Mobile application source code security auditing system based on code dynamic analysis
A mobile application and security auditing technology, applied in the field of network security, can solve the problems of high cost, non-compliance with industry characteristics, and high maintenance and upgrading costs of security testing products, so as to reduce labor and time costs, reduce security risks, and improve efficiency. Effect
Active Publication Date: 2020-04-14
ELECTRIC POWER RESEARCH INSTITUTE OF STATE GRID SHANDONG ELECTRIC POWER COMPANY +1
View PDF15 Cites 7 Cited by
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
[0006] 1. Unable to be independently controllable: In the "Power Industry Cyber Security Action Plan (2018-2020)" organized by the National Energy Administration, it is clearly stated: "Insist on independent innovation, accelerate the promotion of independent controllable and core technology breakthroughs in the power system";
[0007] 2. Does not conform to industry characteristics: Due
Method used
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
View moreImage
Smart Image Click on the blue labels to locate them in the text.
Smart ImageViewing Examples
Examples
Experimental program
Comparison scheme
Effect test
 Login to View More
Login to View More PUM
 Login to View More
Login to View More Abstract
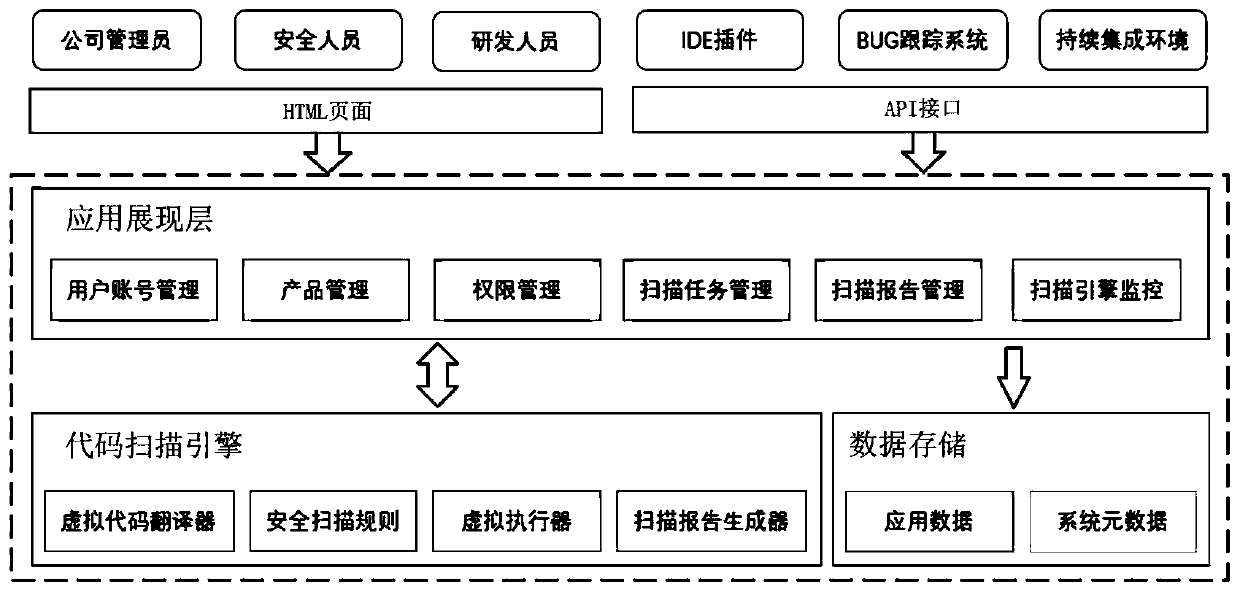
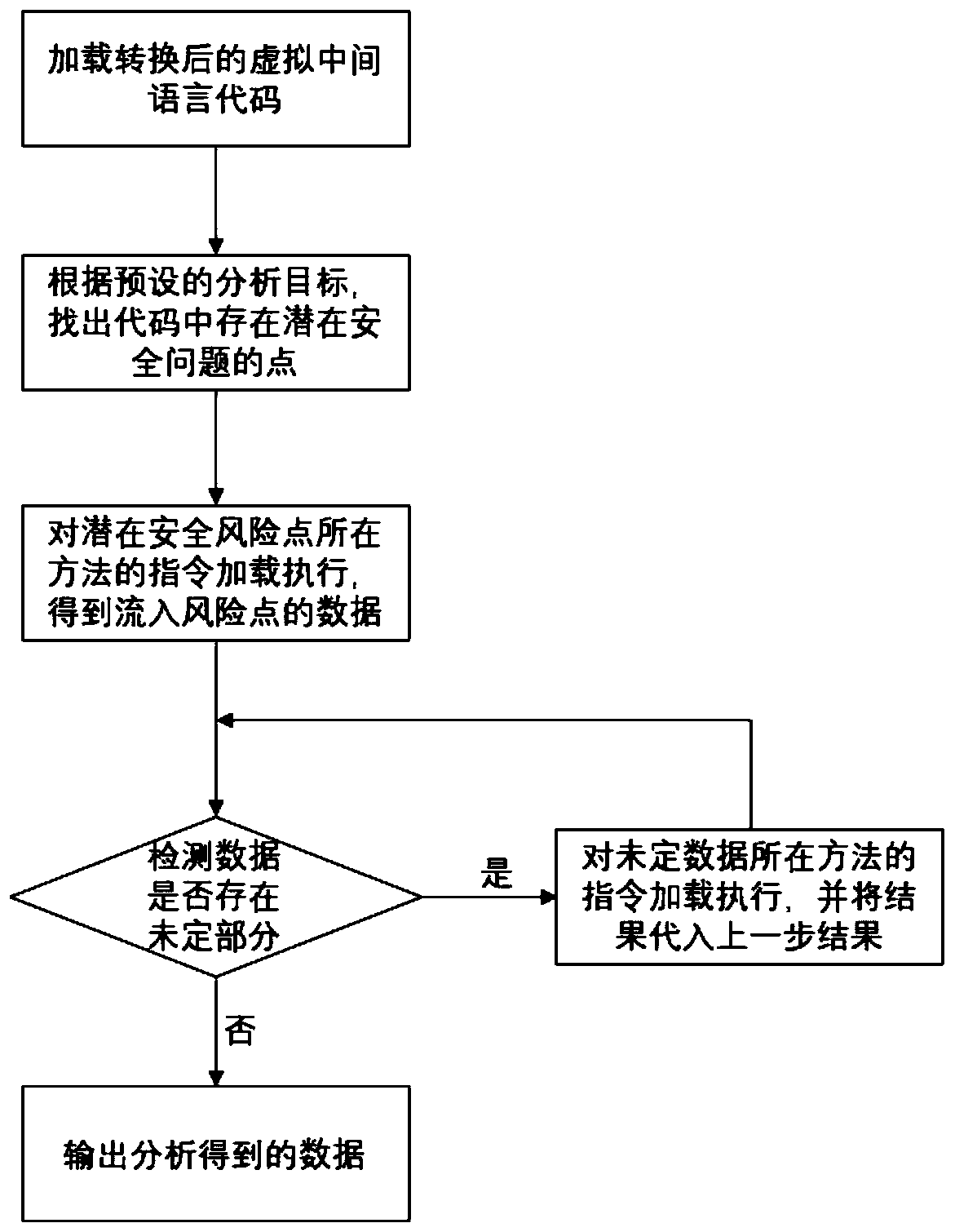
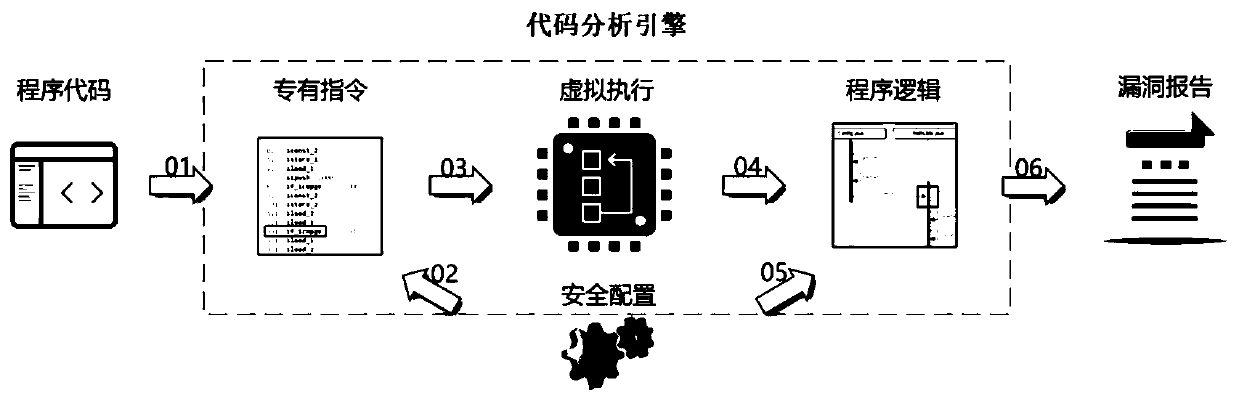
The invention discloses a mobile application source code security auditing system based on code dynamic analysis. The system comprises a code scanning engine module, an application presentation layermodule and a data storage module. The application presentation layer module provides an external system integration interface for a front-end interface of the system. The code scanning engine module cooperates with the application presentation layer module to realize planning, creation, scanning and report generation of a code security scanning task. The data storage module is used for system datastorage. A virtual execution technology is adopted, so that the problems of low efficiency and low accuracy of first-generation and second-generation technologies based on pattern matching, data flow/control flow analysis and the like are solved. The labor and time cost wasted for coping with invalid vulnerabilities is reduced, and the security risk brought to a company due to missing report of atraditional code scanning tool is reduced. Customization can be carried out according to actual requirements of the company. The efficiency is further improved. The code security level of the companyis comprehensively improved with the cost as low as possible.
Description
technical field [0001] The invention belongs to the technical field of network security, and relates to a mobile application source code security audit system based on code dynamic analysis. Background technique [0002] With the development of the times, information technology has profoundly affected people's work and life. But while bringing convenience to people, information technology has also become a new means of crime. Hacking attacks in information systems are more subtle and difficult to prevent than traditional crimes. In silence, people's information assets and even physical security may be compromised. The introduction of defensive devices, including firewalls, IDS, IPS, etc., has improved the security level of the system to a certain extent, but these devices cannot effectively prevent application-level attacks, especially the 0day attacks of unknown vulnerabilities in the system. . Every time a new 0day attack brings about a large-scale fall of the entire I...
Claims
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More Application Information
Patent Timeline
 Login to View More
Login to View More IPC IPC(8): G06F21/53G06F21/56
CPCG06F21/53G06F21/566
Inventor 刘冬兰刘新马雷张昊王睿于灏王文婷常英贤陈剑飞赵晓红赵洋赵勇吕国栋王晓峰任天成井俊双刘鑫
Owner ELECTRIC POWER RESEARCH INSTITUTE OF STATE GRID SHANDONG ELECTRIC POWER COMPANY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com