Operation and maintenance operation instruction security analysis method and system and storage medium
A security analysis, operation and maintenance operation technology, applied in the direction of neural learning methods, computer security devices, instruments, etc., can solve the problems of cumbersome manual labeling and category labeling, and difficult operation and maintenance operation instructions, so as to improve the degree of automation and enhance the security of the system Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
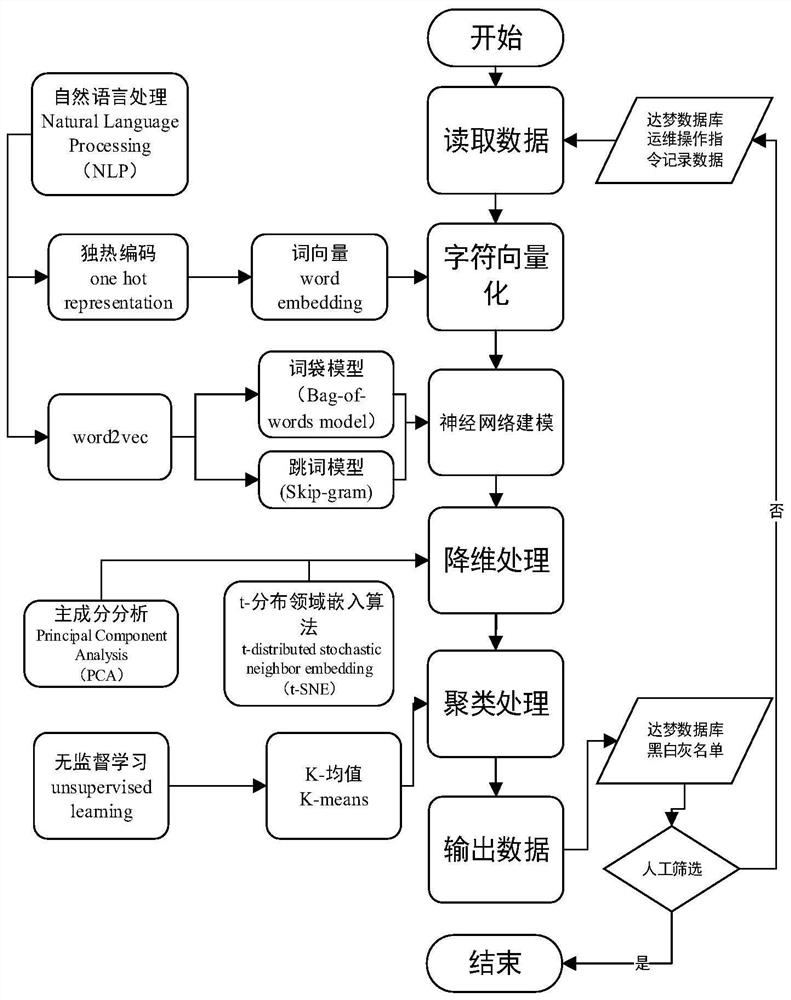
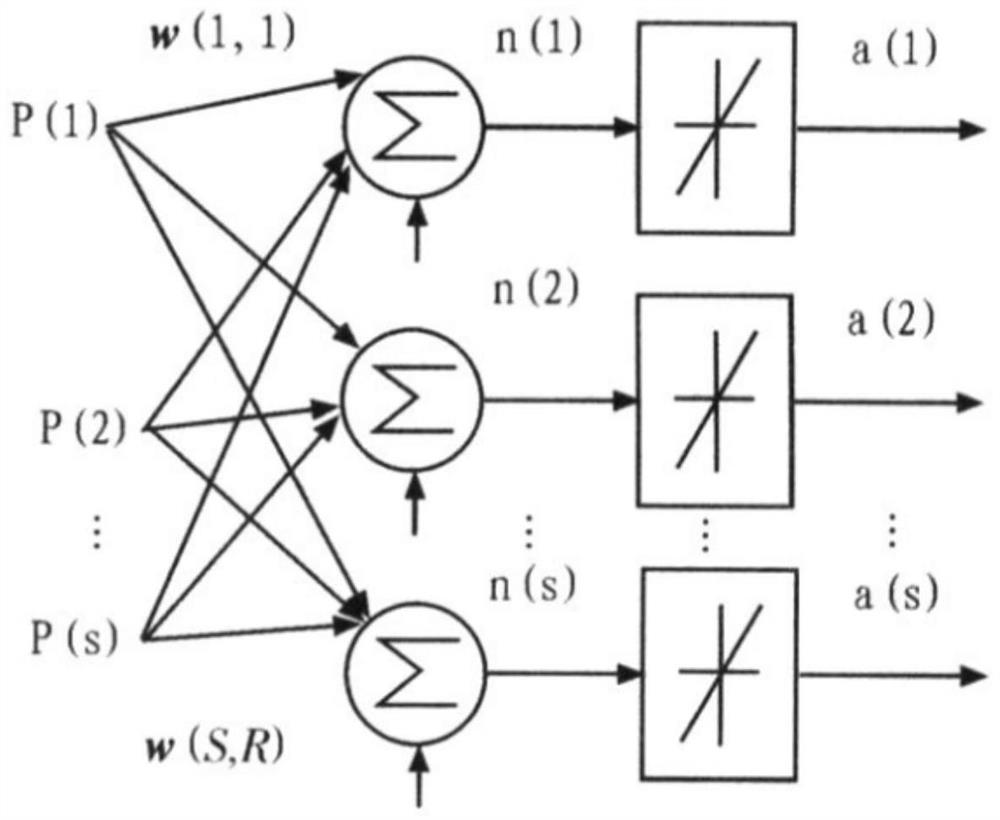
[0035] figure 1 Schematic diagram of the overall framework of the security analysis model for user operation and maintenance operations. On the basis of the theoretical basis and the scene of equipment operation and maintenance operations, a security analysis model for user operation and maintenance operation instructions is constructed. An operation and maintenance operation instruction security analysis method of the present invention includes Follow the steps below:
[0036] Step 1, read the historical operation instruction data, and perform character vectorization processing on the character set of the historical operation instruction data;
[0037] 1) Read the historical data from the specified database, respectively SSH (Secure Shell abbreviation, formulated by the Network Working Group of IETF, SSH is a security protocol based on the application layer and transport layer.) Remote Operation instruction set (133142 groups of instruction data) and Local local operation in...
Embodiment 2
[0057] In step three, the dimensionality reduction method is t-distribution domain embedding algorithm (t-SNE). Compared with the principal component analysis (PCA) method, the two dimensionality reduction methods have their own advantages and disadvantages. However, for the current For the actual data in the scene, the two methods can compare the output data respectively.
[0058] Other technical characteristics are identical with embodiment 1.
Embodiment 3
[0060] In Step 4, the clustering method can also choose K-medoid algorithm, CURE, Chameleon and BIRCH algorithms, etc.
[0061] Other technical characteristics are identical with embodiment 1.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com