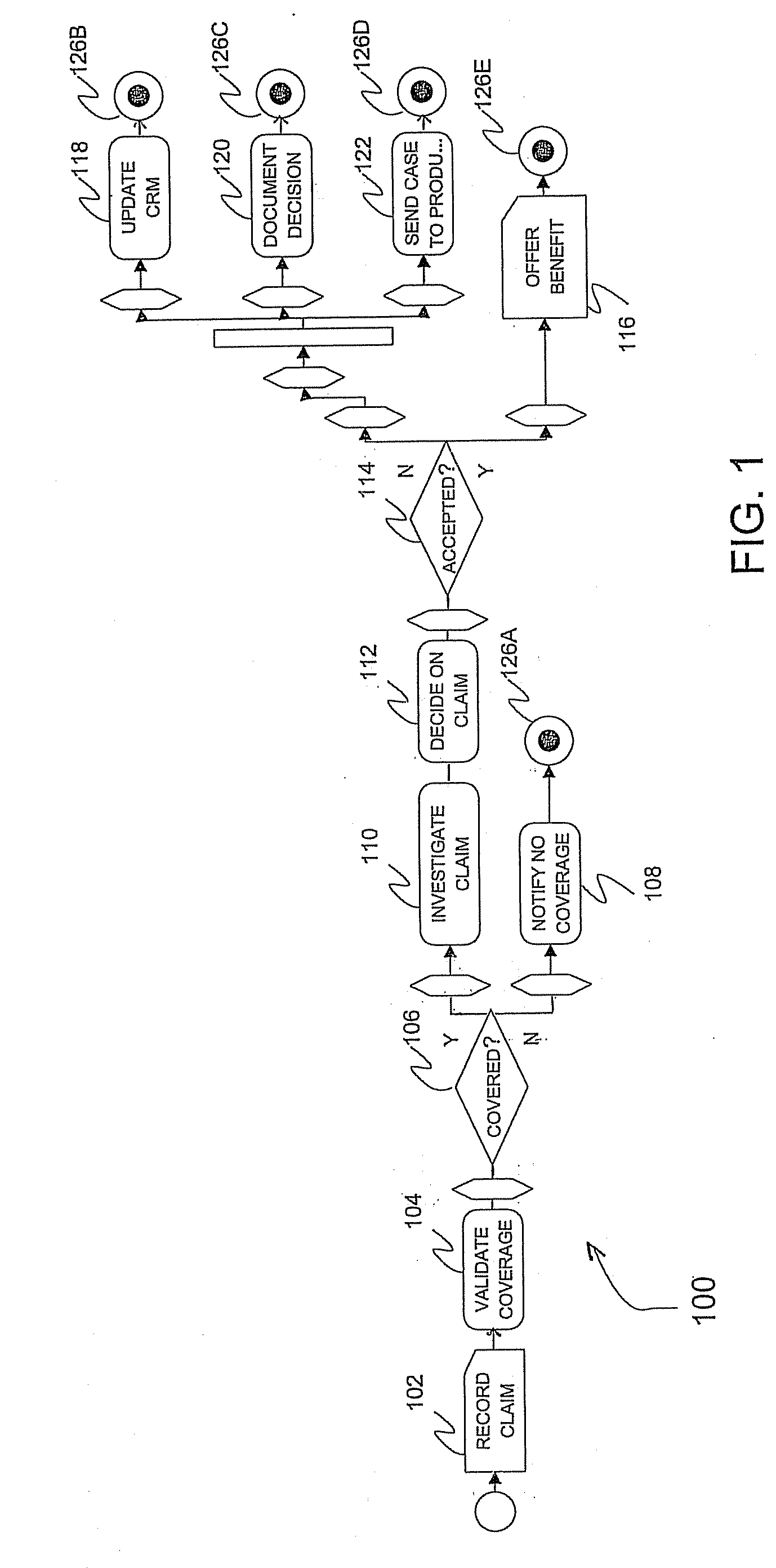
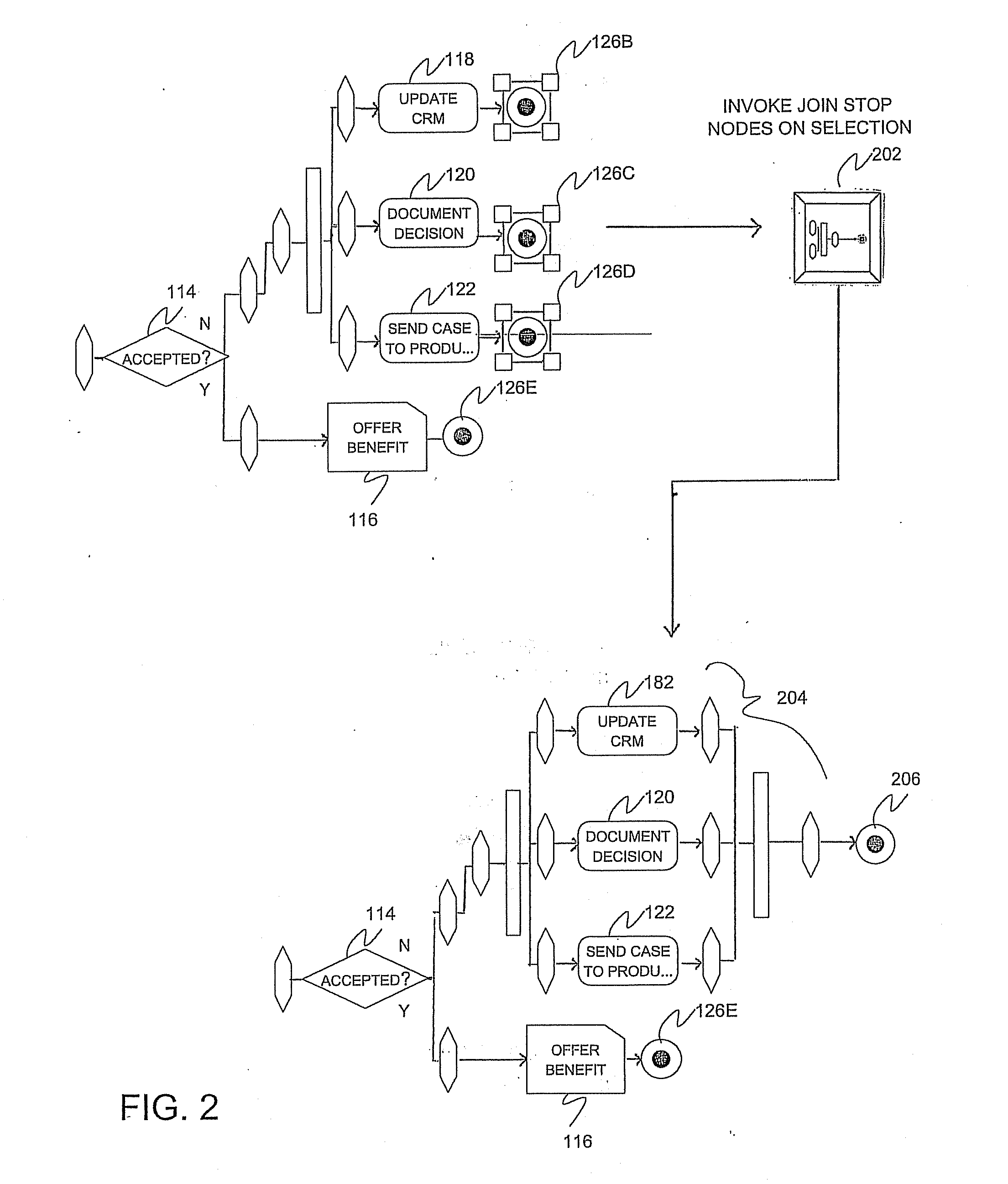
Patents
Literature
55 results about "Control flow analysis" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
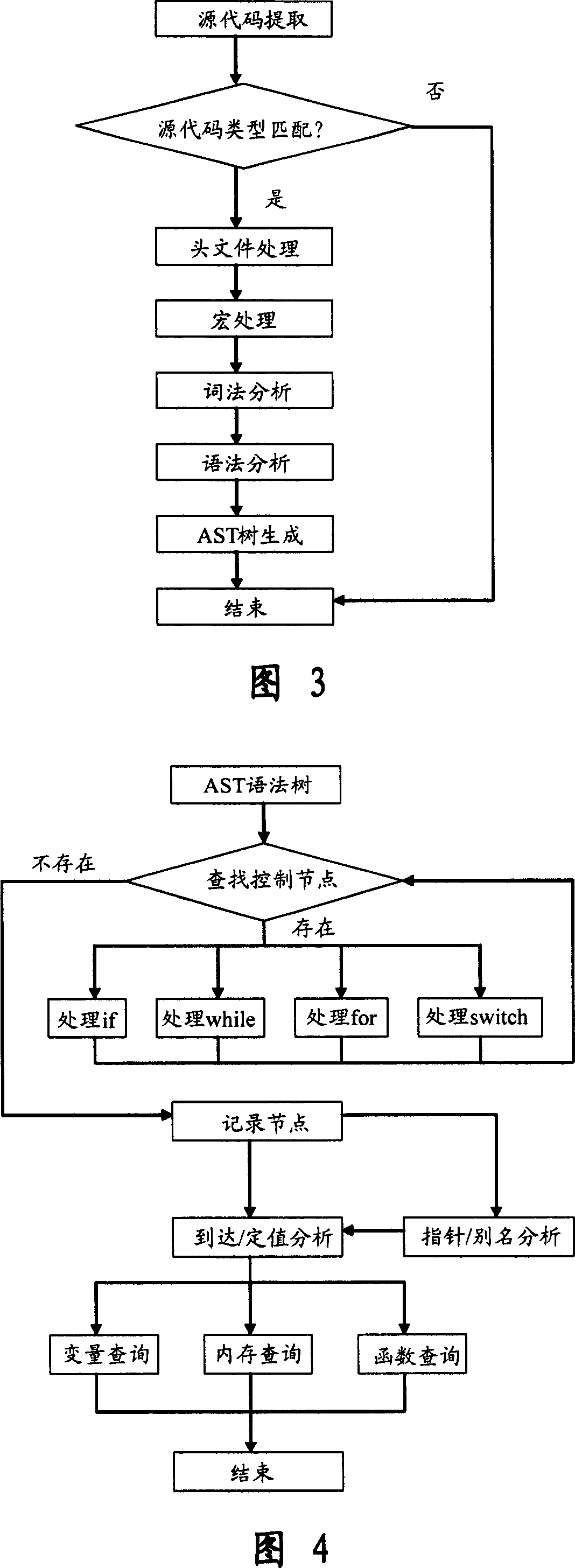
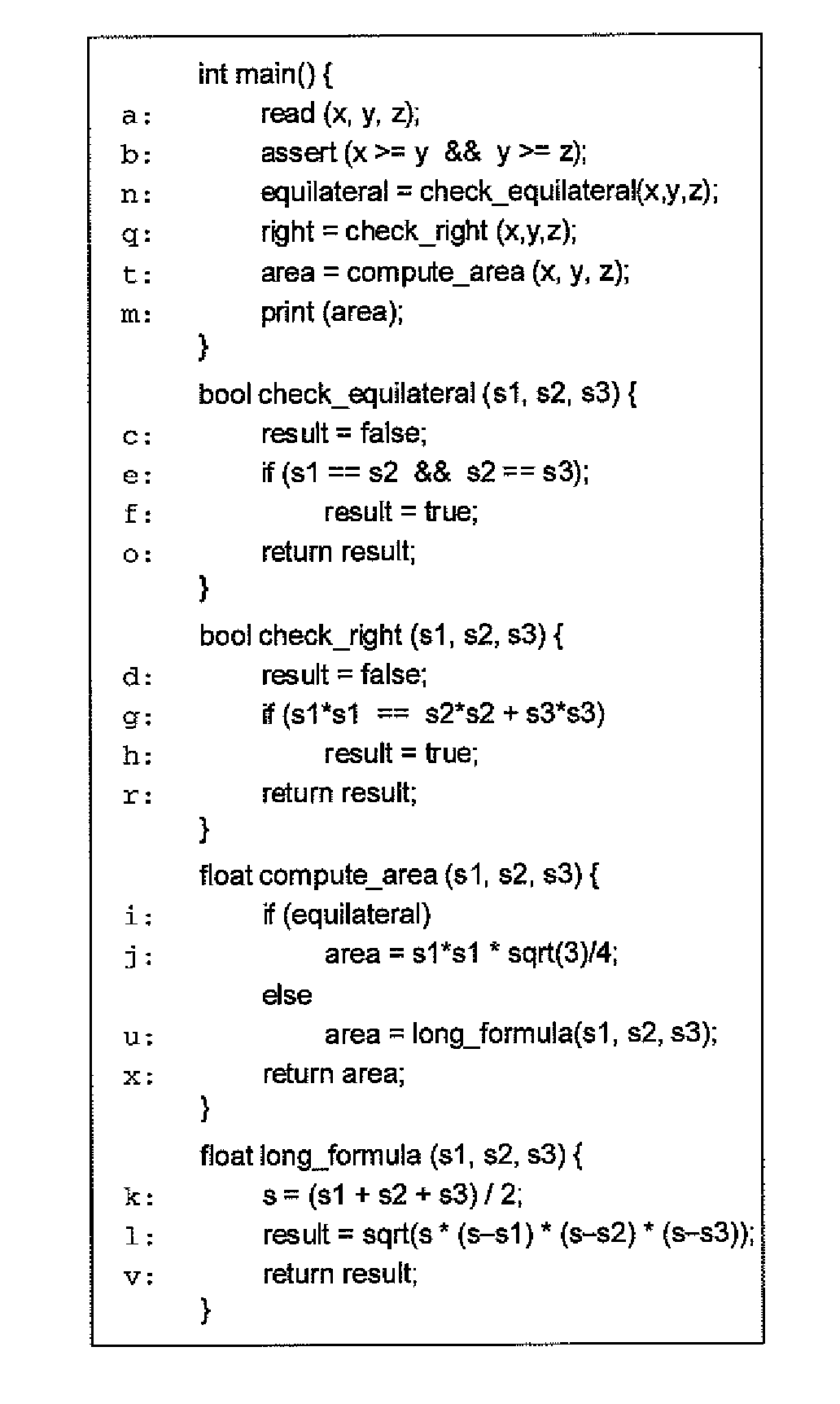
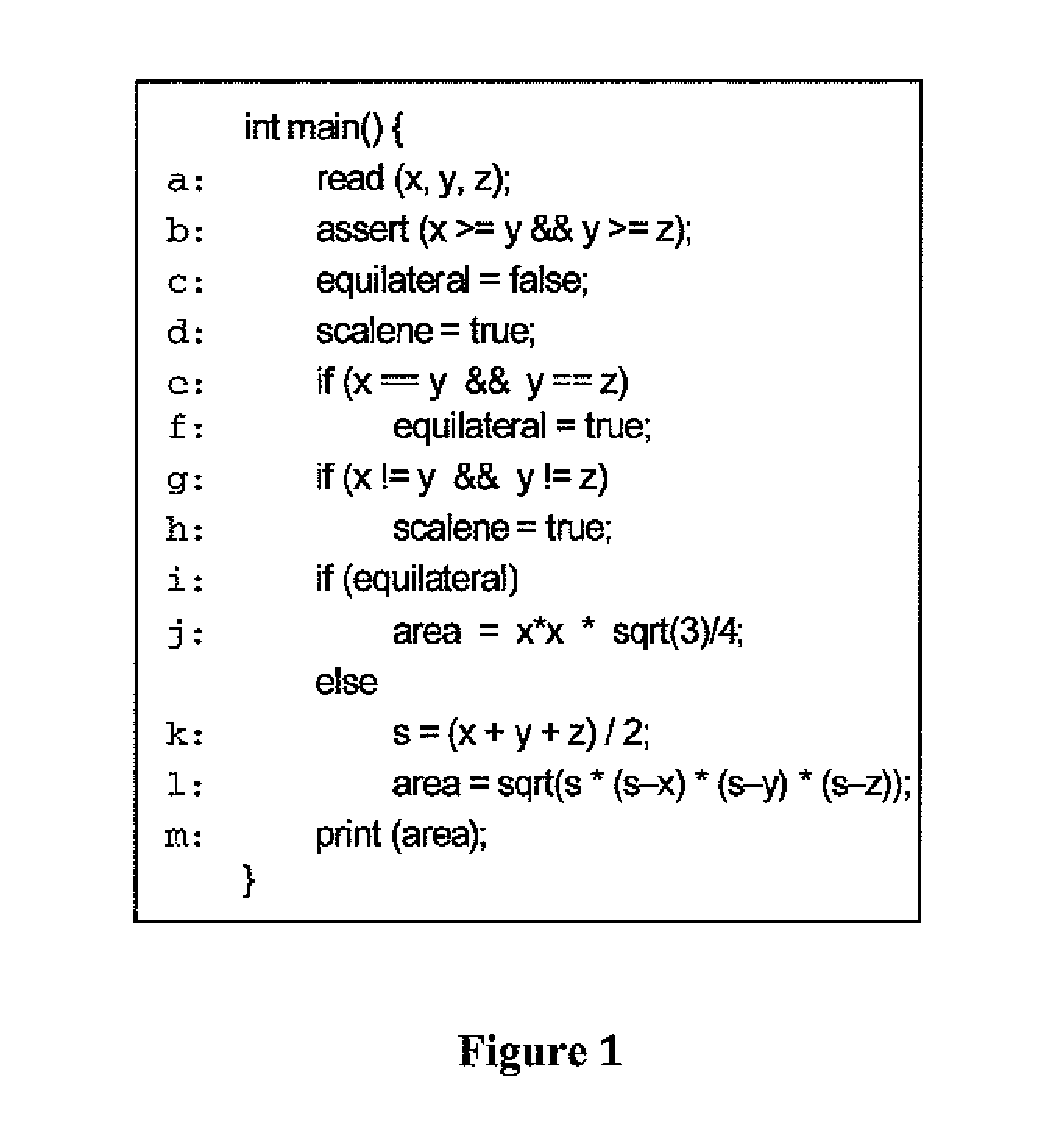
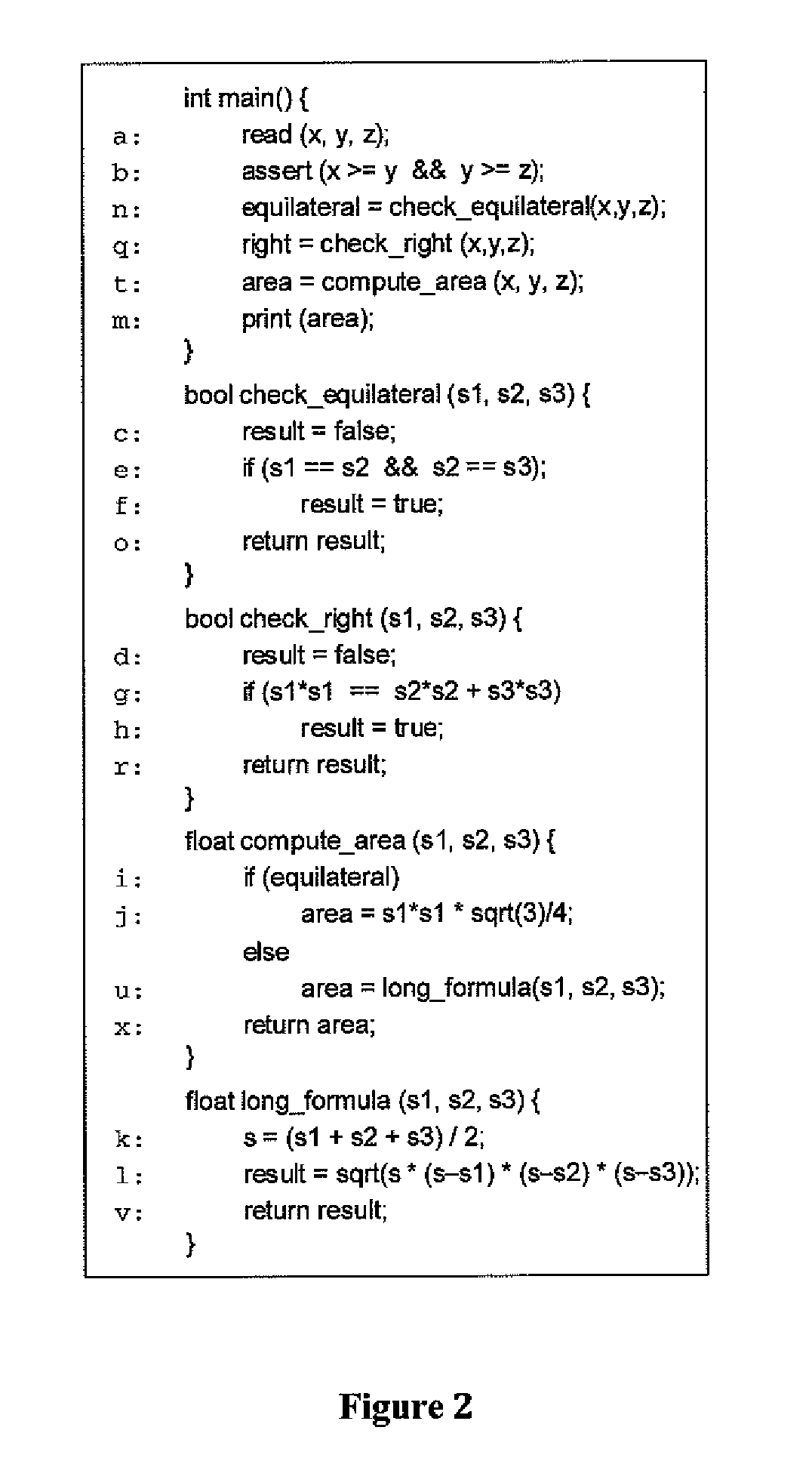
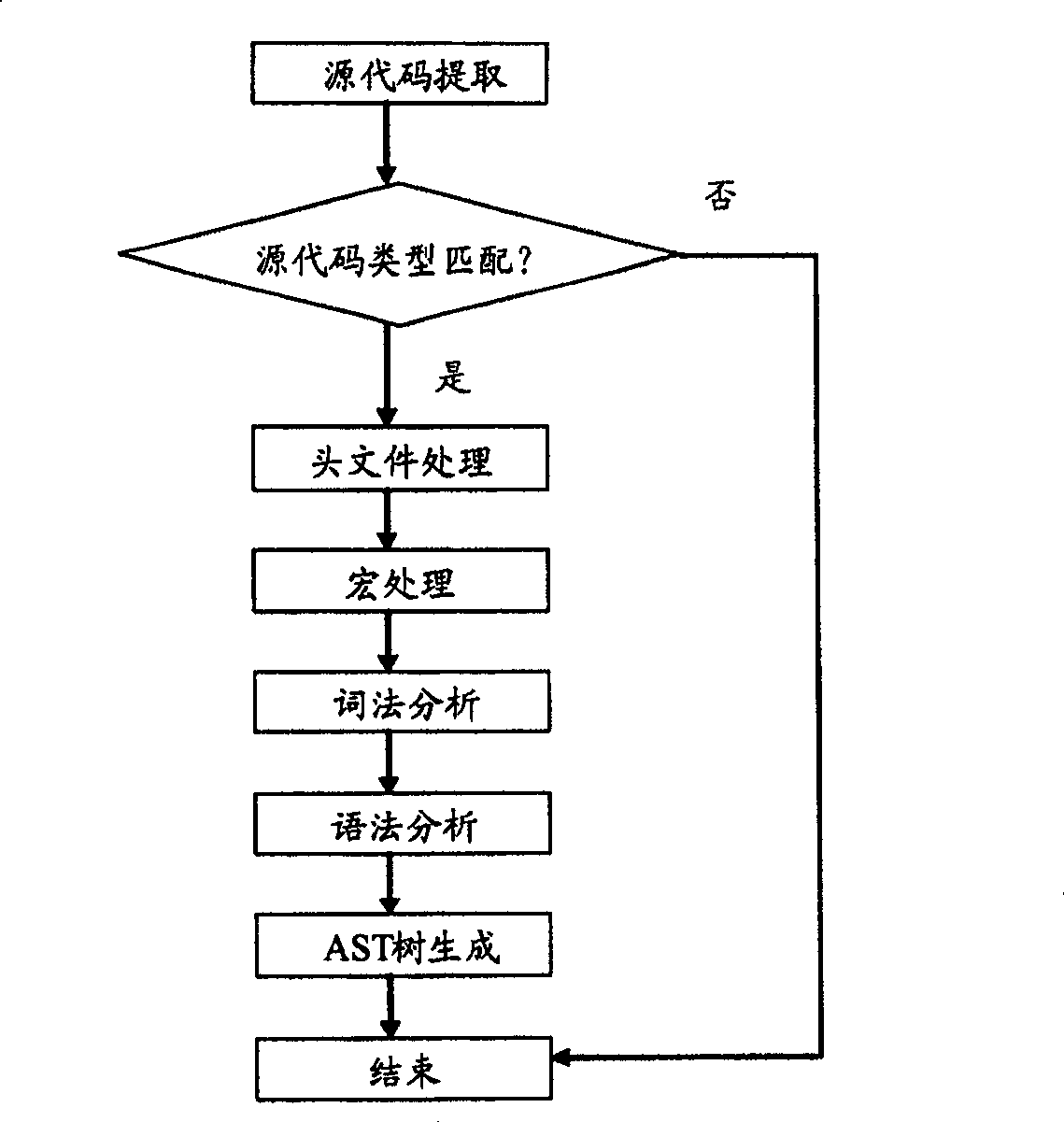
In computer science, control-flow analysis (CFA) is a static-code-analysis technique for determining the control flow of a program. The control flow is expressed as a control-flow graph (CFG). For both functional programming languages and object-oriented programming languages, the term CFA, and elaborations such as k-CFA, refer to specific algorithms that compute control flow.
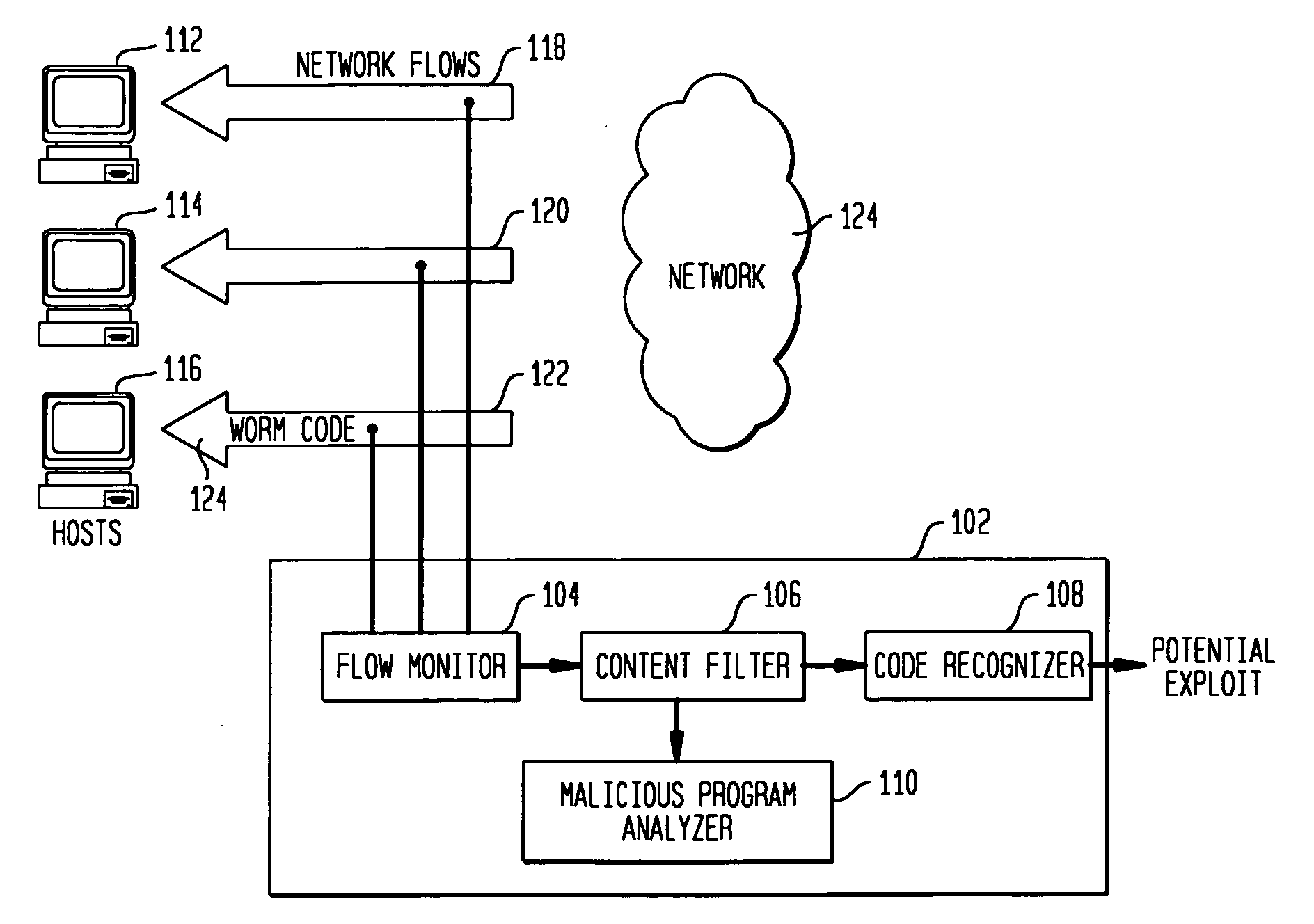
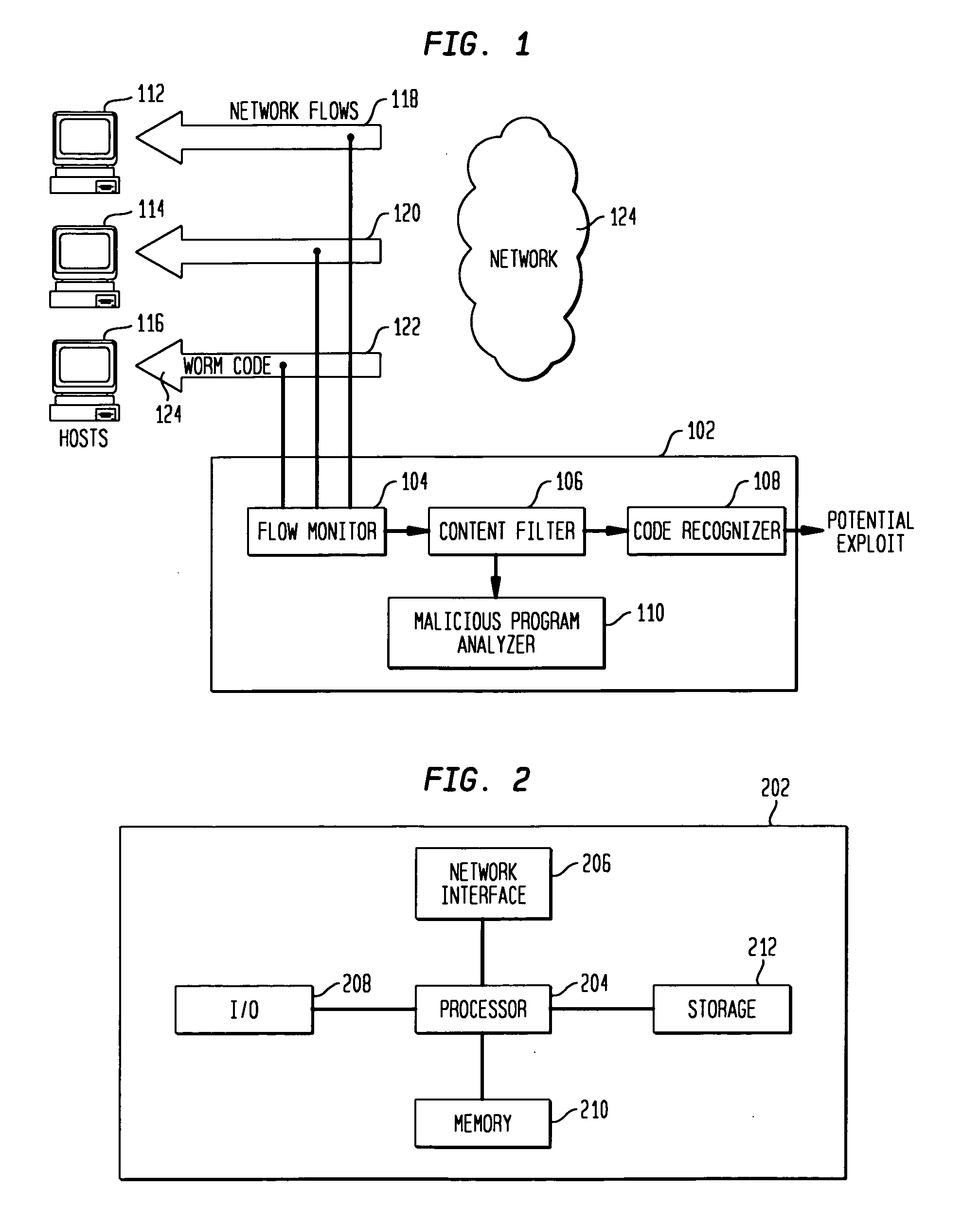
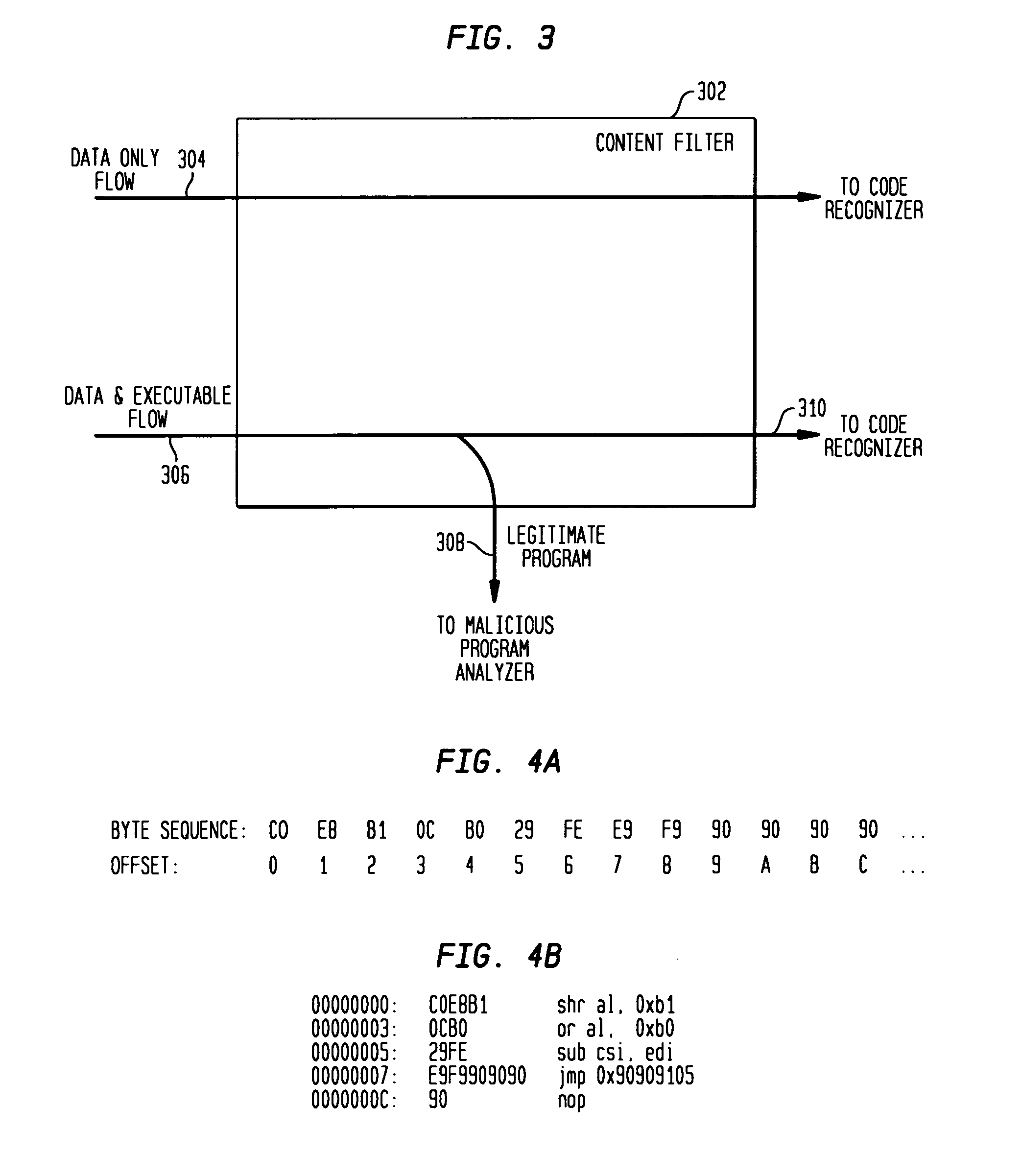
Detecting exploit code in network flows
InactiveUS20090328185A1Memory loss protectionUnauthorized memory use protectionData streamNetwork packet
Disclosed is a method and apparatus for detecting exploit code in network flows. Network data packets are intercepted by a flow monitor which generates data flows from the intercepted data packets. A content filter filters out legitimate programs from the data flows, and the unfiltered portions are provided to a code recognizer which detects executable code. Any embedded executable code in the unfiltered data flow portions is identified as a suspected exploit in the network flow. The executable code recognizer recognizes executable code by performing convergent binary disassembly on the unfiltered portions of the data flows. The executable code recognizer then constructs a control flow graph and performs control flow analysis, data flow analysis, and constraint enforcement in order to detect executable code. In addition to identifying detected executable code as a potential exploit, the detected executable code may then be used in order to generate a signature of the potential exploit, for use by other systems in detecting the exploit.
Owner:TELCORDIA TECHNOLOGIES INC
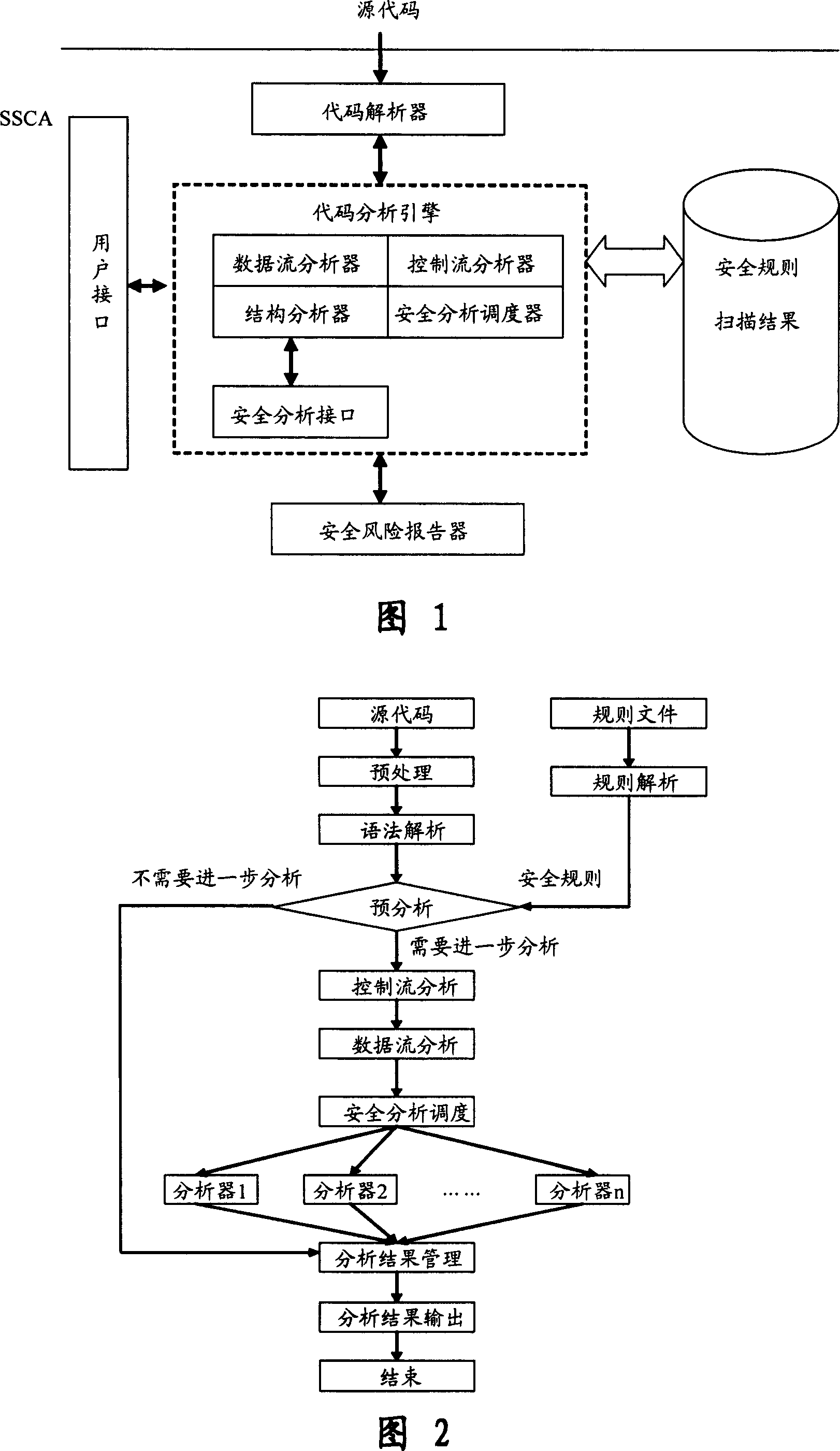
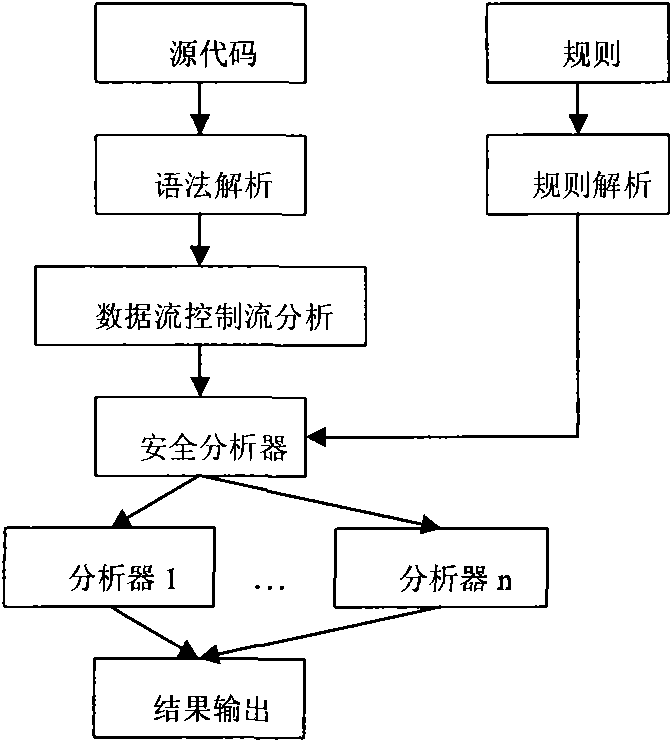
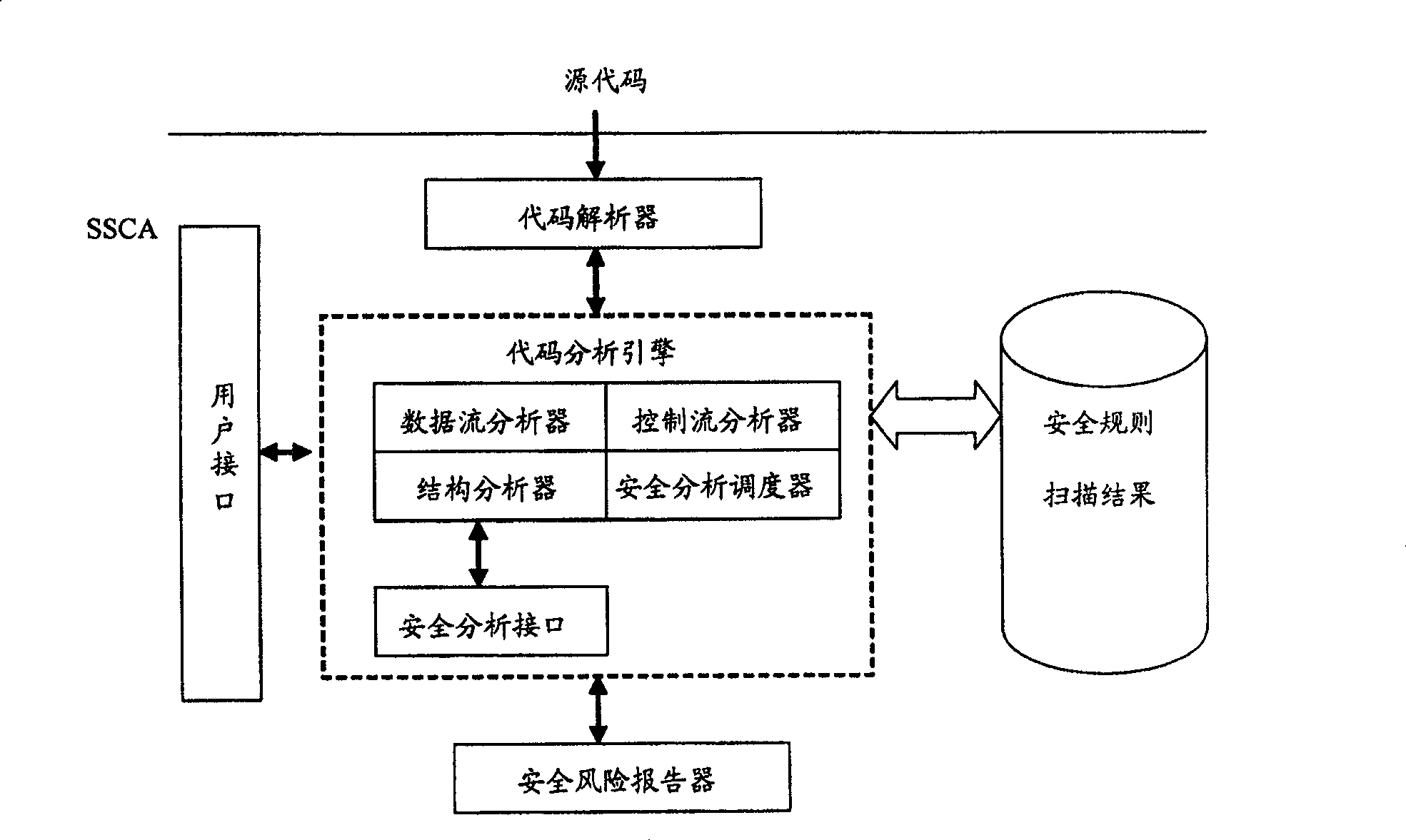
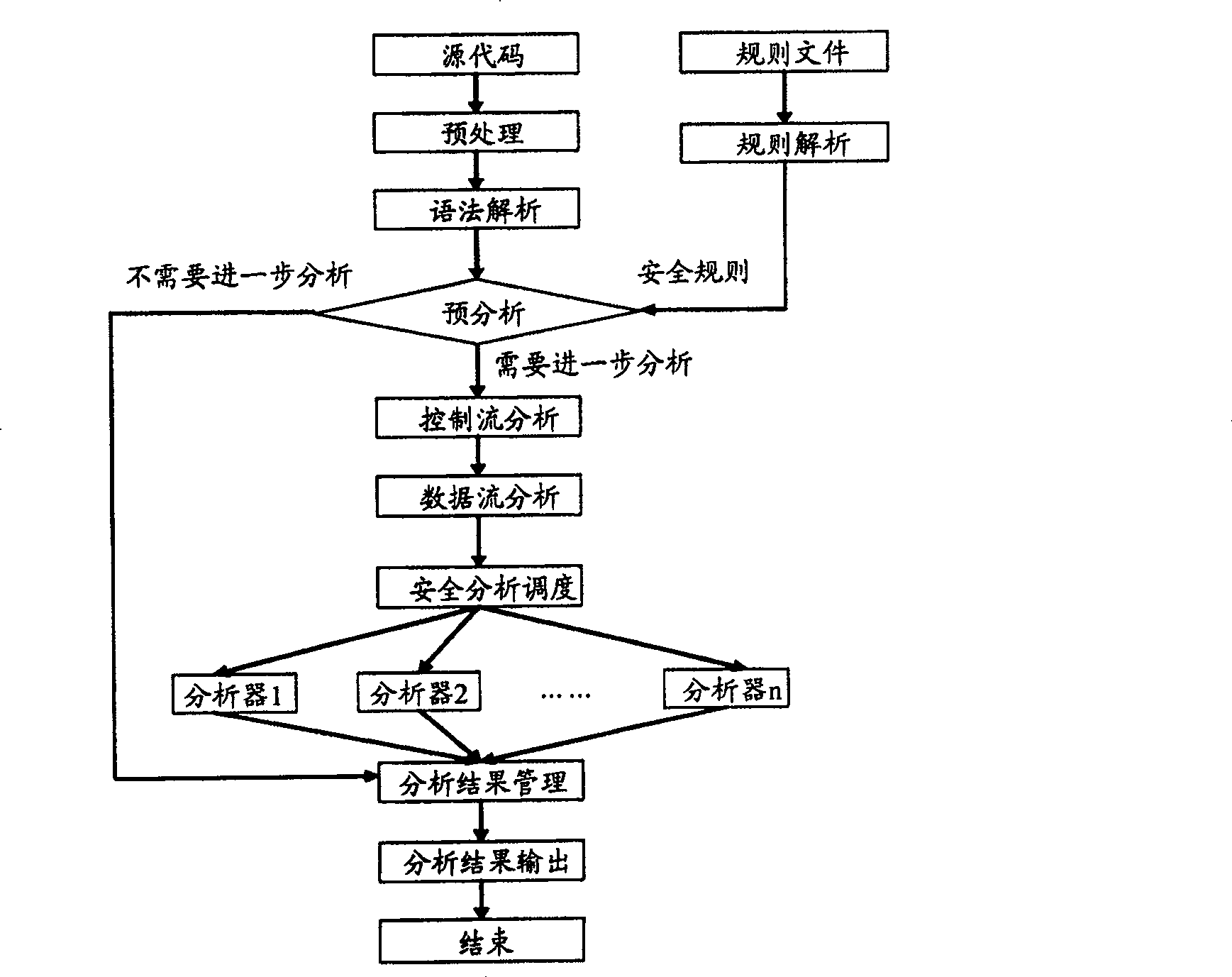
Software safety code analyzer based on static analysis of source code and testing method therefor
InactiveCN101017458AImprove accuracySupport for expansionSoftware testing/debuggingStatic timing analysisStructure analysis
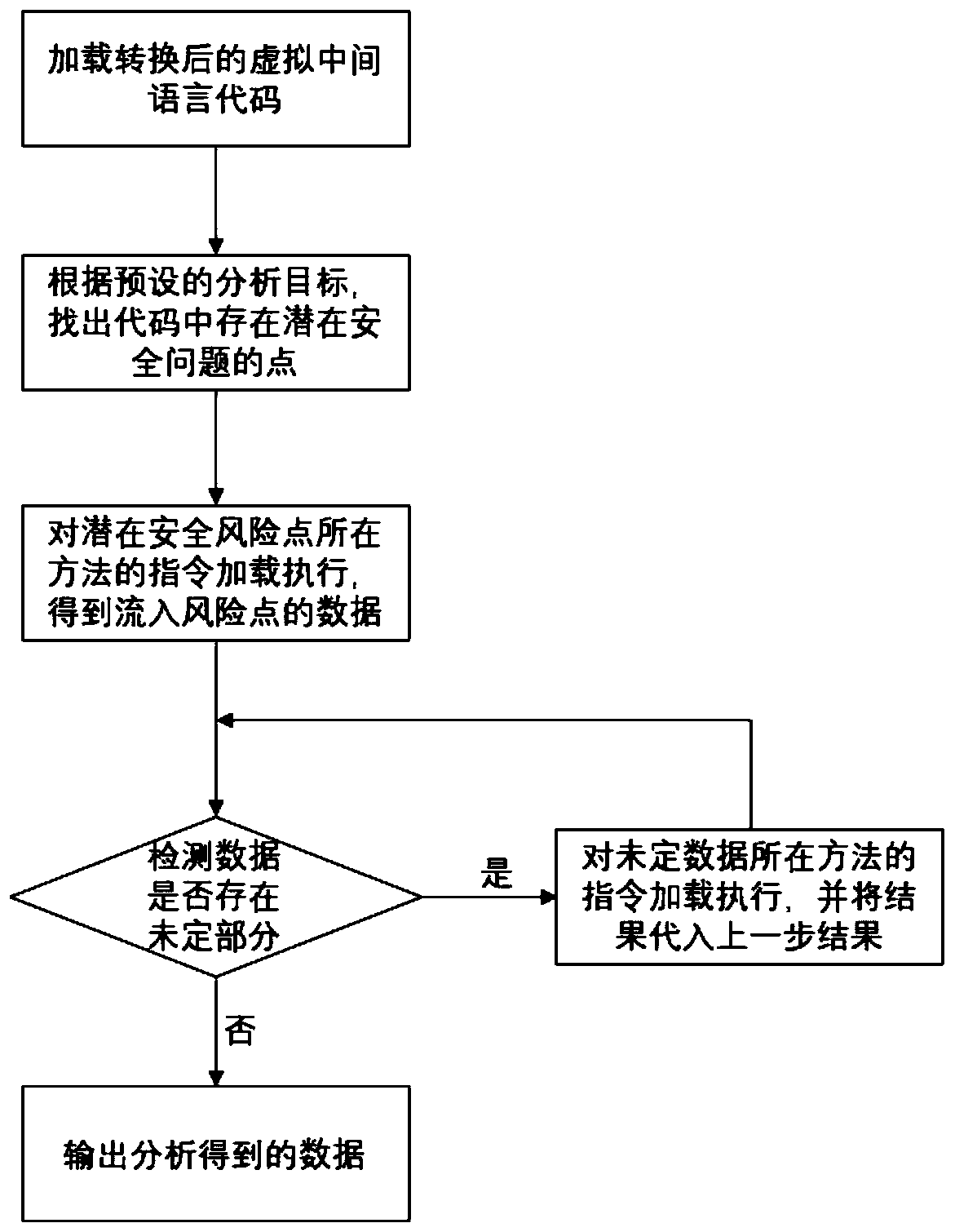
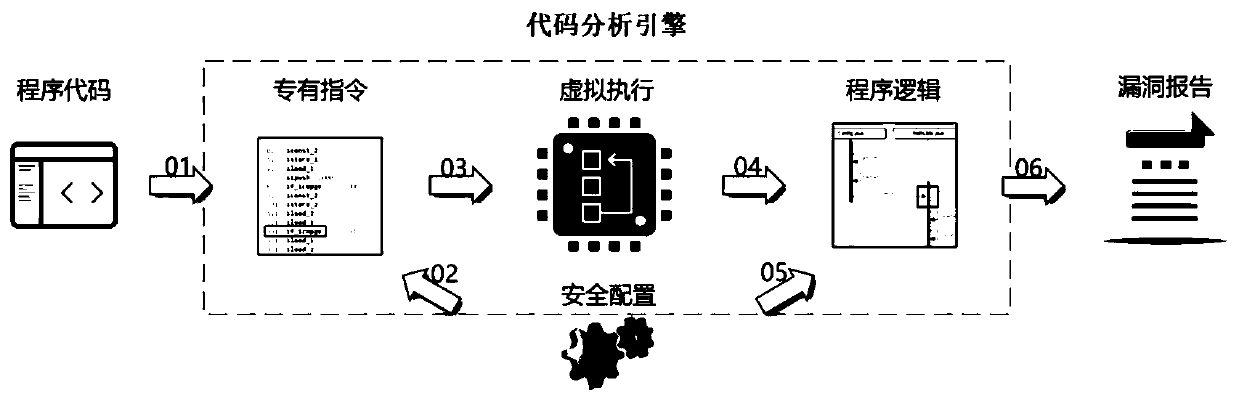
This invention relates to one software analyzer and its test method based on source codes static analysis, wherein the analysis device comprises five function modules of code analysis device, codes analysis engine, safety risk report device, safety rules database and user interface; this invention gets programs safety risk to user according to the source program and grammar and meanings and delivers the safety leak to the user for audit and evaluation.
Owner:深圳北邮网络科技有限公司
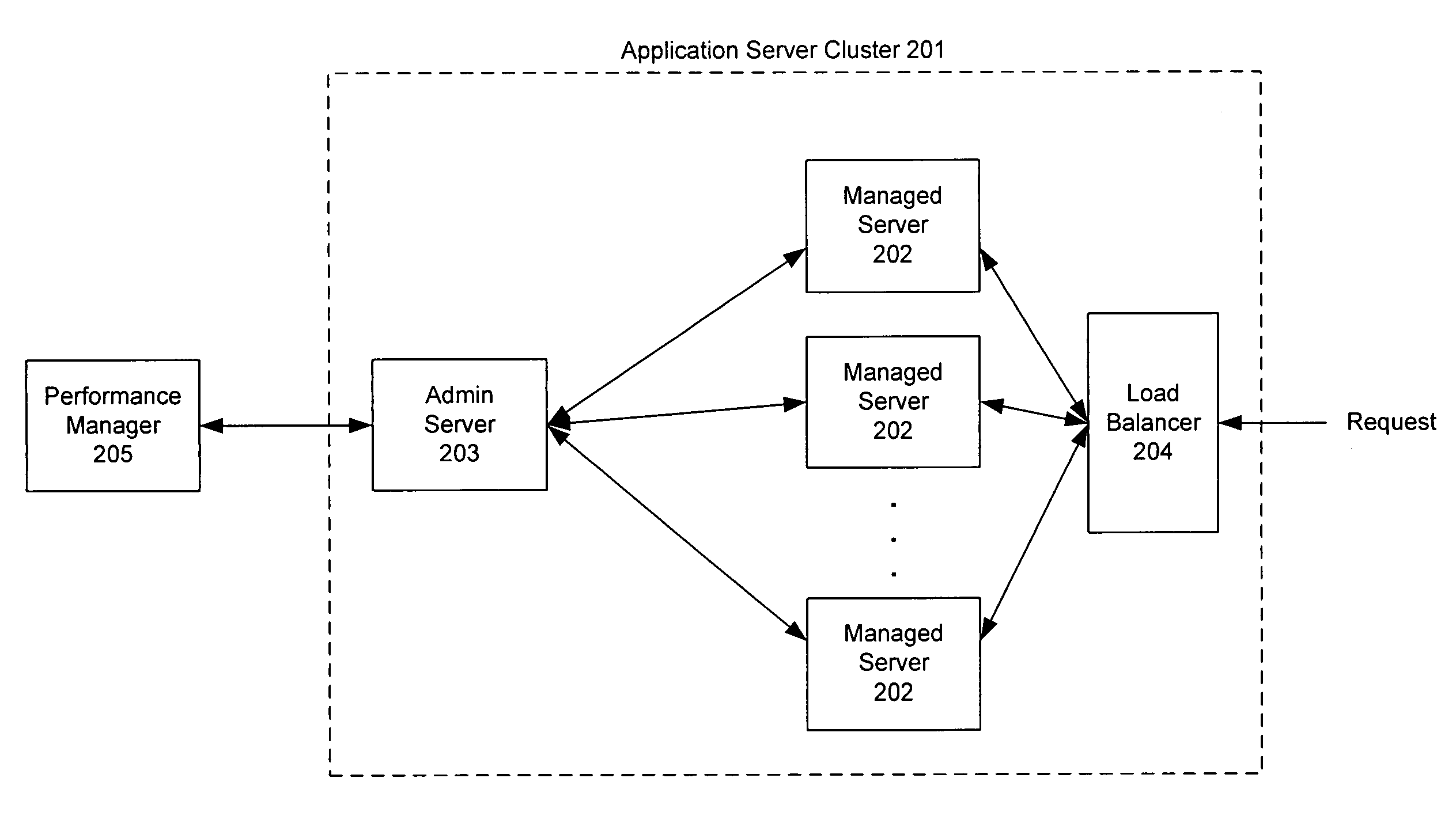
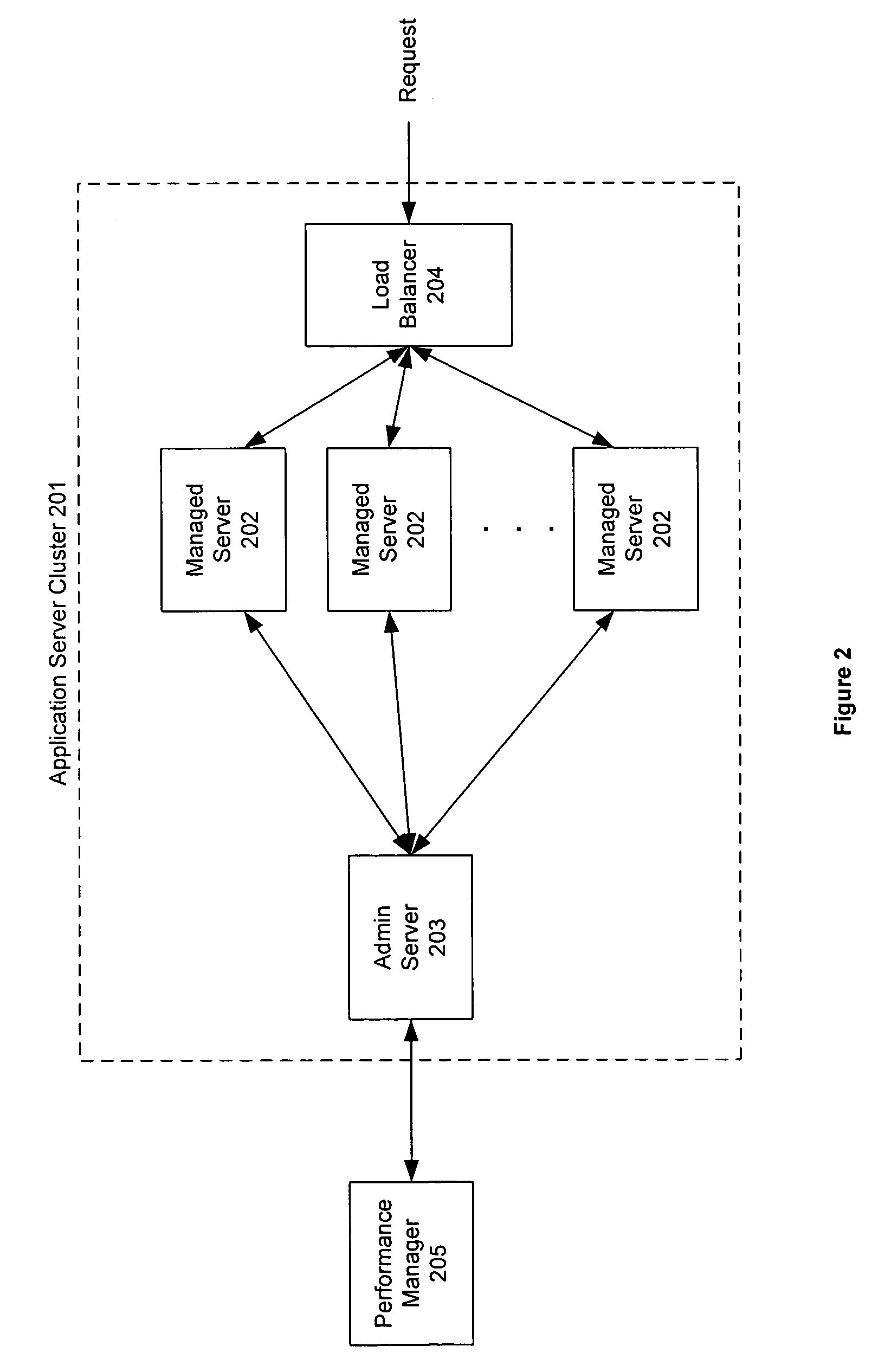
Monitoring and performance management of component-based applications
ActiveUS7627671B1Error detection/correctionDigital computer detailsManagement toolApplication software
Invention manages underlying application objects that support implemented business functions. A performance manager accesses and interprets application metadata and execution environment metadata, using a hierarchical entity to model complex relationships between application abstractions, components and resources. The performance manager encodes common behavioral and architecture information in models resulting from analysis of component architecture standards, vendor application servers, development tools and administration tools. The performance manager conducts inter-component dependency and control flow analysis, for example by generating control flow graphs from application metadata and performing byte code analysis without access to application source code. The performance manager collects metrics from standardized and vendor-specific sources, instruments interpreters (such as the Java Virtual Machine), and collects and utilizes resource metrics, code performance metrics, configuration parameters, and transaction, failure and lifecycle events.
Owner:ORACLE INT CORP
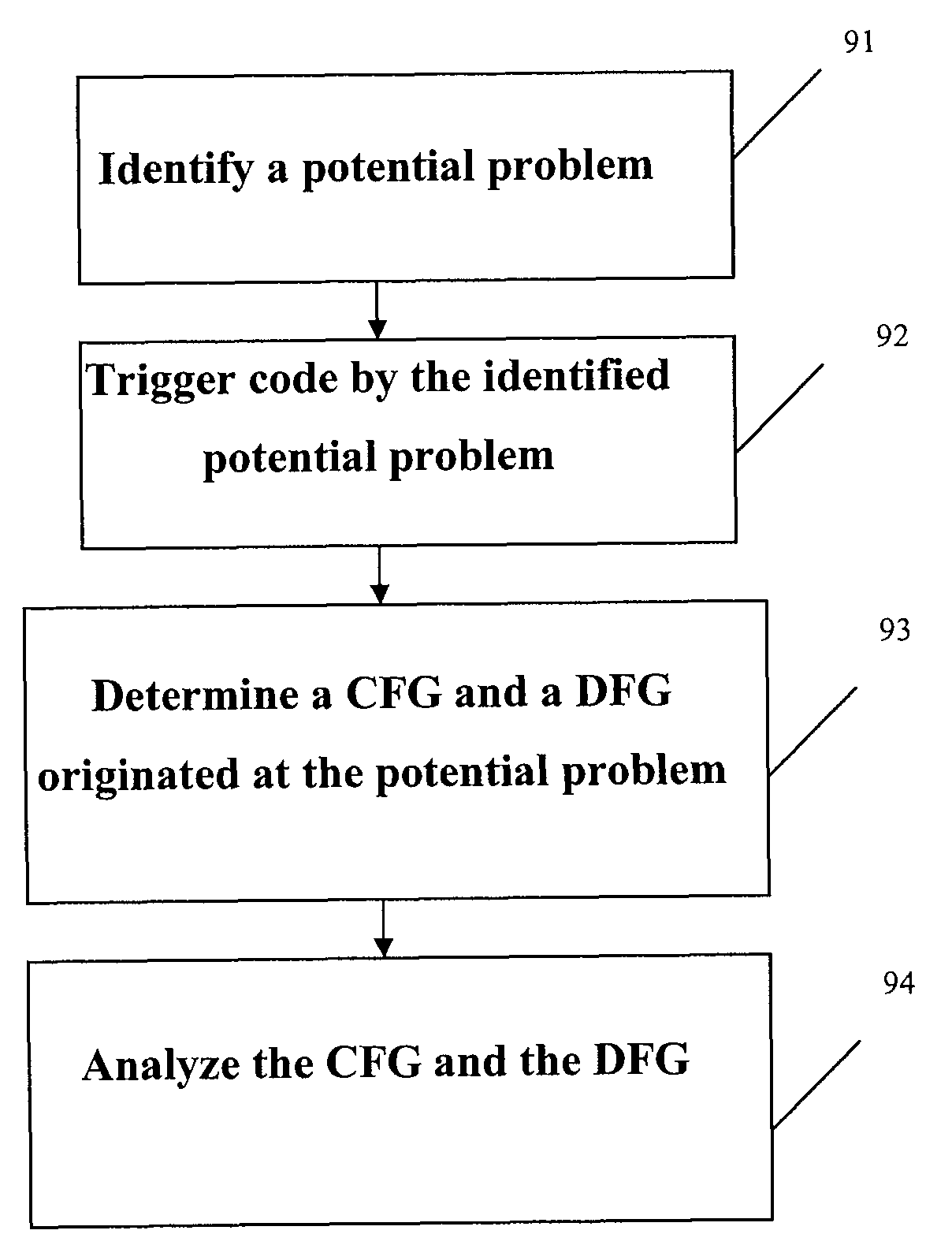
System and method for detecting defects in a computer program using data and control flow analysis
ActiveUS7900193B1Keep trackError detection/correctionSpecific program execution arrangementsTheoretical computer scienceControl flow analysis
A system and method for identifying errors in a computer software include: identifying a potential problem in the computer software; triggering a portion of the computer software by the identified potential problem; determining a control flow graph and a data flow graph for the triggered portion of the computer software originating at the identified potential problem; and analyzing the control flow graph and the data flow graph to verify that the identified potential problem is an actual error. The potential problem may be identified using test tools such as a static analysis tool or a unit test tool.
Owner:PARASOFT
Static taint analysis and symbolic execution-based Android application vulnerability discovery method
ActiveCN106709356ATargetedImprove efficiencyPlatform integrity maintainanceStatic timing analysisData stream
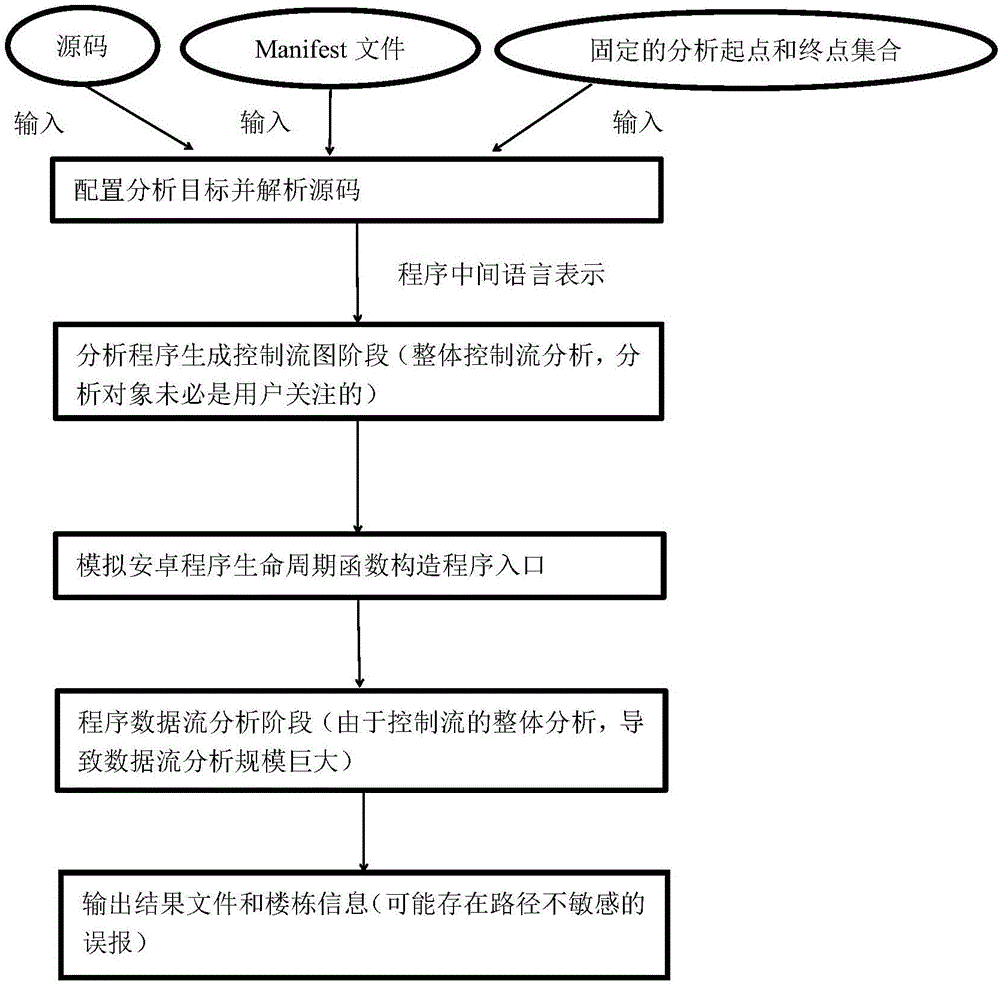
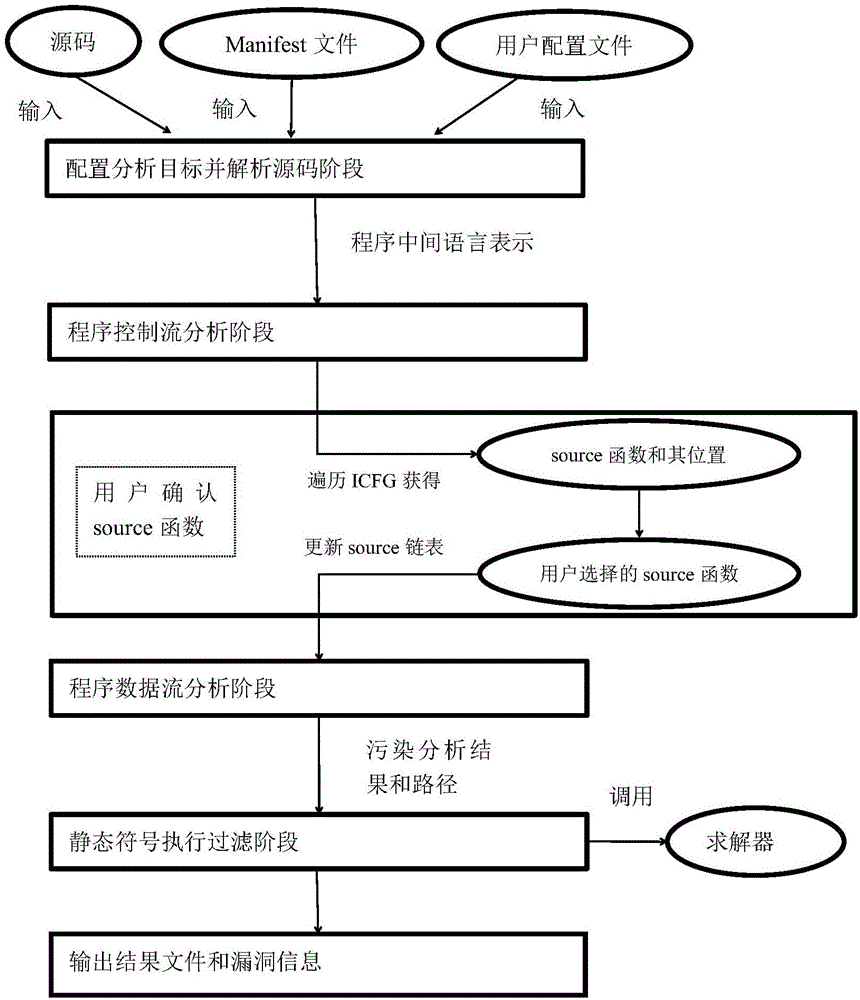
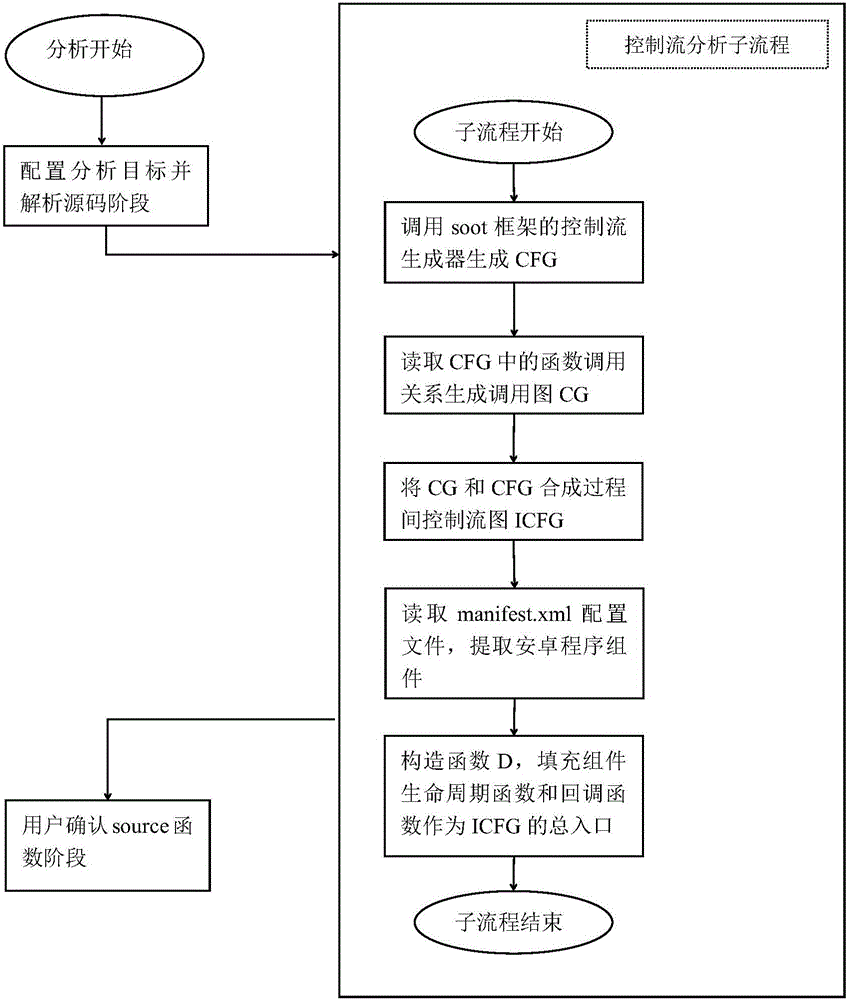
The invention discloses a static taint analysis and symbolic execution-based Android application vulnerability discovery method, and mainly aims at solving the problems that the analysis range is fixed, the memory consumption is huge and the analysis result is mistakenly reported in the process of discovering vulnerabilities by using the existing static taint analysis method. The method is realized through the following steps of: 1) configuring an analysis target and decompiling a program source code; 2) carrying out control flow analysis on the decompilation result; 3) selecting a source function by a user according to the control flow analysis result, so as to narrow an analysis target; 4) carrying out data flow analysis according to the control flow analysis result, so as to generate a vulnerability path; and 5) filtering the data flow analysis result by adoption of a static symbolic execution technology, taking the residual parts after the filtration as discovered vulnerabilities, warning the user and printing the vulnerability path. On the basis of the existing static taint analysis technology, the method disclosed by the invention has the advantages of extending the vulnerability discovery range, decreasing the memory consumption of vulnerability discovery and improving the accuracy of vulnerability discovery results, and can be applied to the discovery and research of Android application program vulnerabilities.
Owner:XIDIAN UNIV
Method and system for combining quality assurance and model transformations in a business-driven development environment
InactiveUS20090150860A1ResourcesSpecific program execution arrangementsQuality assuranceDecomposition
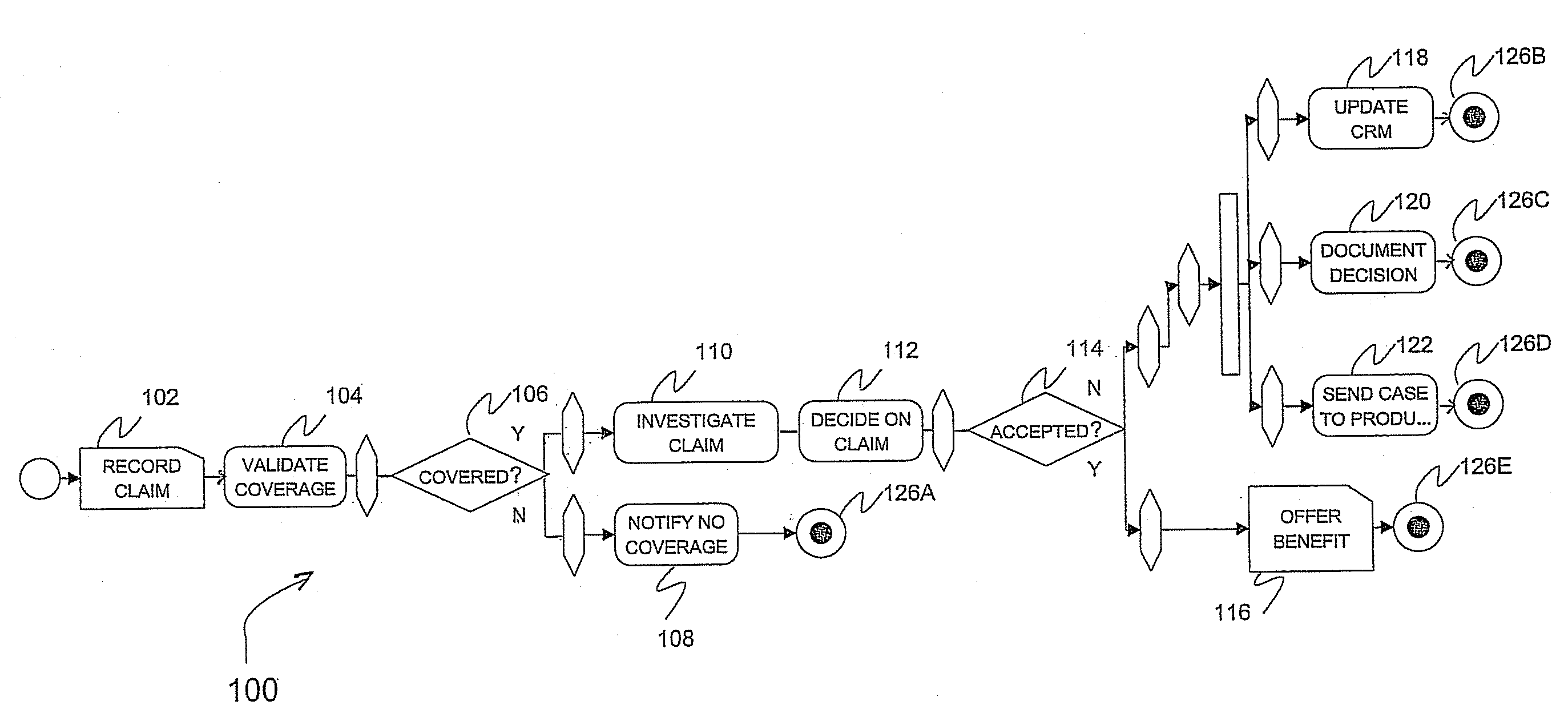
A system for combining quality assurance and model transformations in a business-driven development environment includes a host system executing a business modeling application, a transformation framework including a transformation programming interface (TPI) and a quality assurance framework executing on top of the business modeling application, and a plurality of transformation plug-in tools in communication with the TPI. The TPI includes options for model access and traversal, model element creation / removal, model element property editing and analysis. The options are applied to the transformations, via the selected transformation plug-in tools, to a business model resulting in a modified business model that conforms to an information technology (IT)-based executable code. The quality assurance framework performs single-entry-single-exit (SESE) fragment decomposition of the modified business model, control-flow analysis, and notification to the user of any detected error conditions, the notification presented to the user with the modified business model via the TPI.
Owner:IBM CORP
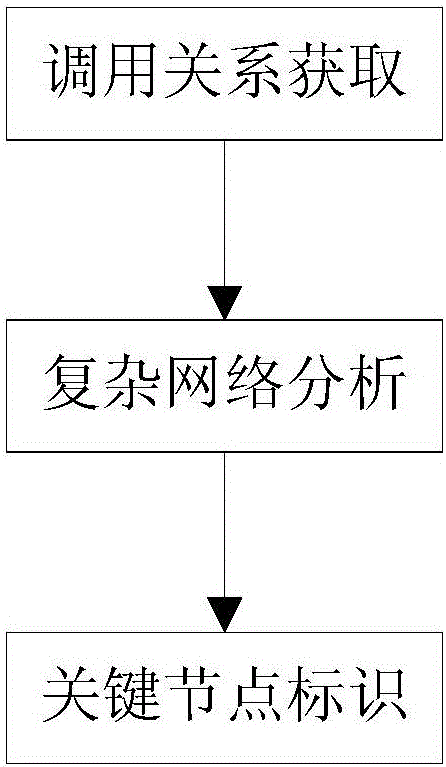
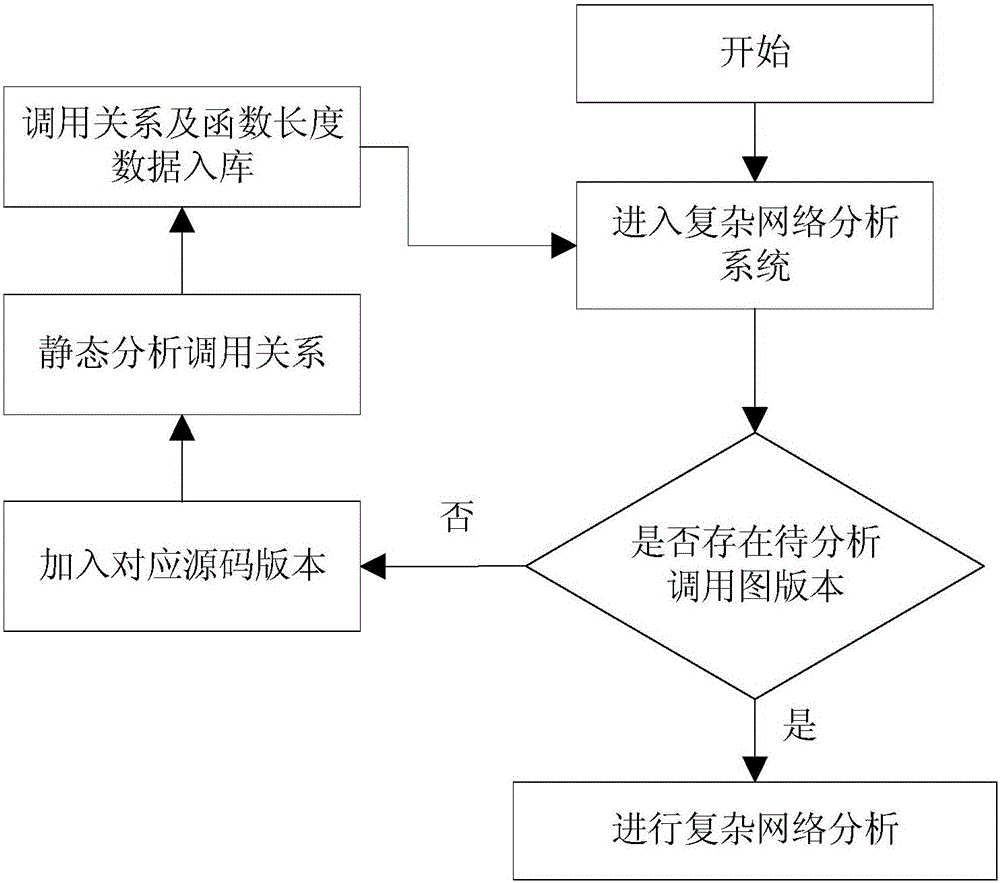
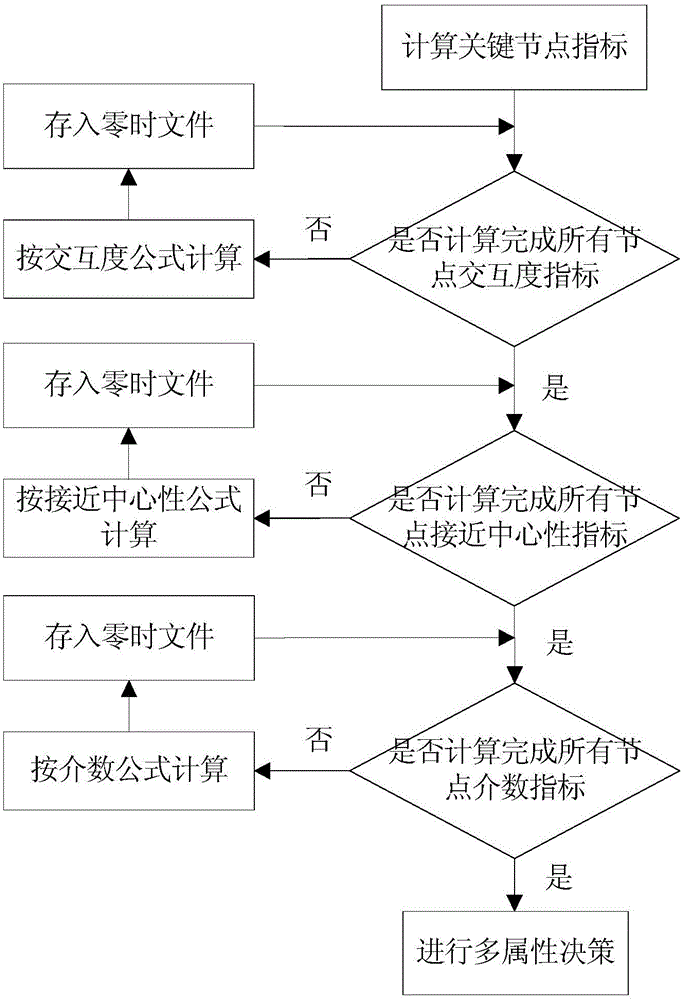
Function call graph key node recognition and identification method based on complex network analysis
ActiveCN106020950AImprove work efficiencyProgram initiation/switchingInterprogram communicationComplex network analysisLexical analysis
The invention relates to a function call graph key node recognition and identification method based on complex network analysis. The method comprises the steps of carrying out lexical analysis, grammatical analysis and control stream analysis through a sound code static analysis technology, thereby obtaining source code call relationship data and function length data, and storing all data in a database in a classification mode; generating a call graph according to the obtained data, calculating node indexes of the call graph by employing a complex network analysis method, wherein the indexes comprise interaction degree, closeness centrality, node betweenness and function length, and calculating node key degree by employing a multi-attribute decision-making method; and through combination of user demands and state data stored in the database, calculating a key node rank and corresponding grey proportion data by employing the obtained node key degree data of the function call graph, and carrying out visual display. According to the method, the key nodes in the complex call relationship graph can be recognized and identified rapidly, and the working efficiency is remarkably improved.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
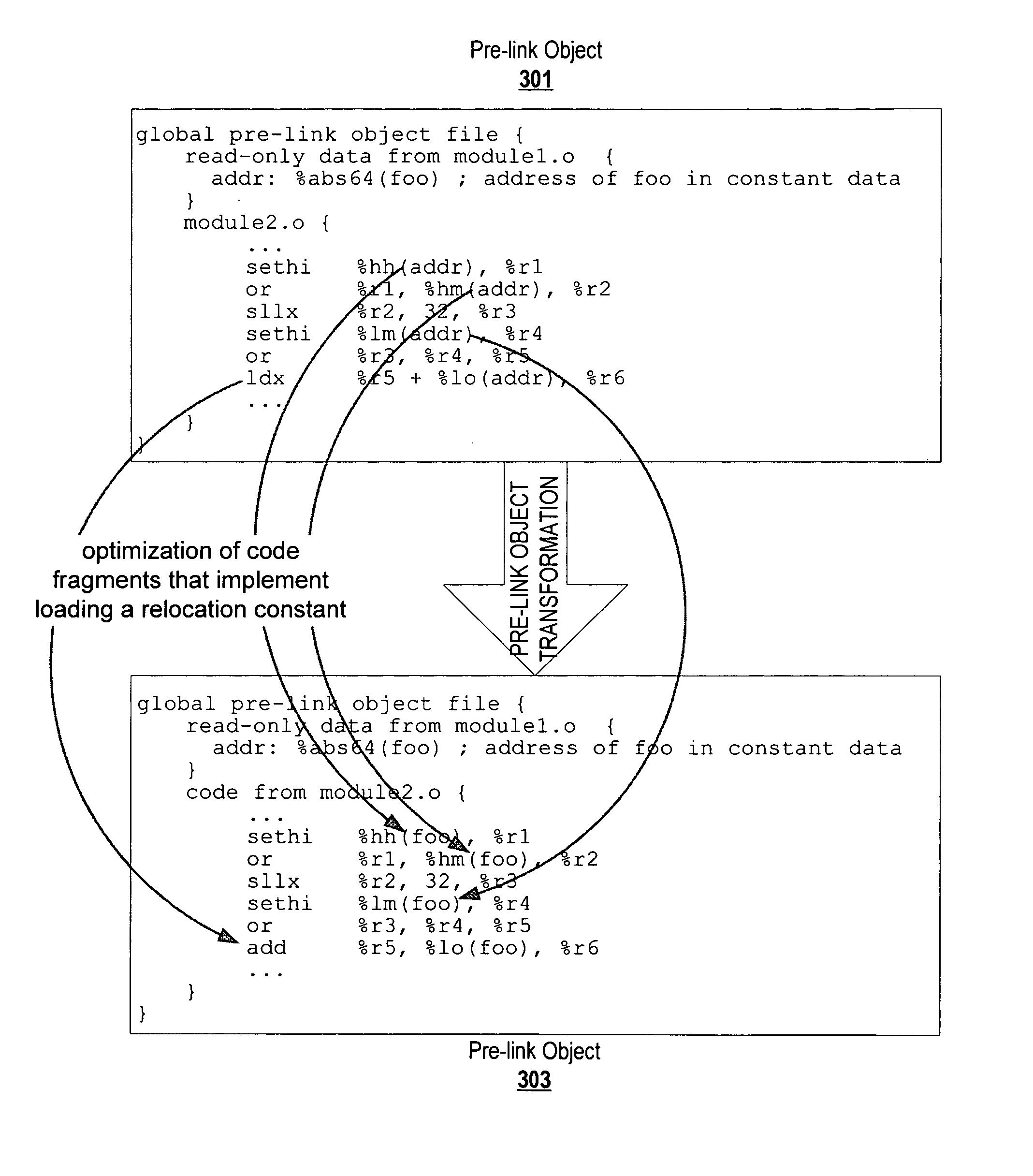
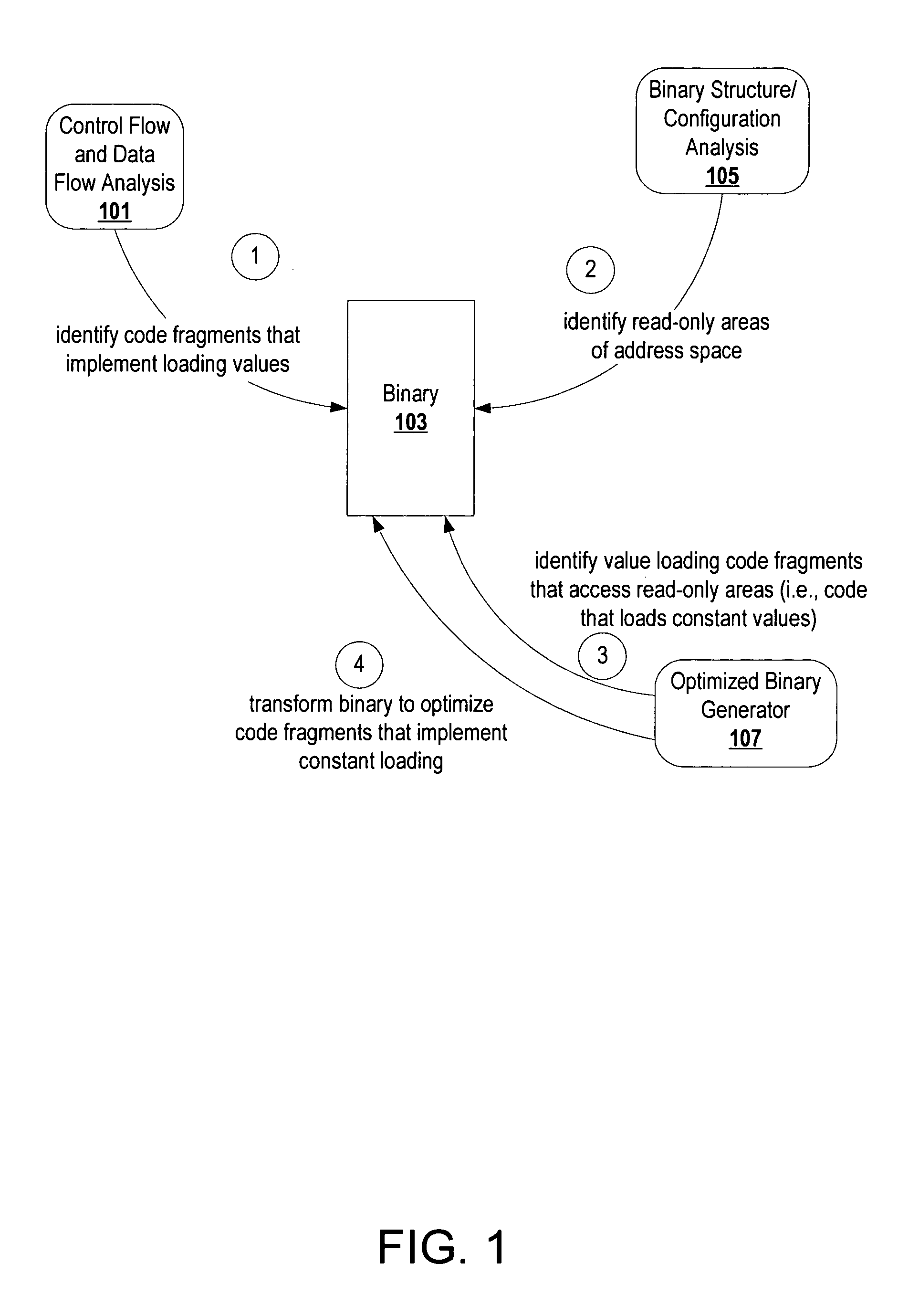
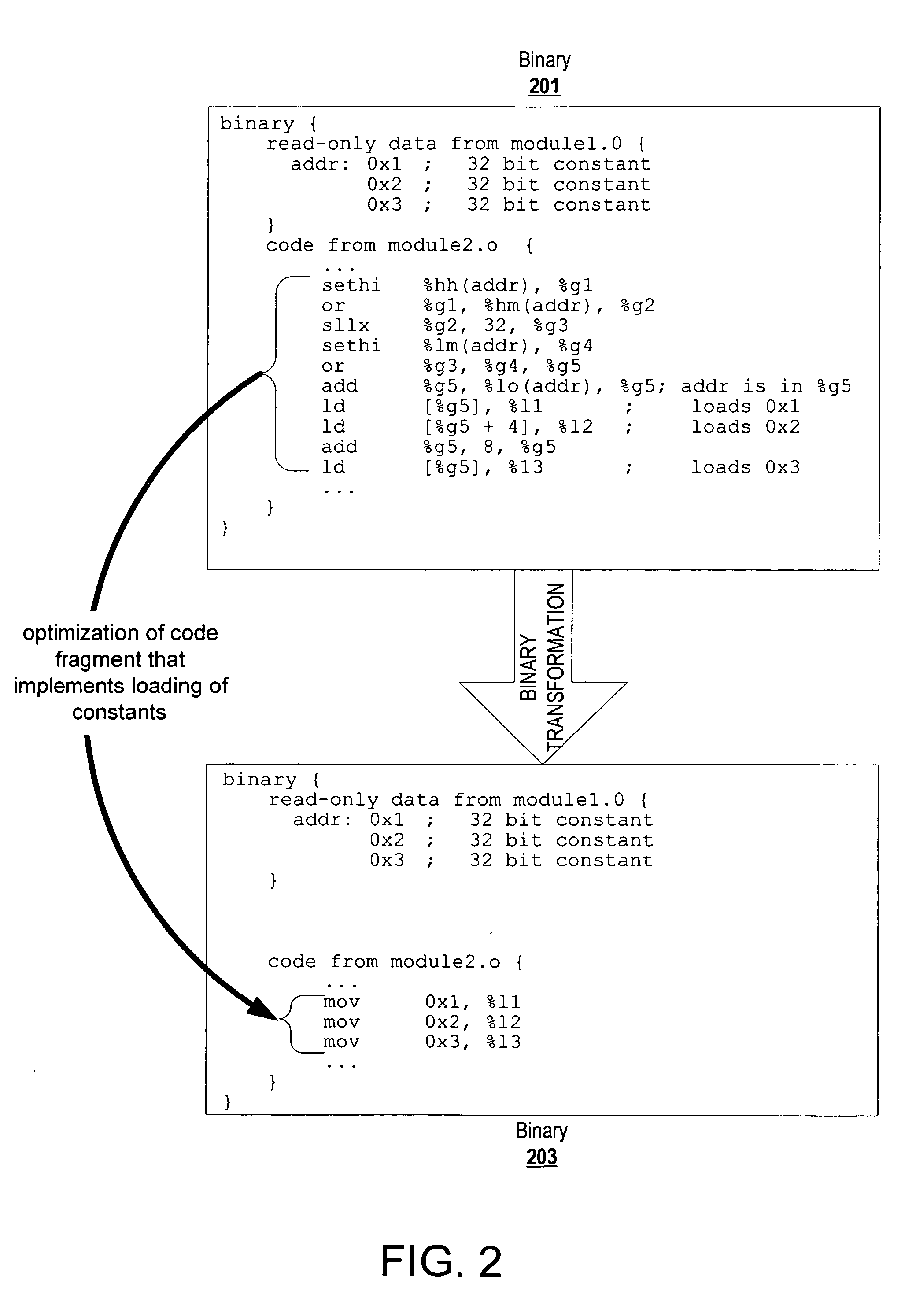
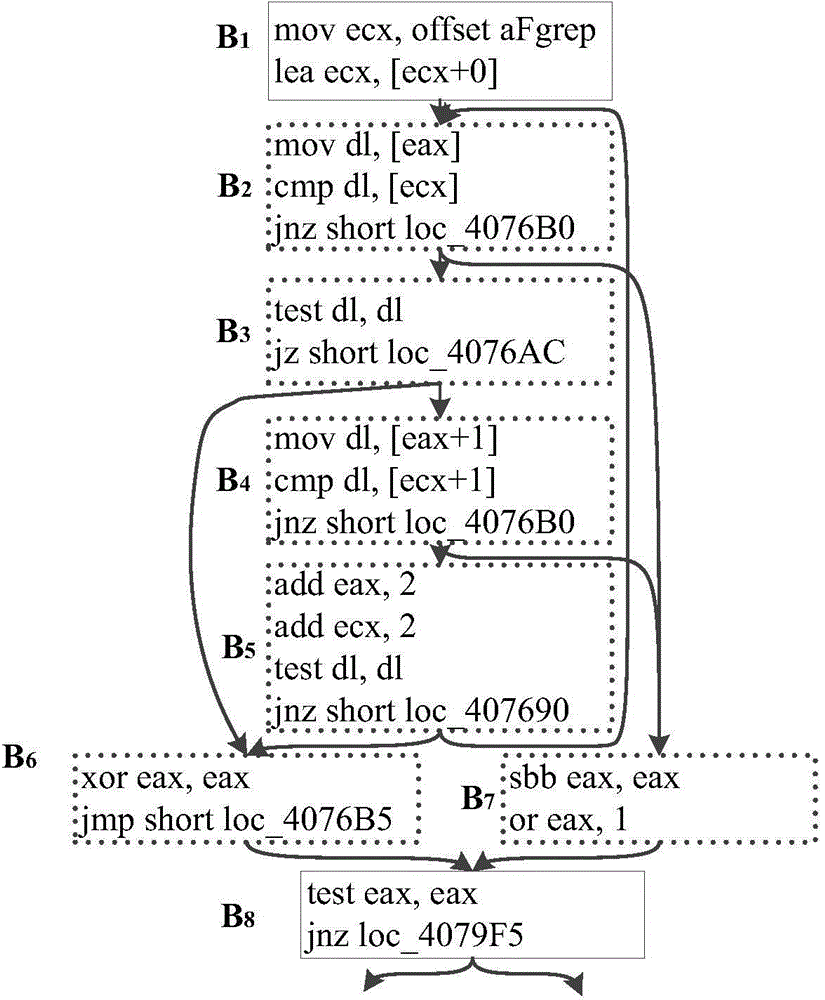
Code transformation to optimize fragments that implement constant loading
ActiveUS20070226717A1Relieve pressureEliminate operationSoftware engineeringSpecific program execution arrangementsConfiguration analysisInline function
Owner:ORACLE INT CORP
Detection of global metamorphic malware variants using control and data flow analysis
InactiveUS20120072988A1Easily defeatedSimple structureMemory loss protectionError detection/correctionData streamFeature extraction
Malware feature extraction derives semantic summaries of executable malware using global, inter-procedural program analysis techniques. A combination of global, inter-procedural program analysis techniques constructs semantic summaries of malware which automatically detect and discard any noise introduced by transformations and capture the essence of the underlying computations in a succinct form. This is achieved in two ways. First, global control flow analysis techniques are used to derive a high level representation of malware code that, for instance, removes the effects of subroutine calls. Second, global data flow analysis techniques are employed to detect and remove all spurious elements of malware that do not contribute towards its underlying computation, thereby preventing the resulting summaries from being “corrupted” with unnecessary, extraneous elements.
Owner:TT GOVERNMENT SOLUTIONS
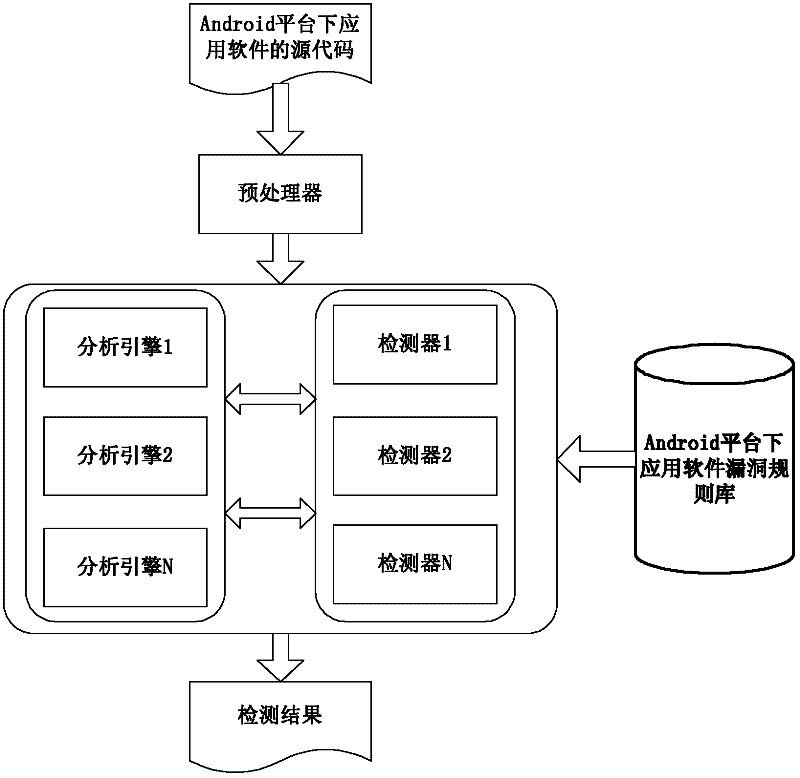
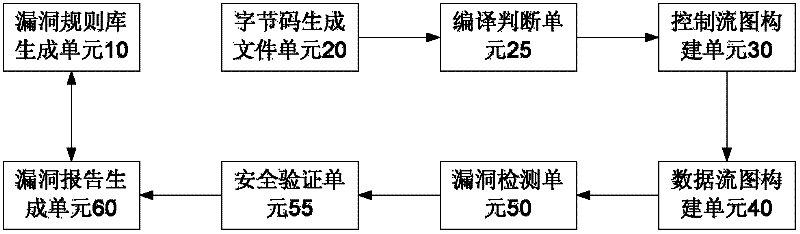
Safety loophole mining method and device of application software under Android platform
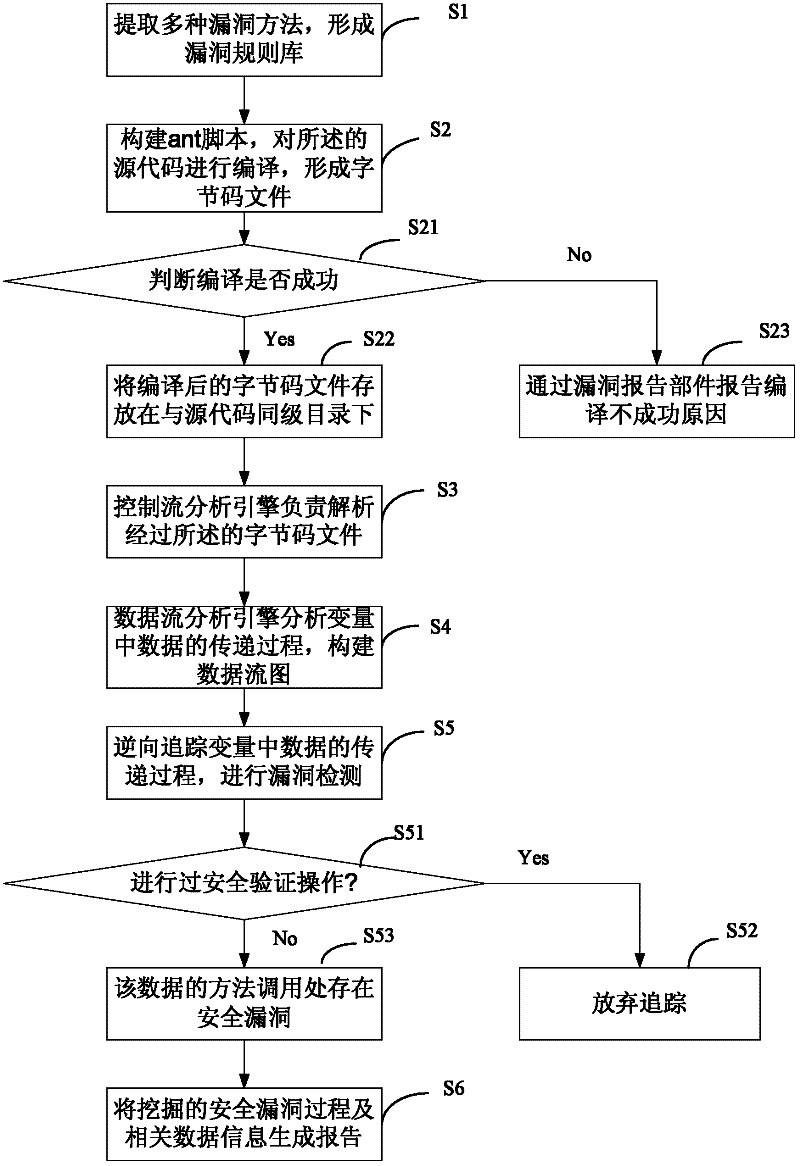
ActiveCN102411690AConducive to safe developmentPlatform integrity maintainanceData streamData information
The invention discloses a safety loophole mining method and device of application software under an Android platform. The safety loophole mining method comprises the following steps of: S1, extracting a plurality of loophole rules of source codes of application software under the Android platform to form a loophole rule library; S2, establishing an ant script, and compiling the source codes to form a bytecode file; S3, analyzing the bytecode file by using a control flow analysis engine; S4, analyzing a transmission process of data in variables by using a data flow analysis engine to establish a data flow diagram so as to provide basis for reverse dynamic data tracing; S5, carrying out loophole detection according to the rules in the loophole rule library; and S6, generating a report from a safety loophole mining process and related data information. The invention also discloses a safety loophole mining device of application software under the Android platform. The safety loophole mining method and device disclosed by the invention are beneficial to discovering safety loopholes in software as soon as possible and is also beneficial to safe development of application software under the Android platform.
Owner:CHINA INFORMATION TECH SECURITY EVALUATION CENT
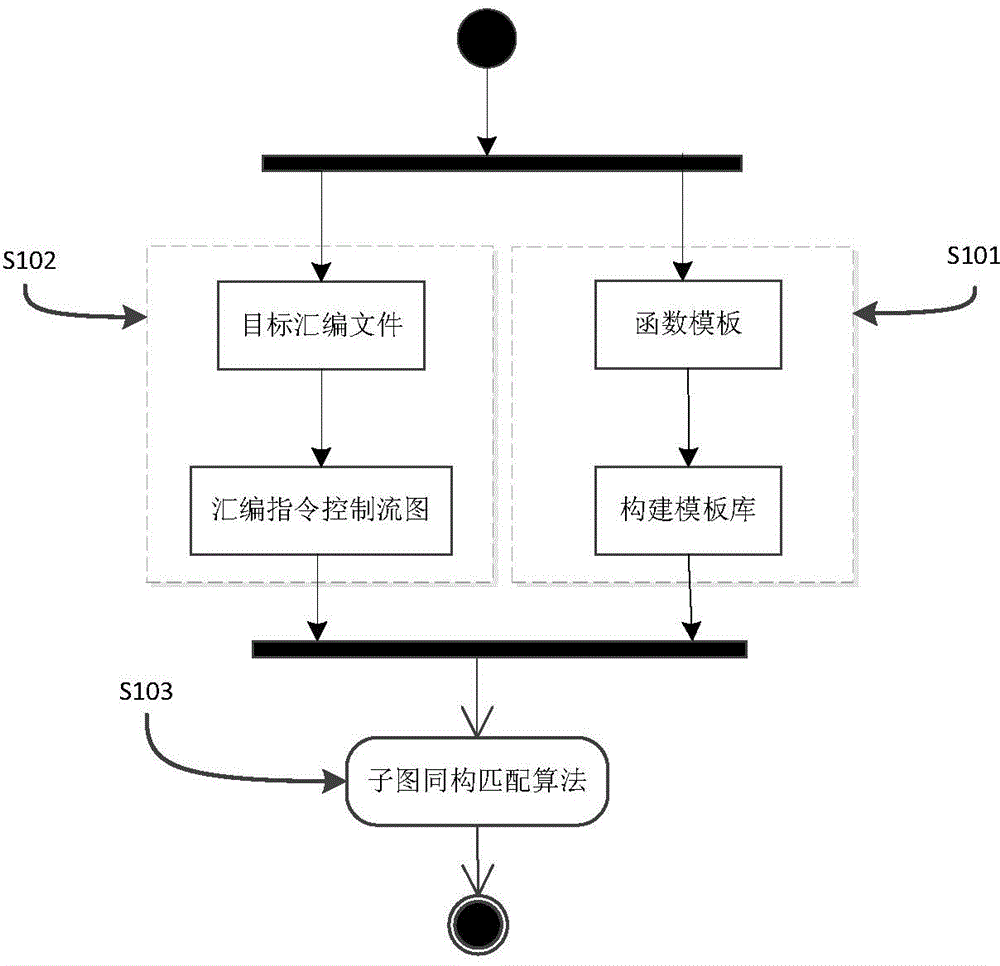
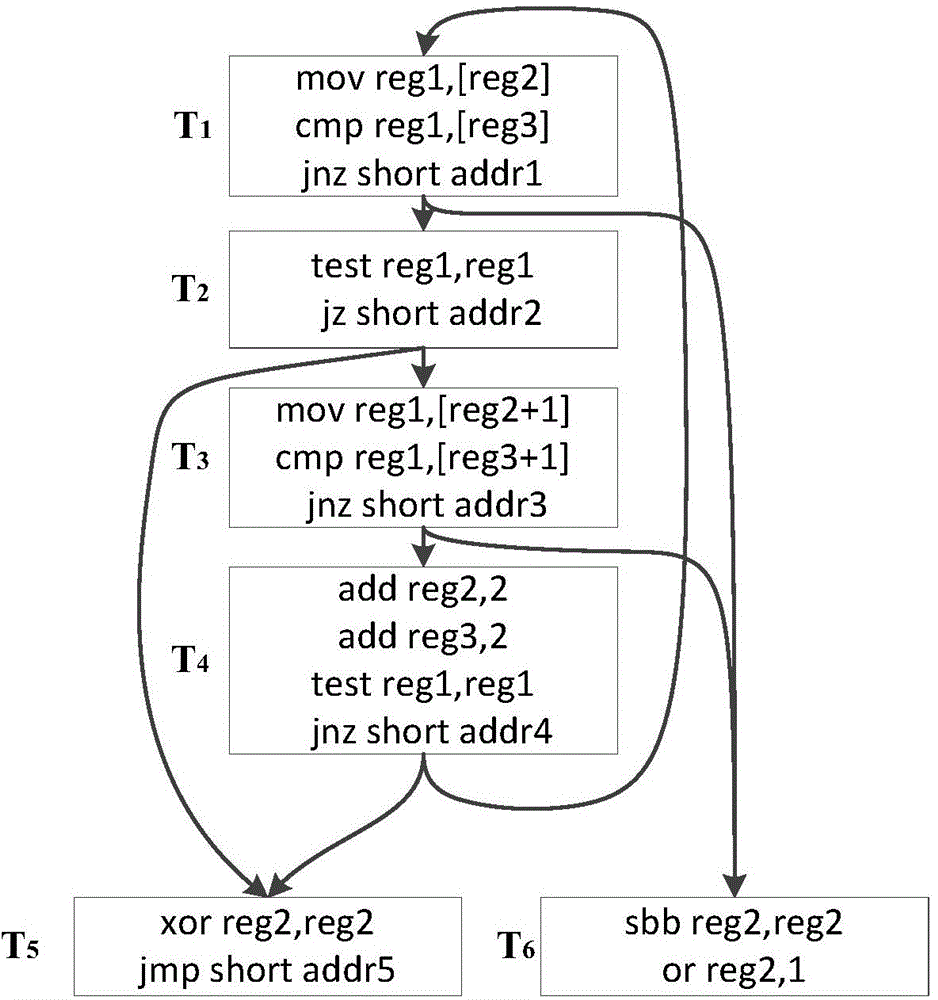
Intrinsic function recognition method based on sub-graph isomorphism matching algorithm in decompilation
InactiveCN104915211ARealize automatic identificationEfficient identificationSpecific program execution arrangementsTheoretical computer scienceInline expansion
The invention discloses an intrinsic function recognition method based on a sub-graph isomorphism matching algorithm in decompilation, and belongs to the technical field of decompilation. According to the method, an intrinsic function template library is established, sub-graph isomorphism matching is conducted on intrinsic function templates and target assembling files generated through decompilation on the basis of a control flow diagram, and intrinsic functions which are subjected to compiler optimization and inline expansion in target programs of the target assembling files are positioned. According to the intrinsic function recognition method, inline intrinsic functions in the decomplation process can be recognized automatically, meanwhile, the templates and prototypes of the intrinsic functions are analyzed, the function names, returned values, returned value types and function parameters of the intrinsic functions are recovered, and thus the purpose of promoting the semantics of the inline intrinsic functions is achieved. More type information is provided for type analysis in decompilation through the promoted inline intrinsic functions, the complexity of data flow analysis and control flow analysis is lowered, the level of abstraction of intermediate codes is improved, and the readability of decompilation results is enhanced.
Owner:XI AN JIAOTONG UNIV
Code transformation to optimize fragments that implement constant loading
ActiveUS7873952B2Software engineeringSpecific program execution arrangementsConfiguration analysisInline function
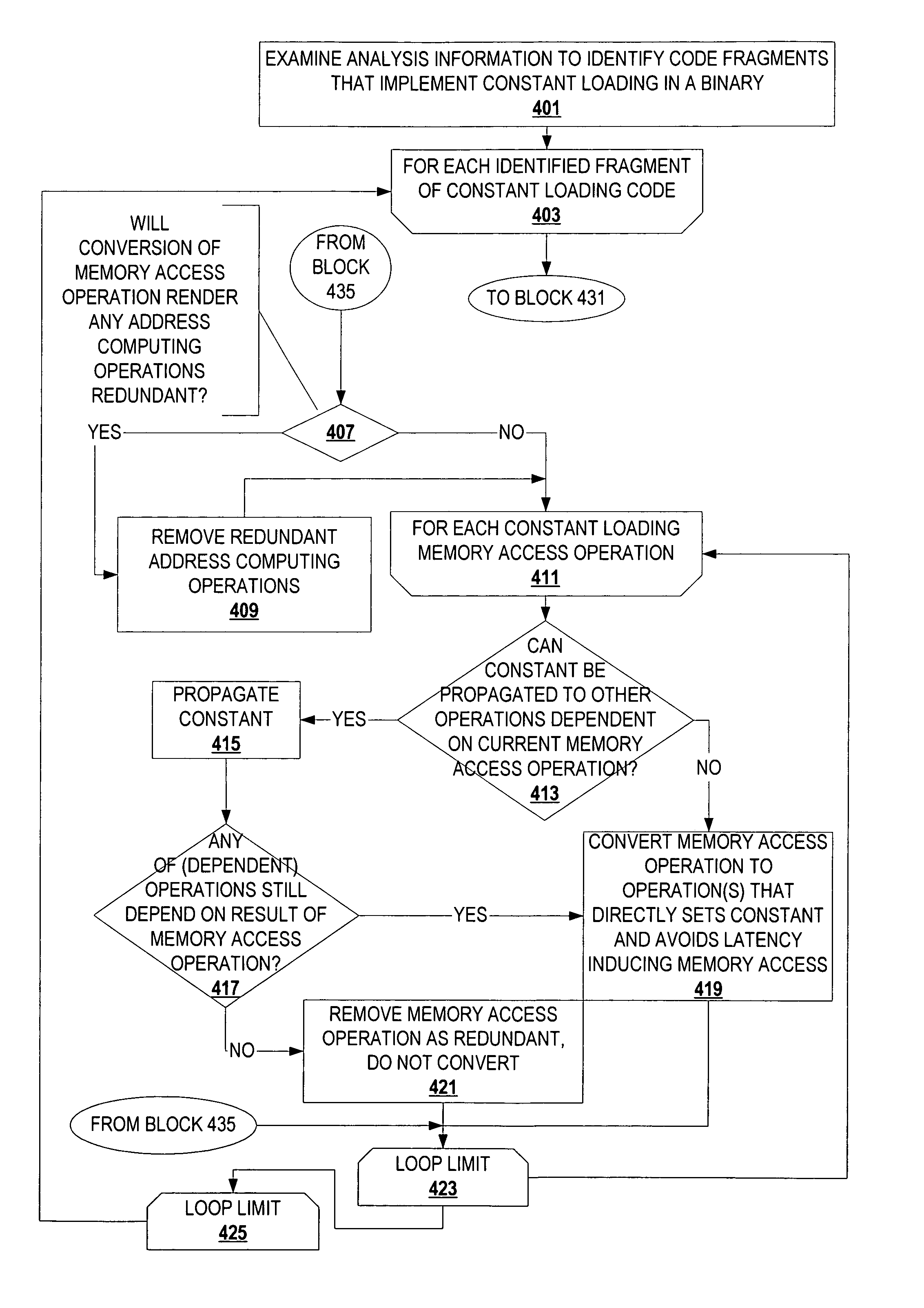
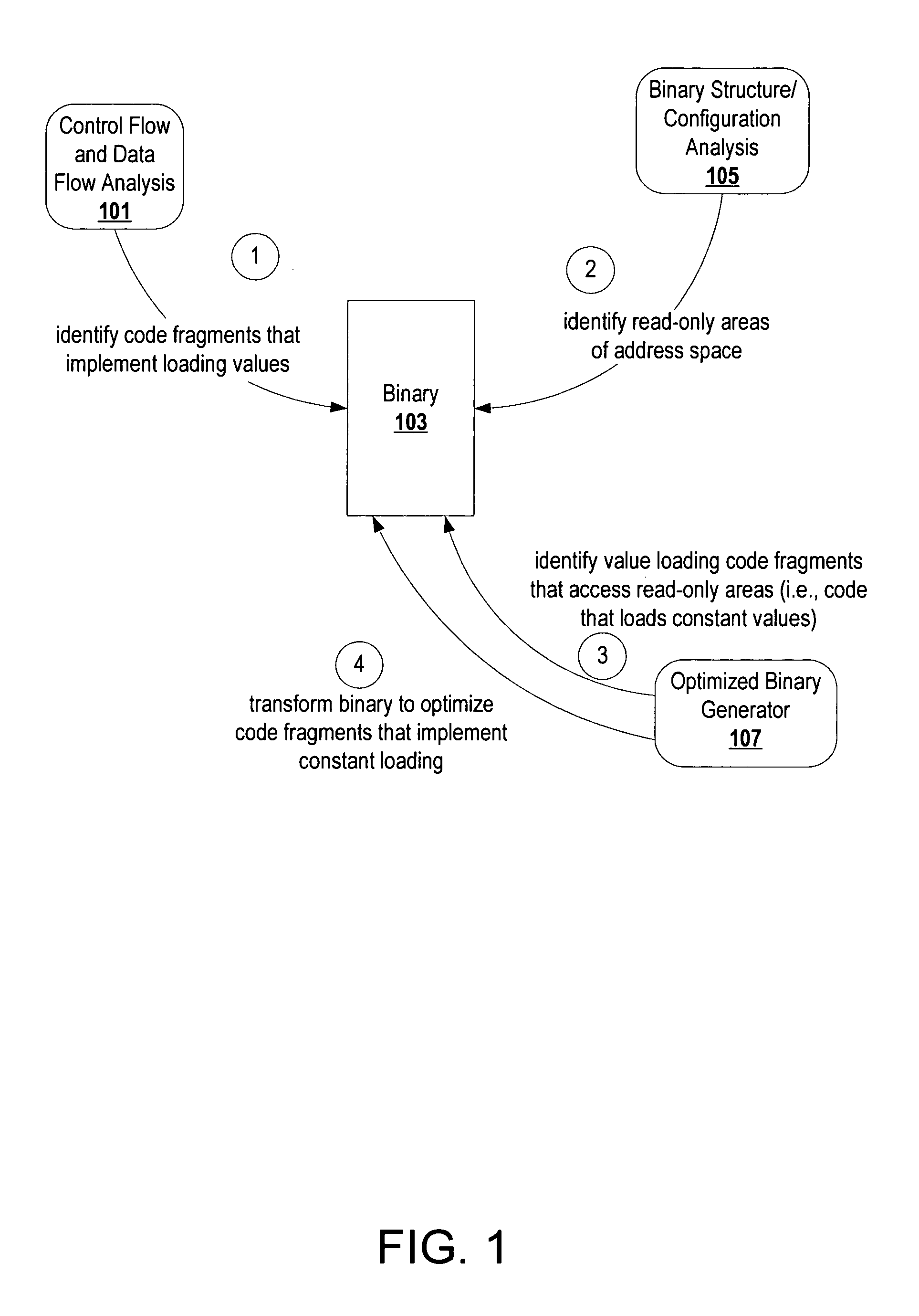
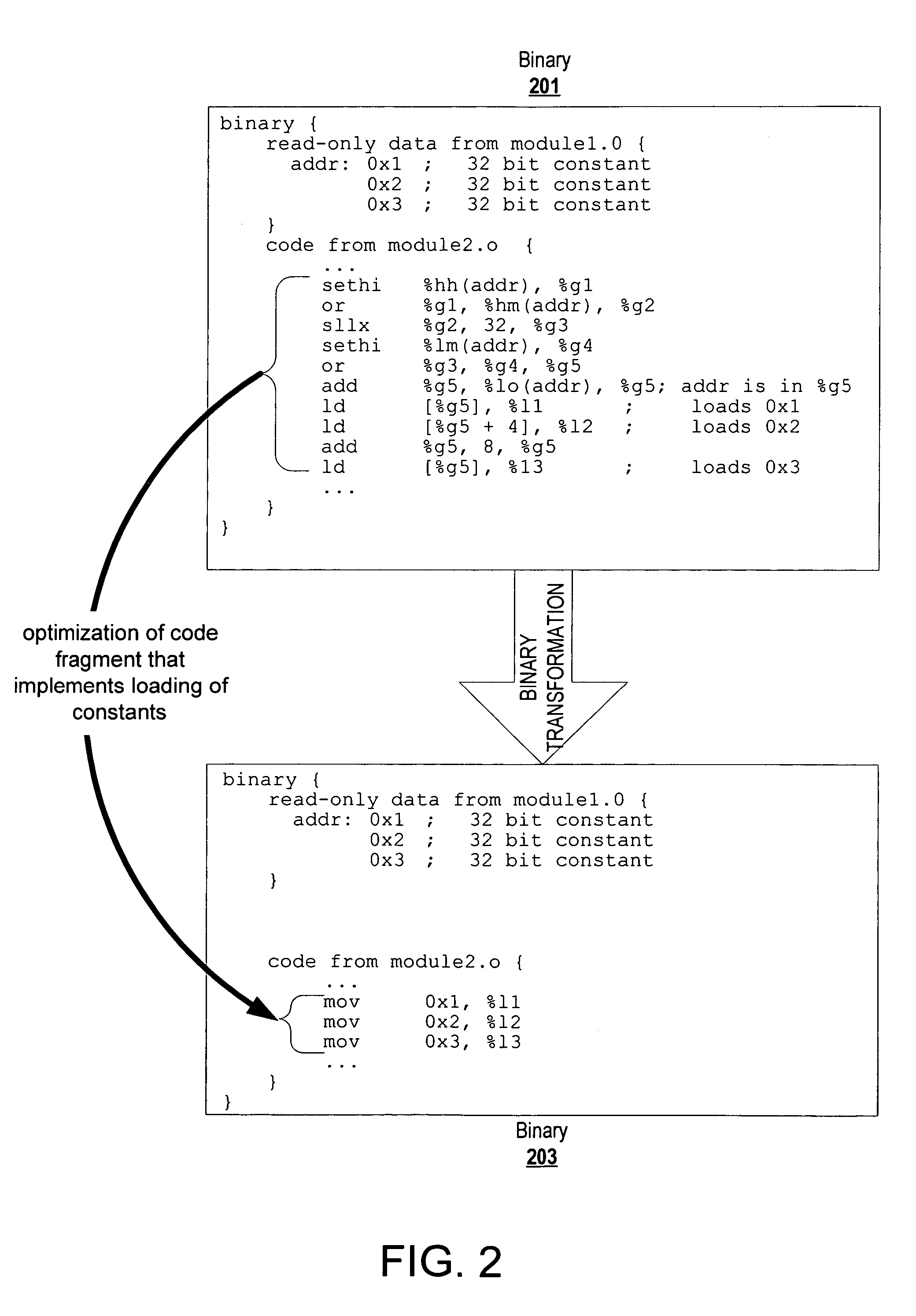
A code, which may be a post-link binary or a pre-link object file, can be transformed to optimize code fragments that implement loading a constant from memory. A constant loading code fragment includes address computing operations that compute (or copy) an address representation of a constant for consumption by a memory access operation, and the memory access operation that loads the constant. Information from control flow analysis, data flow analysis, and binary structure / configuration analysis are examined to identify code fragments of a code that implement constant loading. A tool transforms the code to convert the identified code fragments. To optimize, the tool may convert operations, eliminate operations, convert indirect calls to direct calls, inline functions called indirectly, eliminate unused constant data, modify relocations, etc. This optimization can also be applied recursively. The same tool or another tool can subsequently analyze the transformed code one more times to identify additional opportunities for optimizations revealed by the transformation or to apply the transformation for a different profile of the application.
Owner:ORACLE INT CORP
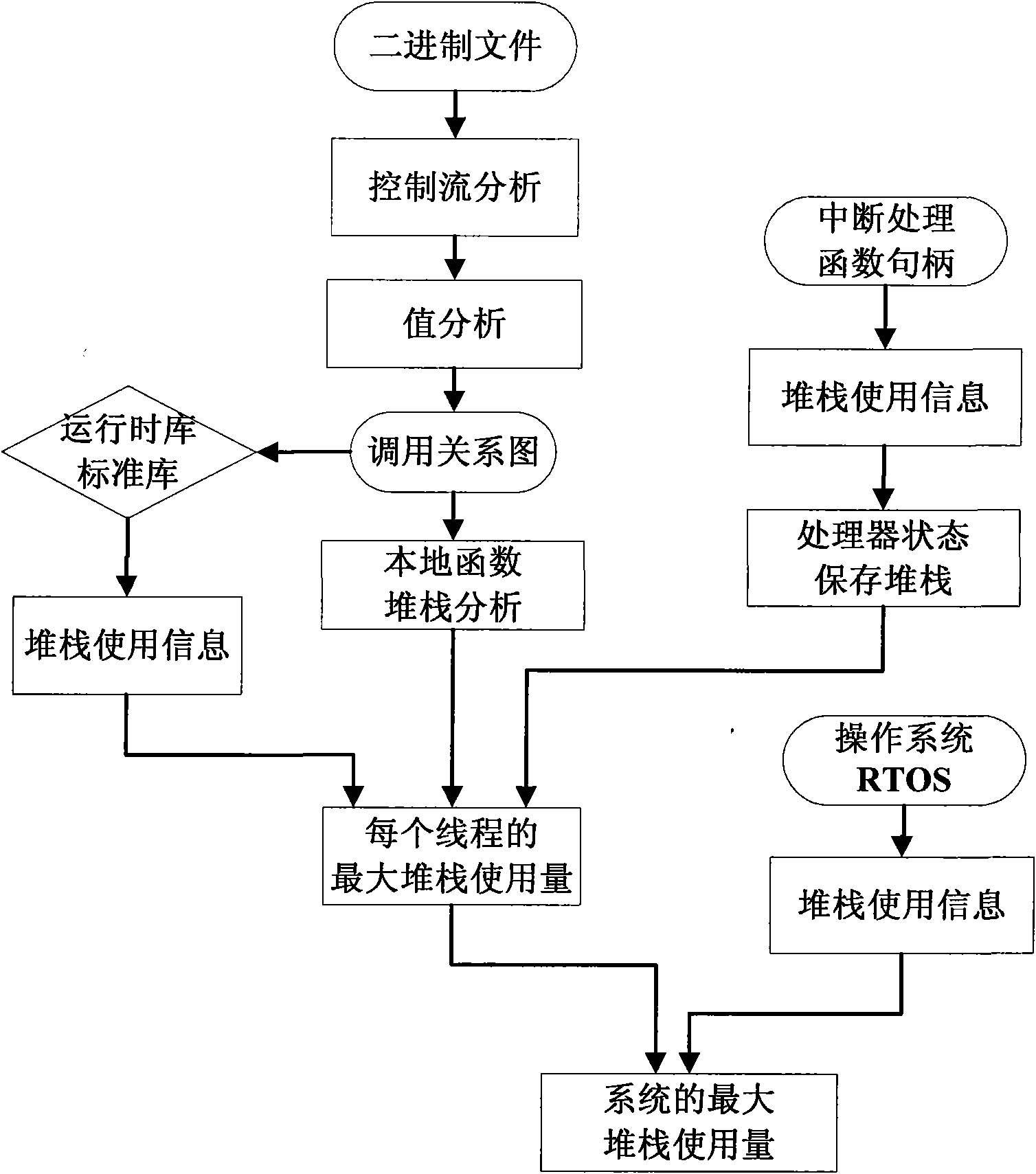
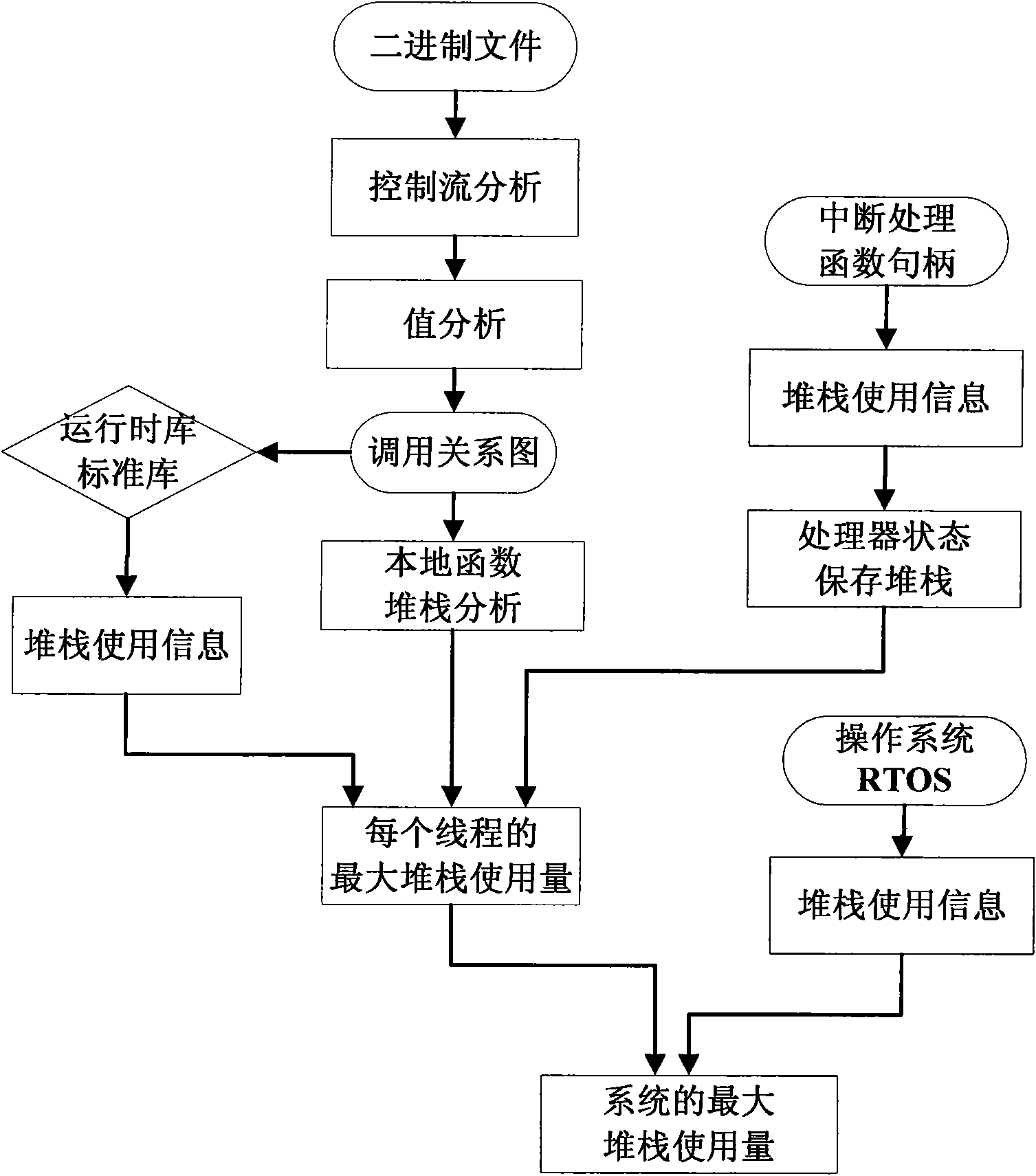
Method for accurately estimating stack demand in embedded system
InactiveCN101876923AGuarantee safety and reliabilityThe calculation result is accurateResource allocationMemory systemsOperational systemRelational graph
The invention provides a method for accurately estimating stack demand in an embedded system, which comprises the following steps of: performing stack demand analysis on the stack demand of a runtime library and a standard library of a local function and each call tree by using a complete function call relational graph, and summing; determining the maximum stack demand of each interrupt program in each priority level, summing, and adding the additional stack demand increased by saving the processor state; and summing the results to obtain the maximum stack demand of a single thread, wherein the complete function call relational graph is obtained by the following steps of: performing control flow analysis on a complete function relational graph to obtain a primary function relational graph, further analyzing by using a value analysis method of an abstract interpretation algorithm aiming at an indirect call function and a recursive call function, and noting function calls which cannot be analyzed by users. Aiming at multi-thread, a single thread step is repeated, a sum is calculated, and finally the sum plus the stack demand of the operation system is the total stack demand of the system.
Owner:INST OF ACOUSTICS CHINESE ACAD OF SCI
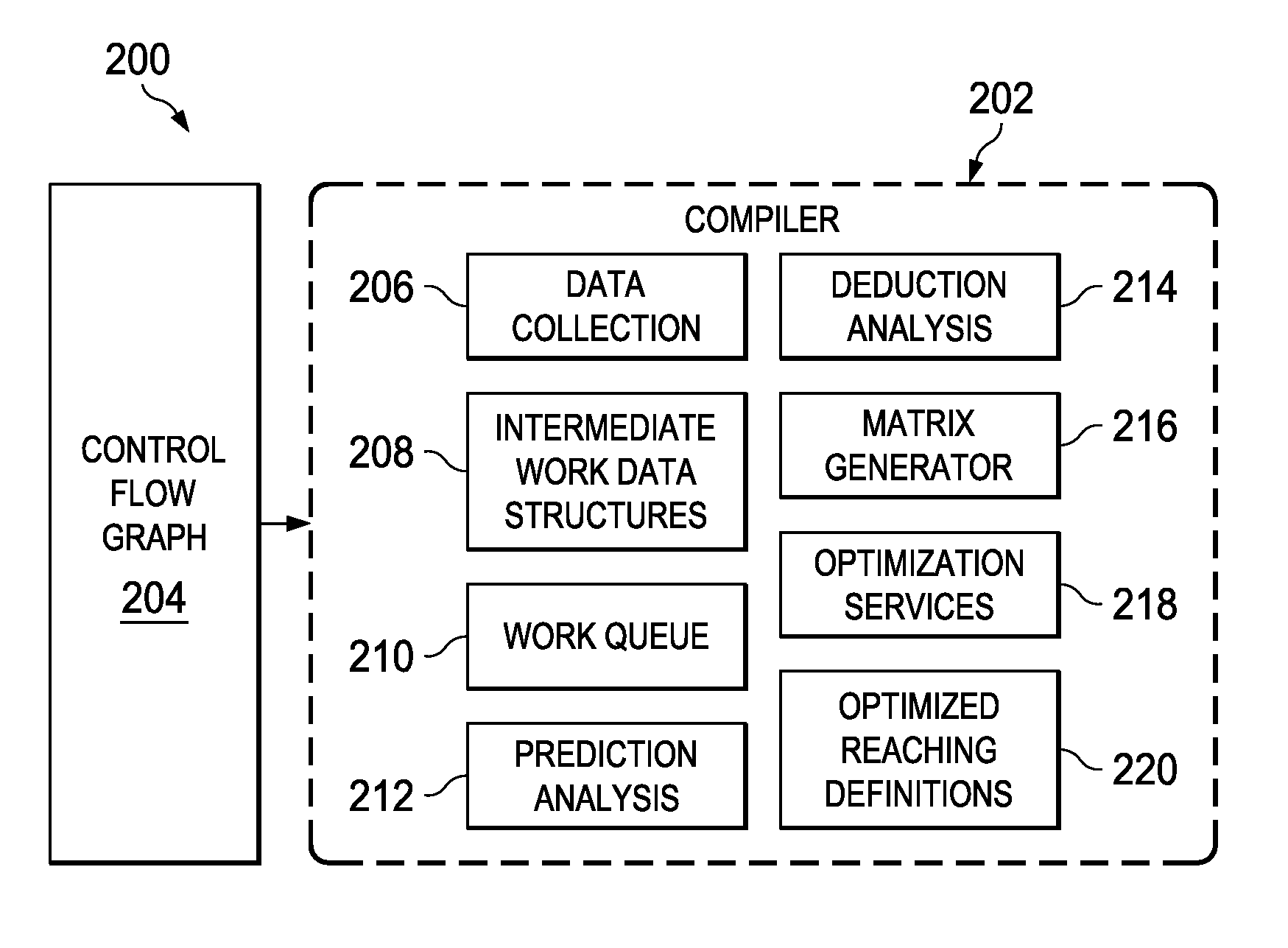
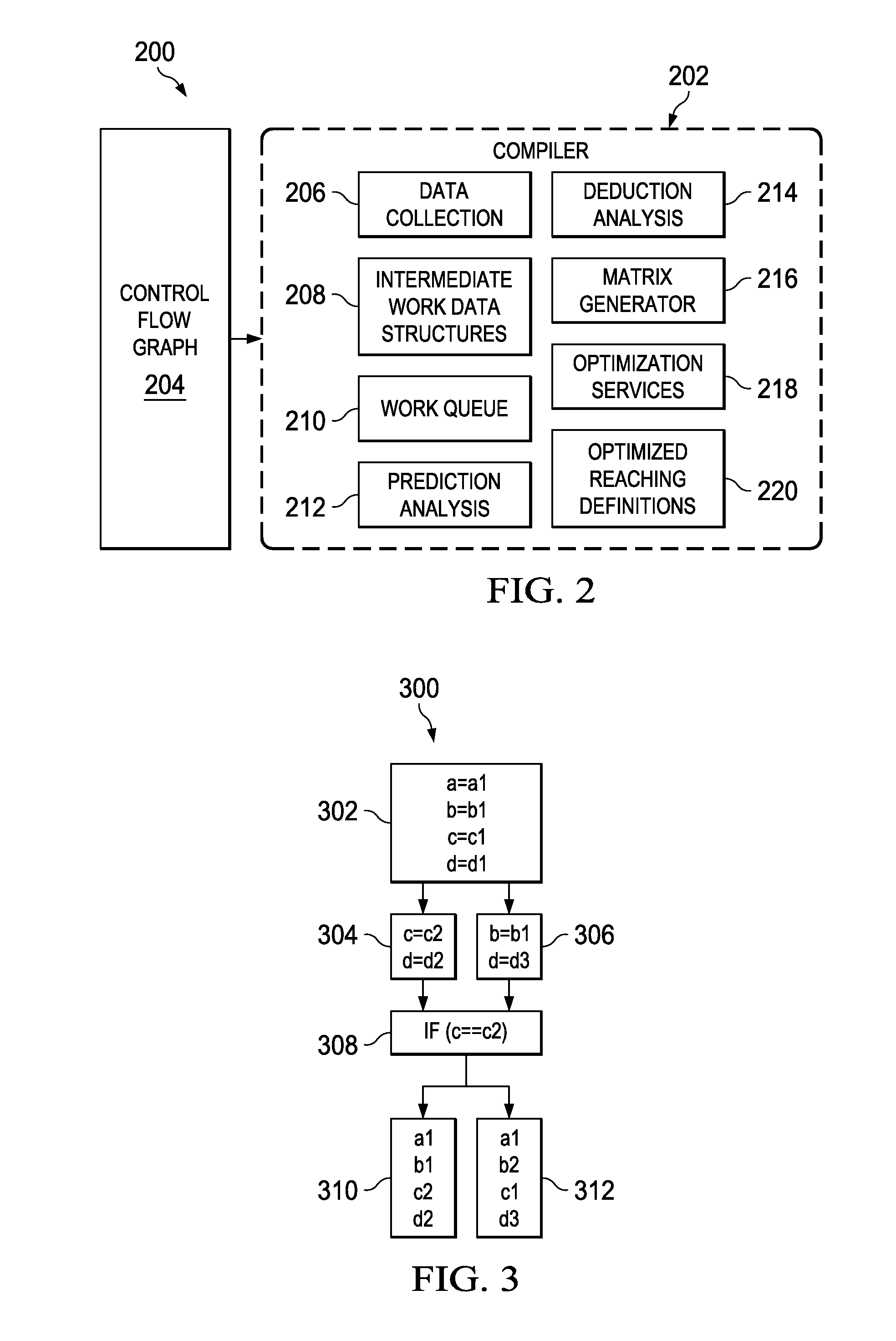
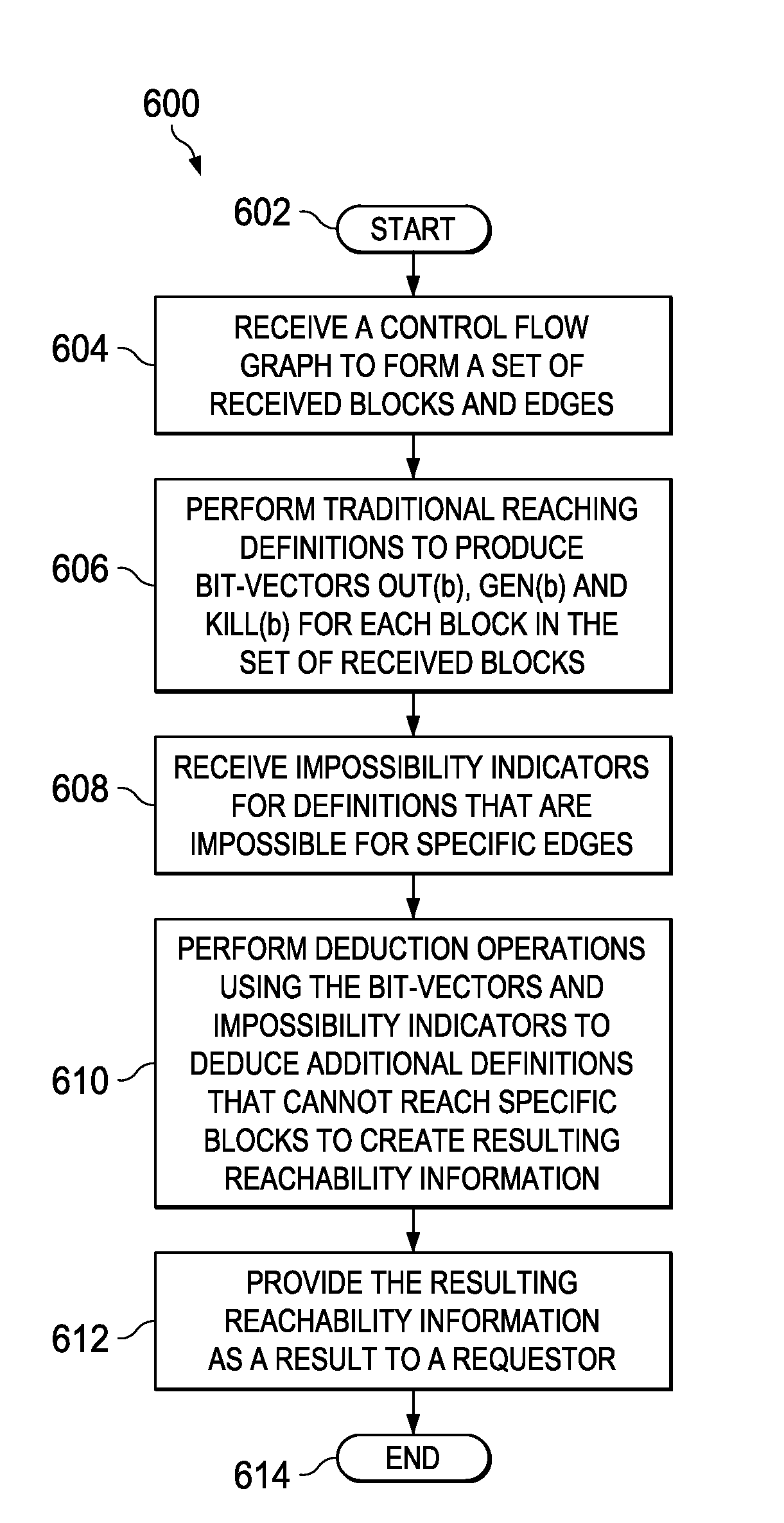
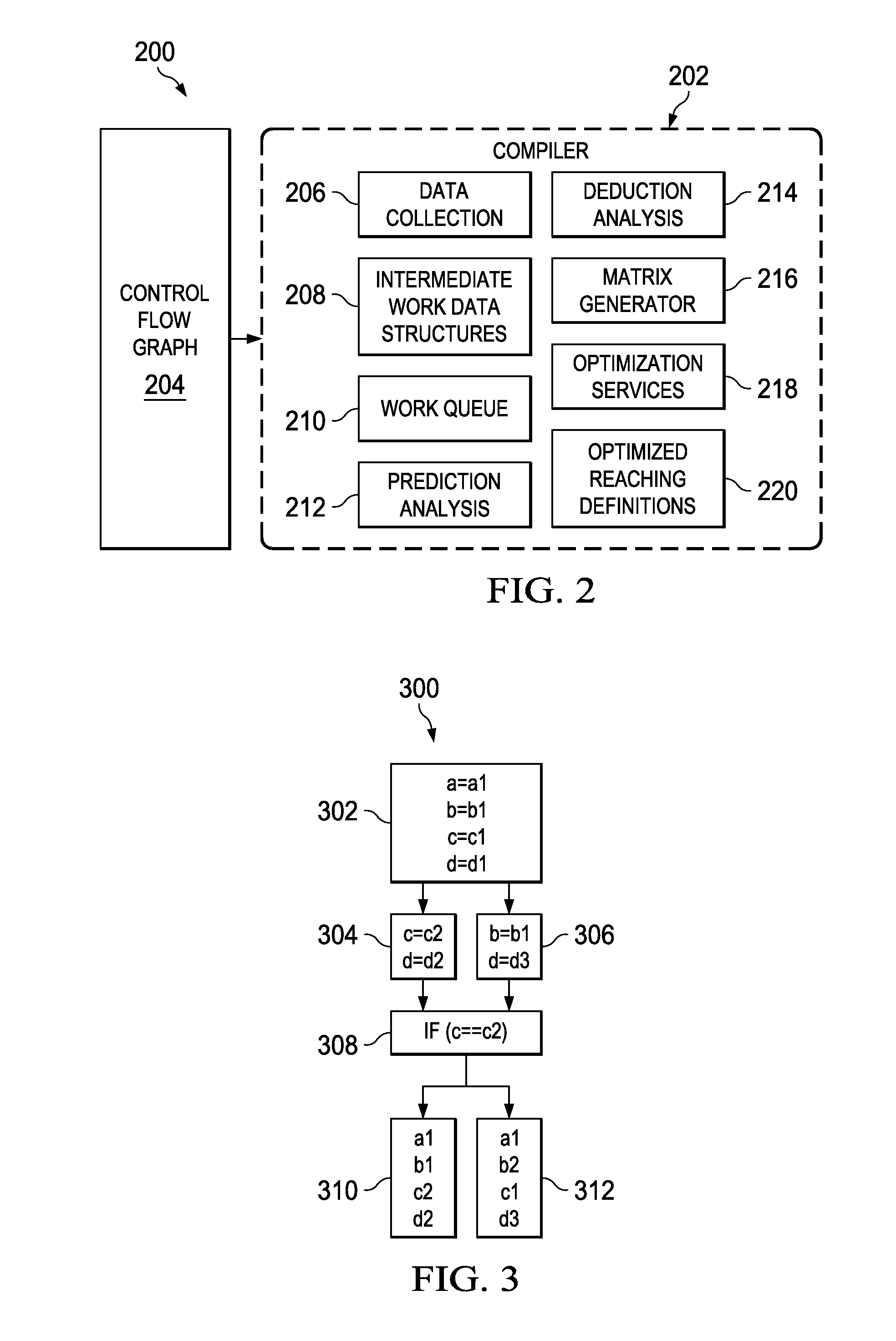
Control Flow Analysis Using Deductive Reaching Definitions
A computer-implemented process for deductive reaching definition analysis receives a control flow graph to form a set of received blocks and edges, performs traditional reaching definitions to produce bit-vectors OUT(b), GEN(b) and KILL(b) for each block in the set of received blocks and receives impossibility indicators for a set of definitions that are impossible on specific edges. The computer-implemented process further performs deduction operations using a combination of the bit-vectors and impossibility indicators to deduce that additional definitions cannot reach certain blocks to create resulting reachability information and provides the resulting reachability information as a result to a requestor. A related system and program product is also provided.
Owner:IBM CORP +1
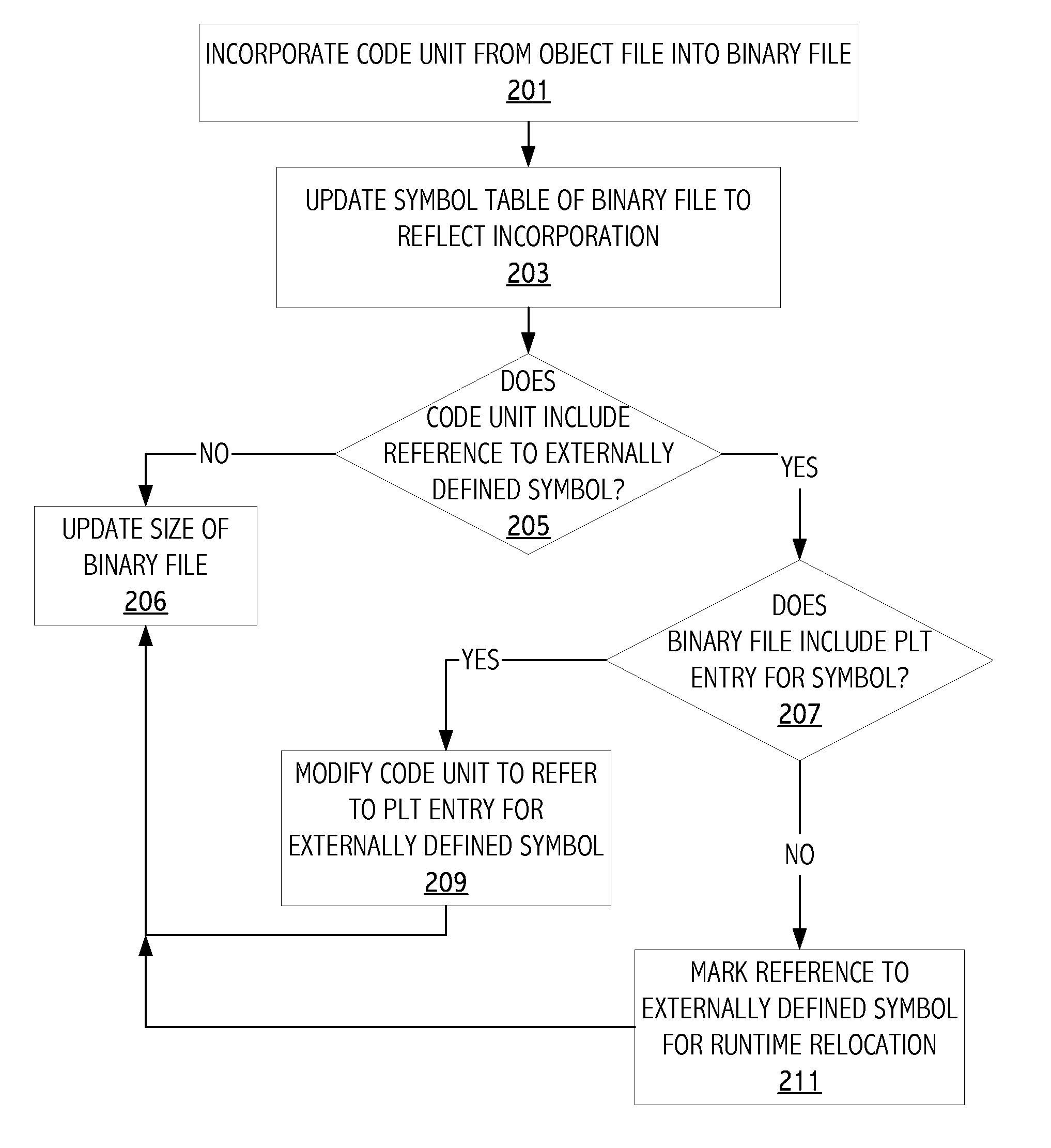
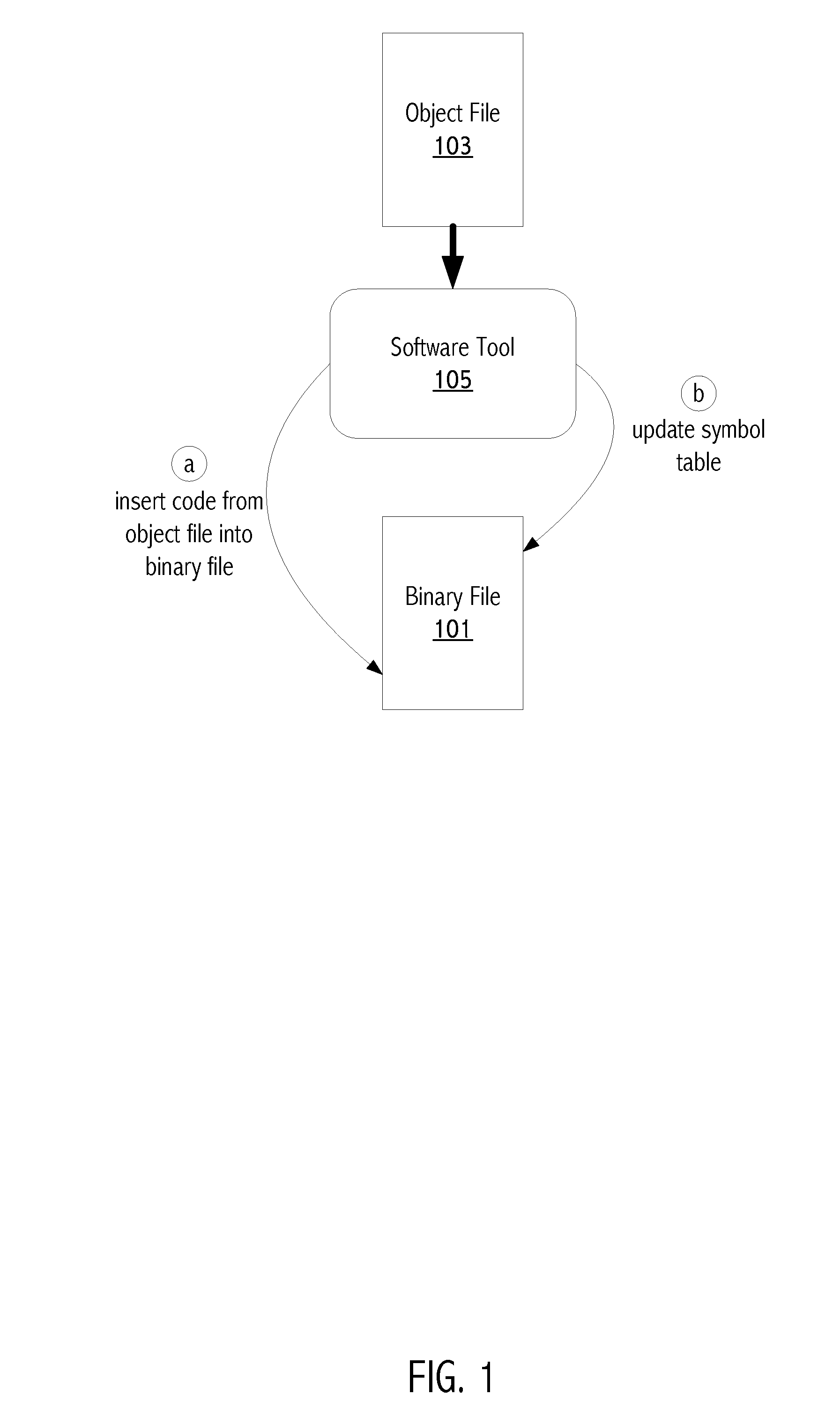
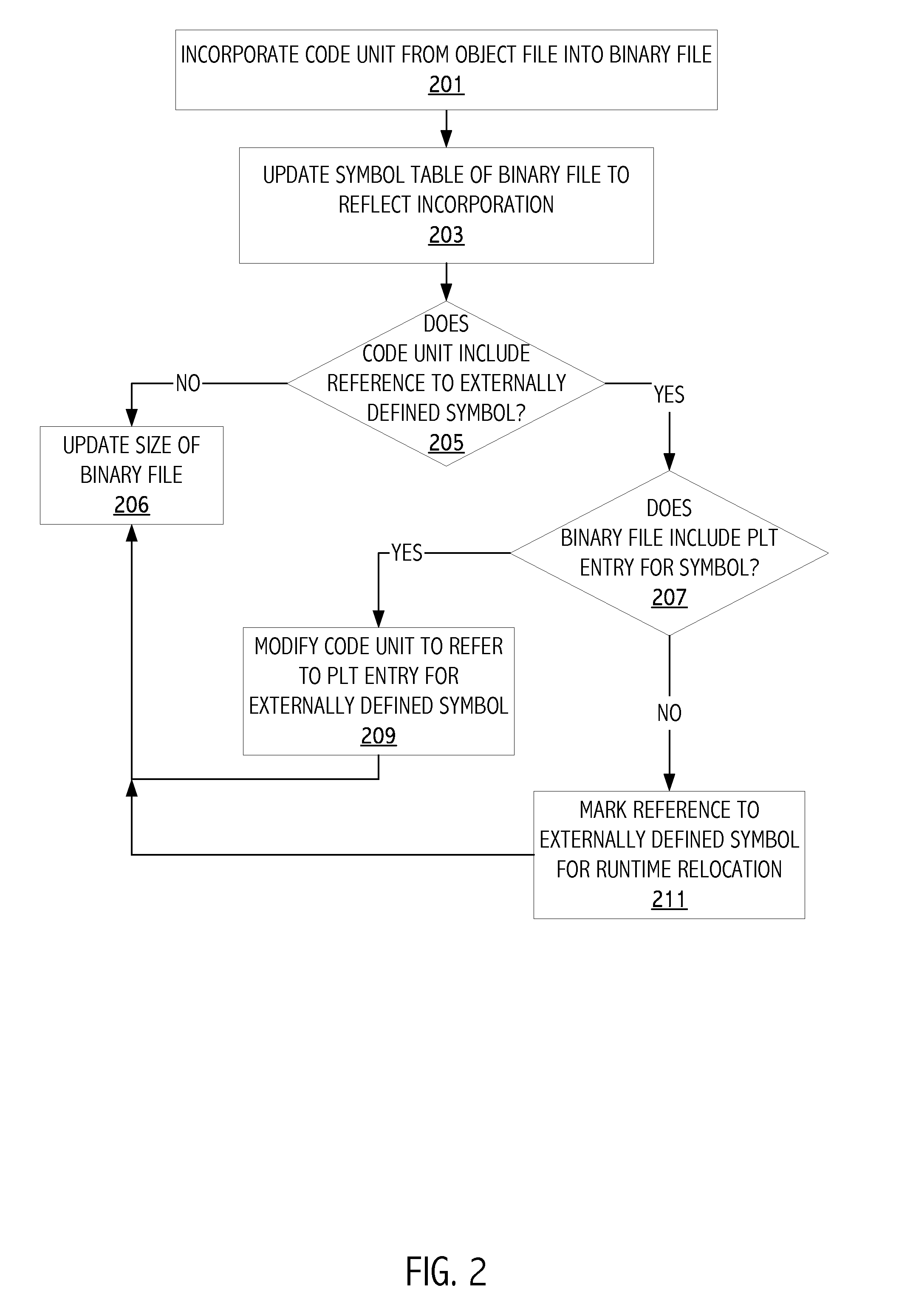
Incorporating functionality from an object file into an existing binary file
ActiveUS20080092129A1Extending and modifying functionalitySoftware engineeringSpecific program execution arrangementsProgramming languageControl flow analysis
Functionality from an object file can be incorporated into an already existing binary file. Functions from the object file can be intelligently inserted into the binary file with the guidance of control flow analysis of both the binary file and the object file. Symbols not defined in the symbol table of the binary file are added to the symbol table of the binary file. When symbols of the object file and the binary file overlap, then priority is given to the object file symbol definitions. The ability to incorporate functionality from an object file into an existing binary file reduces logistical overhead and provides flexibility in code development and maintenance.
Owner:ORACLE INT CORP
Java program static analysis method based on control flow analysis and data flow analysis
ActiveCN105608003AImprove analysis efficiencyFast executionSoftware testing/debuggingExtensibilityData stream
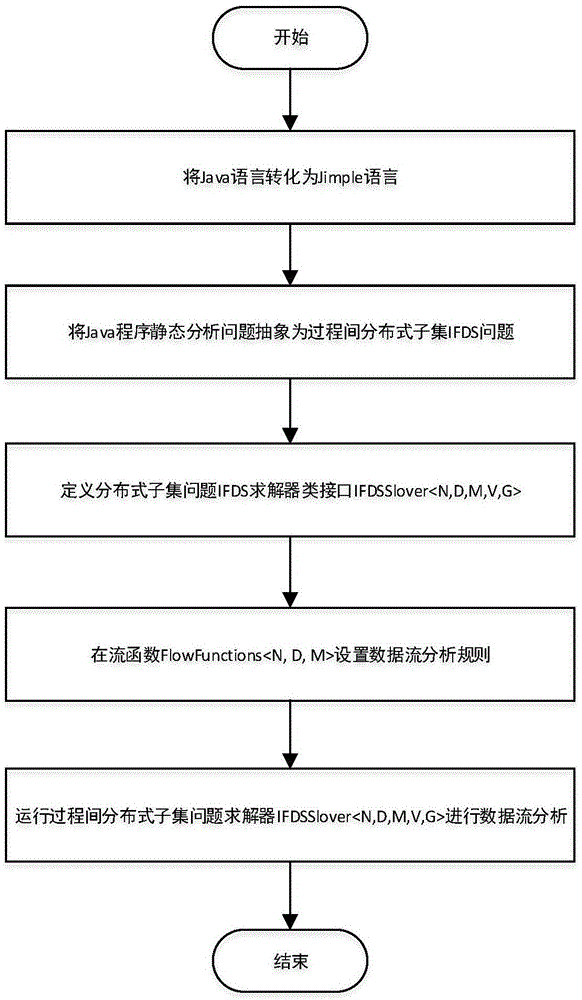
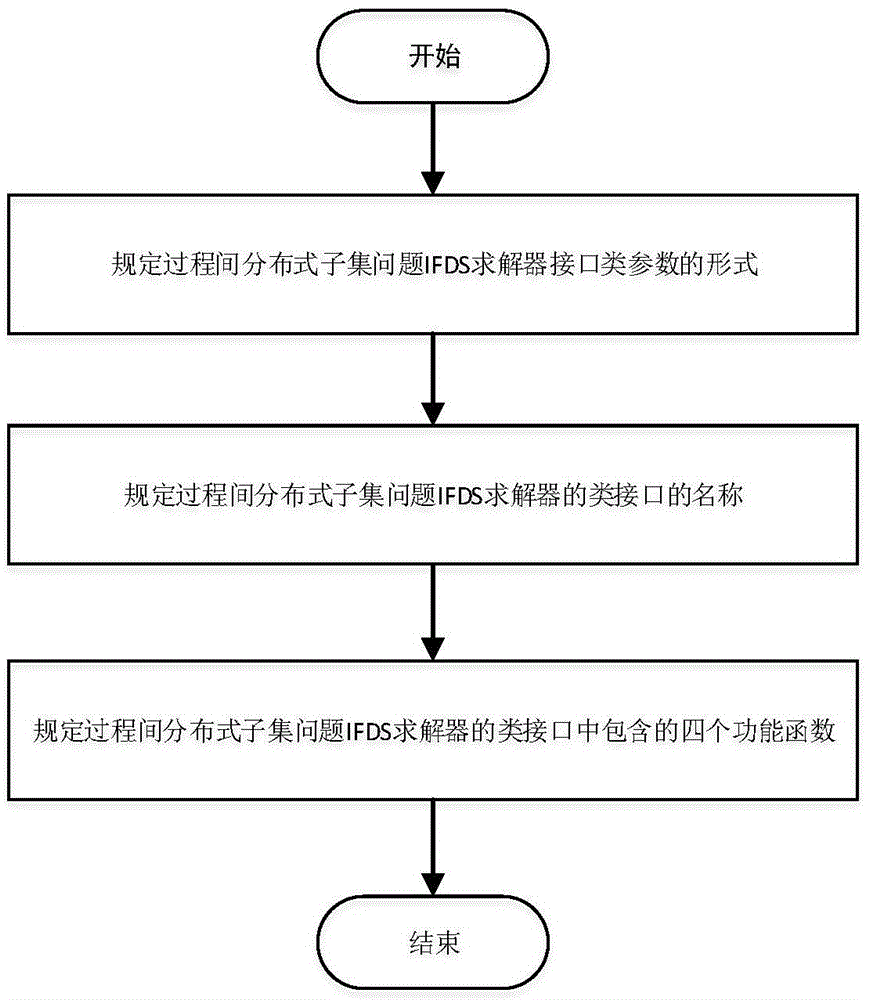
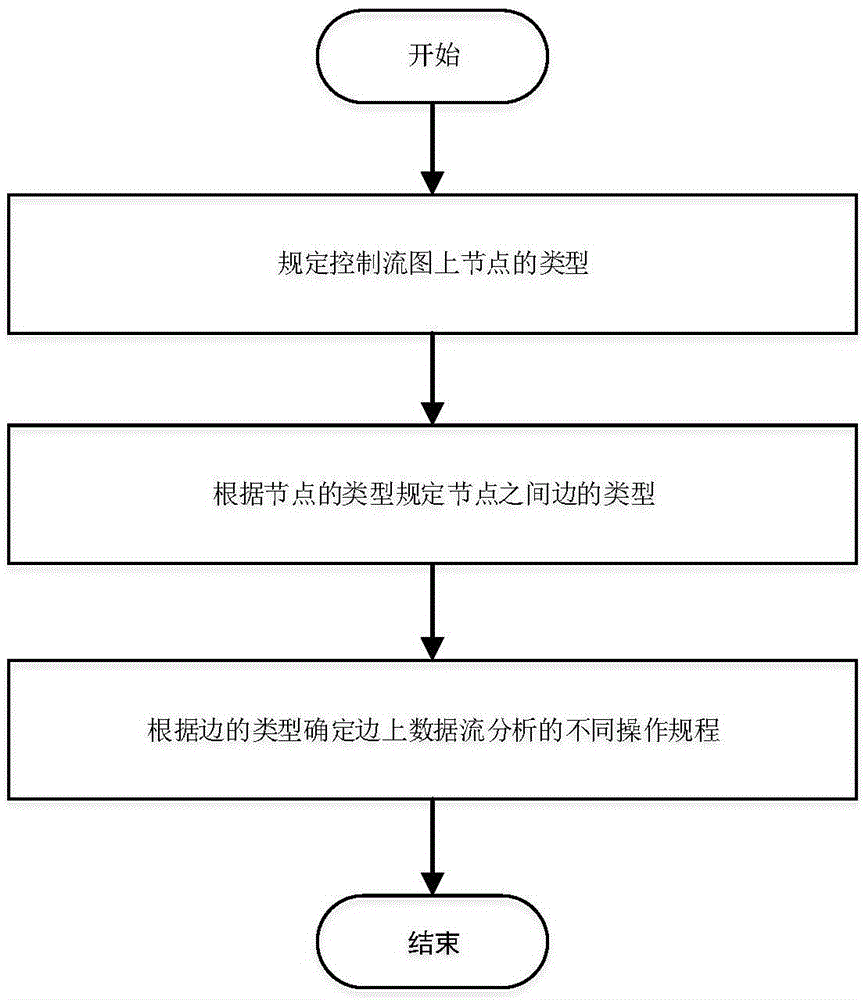
The present invention discloses a Java program static analysis method based on control flow analysis and data flow analysis, so as to mainly solve the problem of a low analysis accuracy rate of the conventional static analysis method. The implementation steps of the method are as follows: 1. transforming a Java source program into an intermediate expression form of a Jimple language; 2. abstracting a Java program static analysis problem into an interprocedural distributive subset IFDS problem; 3. defining an interface class of a solver of the interprocedural distributive subset IFDS problem; 4. by means of a data flow functional function FlowFunctions<N,D,M> in a solver class interface, setting a data flow analysis rule; and 5. running the interprocedural distributive subset IFDS problem, and performing data flow analysis on the basis of a control flow graph, so as to obtain an analysis result. The method disclosed by the present invention improves integrity and accuracy of static analysis, and the method is high in analysis efficiency and strong in extensibility and can be used for performing analysis on programs in a relatively large system scale.
Owner:XIDIAN UNIV
Method for detecting Java source code insecure input loophole
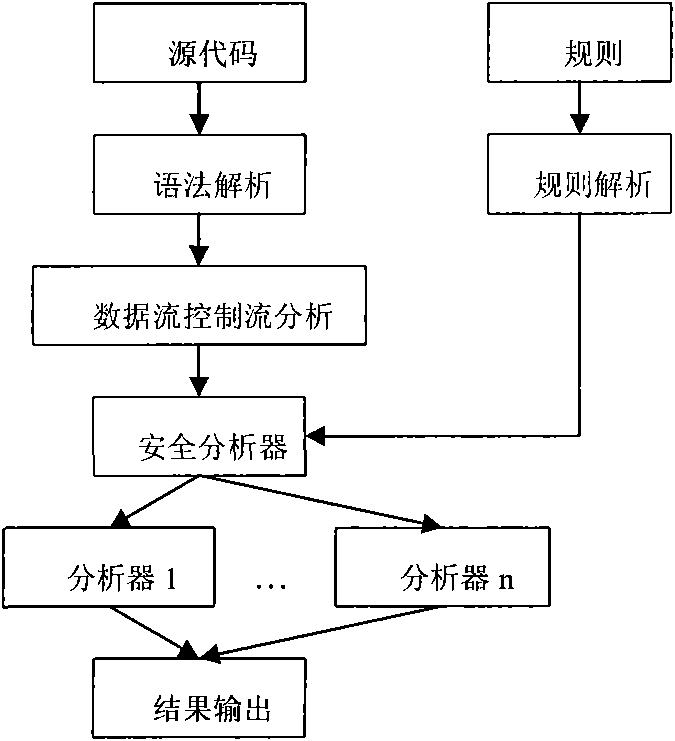
The method provides a new method for detecting Java source code security loophole caused by insecure input. The method adopts the parsing and data and control flow analysis technology and achieves the purpose of detecting different types of loopholes by calling a security analyzer through security rules. Proved by tests, the method can be used for scanning various engineering source codes developed in java language and achieves higher accuracy rate.
Owner:牛婷芝
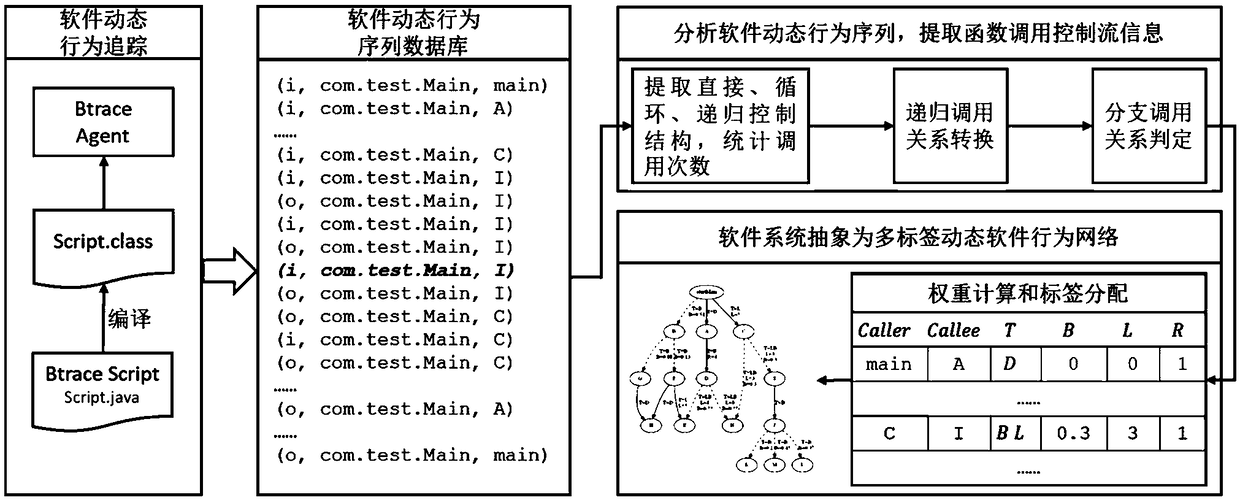
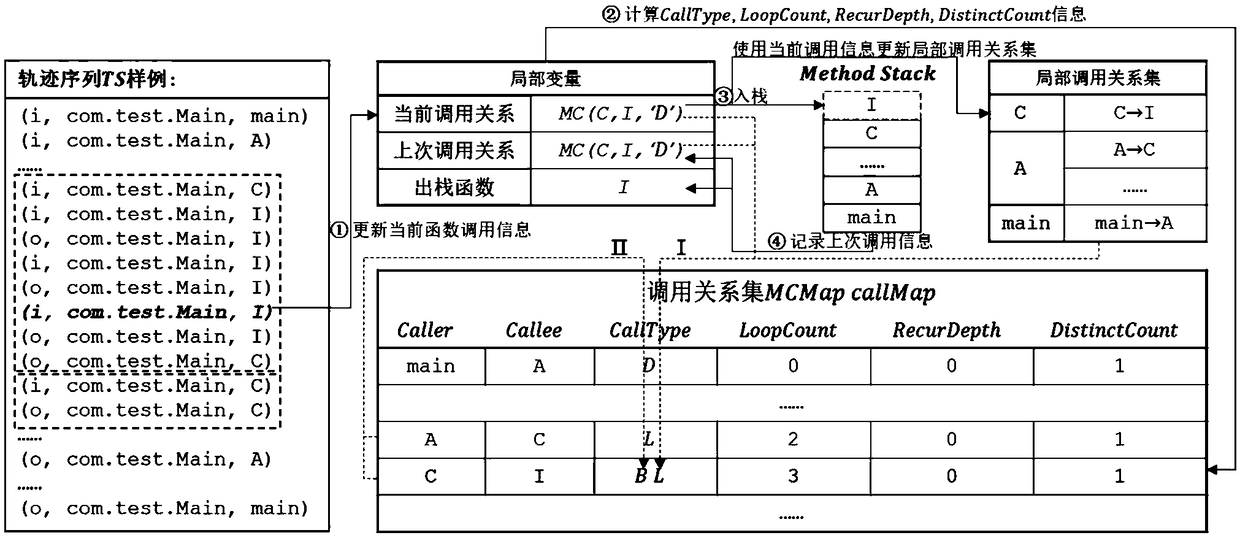
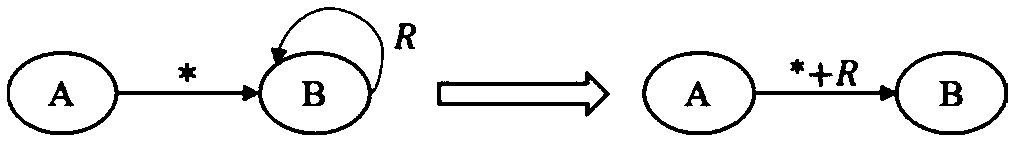
Software dynamic behavior modeling method and device based on control flow analysis
ActiveCN108628600ARealize control structure identification functionScientific descriptionSoftware designSoftware metricsSoftware systemSequence database
The invention discloses a software dynamic behavior modeling method and a software dynamic behavior modeling device based on control flow analysis. This method traces the function execution trajectoryof software dynamic execution process, establishes a software dynamic behavior sequence database described by function execution; analyzes the software dynamic behavior sequence, extracts the function call logic relation and the function call statistics to form function call control flow information; and abstract the software system into a multi-label dynamic software behavior network model according to the function call control flow information. From the angle of control flow analysis and statistics, combined with the theory method of complex network, the dynamic calling relation of the software function is analyzed in a more comprehensive and detailed way and the software behavior can be expressed and measured in a more comprehensive and scientific way.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY +1
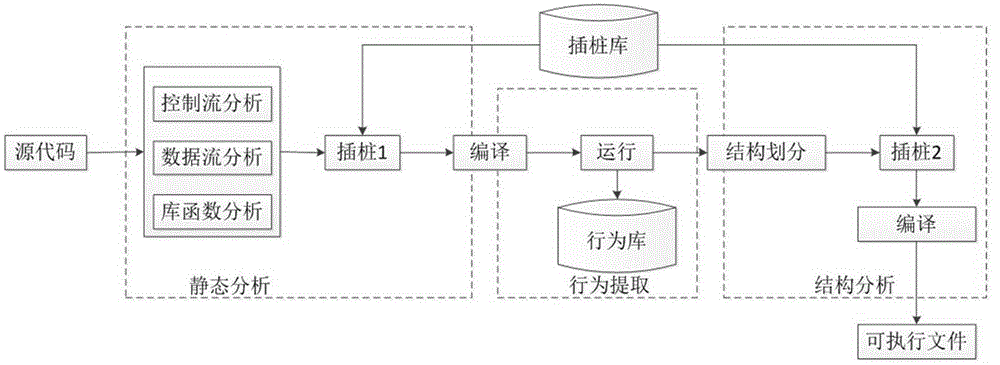
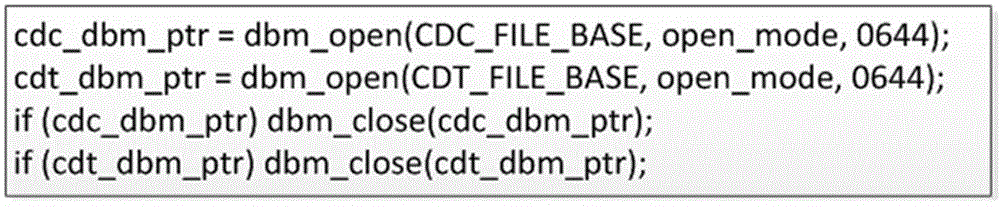
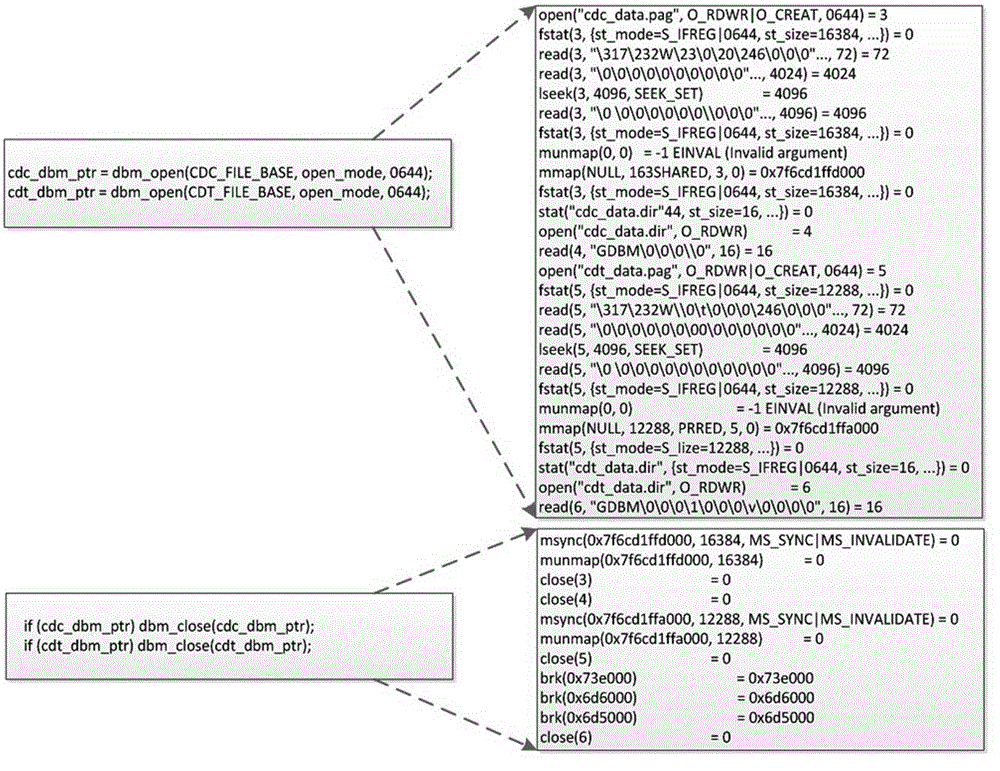
Instrumentation based program behavior acquisition and structural analysis method
ActiveCN105183642AStructural awarenessGood behavior acquisition abilitySoftware testing/debuggingData streamStructural analysis
The present invention relates to an instrumentation based program behavior acquisition and structural analysis method. The program behavior acquisition and structural analysis method comprises the following steps of: step 1. static analysis: performing control flow analysis, data flow analysis and library function analysis on a program, performing analysis on functions of the program, determining a scope of each function of the program, analyzing a structure of the program, determining an initial instrumentation position of the program, and performing a first-pass instrumentation; step 2. program behavior extraction: performing simulation execution on the program subjected to the first-pass instrumentation, extracting a program behavior in a library function running process according to a flag bit of a pile function, and storing the program behavior into a behavior library; and step 3. program behavior analysis: performing partitioning on structural characteristics shown in a program running process according to a structural partitioning rule, and performing a second-pass instrumentation, and finally performing compiling to obtain an executable file. The instrumentation based program behavior acquisition and structural analysis method provided by the present invention has an excellent software behavior acquisition ability and structural analysis ability.
Owner:THE PLA INFORMATION ENG UNIV
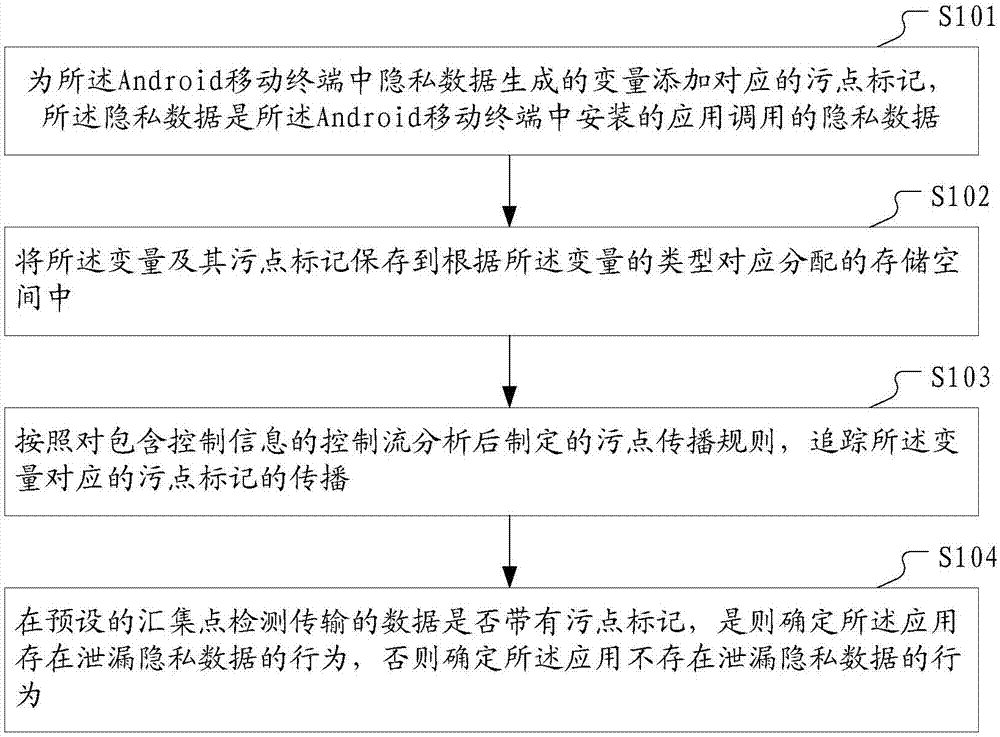
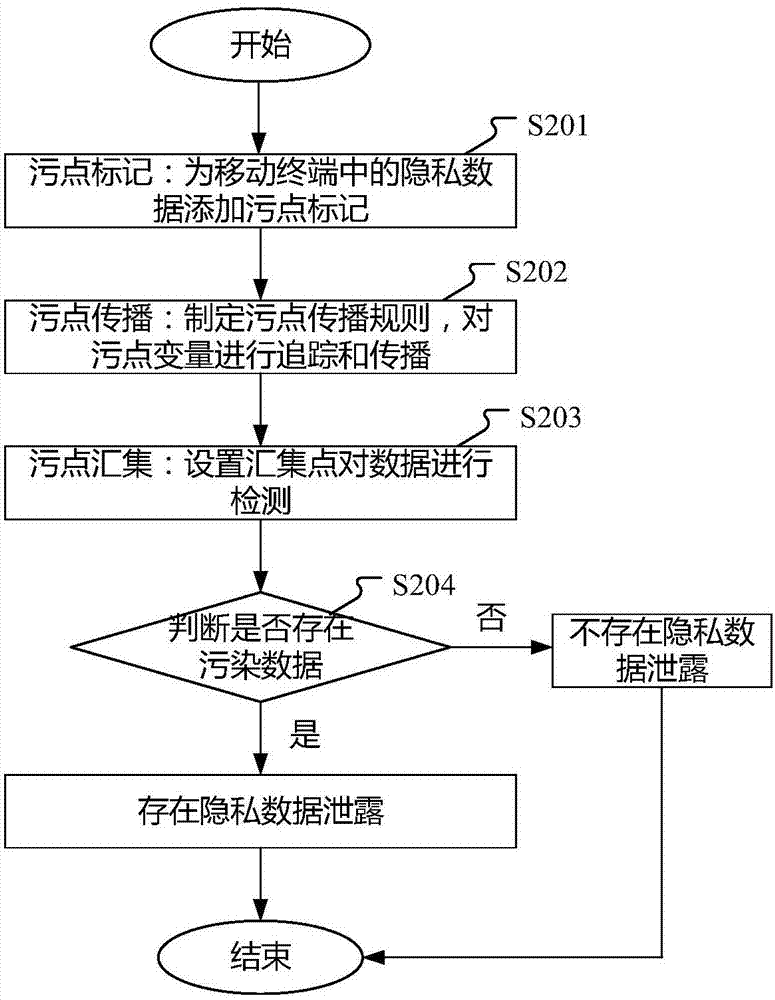
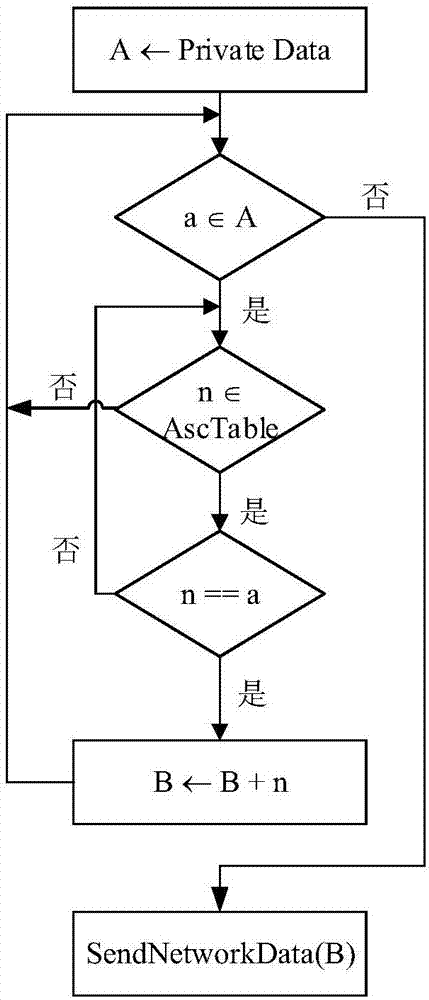
Method and device for detecting privacy data leakage
ActiveCN107330345APrevent leakageImprove accuracyDigital data protectionPlatform integrity maintainanceControl flowComputer terminal
The invention discloses a method and device for detecting privacy data leakage, and the method and device are applied to Android mobile terminals. The method comprises the steps of adding corresponding stain marks to variables generated by privacy data in an Android mobile terminal, and saving the variables and their stain marks to corresponding allocated storage space according to the types of the variables; tracing the propagation of the stain marks corresponding to the variables according to the rule of stain propagation set after analyzing a control flow which contains control information; detecting whether or not the transmitted data at a preset aggregation point has the stain mark, determining that an application has the behavior of leaking privacy data if the data has the stain mark, and otherwise determining that the application does not have the behavior of leaking privacy data. According to the method and device for detecting the privacy data leakage, the accuracy of privacy data leakage detection is improved, and the information security of a user is ensured.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
Software safety code analyzer based on static analysis of source code and testing method therefor
InactiveCN100461132CGuaranteed dynamic loadingImprove accuracySoftware testing/debuggingStatic timing analysisStructure analysis
This invention relates to one software analyzer and its test method based on source codes static analysis, wherein the analysis device comprises five function modules of code analysis device, codes analysis engine, safety risk report device, safety rules database and user interface; this invention gets programs safety risk to user according to the source program and grammar and meanings and delivers the safety leak to the user for audit and evaluation.
Owner:深圳北邮网络科技有限公司
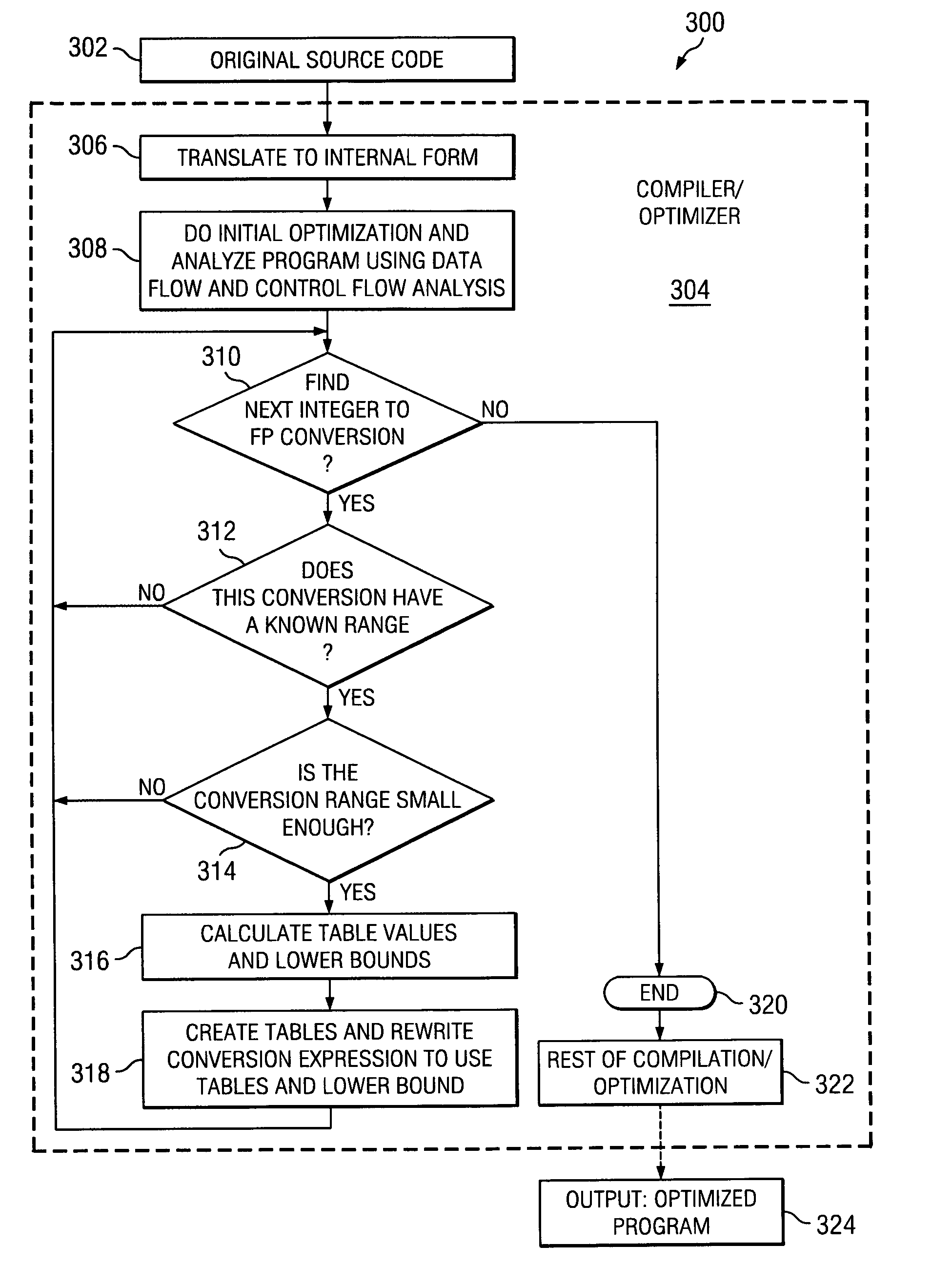
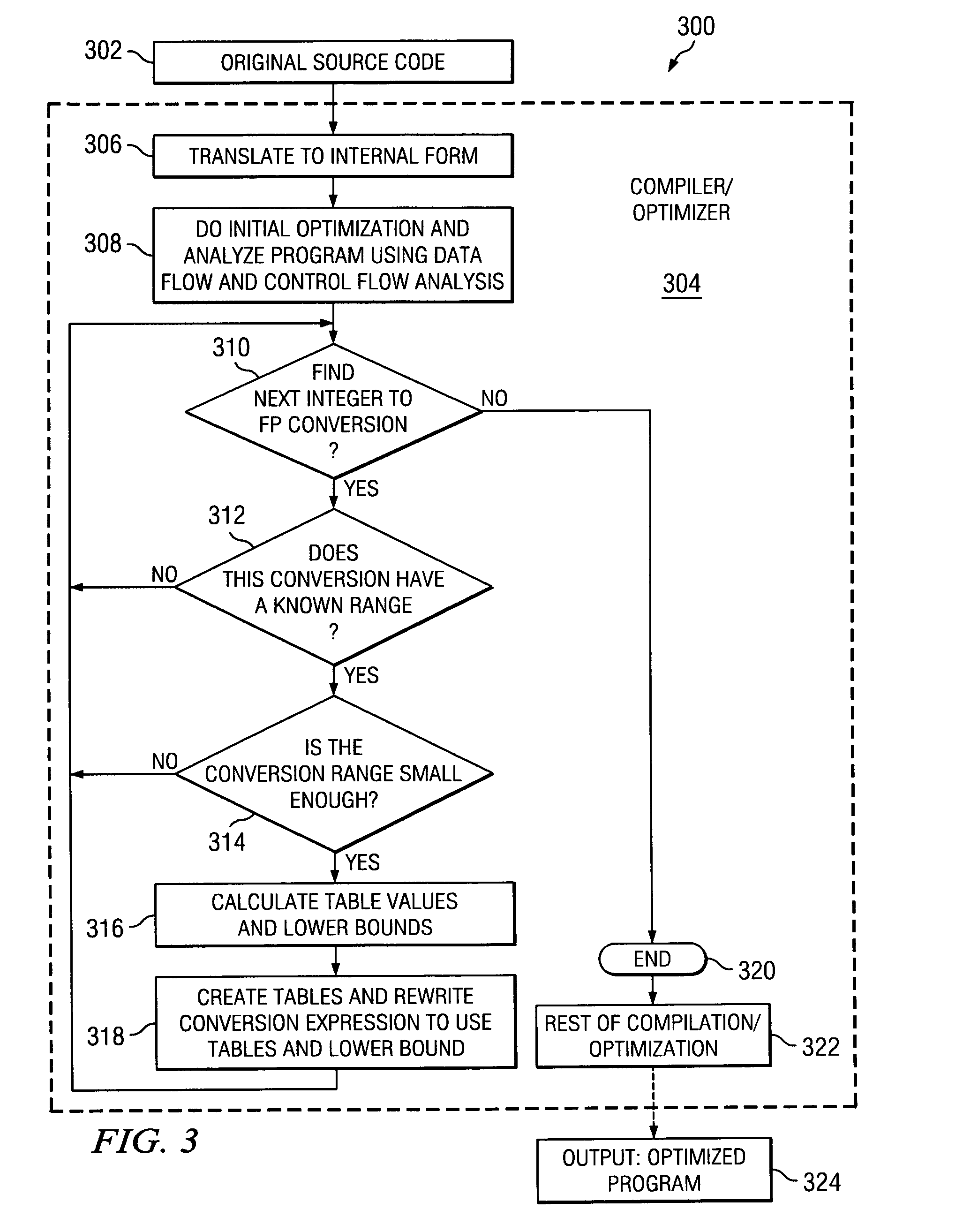
Fast conversion of integer to float using table lookup
InactiveUS20060047734A1Reduce memory trafficAddressing slow performanceDigital data processing detailsDigital computer detailsData processing systemParallel computing
Method, system and computer program product for converting integers to floating point values in a data processing system. The method utilizes data flow analysis and control flow analysis to recognize that a particular integer that is to be converted contains only a limited range of values. Knowledge of this limited range is used to establish a table of floating point values indexed by the integer value. By using the table of floating point values, conversion of an integer to a floating point value can be performed faster and with reduced memory traffic.
Owner:IBM CORP
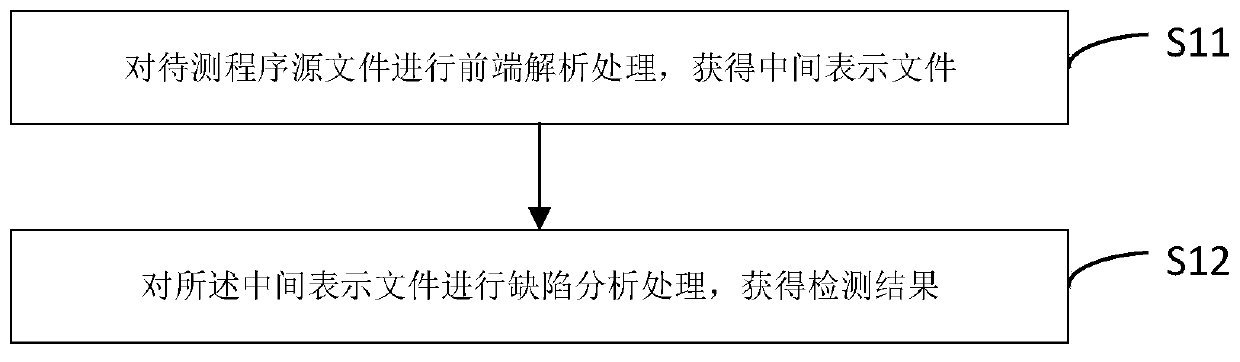
Method and device for detecting defects of program source file
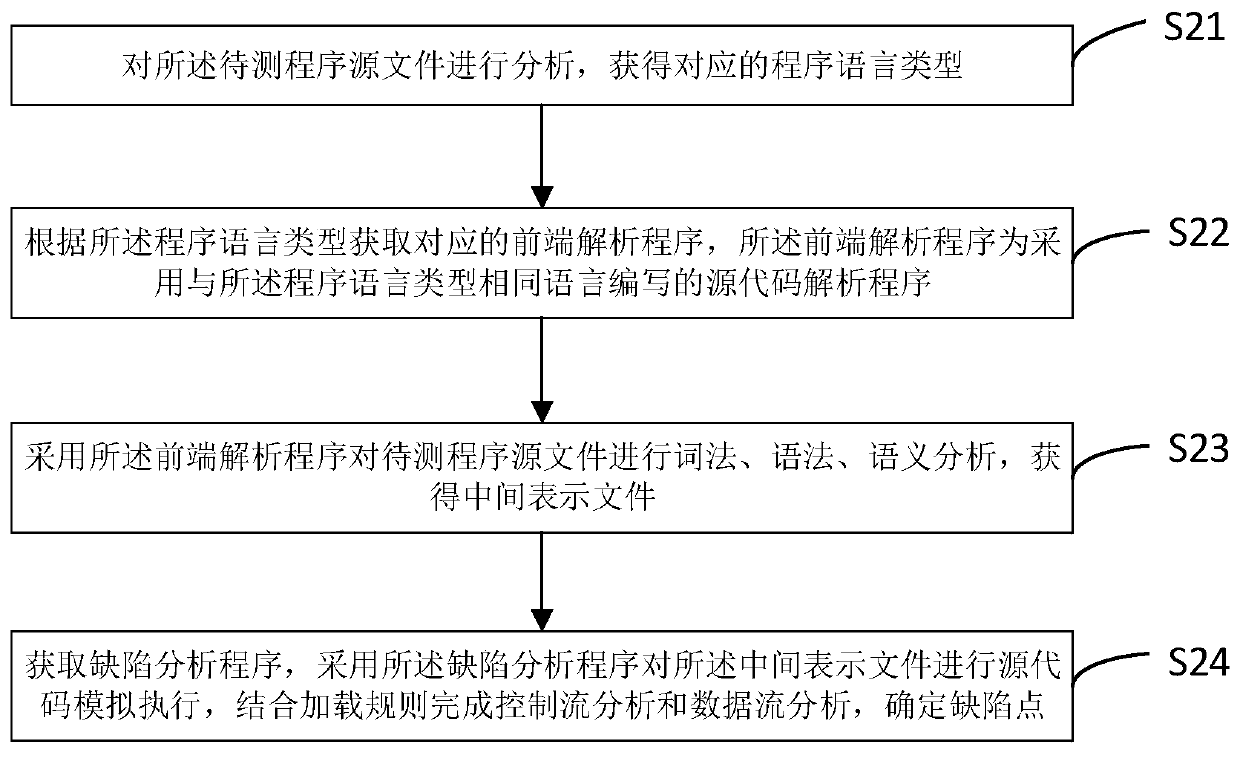
ActiveCN109857641AImprove defect coverageImprove accuracySoftware testing/debuggingPlatform integrity maintainanceSeparation technologyControl flow analysis
The embodiment of the invention provides a method and a device for detecting defects of a program source file, and the method comprises the steps: analyzing a to-be-detected program source file, and obtaining a corresponding program language type; obtaining a corresponding front-end analysis program according to the program language type, wherein the front-end analysis program is a source code analysis program compiled by adopting the same language as the program language type; carrying out lexical, grammatical and semantic analysis on a to-be-tested program source file by adopting the front-end analysis program to obtain an intermediate representation file; obtaining a defect analysis program, performing source code simulation execution on the intermediate representation file by adoptingthe defect analysis program; control flow analysis and data flow analysis are completed in combination with a loading rule, defect points are determined, a source code analysis and defect detection separation technology is adopted, the defect coverage of source code detection is improved, and meanwhile the accuracy of source code defect detection is improved.
Owner:BEIJING QIANXIN TECH +1
Mobile application source code security auditing system based on code dynamic analysis
ActiveCN111008376ASolve efficiency problemsResolve accuracyPlatform integrity maintainanceData streamPattern matching
Owner:ELECTRIC POWER RESEARCH INSTITUTE OF STATE GRID SHANDONG ELECTRIC POWER COMPANY +1
Method for de-obfuscating JavaScript code in web page
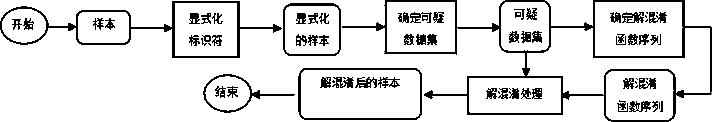
ActiveCN108694042AHigh speedLow process overheadCreation/generation of source codeData streamSemantics
The invention relates to a method for de-obfuscating a JavaScript code in a web page, which improves a feature-based static detection method by de-obfuscating processing of script codes. The method comprises the step of formatting and semantically restoring the script code in the web page; determining a de-obfuscated code corresponding to each obfuscated code from the script code; and restoring the original code hidden in the obfuscated code through the de-obfuscated code. The invention can effectively restore the original code hidden in the obfuscated code in the web page, so as to re-exposethe obfuscated characteristics, thereby remarkably improving the detection rate of the malicious web page detection engine to the obfuscated malicious web page. In addition, the code structure, semantics and format after deobfuscated processing are improved to facilitate the data flow and control flow analysis for the method which can be combined with other tools to assist code analysis, improve efficiency, or as a browser plug-in, to quickly evaluate the browsed web pages, and give a security analysis report.
Owner:FUZHOU UNIV
Control flow analysis using deductive reaching definitions
A computer-implemented process for deductive reaching definition analysis receives a control flow graph to form a set of received blocks and edges, performs traditional reaching definitions to produce bit-vectors OUT(b), GEN(b) and KILL(b) for each block in the set of received blocks and receives impossibility indicators for a set of definitions that are impossible on specific edges. The computer-implemented process further performs deduction operations using a combination of the bit-vectors and impossibility indicators to deduce that additional definitions cannot reach certain blocks to create resulting reachability information and provides the resulting reachability information as a result to a requestor. A related system and program product is also provided.
Owner:INT BUSINESS MASCH CORP +1
Correcting method for solar water heater capacitance water level sensor measuring value
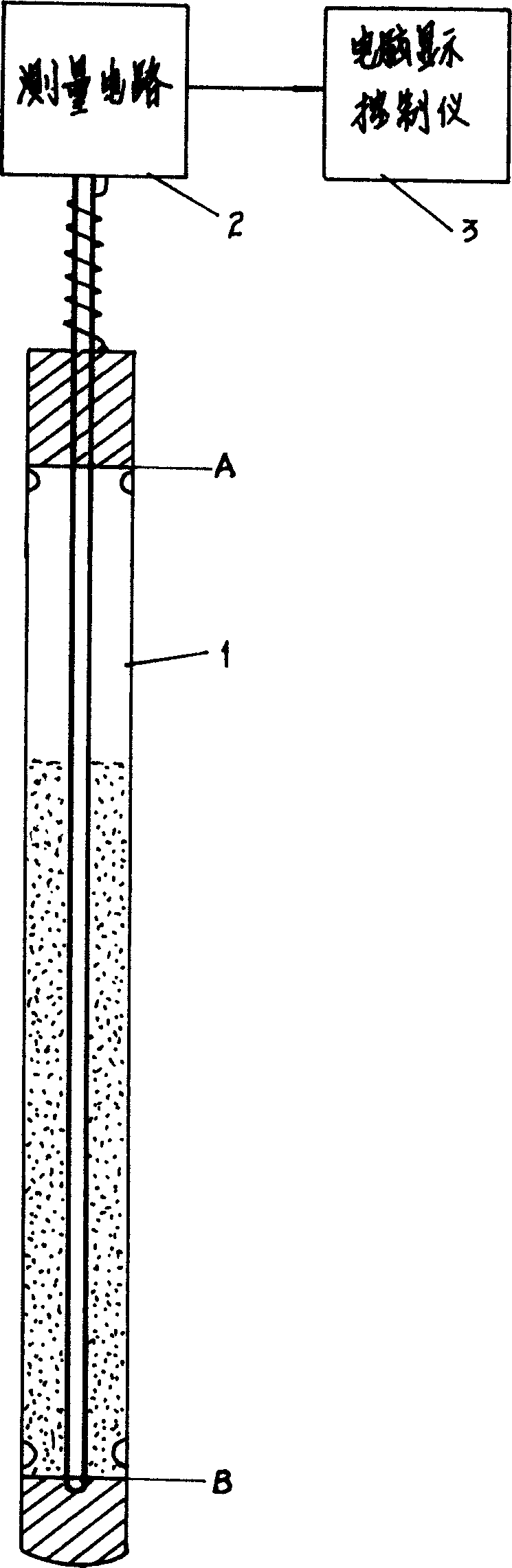
InactiveCN1587859ASimple structureHigh resolutionSolar heat devicesLevel indicators by physical variable measurementCapacitanceControl flow
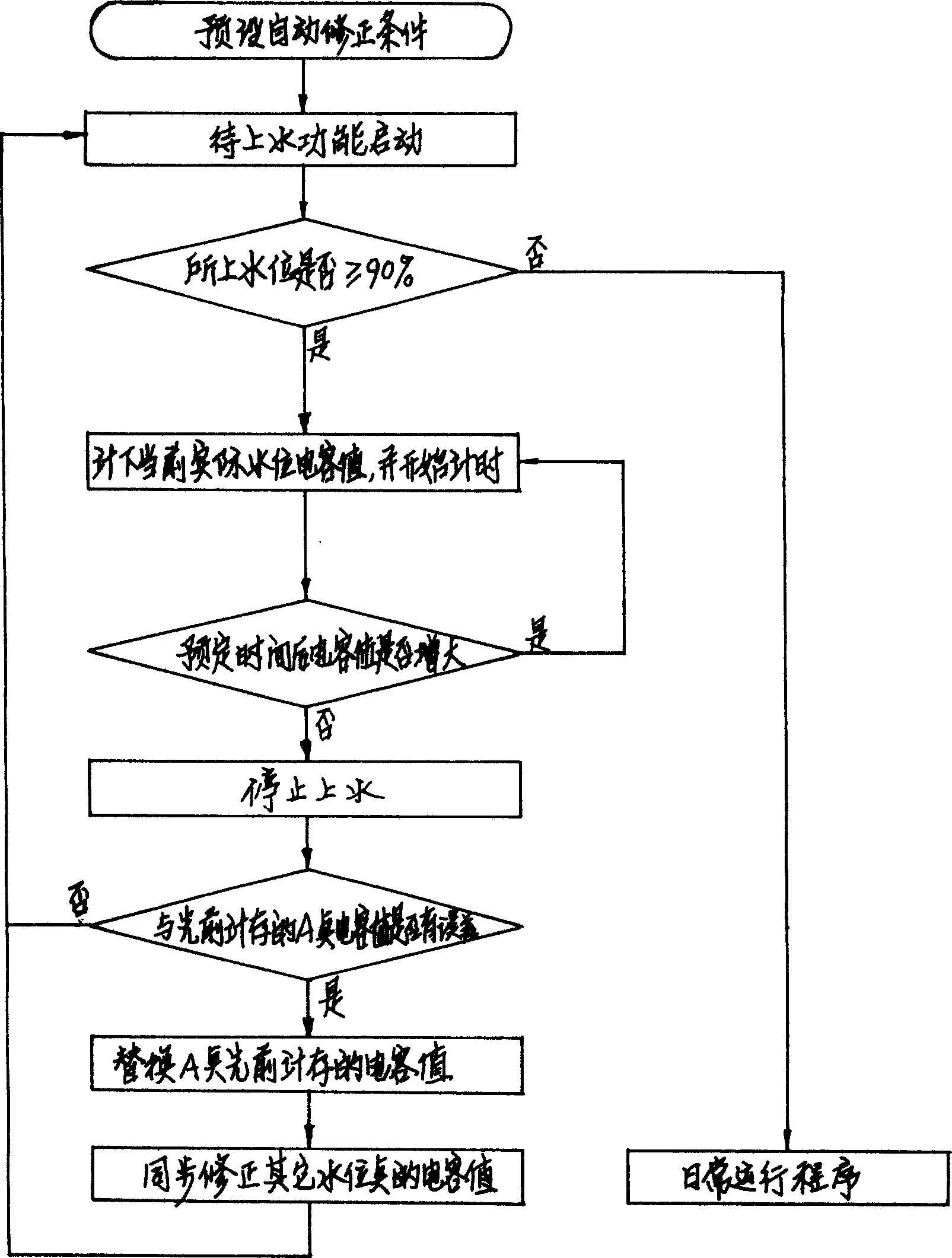
The invention discloses a correction method for capacitance water level sensor measured value of solar energy water heater, its control-flow analysis is as follows: A. presuppose corrected condition; B. wait for the feeding water function to start up; C. judge whether or not the water level is not less than 90%; D. begin to time after taking notes of the practical water level capacity value; E. beyond the schedule time judge whether or not the capacity value becomes larger, if not, go to the next step, otherwise, go back to the last step; F, stop feeding water; G. compare with the capacity value of A point taken before, if the error exists, go back to wait feeding water function starting up program, otherwise, go to the next step; H. take place of the capacity value taken before; I. correct the capacity value of other water level point automatically, go back to wait feeding water function starting up program ; the solar energy water heater using the correction method above has the advantages of simple structure, high resolving power, good precontrol ability, small influence of sediment incrustation, and long service life.
Owner:金蔚东
A control flow graph construction method for object-oriented programming
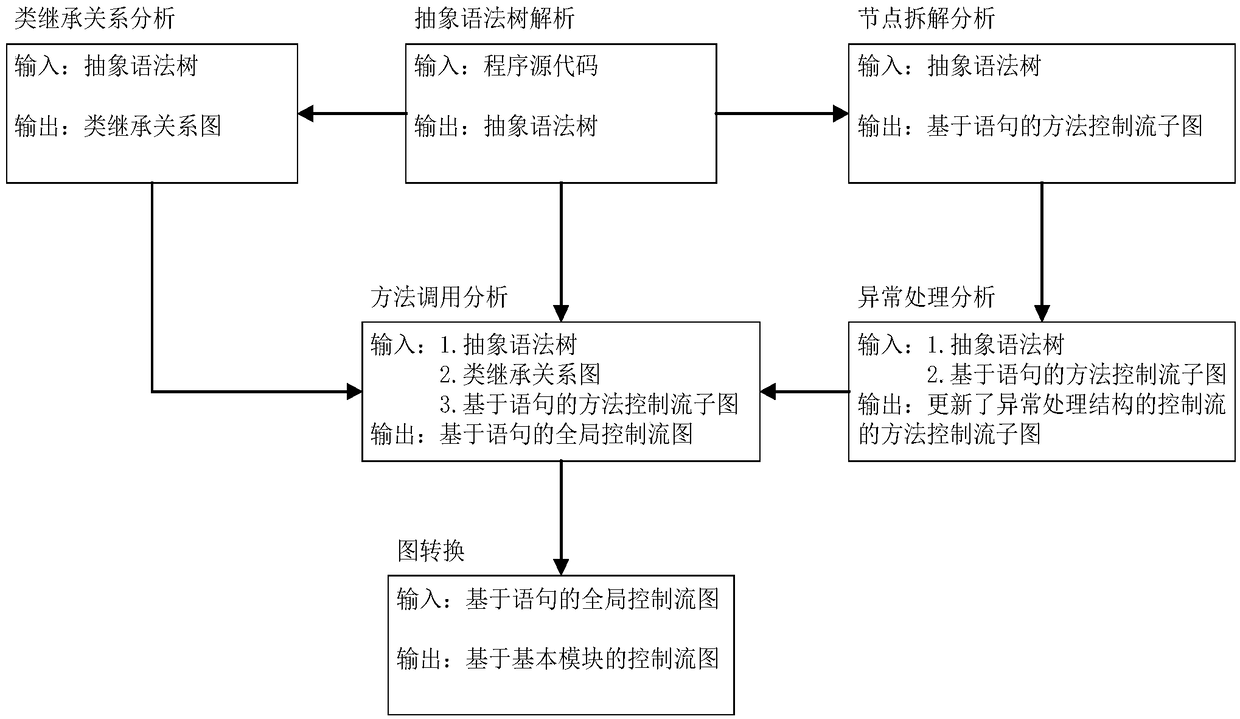
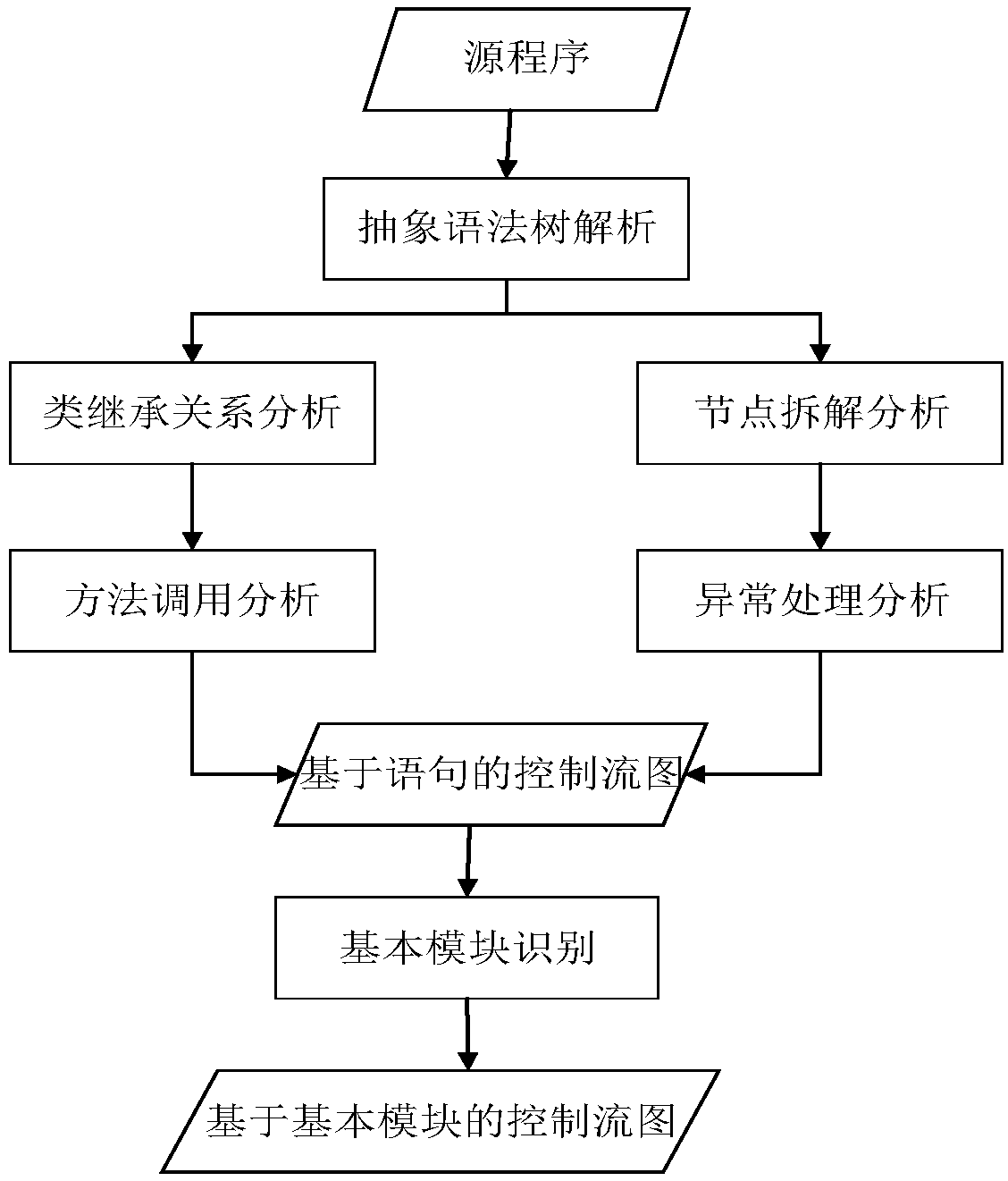
The invention provides a control flow graph construction method for object-oriented programming, which comprises the following steps: 1) constructing an abstract syntax tree according to a source code; 2) constructing a class inheritance relation graph base on an abstract syntax tree; 3) constructing a coarse-grained control flow sub-graph according to a sentence position relation as a method, andthen construct a fine-grained control flow sub-graph by utilizing node disassembly and a virtual finally node method; 4) analyzing that control flow of the exception throwing point and the nested exception handle structure by using the exception floating method; 5) parsing that method invocation information to construct a statement-based control flow diagram; 6) merging the set of statements thatdo not cause the program execution order to change to form a basic module, constructing a control flow graph based on the basic module. The construction method of the invention not only supports theanalysis of the influence of the polymorphic features on the control flow, but also supports the control flow analysis of the multi-layer nested exception handling structure.
Owner:SOUTHEAST UNIV
Global escape analysis using instantiated type analysis
ActiveUS7685586B1Maximize optimization potentialQuick and easily bounded in timeSoftware engineeringSpecific program execution arrangementsControl flowEscape analysis
Global escape analysis using instantiated type analysis (ITA) is applied to a method of an object-oriented application to analyze control flow beginning with an invocation of the method. The instantiated type analysis methodology (inter-procedural control flow analysis) tracks instantiated objects, following both the flow of execution and the flow of these objects throughout the method invocations and field instances of the software, ultimately determining which instantiated objects do not escape. Not all method invocations must be followed and therefore a closed system is not required. This ITA algorithm has been enhanced for the purposes of escape analysis, so that is well-suited for runtime environments in which classes are loosely specified, or in circumstances in which a subset of a program is unavailable.
Owner:TWITTER INC
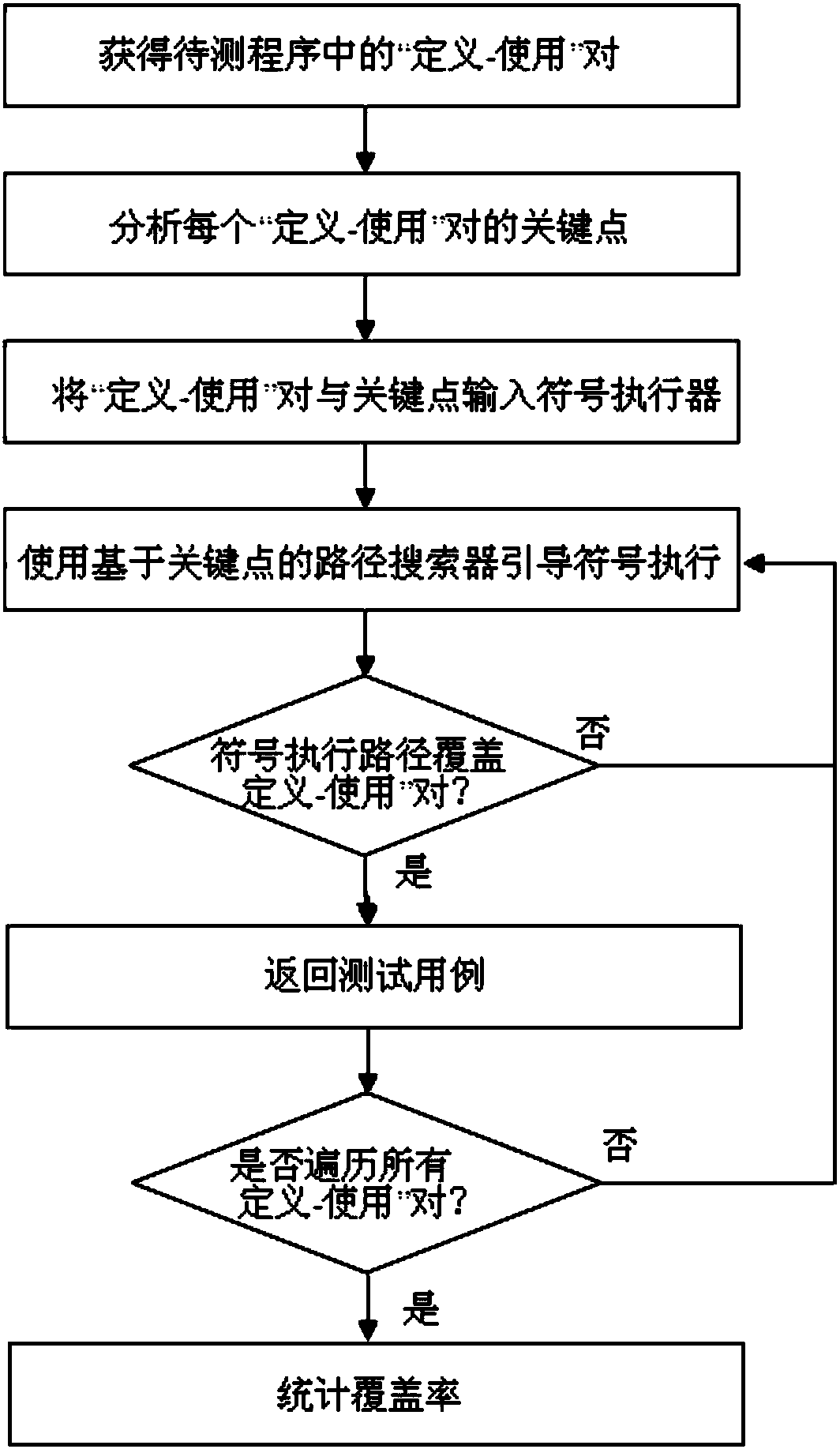
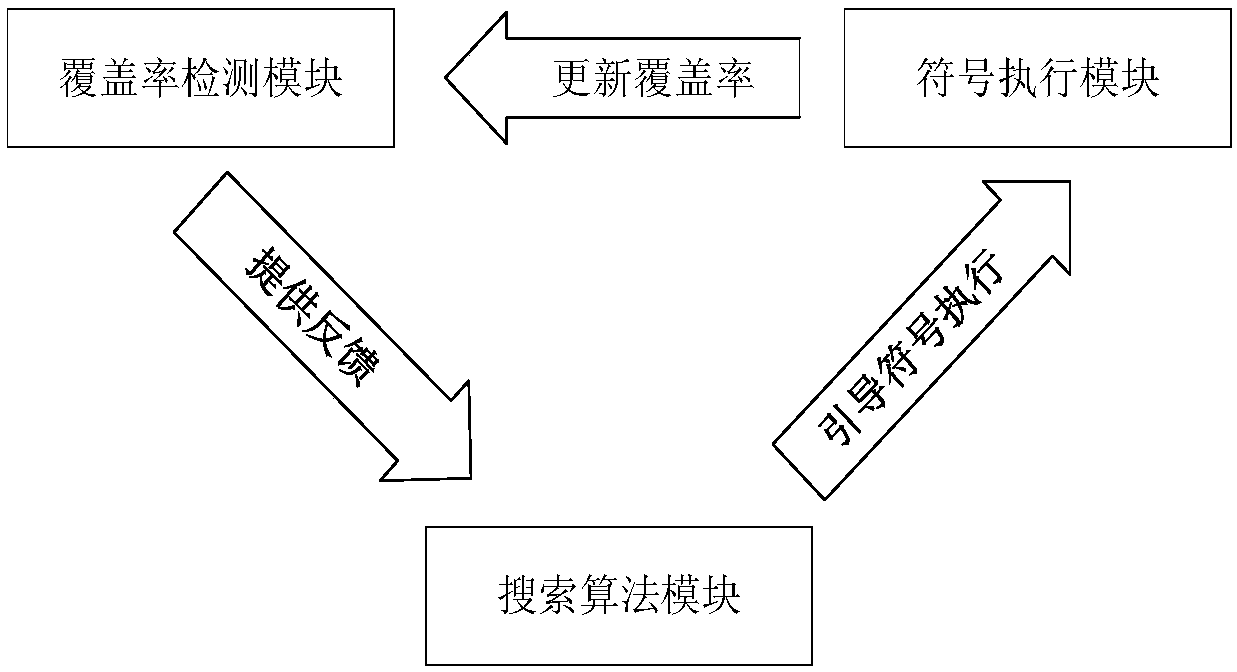
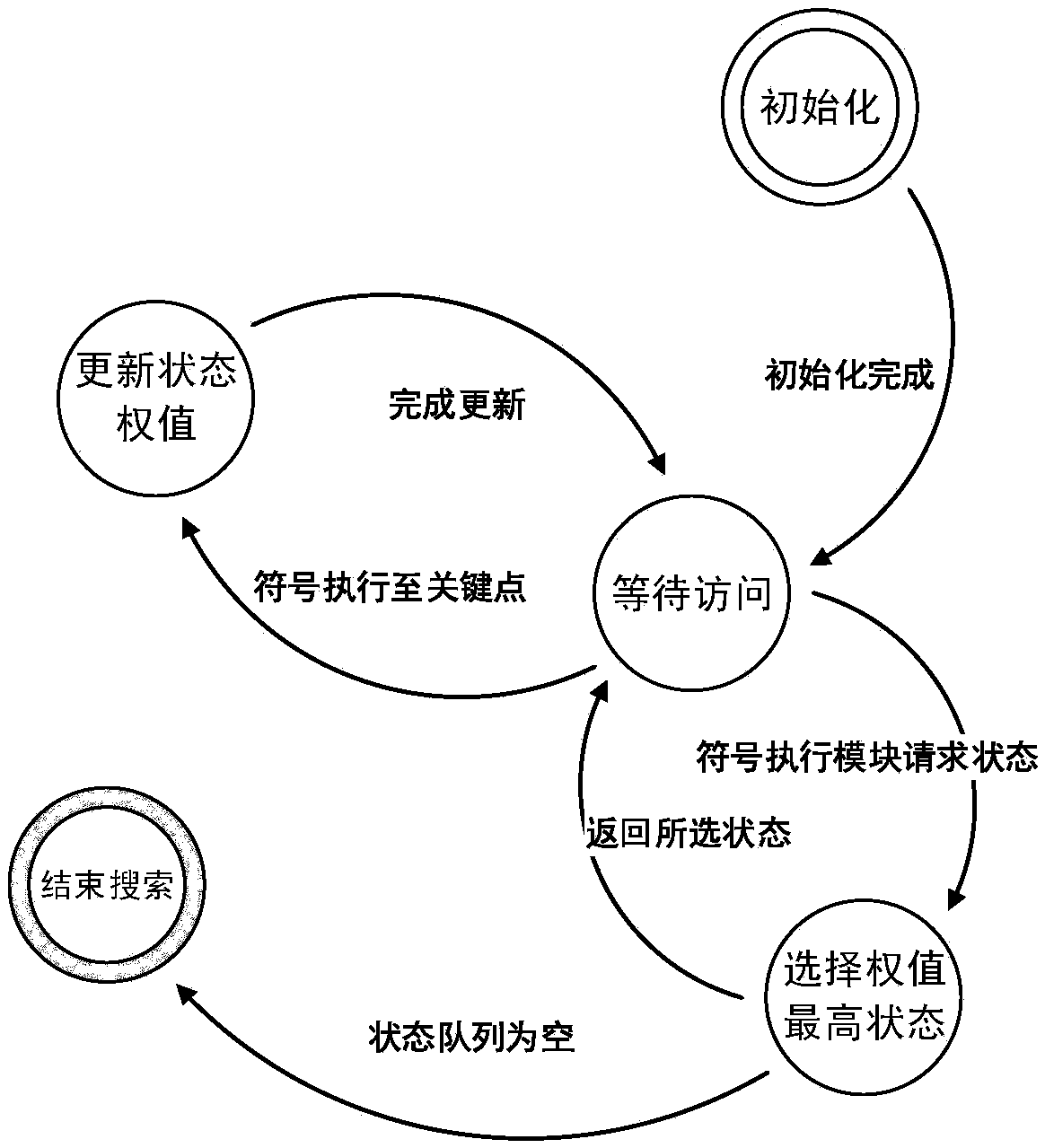
Data stream testing method and testing system based on key point guidance
InactiveCN107656863ASearch orientationEfficient coverage definitionSoftware testing/debuggingProgramming languagePath cover
The invention discloses a data stream testing method based on key point guidance. The method comprises the following steps that: through a standard data stream analysis method, obtaining a definition-use pair in a program to be tested; according to a control stream analysis method, analyzing key points in the definition-use pair; inputting the definition-use pair and the key point into a symbol actuator; using a path searcher based on the key point to guide a symbol in execution by the symbol actuator; if a symbol execution path covers the definition-use pair, returning a test case corresponding to the symbol execution path, otherwise, continuously executing S4 until the corresponding test case is generated for all definition-use pairs or all symbol execution paths finish being executed, and ending the execution of the symbol actuator; and according to a symbol execution result, carrying out statistics on a coverage rate. The invention also discloses a data stream testing system basedon the key point guidance.
Owner:EAST CHINA NORMAL UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com