Static taint analysis and symbolic execution-based Android application vulnerability discovery method
A taint analysis and symbolic execution technology, applied in computer security devices, instruments, computing, etc., can solve the problems of static taint analysis, large memory consumption and time, false positives of analysis results, complex analysis process, etc., and achieve the insensitivity of the path Problems, increase operating efficiency, and the effect of accurate analysis results
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
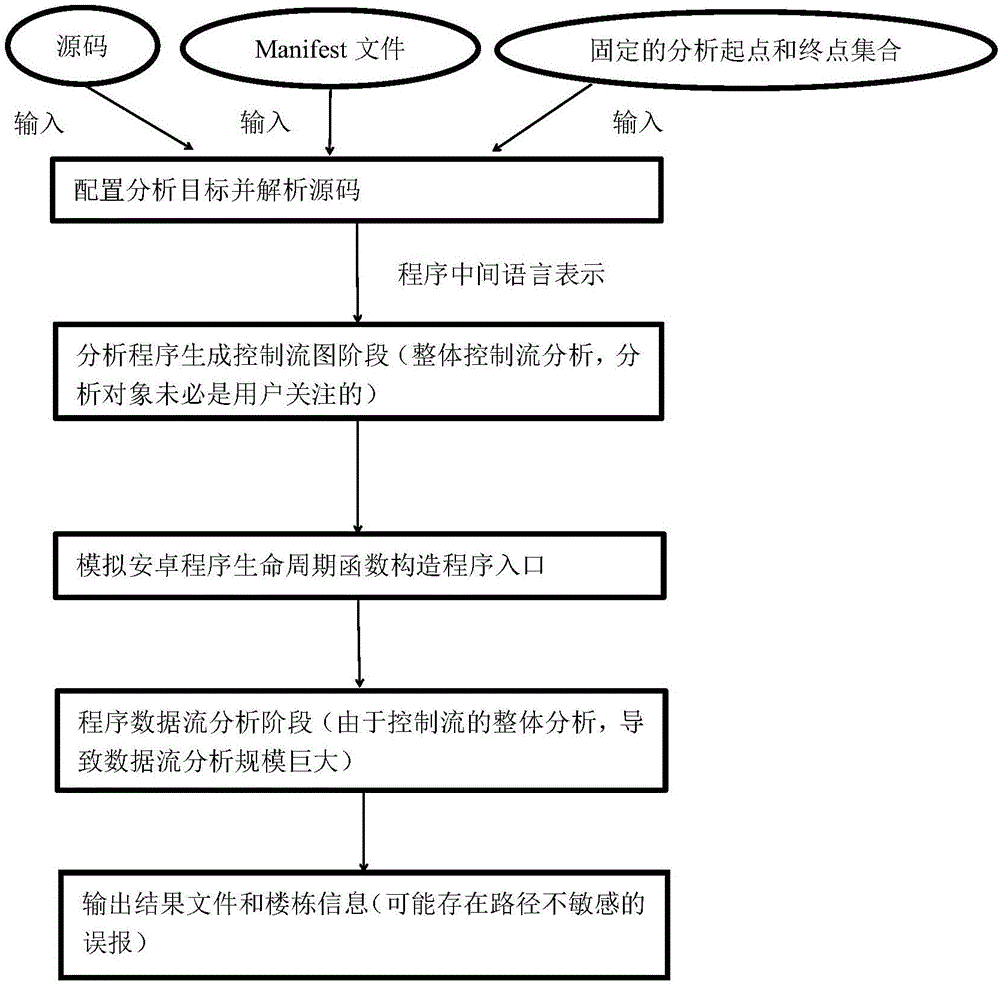
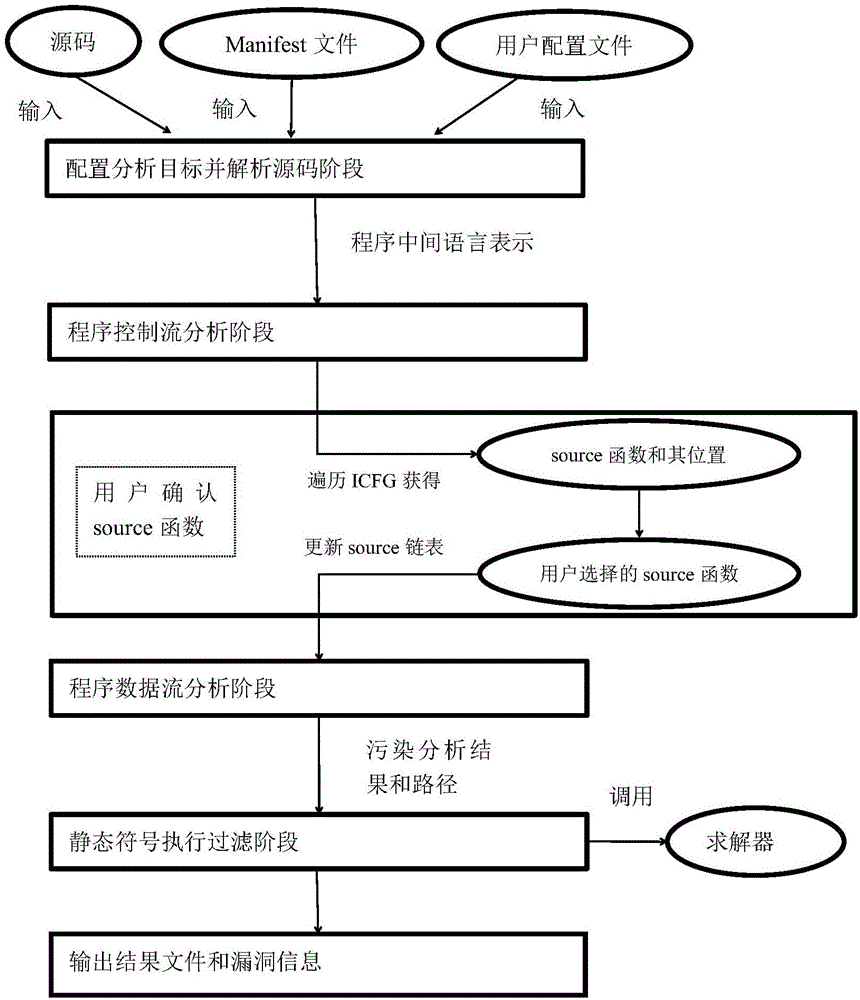
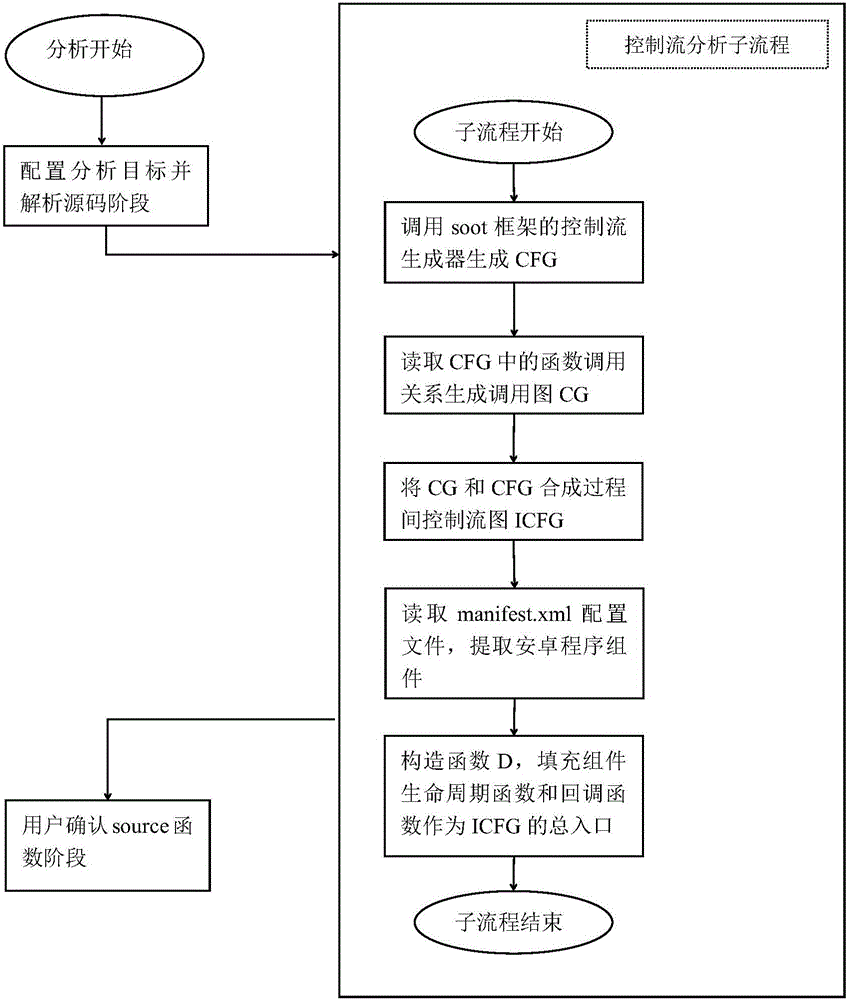
[0047] In today's society, the number of users of mobile smart devices has far exceeded the number of users of the host terminal, and Android mobile phone users account for the vast majority of end users, and the open source nature of the Android system framework makes Android mobile phone applications always vulnerable This has seriously affected personal information security and social security.
[0048]Under the current technical conditions, the dynamic analysis method mainly used for vulnerability mining of Android mobile phone applications, although the accuracy is high, requires program analysts to have rich experience in security analysis, and manual dynamic analysis will consume a lot of human resources. and time. Therefore, how to more efficiently and automatically exploit vulnerabilities in Android applications has become an urgent problem in the field of information security.
[0049] The present invention is based on the theory of program static taint analysis, on...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com