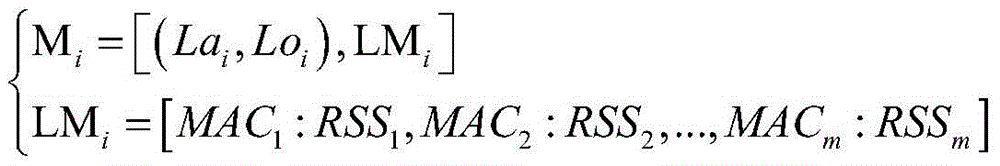RSS-based wireless spoofing attack positioning method
A technology of spoofing attack and positioning method, which is applied in the direction of location information-based services, wireless communication, radio wave measurement system, etc., and can solve problems such as inability to determine the physical location of the attacker, difficult to process RSS data, and multiple noises
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
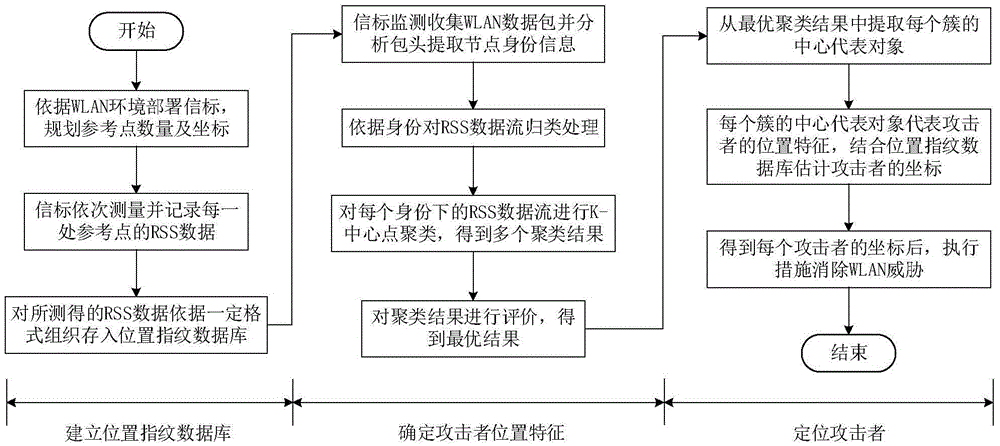
[0065] The invention provides an RSS-based wireless spoofing attack positioning method, including:
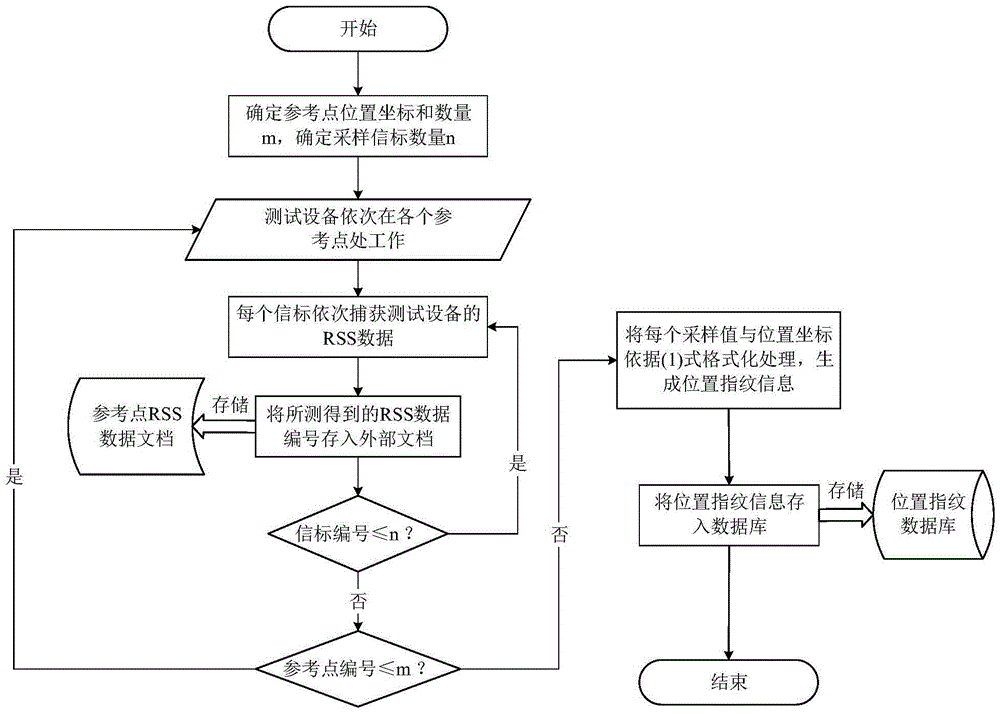
[0066] S1. Establishing a location fingerprint database corresponding to the WLAN environment;
[0067] S2. Using the beacon to monitor the wireless data packets in the WLAN in real time, and then extract and obtain the RSS data stream of each node;
[0068] S3. Use the K-central point algorithm to select multiple K values, and cluster the RSS data streams of each node in turn according to each K value to obtain the corresponding clustering results, and finally obtain multiple clustering results for each node Class results; in the K-center point algorithm, the initial value of K is 2, and the value of K is increased by 1 each time it is clustered until it reaches the preset maximum value;
[0069] S4. After evaluating multiple clustering results obtained by each node, an optimal clustering result corresponding to each node is obtained;
[0070] S5. After sequentially obtainin...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com