a white list self-adapting program management method and system, a terminal and a storage medium. The method comprises the following steps: scanning program information of a target server; uploading the program information to a program centralized management center in the form of a list for permission identification, identifying white list programs and black list programs on the list, and dividing unidentified programs into a grey list; monitoring operation behaviors of the grey list programs in an observation period according to a built-in malicious behavior rule base, and generating credit scores of the grey list programs according to monitoring results; and adjusting operation permissions of the grey list programs according to the credit scores of the grey list programs, and performing list division on programs according to the credit scores of the grey list programs after the observation period ends. According to the invention, the program list of all executable programs on a host is managed, so that attacks of unknown malicious software are effectively prevented, and continuity and safety of services are guaranteed to the maximum extent; and meanwhile, the operation and maintenance efficiency of safety operation and maintenance personnel is improved, and the operation and maintenance cost is reduced.
Owner:INSPUR SUZHOU INTELLIGENT TECH CO LTD
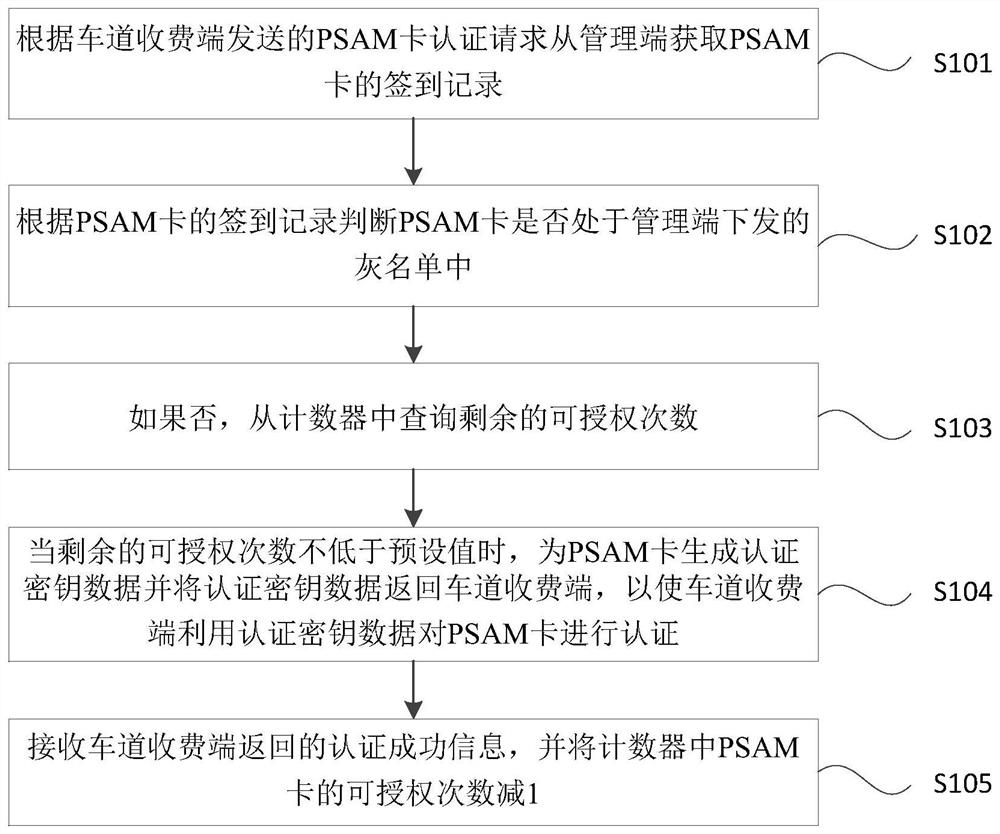
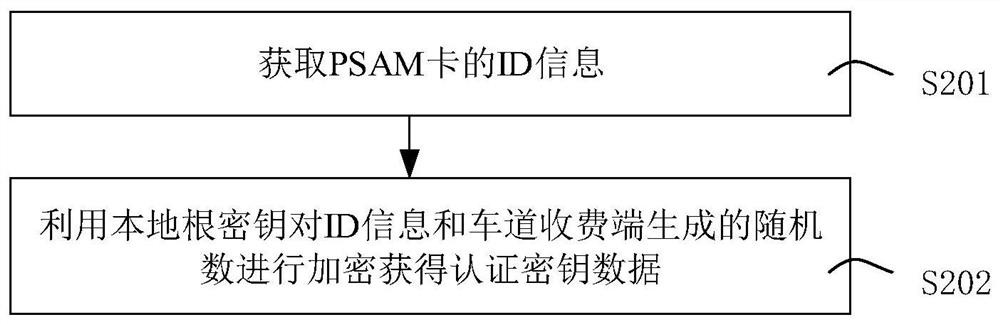
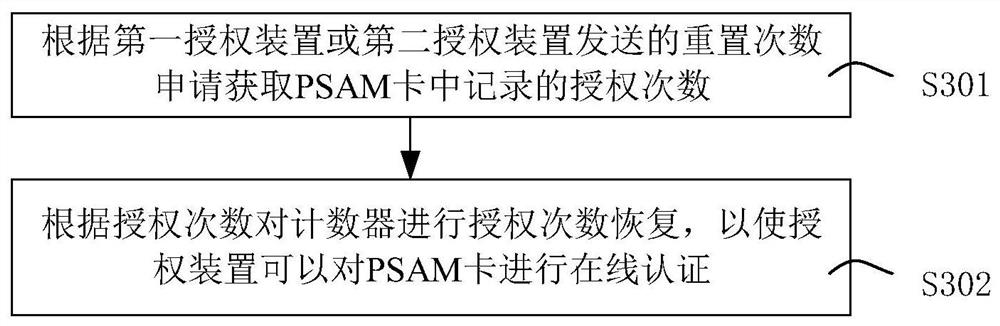
PSAM card two-stage online authorization authentication method, device and system
The invention provides a PSAM card two-stage online authorization authentication method, device and system. The method comprises the following steps: judging whether a PSAM card is in a sign-in grey list issued by a management end according to a PSAM card authentication request sent by a lane charging end; if not, inquiring the number of remaining authorizable times from the counter; when the number of remaining authorizable times is not lower than a preset value, generating authentication key data for the PSAM card and returning the authentication key data to the lane charging end so that the lane charging end uses the authentication key data to authenticate the PSAM card; and receiving authentication success information returned by the lane charging end, and subtracting 1 from the number of authorizable times of the PSAM card in the counter. According to the invention, a plurality of response paths are expanded for the PSAM authorization request sent by the lane charging system, the authorization request sent by the lane charging system can be responded in time no matter whether the network is normal or not, and the availability and network anomaly resistance of the system are improved.
Owner:北京中交国通智能交通系统技术有限公司
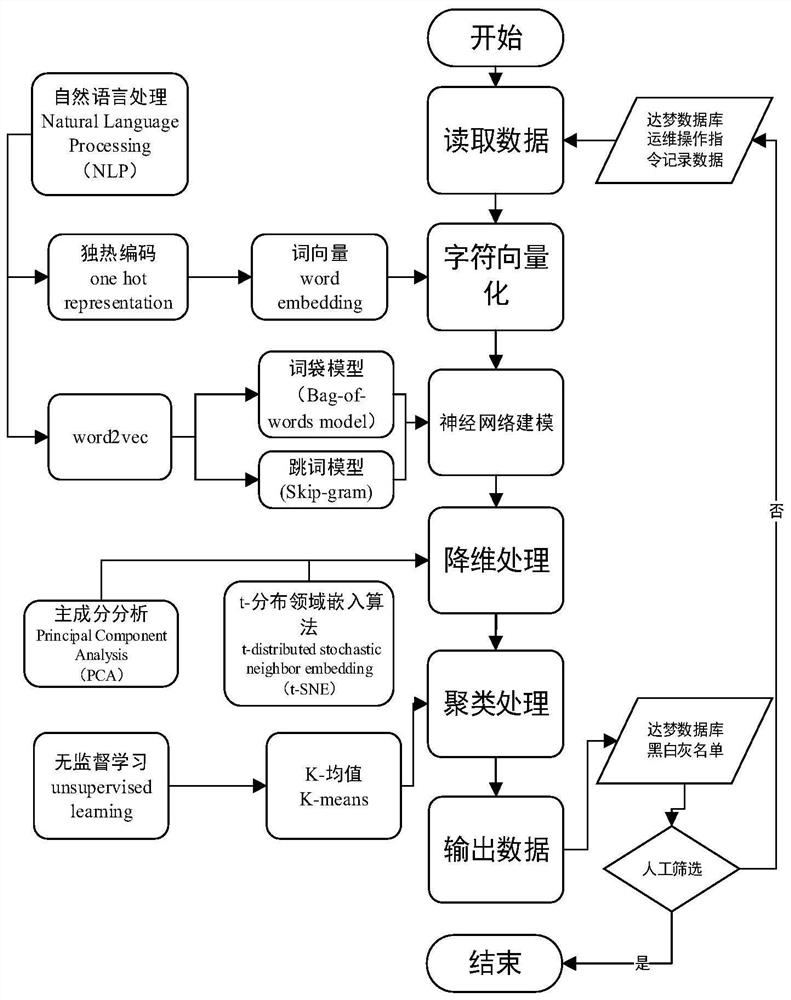
Operation and maintenance operation instruction security analysis method and system and storage medium
ActiveCN111611774AHigh degree of automationDiscover hidden risks in timeCharacter and pattern recognitionDigital data protectionData setGrey list
The invention discloses an operation and maintenance operation instruction security analysis method and system and a storage medium, and the method comprises the following steps: 1) reading historicaloperation instruction data, and carrying out character vectorization of a character set of the historical operation instruction data; 2) taking the vectorized operation instruction data as input, establishing a neural network model, and forming a mesh relation graph of the operation instruction data; 3) performing data dimension reduction processing on the operation instruction character data inthe mesh relation graph; 4) performing data clustering processing after the data dimension reduction processing is finished; and 5) performing definition and arrangement of black and white grey listson the operation and maintenance instruction data set clustered in the step 4) according to an actual service scene to form output data, and writing all black and white grey list output data into a specified database. According to the method, the problems of difficulty in manually labeling categories, excessively complicated labeling and the like in the operation and maintenance operation instruction security analysis process are solved, and the automation degree of operation and maintenance operation instruction security analysis is improved.
Owner:STATE GRID CORP OF CHINA +6
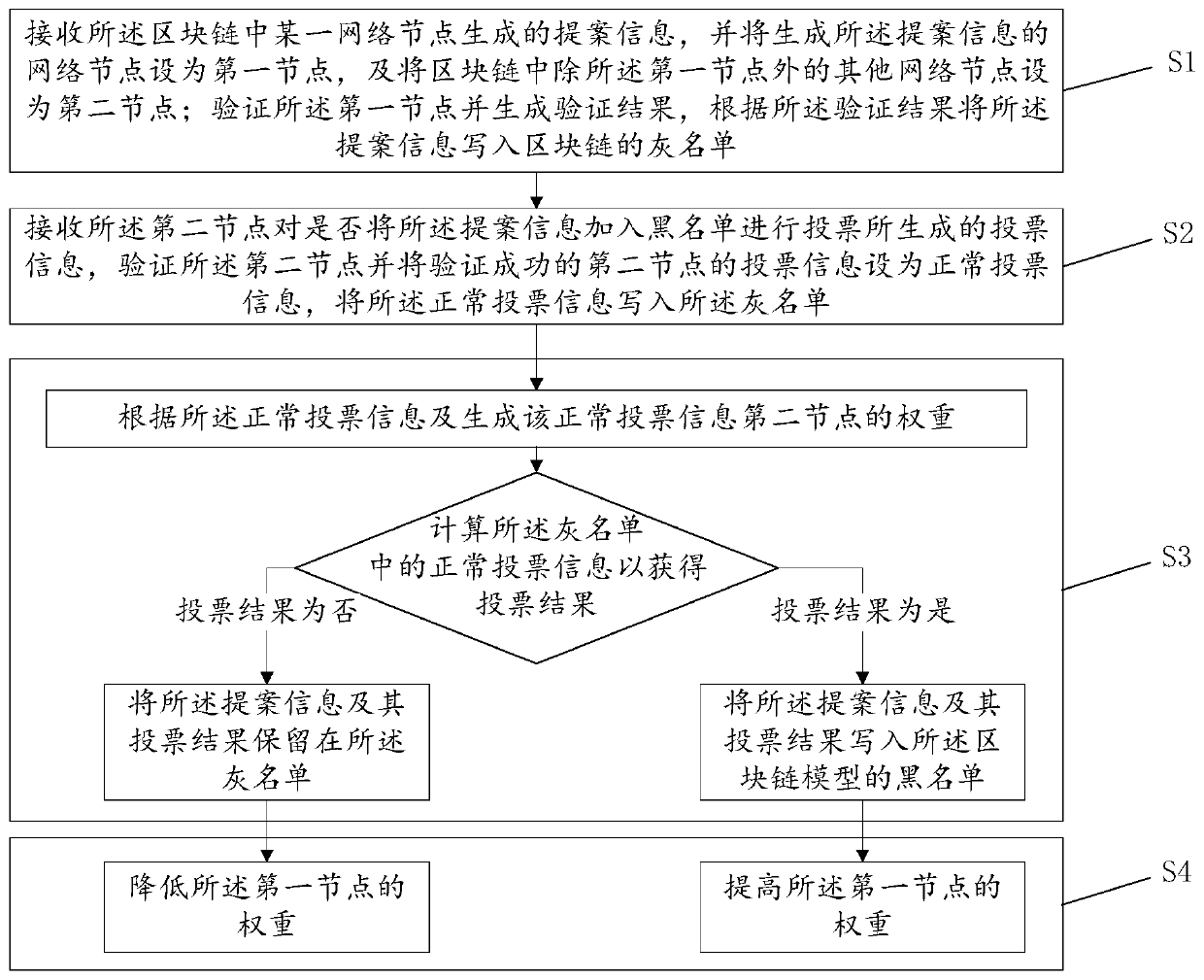
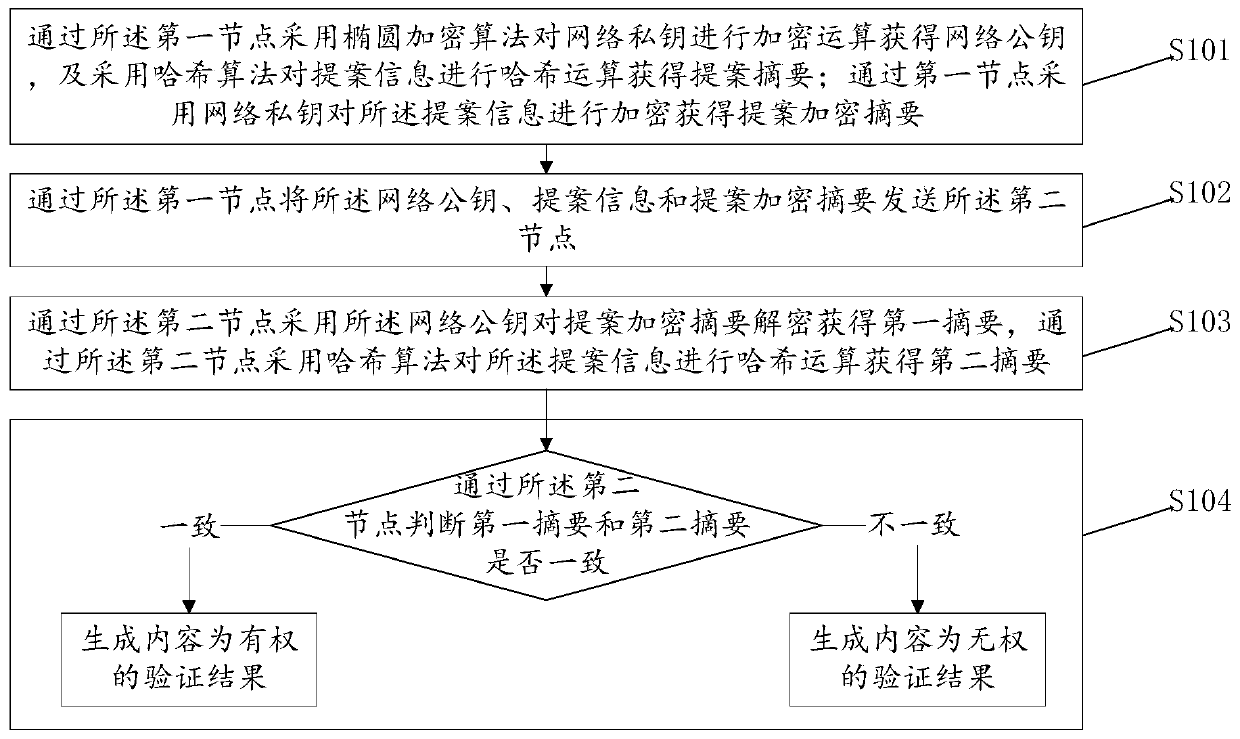
Blacklist management method and device, computer system and readable storage medium
InactiveCN111131218AGuaranteed validityGuaranteed closureKey distribution for secure communicationPublic key for secure communicationGrey listEngineering
The invention discloses a blacklist management method and device, a computer system and a readable storage medium, and the method comprises the following steps: receiving proposal information, verifying a first node, generating a verification result, and writing the proposal information into a grey list of a blockchain according to the verification result; receiving voting information, setting successfully verified voting information of a second node as normal voting information, and writing the normal voting information into a grey list; calculating a voting result according to the normal voting information and the weight of the second node generating the normal voting information; if the voting result is yes, writing the proposal information and the voting result thereof into a blacklistof the block chain; if the voting result is negative, reserving the proposal information and the voting result thereof in a grey list; increasing or decreasing the weight of the first node accordingto the proposal information written into the blacklist or reserved in the grey list and the voting result thereof. According to the method disclosed in the invention, blockade and privacy of the proposal information and the voting information are ensured, and authenticity of the proposal information written into the blacklist is ensured.
Owner:PING AN ASSET MANAGEMENT CO LTD
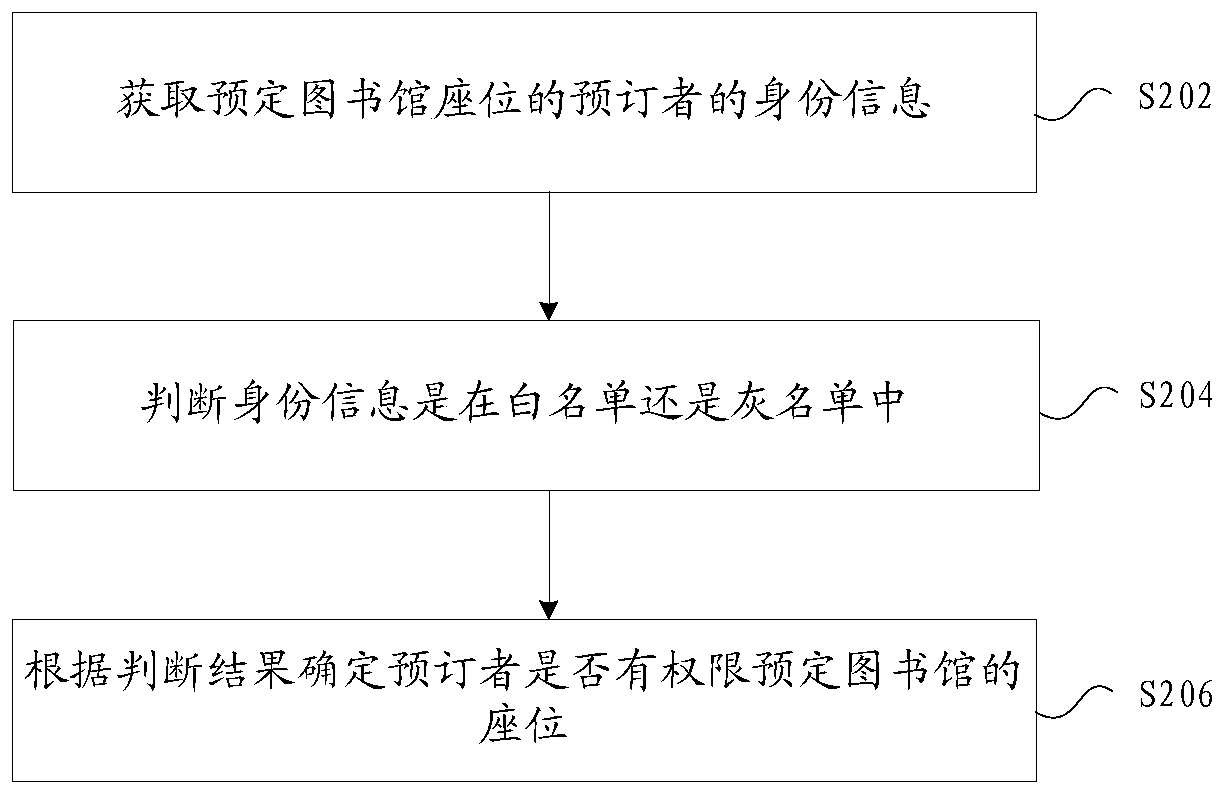
Library seat distribution method and device, storage medium and electronic device
InactiveCN110458306ASolve the low efficiency of managementImprove experienceReservationsResourcesGrey listDistribution method
The invention provides a library seat distribution method and device, a storage medium and an electronic device. The method comprises the following steps: acquiring identity information of a subscriber who reserves a library seat; judging whether the identity information is in a white list or a grey list, whrein the white list records the identity information of a booker who has permission to reserve a library seat, and the grey list records the identity information of the booker who has permission to reserve the library seat after a preset period of time; and determining whether the subscriber has permission to reserve the seat of the library or not according to a judgment result. The problem of low library seat management efficiency in related technologies is solved, and the effect of improving the user experience is achieved.
Owner:MIAOZHEN INFORMATION TECH CO LTD
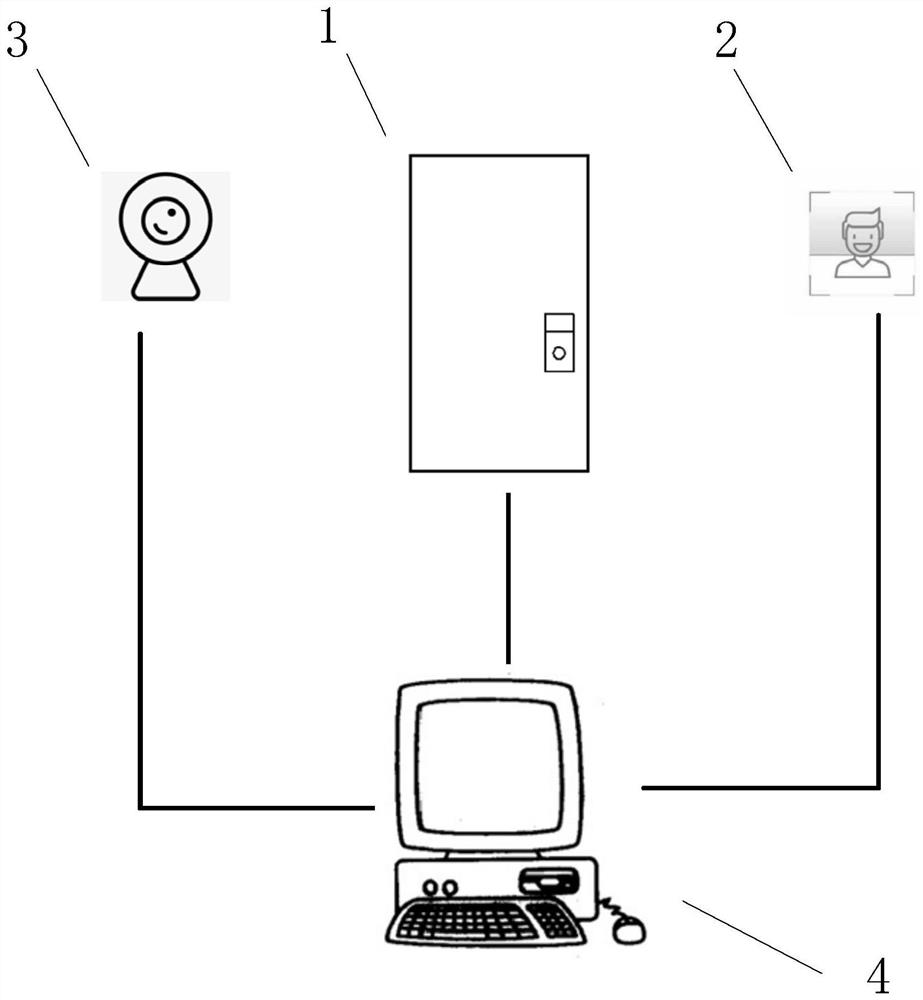
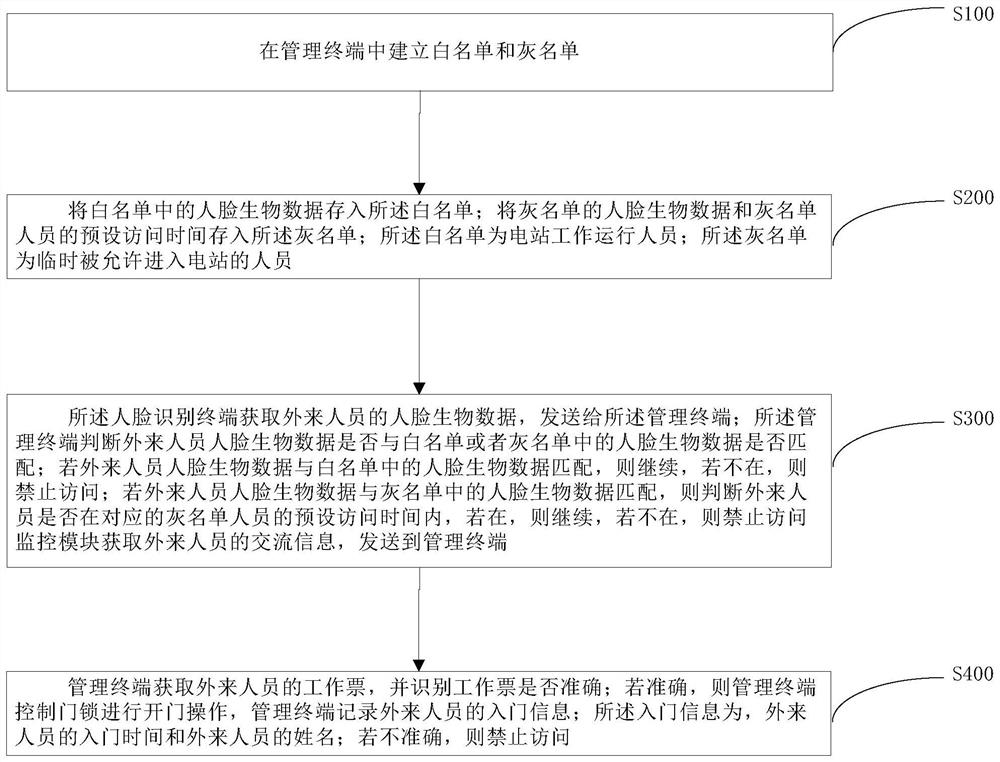
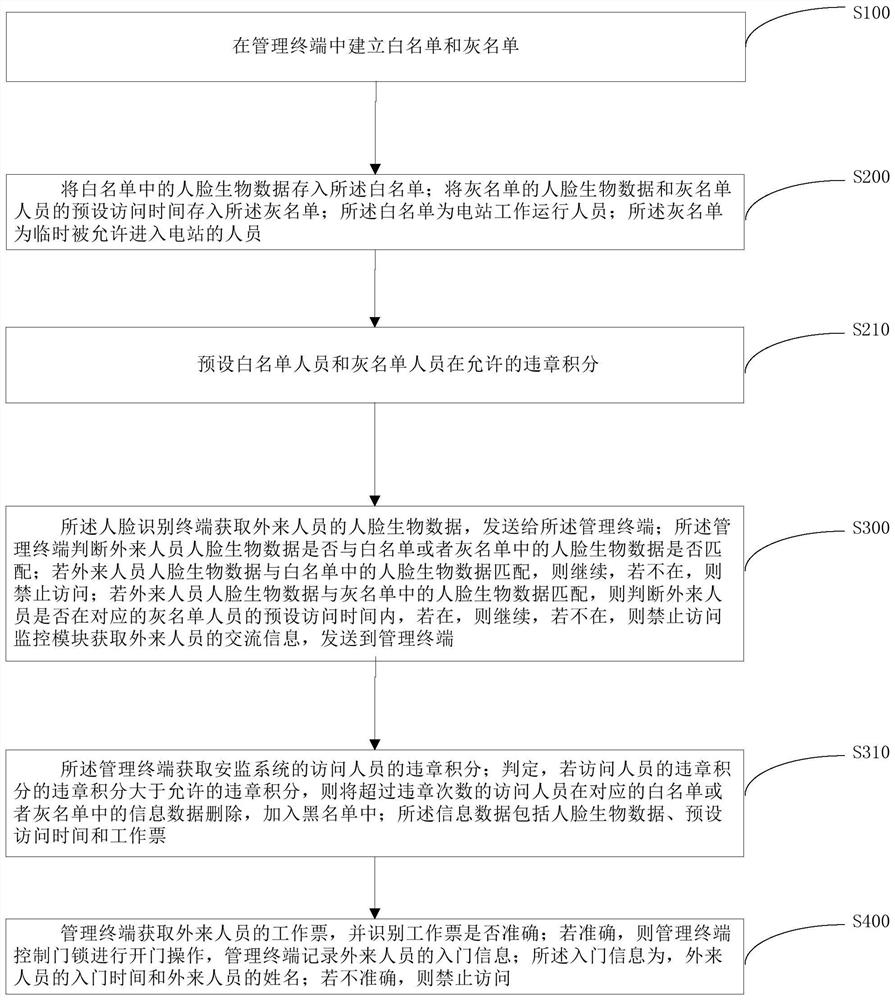
Intelligent security access control management method and system for power grid operation
PendingCN114360136AImprove practicalitySave manpower and material resourcesIndividual entry/exit registersAlarmsPower stationGrey list
The invention provides an intelligent security access control management method and system for power grid operation, and the system comprises a door lock, a face recognition terminal, a monitoring module and a management terminal; the main method comprises the following steps: acquiring face biological data in a white list, face biological data in a grey list and face biological data in a black list, and storing the face biological data in a management terminal; and aiming at different matching types of the visitors, the management terminal adopts different coping processes. According to the scheme, an overall refined management and control scheme for safe access of different types of personnel is adopted, manpower and material resources are reduced, more importantly, the practicability of an access control system is improved, power grid operation accidents are reduced, and the safety of a power station is improved.
Owner:YUNNAN POWER GRID CO LTD ELECTRIC POWER RES INST
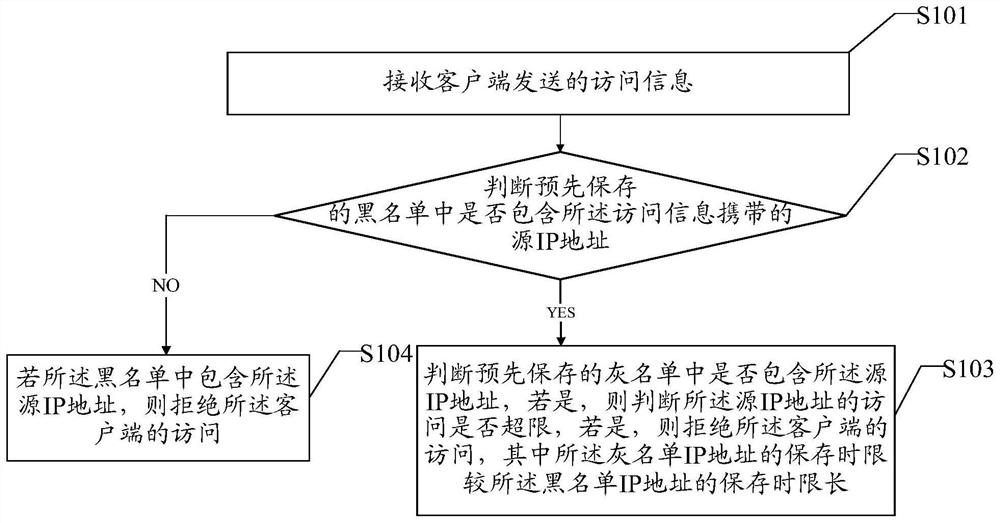
Frequency limiting method and device, equipment and medium
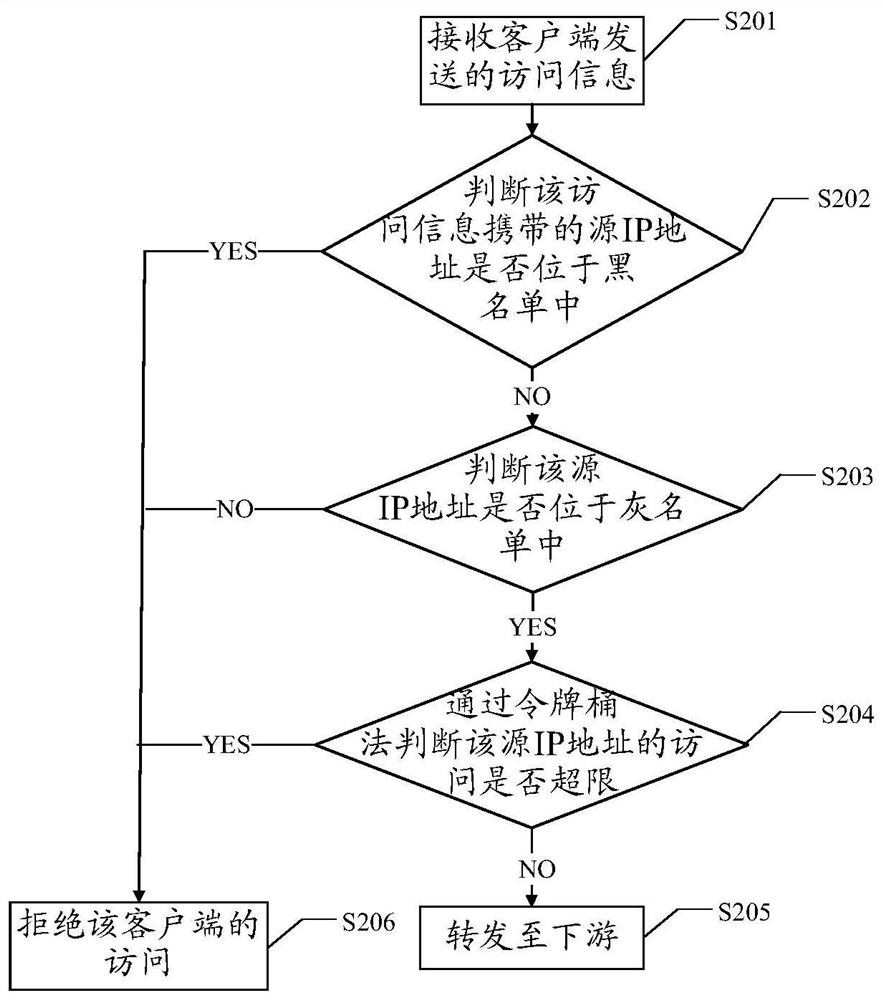
ActiveCN112929347AEffective frequency limitImprove frequency limit timeTransmissionIp addressGrey list
The invention discloses a frequency limiting method and device, equipment and a medium, which are used for solving the problems of low frequency limiting timeliness and poor frequency limiting effect in the prior art. In the embodiment of the invention, after the access information sent by the client is received, whether the pre-stored blacklist contains the source IP carried by the access information or not is judged, if not, whether the pre-stored grey list contains the source IP address or not is judged, and if yes, the access of the client is limited to a certain extent. In the embodiment of the invention, the access information sent based on the IP address in the grey list is limited, and the storage time limit of the IP address in the grey list is longer than the storage time limit of the IP address in the black list, so that the frequency of the access of the client is effectively limited, and the frequency limiting time efficiency and the frequency limiting effect are improved.
Owner:BIGO TECH PTE LTD
Intelligent question and answer-based fax machine with advertisement shielding function
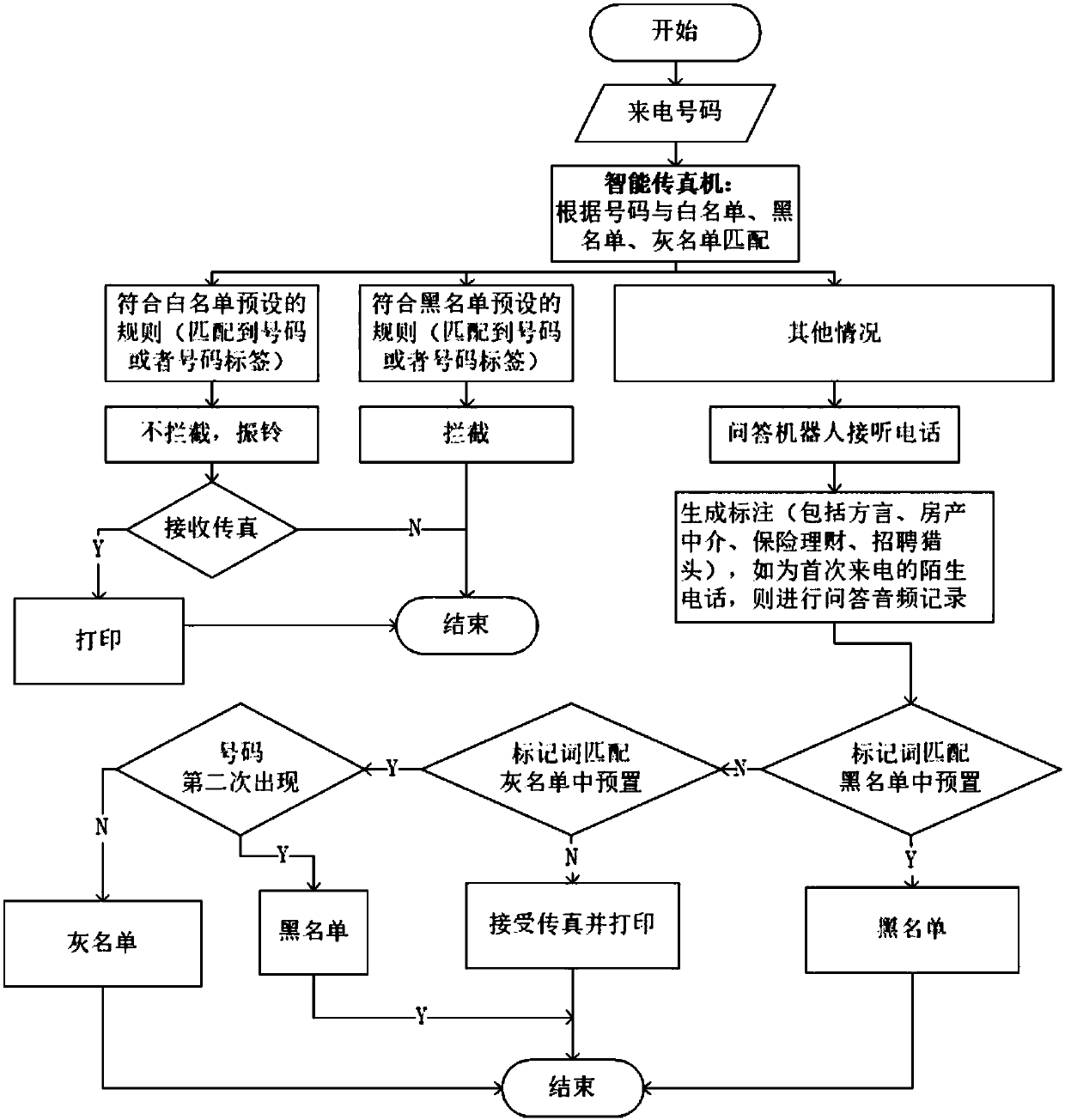
InactiveCN109547659AEffective shieldingReduce acceptancePictoral communicationGrey listQuestions and answers
The invention relates to an intelligent question and answer-based fax machine with an advertisement shielding function. A grey list and an intelligent question and answer module are arranged in the fax machine. For each dialed fax number, the fax number is matched with numbers in a white list, a black list and the grey list through the intelligent question and answer module; if the matching succeeds and a fax is determined as a known fax in the white list, ringing is performed for notifying an owner and the fax is received; if the matching succeeds and the fax is determined as a known fax in the black list, the fax is directly intercepted; and if the matching succeeds and the fax is determined as a known fax in the grey list, or if the matching fails and the fax is determined as a strangefax, a robot is enabled to carry out intelligent question and answer with a fax sender, marked words are extracted according to question and answer contents, and whether the ringing is performed for notifying the owner to receive the fax or add the fax to the grey list or the black list is determined through marked word matching. The fax machine can effectively determine whether the strange fax isa junk fax of an advertisement harassment type or not, so that the purpose that advertisement faxes are accurately shielded can be effectively realized.
Owner:SOUTHEAST UNIV
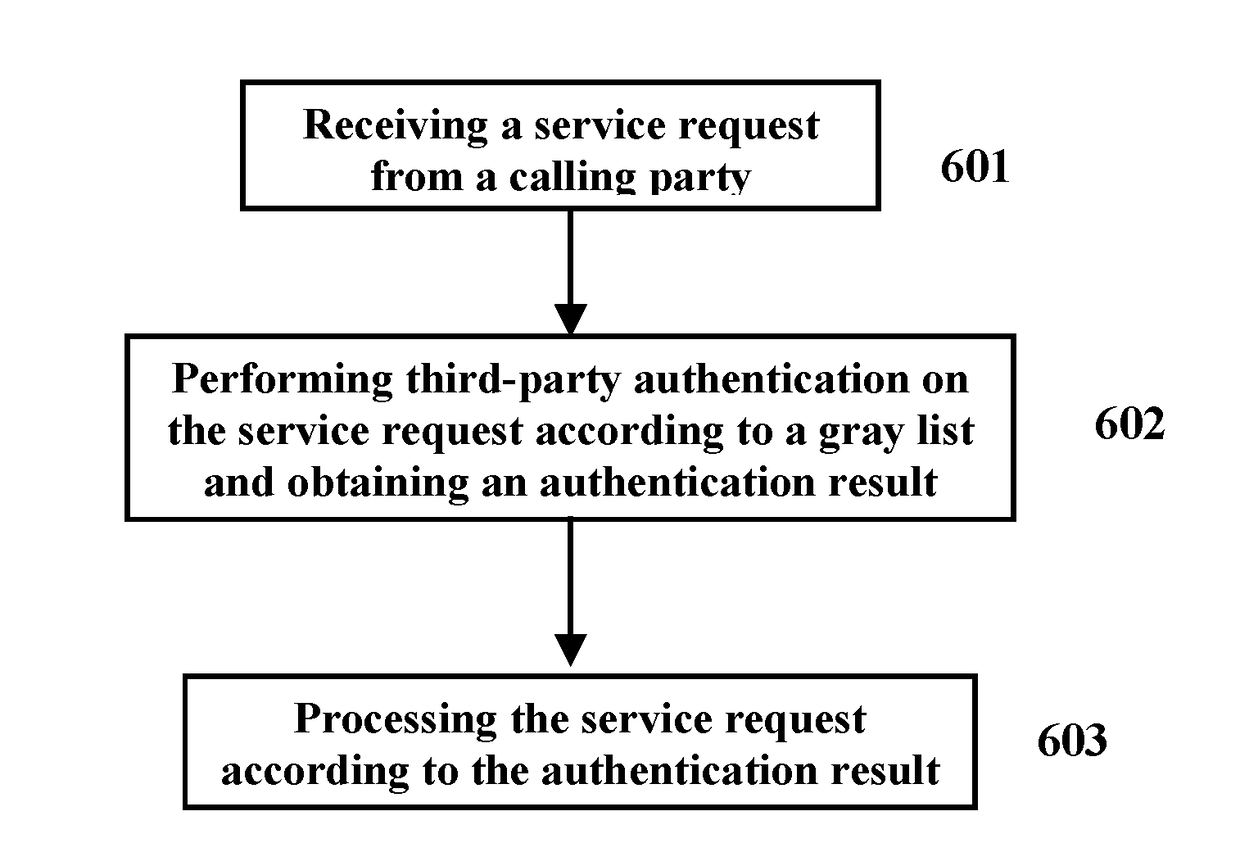
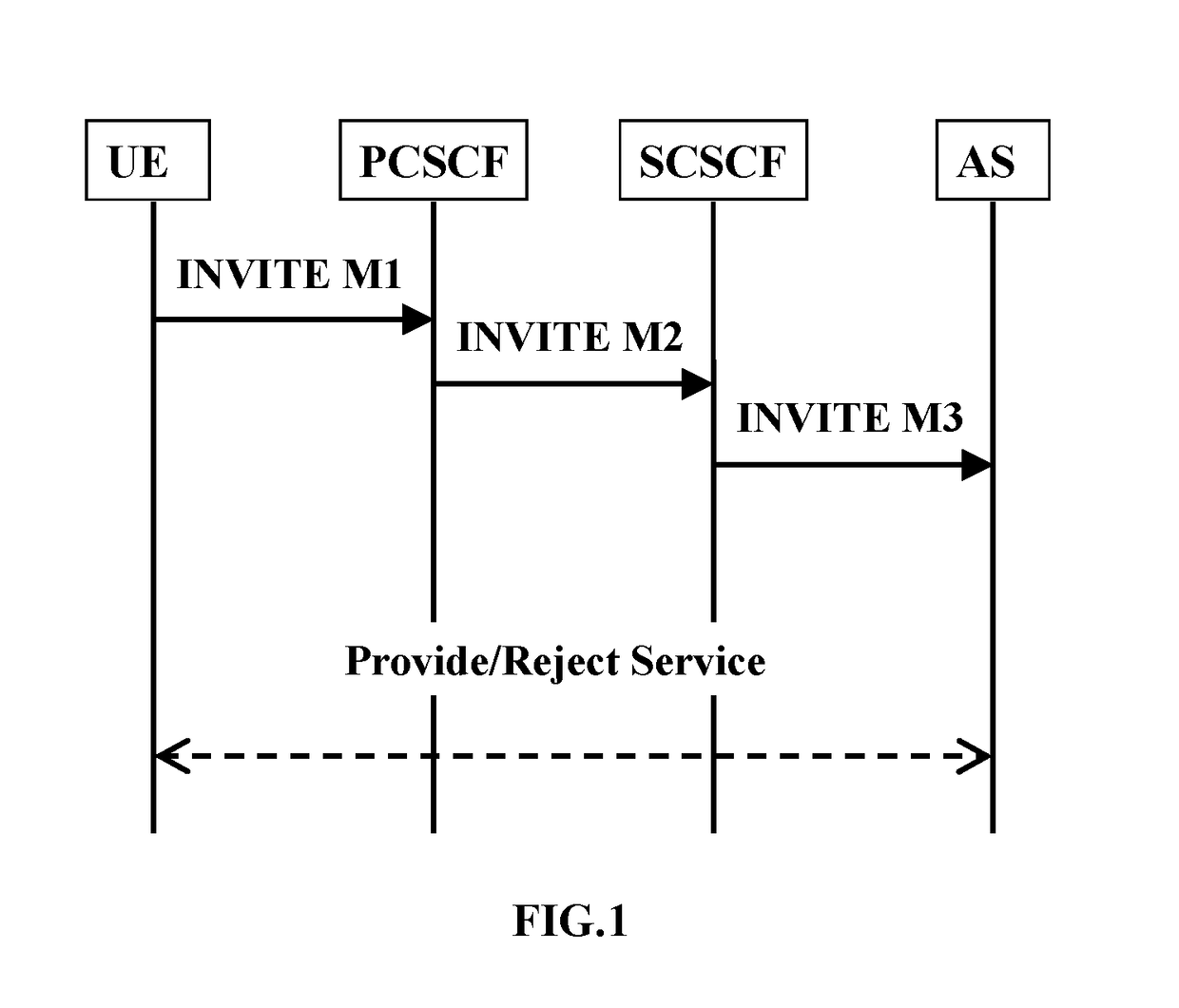
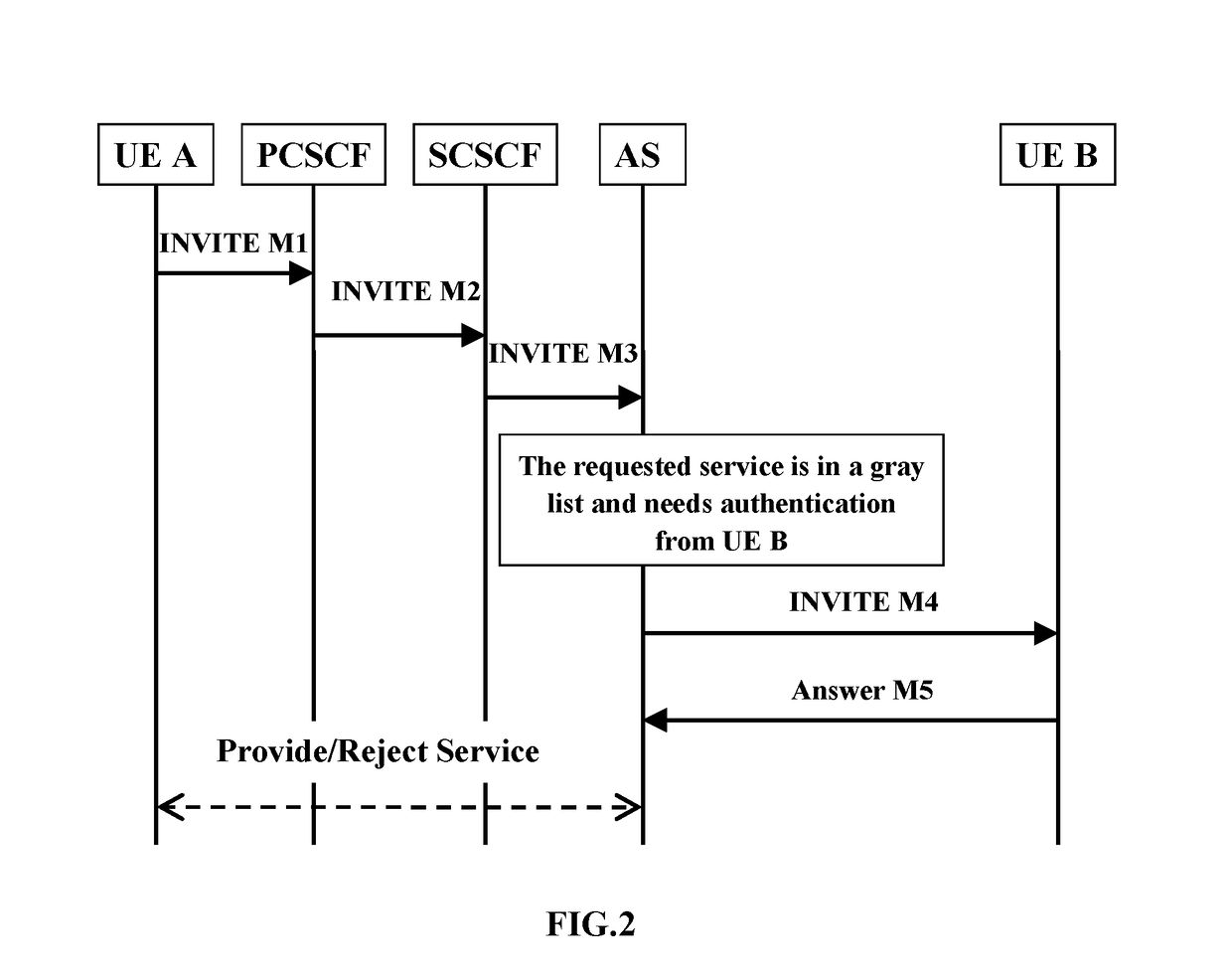
Method and system for implementing third-party authentication based on gray list
The present invention relates to a communication method, comprising: receiving a service request from a requesting party; performing a third-party authentication on the service request according to a gray list and obtaining an authentication result; and processing the service request according to the authentication result. The present invention relates to a communication system, comprising: means for receiving a service request from a requesting party; means for performing a third-party authentication on the service request according to a gray list and obtaining an authentication result; and means for processing the service request according to the authentication result. The present invention implements a third-party control of services based on the gray list, and can effectively manage a variety of services in the communication system.
Owner:ALCATEL LUCENT SAS
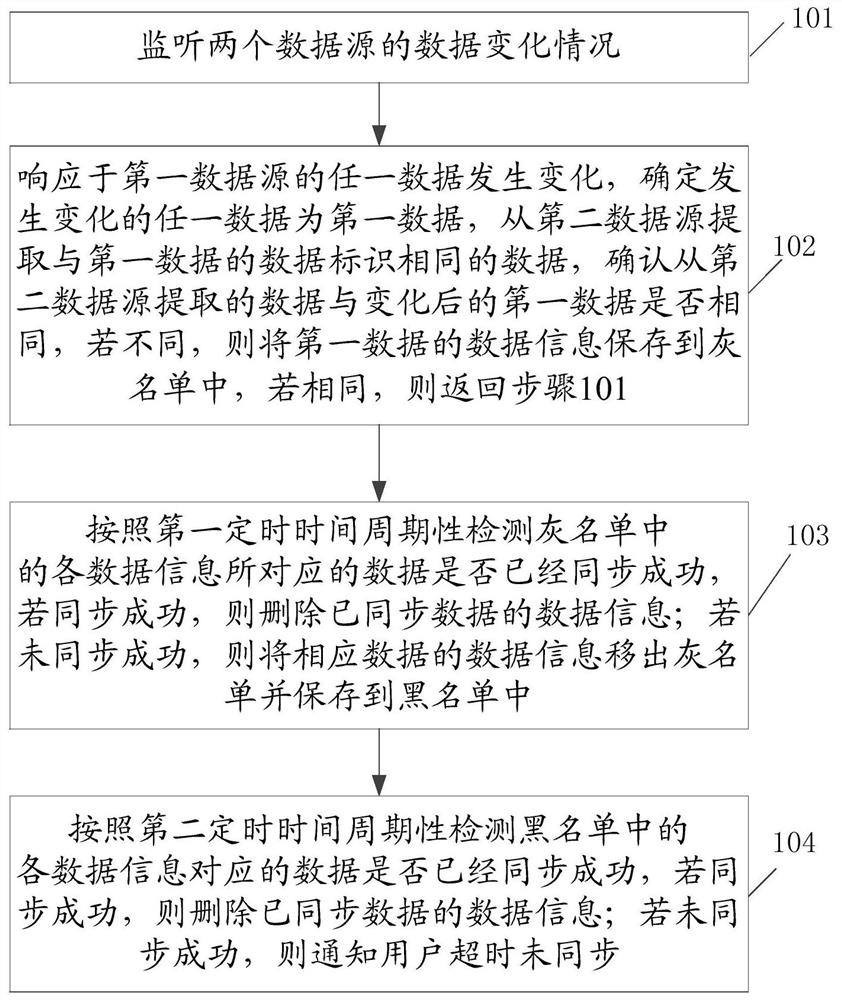
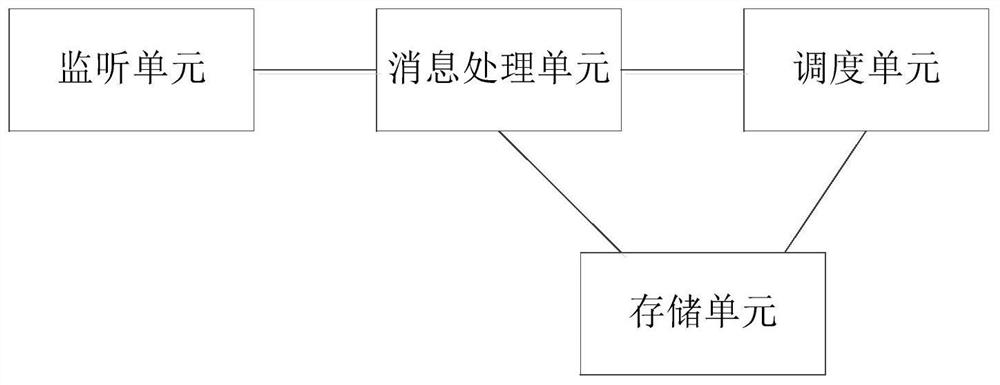
Bidirectional real-time data monitoring method and device
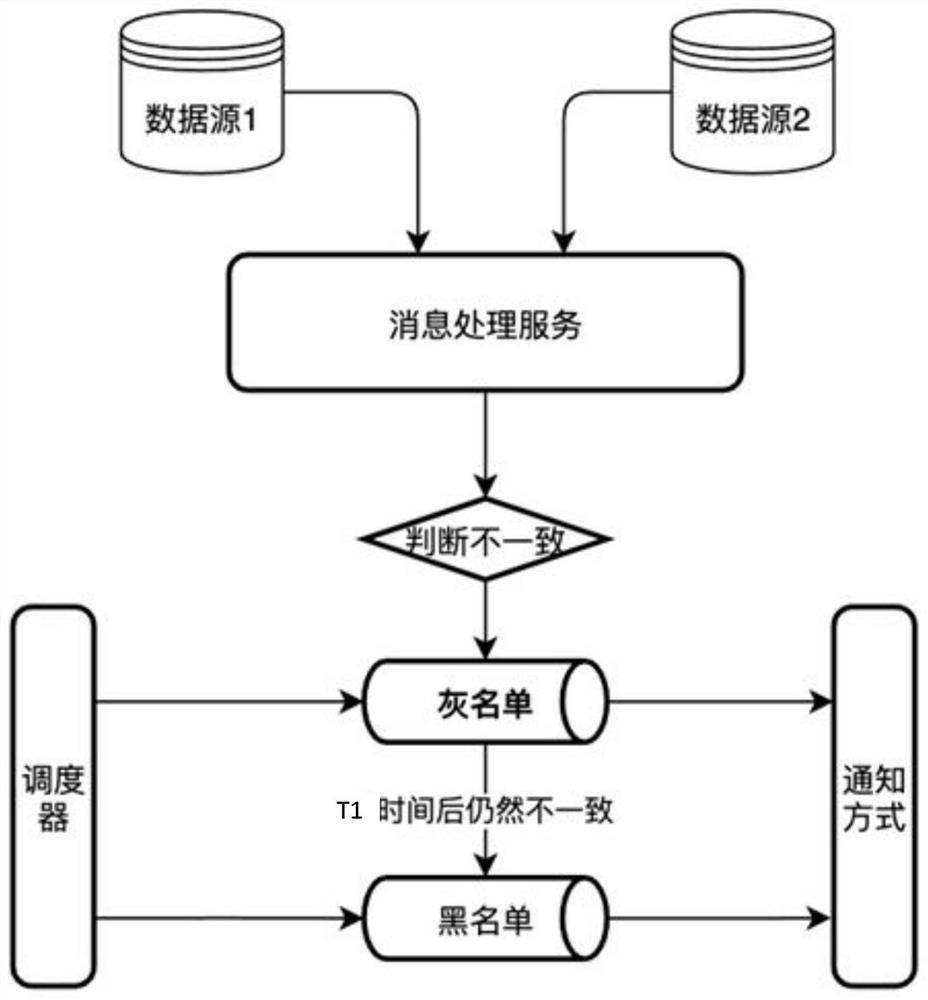
InactiveCN113886497AGuaranteed synchronizationAchieving processing powerDatabase distribution/replicationSpecial data processing applicationsData synchronizationData information
The invention discloses a bidirectional real-time data monitoring method, which comprises the steps of monitoring data of two data sources, determining any changed data as first data in response to the change of any data of a first data source, extracting data with the same data identifier as the first data from a second data source, determining whether the data extracted from the second data source is the same as the changed first data or not, and if not, storing the data information of the first data in a grey list; periodically detecting whether the data information in the grey list is synchronized or not according to the first timing time, and if so, deleting the data information; if not, moving the corresponding data information out of the grey list, and storing in a blacklist; periodically detecting whether the data information in the blacklist is synchronized or not according to a second timing time, and if so, deleting the information of the synchronized data; and if not, notifying the user that the time is out of synchronization. By applying the method and the device, data synchronization and data consistency among different data sources can be better guaranteed.
Owner:KE COM (BEIJING) TECHNOLOGY CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com