Excavating device and excavating method of binary system program loopholes
A binary program and vulnerability mining technology, applied in computer security devices, instruments, electrical digital data processing, etc., can solve problems such as lack of guidance, high false negative rate and false positive rate, easy to miss program paths, etc., to avoid blindness effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0047] In order to make the object, technical solution and advantages of the present invention clearer, the present invention will be further described in detail below in conjunction with the accompanying drawings.
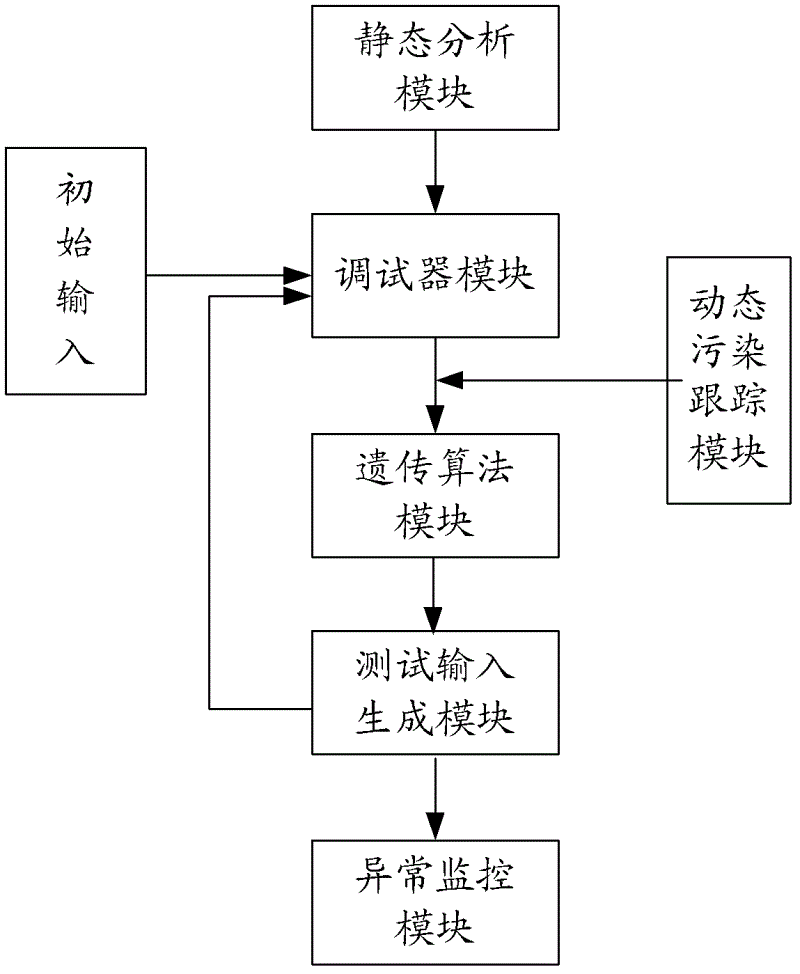
[0048] see figure 1 , first introduce the structural composition of the device for mining binary program vulnerabilities that integrates genetic algorithm and dynamic pollution tracking: the device is equipped with sequentially connected static analysis module, debugger module, genetic algorithm module, test input generation module and abnormal monitoring module , and a dynamic pollution tracking module located between the debugger module and the genetic algorithm module; where:
[0049] Static analysis module, which is developed and implemented based on the interactive disassembler professional version IDAPro (Interactive Disassembler Professional), is used to extract the control flow structure, basic block information and call address of dangerous functions in t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com