Industrial environment vulnerability discovering device and method
A vulnerability mining and industrial environment technology, which is applied in the direction of instruments, computer control, simulators, etc., can solve problems that do not have function libraries and custom function blocks, single and simple functions, and do not have rich function libraries and custom function blocks, etc. problem, to achieve the effect of enriching the function library
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
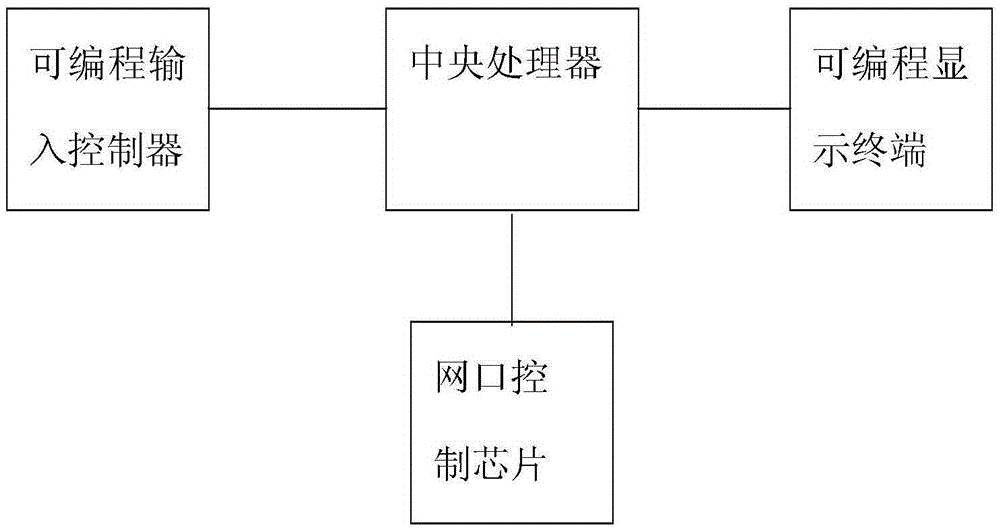
[0051] Embodiments of the present invention will be described in detail below in conjunction with the accompanying drawings. Such as figure 1 As shown, the industrial environment vulnerability mining device of the present invention includes: a main board composed of a central processing unit and a network port control chip, a programmable input controller, and a programmable display terminal. The industrial environment loophole mining device of the present invention can be connected with an external control platform through the network port of the main board of the network port control chip. The central processing unit of the main board is respectively connected with the programmable input controller and the programmable display terminal, and the central processing unit is connected with the network port control chip. The mainboard network port is led out by the network port control chip, and is used for service access and software platform management. The programmable input...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com