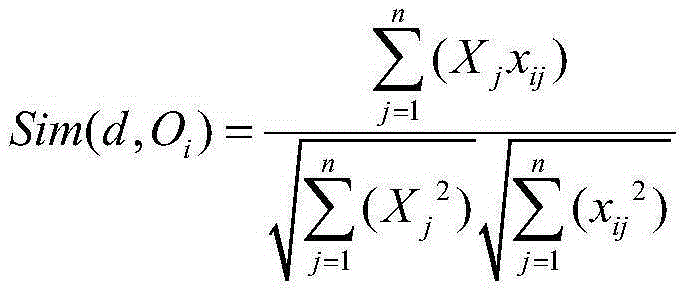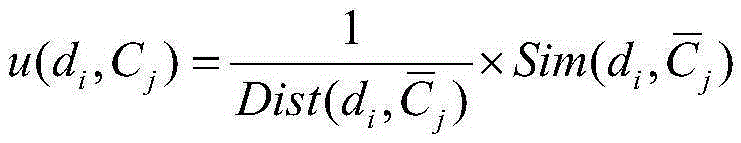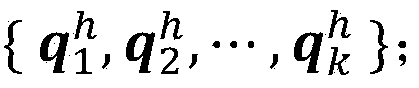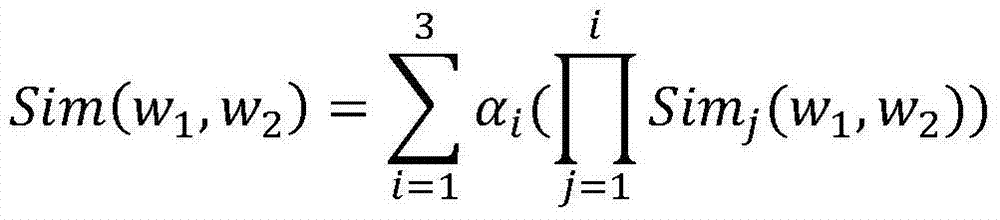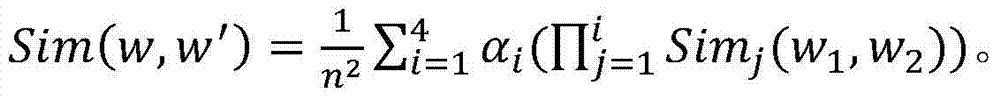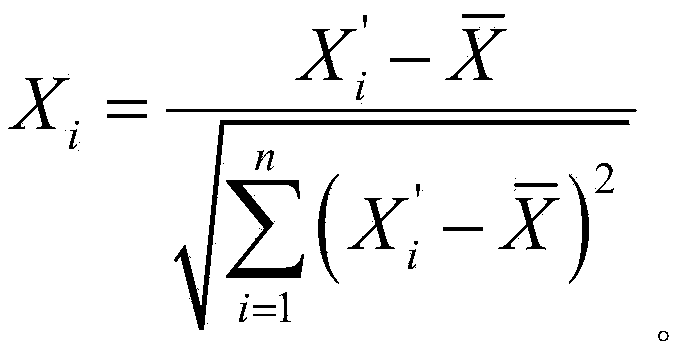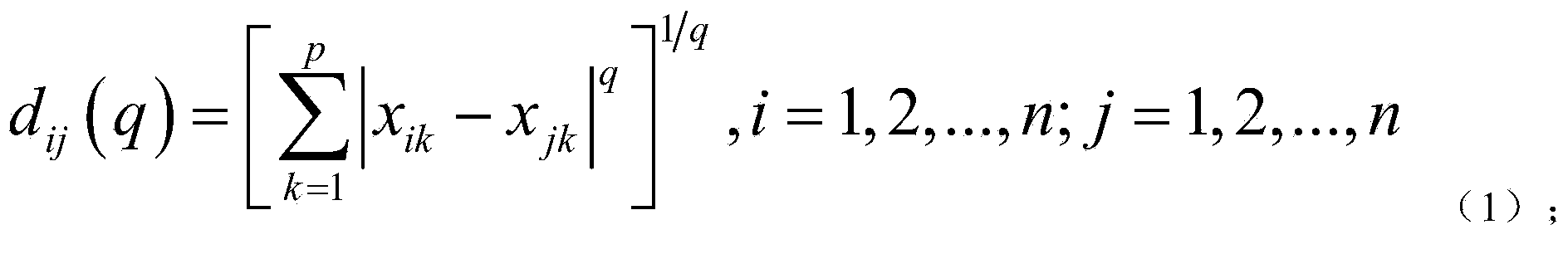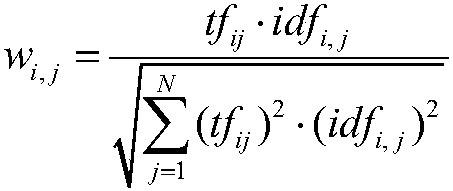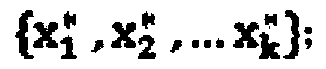Patents
Literature
83 results about "Medoid" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Medoids are representative objects of a data set or a cluster with a data set whose average dissimilarity to all the objects in the cluster is minimal. Medoids are similar in concept to means or centroids, but medoids are always restricted to be members of the data set. Medoids are most commonly used on data when a mean or centroid cannot be defined, such as graphs. They are also used in contexts where the centroid is not representative of the dataset like in images and 3-D trajectories and gene expression (where while the data is sparse the medoid need not be). These are also of interest while wanting to find a representative using some distance other than squared euclidean distance (for instance in movie-ratings).
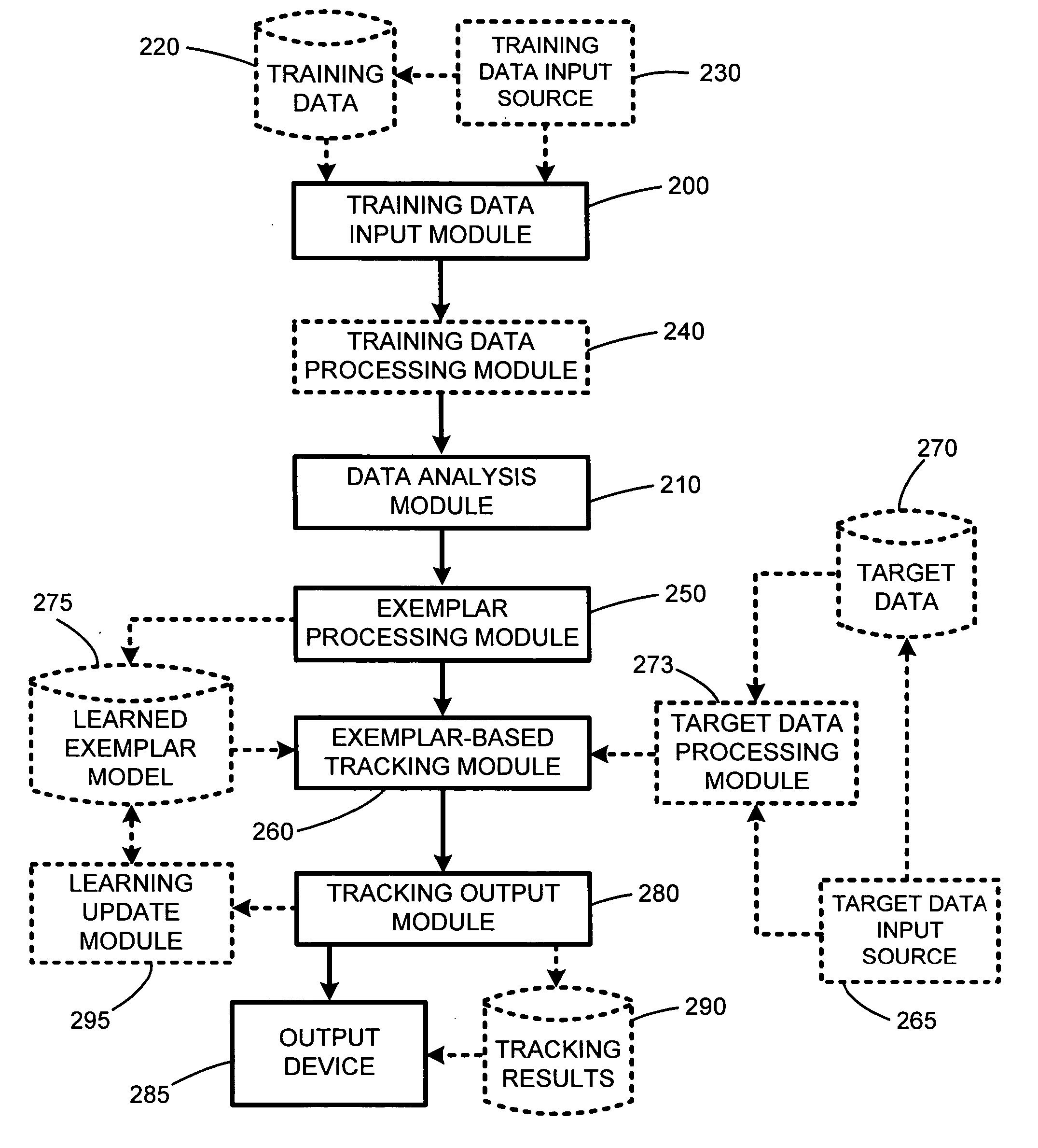
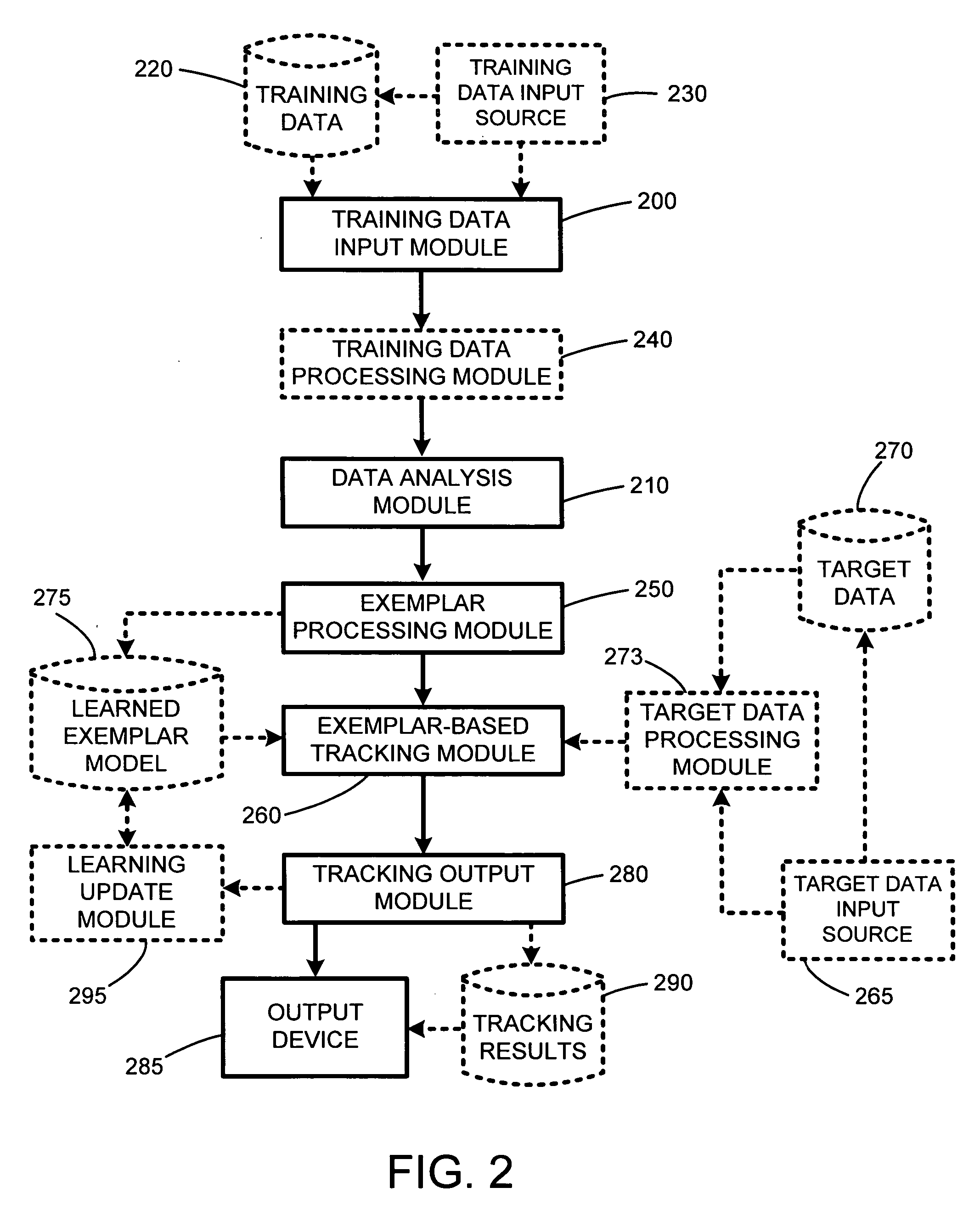
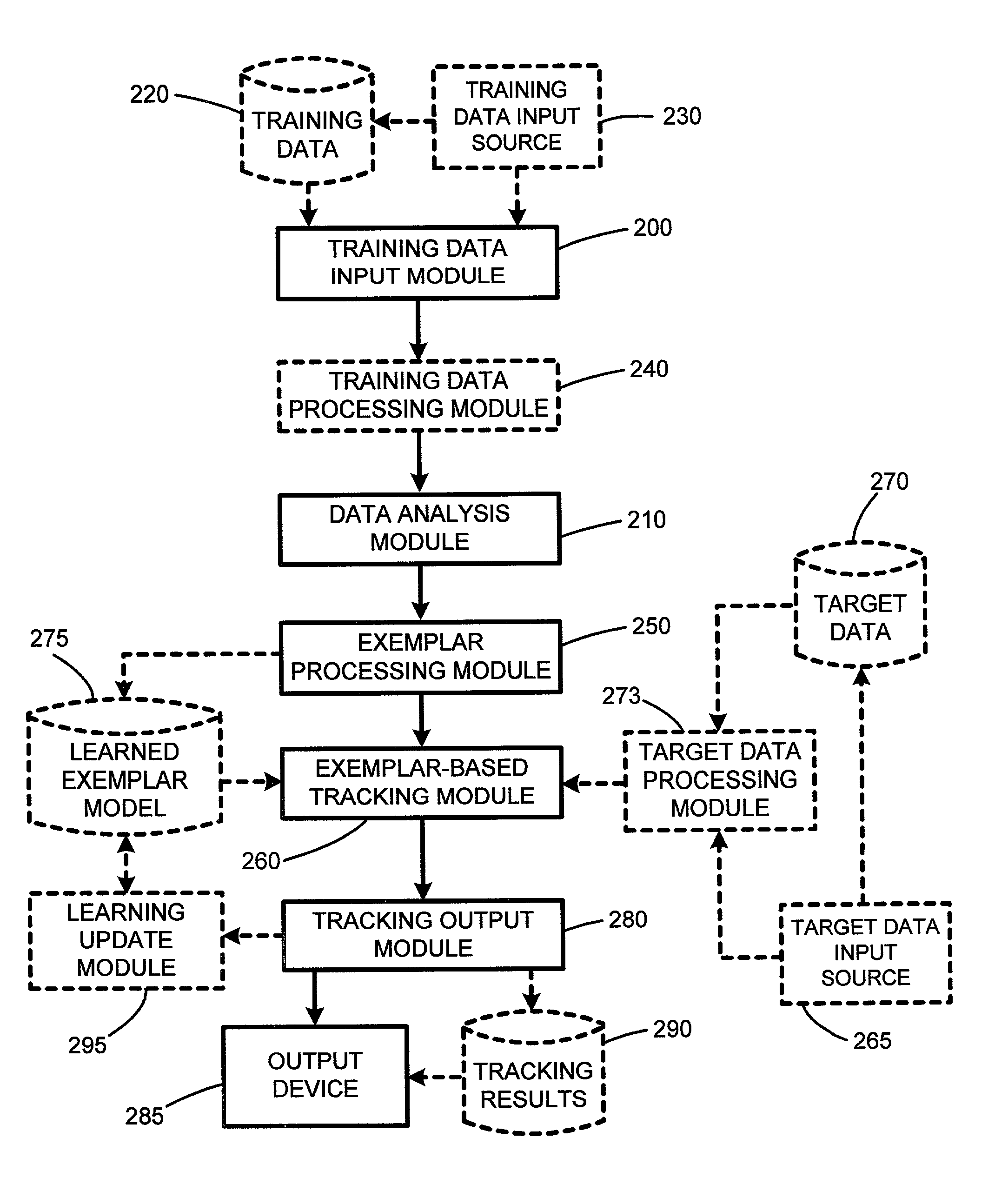
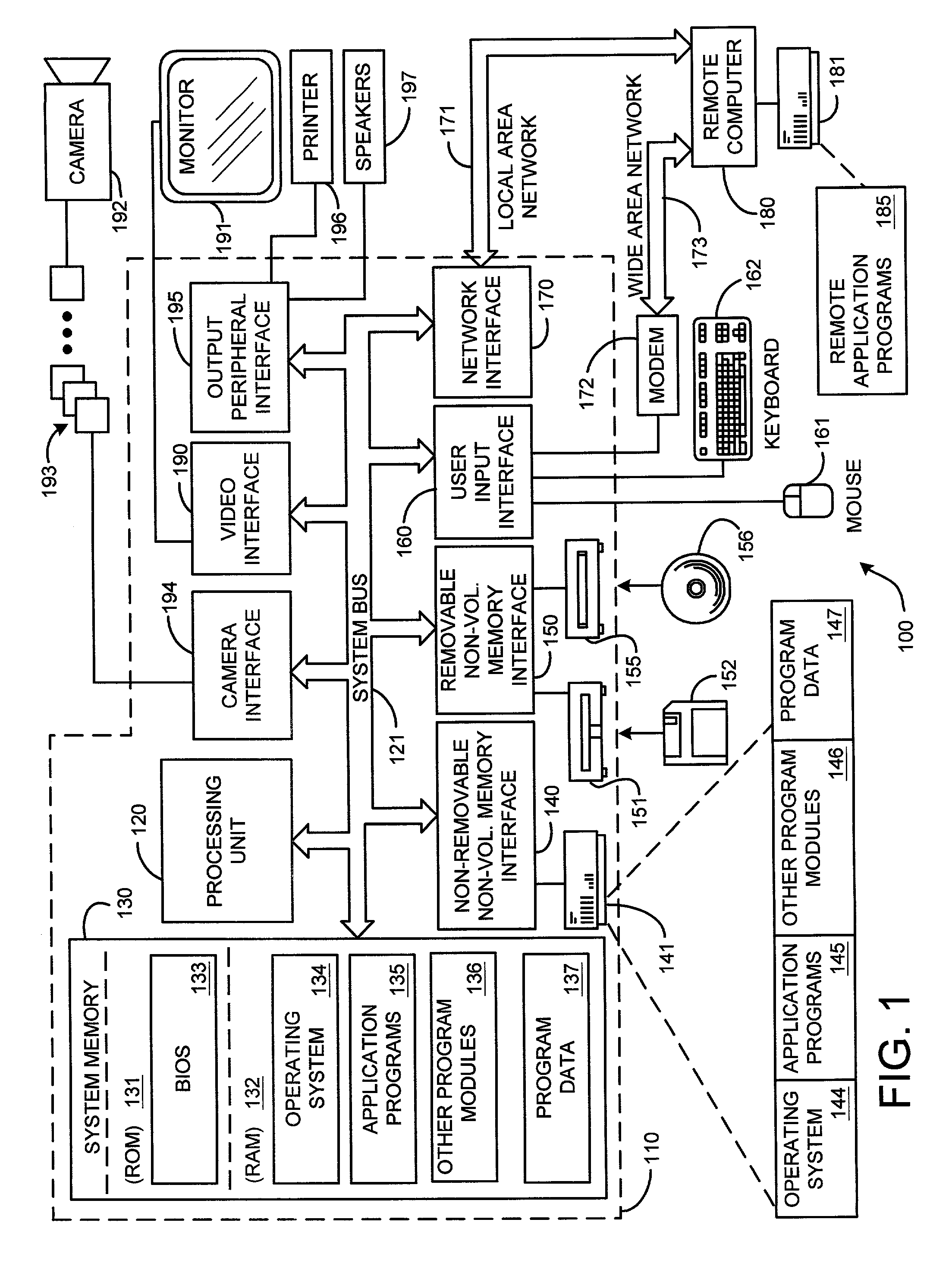
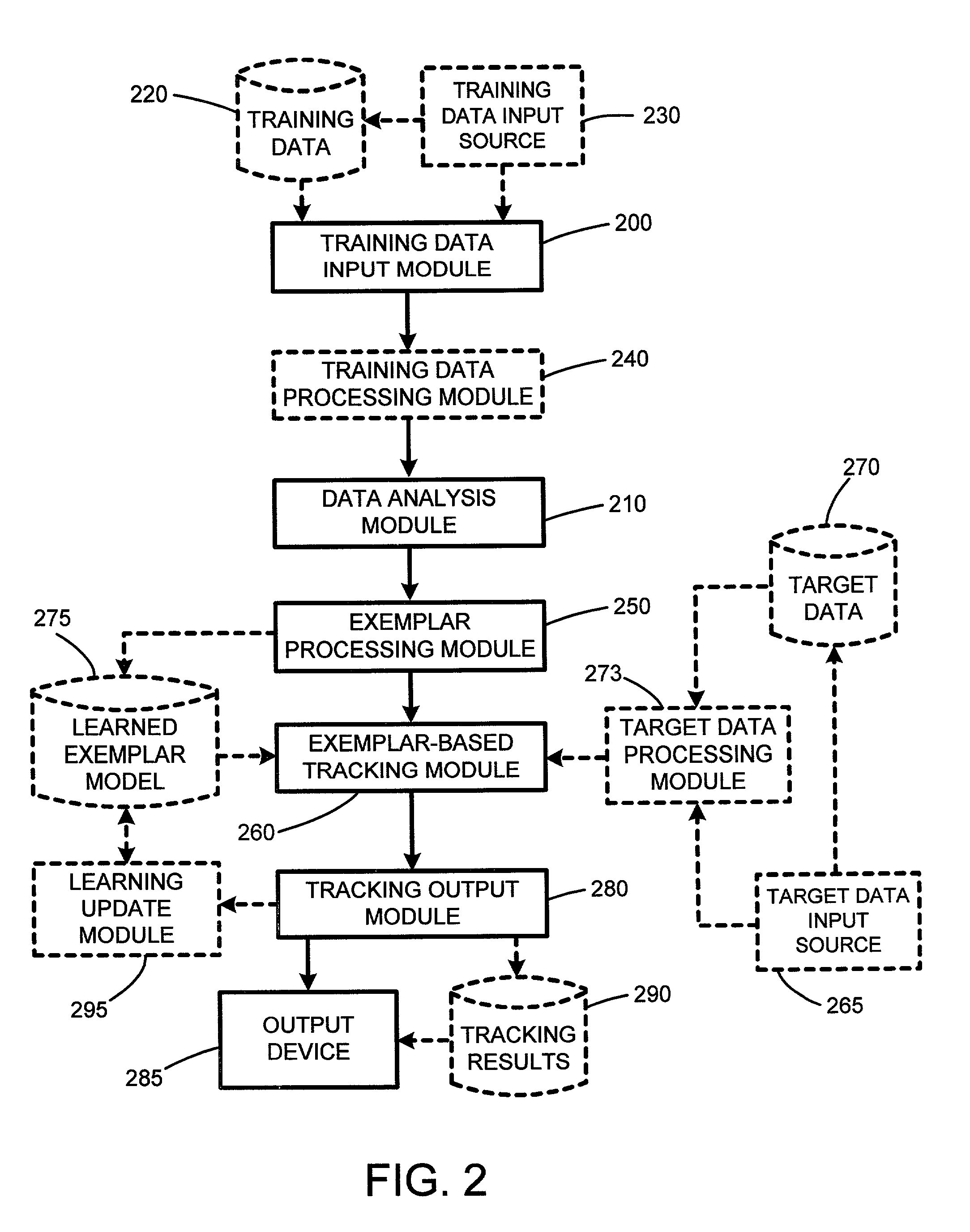
Probabilistic exemplar-based pattern tracking
InactiveUS20060093188A1Expensive analysisConstruction of expensiveImage analysisCharacter and pattern recognitionPattern recognitionCombined use
The present invention involves a new system and method for probabilistic exemplar-based tracking of patterns or objects. Tracking is accomplished by first extracting a set of exemplars from training data. The exemplars are then clustered using conventional statistical techniques. Such clustering techniques include k-medoids clustering which is based on a distance function for determining the distance or similarity between the exemplars. A dimensionality for each exemplar cluster is then estimated and used for generating a probabilistic likelihood function for each exemplar cluster. Any of a number of conventional tracking algorithms is then used in combination with the exemplars and the probabilistic likelihood functions for tracking patterns or objects in a sequence of images, or in a space, or frequency domain.
Owner:MICROSOFT TECH LICENSING LLC
System and method for probabilistic exemplar-based pattern tracking
InactiveUS7035431B2Improve scalabilityExpensive analysisImage analysisCharacter and pattern recognitionPattern recognitionCombined use
The present invention involves a new system and method for probabilistic exemplar-based tracking of patterns or objects. Tracking is accomplished by first extracting a set of exemplars from training data. The exemplars are then clustered using conventional statistical techniques. Such clustering techniques include k-medoids clustering which is based on a distance function for determining the distance or similarity between the exemplars. A dimensionality for each exemplar cluster is then estimated and used for generating a probabilistic likelihood function for each exemplar cluster. Any of a number of conventional tracking algorithms is then used in combination with the exemplars and the probabilistic likelihood functions for tracking patterns or objects in a sequence of images, or in a space, or frequency domain.
Owner:MICROSOFT TECH LICENSING LLC
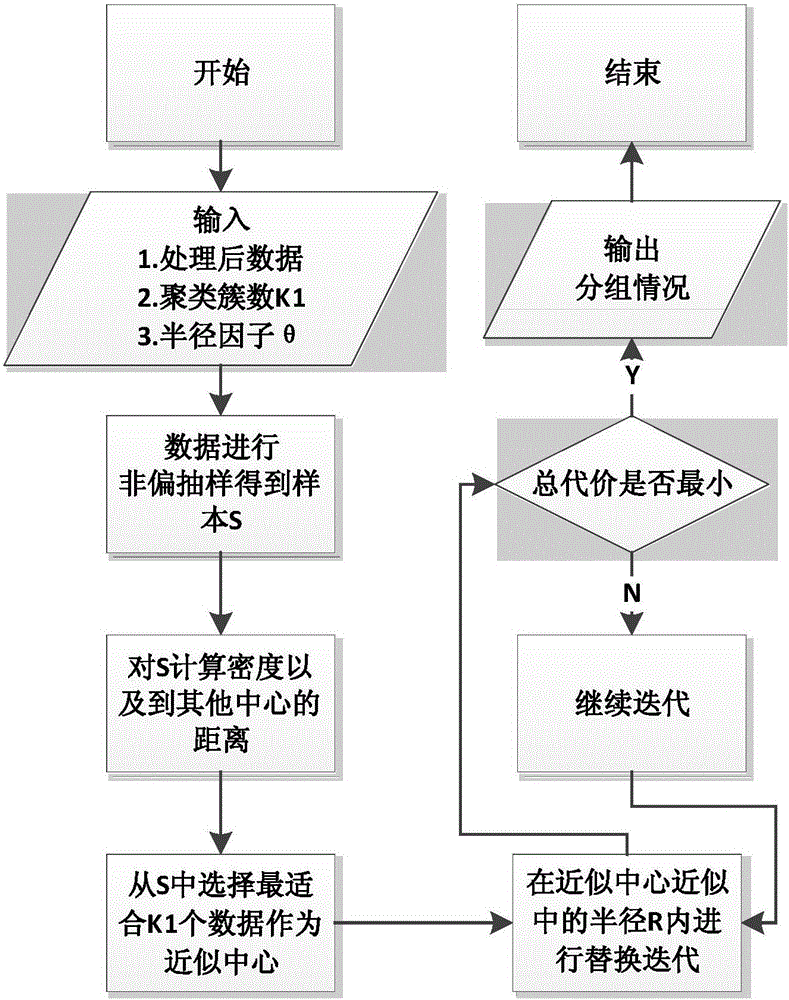
Network abnormal traffic detection method based on PAM (Partitioning Around Medoids) clustering algorithm
The invention discloses a network abnormal traffic detection method based on a PAM (Partitioning Around Medoids) clustering algorithm. The method comprises a traffic collection stage of monitoring a network to obtain network data packets through a network analysis tool; a feature extraction stage of extracting attributes of the network data packets, and carrying out information entropy calculation on the attributes of the network data packets in a time period, thereby obtaining multiple multi-dimensional data records; a center selection stage of clustering data points of the network data packets by employing the PAM clustering algorithm according to the multi-dimensional data records, and selecting precise clustering centers through approximate clustering after approximate clustering centers are obtained; and an outlier judgment state of setting a threshold value, and screening data points of which precise clustering center distance and partial outlier factors are greater than the threshold value, thereby obtaining outlier abnormal data. According to the method, the improved PAM clustering algorithm is applied to abnormal traffic detection, the advantage that clustering is unnecessarily marked is inherited, moreover, the operation time required by the algorithm is reduced, and the capability of processing more data can be realized.
Owner:EAST CHINA NORMAL UNIV
Touch information classified computing and modelling method based on machine learning
InactiveCN105956351AEasy to identifySpecial data processing applicationsTouch PerceptionPattern perception
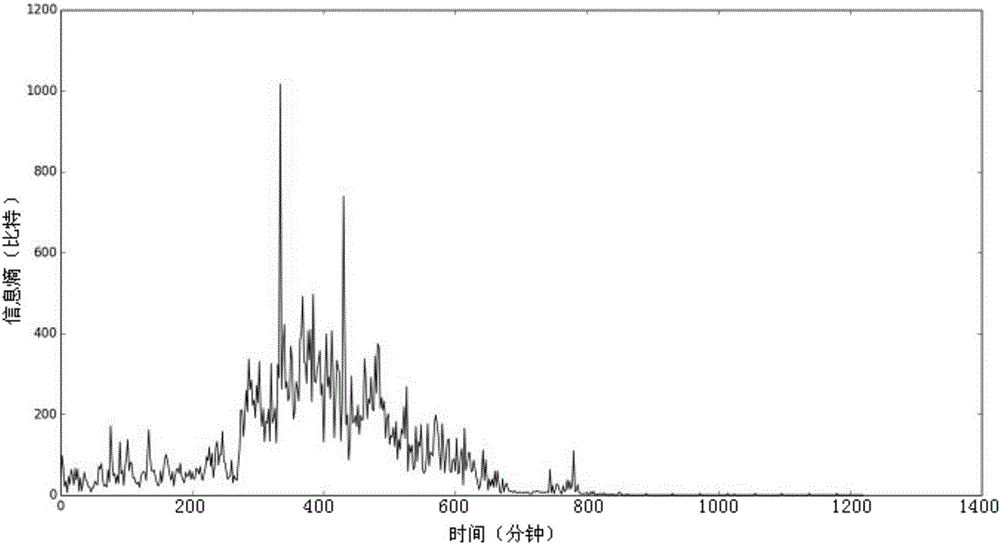
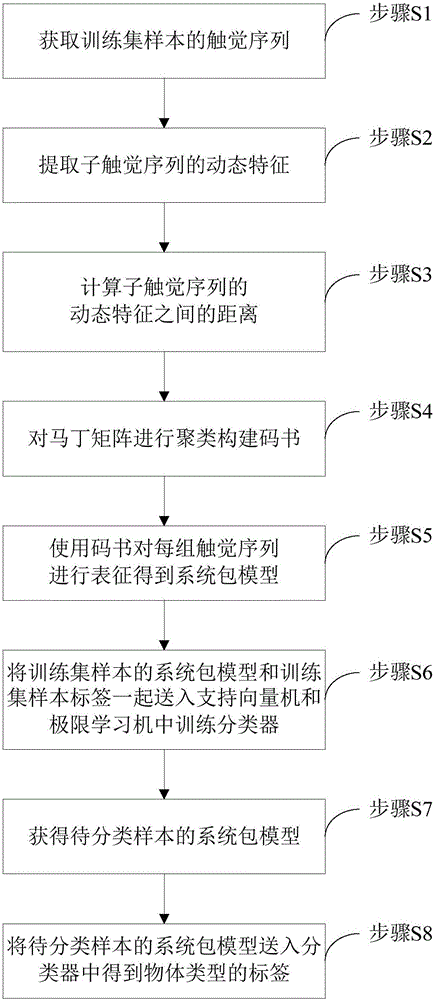
The invention relates to a touch information classified computing and modelling method based on machine learning. The method comprises the following steps: acquiring a touch sequence of a training set sample, modelling by adopting a linear dynamic system model, extracting dynamic characteristics of a sub touch sequence, calculating distance of the dynamic characteristics of the sub touch sequence by adopting Martin distance, clustering a Martin matrix by adopting a K-medoids algorithm, constructing a code book, carrying out characterization on each touch sequence by adopting the code book to obtain a system packet model, putting the system packet model of the training set sample and a training set sample label into an extreme learning machine for training a classifier, and putting the system packet model of a to-be-classified sample into the classifier to obtain a label for type of an object. The touch information classified computing and modelling method has the advantages that the actual demand of a robot on stable and complaisant grasping of a non-cooperative target is met, data foundation is provided for completion of a precise operation task, and other sensing results can be fused and computed, so that the description and recognition capability on different targets is enhanced by virtue of multi-source deep perception, and a technical foundation is laid for implementation of intelligent control.
Owner:SHANGHAI AEROSPACE CONTROL TECH INST
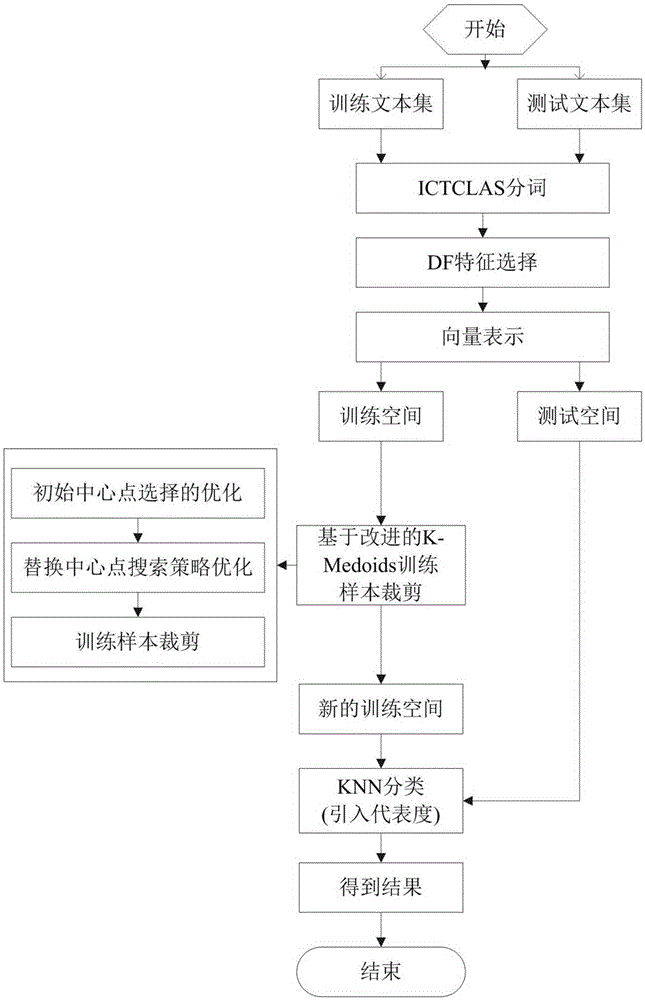
KNN text classification method based on improved K-Medoids
InactiveCN105426426AImplement classificationReduce the effect of initial center point sensitivityCharacter and pattern recognitionSpecial data processing applicationsCategory attributeAlgorithm
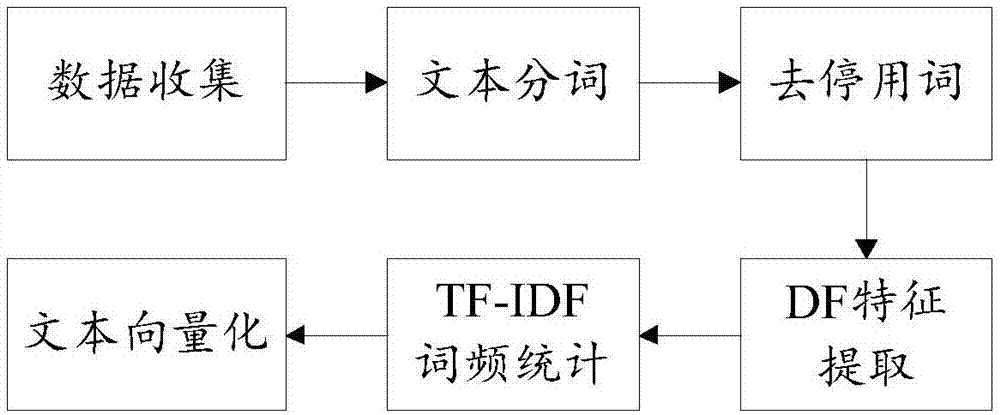
The invention provides a KNN (K-Nearest-Neighbor) text classification method based on improved K-Medoids and relates to the field of computer text data processing. The method comprises the following steps: pre-processing a training text set and a testing text set, wherein preprocessing comprising removal of participles and stop words, DF feature selection and vector representation, so as to obtain a training text vector space and a testing text vector space; carrying out training sample clipping on the basis of an improved K-Medoids method, namely, optimizing from the points of initial center point selection and replacement of center point search strategy, and applying optimization to the training sample clipping so as to obtain a new training text space; and finally, carrying out KNN classification, defining a representative function and applying the representative function to class attribute functions for KNN classification so as to obtain a final result. Experimental results show that compared with a conventional KNN method and a KNN method based on the K-Medoids, the KNN text classification method provided by the invention has higher classification accuracy and classification efficiency.
Owner:BEIJING UNIV OF TECH
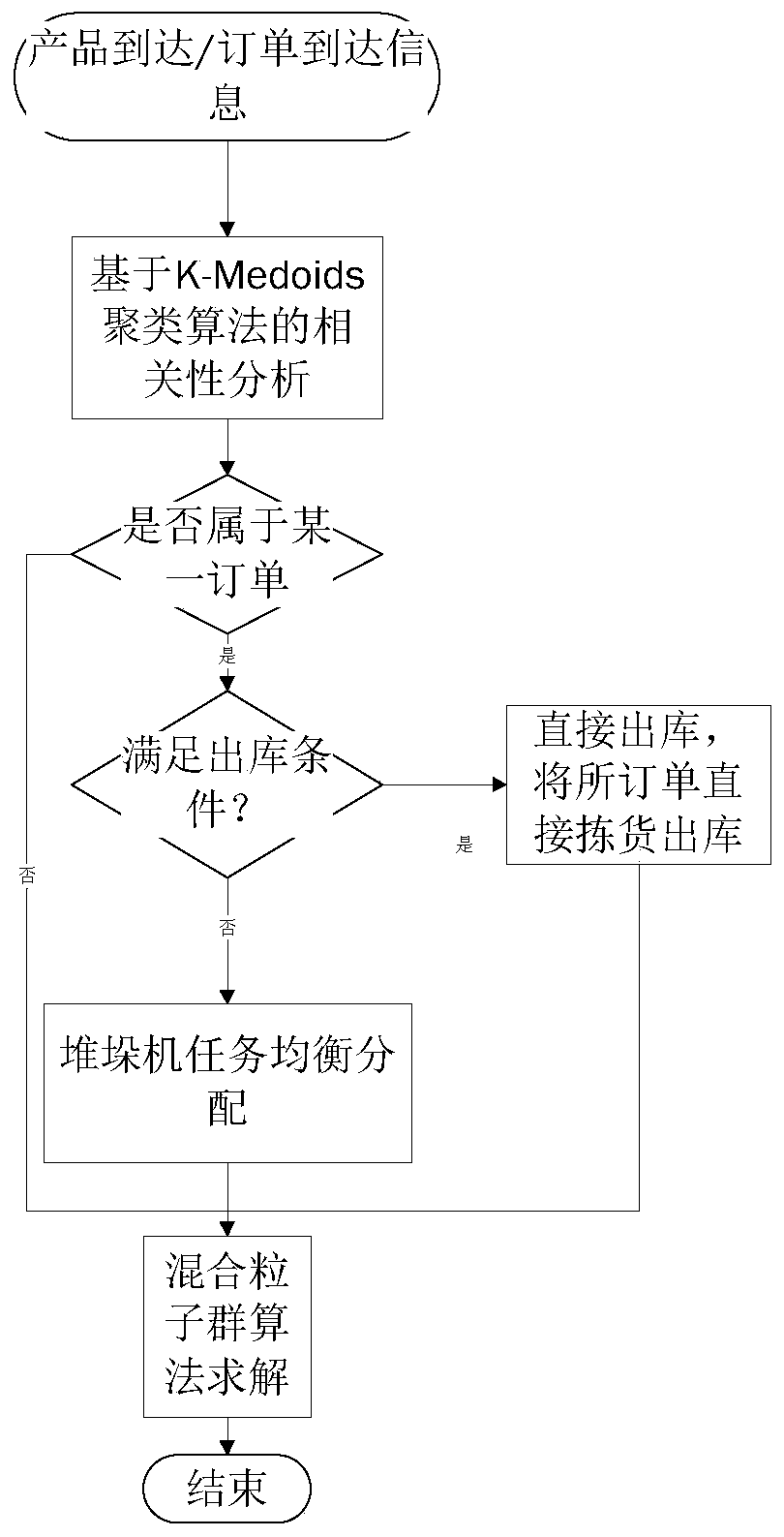
Integrated scheduling method for multi-roadway automatic stereoscopic warehouse based on mixed integer programming model
ActiveCN110084545AReduce complexitySuccessfully Solve Integration Scheduling ProblemsCharacter and pattern recognitionLogisticsOperation schedulingProduct order
The invention discloses an integrated scheduling method for a multi-roadway automatic stereoscopic warehouse based on a mixed integer programming model which comprises the steps that step 1, a tray / order arrives so as to perform step 2; if no tray / order arrives, performing the step 5; step 2, carrying out correlation analysis based on a K-Medoids clustering algorithm on arrived tray products making clustering analysis on arrived tray products, finding class clusters where tray products are located, solving an initial goods allocation range, wherein correlation analysis implementation process based on K-Medoids clustering algorithm is as follows: K-Medoids clustering algorithm is used for carrying out correlation analysis: step3, directly warehousing products ordered the same day and performing the step 6; if not, skipping to the step 4, directly warehousing products ordered the same day; step 4, stacking machine task distribution based on operation balance, step 5: distributing a sorting mode, and step 6: performing goods allocation and operation scheduling distribution; step 7, generating a stacking machine operation list until an optimal solution is not changed, otherwise, repeating the step 5 -step 7.
Owner:ZHEJIANG UNIV OF TECH
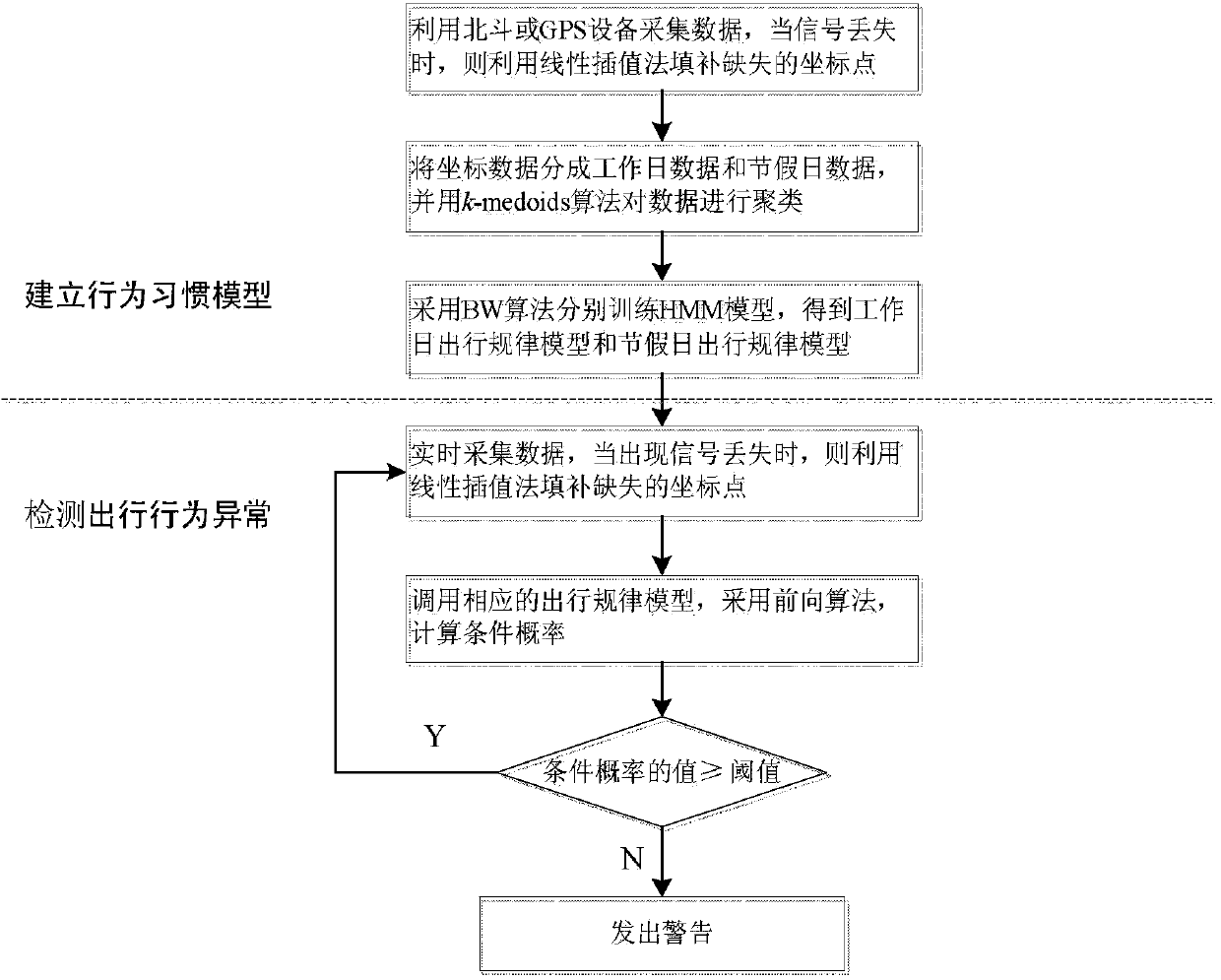
Travel anomaly detection method based on hidden Markov model
InactiveCN103793599AHigh precisionImprove reliabilitySpecial data processing applicationsAnomaly detectionHide markov model
A travel anomaly detection method based on a hidden Markov model includes the following steps that firstly, a Beidou or GPS positioning device is utilized to acquire monitoring data such as longitude, latitude and dates, and the data are sent to a travel behavior monitoring platform through a GPS module; secondly, coordinate data are divided into workday data and holiday data, and the workday data and the holiday data are clustered through a k-medoids algorithm to acquire two clustering mark point sets respectively; thirdly, the workday coordinate data and the holiday coordinate data are used as two sets of observed quantities, an HMM model is trained through a Baum-Welch algorithm, and then a workday travel rule model and a holiday travel rule model are respectively acquired; fourthly, travel behavior anomalies are detected through the travel rule models. The travel anomaly detection method is high in accuracy and good in reliability.
Owner:浙江远图技术股份有限公司
Multi-document subject discovery method based on two-layer clustering
InactiveCN104778204ASolve the "non-orthogonal" caseReduce the dimensionality of the eigenvector spaceSpecial data processing applicationsFeature vectorAlgorithm
The invention discloses a multi-document subject discovery method based on two-layer clustering. The multi-document subject discovery method comprises the following steps: S1 using a plurality of documents as input, pretreating each document, i.e. the documents are broken up into clauses, and the clauses are broken up into words, so as to obtain a noun group and a verb group in a multi-document group, and performing emantic disambiguation processing on polysemes in the noun group and the verb group; S2 respectively performing word clustering analysis on the noun group and the verb group which are output in the step S1 according to word similarity by adopting an improved OPTICS algorithm, extracting semantic concepts, and establishing vector space models on the clauses according to the semantic concepts; S3 performing clustering analysis on the clauses by using an improved K-medoid algorithm, so as to obtain a subject. Inner semantic relations between words are extracted by the multi-document subject discovery method, and the problem of non-orthogonality among feature items when feature vectors of the clauses are established is solved.
Owner:SOUTH CHINA UNIV OF TECH +2
RSS-based wireless spoofing attack positioning method
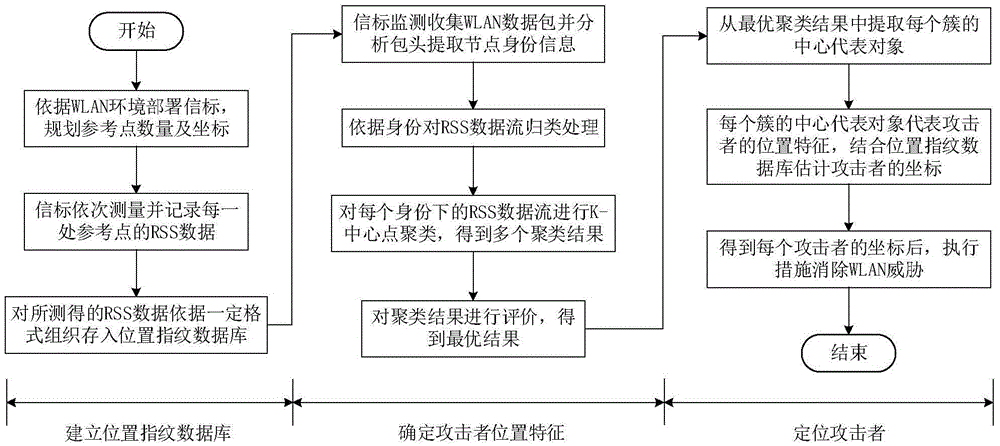
InactiveCN105554762AOvercome Cluster Analysis ImpactImprove positioning accuracyUsing reradiationLocation information based serviceNetwork packetWireless data
The invention discloses an RSS-based wireless spoofing attack positioning method. The method comprises steps: a position fingerprint database corresponding to a WLAN (Wireless Local Area Network) environment is built; a beacon is adopted to monitor wireless data packets in the WLAN in real time, and an RSS data flow for each node is further acquired; a K-medoid algorithm is used for selecting multiple K values, and according to a corresponding clustering result after each K value carries out clustering on the RSS data flow for each node sequentially, multiple clustering results for each node can be acquired finally; after the acquired multiple clustering results for each node are evaluated, the optimal clustering result corresponding to each node is acquired; and after a representative object of multiple clusters in the optimal clustering result is acquired sequentially, the position fingerprint database is combined to calculate and acquire the position coordinates of an attacker, and a positioning result is outputted. One or more attackers can be positioned, the positioning accuracy is high, and the method of the invention can be widely applied to the wireless information safety field.
Owner:GUANGDONG UNIV OF TECH
Bug knowledge modeling method based on graphic database
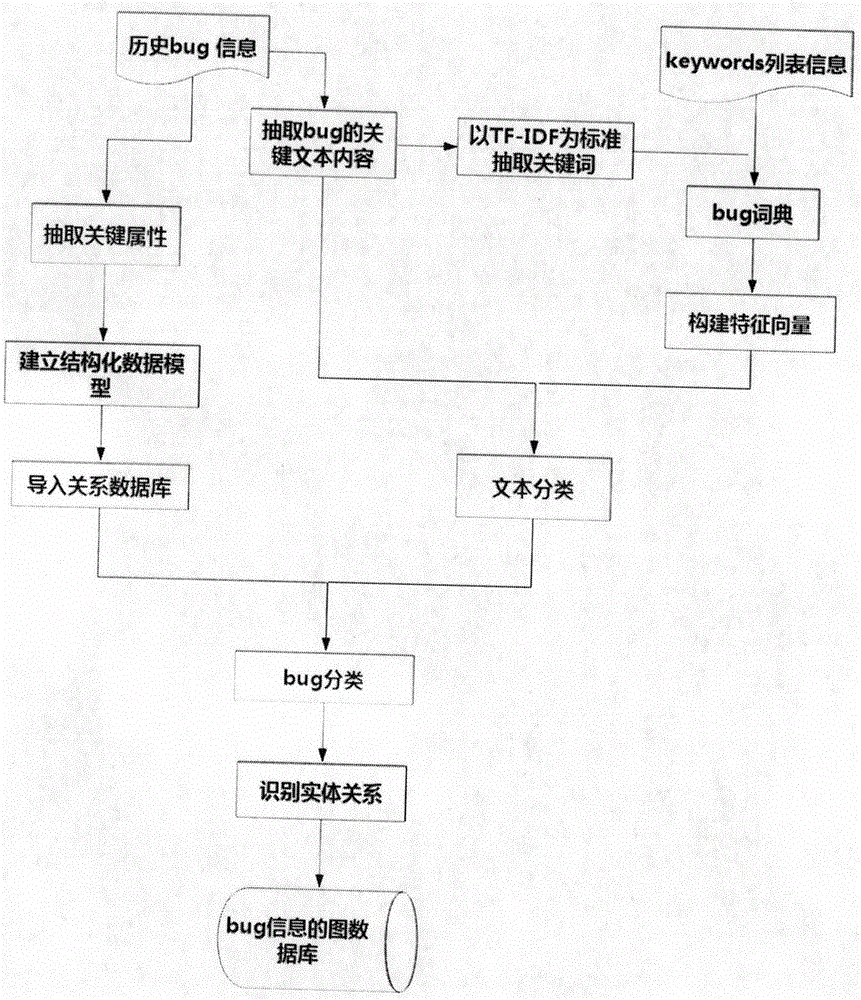
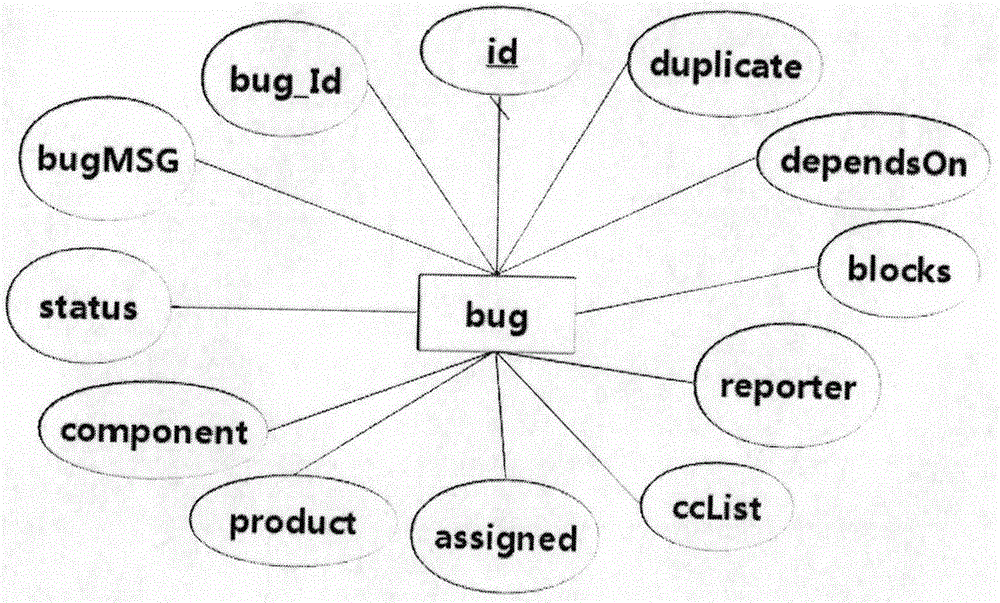
ActiveCN105608232ADeepen understandingAccelerated settlementStill image data indexingSpecial data processing applicationsFeature vectorGraphics
The invention relates to a bug knowledge modeling method based on a graphic database. According to the method, term extraction is performed on short text content in bug information, and relatively important vocabularies in a document are selected by the adoption of the TF-IDF standard; feature vectors are established for comprehensively extracted terms, keywords provided by bugzilla and a dictionary built artificially, a KNN algorithm based on K-Medoids optimization is adopted for classifying sketch information (bug MSG) texts, description information (description) texts and comment information (comment) texts respectively, and therefore classification of corresponding bugs is realized. The method overcomes the defects of complexity, interlinkage, lower-structuralization data change and a large amount of table connection by means of an existing search method. According to the method, starting from the graphic database, a database of bug information is optimized, it is not limited to solution to a single problem, multi-angle correlation can be provided, and the graphic database is a high-performance data structural form used for storing data.
Owner:YANGZHOU UNIV
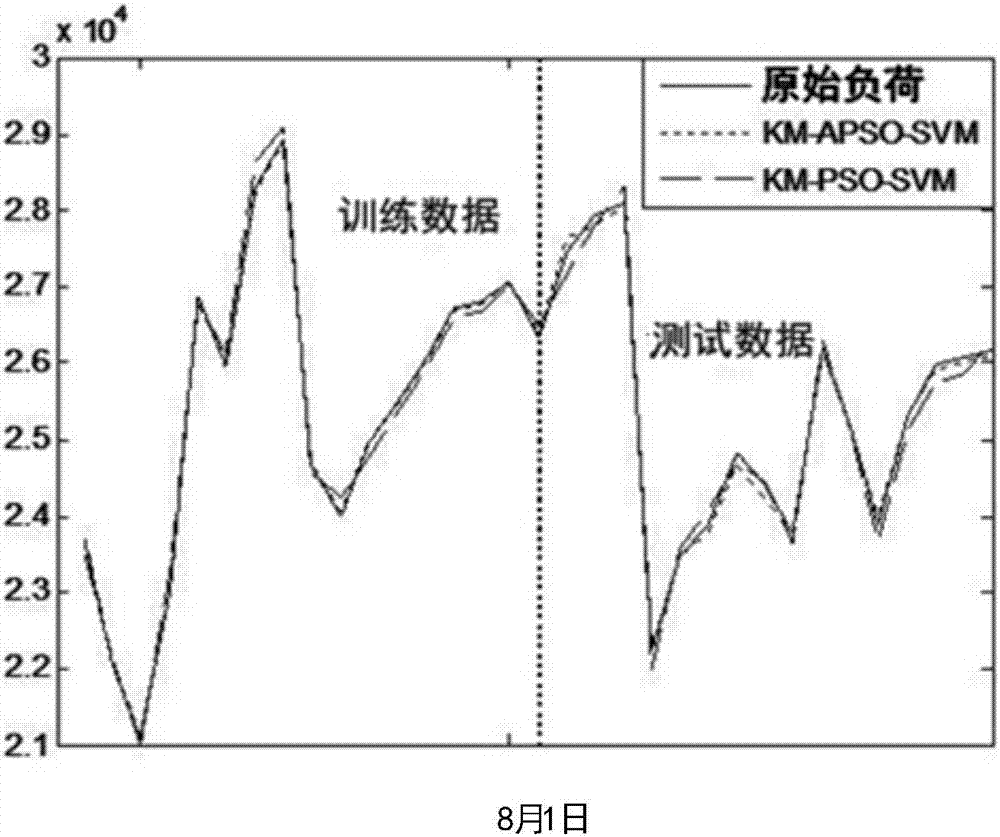
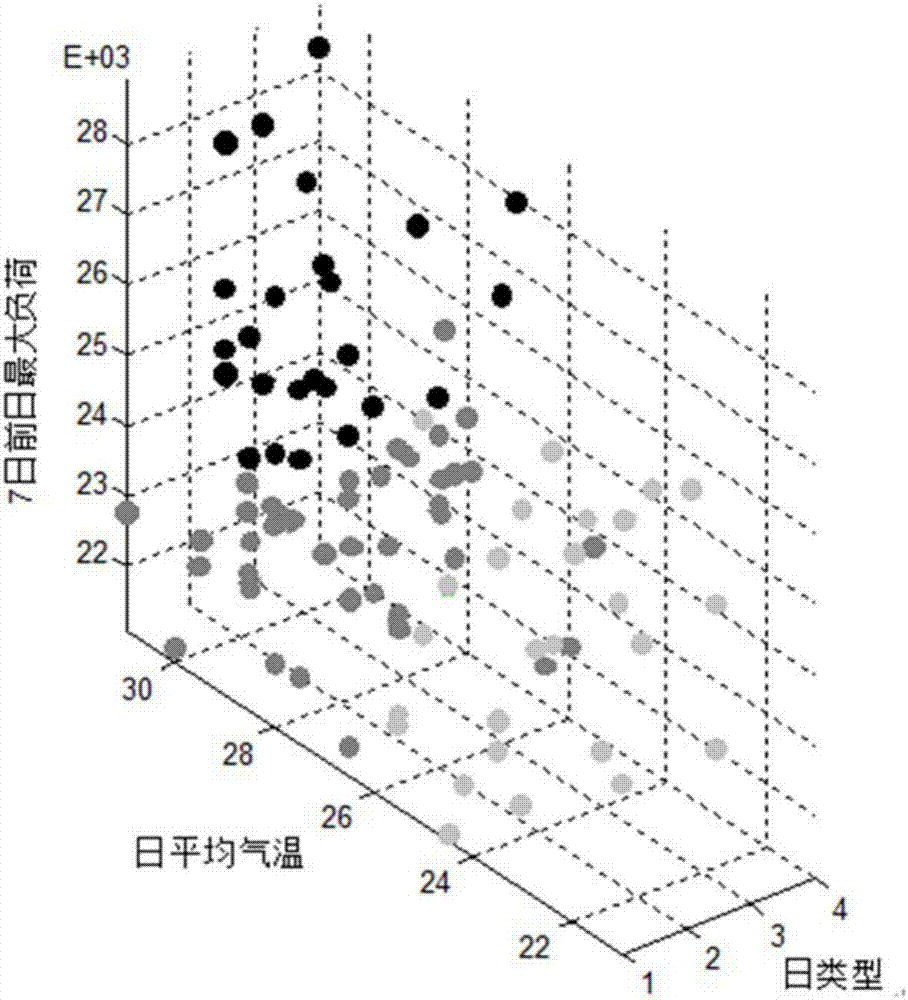
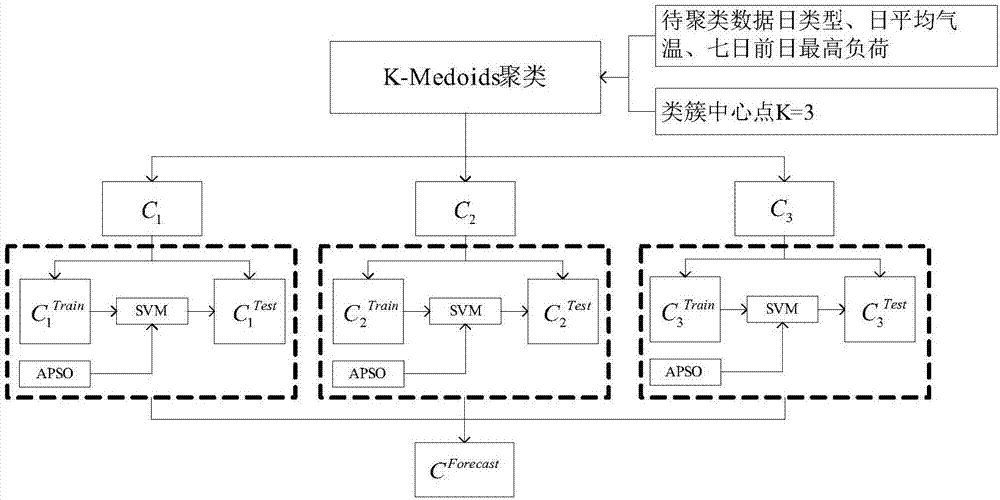
Short-term power load prediction method based on KM-APSO-SVM (K-medoids-Adaptive Particle Swarm Optimization-Support Vector Machine) model
InactiveCN107229993AImprove regularityGuaranteed prediction accuracyForecastingCharacter and pattern recognitionCluster algorithmSupport vector machine
The invention discloses a short-term power load prediction method based on a KM-APSO-SVM (K-medoids-Adaptive Particle Swarm Optimization-Support Vector Machine) model. The short-term power load prediction method comprises the following steps that: (1) on the basis of big data, carrying out the analysis of a power grid daily load change rule: collecting the data information of prediction site environment, utilizing grey relational analysis to analyze a relationship between each meteorological factor and a load, and laying a foundation for establishing a load prediction model; (2) applying a K-medoids clustering algorithm to carry out clustering analysis on a sample: arranging collected data to form a clustering sample, setting a classification number, selecting a relevant factor to form a sample feature vector, applying the K-medoids clustering algorithm to carry out the clustering analysis on the sample, and mapping to a specific zone through nondimensionalizign processing to form a clustering result; and (3) applying an APSO-SVM prediction model to carry out load prediction: carrying out accumulation preprocessing on the collected data to obtain a training sample, inputting the data of the clustering sample into the SVM to be trained, using the APSO to optimize SVM parameters, establishing a prediction model, and carrying out accumulation reduction on an obtained prediction result.
Owner:NORTH CHINA ELECTRIC POWER UNIV (BAODING)
Wind power plant aggregation method based on K-MEDOIDS aggregation
InactiveCN103886181ALow reliabilityLow costSpecial data processing applicationsDependabilityComputer science
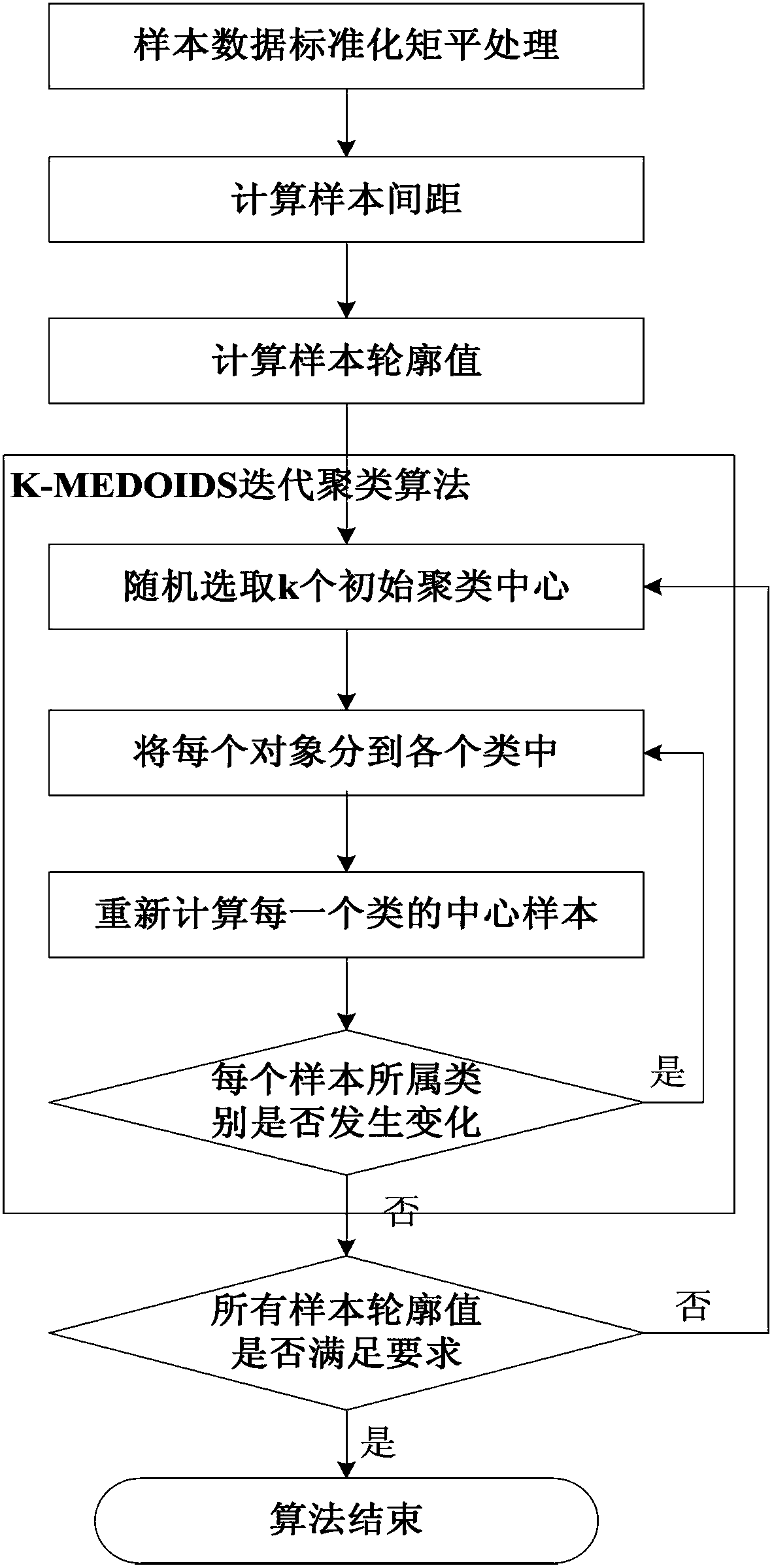
The invention discloses a wind power plant aggregation method based on K-MEDOIDS aggregation. The method mainly includes: performing data standardization moment flattening on to-be-measured wind power plant unit samples; calculating sample intervals according to the data standardization moment flattening results; calculating sample contour values according to the sample interval calculation results; performing K-MEDOIDS iteration aggregation calculation according to the sample contour value calculation values to obtain sample contour values and complete wind power plant aggregation. The method has the advantages that the defects of poor stability, low reliability, high cost and the like in the prior art can be overcome, and the method is good in stability, high in reliability and low in cost.
Owner:STATE GRID CORP OF CHINA +2
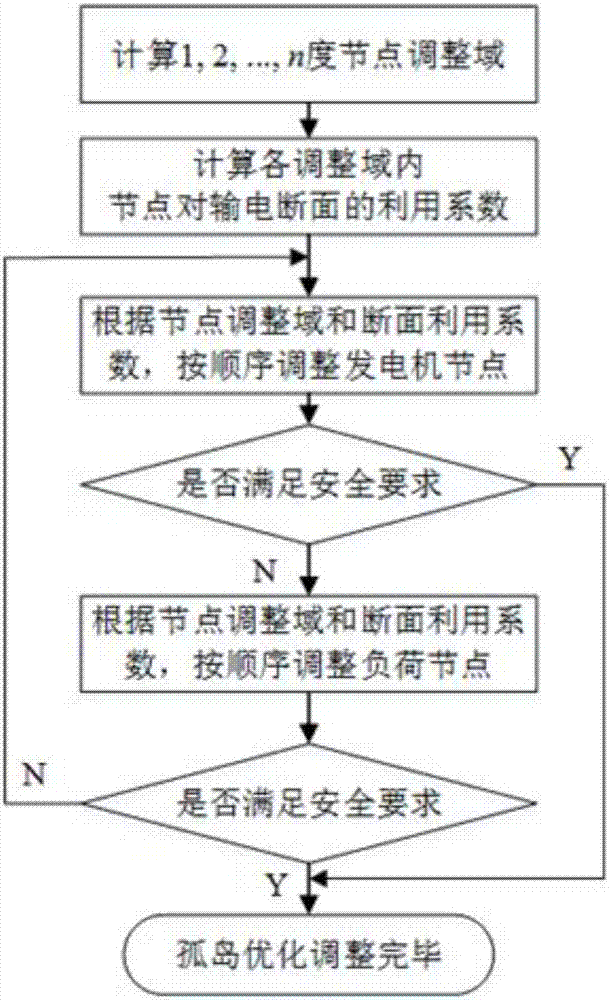
Active splitting section searching method for power system, and island adjustment strategy
ActiveCN107017632ACharacter and pattern recognitionAc network circuit arrangementsSearch problemCluster algorithm
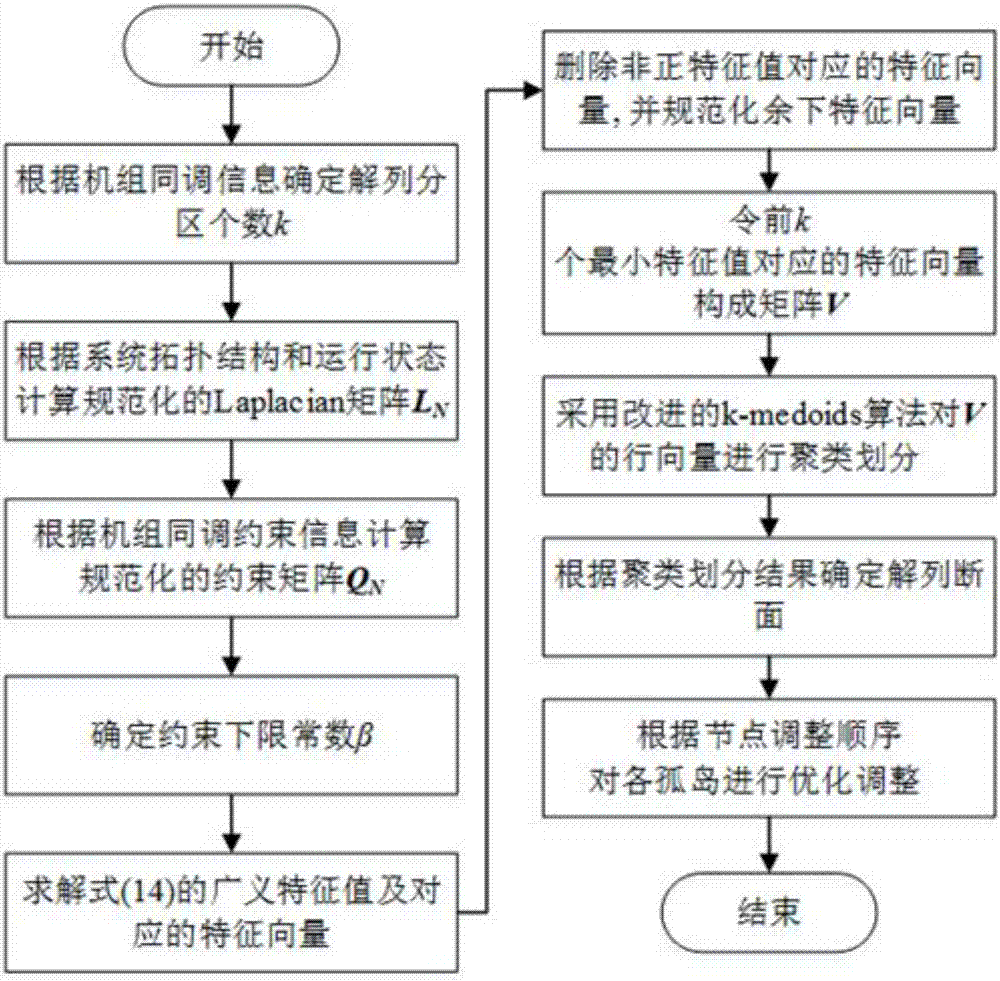
The invention proposes an active splitting section searching method for a power system, and an island adjustment strategy. The method improves a spectrum cluster algorithm developing in a machine learning field, and proposes a constraint-contained spectrum cluster algorithm so as to give consideration to the coherent constraints of a generator set, thereby enabling a splitting selection searching problem to be converted into a generalized eigenvalue solving problem. In order to iron out the defects that it is sensitive to an initial central point and the searching efficiency is low because the constraint-contained spectrum cluster algorithm employs a conventional k-medoids algorithm, proposes the improving of the k-medoids algorithm, and enables the k-medoids algorithm to be combined with the constraint-contained spectrum cluster algorithm, so as to solve an optimal splitting section. For each island which does not need the safety constraint, the output of the generator set is optimized and adjusted, and some loads can be reduced during needs, so as to meet the safety operation of each island. Finally, an IEED 118 node is taken as a sample, thereby indicating the feasibility and effectiveness of the method.
Owner:POWER DISPATCHING CONTROL CENT OF GUANGDONG POWER GRID CO LTD +1
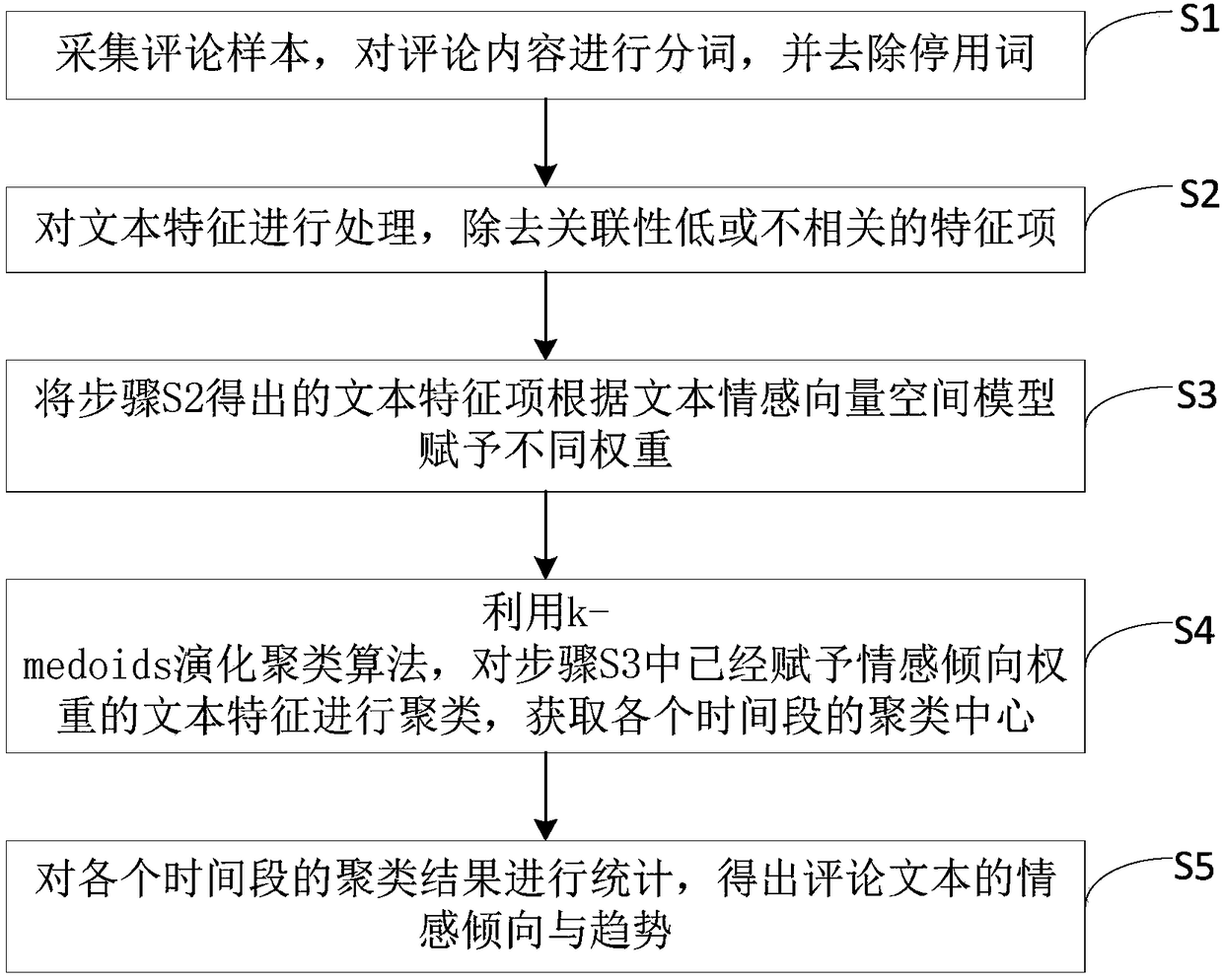
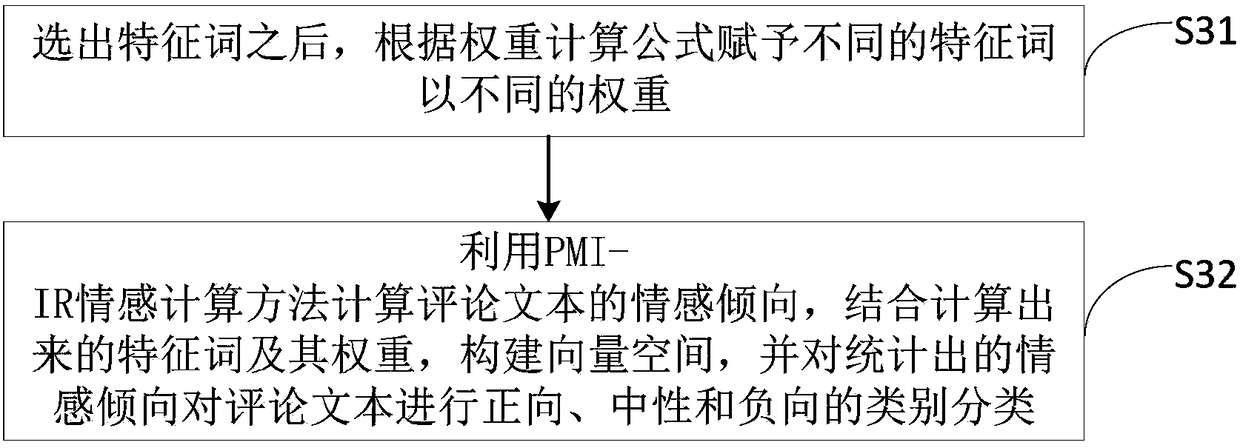
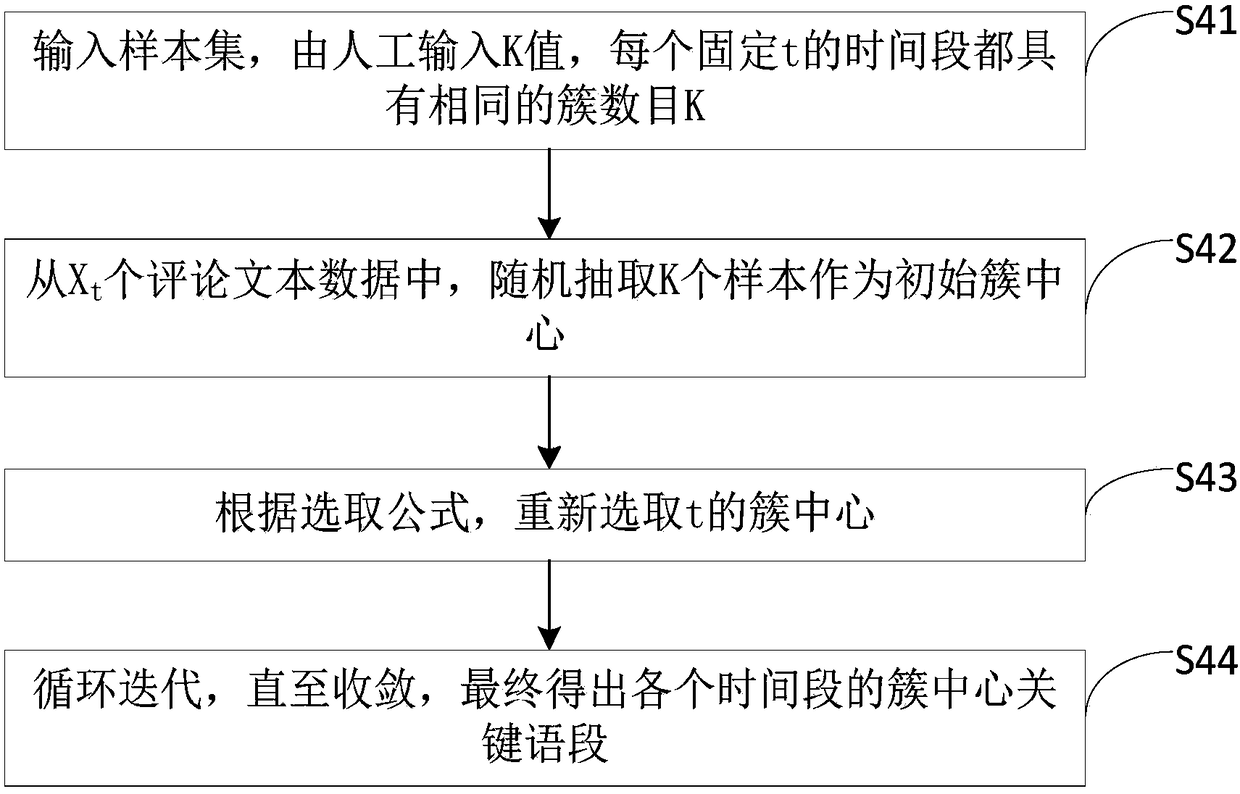
Method for comment text classified extraction based on evolution clustering
InactiveCN108268470ASolve the problem of "sparseness"Increased sensitivitySpecial data processing applicationsText database clustering/classificationCluster algorithmText categorization
The invention provides a method for comment text classified extraction based on evolution clustering. The method comprises: step S1, acquiring comment samples, performing word segmentation on commentcontents, and removing stop words; step S2, processing text features, removing feature items which are in low relevance or are irrelevant; step S3, according to a textual emotion vector space model, giving different weights to the text feature items; step S4, using a k-medoids evolution clustering algorithm to cluster the text features; step S5, counting clustering results in each time period, todraw a conclusion. Compared with the prior art, the method for comment text classified extraction based on evolution clustering solves a problem of data sparsity which the text features may face, andreduces calculation complexity. The method has high susceptibility and good stability on abnormal data, and has relatively high clustering precision.
Owner:GUANGDONG KINGPOINT DATA SCI & TECH CO LTD
Machine-learning-based spectrum sensing method and apparatus
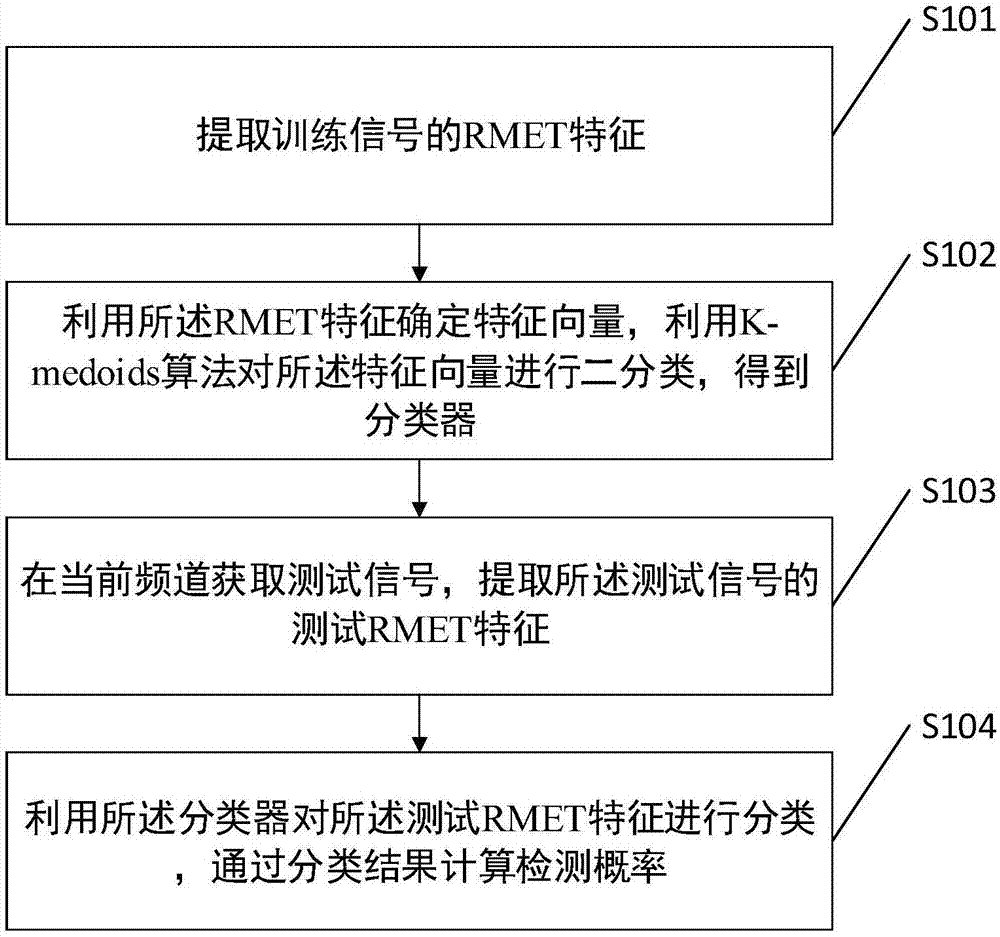
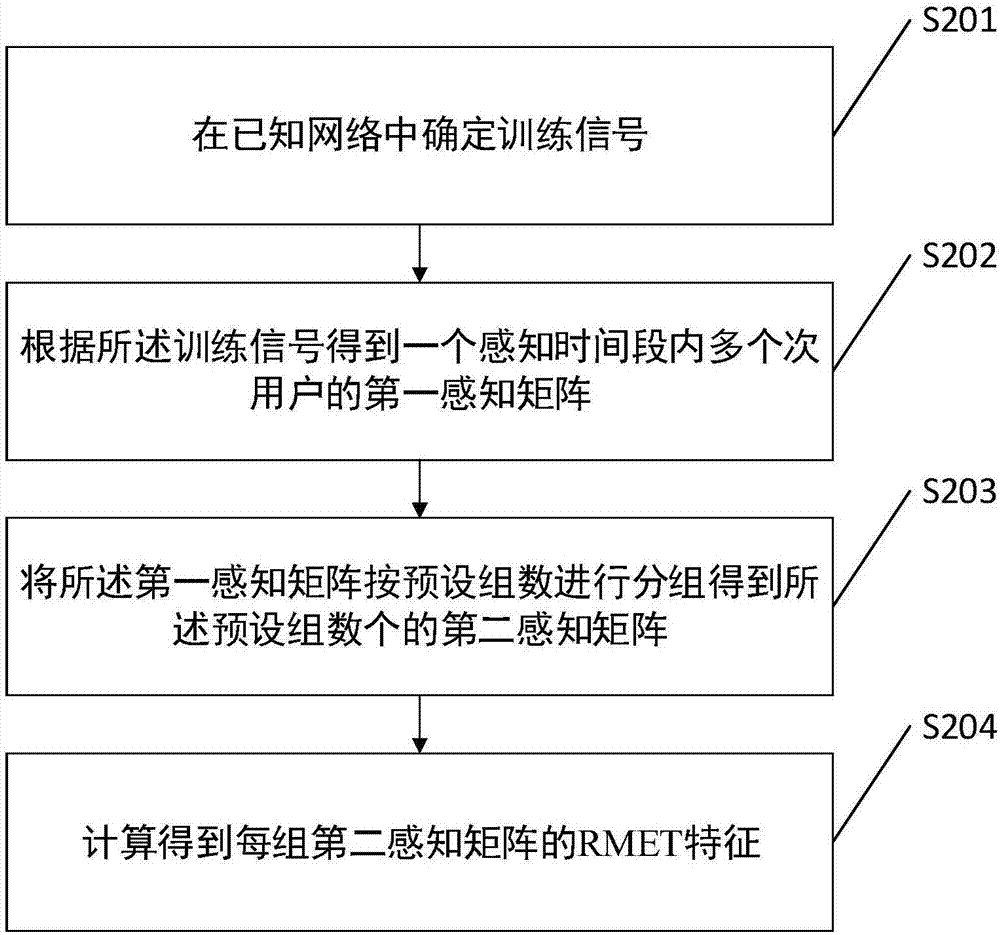
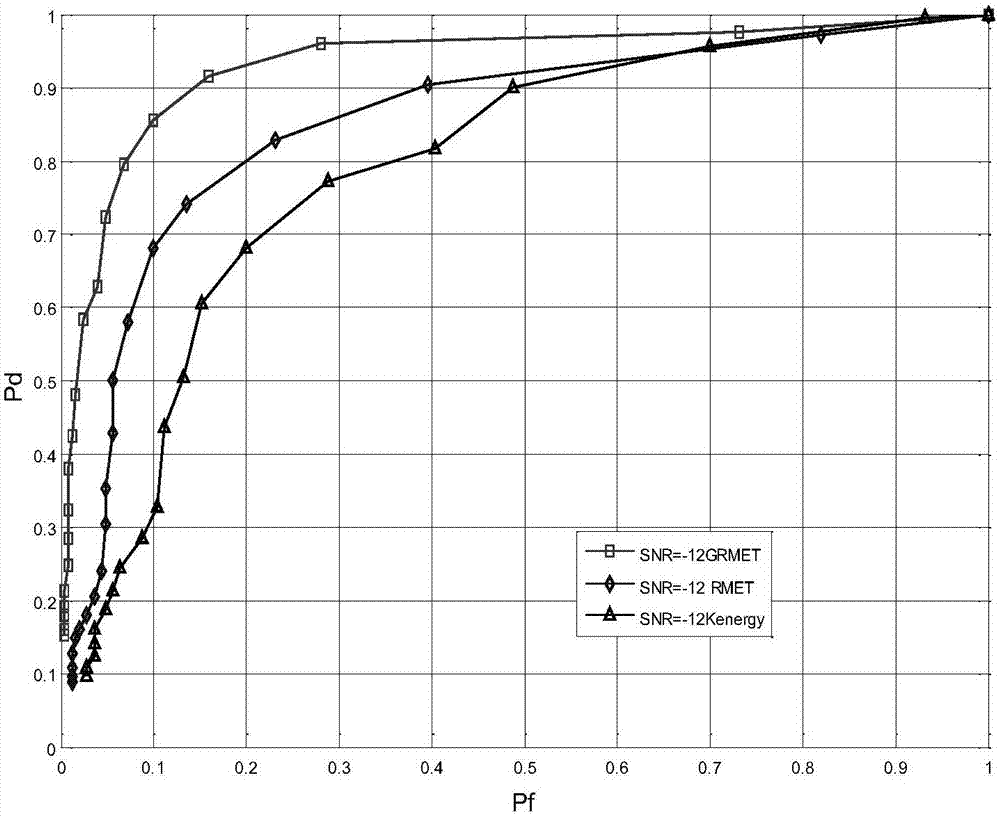
ActiveCN107360577AImprove accuracyTransmission monitoringNetwork planningLearning basedFeature vector
The invention discloses a machine-learning-based spectrum sensing method. An RMET feature of a training signal is extracted; a feature vector is determined based on the RMET feature and a classifier is determined according to a K-medoids algorithm and the feature vector; a testing signal is obtained at a current channel and a testing RMET feature of the testing signal is extracted; and the testing RMET feature is classified by using the classifier and a detection probability is calculated based on the classification result. According to the method disclosed by the invention, the RMET is used as the feature; the K-medoids algorithm is used for classification; the classifier is trained; data of the testing signal are inputted into the classifier to carry out classification and the classification result is obtained. On the basis of combination of the RMET and the K-medoids, whether a channel is available is sensed, so that the accuracy of detection is improved.
Owner:佛山国防科技工业技术成果产业化应用推广中心
Method and system for realizing data leakage prevention
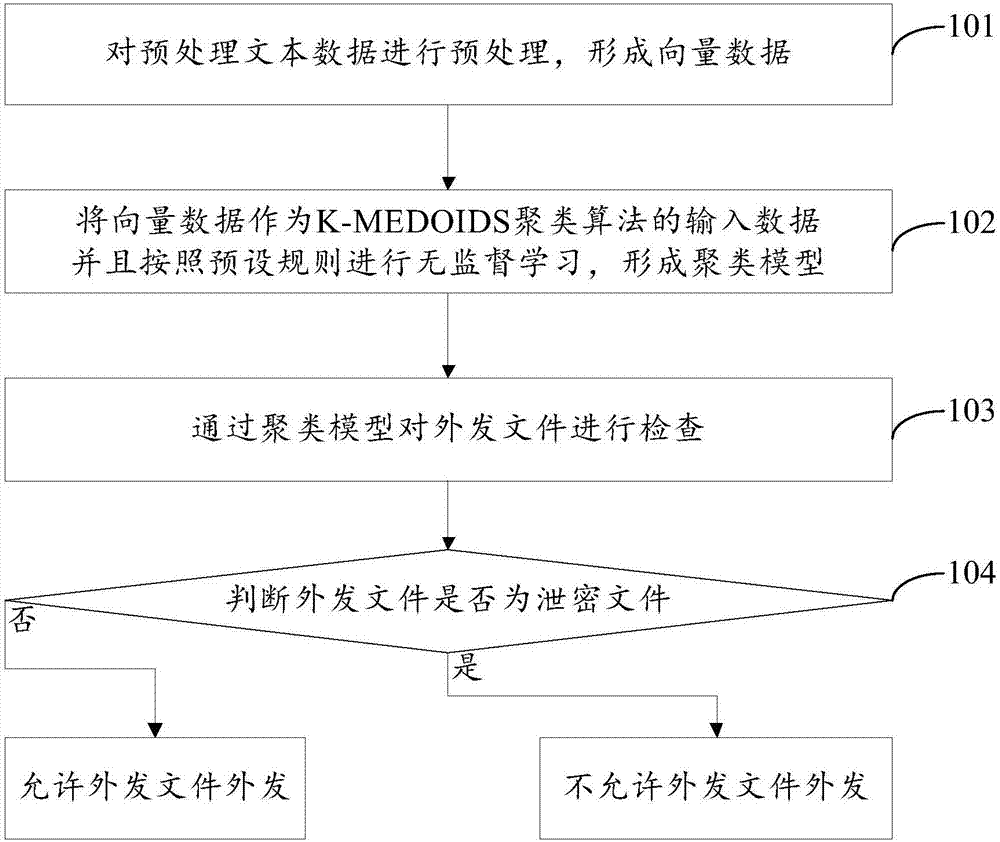
InactiveCN107292193ASolve the problem of finding more rigidSolve undetected problemsDigital data protectionNatural language data processingK-medoidsUnsupervised learning
The invention discloses a method and a system for realizing data leakage prevention. The method comprises the steps that preprocessed text data is preprocessed to form vector data; the vector data is used as input data of a K-MEDOIDS clustering algorithm, and unsupervised learning is performed according to preset rules to form a clustering model; an external release file is detected through the clustering model; whether the external release file is a secret leakage file is judged; if yes, the external release file is not allowed to be released externally; and otherwise the external release file is allowed to be released externally. The K-MEDOIDS clustering algorithm is adopted to perform unsupervised learning training on the preprocessed text data, the external release file is detected through the clustering model, and therefore the problems that in traditional DLP technologies, keyword search is hidebound in a basic detection technology, and a file cannot be detected through an EDM and an IDM after file content is modified in an advanced detection technology are solved; and meanwhile, the number of categories of the K-MEDOIDS algorithm does not influence the clustering result, the algorithm is more flexible than an SVM algorithm, and the detection result of the file cannot be influenced even under the condition that a keyword is replaced.
Owner:BEIJING VRV SOFTWARE CO LTD
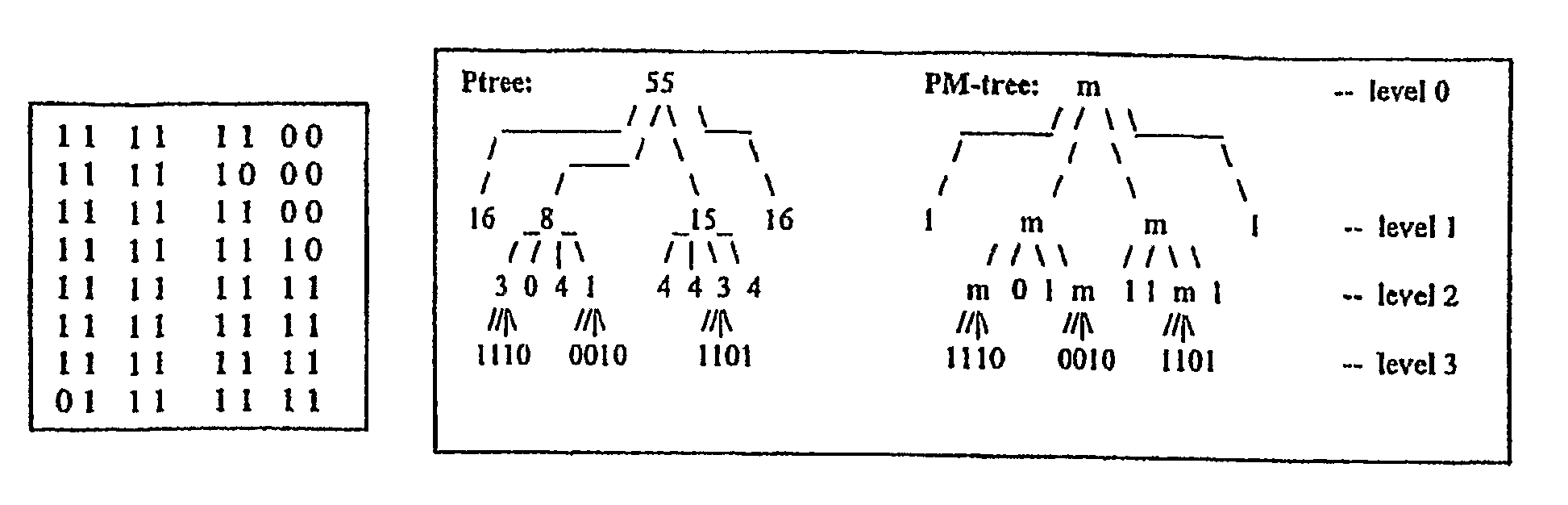
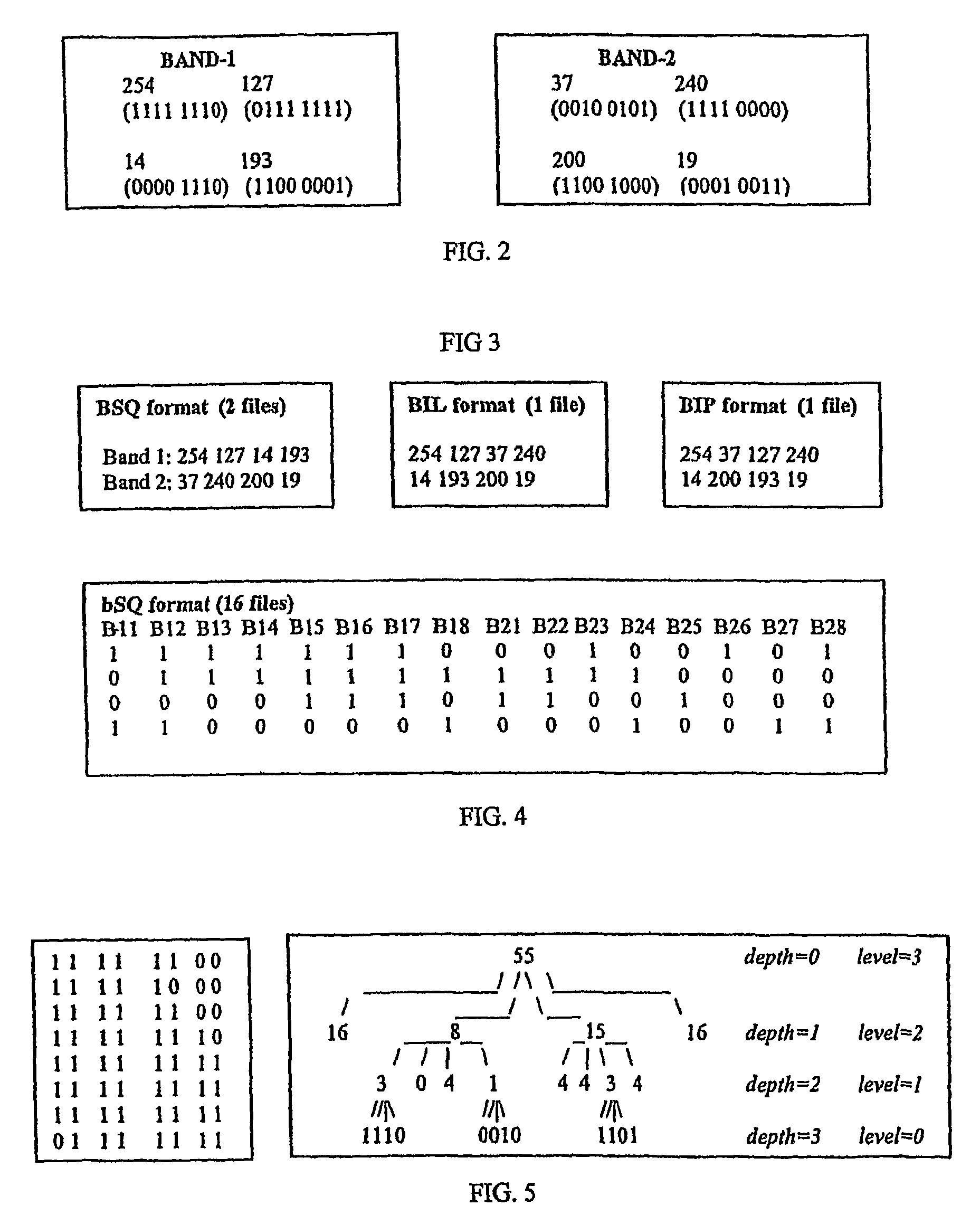
Method and system for data mining of very large spatial datasets using vertical set inner products
InactiveUS7836090B2SpeedThe process is fast and accurateDigital data processing detailsCharacter and pattern recognitionData setFixation point
A system and method for performing and accelerating cluster analysis of large data sets is presented. The data set is formatted into binary bit Sequential (bSQ) format and then structured into a Peano Count tree (P-tree) format which represents a lossless tree representation of the original data. A P-tree algebra is defined and used to formulate a vertical set inner product (VSIP) technique that can be used to efficiently and scalably measure the mean value and total variation of a set about a fixed point in the large dataset. The set can be any projected subspace of any vector space, including oblique sub spaces. The VSIPs are used to determine the closeness of a point to a set of points in the large dataset making the VSIPs very useful in classification, clustering and outlier detection. One advantage is that the number of centroids (k) need not be pre-specified but are effectively determined. The high quality of the centroids makes them useful in partitioning clustering methods such as the k-means and the k-medoids clustering. The present invention also identifies the outliers.
Owner:NORTH DAKOTA STATE UNIV RES FOUND
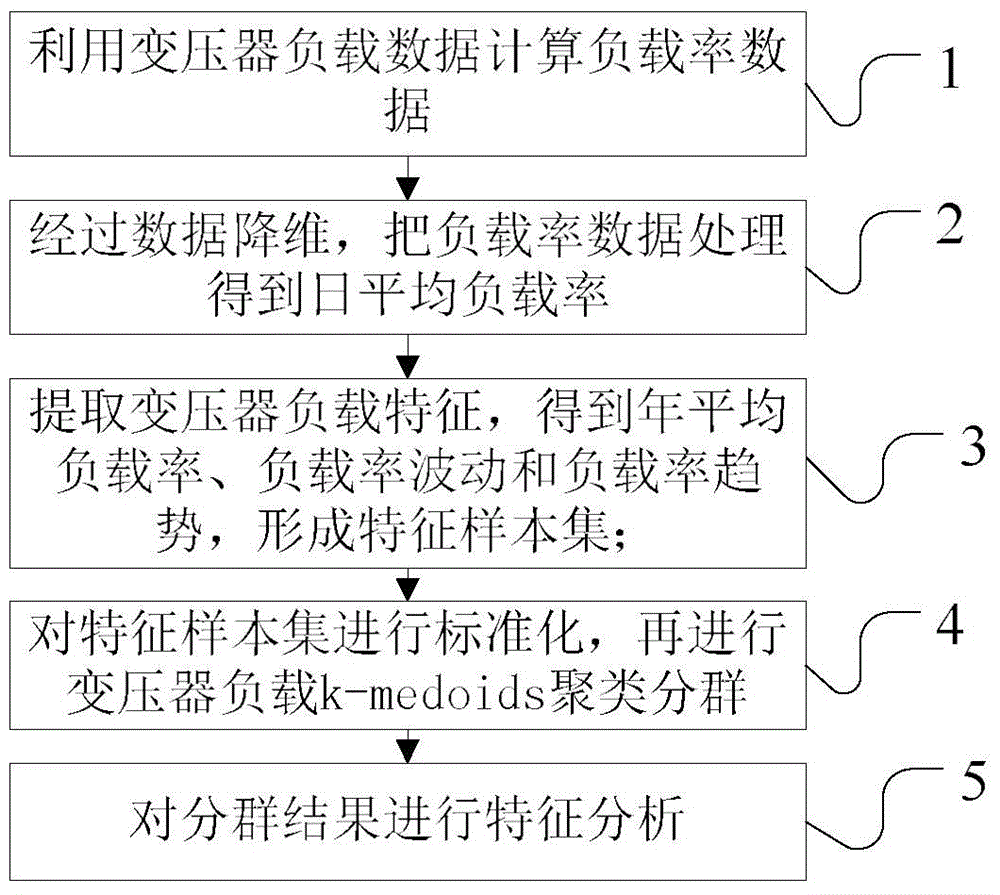
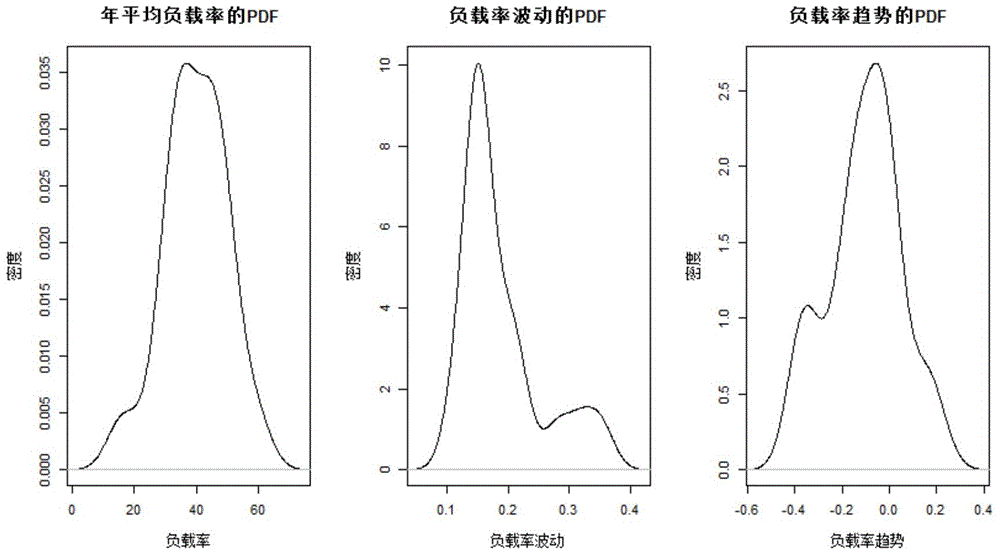
Transformer grouping method based on load characteristic analysis
ActiveCN104318489AEasy to classifyData processing applicationsSpecial data processing applicationsTransformerDimensionality reduction
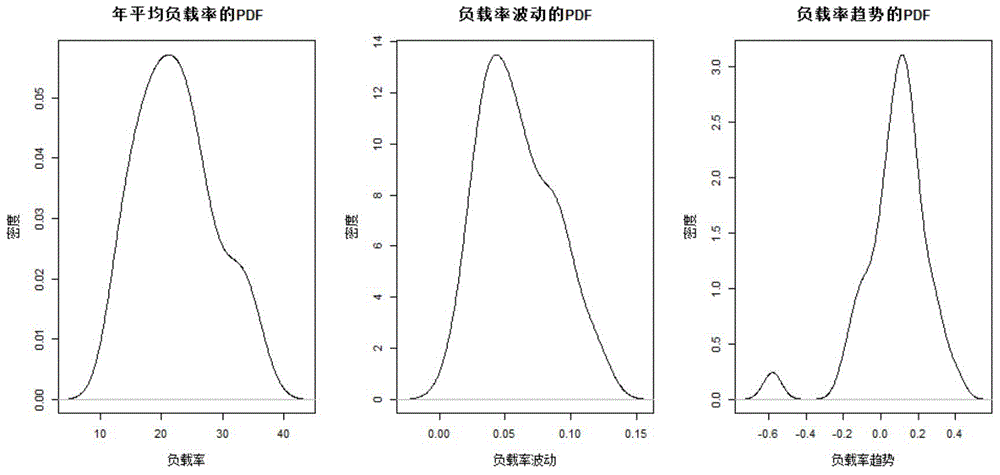
Disclosed is a transformer grouping method based on load characteristic analysis. The transformer grouping method based on load characteristic analysis includes the following steps that firstly, transformer load data are processed to form load rate data, and dimensionality reduction is performed to extract three transformer load characteristics such as annual average load rate, load rate fluctuation and load rate trend; then transformer load characteristic samples are formed through index calculation, and a characteristic sample set is subjected to standardization and to clustering grouping processing by a k-medoids algorithm; finally, grouping results are subjected to characteristic analysis. The transformer grouping method based on load characteristic analysis is provided in consideration of differences of different transformer load characteristics, transformer operation grouping results and suggestions are obtained, and a technological means is provided for grasping transformer economical operation conditions and trends.
Owner:ELECTRIC POWER RES INST OF GUANGDONG POWER GRID
High-resolution remote sensing image scene multi-label classification method based on multi-packet fusion
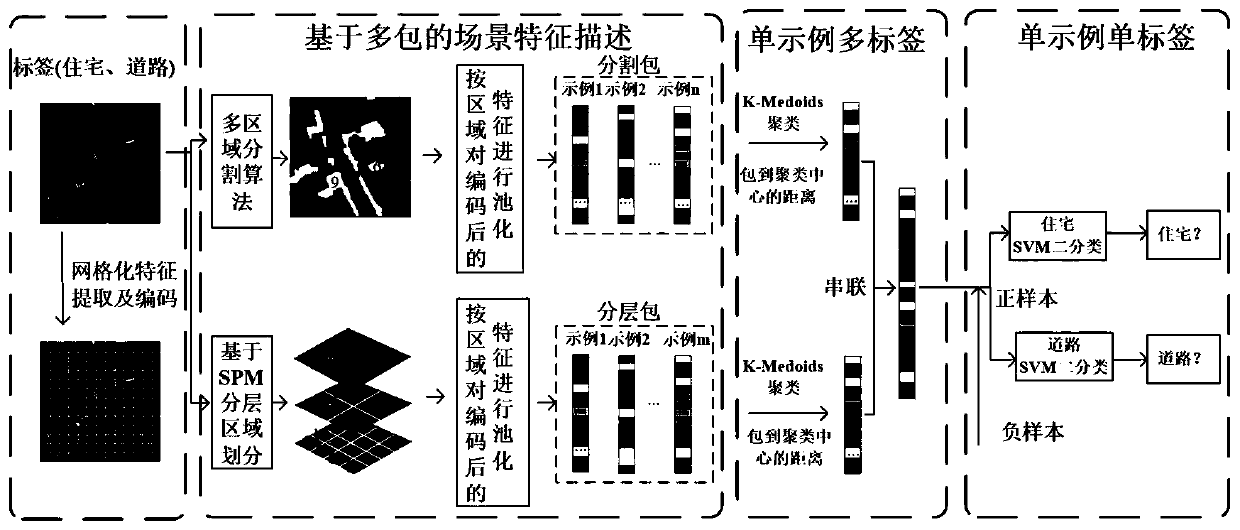
ActiveCN110210534ASolve the defect of losing the correlation information between targetsAvoid defectsScene recognitionMulti-label classificationMahalanobis distance
The invention discloses a high-resolution remote sensing image scene multi-label classification method based on multi-packet fusion. The method comprises the following steps: firstly, extracting multiple heterogeneous features on a high-resolution remote sensing image according to grid division and performing encoding; secondly, dividing sub-regions through a layering method and a segmentation method to pool the coded features, and obtaining a layering example package and a segmentation example package; using Mahalanobis distance to cluster the packets by a K-Medoids method, solving distancesfrom the packets to all clustering centers, and forming vectors by all distance values, so as to convert a multi-instance packet into a single instance; carrying out series fusion on the obtained single examples; and finally, designing a plurality of binary classifiers through a pair of other methods to solve the multi-label problem. According to the multi-packet fusion-based high-resolution remote sensing image scene multi-label classification method provided by the invention, the classification performance is improved, and a more excellent classification result is obtained compared with an existing classification method.
Owner:HOHAI UNIV
Full-coverage granular computing based K-medoids text clustering method
InactiveCN107908624AReduce complexityImprove accuracyCharacter and pattern recognitionNatural language data processingDensity basedK-medoids
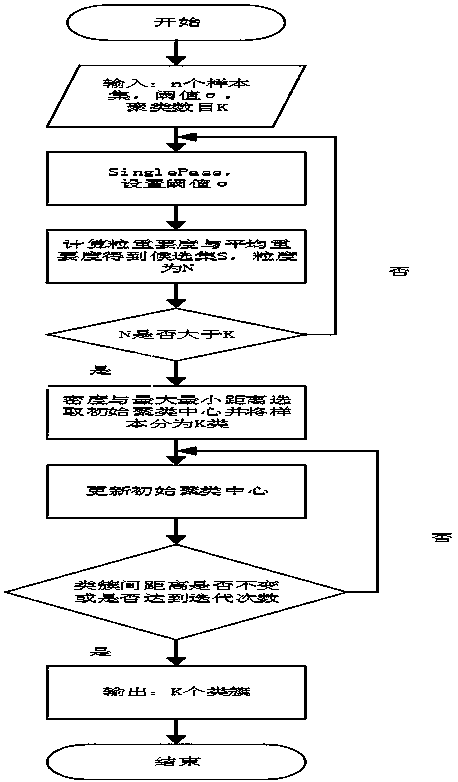
The invention discloses a full-coverage granular computing based K-medoids text clustering method. The method comprises the steps of 1) preprocessing texts, including, Chinese word segmentation and stop word removal; 2) performing characteristic extraction on the texts, setting a high frequency word threshold and a low frequency word threshold, filtering away high-frequency words with insufficientdiscrimination degrees and low-frequency words with weak representativeness, and then building a word vector spatial model by utilizing a TF-IDF algorithm; and 3) clustering the texts, firstly performing coarse clustering on the texts by utilizing single-pass and calculating an initial clustering center candidate set by utilizing a concept of granularity importance of a full-coverage granular computing theory, and then calculating an initial clustering center based on the density and a maximum-minimum distance algorithm, and finally performing text clustering by utilizing a k-medoids algorithm. The full-coverage granular computing based K-medoids text clustering method solves the problems of iteration times increase and relatively big fluctuation of clustering results of the traditional K-medoids clustering algorithm in which the initial clustering center is selected randomly, and also solves the problem that the initial clustering center is located at the same type of the cluster inthe currently improved K-medoids clustering algorithm.
Owner:TAIYUAN UNIV OF TECH
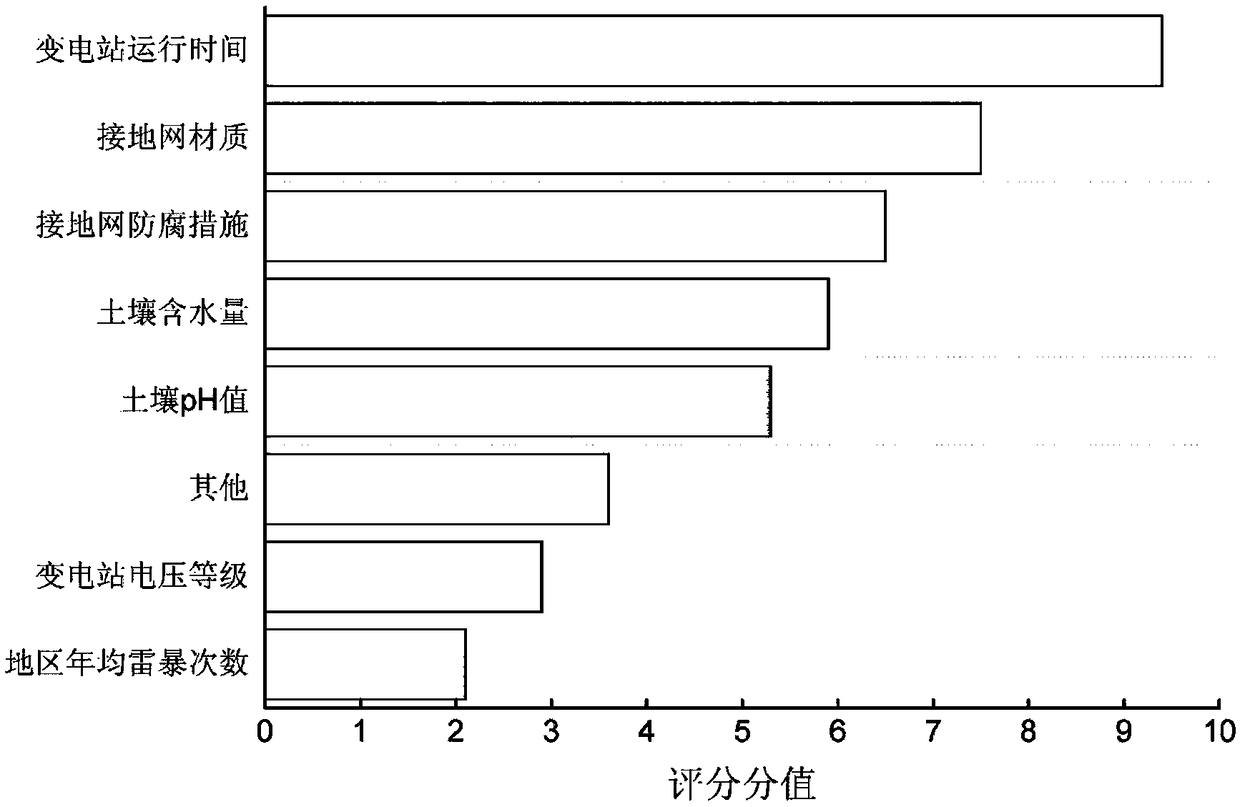
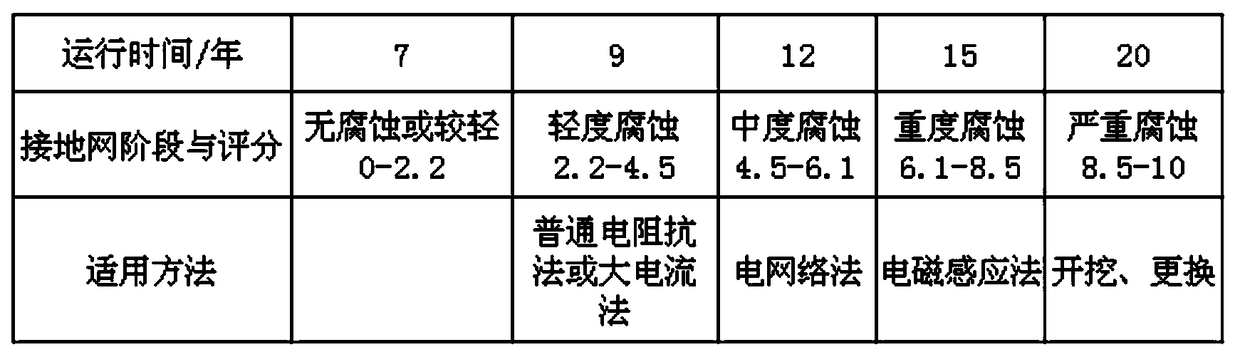
Method and device for predicting operation stage and service life of grounding grid of substation
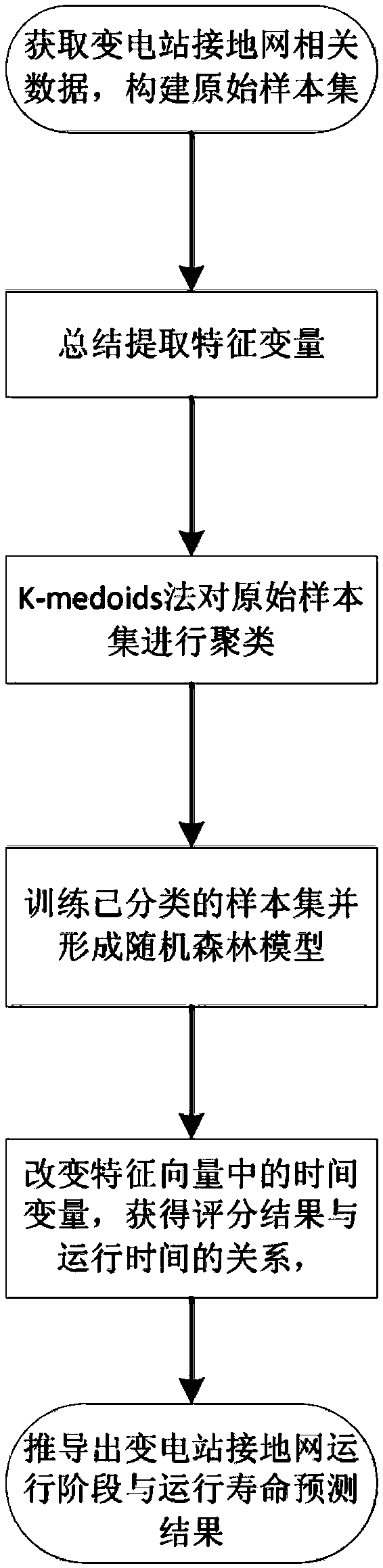
ActiveCN109507535AIncrease randomnessGeneralization error is controllableWeather/light/corrosion resistanceFault locationGeneralization errorAlgorithm
The invention discloses a method and device for predicting the operation stage and service life of a grounding grid of a substation based on the improved random forest algorithm. The method includes the following steps that initial data is obtained, and an original sample set is constructed; based on the characteristics of an original sample set, characteristic variables are extracted; the K-medoids method is used for clustering of the original sample set; the random forest algorithm is used for processing various samples, and a random forest model is formed; the to-be-predicted substation grounding grid characteristic variables are loaded into a random forest model, and the operation time in a feature vector is changed to obtain the relationship of an evaluation result and the operation time, and the predicted result of an operation stage and operation life are deduced. The randomness of the original sample set classification in the random forest algorithm is improved; the forest model is generated on the basis of the random forest algorithm, the generalization error is controllable, and the clustering accuracy is high; various factors affecting the state of the grounding grid ofthe substation are taken into account comprehensively, and different operation stages are divided to identify the corrosion state of the grounding grid in the corresponding stage through combination of the most suitable grounding grid fault detection method.
Owner:STATE GRID HENAN ELECTRIC POWER ELECTRIC POWER SCI RES INST +3
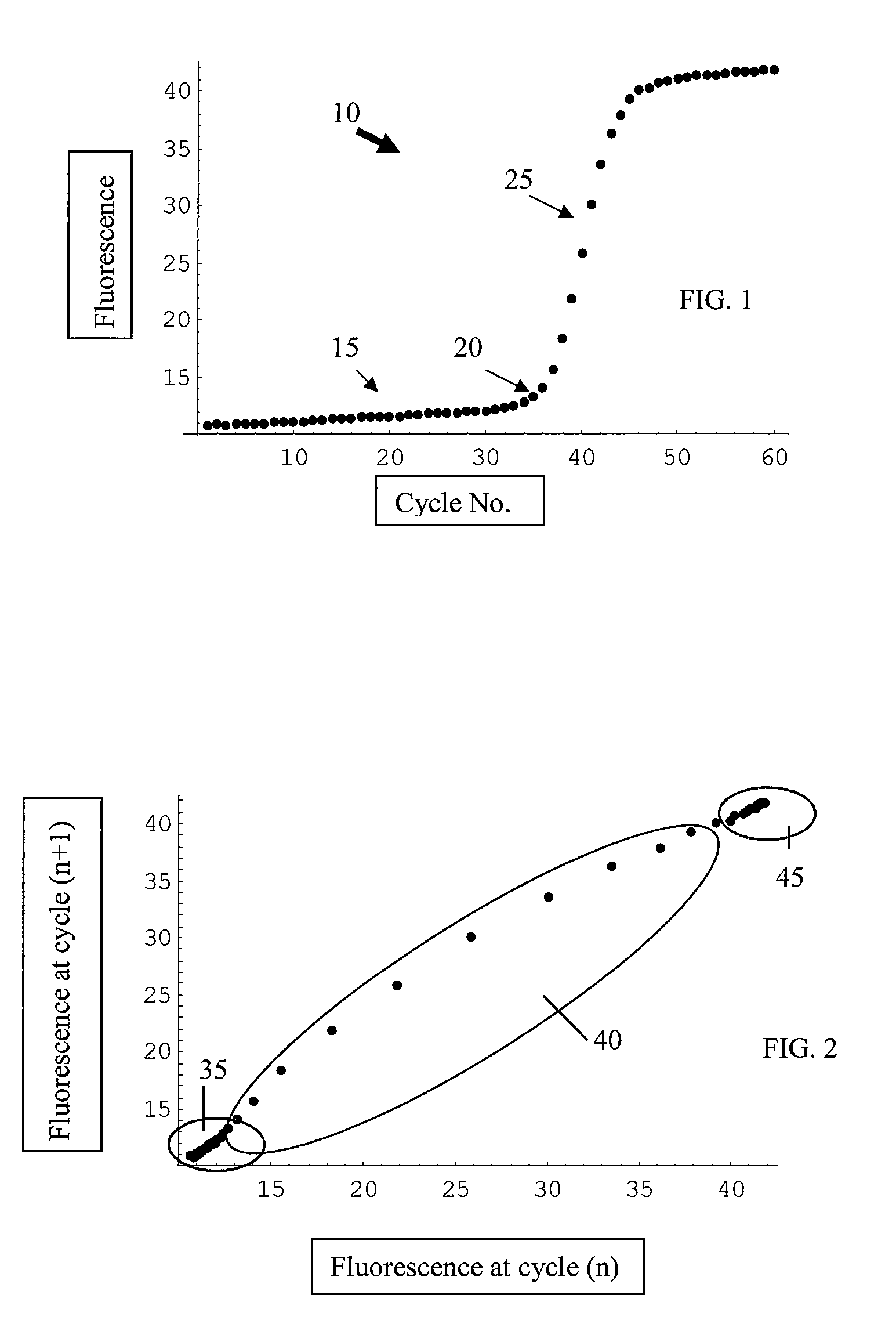
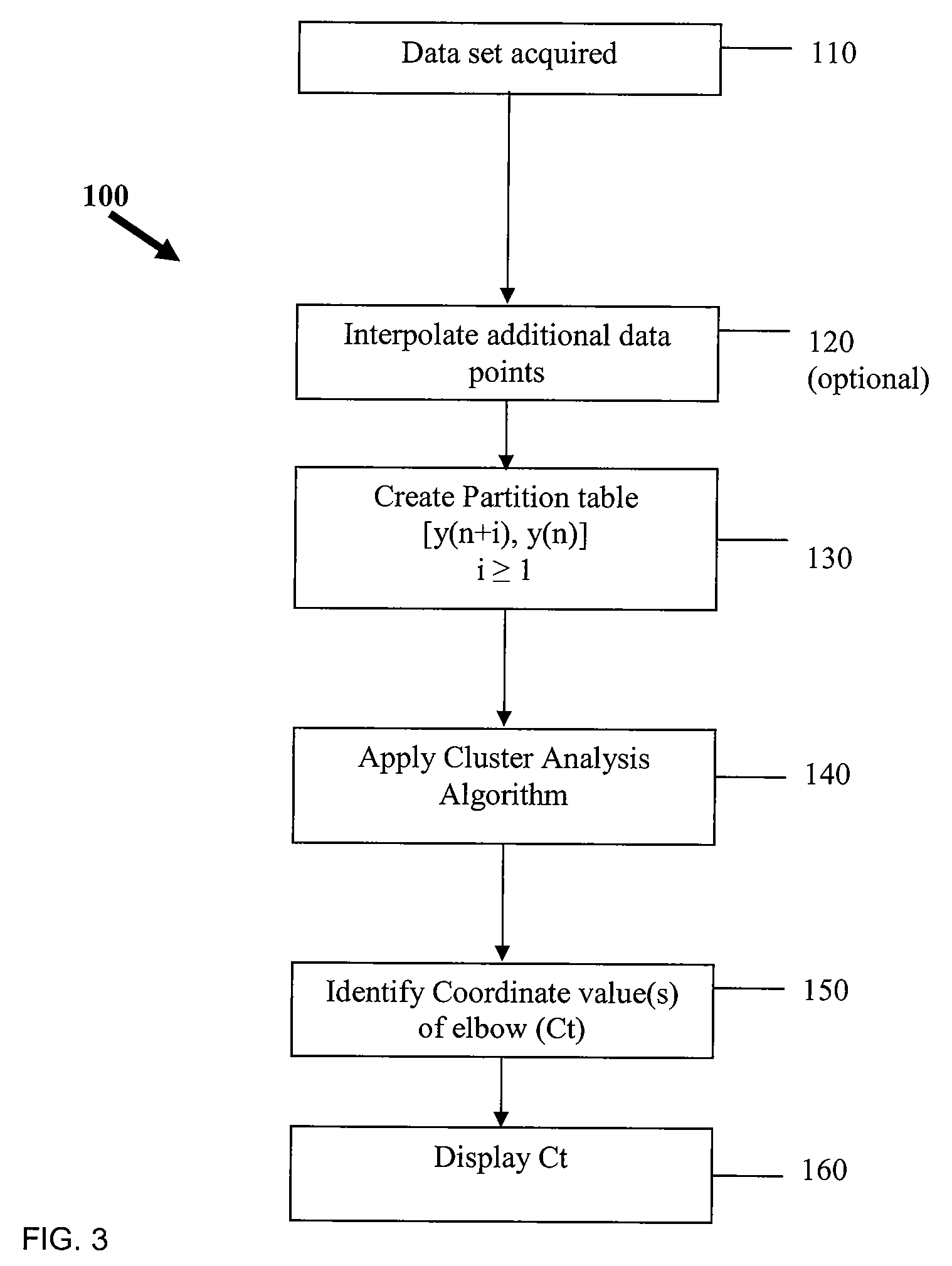
Ct determination by cluster analysis with variable cluster endpoint
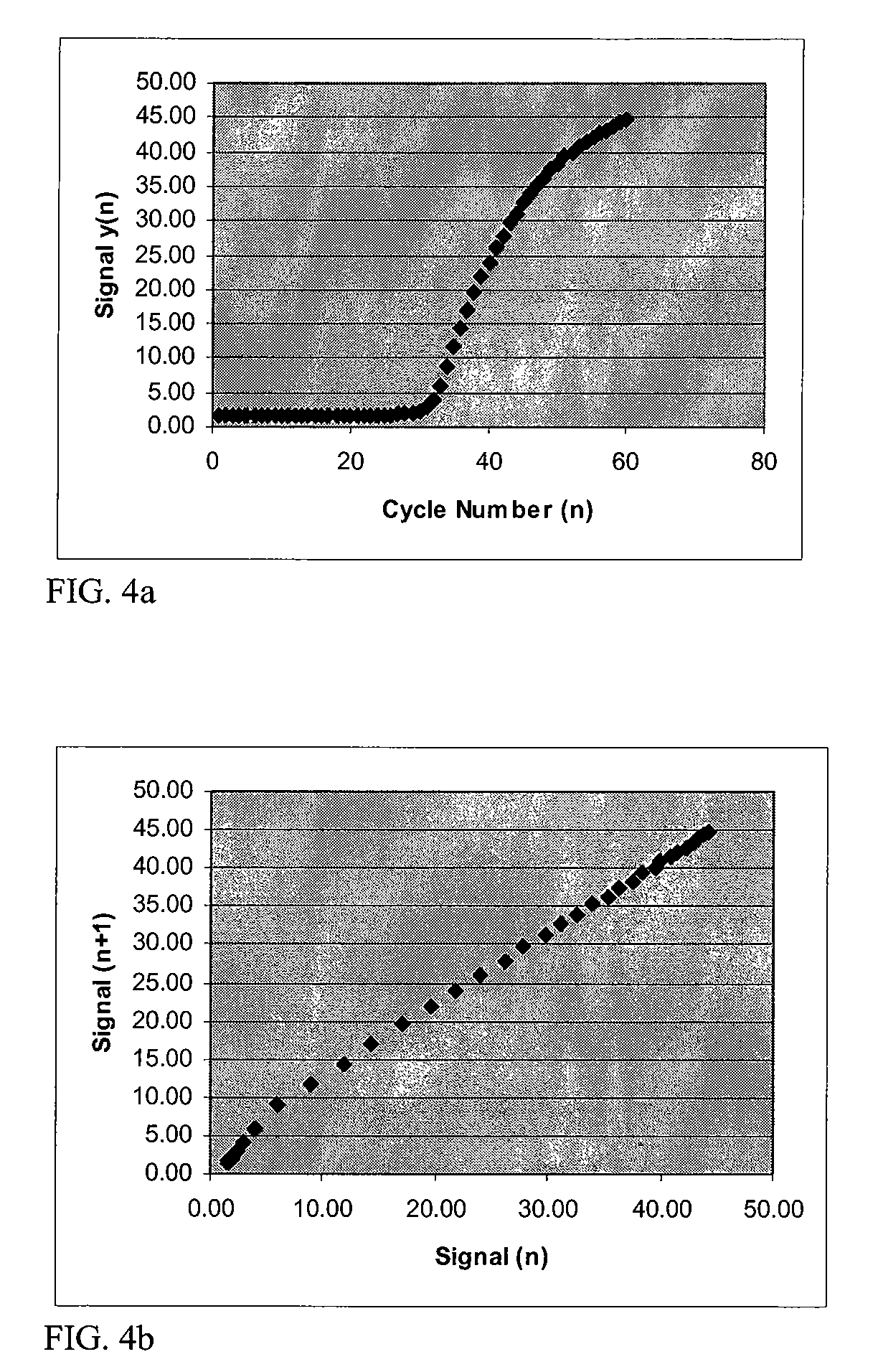
Systems and methods for determining the cycle threshold (Ct) value in a kinetic PCR amplification curve. The PCR data set may be visualized in a two-dimensional plot of fluorescence intensity (y-axis) vs. cycle number (x-axis). The data set is transformed to produce a partition table of data points with one column including the fluorescence at cycle (n) and a second column including the fluorescence at cycle (n+i), where i is typically 1 or greater. A cluster analysis process is applied to the partition table data set to determine a plurality of clusters in the partition table data set. In one aspect, the clustering process used includes a k-means clustering algorithm, where the number of identified clusters, k, is greater than or equal to three. In another aspect, a Partitioning Around Medoids (PAM) algorithm is used to identify three or more clusters. Using the identified clusters, a linear slope of each of the clusters is determined based on y(n+1) vs. n, and for each cluster, a ratio of the slope of that cluster with the slope of an adjacent cluster is determined. The ratios are then compared. An end point of a cluster having the largest or smallest ratio represents a specific point of interest in the data curve. The data point representing the elbow or Ct value of the PCR curve is identified as an end point of one of the identified clusters, and the cycle number corresponding to this data point is returned or displayed.
Owner:ROCHE MOLECULAR SYST INC
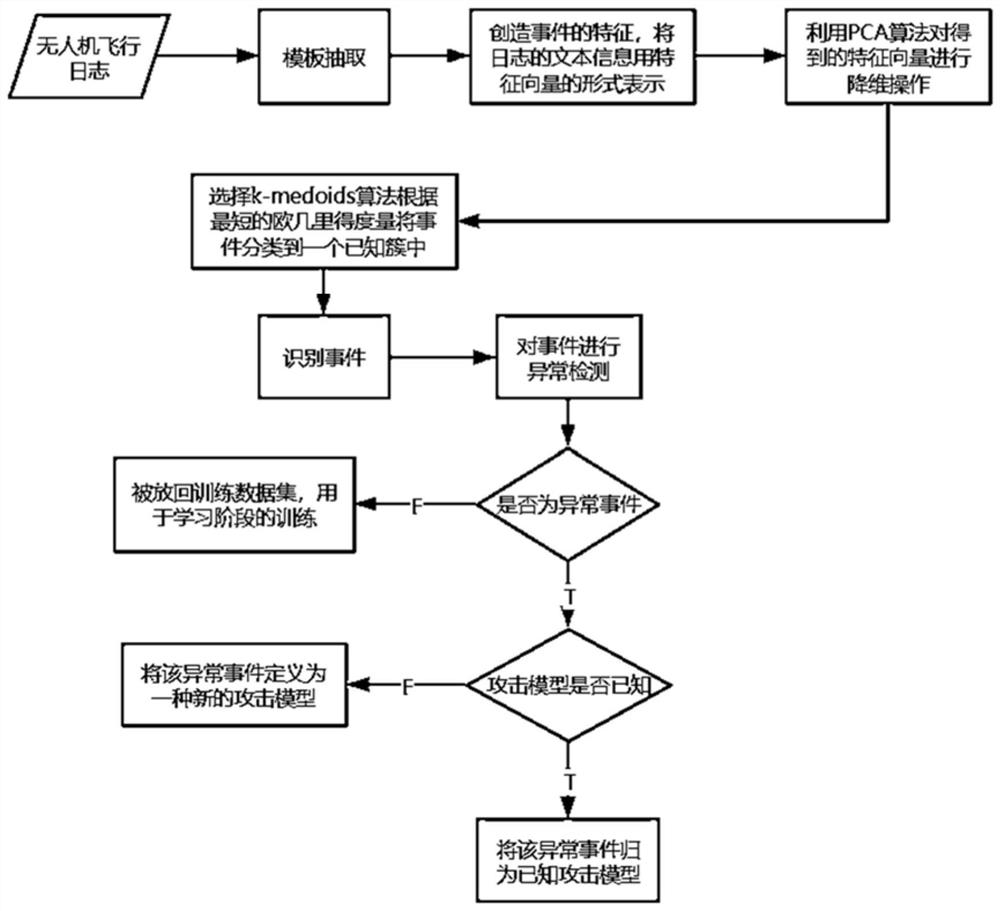
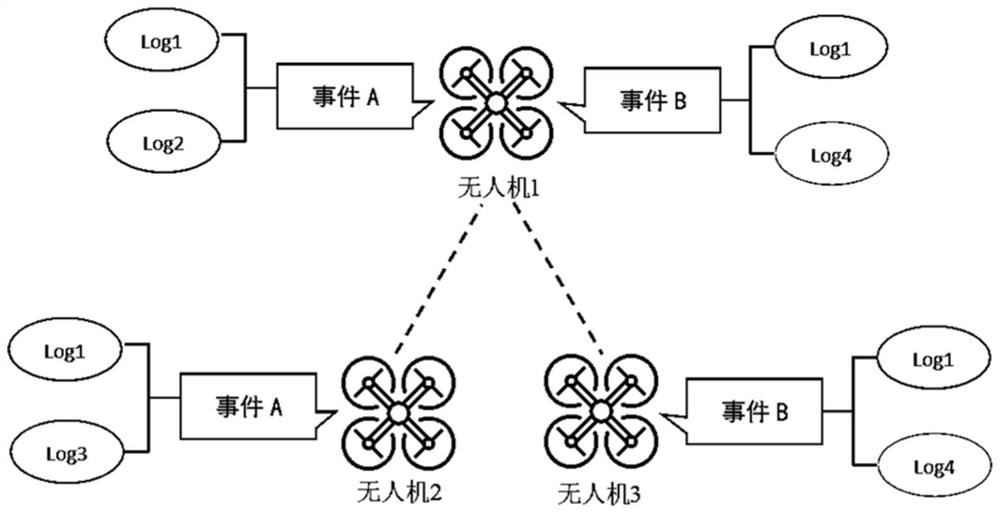
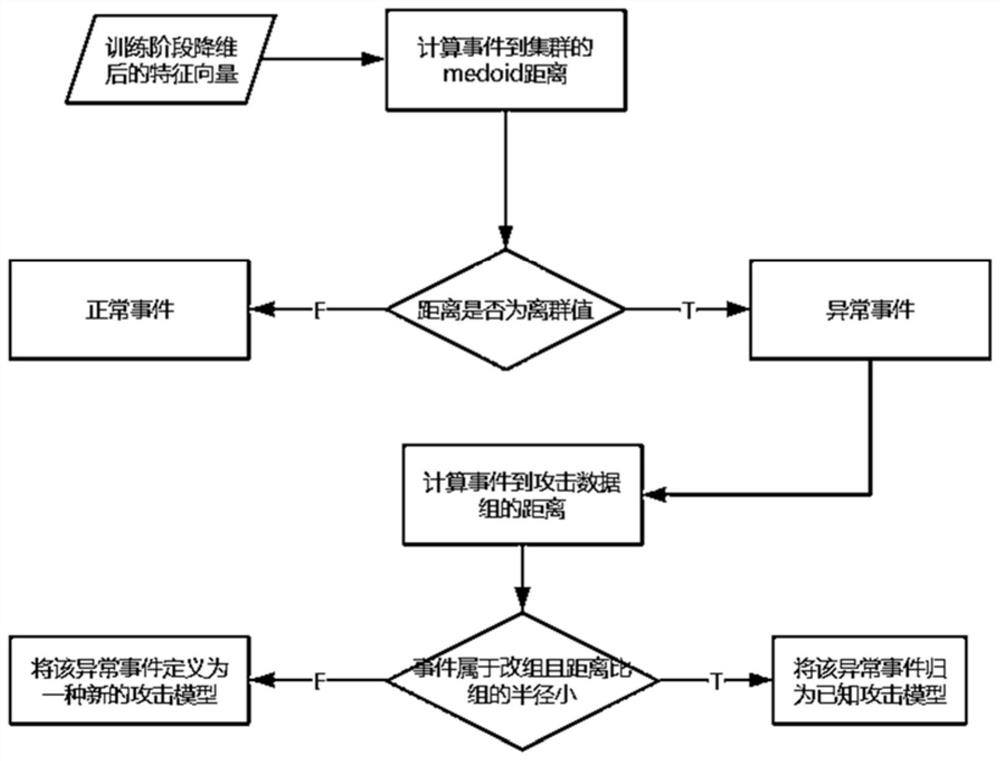
Unmanned aerial vehicle anomaly detection method based on multi-log collaborative analysis
PendingCN112100137AReduce consumptionSmall computational burdenCharacter and pattern recognitionNatural language data processingFeature vectorData set
An unmanned aerial vehicle anomaly detection method based on multi-log collaborative analysis comprises the following steps: conducting template extraction in an unmanned aerial vehicle flight log, extracting features of different events, and expressing text information of the unmanned aerial vehicle flight log in the form of feature vectors; carrying out dimension reduction operation on the obtained feature vectors by utilizing a PCA algorithm; classifying events into a known cluster according to the shortest Euclidean metric by using a k-medoids algorithm; identifying the events, carrying out anomaly detection on the events, judging whether the events are abnormal events or not, if not, putting the events back to the training data set for training in the learning stage, and if yes, continuing to judge whether the attack model is known or not, and if not, defining the abnormal events as a new attack model, and if so, classifying the abnormal events as a known attack model. According to the method, the speed and accuracy of module extraction and the accuracy of exception detection can be improved, and finally the attack model of the abnormal events is given.
Owner:XIDIAN UNIV
Voltage sag characteristic quantity random evaluation method based on scene construction
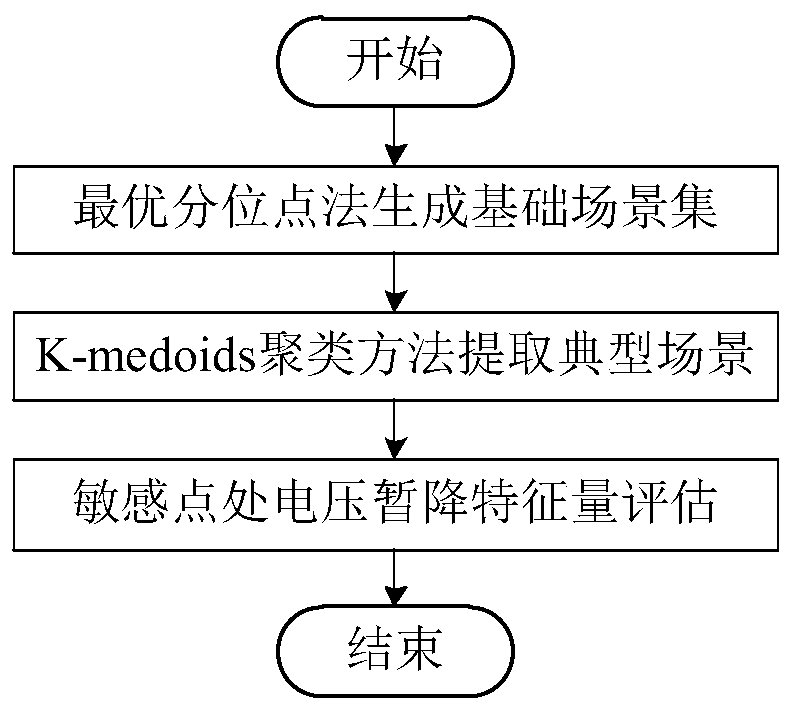
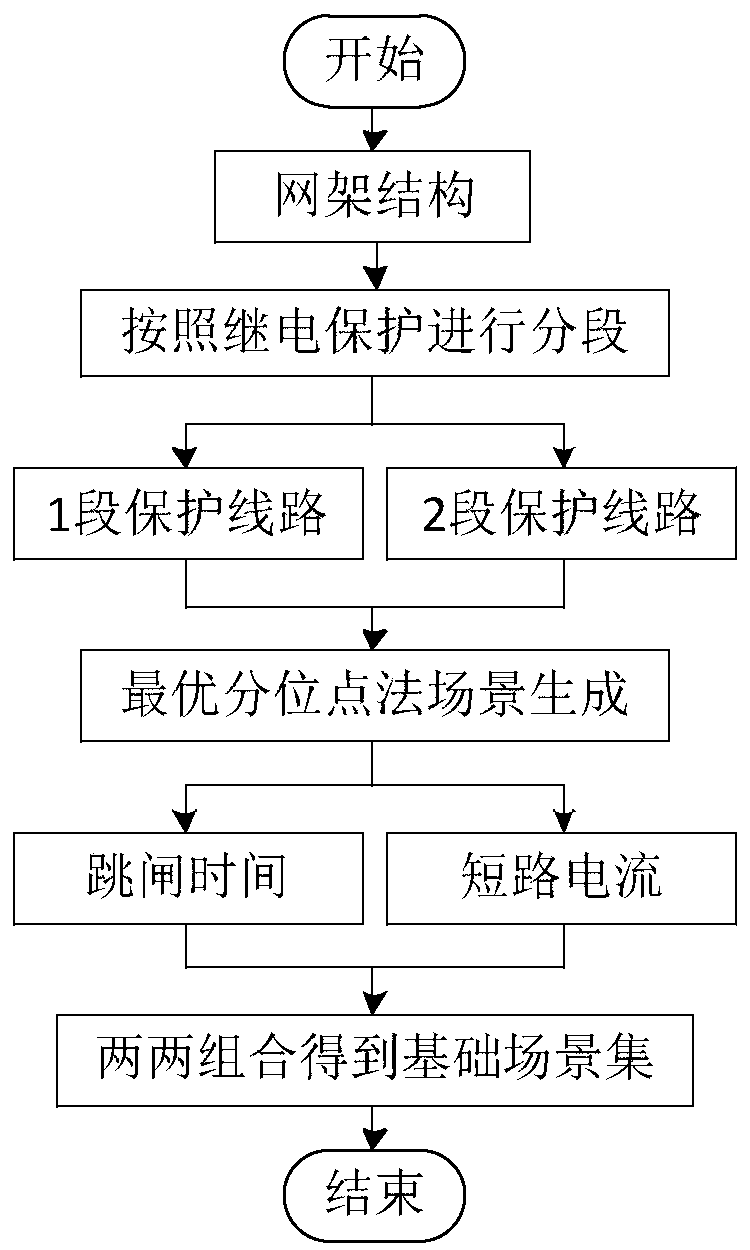
ActiveCN111429043AReduce random errorReduce the number of calculationsCharacter and pattern recognitionResourcesIndustrial engineeringLarge range
The invention relates to the technical field of power distribution network operation management, and discloses a voltage sag characteristic quantity random evaluation method based on scene construction, and the method comprises the following steps: 1, generating a basic scene set through employing an optimal quantile method based on a power distribution network grid structure according to relay protection segmentation parameters; 2, reducing the basic scene set into a few typical scene sets by applying a K-medoids clustering method; and step 3, according to a short-circuit calculation principle, in combination with historical monitoring data of the short-circuit fault of the power distribution network, performing voltage sag characteristic quantity evaluation at the sensitive load point. According to the method, a K-medoids clustering method is applied, a method for reducing a basic scene set into a few typical scenes is adopted. The difficulty of a large number of repeated tests of methods such as short-circuit calculation or simulation tests is avoided, the number of groups needing to be calculated is greatly reduced in a preprocessing mode, most similarity calculation is avoided, the calculation difficulty and time are reduced, and the applicability of the method in a large-range power distribution network is improved.
Owner:WUHAN UNIV +2
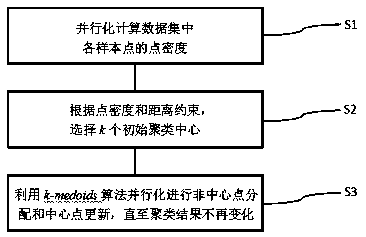
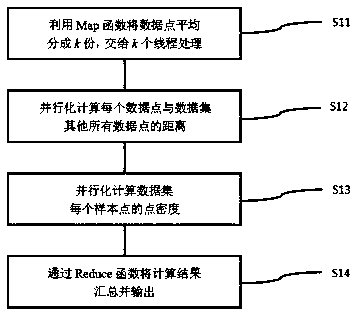
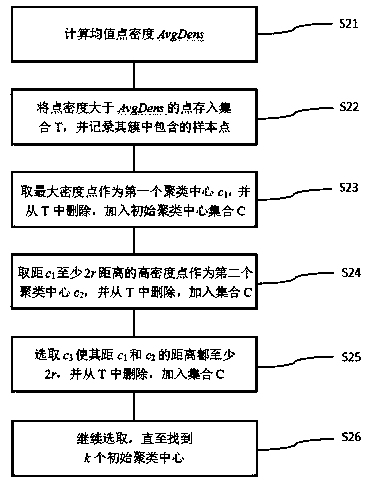
Parallelization clustering method for power communication data resources
InactiveCN108776814AImproved selection mechanismClustering iterative operation worksData processing applicationsCharacter and pattern recognitionCluster algorithmData set
The invention belongs to the technical field of power systems and more specifically relates to a parallelization clustering method for power communication data resources. First, point density of different sample points in a data set is calculated in parallel; k initial clustering centers are selected according to the size of the point density and the mutual distance; finally, a k-medoids algorithmis utilized for non-center point distribution and center point update on a Hadoop platform in parallel until the center point and the non-center point of each cluster do not change any more and the final clustering result is obtained. According to the invention, the initial points of the clustering algorithm are selected through combination of the size of the point density calculated according tothe sample points and the mutual distance, the initial cluster center selection mechanism is improved, the clustering iteration operation effectiveness is improved, the search range is reduced and the clustering effect is improved; parallelization resource allocation is optimized, clustering time is shortened and clustering precision is improved, effective analysis and utilization of power data are well supported and the comprehensive benefits of power communication network related data are developed.
Owner:GUANGDONG POWER GRID CO LTD +1
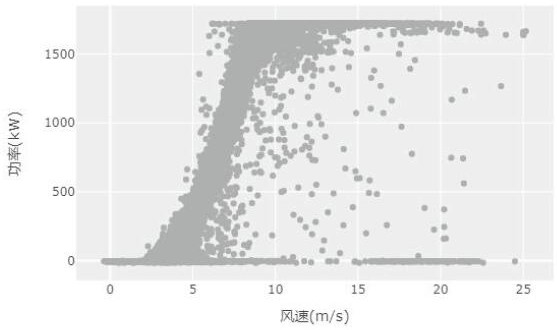
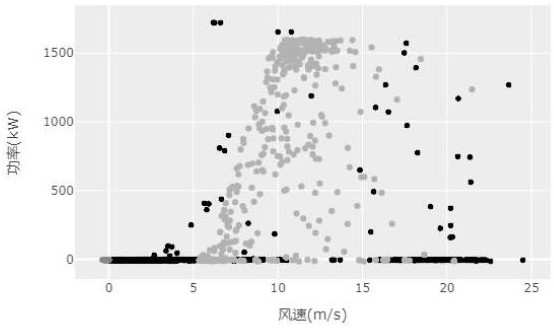
Wind turbine generator power curve modeling method based on k-medoids algorithm
InactiveCN112597620AGain insight into actual operating statusUnderstand the actual operating statusDesign optimisation/simulationSpecial data processing applicationsAlgorithmIndustrial engineering
The invention discloses a wind turbine generator power curve modeling method based on a kmedoids algorithm. The wind turbine generator power curve modeling method comprises the following steps of S1,reading related data, wind power plant fault records and related maintenance records in an SCADA database; s2, performing data cleaning on the collected data; s3, carrying out abnormal value screeningon the cleaned data; s4, performing standardized correction on the data; and S5, performing interval division statistics on corresponding indexes, and establishing a standard power curve data model.The method overcomes the defects in the prior art, can effectively play a key role in judging the standard conformity of the power curve of the wind generating set, is beneficial to evaluating the related index completeness of the generating capacity of the wind power plant, and can deeply understand the actual running state of the wind generating set; The guidance is provided for regular inspection, early warning and other operation and maintenance work of the wind turbine generator.
Owner:新天绿色能源股份有限公司 +2
Enterprise re-work auxiliary judgment method based on electric power big data analysis
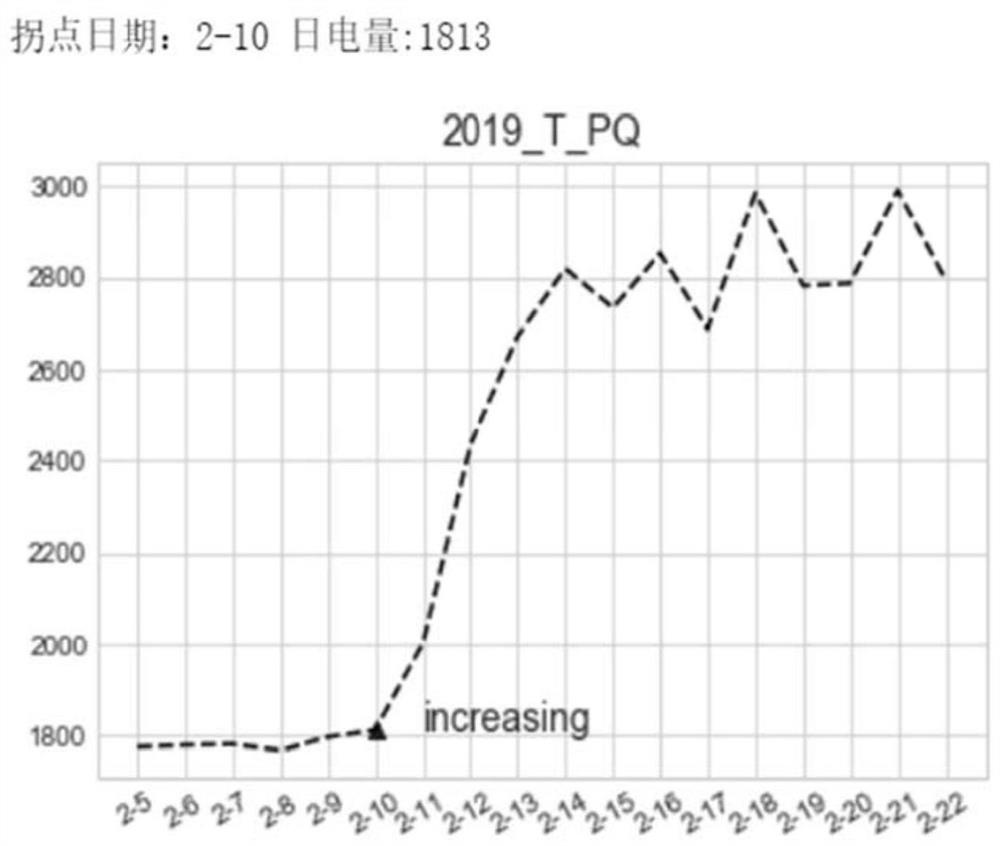
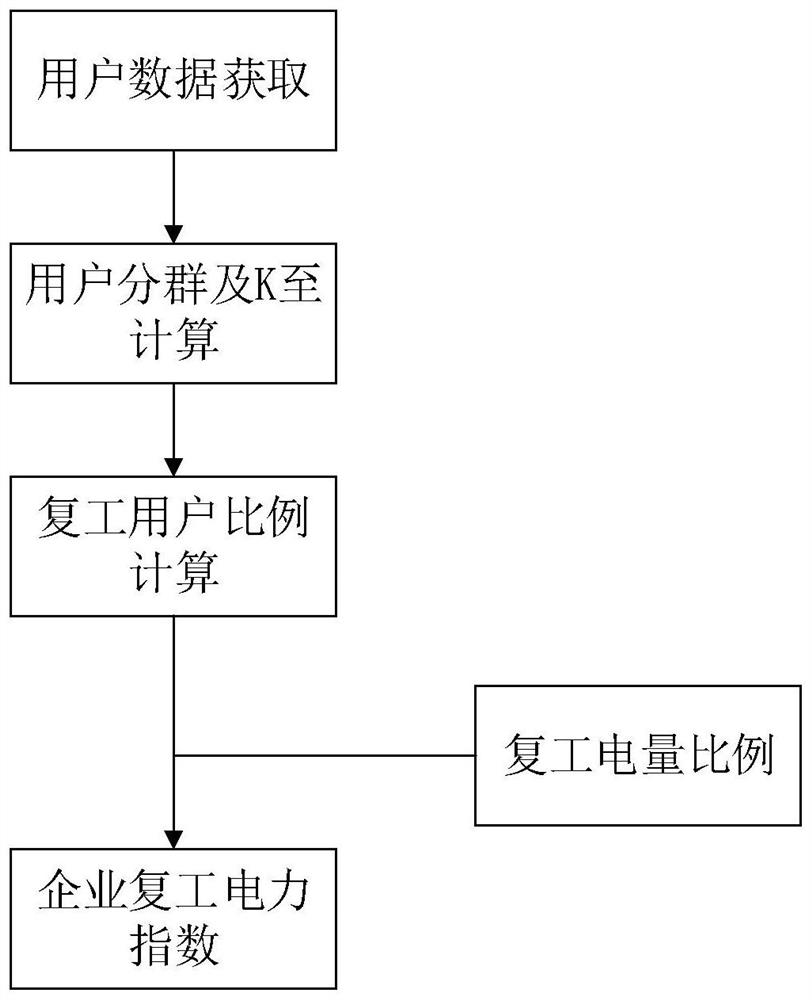
ActiveCN111784093AImprove accuracyImprove efficiencyCharacter and pattern recognitionResourcesBusiness enterprisePower usage
The invention discloses an enterprise rework auxiliary judgment method based on electric power big data analysis, and relates to an enterprise rework judgment method. At present, whether an enterpriserestarts to work or not needs to be checked home by home, and the efficiency is low. The method comprises the following steps: acquiring related power utilization data of corresponding users, grouping the users based on the related power utilization data of the users and calculating a corresponding threshold value K, calculating the proportion of rework users in an area based on the calculated threshold value K, and finally obtaining an enterprise rework power index based on the calculated rework power proportion in the area. According to the technical scheme, an objective means is adopted, human factors are eliminated, the data accuracy is effectively improved, the efficiency is high, the real-time performance is high, the reworking condition of the day can be mastered, and the development of epidemic prevention and other work is facilitated. And a K-medoids algorithm is adopted to perform user grouping, so that the quickity and accuracy of classification are effectively improved.
Owner:STATE GRID ZHEJIANG ELECTRIC POWER +1
Clustering method based on network for disease subtype problem
InactiveCN105160208AWeaken the identification effectGood similarity between groupsSpecial data processing applicationsDistance matrixK-medoids
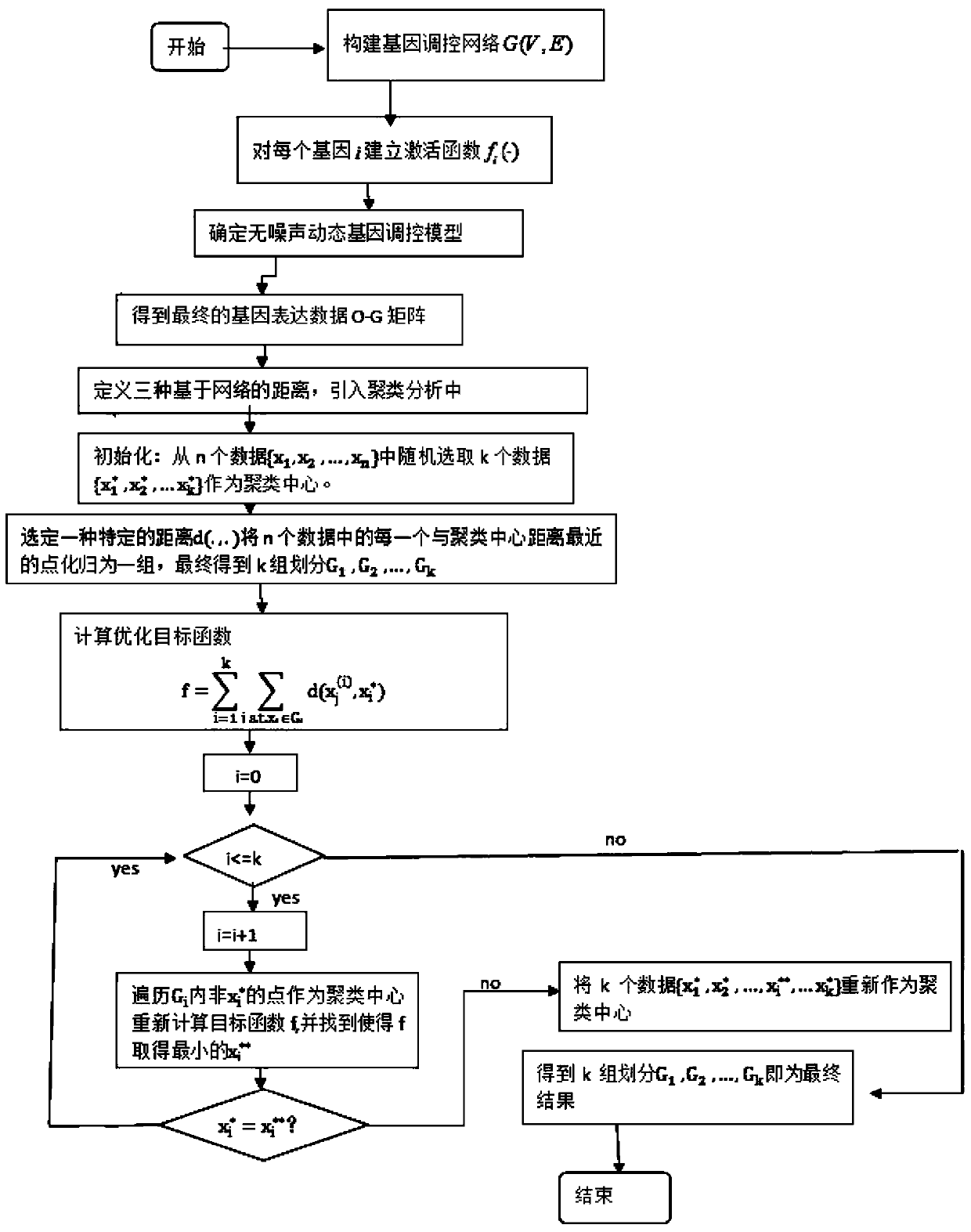
The present invention relates to the field of reverse research of disease subtype, and aims to provide a clustering method based on a network for disease subtype problems. The clustering method based on the network for disease subtype problems comprises the processes: obtaining an O-G matrix and a gene regulatory network; selecting a distance definition based on the network applicable to specific questions, and constructing a distance matrix; and using a K-medoids algorithm to perform clustering analysis on the O-G matrix, and selecting a distance based on the network for the clustering distance. The method provided by the invention has a better inter-group similarity to a specific gene network, and reduction of three subtypes can be effectively carried out; and when expression data of a large number of genes needs to be determined, the identification effect of disease subtype is not greatly weakened by precisely measuring the expression data of information genes preferentially.
Owner:杭州奥视图像技术有限公司
Node annealing method in SDN
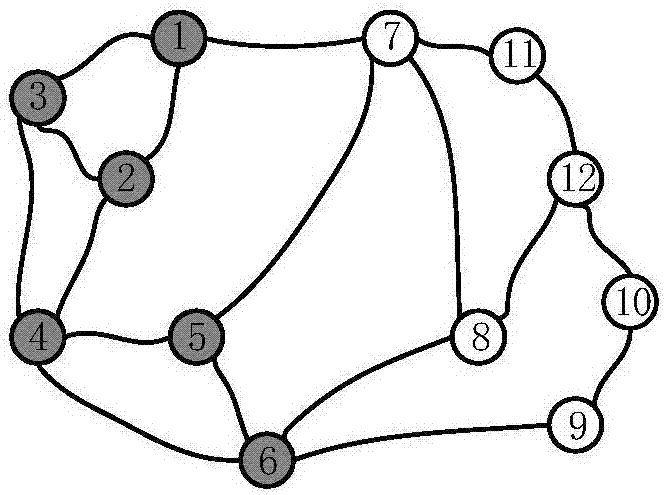
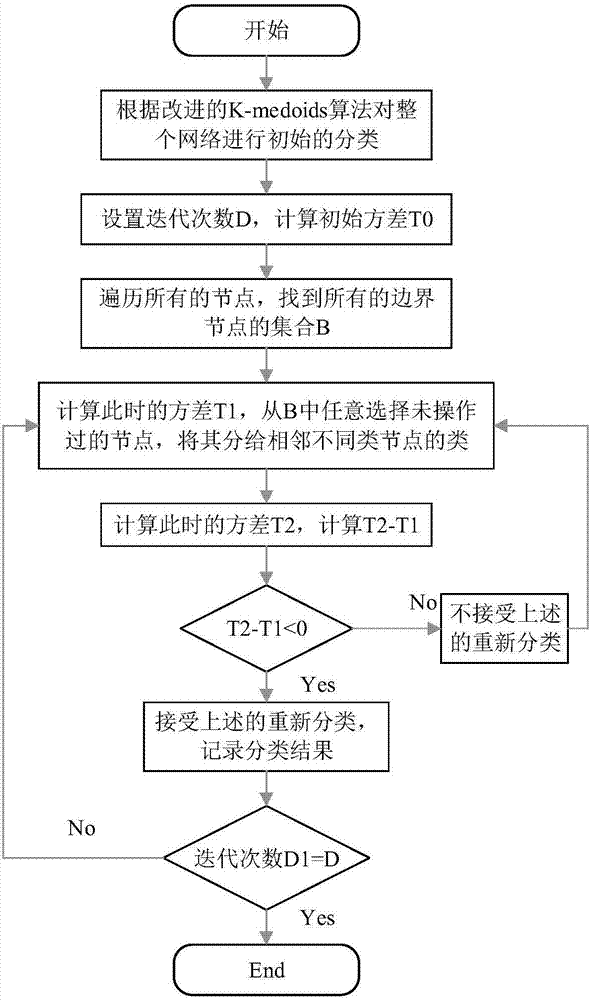
InactiveCN107241277AReasonable deployment resultsReduce complexityData switching networksNODALK-medoids
The invention belongs to the field of next generation network control and management and software definition networks so as to ensure the load balance of a controller. The invention provides a node annealing method in an SDN. The method comprises the following steps: step 1, performing primary classification on the network according to an improved K-medoids algorithm, and returning a classification result center point set P and a label set Q of each node; step 2, setting iterations and calculating the initial variance of the whole network node number; step 3, traversing all nodes to find all boundary nodes; step 4, finding an un-operated boundary node from all boundary nodes to perform a re-classification operation, and allocating the boundary node to the type of a neighbor node; step 5, calculating the variance at the moment, and comparing the variance with the previous variance; and step 6, judging whether the iterations are satisfied at the moment; if not, returning to step 4; and otherwise, returning the classification result at the moment and terminating. The node annealing method is mainly applied to software definition network occasions.
Owner:TIANJIN UNIV
Power grid economic operation domain generation method and system considering source-load double-side uncertainty
ActiveCN114336607AImprove the ability to deal with uncertain factorsAbility to enhance uncertaintiesPower network operation systems integrationSingle network parallel feeding arrangementsPower system schedulingControl engineering
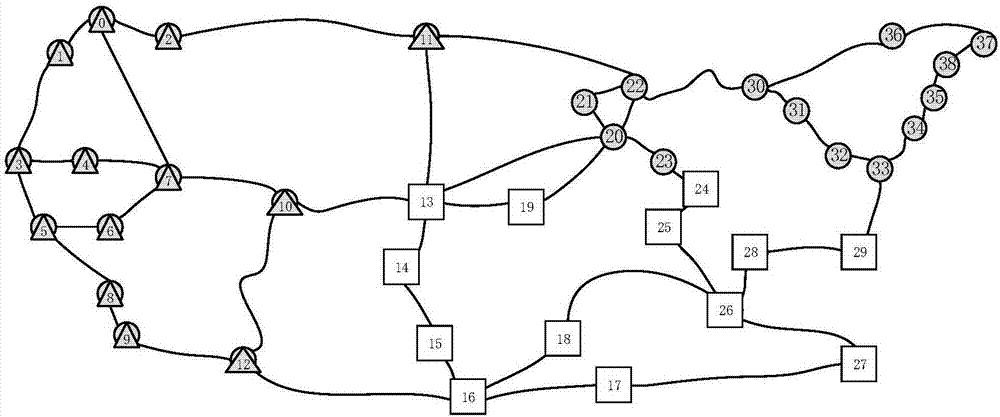
The invention discloses a power grid economic operation domain generation method and system considering source-load double-side uncertainty. Most of the current power system scheduling methods give out a unit output plan curve, which is difficult to reflect the influence of uncertainty on a power grid scheduling plan. The method comprises the following steps: acquiring a typical wind power output scene and a corresponding probability thereof based on tLocation-scale distribution, Latin hypercube sampling and K-medoids clustering; establishing a demand side response model according to the price type demand side response rule; and on the basis, according to the definition of the economic operation domain, establishing a power grid economic operation domain generation model considering the uncertainty of both sides of the source and the load, and directly solving through a commercial solver. According to the method, the economic operation domain concept and power system dispatching are combined, the economic operation output interval of the unit is generated, the requirement for dispatching operation of the power system is met and further improved, and the influence of uncertainty on a power grid dispatching plan can be quantitatively described.
Owner:ELECTRIC POWER RES INST OF STATE GRID ZHEJIANG ELECTRIC POWER COMAPNY +2
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com