Embedded-device-oriented firmware vulnerability detection method and embedded-device-oriented firmware vulnerability detection system
A technology for embedded devices and vulnerability detection, which is applied in the fields of instruments, electrical digital data processing, platform integrity maintenance, etc., to achieve the effect of improving speed, accuracy and robustness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0038] The present invention will be described in detail below in conjunction with specific embodiments.
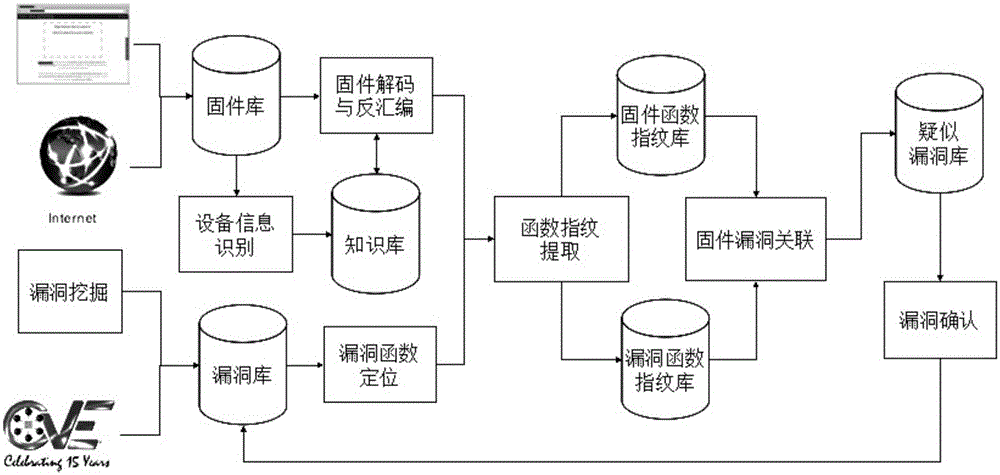
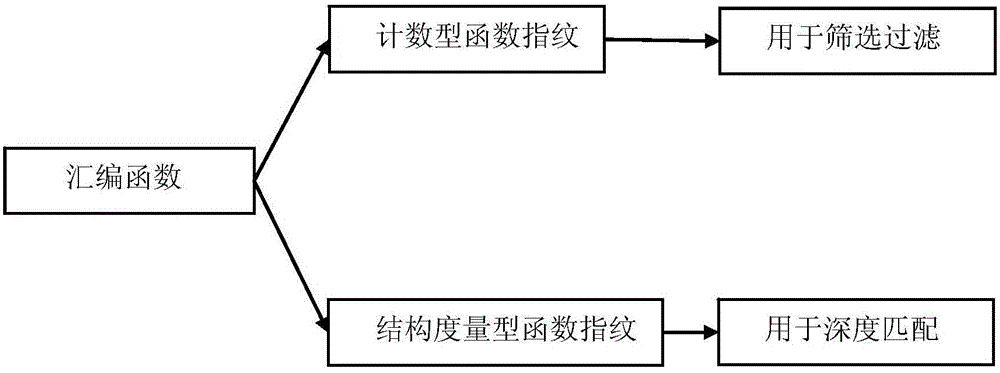
[0039] The overall block diagram of the method is as follows figure 1 shown. include:
[0040] a) Use a web crawler to regularly crawl the firmware published by each manufacturer on its firmware update website, and store it in the firmware library;
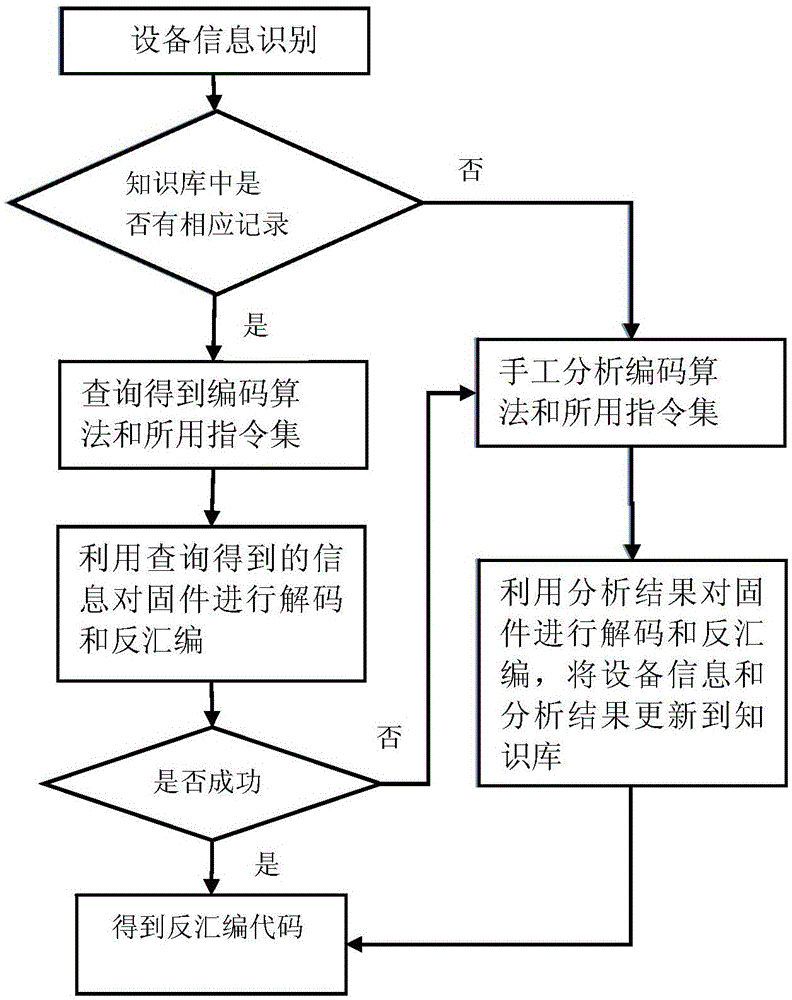
[0041] b) Identify the device information of the firmware in the firmware library, if the device information of the firmware is not in the knowledge base, continue to step c), otherwise, query the encoding algorithm and the instruction set used for the firmware from the knowledge base and then jump to step d);
[0042] Embedded devices of the same manufacturer and product series often have the same encoding algorithm, have the same processor, and use the same instruction set. The knowledge base mainly saves the mapping relationship between the manufacturer's product series and the coding algorithm instruction set.
[004...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com