Software safety code analyzer based on static analysis of source code and testing method therefor
A code analysis and software security technology, applied in software testing/debugging, etc., can solve problems such as danger, algorithm function limitations, and not easy for developers to discover
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0074] In order to make the objectives, technical solutions and advantages of the present invention clearer, the present invention will be further described in detail below with reference to the accompanying drawings.
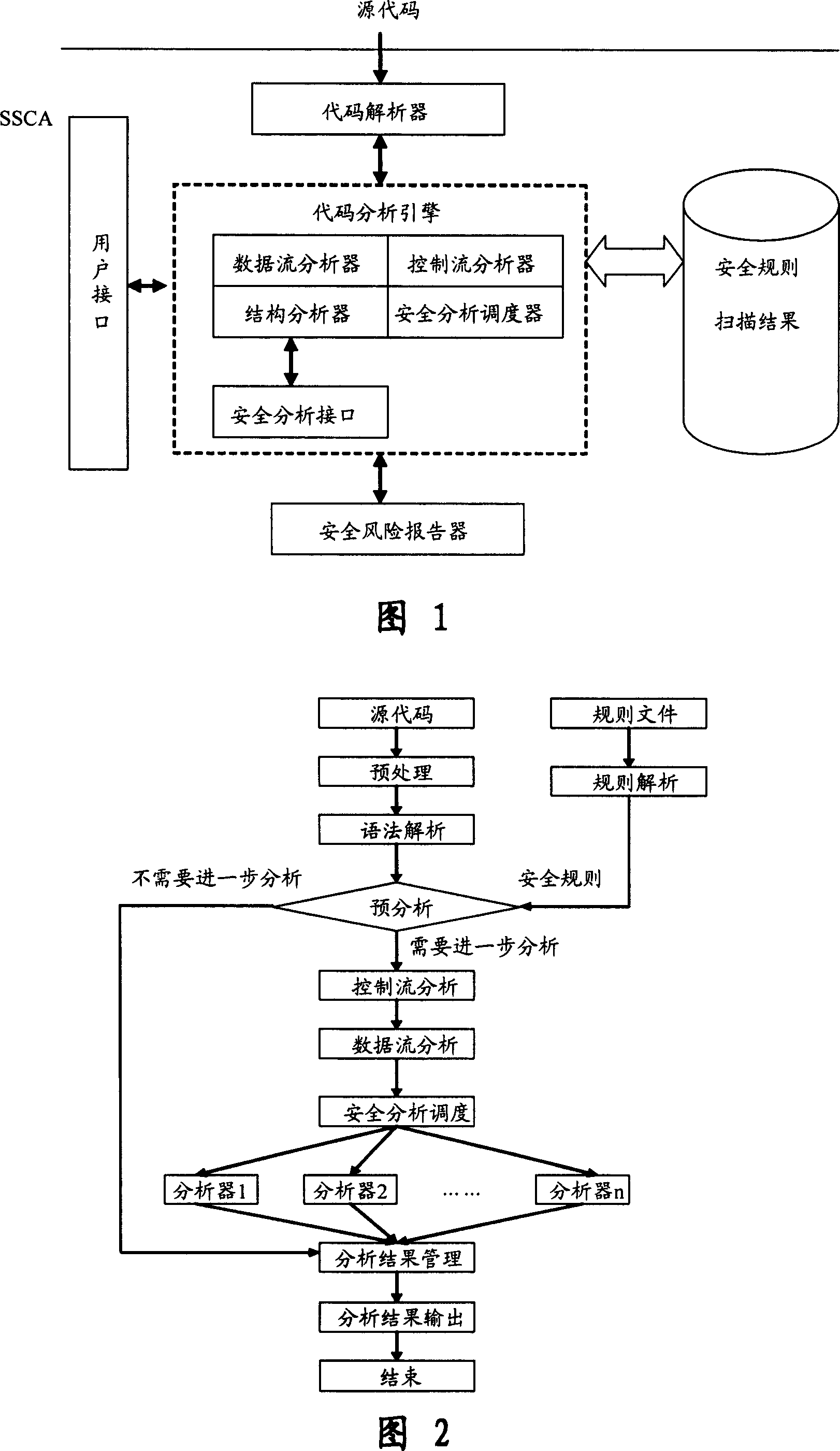
[0075] Referring to FIG. 1, the structure of the software security code analyzer SSCA based on the source code static analysis technology of the present invention is introduced, which mainly includes the following five functional modules:
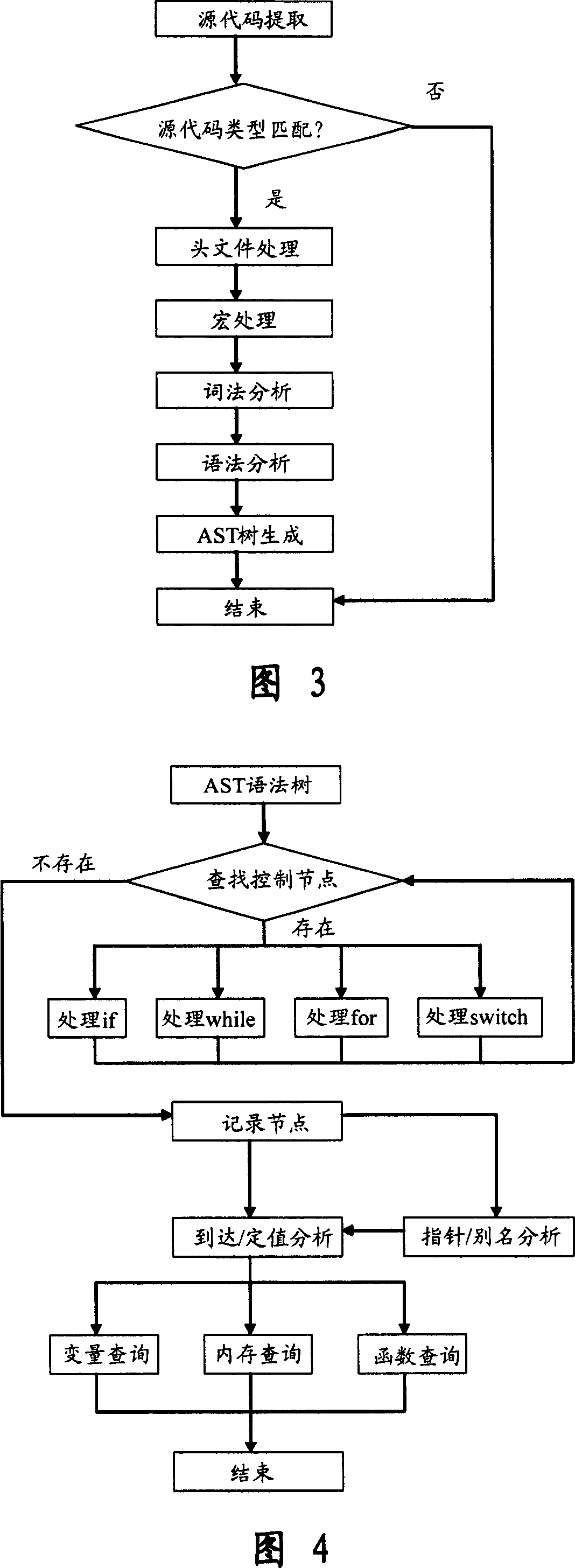
[0076] 1. The code parser is responsible for lexical and grammatical analysis of the source program. Then abstract enough information and convert it into an abstract syntax tree AST to represent it, and then send it to the code analysis engine to facilitate subsequent analysis; this module can also support parsing project project files and obtain all source code information in the project;
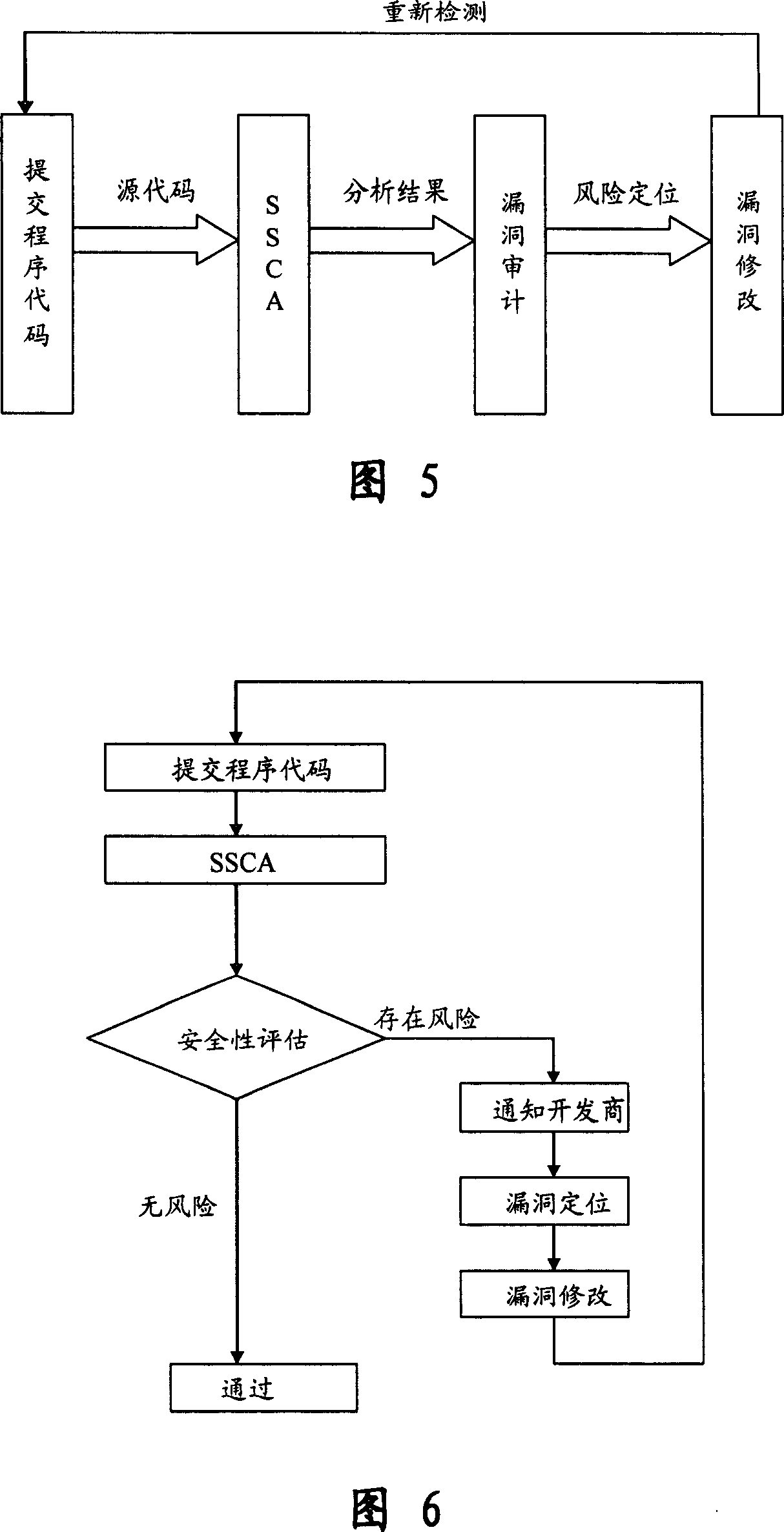
[0077] 2. The code analysis engine is responsible for analyzing the structure and key features of the program according to the rule bas...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com