Test data generating device and method based on binary program
A binary program and test data technology, applied in software security analysis, communication and computer fields, can solve problems such as many uncertain factors, path explosion, difficulty in approximating paths and timing attributes, etc., to improve effectiveness and accuracy, and improve accuracy. degree, the effect of alleviating the path explosion problem
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0047]In order to make the objectives, technical solutions and advantages of the present invention clearer, the present invention will be further described in detail below with reference to the accompanying drawings.
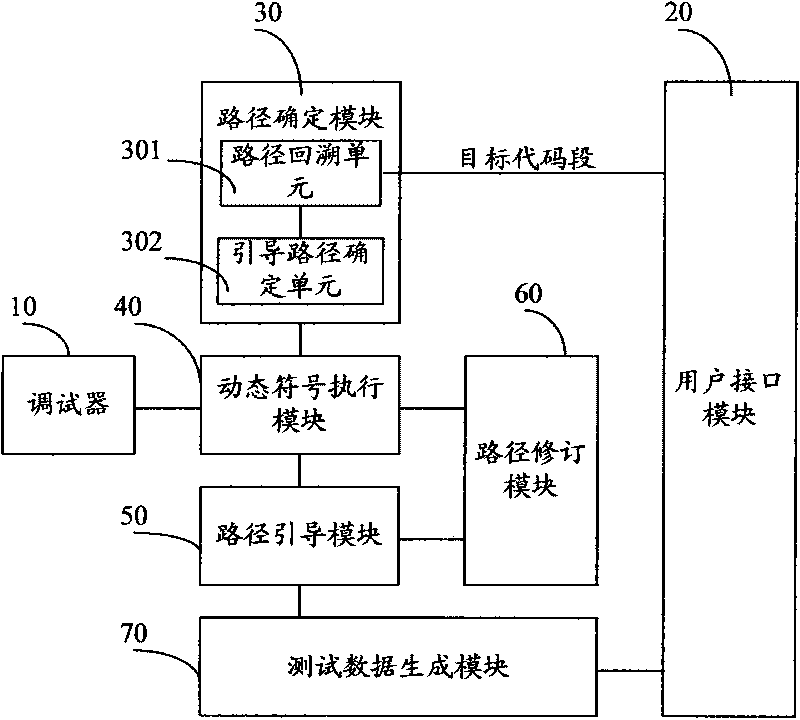
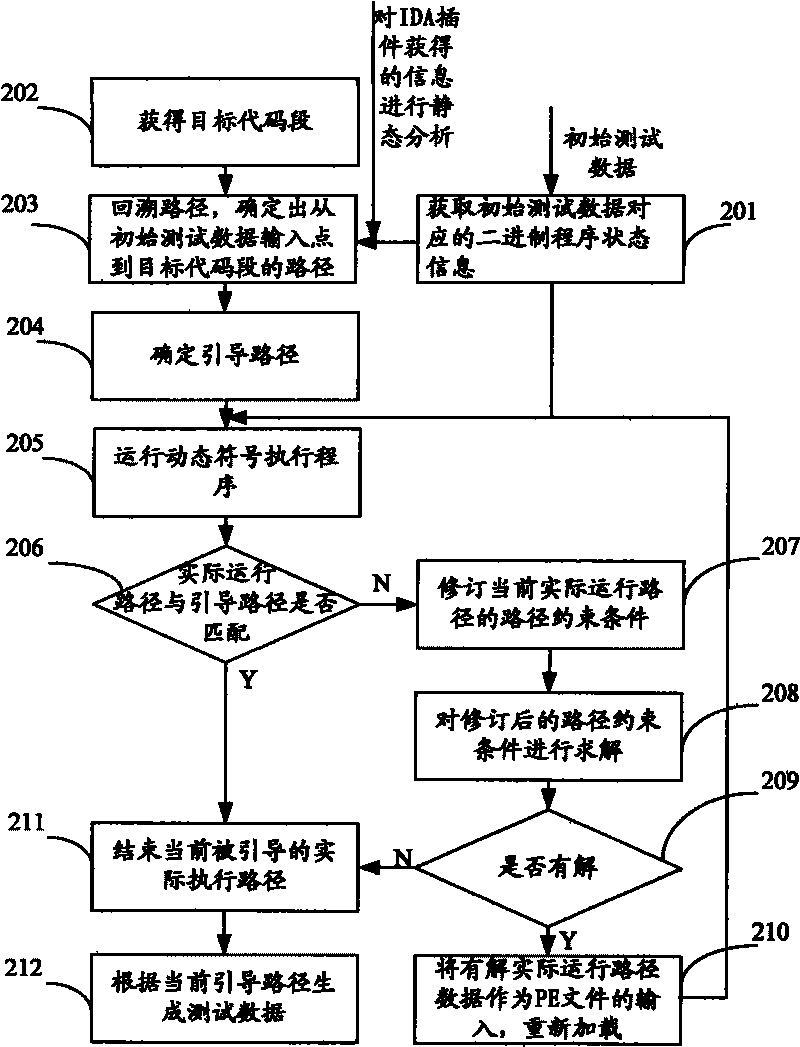
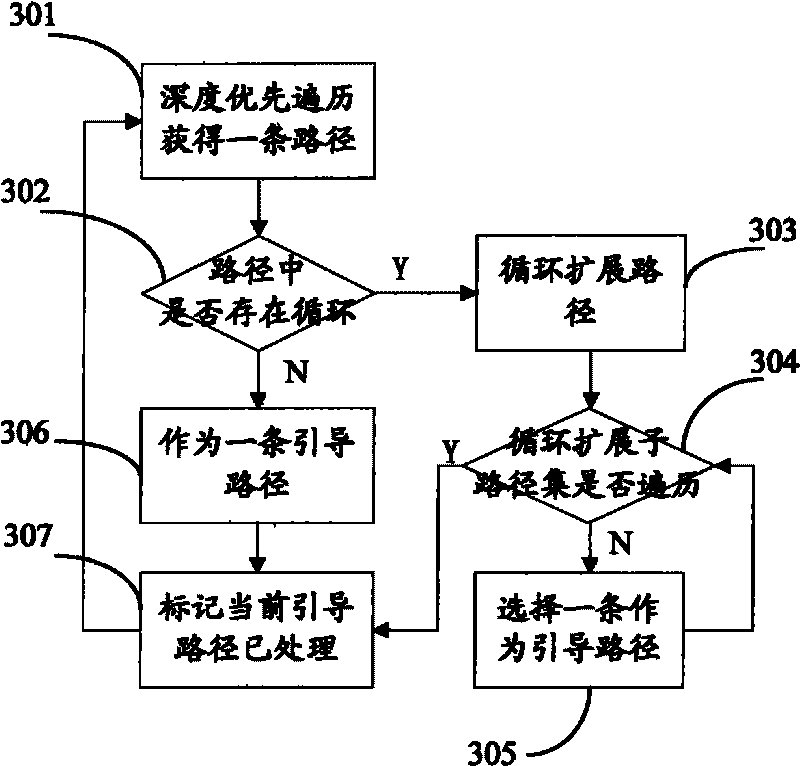
[0048] The first embodiment of the present invention provides a binary program-based test data generator. The binary program-based test data generator starts from the initial test data based on the binary program, and combines actual execution and symbolic execution to solve the problems faced by software security detection. question. In order to alleviate the problem of path explosion, the binary program-based test data generator focuses on the code parts that have security risks. The input points based on the initial test data of the binary program are actually executed along all possible different paths to the test data set of the target code segment. Its structural principle diagram is as follows figure 1 shown, including the following modules:
[0049] A...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com