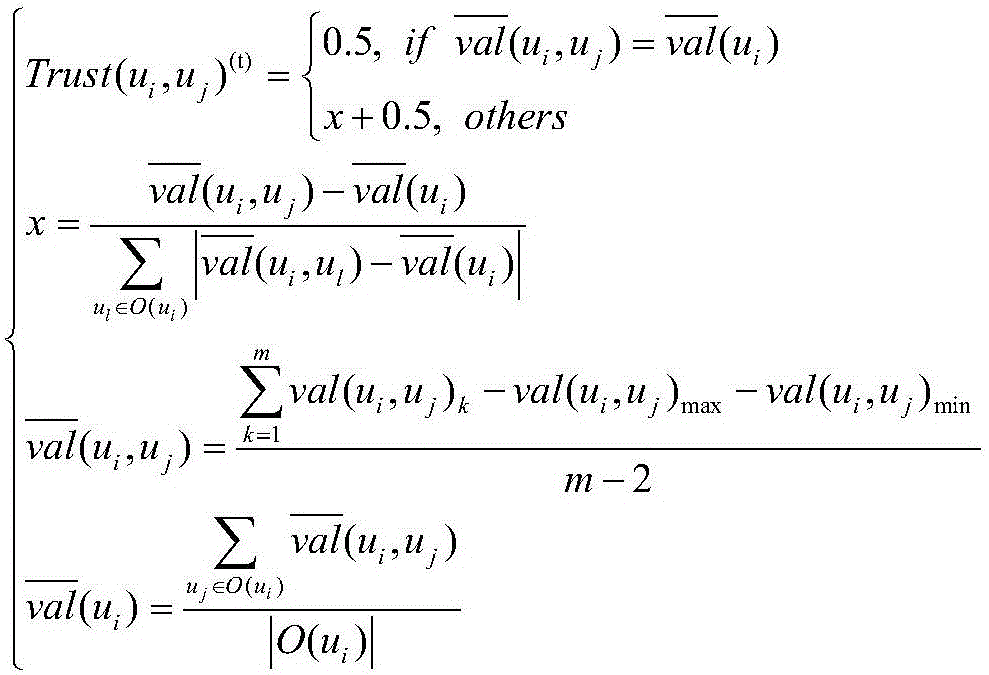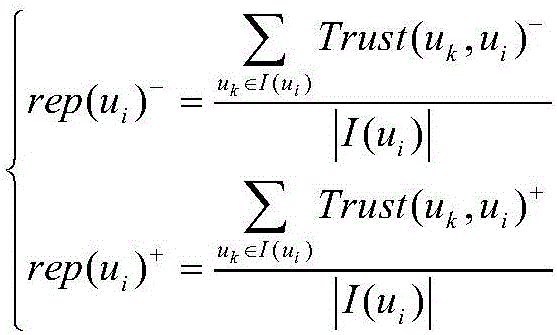Patents
Literature
75results about How to "Improve discovery" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
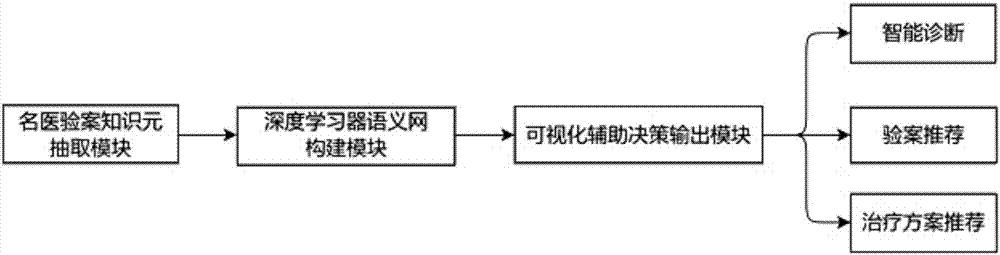
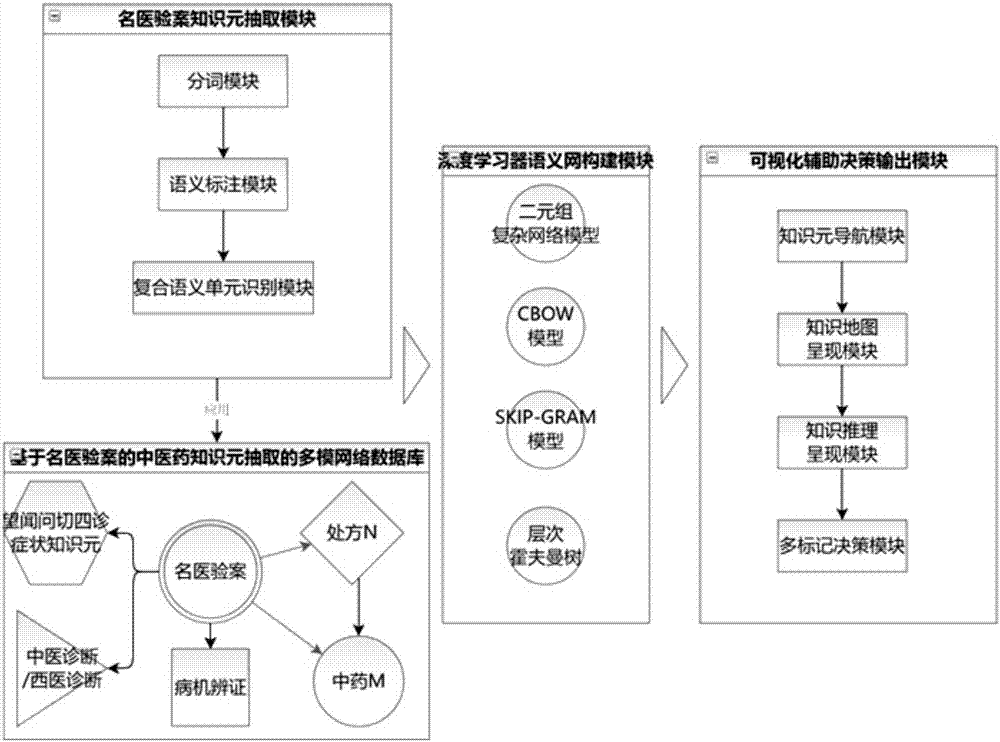
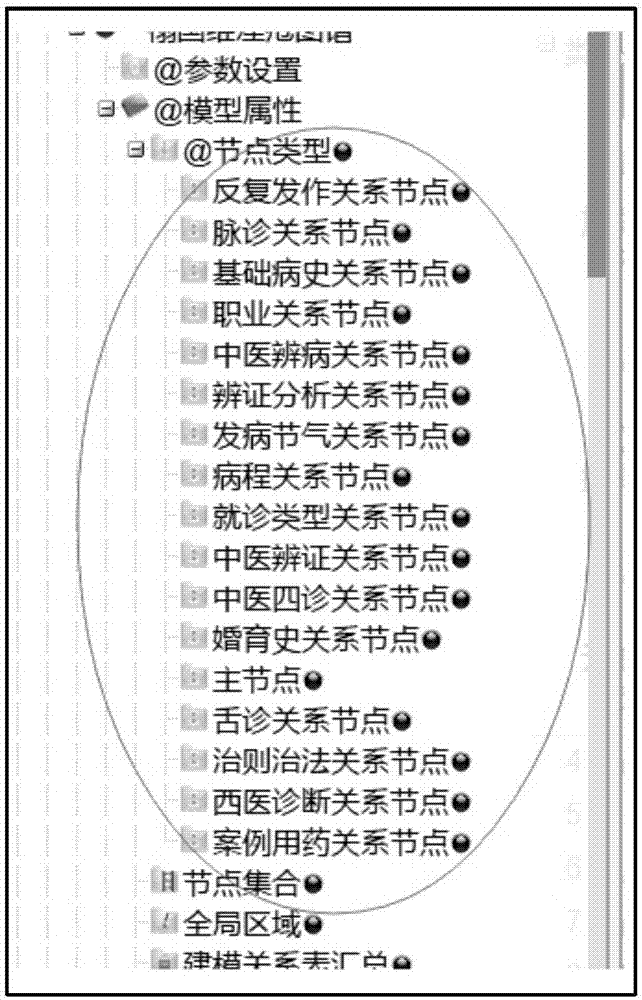
Mining and auxiliary decision intelligent system for traditional Chinese medicine text medical records
ActiveCN106919671AImprove discoveryRich viewing anglesMedical data miningSpecial data processing applicationsNODALMedical record
The invention discloses a mining and auxiliary decision intelligent system for traditional Chinese medicine text medical records and relates to the technical field of natural language processing and traditional Chinese medicine diagnosis auxiliary information. The system is based on unstructured text medical record of real standard clinic medical record; automatic traditional Chinese medicine principle-method-recipe-medicines, treatment according to syndrome differentiation and knowledge extraction and expression are realized; the system comprises a database which is in a rear end server and traditional Chinese medicine and pharmacy knowledge atlas on-line\off-line applications in a front end computer; major formulas, symptom pairs, syndromes, traditional Chinese medicine pathogenesis evolution rule and data links of mutual relation among the above knowledge elements are stored in the database according certain data storage structure. Through the map node retrieval, node set retrieval and area positioning of the traditional Chinese medicine and pharmacy knowledge atlas, the obtained analysis results are mixed with features such as directed network, semantic distance, coordinate setting and topology analysis based on hierarchical cluster, which greatly increases the discovery capability of major formulas, symptom pairs, syndromes, traditional Chinese medicine pathogenesis evolution rule and mutual relation among the above knowledge elements.
Owner:GUANGDONG HOSPITAL OF TRADITIONAL CHINESE MEDICINE
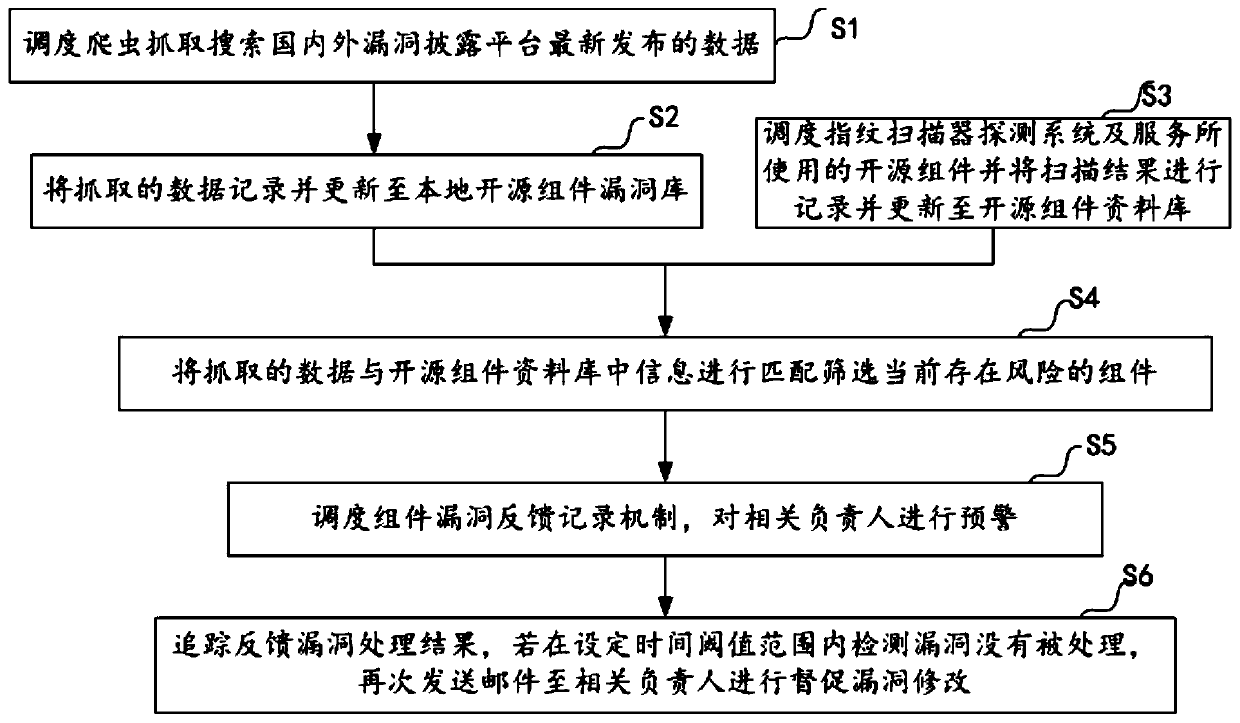
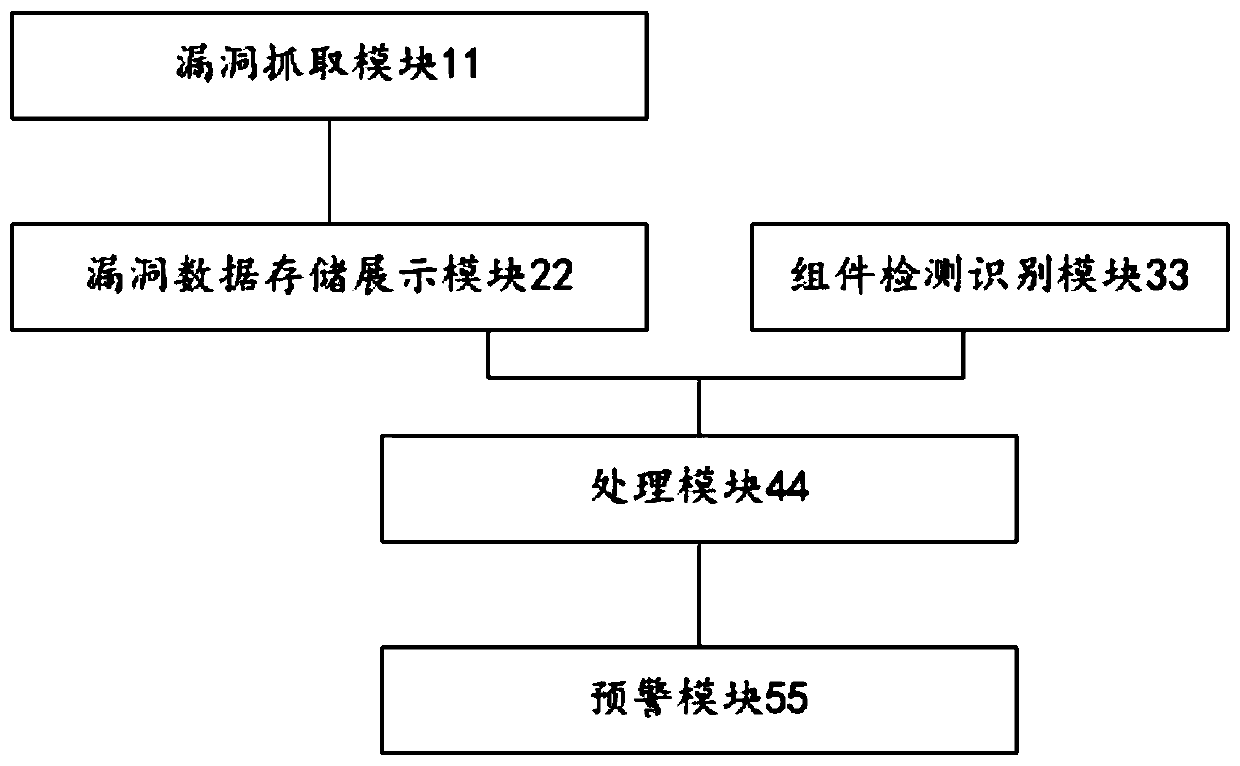
Automatic monitoring method and system for open source component vulnerabilities
InactiveCN110543767AImprove discoveryImprove efficiencyPlatform integrity maintainanceOpen sourceWorkload
The invention provides an automatic monitoring method and system for open source component vulnerabilities. The automatic monitoring method comprises the following steps: scheduling crawlers to searchand capture data newly published by bug disclosure platforms at home and abroad; recording the grabbed data and updating the grabbed data to a local open source component vulnerability library; scheduling an open source component used by the fingerprint scanner detection system and service, recording a scanning result and updating the scanning result to an open source component database; matchingthe grabbed data with information in an open source component database to screen components with risks at present; and performing early warning on related responsible persons by a scheduling component vulnerability feedback recording mechanism. The automatic monitoring method can realize Automatic vulnerability early warning tracking and security construction, so that security personnel only needto pay attention to screened vulnerabilities related to products and companies. Therefore, the extra-large workload is saved, and the security vulnerability discovery and tracking efficiency is improved; the vulnerability tracking range is expanded; and the latest burst vulnerability can be responded within 24 hours, so that the company network security response timeliness is improved.
Owner:SUZHOU LANGCHAO INTELLIGENT TECH CO LTD
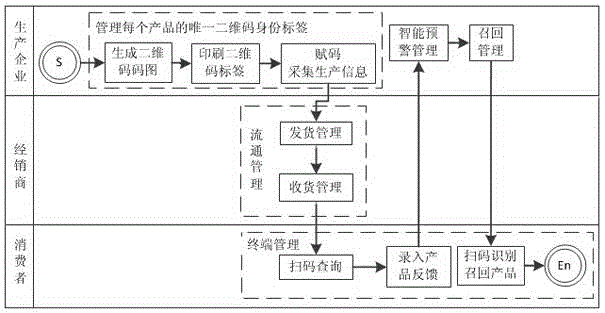
Product recall warning system and method based on two-dimension codes
ActiveCN104700229AIncrease positive feedbackImprove discoveryResourcesLogisticsProduct defectLibrary science
The invention discloses a product recall warning system based on two-dimension codes. The product recall warning system comprises a data management module, a label management module interacting data with the data management module through an internet, a circulation management module, a mobile inquiring terminal, an intelligent pre-warning module and a recall management module. The invention further discloses a product recall warning method based on the two-dimension codes, and the method is characterized in that the unique two-dimension code identity identification label of each product is managed by the label management module, circulation is managed by the circulation management module, the terminal is managed by the mobile inquiring terminal, intelligent pre-warning management is performed to product defects by the intelligent pre-warning module, and product recall management is performed by the recall management module. According to the product recall warning system and the product recall warning method, the user's feedback positivity can be improved, thereby effectively regulating and guiding the user to completely achieve the product's using feedback, effectively performing intelligent pre-warning to a production enterprise, and ensuring that defective products are precisely recalled by the production enterprise.
Owner:广州回我信息科技有限公司
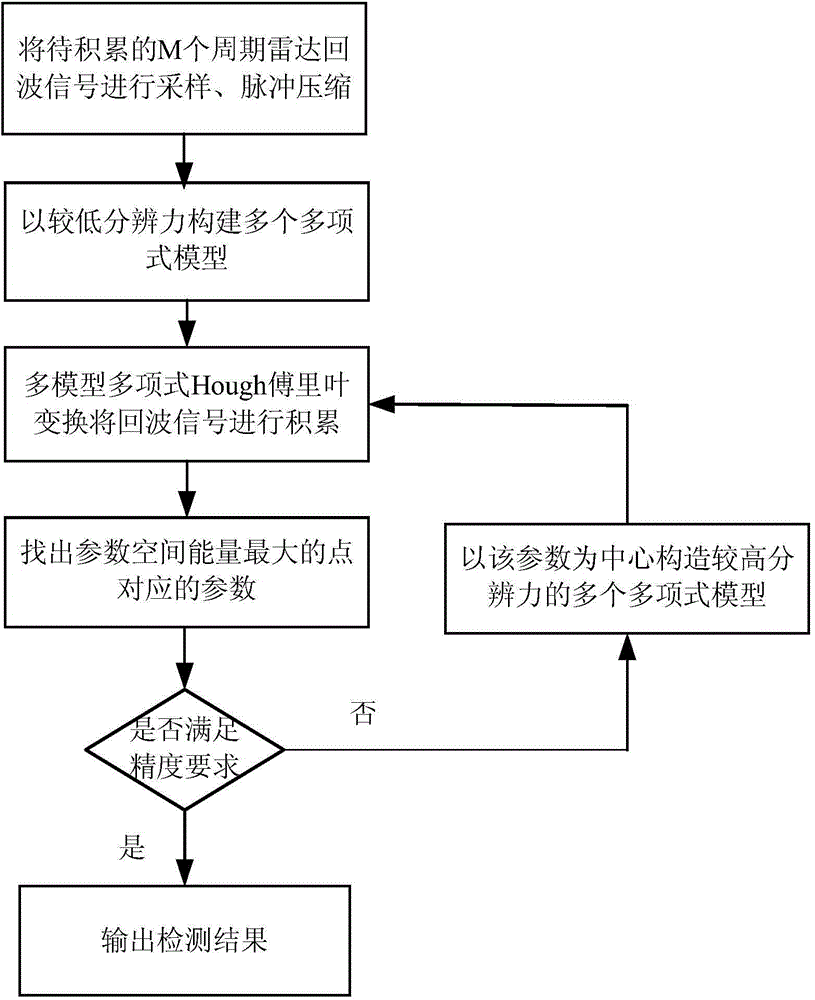
High-speed stealth target detection method of polynomial Hough Fourier transform
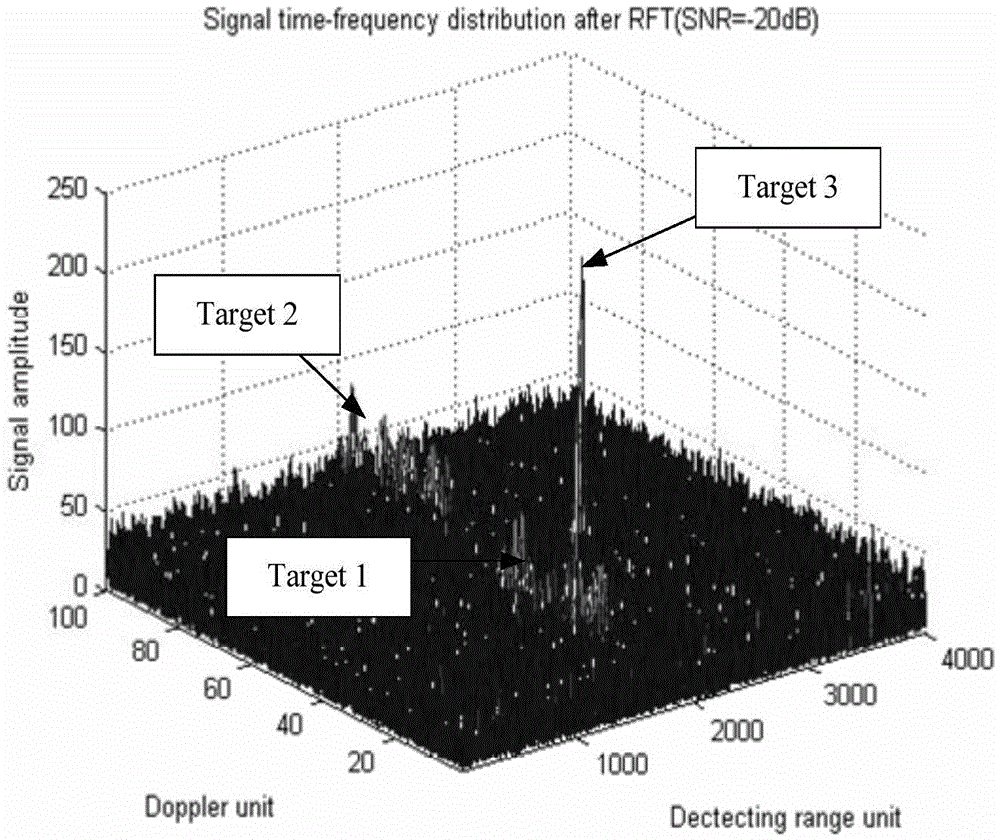
ActiveCN104808188AImplementing coherent accumulation detectionImprove discoveryRadio wave reradiation/reflectionDoppler spreadParametric search
The invention provides a high-speed stealth target detection method of the polynomial Hough Fourier transform, and aims at solving the problems in distance walk and Doppler expansion in accumulated detection of a high-speed maneuvering stealth target. The detection method comprises that polynomial models of relatively high resolution are established, energy accumulation of a parameter space is realized by the polynomial Hough Fourier transform, polynomial models of higher resolution are established according to a parameter corresponding to the maximal energy value of the parameter space, polynomial Hough Fourier transform of high resolution is then carried out in small areas and so on till the requirement for compensation precision is met, and thus, coherent accumulation detection for the high-speed maneuvering stealth target is realized. The searching train of thought is approached layer by layer via the multiple resolution levels of the polynomial models, accumulation detection for the target is realized by the provided polynomial Hough Fourier transform, and compared with multi-dimension parameter search in a large range in a traditional method, the computational complexity, the memory amount and the complex degree can be substantially decreased, and convenience is provided for engineering.
Owner:NAVAL AERONAUTICAL UNIV
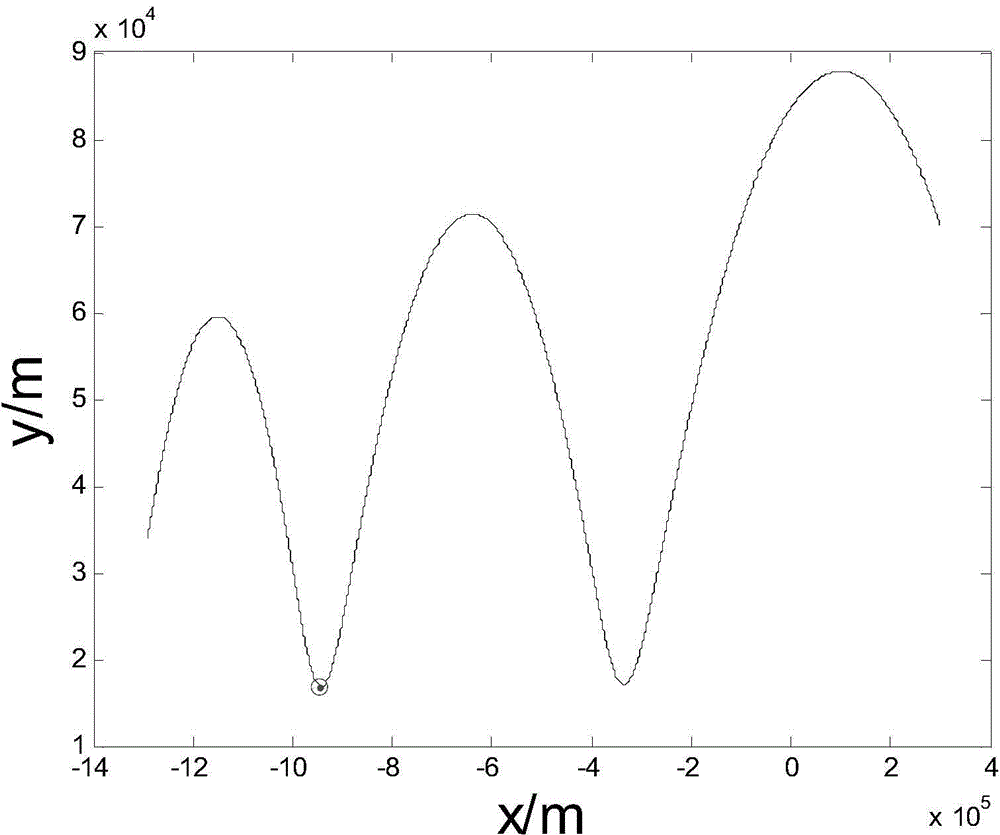
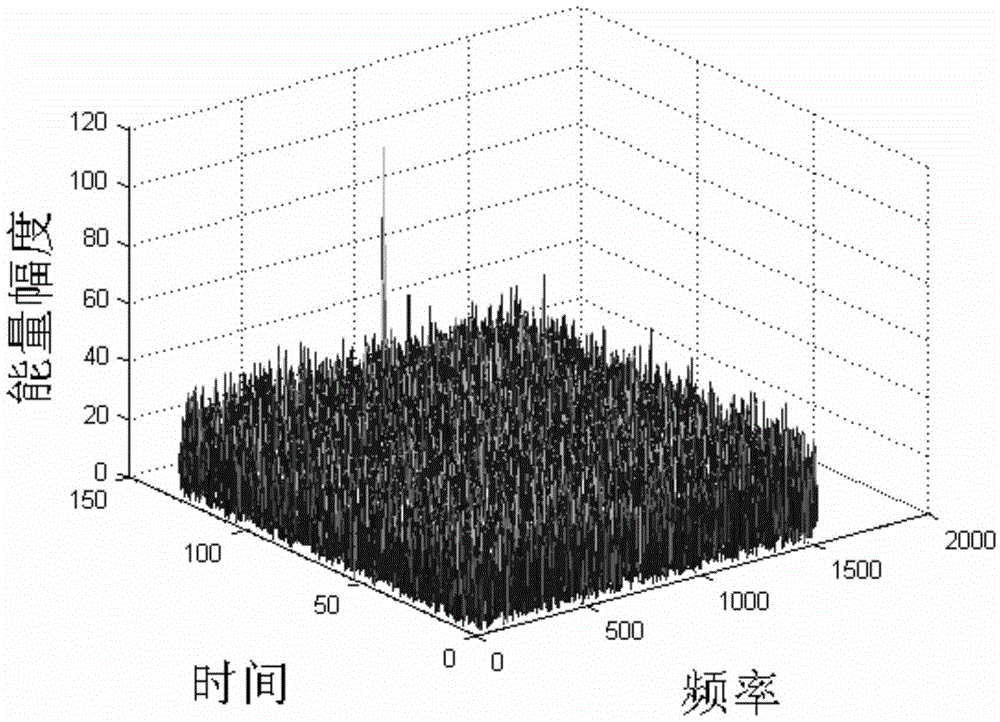
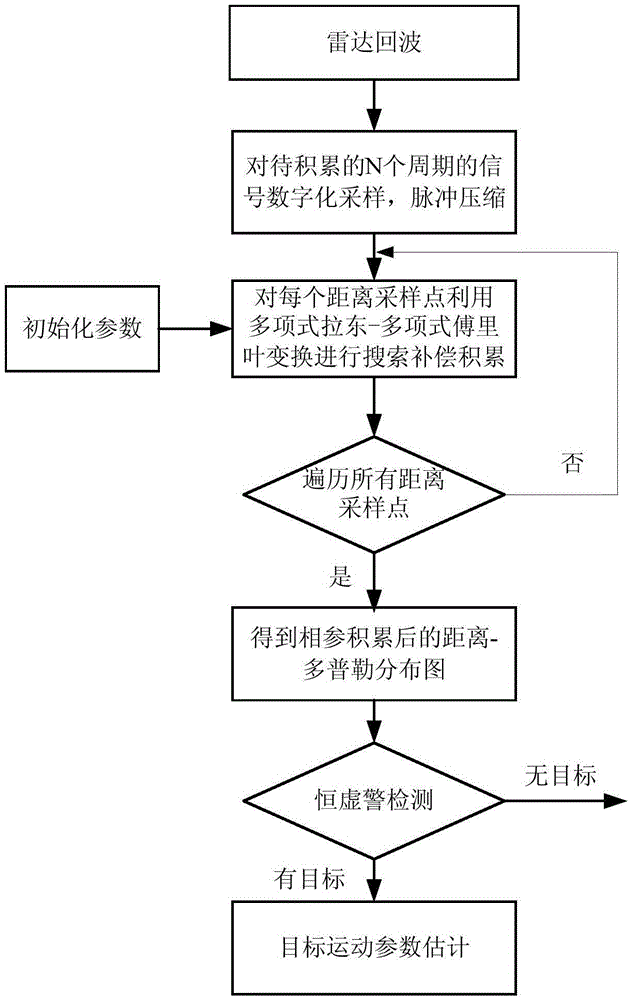
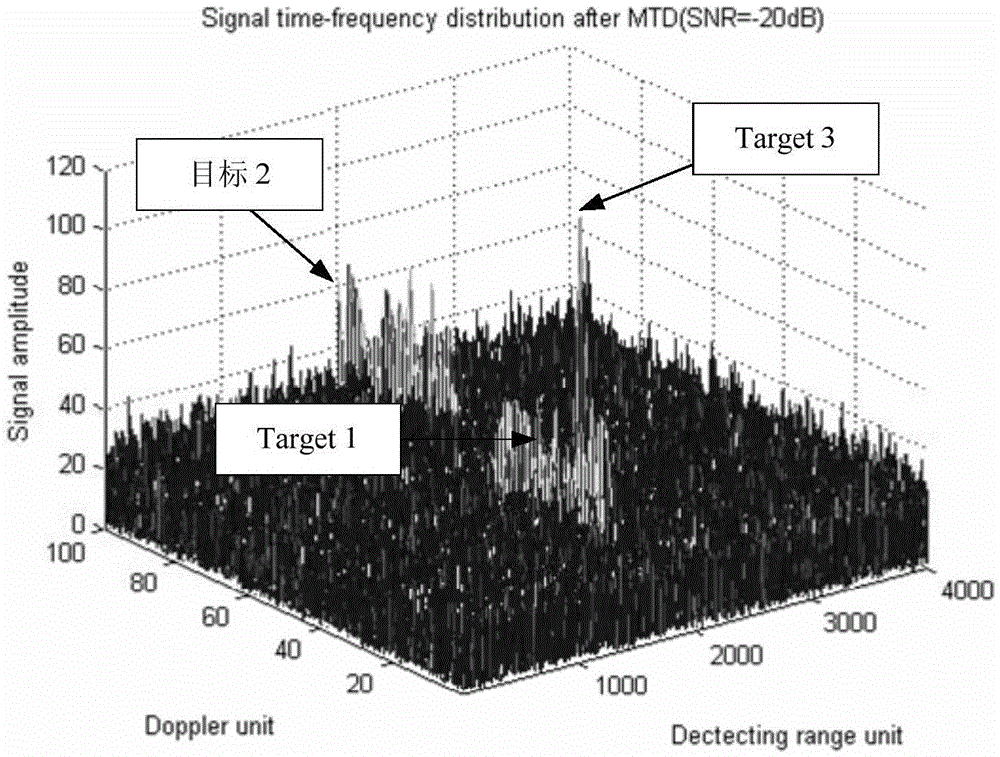
Hypersonic speed target detecting method for polynomial Radon-polynomial Fourier transform
ActiveCN105652258AImprove discoveryCoherent accumulation implementationWave based measurement systemsParametric searchRadar signal processing
The invention relates to a hypersonic speed target detecting method for polynomial Radon-polynomial Fourier transform, and belongs to the technical field of radar signal processing and detecting. The method comprises the steps that N periodic signals to be accumulated are sampled, a slow time-fast time target observed value is extracted, and pulse compression is performed on the sampled signals separately; initialization parameters of polynomial Radon-polynomial Fourier transform are determined; search, compensation and accumulation are performed in a parameter space through polynomial Radon-polynomial Fourier transform to obtain a range-Doppler distribution diagram subjected to phase-coherent accumulation; constant false-alarm detection and target motion parameter estimation are performed on the range-Doppler distribution diagram. According to the method, model building is performed on target motion through polynomial, range walk and Doppler spread of the signals are compensated through parameter search of the polynomial, and therefore effective accumulation detection on a high-speed high-mobility target can be achieved under a low signal-to-noise ratio background; in addition, effective search on the multi-dimensional parameter space is achieved in a multi-resolution search mode, and therefore the search real-time performance is improved.
Owner:NAVAL AVIATION UNIV
Automatic target discovery method based on water sound target bearing history plot
ActiveCN110542904AImprove discoveryImprove noise immunityAcoustic wave reradiationLeak detectionDependability
The invention discloses an automatic target discovery method based on a water sound target bearing history plot. The method comprises steps as follows: establishing an observation window at the current moment on the water sound target bearing history plot; sliding a plurality of established matching templates on the observation window, calculating a correlation coefficient spectrum of each matching template relative to the observation window, and accordingly, establishing a correlation coefficient matrix of the current observation window; calculating a target detection probability spectrum ofthe current moment on the basis of the correlation coefficient matrix; and determining whether a target exists in the corresponding bearing of each element of the target detection probability spectrum, and obtaining a target direction-finding result. The method has higher finding capability for a target with the bearing rapidly changing, has higher anti-noise capability for image-level noise, canbetter balance false alarm and leaking detection and has higher reliability.
Owner:INST OF ACOUSTICS CHINESE ACAD OF SCI
Surface wave in-situ flaw detection method of rotor blade with coating
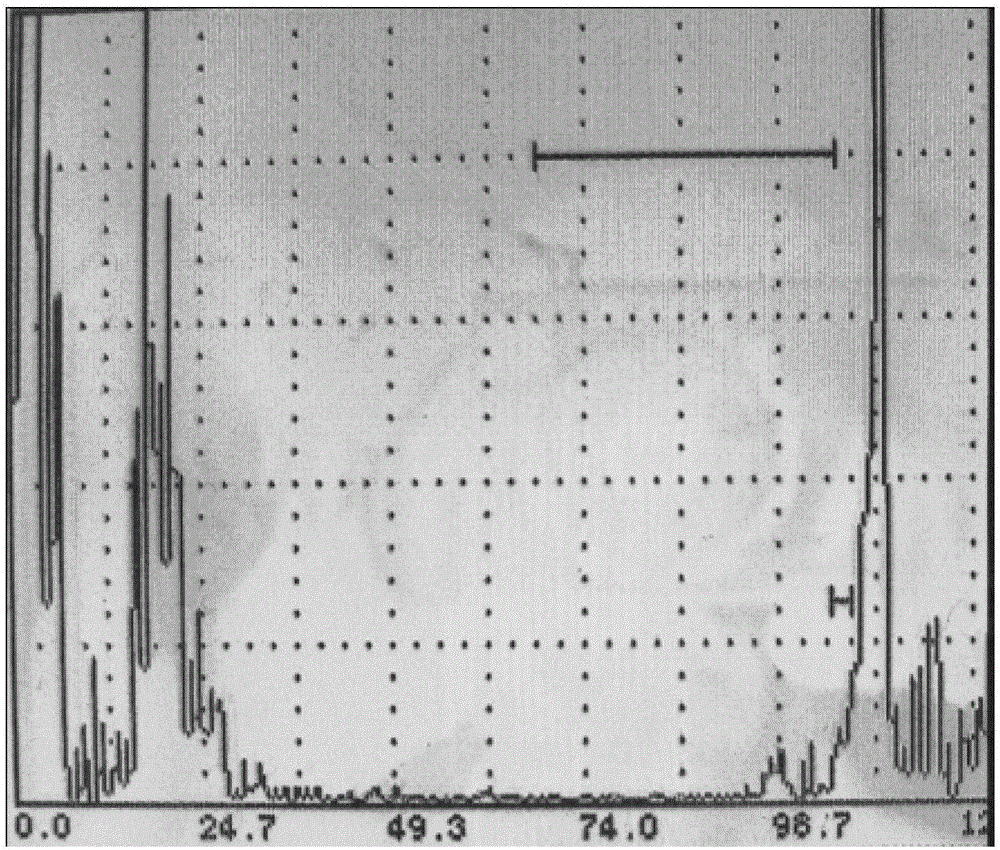
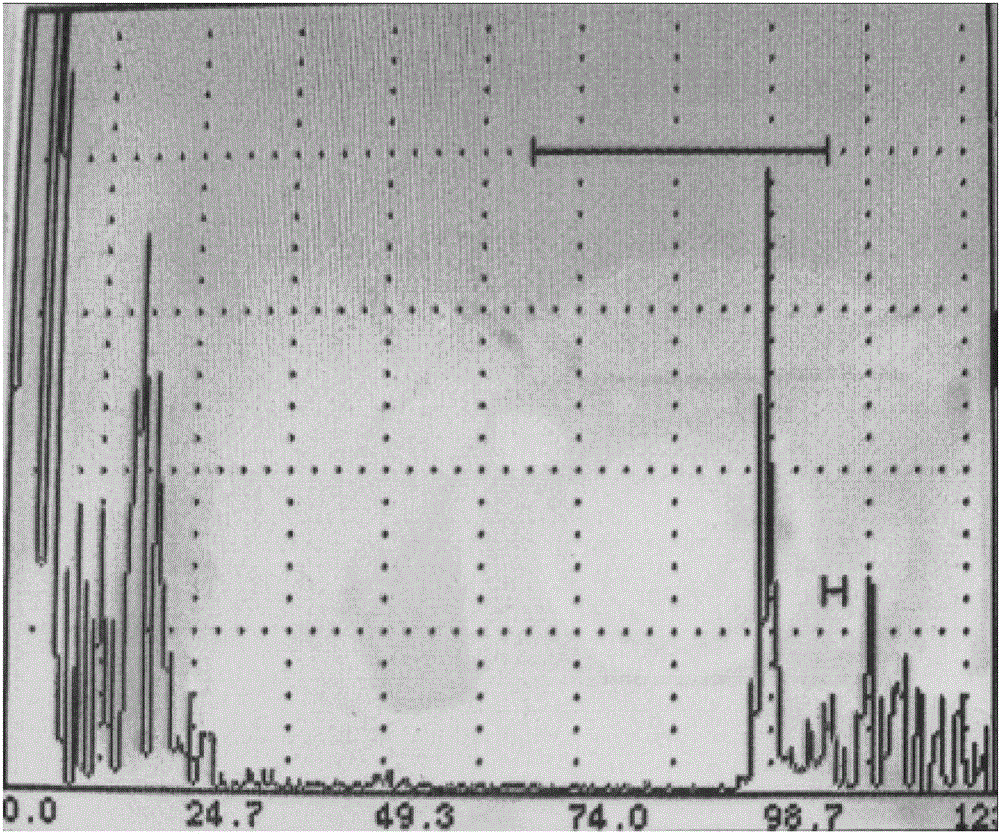
InactiveCN103063742AImprove discoveryAccurate scanning of small defectsAnalysing solids using sonic/ultrasonic/infrasonic wavesSurface waveEngineering
The invention relates to a surface wave in-situ flaw detection method of a rotor blade with a coating. The invention belongs to the technical field of aircraft engine, and is mainly used in surface wave in-situ detection of aircraft engine rotor blades with coatings. With the method provided by the invention, coating thickness influence can be sufficiently excluded, and discovery capability of tiny defects on blade surface and near-surface can be improved. The method comprises the steps that: an ultrasonic flaw detector is started, and a surface wave probe is connected to the ultrasonic flaw detector; a positioning fixture is placed on a blade contrast sample with artificial flaw, and sensitivity is checked; the positioning fixture is fetched from the blade contrast sample, and is placed on a blade requiring flaw detection; the surface wave probe is moved from outside to inside along a slot of the positioning fixture, and is swung left and right, until the probe reaches a slot limit end, such that blade scanning is finished; when blade scanning is finished, the positioning fixture is removed, and an coupling agent on the blade is wiped off; and the other blades are scanned one by one with the same method.
Owner:SHENYANG LIMING AERO-ENGINE GROUP CORPORATION
Method for improving finding ability of local area network device
InactiveCN107493213AImprove discoverySpecial service provision for substationData switching by path configurationClient-sideProtocol for Carrying Authentication for Network Access
The invention discloses a method for improving finding ability of a local area network device. The method comprises steps that A, after a server end is connected to the network, the server end establishes two threads, wherein the first thread periodically broadcasts the service IP and port information of the server end to the outside once at the time interval of T1 and the second thread uses an mDNS protocol to publish the service IP and the port information of the server end when being started at an interval of 30 seconds; B, after a client is connected to the network, the client receives the service IP and the port information of the server end sent by the two threads, and queries the server end according to the service IP and the port information of the server end, and meanwhile, the server end sends broadcasting, multicasting and mDNS messages to the client in the local area network; and C, the client starts the threads to query the server end at the time interval of T2 periodically. According to the invention, by combining the multicasting, the broadcasting and the mDNS finding technology, the finding ability of the client device in the local area network is improved.
Owner:SICHUAN PANOVASIC TECH
Wireless network coverage blind area sensing method and system
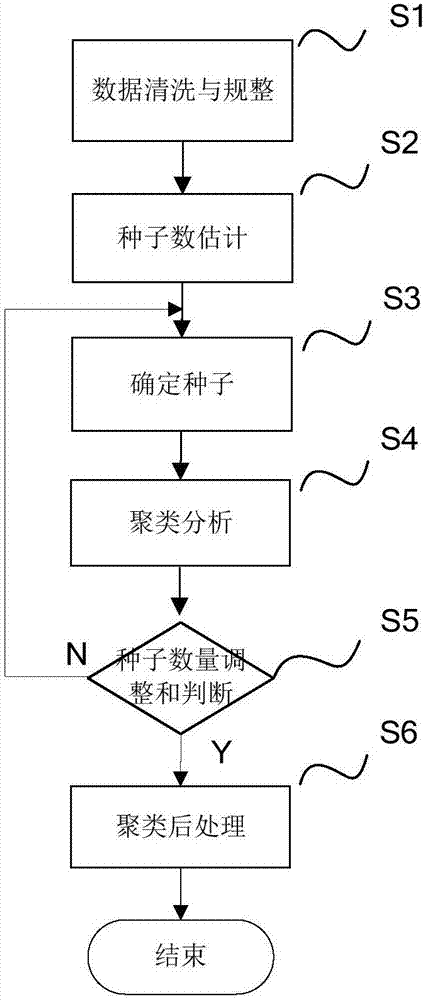
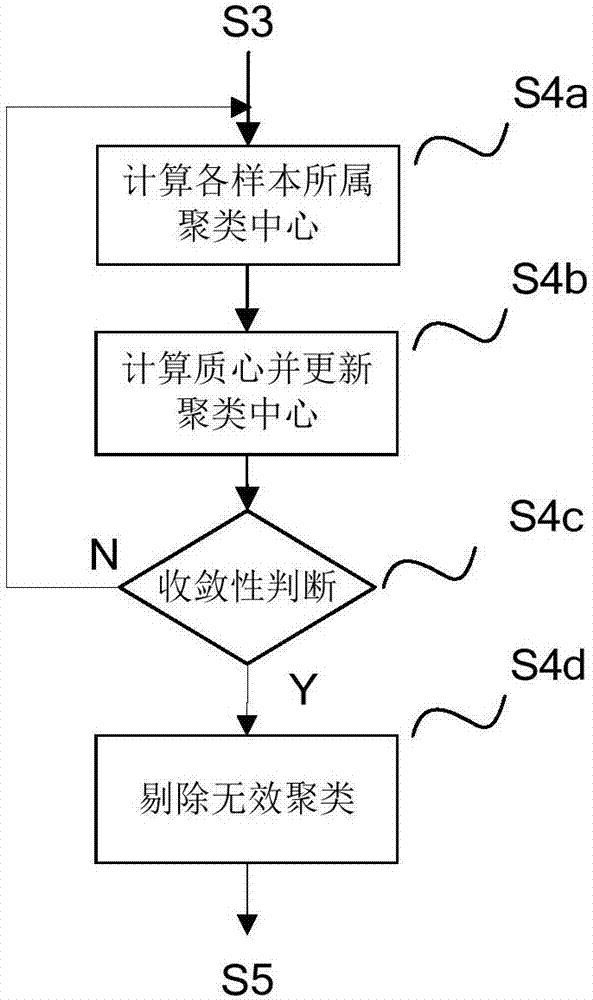
ActiveCN106992902AImprove coverage qualityImprove discoveryLocation information based serviceData switching networksData setComputer science
The invention relates to a wireless network coverage blind area sensing method and system. According to the method, an analysis area and an analysis period are selected and a wireless network signal data sample set collected from a mobile terminal is received. The method is characterized in comprising the following steps of carrying out data washing and sorting on a data set collected in the analysis period; determining a value range of the seed number and taking the value range of the seed number as a control parameter for outer layer circulation of clustering analysis; selecting k initial clustering centers as seeds in a test target analysis area; on the basis of the determined seed number k and the selected k seeds, carrying out inner layer iteration through adoption of a k-means method, changing a value of the seed number k according to the determined value range of the seed number, repeating a process of calculating and selecting the seeds until all seed number is iterated completely; and determining a final output result. According to the method and the system, a coverage blind area of the mobile terminal can be timely and accurately discovered, and a blind area position, a range and the serious degree are calibrated.
Owner:BEIJING UNION UNIVERSITY
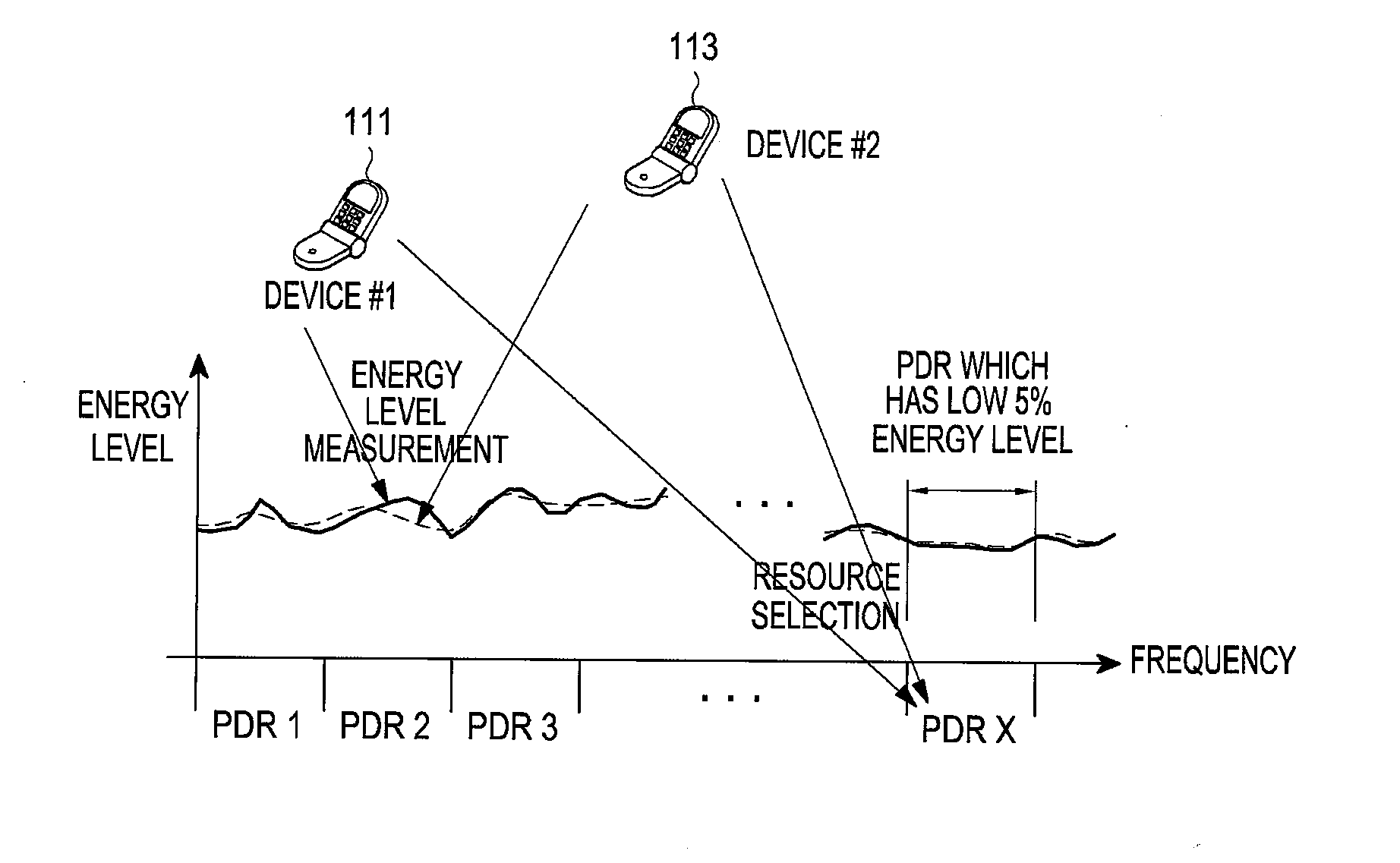
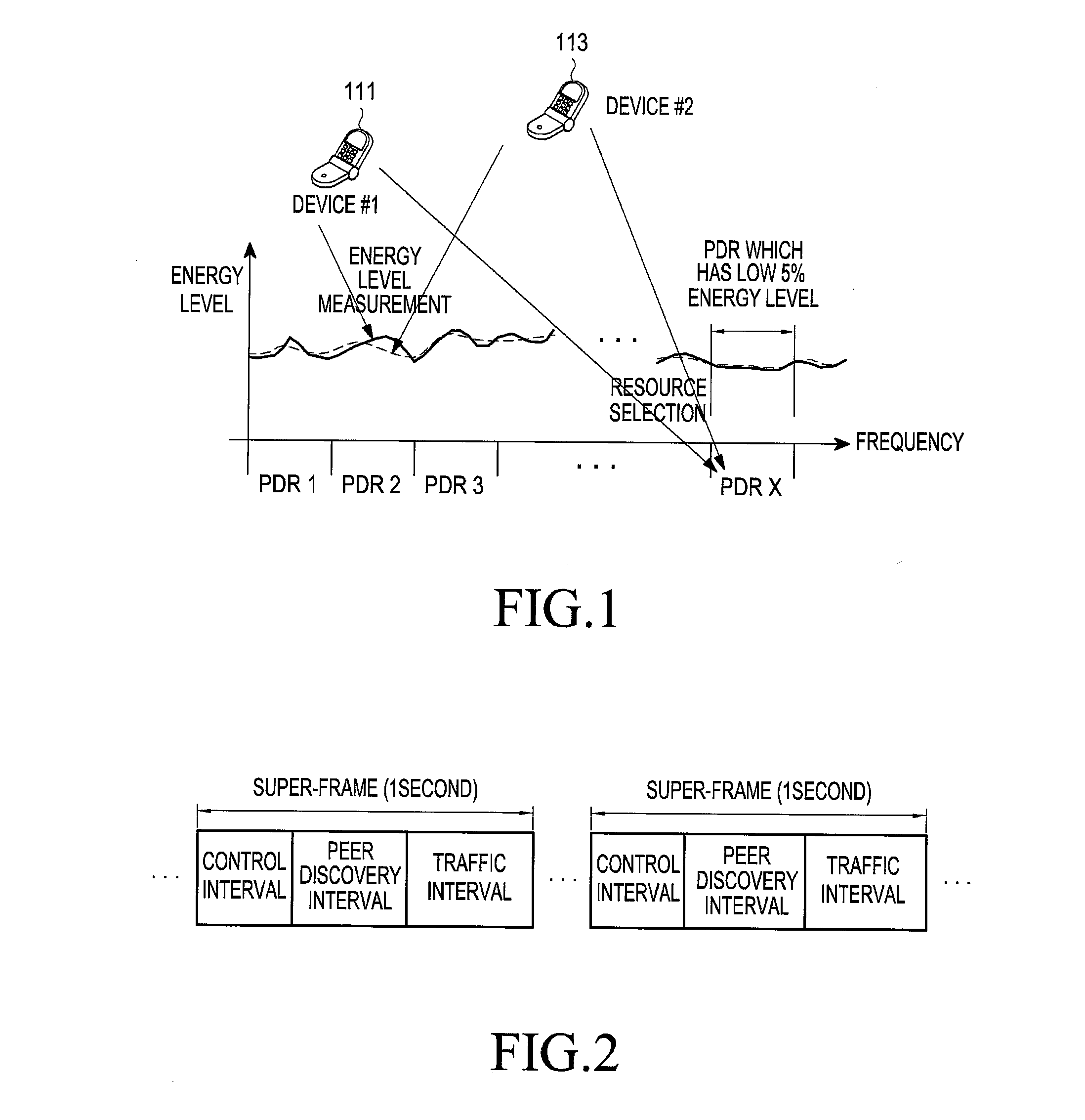
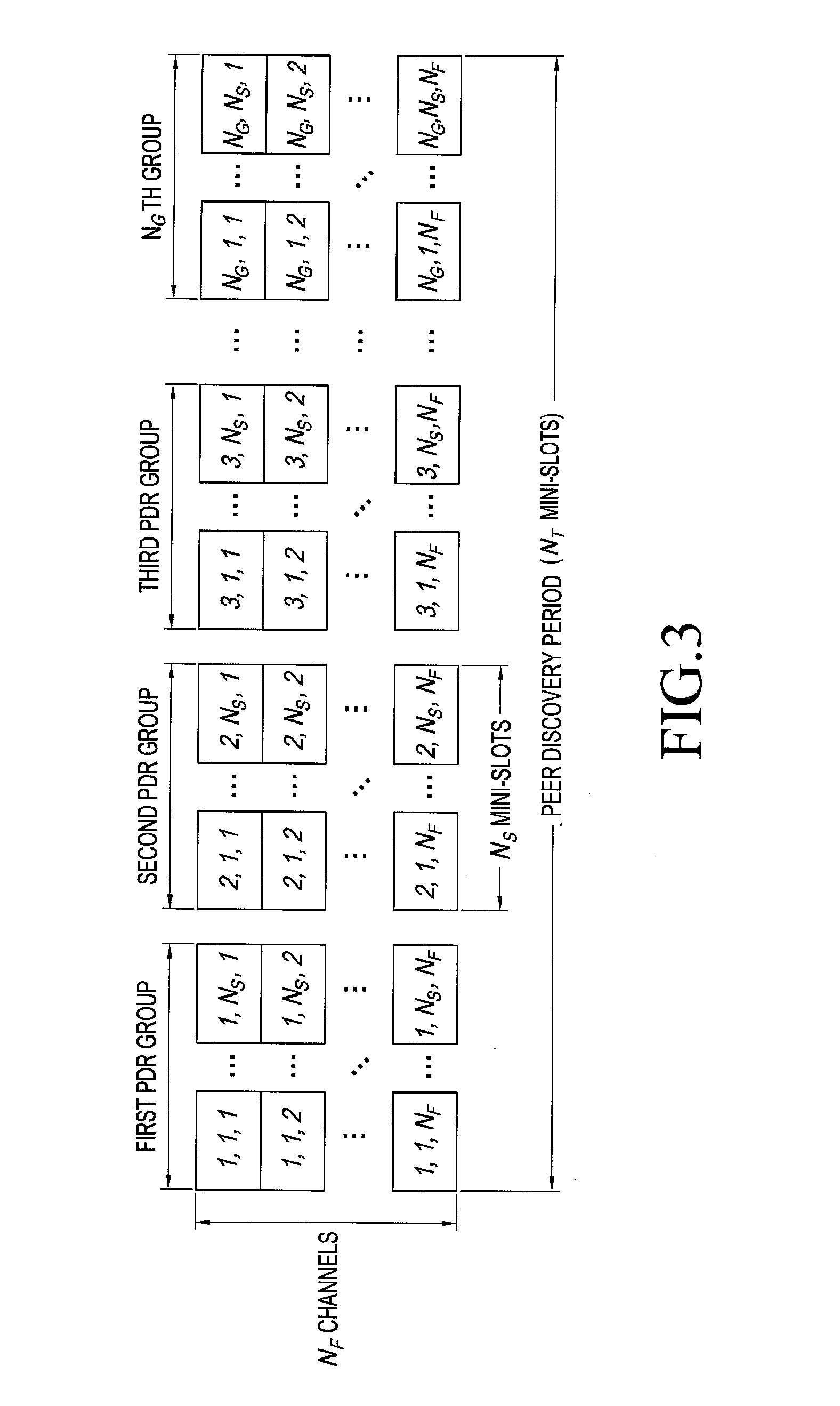
Apparatus and method for selecting peer discovery resource in device-to-device communication system
ActiveUS20160198330A1Improve discoveryMinimize collisionError preventionConnection managementCommunications systemHigh data rate
The present disclosure relates to a pre-5th-generation (5G) or 5G communication system to be provided for supporting higher data rates beyond 4th-generation (4G) communication system such as a long term evolution (LTE). The present invention relates to a method for selecting, by a device, a peer discovery resource (PDR) in a device-to-device (D2D) communication system, the method comprising the steps of: determining a PDR selection range which can be selected by the device; and selecting a PDR in the determined PDR selection range.
Owner:SAMSUNG ELECTRONICS CO LTD +1
Regression testing method
InactiveCN107391376AReduce crossoverReduce complexitySoftware testing/debuggingRegression testingMilestone
The invention relates to the technical field of software testing and discloses a regression testing method. The regression testing method comprises the following steps that 1, examples are screened, and example sets are established; 2, example-example set-automatic example interface multi-mapping relation is established; 3, example set milestones are established; 4, the crossing degree and multi-mapping rate of the example sets are quantified. The example sets are screened based on service logic combination and bug analysis. The complexity of traditional example screening based on a function and path analysis mode is reduced. The path coverage degree is improved, and the crossing degree of the examples is reduced. The multi-mapping rate is established, the example reuse rate is improved, and the efficiency of establishing automatic regression is improved, and the whole regression testing process is optimized. The execution priorities of the examples are classified. The process of executing example scheduling, the execution efficiency, the time consumed for execution and example set milestones are controlled. The method is conductive to advanced finding of issued bug and facilitates multiple times of iterations, the regression testing cost is reduced, and the bug finding capability is improved.
Owner:COLASOFT
A text subtopic discovery method based on improved LDA
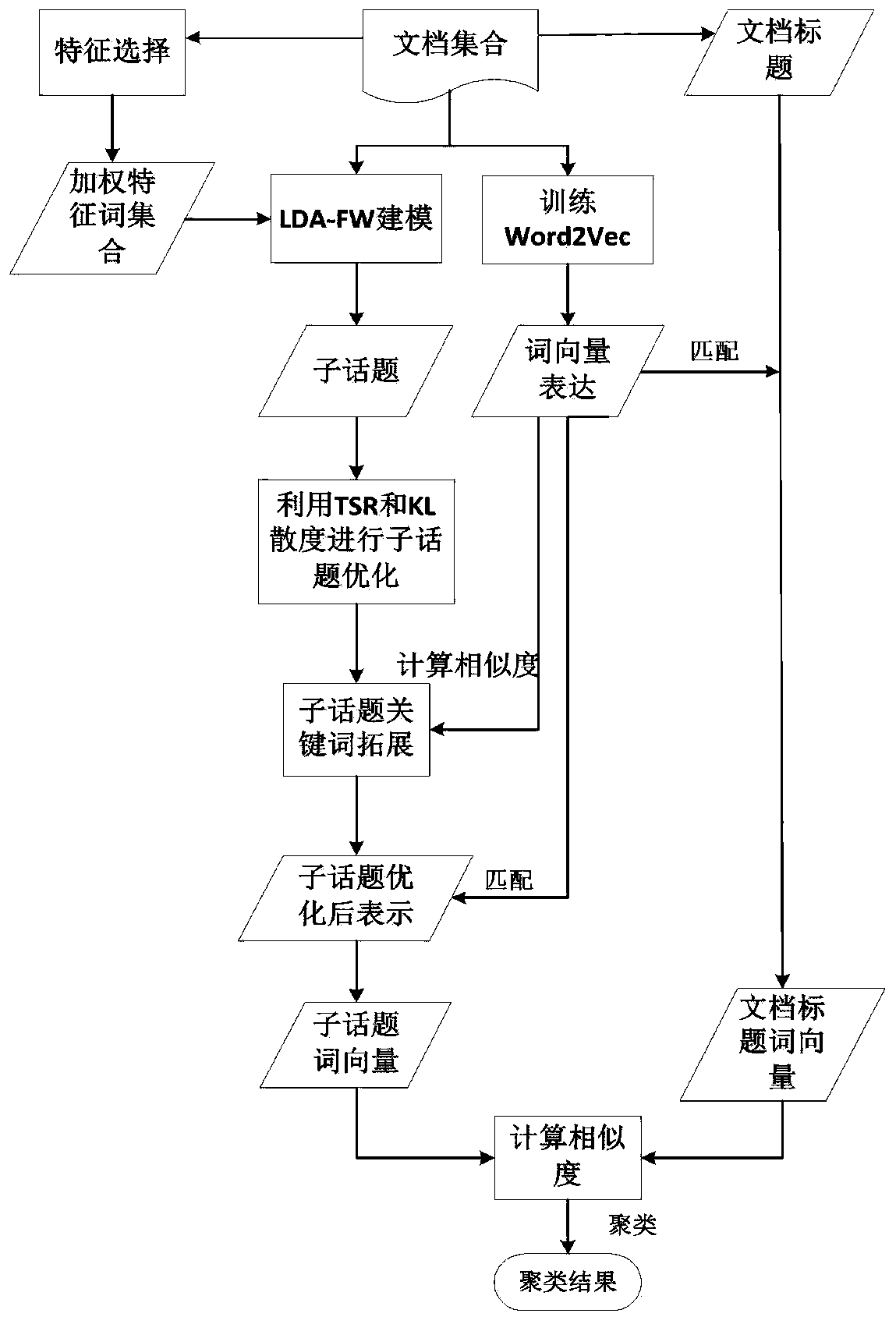
ActiveCN109885675AOvercome the problem of weak semantic understandingImprove discoveryText database queryingSpecial data processing applicationsAlgorithmTf–idf
The invention discloses an improved LDA-based text subtopic discovery method. The method comprises the following steps: 1, calculating TF-IDF value of words in a text set; taking nouns and verbs withTF-IDF values greater than a threshold value as feature words of next weighting; 2, finding subtopics and corresponding keywords based on a feature word weighted LDA model; 3, optimizing the subtopicsbased on a TSR method and KL divergence; 4, enabling the Word2Vec model to expand for the subtopic keywords, and improving the semantic comprehensiveness of the subtopic keywords; and 5, constructinga subtopic word vector and a title word vector, and clustering by utilizing a cosine distance. According to the method, the subtopic discovery effect can be improved on the aspects of topic discrimination and semantic comprehensiveness.
Owner:HEFEI UNIV OF TECH
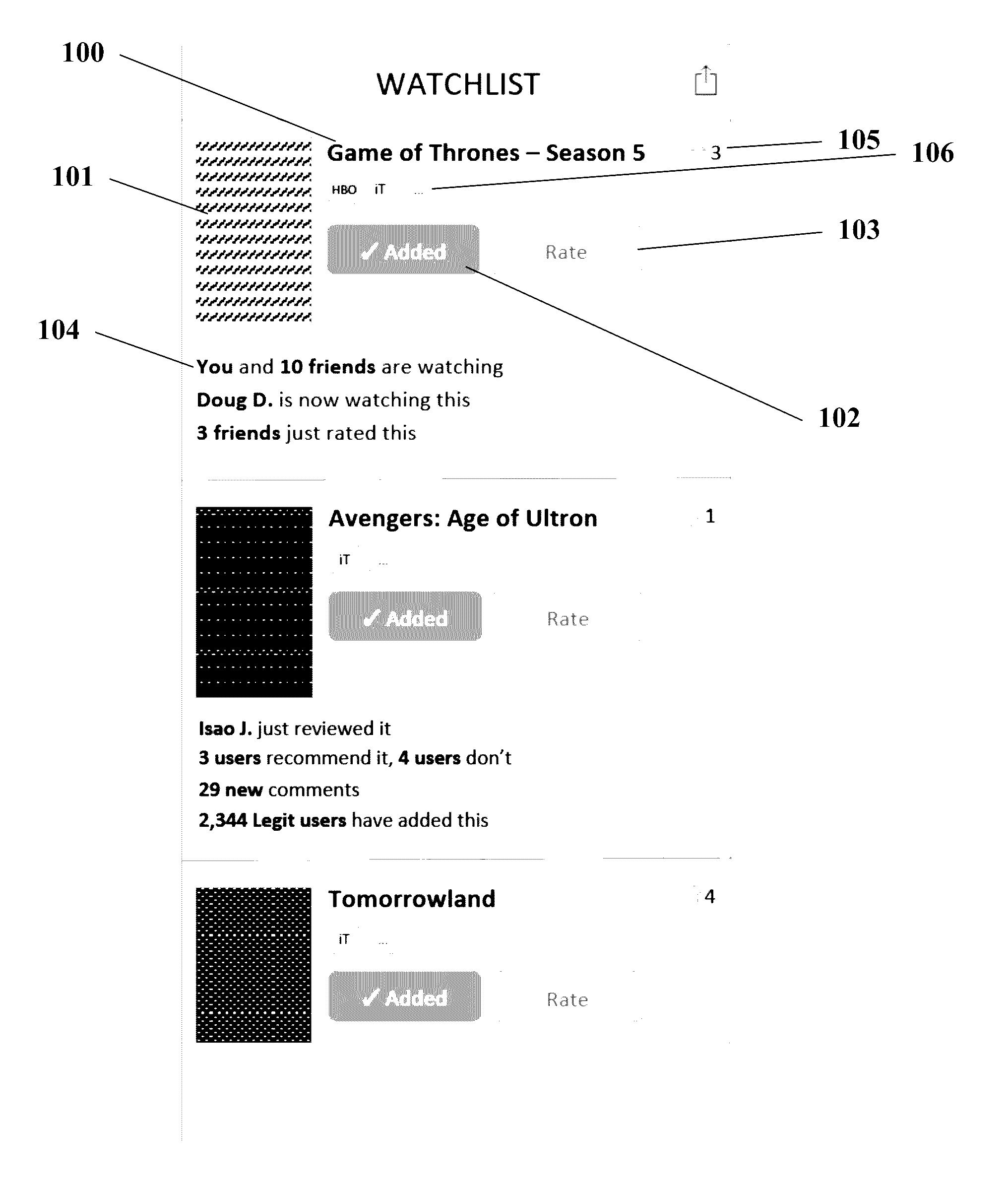
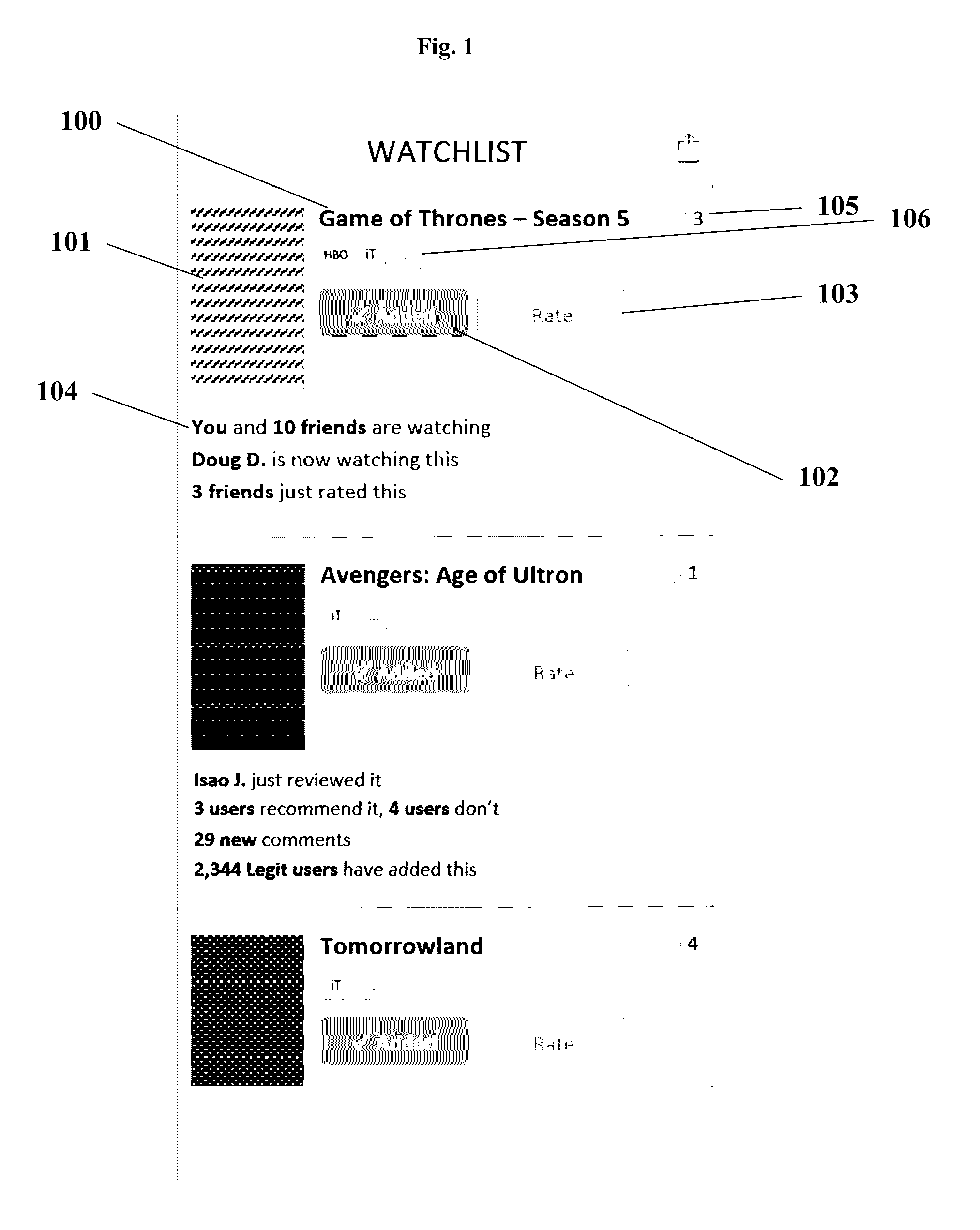
Systems, media, and methods for providing an algorithmically sorted watchlist or wishlist
ActiveUS20160360253A1Enhance interestIncrease engagementSelective content distributionCommunity orSocial web
Described are platforms, systems, applications, and methods for algorithmically updating a user configured watchlist or wishlist based on activity of social network connections including: adding an item to a watchlist, consuming or acquiring an item, rating an item, recommending an item, and discussing an item, as well as aggregated activity of a community or population of users within the social network.
Owner:BLAB VENTURES LLC
Method for assisting a user of a motor vehicle, multimedia system, and motor vehicle
ActiveUS20140236423A1Improve discoveryEasy to findRoad vehicles traffic controlDigital data processing detailsMultimedia systemMotorized vehicle
A method for assisting a user of a motor vehicle, including: acquiring parameters associated with a context in which the motor vehicle is being used; developing a list of suggested actions; selecting a suggested action from among the list of suggested actions in accordance with the context in which the motor vehicle is being used; and transmitting the selected suggested actions to the user via a man / machine interface. A multimedia system, a motor vehicle, and a computer medium can implement the method.
Owner:RENAULT SA
Patrol process management system
The invention discloses a patrol process management system structurally comprising patrol management, rights management, daily work, and talent pool management. Specific operation content and a related table certificate book embedding system are managed in the form of workflow. The system satisfies the actual requirement of patrol bottleneck and the urgent requirement for improving the efficiency of patrol work and the effectiveness of patrol. By use of the means of informatization, the purpose of 'concentrating the scattered, bringing the far closer and refining the coarse' is achieved, doubtful points can be found and deviation can be rectified, and the risk can be eliminated in the bud. Informatization develops quickly. Massive data is accumulated, which can provide a powerful data support for the inspection group to analyze doubtful points and find problems. The data is directly transferred through a system workflow engine, and is developed and utilized on the basis. The basis of in-depth analysis is provided for inspecting key contents. The capacity of finding problems is improved. Conditions are created for informationized and electronic management. The effectiveness of patrol work is further improved.
Owner:INSPUR QILU SOFTWARE IND
Electronic inspection method based on data analysis
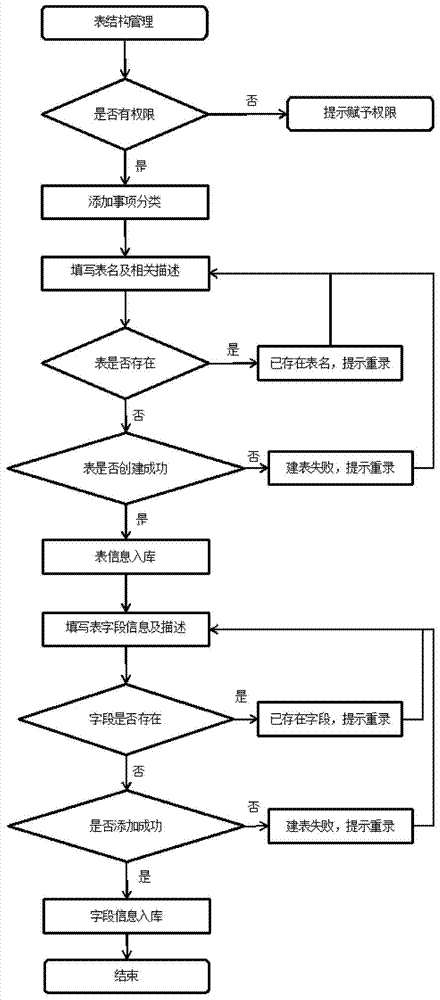
InactiveCN107358409AImprove discoveryImprove securityDigital data protectionOffice automationProcess orientedWorkload
The invention discloses an electronic inspection method based on data analysis. The method comprises steps that firstly, an electronic inspection system is constructed; a table structure is dynamically generated in the electronic inspection system; early warning events are added to the electronic inspection system and are used for providing prompting for data violating rules when various data are filled into tables; in the electronic inspection system, dynamic splicing of a static page and script events is carried out according to the generated table structure information and the early warning operation information; the inspection information is filled into the electronic inspection system, the inspection information is analyzed by the system, and the analysis result is displayed on the static page. Compared with the prior art, inspection work efficiency is substantially improved, standardized, process-oriented and intelligent inspection work is realized, manual audit workload is substantially reduced, acquisition accuracy of suspected points is effectively improved, and strong practicality is realized.
Owner:SHANDONG INSPUR COMML SYST CO LTD
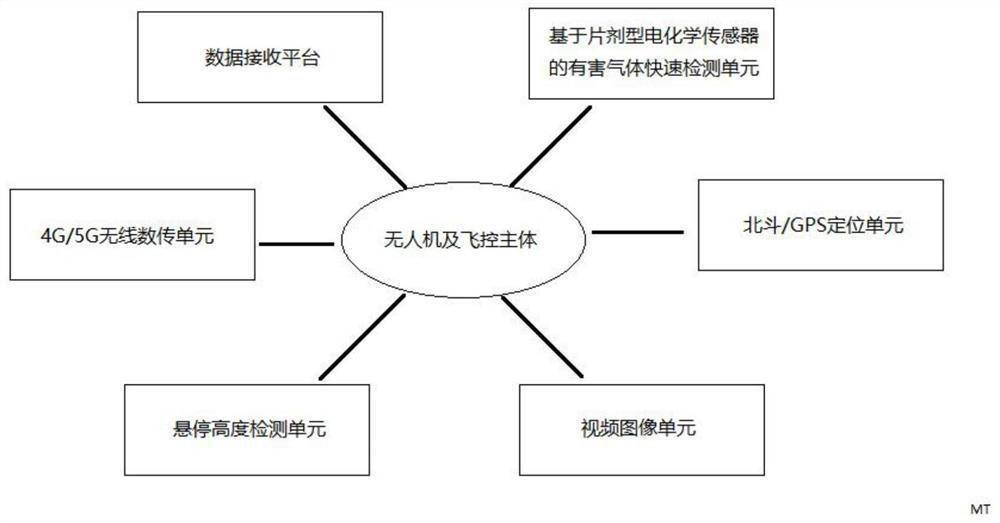
Harmful gas distribution and traceability detection method in airspace range based on unmanned aerial vehicle
PendingCN112327904AIncrease awarenessReduce weightAnalysing gaseous mixturesHeight/levelling measurementUncrewed vehicleEngineering
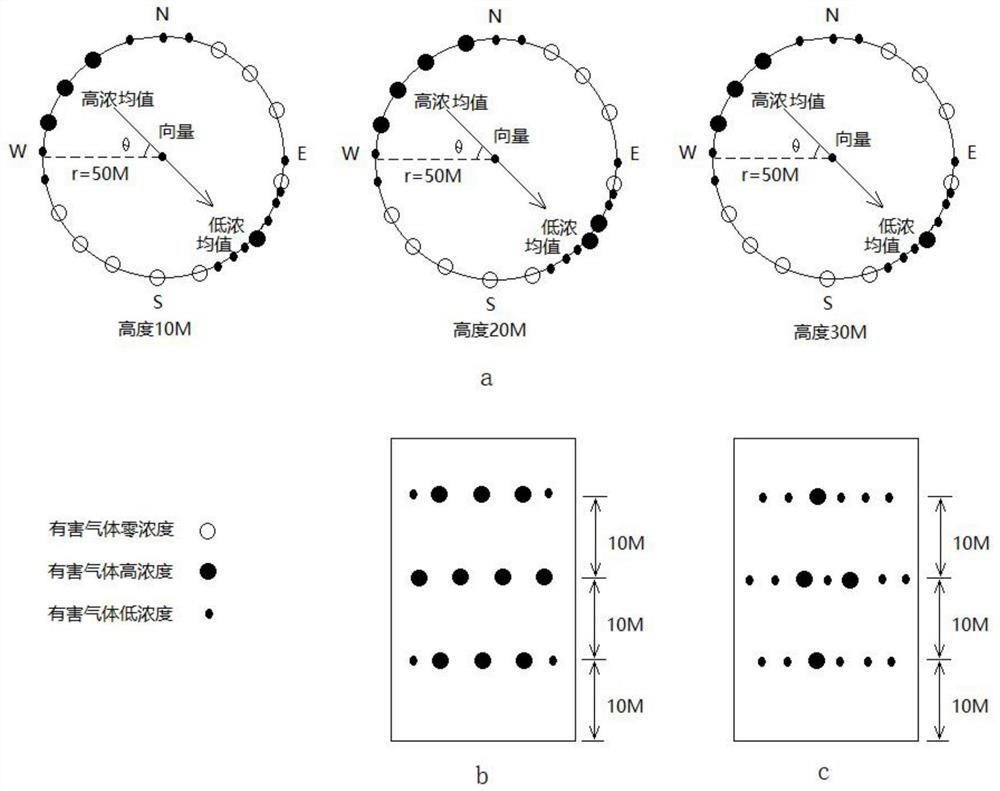
The invention relates to a harmful gas distribution and traceability detection method in an airspace range based on an unmanned aerial vehicle. An unmanned aerial vehicle system carrying a harmful gasrapid detection unit based on a tablet electrochemical sensor, a hovering height detection unit, a video image unit, a positioning unit and a wireless data transmission unit and a data receiving platform are used for carrying out harmful gas distribution and traceability detection in an airspace range; and harmful gas concentration data detected by the unmanned aerial vehicle at different positions and different heights are uploaded to the data receiving platform in real time, and on-site videos are transmitted in real time. Compared with a traditional ground station measurement mode, the measurement mode is improved from a plane to a three-dimensional mode, and the understanding of harmful gas distribution is greatly improved; by using the tablet electrochemical sensor, the weight of a detection device is greatly reduced, and the hang time of the unmanned aerial vehicle is favorably prolonged; and through construction of spatial vectors of harmful gas distribution, discovery and pre-judgment of harmful gas diffusion channels are greatly improved.
Owner:北京鑫康尔兴科技发展有限公司
Full-artificial-intelligence system based on multi-rotor unmanned aerial vehicle flight type nuclide identification instrument
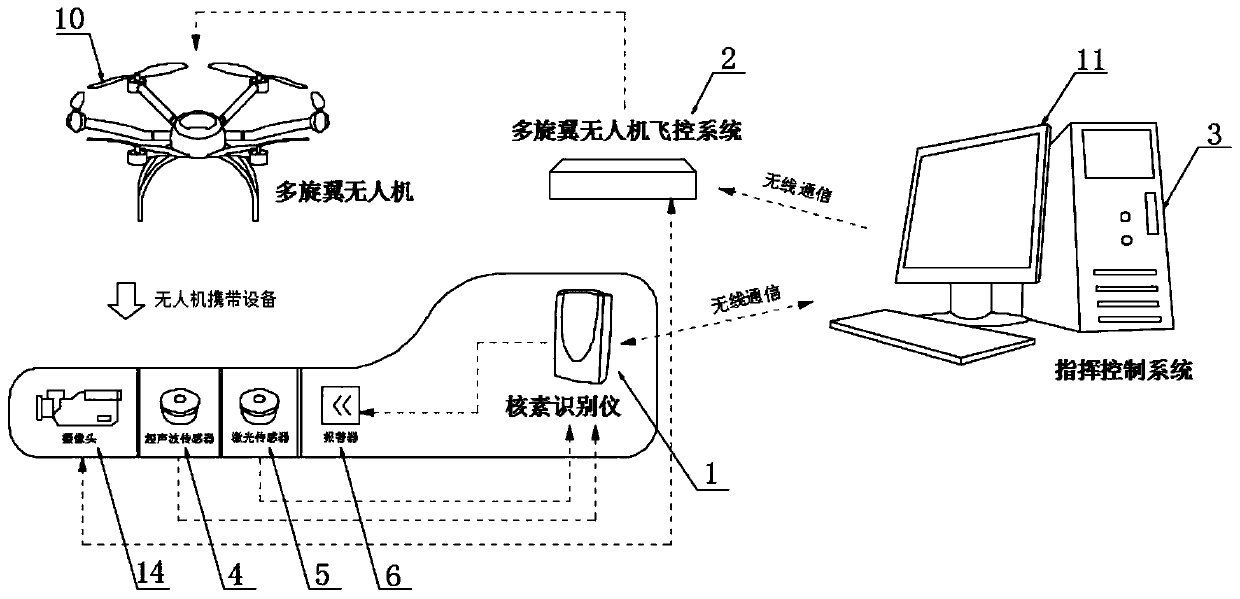
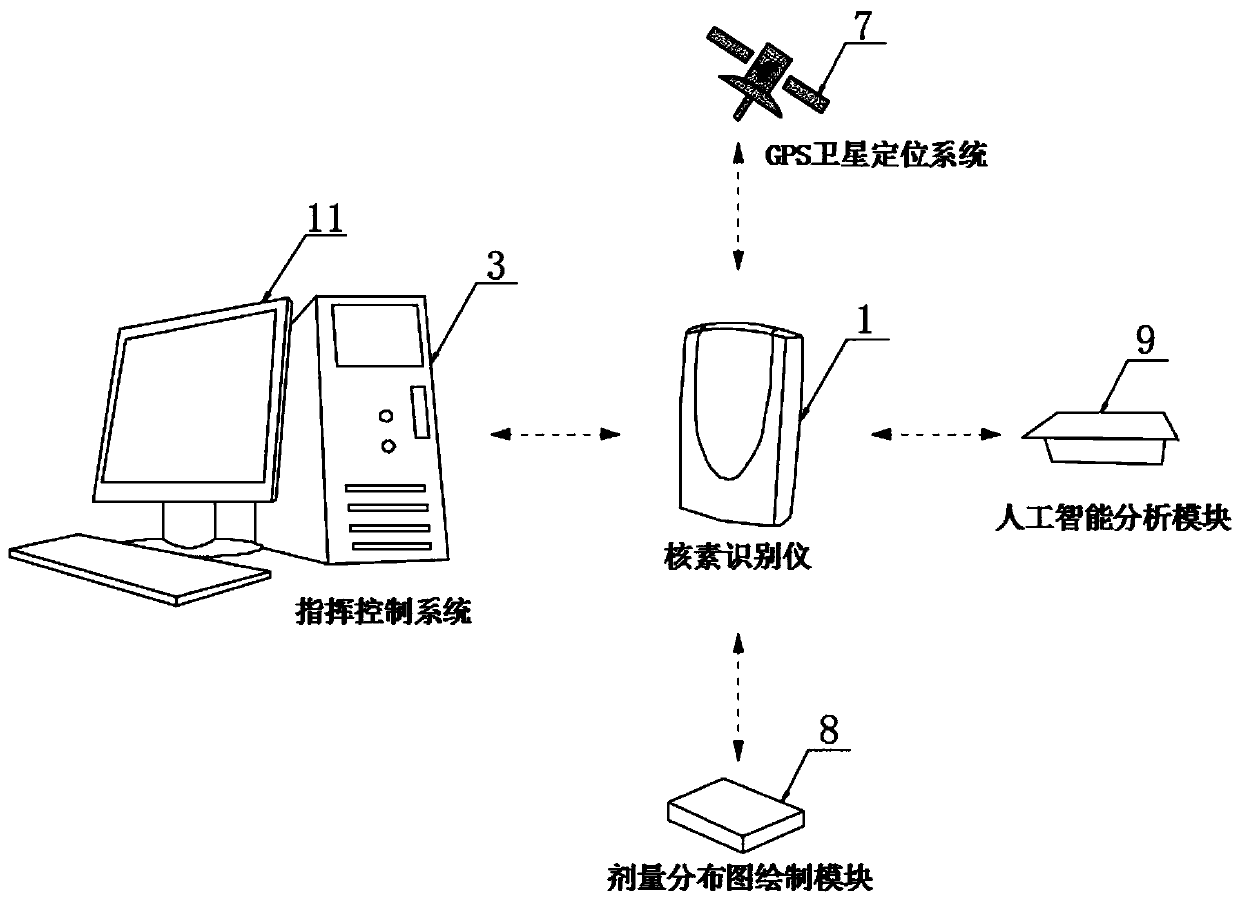
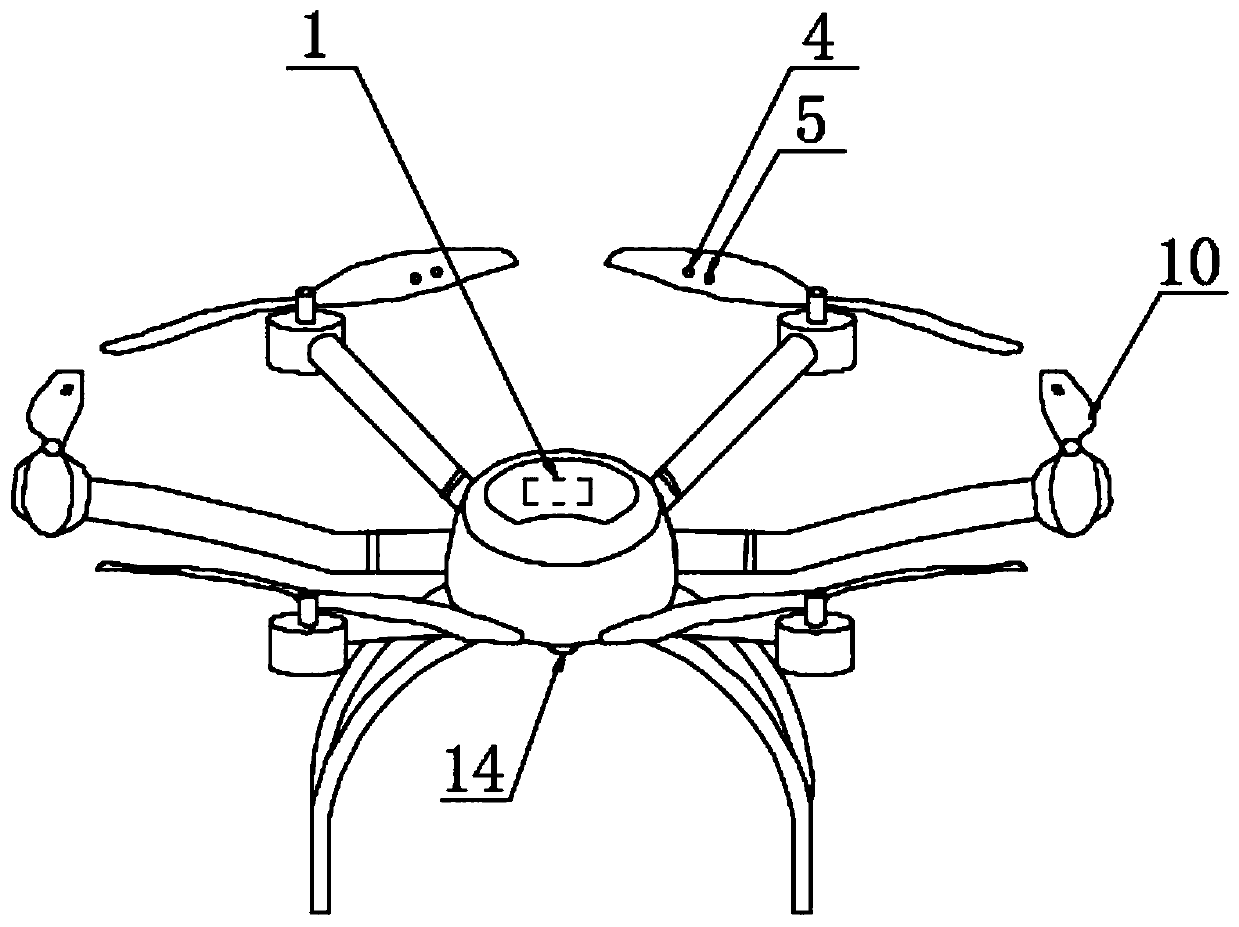
ActiveCN110554422AFully automatedRealize artificial intelligencePhotographic dosimetersClosed circuit television systemsUltrasonic sensorEngineering
The invention discloses a full-artificial-intelligence system based on a multi-rotor unmanned aerial vehicle flight type nuclide identification instrument, and relates to the field of nuclear industry. The system comprises the nuclide identification instrument, a multi-rotor unmanned aerial vehicle flight system and a command and control system, wherein the nuclide identification instrument and the multi-rotor unmanned aerial vehicle flight system are connected with the command and control system through a wireless communication module; the input end of the nuclide identification instrument isprovided with an ultrasonic sensor and a laser sensor; the output end of the nuclide identification instrument is provided with an alarm; and the connecting end of the nuclide identification instrument is connected with a camera, a GPS satellite positioning system, a metering distribution diagram drawing module and an artificial intelligence analysis module. The invention provides the multi-rotorunmanned radiographic surveying and mapping and nuclide identification scheme which is unmanned, of a full-artificial-intelligence type and safe in the true sense, the labor cost and the risk of manual misoperation are greatly reduced, the full-artificial-intelligence system is convenient, simple and efficient, and a radiographic surveying and mapping result and a nuclide identification result can be obtained at the first time.
Owner:INST OF RADIATION MEDICINE CHINESE ACADEMY OF MEDICAL SCI +2
Method of setting scanning threshold based on circuit design figure
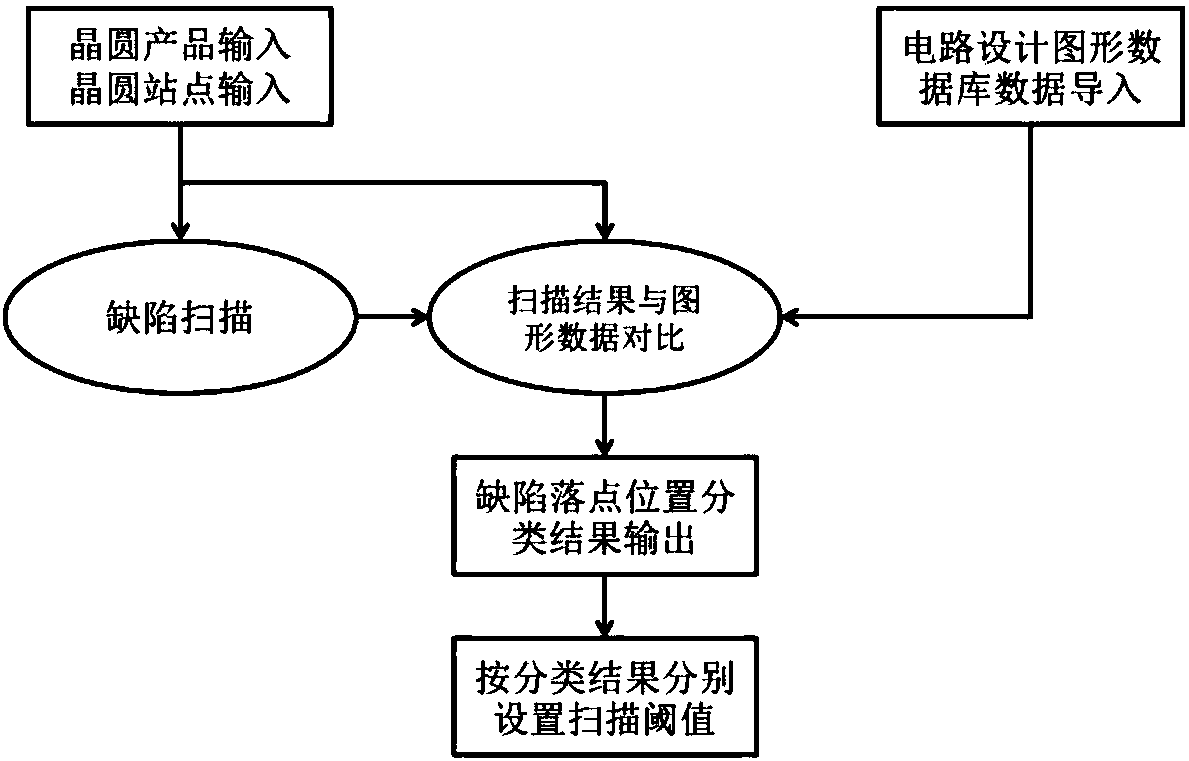
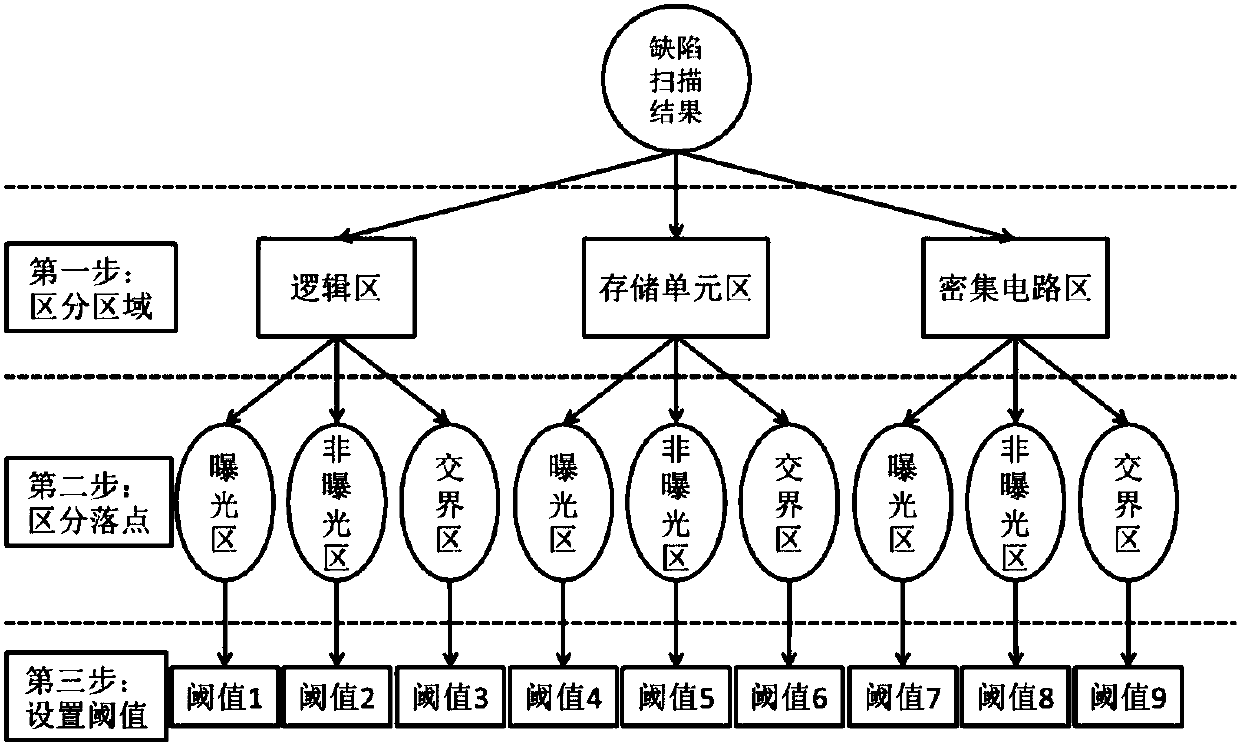
ActiveCN108039326AEffective distinctionImprove filtering effectImage enhancementImage analysisGraphicsComputer module
The invention discloses a method of setting a scanning threshold based on a circuit design figure. A processing module containing a circuit design figure database is added to an optical detection stock; through comparing a digital grayscale image obtained by a scanning part and a circuit design figure of the coordinate size of the extracted digital grayscale image in the circuit design figure database, the module divides a falling position of a defect signal point; and after scanning, the defect signal points obtained through scanning are divided to three different types according to falling at an exposure position, falling at non-exposure positions and falling at junction positions between exposure and non-exposure, and scanning threshold parameters are set respectively. The number of signals with front-station defects in scanning can be reduced, and the non-real defect rate of defect scanning is thus reduced.
Owner:SHANGHAI HUALI MICROELECTRONICS CORP
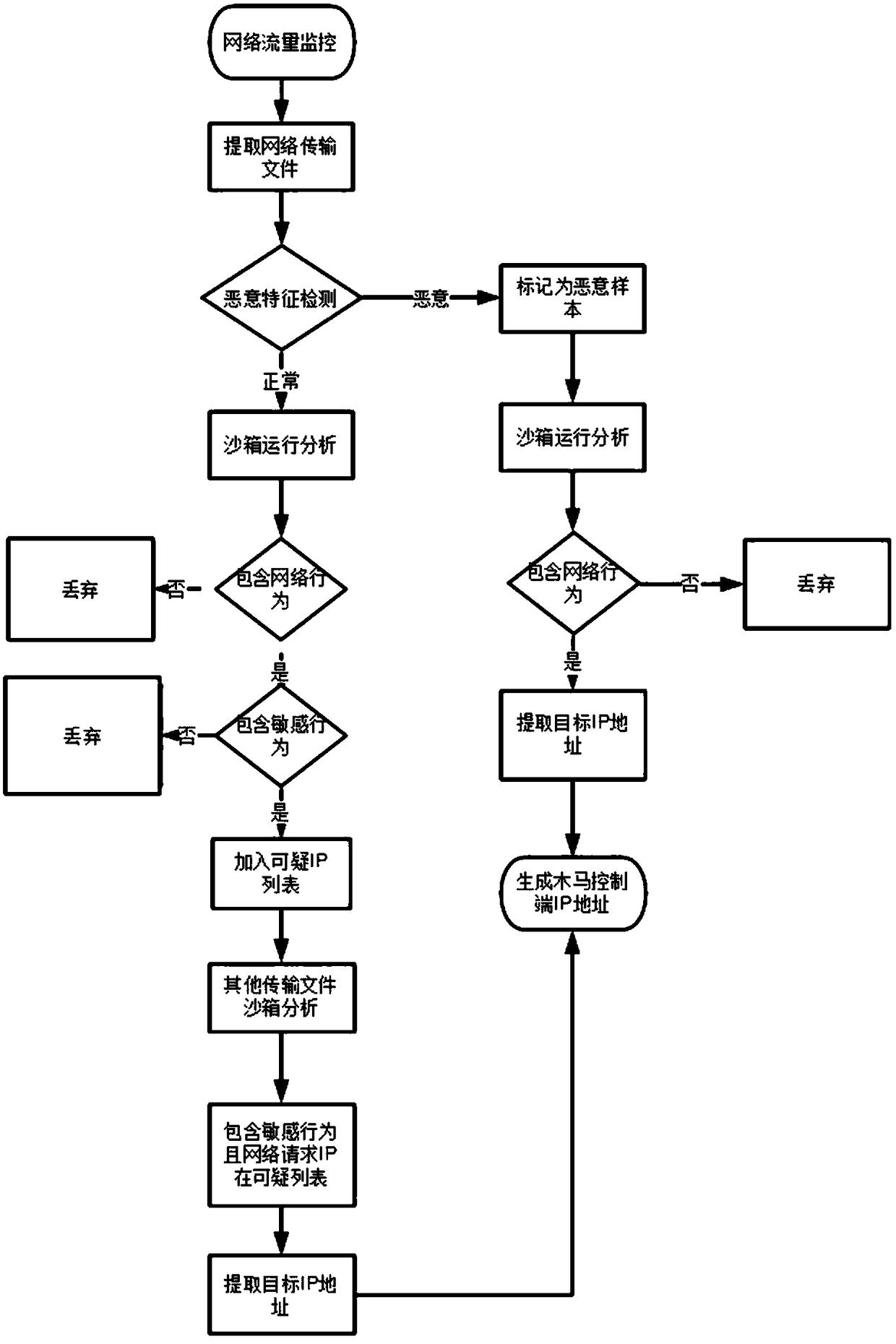
Method and system for obtaining IP address of trojan horse control terminal based on self-learning mode
ActiveCN109274676AComprehensive detection effectImplement extractionTransmissionTraffic capacityIp address
The invention relates to network security, aiming at providing a method and a system for acquiring IP address of a Trojan horse control terminal based on a self-learning mode. The method and the system for obtaining the IP address of the Trojan horse control terminal based on the self-learning mode are realized through the following steps: extracting the files transmitted in the network traffic and analyzing the files; extracting the IP address of the malicious Trojan horse control terminal and marking suspicious IP; continuously monitoring the network traffic of the protected host and the transmitted files, and marking the malicious target IP address; Malicious target IP address and malicious Trojan horse control IP address are Trojan horse control IP address. The invention utilizes network flow analysis and continuous monitoring to analyze the behavior of the Trojan horse by using sandbox technology, and utilizes self-learning mode to continuously improve the detection capability ofthe Trojan horse control end IP, thereby realizing automatic identification and extraction of the IP address of the Trojan horse control end server.
Owner:HANGZHOU ANHENG INFORMATION TECH CO LTD
Control system and method of ground walking robot for routing inspection of power machine room
InactiveCN108319265AImprove discoveryEnsure safe, reliable and efficient operationPosition/course control in two dimensionsWork statusPower equipment
The invention discloses a control system and method of a ground walking robot for routing inspection of a power machine room. The system is composed of a ground walking control system, a cloud platform lifting control system, a routing inspection information collecting system, a power supply system, an alarm system, an industrial control host and a remote control platform. Therefore, the working states of equipment in a power machine room can be detected and collected accurately, collected information is transmitted to a control center immediately, and the internal environment data of the machine room are monitored in real time, so that automatic routing inspection, key area routing inspection, and remote control routing inspection are realized; the potential safety hazard in equipment canbe discovered timely; various linked alarming is carried out; the discovery capability of the potential safety hazards of the equipment is improved effectively; and thus the power equipment in the machine room can work safely, reliably, and efficiently.
Owner:SHANXI DIMAI WOKE PHOTOELECTRIC IND CO LTD
Reputation system-oriented collusion attack fuzzy detection method in social network
ActiveCN105809032AImprove detection success rateHigh precisionPlatform integrity maintainanceTrust relationshipSocial web
The invention relates to a reputation system-oriented collusion attack fuzzy detection method in a social network. The method comprises following steps of 1), determining reputations of users and the trust relationships among the users; 2), determining whether there is at least one malicious user according to evaluation differences of the users to items; executing a step 3) when there is the malicious user; 3), through taking the obtained malicious user as a detection start point, traversing the users in the social network; and determining whether other users are the collusion attackers of the malicious user or not according to the trust relationships and the reputation similarity levels of the other users and the malicious user. Compared with the prior art, the method has the advantages that the collusion attackers are found out more accurately according to the social relationships, and the detection success rate of the collusion attacks is improved.
Owner:SHANGHAI NORMAL UNIVERSITY +1
Article recommendation method and device, short video recommendation method and device and server
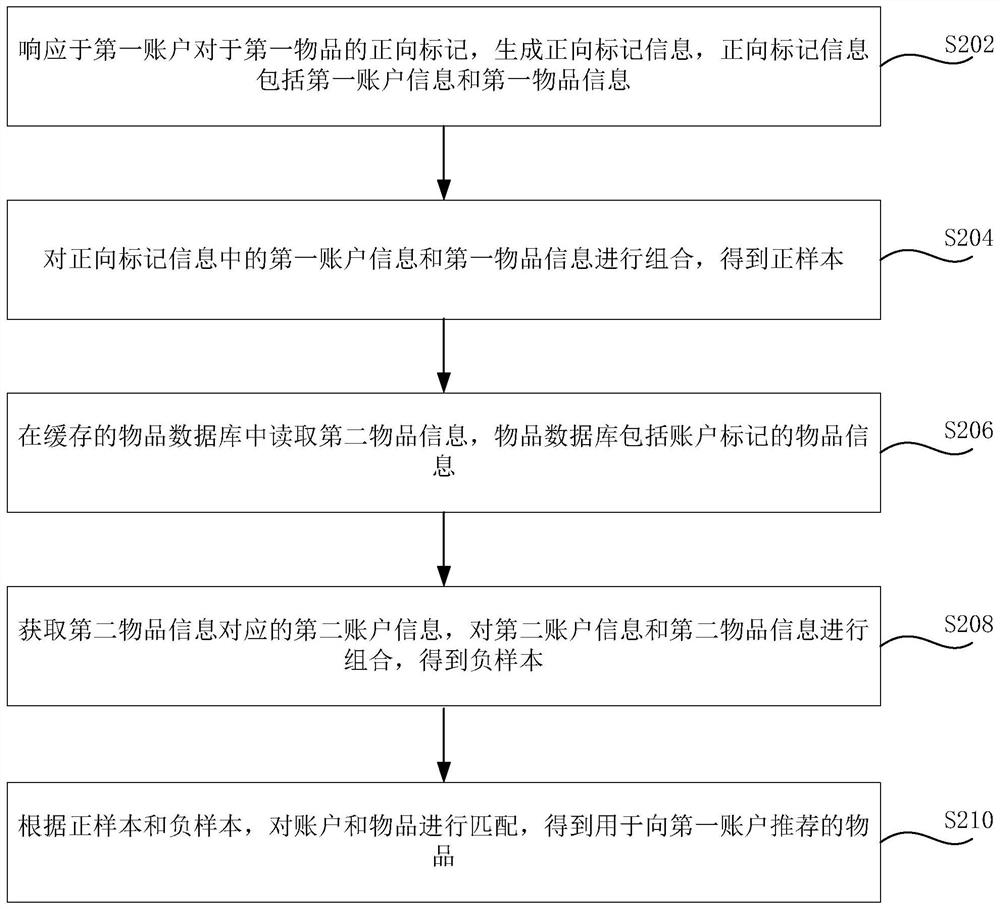
PendingCN113495985AAddress data biasImprove discoverabilityDigital data information retrievalSpecial data processing applicationsData scienceData library
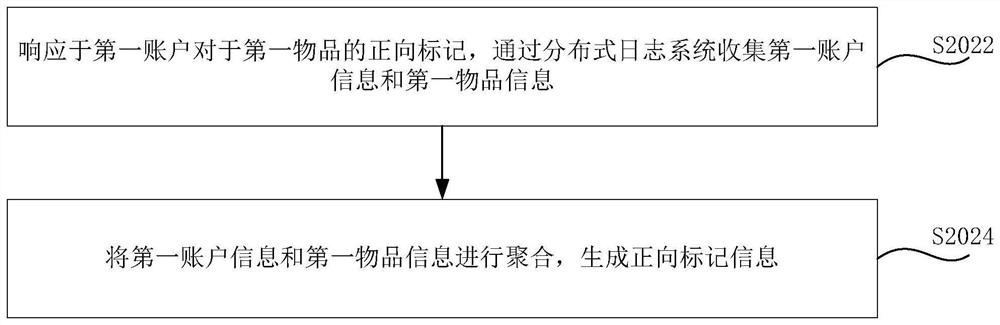
The invention relates to an article recommendation method and device, a short video recommendation method and device and a server. The article recommendation method comprises the steps: in response to a forward mark of a first account for a first article, generating forward mark information, wherein the forward mark information comprises first account information and first article information; combining the first account information and the first article information in the forward mark information to obtain a positive sample; reading the second article information in a cached article database, wherein the article database comprises the article information marked by the account; obtaining second account information corresponding to the second article information, and combining the second account information and the second article information to obtain a negative sample; and matching the account and the article according to the positive sample and the negative sample to obtain the article recommended to the first account. The problem of data deviation can be effectively solved, the user can be well helped to discover potential interest points, and the object recommendation effect is improved by improving the discoverability of the recommendation result.
Owner:BEIJING DAJIA INTERNET INFORMATION TECH CO LTD
NLP knowledge graph construction method combining information amount and BERT-BiLSTM-CRF
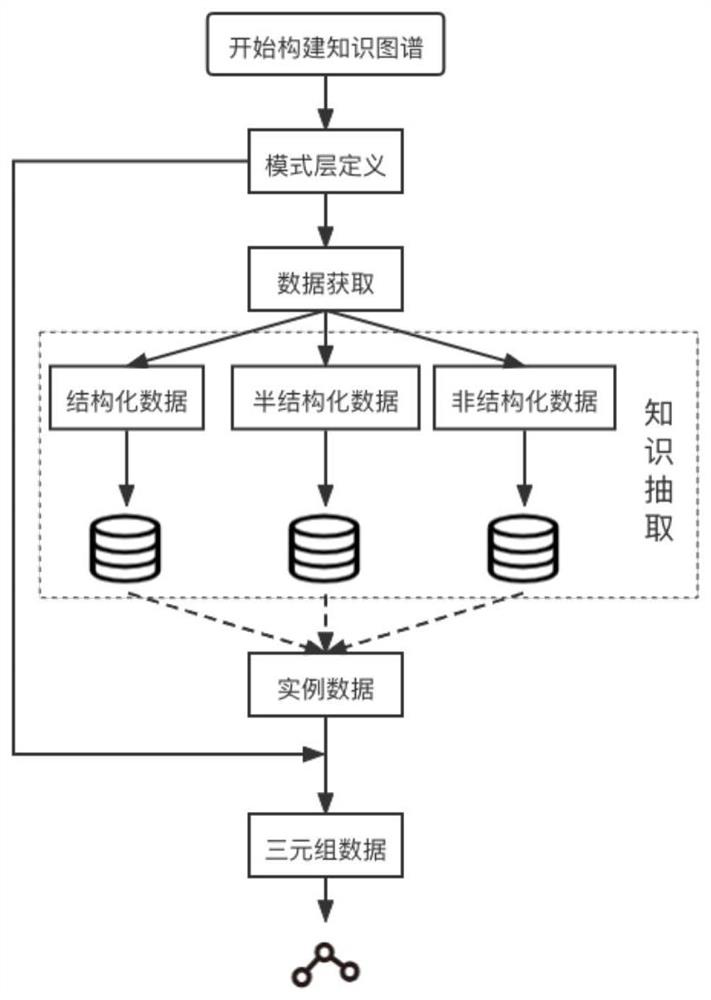
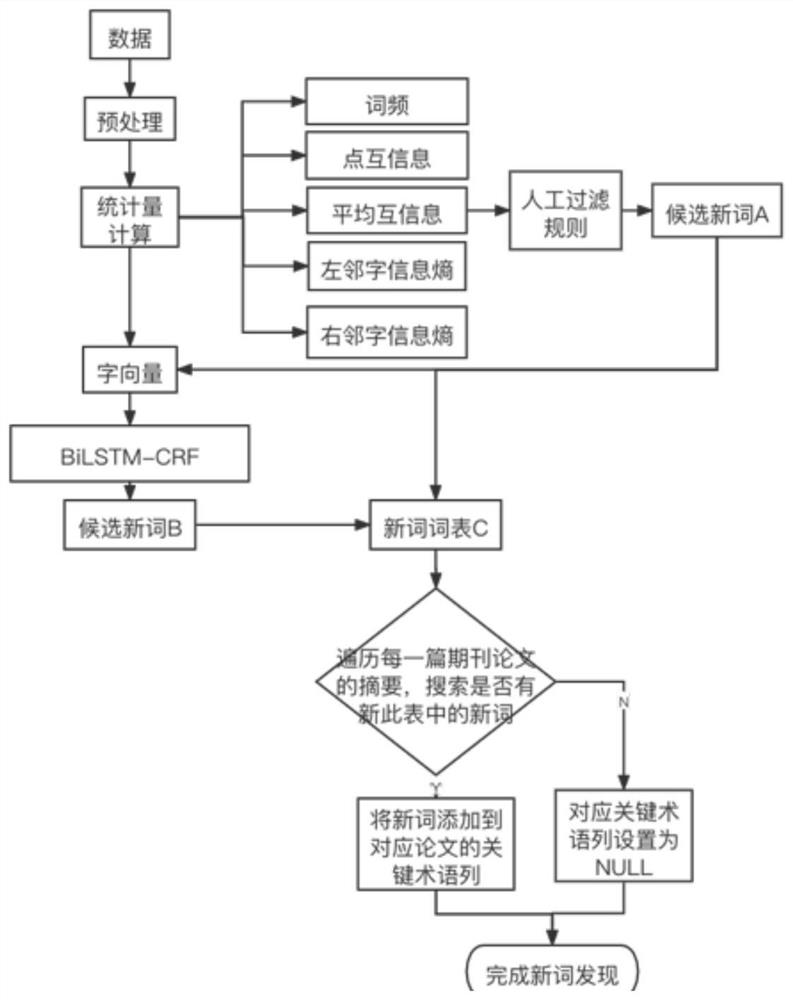
PendingCN114817454AImprove discoveryAccurate identificationMachine learningText database queryingGranularityRecognition algorithm
The invention discloses an NLP knowledge graph construction method combining information amount and BERT-BiLSTM-CRF. The method comprises the following steps: providing a mode layer structure of a knowledge graph in the field of natural language processing by analyzing the structure of knowledge network journal paper data and combining a research task of natural language processing; a key term entity class in paper data is obtained by proposing a new word discovery algorithm, and a fine-grained NLP research task entity class of the paper is obtained by proposing a feature fusion multi-classification algorithm; and then the knowledge extraction module obtains the triple, and finally the natural language processing knowledge graph is constructed. According to the new word recognition algorithm, the defect that in the prior art, only information is used for obtaining new words is overcome, and the new word discovery effect is greatly improved. Compared with other machine learning models, classification of paper fine granularity research tasks by using the XGBoost model has higher accuracy, and in addition, through feature fusion, the accuracy of the classification model is improved by about five percent compared with the classification accuracy of a model without feature fusion.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Wireless optical communication neighbor discovery system and method for underwater multi-robot formation
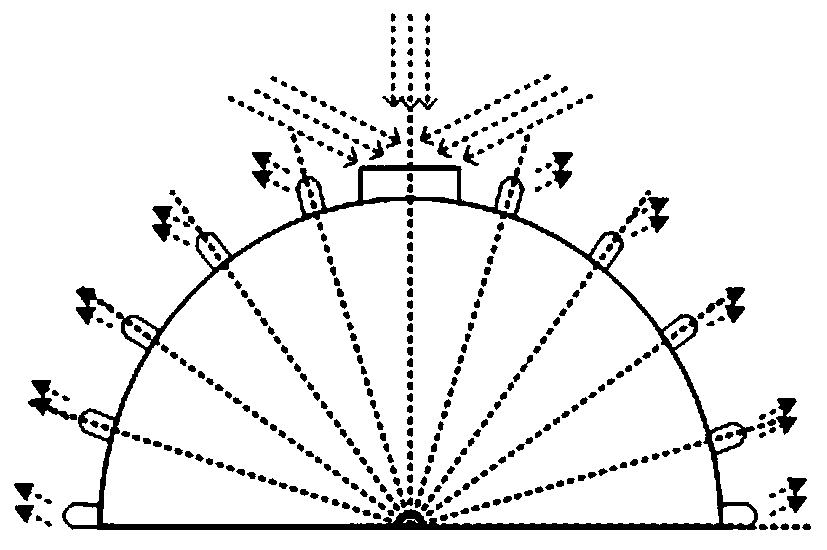
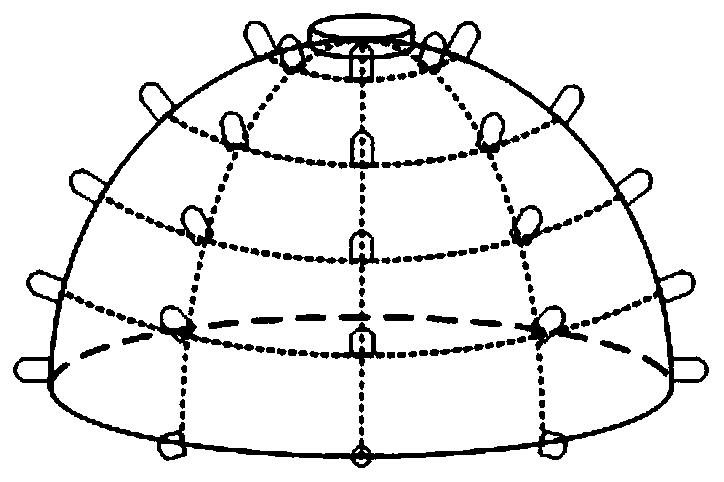
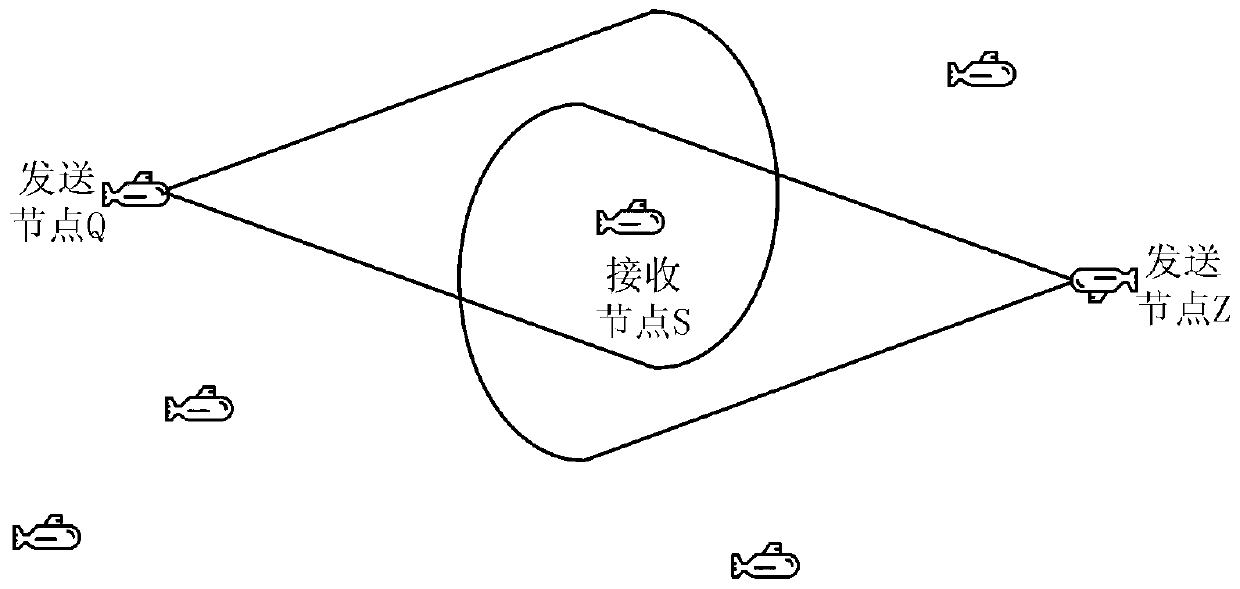
ActiveCN110380782AFind quick successExpand the transmission rangeClose-range type systemsRadio-over-fibreComputer networkUnderwater
A wireless optical communication neighbor discovery system for underwater multi-robot formation comprises light source LEDs which are arranged on the surface of a hemisphere in the longitude and latitude directions. An omnidirectional receiver is mounted at the top of the hemisphere to form a node structure, and each node can independently send messages. A wireless optical communication neighbor discovery method for an underwater multi-robot formation comprises the following steps: selecting K nodes to hold tokens; the node with the token sending a request information frame; after the requestinformation frame is received, sending, by the neighbor node, a response information frame; after the token holding node sends the request information frame, starting a timer T1, and determining arrival information; starting a timer T2 after the neighbor node sends the response information frame, and determining confirmation information; if the response information is not received, ending the discovery; if the response information is received, sending an acknowledgement information frame; after the neighbor discovery of the token holding node is completed, transmitting the token to the neighbor node; and completing neighbor discovery. The transmission range is relatively long, the data rate is relatively high, the anti-interference performance is strong, and the energy consumption is low.
Owner:XIAN UNIV OF TECH
Online monitoring device for lightning arrester
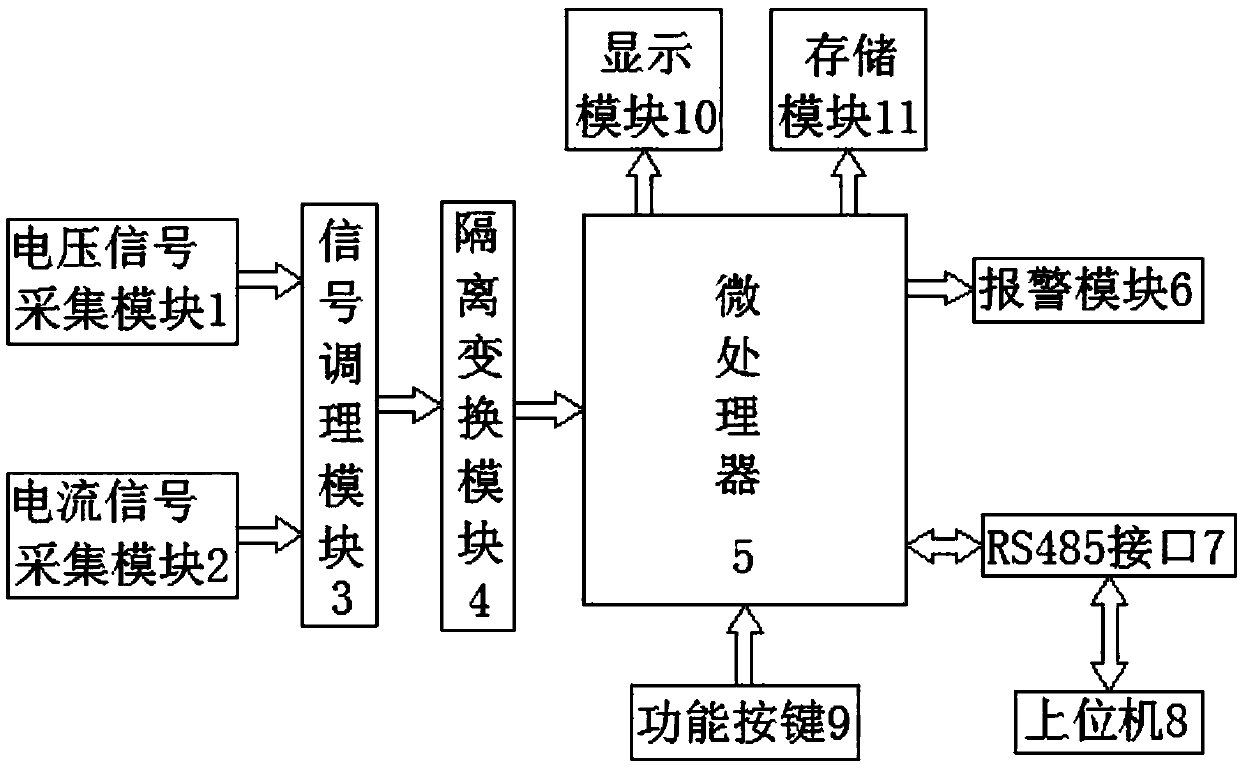
InactiveCN105954634ARealize online monitoringImprove the efficiency of troubleshooting fault pointsElectrical testingPower flowSignal conditioning
The invention discloses an online monitoring device for a lightning arrester. The online monitoring device comprises a voltage signal collecting module, a current signal collecting module, a signal conditioning module and a microprocessor. The output ends of the voltage signal collecting module and the current signal collecting module are connected to the input end of the signal conditioning module. The input end of the microprocessor is connected with an isolation conversion module and a functional key. The output end of the microprocessor is connected with an alarm module, a display module and a storage module. The output end of the signal conditioning module is connected to the isolation conversion module. Due to the arrangement of the voltage signal collecting module and the current signal collecting module, online detection of a lightning arrester is achieved; collected signals are processed to be monitoring data and stored through the microprocessor, and injury is convenient; alarm prompts are performed through the alarm module, and the efficiency for finding and removing faults is improved; monitored data are displayed in real time through the display module, and the efficiency of investigating faults is improved; remote monitoring is achieved through the upper computer, and the working efficiency is improved.
Owner:安徽亚辉电气自动化有限公司
Method and system for judging waterlogging ponding depth of scene
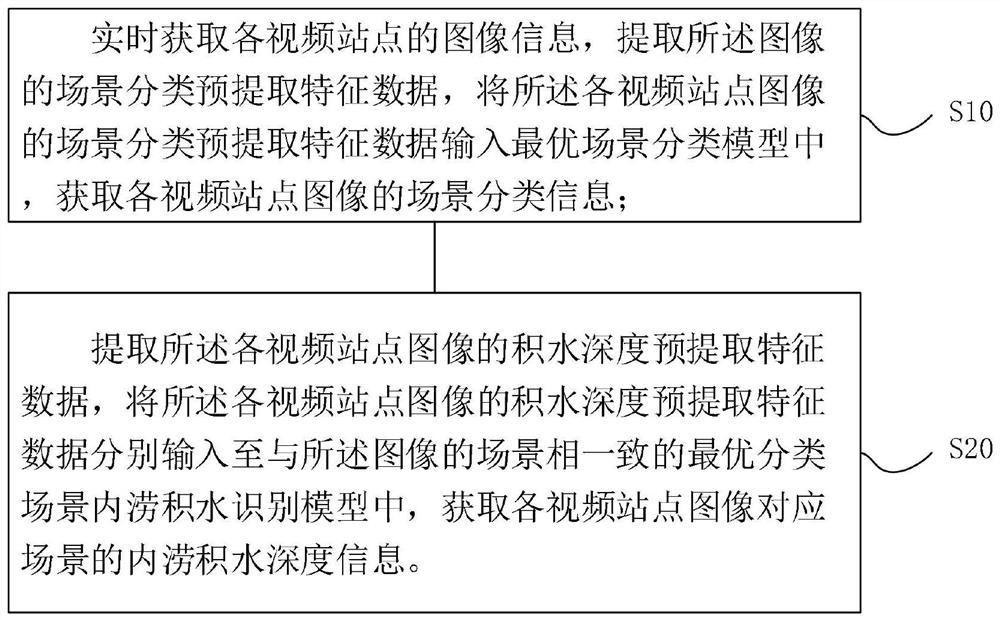
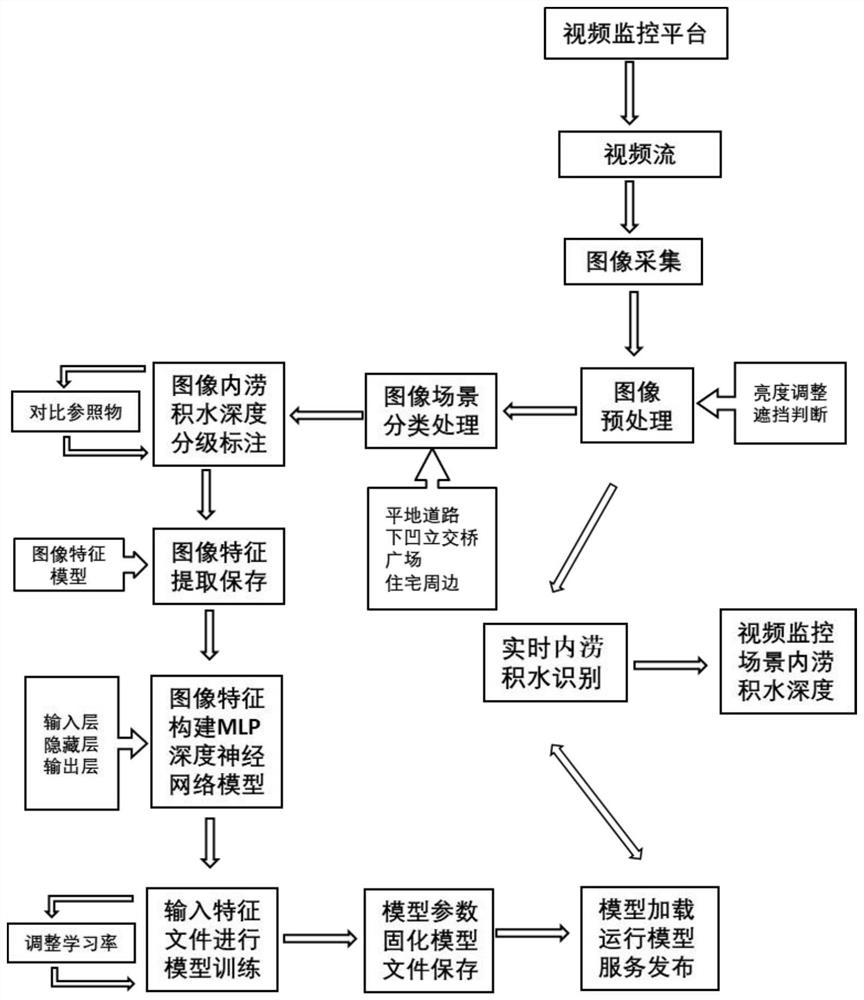
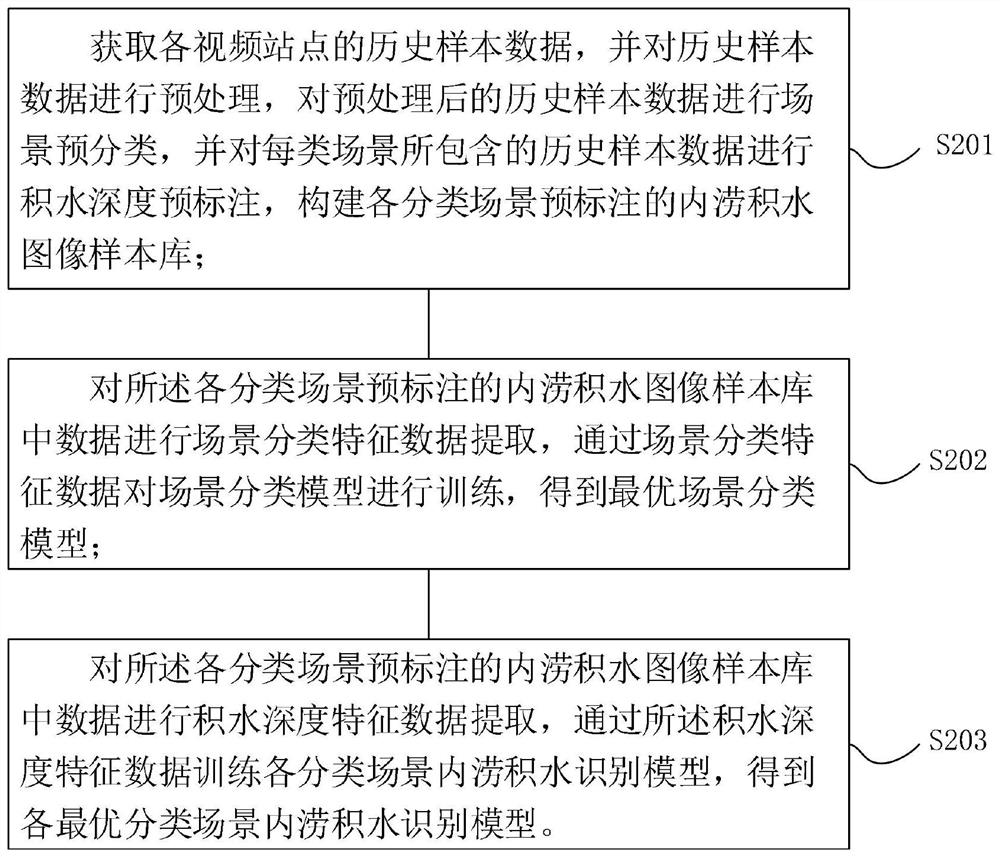
ActiveCN114663827AReal-time automatic identification and judgmentImprove recognition accuracyImage enhancementImage analysisVideo monitoringRadiology
The invention relates to a method and system for judging the waterlogging depth of a scene, belongs to the technical field of artificial intelligence image recognition, and solves the problems that in the prior art, the waterlogging depth cannot be effectively recognized according to historical data, and waterlogging depth auxiliary measurement equipment has high requirements for the environment, the angle of video monitoring equipment, illumination and shielding, and the waterlogging depth cannot be effectively recognized. And normal work is difficult in complex scenes such as rainstorm. The method comprises the following steps: acquiring image information of each video site in real time, extracting scene classification pre-extraction feature data, inputting the scene classification pre-extraction feature data of each video site image into an optimal scene classification model, and acquiring scene classification information of each video site image; and extracting waterlogging depth pre-extraction feature data of each video site image, respectively inputting the waterlogging depth pre-extraction feature data of each video site image into the optimal classification scene waterlogging identification model consistent with the scene of the image, and obtaining waterlogging depth information of the scene corresponding to each video site image.
Owner:北京慧图科技(集团)股份有限公司
Word bank updating method and device and electronic equipment
PendingCN111325019AData Quality BalanceDiscovery effect and efficiency improvementDigital data information retrievalNatural language data processingEngineeringLexicon
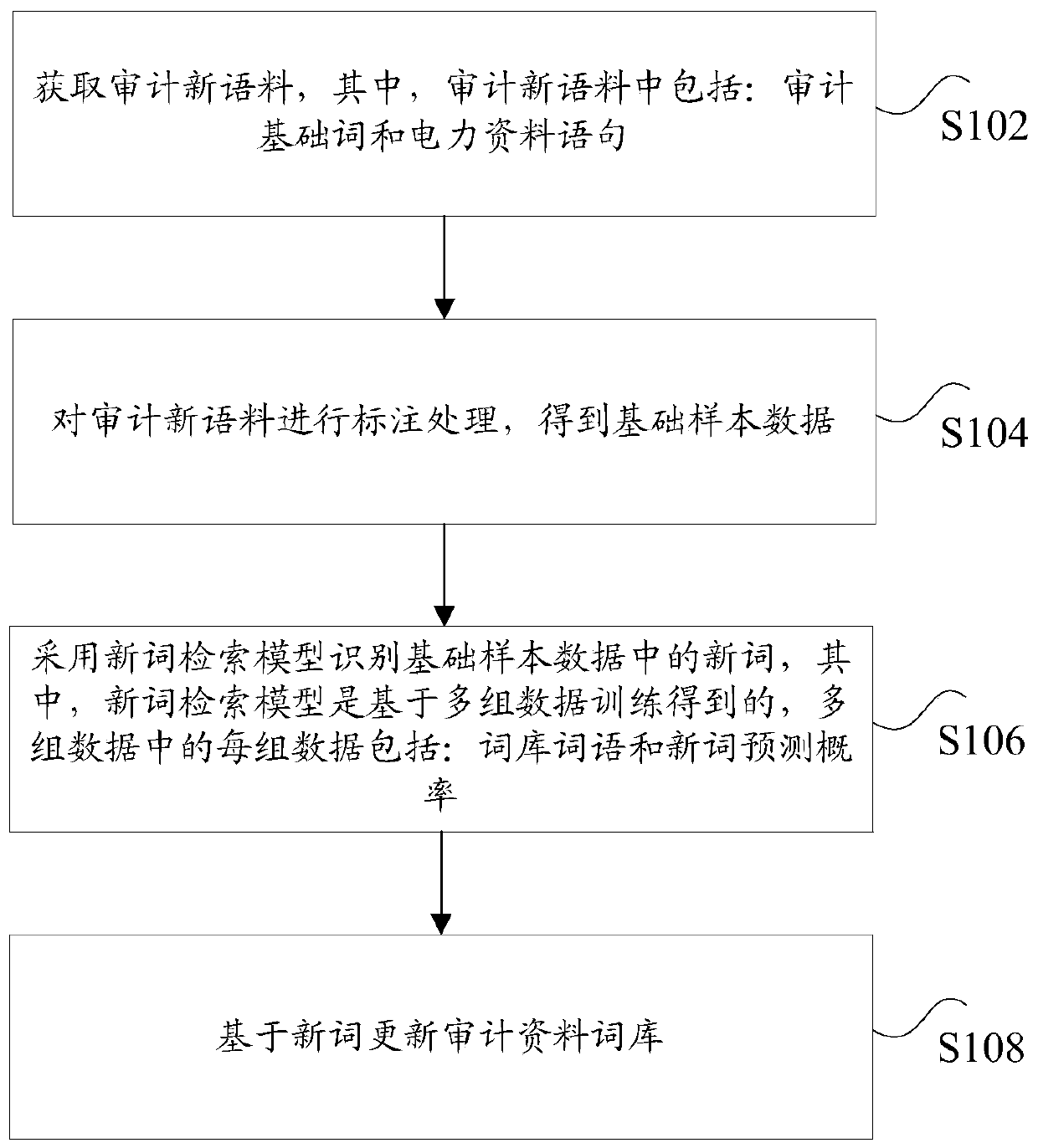
The invention discloses a lexicon updating method and device and electronic equipment. The method comprises the steps that audit new corpora are acquired, and the audit new corpora comprise audit basic words and electric power data statements; labeling the audit new corpus to obtain basic sample data; a new word retrieval model is adopted to identify new words in the basic sample data, the new word retrieval model is obtained on the basis of training of multiple sets of data, and each set of data in the multiple sets of data comprises lexicon words and new word prediction probabilities; and updating the audit data lexicon based on the new words. According to the method and the device, the technical problems of unbalanced data quality and incomplete data of a term database due to the fact that professional terms are easy to miss when corpora are extracted in related technologies are solved.
Owner:STATE GRID BEIJING ELECTRIC POWER +2
A Surface Wave In-Situ Flaw Detection Method for Coated Rotor Blades
InactiveCN103063742BImprove discoveryAccurate scanning of small defectsAnalysing solids using sonic/ultrasonic/infrasonic wavesEngineeringSurface wave
The invention relates to a surface wave in-situ flaw detection method of a rotor blade with a coating. The invention belongs to the technical field of aircraft engine, and is mainly used in surface wave in-situ detection of aircraft engine rotor blades with coatings. With the method provided by the invention, coating thickness influence can be sufficiently excluded, and discovery capability of tiny defects on blade surface and near-surface can be improved. The method comprises the steps that: an ultrasonic flaw detector is started, and a surface wave probe is connected to the ultrasonic flaw detector; a positioning fixture is placed on a blade contrast sample with artificial flaw, and sensitivity is checked; the positioning fixture is fetched from the blade contrast sample, and is placed on a blade requiring flaw detection; the surface wave probe is moved from outside to inside along a slot of the positioning fixture, and is swung left and right, until the probe reaches a slot limit end, such that blade scanning is finished; when blade scanning is finished, the positioning fixture is removed, and an coupling agent on the blade is wiped off; and the other blades are scanned one by one with the same method.
Owner:SHENYANG LIMING AERO-ENGINE GROUP CORPORATION
Power plant ultrafiltration membrane integrity online diagnosis device and control method thereof
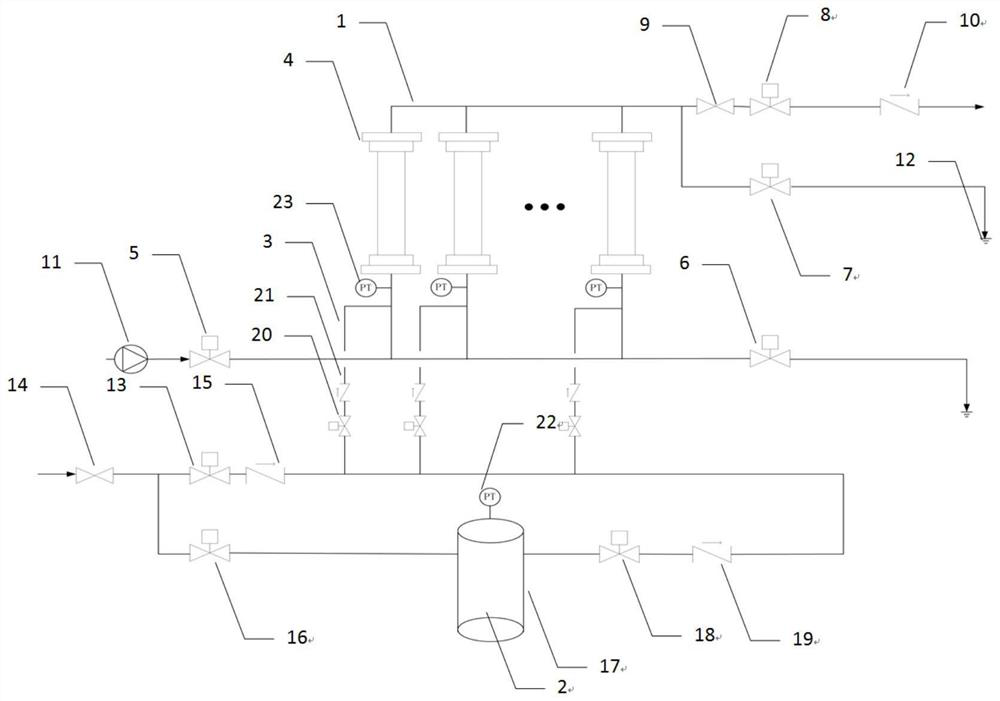
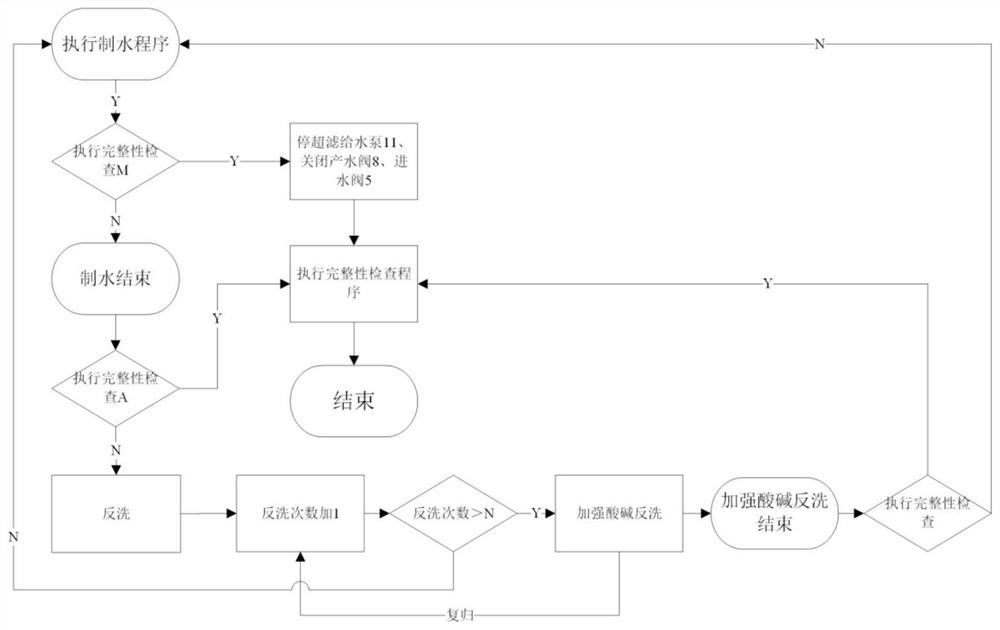
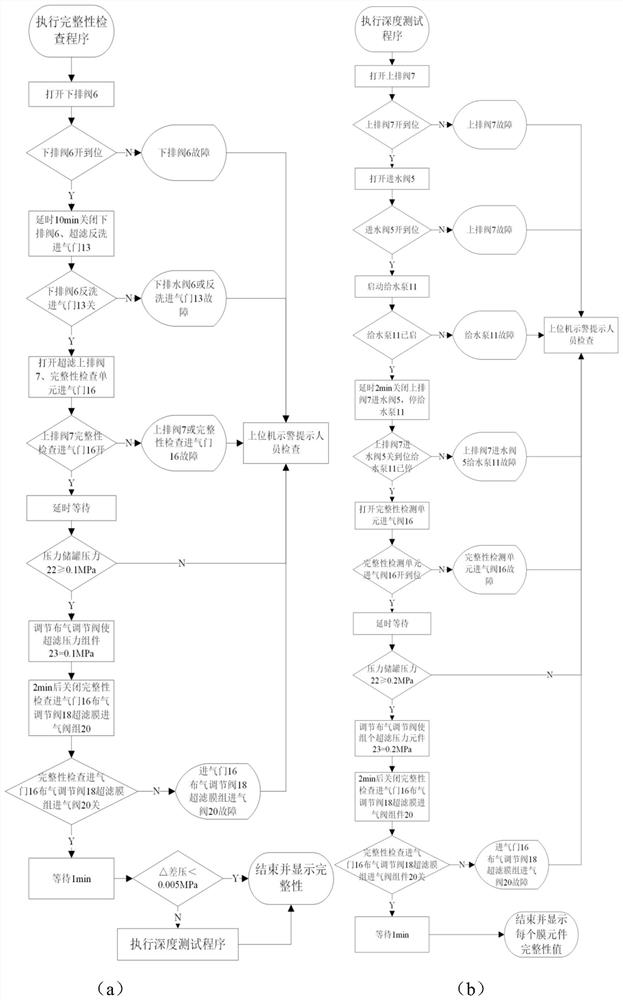
PendingCN112429811AImprove operating economyImprove securityWater treatment parameter controlWater/sewage treatment bu osmosis/dialysisIsolation valvePower station
The invention discloses a power plant ultrafiltration membrane integrity online diagnosis device and a control method thereof. The device comprises an ultrafiltration membrane device unit, an integrity detection unit and a control unit, wherein the ultrafiltration membrane device unit comprises an ultrafiltration membrane assembly, an ultrafiltration system water inlet valve is connected with an ultrafiltration membrane assembly inlet and an ultrafiltration system lower discharge valve, an ultrafiltration membrane assembly outlet is divided into two paths, one path is connected with an ultrafiltration system water production manual valve, and the other path is connected with an ultrafiltration system upper discharge valve; the integrity detection unit comprises an ultrafiltration air inletvalve manual isolation valve, an outlet of the ultrafiltration air inlet valve manual isolation valve is divided into two paths, one path is connected with an ultrafiltration membrane assembly air inlet valve set through an ultrafiltration air inlet valve, and the other path is connected with an ultrafiltration membrane assembly inlet. According to the invention, the stability of water quality can be powerfully guaranteed, the operation economy and safety of a unit are improved, the influence caused by the use of ultrafiltration membrane equipment, especially the aging of the equipment or thedamage of the equipment after the continuous water backwashing gas washing process, is reduced, the discovery and diagnosis of fault problems are improved, and the hysteresis quality and randomness are reduced.
Owner:XIAN THERMAL POWER RES INST CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com