Method for detecting Java source code insecure input loophole
A source code, secure technology, applied in computer security devices, instruments, electrical digital data processing and other directions, can solve problems such as few types of security vulnerabilities, unsupported security vulnerabilities, and inability to detect security vulnerabilities.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
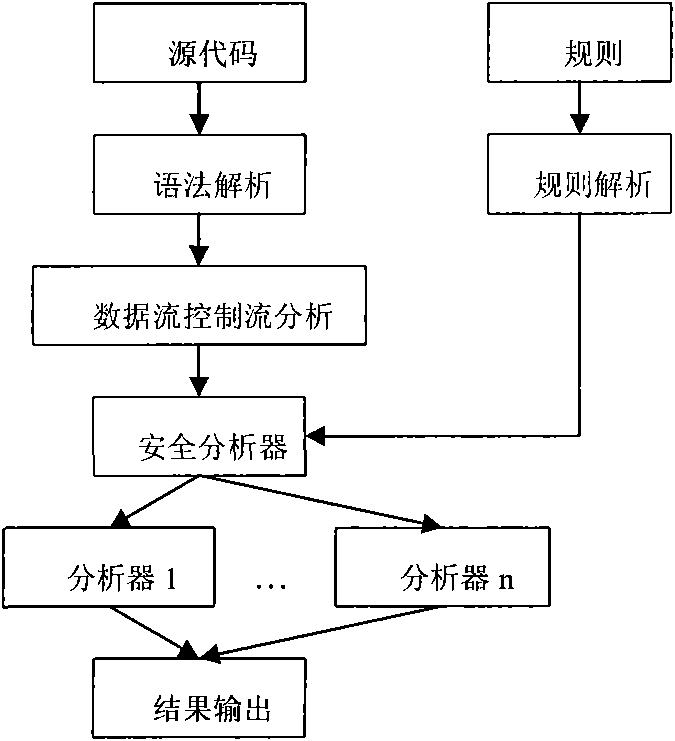
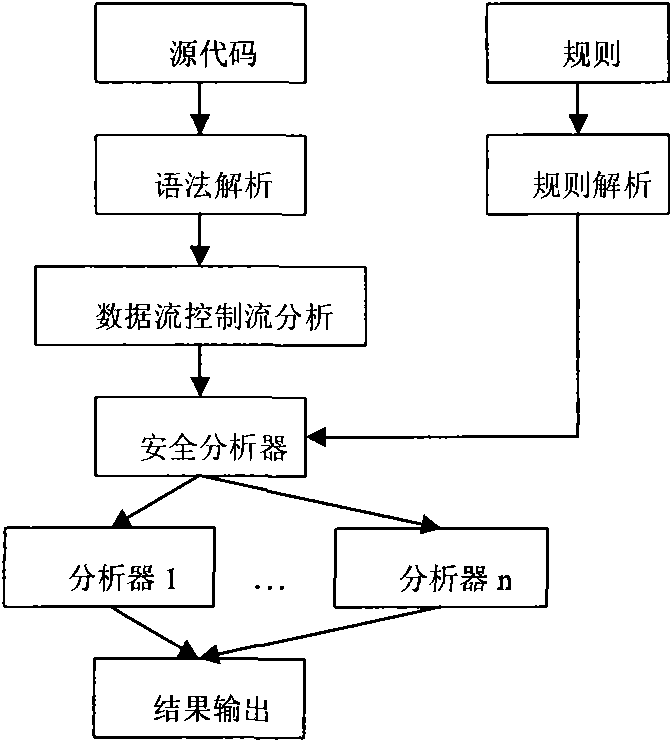
[0023] According to the detection method of the present invention, the scanning process of the above-mentioned source code is specifically as follows: first, the source code is parsed into a standard AST tree, and then data flow and control flow analysis are performed on the AST tree. If our rule is defined as the initial api is execute, Terminate the api as getParameter, then when calling the parser, the specific parsing process is as follows:
[0024] ●First search for the code with the api name execute in the data flow results, and check one by one if you find more than one
[0025] ●Analyze the parameters of execute to get the query
[0026] ●Find the call list of the variable query in the data flow result, and find the definition statement String query=”SELECT*FROM student WHERE owner=”’+userName+”’AND studentname=”’+studentName+””’;
[0027] ●Analyze the definition statement and find that the query is related to the variables userName and studentName
[0028] ●Find the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com