Automatic vulnerability discovery system and method based on protocol reverse parsing
A protocol reverse and loophole mining technology, applied in transmission systems, electrical components, etc., can solve the problems of high target object authority requirements, lower target object authority requirements, and low degree of automation, so as to reduce authority requirements, improve efficiency and automation. , the effect of expanding the scope of application
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0025] The specific implementation manners of the present invention will be described in detail below in conjunction with the accompanying drawings.
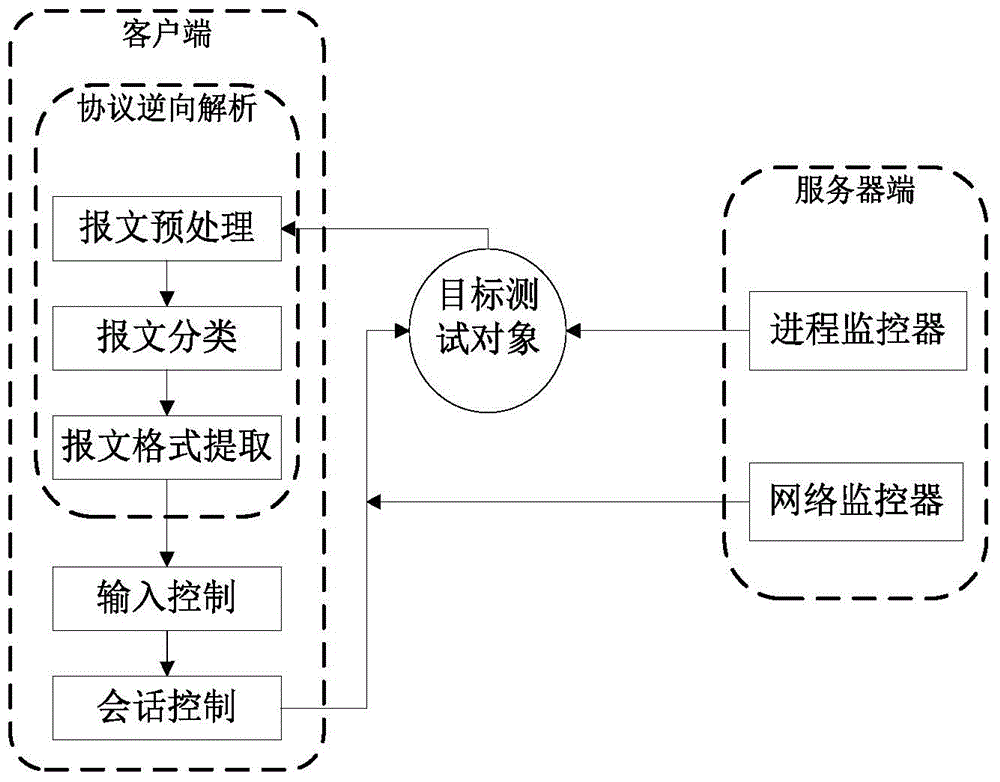
[0026] Such as figure 1 As shown, the automatic vulnerability mining system based on protocol reverse analysis in the present invention combines the protocol reverse analysis technology and fuzzy testing technology to effectively improve the automation of network service software vulnerability mining. The system includes a server and a client, and the server includes process monitoring. module and a network monitoring module; the client includes a packet preprocessing module, a packet classification module, a packet format extraction module, an input control module and a session control module. The main implementation steps of the system are as follows:
[0027] (1) Message preprocessing
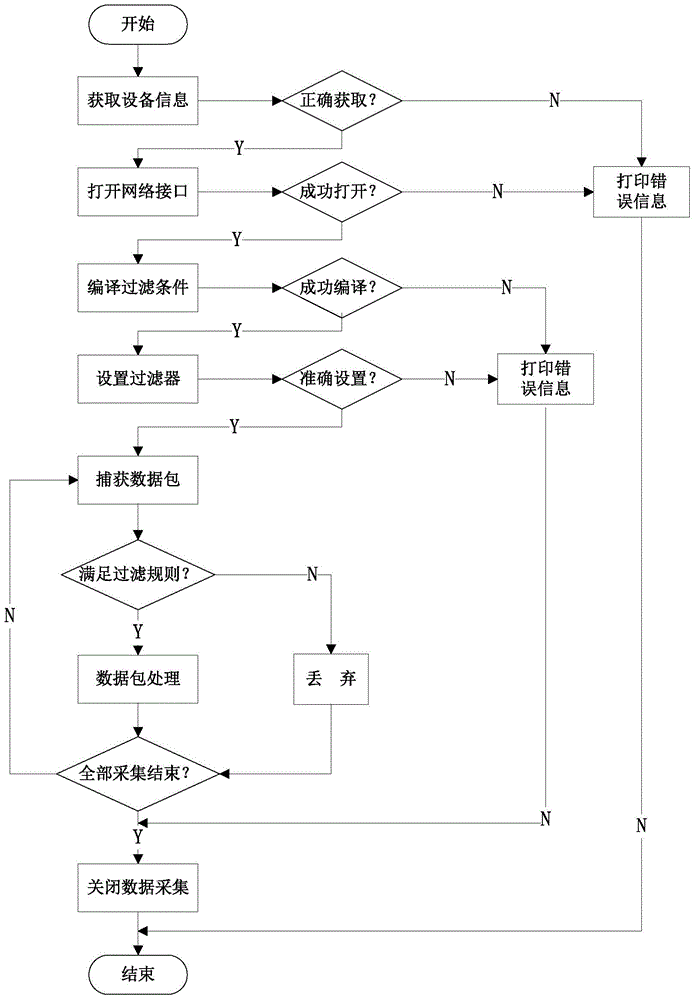
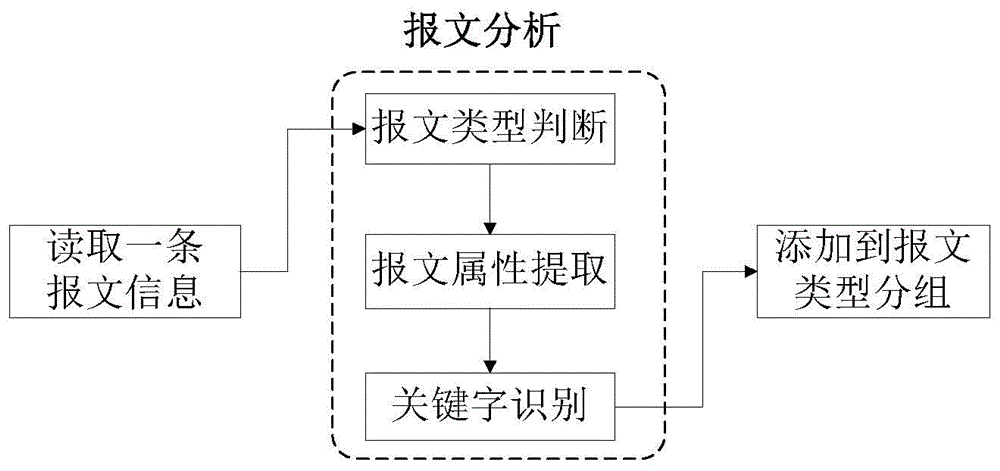
[0028] Message preprocessing first captures the communication data packets of the target test object, then processes the data packets, and ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com