Patents
Literature
272 results about "Group operation" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
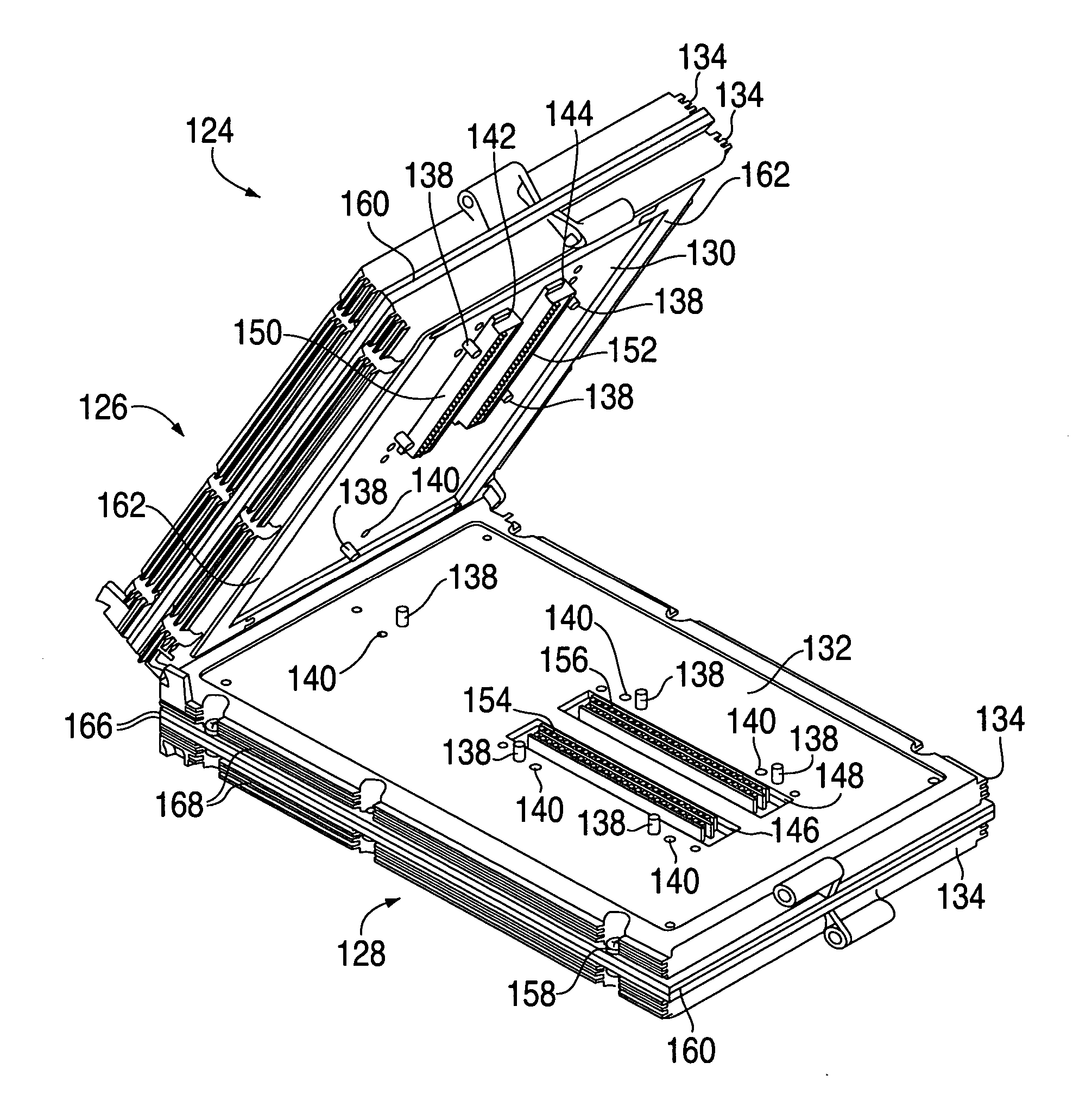
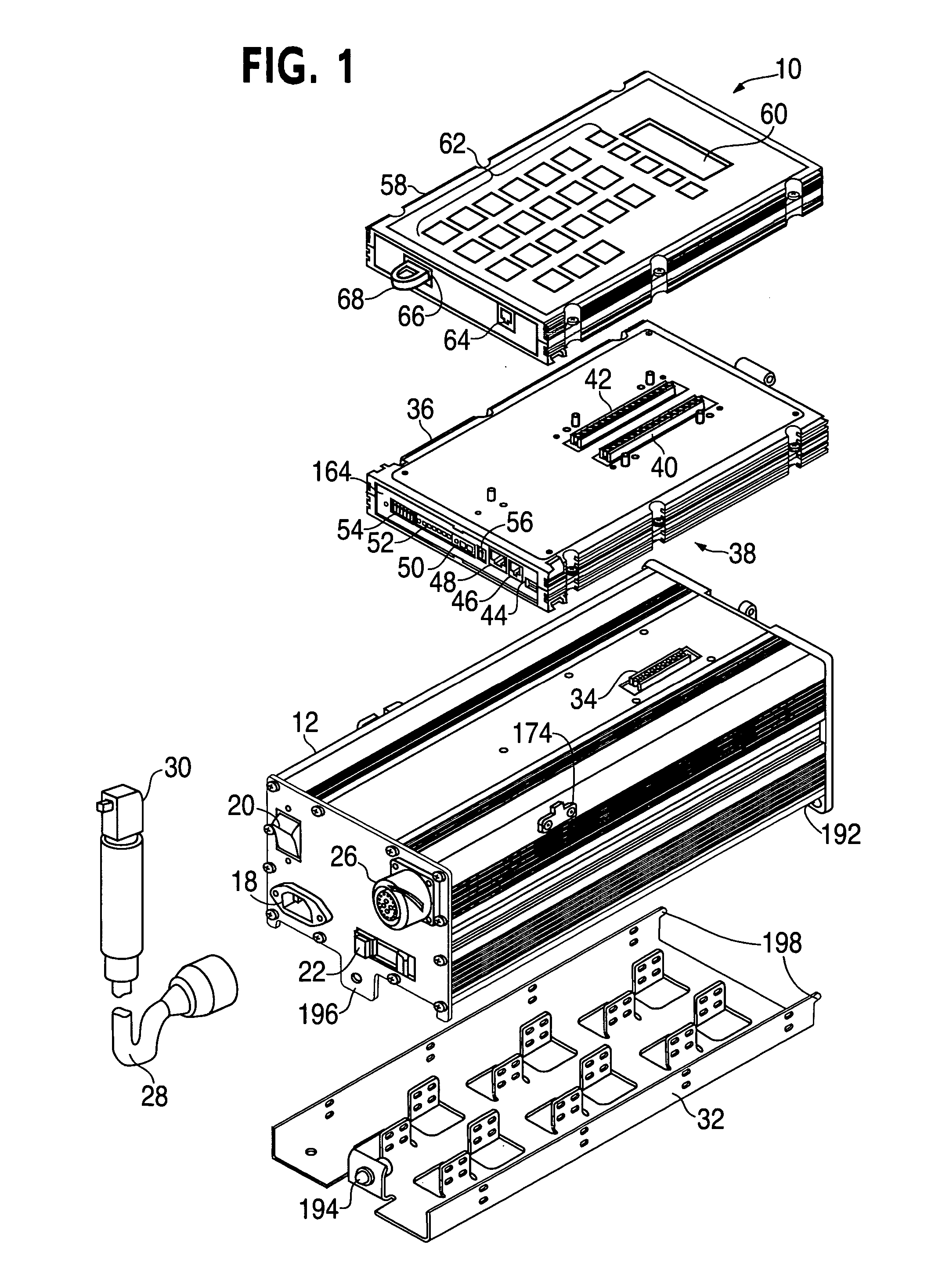
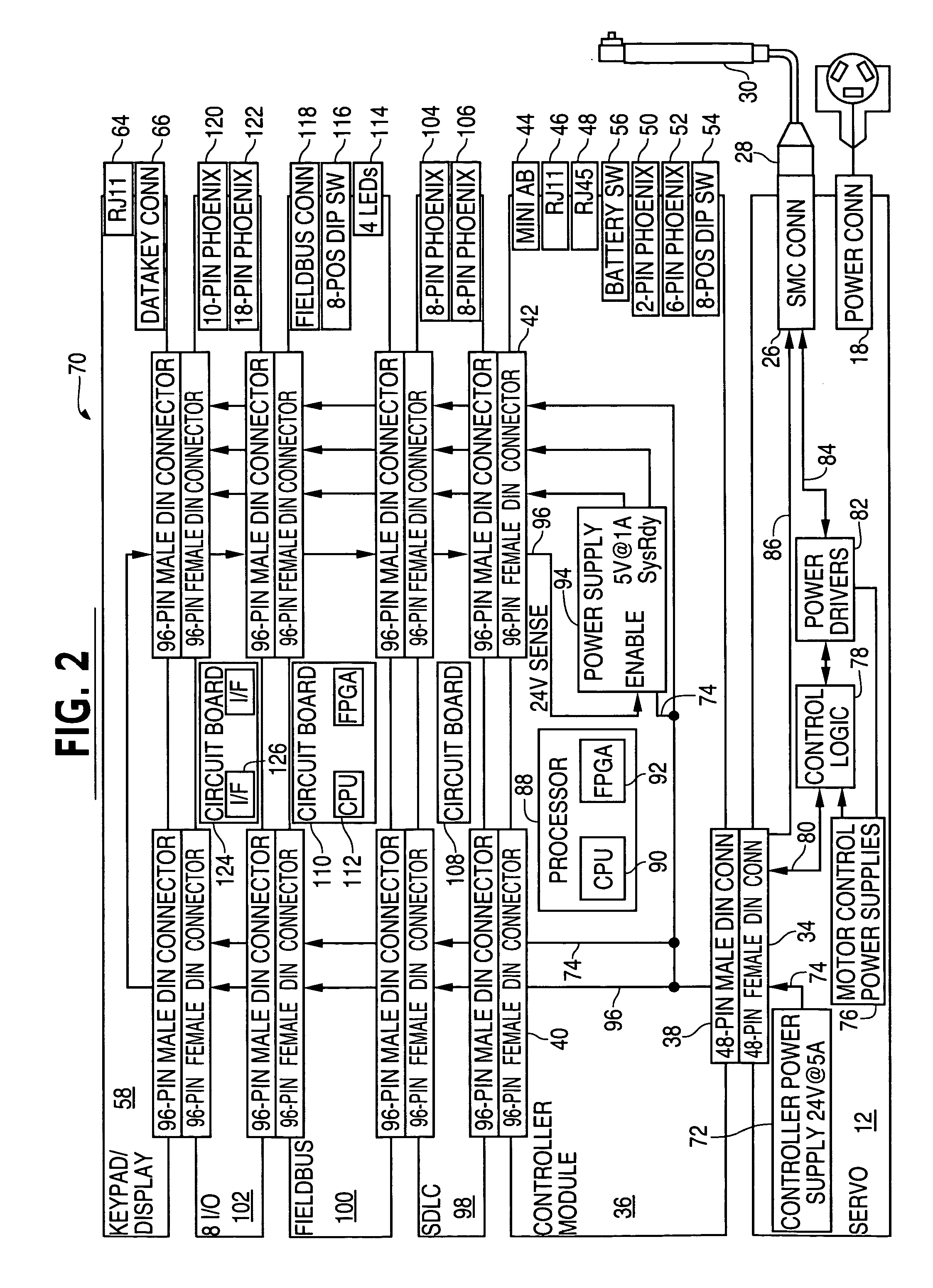
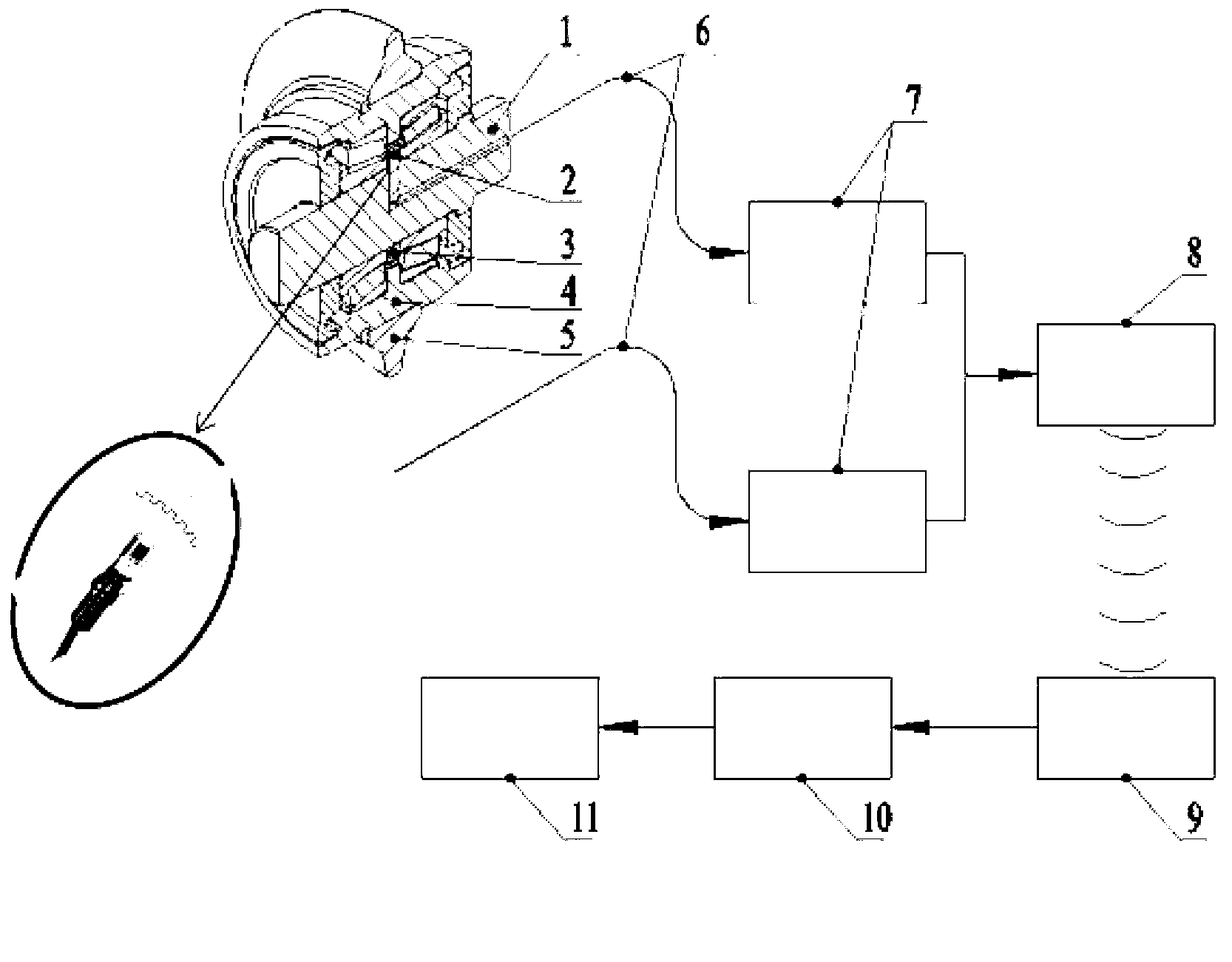
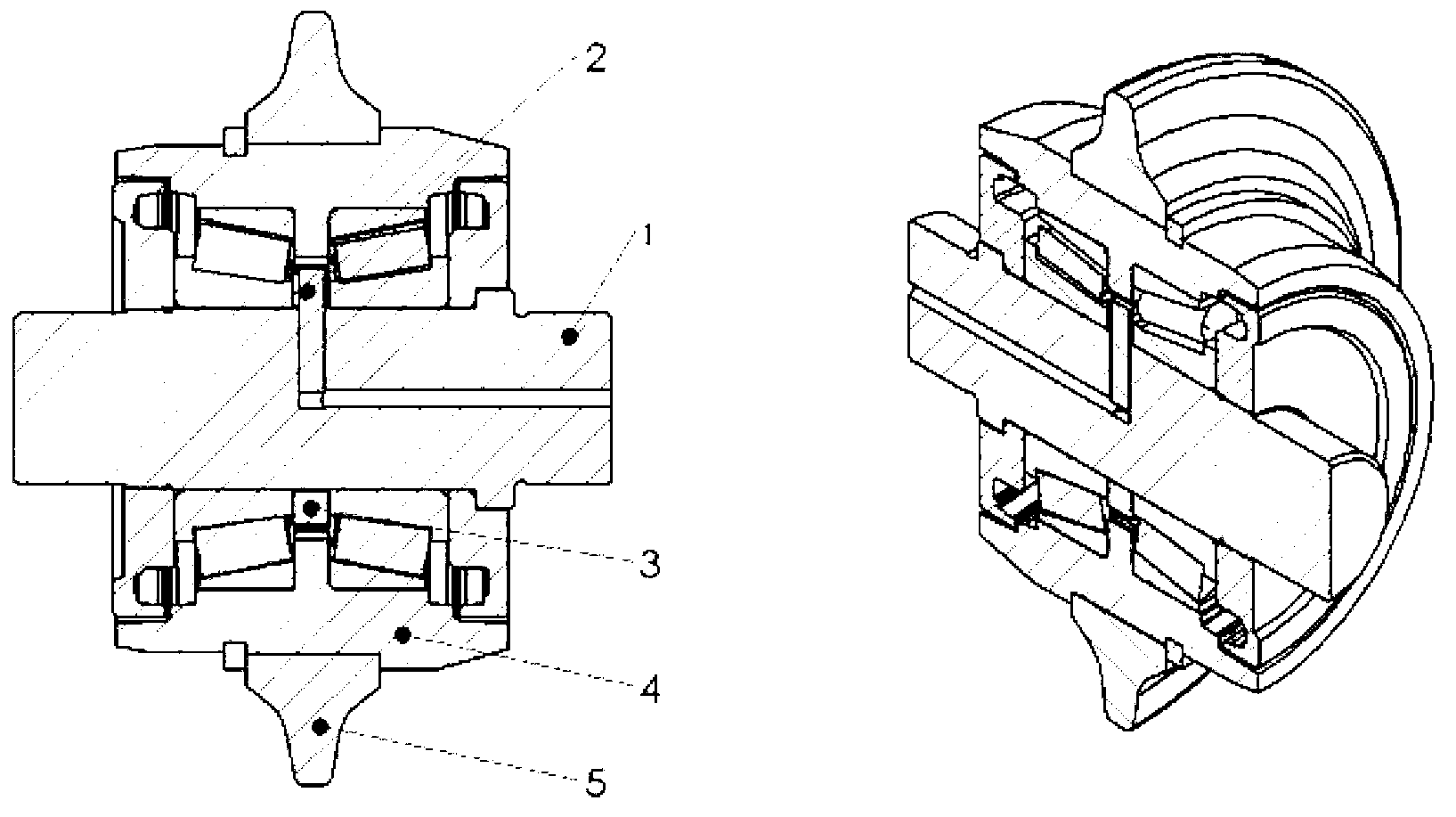
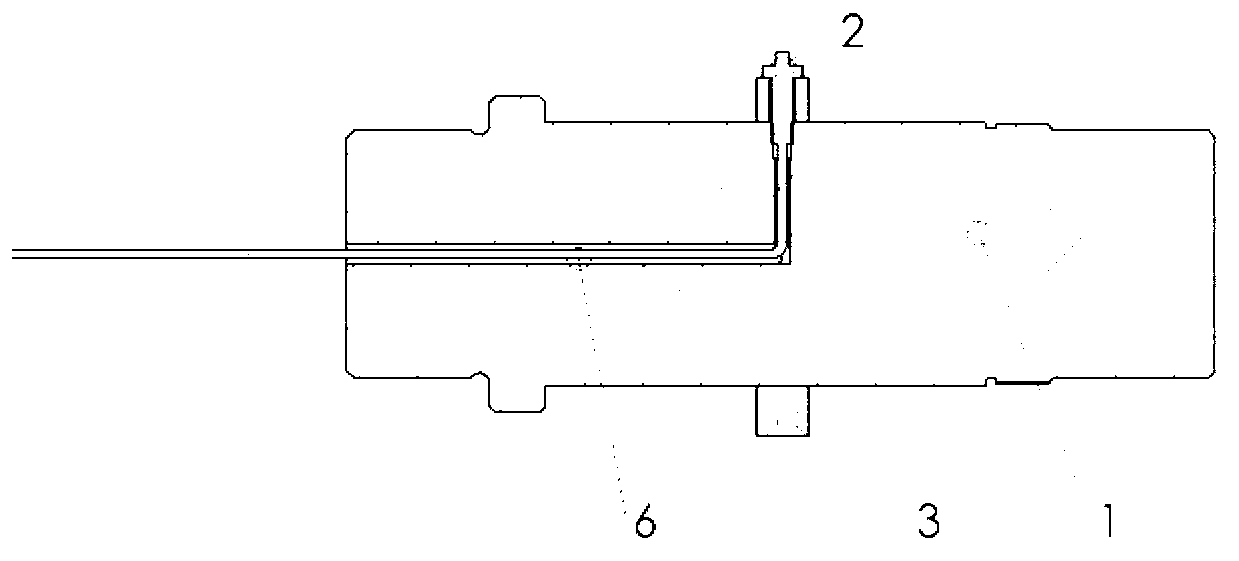
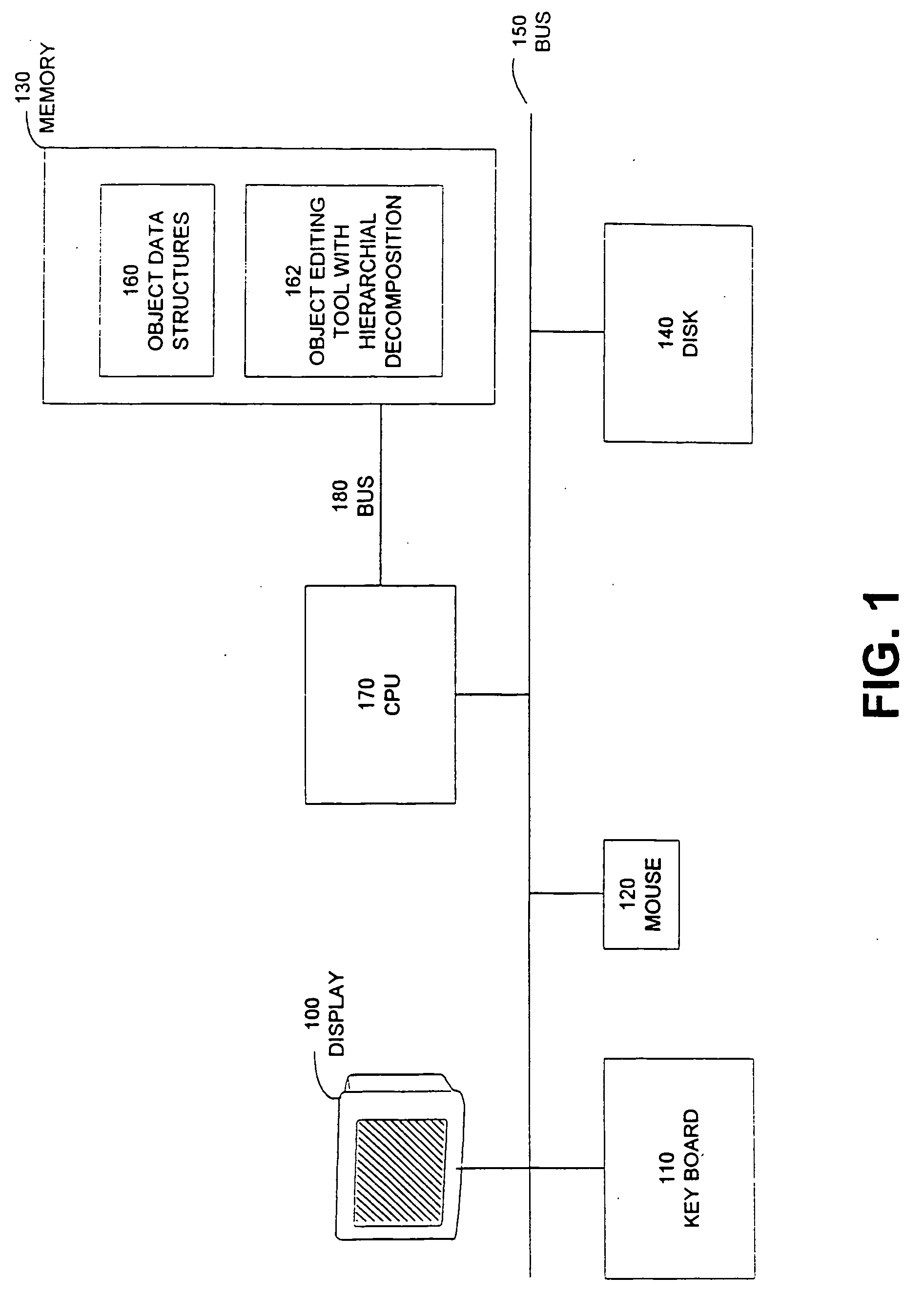
Modular controller apparatus and method
InactiveUS20060136622A1Side-by-side/stacked arrangementsPLC for automation/industrial process controlModularityGroup operation
A servomotor controller provides nut runner and other functions in a set of stackable modules. Extended-function modules can be added into and removed from the stack as needed. Destacking of closely spaced, wall-mounted controllers can be performed without demounting. Module assemblies are dripproof. Multiple sizes of nutrunner driver electronics and multiple keyboard and display options can be selected. A reprogrammable central processor can identify newly installed or removed features within a controller and reconfigure itself F accordingly. Stackable modules include Ethernet(®, multiple-bit I / O, and proprietary interfaces for many industries. The other modules communicate with the processor module via a backplaneless bus architecture. The central processor supports master / satellite group operation, whereby one controller unit can command multiple others, and whereby a higher-level system can command multiple controllers or multiple master / satellite controller groups.
Owner:CHICAGO PNEUMATIC TOOL
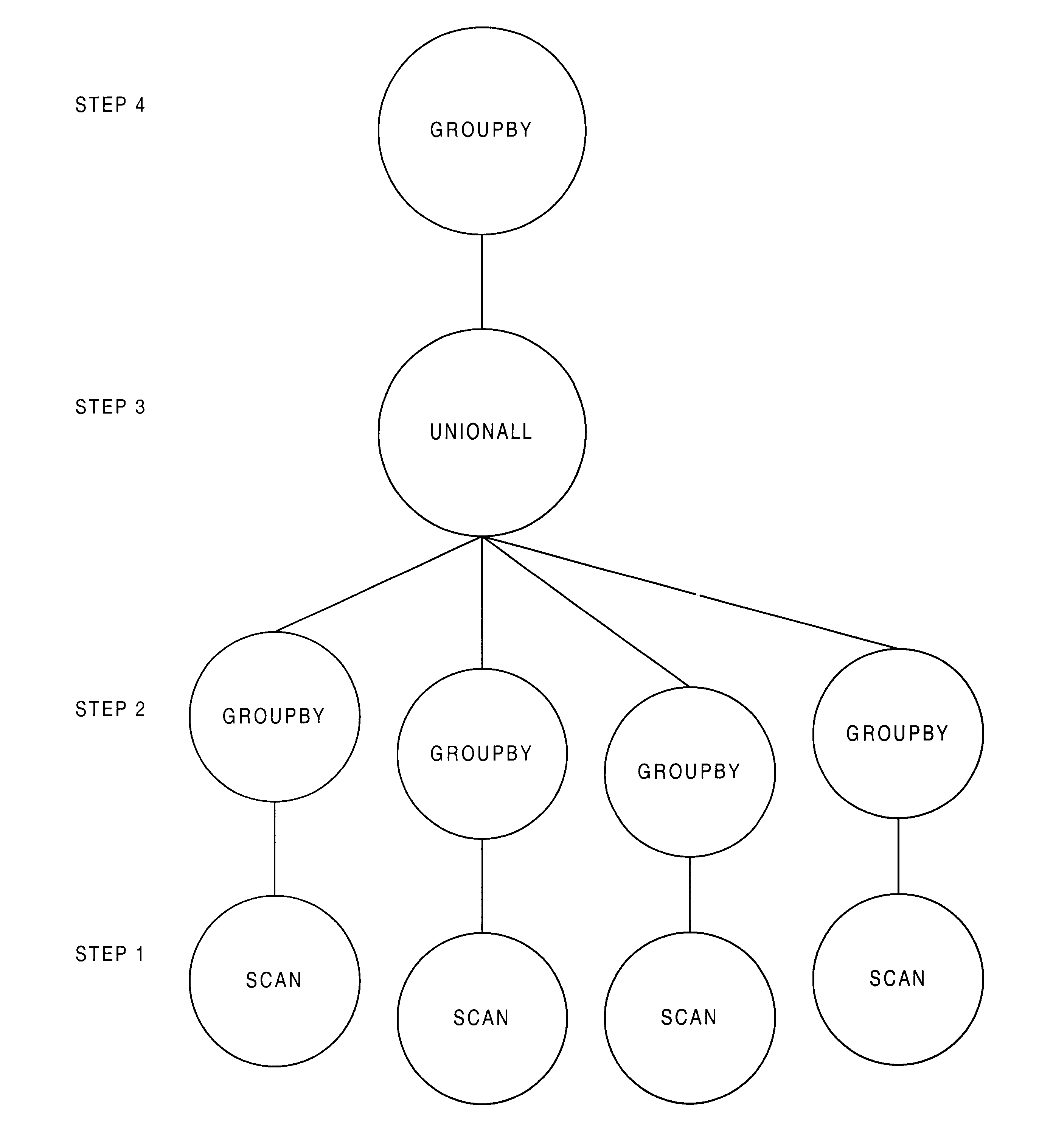
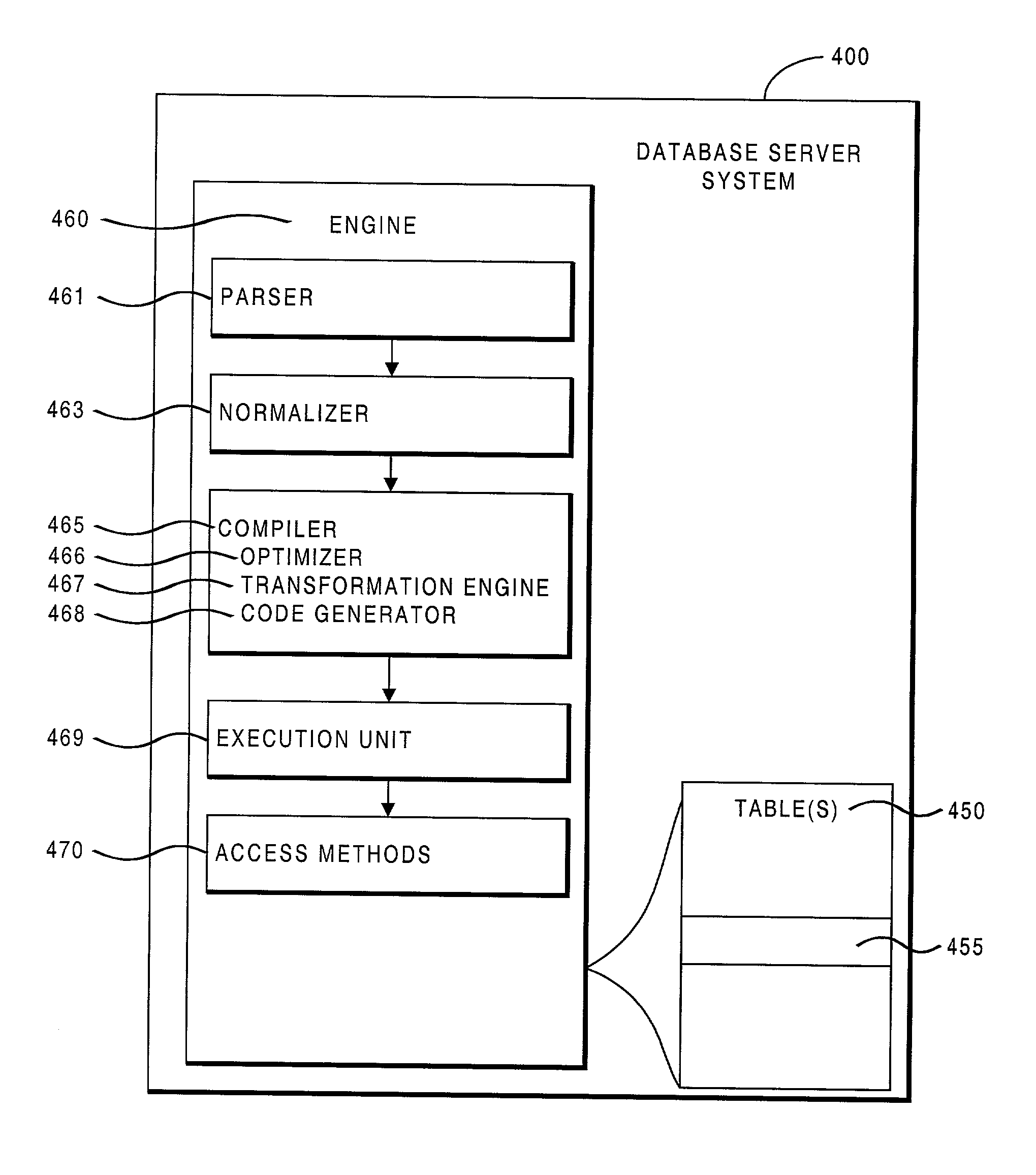
Database system providing optimization of group by operator over a union all
InactiveUS6691101B2Data processing applicationsDigital data information retrievalExecution planImproved method
A database system providing improved methods for optimization and execution of queries aggregating information from multiple database tables is described. The improved method breaks serial operations into a group of child operations that can be individually optimized and processed in parallel. A query including a grouping operator over a union node is split by pushing the grouping operation down into each input arm of the union node. Specifically, grouping operators are inserted into each child arm of qualifying union nodes, enabling separate physical database tables to be summarized in parallel. Each of the child grouping operators concurrently groups data and generates summary results in parallel, taking advantage of capabilities of available parallel processing hardware. The aggregate operators of the original master grouping operator are modified to accept and correctly synthesize sub-aggregated results generated by each of the child grouping operators. The method also enables individual optimization of operations on each database table, including use of advantageous index-only execution plans.
Owner:SAP AMERICA
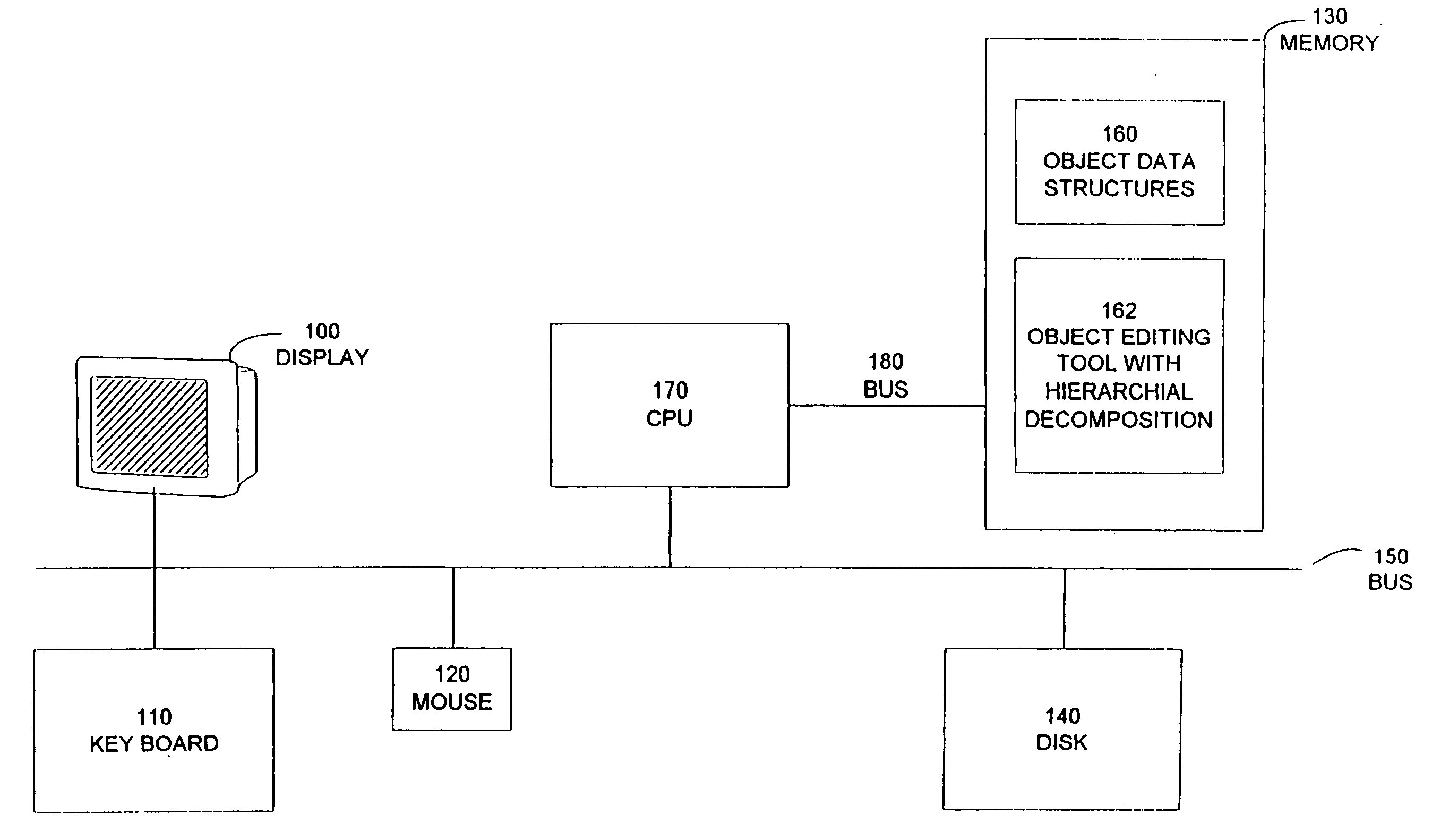
Methods and apparatus for supporting and implementing computer based animation
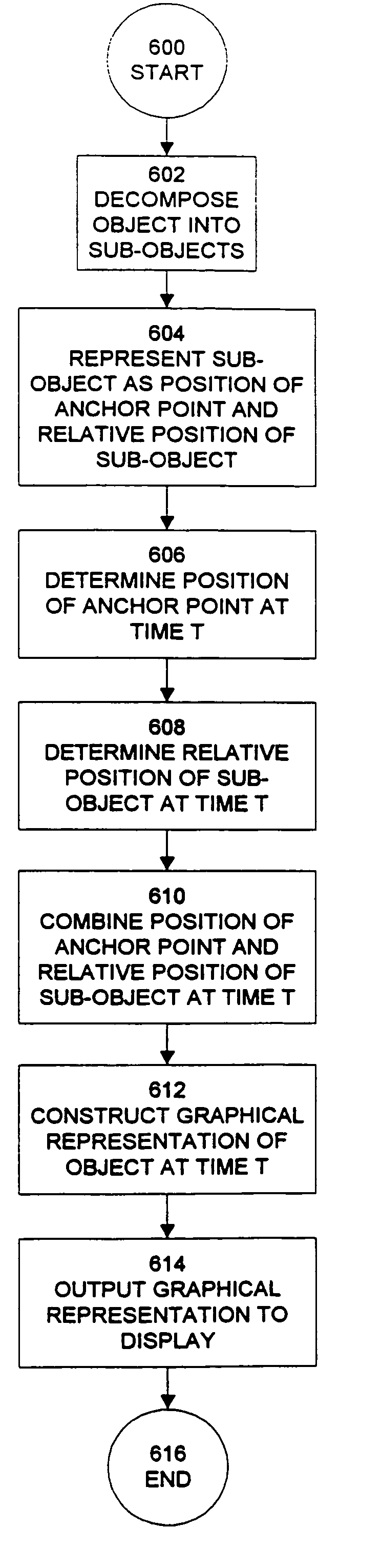
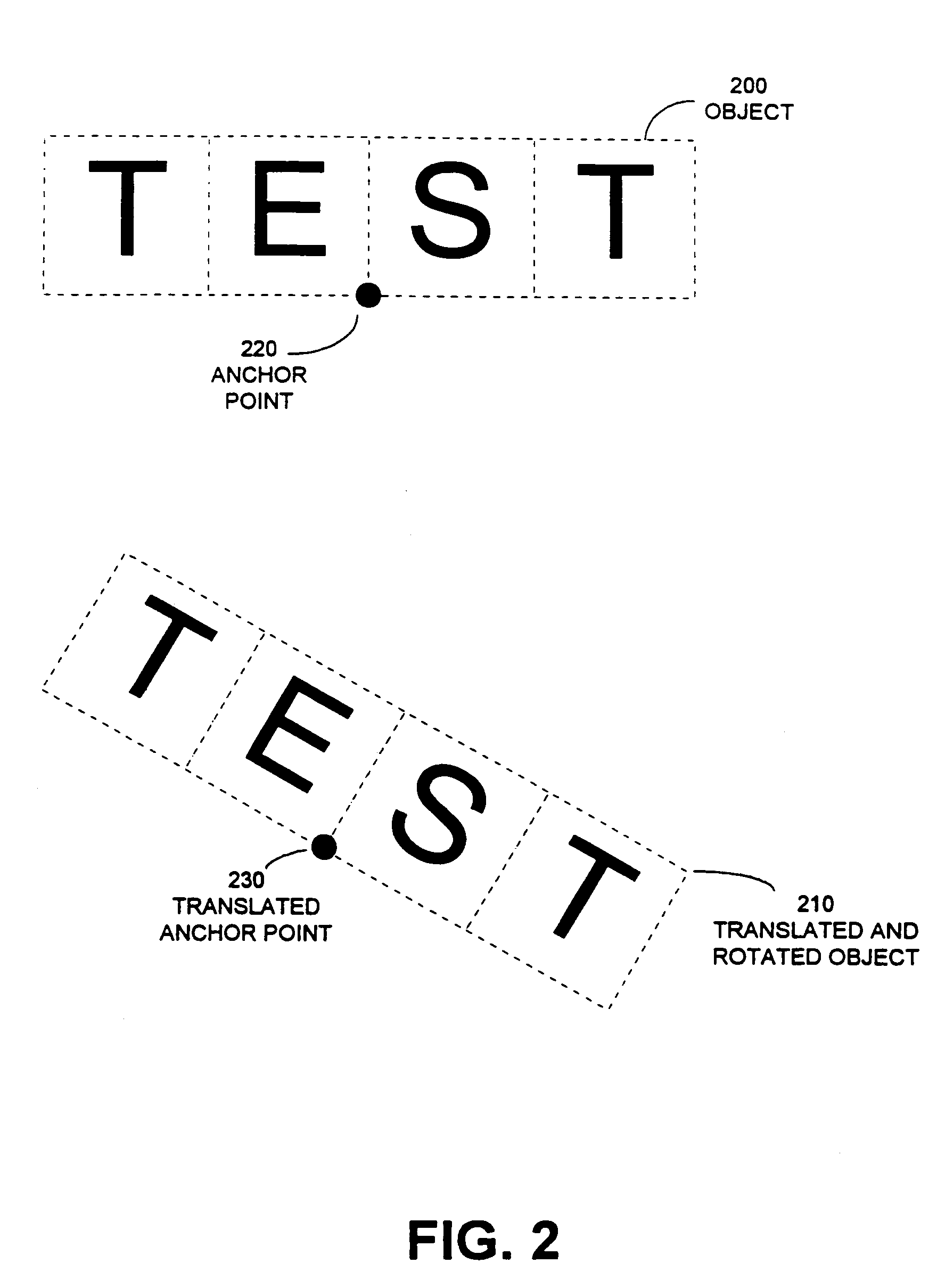
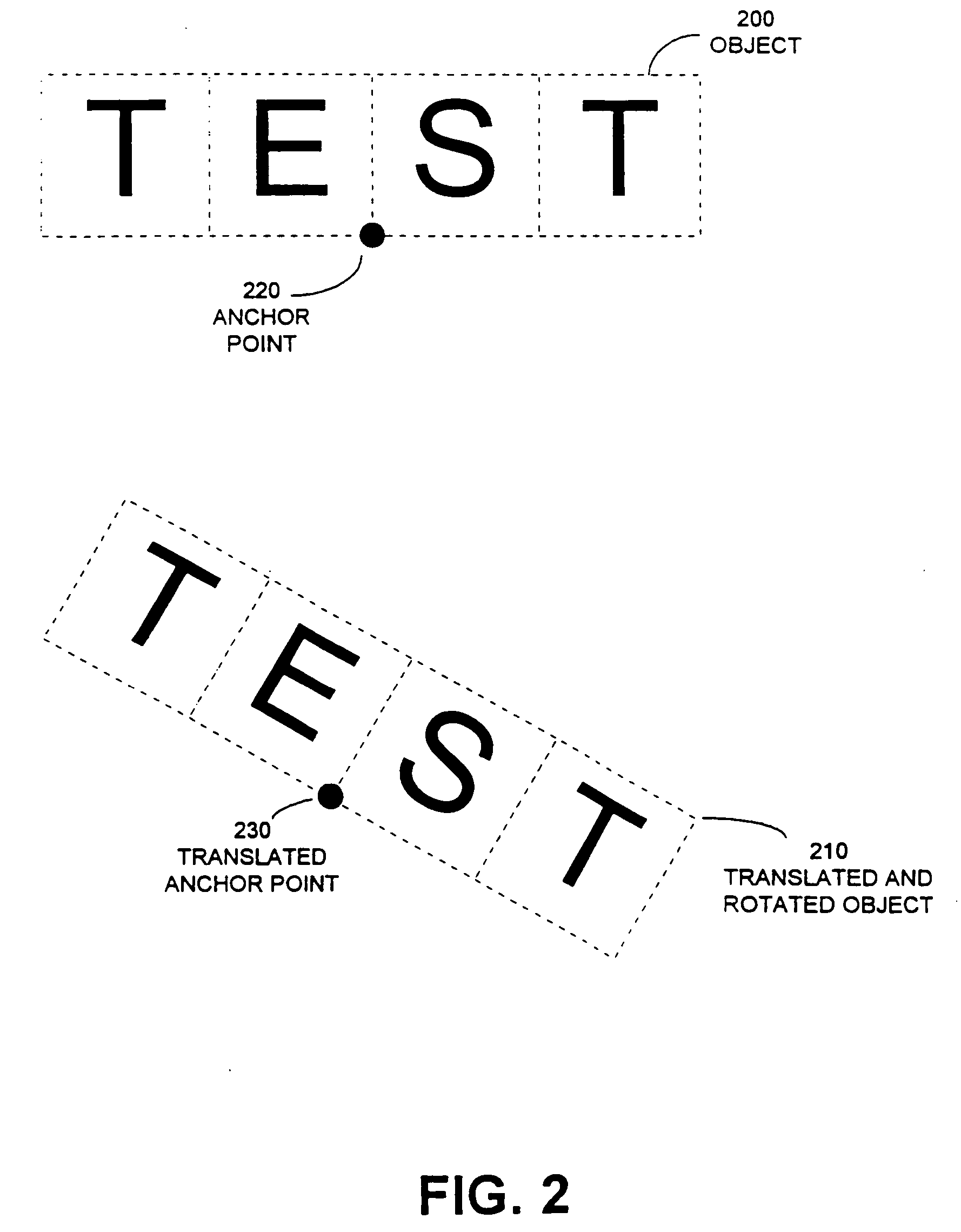
The present invention provides a method for hierarchically decomposing a visual or audio object within an animation into plurality of objects which can be individually edited to achieve particular animation effects. For example, a graphical object may be decomposed into a plurality of graphical sub-objects, each of which is inherits an anchor point from the original object, or is given an original anchor point distinct from the original object. Each sub-object also includes a relative position for the sub-object relative to the anchor point. The path of the anchor point is combined with relative positions of the sub-objects to produce an animation for the object as a whole. This decomposition technique can greatly increase computational efficiency of an animation. It also provides for inheritance of attributes between objects and descendent sub-objects. The objects may support functions, or behaviors, such as morphing or motion blurring. The present invention additionally provides a flexible grouping operation to facilitate modifications to a group of objects. When a first type of modification is made to an attribute of an object in a group, this change is applied to corresponding attributes of other objects in the group. When a second type of modification is made to an attribute of an object in a group, the change only applies to the selected object or objects, and not to other objects in the group. The present invention allows objects to be manipulated on servers which are connected to a display via the Internet.
Owner:RATEZE REMOTE MGMT LLC
Multi-dimensional OLAP (On Line Analytical Processing) inquiry processing method facing column storage data warehouse
ActiveCN102663116AReduce complexityImprove performanceSpecial data processing applicationsSurrogate keyGroup operation
The invention discloses a multi-dimensional OLAP (On Line Analytical Processing) inquiry processing method facing a column storage data warehouse. In the multi-dimensional OLAP inquiry processing method, the OLAP inquiry is decomposed into a bitmap filtering operation, a grouping operation and an aggregation operation. In the bitmap filtering operation, firstly, the predication is executed on a dimension table and a predicate vector bitmap is generated; and a connection operation is converted into a direct dimension table record access operation by surrogate key address mapping so as to implement access according to the positions. In the grouping operation, the pre-generation of grouping units is carried out on fact table records which meet the filtering conditions according to grouping attributes in an SQL (Structured Query Language) command and increasing IDs (identity) are distributed. In the aggregation operation, the grouping aggregation calculation which is carried out according to a grouping item of a grouping filtering vector of a fact table is implemented by carrying out column scanning on the metric attribute of the fact table for once. According to the invention, all OLAP processing tasks can be completed only by carrying out column scanning on the fact table for once, so that the cost of repeatedly scanning is avoided.
Owner:RENMIN UNIVERSITY OF CHINA
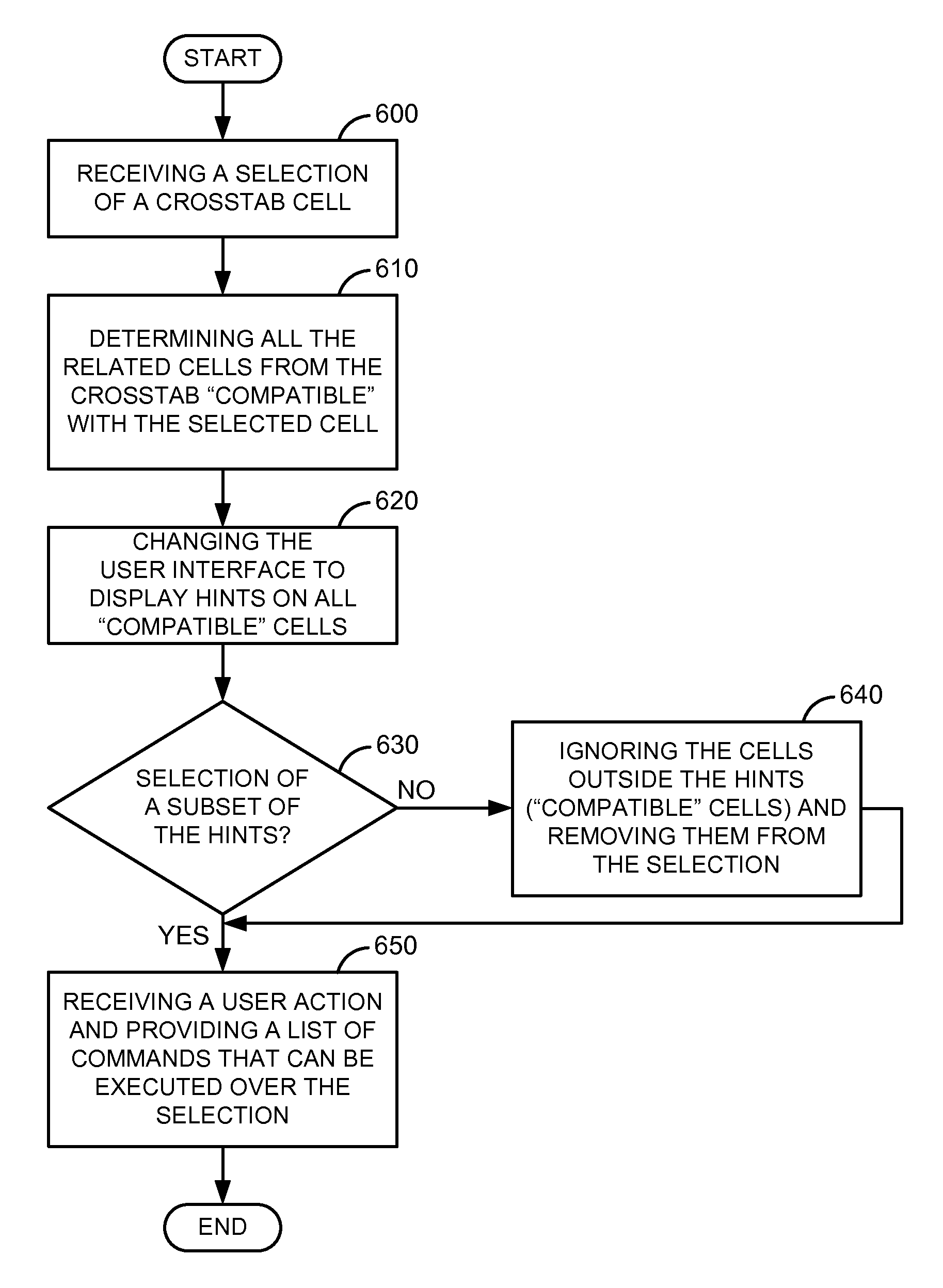
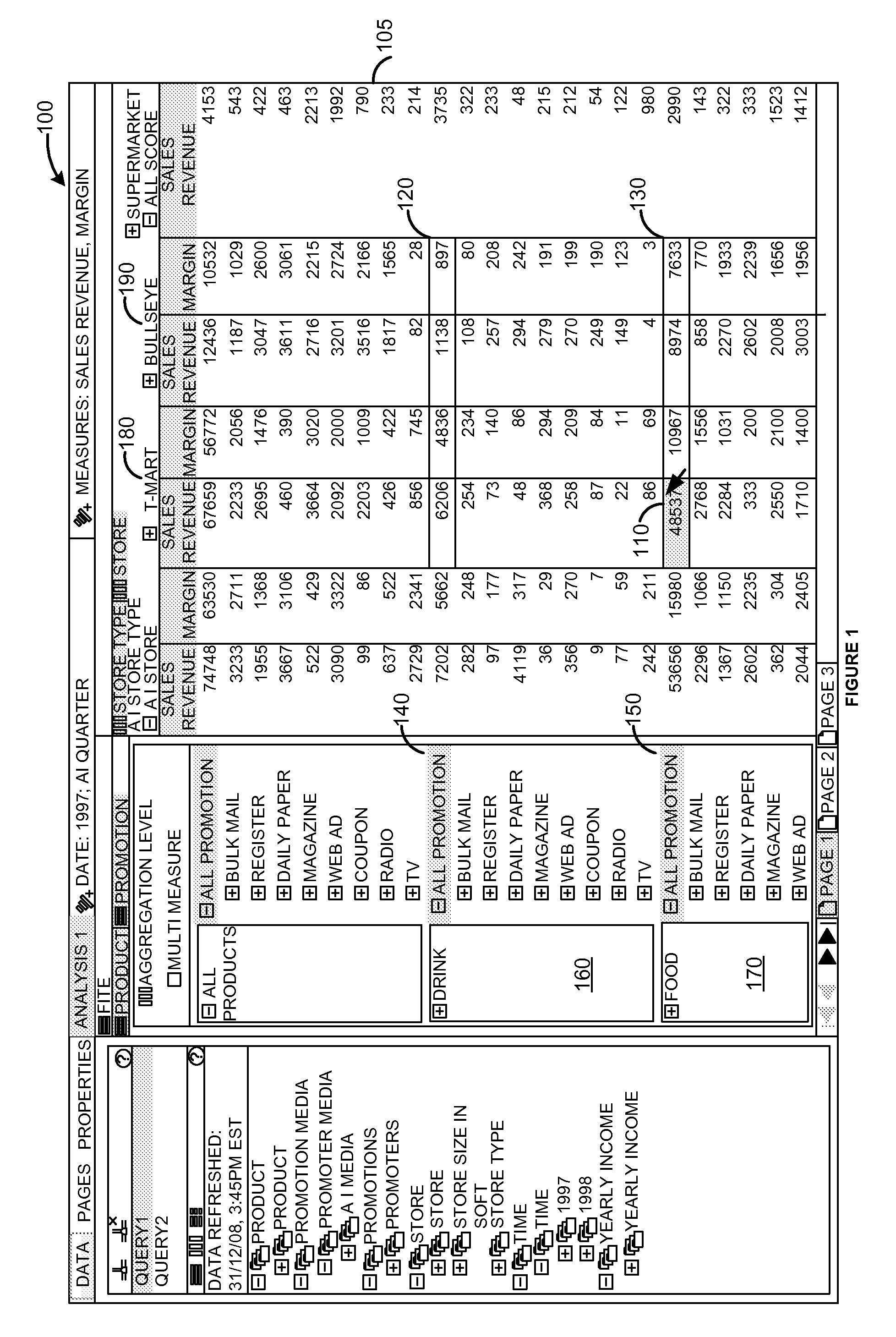
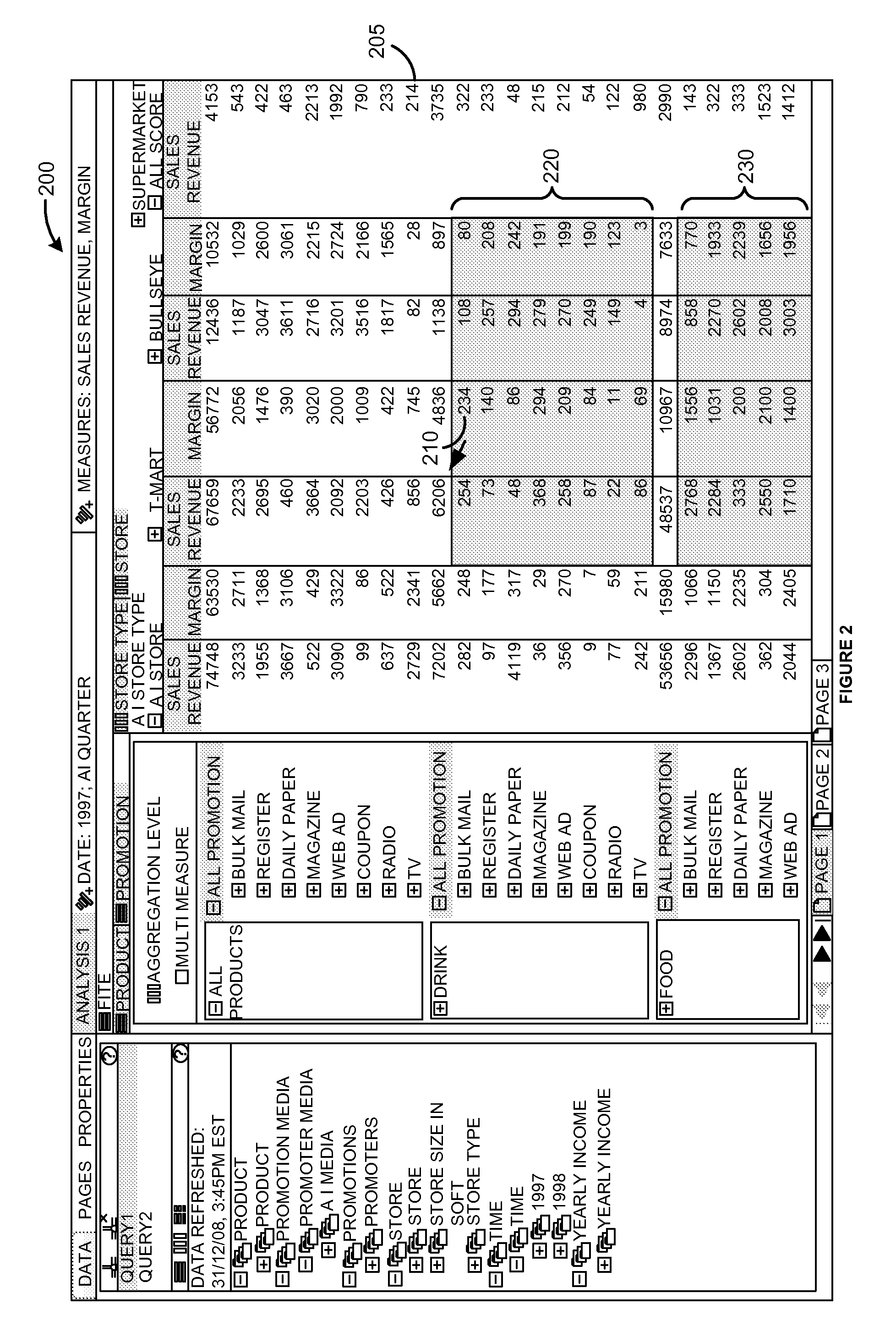
Aggregation level and measure based hinting and selection of cells in a data display
ActiveUS20100313127A1Digital data processing detailsText processingData displayComputer compatibility
Owner:BUSINESS OBJECTS SOFTWARE
Database system providing optimization of group by operator over a union all
InactiveUS20020198872A1Digital data information retrievalData processing applicationsExecution planImproved method
A database system providing improved methods for optimization and execution of queries aggregating information from multiple database tables is described. The improved method breaks serial operations into a group of child operations that can be individually optimized and processed in parallel. A query including a grouping operator over a union node is split by pushing the grouping operation down into each input arm of the union node. Specifically, grouping operators are inserted into each child arm of qualifying union nodes, enabling separate physical database tables to be summarized in parallel. Each of the child grouping operators concurrently groups data and generates summary results in parallel, taking advantage of capabilities of available parallel processing hardware. The aggregate operators of the original master grouping operator are modified to accept and correctly synthesize sub-aggregated results generated by each of the child grouping operators. The method also enables individual optimization of operations on each database table, including use of advantageous index-only execution plans.
Owner:SAP AMERICA
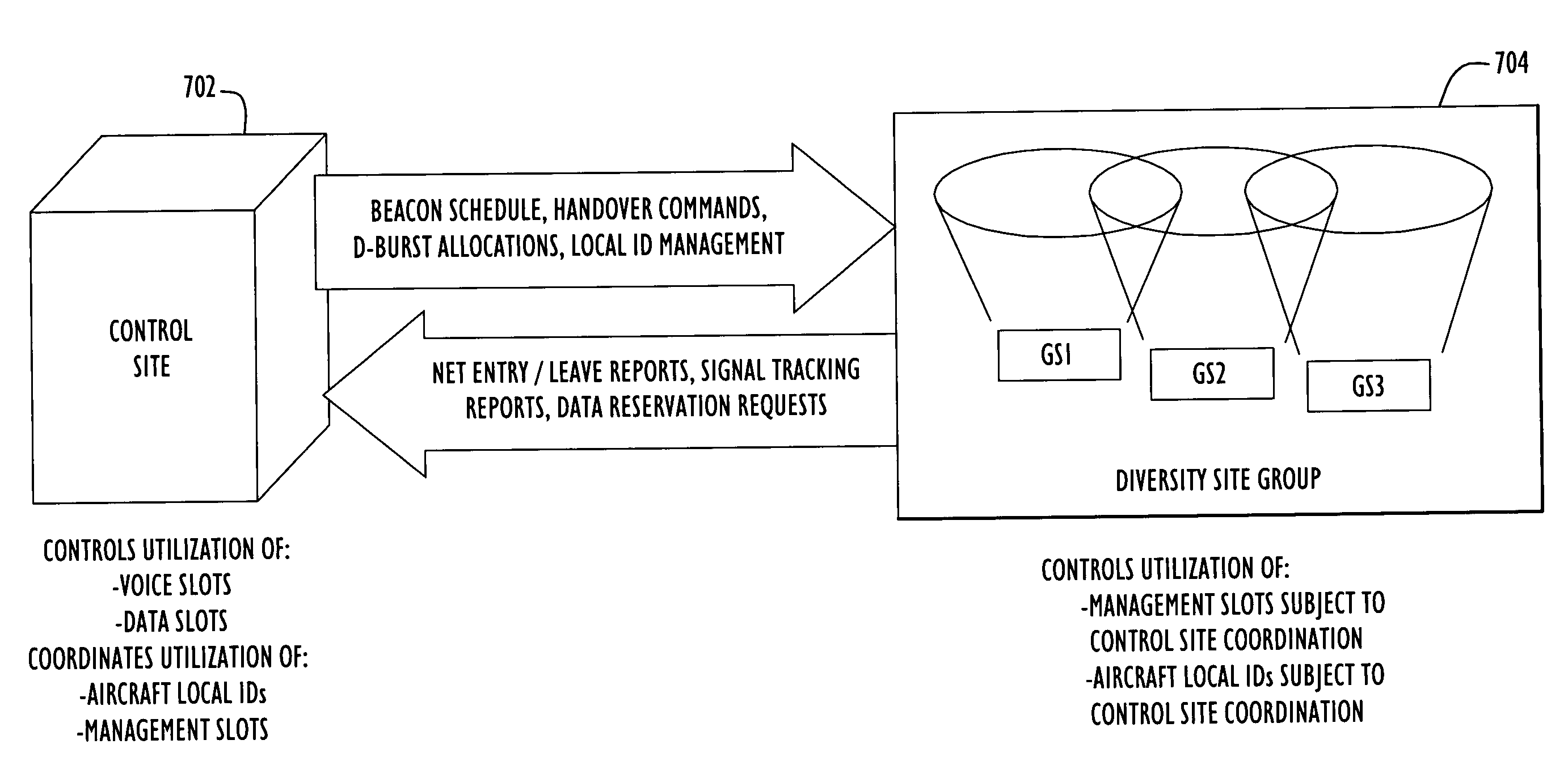
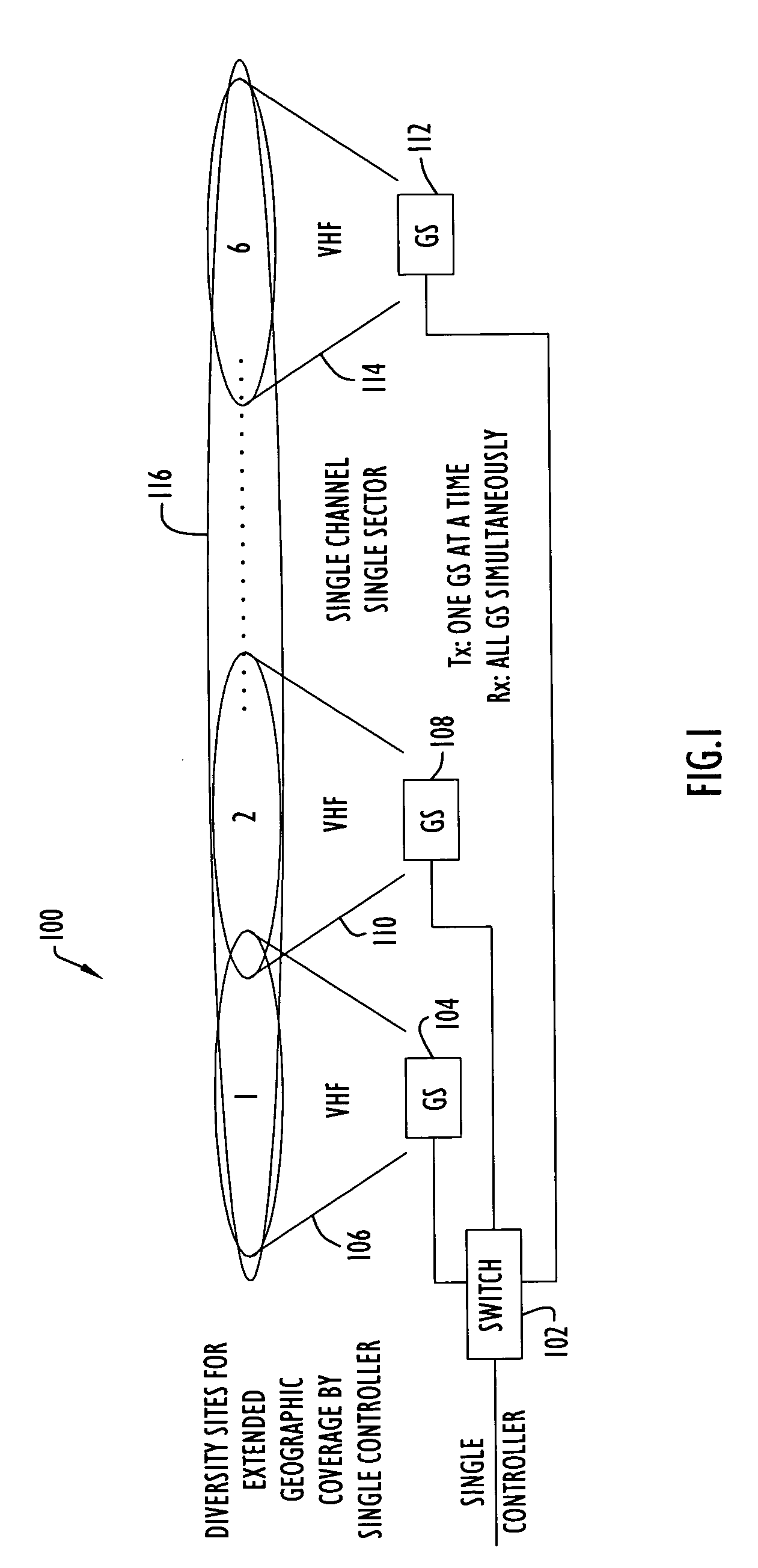
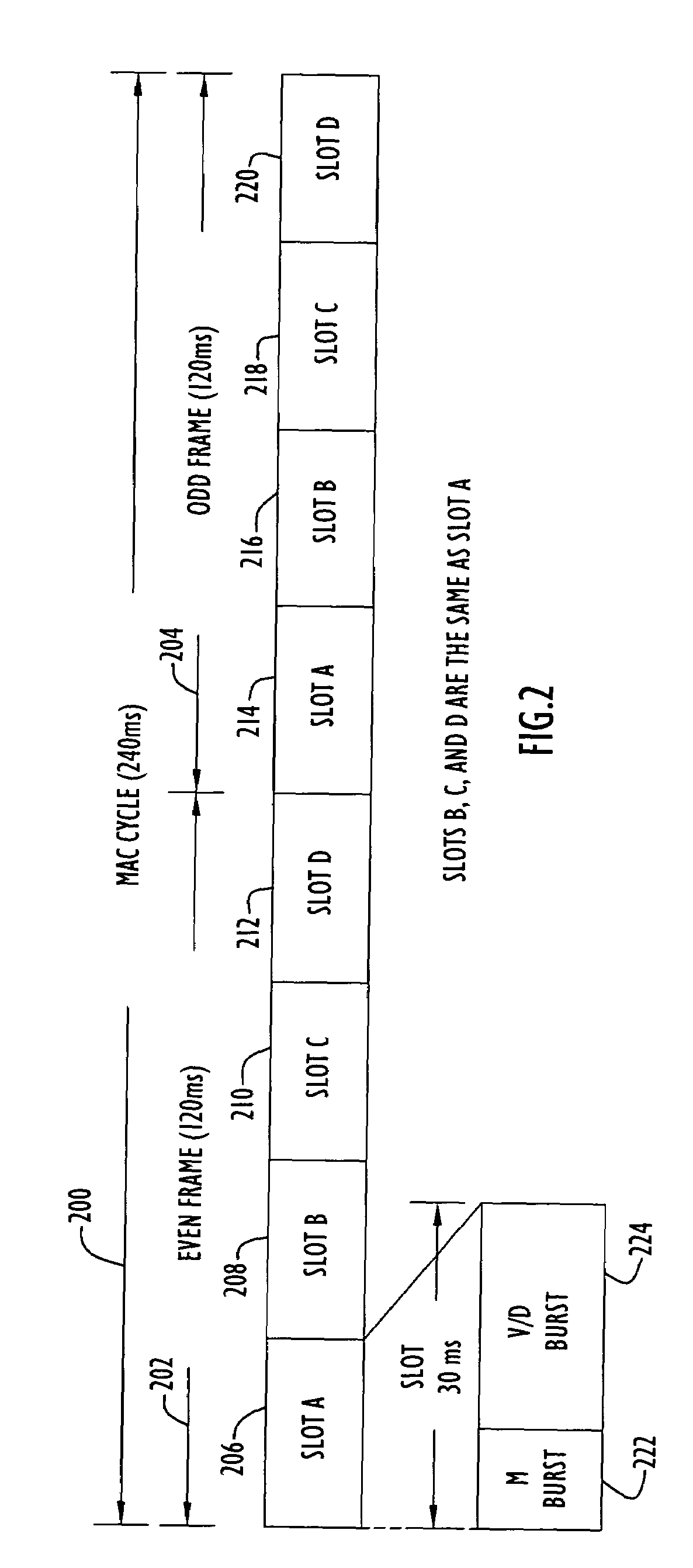
Method for diversity site group operations in air/ground communications
ActiveUS7313143B1Avoid interferenceLimited knowledgeAnalogue computers for vehiclesAnalogue computers for trafficCommon baseSignal quality
Shortcomings in conventional Very High Frequency (VHF) Digital Link Mode 3 (VDL-3) communication techniques for implementing air / ground (A / G) diversity site group (DSG) communication are identified and resolved. Beacon schedules are used to coordinate the use of VDL-3 TDMA management slots. Limited autonomy local address management techniques are used to distribute blocks of unique addresses to the ground stations (GS's) of a DSG from a common base of local addresses maintained at a control site, thus assuring that the respective ground stations assign a unique local identifier to each aircraft supported by the DSG. Aircraft supported by a DSG are polled to obtain time of arrival (TOA) and signal quality information used to: intelligently select the transmit ground station and the receive ground station used for communication between an specific aircraft and the control site; and, intelligently manage contiguous communication handoffs of aircraft from one ground station to another ground station of the DSG.
Owner:HARRIS CORP
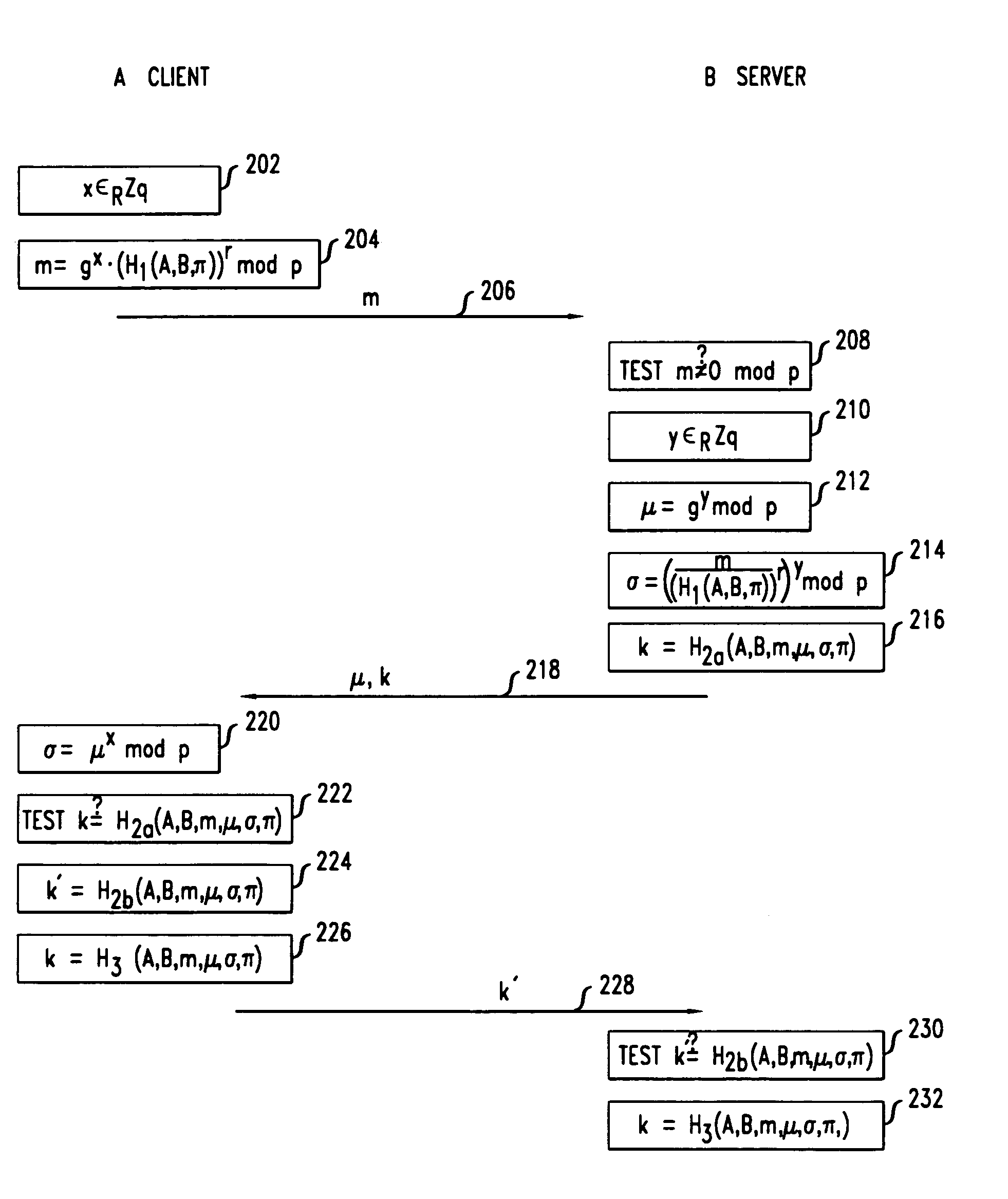
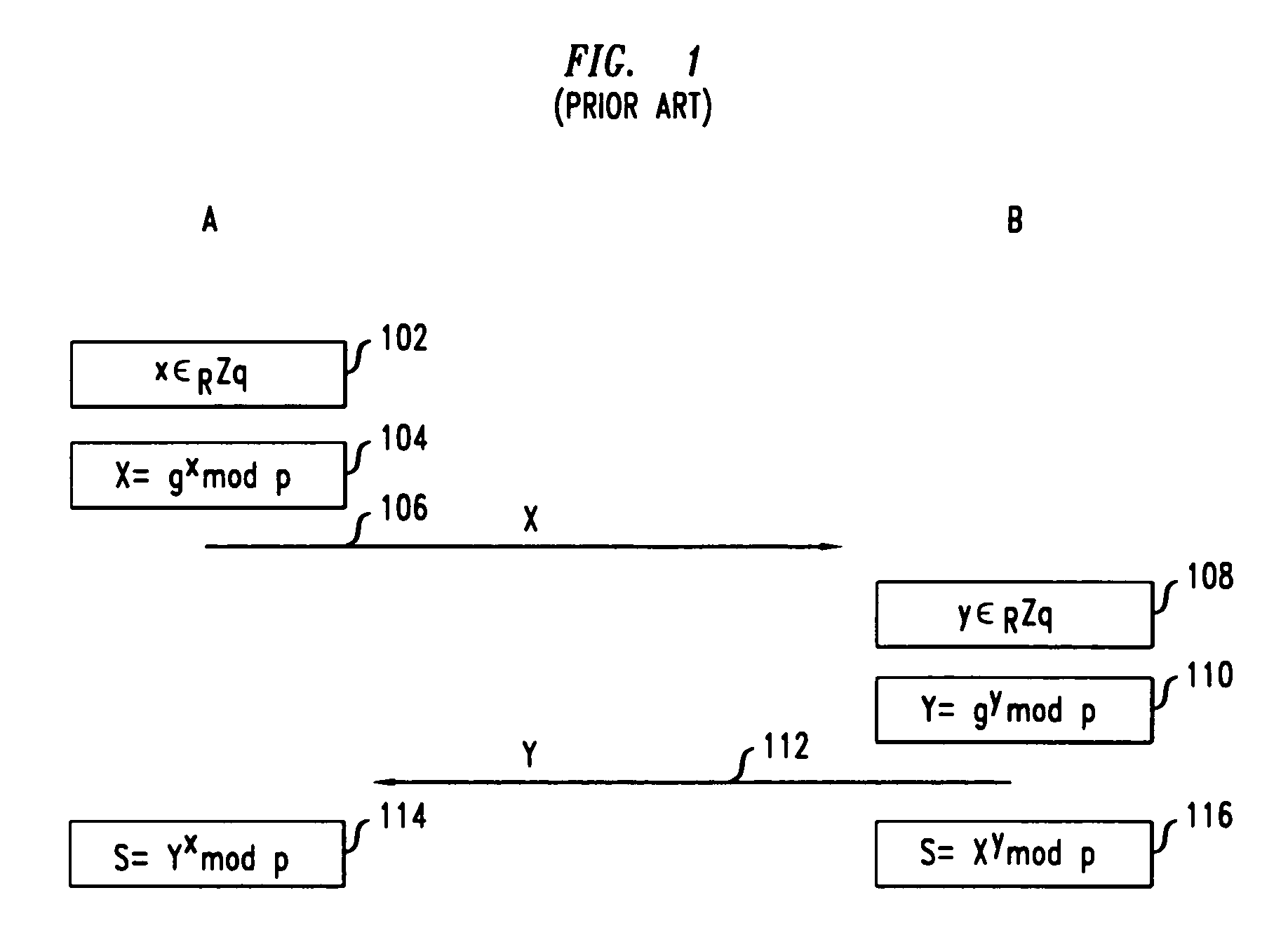
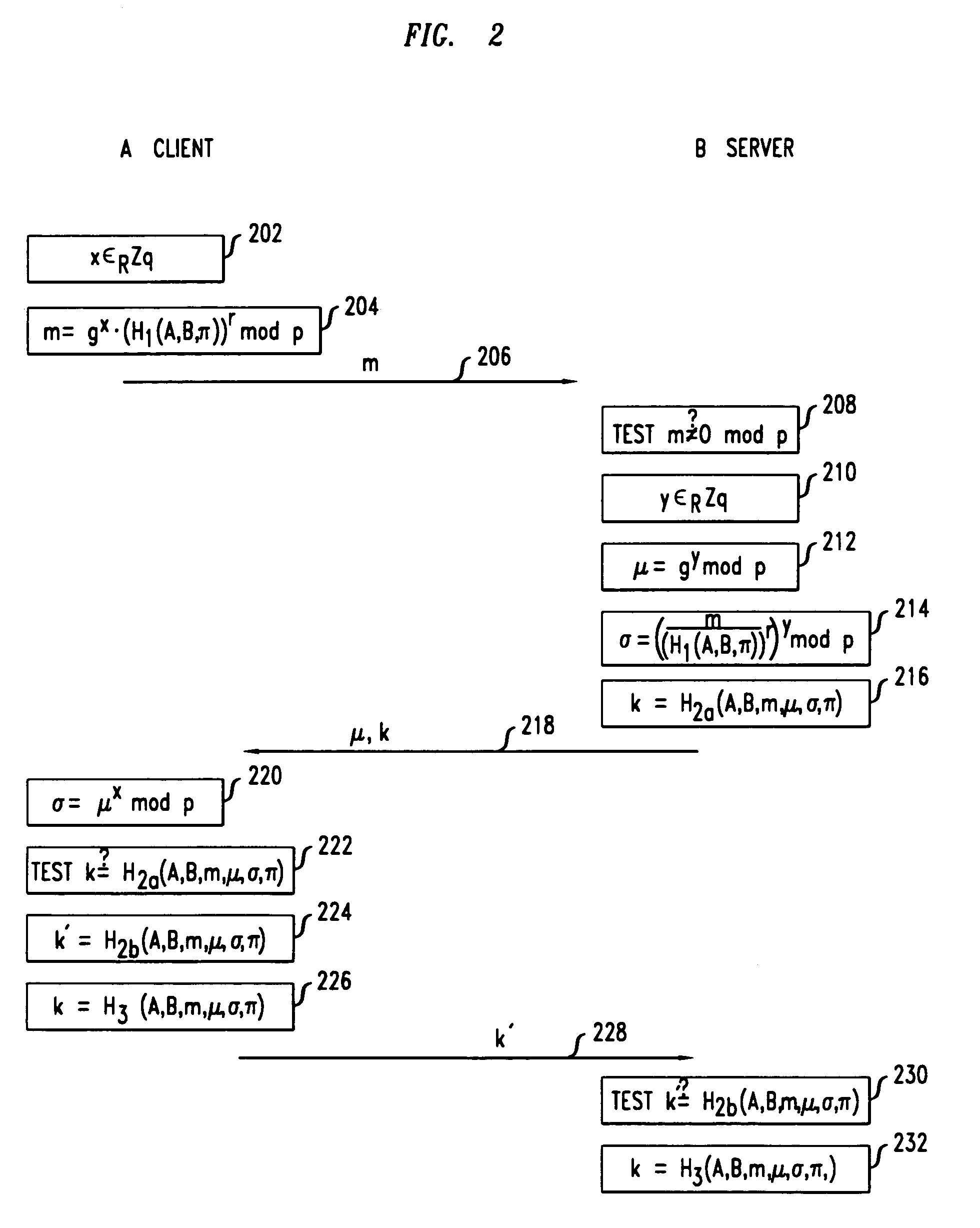
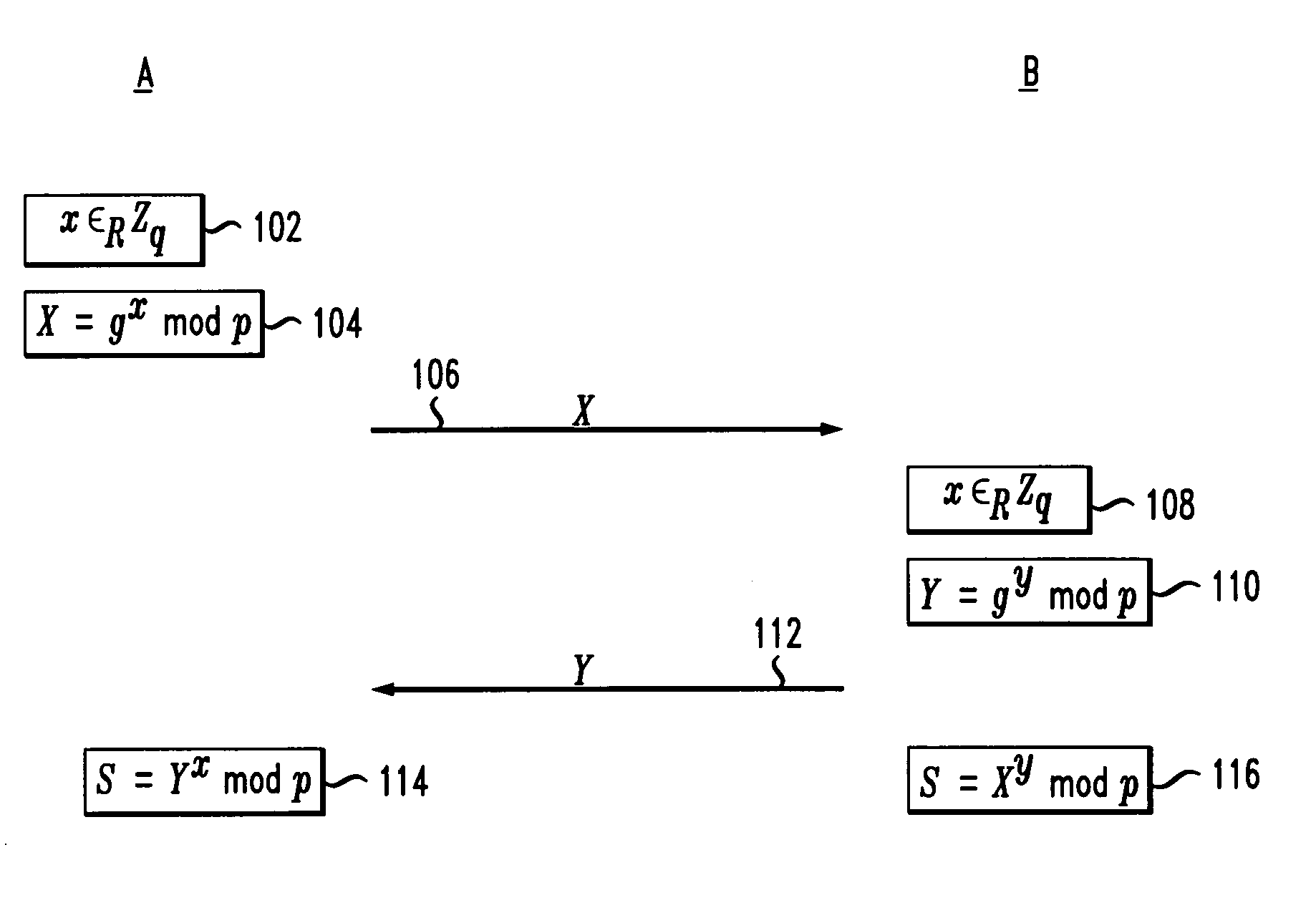
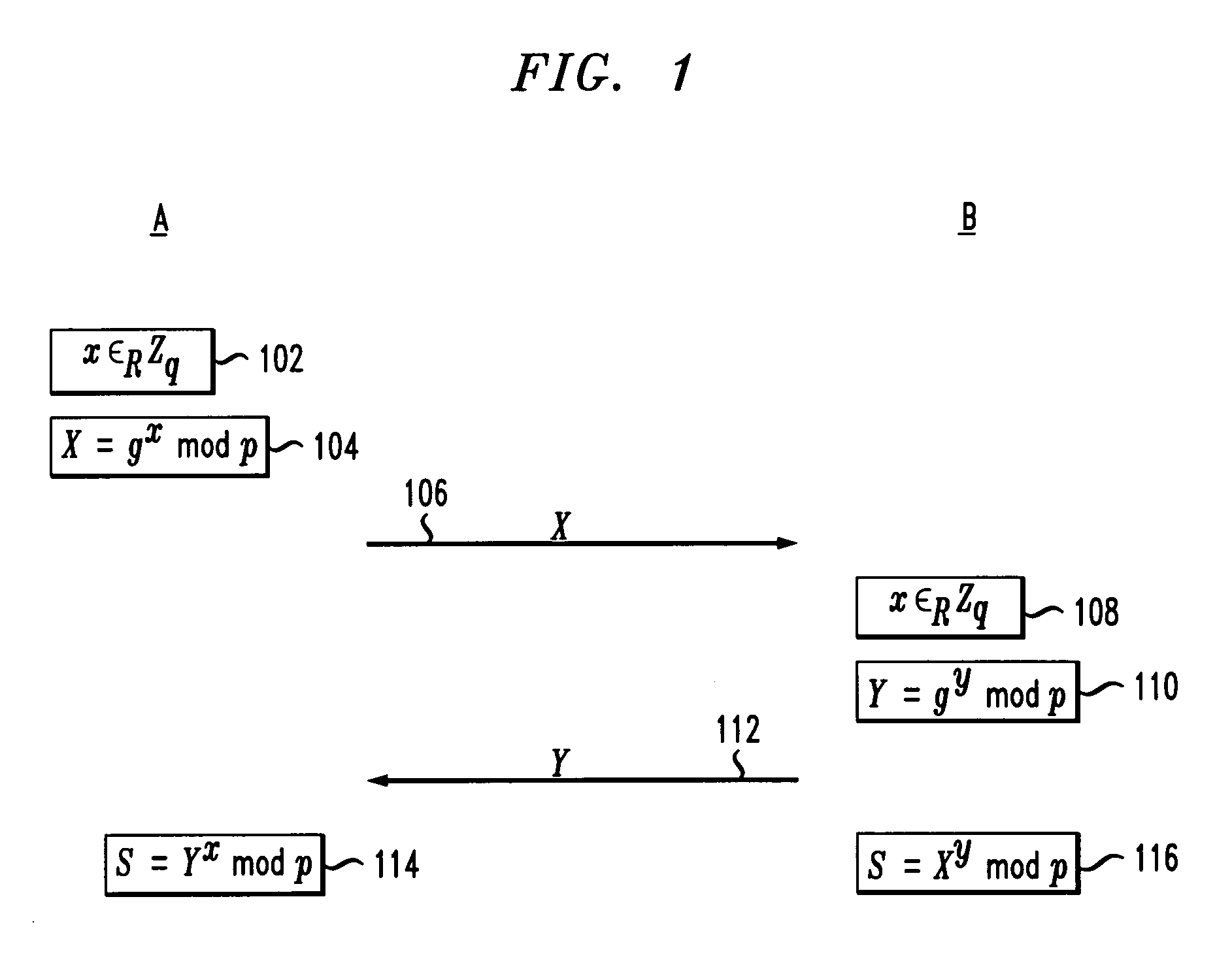
Secure mutual network authentication and key exchange protocol
InactiveUS7047408B1Key distribution for secure communicationUser identity/authority verificationKey exchangeSecure communication
Secure communication protocols are disclosed in which two parties generate a shared secret which may be used as a secure session key for communication between the parties. The protocols are based on Diffie-Hellman type key exchange in which a Diffie-Hellman value is combined with a function of at least a password using the group operation such that the Diffie-Hellman value may be extracted by the other party using the inverse group operation and knowledge of the password. In one embodiment, each of the parties explicitly authenticates the other party, while in another embodiment, the parties utilize implicit authentication relying on the generation of an appropriate secret session key to provide the implicit authentication. Typically, the parties will be a client computer and a server computer. In accordance with other embodiments of the invention, in order to protect against a security compromise at the server, the server is not in possession of the password, but instead is provided with, and stores, a so-called password verifier which is a function of the password and where the password itself cannot be determined from the value of the password verifier.
Owner:ALCATEL-LUCENT USA INC
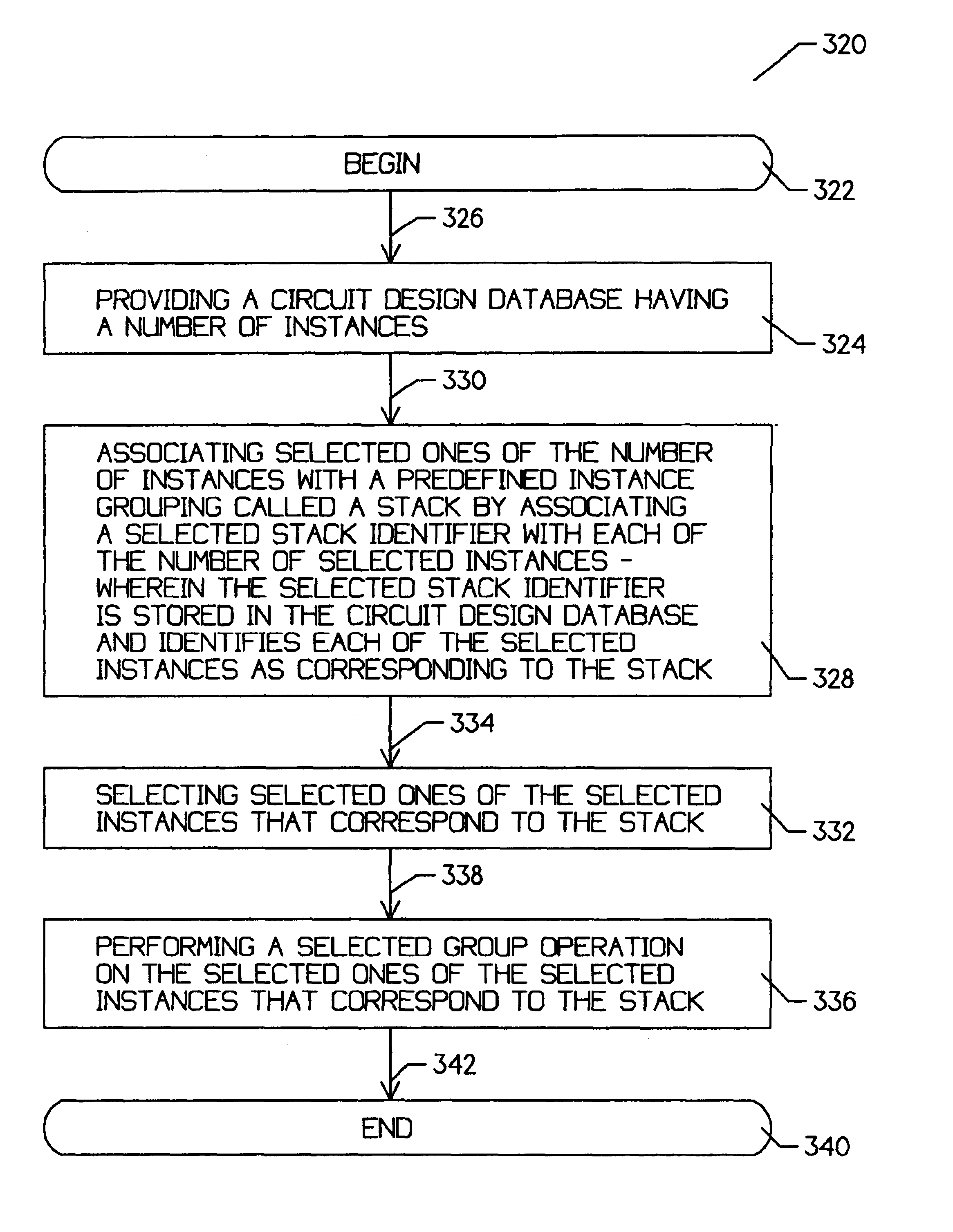
Method and apparatus for associating selected circuit instances and for performing a group operation thereon
InactiveUS6910200B1Effective placementImprove efficiencyAnalogue computers for electric apparatusComputer programmed simultaneously with data introductionGroup operationDatabase
A method and apparatus for associating selected circuit instances, and for allowing a later group manipulation thereof. Prior to entering a database editor tool, selected instances may be associated with one another, and the association may be recorded in the circuit design database. The database editor tool may then read the circuit design database and identify the selected instances and the association therebetween. The associated instances may be called a group, or preferably a stack. The database editor tool may then perform a group operation on the instances associated with the stack.
Owner:UNISYS CORP
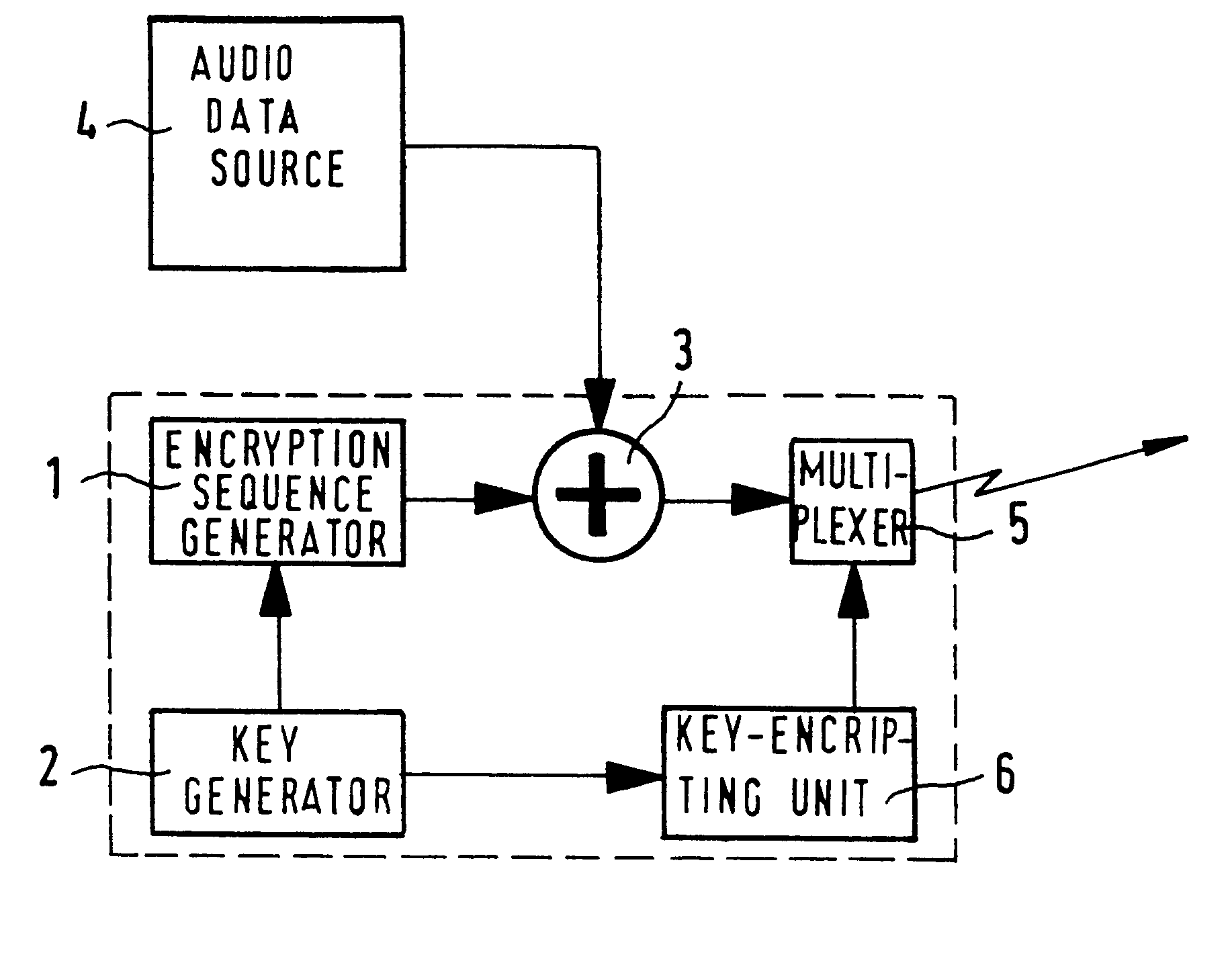
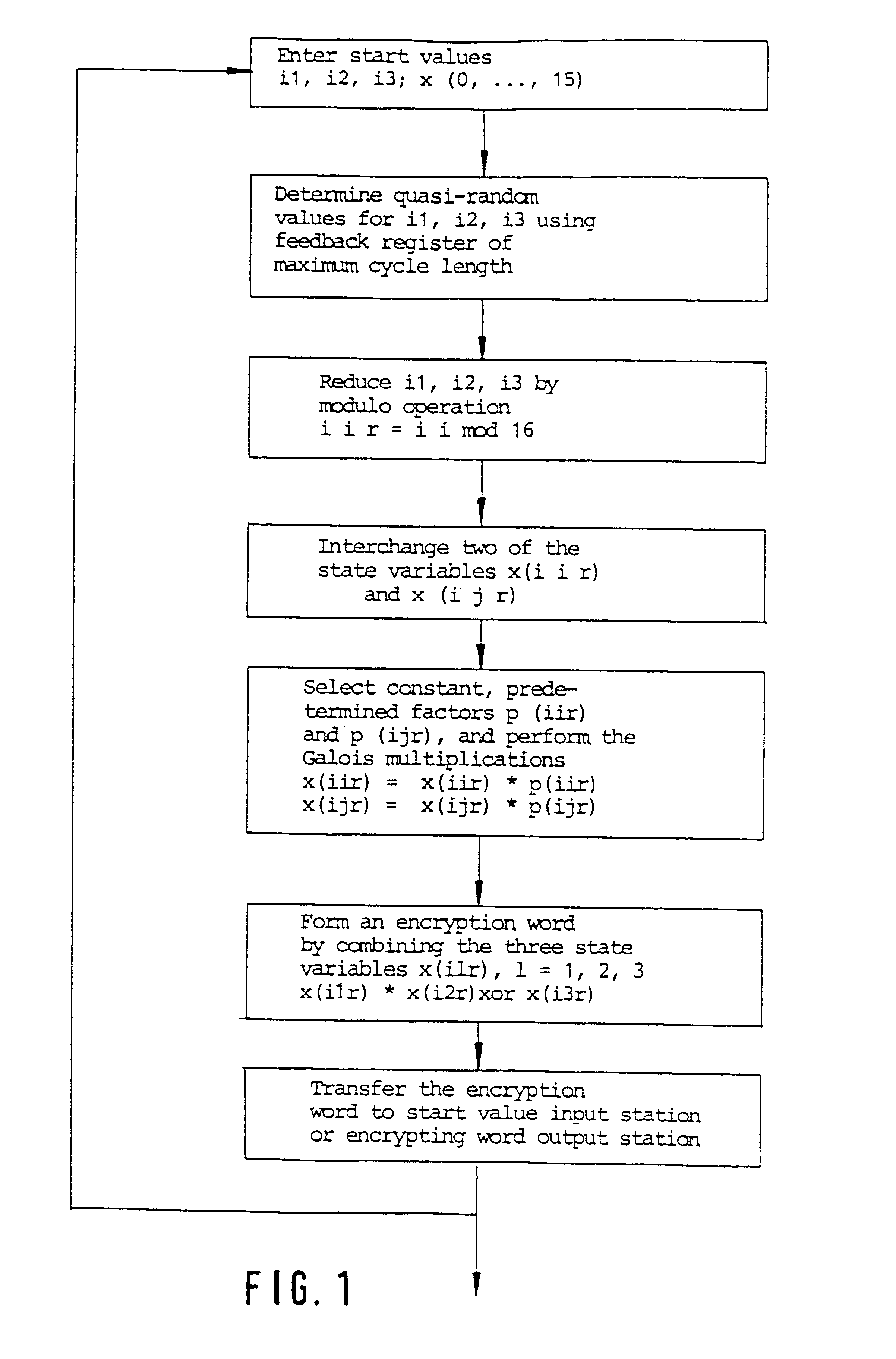
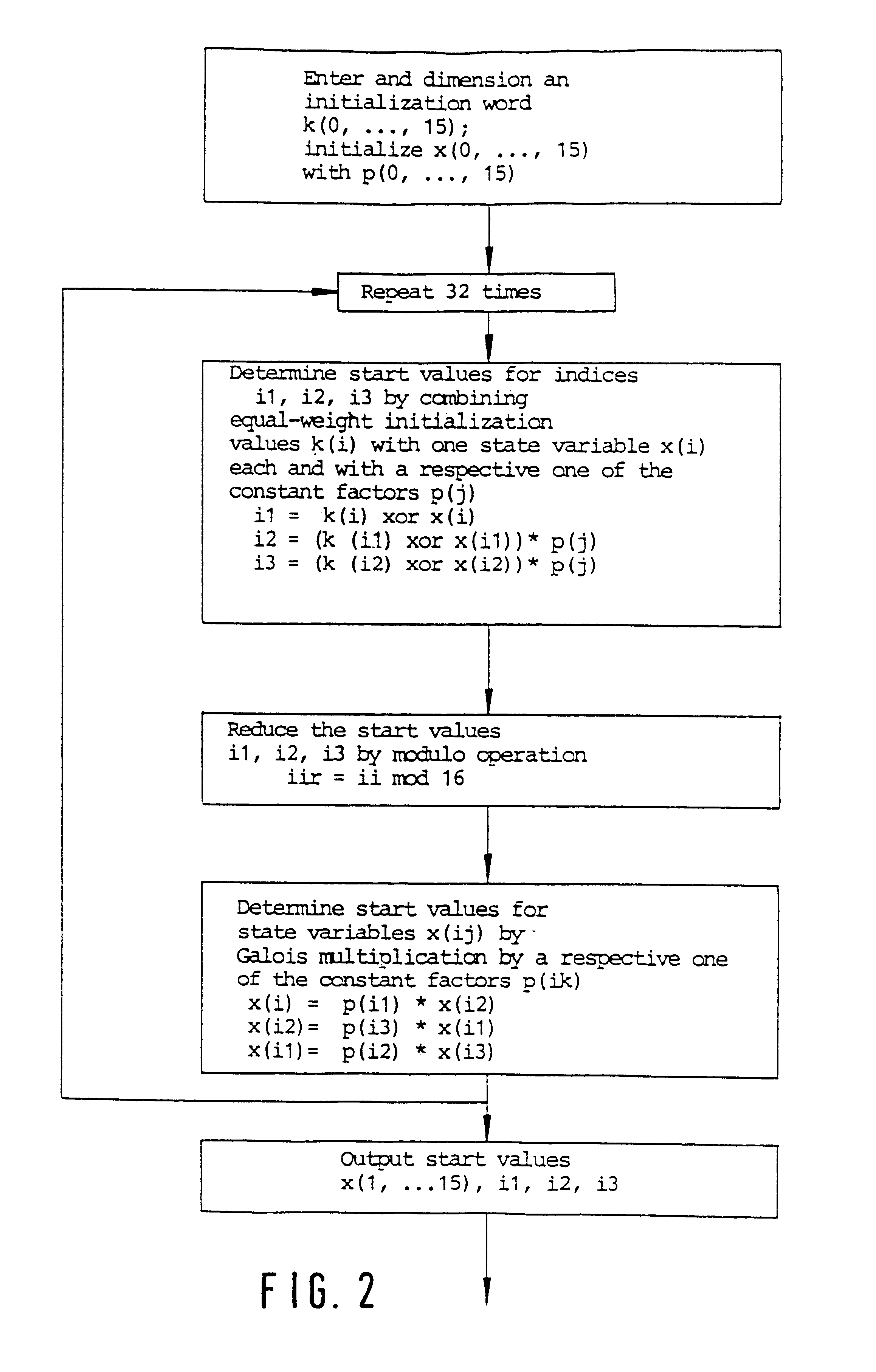
Method for encryption or decryption using finite group operations
InactiveUS6314187B1Decryption is difficultLow costSecret communicationAnalogue-digital convertersComputer hardwareGroup operation
The invention relates to a method for encrypting or decrypting a sequence of successive data words in a data communications device, the method comprising executing an algorithm in which a sequence of quasi-random encryption words is generated from predetermined start values by performing operations in a finite group, and in which a respective one of the encryption words is combined with a respective one of the data words.
Owner:MICRONAS INTERMETTAL GMBH
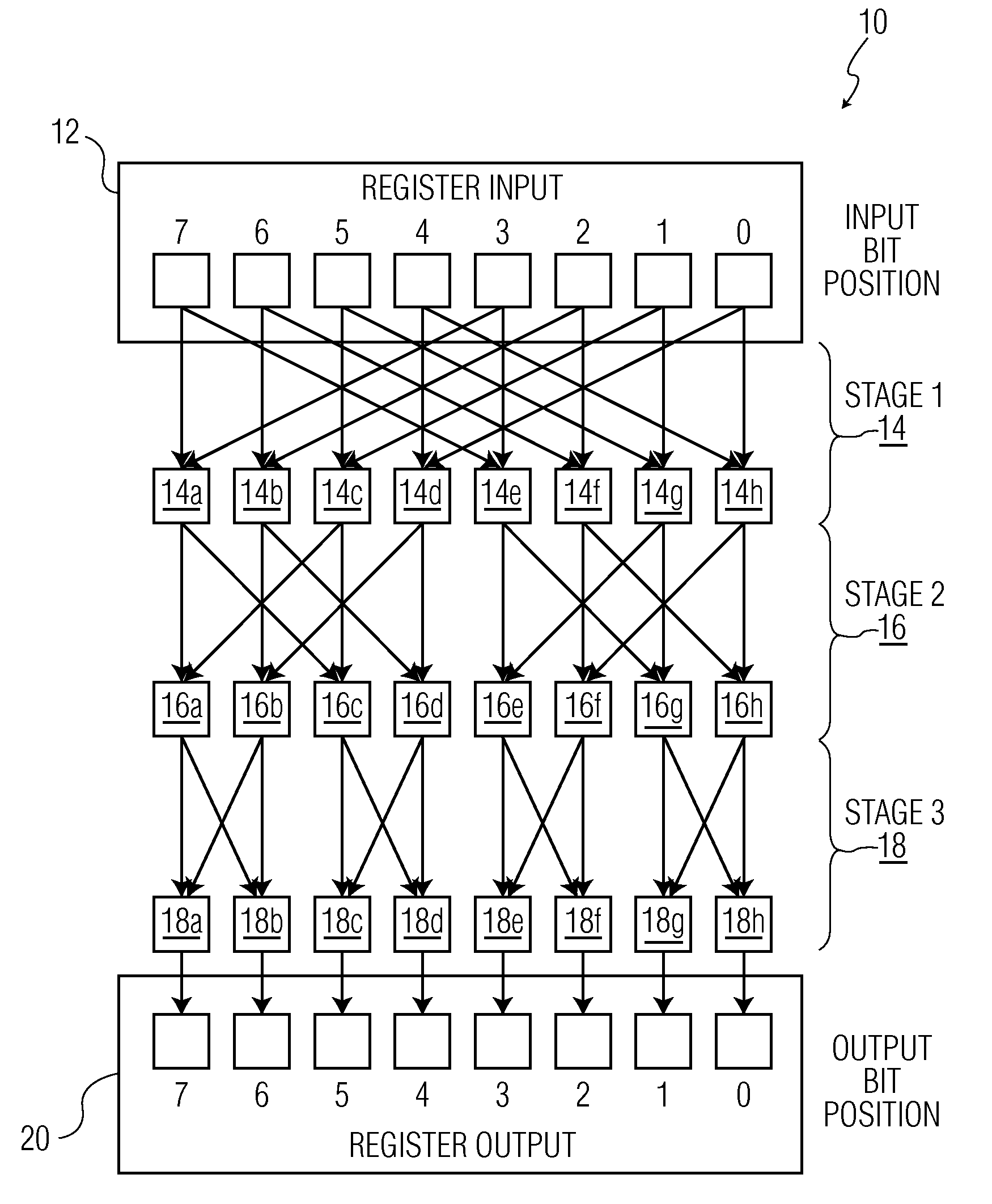
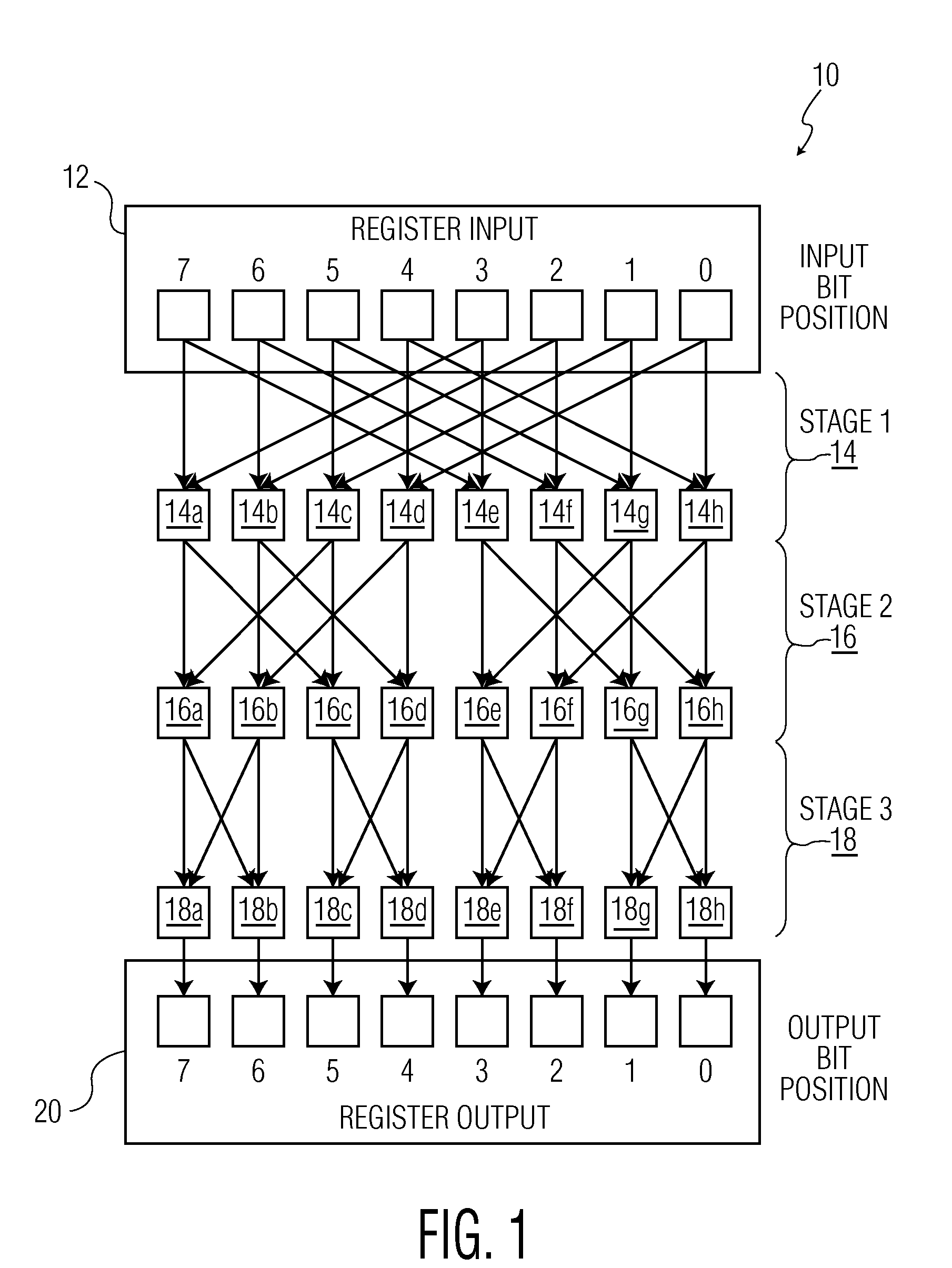
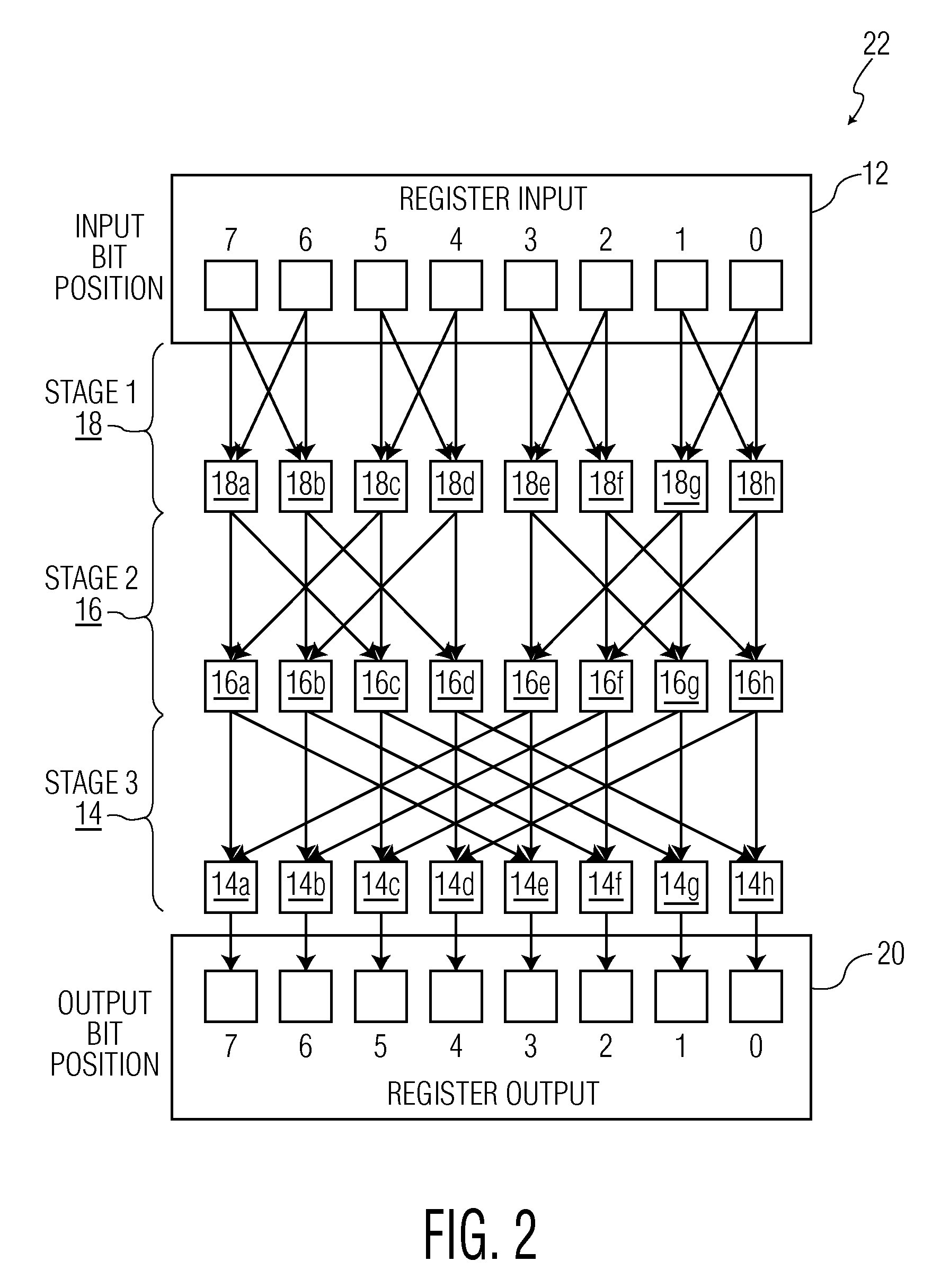
Microprocessor Shifter Circuits Utilizing Butterfly and Inverse Butterfly Routing Circuits, and Control Circuits Therefor
ActiveUS20090138534A1Saving chip spaceReduce the amount requiredDigital data processing detailsDigital computer detailsGroup operationControl circuit
Microprocessor shifter circuits utilizing butterfly and inverse butterfly circuits, and control circuits therefor, are provided. The same shifter circuits can also perform complex bit manipulations at high speeds, including butterfly and inverse butterfly operations, parallel extract and deposit operations, group operations, mix operations, permutation operations, as well as instructions executed by existing microprocessors, including shift right, shift left, rotate, extract, deposit and multimedia mix operations. The shifter circuits can be provided in various combinations to provide microprocessor functional units which perform a plurality of bit manipulation operations.
Owner:THE TRUSTEES FOR PRINCETON UNIV
Mobile object recognizing device, mobile object recognizing method, and computer program thereof
ActiveUS20090252377A1Accurate detectionImage enhancementImage analysisIdentification deviceOptical flow
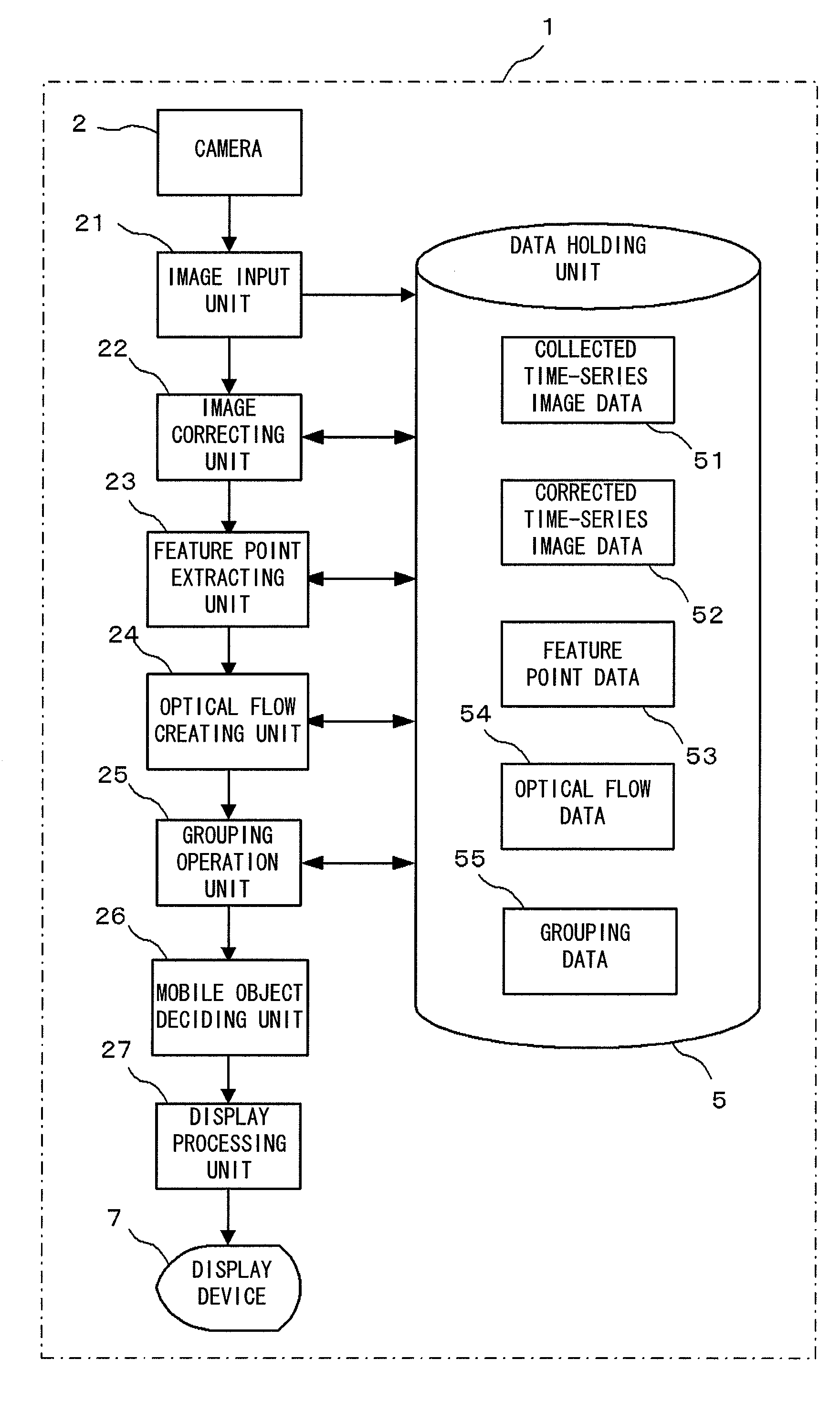
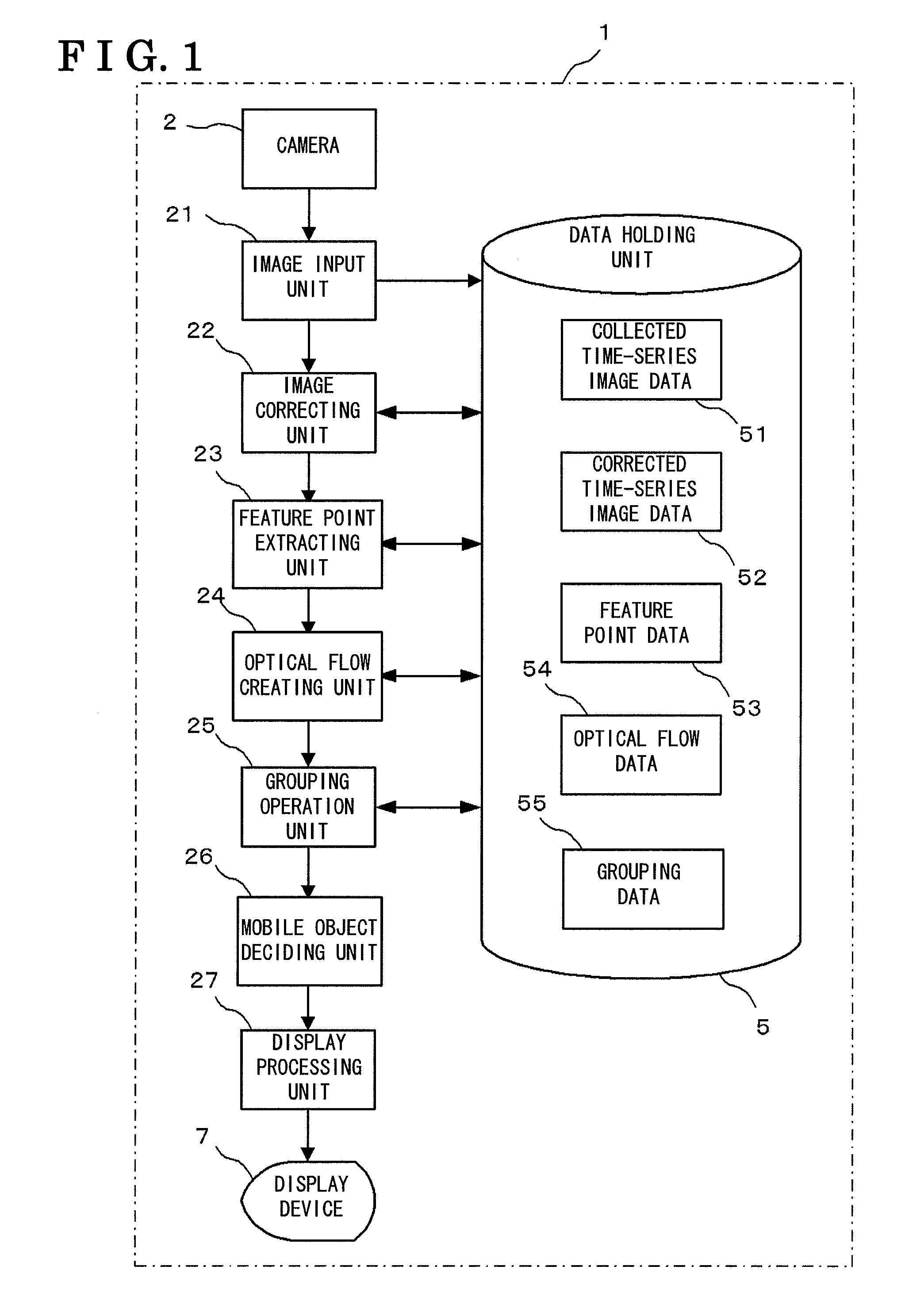
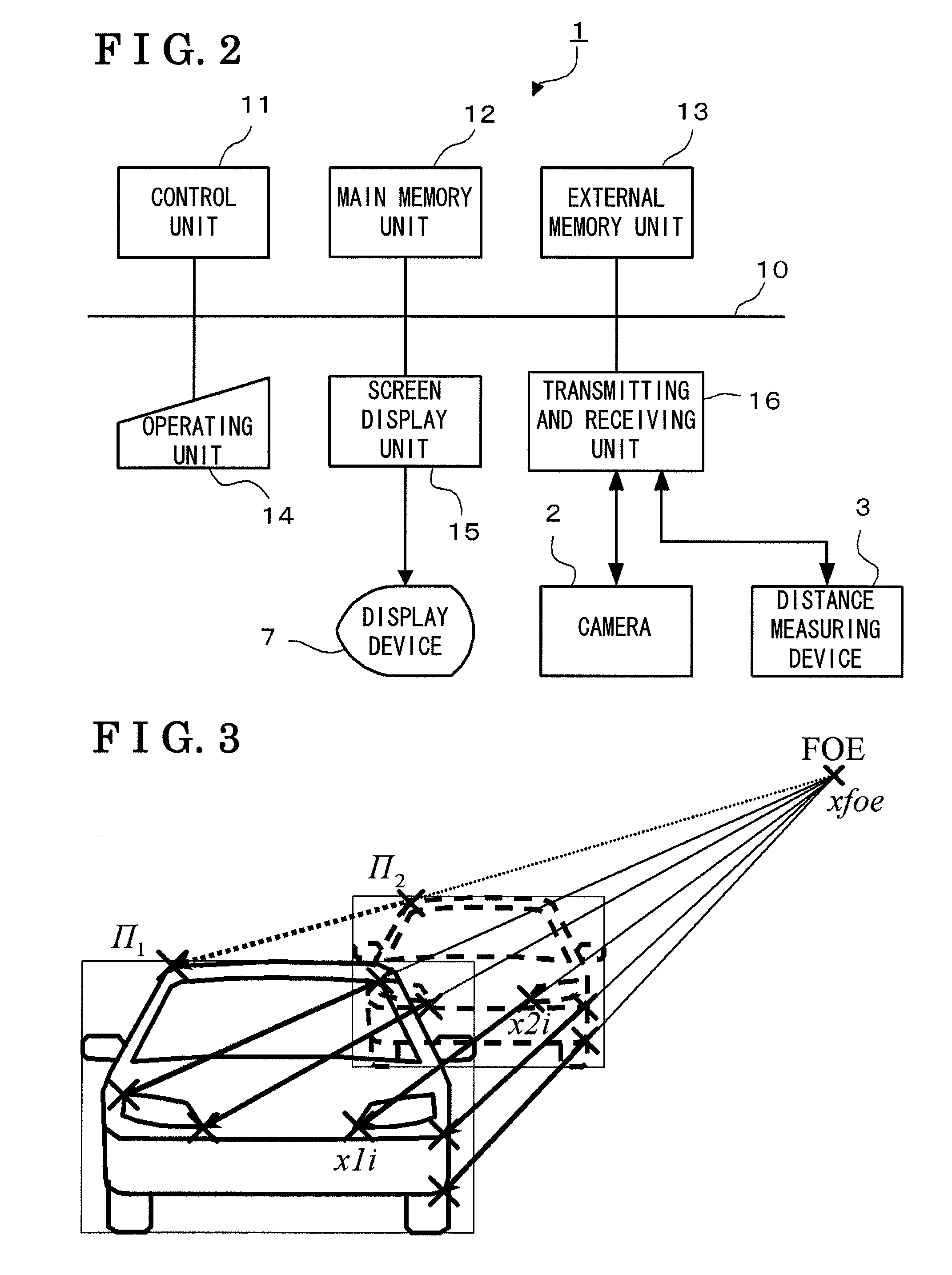
A mobile object recognizing device comprises a camera (2) for taking time-series images, a feature point extracting unit (23) for extracting the feature points of the individual time-series images taken by the camera (2), an optical flow creating unit (24) for comparing the feature points of the time-series images between different images, to create an optical flow joining the feature points having the same pattern, and a grouping operation unit (25) for selecting that optical flow as one belonging to one mobile object, the prolonged line of which intersects with one vanishing point within a predetermined error range and in which the external ratio of a segment joining the other end point and the vanishing point with one end point of the optical flow being the externally dividing point in the extension of the optical flow. The mobile object recognizing device may further comprise an image correcting unit (22) for correcting the image taken by the camera (2), into a transparent diagram in accordance with the characteristics of the lens of the camera (2).
Owner:AISIN SEIKI KK
System and Method for Text Entery
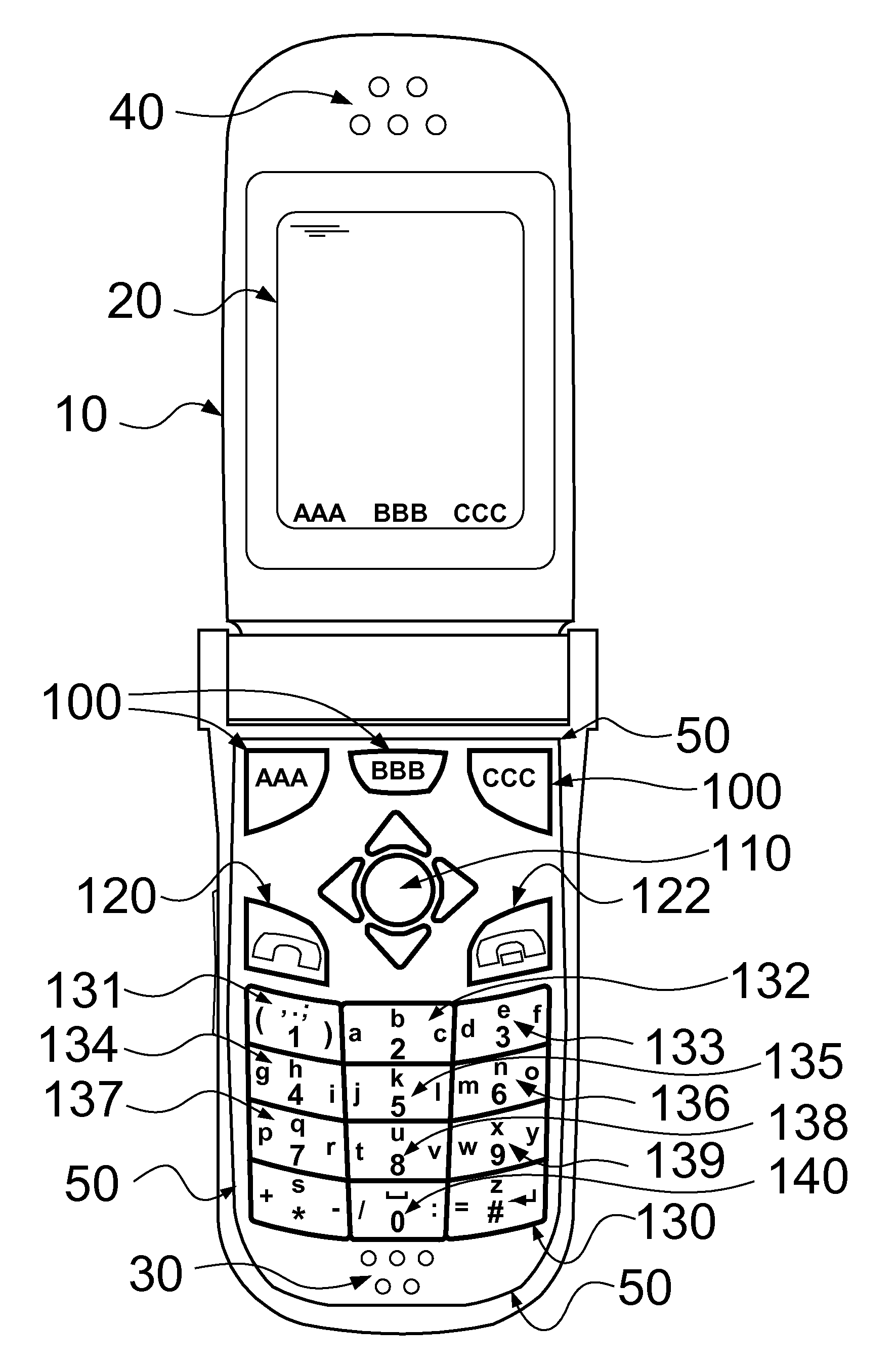
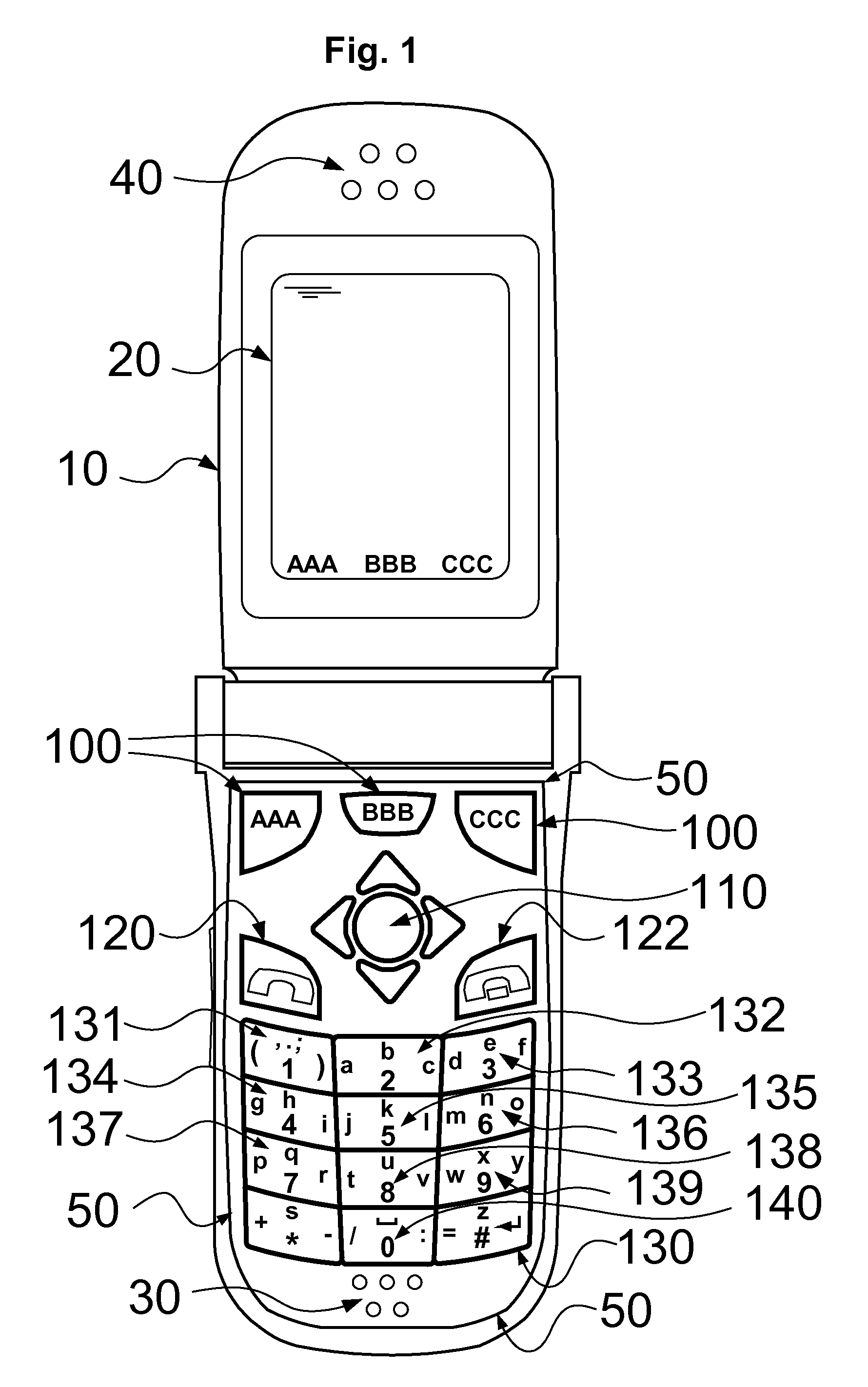
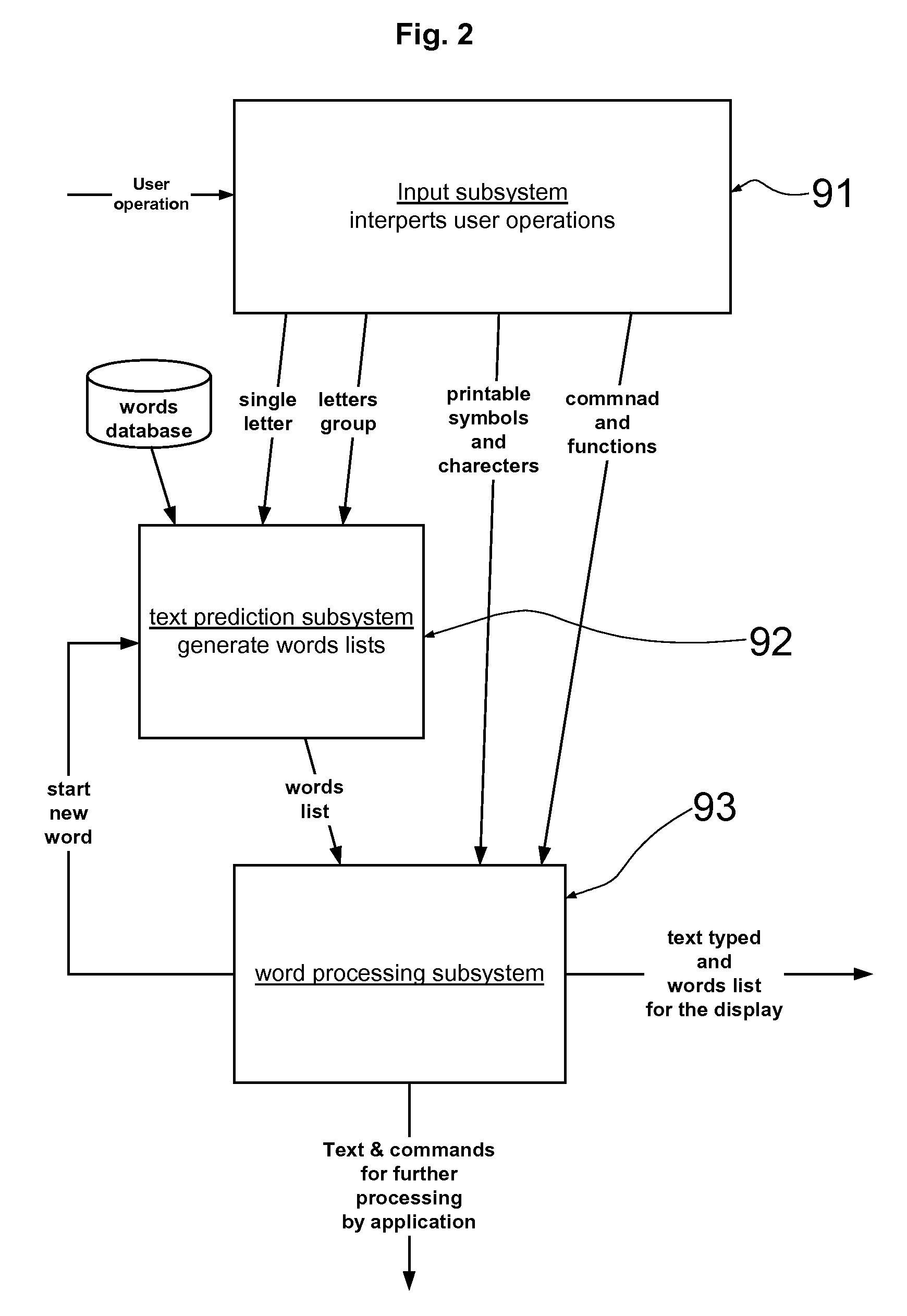
A text entry system for an electronic device comprising: an input subsystem receives user input operations, interprets them as letters, characters, symbols, commands or functions, where the said received user operations interpreted as letters are comprising:(1) single letter operations that select any possible letter from the alphabet,(2) letter group operations that select a group of possible letters from the alphabet; anda text prediction subsystem receives a sequence of the said single letter entries and letter group entries, and produces a list of possible words the user intends to enter based on a priori database of words; and a word processing subsystem, receives the said list of possible words, displays them to the user, receives the user selection of the desired word and further processes the text entry as required.
Owner:HIRSHBERG DAVID
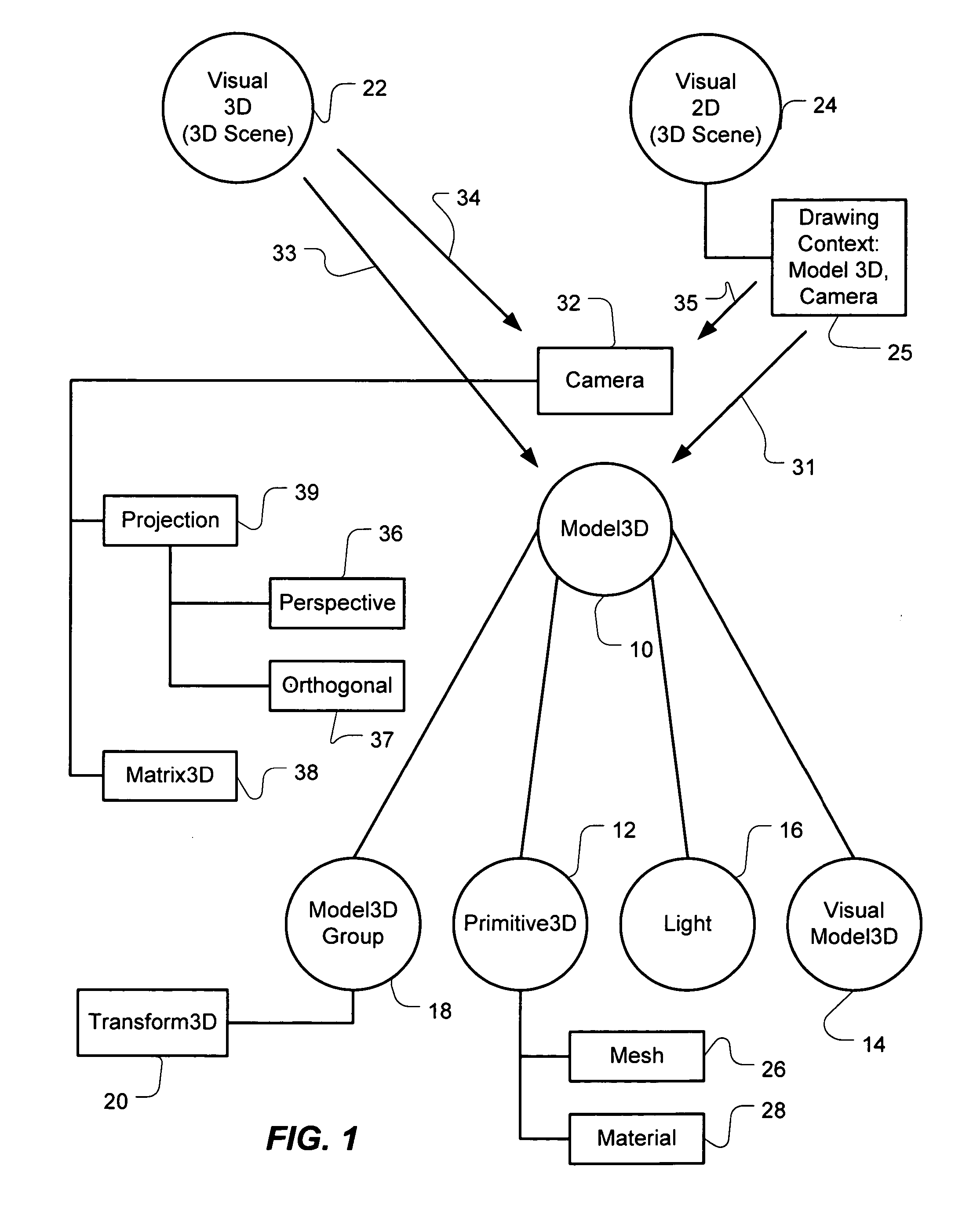
Model 3D construction application program interface
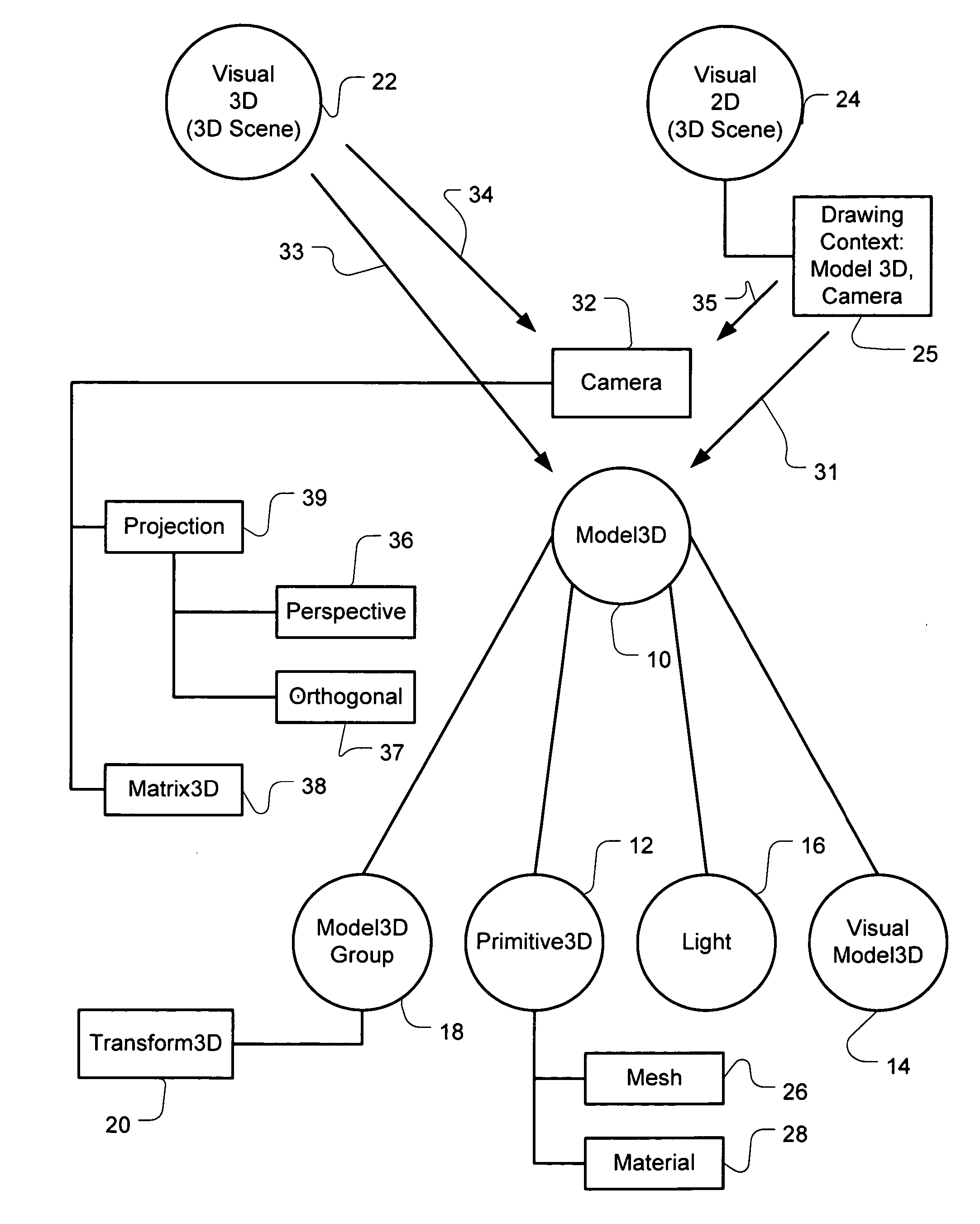
InactiveUS20050243085A1AnimationSpecific program execution arrangementsComputer graphics (images)Object definition
An application program interface may be used to construct a three-dimensional (3D) scene of 3D models defined by model 3D objects. The interface has one or more group objects and one or more leaf objects. The group objects contain or collect other group objects and / or leaf objects. The leaf objects may be drawing objects or an illumination object. The group objects may have transform operations to transform objects collected in their group. The drawing objects define instructions to draw 3D models of the 3D scene or instructions to draw 2D images on the 3D models. The illumination object defines the light type and direction illuminating the 3D models in the 3D scene. A method processes a tree hierarchy of computer program objects constructed with objects of the application program interface. The method traverses branches of a 3D scene tree hierarchy of objects to process group objects and leaf objects. The method detects whether the next unprocessed object is a group object of a leaf object. If it is a leaf object, the method detects whether the leaf object is a light object or a drawing 3D object. If the leaf object is a light object, the illumination of the 3D scene is set. If a drawing 3D object is detected, a 3D model is drawn as illuminated by the illumination. The method may also performs a group operation on the group of objects collected by a group object.
Owner:MICROSOFT TECH LICENSING LLC
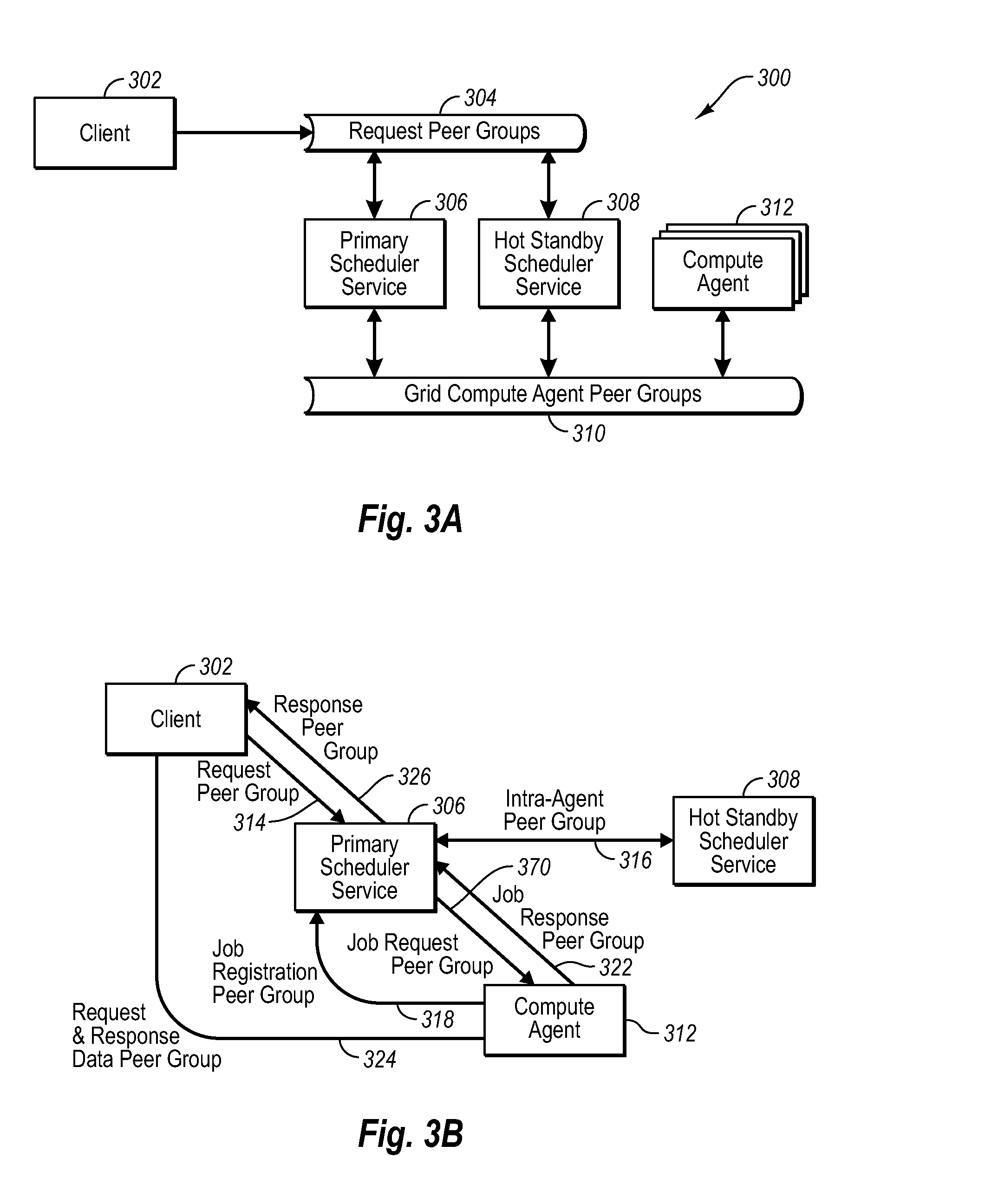
Multiple peer groups for efficient scalable computing
InactiveUS20080080530A1Time-division multiplexData switching by path configurationScalable computingGroup operation
Owner:MICROSOFT TECH LICENSING LLC
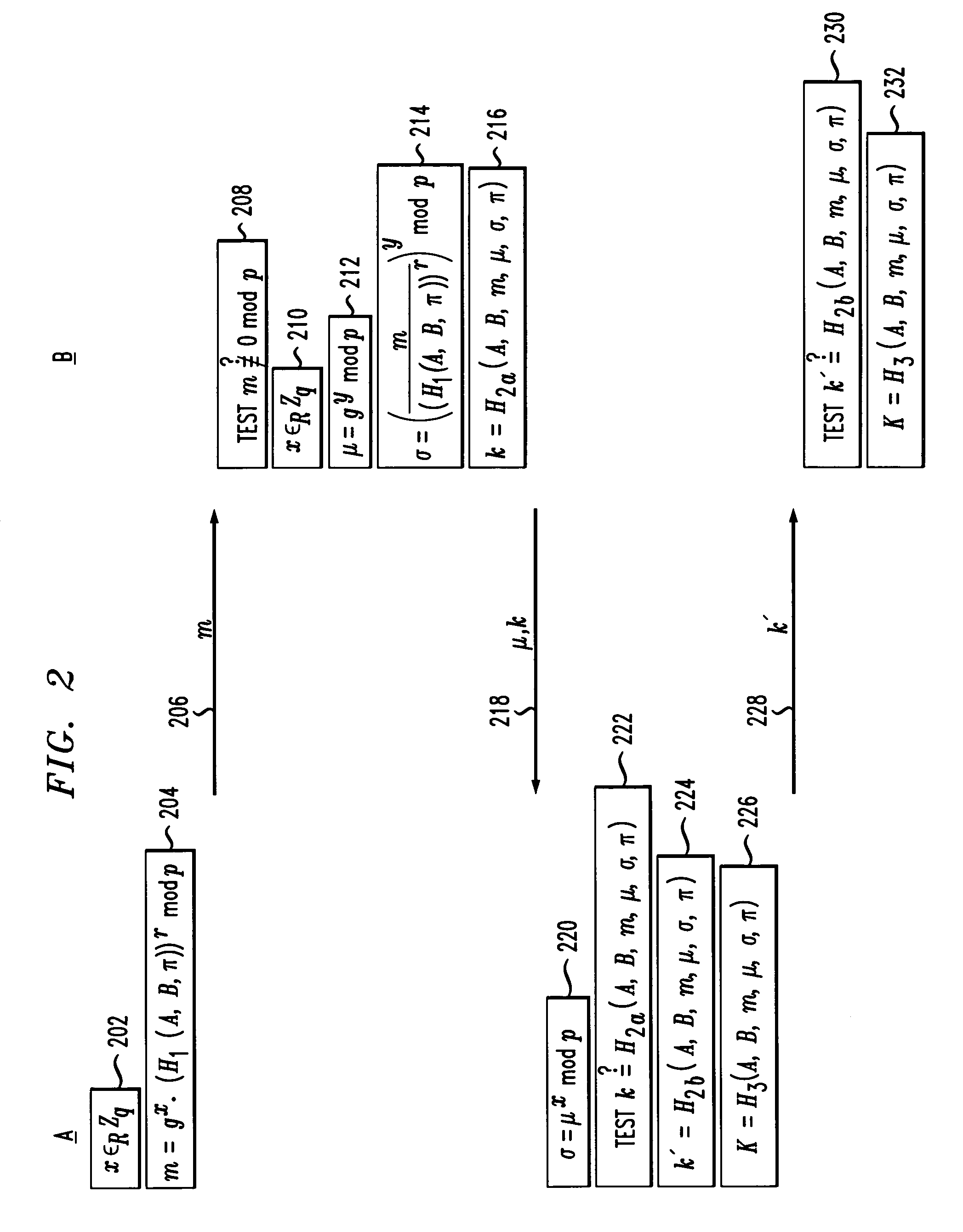
Methods and apparatus for providing efficient password-authenticated key exchange
InactiveUS7076656B2Reduce computational intensityKey distribution for secure communicationUser identity/authority verificationPasswordCryptographic protocol
A secure protocol is provided which uses a Diffie-Hellman type shared secret, but modified such that the two parties may authenticate each other using a shared password. In accordance with the invention, a party generates the Diffie-Hellman value gx and combines it with a function of at least the password using a group operation, wherein any portion of a result associated with the function that is outside the group is randomized. The resulting value is transmitted to the other party. The group operation is defined for the particular group being used. Every group has a group operation and a corresponding inverse group operation. Upon receipt of the value, the other party performs the inverse group operation on the received value and the function of at least the password, and removes the randomization of any portion of the result associated with the function that is outside the group, to extract gx such that the other party may then generate the shared secret gxy using its knowledge of y.
Owner:ALCATEL-LUCENT USA INC
Diesel engine with differential cylinder group operation
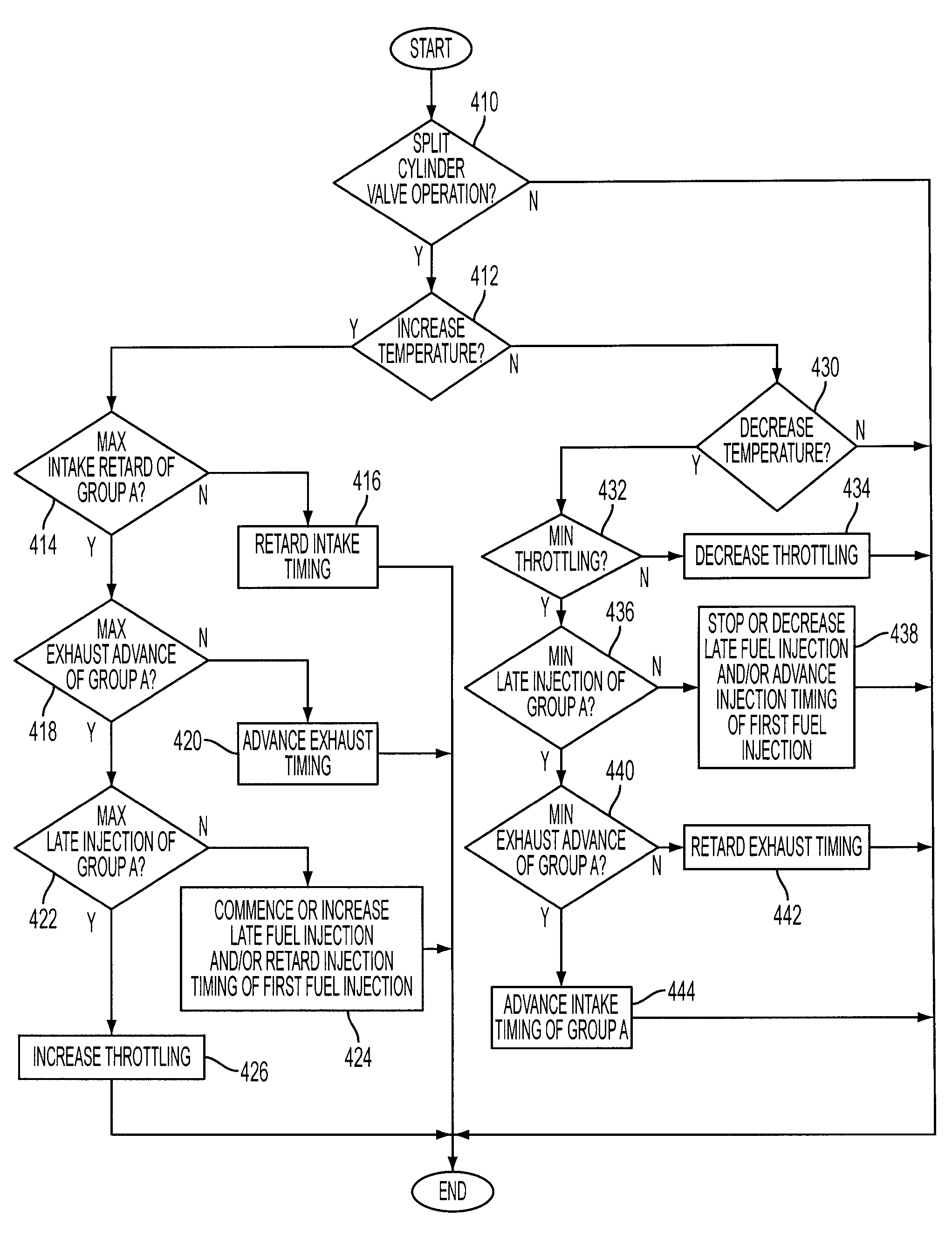
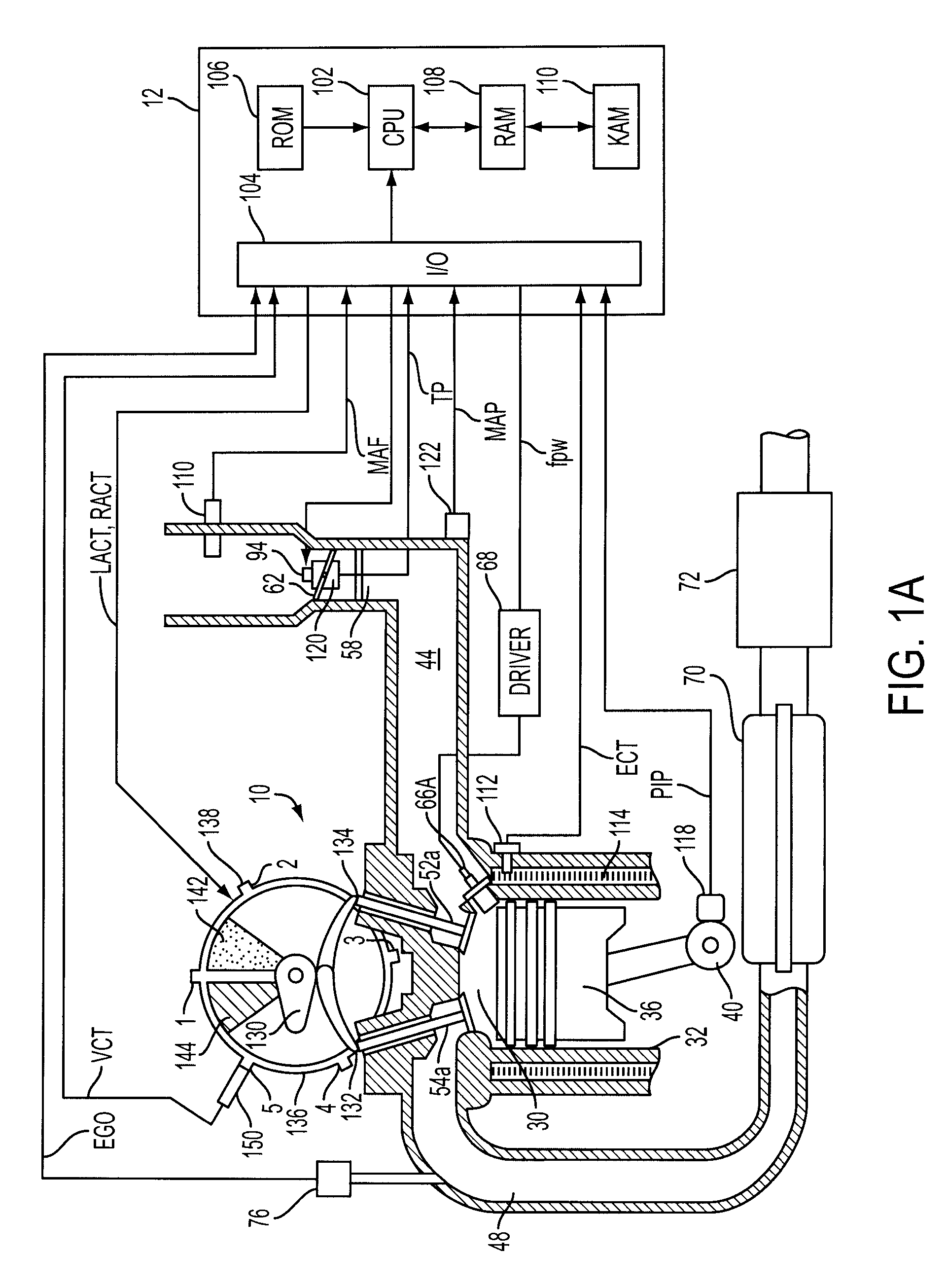
InactiveUS7246595B1Less torqueIncreasing throttlingValve arrangementsElectrical controlCombustionExhaust valve
A method for controlling operation of a diesel engine having a plurality of cylinders, the engine including a first group of cylinders and a second group of cylinders, the method comprising of operating the first group of cylinders with a first intake and exhaust valve timing, the first group of cylinders inducting air and performing diesel compression ignition combustion of injected fuel; and operating the second group of cylinders with a second intake and exhaust valve timing, the second group of cylinders inducting air and performing diesel compression ignition combustion of injected fuel, wherein said second intake valve timing is retarded compared to said first intake valve timing or said second exhaust valve timing is advanced compared to said first exhaust valve timing.
Owner:FORD GLOBAL TECH LLC
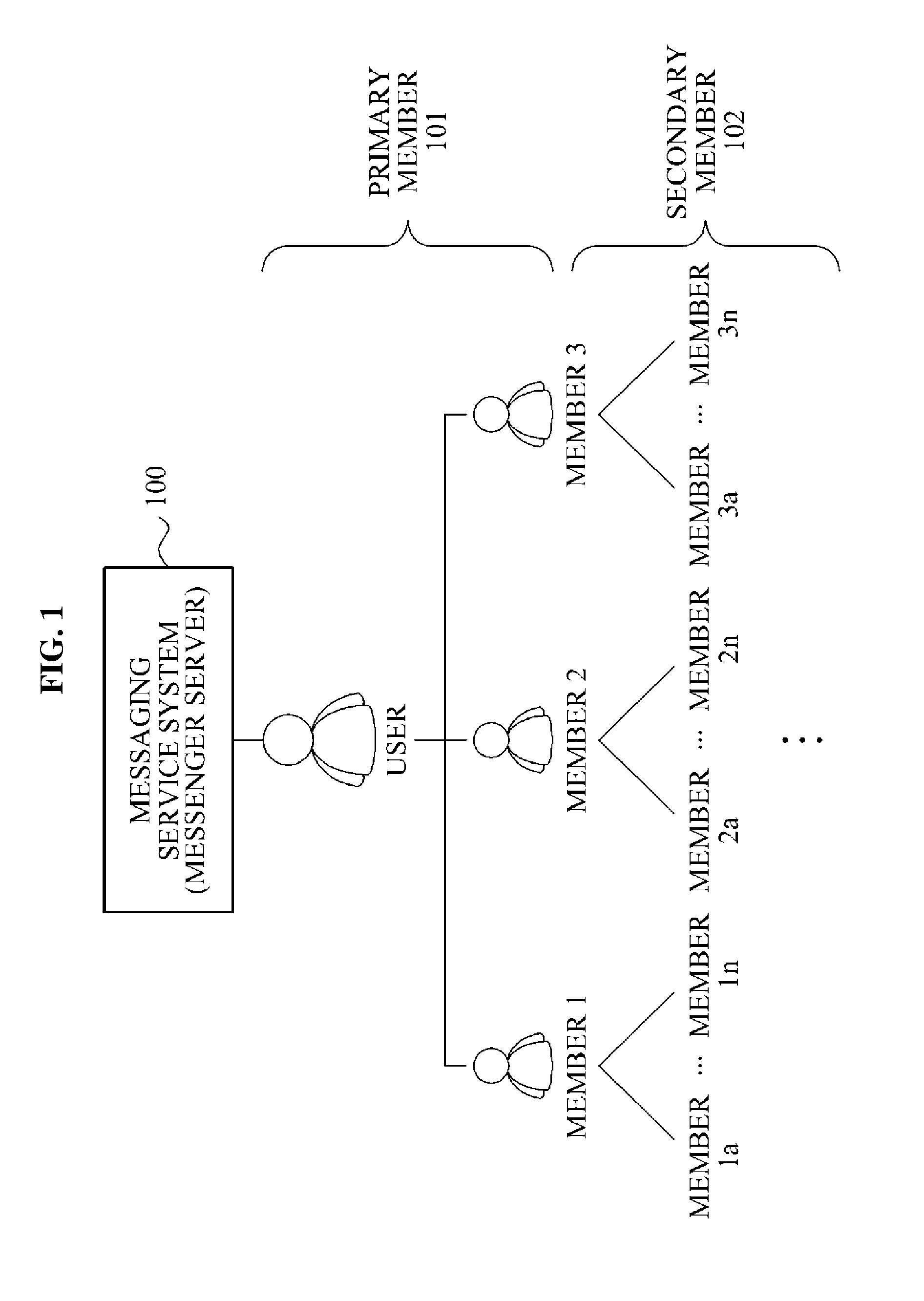
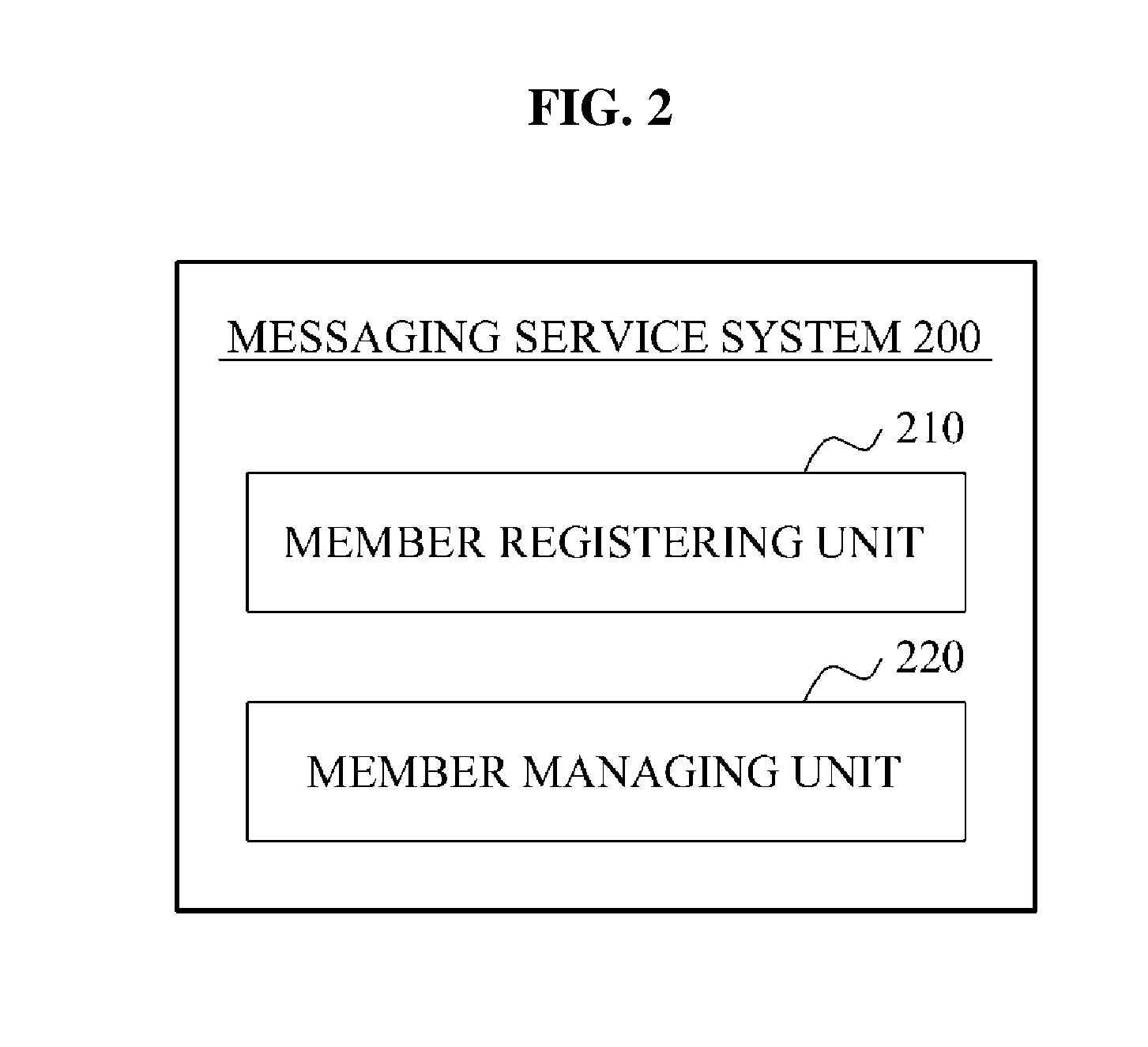
Messaging service system and method for expanding member addition operation
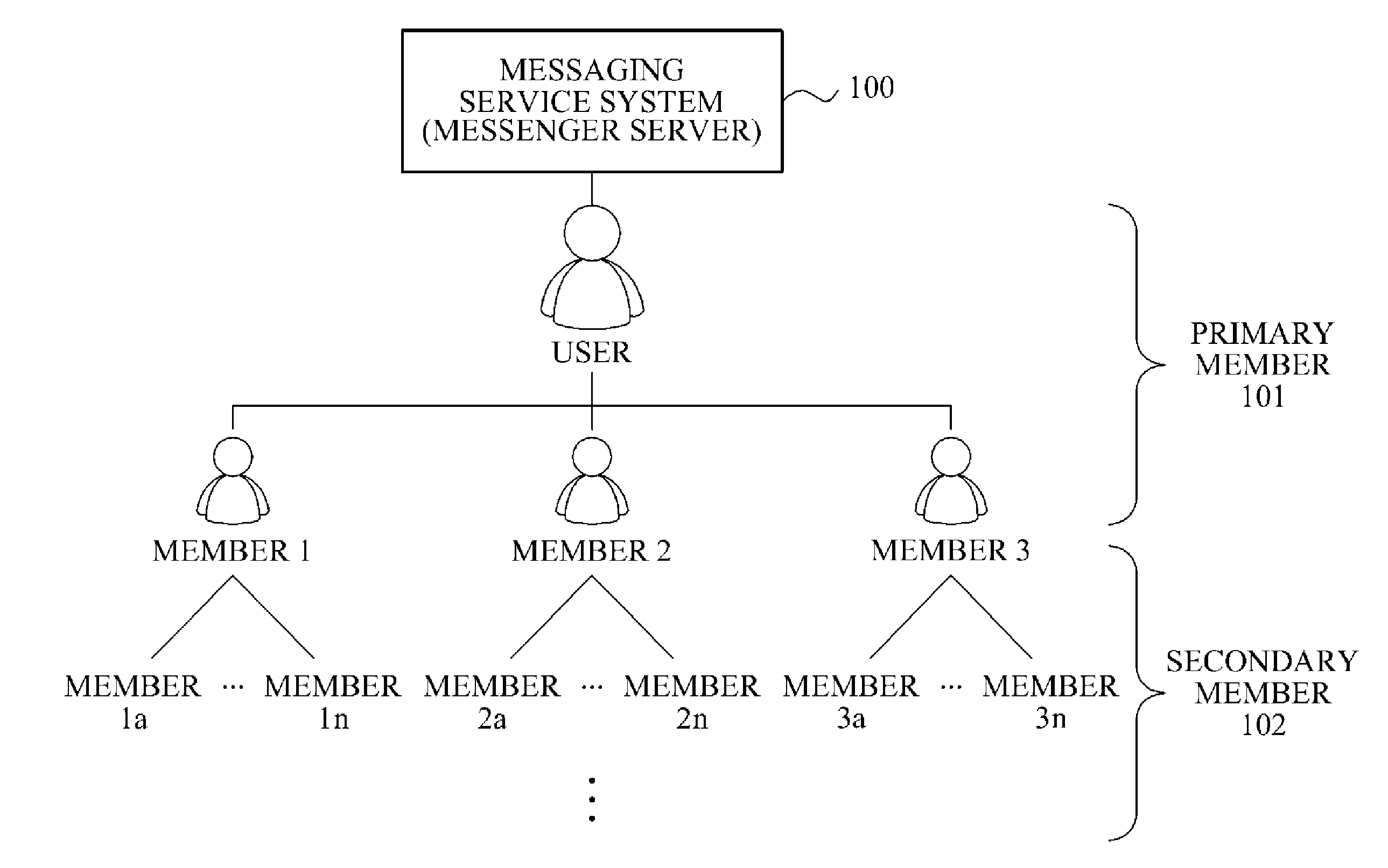
ActiveUS20120311052A1Data processing applicationsMultiple digital computer combinationsManagement unitGroup operation
Provided is a messaging service system and method for adding a contact through a grouping operation. The messaging service system includes a member registering unit configured to create a group, and to register a first member designated by a user as a first participant of the group; and a member managing unit configured to disclose the group to the first participant of the group, to assign, to the first participant, a permission to add a second participant to the group, in which, the member registering unit is configured to add a second member designated by the first participant of the group as the second participant of the group, and the member managing unit is configured to display a list of members registered by the member registering unit and a list of groups created by the member registering unit.
Owner:LINE CORPORATION
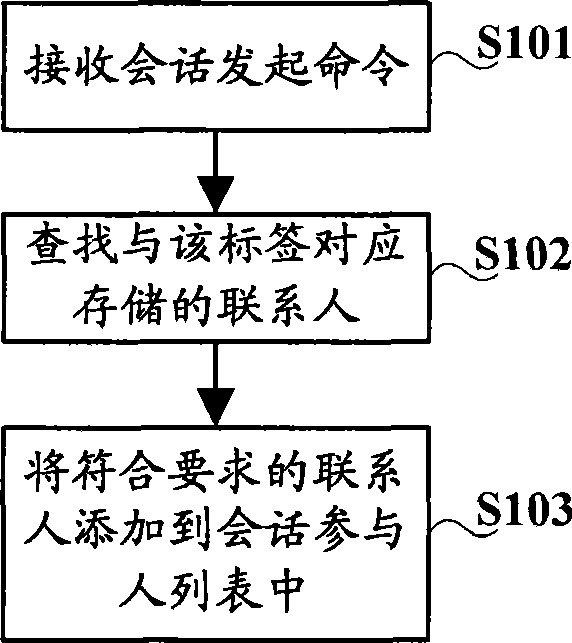
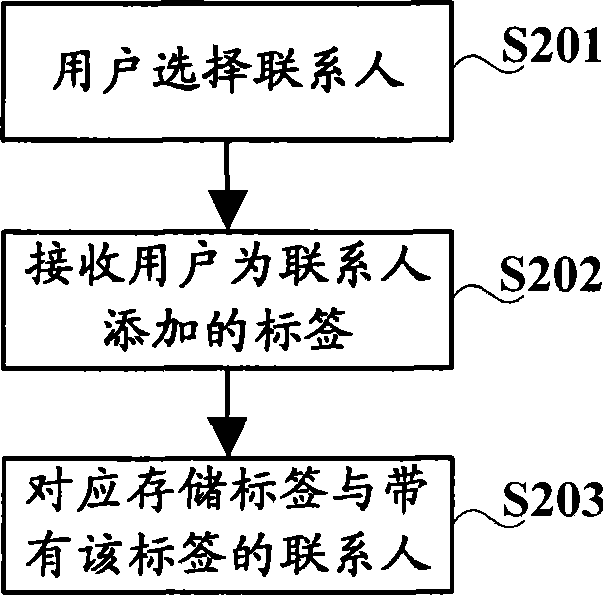
Method and apparatus for selecting conversation participant in instant communication
InactiveCN101431486AEasy to operateEasy to manageData switching networksGroup operationUser management
The invention discloses and method and device for selecting session participant in instant messaging, relating to communication technology. The method comprises: receiving session launching command dealing with label sent by user, the label being used for marking user characteristic; looking for corresponding linkman of label with which user deals; adding the linkman to session participant list. Because every linkman is provided with a label, linkman of same label are grouped according to label the session deals with, simplifies session grouping operation, facilitates user to administrate linkman information.
Owner:CHINA MOBILE GRP BEIJING
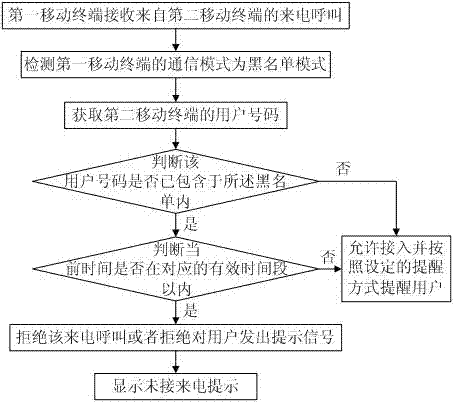
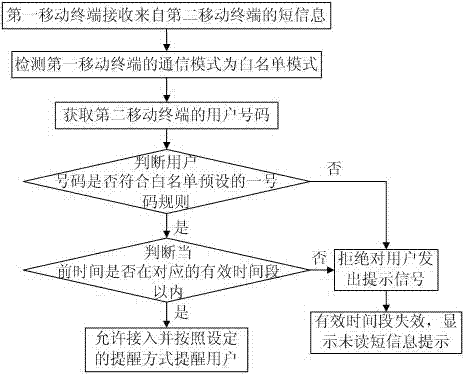
Do not disturb control method for mobile terminal
The invention relates to a do not disturb control method for a mobile terminal. Communication modes of the mobile terminal comprise a black list mode and a white list mode. The do not disturb control method comprises the following steps that a first mobile terminal receives the communication business from a second mobile terminal; the first mobile terminal accesses the communication business of the user number contained in the black list or the communication business of the user number meeting a preset number rule of the black list into the refusal operation or the omitting ignoring operation in the black list mode, and allows to access the communication business of the user number contained in the white list or the communication business of the user number meeting the preset number rule of the white list in the white list mode, and prompt the user. The do not disturb setting can be quickly completed for a plurality of persons or groups in particular time through the black list mode / white list mode, and contains the identification and distinguishing operations of stored numbers and strange numbers are contained, and so is not limited to the grouping operation of the stored numbers is realized, the black list / white list is set in a specific and intelligent way, and the experience effect of the user is improved.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
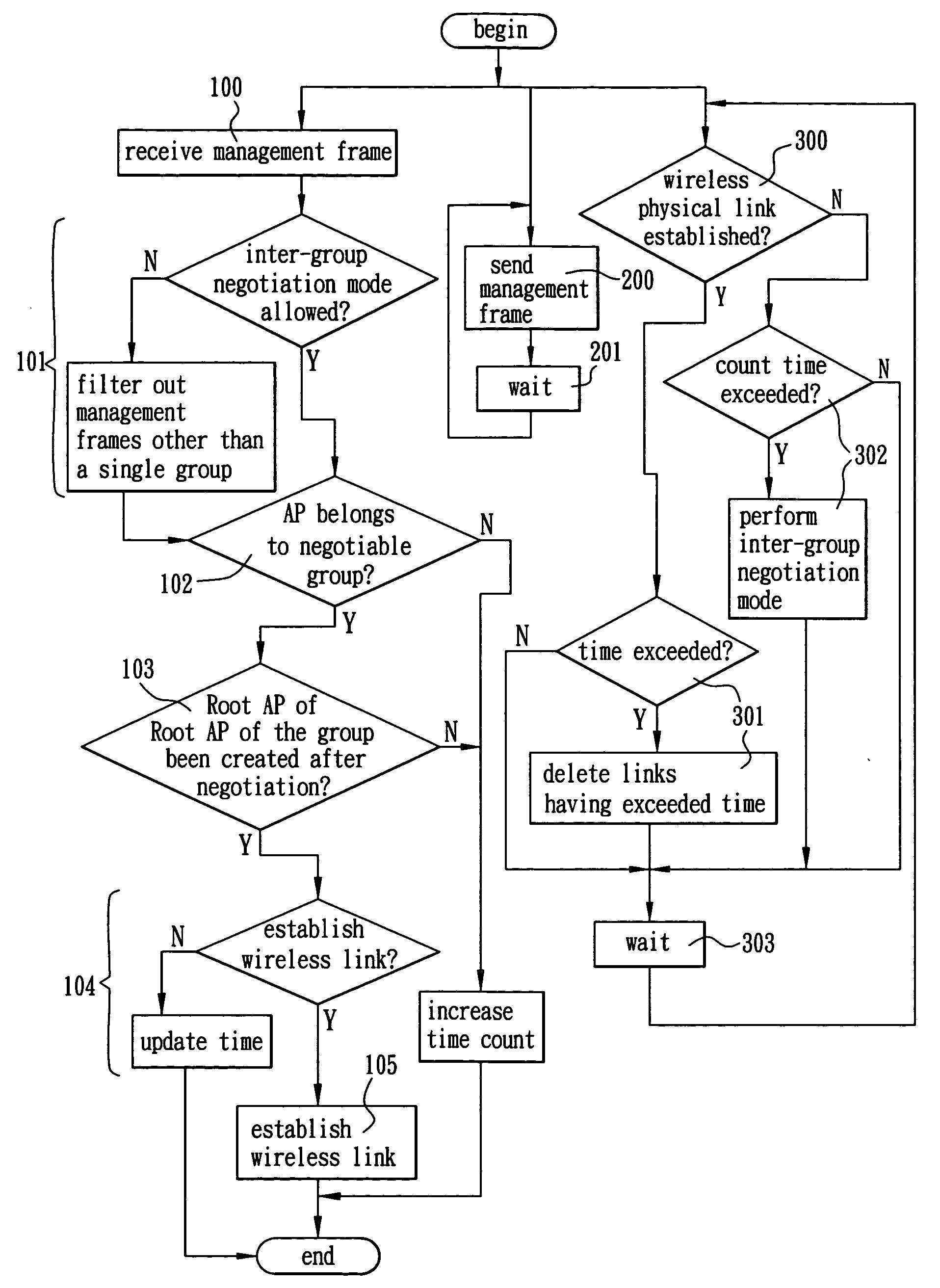
Wireless routing mechanism for same group and inter-group operations covering both wire network and wireless network
ActiveUS20070030823A1Eliminating detail settingImprove network performanceNetwork topologiesTime-division multiplexTelecommunicationsGroup operation
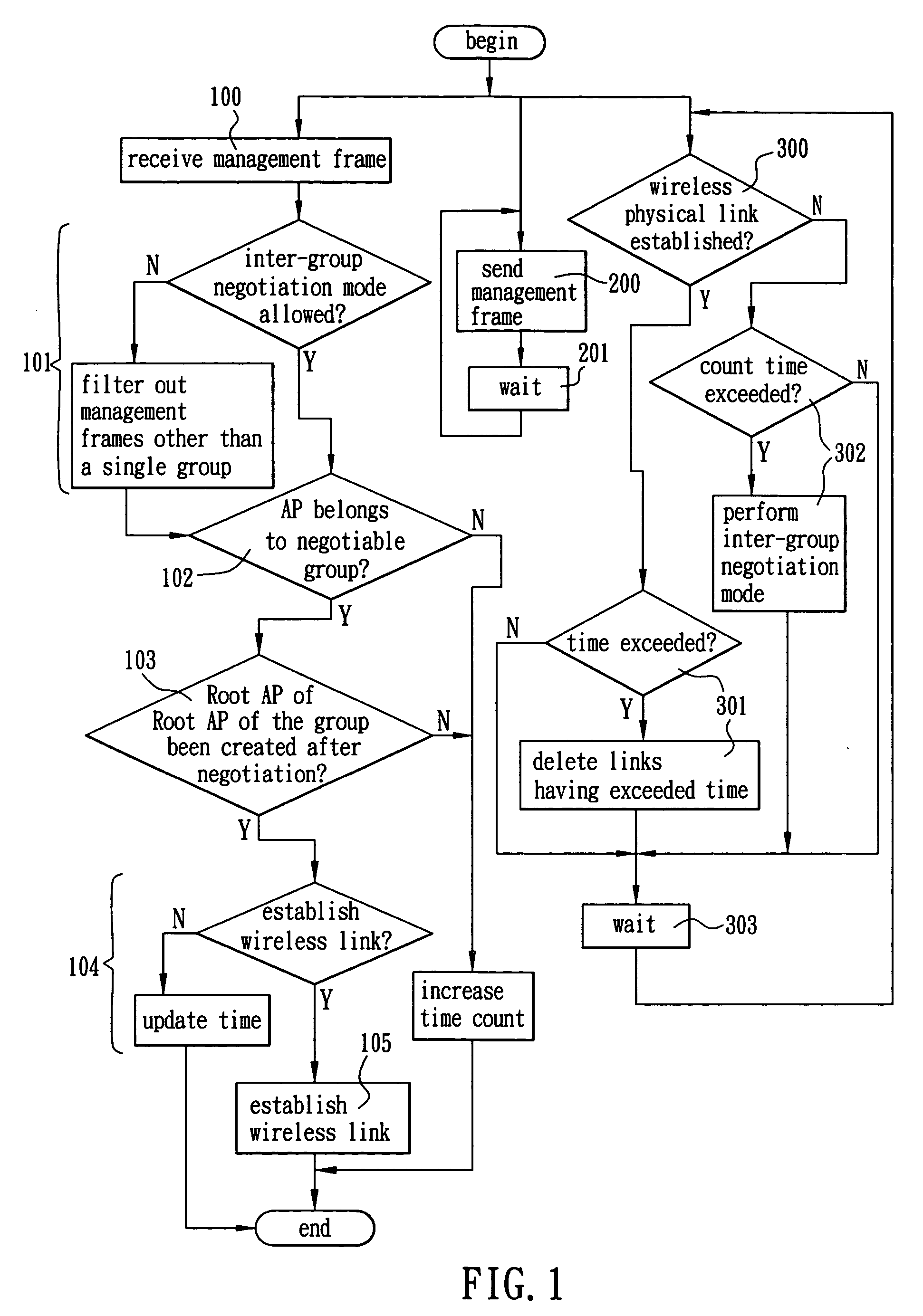
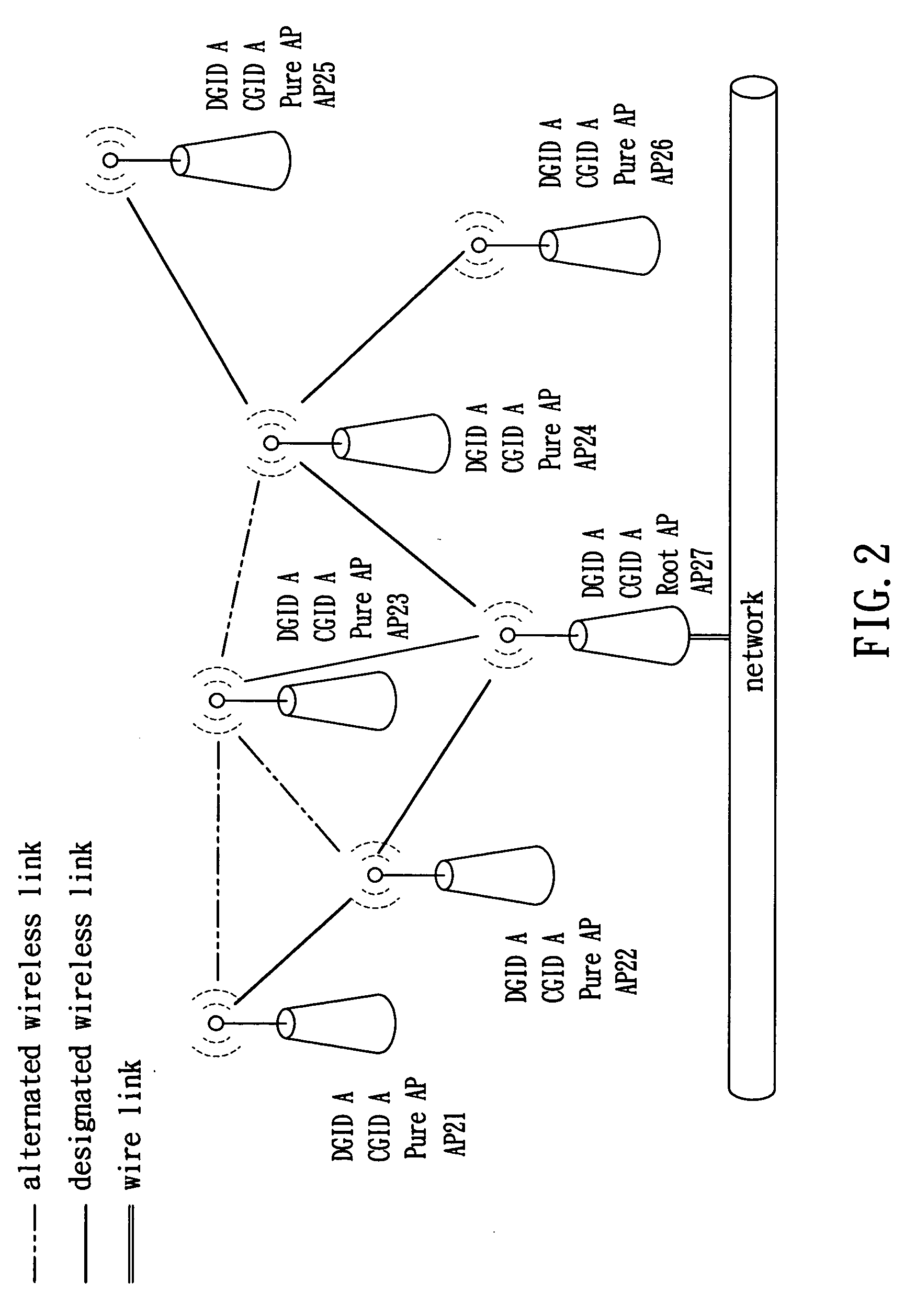
The present invention is to provide a wireless routing mechanism by applying a management frame defined in IEEE 802.11 standard to different access points (AP) in a wireless distribution system (WDS) and adding an information element (IE) to the management frame, enabling any AP to be capable of maintaining the integrity of IE based on its own setting and state, determining other APs' operations in WDS based on a received IE and determining whether a physical link (i.e., wireless link) between itself and any of other APs should be established to provide a channel for sending data frames therebetween and automatically establishing a stable, flexible and expansible wireless network topology in a wire network infrastructure based on information contained in a plurality of fields of the IE.
Owner:ALPHA NETWORKS INC
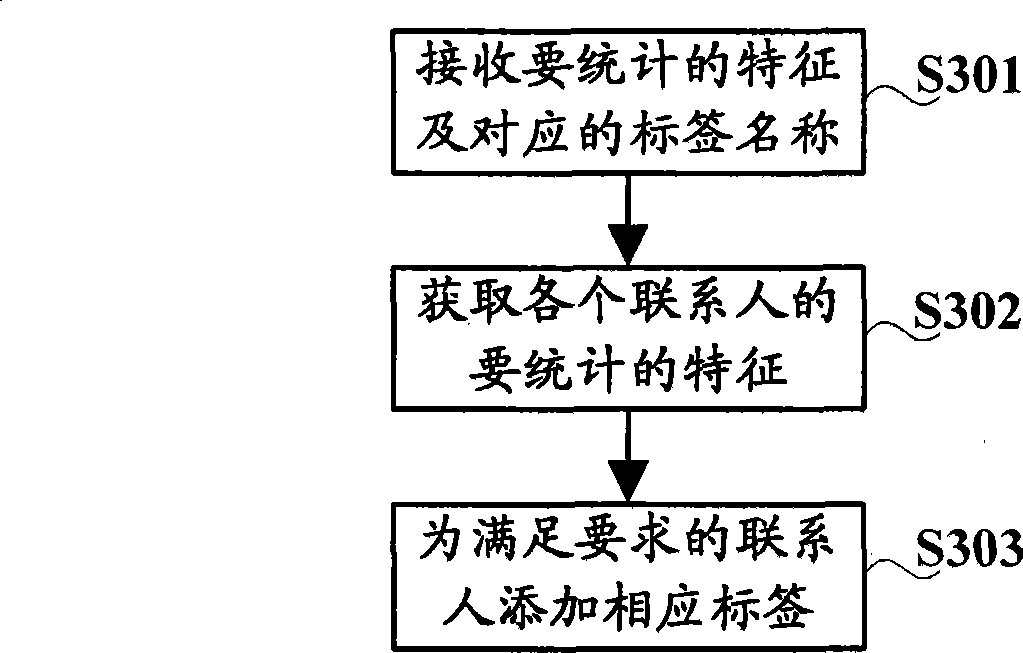
Contact person grouping method and terminal
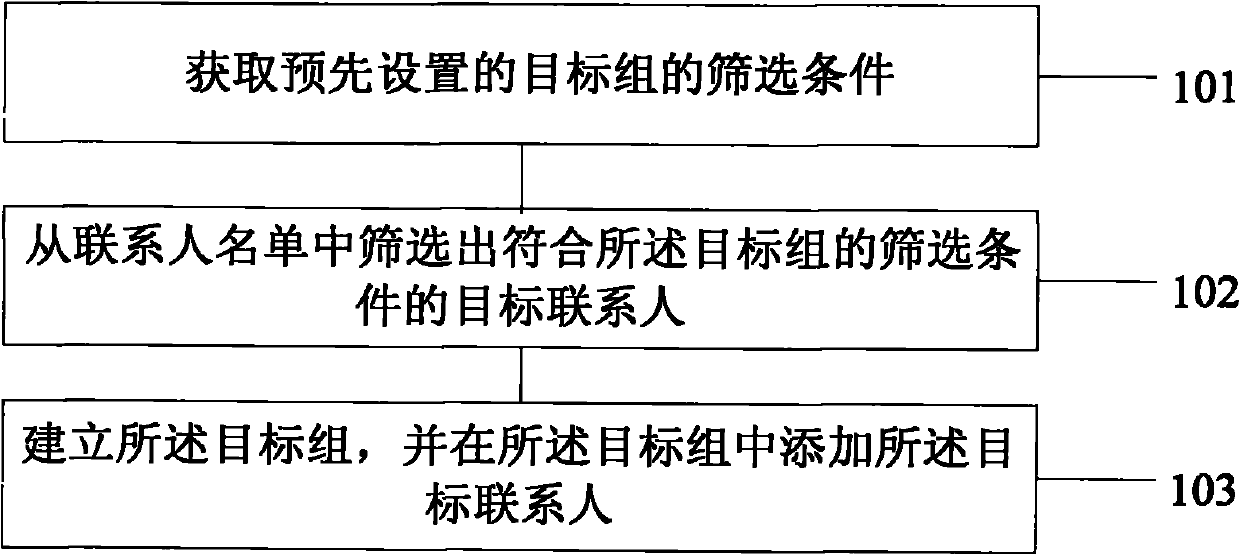
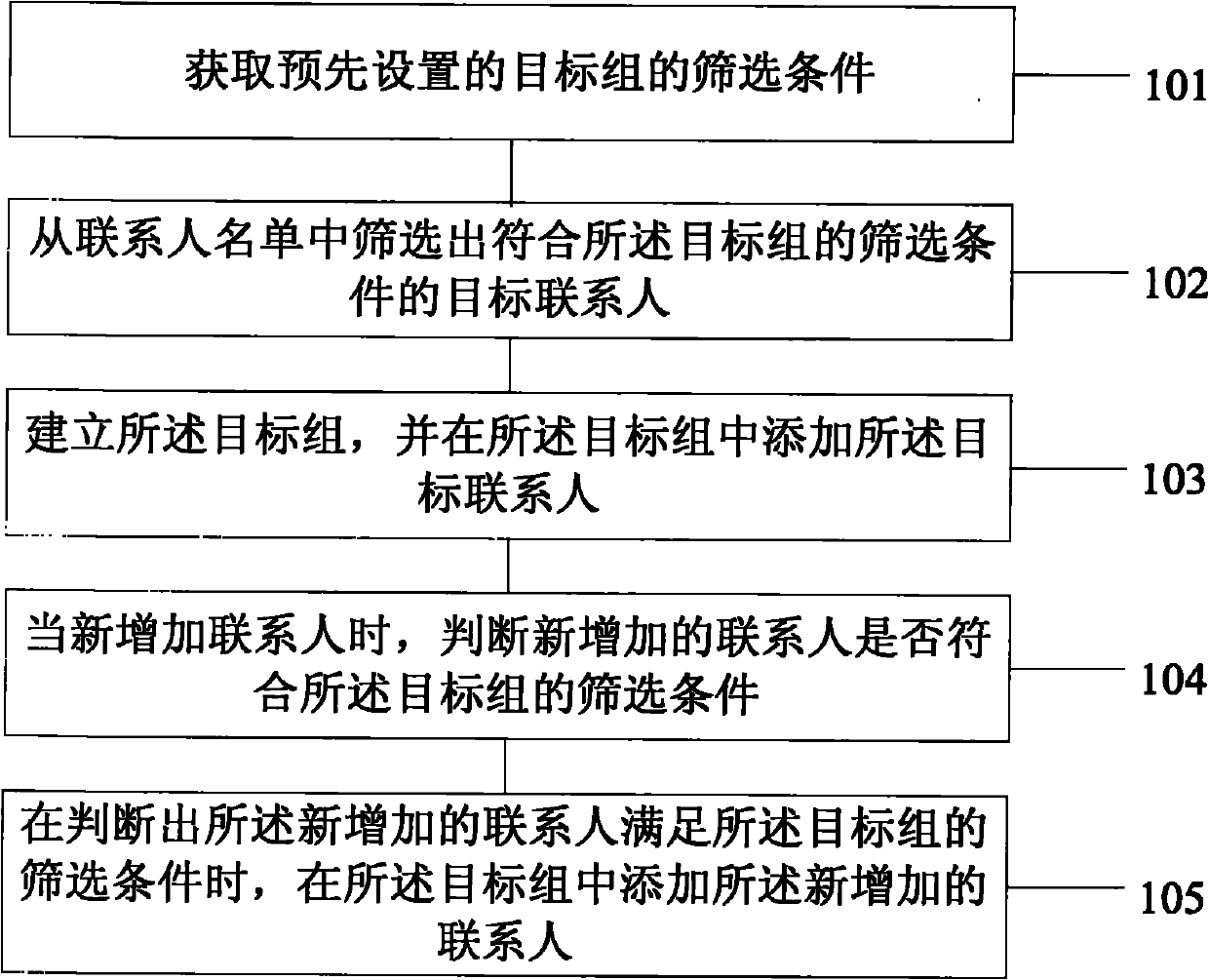
The embodiment of the invention discloses a contact person grouping method and a contact person grouping terminal, which relate to the technical field of electronic products and can quickly and conveniently realize contact person grouping. The contact person grouping method comprises the following steps of: acquiring preset screening conditions of a target group; screening target contact persons who meet the screening conditions of the target group from a contact list; and establishing the target group and adding the target contact persons into the target group. In the embodiment of the invention, when a user needs to group the contact persons, the target contact person can be automatically screened according to the preset screening conditions of the target group, the target group is established and the contact persons are added into the target group, so that a grouping step is saved, and grouping operation is simple and fast.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
Application characteristic-based isomeric group operation self-adapting dispatching method and system
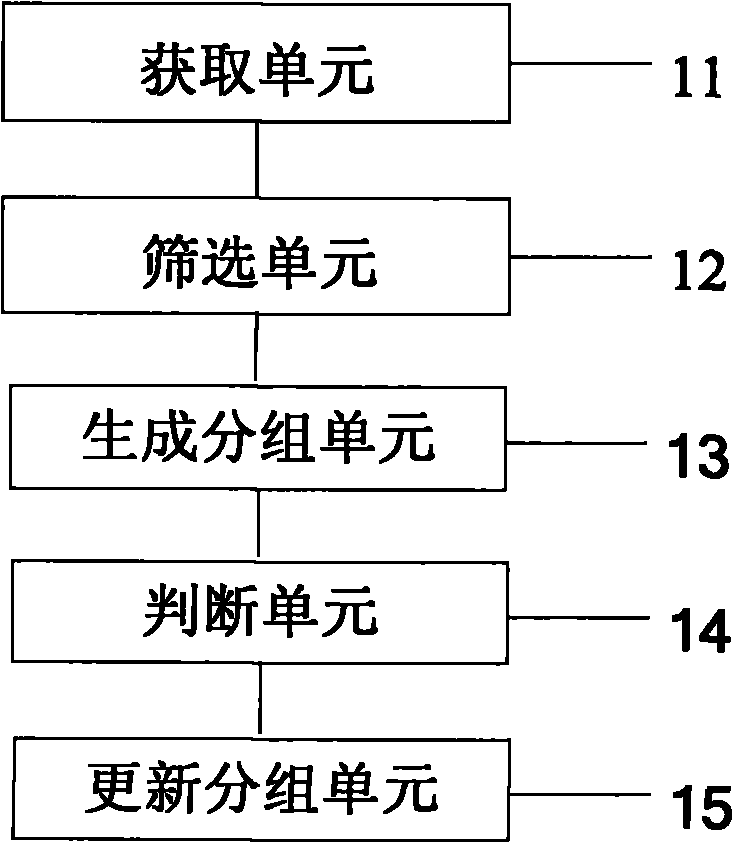
ActiveCN101739292AImprove efficiencyImprove accuracyResource allocationData profilingGroup operation
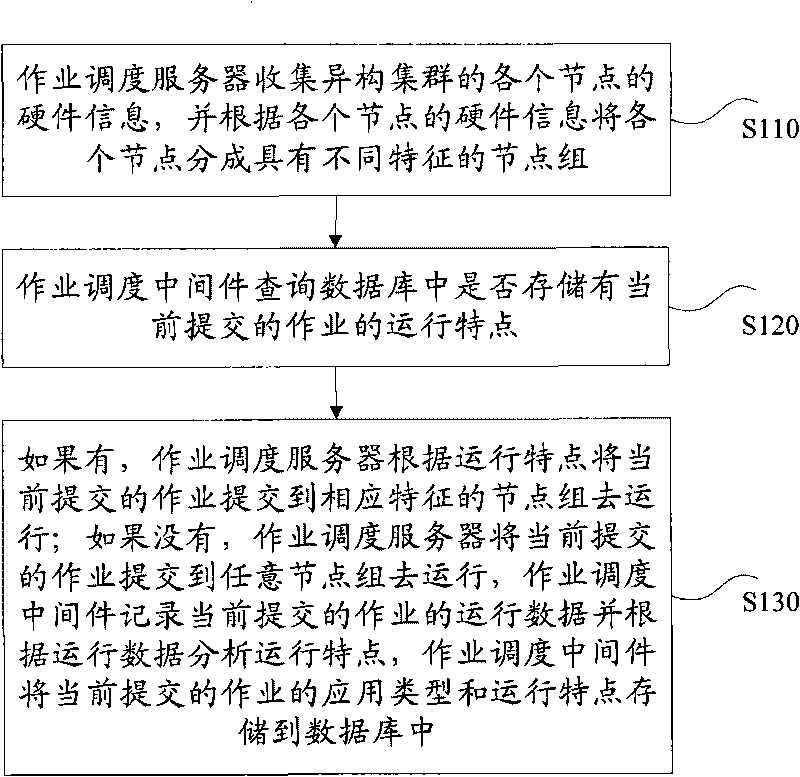
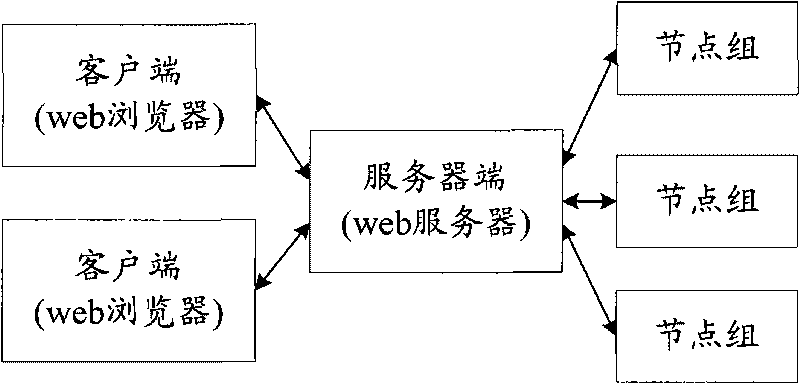
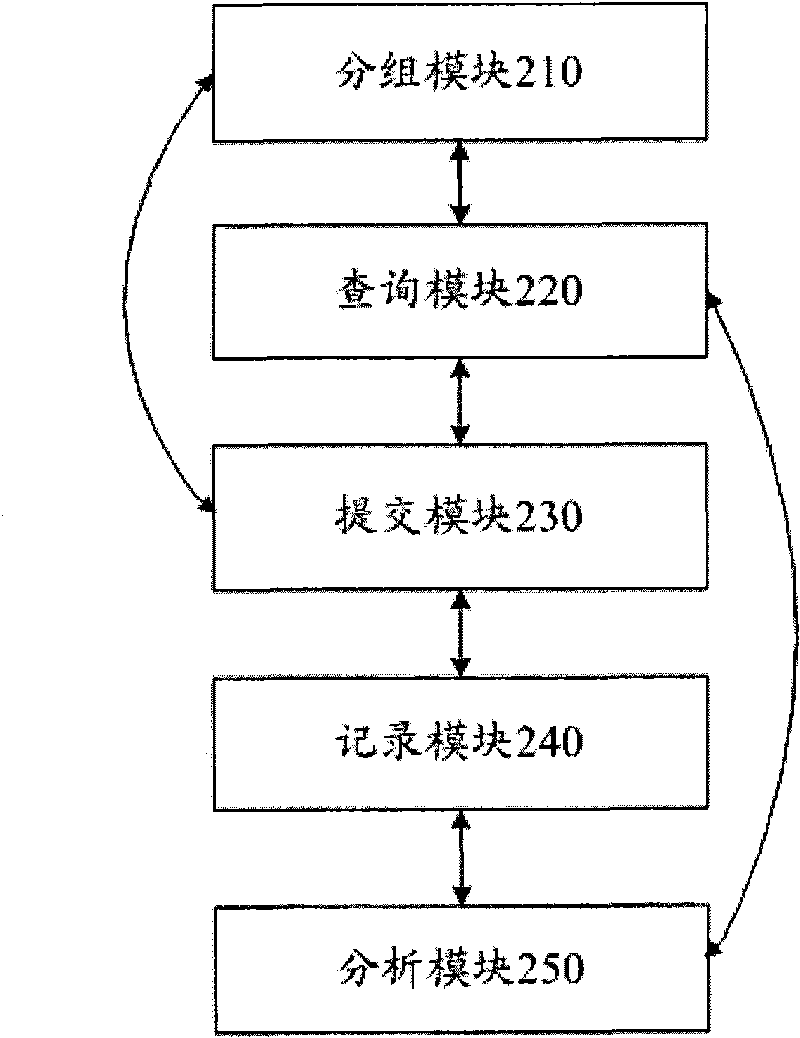
The invention provides an application characteristic-based isomeric group operation self-adapting dispatching method and an application characteristic-based isomeric group operation self-adapting dispatching system, wherein the dispatching method comprises the following steps that: an operation dispatching server collects hardware information of all nodes of the isomeric group and divides the nodes into node groups with different characteristics according to the hardware information of each node; an operation dispatching middleware inquires whether the operating characteristics of the operation currently submitted is stored in the data base; if so, the operation dispatching server submits the operation currently submitted to the node group with corresponding characteristics for operation according to the operating characteristics; and otherwise, the operation dispatching server submits the operation currently submitted to any node group for operation, and the operation dispatching middleware records the operating data of the operation currently submitted, analyzes the operating characteristics according to the operating data and stores the application type and the operating characteristics of the operation currently submitted in the data base. The method and the system of the invention can improve the efficiency of the high-performance software and also improve the use efficiency of the isomeric group.
Owner:DAWNING INFORMATION IND BEIJING +1
Method for efficient computation of odd characteristic extension fields
InactiveUS7069287B2Acceptable computational performanceLow costDigital computer detailsSecret communicationMicrocontrollerTheoretical computer science
A method for implementing an elliptic curve or discrete logarithm cryptosystem on inexpensive microprocessors is disclosed which provides for advantageous finite field computational performance on microprocessors having limited computational capabilities. The method can be employed with a variety of commercial and industrial imbedded microprocessor applications such as consumer smart cards, smart cards, wireless devices, personal digital assistants, and microprocessor controlled equipment. In one embodiment, a Galois Field (GF) implementation based on the finite field GF((28−17)17) is disclosed for an Intel 8051 microcontroller, a popular commercial smart card microprocessor. The method is particularly suited for low end 8-bit and 16-bit processors either with or without a coprocessor. The method provides for fast and efficient finite field multiplication on any microprocessor or coprocessor device having intrinsic computational characteristics such that a modular reduction has a greater computational cost than double precision, long number additions or accumulations. The disclosed method offers unique computational efficiencies in requiring only infrequent subfield modular reduction and in employing an adaptation of Itoh and Tsujii's inversion algorithm for the group operation. In one embodiment, a core operation for a signature generation, an elliptic curve scalar multiplication with a fixed point, is performed in a group of order approximately 2134 in less than 2 seconds. In contrast to conventional methods, the method does not utilize or require curves defined over a subfield such as Koblitz curves.
Owner:WORCESTER POLYTECHNIC INSTITUTE
Group user level association method and system
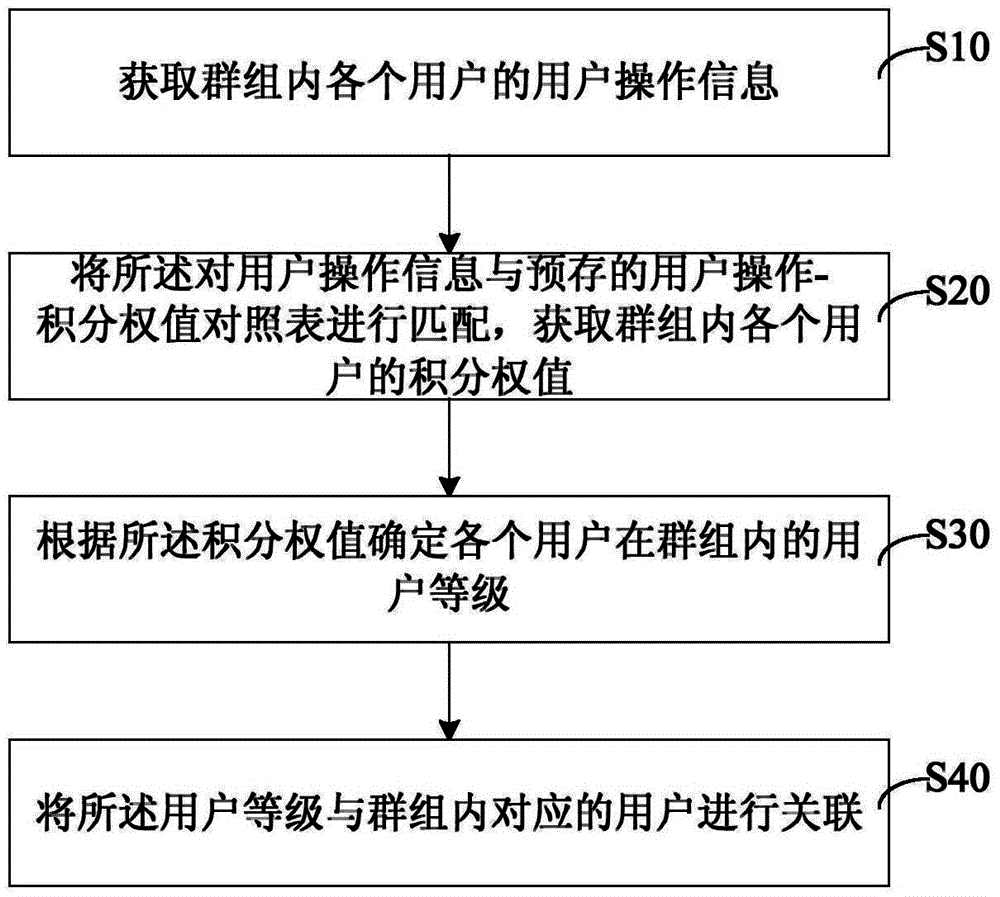
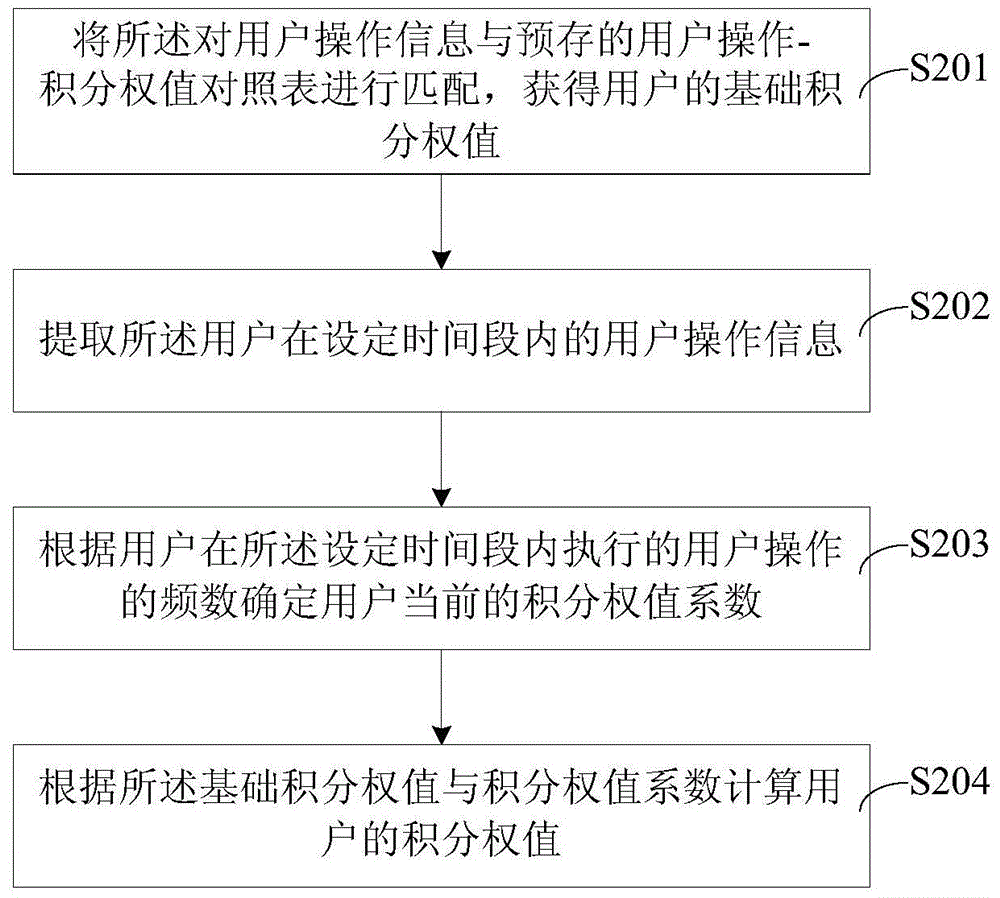
ActiveCN105302809AImprove experienceIncrease motivationData processing applicationsRelational databasesManagement efficiencyGroup operation
The present invention provides a group user level association method and system, comprising the steps of: acquiring user operation information of each user in a group; matching the user operation information with a user operation-integral weight value comparison table that is pre-stored, and acquiring an integral weight value of each user in the group; determining a user level of each user in the group according to the integral weight value; and associating the user level with a corresponding user in the group. In addition, the present invention further provides a group user level association system. Compared with a user level based on online time and an active degree, according to the technical solution of the present invention, a level difference between users in the group can be reflected truly and objectively, so as to improve application and management efficiency of a group advocate and an administrator for the group, thereby improving activeness of using group operation by the user and enhancing user experience.
Owner:TENCENT TECH (SHENZHEN) CO LTD
System for control, management, and transmission for soft handoff in an ofdma-based communication system
InactiveUS20080076429A1Improve performance-particularlyReliable and minimal signaling overheadRadio/inductive link selection arrangementsWireless communicationAccess networkCommunications system
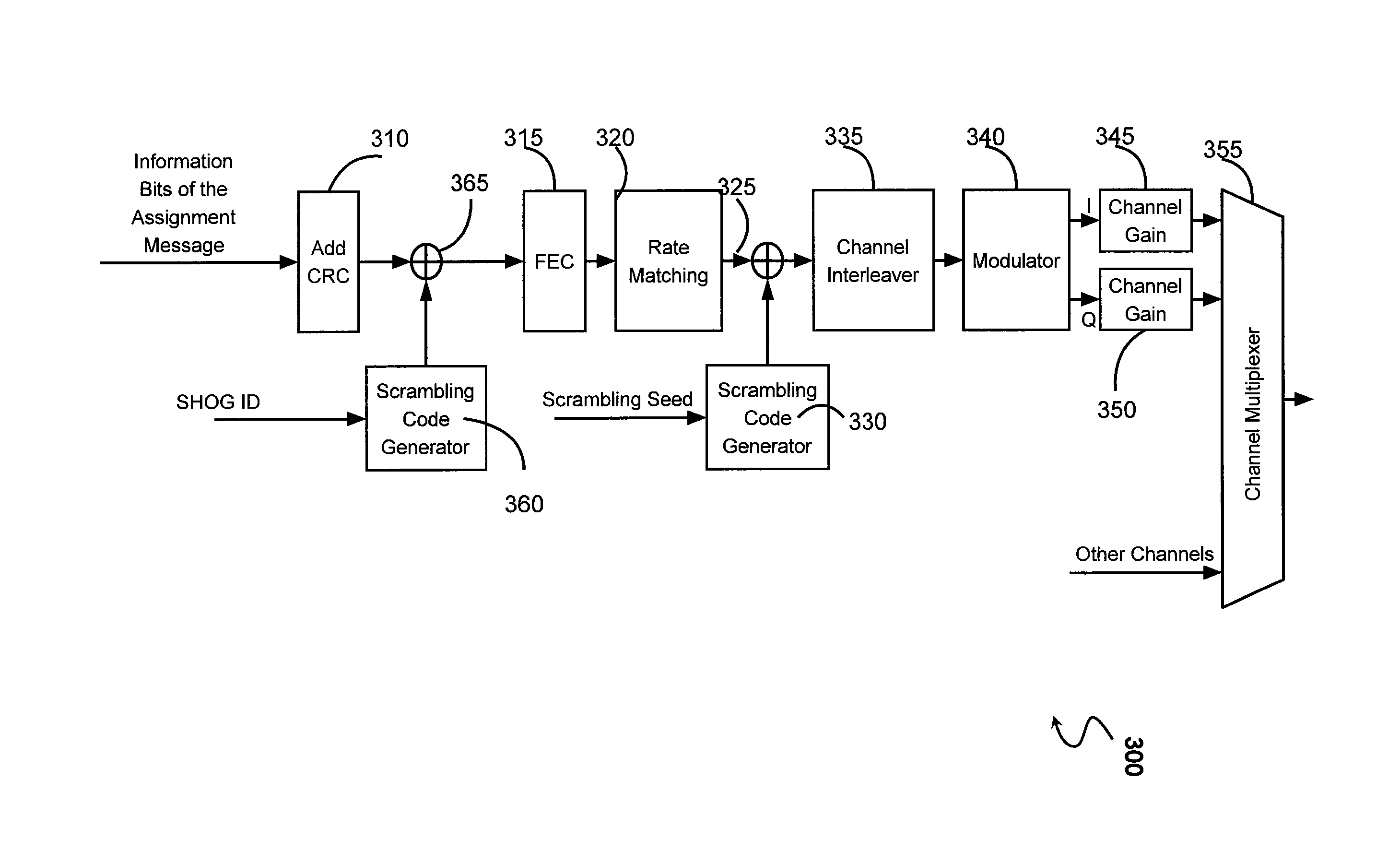
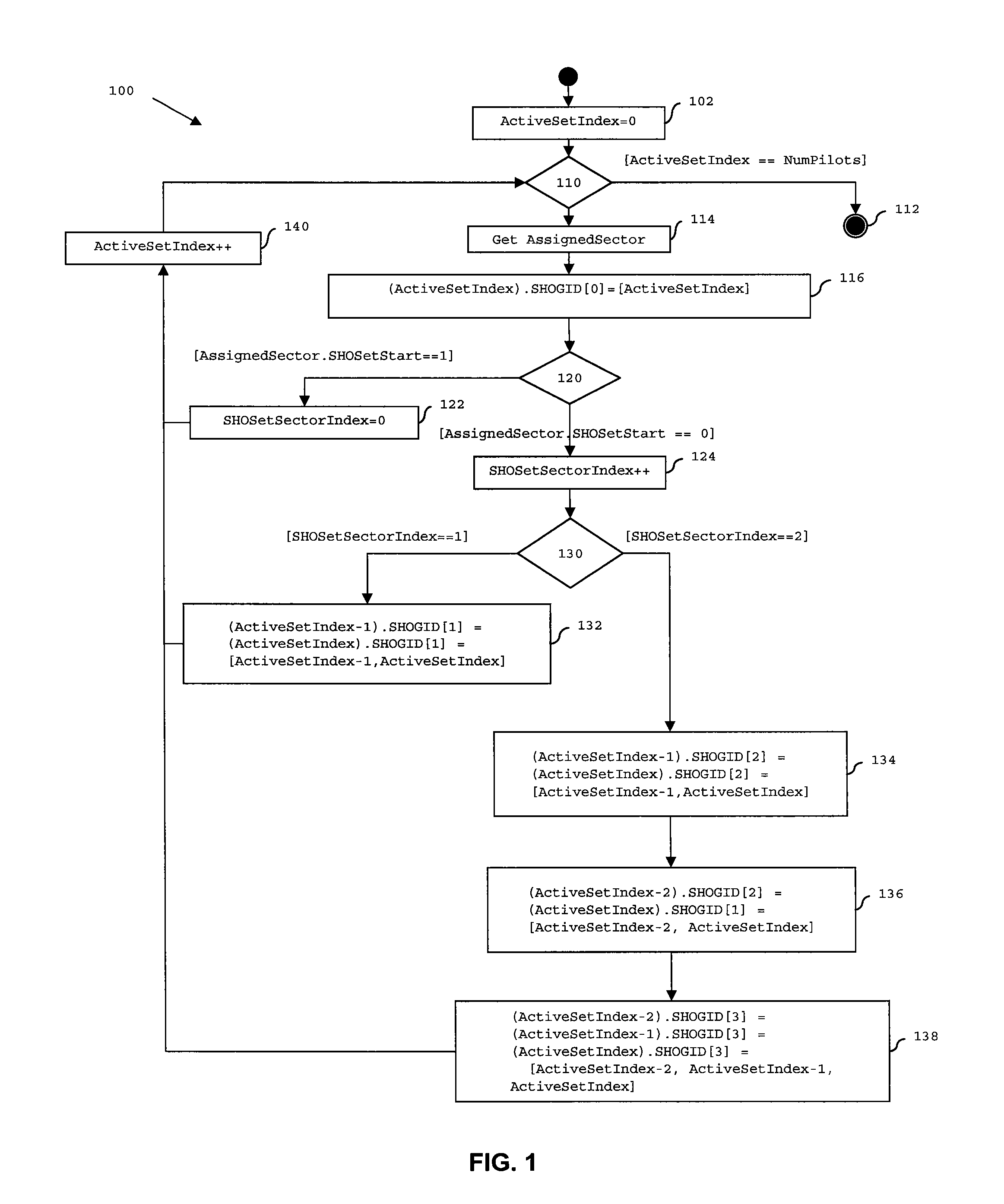
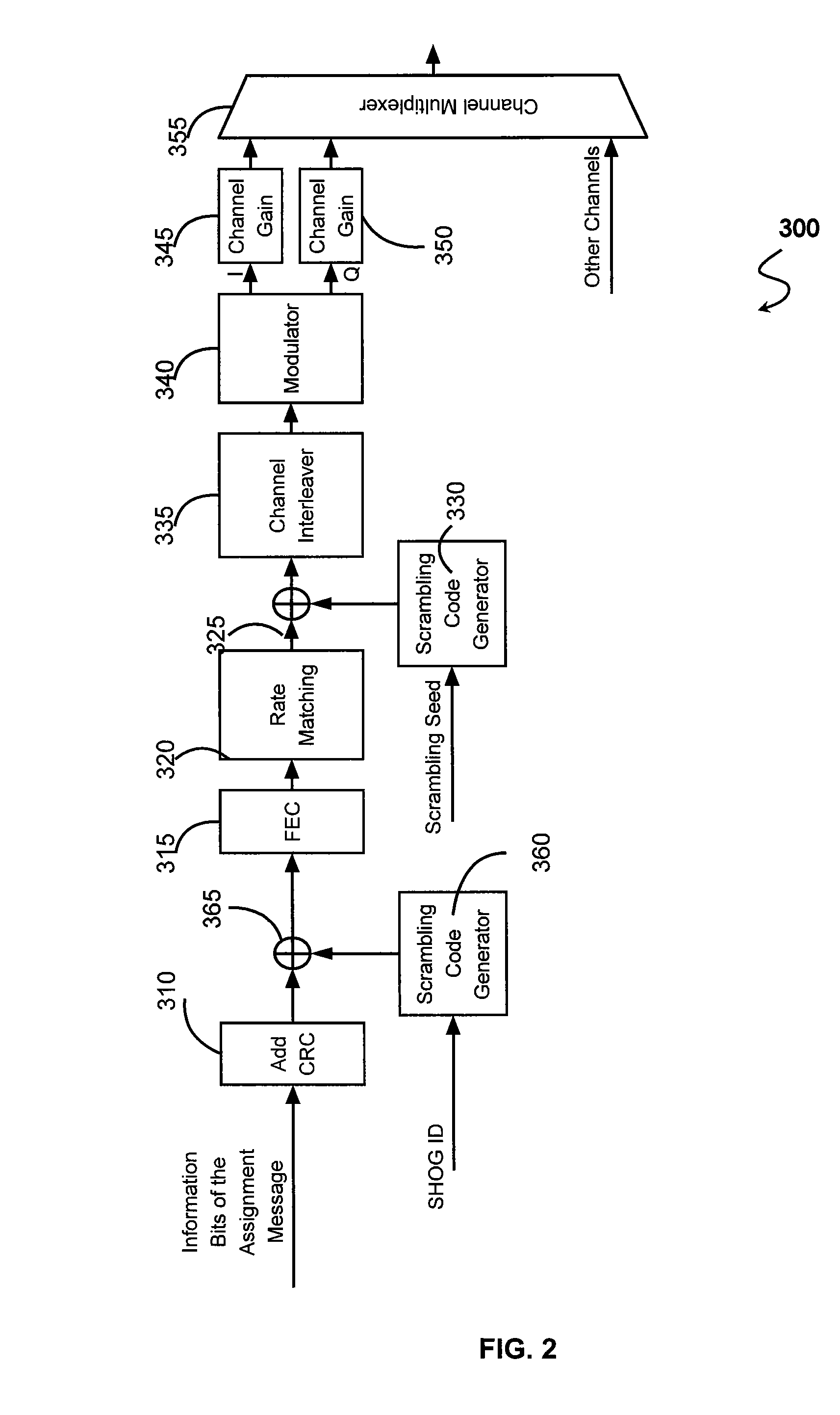
A versatile system for controlling and managing resources for Soft Handoff Group operations is disclosed. The system determines which of a plurality of sectors in an access network is a serving sector for an access terminal. An active set of the plurality of sectors is assigned to the access terminal, comprising the serving sector. A soft handoff set for the access terminal is identified from the active set. A soft handoff group for the access terminal is identified from the soft handoff set. The access terminal's transmissions within the access network are managed according to the identified soft handoff group.
Owner:FUTUREWEI TECH INC
System and method for monitoring operation state of disc cutter group of cutterhead of tunneling machine
ActiveCN103226151AGroup performance is goodGuaranteed uptimeMachine part testingAnalysing solids using sonic/ultrasonic/infrasonic wavesMonitoring systemControl room
The invention discloses a system and a method for monitoring the operation state of a disc cutter group of a cutterhead of a tunneling machine. The method comprises the following steps: detecting the autorotation speed of each disc cutter by using a sensor; and transmitting a rotating speed signal to a computer in a control room of the tunneling machine by using a wireless data transmission device so as to judge the operation state of the disc cutters according to the rotating speed signal and the preset reference value relationship. The system and the method have the technical effect that the individual reference value of each individual of the disc cutter group is subjected to data processing and visual display, so that the operation state and the wear state of the disc cutter group of the tunneling machine can be displayed in real time. The monitoring system can provide selection help for an operator of the tunneling machine so as to determine whether to replace and maintain cutters or not, or change a tunneling control parameter to reach higher cutter group operation performance. By the method, manpower consumption can be reduced obviously, construction risk can be reduced, and work efficiency can be improved.
Owner:湖南奥通智能研究院有限公司
Methods and apparatus for supporting and implementing computer based animation
InactiveUS20050270294A1Preserve integrityEfficiently conveyedAnimation3D-image renderingMorphingGraphics
The present invention provides a method for hierarchically decomposing a visual or audio object within an animation into plurality of objects which can be individually edited to achieve particular animation effects. For example, a graphical object may be decomposed into a plurality of graphical sub-objects, each of which inherits an anchor point from the original object, or is given an original anchor point distinct from the original object. Each sub-object also includes a relative position for the sub-object relative to the anchor point. The path of the anchor point is combined with relative positions of the sub-objects to produce an animation for the object as a whole. This decomposition technique can greatly increase computational efficiency of an animation. It also provides for inheritance of attributes between objects and descendent sub-objects. The objects may support functions, or behaviors, such as morphing or motion blurring. The present invention additionally provides a flexible grouping operation to facilitate modifications to a group of objects. When a first type of modification is made to an attribute of an object in a group, this change is applied to corresponding attributes of other objects in the group. When a second type of modification is made to an attribute of an object in a group, the change only applies to the selected object or objects, and not to other objects in the group. The present invention allows objects to be manipulated on servers which are connected to a display on the internet.
Owner:RATEZE REMOTE MGMT LLC
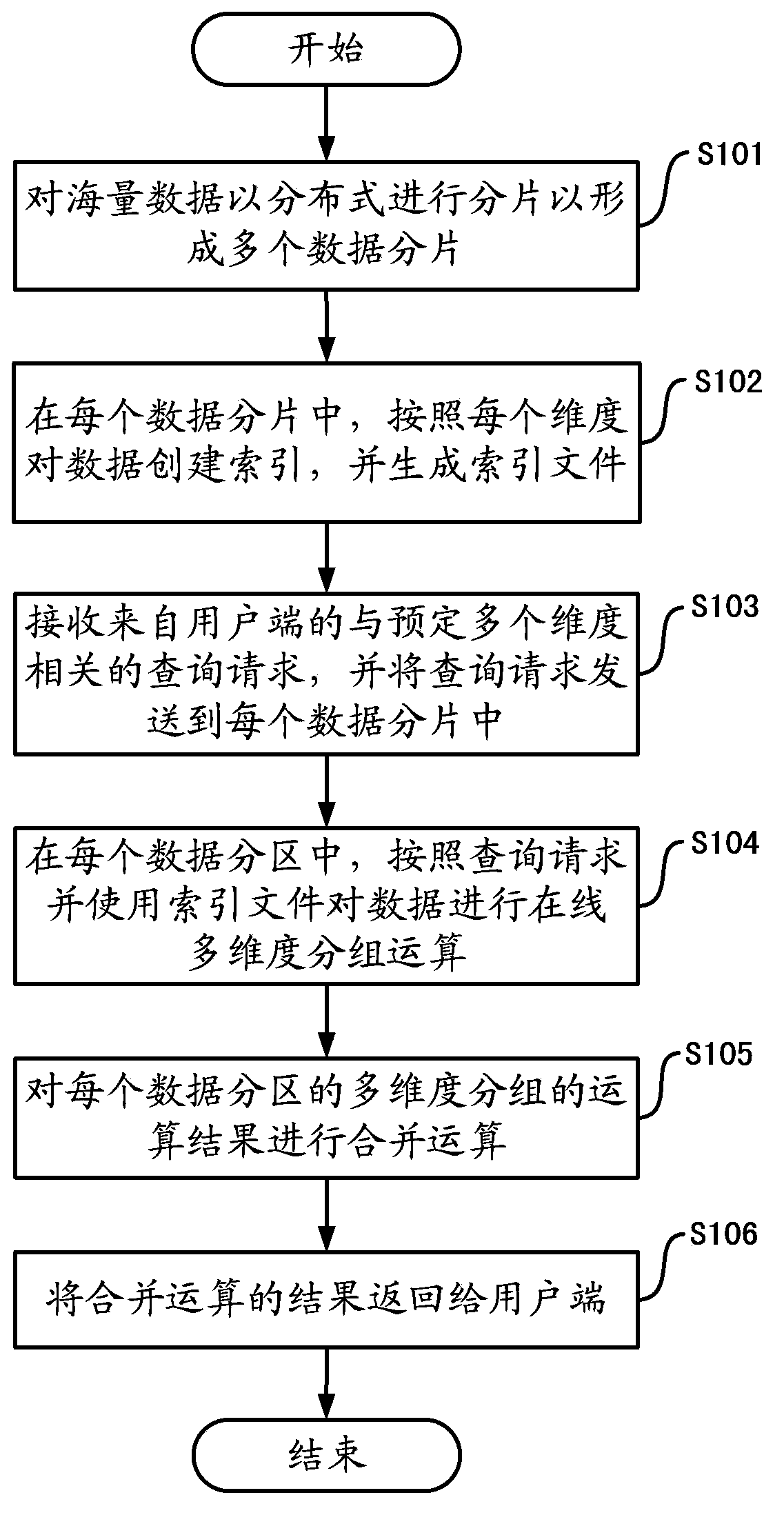
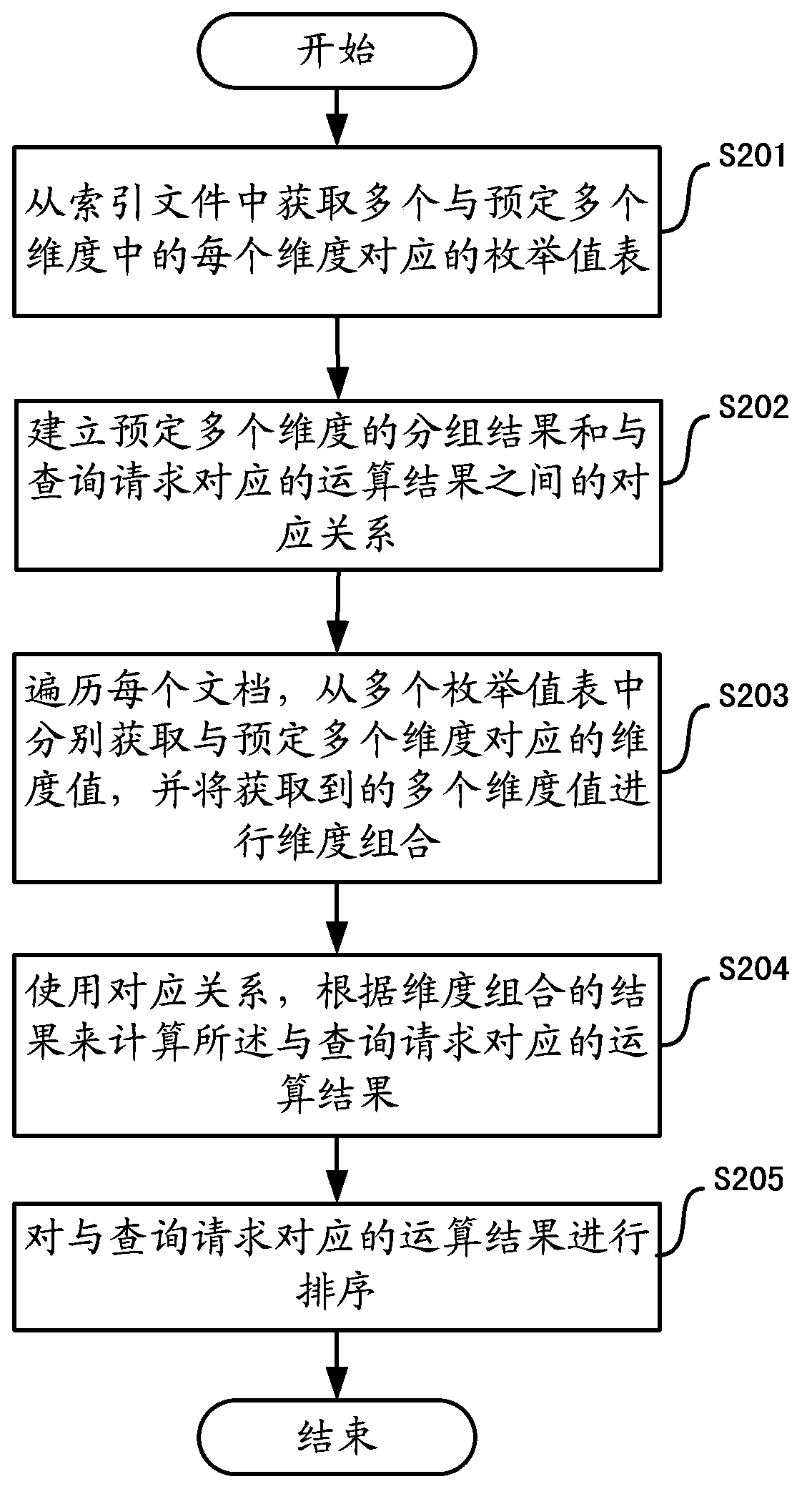
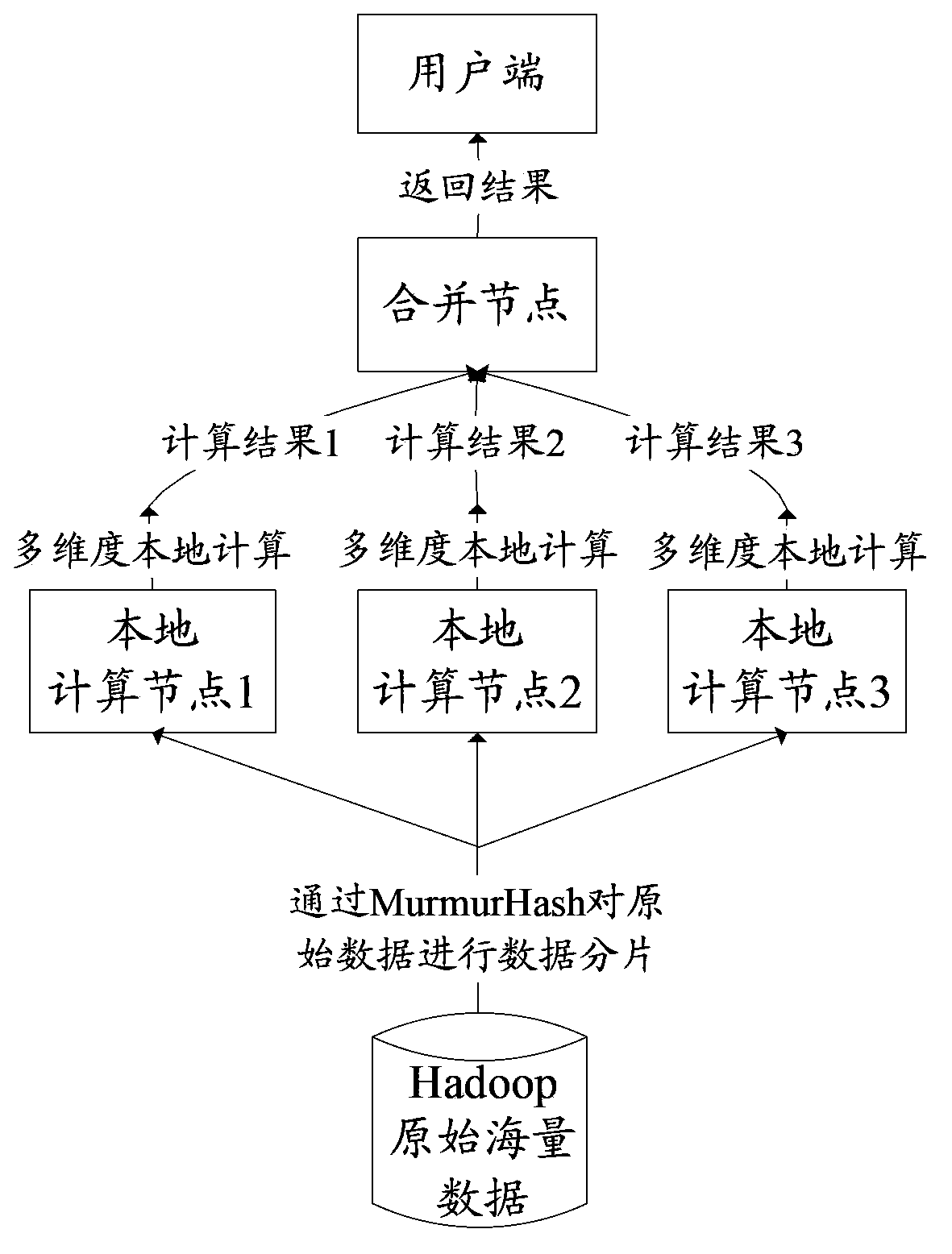
Multi-dimensional grouping operation method and system
InactiveCN104063376ARealize the operation of online multi-dimensional groupingSpecial data processing applicationsGroup operationMulti dimensional
The invention provides a multi-dimensional grouping operation method and system. The multi-dimensional grouping operation method comprises steps as follows: fragmenting mass data in a distributed manner to form a plurality of data fragments; creating indexes for data according to each dimensionality in each data fragment, and generating a plurality of created indexes into an index file; performing online multi-dimensional grouping operation on the data by using the index file; and performing combination operation on an operation result of each data fragment. With the adoption of the method and system, online multi-dimensional grouping operation on the mass data can be realized, and a multi-dimensional grouping operation result of ten hundred million grade mass data can be returned in milliseconds.
Owner:ALIBABA GRP HLDG LTD
Group gang control system and method based on group MAC (Media Access Control) address for plurality of pieces of Wi-Fi Internet of things equipment
ActiveCN104994530AReduce in quantityReduce power consumptionNetwork topologiesBroadcast service distributionWi-FiControl system
The invention relates to a group gang control system and method based on a group MAC (Media Access Control) address for a plurality of pieces of Wi-Fi Internet of things equipment. The plurality of pieces of Wi-Fi Internet of things equipment are grouped to form a plurality of equipment groups; each equipment group has a local unique group MAC address in order to uniquely identify the equipment group; a plurality of pieces of Wi-Fi Internet of things master control equipment are provided; the group MAC address of any equipment group which is matched with each piece of master control equipment is taken as a target address for transmitting information; and synchronous control or synchronous data transmission is performed on all controlled equipment in the equipment groups. Group operation is performed on a large amount of Wi-Fi Internet of things equipment with similar functions through the group MAC address, so that the data packet transmitting quantity can be reduced; the control process is simplified; and the reaction speed of the controlled equipment is increased.
Owner:ESPRESSIF SYST SHANGHAI
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com