Method and system for monitoring junk short message
A technology of spam text messages and text messages, which is applied in wireless communication, electrical components, messages/mailboxes/notifications, etc., which can solve problems such as judgment errors and achieve the effect of improving accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
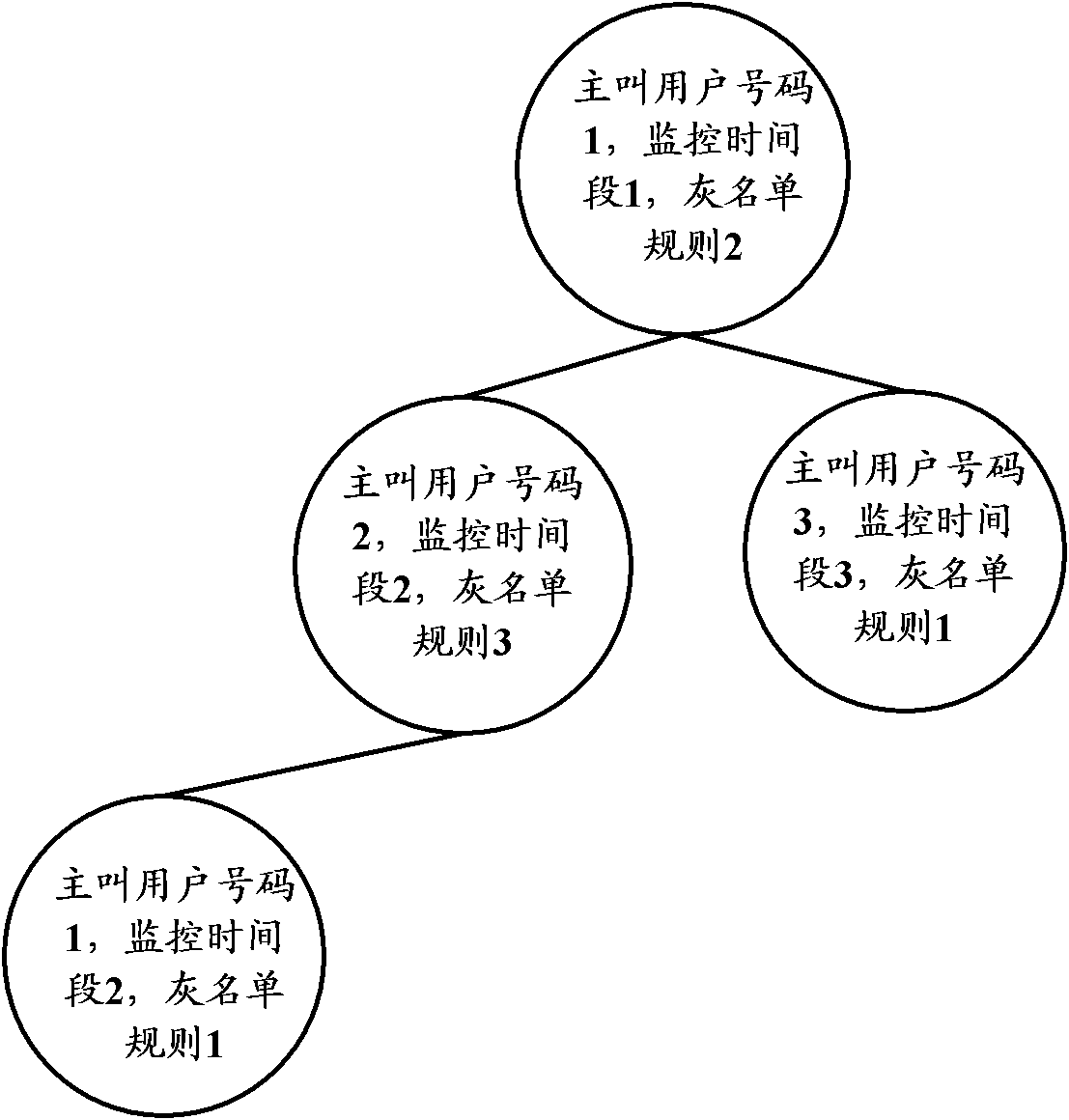
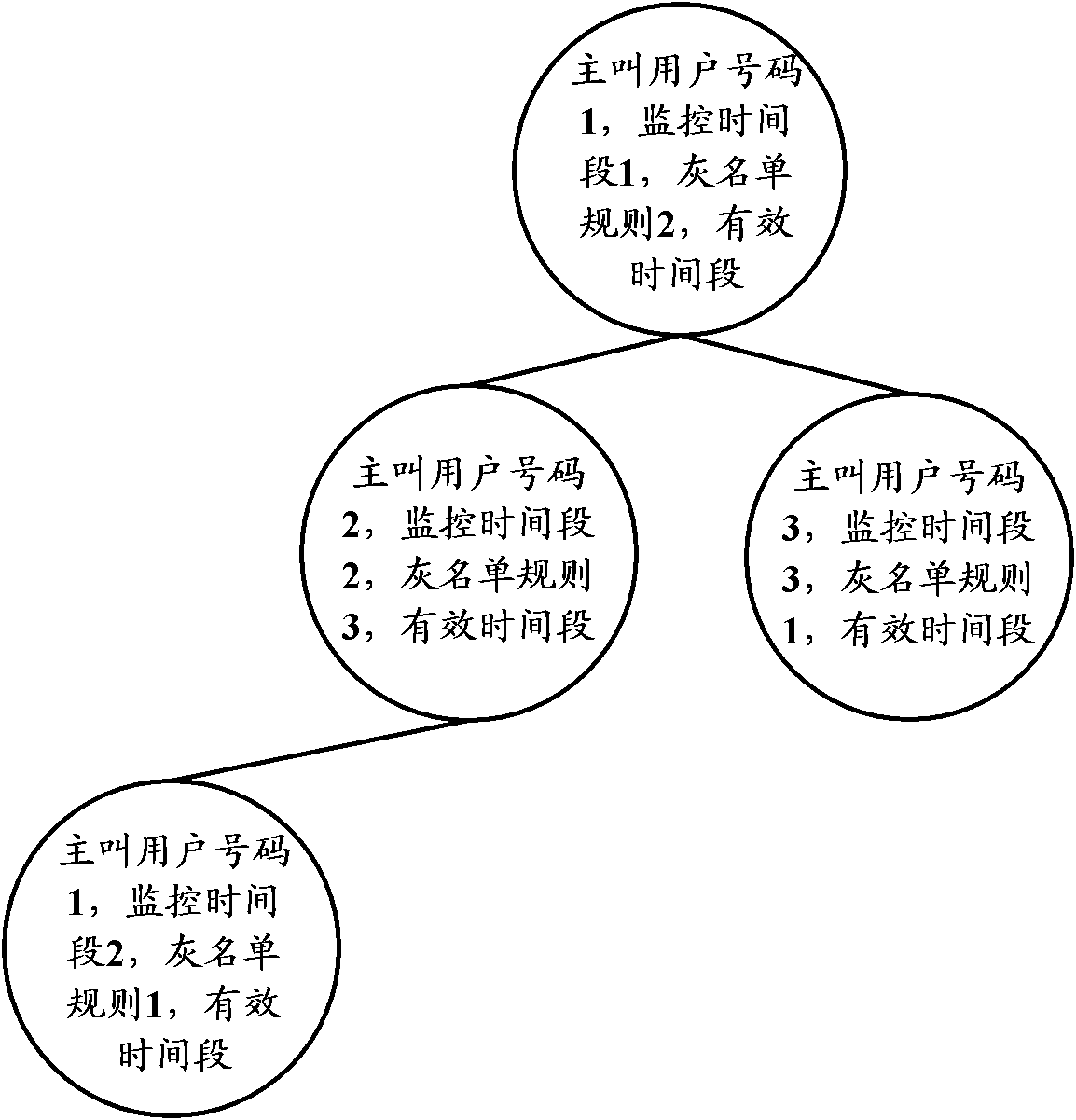
[0088] Embodiment 1 Use the gray list sending tree to add the gray list sending information, and the gray list expiration tree to add the valid time period of the gray list sending information, the calling party number tree to add a new calling party number, and the calling party number to expire the tree to add the The effective time period of the calling party number is described as an example. In the embodiment of the present invention, the monitoring condition of spam text messages involved is set to the top three text messages with the same content that are sent the most times.
[0089] Assume that the current greylist sending tree data structure is as follows Figure 2a As shown, a certain calling user number is 13800000000. After the number of short messages sent in the current monitoring period (assumed to be 9:00-10:00) reaches the storage threshold (assumed that the storage threshold is 100), and the subsequent sending SMS triggers the pre-set gray list rule (assumin...
Embodiment 2
[0094] Such as Figure 6 As shown, in the embodiment of the present invention, for a certain calling party number, a schematic diagram of the implementation process of the spam SMS monitoring method, including the following steps:
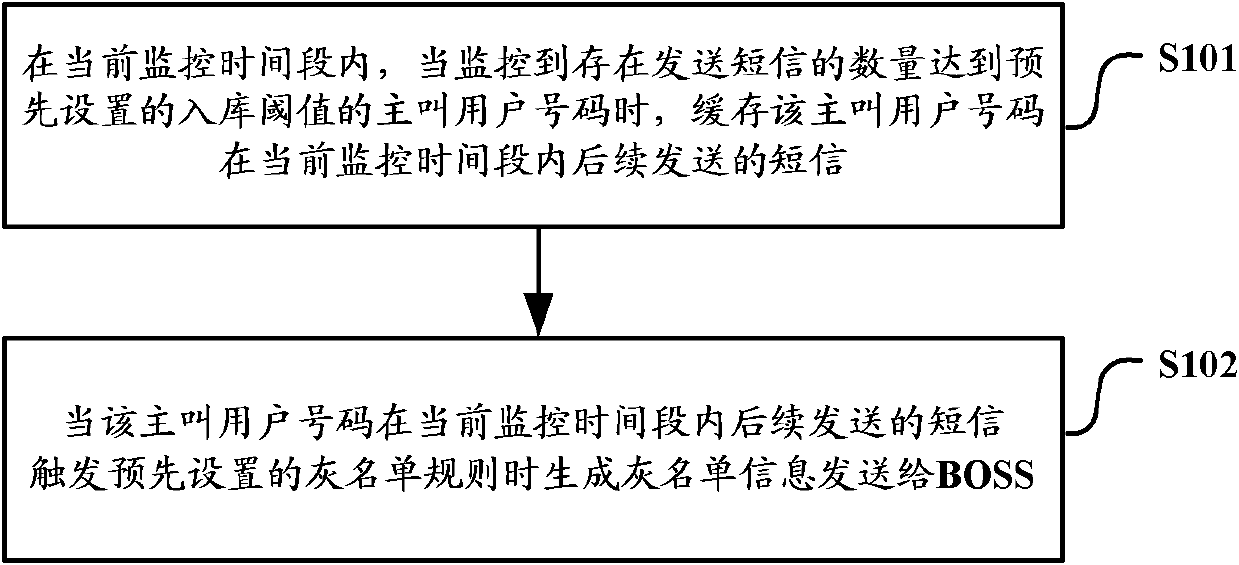
[0095] S601. During the current monitoring time period, monitor the number of short messages sent by the calling user number;
[0096] S602, judging whether the number of short messages sent by the calling party number reaches the preset storage threshold; if yes, execute step S603, if not, execute step S601;
[0097] S603. Buffering each short message subsequently sent by the calling party number within the current monitoring time period;
[0098] S604. Monitor the short messages subsequently sent by the calling party number within the current monitoring time period;
[0099] S605. Determine whether the short message sent by the calling party number within the current monitoring time period triggers a certain preset gray list rule, if yes, execu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com