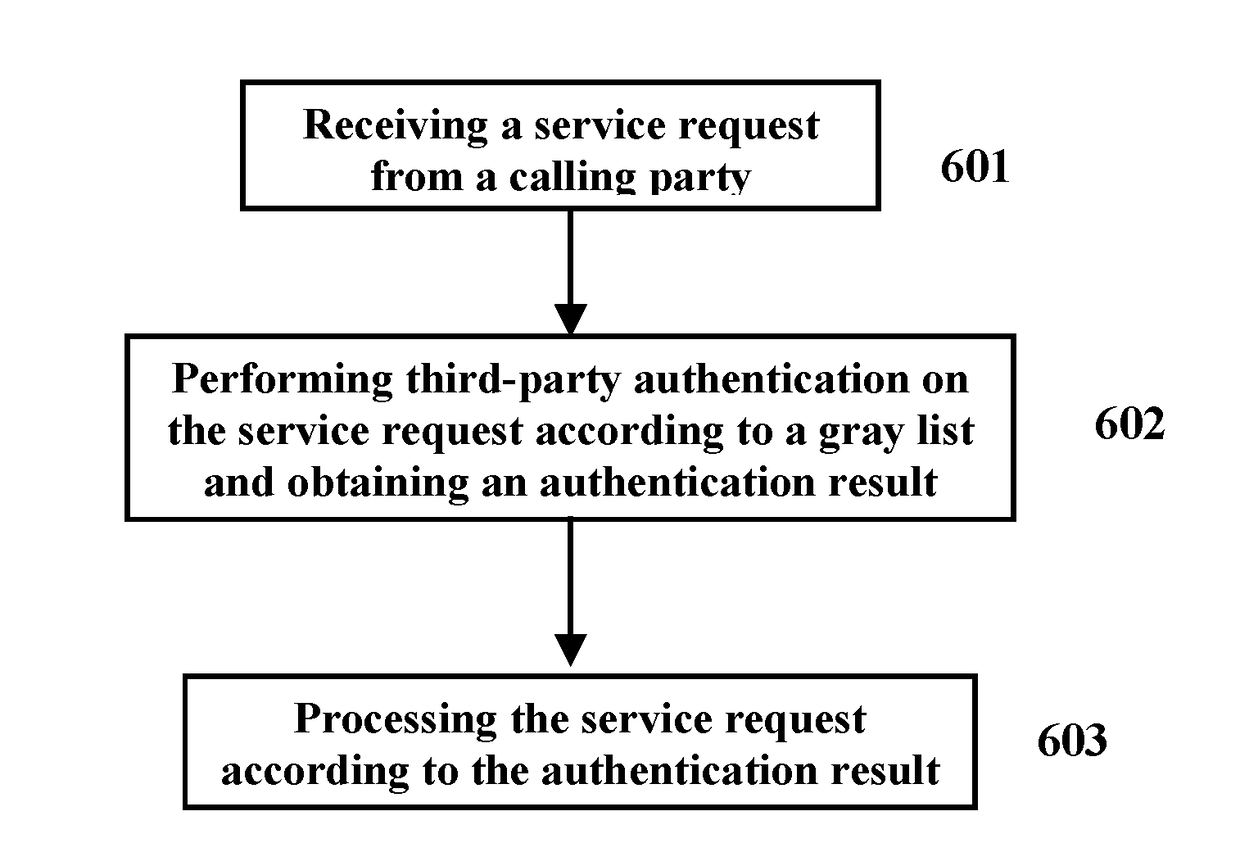
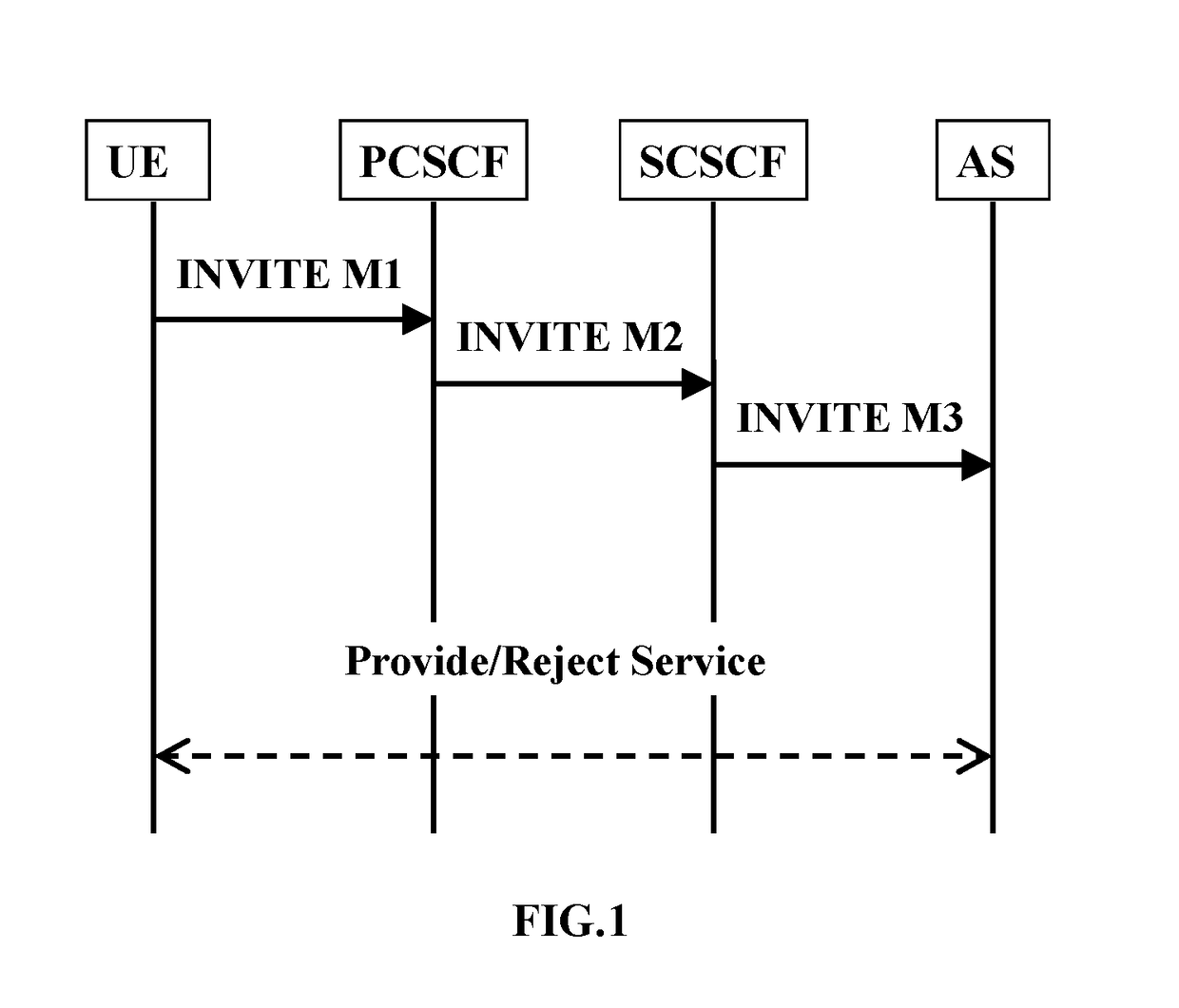
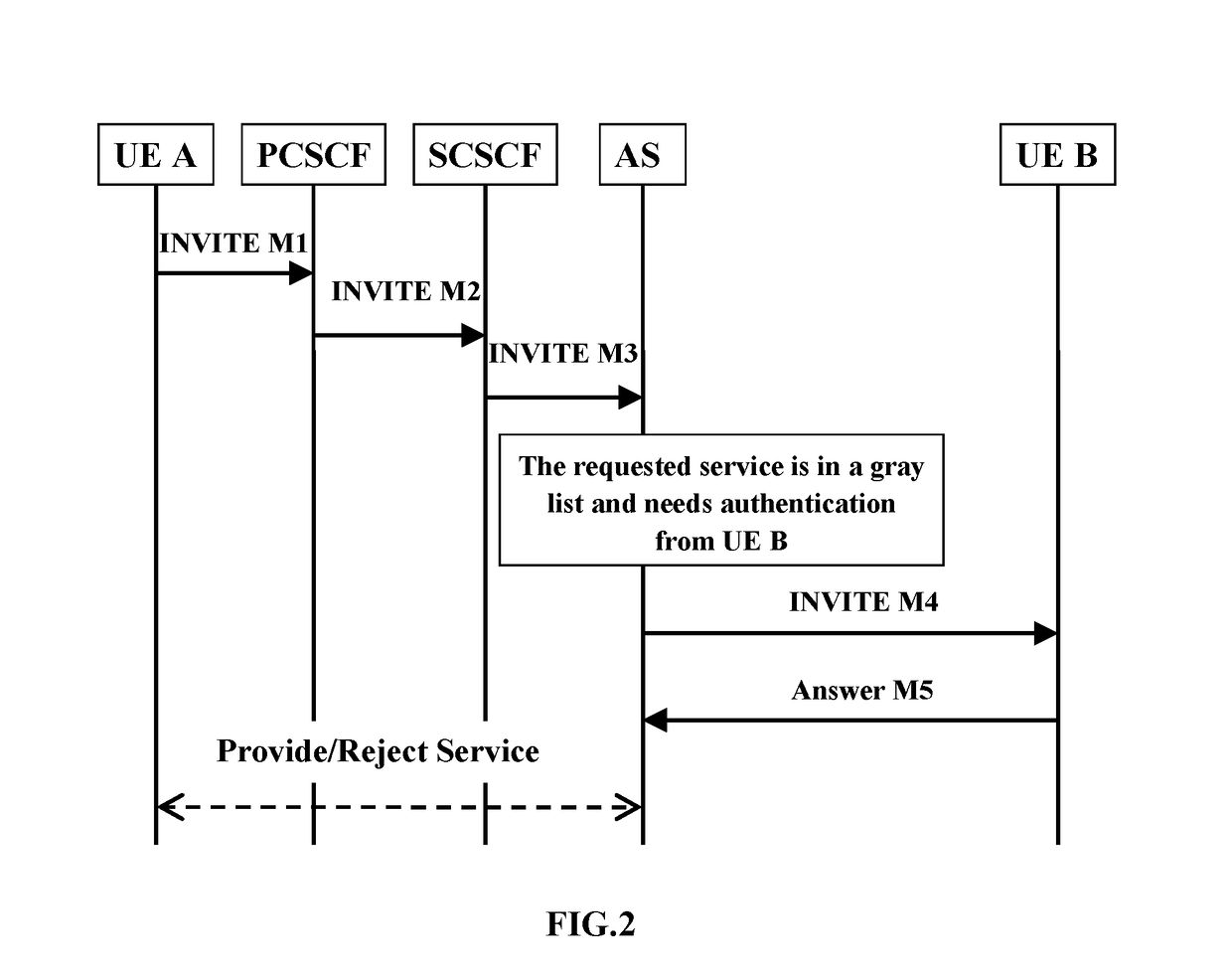
Method and system for implementing third-party authentication based on gray list
a third-party authentication and gray list technology, applied in the field of communication systems, can solve the problems of not being able to get a certain service or all services, implement third-party control of services, and not being able to obtain the grant of the system by the lis
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0047]Exemplary embodiments for carrying out the invention are described now by reference to the drawings. However, the invention may be performed in various forms, not limited to the embodiments described herein. These embodiments are provided for extensively and comprehensively disclosing the invention, and for sufficiently conveying the extent of the invention to those skilled in the art. Terms in exemplary modes for carrying out the invention illustrated in the drawings do not define the invention. In the figures, identical units / elements are represented by identical reference signs.
[0048]Detailed exemplary modes for carrying out the invention are disclosed here. However, the specific constructions and function details disclosed here are only for the purpose of the typical description of the exemplary implementation of the invention. However, the present invention can be embodied in a variety of alternative forms and should not be constructed to be limited to implementations as ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com