Test model and test method of vulnerability discovery technology
A technology of vulnerability mining and testing methods, which is applied in software testing/debugging, error detection/correction, instruments, etc., to achieve the effect of improving the level of automation and facilitating use
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
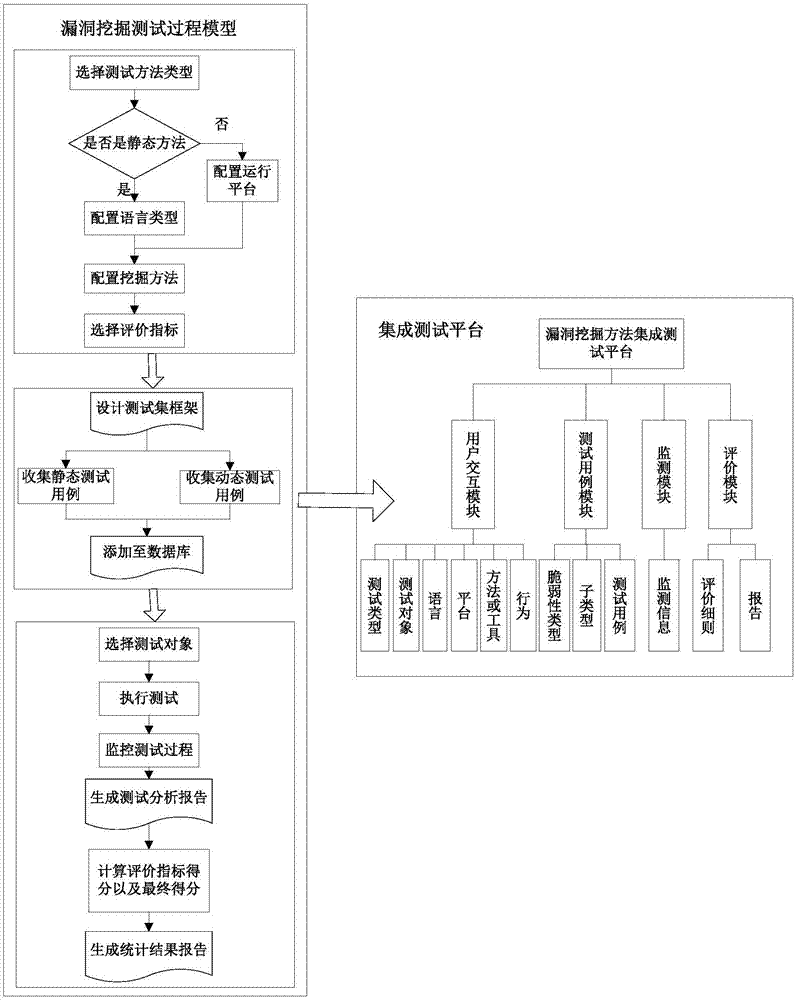
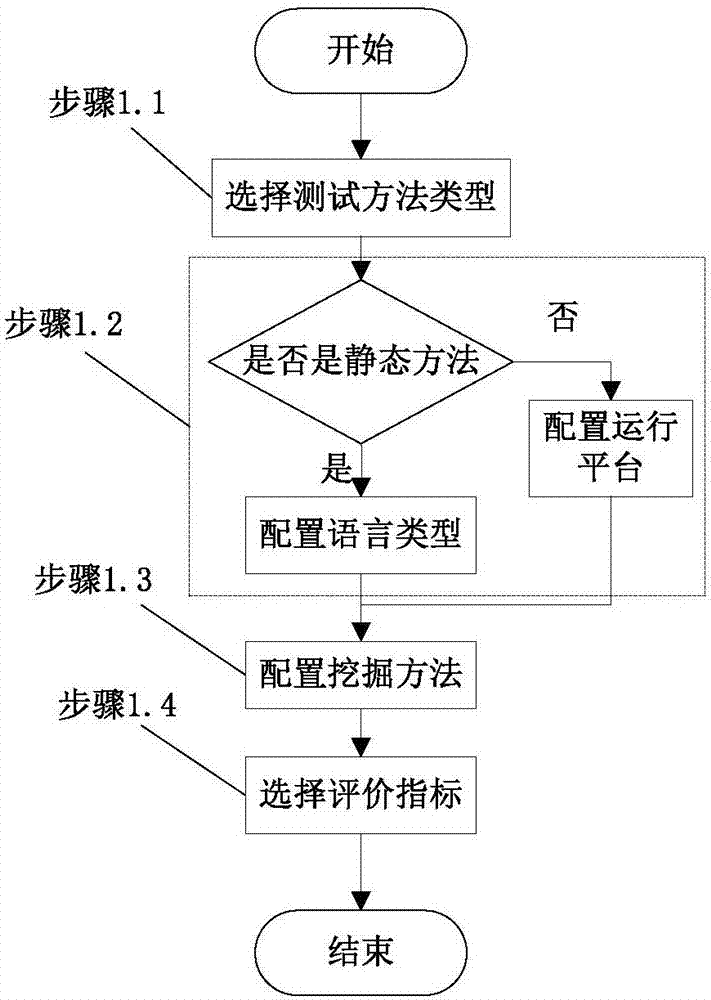
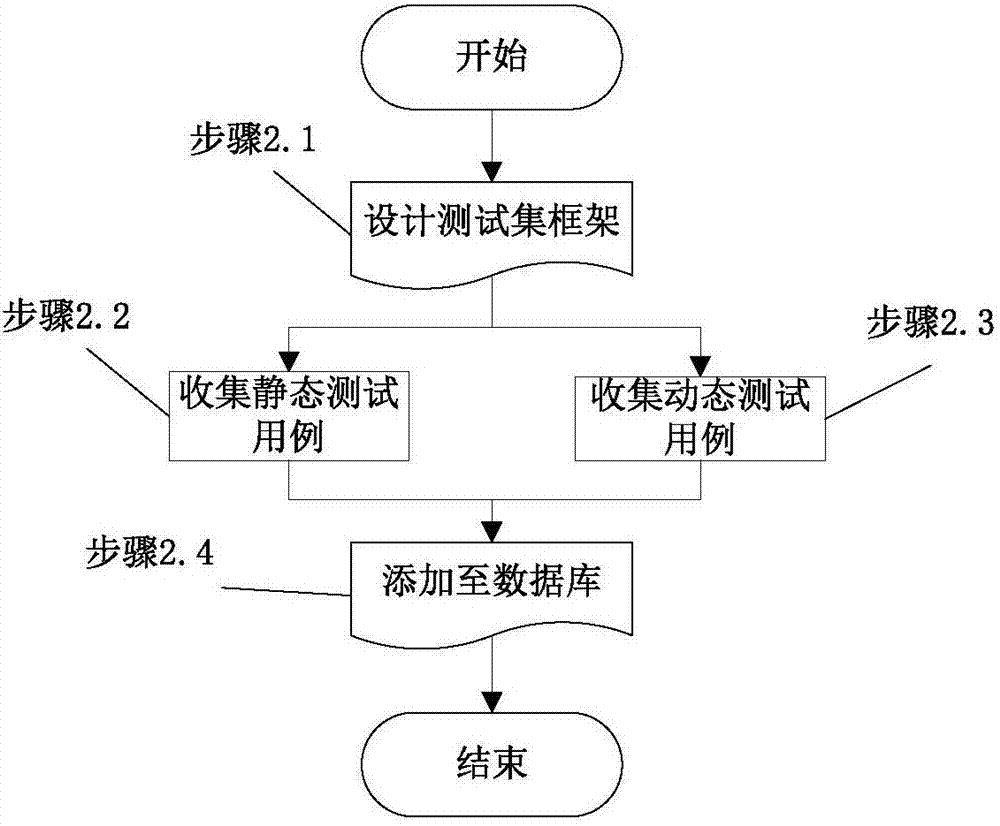
[0053] In order to understand more clearly the technical content of the test model and test platform of a vulnerability mining method of the present invention, the present invention will be further described below in conjunction with the accompanying drawings and specific implementation cases. It should be pointed out that the described implementation cases are intended to This is to facilitate understanding of the present invention without requiring any limitation thereto.
[0054] The purpose of the present invention is to solve the problem of how to select suitable and effective vulnerability mining methods and tools for different environments and different scenarios in actual vulnerability mining, and provides a test process model of a vulnerability mining method, which effectively improves the vulnerability The automation level of the mining method, and an integrated testing platform is designed and implemented based on the testing process model of the vulnerability mining...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com