Android file lockbox system based on double chaotic hash file control
A file control and password box technology, which is applied in the field of password box systems to avoid the occupation of effective space, realize data management, and strengthen security management.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
[0133] Example 1: The user installs and uses the lockbox system for the first time.
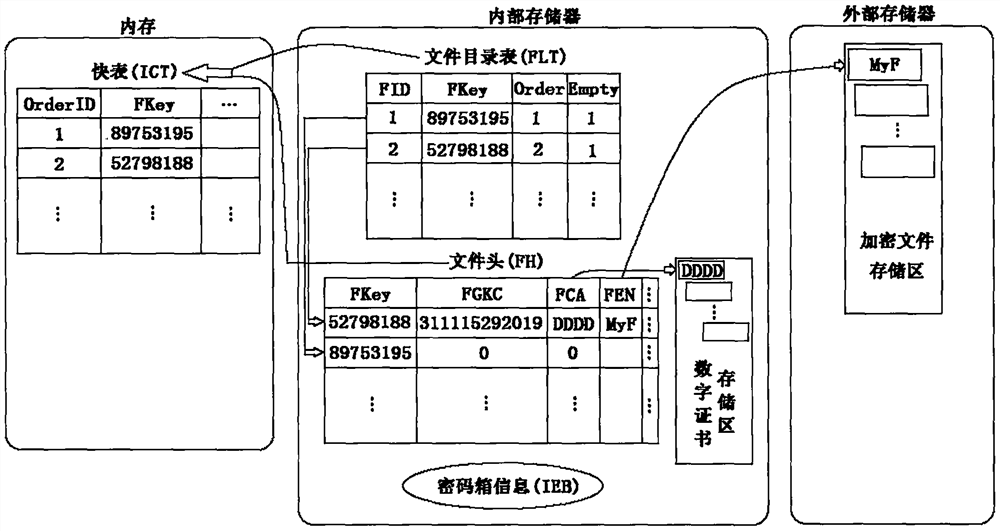
[0134] When installing and using the lockbox system for the first time, the user needs to set the password to enter the system, and set the total number of files saved in the lockbox, that is, the number of nodes, and the directory information of the encrypted files stored in the external memory.
[0135] The password set by the user is converted into the parameters cp_1, t[0]_1, cp_2, t[0]_2, Init_Num and RNum of the two Logistic equations through the system conversion function strConver, and through the system function kValue=Hkey(cp_1, t[0 ]_1, cp_2, t[0]_2, Init_Num, RNum) generate a digital certificate for user login verification and store it in the internal memory.
[0136] The user sets the total number of nodes in the system (NumNodes). When the system is installed with an SD card, the system obtains the directory status through the Environment class. In Android 6.0 and above, the per...
example 2
[0141] Example 2: The user adds files to the lockbox.
[0142] The user enters the personal password, and the lockbox system uses the conversion function strConver to generate a digital certificate for the current user login verification through the system function kValue=Hkey(). This certificate is compared with the user's original digital certificate stored in the internal memory. If they are consistent, the verification is passed. , the login is successful; otherwise, the authentication error occurs, and the user will not be able to log in to the system.
[0143] The user chooses to browse the folder, finds the file that needs to be added to the lockbox, and after selecting the Add function button, it first needs to compare whether the total number of nodes in the current fast table is less than CB_NNum. If it is greater than or equal to CB_NNum, it means that the lockbox system has reached the upper limit and cannot be stored any more. Encrypted files.
[0144] If there a...
example 3
[0147] Example 3: Expand the lockbox.
[0148] This system can establish the user's digital certificate according to the correct password provided by the user, and rebuild the file directory table FLT. The user needs to back up the file header FH file, and copy the backed up encrypted file to the directory where the encrypted file is stored in the external storage. Open the file header FH, reverse initialize the file directory table FLT, read the content of each node in the file header FH in turn, set the value of Order according to the value of FKey, and initialize Empty, restore the digital certificate according to the FGKC item to generate a digital certificate file .
[0149] When the user provides a wrong password, because the user's current digital certificate is inconsistent with the original digital certificate, the FKey value of the established file directory table FLT is inconsistent with the FKey value of the original file header FH that needs to be restored; there...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com